
Serious Flaw Found in Many Siemens Industrial Products
7.12.2017 securityweek ICS
Several product lines from Siemens are affected by a serious vulnerability that can be exploited by a remote attacker to cause systems to enter a denial-of-service (DoS) condition.
The flaw, tracked as CVE-2017-12741 and rated “high severity,” was reported to Siemens by George Lashenko of industrial cybersecurity firm CyberX.
According to Siemens, the list of affected products includes SIMATIC S7-200 Smart micro-PLCs for small automation applications, some SIMATIC S7 CPUs, SIMATIC WinAC RTX software controllers, SIMATIC ET 200 PROFINET interface modules, SIMATIC PN/PN couplers, SIMATIC Compact field units, development kits for PROFINET IO, SIMOTION motion control systems, SINAMICS converters, SINUMERIK CNC automation solutions, SIMOCODE motor management systems, and SIRIUS 3RW motor soft starters.
An attacker can cause affected systems to malfunction by sending them specially crafted packets via UDP port 161, which is used for the simple network management protocol (SNMP). In order to recover from the DoS condition, the devices must be manually restarted.
The mitigating factors section of Siemens’ advisory lists the requirement that the attacker must have network access for exploitation, and the fact that it advises organizations to operate these devices only in trusted environments.
However, CyberX told SecurityWeek that there are roughly 2,000 Siemens devices accessible from the Internet, including approximately 400 that have an open SNMP port, which could make them vulnerable to the company’s exploit.
“DoS vulnerabilities shouldn’t be taken lightly,” CyberX said. “The December 2016 attack on the Ukrainian electrical grid used this type of exploit to disable protection relays and make it more difficult for operators to recover.”
The security firm said Siemens was very responsive to its vulnerability report. The vendor has released firmware updates that patch the flaw in some SIMATIC S7, EK-ERTEC, SIMOTION and SINAMICS products.
Until fixes become available for the other affected products, Siemens recommends disabling SNMP, which fully mitigates the vulnerability, protecting network access to port 161, applying defense-in-depth and cell protection concepts, and using VPNs.
HBO hacker linked to the Iranian Charming Kitten APT group
7.12.2017 securityweek APT
A new report published by ClearSky linked a man accused by U.S. authorities of hacking into the systems of HBO to the Iranian cyber espionage group Charming Kitten.
Experts from the security firm ClearSky have published a new detailed report on the activities of Charming Kitten APT group, also known as Newscaster and NewsBeef.
The Newscaster group made the headlines in 2014 when experts at iSight issued a report describing the most elaborate net-based spying campaign organized by Iranian hackers using social media.
Iranian Hackers used a network of fake accounts (NEWSCASTER network) on principal social media to spy on US officials and political staff worldwide, this is reported in an analysis done by iSIGHTPartners. The Charming Kitten group is also known for the abuse of Open Source Security Tools, including the BeEF.
The threat actor targeted numerous entities in Iran, the U.S., Israel, the U.K. and other countries. The hackers also hit individuals involved in academic research, human rights, and the media.
ClearSky detailed the group’s activities during 2016-2017, the report includes information related to the infrastructure used by the APT and to a new strain of malware dubbed DownPaper.
The report also linked the hacker behind the HBO security breach to the Charming Kitten, and reveals the identities of two other alleged members of the group.
Last month, the United States charged the Iranian computer expert Behzad Mesri of ‘Games of Thrones‘ HBO Hack, the man was charged with stealing scripts and plot summaries for ‘Games of Thrones’.
The Manhattan US attorney Joon Kim said Mesri is “had previously hacked computer systems for the Iranian military”. The man threatened to release stolen data unless HBO paid a $6 million ransom in Bitcoin.
Prosecutors confirmed that the Iranian man was a member of the Iranian-based Turk Black Hat Security hacking group that targeted hundreds of websites in the United States and around the world.
“MESRI is an Iran-based computer hacker who had previously worked on behalf of the Iranian military to conduct computer network attacks that targeted military systems, nuclear software systems, and Israeli infrastructure.” continues the DoJ.
“At certain times, MESRI has been a member of an Iran-based hacking group called the Turk Black Hat security team and, as a member of that group, conducted hundreds of website defacements using the online hacker pseudonym “Skote Vahshat” against websites in the United States and elsewhere.”
Experts discovered that Masri and Charming Kitten were linked through the member of Turk Black Hat group “ArYaIeIrAN.” another member of Turk Black Hat.

