Malformed URL Prefixes
The offer in your email inbox from “amozon.com”? Most people probably know not to click on that. (If there are people in your organization who don’t, forward them this blog post on identifying suspicious URLs.)
The latest tactic used by email phishing attackers doesn’t involve changing letters of the URL. In fact, it doesn’t change anything in the URL at all. This attack changes the symbols used in the prefix that goes before the URL.
The GreatHorn Threat Intelligence Team has identified a new email attack trend, where cybercriminals are able to bypass traditional URL defenses to attack end users. The URLs are malformed, not utilizing the normal URL protocols, such as http:// or https://. Instead, they use http:/\ in their URL prefix.
Cybercriminals understand the requirement of each of the URL components and all URLs can be broken into five (5) parts.
Scheme: The Hypertext Transfer Protocol or HTTP (or could be ftp, mailto or git) to tell the web client how to access the resource. Also can be referred to as protocol.
Host: The primary domain (www.example.com) where the resource is hosted or located
Port: A number (:00) used only if another port is desired outside the default.
Path: The local resource being requested (optional).
Query String: Information applied to send data about that unique visitor to the server (optional).
Because the colon and two forward slashes have always been used in the standard URL format, most browsers automatically ignore this factor, using the scheme and subsequent components to take a user to the final destination. In fact, in an article published by BBC News, “Sir Tim Berners-Lee, the creator of the World Wide Web, has confessed that the // in a web address were actually “unnecessary”.”
Attackers are able to get around many email scanners using these malformed URL prefixes between the Scheme and Host. The URLs don’t fit the “known bad” profiles developed by simple email scanning programs, allowing them to slip through undetected. They may also slip past human eyes that aren’t accustomed to looking in the prefix for signs of suspicious activity.
First emerging in email environments in October 2020, this type of attack began gaining momentum through the end of the year. Between the first week of January and early February, the volume of email phishing attacks using malformed URL prefixes increased by 5,933%.
GreatHorn Threat Intelligence has identified these phishing attempts across all kinds of organizations. However, organizations in the following verticals are being targeted at a higher rate than others:
Pharmaceuticals
Lending
General contracting and construction management
Cable, mobile and high-speed broadband
Across the board, organizations running Office 365 are the targets of these attacks at a much higher rate than organizations running Google Workspace as their cloud email environment.
The earliest versions of the malformed prefix attack used a familiar approach to dupe the user: mimicking a voicemail-over-email service. Recent examples have shown more variety in the body copy and call-to-action to the user.
Here are a few recent examples of tactics employed by phishing attackers using malformed URL prefixes.
Spoofed Display Name: In order to deceive the recipient, the attacker impersonates the targeted company’s internal mail system by changing the display name.
Unusual Sender Behavior: This tactic avoids “known bad” scanners by using email addresses and domains that have no previous relationship between the sending address and recipient/organization. Scanners have yet to establish a reputation for the sender or domain.
Payload: The message contains a suspicious link that employs an open redirector domain.
Sense of Urgency: The subject line or body of the message projects a sense of importance. The attacker is attempting to rush users into making a mistake.
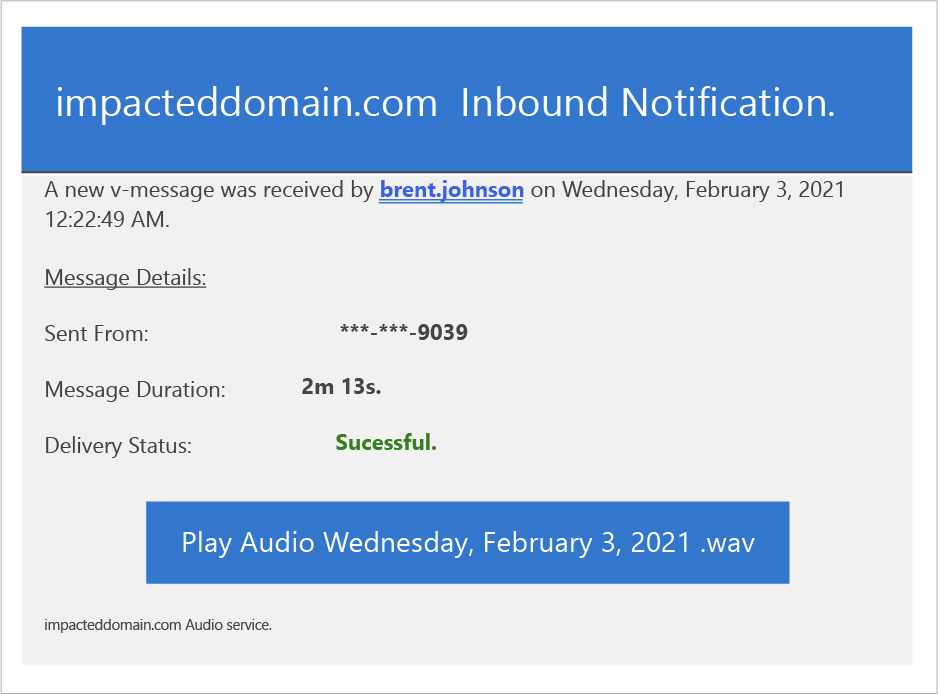
Example phishing email
Here is an example of a phishing attack identified by GreatHorn Threat Detection. The harmful URL that the sender is trying to get users to click is: http:/\brent.johnson.australiasnationalskincheckday.org.au//exr/brent.johnson@impacteddomain.com
This specific phishing attempt impersonates a voicemail service, informing the recipient that they have a voice message. It emulates the appearance and behavior of many email platforms that use cloud-based voicemail services.

