What are botnets downloading?
5.9.2018 Kaspersky BotNet
Statistics for the past year on files downloaded by botnets
CONTENTS
Spam mailshots with links to malware and bots downloading other malware are just a couple of botnet deployment scenarios. The choice of infectious payload is limited only by the imagination of the botnet operator or customer. It might be a ransomware, a banker, a miner, a backdoor, the list goes on, and you don’t need to go far for examples: take Gandcrab and Trik, or Locky and Necurs, for instance. Every day we intercept numerous file-download commands sent to bots of various types and families. Here we present the results of our botnet activity analysis for H2 2017 and H1 2018.
Methodology
Excluded from the statistics are update files downloaded by bots, since their number depends heavily on the algorithm of the particular malware in question and has an impact on the final distribution. The analysis also excludes configuration files whose download depends on the botnet algorithm and is not relevant to this article. What’s more, we only took account of unique (in terms of MD5 hash) files. The results are based on the analysis of commands from more than 60,000 different C&C associated with 150 bot families and their modifications.
Kaspersky Lab tracks the activity of botnets using Botnet Tracking, a technology that emulates infected computers (bots) to retrieve operational data about the actions of botnet operators.
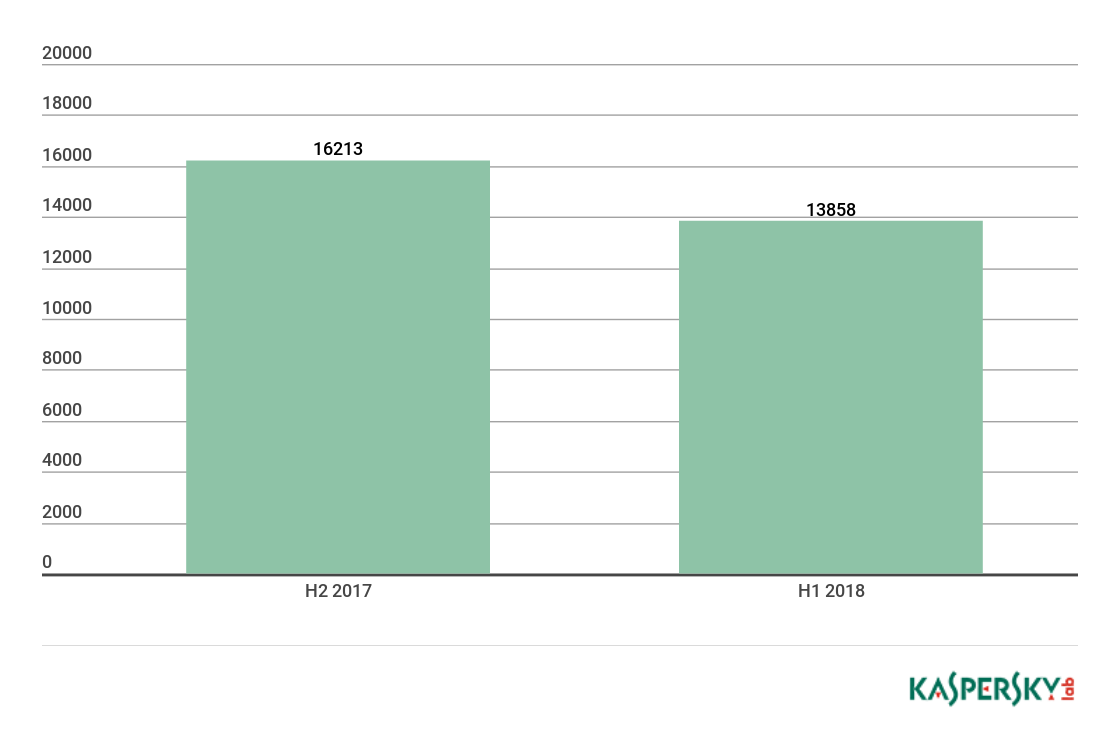
The total number of unique malicious files downloaded by our bots in H1 2018 fell by 14.5% against H2 2017.
