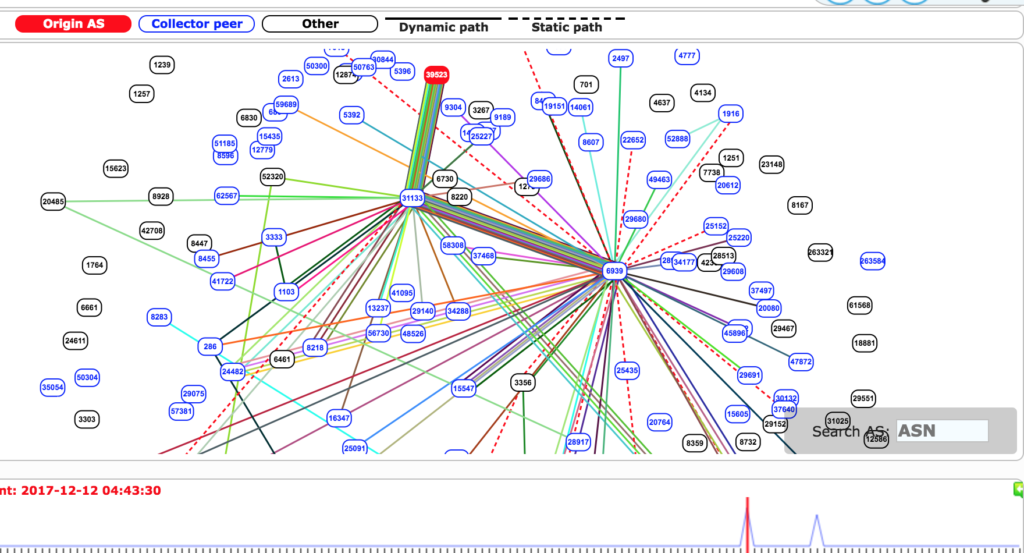
BGP hijacking – Traffic for Google, Apple, Facebook, Microsoft and other tech giants routed through Russia
18.12.2017 securityaffairs Attack
Traffic for Google, Apple, Facebook, Microsoft and other tech giants routed through Russia, experts believe it was an intentional BGP Hijacking.
Last week a suspicious event routed traffic for major tech companies (i.e. Google, Facebook, Apple, and Microsoft) through a previously unknown Russian Internet provider. The event occurred on Wednesday, researchers who investigated it believe the traffic was intentionally hijacked.
The incident involved the Internet’s Border Gateway Protocol that is used to route traffic among Internet backbones, ISPs, and other large networks.
BGPmon.net
@bgpmon
Example of a @facebook prefix briefly routed towards AS39523 DV-LINK-AShttps://bgpmon.net/popular-destinations-rerouted-to-russia/ … https://twitter.com/bgpstream/status/940455830893334528 …
12:27 AM - Dec 13, 2017
Replies 48 48 Retweets 46 46 likes
Twitter Ads info and privacy
A similar incident occurred eight months when a huge amount of traffic belonging to MasterCard, Visa, and more than two dozen other financial services was briefly routed through a telecom operator controlled by the Russian Government.
“Early this morning (UTC) our systems detected a suspicious event where many prefixes for high profile destinations were being announced by an unused Russian Autonomous System. Starting at 04:43 (UTC) 80 prefixes normally announced by organizations such Google, Apple, Facebook, Microsoft, Twitch, NTT Communications and Riot Games were now detected in the global BGP routing tables with an Origin AS of 39523 (DV-LINK-AS), out of Russia.” states a blog post published by Internet monitoring service BGPMon.
“Looking at timeline we can see two event windows of about three minutes each. The first one started at 04:43 UTC and ended at around 04:46 UTC. The second event started 07:07 UTC and finished at 07:10 UTC.
Even though these events were relatively short lived, they were significant because it was picked up by a large number of peers and because of several new more specific prefixes that are not normally seen on the Internet. So let’s dig a little deeper. “
BGPMon observed two distinct events for a total of six minutes that affected 80 separate address blocks.

Another monitoring service, Qrator Labs, stated the event lasted for two hours during which the number of hijacked address blocks varied from 40 to 80.

BGPMon experts consider the incident as suspicious for the following reasons:
The rerouted traffic belonged to big tech companies.
Hijacked IP addresses belong to small and specific blocks that aren’t’ normally seen on the Internet.
“What makes this incident suspicious is the prefixes that were affected are all high profile destinations, as well as several more specific prefixes that aren’t normally seen on the Internet. This means that this isn’t a simple leak, but someone is intentionally inserting these more specific prefixes, possibly with the intent the attract traffic.” continues the analysis from BGPMon.
