Common Infiltration, Exfiltration Methods Still Successful: Report
5.12.2017 securityweek Virus
Many organizations are still having difficulties protecting their systems against the most common infiltration, exfiltration and lateral movement methods used by attackers, according to the latest Hacker’s Playbook report from SafeBreach.
The company provides a platform designed to test an organization’s defenses by continuously simulating attacks and breaches. For the third edition of its Hacker’s Playbook report, SafeBreach has analyzed data from roughly 11.5 million automated simulations conducted between January and November 2017. The simulations covered more than 3,400 attack methods – from exploit kits and malware to brute force and credential harvesting – that allowed the company to see where attackers are blocked and where they are successful.
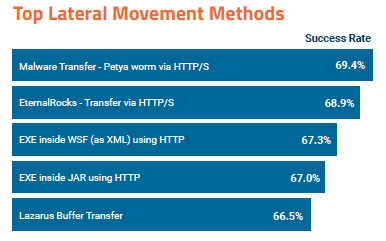
An analysis of the top 5 infiltration methods used by malware showed that more than 55 percent of attack attempts are successful. The methods used by notorious malware families such as the WannaCry ransomware, which leverages SMB, and the Carbanak (Anunak) banking Trojan, which relies on HTTP, had a success rate of 63.4% and 59.8%, respectively, in SafeBreach’s simulations.
Other popular infiltration methods involve malicious executables packed in CHM, VBS and JavaScript files. These help attackers trick both end users and high-level scanners, and they had success rates between 50% and 61%.
Once they gain access to a targeted organization’s network, attackers use various methods for lateral movement. The most common methods, all of which involve a piece of malware or exploit, were successful in 65%-70% of the simulations run by SafeBreach.
The relatively high success rates show that organizations often fail to implement proper segmentation controls. Once the perimeter has been breached, there is no malware scanning in place within the network, allowing attackers to easily move from one machine to another.
As for exfiltrating data, success rates range between 40% and 57% for methods involving MySQL queries, TLS, SSL, HTTP POST and HTTP GET. The most commonly targeted ports are 123 (NTP), 443 (HTTPS), and 80 (HTTP).

“Attackers will always try the easiest routes first - and sadly, it appears they will often find success,” SafeBreach said in its report. “Techniques like DNS tunneling, or trickling data out within packet headers to slowly steal data without raising suspicion are clever, but attackers don’t get bonus points for creativity. When simply sending data outbound via clear or encrypted web traffic will work - attackers will happily take the easy way out.”
“We also took a deeper look into this traffic, and validated that indeed traditional web traffic, over traditional web ports, is the leading risk of data exfiltration. However, some sneakier tactics were also highlighted, as we were often able to sneak data out over NTP - which is often open and unscanned,” the company added.
WannaCry, Locky and Cryptolocker have made many organizations realize that ransomware should be taken seriously. However, SafeBreach found that these types of attacks are often successful even if the deployed security solutions are working as designed.
The security firm pointed out that most of its customers have managed to significantly reduce attack success rates simply by optimizing existing security controls.
“Security teams already have the tools/controls they need for security. Oftentimes, teams chase after every new security fad, when they should be optimizing their current technology,” SafeBreach told SecurityWeek.
SEC Files Charges in Digital Currency Investment Scam
5.12.2017 securityweek Spam
The US Securities and Exchange Commission said Monday its newly-created Cyber Unit shut down a digital currency investment scam, charging a company that took millions from investors, "falsely promising" a speedy, 13-fold profit.
The SEC's Cyber Unit filed charges against and froze the assets of Dominic Lacroix, a Canadian with a history of securities law violations, and his company PlexCorps in an initial coin offering fraud.
Using Facebook, the company sold securities called PlexCoin -- that its website billed as "the next cryptocurrency" -- to investors in the US and elsewhere, raising $15 million since August, and promising a return of 1,354 percent within 29 days, the SEC said in a statement.
These were the first charges filed by the unit the SEC created in September to focus on fraudulent initial coin offerings of digital currency and other crimes.
"This first Cyber Unit case hits all of the characteristics of a full-fledged cyber scam and is exactly the kind of misconduct the unit will be pursuing," the unit's chief Robert Cohen said in a statement. "We acted quickly to protect retail investors from this initial coin offering's false promises."
The SEC won an emergency court order to freeze the assets of PlexCorps, Lacroix, 35, and his partner Sabrina Paradis-Royer, 26, accusing them of trading in unregistered securities.
PlexCorps promotional materials claimed the company's executives could not be identified for security and privacy reasons when in reality this was because Lacroix had already been pursued by Canadian authorities for securities law violations, the agency said.
The SEC's move comes amid mounting interest in digital currencies, with the most well-established, bitcoin, seeing its value soar this year to dizzying heights, attracting both investor interest and skepticism.
The US Commodities Futures Trading Commission, which regulates trade in derivatives, last week cleared the way for mainstream exchanges, including the CME Group and Cboe Futures Exchange, to offer contracts for futures of the virtual currency.
Cboe was the first out of the gate Monday, announcing it would launch bitcoin futures trading beginning Sunday. CME plans to allow trading in bitcoin futures later this month.
Leaked Credentials Service Shuts Down
5.12.2017 securityweek Hacking
LeakBase, an online service that provided paid access to leaked credentials, was shut down over the weekend.
The service started selling membership access in September last year, claiming to provide access to two billion credentials that leaked in major hacking incidents. The service received a boost in January 2017, when paid breach notification service LeakedSource went dark.
LeakBase claimed to be providing users with information on leaked credentials to help them better understand the risks hacked information poses and to allow them to remedy the situation.
The leaked credentials, however, were leveraged for financial gain, as LeakBase visitors (the same as LeakedSource) had to pay for using the service. Subscribers were provided access to the entire database of leaked credentials and passwords.
A message posted on LeakBase’s Twitter account on Saturday is informing users that the service has been discontinued. In a subsequent tweet, the service’s operators said they were willing to refund users who had paid for access but couldn’t take advantage of the service anymore.
2 Dec
LeakBase
@LeakbasePW
This project has been discontinued, thank you for your support over the past year and a half.
LeakBase
@LeakbasePW
We understand many of you may have lost some time, so in an effort to offer compensation please email, refund@leakbase.pw
Send your LeakBase username and how much time you had left.
We will have a high influx of emails so be patient, this could take a while
3:38 AM - Dec 3, 2017
2 2 Replies 1 1 Retweet 2 2 likes
Twitter Ads info and privacy
Over the weekend, the service started redirecting users to haveibeenpwned.com, a breach alerting service created and maintained by security researcher Troy Hunt. HIBP allows users to check whether their email address appeared in a breach but doesn’t store the hacked passwords.
While the exact reasons behind the service’s shutdown haven’t been revealed as of now, security blogger Brian Krebs suggests that one of the owners of LeakBase was identified and apprehended due to their connection with the dark web marketplace Hansa.