Number of unique malicious files, H2 2017 — H1 2018 (download)
Most popular
After analyzing the files downloaded by the bots, we identified the most widespread families. Note that the top of the list of most “popular” downloads changes little over time. In 2018, as last year, the backdoor njRAT accounted for many downloads. Its share among all files downloaded by bots increased from 3.7% to 5.2%, meaning that more than 1 in each 20 bot-downloaded files is njRAT. This widespread distribution is due to the variety of versions of the malware and the ease of setting up one’s own backdoor, creating a low entry threshold.
H2 2017 Share H1 2018 Share
1 Lethic 17.0% njRAT 5.2%
2 Neutrino.POS 4.6% Lethic 5.0%
3 njRAT 3.7% Khalesi 4.9%
4 Emotet 3.5% Miners 4.6%
5 Miners 2.9% Neutrino.POS 2.2%
6 Smoke 1.8% Edur 1.3%
7 Cutwail 0.7% PassView 1.3%
8 Ransomware 0.7% Jimmy 1.1%
9 SpyEye 0.5% Gandcrab 1.1%
10 Snojan 0.3% Cutwail 1.1%
Most downloaded threats, H2 2017 — H1 2018
Very often, botnets are used to distribute cryptocurrency mining tools. In H1 2018 miners accounted for 4.6% of all downloaded files, a far higher figure than in H2 2017 (2.9%).
Yet cybercriminal interest in ordinary currencies remains high, as evidenced by the presence of Neutrino.POS and Jimmy in the Top 10. In H2 2017, Neutrino.POS was downloaded in 4.6% of all cases. In 2018, its share in the overall stream of downloaded files declined, but its “cousin” Jimmy helped out by adding 1.1% to the share of banking Trojans.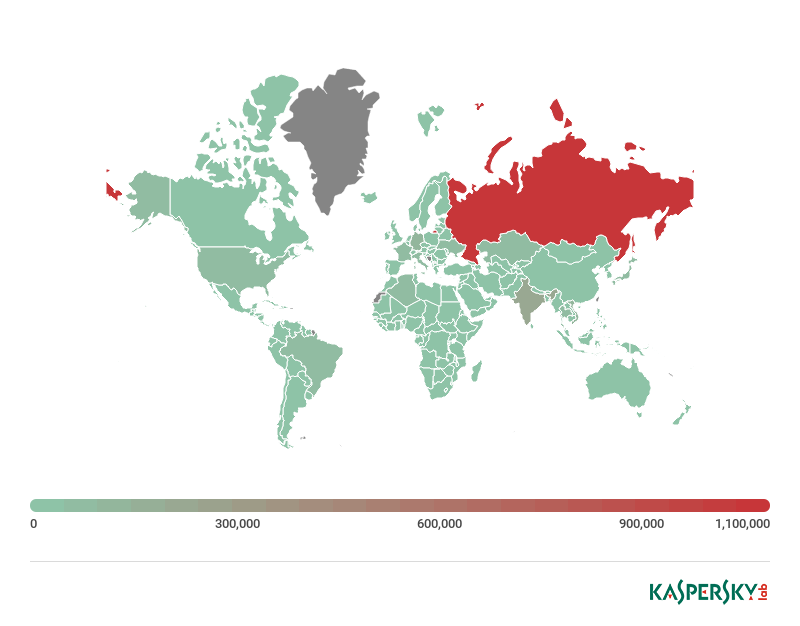
Distribution map of the Top 10 downloaded threats, H2 2017 (download)
In H1 2018, the Trojan Khalesi was in third place in our ranking, accounting for 4.9% of downloaded files. But while in 2017 the Remcos, BetaBot, Smoke, and Panda bots were involved in downloading the Trojan, in 2018 Khalesi was downloaded only by the spam bot Lethic.
On a separate note, the H1 2018 Top 10 features Mail PassView, a legal password recovery tool for various email clients. Distributed via the Remcos backdoor, it is likely used to obtain passwords for victim mailboxes.