The BGP hijacking was caused by an autonomous system located in Russia that added entries to BGP tables claiming it was the legitimate origin of the 80 affected prefixes. This assertion caused large amounts of traffic sent to and received by the affected companies to pass through the Russian AS 39523 before being routed to its final destination.
Below the list of ISPs that picked up the new route:
xx 6939 31133 39523 (path via Hurricane Electric)
xx 6461 31133 39523 (path via Zayo)
xx 2603 31133 39523 (path via Nordunet)
xx 4637 31133 39523 (path via Telstra)
AS39523 is a previously unused autonomous system that hasn’t been active in years, but he made the headlines in August when it was involved in another BGP incident that involved Google.
“Whatever caused the incident today, it’s another clear example of how easy it is to re-route traffic for 3rd parties, intentionally or by accident. It also is a good reminder for every major ISP to filter customers. ” concluded BGPMon.
“This hijack highlights a common problem that arises due to lack of route filtering. We can blame AS39523 for the accident, but without proper filters at the intermediate transit providers boundaries we are doomed to see similar incidents again and again. We’d like to encourage all networks involved in this incident to review their route filtering strategy, and at the very least implement prefix-based BGP filters on all interconnections towards their customers.” concluded Qrator Labs.
The Russian pipeline giant Transneft infected with a Monero cryptocurrency miner
18.12.2017 securityaffairs Virus
The Russian pipeline giant Transneft admitted its computers were used for mining Monero cryptocurrency, the company removed the malware from its computers.
The Russian pipeline giant Transneft announced its systems were infected with a Monero cryptocurrency miner. The company confirmed it has successfully removed the threat from its systems, the company spokesman Igor Demin told Reuters the cryptomining software was automatically downloaded by a Transneft computer and was later erased.
“[Demin ] noted that the company now has programmes to block such downloads and prevent similar incidents in the future.” reported IBTimes.

The news of the security breach was reported to the company by Transneft vice president and former interior minister Vladimir Rushailo.
“Incidents where the company’s hardware was used to manufacture cryptocurrency have been found. It could have a negative impact on the productivity of our processing capacity,” he explained during a meeting without providing further details on the infection.
The spike in the values for some cryptocurrencies such as Bitcoin and Monero is attracting crooks that are spending a lot of efforts in the attempt to steal funds stored in the wallets used for these two cryptocurrencies or to abuse resources to mine crypto coins.
The company now announced that it has improved its systems to prevent similar security breach will happen again.
A growing number of businesses were caught running cryptomining scripts on their websites to secretly generate digital currencies as an alternative to online advertising.
The list of websites running cryptominins code includes The Pirate Bay, Politifact, Showtime, Starbucks, and UFC.
The Russian Government is planning to create a specific legislative framework to address the regulation of virtual currencies, the authorities will allow purchasing cryptocurrencies but the new legislation aim to make mining illegal.
“The penalties will be different, mostly administrative, but if someone created the cryptocurrency for the purpose of settlements, then there will be a criminal punishment,” explained the Deputy Finance Minister Aleksey Moiseev.
New PRILEX ATM Malware used in targeted attacks against a Brazilian bank
18.12.2017 securityaffairs Virus
PRILEX is a new ATM malware analyzed by researchers at Trend Micro that was used in high-targeted attacks against a Brazilian bank.
Security researchers from Trend Micro recently discovered a strain of ATM malware dubbed PRILEX that was involved in targeted attacks in Brazil.
PRILEX is written in Visual Basic 6.0 (VB6), it was specifically designed to hijack a banking application and steal information from ATM users.
he first PRILEX attack was spotted in October 2017 by Kaspersky Lab, but the analysis conducted by Trend Micro revealed very atypical behavior. The ATM malware works by hooking certain dynamic-link libraries (DLLs), replacing it with its own application screens on top of others. These DLLs targeted by the malicious code are:
P32disp0.dll
P32mmd.dll
P32afd.dll
Further investigation allowed the researcher to determine that the DLLs belong to the ATM application of a bank in Brazil.
The atypical behavior along with the fact that the malware only affects a specific brand of ATMs, suggests the malware was designed for high-targeted attacks.
Once infected an ATM, the PRILEX malware starts interfering with the banking application, it displays its own fake screen requesting the user to provide their account security code. The code is delivered to the user as part of a two-factor authentication process and the malware captures and stores it.
One of the aspects that caught the attention of the researchers is that the ATM malware tries to send data back to a C&C server, a behavior very uncommon for ATM malware. It is likely that this bank’s ATMs are connected and the attackers seem to be very familiar with these specific machines.
