The Lazarus Group is far from the only infamous client to have used the service to obfuscate the financial tracks. The other prominent actors consist of ransomware crews like LockBit, Sodinokibi (aka REvil), Zeppelin, Mamba, Dharma, and SunCrypt.
Authorities Shut Down ChipMixer Platform Tied to Crypto Laundering Scheme
16.3.23 Cryptocurrency The Hacker News
A coalition of law enforcement agencies across Europe and the U.S. announced the takedown of ChipMixer, an unlicensed cryptocurrency mixer that began its operations in August 2017.
"The ChipMixer software blocked the blockchain trail of the funds, making it attractive for cybercriminals looking to launder illegal proceeds from criminal activities such as drug trafficking, weapons trafficking, ransomware attacks, and payment card fraud," Europol said in a statement.
The coordinated exercise, besides dismantling the clearnet and dark web websites associated with ChipMixer, also resulted in the seizure of $47.5 million in Bitcoin and 7 TB of data.
Mixers, also called tumblers, offer full anonymity for a fee by commingling cryptocurrency from different users – both legitimate and criminally-derived funds – in a manner that makes it hard to trace the origins.
This is achieved by funneling different payments into a single pool before splitting up each amount and transmitting them to designated recipients, thereby turning it into an attractive option for criminals looking to cash out and exchange the tainted money for fiat currency.
According to a report from Chainalysis in January 2023, "mixers processed a total of $7.8 billion in 2022, 24% of which came from illicit addresses," and "the vast majority of illicit value processed by mixers is made up of stolen funds, the majority of which were stolen by North Korea-linked hackers."
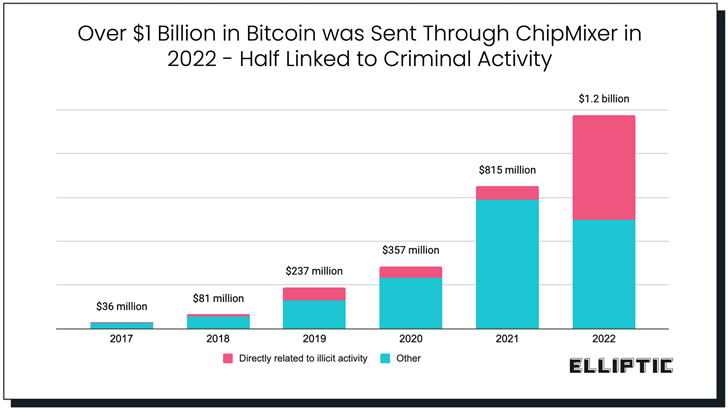
ChipMixer, the world's largest centralized crypto mixer service, is estimated to have laundered no less than $3.75 billion worth of digital assets (152,000 BTC) to further a wide range of criminal schemes.
Blockchain analytics firm Elliptic said ChipMixer has been used to launder over $844 million in Bitcoin that can be linked directly to criminal activity.
"ChipMixer was one of a variety of mixers used to launder the proceeds of hacks perpetrated by North Korea's Lazarus Group," Elliptic's co-founder and chief scientist, Tom Robinson, said.
This comprises the KuCoin theft in September 2020 as well as the Axie Infinity Ronin Bridge and Harmony Horizon Bridge hacks that took place last year.

The Lazarus Group is far from the only infamous client to have used the service to obfuscate the financial tracks. The other prominent actors consist of ransomware crews like LockBit, Sodinokibi (aka REvil), Zeppelin, Mamba, Dharma, and SunCrypt.
Additionally, ChipMixer is said to have attracted more than $200 million in Bitcoin linked to purchases originating from darknet markets, including $60 million from customers of the now-defunct Hydra.
The mixer platform, per the U.S. Department of Justice (DoJ), also processed cryptocurrency used by the Russia-linked APT28 hacking group (aka Fancy Bear or Strontium) to procure infrastructure employed in connection with a malware called Drovorub.
Coinciding with the crackdown, the DoJ further charged a 49-year-old Vietnamese national, Minh Quốc Nguyễn, for his role in creating and running ChipMixer's online infrastructure and advertising its services.
"ChipMixer facilitated the laundering of cryptocurrency, specifically Bitcoin, on a vast international scale, abetting nefarious actors and criminals of all kinds in evading detection," U.S. Attorney Jacqueline C. Romero said.
"Platforms like ChipMixer, which are designed to conceal the sources and destinations of staggering amounts of criminal proceeds, undermine the public's confidence in cryptocurrencies and blockchain technology."
The development is the latest in a string of law enforcement actions undertaken by governments across the world to tackle cybercrime, and comes weeks after "penal procedures" were initiated against suspected core members of the DoppelPaymer ransomware gang.
ChipMixer is also the fourth mixer service to be outlawed over the past few years following the disruption of Bestmixer, Blender, and Tornado Cash, the latter two of which were sanctioned by the U.S. Treasury Department last year for abetting Lazarus Group and other threat actors in laundering ill-gotten proceeds.