Cryptocurrency mining operations target Windows Server, Redis and Apache Solr servers online
12.3.2018 securityaffairs Cryptocurrency
Researchers from the ISC SANS group and the Anti-DDoS company Imperva discovered two distinct campaigns targeting Windows Server, Redis and Apache Solr servers online.
Last week new mining campaigns targeted unpatched Windows Server, Apache Solr, and Redis servers, attackers attempted to install the cryptocurrency miner Coinminer.
Two campaigns were spotted by researchers from the ISC SANS group and the Anti-DDoS company Imperva.
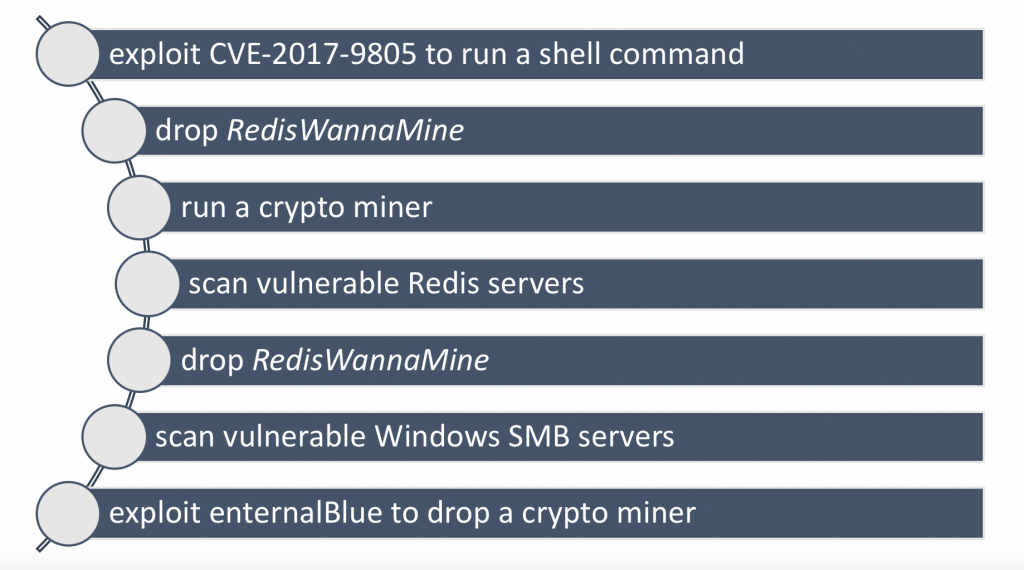
The campaign observed by Imperva has been targeting Redis and Windows Server installs, the company tracked the operation as RedisWannaMine.
Crooks are conducting an Internet mass-scanning for systems running outdated Redis versions, the attackers attempt to trigger the CVE-2017-9805 vulnerability.
“This week we saw a new generation of cryptojacking attacks aimed at bothdatabase servers and application servers. We dubbed one of these attacks RedisWannaMine.” reads the blog post published by Imperva.
“RedisWannaMine is more complex in terms of evasion techniques and capabilities. It demonstrates a worm-like behavior combined with advanced exploits to increase the attackers’ infection rate and fatten their wallets.”
RedisWannaMine executes a script to download a publicly available tool, dubbed masscan, that is stored on Github repository, then compiles and installs it.
The experts observed that once attackers gain access to a host, they will drop the ReddisWannaMine malware as a first stage payload, then it installs a second-stages cryptocurrency miner.

RedisWannaMine is a complex threat due to the sophisticated evasion techniques and capabilities it implements. The malicious code combines advanced exploits with worm-like behavior, it uses the EternalBlue NSA exploit to spread.
But the ReddisWannaMine campaign also displays the classic behavioral pattern of a self-propagating worm.
The cybercrime gang behind ReddisWannaMine targets Redis servers and also Windows Servers with that expose SMB ports.
The second mining campaign is targeting Apache Solr by exploiting the CVE-2017-12629, it was spotted by researchers at ISC SANS.
“the number of victims is getting higher. From Feb, 28 to Mar, 8 this campaign infected 1777 victims, of which 1416 are SOLR servers. See below the worldwide SOLR victims distribution.” reads the analysis published by ISC SANS.

Both campaigns are just the tip of the iceberg, the number of mining campaigns and attacks against the cryptocurrency industry is on the rise, and for sure this is the trend we will see in the next months.