Introduction
Malicious spam (malspam) pushing Hancitor malware (also known as Chanitor or Tordal) changed tactics on Monday 2017-10-16. Instead of pushing Microsoft Word documents with malicious macros, this malspam began pushing Word documents taking advantage of Microsoft's Dynamic Data Exchange (DDE) technique. According to BleepingComputer, attacks using this technique have existed since the early 90s, but DDE has gained notoriety in the past few weeks due to a series of recent reports. (Use a search engine for "DDE attack" or "DDE exploit" to find some results).
Ultimately, these DDE attacks are somewhat less effective than malicious macros, and Microsoft maintains DDE functionality is not a vulnerability. Victims must click through several warnings to get infected from these documents. Otherwise, little has changed for infection characteristics noted in my previous diary covering Hancitor malspam last month. Today's diary examines a wave of Hancitor malspam from Monday, 2017-10-16.
The emails
Monday's wave used a DocuSign template we've seen before from Hanictor malspam. Several people on Twitter also saw Monday's malspam, including @cheapbyte, @GossiTheDog, @James_inthe_box, @noottrak, and @Ring0x0. Links from the emails went to newly-registered domains that returned a malicious Word document.
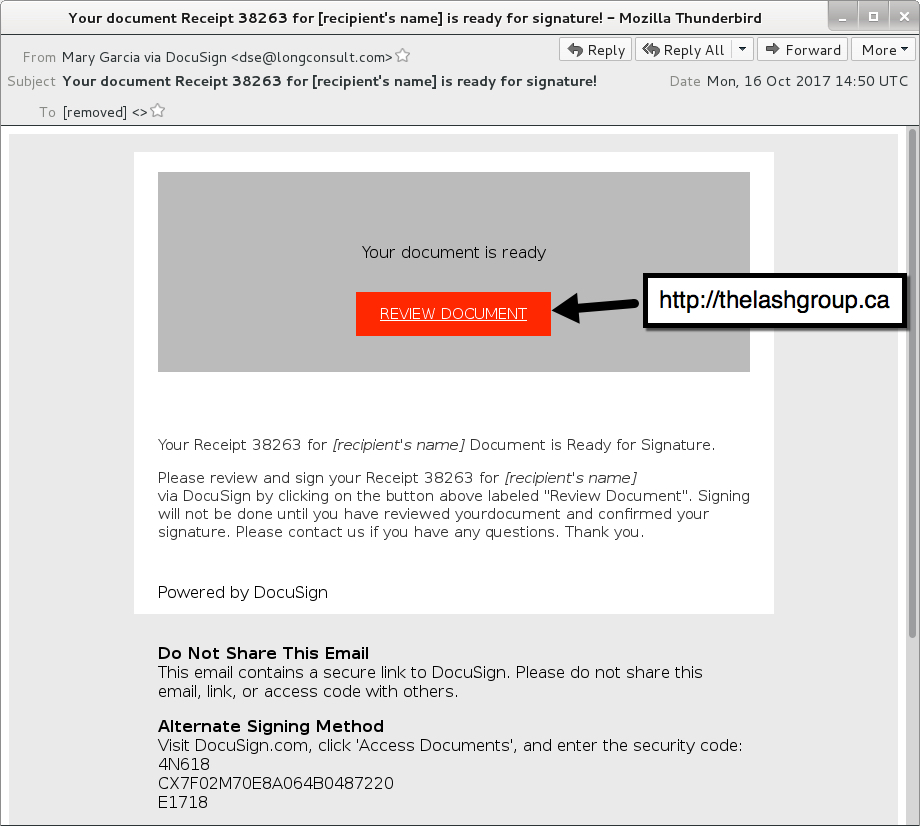
Shown above: An example of the malspam.
The Word document
I tried a link from the emails in Windows 10 running Office365. As usual, people must ignore various warnings to kick off an infection. First, because the Word document was downloaded from the Internet, I had to enable editing to escape Protected View. Then, I had to click through three dialogue windows to infect my Windows host.