The information that led to the arrest was supposedly provided by the Dutch police, which had secretly seized Hansa in July and operated it for a while to gather data on its users.
A tweet posted on LeakBase’s account several moments ago suggests that none of the LeakBase operators have any connections to Hansa.
4 Dec
LeakBase
@LeakbasePW
The fact that we need to tweet this is disappointing in its self, non of the LeakBase operators have any connections to Hansa.
The fact that this can be portrayed as near fact is astonishing as it is only a claim.
LeakBase
@LeakbasePW
If claims as simple as that hold such weight, than our claim, as stated above should hold equal if not much more power.
4:11 PM - Dec 4, 2017
Replies 2 2 Retweets 1 1 like
Twitter Ads info and privacy
Regardless of whether a connection to Hansa exists, the owners of services such as LeakBase could face criminal charges in the event prosecutors could prove that they intended to sell passwords to facilitate further crimes.
UK Members of Parliament Share Passwords with Staff
5.12.2017 securityweek BigBrothers
UK member of parliament (MP) Nadine Dorries has declared on Twitter that she shares the password to her work computer with staff 'including interns'.
The immediate purpose of the statement was to lend political support to under-fire First Secretary of State Damian Green. Green was accused by a former Metropolitan Police assistant commissioner of accessing porn on his work computer following a 2008 police raid investigating Home Office leaks. Dorries' tweet includes the statement, "For the officer on @BBCNews just now to claim that the computer on Greens desk was accessed and therefore it was Green is utterly preposterous!!"
But in supporting her colleague, she might have stirred a bigger scandal than that concerning Green: MPs' attitude towards passwords. Several other MPs have agreed with and supported Dorries' position.
The Dorries' Green defense is common in both politics and international cyber relations: plausible deniability through the difficulty of attribution. If multiple people can be guilty of an act, you cannot easily prove which one is the guilty party. And if multiple people have access to the password, it's hard to prove who did what with the computer.
In security, however, the fourth criterion after confidentiality, integrity and availability (CIA) is often defined as accountability. It is clear that any MP that shares his or her password is automatically failing to maintain, or specifically obfuscating, accountability. In reality, they are also guilty of ignoring official policy. The House of Commons Staff Handbook (section 5.8) says, "You MUST NOT... share your password."
The UK's National Cyber Security Center (NCSC) Password Guidance, updated in August 2016, also states, "You should never allow password sharing between users. Sharing accounts, or even occasional use by anyone other than the account holder, negates the benefit of authenticating a specific user. In particular, the ability to audit and monitor a specific user's actions is lost."
However, the sharing of MPs' passwords may go beyond simply ignoring advice and/or policy. Although sharing passwords is not in itself a breach of the UK's Data Protection Act, it could lead to a breach. The UK's data protection regulator, the ICO, itself tweeted, "We're aware of reports that MPs share logins and passwords and are making enquiries of the relevant parliamentary authorities. We would remind MPs and others of their obligations under the Data Protection Act to keep personal data secure."
It is questionable whether giving interns access to the potentially sensitive personal information of constituents is within the spirit if not letter of the current law. It is also concerning that Britain's lawmakers should have such a lax attitude towards security at a time when its intelligence agencies are increasingly warning about Russia targeting the UK government.
Security researcher Troy Hunt suggests, without condoning, that this is an example of users bypassing policy in order to work more efficiently. "Her approach to password sharing may simply be evidence of humans working around technology constraints." This is common in all organizations -- and is generally countered by security awareness training supported by technological controls.
The need to share data among several different people is not uncommon -- and there are numerous technology solutions that could be employed. These include delegated access, shared access to collaboration tools (where the MP's staff would have password-controlled access to the documents rather than to the MP's computer), or even Microsoft's SharePoint.
The most worrying aspect to MPs and their password sharing is their common belief that there is nothing wrong in this. This in turn suggests that MPs do not receive adequate security awareness training and/or that parliament's IT department isn't offering sufficient options to make this unnecessary -- or controls to make it impossible. In most private enterprises,sharing passwords would be considered a disciplinary offense.
Critical Flaw in WAGO PLC Exposes Organizations to Attacks
5.12.2017 securityweek ICS
Programmable logic controllers (PLCs) from Germany-based industrial automation company WAGO are affected by a potentially serious vulnerability that could give a remote attacker access to an organization’s entire network.
The flaw, discovered by a researcher at security services and consulting company SEC Consult, impacts Linux-based WAGO PFC200 series PLCs, specifically a total of 17 750-820X models running firmware version 02.07.07 (10). The affected devices are advertised by the vendor as ultra-compact and secure automation systems that can be used for traditional machine control, process technology, and in the offshore sector.
The security hole exists due to the use of version 2.4.7.0 of the CODESYS Runtime Toolkit. This embedded software is developed by 3S-Smart Software Solutions and it’s used by several vendors in hundreds of PLCs and other industrial controllers.
A few years ago, researcher Reid Wightman discovered that versions 2.3.x and 2.4.x of CODESYS Runtime were affected by critical access control and directory traversal vulnerabilities that could have been exploited to hack devices.
Building on Wightman’s research, SEC Consult discovered that various functions of a service named “plclinux_rt” can be accessed without authentication by sending specially crafted TCP packets on port 2455, which is the programming port.
An attacker can use this method to write, read or delete arbitrary files, which can be done with a tool created by Digital Bonds several years ago for interacting with PLCs that use CODESYS. Since SSH is enabled by default on PFC200 PLCs, an unauthenticated hacker can exploit this to rewrite the etc/shadow file, which stores password hashes, and gain root privileges to the device.
SEC Consult said the vulnerability can also be exploited to modify the PLC program during runtime and cause the device to step over a function, restart or crash.
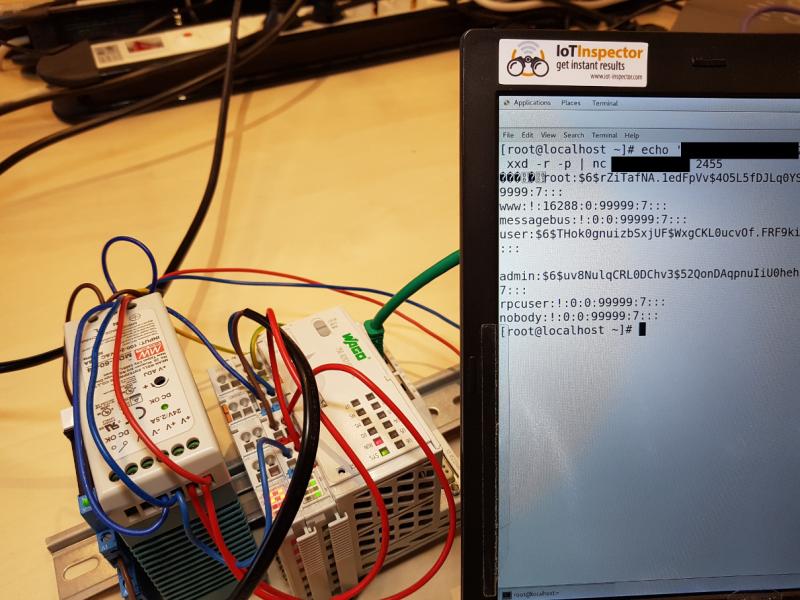
The security firm told SecurityWeek that while it hasn’t scanned the Internet for devices that can be exploited on port 2455, it has found nearly 2,500 WAGO PFC200 devices on the Web via the Censys search engine. These devices are often found in critical infrastructure organizations, including power plants, the company said.