“In our analysis of the code, we noticed something interesting that happens at some point after it steals data: The malware tries to communicate with a remote command-and-control (C&C) server and upload both credit card data and the account security code.” reads the analysis published by Trend Micro.
“To our knowledge, this is the first ATM malware that assumes it is connected to the internet. It is likely that this bank’s ATMs are connected, since the attackers seem to be very familiar with this particular bank’s methods and processes.”
Another element that makes this attack singular is that attackers aim to steal user information instead of jackpotting the ATM, a circumstance that suggests the criminal gang behind the attack deals with bulk credit card credentials.
“There is something more important to be learned from Prilex, though. Any bank is subject to have their methods and processes analyzed by criminals and then later abused with highly targeted attacks. It’s concerning, and something that is worth looking into if you’re trying to defend your ATM infrastructure. Jackpotting attacks are very notorious, but a silent attack like this can go unnoticed for months, if not years.” continues the analysis.
“A targeted malware likely took significant time and resources to develop. This shows that in today’s world, criminals consider that a worthwhile investment.”

The researchers at Trend Micro also analyzed the recently discovered CUTLET MAKER ATM malware that was offered for sale on the Dark Web for around $5000.
The crimeware kit was discovered in October by Kaspersky, it is designed to target various Wincor Nixdorf ATM models using a vendor API, without interacting with ATM users and their data.
However, it seems that competitors have already managed to crack its code, allowing anyone to use it for free.
“Careful examination reveals that the license code is not time-based, it’s just an algorithm. This is a fancy way of saying that the same input would yield the same output. Some other criminal realized this and, at some point, created a standalone program that’s similar to a classic key generator or ‘keygen’ that automatically calculates the return code.” reads the analysis.
“The code is available on the internet and relatively easy to find. This means that anybody can start victimizing ATMs without having to pay for the program—or at least ATMs with an accessible USB port.”
Other crooks have started selling the malware along with the keygen for much lower prices compared to the original. Till now, the legitimate author hasn’t released a new version to solve the problem.
Zealot Campaign leverages NSA exploits to deliver Monero miners of both Windows and Linux servers
18.12.2017 securityaffairs BigBrothers
Security researchers spotted a sophisticated malware campaign, tracked as Zealot campaign targeting Linux and Windows servers to install Monero miners.
Security researchers from F5 Networks spotted a sophisticated malware campaign, tracked as Zealot campaign (after the name zealot.zip, one of the files dropped on targeted servers), targeting Linux and Windows servers to install Monero cryptocurrency miners.
The campaign was detected by security researchers from F5 Networks, who named it Zealot, after zealot.zip, one of the files dropped on targeted servers.
Hackers are using a wide arsenal of exploits to compromise the servers and install the malware, including the same code used in the Equifax hack
F5 Networks experts observed threat actors scanning the Internet for particular unpatched servers and hack them with two exploits, one for Apache Struts (CVE-2017-5638) and one for the DotNetNuke ASP.NET CMS (CVE-2017-9822).
“F5 threat researchers have discovered a new Apache Struts campaign. This new campaign is a sophisticated multi-staged attack targeting internal networks with the NSA-attributed EternalBlue and EternalSynergy exploits.” states the analysis from F5 Networks.
“We have dubbed the campaign “Zealot” based on the name of the zip file containing the python scripts with the NSA-attributed exploits. As we continue to research this campaign, we will update this publication.”
The exploit for the Struts vulnerability includes malicious code for targeting both Linux and Windows machines at the same time.
Once the hackers infected a Windows machine, they used the EternalBlue and EternalSynergy exploits (both exploits belong to the huge trove of data belonging to the NSA that was leaked by the Shadow Brokers earlier this year) for lateral movements in the target network.
In the last stage of the attack, threat actors would use PowerShell to download and install the Monero miner.
The attack against Linux servers sees attackers using Python scripts that appear to be taken from the EmpireProject post-exploitation framework, to install the same Monero miner.
“Zealot seems to be the first Struts campaign using the NSA exploits to propagate inside internal networks. There were other malware campaigns like NotPetya and WannaCry ransomware, and also Adylkuzz cryptominer launching attacks by directly scanning the Internet for SMBs to exploit with the NSA tools the ShadowBrokers released.” continues the analysis.
“The Zealot campaign, however, seems to be opening new attack vector doors, automatically delivering malware on internal networks via web application vulnerabilities.”
