Smartphone Exploits Earn Hackers Over $500,000
2.11.2017 securityaffairs Congress
White hat hackers earned more than half a million dollars at this year’s Mobile Pwn2Own competition after successfully demonstrating exploits against Samsung’s Galaxy S8, Apple’s iPhone 7 and Huawei’s Mate 9 Pro.
The hacking contest, organized by Trend Micro’s Zero Day Initiative (ZDI) at the PacSec conference in Tokyo, Japan, offered more than $500,000 for exploit chains targeting browsers, short distance communications (Wi-Fi, Bluetooth and NFC), messaging, and baseband components in the Google Pixel, Galaxy S8, iPhone 7 and Mate 9 Pro.
All devices had been running the latest versions of the software and operating systems – Apple, Google and Huawei released patches the night before the event started.
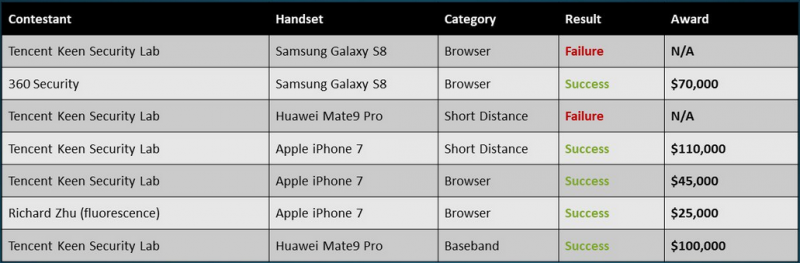
On the first day, participants earned a total of $350,000 for disclosing vulnerabilities that allow attacks against Internet Browser on the Galaxy S8, Safari on the iPhone 7, Wi-Fi on the iPhone 7, and the baseband on the Mate 9 Pro.
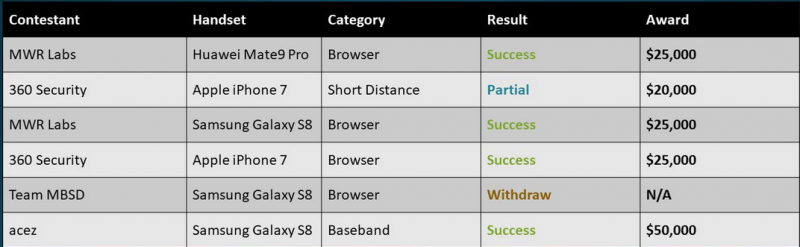
On the second day, MWR Labs earned $25,000 for hacking Google Chrome of the Mate 9 Pro via 5 logic bugs in Huawei apps that allowed a browser sandbox escape and data exfiltration.
The same team took home an additional $25,000 after exploiting 11 flaws across six different apps to hack Internet Browser on the Galaxy S8. The exploit resulted in arbitrary code execution and sensitive data leakage.
A researcher from China-based Qihoo 360 earned $20,000 for a partially successful exploit targeting the iPhone 7’s Wi-Fi component. The exploit worked properly, but one of the three vulnerabilities it leveraged had been previously disclosed at Pwn2Own by a different contestant. The same Chinese expert was awarded another $25,000 for hacking Safari on the iPhone 7.
The last entry came from the researcher Amat Cama (aka Acez), who earned $50,000 for a baseband exploit targeting the Galaxy S8. The exploit relied on a stack-based buffer overflow that allowed arbitrary code execution.
The total amount of money paid to researchers over the course of two days at Mobile Pwn2Own 2017 was $495,000. The Tencent Keen Security Lab team got the highest number of Master of Pwn points, which also earned them 65,000 ZDI reward points, worth roughly $25,000.

While one successful entry did target the Chrome browser, no one has attempted to demonstrate an exploit on Google’s Pixel phone.
Affected vendors have been provided the details of the vulnerabilities used at the event and ZDI will give them 90 days to release fixes before a limited advisory describing the flaws will be made public.