“Because of the use in industrial and safety-critical environments the patch has to be applied as soon as it is available,” SEC Consult warned in a blog post. “We explicitly point out to all users in this sector that this device series in the mentioned device series with firmware 02.07.07(10) should not be connected directly to the internet (or even act as gateway) since it is very likely that an attacker can compromise the whole network via such an device.”
WAGO was informed about the vulnerability in August, but it has yet to release a patch. The vendor estimates that a fix will be made available in January 2018.
SEC Consult has published an advisory describing the flaw, but it will not release a proof-of-concept (PoC) exploit until a patch is available. In the meantime, the security firm has advised users to either delete the “plclinux_rt” service or close the 2455 port in order to prevent potential attacks.
The company believes the vulnerability could affect devices from other vendors that use CODESYS Runtime 2.3.x or 2.4.x. These are older versions of the tool – versions 3.x are not impacted.
This is not the first time a significant number of ICS devices have been exposed to attacks due to the use of a CODESYS component. Earlier this year, CyberX warned that hundreds of thousands of Industrial Internet of Things (IIoT) and ICS devices had been vulnerable due to a critical flaw in the web server component of the CODESYS WebVisu visualization software.
Člověk z NSA se přiznal, že vynesl tajná data. Kaspersky je prý smazal
4.12.2017 Idnes.cz BigBrother
Americké ministerstvo spravedlnosti obvinilo bývalého zaměstnance NSA z vynášení tajných materiálů. Ze soukromého počítače se pak tyto materiály údajně dostaly k ruským hackerům
NSA The National Security Agency - Národní bezpečnostní agentura, vznikla v listopadu 1952 | foto: thedailysheeple.com
Ministerstvo zahraničí USA obvinilo Nghia Pho, bývalého zaměstnance NSA, z nelegálního „vědomého přechovávání informací související s národní bezpečností“. Konkrétně mělo jít o materiály v digitální i tištěné podobě, který Pho během let 2006 a 2016 vynesl ze své kanceláře NSA v Marylandu do svého domova v Ellicott City (podrobnosti o žalobě v PDF na Justice.gov).
Tím, že Pho data vynesl z NSA na svůj soukromý počítač, porušil nejen vnitřní bezpečnosti předpisy NSA, ale také zákon o informacích souvisejících s bezpečností USA, konkrétně paragraf o sběru, přenosu a ztrátě bezpečnostních informací (viz 18 U.S. Code paragraf 793)
![]()
Kanceláře NSA v Marylandu (červená značka) a Ellicot City (modrá značka)
Pho podle obžaloby vynesl i data klasifikována jako TOP SECRET, SECRET a CONFIDENTIAL, což jsou označení vyhrazená pro dokumenty, jejichž únik by mohl znamenat „závažné ohrožení národní bezpečnosti“.
Sedmašedesátiletý Nghia Hoang Pho se k činu přiznal (PDF) a přijal tak nabídku žalobce výměnou za mírnější trest. Podmínky dohody (“plea deal“) nejsou zveřejněny.
Role společnosti Kaspersky není jasná
O případu jsme na Technet.cz informovali v říjnu, kdy se objevily informace o tom, že vynesená data získali ruští hackeři. Spekulovalo se totiž o tom, že ruští hackeři se k utajovaným dokumentům - jmenovitě těm o pronikání do cizích počítačových sítí - dostali skrze antivirový systém Kaspersky, který měl prý Pho nainstalovaný na svém domácím počítači.
Američtí vyšetřovatelé tehdy podle informací The Wall Street Journal spekulovali o tom, že ruští hackeři se o umístění tajných materiálů na soukromém počítači dozvěděli právě díky antiviru ruské firmy Kaspersky Lab.
Ruská antivirová firma od začátku takové nařčení odmítá. Dále společnost Kaspersky Lab uvedla, že je ochotna setkat se s vládními představiteli USA nebo poskytnout své zdrojové kódy k oficiálnímu auditu.
Firma Kaspersky Lab se dostala do nemilosti federálních úřadů USA, které ji označily za nedůvěryhodnou a software Kaspersky od září 2017 nesmí být instalován na vládní počítače USA. Existuje totiž podezření, že Kaspersky spolupracoval či spolupracuje s ruskou rozvědkou FSB. Také toto obvinění zakladatel firmy, Eugen Kaspersky, rezolutně odmítl: „Společnost Kaspersky Lab nemá žádné vazby na vlády, nikdy nepomáhala a ani nebude pomáhat žádným vládám jakéhokoliv státu v kyberšpionážních aktivitách.“
Eugene Kaspersky (Twitter)
@e_kaspersky
05.října 2017 v 20:05, příspěvek archivován: 03.prosince 2017 v 23:03
OK, here is our official statement re the recent article in WSJ. https://t.co/rdH6YcsZBZ
323 lidí to sdílíodpovědětretweetoblíbit
Podle interního vyšetřování má incident nevinné vysvětlení
Kaspersky Lab zveřejnily předběžné výsledky svého interního vyšetřování. Podle nich došlo k běžné detekci škodlivého software na soukromém počítači: „Náš produkt detekoval známý malware Equation na uživatelově počítači. Později na stejném počítači našel i stopy po pirátské verzi Microsoft Office a komprimovaný soubor 7zip obsahující do té doby neznámý malware.“
Kaspersky Internet Security
V souladu s nastavením poté antivir poslal vzorek tohoto neznámého malware do laboratoří na testování. „Ukázalo se, že komprimovaný soubor obsahoval několik malware spojených se skupinou Equation, a také několik wordovských dokumentů označených jako tajné.“
Kaspersky Lab tak vysvětlují, že necílily úmyslně na konkrétní počítač: „Komprimovaný soubor byl detekován automaticky naší proaktivní technologií.“ Navíc byl údajně archiv, automaticky zaslaný do Kaspersky Lab, vzápětí smazán, a to na příkaz šéfa Kaspersky Lab.
Kromě toho Kaspersky tvrdí, že daný počítač byl možná „napaden více hackery“, neboť na něm antivir našel stopy po velkém množství malware. Výsledky svého interního šetření je firma Kaspersky údajně hotova poskytnout k prověření třetí straně.