The researchers reported that the amount that was paid for the miner address associated with the Zealot campaign was approximately $8,500 USD, we cannot exclude that crooks also used other Monero wallets.

The researchers warned of the possible change for the final-stage payload, they could use the same campaign to deliver ransomware.
Another curiosity emerged from the analysis it that the attackers appear to be big fans of the legendary StarCraft game, in fact, many of the terms and file names used for this campaign are characters of the game (i.e. Zealot, Observer, Overlord, Raven).
“The level of sophistication we are currently observing in the Zealot campaign is leading us to believe that the campaign was developed and is being run by threat actors several levels above common bot herders,” concluded the analysis.
Google Researcher Finds Critical Flaw in Keeper Password Manager
18.12.2017 securityweek Vulnerebility
Google Project Zero researcher Tavis Ormandy recently discovered that the Keeper password manager had been affected by a critical flaw similar to one he identified just over one year ago in the same application.
Ormandy found the security hole after noticing that Keeper is now installed by default in Windows 10. He remembered a vulnerability he reported last year and managed to reproduce the same attack with only a few minor modifications.
“I've heard of Keeper, I remember filing a bug a while ago about how they were injecting privileged UI into pages,” the researcher said. “I checked and, they're doing the same thing again with this version.”
The vulnerability affects the Keeper browser extensions, which, unless users opt out, are installed alongside the Keeper desktop application. The security hole allows attackers to steal passwords stored by the app if they can convince an authenticated user to access a specially crafted website.
Keeper released a patch within 24 hours of being notified by Ormandy. The fix has been rolled out with version 11.4.4 and it has already been delivered to Edge, Chrome and Firefox users via the browsers’ automatic extension update process. Safari users will need to manually update the extension.
“This potential vulnerability requires a Keeper user to be lured to a malicious website while logged into the browser extension, and then fakes user input by using a clickjacking and/or malicious code injection technique to execute privileged code within the browser extension,” Keeper said in a blog post informing customers of the vulnerability and the patch.
The company said there had been no evidence of exploitation in the wild, and pointed out that the mobile and desktop apps were not affected by the flaw.
Ormandy has made available a proof-of-concept (PoC) exploit that steals a user’s Twitter password from Keeper.
Tavis Ormandy finds critical vulnerability in Keeper password manager
Microsoft Disables Dynamic Update Exchange Protocol in Word
18.12.2017 securityweek Vulnerebility
In an attempt to prevent cybercriminals from abusing the Dynamic Update Exchange protocol (DDE) for nefarious operations, Microsoft has disabled the feature in all supported versions of Word.
The DDE protocol was designed to allow Windows applications to transfer data between each other and consists of a set of messages and guidelines.
Using shared memory to exchange data between Office applications, the DDE protocol has been replaced in Office with Object Linking and Embedding (OLE), but DDE is still supported in the popular productivity suite.
Abusing DDE to deliver malware via Office documents isn’t alwasys easy. In addition to creating a malicious document, an attacker would also need to convince the victim to disable Protected Mode and click through a series of prompts referencing linked files and remote data.
Regardless, security researchers stumbled upon numerous malware infection campaigns abusing DDE, ranging from DNSMessenger malware attacks orchestrated by the FIN7 hacking group, to Hancitor infections, and to Necurs-fueled Locky ransomware campaigns.
The Russia-linked cyber espionage group known as Fancy Bear has been seen leveraging DDE for malware infection purposes.
This prompted Microsoft to publish a security advisory in early November to inform users on how to protect themselves from such attacks. The tech giant also underlined that the Attack Surface Reduction (ASR) mitigation included in Windows Defender Exploit Guard as part of the Windows 10 Fall Creators Update keeps users protected from such attacks.
Previous mitigations against such attacks included setting specific registry keys to disable automatic data updates from linked fields, and Microsoft previously provided detailed information on how users could perform the action for Excel, Outlook, Publisher and Word.
Now, the company has decided to completely disable DDE in all supported versions of Word. The change was made as part of the December 2017 Patch Tuesday.
In a security advisory, the Microsoft said that it continues to investigate this issue and that further updates will be provided if necessary.
Users unable to install the newly released Office security update or looking to disable the DDE protocol in other Office applications such as Excel, can do so manually by applying previously announced mitigations.
To change DDE functionality in Word after installing the update, users should navigate to:
\HKEY_CURRENT_USER\Software\Microsoft\Office\version\Word\Security AllowDDE(DWORD)
Next, users should set the DWORD value based on their requirements: 0 to disable DDE; 1 to allow DDE requests to an already running program (but prevent requests that launch another executable program); or 2 to fully allow DDE requests.
