Backdoored Captcha Plugin Hits 300,000 WordPress Sites
21.12.2017 securityweek Hacking
Yet another plugin was removed from the WordPress repository after a backdoor was added to it following a recent update.
Called "Captcha" and featuring 300,000 active installs at the time it was removed, the plugin was found to have changed ownership several months ago. Initially developed and maintained by BestWebSoft, it was owned by an unnamed developer at the time the backdoor was added.
Through an update on December 4, code designed to trigger an automatic update process and download a ZIP file from the simplywordpress[dot]net domain was added to the plugin. The archive would extract and install itself over the copy of the Captcha plugin already running on site.
Inside the ZIP archive, a file called plugin-update.php, which was found to be the backdoor, was included, in addition to small changes to the plugin itself. The file would grant the author unauthorized administrative access to the WordPress websites using the plugin.
The backdoor was designed to create a session with user ID 1 (the default admin user WordPress creates at install), to set authentication cookies, and delete itself. Because the backdoor’s installation code was unauthenticated, anyone could trigger it, Wordfence reports.
The ZIP file also included an update to the URL using the same process that installed the backdoor, only this time to remove all traces of the malicious code.
The simplywordpress[.]net domain hosting the ZIP file is registered to a Stacy Wellington (scwellington@hotmail.co.uk), who apparently has registered a large number of other domains as well. One of the domains is unsecuredloans4u[.]co[.]uk, which is linked to Mason Soiza, an individual previously associated with similarly backdoored WordPress plugins.
“[Soiza] has a long history of buying WordPress plugins in order to place cloaked backlinks on his users’ sites. He then uses these backlinks to increase page rank in SERPs (Search Engine Results Pages) since only web crawlers such as Googlebot can read them,” Wordfence explains.
The individual buys plugins and, after a few months, adds the backdoor code to them to create cloaked backlinks to its own loan sites and boost site rankings for different search terms.
simplywordpress[.]net also includes the backdoored plugins Covert me Popup, Death To Comments, Human Captcha, Smart Recaptcha, and Social Exchange.
Looking at the website’s DNS history, Wordfence discovered a previous A-record of 195.154.179.176, which is the current A-record for unsecuredloans4u[.]co[.]uk, Mason Soiza’s domain. The same IP address is also used to host pingloans[.]co[.]uk, a site registered to Serpable Ltd, which is owned by a Charlotte Ann Wellington.
By digging deeper, Wordfence also discovered that both Wellingtons and Mason Soiza are linked to a Quint Group Limited. Stacy Wellington mentions working for Serpable, which is (or was previously) an SEO company and also “is an Introducer Appointed Representative of Quint Group Limited.”
“However, at this time, it’s unclear if either Charlotte or Stacy Wellington is the creator of the backdoor code we discovered in the Captcha plugin,” Wordfence notes.
Given the strong correlation between Stacy Wellington, simplywordpress[.]net, and heyrank[.]co[.]uk (another domain hosted on 195.154.179.176 and registered to the individual), the researchers suggest that wpdevmgr2678, the new owner of the Captcha plugin, could be Stacy Wellington.
Wordfence and the WordPress.org plugins team released a patched version of Captcha (v4.4.5) that no longer includes the backdoor. The automatic update mechanism was used to upgrade all backdoored versions (4.3.6 – 4.4.4) up to the new one and over 100,000 sites running versions the backdoored iterations were upgraded over the weekend.
Authorities Dismantle Ransomware Cybergang
21.12.2017 securityweek Ransomware
Five Romanian nationals suspected of being part of a cybercrime group focused on distributing ransomware were arrested last week as part of a global cybercrime crackdown operation.
Three of the individuals are suspected of spreading the CTB-Locker (Curve-Tor-Bitcoin Locker, also known as Critroni) ransomware, while the other two were arrested in a parallel ransomware investigation linked to the United States, Europol has revealed.
Called operation “Bakovia,” the joint investigation was carried out by Romanian Police (Service for Combating Cybercrime), the Romanian and Dutch public prosecutor’s office, the Dutch National Police (NHTCU), the UK’s National Crime Agency, the US FBI with the support of Europol’s European Cybercrime Centre (EC3), and the Joint Cybercrime Action Taskforce (J-CAT).
The Dutch High Tech Crime and other authorities informed the Romanian authorities in early 2017 that a group of individuals were involved in the sending of spam messages that appeared to have been sent by companies in countries like Italy, the Netherlands and the UK.
The spam emails contained what appeared to be an archived invoice that would hide malware inside. As soon as the intended victim would open the attachment, the CTB-Locker ransomware would be dropped and the data on the system would start being encrypted.
First observed in 2014, CTB-Locker was among the first ransomware families to use the Tor network to hide its command and control (C&C) infrastructure. New variants of the ransomware were observed over time, and a “vaccine” was released for it last year.
Targeting systems running Windows versions from XP to 8, the malware can encrypt user’s files asymmetrically, making it difficult to decrypt without a key that the attackers would release only after a ransom was paid.
Two people in the same criminal group are suspected to have been also involved in the distribution of the Cerber ransomware and to have infected a large number of computers in the United States. An investigation into the Cerber ransomware infections is undergoing.
Although the two investigations were separate in the beginning, they were joined when authorities discovered that the same group was behind both. The two suspects in the Cerber investigation hadn’t been located at the time of the actions on CTB-Locker, but were arrested one day after the US authorities issued an international arrest warrant for them.
As part of the operation, investigators searched six houses in Romania and seized a large amount of hard drives, laptops, external storage devices, cryptocurrency mining devices, and numerous documents.
“The criminal group is being prosecuted for unauthorised computer access, serious hindering of a computer system, misuse of devices with the intent of committing cybercrimes and blackmail,” Europol says.
The suspects did not develop the malware themselves, but acquired it from specific developers as part of the Ransomware-as-a-service (RaaS) model. They would launch the infection campaigns and pay around 30% of the profits to the developers. Wide-spread among cybercriminals, this modus operandi provides even wannabe criminals with access to powerful malicious applications.
“Ransomware attacks are relatively easy to prevent if you maintain proper digital hygiene. This includes regularly backing up the data stored on your computer, keeping your systems up to date and installing robust antivirus software. Also, never open an attachment received from someone you don’t know or any odd looking link or email sent by a friend on social media, a company, online gaming partner, etc.,” Europol notes.