Ruský antivirus Kaspersky podezírají v Británii ze špionáže
4.12.2017 Idnes.cz BigBrother
Putinovo Rusko je bezpečnostní hrozba. Britské Národní středisko kybernetické bezpečnosti (NCSC) varovalo vládní úřady před používáním antivirového softwaru od ruské společnosti Kaspersky Lab kvůli obavám ze špionáže.
Eugene Kaspersky osobně zahajuje Security Analyst Summit 2017. | foto: Jan Kužník, Technet.cz
Šéf NCSC Ciaran Martin v dopise stálým sekretářům uvedl, že ruský antivirový software by se neměl používat v systémech obsahujících informace, které by mohly poškodit národní bezpečnost, pokud by k nim získala přístup ruská vláda.
Dodal, že NCSC jedná se společností Kaspersky Lab o vytvoření mechanismu, který by produkty firmy umožnil v Británii kontrolovat. Firma Kaspersky k situaci také vydala prohlášení, ve kterém se mimo jiné uvádí, že se na spolupráci s NCSC těší. Šéf společnosti na Twitteru navíc upřesnil, že výrobky firmy nebyly v žádném případě na britském trhu zakázány.
Eugene Kaspersky (Twitter)
@e_kaspersky
02.prosince 2017 v 14:10, příspěvek archivován: 04.prosince 2017 v 13:44
Let me stress: there is *no* ban for KL products in the UK. We are in touch with @NCSC regarding our Transparency Initiative and I am sure we will find the way to work together
92 lidí to sdílíodpovědětretweetoblíbit
Jak jsme na Technet.cz informovali, administrativa amerického prezidenta Donalda Trumpa již dříve nařídila vládním úřadům v USA odstranit z počítačů produkty společnosti Kaspersky Lab. Zdůvodnila to obavami z úzkých vztahů firmy s ruskými zpravodajskými službami a z možného využívání softwaru k ruské špionáži.
Člověk z NSA se přiznal, že vynesl tajná data. Kaspersky je prý smazal
Americké ministerstvo spravedlnosti obvinilo bývalého zaměstnance NSA z vynášení tajných materiálů. Ze soukromého počítače se pak tyto materiály údajně dostaly k ruským hackerům.
NSA měla v plánu infikovat aplikace v Google Play a skrze ně pak sledovat...
Podezření zesílilo již letos v květnu, kdy se podle agentury Bloomberg objevily e-maily z roku 2009, které spolupráci antivirové firmy s ruskou tajnou službou naznačují. Zakladatel firmy Eugene Kaspersky to samozřejmě kategoricky popřel. Jeho tvrzení a další podrobnosti naleznete v našem článku. Kaspersky Lab tvrdí, že se stala obětním beránkem rostoucího napětí mezi Washingtonem a Moskvou.
Ruská antivirová firma Kaspersky Lab patří celosvětově mezi deset firem s největším podílem na trhu antivirových aplikací. Jejich antivirus patří k nejlépe hodnoceným na trhu. V bezpečnostní komunitě se ovšem neoficiálně mluví i o tom, že Kaspersky „zřejmě nějakým způsobem spolupracuje s ruskými autoritami“.
Podobné problémy řeší už delší dobu také čínská společnost Huawei, která dodává síťovou infrastrukturu operátorům po celém světě. V roce 2014 před firmou varovala i česká BIS. Přitom už v roce 2012 americké úřady obvinily Huawei ze špionáže.
Britské úřady byly varovány před antivirovým programem Kaspersky
4.12.2017 Novinky/Bezpečnost BigBrother
Britské Národní středisko kybernetické bezpečnosti (NCSC) varovalo vládní úřady před používáním antivirového softwaru od ruské společnosti Kaspersky Lab. Spojené státy již dříve používání tohoto softwaru vládním úřadům zakázaly kvůli obavám z ruské špionáže.
Šéf NCSC Ciaran Martin uvedl, že ruský antivirový software by se neměl používat v systémech obsahujících informace, které by mohly poškodit národní bezpečnost, pokud by k nim získala přístup ruská vláda. Dodal, že NCSC jedná se společností Kaspersky Lab o vytvoření mechanismu, který by produkty firmy umožnil v Británii kontrolovat.
Administrativa amerického prezidenta Donalda Trumpa v září nařídila vládním úřadům v USA odstranit z počítačů produkty společnosti Kaspersky Lab. Zdůvodnila to obavami z úzkých vztahů firmy s ruskými zpravodajskými službami a z možného využívání softwaru k ruské špionáži.
Společnost Kaspersky Lab ale popírá, že by Rusku se špionáží pomáhala. Tvrdí, že se stala obětním beránkem rostoucího napětí mezi Washingtonem a Moskvou.
ICS-CERT Advice on AV Updates Solid, But Impractical
4.12.2017 securityweek ICS
The U.S. Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) has offered some advice on how antivirus software should be updated in industrial environments, but the recommended method is not very practical and experts warn that organizations should not rely only on antiviruses to protect critical systems.
ICS-CERT recommendations on updating AVs in industrial networks
ICS-CERT, a component of the Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC), coordinates security incidents involving control systems and facilitates information sharing in an effort to reduce the risk of cyberattacks. The organization’s latest Monitor newsletter provides some advice on how organizations should update their antiviruses in ICS environments.
“Antivirus software, when properly deployed and up-to-date, is an important part of a defense-in-depth strategy to guard against malicious software (malware),” ICS-CERT said. “Such software is widely used in Information Technology (IT) and ICS infrastructures. In business IT environments, it is common practice to configure each antivirus client to update directly from the antivirus vendor; however, because ICS and IT systems require separation by the ICS demilitarized zone (DMZ), ICS systems require different antivirus update methods.”
The ICS DMZ is the level between the enterprise zone and the control network. The DMZ, in addition to historians and remote access servers, can include the antivirus, Windows Server Update Services (WSUS), and patch servers.
Since the ICS DMZ is typically not allowed to communicate directly to the Internet, updating these services cannot be done automatically from the vendor’s server. One method for updating antiviruses on these systems is to manually download the update, copy it to a removable media drive, and then connect that drive to the machine needing the update.
However, the process is not as straightforward as it sounds. ICS-CERT has advised organizations to first verify the source of the update, and then download the update file to a dedicated host. The file should be scanned for malware and its cryptographic hash needs to be verified in order to ensure it hasn’t been tampered with.
The removable media drive should also be scanned for malware and locked (i.e. prevent files from being written to it) once the update files have been copied. Before the updates are deployed on a production system, they should be tested and validated on a test environment that mimics production machines as closely as possible.
“This process is more labor intensive than an automatic chaining of updates, but it is not prohibitively time-consuming,” ICS-CERT said. “This ‘sneakernet’ method is common in air-gapped networks. Automatically ‘daisy chaining’ the updates, which is similar to the process used in many IT environments, is convenient but not recommended.”
Experts say the method is not very practical and AVs alone are not enough
SecurityWeek has reached out to several ICS security experts for comment on the recommendations from ICS-CERT.
