"This attack is hilarious. Install a client cert in a browser, MITM any connection it makes to certain servers."
-- Prof. Matt Green
(John Hopkins University) Attack Overview
Overview of the Attack
KCI Attacks against TLS
Protection of Internet communication is crucial in today's hyperconnected world. The industry standard for encrypting private and sensitive communication data over potentially adversarial controlled network cables and radio signals is TLS. ESSE, the security team of RISE GmbH, discovered a new vulnerability in the ageing TLS protocol. The newly discovered weakness allows to open supposedly securely encrypted TLS communication to full-blown Man-in-the-Middle (MitM) attacks: An attacker can impersonate trusted servers without being in possession of the servers' secret keys, and can so eavesdrop on the unencrypted messages, snoop on passwords, love letters, payment data, and modify personal, private communication and transactions at will. Highly used systems such as the Safari Web Browser on Mac OS X and Facebook have been vulnerable to the attack. Paired with insecure practices common in various systems, we found the attack to be easily exploitable. Outdated, insecure protocol options have to be disabled by system implementers, and secure practices concerning the handling and configuration of client and server certificates have to be adopted by the wider Internet community in order to bury the issue forever as an historical anecdote in the annals and history books of cryptographic communication.

"This attack is hilarious. Install a client cert in a browser, MITM any connection it makes to certain servers."
-- Prof. Matt Green
(John Hopkins University) Attack Overview
Overview of the Attack
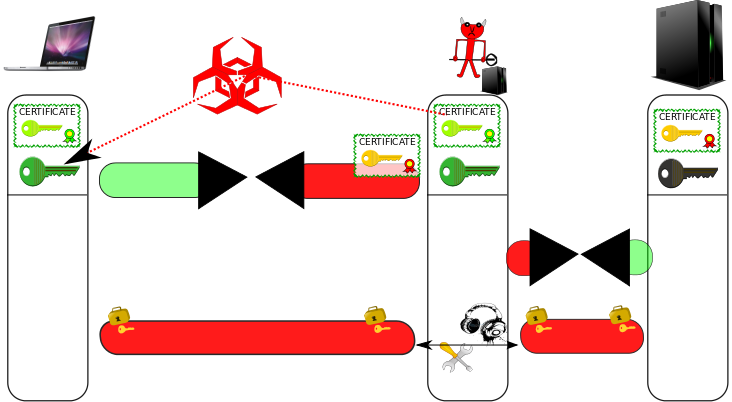
In a KCI-based MitM attack, an attacker who is in possession of a client certificate's private key installed at a victim, can impersonate any server. The attack is illustrated in the following figure.
Figure: KCI-based MitM attack
Man-in-the-Middle Scenario / Motivation
Assume an attacker sits anywhere on the communication line between the client and the server. He can eavesdrop on all messages exchanged between client and server, and tamper with, modify, or block messages at his discretion. This is a common assumption (e.g., a hacker could control your wifi traffic or let your device automatically connect to a rogue access point, or he could sit on any network node between your device and the server, he could re-route your traffic using ARP Spoofing or BGP manipulations. The NSA uses QUANTUM INSERT, which amounts to equivalent capabilities). That is why many systems on the Internet use cryptographic protocols such as TLS to prevent attackers from eavesdropping on sensitive communication data and from modifying the plaintext of exchanged data.
Steps to Attack
However, the TLS protocol (also known as SSL) is very convoluted, old, and carries too much historical baggage. During a KCI-based MitM attack (KCI stands for "Key Compromise Impersonation"), as depicted in the figure above, the attacker interferes with the communication initialization of the TLS protocol between client and server, and forces the client to use insecure TLS handshake/authentication options together with a client certificate for which he is in possession of the private key. If the client bends to the server's demand, the attacker then impersonates the server, and the client establishes an encrypted and authenticated connection to the attacker, believing it is talking to the server. Subsequently, the attacker initiates a normal encrypted connection to the server. He then forwards messages from the client to the server (and vice versa), and is able to eavesdrop on the plaintext, and also to modify arbitrarily the content of the communication. For many web and mobile applications, a successful attack means that a user's session or profile is completely compromised and under the control of the attacker from this point on: Electronic payments may be initiated and re-directed to the attacker's account, private messages could be read and spoofed, etc. Possible damage is in most cases only limited by the attacker's imagination and creativity.