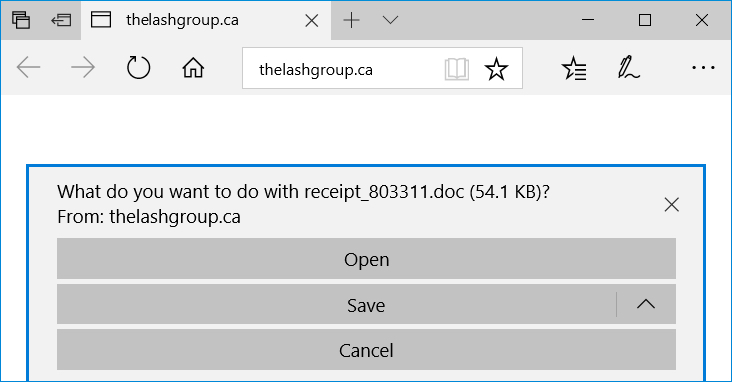
Shown above: Following a link from one of the emails.
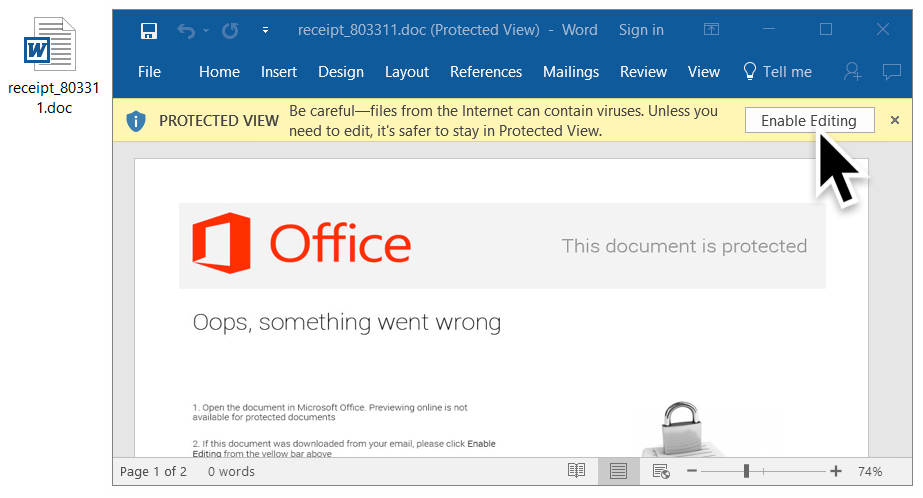
Shown above: Escaping Protected View by enabling editing.

Shown above: 1st dialogue box (1 of 3).
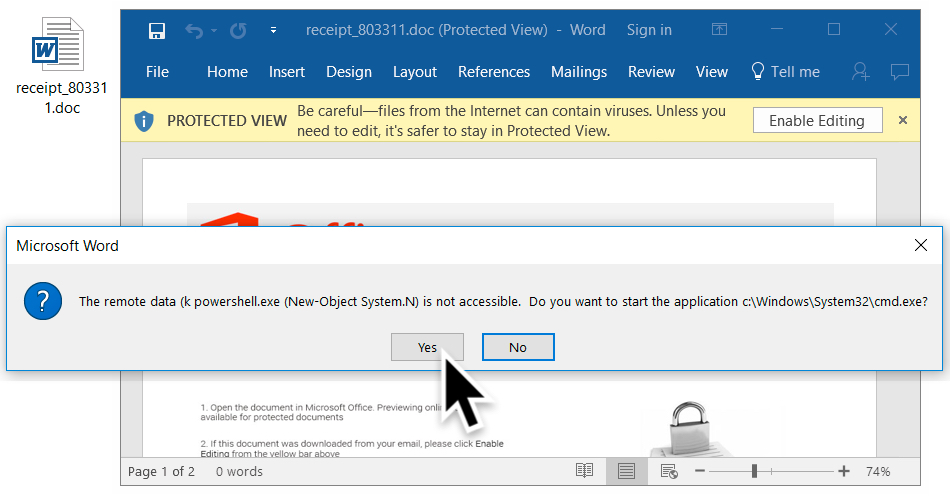
Shown above: 2nd dialogue box (2 of 3).