The message contains a text-embedded link (Play Audio Date.wav) that redirects to malicious website. The website even includes a reCAPTCHA, a common security feature of legitimate websites, showing the sophistication and subtlety of the attempted attack.
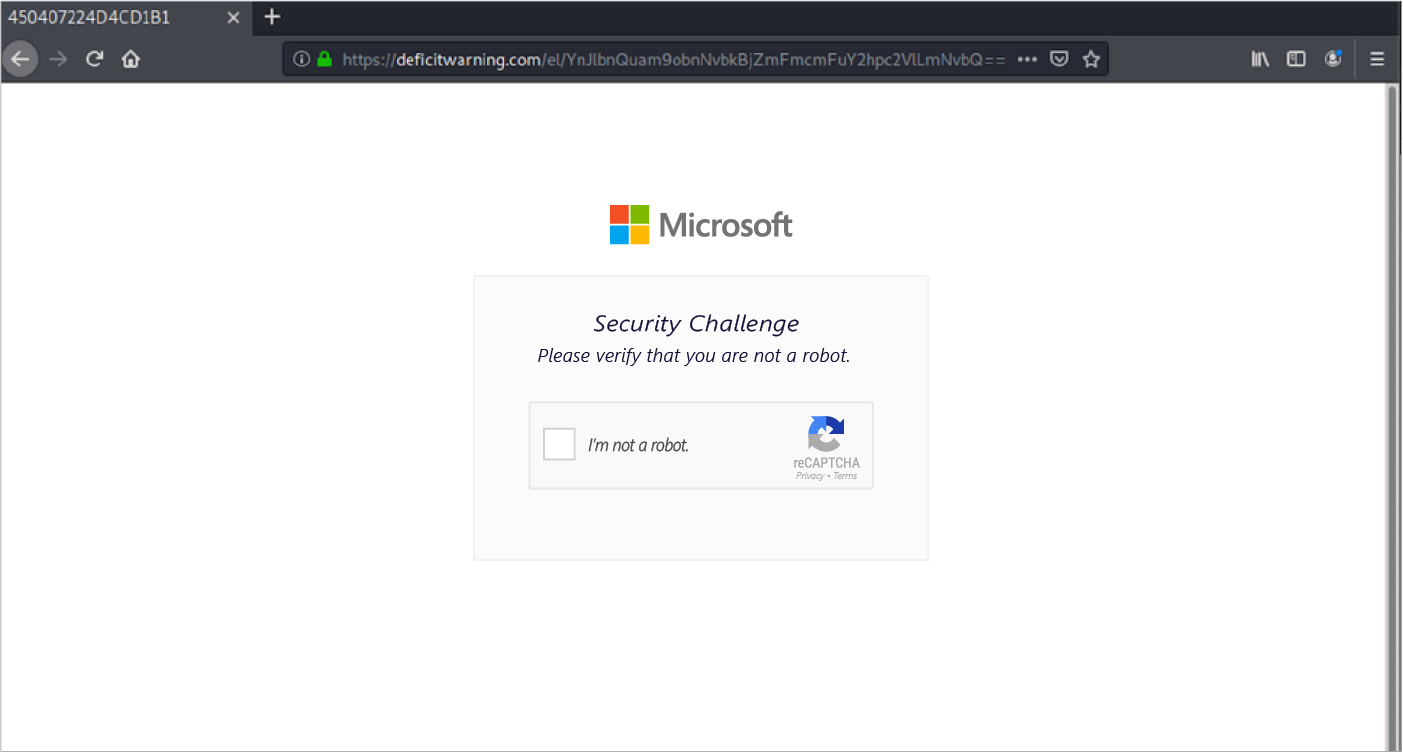
If the recipient continues, they will come to a landing page that is nearly identical to a Microsoft Office login page. The recipient’s email address is already entered, and they are prompted to hit “next.”
