Název
Obrázek
Popis
DHCP
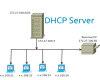



DHCP
Název | Obrázek | Popis |
DHCP |  | Dynamic Host Configuration Protocol) je v informatice název protokolu z rodiny TCP/IP nebo označení odpovídajícího DHCP serveru či klienta. |
| ||
| DHCP Attack |  | To dynamically obtain IP address information, a client makes a DHCP request. A DHCP server sends back a DHCP response in which includes information as an IP address, subnet mask, and default gateway. If an attacker puts and false DHCP server in our LAN network, the rogue DHCP server can respond to a client’s DHCP request. Even if the rogue DHCP server and the actual DHCP server both respond to the request of our PC, the PC will use the rogue DHCP server’s response if it reaches the PC faster than actual DHCP server. |
| DHCP snooping |  | The DHCP snooping feature on Cisco and Juniper switches can be used to mitigate a DHCP server spoofing attack. With this mechanism switch ports are configured in two different state, the trusted and untrusted state. If a port is configured to be trusted, it can receive DHCP responses. In other way, if a port is untrusted, it is not allowed to receive DHCP responses, and if a false attackers DHCP response attempts to enter an untrusted port, the port will be disabled. |
| Special situation DoS attack |  | DoS attack against the DHCP server is another kind of attack that we can slow down by a special technique. This attack is special because the attacker can in this situation repeatedly request IP address assignments from the DHCP server and in this way drain the pool of addresses available from the DHCP server. The attacker can accomplish this by making the DHCP requests appear to come from different MAC addresses. To resolve this DoS attack, the DHCP snooping feature can be set to limit the number of DHCP messages per second that are allowed to pass the interface. In this way we will slow down or completely prevent a flood of spoofed DHCP requests. To set the limit of DHCP messages on a port to five messages per second we use this command: |