9.11.23 Social The Hacker News
WhatsApp Introduces New Privacy Feature to Protect IP Address in Calls
9.11.23 Social The Hacker News
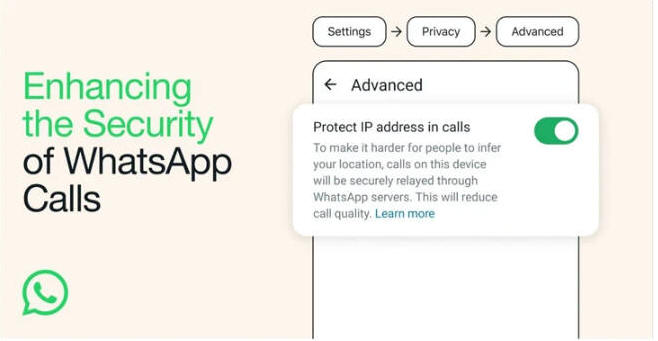
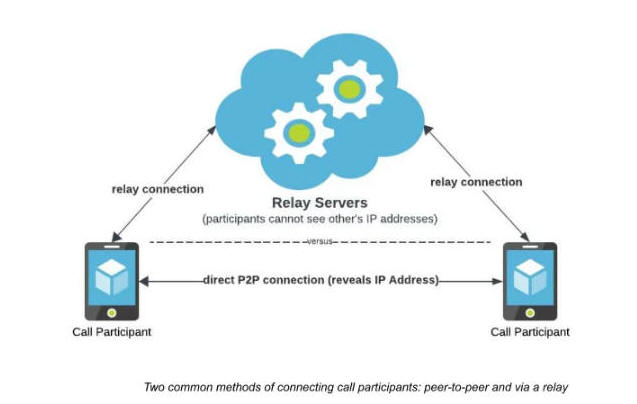
Meta-owned WhatsApp is officially rolling out a new privacy feature in its messaging service called "Protect IP Address in Calls" that masks users' IP addresses to other parties by relaying the calls through its servers.
"Calls are end-to-end encrypted, so even if a call is relayed through WhatsApp servers, WhatsApp cannot listen to your calls," the company said in a statement shared with The Hacker News.
The core idea is to make it harder for bad actors in the call to infer a user's location by securely relaying the connection through WhatsApp servers. However, a tradeoff to enabling the privacy option is a slight dip in call quality.
Viewed in that light, it's akin to Apple's iCloud Private Relay, which adds an anonymity layer by routing users' Safari browsing sessions through two secure internet relays.
It's worth noting that the "Protect IP Address in Calls" feature has been under development since at least late August 2023, as reported earlier by WABetaInfo.
"With this feature enabled, all your calls will be relayed through WhatsApp's servers, ensuring that other parties in the call cannot see your IP address and subsequently deduce your general geographical location," WhatsApp said.
"This new feature provides an additional layer of privacy and security particularly geared towards our most privacy-conscious users."
The feature builds upon a previously announced privacy feature referred to as "Silence Unknown Callers," which aims to not only protect users from unwanted contact but also minimize the risk of zero-click attacks and spyware.
WhatsApp's implementation of silenced calls involves the use of a custom protocol that's designed to reduce the processing of attacker-controlled data by incorporating what's called a privacy token.
"When a call is placed, the caller includes the privacy token of the recipient in the protocol message," the company explained. "Next, the server checks the token's validity along with a few other factors to determine if the intended recipient allows this sender to ring them.
"Crucially, for our user's privacy, the server does not learn anything about the exact relationship between the caller and the recipient from the token. With our design of this feature, calling becomes a much less attractive vector for attackers."