You might not believe it, but it's possible to spy on secret conversations happening in a room from a nearby remote location just by observing a light bulb hanging in there—visible from a window—and measuring the amount of light it emits.
A team of cybersecurity researchers has developed and demonstrated a novel side-channel attacking technique that can be applied by eavesdroppers to recover full sound from a victim's room that contains an overhead hanging bulb.
The findings were published in a new paper by a team of academics—Ben Nassi, Yaron Pirutin, Adi Shamir, Yuval Elovici and Boris Zadov—from the Israeli's Ben-Gurion University of the Negev and the Weizmann Institute of Science, which will also be presented at the Black Hat USA 2020 conference later this August.
The technique for long-distance eavesdropping, called "Lamphone," works by capturing minuscule sound waves optically through an electro-optical sensor directed at the bulb and using it to recover speech and recognize music.
How Does the 'Lamphone Attack' Work?
The central premise of Lamphone hinges on detecting vibrations from hanging bulbs as a result of air pressure fluctuations that occur naturally when sound waves hit their surfaces and measuring the tiny changes in the bulb's output that those small vibrations trigger to pick up snippets of conversations and identify music.
"We assume a victim located inside a room/office that contains a hanging light bulb," the researchers said. "We consider an eavesdropper a malicious entity that is interested in spying on the victim in order to capture the victim's conversations and make use of the information provided in the conversation (e.g., stealing the victim's credit card number, performing extortion based on private information revealed by the victim, etc.)."
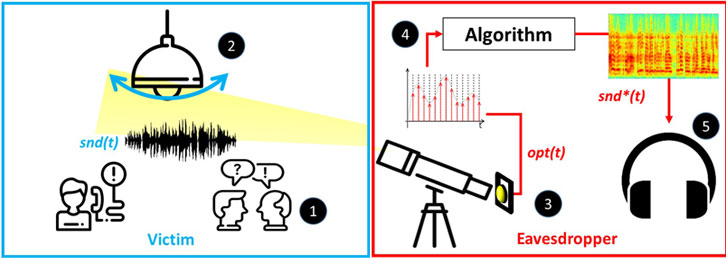
To achieve this, the setup consists of a telescope to provide a close-up view of the room containing the bulb from a distance, an electro-optical sensor that's mounted on the telescope to convert light into an electrical current, an analog-to-digital converter to transform the sensor output to a digital signal, and a laptop to process incoming optical signals and output the recovered sound data.
"Lamphone leverages the advantages of the Visual Microphone (it is passive) and laser microphone (it can be applied in real-time) methods of recovering speech and singing," the researchers said.
Lamphone Attack Demonstration
The result? The researchers recovered an audible extract of President Donald Trump's speech that could be transcribed by Google's Speech to Text API. They also reproduced a recording of the Beatles' "Let It Be" and Coldplay's "Clocks" that were clear enough to be recognized by song identification services like Shazam and SoundHound.