Anton Shipulin, an ICS security expert with Kaspersky Lab, pointed out that while the sneakernet method does work for updating protection software in air-gapped networks, in practice, organizations are having difficulties keeping their systems updated. Kaspersky often finds outdated antimalware signature databases in the ICS networks analyzed during its assessments, Shipulin said.
“For the process to work, there should be good discipline in place to carry it out regularly, as well as a technically advanced endpoint solution - with capability to get updates from centralized on-premise update servers; it’s much simpler and faster to deliver updates only to a single point,” Shipulin explained. “It’s also worth mentioning that the same process should be a requirement for all OS, control systems and device software updates (with the agreement of ICS suppliers and vendors).”
Rick Kaun, VP of solutions at industrial cybersecurity firm Verve, noted that manually applying updates can be much more complicated than the process described by ICS-CERT.
“For example, not all AV updates are the same,” Kaun explained. “If you are under warranty support with a specific vendor for a specific AV function you not only need to download the AV file, you need to either get it from the vendor or at least confirm the vendor supports it. Further, many organizations may have multiple OEM vendors each with different AV solutions so you are needing to follow this practice for more than one set of files on different target systems – tracking and reporting of completion becomes a challenge.”
“Now let’s add into the mix the frequency at which AV files are generated. If they files are updated once a month this is likely manageable. If they are updated weekly this is more challenging. Now what happens when AV files get updated daily or even faster than that? What is your corporate stance on AV update frequency? This is an important consideration in deciding an appropriate balance between latest and greatest definition files (maximum protection) versus significant human effort (convenience/manpower),” Kaun added.
“There are very few organizations that are able to maintain the rigor and frequency of an AV program as outlined in the ICS article. It is well written and good advice but not overly practical in day to day application without significant dedication of manpower and/or automated tools,” Kaun said.
All the experts contacted by SecurityWeek agree that antiviruses should not be used – especially not on their own – to protect ICS. While industrial organizations are often concerned that security software could have a negative impact on their operations, modern solutions created specifically for ICS are designed to have minimal impact while still providing comprehensive protection. Furthermore, antiviruses cannot be installed directly on critical control devices, such as PLCs and DCSs. Modern products, however, passively monitor networks for any suspicious activity, regardless of the type of device targeted.
Patrick McBride, CMO at Claroty, pointed out that security products designed for IT environments should never be used in operational technology (OT) networks.
“AV has been proven ineffective and since it is not designed to work in OT environments, you need a Rube Goldberg process just to make ineffective stuff work poorly,” McBride said. “Unfortunately, some companies rely on outdated, ineffective AV solutions because various regulations require them.”
Dana Tamir, vice president of market strategy for Indegy, pointed out another interesting aspect. While antiviruses can provide partial protection, especially against known threats, the use of traditional antiviruses may not even be possible in some organizations due to the fact that many still rely on legacy systems such as Windows NT and XP in their ICS networks, and these legacy systems may not be supported by antivirus vendors, Tamir said.
This is confirmed by a recent CyberX study, which found that three out of four industrial sites are still running outdated operating systems in their ICS networks.
“[ICS-CERT’s advice] ignores the reality that many ICS environments aren't installing any Windows security patches or running any AV protection whatsoever because of unsupported OSs like Windows 2000 and XP,” Phil Neray, VP of Industrial Cybersecurity at CyberX, told SecurityWeek.
Tamir also noted that an organization can install antiviruses on all managed computers, but if it doesn’t use a more comprehensive solution to monitor unmanaged endpoints, threats can make it into the organization’s ICS network via the devices brought in by integrators and consultants.
Google to Warn Android Users on Apps Collecting Data
4.12.2017 securityweek Android
Google is stepping its fight against unwanted and harmful applications on Android up and will soon alert users on apps and websites leading to apps that collect personal data without their consent.
Produced by Google Safe Browsing, the alerts will start popping up on Android devices in a couple of months, as part of expanded enforcement of Google’s Unwanted Software Policy, the Internet giant announced.
The expanded enforcement also covers applications handling personal user data, such as phone numbers or email, or device data, all of which will be required to inform users on their activities and “to provide their own privacy policy in the app.”
What’s more, Google is now requesting applications that collect and transmit personal data unrelated to the functionality of the app to “prominently highlight how the user data will be used and have the user provide affirmative consent for such use,” prior to performing the collection and transmission operations.
“These data collection requirements apply to all functions of the app. For example, during analytics and crash reporting, the list of installed packages unrelated to the app may not be transmitted from the device without prominent disclosure and affirmative consent,” Paul Stanton, Safe Browsing Team, explains in a blog post.
The Internet search provider is enforcing the new requirements to applications in both Google Play and non-Google Play app markets. The company also published guidelines for how Google Play apps should handle user data and provide disclosure.
The warnings might start appearing in late January 2018 on user devices via Google Play Protect or on webpages that lead to these apps.
Webmasters should refer to the Search Console for guidance on remediation and resolution of the warnings, while developers should refer to guidance in the Unwanted Software Help Center. Also, application builders can request app reviews.
Authorities Take Down Andromeda Botnet
4.12.2017 securityweek BotNet
The Federal Bureau of Investigation (FBI) and law enforcement agencies in Europe managed to dismantle the Andromeda botnet last week.
Also known as Gamarue, Andromeda malware has been around since 2011 and used to ensnare the infected computers into a botnet. The main purpose of this network of infected machines was to distribute other malware families, including the Dridex banking Trojan or point-of-sale (PoS) malware GamaPoS.
In a FortiGuard Labs report detailing the top 5 methods used to attack healthcare in Q4, 2016, Andromeda emerged as the top botnet.
Packing a loader that features virtual machine and debug evasion techniques, Andromeda downloads modules and updates from its command and control (C&C) server. Overall associated with 80 malware families, the threat was detected on or blocked on an average of over 1 million computers every month for the past six months.
The takedown, a joint effort from the FBI, the Luneburg Central Criminal Investigation Inspectorate in Germany, Europol’s European Cybercrime Centre (EC3), the Joint Cybercrime Action Task Force (J-CAT), Eurojust, and private-sector partners, was performed on November 29.
The operation was the result of information gathered following last year’s shut down of a large criminal network known as Avalanche, a platform used for mass global malware attacks and money mule recruiting. Andromeda was also used in the Avalanche network.
“Insights gained during the Avalanche case by the investigating German law enforcement entities were shared, via Europol, with the FBI and supported this year’s investigations to dismantle the Andromeda malware last week,” a Europol announcement reads.
Investigators focused on taking down servers and domains used to spread the Andromeda malware and resulted in the sinkholing of 1500 domains. 48 hours of sinkholing resulted in around 2 million unique Andromeda victim IP addresses from 223 countries being captured.
The takedown operation also included the search and arrest of a suspect in Belarus.
The investigators also decided to extend the sinkhole measures of the Avalanche case for another year, as globally 55% of the computers originally infected in Avalanche continue to be infected.
