Zerodium Discloses Flaw That Allows Code Execution in Tor Browser
12.9.2018 securityweek Vulnerebility
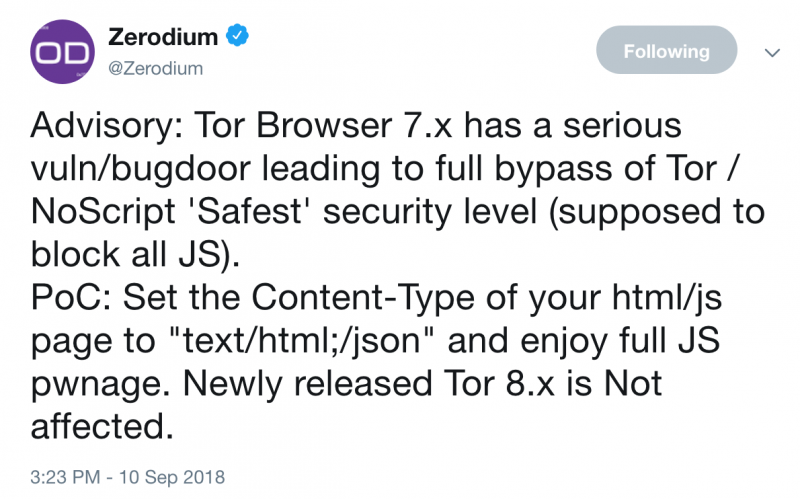
Exploit acquisition firm Zerodium has disclosed a NoScript vulnerability that can be exploited to execute arbitrary JavaScript code in the Tor Browser even if the maximum security level is used.
Zerodium disclosed the flaw and provided instructions on how it can be reproduced in a single message posted to Twitter on Monday. The recently released Tor Browser 8 is not affected.
While the tweet describes the issue as a vulnerability or backdoor in the Tor Browser, the flaw actually impacts NoScript, a popular Firefox extension designed to protect users against malicious scripts by allowing JavaScript, Java, and Flash plugins to be executed only on trusted websites. The Tor Browser is based on Firefox and it includes NoScript by default.

Giorgio Maone, the Italian developer who created NoScript, patched the vulnerability in roughly two hours with the release of version 5.1.8.7. Maone noted that only the “Classic” branch of NoScript 5 is impacted.
The developer explained that the bug exists due to a “work-around for NoScript blocking the in-browser JSON viewer.” He also noted that the vulnerability was introduced in May 2017 with the release of NoScript 5.0.4.
Contacted by SecurityWeek, Tor Project representatives highlighted that this is not a Tor Browser zero-day vulnerability.
“This was a bug in NoScript and not a zero-day exploit of Tor Browser that could circumvent its privacy protections. For bypassing Tor, a real browser exploit would still be needed,” the Tor Project explained.
Chaouki Bekrar, the CEO of Zerodium, told SecurityWeek that the exploit basically circumvents the protection provided by NoScript, even if the Tor Browser is set to the “Safest” security level.
“If a user sets his Tor browser security level to ‘Safest’ to block JavaScript from all websites (e.g. to prevent browser exploits or data gathering), the exploit would allow a website or a hidden service to bypass all NoScript restrictions and execute any JavaScript code despite the maximum security level being used, making it totally ineffective,” Bekrar explained.
Bekrar said his company acquired the vulnerability as a zero-day “many months ago” and shared it with its government customers. He claims Zerodium has acquired – including as part of a time-limited $1 million bug bounty program – what he describes as “high-end Tor exploits.” The company’s customers have allegedly used these exploits to “fight crime and child abuse, and make the world a better and safer place for all.”
Asked if he is concerned that the vulnerability may be exploited for malicious purposes now that it has been disclosed by Zerodium, Bekrar highlighted that version 8 of Tor Browser is not impacted and that it’s highly recommended that users upgrade to the newest release.