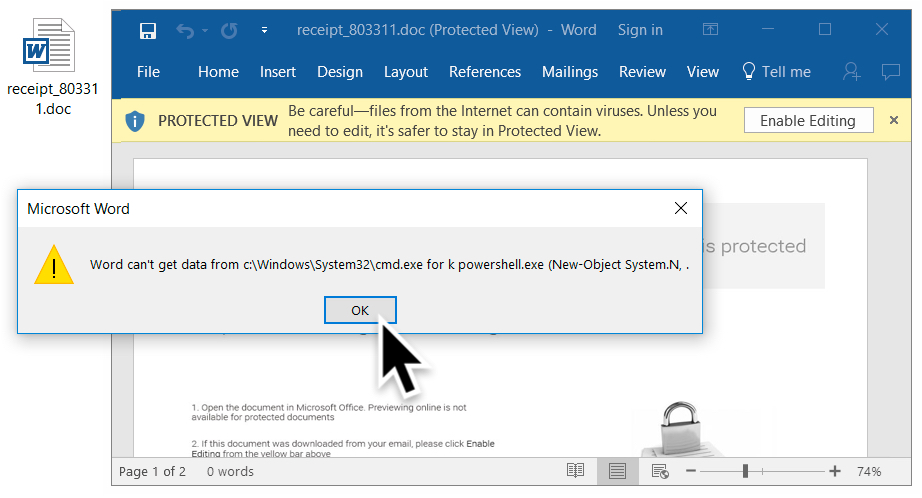
Shown above: 3rd dialogue box (3 of 3).
The traffic
Traffic remains the same as last time, except we find an HTTP GET request for a Hancitor (or a Hancitor-related) executable after the document is downloaded. Previously, this initial malware was part of the malicious document macro. However, with this DDE attack, the initial executable is downloaded separately.
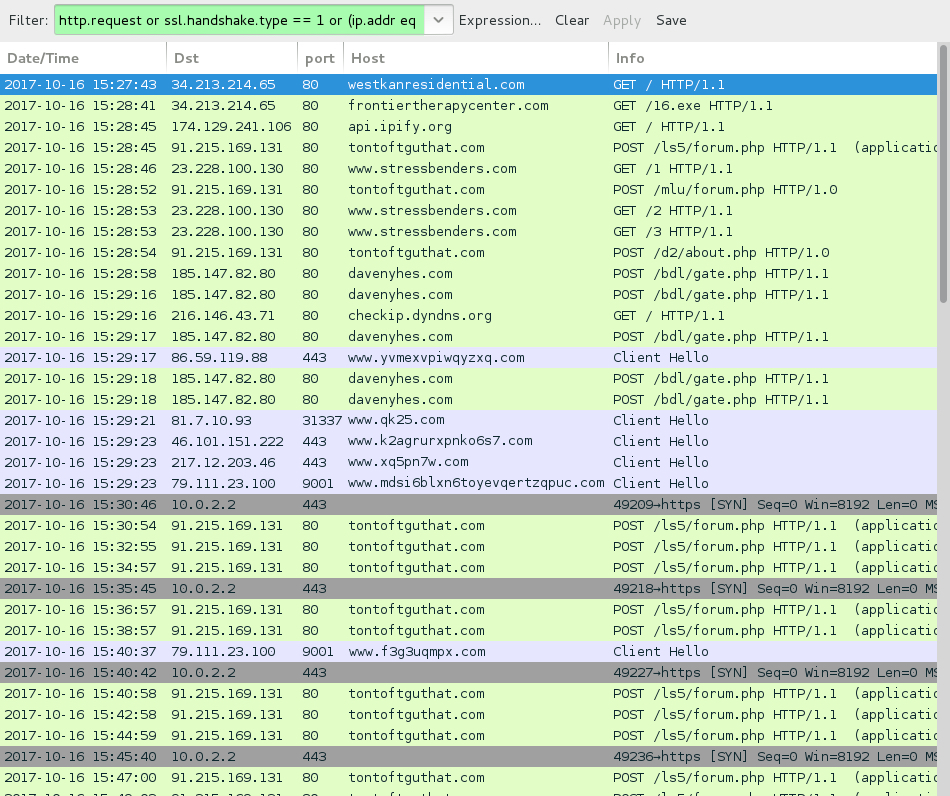
Shown above: Traffic from an infection filtered in Wireshark.
Indicators of compromise (IOCs)
Emails collected:
Date/Time: Monday 2017-10-16 as early as 14:50 UTC thru at least 16:11 UTC
Subject: Your document Receipt [random 5-digit number] for [recipient's name] is ready for signature!