The measures to combat Andromeda and Avalanche involved the following countries: Austria, Belgium, Finland, France, Italy, the Netherlands, Poland, Spain, the United Kingdom, Australia, Belarus, Canada, Montenegro, Singapore, and Taiwan.
Private and institutional partners involved in the takedown include: Shadowserver Foundation, Microsoft, Registrar of Last Resort, Internet Corporation for Assigned Names and Numbers (ICANN) and associated domain registries, Fraunhofer Institute for Communication, Information Processing and Ergonomics (FKIE), and the German Federal Office for Information Security (BSI).
“This is another example of international law enforcement working together with industry partners to tackle the most significant cyber criminals and the dedicated infrastructure they use to distribute malware on a global scale. The clear message is that public-private partnerships can impact these criminals and make the internet safer for all of us,” Steven Wilson, the Head of Europol’s European Cybercrime Centre, said.
Kyberbezpečnost je nutné brát jako strategickou záležitost, nikoli jako investici do IT
4.12.2017 SecurityWorld Bezpečnost
Podniky se vydávají na cestu digitální transformace, která by jim měla pomoci nalézat nové obchodní příležitosti, zefektivňovat provoz a lépe uspokojovat potřeby jejich zákazníků. Digitální transformace vede podniky k zavádění cloudu, internetu věcí, velkých dat a dalších a dalších digitálních technologií a nutí je měnit zavedené postupy a automatizovat vše, od rozhodování po zákaznickou podporu.
Nové příležitosti s sebou ale nesou i nové hrozby pro kybernetickou bezpečnost. A hrozby jsou to reálné. Podle předpovědi analytické společnosti Gartner se očekává, že téměř 60 % digitálních podniků utrpí závažný výpadek kvůli neschopnosti svého bezpečnostního týmu zvládat digitální rizika. Problém částečně pramení z toho, že vyšší management a představenstvo podniků nepovažují bezpečnost z obchodního hlediska za naléhavý problém.
Na problém upozornil mimo jiné globální průzkum společnosti Fortinet (článek o průzkumu zde) zaměřený na kybernetickou bezpečnost v podnicích, jehož se zúčastnilo přes 1800 pracovníků IT s rozhodovací pravomocí. Zjistili jsme, že podle téměř poloviny respondentů není pro představenstvo podniku bezpečnost mezi hlavními prioritami.
Bylo by možné očekávat, že v důsledku kybernetických útoků z poslední doby – a jejich závažných dopadů na postižené podniky – mezi nejvyššími manažery výrazně vzroste zájem o problematiku bezpečnosti. Ti sice na bezpečnostní incidenty reagují, avšak zabývají se spíše řešením následků než prevencí.
Proti hrozbě průniku do systémů, vyděračského softwaru nebo narušení provozu není imunní nikdo. Cílem se stávají podniky všech oborů, typů a velikostí. Průzkum společnosti Fortinet to potvrzuje. 85 % dotázaných podniků se v uplynulých dvou letech stalo obětí narušení bezpečnosti, přičemž téměř polovina zaznamenala napadení škodlivým nebo vyděračským softwarem.
Proč se kybernetická bezpečnost stává prioritou vedení firem
Nejvyšší vedení podniků a manažery IT povede k zaměření na kybernetickou bezpečnost v roce 2018 řada faktorů. Uveďme si několik nejdůležitějších.
1. Narušení bezpečnosti a globální útoky. Naprostá většina podniků v uplynulých dvou letech zaznamenala nějaký druh narušení bezpečnosti nebo útoku. Po globálním útoku, jako byl např. WannaCry, začaly podniky věnovat bezpečnosti zvýšenou pozornost. Větší publicita a pozornost spolu s potenciálními dopady na pověst a provoz firmy posouvají kyberbezpečnost z problému, který by mělo řešit podnikové IT, mezi záležitosti, jimiž se musí zabývat nejvyšší vedení.
2. Prostor pro potenciální útoky. Širší využití cloudu, zavádění internetu věcí a rozvoj velkých dat vytváří nové příležitosti k útoku a zároveň komplikují obranu. S narůstajícími požadavky na objemy dat a jejich zpracování stoupá pro podniky priorita cloudové bezpečnosti. Neméně důležitým faktorem, který rozšiřuje možnosti pro útok, je internet věcí (IoT). Podle odhadů analytické společnosti Gartner vzroste do konce roku počet připojených zařízení IoT na více než 8,4 miliardy. Z nich bude 3,1 miliardy sloužit podnikovým účelům. Takové množství zařízení IoT je těžké ochránit a odborníci se shodují v předpovědích, že podíl útoků namířených proti zařízením IoT do roku 2020 přesáhne 25 % všech počítačových útoků.
3. Zákonné a regulatorní povinnosti. Nové zákony a oborové předpisy rovněž zvyšují význam zabezpečení. 34 % respondentů uvedlo, že předpisy jsou jedním z faktorů, které přispívají k tomu, že vedení firmy věnuje bezpečnosti zvýšenou pozornost. Příkladem je přijetí obecného nařízení o ochraně osobních údajů (GDPR), které nabyde účinnosti ve všech členských státech EU v roce 2018.
Tyto trendy vedou k tomu, že je kybernetická bezpečnost považována za strategickou otázku v rámci širší strategie řízení podnikových rizik, nikoli za pouhou investici do IT. Mají-li manažeři IT bezpečnosti uspět při digitální transformaci, musí přehodnotit svůj přístup k bezpečnosti, zejména získat lepší přehled o celém prostředí a možných směrech útoku, zkrátit dobu mezi detekcí a neutralizací hrozeb, zajistit dostatečný výkon bezpečnostních řešení a automatizovat sběr bezpečnostních informací a řízení.
Šest nejobávanějších virů počítačového a mobilního světa
4.12.2017 Novinky/Bezpečnost Virus
Každý den kolují internetem tisíce virů, které cílí na klasické počítače, tablety i chytré telefony. Antivirová společnost Check Point zveřejnila žebříček šesti škodlivých kódů, které cílí právě na zmiňovaná zařízení. Právě na ně – a na způsob, jakým je kyberzločinci šíří – by si měli dát uživatelé velký pozor.
Žebříček je rozdělen na dvě části. V jedné je přehled třech nejrozšířenějších virů, které útočí na klasické počítače, v druhé pak trojice malwarů cílících na mobilní zařízení, jako jsou tablety a chytré telefony.
Nejprve se pojďme podívat, jaké škodlivé kódy útočí na klasická PC. První příčku obsadil RoughTed. Rozsáhlá malvertisingová kampaň RoughTed je využívána k šíření odkazů na nebezpečné webové stránky a k šíření škodlivého obsahu, jako jsou scam, adware, exploit kity a ransomware. Může být použita k útoku na jakýkoli typ platformy a operačního systému, vyhne se nástrojům na blokování reklamy a sleduje chování uživatelů, aby byl finální útok co nejrelevantnější.
