
Scarab-DiskDoctor Ransomware
(coder-bleeder)
This crypto ransomware encrypts user data using the AES, and then you want to associate with the extortionists by email, to find out Bitcoin address to which you want to pay a ransom # BTC, to get the decoder and restore files. Original title: DiskDoctor (by extension). A file is written: the Local Security Authority Process.exe or something else. See. Genealogy below. It is written in Delphi. Files can be decrypted!
cryptographer cryptologist trojan virus-aes cipher crypto-extortionist remove the restore files decryption decrypt decrypt decrypt decryption algorithm crypto-ransomware virus-encoder filecoder key ransom decrypt decryption recovery remove restore files data public private
© Genealogy / Genealogy: now Scarab >> now Scarab the Family >> now Scarab-DiskDoctor to encrypted files is added to the expansion / Appends to encrypted files is the extension : .DiskDoctor file names remain the same, are not renamed. The activity of this crypto-extortionist came at the beginning of June 2018 Focuses on English-speaking users, which does not prevent spread it around the world. Ransom note called / the Name of ransom note Note : HOW the TO the RECOVER The ENCRYPTED files.txt
Scarab-DiskDoctor Ransomware note
The content of the note for redemption / Contents E of ransom note Note :
Warning all your files are encrypted !!! \ \ ___ / |
/ - _ `- / '
To receive the decoder, you must send an email to (/ \ / \ \ / \
the email address with your personal ID: / / | `\
OO) / |
DiskDoctor@protonmail.com `- ^ - '` <'
(_.) _) /
In response you will receive further instructions. `.___ /` /
`----- '/
ATTENTION !!! <----. __ / __ \
* Do not attempt to uninstall the program or run <---- | ==== O))) ==) \) / ====
antivirus software. <---- ' `-'` .__, '\
* Attempts to self-decrypt files will result in the | |
loss of your data. \ /
* Decoders of other users are incompatible with your ______ ((_ / \ ______
data, as each user has a unique encryption key. , ', -----' | \
`- {__________) \ /
Your personal identifier:
================================================== =========================================
6A02000000000000 *** 95611F
================================================== =========================================
The content of the text only (no figure):
Warning all your files is encrypted are !!!
The receive the decoder's the To, a must you the send an email to the email address with your personal ID:
DiskDoctor@protonmail.com
with In response you will of the receive Further instructions.
ATTENTION !!!
The Do not Attempt * to uninstall the program or the run antivirus software.
Attempts to the self *-decrypt the files is will of of result in the loss of your data.
Decoders of OTHER * the users are Incompatible with your data, as with the each user has a unique encryption key.
Personal identifier Your:
6A02000000000000 *** 95611F Translation notes on the Russian language: Warning that all your files are encrypted !!!
To get a decoder, you must send an email to the email-address with a personal identifier:
DiskDoctor@protonmail.com
In return you will receive further instructions.
ATTENTION !!!
* Do not attempt to remove the program or run an antivirus program.
* Attempts to independently decrypt files will result in the loss of your data.
* Decoders other users are not compatible with your data, since each user has a unique encryption key.
Your personal ID:
6A02000000000000 *** 95611F
Technical Details / Contents Technical details
It can spread by breaking through the RDP unprotected configuration, using email, spam and malicious attachments, fraudulent downloads, botnets (Necurs and others), exploits, web injects, malicious ads, fake update, repackage and infected installers. See. Also "Key distribution methods kriptovymogateley" on the introductory page of the blog . !!! If you neglect a comprehensive antivirus protection class Internet Security or Total Security, then at least make a backup of important files on the method 3-2-1 . ➤ UAC bypasses needed permission to run as an administrator. 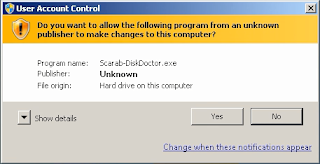
➤ Eliminates shadow copies of files, disables the Windows Recovery and correction function in step download instructions:
cmd.exe / c wbadmin the DELETE systemstatebackup
the wbadmin.exe wbadmin the DELETE systemstatebackup
cmd.exe / c wmic ShadowCopy the DELETE
Wmic.exe wmic ShadowCopy the DELETE
cmd.exe / c Shadows Delete vssadmin / All / Quiet
vssadmin.exe vssadmin Delete Shadows / All / Quiet
cmd.exe / c bcdedit / default set {} recoveryenabled No
bcdedit.exe bcdedit / default set {} recoveryenabled No
cmd.exe / c bcdedit / set { } bootstatuspolicy ignoreallfailures default
bcdedit.exe bcdedit / default set {} bootstatuspolicy ignoreallfailures ➤ ID contains from 642 to 652 characters.
List of file extensions that are encrypted / the Extensions of target files is : Most file types. It will certainly be MS Office documents, OpenOffice, PDF, text files, databases, photos, music, video, image files, archives and so on. The results of the analysis, I could see only the following file types: .aapp, .bat, .bin, .cab, .CAT, .cer, .CHS, .CHT, .css, .CZE, .DAN, .DEU, .dll, .doc, .docx, .ESP, .EUQ, .exe, .fdb, .FRA , .gif, .HRV, .htm, .html , .HUN, .ini, .ITA, .jpg, .JPN, .js, .KOR, .kt1, .NLD, .NOR, .pak, .pdf,. png, .POL, .pst, .PTB, .RUM, .RUS, .SKY, .SLV, .SYO, .sys, .SVE, .tmp, .TUR, .txt, .UKR, .wmv, .zip , and others. Target directory (files in folders): the Windows intel, the nvidia
The Volume Information Part the System
the All Users Offline, the AppData, the Application the Data
Program Files, Program Files (the x86)
$ RECYCLE.BIN The objectives also include the following elements:
XXXX, ANUBIS, WANNACRY, DELPHIN, GAGRA, FANNY Files associated with this ransomware / Files of Rw : HOW the TO the RECOVER The ENCRYPTED files.txt LocalSecurityAuthorityProcess.bak.exe <random> .exe - random name Layouts: \ Desktop \ -> \ User_folders \ -> \% the TEMP% \ -> % APPDATA% \ the Local Security Authority Process.exe The registry entries associated with this ransomware / registry entries of Rw : See below for test results.. Networking and communication / URLs of, contacts, payments : Email: DiskDoctor@protonmail.com . See below for test results. Test results