The Cutwail, Lethic, and newly rebranded Emotet bots are also firmly rooted in the Top 10.
Compared to H2 2017, the number of ransomware encryptors downloaded by bots has risen this year. Despite the overall decline in the distribution of ransomware programs, botnet operators continue to deliver them to victims. According to our data, most ransomware programs in 2017 were downloaded by the Smoke bot, but in 2018 top spot has been seized by Nitol. GandCrab ransomware is a newbie in the Top 10 most downloaded families of 2018. It appeared in 2018 and was immediately deployed and distributed by several botnet operators, most actively by Trik.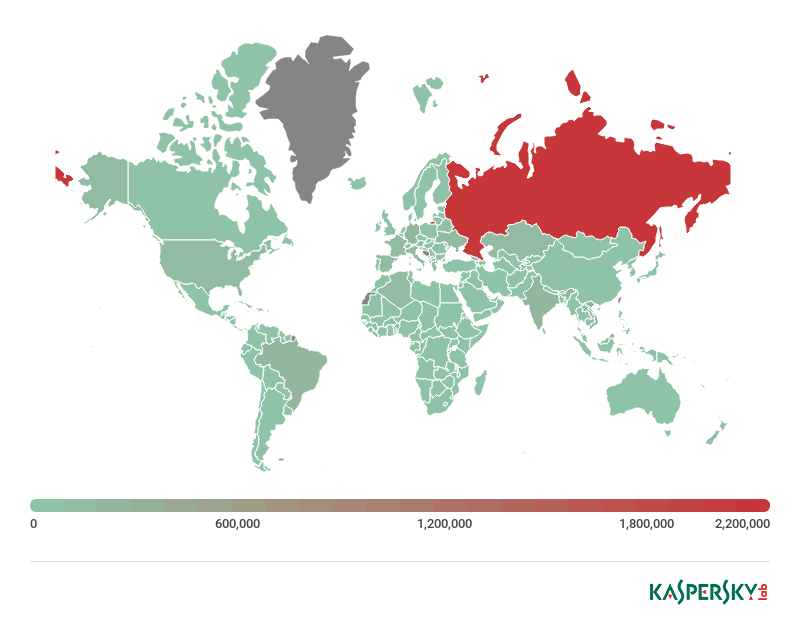
Distribution map of the Top 10 downloaded threats, H1 2018 (download)