Vyděračské viry na scéně
Druhá příčka pak patří vyděračskému viru Locky. Tento ransomware, který byl poprvé detekován v únoru 2016, se šíří především prostřednictvím spamu s infikovanou wordovou přílohou nebo přílohou ve formátu Zip, která obsahuje kód pro stažení a instalaci malwaru šifrujícího uživatelské soubory.
Nezvaný návštěvník Locky dokáže uzamknout počítač a za zpřístupnění zašifrovaných dat požaduje výkupné.
Trojici nejrozšířenějších virů pak uzavírá Seamless. Jde o systém distribuce provozu (TDS), který nenápadně přesměruje oběti na škodlivou webovou stránku, což vede k infekci pomocí tzv. exploit kitu. To jinými slovy znamená, že poté, co se tento záškodník uhnízdí v počítači, mohou do něj počítačoví piráti stahovat jakékoliv další škodlivé kódy.
V bezpečí nejsou ani mobily
Ani mobilní zařízení nejsou před škodlivými kódy v bezpečí. Nejvíce by se měli mít uživatelé na pozoru před virem Triada, který je nejrozšířenějším malwarem pro chytré telefony a počítačové tablety. Tento modulární backdoor cílí na zařízení s operačním systémem Android.
Škodlivý kód uděluje superuživatelské oprávnění útočníkům, takže kyberzločinci mohou stahovat do mobilních zařízení další malware. Triada také umí zfalšovat URL odkazy uložené v prohlížeči a nasměruje tak uživatele na podvodné stránky.
Druhá příčka patří vyděračskému viru LeakerLocker, který opět cílí na zařízení se systémem Android. Čte osobní uživatelská data a následně je ukazuje uživateli a hrozí, že pokud nedojde k zaplacení výkupného, tak budou informace zveřejněny na internetu.
Trojici nejrozšířenějších mobilních škodlivých kódů uzavírá Lotoor. Jde o hackerský nástroj, který zneužívá zranitelnosti v operačním systému Android, aby získal root oprávnění na napadeném zařízení. Díky tomu pak mohou útočníci zotročit zařízení na dálku.
Pro Windows 10 verze 1709 vyšla servisní aktualizace KB4051963. Co řeší?
4.12.2017 CNEWS.cz Zranitelnosti
Microsoft v posledních dnech vydával různě aktualizace pro Windows 10. Blíže se podíváme na tu pro nejnovější vydání Desítek.
Probíhá instalace nové verze Windows 10
Probíhá instalace nové verze Windows 10 (Ilustrační foto)
Jsou to skoro tři týdny od listopadového záplatovacího úterý. Někteří ale v posledních dnech mohli obdržet další aktualizace pro Windows nabízející nové opravy. Osobně jsem zaznamenal hlavně KB4051963, jež je určena pro Windows 10 v1709.
Kdo na nejnovější vydání Desítek přešel, může aktualizaci nainstalovat, takže se číslo sestavení zdvihne na 16299.98. Balík byl oficiálně vydán 30. listopadu, byť v Katalogu služby Microsoft Update najdete datum zveřejnění 29. listopadu. Přináší opravy následujících chyb:
Problém se skripty způsoboval selhání Internet Exploreru.
Okno pro zadání textu (od IME) mělo při použití s Internet Explorerem blíže nespecifikované problémy.
V Internet Exploreru mohly nastat problémy s vykreslováním grafických prvků.
V Internet Exploreru mohly nastat problémy s odesíláním formulářů.
Location hash byl ztracen, pakliže jste se vrátili zpět na neplatnou adresu URL.
Aplikace mohly vypovědět funkci, pokud jste použili proxy pomocí skriptu PAC. Mohlo v důsledku docházet k následujícím scénářům:
Outlook se nepřipojil k Office 365,
Internet Explorer a Edge nedokázaly správně vykreslit žádný obsah,
Cisco Jabber přestal odpovídat,
zasažena byla jakákoli aplikace či služba spoléhající na WinHTTP.
Aktualizace KB4051963 řeší mnoho nalezených chyb
Blíže nespecifikovaná chyba způsobovala degradaci výkonu her a jiných aplikací v celoobrazovkovém režimu, které používají DirectX 9. (Že by vyřešení další části potíží objevených koncem léta? Pozn. red.)
Forza Motorsport 7 a Forza Horizon 3 neběžely na některých high-endových laptopech.
Volba frekvence dotazování se na zpětnou vazbu nebyla pokaždé uložena.
Síťová zařízení RNDIS 5 nezískala platnou adresu IP, případně nevykazovala síťovou aktivitu. Pokud vaše problémy budou přetrvávat, budete muset přeinstalovat Vzdálený NDIS síťový adaptér.
Manuální změna časového pásma, aniž byste počítač restartovali či se odhlásili, se neprojevila na zobrazovaném čase na zamykací obrazovce.
Některé tiskárny Epson SIDM a TM netiskly na systémech architektur x86 a x64. Tento problém se týká aktualizace KB4048955 (tj. aktualizace z posledního záplatovacího úterý).
Na seznamu známých chyb přetrvává jen jediná položka, kterou už ale Microsoft řeší několik týdnů. Naštěstí se jedná o nepodstatnou věc, aspoň pro běžné uživatele a uživatelky: ve specifických situacích (tj. když pracujete s SQL Server Reporting Services) v rozbalovacích nabídkách na webech nemusí být možné se při prohlížení v Internet Exploreru posunout až dolů pomocí posuvníku.
Aktualizace pro další verze Desítek
Dne 22. listopadu pak Microsoft vydal aktualizaci KB4055254 pro Windows 10 v1703, jež sestavení systému povyšuje na 15063.729. Obsahuje pouze jeden lék, a sice na výše zmíněnou nemoc postihující tiskárny Epson.
Dále byla uvolněně aktualizace KB4051033 pro Windows 10 v1607, jež číslo sestavení zvedá na 14393.1914. Kromě výše uvedeného napravuje mnoho dalších chyb. Vydána byla pro změnu 27. listopadu. Aktualizace tedy vychází v různé dny. Nejvíce by vás měly zajímat první dvě uvedené, protože většina lidí používá právě tyto verze Desítek. Stále relativně čerstvý Fall Creators Update pohání 20,5 % zařízení s Windows 10.
Google Unwanted Software Policy – It’s a fight against snooping apps
4.12.2017 securityaffairs
Google has expanded enforcement of Google’s Unwanted Software Policy waring Android developers to explicitly declare data collection behaviors.
A few days ago, Google was caught collecting users’ location data even when location services were disabled, many privacy experts questioned the behavior of the tech giant.
Google promptly admitted the practice and suspended it.
Now Google made another move to protect the privacy of its users, it has warned Android developers to explicitly declare data collection behaviors of their apps.
Google revisioned the Safe Browsing rules expanding the enforcement of Google’s Unwanted Software Policy.