The email addresses associated with this individual have been used to register several domains used by the Charming Kitten. ClearSky also discovered that the same email address was also used by threat actors to registered a domain for an Iranian hosting firm named MahanServer, which has hosted Charming Kitten infrastructure.
“To sum up, the HBO hacker – Behzad Mesri is a member of Turk Black Hat along with ArYaIeIrAn, who provides infrastructure for Charming Kitten activity via PersianDNS / Mahanserver together with Mohammad Rasoul Akbari, who is a Facebook friend of Behzad Mesri’s.” states the report. “We tend to identify ArYaIeIrAn with Mohammadamin Keshvari, because the latter is the only other employee of Mahanserver and works in a company whose domain was registered by the former (and both have a similar and unique profile picture). We estimate with medium certainty that the three are directly connected to Charming Kitten, and potentially, along with others – are Charming Kitten”
Iranian hackers are becoming even more aggressive even if experts believe that they are not particularly sophisticated.
Recently we discussed the OilRig gang has been using a new Trojan in attacks aimed at targets in the Middle East.
OilRig is just one of the Iran-linked hacker crews, other groups tracked by security experts are APT33, Rocket Kitten, Cobalt Gypsy (Magic Hound), Charming Kitten (aka Newscaster and NewsBeef) and CopyKittens.
NiceHash Hacked – Crooks have allegedly stolen $60m worth of Bitcoin
7.12.2017 securityweek Incindent
The cryptocurrency mining market NiceHash confirmed it has fallen victim to a hacking attack that may have resulted in the loss of $60m worth of Bitcoin
Cryptocurrency companies continue to be a privileged target of hackers, the last victim in order of time is the cryptocurrency mining market NiceHash. The NiceHash marketplace allows users to buy and sell their computing cycles to mine cryptocurrency, the company confirmed it was hacked, attackers stole its entire Bitcoin wallet.
“Unfortunately, there has been a security breach involving NiceHash website. We are currently investigating the nature of the incident and, as a result, we are stopping all operations for the next 24 hours.” reads the statement issued by NiceHash.
“Importantly, our payment system was compromised and the contents of the NiceHash Bitcoin wallet have been stolen. We are working to verify the precise number of BTC taken.”

The security breach has been reported to law enforcement, the company is also investigating the attack.
Even if NiceHash did not provide financial data on the security breach, it has been estimated hackers have stolen around $60m.
NiceHash declared that it is fully committed to restoring the service with the highest security measures, it doesn’t want to exit from the market due to the incident.
The company doesn’t provide further details on the hack, as a precaution it recommends users to change their online passwords.
“While the full scope of what happened is not yet known, we recommend, as a precaution, that you change your online passwords.” concludes the statement.“We are truly sorry for any inconvenience that this may have caused and are committing every resource towards solving this issue as soon as possible.”
The security breach was disclosed just hours after NiceHash confirmed its website was down for maintenance.
NiceHash
@NiceHashMining
Dear NiceHash user, our service is currently under maintenance.
We are sorry for the inconvenience and please stay tuned for updates.
Thank you for your understanding.
8:52 AM - Dec 6, 2017
201 201 Replies 64 64 Retweets 179 179 likes
Twitter Ads info and privacy
At the time of writing, The NiceHash website still shows a maintenance page.
Cybercriminals vs financial institutions in 2018: what to expect
7.12.2017 Kaspersky CyberCrime
Introduction – key events in 2017
2017 was a year of great changes in the world of cyberthreats facing financial organizations.
Firstly, in 2017 we witnessed a continuation of cyberattacks targeting systems running SWIFT — a fundamental part of the world’s financial ecosystem. Attackers were able to use malware in financial institutions to manipulate applications responsible for cross-border transactions, making it possible to withdraw money from any financial organization in the world, because SWIFT software is unified and used by almost all the major players in the financial market. Victims of these attacks included several banks in more than 10 countries around the world.
Secondly, in 2017 we saw the range of financial organizations that cybercriminals have been trying to penetrate, expand significantly. Different cybercriminal groups penetrated bank infrastructure, e-money systems, cryptocurrency exchanges, capital management funds, and even casinos. Their main goal was to withdraw very large sums of money.
To complete their cybercriminal activities, attackers rely on proven schemes of monetizing network access. In addition to their attacks on SWIFT systems, cybercriminals have been actively using ATM infections, including those on financial institution’s own networks, as well as wielding RB (remote banking) systems, PoS terminal networks, and making changes in banks’ databases to ‘play’ with card balances.