Ransomware victims are advised to refrain from paying the ransom, as it would not guarantee the safe recovery of the data.
“Today, a clear message has been sent—involvement in cybercrime is not zero risk. These ransomware families claimed many victims in Belgium, Italy, the Netherlands, and the United States, and the arrests of the actors behind them is a significant takedown operation,” Raj Samani, Chief Scientist at McAfee, the security firm involved in the takedown, told SecurityWeek in an emailed statement.
Facebook Launches New Anti-Phishing Feature
21.12.2017 securityweek Social
Facebook announced on Wednesday the introduction of a new security feature designed to help users check if the emails they receive are legitimate or if they have been sent by cybercriminals.
When it detects a suspicious login attempt or a password change, Facebook notifies users by sending them an email from the Facebookmail.com domain. Cybercriminals often try to spoof these emails in an effort to lure internauts to phishing or other malicious websites.
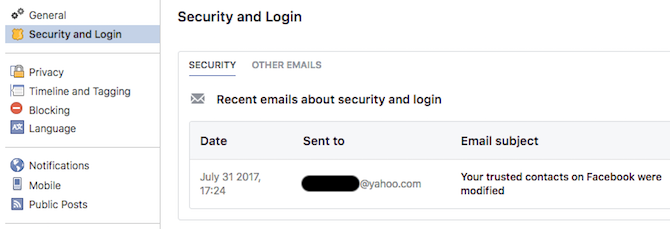
Users can now check if the email in their inbox really does come from Facebook by going to Settings -> Security and Login -> See recent emails from Facebook. Here they can see recent emails, including ones related to security and logins, and if the message from their inbox is not listed, it’s most likely fake.

“If you've checked this tool and determined that an email you received is fake, we encourage you to report it to phish@facebook.com, and if you believe your account has been compromised due to a phishing attempt, you may attempt to regain access to your account at: facebook.com/hacked,” said Scott Dickens, Product Manager with Facebook Account Integrity.
The new feature has apparently not been rolled out to all accounts so users who don’t immediately find it in the settings menu should check back in a few days.
The new feature comes just weeks after the social media giant’s founder and CEO, Mark Zuckerberg, claimed his company has prioritized security over profit.
“We're serious about preventing abuse on our platforms. We're investing so much in security that it will impact our profitability. Protecting our community is more important than maximizing our profits,” Zuckerberg said.
Facebook recently awarded researchers $100,000 for discovering a novel technique of detecting credential spear-phishing attacks in enterprise environments. The method combines a new anomaly scoring technique for ranking security alerts with features derived from the analysis of spear-phishing emails.
Windows Hello Face Recognition Tricked by Photo
21.12.2017 securityweek Safety
The facial recognition-based authentication system in Windows Hello has been bypassed by researchers using a printed photo, but the method does not work in the latest versions of Windows 10.
Windows Hello, a feature available in Windows 10, allows users to quickly and easily log into their devices using their face or fingerprints. The face authentication system uses near-infrared (IR) imaging and it’s advertised by Microsoft as “an enterprise-grade identity verification mechanism.”
Researchers have demonstrated on several occasions that face authentication can be bypassed, but some systems, such as Apple’s Face ID, are more difficult to bypass than others. In the case of Windows Hello, experts managed to bypass facial authentication using only a photograph of the legitimate user printed in a certain way.
Matthias Deeg and Philipp Buchegger of Germany-based penetration testing firm SySS managed to conduct successful attacks using low-resolution near-IR photos even with the “enhanced anti-spoofing” feature enabled, which should make it more difficult to trick the system.
“By using a modified printed photo of an authorized user, an unauthorized attacker is able to log in to or unlock a locked Windows 10 system as this spoofed authorized user,” the researchers said in an advisory. “Thus, by having access to a suitable photo of an authorized person (frontal face photo), Windows Hello face authentication can easily be bypassed with little effort, enabling unauthorized access to the Windows system.”
The attack was successfully replicated on Windows 10 versions 1511 and 1607 even with the “enhanced anti-spoofing” feature enabled. In newer versions of the operating system, such as 1703 and 1709, the method no longer works if the anti-spoofing mechanism is turned on.
However, the researchers highlighted that updating to newer versions of Windows 10 and enabling the anti-spoofing feature is not enough to block attacks. Users must also reconfigure Hello Face Authentication.
North Korea Denies Role in WannaCry Ransomware Attack
21.12.2017 securityweek BigBrothers
North Korea on Thursday denied US accusations it was behind the WannaCry global ransomware cyberattack, saying Washington was demonising it.
WannaCry infected some 300,000 computers in 150 nations in May, encrypting user files and demanding hundreds of dollars from their owners for the keys to get them back.
The White House this week blamed Pyongyang for it, adding its voice to several other countries that had already done so.
A spokesman for Pyongyang's foreign ministry said the US allegations were "absurd", adding: "As we have clearly stated on several occasions, we have nothing to do with cyber-attacks."
Washington had "ulterior" motives, the spokesman added according to the North's KCNA news agency.
"This move is a grave political provocation by the US aimed at inducing the international society into a confrontation against the DPRK by tarnishing the image of the dignified country and demonising it," he said.
North Korea is subject to multiple United Nations sanctions over its banned nuclear and ballistic missile programs, and tested its third ICBM last month.
Leader Kim Jong-Un declared his country had achieved full nuclear statehood, in a challenge to US President Donald Trump who responded with promises of "major sanctions".
According to experts North Korea's cyberwarfare targets have expanded from the political -- it was accused of hacking into Sony Pictures Entertainment in 2014 to take revenge for "The Interview", a satirical film that mocked Kim -- to the financial, as it seeks new sources of funding.
A South Korean cryptocurrency exchange shut down on Tuesday after losing 17 percent of its assets in a hacking -- its second cyberattack this year, with the North accused of involvement in the first.
Investigators are probing the possibility that Pyongyang was also behind Tuesday's incident, the Wall Street Journal and Bloomberg News reported.
The North is blamed for a massive $81 million cyber-heist from the Bangladesh Central Bank (BCB) in 2016, as well as the theft of $60 million from Taiwan's Far Eastern International Bank in October.
Pyongyang has angrily denied the accusations -- which it described as a "slander" against the authorities -- but analysts say the digital footprints left behind suggest otherwise.
