MDS Attack
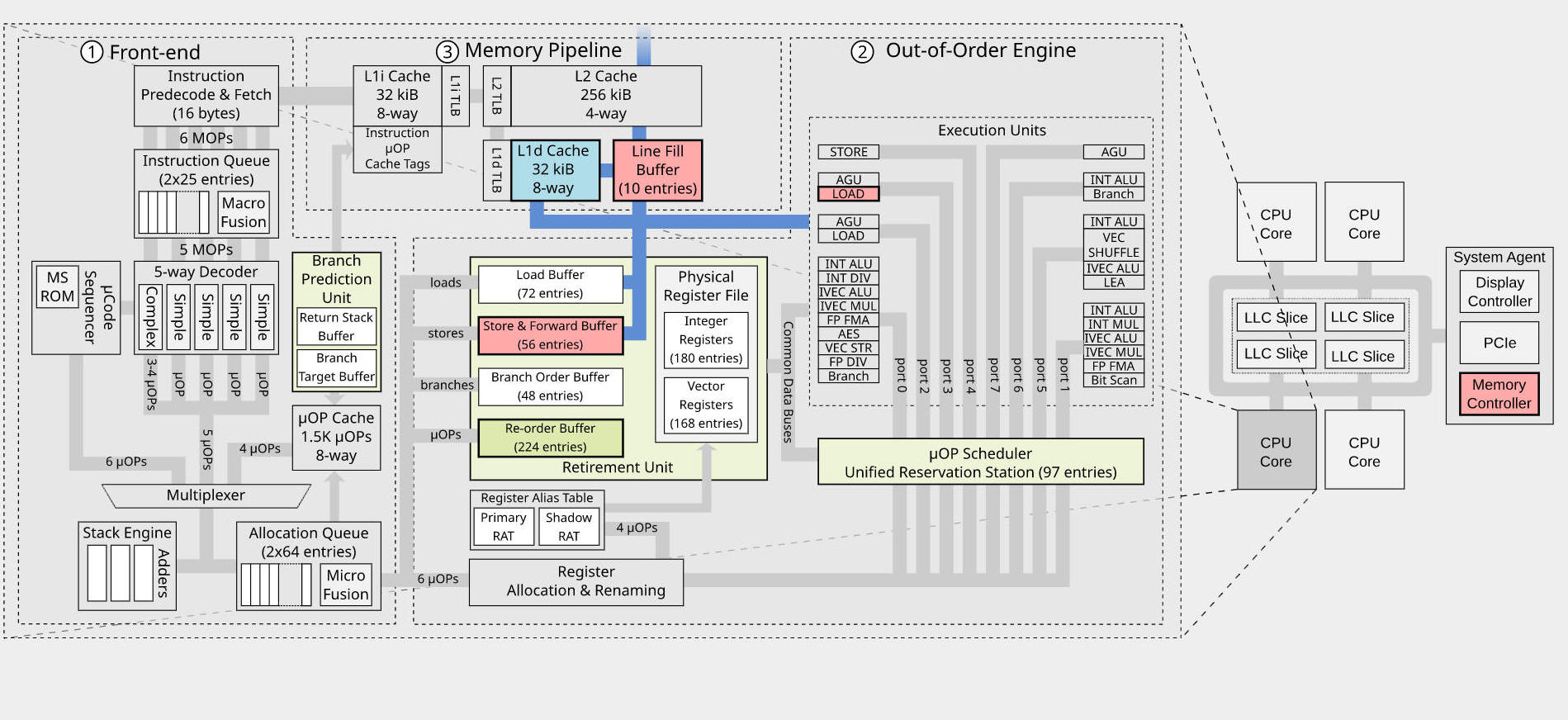
The RIDL and Fallout speculative execution attacks allow attackers to leak private data across arbitrary security boundaries on a victim system, for instance compromising data held in the cloud or leaking your data to malicious websites. Our attacks leak data by exploiting the 4 newly disclosed Microarchitectural Data Sampling (or MDS) side-channel vulnerabilities in Intel CPUs. Unlike existing attacks, our attacks can leak arbitrary in-flight data from CPU-internal buffers (Line Fill Buffers, Load Ports, Store Buffers), including data never stored in CPU caches. We show that existing defenses against speculative execution attacks are inadequate, and in some cases actually make things worse. Attackers can use our attacks to leak sensitive data despite mitigations, due to vulnerabilities deep inside Intel CPUs.
RIDL
RIDL (Rogue In-Flight Data Load) shows attackers can exploit MDS vulnerabilities to mount practical attacks and leak sensitive data in real-world settings. By analyzing the impact on the CPU pipeline, we developed a variety of practical exploits leaking in-flight data from different internal CPU buffers (such as Line-Fill Buffers and Load Ports), used by the CPU while loading or storing data from memory.
We show that attackers who can run unprivileged code on machines with recent Intel CPUs - whether using shared cloud computing resources, or using JavaScript on a malicious website or advertisement - can steal data from other programs running on the same machine, across any security boundary: other applications, the operating system kernel, other VMs (e.g., in the cloud), or even secure (SGX) enclaves.
We presented our paper titled RIDL: Rogue In-Flight Data Load on these attacks at the 40th IEEE Symposium on Security and Privacy, on May 20th 2019.
Fallout
Fallout demonstrates that attackers can leak data from Store Buffers, which are used every time a CPU pipeline needs to store any data. Making things worse, an unprivileged attacker can then later pick which data they leak from the CPU's Store Buffer.
We show that Fallout can be used to break Kernel Address Space Layout Randomization (KASLR), as well as to leak sensitive data written to memory by the operating system kernel.
Ironically, the recent hardware countermeasures introduced by Intel in recent Coffee Lake Refresh i9 CPUs to prevent Meltdown make them more vulnerable to Fallout, compared to older generation hardware.
We will present our paper titled Fallout: Leaking Data on Meltdown-resistant CPUs at the 26th ACM Conference on Computer and Communications Security, on November 2019.
Overview
Our attacks can leak confidential data across arbitrary security boundaries in real-world settings (cloud, browsers, etc.). The reason our attacks are impervious to all the existing defenses against speculative execution attacks is that they can leak in-flight data. Unlike other recent attacks such as Spectre, Meltdown, and Foreshadow which are based on vulnerabilities leaking data from the CPU caches, RIDL and Fallout collect data from internal CPU buffers (Line Fill Buffers, Load Ports, Store Buffers). Intel describes the exploited vulnerabilities as "Microarchitectural Data Sampling" (MDS) - where "sampling" is another way of saying that we can leak in-flight (or "sampled") data from many of these microarchitectural buffers. A total of 5 CVEs were assigned by Intel for RIDL ([MFBDS] CVE-2018-12130, [MLPDS] CVE-2018-12127, [MDSUM] CVE-2019-11091, [TAA] CVE-2019-11135) and Fallout ([MSBDS] CVE-2018-12126) exploits.
Most importantly, our research shows that what last year appeared to be exceptional one-time speculative execution bugs are actually systemic, and the problems in modern CPUs may go much deeper than we initially thought. If CPUs have become so complex that chip vendors cannot keep their security under control, hardware vulnerabilities will be the new hunting ground for sophisticated attackers. And we may have no idea how many zero-day hardware vulnerabilities are still up for grabs. If we can no longer trust our hardware, the foundation on which we build all security solutions is crumbling away.
