Kubernetes RBAC Exploited in Large-Scale Campaign for Cryptocurrency Mining
22.4.23 Cryptocurrency The Hacker News
A large-scale attack campaign discovered in the wild has been exploiting Kubernetes (K8s) Role-Based Access Control (RBAC) to create backdoors and run cryptocurrency miners.
"The attackers also deployed DaemonSets to take over and hijack resources of the K8s clusters they attack," cloud security firm Aqua said in a report shared with The Hacker News. The Israeli company, which dubbed the attack RBAC Buster, said it found 60 exposed K8s clusters that have been exploited by the threat actor behind this campaign.
The attack chain commenced with the attacker gaining initial access via a misconfigured API server, followed by checking for evidence of competing miner malware on the compromised server and then using RBAC to set up persistence.
"The attacker created a new ClusterRole with near admin-level privileges," the company said. "Next, the attacker created a 'ServiceAccount', 'kube-controller' in the 'kube-system' namespace. Lastly, the attacker created a 'ClusterRoleBinding', binding the ClusterRole with the ServiceAccount to create a strong and inconspicuous persistence."
In the intrusion observed against its K8s honeypots, the attacker attempted to weaponize the exposed AWS access keys to obtain an entrenched foothold into the environment, steal data, and escape the confines of the cluster.
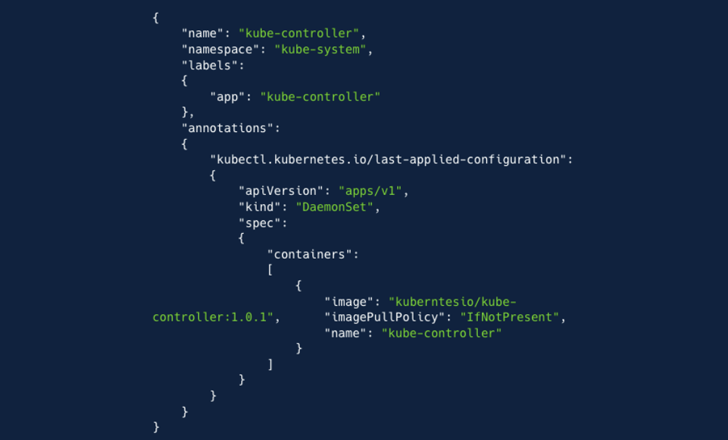
The final step of the attack entailed the threat actor creating a DaemonSet to deploy a container image hosted on Docker ("kuberntesio/kube-controller:1.0.1") on all nodes. The container, which has been pulled 14,399 times since its upload five months ago, harbors a cryptocurrency miner.
"The container image named 'kuberntesio/kube-controller' is a case of typosquatting that impersonates the legitimate 'kubernetesio' account," Aqua said. "The image also mimics the popular 'kube-controller-manager' container image, which is a critical component of the control plane, running within a Pod on every master node, responsible for detecting and responding to node failures."
Interestingly, some of the tactics described in the campaign bear similarities to another illicit cryptocurrency mining operation that also took advantage of DaemonSets to mint Dero and Monero. It's currently not clear whether the two sets of attacks are related.