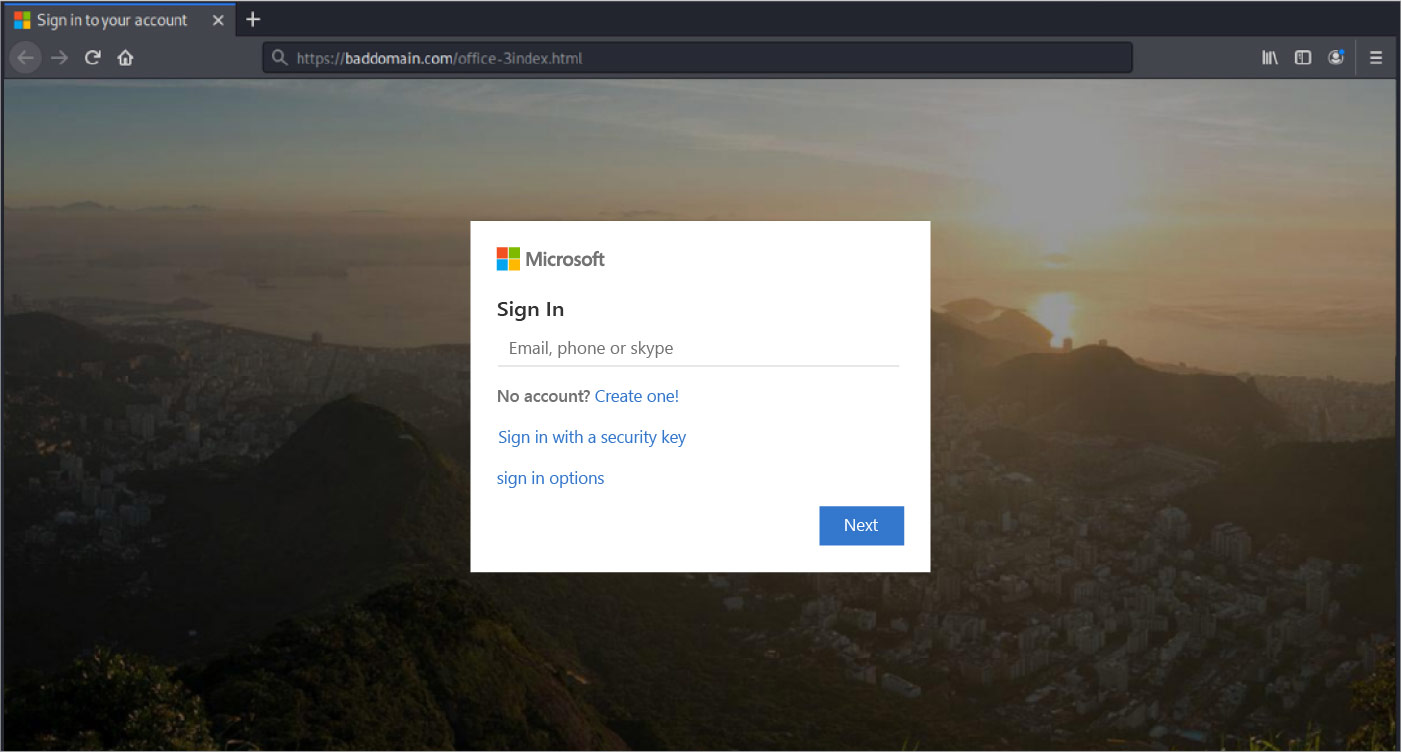
If the user then enters both their username and password, they’ll be providing scammers with their login credentials. The attackers can then gain access to the recipient’s email contact lists and other sensitive data, including cloud storage.
GreatHorn recommends that security teams search their organizational email for messages containing URLs that match the threat pattern (http:/\) and remove any matches.
For customers of the GreatHorn Email Security platform, a protective policy has already been deployed, and protection against this phishing attack has been enforced globally.