In terms of behavior, the clear leaders in both halves are Trojans with such diverse capabilities that it’s difficult to pinpoint their “specialization.” A significant proportion is made up of bankers and backdoors ensuring maximum theft of important information. What’s more, last year’s most common malware included a large number of spam bots, largely due to the above-mentioned Lethic.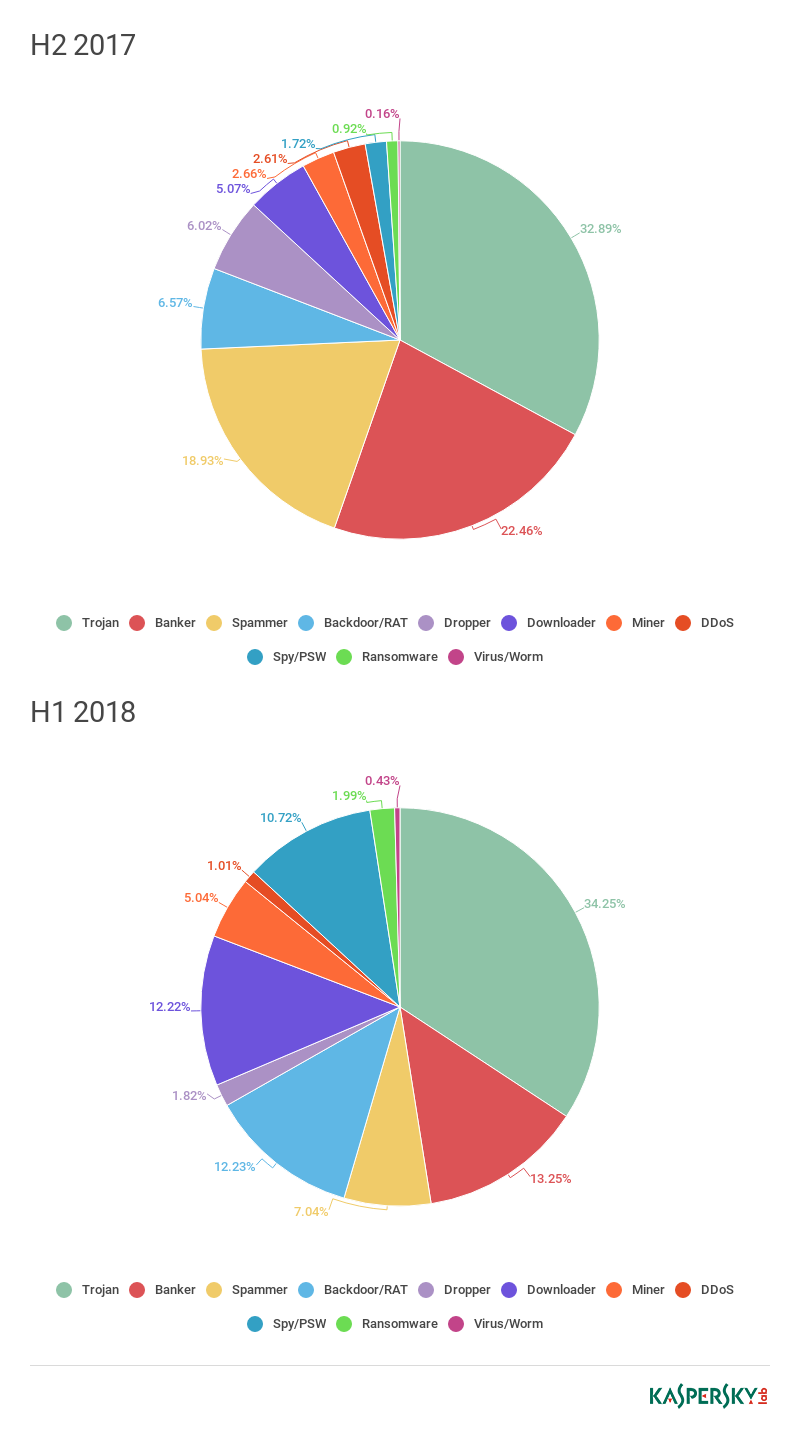
Distribution of downloaded files by behavior, H2 2017 — H1 2018 (download)
Most “versatile”
Among the families under observation, we identified the most “versatile” — that is, those downloading the largest number of different files. Such diversity can be the result of several factors:
Different botnets from the same family are managed by different operators with varying objectives.
Operators “lease” their botnets, allowing them to be used to distribute malware.
