X.Org Flaw Exposes Unix-Like OSes to Attacks
30.10.2019 securityweek Vulnerebility
Several Unix-like operating systems are affected by a potentially serious X.Org vulnerability that can be exploited for privilege escalation and arbitrary code execution.
X.Org is a popular open source implementation of the X Windows System (also known as X11, X or X-Windows), the graphical windowing system used by BSD and Linux operating systems.
Narendra Shinde discovered that X.Org X Server versions 1.19 and later are affected by an arbitrary file overwrite vulnerability that can be exploited by an authenticated attacker to elevate permissions and execute arbitrary code with root privileges.
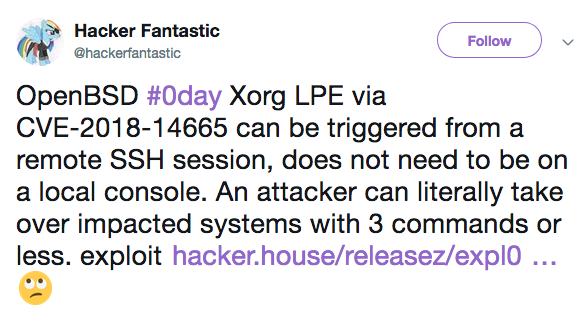
The security hole, tracked as CVE-2018-14665, was introduced nearly two years ago and it affects operating systems that run X Server with elevated privileges.
“Incorrect command-line parameter validation in the Xorg X server can lead to privilege elevation and/or arbitrary files overwrite, when the X server is running with elevated privileges (ie when Xorg is installed with the setuid bit set and started by a non-root user),” X.Org developers said in an advisory.
The list of impacted operating systems includes Red Hat, CentOS, Debian, Ubuntu, and OpenBSD.
Some security experts pointed out that the vulnerability is very easy to exploit — they published a proof-of-concept (PoC) that can fit into a single tweet. While local access is normally required for exploitation, remote attackers can also — in certain circumstances — leverage the vulnerability to take control of a vulnerable system.

X.Org developers released a patch on October 25 and operating systems have also started creating fixes. There is also a workaround, but some users may not be able to apply it.
Shinde said he reported the vulnerability to Red Hat on October 10 and X.Org developers two days later. OpenBSD developers, however, were displeased with the fact that they were only notified an hour before the flaw was disclosed.