Fake Bitcoin Wallet Apps Removed from Google Play
21.12.2017 securityweek Android
Three fake Bitcoin applications were recently removed from Google Play after security researchers discovered they were tricking users into sending funds to their developers, mobile security firm Lookout has discovered.
The impressive increase in Bitcoin value over the past several months has stirred interest from individuals worldwide, including cybercriminals. The number of attacks involving the cryptocurrency has increased recently, and it appears that they moved to mobile as well.
Detected as PickBitPocket, the rogue applications in Google Play were designed in such a way that they provide the attacker’s Bitcoin address instead of the seller’s. The malicious programs registered a total of up to 20,000 downloads before Google removed them from the application storefront.
Basically, when attempting to buy goods or services from an Android device where a PickBitPocket wallet app is installed, the user ends up routing the Bitcoin payment to the attacker.
The three fake Bitcoin apps, Lookout reports, included Bitcoin mining, which had between 1,000 and 5,000 installs at the time it was removed, Blockchain Bitcoin Wallet – Fingerprint, which had between 5,000 and 10,000 installs, and Fast Bitcoin Wallet, with between 1,000 and 5,000 installs.
“As Bitcoin captures broader interest, this means more people may be purchasing the cryptocurrency, or looking for mobile wallets to store their coins. Individuals should be vigilant in choosing a secure wallet and should also have a security solution in place to identify malicious activity on their device,” Lookout concludes.
VMWare addressed severe Code Execution vulnerabilities in several products
21.12.2017 securityweek Vulnerebility
VMware has released security updates to address four vulnerabilities in its ESXi, vCenter Server Appliance (vCSA), Workstation and Fusion products.
The flaws were addressed with the release of six patches for ESXi, version 12.5.8 of Workstation, version 8.5.9 of Fusion, and version 6.5 U1d of vCSA.
Some of the flaws could be exploited by an attacker for arbitrary code execution.
Security experts from Cisco Talos group discovered two of the code execution vulnerabilities that ranked as critical and assigned them a CVSS score of 9.0, while VMware classified them as having “important” severity. The flaws analyzed by the Talos group affects the VNC implementation in VMWare products used to allow remote access to the solutions.
“Today, Talos is disclosing a pair of vulnerabilities in the VNC implementation used in VMWare’s products that could result in code execution. VMWare implements VNC for its remote management, remote access, and automation purposes in VMWare products including Workstation, Player, and ESXi which share a common VMW VNC code base. The vulnerabilities manifest themselves in a way that would allow an attacker to initiate of VNC session causing the vulnerabilities to be triggered.” reads the security advisory published by CISCO.
The vulnerability CVE-2017-4941 resides in the remote management functionality of VMWare, it could be exploited by a remote attacker to execute code in a virtual machine via an authenticated virtual network computing (VNC) session.
“A specially crafted set of VNC packets can cause a type confusion resulting in stack overwrite, which could lead to code execution.” reads the advisory published by Cisco Talos.
The second issue discovered by Cisco Talos is a heap overflow bug tracked as CVE-2017-4933 that could be triggered by an attacker to execute arbitrary code in a virtual machine using specially crafted VNC packets.
“An exploitable code execution vulnerability exists in the remote management functionality of VMware . A specially crafted set of VNC packets can cause a heap overflow resulting in heap corruption. An attacker can create a VNC session to trigger this vulnerability.” states Cisco Talos in the security advisory.
VMware hasn’t classified the flaws as critical because it argued that their exploitation is possible in ESXi only if VNC is manually enabled in the VM’s configuration file and the application is set to allow VNC traffic through the built-in firewall.
VMware
VMware also patched a stored cross-site scripting (XSS) flaw tracked as CVE-2017-4940 and affecting the ESXi Host Client, the issued could be exploited to inject code that gets executed when users access the Host Client. The company credited the expert Alain Homewood from Insomnia Security for its discovery.
The fourth flaw addressed by VMWare is a privilege escalation affecting vCSA that is tracked as CVE-2017-4943. The vulnerability was discovered by Lukasz Plonka and resides in the showlog plugin, it could be exploited by an attacker with low privileges to obtain root level access to the appliance’s base operating system.
Operation Bakovia – Romanian authorities arrest 5 individuals for Spreading CTB Locker and Cerber Ransomware
21.12.2017 securityweek Ransomware
Operation Bakovia – Romanian police arrested 5 individuals suspected of infecting tens of thousands of computers across Europe and the US with Ransomware.
Another success of law enforcement against cybercrime, this time Romanian police have arrested five individuals suspected of infecting tens of thousands of computers across Europe and the United States with Ransomware.
The arrests are part of an international operation tracked as Operation Bakovia conducted by Europol, the FBI and law enforcement agencies from Romanian, Dutch, and the UK.
The suspects have been arrested for spreading the dreaded Cerber and CTB Locker (Curve-Tor-Bitcoin Locker) ransomware, the police arrested them and raided six houses in East Romania last week.
Three suspects were arrested in Romania, the remaining two men belonging to the same organization were arrested in Bucharest as part of a parallel investigation conducted with the help of US authorities.
“During the last week, Romanian authorities have arrested three individuals who are suspected of infecting computer systems by spreading the CTB-Locker (Curve-Tor-Bitcoin Locker) malware – a form of file-encrypting ransomware. Two other suspects from the same criminal group were arrested in Bucharest in a parallel ransomware investigation linked to the US.” states the announcement published by Europol.
“During this law enforcement operation called “Bakovia“, six houses were searched in Romania as a result of a joint investigation carried out by the Romanian Police (Service for Combating Cybercrime), the Romanian and Dutch public prosecutor’s office, the Dutch National Police (NHTCU), the UK’s National Crime Agency, the US FBI with the support of Europol’s European Cybercrime Centre (EC3) and the Joint Cybercrime Action Taskforce (J-CAT).”
As a result of the investigation, during the raid, the police seized a significant amount of hard drives, external storage, laptops, cryptocurrency mining devices, numerous documents and hundreds of SIM cards.
The suspects are being prosecuted for unauthorized computer access, serious hindering of a computer system, misuse of devices with the intent of committing cybercrimes and blackmail.
The Europol published a video of the arrests that shows the police’s incursion in the suspects’ residence.
CTB Locker, aka Critroni, is based on CryptoLocker, it was the first ransomware to use the Tor anonymizing network to hide the command and control infrastructure.