Sending email address (spoofed): "Benjamin Garcia via DocuSign" <dse@longconsult.com>
Sending email address (spoofed): "Carrie Robinson via DocuSign" <dse@longconsult.com>
Sending email address (spoofed): "Carrie Stanley via DocuSign" <dse@longconsult.com>
Sending email address (spoofed): "Mary Garcia via DocuSign" <dse@longconsult.com>
Sending email address (spoofed): "Monique Clark via DocuSign" <dse@longconsult.com>
Sending email address (spoofed): "Monique Wilson via DocuSign" <dse@longconsult.com>
Sending email address (spoofed): "Saul Walker via DocuSign" <dse@longconsult.com>
Received: from longconsult.com ([45.49.169.80])
Received: from longconsult.com ([68.98.214.133])
Received: from longconsult.com ([68.188.99.59])
Received: from longconsult.com ([173.209.154.162])
Received: from longconsult.com ([205.144.215.157])
Received: from longconsult.com ([208.181.214.155])
Links from the malspam:
bridlewoodpark[.]ca
celebration-living[.]ca
celebration-living[.]com
cloudninecondos[.]com
condoallure[.]com
donmillstowns[.]ca
me2condominium[.]com
me2condominiums[.]com
thelashgroup[.]ca
tier1mc[.]com
westkanresidential[.]ca
westkanresidential[.]com
woodstockliving[.]ca
y2mediagroup[.]ca
y2mediagroup[.]com
Traffic noted during while infecting hosts in my lab:
34.213.214.65 port 80 - frontiertherapycenter[.]com - GET /16.exe
185.82.217.224 port 80 - frontiertherapycenter[.]com - GET /16.exe
185.124.188.82 port 80 - aningrolcoligh[.]ru - POST /ls5/forum.php
91.215.169.131 port 80 - tontoftguthat[.]com - POST /ls5/forum.php
91.215.169.131 port 80 - tontoftguthat[.]com - POST /mlu/forum.php
91.215.169.131 port 80 - tontoftguthat[.]com - POST /d2/about.php
27.121.64.185 port 80 - leicam[.]com[.]au - GET /1
23.228.100.130 port 80 - www.stressbenders[.]com - GET /1
23.228.100.130 port 80 - www.stressbenders[.]com - GET /2
23.228.100.130 port 80 - www.stressbenders[.]com - GET /3
185.147.82.80 port 80 - davenyhes[.]com - POST /bdl/gate.php
api.ipify.org - GET / (location check by the infected host)
checkip.dyndns.org - GET / (location check by the infected host)
Various IP addresses, various ports - Tor traffic
10.0.2.2 port 443 - TCP SYN packet sent every 5 minutes
Artifacts from an infected host:
SHA256 hash: f945105f5a0bc8ea0d62a28ee62883ffc14377b6abec2d0841e88935fd8902d3
File name: receipt_[6 random digits].doc
File description: Word document using DDE attack technique
SHA256 hash: a647d12d6298c8aef225d77f1e2b605ae78fadd7360ab0c48363d2e461612150
File location: C:\Users\[username]\AppData\Local\Temp\tvs.exe
File description: Hancitor or Hancitor-related executable
SHA256 hash: 8f94cee61a76c7b9612381978876dcd996c15ae8da50fd75d700a05df571d10a
File location: C:\Users\[username]\AppData\Local\Temp\tvs.exe
File description: Hancitor or Hancitor-related executable seen later on another infected host
SHA256 hash: 15e9493c4f50b672fe801108d31ac6660d1d5787e0c71964a935a893aab12032
File location: C:\Users\[username]\AppData\Local\Temp\BN5A30.tmp
File location: C:\Users\[username]\AppData\Roaming\Yhaba\ehyl.exe
File description: DELoader/ZLoader
Final words
As mentioned earlier, these DDE attacks are no more effective than malicious macro-based attacks. Each requires victims to click through a series of warnings to get infected. Furthermore, it's relatively easy for system administrators (and the technically inclined) to follow best security practices on their Windows computers. Using Software Restriction Policies (SRP) or AppLocker can easily prevent these types of malspam-based infections from occurring.
Traffic and malware samples for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net