LockBit Ransomware Extorts $91 Million from U.S. Companies
15.6.23 Ransom The Hacker News
The threat actors behind the LockBit ransomware-as-a-service (RaaS) scheme have extorted $91 million following hundreds of attacks against numerous U.S. organizations since 2020.
That's according to a joint bulletin published by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), the Multi-State Information Sharing and Analysis Center (MS-ISAC), and other partner authorities from Australia, Canada, France, Germany, New Zealand, and the U.K.
"The LockBit ransomware-as-a-service (RaaS) attracts affiliates to use LockBit for conducting ransomware attacks, resulting in a large web of unconnected threat actors conducting wildly varying attacks," the agencies said.
LockBit, which first burst onto the scene in late 2019, has continued to be disruptive and prolific, targeting as many as 76 victims in May 2023 alone, per statistics shared by Malwarebytes last week. The Russia-linked cartel has claimed responsibility for at least 1,653 ransomware attacks to date.
The cybercrime operation has attacked a wide array of critical infrastructure sectors, including financial services, food and agriculture, education, energy, government and emergency services, healthcare, manufacturing, and transportation.
LockBit has received three substantial upgrades so far: LockBit Red (June 2021), LockBit Black (March 2022), and LockBit Green (January 2023), the last of which is based on leaked source code from the now-disbanded Conti gang.
The ransomware strain has since been adapted to target Linux, VMware ESXi, and Apple macOS systems, transforming it into an ever-evolving threat. The RaaS operation is also notable for paying people to get tattoos of its insignia and instituting the first-ever bug bounty program.
The business model involves the core developers renting out their warez to affiliates who perform the actual ransomware deployment and extortion. But in a twist, the group allows the affiliates to receive ransom payments before sending a cut to the main crew.
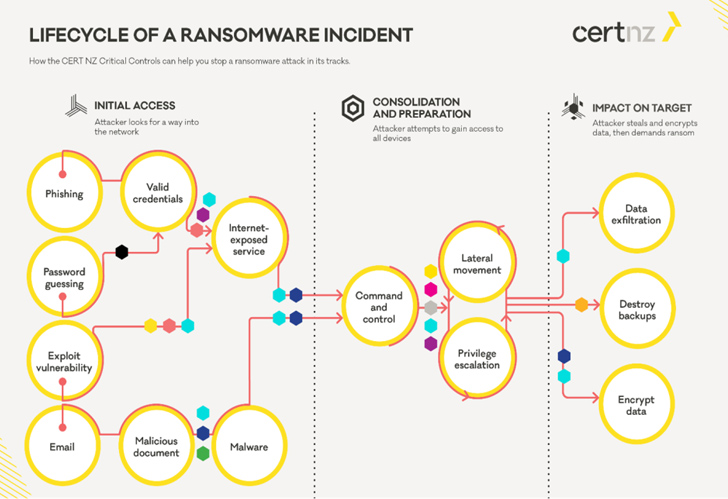
Attack chains involving LockBit have leveraged recently disclosed flaws in Fortra GoAnywhere Managed File Transfer (MFT) and PaperCut MF/NG servers as well as other known bugs in Apache Log4j2, F5 BIG-IP and BIG-IQ, and Fortinet devices to obtain initial access.
Also used by the affiliates are over three dozen freeware and open-source tools that allow for network reconnaissance, remote access and tunneling, credential dumping, and file exfiltration. The intrusions have been found to further abuse legitimate red team software such as Metasploit and Cobalt Strike.
"LockBit has been successful through its innovation and continual development of the group's administrative panel (i.e., a simplified, point-and-click interface making ransomware deployment accessible to those with lower degrees of technical skill), affiliate supporting functions, and constant revision of TTPs," the agencies said.
The development comes as CISA issued a Binding Operational Directive 23-02, instructing federal agencies to secure network devices like firewalls, routers, and switches that are exposed to the public internet within 14 days of discovery and take steps to minimize the attack surface.
"Too often, threat actors are able to use network devices to gain unrestricted access to organizational networks, in turn leading to full-scale compromise," CISA Director, Jen Easterly, said. "Requiring appropriate controls and mitigations [...] is an important step in reducing risk to the federal civilian enterprise."
The developments also follow a new advisory highlighting threats to Baseboard Management Controller (BMC) implementations that could potentially enable threat actors to establish a "beachhead with pre-boot execution potential."
"Hardened credentials, firmware updates, and network segmentation options are frequently overlooked, leading to a vulnerable BMC," CISA and the U.S. National Security Agency (NSA) noted in a joint alert.
"Additionally, a malicious actor could disable security solutions such as the trusted platform module (TPM) or UEFI secure boot, manipulate data on any attached storage media, or propagate implants or disruptive instructions across a network infrastructure."
