
The U.S. Justice Department (DoJ) has officially announced the disruption of the BlackCat ransomware operation and released a decryption tool that more than 500 affected victims can use to regain access to files locked by the malware.
FBI Takes Down BlackCat Ransomware, Releases Free Decryption Tool
21.12.23 Ransom The Hacker News

The U.S. Justice Department (DoJ) has officially announced the disruption of the BlackCat ransomware operation and released a decryption tool that more than 500 affected victims can use to regain access to files locked by the malware.
Court documents show that the U.S. Federal Bureau of Investigation (FBI) enlisted the help of a confidential human source (CHS) to act as an affiliate for the BlackCat group and gain access to a web panel used for managing the gang's victims, in what's a case of hacking the hackers.
The confiscation effort involved collaboration and assistance from multiple law enforcement agencies from the U.S., Germany, Denmark, Australia, the U.K., Spain, Switzerland, and Austria.
BlackCat, also called ALPHV, GOLD BLAZER, and Noberus, first emerged in December 2021 and has since gone on to be the second most prolific ransomware-as-a-service variant in the world after LockBit. It's also the first Rust-language-based ransomware strain spotted in the wild.
The development puts an end to speculations of a rumored law enforcement action after its dark web leak portal went offline on December 7, only to resurface five days later with just a single victim.
The FBI said it worked with dozens of victims in the U.S. to implement the decryptor, saving them from ransom demands totaling about $68 million, and that it also gained insight into the ransomware's computer network, allowing it to collect 946 public/private key pairs used to host the TOR sites operated by the group and dismantle them.
One important thing to note here is that creating a hidden service with the .onion URL on the TOR anonymization network generates a unique key pair comprising a private and public key (aka the identifier) that can be used to access and control the URL.
An actor who is in possession of the key pair can, therefore, broadcast a new route redirecting traffic for the .onion site to a different server under their control.
BlackCat, like several other ransomware gangs, uses a ransomware-as-a-service model involving a mix of core developers and affiliates, who rent out the payload and are responsible for identifying and attacking high-value victim institutions.
It also employs the double extortion scheme to put pressure on victims to pay up by exfiltrating sensitive data prior to encryption.
"BlackCat affiliates have gained initial access to victim networks through a number of methods, including leveraging compromised user credentials to gain initial access to the victim system," the DoJ said.
In all, the financially motivated actor is estimated to have compromised the networks of more than 1,000 victims across the world to earn nearly $300 million in illegal revenues as of September 2023.
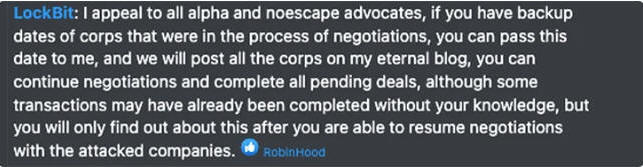
Image Source: Resecurity
If anything, the takedown has proven to be a blessing in disguise for rival groups like LockBit, which is already capitalizing on the situation by actively recruiting displaced affiliates, offering its data leak site to resume victim negotiations.
Speaking to malware research group vx-underground, a BlackCat spokesperson said "they have moved their servers and blogs," claiming that the law enforcement agencies only had access to a "stupid old key" for the old blog site which was deleted by the group a long time ago and has since not been used.
The threat actor's newest leak website remains operational as of writing. "On December 13, the group published the first victim to its new leak site," Secureworks said. "As of December 19, five victims were posted to the new site, demonstrating the group retained some operational capacity."
However, hours after the takedown, the BlackCat group took steps to "unseize" the main leak site using the same set of cryptographic keys necessary to host the hidden service on the TOR network and post its own seizure notice.
It has also given affiliates the green light to infiltrate critical infrastructure entities such as hospitals and nuclear power plants as well as other targets with the exception of those inside the Commonwealth of Independent States (CIS) as a retaliatory measure. The FBI has since re-seized the website.
"The threats seem like 'now you've done it' posturing but, this group has a documented history of attacking healthcare and energy infrastructure targets already, so it feels like bluster," Secureworks Counter Threat Unit (CTU) told The Hacker News.
"Given that such activity appears more likely to bring law enforcement attention – which is why many groups explicitly avoid it – it seems unlikely that affiliates will choose to specifically target such organizations, especially as ransomware is a crime of opportunity for the most part and based on available access to victim networks."
"That said, some less risk averse affiliates may be more willing to target energy and healthcare organizations. The flip side is that it is just as likely that the uncertainty caused by the law enforcement disruption will drive affiliates away from BlackCat into the arms of other ransomware operators, such as LockBit. Such interventions breed distrust and paranoia among ransomware group members and affiliates."
In a conversation with vx-underground, a LockBit administrator described the situation as "unfortunate" and that security loopholes in their infrastructure are a primary threat to "my business."