Third-Party researchers released micropatch for recently disclosed Windows Zero-Day
2.9.18 securityaffairs Vulnerebility
Security researchers from the opatch community released a micropatch for the recently disclosed Windows zero-day vulnerability.
A few days ago, the security researcher who handles the Twitter account @SandboxEscaper has disclosed the details of zero-day privilege escalation vulnerability affecting Microsoft’s Windows operating systems that could be exploited by a local attacker or malicious program to obtain system privileges on the vulnerable system.
The vulnerability resides in the Windows’ task scheduler program and ties to errors in the handling of Advanced Local Procedure Call (ALPC) systems.
Microsoft is expected to address the vulnerability in September security Patch Tuesday, that is scheduled for September 11, meantime a patch was released by 0patch, a community of experts that aims at addressing software flaws.
The community is known to develop tiny patches, usually less than 30 bytes in size, it released a fix within 24 hours after the public disclosure of the issue.
The fix for the Windows zero-day recently disclosed is only 13 bytes in size.
Experts explained that they have validated and verified the micropatch for @SandboxEscaper’s LPE in Task Scheduler.
It currently works only to fully updated 64bit Windows 10 1803.
0patch
@0patch
· Aug 29, 18
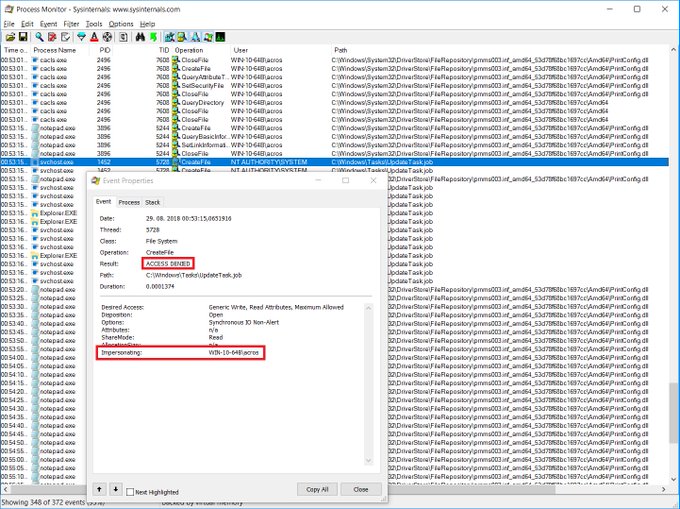
Okay people, 24 hours after the 0day was published we have a micropatch candidate for @SandboxEscaper's LPE in Task Scheduler. As you can see, scheduler's access to user-controlled hardlink is impersonating the user and gets ACCESS DENIED. pic.twitter.com/3kHcXdY42H
0patch
@0patch
Validated and verified, our micropatch for @SandboxEscaper's LPE in Task Scheduler is now published and freely available for everyone to use. It currently applies only to fully updated 64bit Windows 10 1803. We welcome requests for ports to other versions at support@0patch.com. pic.twitter.com/9pNufwUehU
2:19 PM - Aug 30, 18
45
40 people are talking about this
Twitter Ads info and privacy
2:19 PM – Aug 30, 18
View image on Twitter
“As the researcher’s POC demonstrates, one can use this vulnerability to replace a system executable file and wait for a privileged process to execute it. In particular, it was shown that a printing-related DLL could be replaced and then executed by triggering the Print Spooler Service to load it,” reads the analysis published by 0patch.
“SandboxEscaper’s documentation properly identifies the problem being in Task Scheduler’s SchRpcSetSecurity method, which is externally accessible via Advanced Local Procedure Call (ALPC)facility. “
This is just a temporary fix, Windows users are advised to apply the official Microsoft updates as soon as one becomes available.
0patch warns of unexpected errors that could be caused by the unofficial fix they released.
“Can we keep using this micropatch instead of applying Microsoft’s update?
We strongly recommend against that. Microsoft’s update will not only fix this issue in a more informed way, but will also bring fixes for other vulnerabilities that we don’t have micropatches for. Yes, we hate losing hours of our lives to updating our systems too, but wouldn’t dream of outright replacing official updates with our micropatches 😉 ” concludes oparch.