A botnet changes its “specialization” (for example, Emotet turned from a banking Trojan turned into a spam bot)
In 2018, as in 2017, the most “versatile” bots were Hworm, Smoke, and BetaBot (a.k.a. Neurevt).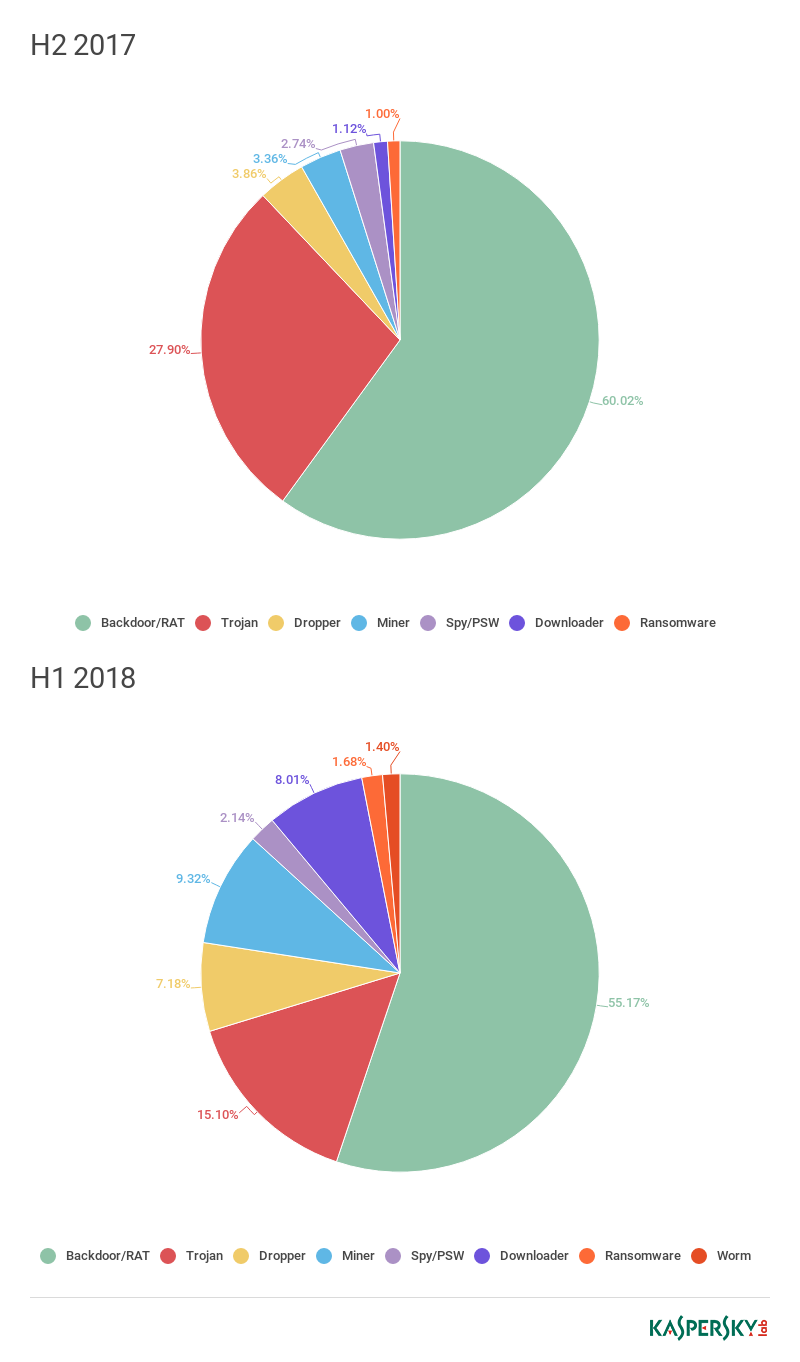
Distribution of downloaded files by behavior for Hworm, H2 2017 — H1 2018 (download)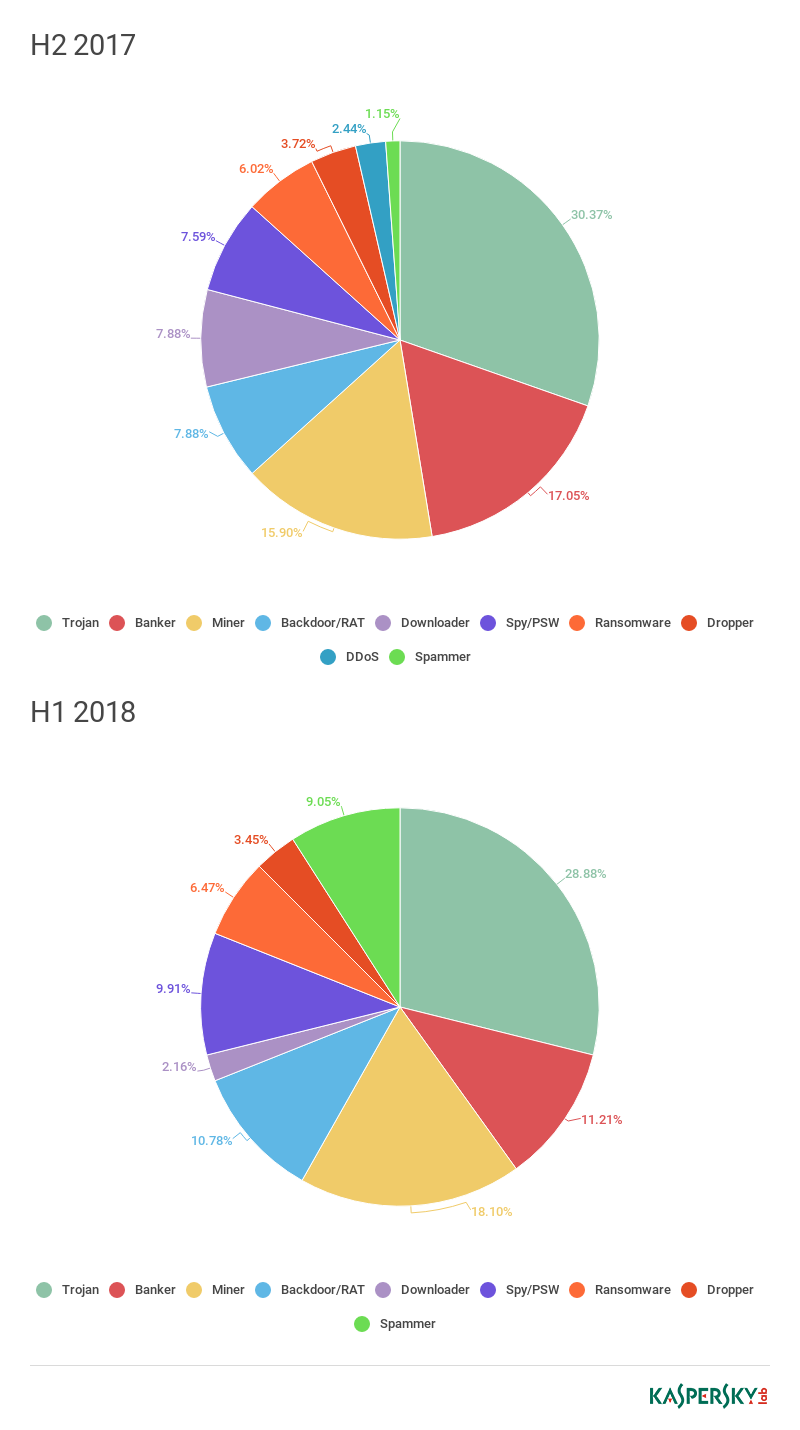
Distribution of downloaded files by behavior for Smoke, H2 2017 — H1 2018 (download)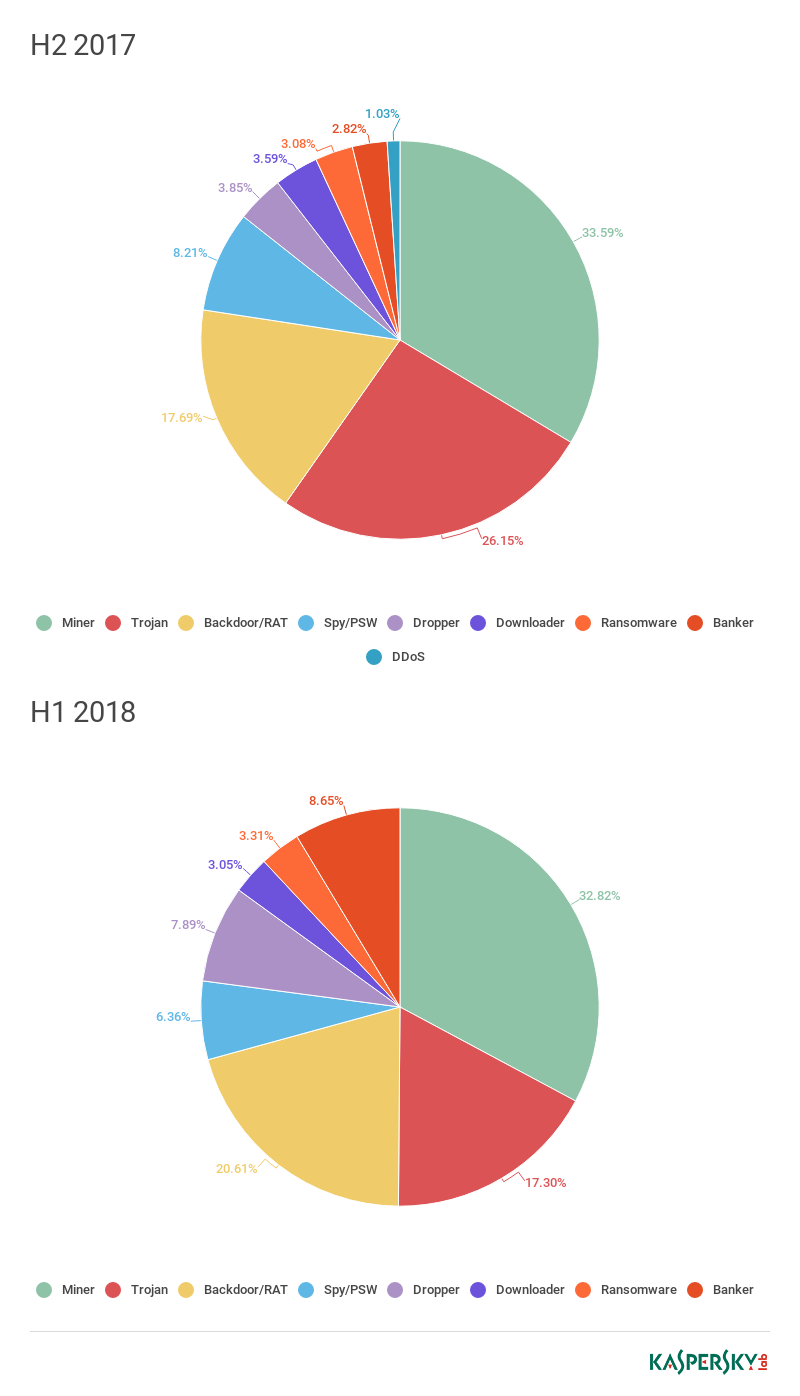
Distribution of downloaded files by behavior for Betabot, H2 2017 — H1 2018 (download)
As we already mentioned, hidden mining software is very popular, as confirmed by the statistics. Despite the variety of downloaded malware, miners invariably end up in the Top 3.
Backdoors also feature heavily due to the wide-ranging options they provide for cybercriminals, from saving screenshots and keystrokes to direct control over the target device.