The Cerber ransomware was first spotted in 2016, it was offered in the criminal underground as a ransomware-as-a-service (RaaS).
“The investigation in this case revealed that the suspects did not develop the malware themselves, but acquired it from specific developers before launching various infection campaigns of their own, having to pay in return around 30% of the profit.” continues the Europol.
“This modus operandi is called an affiliation program and is “Ransomware-as-a-service”, representing a form of cybercrime used by criminals mainly on the Dark Web, where criminal tools and services like ransomware are made available by criminals to people with little knowledge of cyber matters, circumventing the need for expert technological skills.”
The CTB Locker was the most widespread ransomware in 2016, while Cerber was one of the most profitable ransomware in the criminal ecosystem.
Both ransomware were spread through drive-by-download attacks and phishing campaign.
“In early 2017, the Romanian authorities received detailed information from the Dutch High Tech Crime Unit and other authorities that a group of Romanian nationals was involved in sending spam messages,” Europol said in its press release.“The spam messages intended to infect computer systems and encrypt their data with the CTB-Locker ransomware aka Critroni. Each email had an attachment, often in the form of an archived invoice, which contained a malicious file. Once this attachment was opened on a Windows system, the malware encrypted files on the infected device.”
At the time of publishing the press release, the police did not yet release the identities of the arrested individuals,
Exclusive, CSE CybSec ZLAB Malware Analysis Report: The Bladabindi malware
21.12.2017 securityweek Virus
The CSE CybSec Z-Lab Malware Lab analyzed a couple of new malware samples, belonging to the Bladabindi family, that were discovered on a looking-good website.
ZLab team detected two new threats hosted on a looking-good website www[.]6th-sense[.]eu. Both malware looks like a legitimate app that users have to install in order to access the media file hosted on the website.

Figure 1 – Homepage of the malicious website
The malicious website (www[.]6th-sense[.]eu), hosts 2 different malware samples:
“6thClient.exe” can be downloaded clicking the pop-up button on the homepage inviting users to download the client indicated on the screen.
“Firefox.exe” is hosted on the path “www[.]6th-sense[.]eu/Firefox.exe”
Both malware act as spyware, in particular, “Firefox.exe” seems to act as a bot, because it waits for specific commands from a C&C.
Analyzing the TCP stream, we can see the communication session performed by malware with the C&C:

The first row shows the PC’s name, User’s name, and the OS’s version.
There are two recurrent words: “nyan” and “act”
the first word represents a separator among the information sent to the C2C
the second one represents the category of the information sent by the bot. in this case it is the ‘action’ performed by the host, in particular, it is the name of the window in the foreground
In the middle, we can see some strings coded in Base64. These strings represent the window’s title in the foreground.
The C2C acknowledges the result sending the number Zero to the bot, probably this value indicates that there are no commands to execute on the host.
Both Malware would seem to belong to the malware family Bladabindi.
Bladabindi is a Trojan malware that steals confidential information from the compromised computer. Hackers also use it as a Malware downloader to deliver and execute other malware. With this malware, cybercriminals could steal
Your computer name
Your native country
OS serial numbers
Windows usernames
Operating system version
Stored passwords in chrome
Stored passwords in Firefox
You can download the full ZLAB Malware Analysis Report at the following URL:
Malware Analysis Report: Bladabindi.Dec17
Facebook, WhatsApp Both Put Under Notice by Europe
20.12.2017 securityweek Social
The French privacy regulator, the National Commission of Computing and Freedoms (CNIL) has issued a formal notice on WhatsApp. It requires the Facebook company to stop personal data transfers to the parent company in the U.S. unless there is a legal basis for doing so. In particular, WhatsApp must obtain 'user consent' (within the meaning of European law) to gather and transfer that data.
It's a busy time for privacy issues between the U.S. and Europe. CNIL published its notice on Tuesday. On the same day, the powerful German competition authority, the Bundeskartellamt (the Federal Cartel Office or FCO), warned Facebook that it "is abusing [its] dominant position by making the use of its social network conditional on its being allowed to limitlessly amass every kind of data generated by using third-party websites."
Last week the European Commission filed an amicus curiae brief (PDF) with the United States Court of Appeals For the Second Circuit in the ongoing dispute between Microsoft and the U.S. government. Noticeably, this was in support of neither party, but was an attempt to ensure that the the U.S. court has a full understanding of the relevant European law -- in this case, specifically the General Data Protection Regulation (GDPR).
The German FCO concern over Facebook is over the widespread collection of personal user data. In February 2017, the FCO declared that it would investigate Facebook. President Andreas Mundt said at the time, "Dominant companies are subject to special obligations. These include the use of adequate terms of service as far as these are relevant to the market. For advertising-financed internet services such as Facebook, user data are hugely important. For this reason it is essential to also examine under the aspect of abuse of market power whether the consumers are sufficiently informed about the type and extent of data collected."
Now the FCO has stated, "The authority holds the view that Facebook is abusing this dominant position by making the use of its social network conditional on its being allowed to limitlessly amass every kind of data generated by using third-party websites." At the heart of the concern is the inadequate informed consent of the user in allowing personal data collection. Facebook claims that it is not a dominant company in Europe (it has more than 30 million active monthly users in Germany); and that it complies with European law.
The concept of free and informed consent also underlies CNIL's notice against Facebook subsidiary, WhatsApp. In August 2016 WhatsApp changed its Terms of Service and Privacy Policy, explaining that in future, its user data would be transferred to Facebook for targeted advertising, security, and business intelligence. The European regulator grouping, known as Article 29 Working Party, quickly asked WhatsApp to stop the transfer of personal data for targeted advertising.
In a subsequent investigation, WhatsApp told CNIL that French personal data had never been used for targeted advertising. However, CNIL determined that personal data was shared for business intelligence and security. "Thus," says the CNIL statement, "information about users such as their phone number or their use habits on the application are shared." While sharing data for security is not an issue, sharing for business intelligence "is not based on the legal basis required by the Data Protection Act for any processing."
According to CNIL, any user consent to this data collection and sharing is neither free nor informed ("the only way to refuse the data transfer for 'business intelligence' purpose is to uninstall the application"). CNIL requested a sample of data that had been transferred, but this was refused by WhatsApp. The data concerned is now in the U.S., and WhatsApp apparently considers that it is only subject to the law of the U.S.
