Ryuk Ransomware Crew Makes $640,000 in Recent Activity Surge
A new ransomware strain named Ryuk is making the rounds, and, according to current reports, the group behind it has already made over $640,000 worth of Bitcoin.
Attacks with this ransomware strain were first spotted last Monday, August 13, according to independent security researcher MalwareHunter, who first tweeted about this new threat.
MalwareHunterTeam
@malwrhunterteam
From 13th this month, we seen 5 victims of a ransomware. At least 3 of them are companies (from those, 2 are from US, 1 from Germany, and 1 of the 3 is healthcare related).
The ransom note seems Bitpaymer, encrypted files seems Hermes.
Strange.
🤔@BleepinComputer @demonslay335
9:00 PM - Aug 17, 2018
21
20 people are talking about this
Twitter Ads info and privacy
Ryuk used in targeted attacks only
There have been several reports from victims regarding infections with Ryuk in the past week, including one on the Bleeping Computer forums.
But despite these reports, security researchers from various companies have not been successful at identifying how this ransomware spreads and infects victims.
The common train of thought is that this ransomware spreads via targeted attacks, with the Ryuk crew targeting selected companies one at a time, either via spear-phishing emails or Internet-exposed and poorly secured RDP connections, albeit researchers have not been able to pinpoint the exact entry vector for infections as of yet.
"According to what we can see right now, it seems the attacks are targeted, i.e. a result of some manual compromise," Mark Lechtik, a Check Point security researcher, told Bleeping Computer in a private conversation today.
"Reason for this is that the malware needs Admin privileges to run, which it doesn't achieve on its own. Something else that executes it had to achieve this privilege," he added. "But no artifact was found to show what spawned the execution of the malware (i.e. no mail, document, script etc.)."
Ryuk has ties to Hermes, previously tied to North Korea
A report published today by cyber-security firm Check Point also points out that Ryuk may be the work of the same people who developed the Hermes ransomware —or at least someone who gained access to the Hermes ransomware source code.
A BAE Systems report from October 2017 revealed connections between the Hermes 2.0 ransomware source code and past malware used by Lazarus Group, a nation-state cyber-espionage unit previously associated with the North Korean army.
Back then, researchers believed that the Lazarus group deployed Hermes on the network of the Far Eastern International Bank (FEIB) in Taiwan to mask a cyber-heist during which they attempted to steal over $60 million from the bank's accounts.
But despite being used as a diversion in the Taiwan bank heist, Hermes was a fully functional and quite deadly ransomware.
Hermes was first discovered in February 2017 when Emsisoft researcher Fabian Wosar decided to reverse it in a live stream on YouTube. A decrypter was later published for those first versions, which is still available for download from here or here. Hermes v2 appeared soon after as a response and was not decryptable.
Hermes 2.1 was spotted in November 2017, after the FEIB bank heist, and a subsequent report from Intezer Labs also revealed similarities between the code of the Hermes 2.1 ransomware and past Lazarus Group tools.
Hermes 2.1 remained in use until today and appears to be distributed in parallel with the new Ryuk threat. The difference is that Hermes 2.1 is distributed via mass email spam campaigns, while Ryuk is only used in carefully selected attacks.
Ryuk-Hermes similarities are pretty obvious
The connection between the two is pretty obvious, at least to one cyber-security firm which analyzed the two ransomware strains.
Check Point researchers, who analyzed recent Ryuk variants, point out some pretty obvious connections between past Hermes versions and current Ryuk samples, both of which shared large swaths of code.
- The function that encrypts a single file is almost identical
- Ryuk and Hermes use the same file marker for encrypted files
- The check for the file marker is also identical
- Both whitelist similar folders (e.g. “Ahnlab”, “Microsoft”, “$Recycle.Bin” etc.)
- Both write a batch script named “window.bat” in the same path
- Both used a similar script to delete shadow volumes and backup files
- In both strains, there are files dropped to disk (“PUBLIC” and “UNIQUE_ID_DO_NOT_REMOVE”) which resemble in name and purpose
Ryuk versions for 32-bit and 64-bit systems were discovered, suggesting the ransomware can infect all types of systems, new and old alike. Code similarities to the Hermes ransomware were found in both samples.
"Such similarity of code across different architectures might well be a sign of an underlying identical source code," researchers also said.