Most “international”
In terms of territorial distribution of control servers, the backdoor Njrat unsurprisingly claimed the “most international” prize, with C&C centers in 99 countries. This geographical scope is down to the ease of configuring a personal backdoor, allowing anyone to create their own botnet with minimal knowledge of malware development.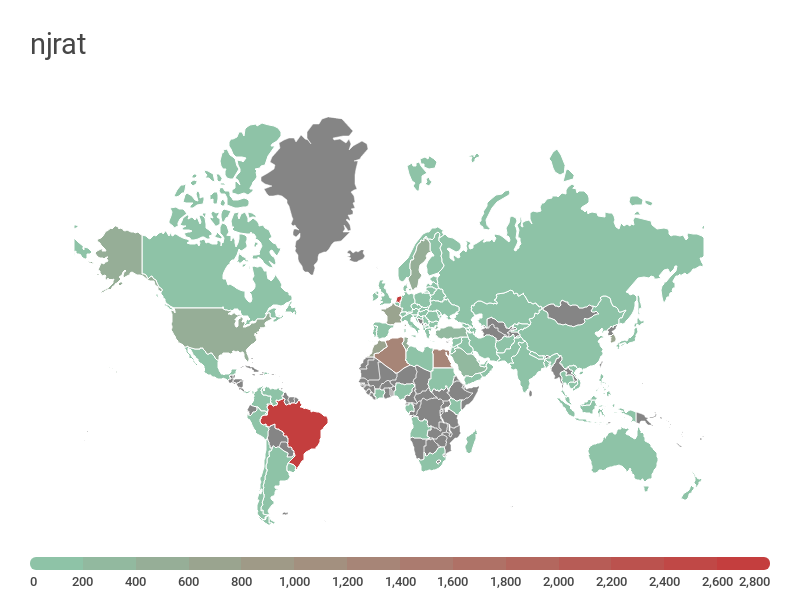
Distribution map of Njrat C&C centers, H2 2017 — H1 2018 (download)
Next come the backdoors DarkComet and NanoCore RAT. They share silver and bronze, having C&Cs in almost 80 countries worldwide. Despite the arrest of the creator of NanoCore, he managed to sell the source code of his privately developed RAT, which is now actively used by other cybercriminals.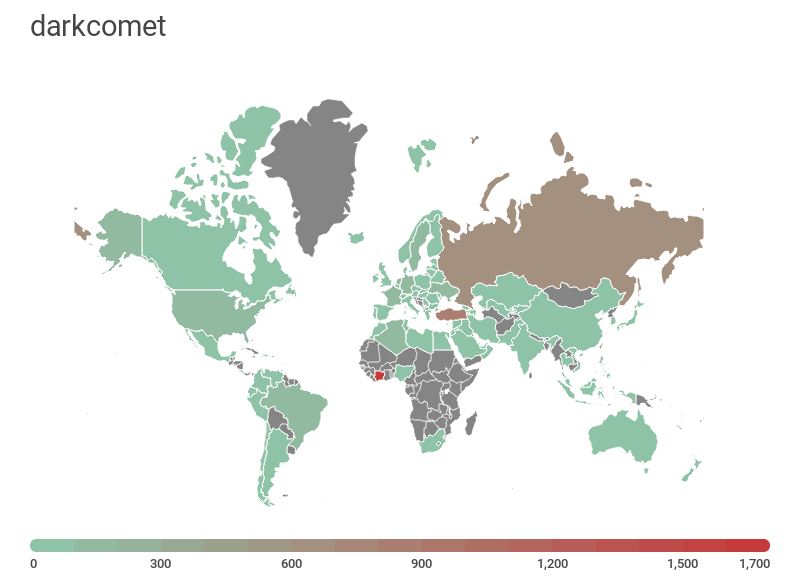
