
USB Drives Deliver Dangerous Malware to Industrial Facilities: Honeywell
2.11.2018 securityweek Virus

Malware is still being delivered to industrial facilities via USB removable storage devices and some threats can cause significant disruptions, according to a report published on Thursday by Honeywell.
The industrial giant last year launched SMX, a product designed to protect facilities from USB-born threats, and the company has also been using it to determine the risk posed by USB drives to such organizations.
Honeywell has analyzed data collected from 50 locations across the United States, South America, Europe and the Middle East. The enterprises whose systems were part of the study represented the energy, oil and gas, chemical manufacturing, pulp and paper, and other sectors.
Honeywell said its product had blocked at least one suspicious file in 44% of the analyzed locations. Of the neutralized threats, 26% could have caused major disruptions to industrial control systems (ICS), including loss of control or loss of view.
Furthermore, Honeywell says 16% of the detected malware samples were specifically designed to target ICS or IoT systems, and 15% of the samples belonged to high profile families such as Mirai (6%), Stuxnet (2%), Triton (2%), and WannaCry (1%).
“These findings are worrisome for several reasons. That high-potency threats were at all prevalent on USB drives bound for industrial control facility use is the first concern. As ICS security experts are well aware, it only takes one instance of malware bypassing security defenses to rapidly execute a successful, widespread attack,” Honeywell said in its report. “Second, the findings also confirm that such threats do exist in the wild, as the high-potency malware was detected among day-to-day routine traffic, not pure research labs or test environments. Finally, as historical trends have shown, newly emerging threat techniques such as TRITON, which target Safety Instrumented Systems, can provoke copycat attackers.”
Learn More About Malware in Industrial Networks at SecurityWeek’s ICS Cyber Security Conference
It’s not uncommon for malware to make its way onto industrial networks and – as shown by previous studies – in a majority of cases these are non-targeted threats. Honeywell’s analysis confirms this, with only few incidents involving malware specifically targeted at industrial systems.
More than half of the threats found by Honeywell were Trojans (55%), followed by bots (11%), hacking tools (6%), and potentially unwanted applications (5%). One-third of samples had RAT functionality and 12% were capable of dropping other malware onto the compromised system. Seven percent of malicious files were hiding ransomware.
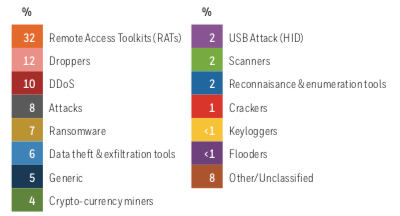
One noteworthy finding is that 9% of malware was designed to directly exploit flaws in the USB protocol or interface.
“Some went further, attacking the USB interface itself. 2% were associated with common Human Interface Device (HID) attacks, which trick the USB host controller into thinking there is a keyboard attached, allowing the malware to type commands and manipulate applications. This supports earlier Honeywell findings that confirmed HID attacks such as BadUSB as realistic threats to industrial operators,” Honeywell said.