Attacks on ATMs are worth mentioning separately. This kind of robbery became so popular that 2017 saw the first ATM malware-as-a-service: with cybercriminals providing on underground forums all necessary malicious programs and video instructions to gain access to ATMs. Those who bought a subscription only needed to choose an ATM, open it following the instructions, and pay the service organizers for activating the malicious program on the ATM, after which the money withdrawal process started. Schemes like this significantly increased the number of cybercriminals, even making cybercrime accessible to non-professionals.
We saw the interception of bank customers’ electronic operations through the hijacking of bank domains. Thus, customers did not have access to their bank’s real infrastructure, but to a fake one created by intruders. For several hours, criminals were therefore able to perform phishing attacks, install malicious code and wield the operations of customers who were using online banking services at the time.
It’s worth noting that, in some countries, banks have forgotten about the most “unimportant” thing – physical security. This has made attacks on banks’ financial assets possible. In some cases, this was due to easy access to cable lines, to which small Raspberry Pi devices were then connected. For several months these devices passively collected information about bank networks and sent intercepted data over LTE connections to the servers of intruders.
Predictions for 2018
Attacks via the underlying blockchain technologies of financial systems
Almost all of the world’s large financial organizations are actively investing in systems based on blockchain technology. Any new technology has its advantages, but also a number of new risks. Financial systems based on blockchain do not exist autonomously, therefore vulnerabilities and errors in blockchain implementation can enable attackers to earn money and disrupt the work of a financial institution. For instance, in 2016-2017, a number of vulnerabilities and errors were discovered in smart contracts, on which a number of financial institution’s services have been built.
More supply chain attacks in the financial sphere
Large financial organizations invest considerable resources in cybersecurity, thus the penetration of their infrastructure is not an easy task. However, a threat vector that is likely to be actively used by cybercriminals in the coming year is attacks on software vendors supplying financial organizations. Such vendors, for the most part, have a weak level of protection compared to the financial organizations themselves. Last year, we witnessed a number of attacks like this: including against NetSarang, CCleaner, and MeDoc. As we can see, attackers replaced or modified updates for very different types of software. In the next year, we can expect cybercriminals to perform attacks via software designed specifically for financial organizations, including software for ATMs and PoS terminals. A few months ago we registered the first attempts of this kind, when attackers embedded a malicious module into a firmware installation file, and placed it on the official website of one of the American ATM software vendors.
Mass media (in general, including Twitter accounts, Facebook pages, Telegram, etc.) hacks and manipulation for getting financial profit through stock/crypto exchange trade
2017 will be remembered as the year of ‘fake news’. Besides the manipulation of public opinion, this phrase can also mean a dishonest way of earning money. While stock exchange trading is mostly carried out by robots manipulating source data, which is used to make certain transactions, it can also lead to enormous changes in the price of goods, financial instruments and cryptocurrencies. In fact, just one tweet from an influencer, or a wave of messages on a social network created with the help of fake accounts, can drive the markets. And this method will certainly be used by intruders. With this approach, it’s almost impossible to find out which of the beneficiaries is the customer of the attack.
ATM malware automation
The first malware for ATMs appeared in 2009, and since then these devices have received constant attention from cyber-fraudsters. There has been a continuous evolution of this type of attack. The past year saw the emergence of ATM malware-as-a-service, and the next step will be the full automation of such attacks – a mini-computer will be connected automatically to an ATM, leading to malware installation and jackpotting or card data collection. This will significantly shorten the time needed for intruders to commit their crime.
More attacks on crypto exchange platforms
For the past year, cryptocurrencies have attracted a huge number of investors, which in turn has led to a boom in new services for trading various coins and tokens. Traditional players in the financial market, with highly developed cybersecurity protection, haven’t rushed to enter this field.
This situation provides attackers with an ideal opportunity to target cryptocurrency exchanges. On the one hand, new companies haven’t managed to test their security systems properly. On the other hand, the entire cryptocurrency exchange business, technically speaking, is built on well-known principles and technologies. Thus, attackers know, as well as have, the necessary toolkit to penetrate the infrastructure of new sites and services working with cryptocurrencies.
Traditional card fraud will spike due to the huge data breaches of the previous year
Big personal data leaks – including the recent Equifax case, which resulted in more than 140 million U.S. residents’ data being leaked to cybercriminals, and the Uber case, when the data of another 57 million customers was leaked – has created a situation where traditional banking security can seriously fail, because it’s based on the analysis of data about current or potential customers.