“In our efforts to protect users and serve developers, the Google Safe Browsing team has expanded enforcement of Google’s Unwanted Software Policy to further tamp down on unwanted and harmful mobile behaviors on Android.” reads the announcement published by Google.
“As part of this expanded enforcement, Google Safe Browsing will show warnings on apps and on websites leading to apps that collect a user’s personal data without their consent.”
If the developers don’t comply with Google rules within 60 days, the company will warn users via Google Play Protect or on webpages that lead to these apps.
“Starting in 60 days, this expanded enforcement of Google’s Unwanted Software Policymay result in warnings shown on user devices via Google Play Protect or on webpages that lead to these apps.” the announcement said.
Developers of apps that handle either personal data (phone number, e-mail) or device data (such as IMEI number) must prompt the user, and include a privacy policy in the app.
“Additionally, if an app collects and transmits personal data unrelated to the functionality of the app then, prior to collection and transmission, the app must prominently highlight how the user data will be used and have the user provide affirmative consent for such use,” added Google.
Data collection requirements apply to all functions of the app, including crash reporting, the company highlighted that apps cannot transmit the list of installed packages unrelated to their app without an affirmative consent.
Developers can also request an app review using this article on App verification and appeals, it contains guidance applicable to apps in both Google Play and non-Play app stores.
UK National Cyber Security Centre (NCSC)’s letter warns against software made in hostile states, specifically Russia
4.12.2017 securityaffairs
The UK National Cyber Security Centre (NCSC) warns of supply chain risk in cloud-based products, including antivirus (AV) software developed by Russia.
We have a long debated the ban of the Russian security software from US Government offices, now part of the UK intelligence is adopting the same strategy.
Last week the CEO of the UK National Cyber Security Centre (NCSC), Ciaran Martin, wrote to permanent secretaries regarding the issue of supply chain risk in cloud-based products, including anti-virus (AV) software.
The NCSC is a branch of the UK Government Communications Headquarters (GCHQ), the UK intelligence and security agency.
The letter warns against software made in hostile states, specifically Russia, as the Prime Minister’s Guildhall speech set out, the Government of Moscow is acting against the UK’s national interest in cyberspace.
The Letter provides an advice to the Government agencies and offices, but isn’t a ban for specific solutions.
The letter highlights the intrusive nature of antivirus software that is necessary to detect malicious code, it is important to remain vigilant to the risk that AV products developed by a hostile actor could person a wide range of malicious activities.
“The job of AV is to detect malware in a network and get rid of it. So to do its job properly, an AV product must (a) be highly intrusive within a network so it can find malware, and (b) be able to communicate back to the vendor so it knows what it is looking for and what needs to be done to defeat the infiltration. It is therefore obvious why this matters in terms of national security. We need to be vigilant to the risk that an AV product under the control of a hostile actor could extract sensitive data from that network, or indeed cause damage to the network itself.” reads the letter.
“That’s why the country of origin matters. It isn’t everything, and nor is it a simple matter of flags – there are Western companies who have non-Western contributors to their supply chain, including from hostile states. But in the national security space there are some obvious risks around foreign ownership.”
“The specific country we are highlighting in this package of guidance is Russia.”
The official warns of the risk of exposure of classified information to the Russian state that would be a risk to national security, for this reason a Russia-based AV company should not be chosen. It is an obvious reference to the Kaspersky case.

The Letter suggests banning the software developed by Russia-based companies from any system processing information classified SECRET and above.
“To that end, we advise that where it is assessed that access to the information by the Russian state would be a risk to national security, a Russia-based AV company should not be chosen. In practical terms, this means that for systems processing information classified SECRET and above, a Russia-based provider should never be used.” continues the Letter.
“This will also apply to some Official tier systems as well, for a small number of departments which deal extensively with national security and related matters of foreign policy, international negotiations, defence and other sensitive information.”
Martin confirmed that the NCSC is currently discussing with Kaspersky Lab about whether the UK Government can develop a framework that can be independently verified giving the Government assurance about the security of the involvement of the Russian firm in the wider UK market.
“In particular we are seeking verifiable measures to prevent the transfer of UK data to the Russian state. We will be transparent about the outcome of those discussions with Kaspersky Lab and we will adjust our guidance if necessary in the light of any conclusions.” continues the Letter.
In response to the current situation, Kaspersky launched the Transparency Initiative in late October that allows government agencies to review the its security software for backdoors.
PayPal-owned company TIO Networks data breach affects 1.6 million customers
4.12.2017 securityaffairs Incindent
PayPal confirmed that one of the companies it owns, TIO Networks, suffered a security breach, that affected 1.6 million customers.
PayPal confirmed that one of the companies it owns, TIO Networks, suffered a security breach, hackers have accessed servers that stored information for 1.6 million customers.
The company TIO Networks was recently acquired by PayPal for $238 million, it is a Canadian firm that runs a network of over 60,000 utility and bills payment kiosks across North America.
On November 10, PayPal suspended the operations of TIO’s network due to the discovery of “security vulnerabilities” affecting the TIO platform and issues with TIO’s data security programme that does not follow PayPal’s security standards.
“While we apologise for any inconvenience this suspension of services may cause, the security of TIO’s systems and the protection of TIO’s customers are our highest priorities.” said TIO Networks.
“We are working with the appropriate authorities to safeguard TIO customers.”
“The PayPal platform is not impacted by this situation in any way and PayPal’s customers’ data remains secure.
“Our investigation is ongoing. We will communicate with TIO customers and merchant partners directly as soon as we have more details. Customer updates will also be posted at www.tio.com.”
The Canadian firm disclosed the data breach, but did not provide any other details.

On Friday, December 1, PayPal published a press release that includes more details on the hack.
“PayPal Holdings, Inc. (Nasdaq: PYPL) today announced an update on the suspension of operations of TIO Networks (TIO), a publicly traded payment processor PayPal acquired in July 2017. A review of TIO’s network has identified a potential compromise of personally identifiable information for approximately 1.6 million customers.” reads the press release.
“The PayPal platform is not impacted in any way, as the TIO systems are completely separate from the PayPal network, and PayPal’s customers’ data remains secure.”
TIO systems are completely separate from the PayPal network, this means that PayPal’s customers’ data were not affected by the incident.
PayPal confirmed that the attackers stole the personal information of both TIO customers and customers of TIO billers, but it avoided to disclose what type of information the hackers compromised.
Likely attackers accessed personally-identifiable information (PII) and financial details.
PayPal is notifying affected customers of the data breach and is offering free credit monitoring memberships.
The customers of TIO Networks can visit the TIO Networks website for more information on the data breach.
“TIO has also begun working with the companies it services to notify potentially affected individuals, and PayPal is working with a consumer credit reporting agency to provide free credit monitoring memberships. Individuals who are affected will be contacted directly and receive instructions to sign up for monitoring.” continue the Press Release.