French Aerospace Giant Thales Acquires SIM Maker Gemalto
18.12.2017 securityweek Mobil
French aerospace and defence group Thales said Sunday it has bought European SIM manufacturer Gemalto in a bid to become a global leader in digital security.
The aerospace giant paid 51 euros ($60) a share for Gemalto, a premium of 57 percent over the closing price on December 8, Thales said in a statement.
The price was also higher than a 46-euro a share bid offer from French tech firm Atos which Gemalto rejected on Wednesday.
The Thales offer showed that it valued the world-leading chipmaker at about 4.8 billion euros.
Gemalto chief executive Philippe Vallee said in the statement that favouring Thales over Atos was "the best and the most promising option for Gemalto and the most positive outcome for our company, employees, clients, shareholders and other stakeholders".
"We share the same values and Gemalto will be able to pursue its strategy, accelerate its development and deliver its digital security vision, as part of Thales."
Thales CEO Patrick Caine said the merger marked "a key milestone" in implementing the firm's digital security strategy, in which it has invested one billion euros in the past three years and acquired three other companies.
"Together with Gemalto's management, we have big ambitions based on a shared vision of the digital transformation of our industries and customers."
The French company, which is worth about 18 billion euros, said that with the merger, the Thales group will rank among the top three players worldwide, with 3.5 billion euros in revenue in the fast growing digital security market.
The new division will focus on security software, biometrics, multifactor authentication and issuing secure electronic and physical ID cards.
The deal is expected to close in the second half of 2018, but can be terminated before then if Gemalto receives a bid that is at least nine percent higher than Thales's offer price.
vBulletin to Patch Disclosed Code Execution, File Deletion Flaws
18.12.2017 securityweek Vulnerebility
The details of two potentially serious vulnerabilities affecting version 5 of the vBulletin forum software were disclosed by researchers last week. The flaws are currently unpatched, but vBulletin developers have promised to release fixes soon.
The security holes were disclosed via Beyond Security’s SecuriTeam Secure Disclosure program by a researcher from Italy-based security firm TRUEL IT and an expert who has not been named.
One of the vulnerabilities has been described as a file inclusion issue. The flaw affects vBulletin installations that use a Windows-based server, and an unauthenticated attacker can exploit it by sending a specially crafted GET request to index.php.
An attacker can inject malicious PHP code into a file on the server (e.g. access.log) and then “include” that file by manipulating the routestring= parameter in the request. This results in the attacker’s code getting executed.
The second vulnerability, tracked as CVE-2017-17672, has been described as a deserialization issue that can be exploited by an unauthenticated attacker to delete arbitrary files and possibly even execute arbitrary code.
“vB_Library_Template’s cacheTemplates() function is a publicly exposed API which allows to fetch information on a set of given templates from the database in order to store them inside a cache variable,” Beyond Security’s advisory explains. “The $temnplateidlist variable, which can come directly from user-input, is directly supplied to unserialize(), resulting in an arbitrary deserialization primitive.”
Detailed technical information and proof-of-concept (PoC) code have been made available for both vulnerabilities.
Beyond Security claims it has been trying to report the vulnerabilities to vBulletin developers since November 21, but has not received any response. vBulletin, on the other hand, told SecurityWeek that it received no email into its ticket system regarding the vulnerabilities until last week. A patch has already been developed and it will be released once it’s tested.
Malicious actors exploiting vBulletin vulnerabilities in the wild is not unheard of. A couple of years ago, researchers had started seeing thousands of daily attempts to exploit a critical flaw less than two weeks after it was patched.
Ruská cenzura nedokáže blokovat produkci trollů
18.12.2017 Novinky/Bezpečnost BigBrother
Hlavní ruský cenzurní orgán nemá v nejbližší době možnost omezit aktivitu takzvaných internetových trollů, tedy osob šířících za úplatu internetem dezinformace a falešné zprávy. Na moskevském semináři o internetové bezpečnosti to prohlásil šéf komunikační dozorové agentury Roskomnadzor Alexandr Žarov.
"Žádná regulace neexistuje, možná se objeví za půldruhého roku. Jaká bude, mi není známo," řekl Žarov, jehož organizace v posledních pěti letech zablokovala přes 275 000 ruských webových stránek. Šlo zejména o servery zprostředkující údajně šíření narkotik nebo dětské pornografie, ilegální herní a sázkové weby a on-line loterie.
"Upřímně řečeno, způsoby zásahu žádné nevidím," konstatoval šéf Roskomnadzoru, který k zákroku proti webům nemusí mít soudní příkaz. Žarov podle agentury Interfax dodal, že "není stoupencem omezování a totálních zákazů".