Controlling a Client Certficate
Various options for an attacker to control the private key of a client certificate installed at a client device exists and are conceivable. One very natural way that comes to mind would be to employ social engineering techniques: E.g., an attacker hands you a client certificate, so that you can access library resources, or be able to use a hotel's wifi (see video demo below). The attacker is then able to compromise connections to completely different, unrelated servers (e.g., to facebook). Other ways for an attacker to install client certificates are discussed in more detail in our research paper: For example, a software vendor might include a benign looking client certificate as a backdoor; or an also completely benign looking mobile app (e.g., a game) might install a client certificate in the system's certificate store, which an attacker then uses to exploit different apps (e.g., an electronic banking application). What aggravates the attack is that it is common practice in many systems to handle client certificates in an insecure way. We hope the publication of this attack raises awareness so that system implementers and administrators move to more secure practices.
Video Demo: Attacking Facebook
To illustrate that KCI-based MitM attacks are not just academically interesting but relevant in the real world, we demonstrate in a proof-of-concept exploit the practicability and feasibility of the attack using widely used systems: In the video below, a user uses the Safari web browser on Mac OS X to connect to facebook. Older Mac OS X systems (OS X 10.7 and earlier) remain vulnerable to the attack, and we recommend users to upgrade their systems to be secure. Also, this attack was recorded after facebook implemented successfully all possible server-side mitigations. Due to old server certificates still being valid for some time (and findable for people who know where to look at), this exact attack is still possible against unprotected, unpatched client machines. In the end of the video, we also show mitigation measures to protect your system from the attack in case your hardware does not allow you to update your operating system to the newest version. For the purpose of this proof-of-concept demonstration, the attacker in the video only swaps lovely cat pictures with an attacker-controlled picture, disseminating disinformation: "Facebook is closing down soon", is the message to the user; and, more disconcertingly: "All cats drowned". Furthermore, the attacker recommends leaving facebook and joining (the decentralized, community-run, non-profit, alternative social network) Diaspora instead. However, in a real attack, the attacker could easily do much more damage than this (while possibly remaining stealthy and fully undetected): The attack gives the attacker complete control over the client-side code running in the user's browser; he can present the user arbitrarily modified content, and even initiate actions on behalf of the user, such as sending of spoofed messages, or controlling facebook payment transactions.
During the first minute of the video, the original, unadulterated facebook profile is presented: Lovely cat photos and drawings. At minute 1:02, the user connects to the Internet (via a maliciously operated) hotel wifi network. At the captive portal of the hotel's wifi, the user is asked to authenticate with his last name and room number, and is subsequently tricked into installing a TLS client certificate. This legitimate looking wifi access point could very well be operated by an attacker sitting in the neighbouring hotel room in the real world. (However, this does not mean that an attacker necessarily has to be close to the victim to pull of this attack: This is just one way for an attacker to control a client certificate. Please find a more detailed discussion about different attack possibilities in the research paper). Captive portal software outside this demo exists which operates similarly. This completes phase 1 of the attack. In phase 2 of the attack, starting at minute 2:03 in the video, the attacker, under the hood, interferes with the connection initialization to facebook, and forces the client to use an insecure handshake with client authentication, requesting the previously installed certificate from the system. The video only displays the visible effects of the attack from the perspective of the victim. Minute 2:03 until 4:20 in the video demonstrate the result of the maliciously altered, attacker controlled communication between the client and facebook. Starting at minute 4:30, a mitigation measure for older, unpatched clients is presented (setting OCSP checking to strict mode, see discussion below).