Z-Wave Downgrade Attack Left Over 100 Million IoT Devices Open to Hackers
7.6.2018 thehackernews IoT
Researchers have found that even after having an advanced encryption scheme in place, more than 100 million Internet-of-Things (IoT) devices from thousands of vendors are vulnerable to a downgrade attack that could allow attackers to gain unauthorized access to your devices.
The issue resides in the implementation of Z-Wave protocol—a wireless, radio frequency (RF) based communications technology that is primarily being used by home automation devices to communicate with each other.
Z-Wave protocol has been designed to offer an easy process to set up pairing and remotely control appliances—such as lighting control, security systems, thermostats, windows, locks, swimming pools and garage door openers—over a distance of up to 100 meters (330 feet).
The latest security standard for Z-Wave, called S2 security framework, uses an advanced key exchange mechanism, i.e., Elliptic-Curve Diffie-Hellman (ECDH) anonymous key agreement protocol, to share unique network keys between the controller and the client device during the pairing process.
Even after Silicon Labs, the company who owns Z-Wave, made it mandatory for certified IoT devices to use the latest S2 security standard, millions of smart devices still support the older insecure version of pairing process, called S0 framework, for compatibility.
S0 standard was found vulnerable to a critical vulnerability in 2013 due to its use of a hardcoded encryption key (i.e. 0000000000000000) to protect the network key, allowing attackers in range of the targeted devices to intercept the communication.
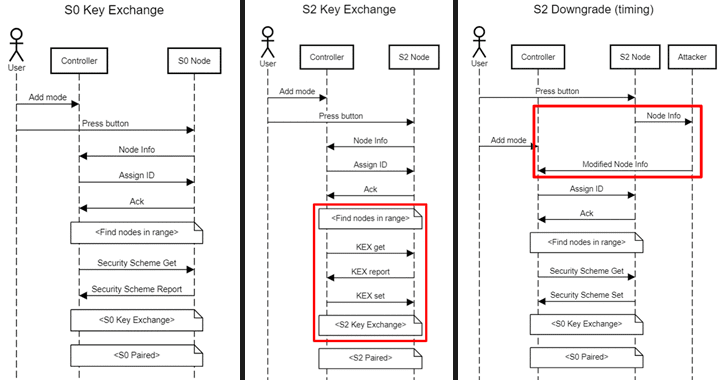
After analyzing Z-Wave, security researchers from UK-based Pen Test Partners discovered that devices which support both versions of key-sharing mechanisms could be forced to downgrade the pairing process from S2 to S0.
Dubbed Z-Shave by the researchers, the downgrade attack makes it easier for an attacker in range during the pairing process to intercept the key exchange, and obtain the network key to command the device remotely.
Researchers found the vulnerability while comparing the process of key exchange using S0 and S2, wherein they noticed that the node info command which contains the security class is being transferred entirely unencrypted and unauthenticated, allowing attackers to intercept or broadcast spoofed node command without setting the security class.
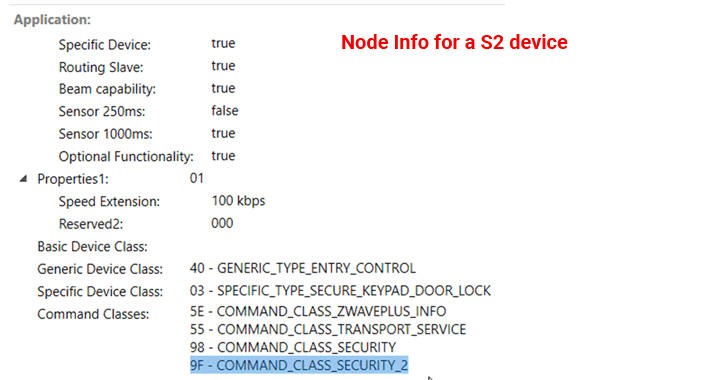
The researchers—Ken Munro and Andrew Tierney—used the Conexis L1 Smart Door Lock, a flagship product of British company Yale that ships for $360, for their exploit, and were able to downgrade its security, and eventually steal the keys and get permanent access to the Yale lock, and therefore the building protected by it, all without the actual user's knowledge.
You can also watch the video of the Z-Shave attack, wherein the researchers demonstrated how an attacker could unlock a door.
The S0 decryption attack was initially revealed by cybersecurity consulting company SensePost back in 2013, but at that time, Silicon Labs didn't see this issue "as a serious threat in the real world" because it was limited to the timeframe of the pairing process.
Silicon Labs published a blog post in response to the Pen Test Partners' findings on Wednesday, saying the company is confident its smart devices are secure and not vulnerable to such threats.
"S2 is the best-in-class standard for security in the smart home today, with no known vulnerabilities, and mandatory for all new Z-Wave products submitted for certification after April 2, 2017," reads the blog post.
However, the company said that since the adoption of S2 framework across the ecosystem could not happen overnight, the issue existed in Z-Wave for providing backward compatibility, so that S2 devices can work in an S0 network (and vice versa).
The company also said there are procedures in place to notify and alert users in times when secure devices connect to networks using downgraded communications, but IoT device manufacturers hardly provide any user interface to show such alerts, leaving users unaware of this attack.