V Rusku podle místních médií existuje několik "trollích farem", tou nejznámější je petrohradská instituce zvaná Agentura pro výzkum internetu, která je považována za prodlouženou ruku ruské vlády. V holdingu pracuje kolem 250 lidí, ročně provoz firmy stojí údajně kolem 270 miliónů rublů (přes 100 miliónů korun).
Hackeři to budou mít těžší. Nová služba má zamezit masivním útokům
18.12.2017 Novinky/Bezpečnost Zabezpečení
Sdružení CZ.NIC, které má na starosti českou národní doménu, spustilo tento týden novou službu. Ta má zajistit funkčnost internetových služeb i v případě masivního hackerského útoku. Prvními společnostmi, které se k aktivitě sdružení přidaly, jsou Seznam.cz a Vodafone.
Služba zvaná ISP DNS Stack má zabránit útokům na DNS servery. Ty standardně překládají webové adresy na číselné adresy fyzických počítačů (IP adresy). Ve chvíli, kdy je hackeři vyřadí z provozu – což se už v minulosti stalo několikrát – jeví se uživateli webové stránky jako nedostupné.
Tím, že nefunguje překladač (DNS servery), webové prohlížeče po zadání adresy totiž nevědí, kam se mají připojit. Zákazníků s ISP DNS Stackem se ale případný útok nijak nedotkne a internetové služby v doméně .CZ pro ně zůstanou plně dostupné.
Budování spolehlivých datových služeb
„Pro Seznam.cz jako poskytovatele obsahu, informací a zábavy, je naprosto klíčová dobře fungující internetová infrastruktura. DNS je její nepostradatelnou součástí a z historie víme, jak vysoce nepostradatelnou,” říká Vlastimil Pečínka, technický ředitel společnosti Seznam.cz.
Ten zároveň dodal, že česká internetová jednička nedávno investovala do zrobustnění DNS služeb používaných v obou svých datových centrech. „Nabídka sdružení CZ.NIC na hostování DNS stacku tuto naši investici posouvá o úroveň výše. Navíc velmi oceňuji snahu sdružení CZ.NIC hledat další cesty, jak pomoci službám a uživatelům na internetu. Jsem tak rád, že mohu jejich snahy podpořit konkrétními kroky,” uzavřel Pečínka.
„Spolupráce s CZ.NIC je součástí naší dlouhodobé strategie budování spolehlivých datových služeb. Služba ISP DNS Stack představuje kopii DNS serveru pro doménu .CZ přímo v síti Vodafone. Zákazníkům tak zajistíme správné fungování DNS pro české domény i v případě útoků na servery CZ.NIC,” vysvětlil Milan Zíka, technický ředitel společnosti Vodafone.
Klíčový systém pro fungování internetu
Službu ISP DNS Stack provozuje výhradně sdružení CZ.NIC. Správce české národní domény se podílí na fungování operačního systému a všech na něm běžících služeb. Zapojené organizace zajišťují nákup potřebného hardware, jeho umístění v datacentru a následný provoz ve vlastní síti.
„Systém DNS je klíčový pro fungování internetu a služeb, které jsou na něm závislé. V případě, že by došlo k jeho napadení nebo výpadku, stal by se internet pro většinu lidí prakticky nepoužitelný. Velice si vážím přístupu společností Seznam.cz a Vodafone, které tímto dávají najevo především svým zákazníkům, že je pro ně dostupnost internetu za jakékoliv situace klíčová,“ prohlásil Ondřej Filip, výkonný ředitel sdružení CZ.NIC.
Vyděračské viry napadly více než čtvrtinu firem
18.12.2017 Novinky/Bezpečnost Viry
Počet útoků vyděračských programů na firmy letos vzrostl. Podíl napadených podniků se meziročně zvýšil o čtyři procentní body na 26 procent. Na vině jsou především tři nebývale mohutné útoky na firemní sítě, které zásadním způsobem změnily prostředí firemních počítačových sítí. Uvedla to antivirová firma Kaspersky Lab.
Firmy celosvětově napadly postupně vlny škodlivých programů WannaCry v květnu, ExPetr na konci června a BadRabbit v říjnu. Všechny se zaměřovaly na korporátní sítě. Na podniky útočily i jiné tzv. ransomwary, které dohromady stály za 240 000 útoky.
