28.4.23 Ransomware The Hacker News
The threat actors behind RTM Locker have developed a ransomware strain that's capable of targeting Linux machines, marking the group's first foray into the open source operating system.
RTM Locker's First Linux Ransomware Strain Targeting NAS and ESXi Hosts
28.4.23 Ransomware The Hacker News
The threat actors behind RTM Locker have developed a ransomware strain that's capable of targeting Linux machines, marking the group's first foray into the open source operating system.
"Its locker ransomware infects Linux, NAS, and ESXi hosts and appears to be inspired by Babuk ransomware's leaked source code," Uptycs said in a new report published Wednesday. "It uses a combination of ECDH on Curve25519 (asymmetric encryption) and Chacha20 (symmetric encryption) to encrypt files."
RTM Locker was first documented by Trellix earlier this month, describing its developers as a private ransomware-as-a-service (RaaS) provider. It has its roots in a cybercrime group called Read The Manual (RTM) that's known to be active since at least 2015.
The group is notable for deliberately avoiding high-profile targets such as critical infrastructure, law enforcement, and hospitals so as to draw as little attention as possible. It also leverages affiliates to ransom victims, in addition to leaking stolen data should they refuse to pay up.
The Linux flavor is specifically geared to single out ESXi hosts by terminating all virtual machines running on a compromised host prior to commencing the encryption process. The exact initial infector employed to deliver the ransomware is currently unknown.
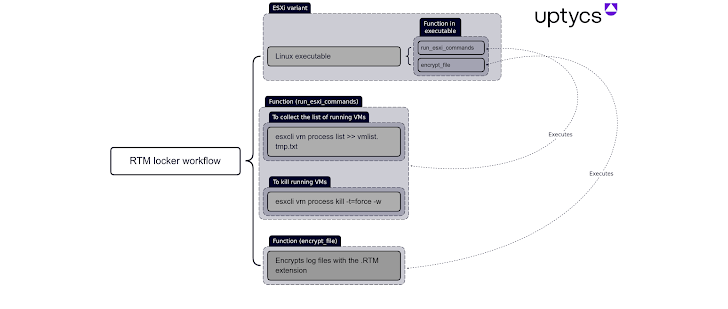
"It is statically compiled and stripped, making reverse engineering more difficult and allowing the binary to run on more systems," Uptycs explained. "The encryption function also uses pthreads (aka POSIX threads) to speed up execution."
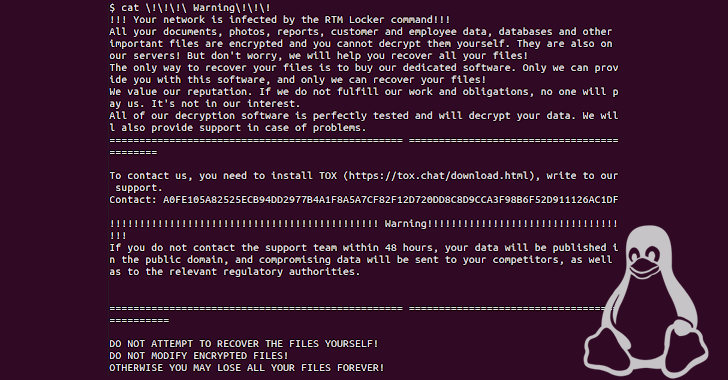
Following successful encryption, victims are urged to contact the support team within 48 hours via Tox or risk getting their data published. Decrypting a file locked with RTM Locker requires the public key appended to the end of the encrypted file and the attacker's private key.
The development comes as Microsoft revealed that vulnerable PaperCut servers are being actively targeted by threat actors to deploy Cl0p and LockBit ransomware.