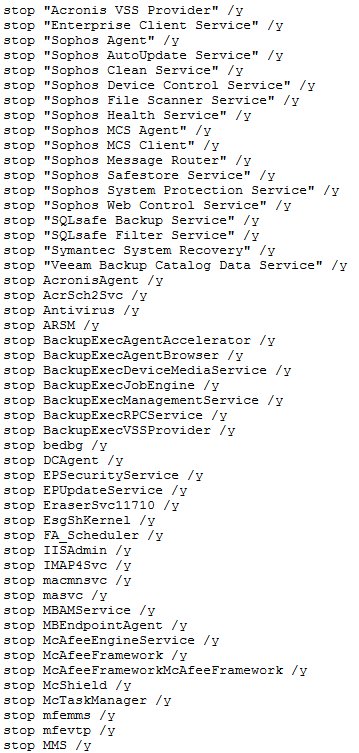
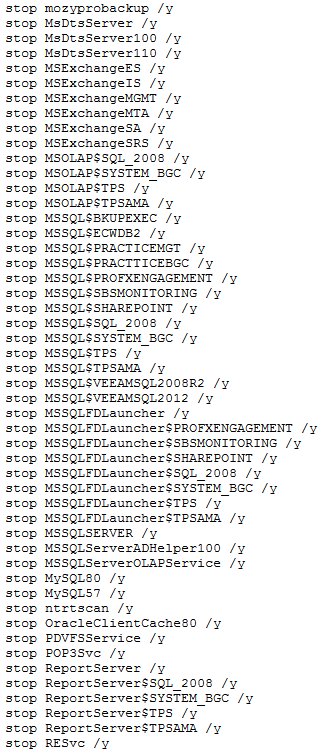
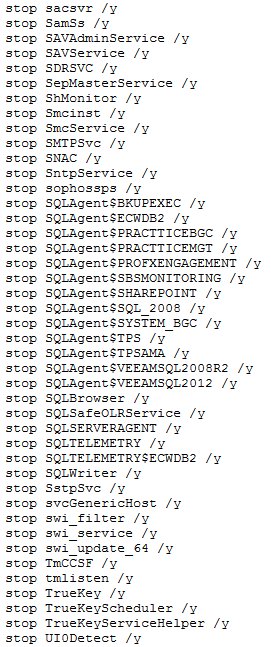
Ryuk shuts down over 180 services on infected hosts
But there are also some differences. The main one, spotted by both Check Point and MalwareHunter is that Ryuk comes with a huge list of apps and services it shuts down before infecting a victim's systems.



MalwareHunterTeam
@malwrhunterteam
184 stop commands found in a ransomware sample today. That's a lot.
Interesting that the word Sophos (nocase) can be found 15 times in it...@BleepinComputer @demonslay335
9:46 PM - Aug 18, 2018
124
87 people are talking about this
Twitter Ads info and privacy
"[T]he ransomware will kill more than 40 processes and stop more than 180 services by executing taskkill and net stop on a list of predefined service and process names," Check Point researchers explained in a report.
The ransom note conundrum
Furthermore, Ryuk's targeted nature is never more obvious than when it comes to its ransom notes. Check Point says it found several Ryuk samples where the ransomware dropped different ransom notes on users' systems.
Researchers found a long, more verbose ransom note, and another, blunter and to-the-point ransom demand.