This refusal has been interpreted by CNIL as a breach of WhatsApp's obligation to cooperate with the regulator under Article 21 of the Data Protection Act. It has consequently issued the formal notice requiring WhatsApp to comply with the Data Protection Act within one month.
Neither the CNIL notice nor the FCO statement can directly lead to sanctions against Facebook/WhatsApp. They can best be viewed as shots across the bow, which -- if ignored -- could lead to the full cannon power of European data protection being leveled against Facebook. Both statements being issued on the same day is a remarkable coincidence. Coming exactly one week after the European Commission used the GDPR-relevant Microsoft vs U.S. government court struggle to make sure that U.S. courts understand Europe's point of view is also remarkable.
It could all be coincidence. But coincidence or not, Europe is warning the large American tech companies -- and indeed, any company that trades with or within Europe -- it is taking its data protection laws seriously. While existing sanctions could be funded out of the running costs of large companies, the potential for future GDPR sanctions of up to 4% of global turnover is not something that can be ignored. Any assumption that Europe will not be quick to enforce GDPR when it comes into force in May 2018 should be rejected.
White House Blames North Korea for Cyberattack
20.12.2017 securityweek BigBrothers
The White House on Tuesday publicly accused North Korea of launching a massive cyberattack that hit 150 countries last May -- hobbling networks from Britain's public health system to FedEx.
"After careful investigation, the United States is publicly attributing the massive 'WannaCry' cyberattack to North Korea," said White House homeland security advisor Tom Bossert.
"We do not make this allegation lightly, we do so with evidence and we do so with partners," he added.
Exploiting a security flaw in Microsoft's Windows XP operating system, the malware infected an estimated 300,000 computers demanding ransom to decrypt data.
The United States is the latest country to point the finger of blame at Pyongyang, attribution which comes as part of a drive to exert "maximum pressure" on the regime.
As yet, no retaliatory measures have been announced.
Among the infected computers were those at Britain's National Health Service (NHS), Spanish telecoms company Telefonica and US logistics company FedEx.
London had already blamed North Korea, which hit a third of Britain's public hospitals.
Pyongyang then denied the allegation, saying it went "beyond the limit of our tolerance" and was a "wicked attempt to lure the international community into harboring greater mistrust of the DPRK."
- US government under scrutiny -
Questions had been raised about whether the US government acted in a timely manner to respond to the attack, with Microsoft accusing Washington of spotting the flaw and using it for its own ends.
"This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem," Microsoft's Brad Smith said at the time.
"Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage," he said, claiming that the National Security Agency of spotting the flaw and saying nothing.
Bossert said that the United States kept only 10 percent of security flaws secret and had no policy of "stockpiling" or withholding information from potential targets.
Since coming to office Donald Trump has sought to put pressure on North Korea, as its reclusive leaders edge ever-closer to developing a ballistic missile that could deliver a nuclear warhead to the United States.
Amid a series of tests Trump's administration has appeared at odds over whether talks could offer a way out of the standoff.
National Security Advisor HR McMaster tried to clean up that question in an interview with the BBC, saying the United States wanted a peaceful solution: "Of course that's what we want but we are not committed to a peaceful resolution."
"We are committed to a resolution, we want the resolution to be peaceful. But, as the president has said, all options are on the table and we have to be prepared if necessary to compel the denuclearization of North Korea without the cooperation of that regime."
Trump's first National Security Strategy released Monday, declared that "North Korea seeks the capability to kill millions of Americans with nuclear weapons."
"Continued provocations by North Korea will prompt neighboring countries and the United States to further strengthen security bonds and take additional measures to protect themselves."
Code Execution Flaws Found in Trend Micro Smart Protection Server
20.12.2017 securityweek Vulnerebility
Researchers at Core Security have discovered five vulnerabilities in Trend Micro’s Smart Protection Server product, including flaws that could have been exploited for remote code execution.
Smart Protection Server is a cloud-based protection solution that leverages file and web reputation technologies to detect security risks. The product’s administration interface was found to contain information exposure, improper authentication, improper control and improper filtering issues.
The vulnerabilities were reported to Trend Micro in early September and they were patched in mid-November with the release of version 3.3. The security firm has made available an advisory of its own for the flaws, which are tracked as CVE-2017-11398, CVE-2017-14094, CVE-2017-14095, CVE-2017-14096 and CVE-2017-14097. The vendor has rated only one of the issues as high severity, while the rest are medium severity.
One of the security holes is related to the fact that an attacker could have accessed diagnostic logs without authentication via HTTP. Accessing the log file can allow an attacker to obtain information needed to hijack active user sessions and perform authenticated requests.
Once authentication has been bypassed using the aforementioned flaw, an attacker could have exploited a weakness related to a PHP script that creates cron jobs when scheduling software updates. Core Security has released proof-of-concept (PoC) exploits that show how a hacker could have leveraged this vulnerability to execute arbitrary commands and open a reverse shell using specially crafted requests.
Researchers also found a local file inclusion vulnerability that can lead to remote command execution. This weakness is more difficult to exploit as the attacker needs to set up a fake update server and get the Trend Micro product to download a malicious file from it.
Successful exploitation results in a PHP script being written to the server. The attacker can then include the script using the file inclusion vulnerability and execute it.
In this case, escalating privileges to root is also possible, including via methods disclosed a few months ago by researchers Steven Seeley and Roberto Suggi Liverani, who reported identifying more than 200 vulnerabilities in Trend Micro products. Core Security said several of the privilege escalation vectors disclosed by the experts remain unpatched.
Core researchers also discovered a stored cross-site scripting (XSS) flaw that could have been leveraged to execute arbitrary code whenever a user accessed a specific URL.
Finally, Trend Micro Smart Protection Server was affected by an improper access control issue that exposed the credentials needed to access monitored servers and other information. The credentials were stored in a SQLite database in an encrypted form, but the database could have been accessed without authentication and the encryption key was stored in an unprotect location and could have been downloaded by an unauthenticated user.
This is not the first time Core researchers have found vulnerabilities in a security product. In late June, the company said it had discovered several potentially serious flaws in Kaspersky Lab’s Anti-Virus for Linux File Server product.
DHS Warns of Malware Targeting Industrial Safety Systems
20.12.2017 securityweek ICS
The National Cybersecurity & Communications Integration Center (NCCIC) of the U.S. Department of Homeland Security (DHS) on Monday published an analysis report on a piece of malware designed to target industrial safety systems.
