RIDL attack
RIDL: Rogue In-Flight Data Load pdf
Researchers from VUSec - the Systems and Network Security Group at Vrije University in Amsterdam, and from the Helmholtz Center for Information Security (CISPA) have developed the RIDL (short for Rogue In-Flight Data Load) attack.
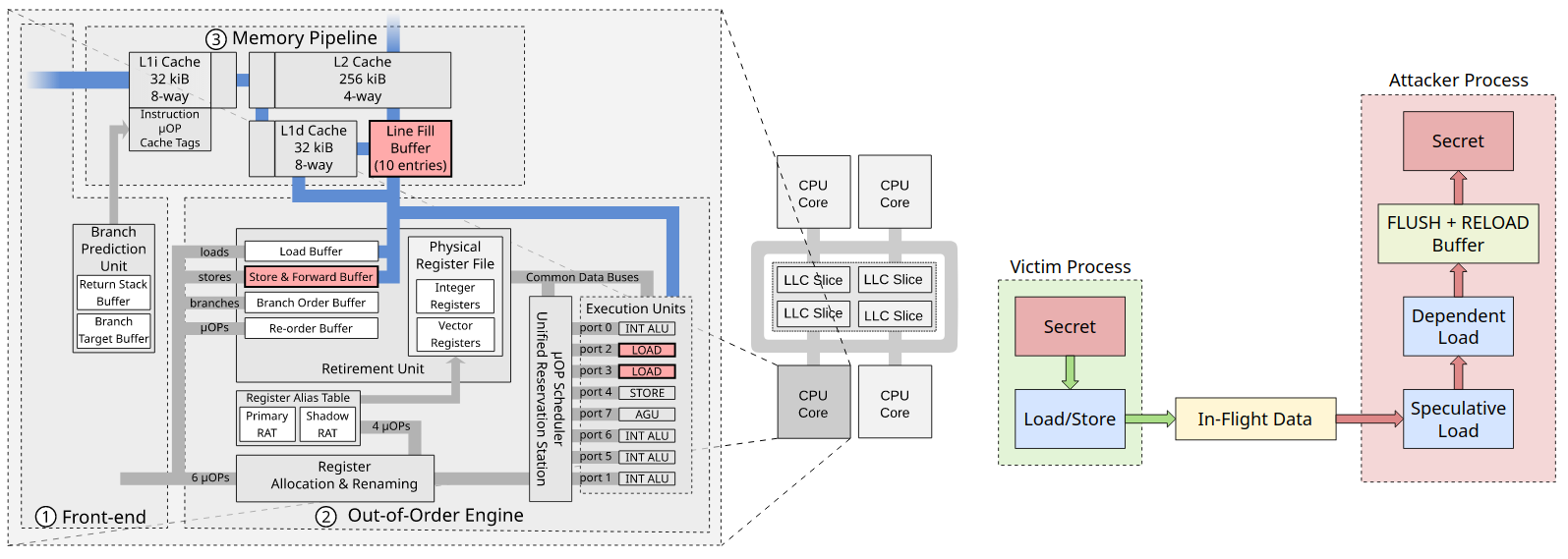
Here's how in-flight buffers work and how sensitive data can flow to the attacker's process:

RIDL exploits three bugs in Intel CPUs to leak data from different internal CPU buffers (e.g. Line-Fill Buffers and Load Ports). The processor uses these buffers for loading or storing data in memory.
After rummaging through CPU patent specifications, VUSec found that leaks from CPU buffers were possible. The researchers say that only Intel CPUs are affected.
Needless to say that Intel's processing technology is present in plenty of devices, from servers, to laptops, and desktop computers. So both the consumer and business sector is impacted.
"We show that attackers who can run unprivileged code on machines with recent Intel CPUs - whether using shared cloud computing resources, or using JavaScript on a malicious website or advertisement - can steal data from other programs running on the same machine, across any security boundary: other applications, the operating system kernel, other VMs (e.g., in the cloud), or even secure (SGX) enclaves."
In the sped-up video below VUSec shows how they were able to obtain information from the /etc/shadow file - where a Linux machine keeps encrypted password, account or expiration values.
They were able to do this by continuously trying to authenticate via an SSH connection. For now, the entire process takes about 24 hours.
In another demo video, the researchers show that they were able to use RIDL to leak recent kernel data.
After first reading 0 bytes from /proc/version, the team could leak the full contents of /proc/version, even if the data was never present in the userspace.
A third video demonstrates how VUSec was able to leak a string from another process using Javascript and WebAssembly in the SpiderMonkey engine.