Punycode Phishing Attack
There are only a handful of rules that you need to know to counter any phishing attack that you may be exposed to on the Internet, right?
Check the web address and make sure it is the right one. Also, make sure you don't follow any links on pages or in messages that you don't trust 100%.
While that is sound advise, and will help you identify the bulk of phishing attacks, Chinese security researcher Xudong Zheng just demonstrated that things may not always be that easy.
Punycode Phishing Attack
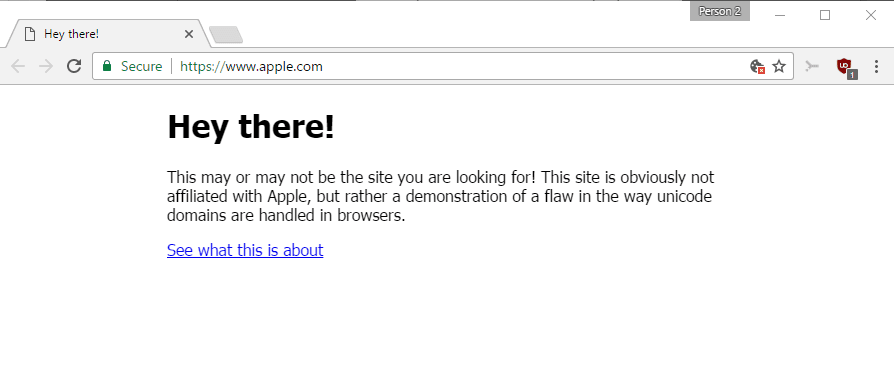
He set up a special domain to demonstrate how this works. Point your browser to https://www.аррӏе.com/ and watch what happens.

Somehow, you did not end up on Apple's website, but on a site that uses the correct URL, seemingly, and has a security certificate. If an attacker would have replicated Apple's website, and not displayed the "hey there" message, would you have noticed that you are not on Apple's site?
You wonder probably how this works. The technique uses something that is called Punycode. Broken down to the essentials, Punycode enables you to register domain names with characters that are not native to a language.
A basic example would be the German city of München. The letter ü is not available in English for instance, and that is where Punycode comes into play. The Punycode version of München is xn--mnchen-3ya. You can convert text on a site like Punycoder to see how other names are converted.
One of the main issues from a security perspective is that some characters are not easily distinguishable. Compare the ASCII "a" with the Cyrillic "а" and tell me if you see the difference.
An attack that makes use of these similarities are called homograph attack. Modern browsers come with security features that protect users from these kind of attacks.
If you open this аpple.com domain name for instance, you will notice that most browsers displays the Punycode version of it (http://xn--pple-43d.com/) instead automatically.
The security researcher discovered however that the protection in Chrome or Firefox fail if every single character is replaced with a foreign one. This is why this аррӏе.com domain name displays as if it is the real deal, even though it is actually xn--80ak6aa92e.com.
Good news is that some browsers protect you against the attack already. If you use Internet Explorer, Microsoft Edge, Safari or Vivaldi, you will notice that the Punycode address is displayed automatically.
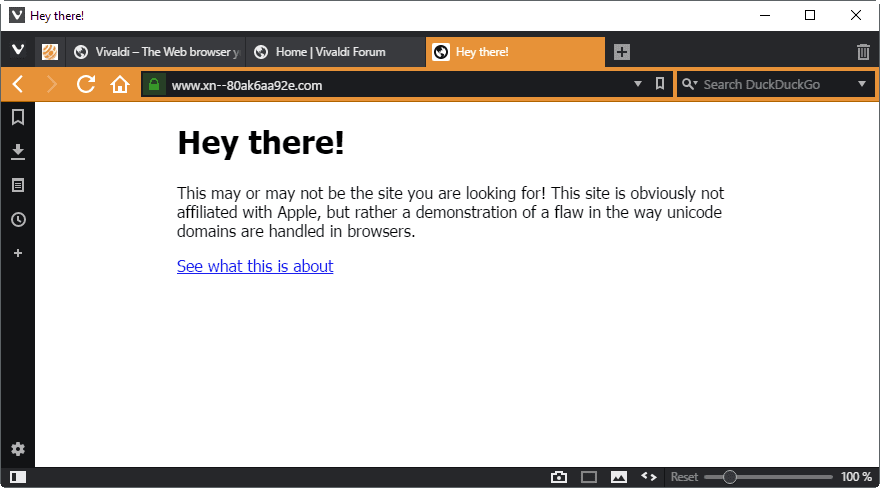
If you open the same domain name in Chrome, Firefox or Opera however, apple.com is displayed instead.
That's a big problem obviously, as that address is not distinguishable from Apple's real domain name.
The researcher disclosed the vulnerability to Google and Mozilla on January 20, 2017. Google created a patch for the issue which the company plans to roll out later this month in Chrome 58.
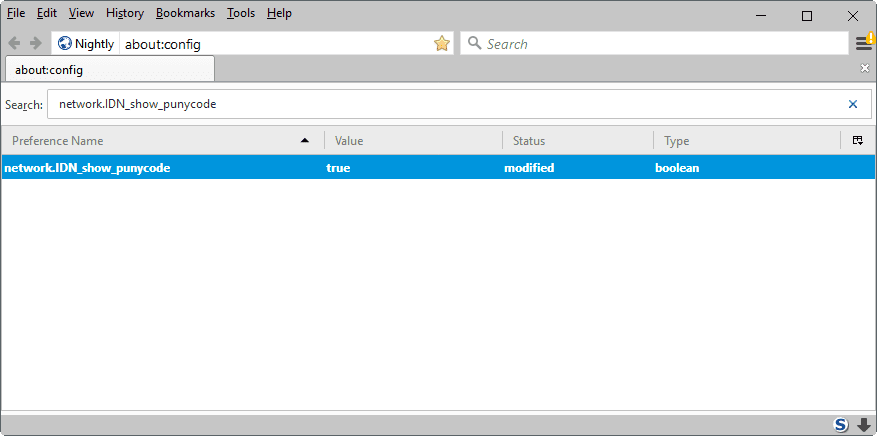
Mozilla filed a bug on Bugzilla, but no consensus appears to have been reached yet. Firefox users who want to be on the safe side of things need to make a change in the configuration:
Type about:config in the Firefox address bar and hit the Enter-key.
Confirm that you will be careful.
Search for network.IDN_show_punycode.
Double-click the preference to set it to true.
This forces Firefox to show Punycode when it is used.
Chrome users on the other hand need to wait until Google releases a fix for the browser.
Update: Chrome users can install Punycode Alert that warns users when a Punycode containing URL is loaded.
Now You: would you have fallen for the attack?
Summary
Punycode Phishing Attack fools even die-hard Internet veterans
Article NamePunycode Phishing Attack fools even die-hard Internet veterans
DescriptionChinese security researcher Xudong Zheng discovered a new phishing attack using Punycode that will fool even die-hard Internet veterans.
AuthorMartin Brinkmann
PublisherGhacks Technology News
Logo