FireEye and Dragos reported last week that sophisticated malware, tracked by the companies as Triton and Trisis, caused a shutdown at a critical infrastructure organization somewhere in the Middle East. CyberX, a firm that specializes in industrial cybersecurity, believes Iran was likely behind the attack and the target was probably an organization in Saudi Arabia.
The NCCIC, which dubbed the malware “HatMan,” published a report that describes the threat, and provides mitigations and YARA rules.
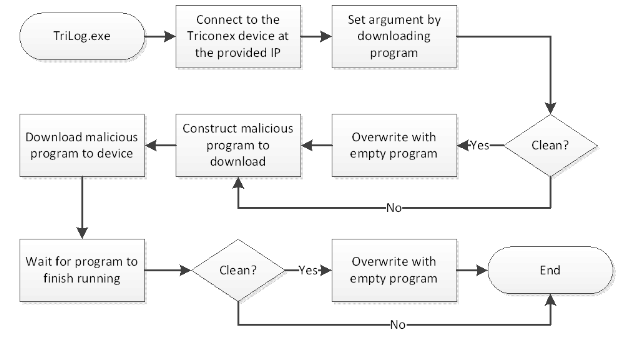
The Python-based HatMan malware targets Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers, designed for monitoring processes and restoring them to a safe state or perform a safe shutdown if a potentially dangerous situation is detected.
The malware communicates with SIS controllers via the proprietary TriStation protocol, and allows attackers to manipulate devices by adding new ladder logic.
The attack on the critical infrastructure organization in the Middle East was discovered after the hackers’ activities resulted in the SIS controller triggering a process shutdown. However, experts believe this was likely an accident, and the final goal may have been to cause physical damage.
The NCCIC pointed out in its report that the malware has two main components: one that runs on a compromised PC and interacts with the safety controller, and one that runs on the controller itself.
“Although by itself HatMan does not do anything catastrophic — safety systems do not directly control the process, so a degraded safety system will not cause a correctly functioning process to misbehave — it could be very damaging when combined with malware that impact s the process in tandem. Were both to be degraded simultaneously, physical harm could be effected on persons, property, or the environment,” NCCIC said in its report.
“It is safe to say that while HatMan would be a valuable tool for ICS reconnaissance, it is likely designed to degrade industrial processes or worse. Overall, the construction of the different components would indicate a significant knowledge about ICS environments — specifically Triconex controllers — and an extended development lifecycle to refine such an advanced attack,” it added.
Schneider Electric has launched an investigation into this incident. The company said there had been no evidence that the malware exploited any vulnerabilities in its products. The automation giant has advised customers not to leave the device in “Program” mode when it’s not being configured as the malware can only deliver its payload if the controller is set to this mode.
“The fact that this actor has the capability to access the safety instrumentation device, and potentially make changes to the device firmware unnoticed, should make critical infrastructure owner-operators sit up and take heed,” said Emily S. Miller, Director of National Security and Critical Infrastructure Programs at Mocana. “Yes, in this case the malware tripped the safety systems and was noticed, but who’s to say the actor won’t learn from its mistakes or hasn’t already?”
North Korea's New Front: Cyberheists
20.12.2017 securityweek BigBrothers
The messages are alluring, the pictures are attractive. But the women seeking to beguile South Korean Bitcoin executives could actually be hackers from Pyongyang in disguise, experts warn.
In the face of sanctions over its banned nuclear and ballistic missile programs, the cash-strapped North is deploying an army of well-trained hackers with an eye on a lucrative new source of hard currency, they say.
Its cyberwarfare abilities first came to prominence when it was accused of hacking into Sony Pictures Entertainment to take revenge for "The Interview", a satirical film that mocked its leader, Kim Jong-Un.
But it has rapidly expanded from political to financial targets, such as the central bank of Bangladesh and Bitcoin exchanges around the world, with Washington this week blaming it for the WannaCry ransomware that wreaked havoc earlier this year.
And a South Korean cryptocurrency exchange shut down on Tuesday after losing 17 percent of its assets in a hacking -- its second cyberattack this year, with the North accused of being behind the first.
According to multiple South Korean reports citing Seoul's intelligence agency, North Korean hackers approach workers at digital exchanges by posing as beautiful women on Facebook, striking online conversations and eventually sending files containing malicious code.
North Korea Cyber AttacksThey also bombard executives with emails posing as job seekers sending resumes -- with the files containing malware to steal personal and exchange data.
Moon Jong-Hyun, director at Seoul cybersecurity firm EST Security, said the North had stepped up online honeytrap tactics targeting Seoul's government and military officials in recent years.
"They open Facebook accounts and maintain the online friendship for months before backstabbing the targets in the end," Moon told a cybersecurity forum, adding many profess to be studying at a US college or working at a research think tank.
- 'Criminal enterprise' -
Simon Choi, director of Seoul cybersecurity firm Hauri, has accumulated vast troves of data on Pyongyang's hacking activities and has been warning about potential ransomware attacks by the North since 2016.
The United States has reportedly stepped up cyberattacks of its own against Pyongyang.
But Choi told AFP: "The North's hacking operations are upgrading from attacks on 'enemy states' to a shady, lucrative moneymaking machine in the face of more sanctions."
Pyongyang's hackers have showed interest in Bitcoin since at least 2012, he said, with attacks spiking whenever the cryptocurrency surges -- and it has soared around 20-fold this year.
US cybersecurity firm FireEye noted that a lack of regulations and "lax anti-money laundering controls" in many countries make digital currencies an "attractive tactic" for the North.
Cryptocurrencies, it said in a September report, were "becoming a target of interest by a regime that operates in many ways like a criminal enterprise".
It documented three attempts by the North to hack into Seoul cryptocurrency exchanges between May and July as a way to "fund the state or personal coffers of Pyongyang's elite".
In October, Lazarus, a hacking group linked with the North, launched a malicious phishing campaign targeting people in the bitcoin industry with a fake but lucrative job offer, according to US cybersecurity firm Secureworks.
- 'Hard to predict' -
Hacking attacks targeting digital currencies are only the latest in the long list of alleged online financial heists by the North.