"Tyto známé útoky z průběhu celého roku jsou extrémním důkazem toho, že se kyberzločinci čím dál více zajímají o firemní cíle. Tento trend jsme ale zaznamenali už v roce 2016. Letos však nabral na obrátkách a zatím se nezdá, že by nějak polevoval," uvedl analytik Kaspersky Lab Fedor Sinitsyn. "Děje se tak především proto, že jsou firmy velmi zranitelné, schopné zaplatit vyšší výkupné než jednotlivci a většinou jsou k tomu i ochotnější, aby udržely v chodu svoji výrobu," dodal.
Letos výrazně klesl počet nově detekovaných vyděračských programů. Jejich počet klesl z loňských 62 na 38 v roce letošním. O to víc se ale zvýšil počet nově detekovaných verzí existujícího ransomwaru, a to na 96 000 proti loňským 54 000. Navýšení je zřejmě výsledkem snahy útočníků skrýt programy před stále lepšími technikami detekce.
Zhruba 65 procent společností, které byly letos ransomwarem napadeny, tvrdí, že přišly o přístup k většině nebo dokonce ke všem datům. Každá šestá firma, která zaplatila výkupné, se ke svým datům už nedostala. Tato čísla se v podstatě shodují s údaji za rok 2016.
Rok 2017 ve znamení ransomwaru
18.12.2017 SecurityWorld Viry
Poměr firem napadených ransomwarem v roce 2017 stoupl na 26,2 %. V předchozím roce bylo na firmy zacíleno o necelá 4 procenta všech ransomwarových útoků méně – 22,6 %. Na vině jsou především tři doposud nebývale mohutné útoky na firemní sítě, které zásadním způsobem změnily prostředí firemních počítačových sítí.
Rok 2017 se do historie kybernetické bezpečnosti zapíše především kvůli ransomwarovým útokům. Ty udeřily na společnosti po celém světě nečekaně prostřednictvím útoků s počítačovými červy. Hlavní motiv zatím zůstává nejasný. Jde o WannaCry z 12. května, ExPetr z 27. června a BadRabbit, který byl aktivní v druhé polovině října.
Všechny využily exploity navržené pro nabourání do korporátních sítí. Na podniky útočily i jiné ransomwary, které dohromady stály za 240 000 útoky. Tolika ransomwarovým infekcím zabránily v napadení korporátních počítačů po celém světě produkty Kaspersky Lab.
„Tyto známé útoky z průběhu celého roku jsou extrémním důkazem toho, že se kyberzločinci čím dál více zajímají o firemní cíle. Tento trend jsme ale zaznamenali už v roce 2016. Letos však nabral na obrátkách a zatím se nezdá, že by nějak polevoval. Děje se tak především proto, že jsou firmy velmi zranitelné, schopné zaplatit vyšší výkupné než jednotlivci a většinou jsou k tomu i ochotnější, aby udržely v chodu svoji výrobu. Není proto překvapením, že se objevují noví útočníci zaměření na firmy, kteří k útokům využívají vzdálené desktopové systémy,“ říká Fedor Sinitsyn, Senior Malware Analyst ze společnosti Kaspersky Lab.
Další trendy spojené s ransomwarem v roce 2017
V roce 2017 bylo celkem napadeno bezmála 950 000 unikátních uživatelů, zatímco v roce 2016 jich bylo 1,5 milionu. Tento markantní rozdíl je způsoben změnou v detekční metodologii. Například downloadery, které jsou běžně spojovány s krypto-malwarem, jsou nyní detekovány heuristickými technologiemi. Telemetrie Kaspersky Lab je už neklasifikuje jako ransomware.
Tři nejznámější útoky, ale i ransomwarové rodiny AES-NI nebo Uiwix, využívaly sofistikované exploity. Ty na veřejnost unikly na jaře 2017, když je zveřejnila skupina známá jako Shadow Brokers.
Došlo k výraznému poklesu nově detekovaných ransomwarových rodin. Jejich počet klesl z 62 v roce 2016 na 38 v roce letošním. O to víc se ale zvýšil počet nově detekovaných verzí existujícího ransomwaru – více než 96 000 v roce 2017 oproti loňským 54 000. Toto navýšení je zřejmě výsledkem snahy útočníků skrýt svůj ransomware před stále lepšími technikami detekce.
Ve druhém čtvrtletí letošního roku řada skupin své ransomwarové aktivity ukončila a klíče potřebné pro dešifrování dat zveřejnila. Pařily mezi ně AES-NI, xdata, Petya/Mischa/GoldenEye a Crysis. Crysis se následně opět objevil, nejspíše v režii jiné skupiny.
Kyberzločinci se stále větší oblibou využívali k infikování firem metodu vzdálených desktopových systémů. Ta se stala hlavním nástrojem mnoha skupin jako jsou Crysis, Purgen/Globelmposter a Cryakl.
