16.11.23 Ransom The Hacker News

The threat actors behind the Rhysida ransomware engage in opportunistic attacks targeting organizations spanning various industry sectors.
CISA and FBI Issue Warning About Rhysida Ransomware Double Extortion Attacks
16.11.23 Ransom The Hacker News
The threat actors behind the Rhysida ransomware engage in opportunistic attacks targeting organizations spanning various industry sectors.
The advisory comes courtesy of the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC).
"Observed as a ransomware-as-a-service (RaaS) model, Rhysida actors have compromised organizations in education, manufacturing, information technology, and government sectors and any ransom paid is split between the group and affiliates," the agencies said.
"Rhysida actors leverage external-facing remote services, such as virtual private networks (VPNs), Zerologon vulnerability (CVE-2020-1472), and phishing campaigns to gain initial access and persistence within a network."
First detected in May 2023, Rhysida makes use of the time-tested tactic of double extortion, demanding a ransom payment to decrypt victim data and threatening to publish the exfiltrated data unless the ransom is paid.
It's also said to share overlaps with another ransomware crew known as Vice Society (aka Storm-0832 or Vanilla Tempest), owing to similar targeting patterns and the use of NTDSUtil as well as PortStarter, which has been exclusively employed by the latter.
According to statistics compiled by Malwarebytes, Rhysida has claimed five victims for the month of October 2023, putting it far behind LockBit (64), NoEscape (40), PLAY (36), ALPHV/BlackCat (29), and 8BASE (21).
The agencies described the group as engaging in opportunistic attacks to breach targets and taking advantage of living-off-the-land (LotL) techniques to facilitate lateral movement and establish VPN access.
In doing so, the idea is to evade detection by blending in with legitimate Windows systems and network activities.
Vice Society's pivot to Rhysida has been bolstered in the wake of new research published by Sophos earlier last week, which said it observed the same threat actor using Vice Society up until June 2023, when it switched to deploying Rhysida.
The cybersecurity company is tracking the cluster under the name TAC5279.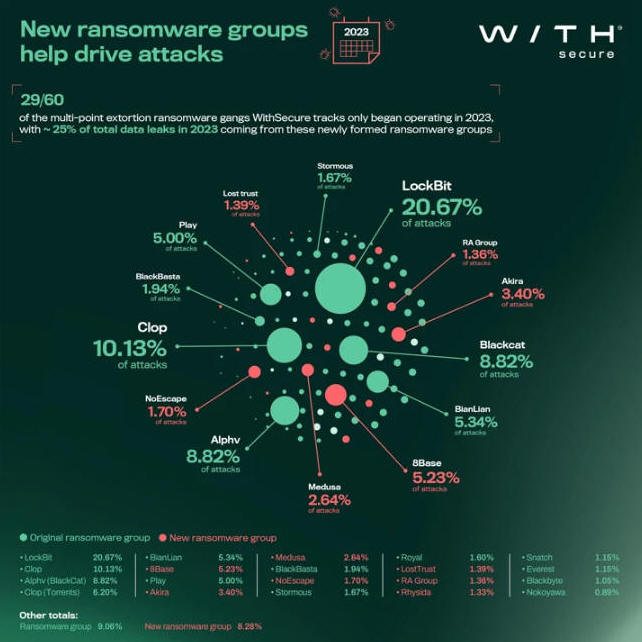
"Notably, according to the ransomware group's data leak site, Vice Society has not posted a victim since July 2023, which is around the time Rhysida began reporting victims on its site," Sophos researchers Colin Cowie and Morgan Demboski said.
The development comes as the BlackCat ransomware Gang is attacking corporations and public entities using Google ads laced with Nitrogen malware, per eSentire.
"This affiliate is taking out Google ads promoting popular software, such as Advanced IP Scanner, Slack, WinSCP and Cisco AnyConnect, to lure business professionals to attacker-controlled websites," the Canadian cybersecurity company said.
The rogue installers, which come fitted with Nitrogen, which is an initial access malware capable of delivering next-stage payloads onto a compromised environment, including ransomware.
Cybersecurity
"Known examples of ransomware-associated initial access malware that leverage browser-based attacks include GootLoader, SocGholish, BATLOADER, and now Nitrogen," eSentire said. "Interestingly, ALPHV has been observed as an end-game for at least two of these browser-based initial access pieces of malware: GootLoader and Nitrogen."
The ever-evolving nature of the ransomware landscape is further evidenced by the fact that 29 of the 60 ransomware groups currently active began operations this year, per WithSecure, in part driven by the source code leaks of Babuk, Conti, and LockBit over the years.
"Data leaks aren't the only thing that leads to older groups cross-pollinating younger ones," WithSecure said in a report shared with The Hacker News.
"Ransomware gangs have staff just like an IT company. And like an IT company, people change jobs sometimes, and bring their unique skills and knowledge with them. Unlike legit IT companies, however, there's nothing stopping a cyber criminal from taking proprietary resources (such as code or tools) from one ransomware operation and using it at another. There's no honor among thieves."