The North is blamed for a massive $81 million cyber-heist from the Bangladesh Central Bank (BCB) in 2016, as well as the theft of $60 million from Taiwan's Far Eastern International Bank in October.
Although Pyongyang has angrily denied the accusations -- which it described as a "slander" against the authorities -- analysts say the digital footprints left behind suggest otherwise.
The attack on the BCB was linked to "nation-state actors in the North", cybersecurity firm Symantec said, while the Taiwanese bank theft had some of the "hallmarks" of Lazarus, according to the British defence firm BAE Systems.
Proceeds from such actions are laundered through casinos in the Philippines and Macau or money exchanges in China, said Lim Jong-In, a cyber-security professor at Korea University in Seoul, making it "virtually impossible" to trace.
The global WannaCry ransomware attack in May infected some 300,000 computers in 150 nations, encrypting their files and demanding hundreds of dollars from their owners for the keys to get them back.
Experts say that young hacking talents are handpicked at school to be groomed at elite Kim Chaek University of Technology or Kim Il Sung Military University in Pyongyang, and now number more than 7,000.
They were once believed to be operating mostly at home or neighbouring China, but analysis by cybersecurity firm Recorded Future noted "significant physical and virtual North Korean presences" in countries as far away as Kenya and Mozambique.
FireEye CEO Kevin Mandia put the North among a quartet of countries -- along with Iran, Russia and China -- that accounted for more than 90 percent of cybersecurity breaches the firm dealt with.
Its hackers, he said, were "interesting to respond to and hard to predict".
Australia, Canada, Others Blame North Korea for WannaCry Attack
20.12.2017 securityweek BigBrothers
The United States is not the only country to officially accuse North Korea this week of being behind the WannaCry ransomware campaign. Canada, Japan, Australia and New Zealand have also blamed Pyongyang for the attack.
The U.K. accused North Korea in late October, and the other Five Eyes countries and Japan have now done the same.
“We are aware of the statements made by our allies and partners concerning the role of actors in North Korea in the development of the malware known as WannaCry,” said Greta Bossenmaier, chief of Canada’s Communications Security Establishment (CSE). “This assessment is consistent with our analysis.”
Australia said its own intelligence agencies reached the same conclusion after consultations with allies. New Zealand attributed the WannaCry attack to North Korean threat actors based on “cyber threat analysis from a range of sources, including the United States and the United Kingdom.”
The WannaCry ransomware was unleashed in May and it infected roughly 300,000 computers across 150 countries. The malware spread using exploits developed by the Equation Group, an actor linked to the U.S. National Security Agency (NSA).
North Korea in October denied the accusations, claiming that they were a “wicked attempt" to further tighten international sanctions. Furthermore, not everyone believes North Korea is responsible. Endpoint security firm Cybereason said in May that the attack did not fit Pyongyang’s style and interests, and the company stands by its initial assessment.
Nevertheless, the United States is convinced that the WannaCry attack is the work of North Korea, which is believed to be responsible for several recent profit-driven campaigns. “We do not make this allegation lightly,” said White House homeland security advisor Tom Bossert. “We do so with evidence, and we do so with partners.”
One of those partners is Microsoft, which concluded that the North Korea-linked threat actor known as Lazarus – the company tracks it as ZINC – was responsible for the ransomware attack.
“Among other steps, last week we helped disrupt the malware this group relies on, cleaned customers’ infected computers, disabled accounts being used to pursue cyberattacks and strengthened Windows defenses to prevent reinfection. We took this action after consultation with several governments, but made the decision independently,” said Brad Smith, president and chief legal officer at Microsoft.
“We are pleased to see these governments making this strong statement of attribution. If the rising tide of nation-state attacks on civilians is to be stopped, governments must be prepared to call out the countries that launch them,” Smith said.
Facebook also had a role in disrupting the activities of the Lazarus group, but pointed out that its actions were not focused on the WannaCry malware itself.
“In this case, we deleted accounts operated by this group to make it harder for them to conduct their activities. Similar to other threat groups, they largely used personal profiles and pretended to be other people in order to do things like learning about others and building relationships with potential targets,” the social media giant stated.
“We also notified people who may have been in contact with these accounts and gave suggestions to enhance their account security, as we have done in the past about other threat groups,” it added.
Code Execution Flaws Patched in Several VMware Products
20.12.2017 securityweek Vulnerebility
VMware has released patches and updates for its ESXi, vCenter Server Appliance (vCSA), Workstation and Fusion products to address a total of four vulnerabilities, including ones that can be exploited for arbitrary code execution.
Two of the code execution flaws, discovered by researchers at Cisco Talos, affect the remote management functionality of VMware ESXi, Workstation and Fusion. While VMware has classified them as having “important” severity, Cisco believes they are critical and assigned them a CVSS score of 9.0.
One of these security holes, CVE-2017-4941, allows a remote attacker to execute code in a virtual machine via an authenticated virtual network computing (VNC) session.
“A specially crafted set of VNC packets can cause a type confusion resulting in stack overwrite, which could lead to code execution. An attacker can initiate a VNC session to trigger this vulnerability,” Cisco Talos said in an advisory.
The second vulnerability found by Cisco researchers also allows an attacker to execute arbitrary code in a virtual machine using specially crafted VNC packets. The bug, described as a heap overflow, is tracked as CVE-2017-4933.
VMware pointed out that exploitation of these flaws is possible in ESXi only if VNC is manually enabled in a virtual machine’s configuration file and the application is set to allow VNC traffic through the built-in firewall.
Another flaw patched this week by VMware is CVE-2017-4940, a stored cross-site scripting (XSS) issue affecting the ESXi Host Client. The weakness, discovered by Alain Homewood of Insomnia Security, allows an attacker to inject code that gets executed when users access the Host Client.
The last vulnerability is a privilege escalation affecting vCSA. Identified by Lukasz Plonka and tracked as CVE-2017-4943, the security hole is related to the showlog plugin and it allows an attacker with low privileges to obtain root level access to the appliance’s base operating system.
VMware fixed the vulnerabilities with the release of six different patches for ESXi, version 12.5.8 of Workstation, version 8.5.9 of Fusion, and version 6.5 U1d of vCSA.
vBulletin Patches Disclosed Vulnerabilities
20.12.2017 securityweek Vulnerebility
vBulletin developers announced on Tuesday that they have patched two recently disclosed vulnerabilities that can be exploited by a remote attacker to execute arbitrary code and delete files from the server.
