Baza (BazarLoader & BazarBackdoor) has been attributed to the organized cybercrime group behind Trickbot by multiple security vendors over the past year. Initially appearing around April of 2020 , the malware was spread in email campaigns utilizing infrastructure previously used to distribute Trickbot. The term BazarLoader was coined due to the reliance and use of Blockchain-DNS and the associated bazar domains used to communicate with the controllers. Since then, the terms Baza or Bazarloader have been used interchangeably to reference this particular malware family.
After the initial appearance of Baza, multiple reports attributing various code to the malware family appeared.It became increasingly obvious that development was on going and multiple projects were under construction. The downside to such a public following, is the common acceptance of activity based on previous TTPS. Combining TTPs such as loading powershell stagers into red team utilities along with similar campaign structures and C2 traffic patterns, can quickly lead to incorrect attribution of malware families and actors.
On Feb 3, we detected campaigns previously attributed to Baza but the malware utilized request headers that were different. Several others noticed oddities as well. Further analysis indicated something completely different and new. Nimar loader did not share the same codebase as the baza family.
NimarLoader or Nimrod recently mistaken as BazarLoader, is coded in Nim. The malware was obfuscated but did not contain the typical hardening seen in large scale campaigns. Since it was something newly developed, crypting the sample was unnecessary but it is curiously absent making analysis less difficult. From the strings, hints at the capability can be clearly seen.
verb in @["GET", "POST"]
@https
@fKHMP]
@SPMVDSD
job_type
job_args
job_results
@heartbeat set
@HEARTBEAT set Failed
@HEARTBEAT set
@Shellcode Done
@heartbeat
@shellcode
@handshake
@No update data recieved
agentId
pathAdj
pathNoun
seqNum
seqTotal
jobIdHeader
userAgent
serverPubKeyEncoded
jitterParamStr
sessionKey
sessionDie
The command table allows to handshake, heartbeat, shellcode, powershell or cmd, as evidenced in the strings seen during execution.
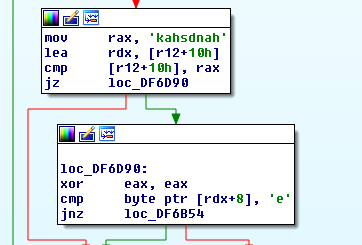
Image1: handshake
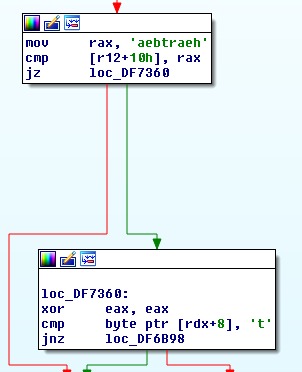
Image2: heartbeat
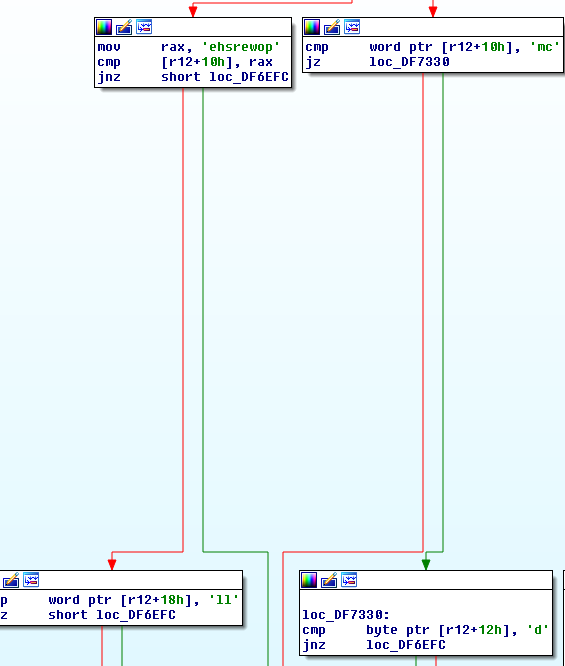
Image3. powershell or cmd
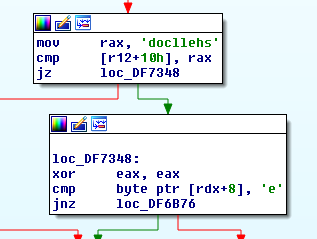
Image4: shellcode
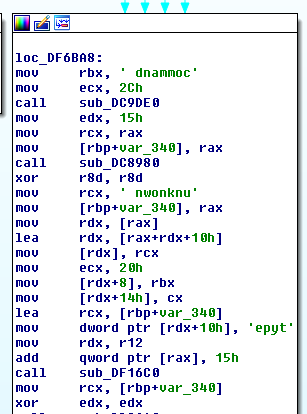
Image5: unknown command
While some of the strings are visible, a string encoding and decoding routine exists.
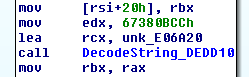
Image6: Decoding routine
The decoding loop XORs every byte of the encoded string with every byte of the key and then increments the key by one, due to how XOR works this is the same as XOR encoding every byte with a single XOR byte and incrementing the key by the iterator in a rolling single byte XOR loop.