Distribution map of DarkComet C&C centers, H2 2017 — H1 2018 (download)
Distribution map of NanoCore RAT C&C centers, H2 2017 — H1 2018 (download)
A look at the geography of infection targets reveals that another backdoor, QRAT, has the largest reach. In H2 2017, we registered infection attempts in 190 countries, and this year QRAT added two more countries, bringing the total to 192.
QRAT distribution map, H2 2017 — H1 2018 (download)
This extensive scope is due to the SaaS (Software-as-a-Service), or rather MaaS (Malware-as-a-Service), distribution model QRAT can be purchased for 30 or 90 days, or for one year. Its cross-platform nature (the malware is written in Java) also plays a role.
Conclusion
By intercepting bot commands, we can track the latest trends in the world of virus writers and provide maximum protection for our users.
Here are the main trends that we identified from analyzing files downloaded by bots:
The share of miners in bot-distributed files is increasing, as cybercriminals have begun to view botnets as a tool for mining cryptocurrency.
Backdoors consistently make up the bulk of downloads; that is, botnet operators are keen to gain maximum possible control over infected devices.
The number of downloaded droppers is also on the rise, indicative of attacks that are multistage and growing in complexity.
The share of banking Trojans among bot-downloaded files in 2018 decreased, but it’s too soon to speak of an overall reduction in number, since they are often delivered by droppers (see above).
Increasingly, botnets are leased according to the needs of the customer, and in many cases it is difficult to pinpoint the “specialization” of the botnet.