The flaws were disclosed last week by Beyond Security. One of the security holes is a file inclusion issue that affects Windows-based vBulletin installations. It allows an unauthenticated attacker to inject malicious PHP code into a file on the server and “include” that file by manipulating the routestring= parameter in a request, which results in the code getting executed.
The second vulnerability, identified as CVE-2017-17672, is a deserialization issue that can be exploited by an unauthenticated attacker to delete arbitrary files and possibly even execute arbitrary code.
Beyond Security said the flaws were reported to vBulletin on November 21, but the developers of the forum software told SecurityWeek they only learned about them last week. By Monday, a patch had already been developed and was being tested.
The vulnerabilities impact versions 5.3.2, 5.3.3 and 5.3.4. Fixes were rolled out on Tuesday with the release of vBulletin 5.3.4 Patch Level 1, 5.3.3 Patch Level 1, and 5.3.2 Patch Level 2. Forums hosted on vBulletin Cloud have been patched automatically.
“Two potential issues have been identified in vBulletin 5.3.2 and higher,” said Wayne Luke, vBulletin Technical Support Lead. “The first affects the template rendering functionality and could lead to arbitrary file deletion. The second allows the possibility of remote file inclusion via the legacy routing system on Windows servers. We have applied fixes for these issues. It is recommended that you apply this patch as soon as possible.”
It’s important that vBulletin forum administrators patch their installations as soon as possible. Malicious actors can quickly start exploiting the flaws in the wild, especially since technical details and proof-of-concept (PoC) code have been made available for both vulnerabilities.
Windows 10 Hello facial recognition feature can be spoofed with photos
20.12.2017 securityaffairs Safety
Experts discovered that the Windows 10 facial recognition security feature Hello can be spoofed using a photo of an authorized user.
Security experts at pen-test firm Syss have discovered that the Windows 10 facial recognition security feature dubbed Hello can be spoofed in the simplest way, using a photo of an authorized user.
“Microsoft face authentication in Windows 10 is an enterprise-grade identity verification mechanism that’s integrated into the Windows Biometric Framework (WBF) as a core Microsoft Windows component called Windows Hello. Windows Hello face authentication utilizes a camera specially configured for near infrared (IR) imaging to authenticate and unlock Windows devices as well as unlock your Microsoft Passport.”
The bad news for the users is that even if they have installed the fixed versions shipped in October (builds 1703 or 1709) the technique is effective. In this scenario, users need to set up the facial recognition from scratch to make it resistant to the attack.
“Due to an insecure implementation of the biometric face recognition in some Windows 10 versions, it is possible to bypass the Windows Hello face authentication via a simple spoofing attack using a modified printed photo of an authorized person.” states the security advisory published on Full Disclosure.
The attack devised by the researchers works on both the default config, and Windows Hello with its “enhanced anti-spoofing” feature enabled.
“Thus, by having access to a suitable photo of an authorized person (frontal face photo), Windows Hello face authentication can easily be bypassed with little effort, enabling unauthorized access to the Windows system.” reads the
“Both, the default Windows Hello configuration and Windows Hello with the enabled “enhanced anti-spoofing” feature on different Windows 10 versions are vulnerable to the described spoofing attack and can be bypassed. If “enhanced anti-spoofing” is enabled, depending on the targeted Windows 10 version, a slightly different modified photo with other attributes has to be used, but the additional effort for an attacker is negligible. In general, the simple spoofing attack is less reliable when the “enhanced anti-spoofing” feature is enabled.”

The Proof of Concept (PoC) detailed by the researchers worked against a Dell Latitude running Windows 10 Pro, build 1703; and a Microsoft Surface Pro running 4 build 1607.
The experts tried to use the “enhanced anti-spoofing” feature on Surface Pro’s , but claimed its “LilBit USB IR camera only supported the default configuration and could not be used with the more secure face recognition settings.”
They successfully bypassed the default Windows Hello configuration on both test devices running all tested Windows 10 versions.
Loapi Android malware can destroy your battery mining Monero
20.12.2017 securityaffairs Android
Experts from Kaspersky have spotted an Android malware dubbed Loapi that includes a so aggressive mining component that it can destroy your battery.
Researchers from security firm Kaspersky Lab have spotted a new strain of Android malware dubbed Loapi lurking in fake anti-virus and porn applications, that implements many features, including cryptocurrency mining.
Loapi can be used to perform a wide range of malicious activities, thanks to a modular architecture it can be used to take part in a DDoS botnet or bombard infected handsets with advertisements.
The strain of malware analyzed by Kaspersky when running a few days to mine the Monero cryptocurrency physically damaged the device due to the load caused by the activity.
“Because of the constant load caused by the mining module and generated traffic, the battery bulged and deformed the phone cover.” reads the analysis published by Kaspersky.

According to the researchers, the Loapi malware is able to destroy an Android device in just 2 days.

The Loapi malware communicates with the following command and control servers:
ronesio.xyz (advertisement module) – A module used for the aggressive display of advertisements on the infected handset.
api-profit.com:5210 (SMS module and mining module) – A module used for the manipulations of text messages. It periodically sends requests to the C&C server to obtain relevant settings and commands.
mnfioew.info (web crawler); A module used for hidden Javascript code execution on web pages with WAP billing in order to subscribe the user to various services
mp-app.info (proxy module) – A module that implements an HTTP proxy server that allows the attackers to send HTTP requests from the device. It is the component used to power DDoS attacks.
Experts believe the gang behind the Loapi malware is the same responsible for the 2015 Android malware Podec.
The Loapi malware was distributed through third-party app stores and advertising campaigns.
“Malicious files are downloaded after the user is redirected to the attackers’ malicious web resource. We found more than 20 such resources, whose domains refer to popular antivirus solutions and even a famous porn site. As we can see from the image below, Loapi mainly hides behind the mask of antivirus solutions or adult content apps” continues the analysis.

Once installed, the Loapi malware tries to obtain ‘device administrator’ permissions by looping a pop-up until a victim clicks yes.
The sample analyzed by Kaspersky checks if the device is rooted, but never subsequently uses root privileges, experts believe cybercriminals will use them in some new module in the future for example to implements spyware features.
Researchers pointed out that the Android malware “aggressively fights any attempts to revoke device manager permissions” by locking the screen and closing phone windows by itself.