TrillClient
TrillClient toolset is an information stealer designed to steal browser data,
and is packed in a single cabinet file (.cab) and extracted through the utility
application expand.exe. The CAB file contains a TrillClient installer and a
stealer. Based on different arguments, the installer performs the following
behaviors:
Table 1. TrillClient arguments and behaviors
Argument Description
-install Installs itself as Windows service Net Connection
-start {victim id}
Creates a victim list based on the input victim ID (File name:
7C809B4866086EF7FB1AB722F94DF5AF493B80DB)
Launches the TrillClient stealer through starting services
-remove Cleans up the installation (Deletes the service)
As TrillClient is a custom browser data stealer written in Go, it is heavily
obfuscated by a custom obfuscator for anti-analysis. Once launched, it looks for
the victim list, 7C809B4866086EF7FB1AB722F94DF5AF493B80DB created by the
installer. Afterward, it connects to a GitHub repository to retrieve the command
for the next set of actions. The repository address is hard-coded in the malware
as follows: hxxps://raw[.]githubusercontent[.]com/trillgb/codebox/main/config.json.
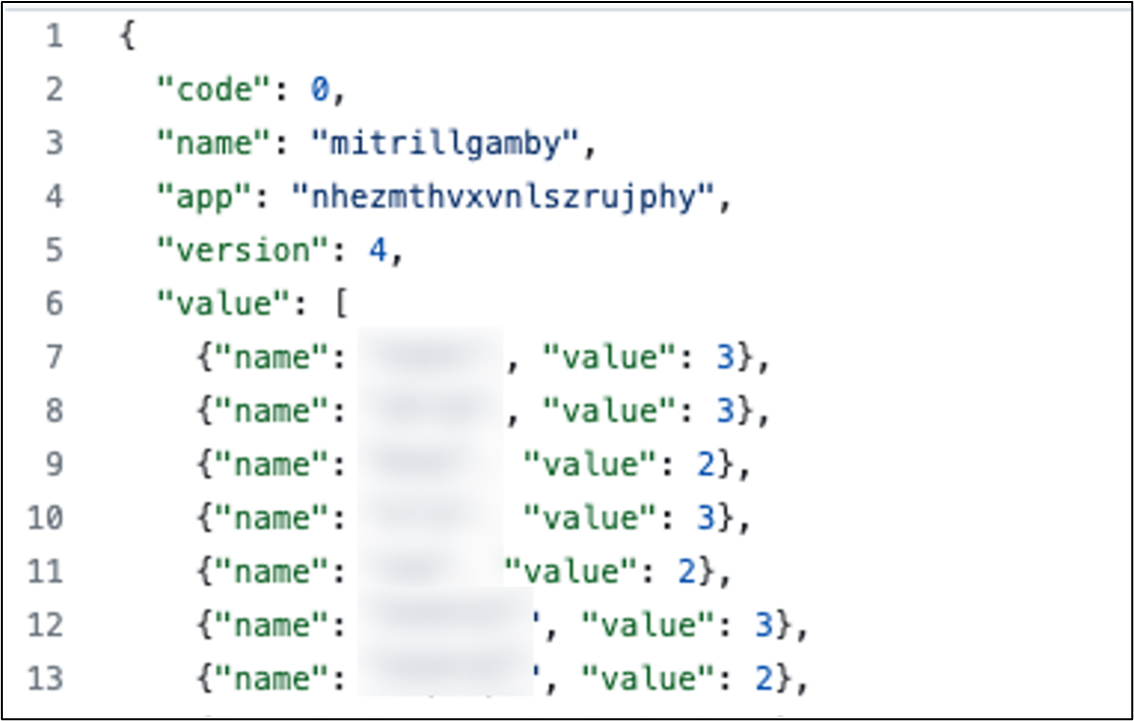
Figure 3. Sample content of “config.json”
Value.name is the victim ID, while value.value is a command. After receiving
this configuration, TrillClient looks for its own victim ID in the value.name
list, and performs malicious activities based on the command defined by value.value.
TrillClient supports the following commands:
Table 2. TrillCient commands and functions
Command Function
1 Does nothing
2 Starts to collect browser credentials
3 Schedules a task to collect browser credentials by 12 p.m. today or tomorrow
4 Starts to collect browser credentials after some time (no definite duration,
estimated to be a random number of seconds)
TrillClient steals the sensitive data found in the following directories:
%LOCALAPPDATA%\Google\Chrome\User
Data\Local State
%LOCALAPPDATA%\Google\Chrome\User Data\<PROFILE>\Login Data
%LOCALAPPDATA%\Google\Chrome\User Data\<PROFILE>\Network\Cookies
%APPDATA%\Microsoft\Protect\*
The collected data will be temporarily copied to <%TEMP%\browser_temp_data<RANDOM>>,
archived usingthe .tar command, and encrypted with an XOR algorithm. Then the
collected data will be sent to the threat actor’s email account trillgamby@gmail[.]com
over SMTP (Simple Mail Transfer Protocol). Another noteworthy capability of
TrillClient is its ability to update its version. As the value of “version”
defined in the downloaded config is newer than the current version number, it
will download the newer one from the GitHub repository and update itself.