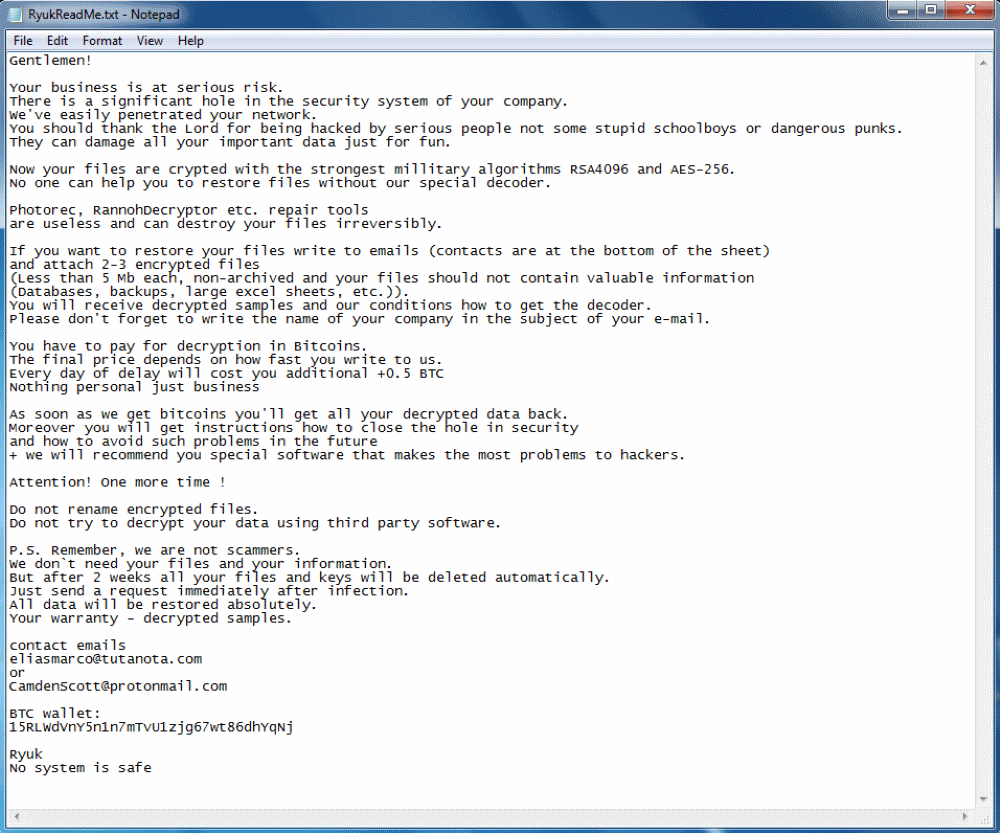
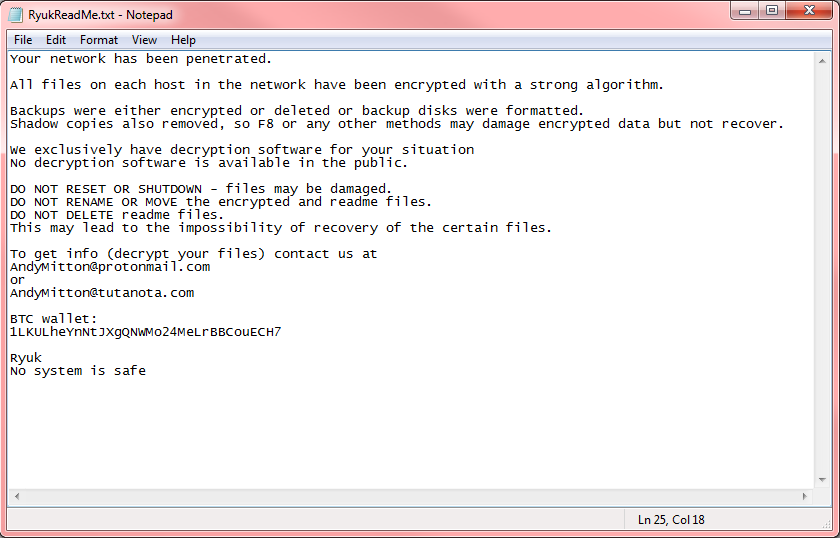 ransom note
ransom note
Both ransom notes asked victims to contact the Ryuk authors via email. Coincidentally or not, the ransom fees demanded via the longer and more detailed ransom note were higher (50 Bitcoin ~ $320,000), compared to the shorter ransom note, where crooks asked for a smaller amount of money (15-35 Bitcoin, ~$224,000).
"There seems to be some adaptation made in the ransom notes," Lechtik told Bleeping Computer, suggesting this particular detail adds up to the assumption that Ryuk is deployed after hackers infect networks and not via mass email spam.
"This could imply there may be two levels of offensive," Check Point said, suggesting that the Ryuk gang may also deploy different Ryuk samples based on the organization they manage to infect, and their ability to pay higher ransom fees.
Ryuk not decryptable at the time of writing
As for the ransomware's encryption, this is a classic AES-RSA combo that's usually undecryptable unless the Ryuk team made mistakes in its implementation. Currently, researchers have not spotted such weakness in Ryuk, as of yet.
Similar to most elite ransomware strains, unique Bitcoin payment addresses are created for each victim. Check Point says that money doesn't stay too much in these addresses, and they are quickly split and laundered through different accounts.
While previous versions of the Hermes ransomware have been an on-and-off threat that surfaces at random intervals with a mass spam campaign, the new Ryuk ransomware strain appears to be a new attempt from the Lazarus Group at developing a SamSam-like strain to use in precise surgical strikes against selected organizations.