65 % společností, které byly letos ransomwarem napadeny, tvrdí, že přišly o přístup k většině nebo dokonce ke všem datům. Každá šestá firma, která zaplatila výkupné, se ke svým datům už nedostala. Tato čísla se v podstatě shodují s údaji za rok 2016.
Velmi úspěšná je iniciativa No More Ransom, která byla spuštěna v červenci 2016. Ta spojuje orgány činné v trestním řízení a soukromé společnosti. Ty společně vyhledávají a následně zneškodňují velké ransomwarové rodiny. Snaží se tak pomoci koncovým uživatelům získat svá data zpět, a zároveň tím narušují lukrativní způsob výdělku kyberzločinců.
Pre-Installed Keeper Password Manager on Windows 10 exposes systems to passwords stealing
17.12.2017 securityaffairs Vulnerebility
White hat hacker discovered some Windows 10 versions come with a pre-installed version of Keeper Password Manager that exposes systems to passwords stealing.
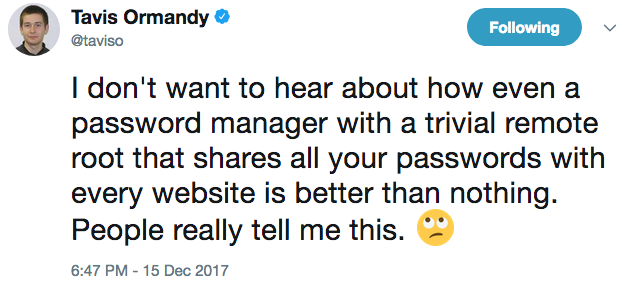
I was reading Tweets when I noticed the following post:
15 Dec
Tavis Ormandy
✔
@taviso
I created a new Windows 10 VM with a pristine image from MSDN, and noticed a third party password manager is now installed by default. It didn't take long to find a critical vulnerability. https://bugs.chromium.org/p/project-zero/issues/detail?id=1481 …
Tavis Ormandy
✔
@taviso
I don't want to hear about how even a password manager with a trivial remote root that shares all your passwords with every website is better than nothing. People really tell me this. 🙄
5:47 PM - Dec 15, 2017
353 353 likes 96 people are talking about this
Twitter Ads info and privacy
Some Windows 10 versions come with a pre-installed 3rd-party password manager app that could allow hackers to steal users credentials remotely.
Starting from Windows 10 Anniversary Update (Version 1607), Microsoft included in its OS a new feature called Content Delivery Manager that silently installs new “suggested apps” without notifying it to the users.
The hidden password manage was reported months ago by several Reddit users.
The presence of the password manager called Keeper was confirmed by the popular Google Project Zero hacker Tavis Ormandy who found the application pre-installed on his new Windows 10 system.
“I recently created a fresh Windows 10 VM with a pristine image from MSDN, and found that a password manager called “Keeper” is now installed by default. I’m not the only person who has noticed this: https://www.reddit.com/r/Windows10/comments/6dpj78/keeper_password_manager_comes_preinstalled_now/
I assume this is some bundling deal with Microsoft.” wrote Ormandy in a blog post published on Chromium Blog.
“I’ve heard of Keeper, I remember filing a bug a while ago about how they were injecting privileged UI into pages ( issue 917 ). I checked and, they’re doing the same thing again with this version. I think I’m being generous considering this a new issue that qualifies for a ninety day disclosure, as I literally just changed the selectors and the same attack works”
Ormandy decided to analyze the Keeper password manager searching for vulnerabilities to exploit to compromise the Windows installation.
After a few tests, Ormandy discovered a critical vulnerability in the Keeper Password Manager that could be exploited by attackers to “complete compromise of Keeper security, allowing any website to steal any password.”
The security vulnerability was quite identical to another issue discovered in August 2016 by Ormandy in the non-bundled version of the Keeper plugin that allowed malicious websites to steal passwords.
Ormandy also published proof-of-concept (PoC) exploit code that steals a user’s Twitter password if it is stored in the Keeper app.
Windows 10 users wouldn’t be affected unless they open Keeper password manager and enable the software to store their passwords.

Ormandy reported the flaw to the Keeper development team that addressed it in the released version 11.4.
Keeper declared it has not news of attacks exploiting the security vulnerability in the wild.
There is anyway a thing that the great Ormandy hasn’t discovered … why the Keeper password manager was pre-installed without users’ knowledge.
To disable the Content Delivery Manager it is possible to use these registry settings.