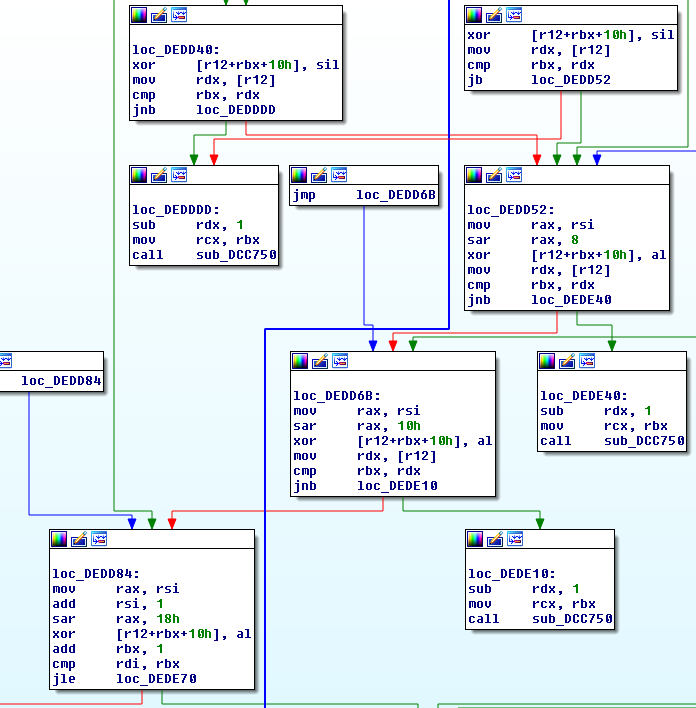
Image7: Decoding Loop
After running the routine the following strings are decrypted:
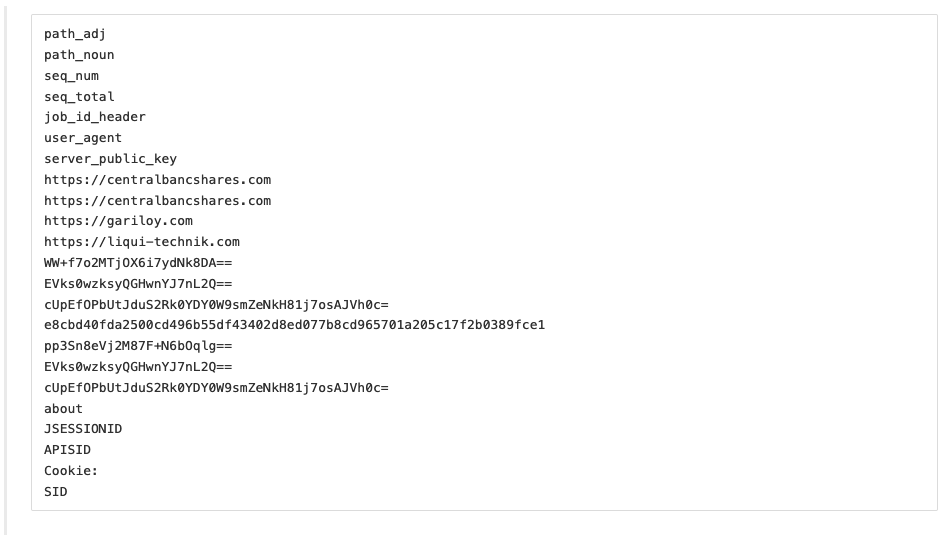
As referenced earlier, the sample functions a bit like a loader, with the ability to process shellcode and execute tasks or jobs via cmd or powershell. Similar to the majority of Baza campaigns, the tasks that were executed came in the form of cobalt strike stagers. The benefit of using this “fileless” mechanism, is nothing touches disk.
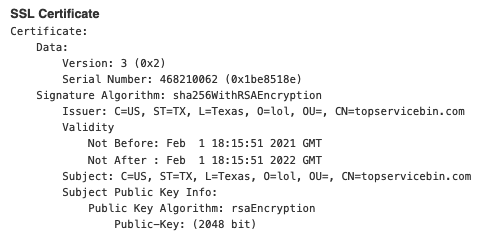
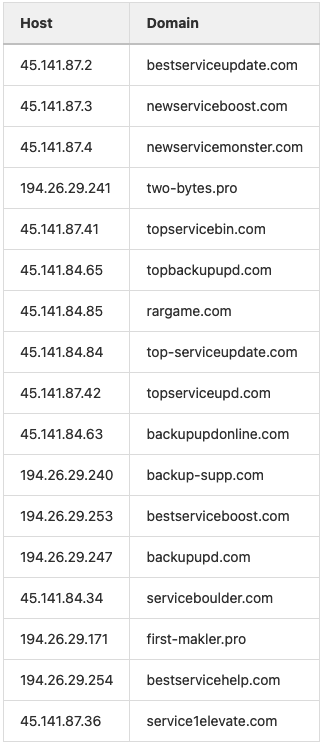
Upon execution, a callout is made by the stager to topservicebin[.]com. During the campaign, the domain resolved to the ip 45.141.87 .41 which contained the following SSL certificate.