iPhones, iPads Can Be Hacked via 'Trustjacking' Attack
19.4.2018 securityweek iOS
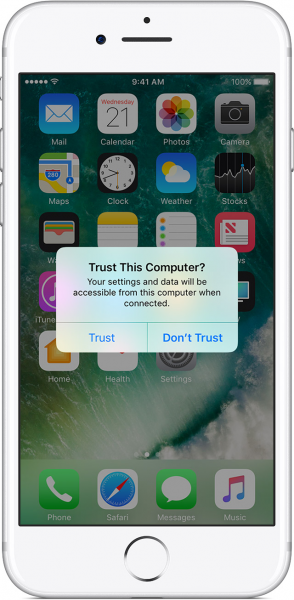
A feature that allows users to wirelessly sync their iPhones and iPads with iTunes can be abused by hackers to take control of iOS devices in what researchers call a “Trustjacking” attack.
This feature can be enabled by physically connecting an iOS device to a computer with iTunes and enabling the option to sync over Wi-Fi. The user is prompted to confirm that the computer is trusted when the mobile device is first connected to it, but no other approval is required to enable the syncing feature or to access the device over Wi-Fi at a later time.
Researchers at Symantec have found a way to abuse the iTunes Wi-Fi sync feature. They discovered that if an attacker can convince the targeted user to connect their iPhone/iPad via a cable to a malicious or compromised device, the hacker gains persistent control over the phone/tablet as long as they are on the same wireless network as the victim.Trustjacking only requires a user to trust a malicious or compromised device
In one attack scenario described by the experts, the Trustjacking attack involves a malicious charger at an airport. Once the user connects a device to the charger, they are asked to confirm that they trust the computer they have connected to – which they will likely do, thinking that the trust will be revoked once the phone/tablet is disconnected. The attacker then enables the Wi-Fi sync option in iTunes in a process that can be automated.
Even after the victim disconnects the iPhone/iPad from the charger, the attacker will still have control over the device, allowing them to conduct a wide range of activities.
For example, an attacker can install a developer image corresponding to the iOS version running on the victim’s system, giving them access to the device’s screen. Repeatedly capturing screenshots allows the hacker to view and record the victim’s every action.
Since the sync feature provides access to the iTunes backup, an attacker can also obtain a user’s photos, SMS and iMessage chats, and application data. The attacker can also install malicious applications or replace existing apps with a modified version.
An attack can also be conducted by hijacking the targeted user’s computer, making it easier to conduct unauthorized activities given that the computer and the mobile device are more likely to be on the same network for extended periods of time.

While the easiest way to conduct a Trustjacking attack involves being on the same Wi-Fi network as the victim, Symantec researchers believe this requirement can be bypassed via what is known as a malicious profile attack.
This method has been known since 2013 and it involves convincing the victim to install a malicious configuration file, or iOS profile, on their iPhone or iPad. These profiles allow cellular carriers, MDM solutions, and apps to configure system-level settings, but they can also be abused to remotely hijack devices.
Symantec says the method can be used to conduct Trustjacking attacks over the Internet by connecting the device to a VPN server and creating a continuous connection between them.
Apple has been informed about the vulnerability and the company has attempted to address it by adding an extra layer of protection in iOS 11. Specifically, users are now asked to enter their passcode when trusting a computer.
“While we appreciate the mitigation that Apple has taken, we’d like to highlight that it does not address Trustjacking in an holistic manner. Once the user has chosen to trust the compromised computer, the rest of the exploit continues to work as described above,” explained Symantec’s Roy Iarchy, one of the people involved in this research.
Some of the mitigations recommended by Symantec include clearing the list of trusted devices and reauthorizing them, enabling encrypted backups in iTunes, setting a strong password, and using mobile security solutions.