For example, detailed knowledge of a victim’s personal data can allow attackers to pose as a banking customer, and extract their victim’s money or security information, while to the bank concerned, their request looks legitimate. Therefore, the coming year may be marked by a spike in quite traditional fraud schemes, with the big data that has been collected (but not properly protected) by organizations about their customers for years, set to help attackers in the successful realization of their fraud schemes.
More nation-state sponsored attacks against financial organizations
The infamous Lazarus group, which is likely to be North-Korean state-sponsored, has attacked a number of banks in different parts of the world in the last few years. These have included banks in countries in Latin America, Europe, Asia and Oceania. Their main purpose has been to withdraw large sums of money, amounting to hundreds of millions of dollars. In addition, the data released by the Shadow Brokers indicates that experienced state-sponsored APT-groups are targeting financial institutions in order to learn more about cash flows. It is very likely that, next year other APT groups from countries that have just joined the cyber-spy game will follow this approach – both to earn money and to obtain information about customers, the flow of funds and the internal procedures of financial organizations.
Fintechs’ inclusion and mobile only-users: a fall in the number of traditional PC-oriented internet-banking Trojans. Novice mobile banking users will be a new prime target for criminals
Digital banks will continue revolutionizing the financial sector on a global scale, especially in emerging markets. For example, in Brazil and Mexico, these banks are gaining more and more momentum and this, of course, has attracted cybercriminal attention. We are sure that the world of cybercrime will see increasing attacks against this type of banks and their customers. Their main feature is the complete absence of branches and traditional customer service. All communication between the bank and its customers actually occur through a mobile application. This can have several consequences.
The first is a decrease in the number of Windows Trojans, aimed at stealing money through traditional internet banking. The second is that the growing number of digital financial institutions will lead to organic growth in the number of users that are easy targets for cybercriminals: people without any mobile banking experience, but with banking applications installed on their mobile devices. These people will be the main targets for both malware attacks, such as Svpeng, and schemes completely built on social engineering. Persuading a customer to transfer money through a mobile application is much easier than forcing them to go to a physical bank and make a transaction.
Conclusion
During the past few years, the number and quality of attacks aimed at financial sector organizations has grown continuously. These are attacks on the infrastructure of an organization and its employees, not its customers.
The financial institutions that have not already thought about cybersecurity will soon face the consequences of hacker attacks. And these consequences will be incompatible with the continuation of these businesses: they will lead to a complete halt in operations as well as extreme losses.
To prevent situations like this from happening, it is necessary to constantly adapt security systems to new emerging threats. This is impossible without analyzing data and information about the most important and relevant cyberattacks aimed at financial organizations.
An effective approach to combating attacks will be for banks to choose the right security solutions, but also to use specialized intelligence reports on attacks as these contain information that must be implemented immediately into overall protection systems. For example, using YARA-rules and IOCs (indicators of compromise), will become vital for financial organizations in the coming months.
Hackers Can Steal Data From Air-Gapped Industrial Networks via PLCs
7.12.2017 securityweek ICS
Researchers have discovered a method that hackers could use to stealthily exfiltrate data from air-gapped industrial networks by manipulating the radio frequency (RF) signal emitted by programmable logic controllers (PLCs).
Attackers may be able to plant a piece of malware on an isolated network, including via compromised update mechanisms or infected USB drives, but using that malware to send valuable data outside the organization poses its own challenges.
In the past few years, Israeli researchers have found several methods that can be used to jump the air gap, including via infrared cameras, scanners, the LEDs on routers and hard drives, heat emissions, radio signals, and the noise made by hard drives and fans. One of their proof-of-concept (PoC) malware, named AirHopper, uses electromagnetic signals emitted by a computer’s graphics card to send data to a nearby receiver.
Researchers at CyberX, a company that specializes in protecting industrial control systems (ICS), have found a way to apply a similar data exfiltration method to systems in air-gapped industrial networks. The method was first disclosed in October at SecurityWeek’s ICS Cyber Security Conference by CyberX VP of Research David Atch.
CyberX shows how malware can jump the air gap via PLCs
The technique relies on PLCs and the RF signals they emit. Tests were conducted using the popular Siemens S7-1200 PLC, but experts believe the attack likely works on PLCs from other vendors as well.
The exfiltration method discovered by CyberX does not leverage any vulnerabilities or design flaws in PLCs. Experts also noted that it does not involve any RF functionality in the device itself. Rather, the RF signals emitted by the device are a byproduct of repeatedly writing to the PLC’s memory in a specific way.
Researchers analyzed the radio waves from these systems and found that the frequency changes when data is written to the device’s memory. If an attacker can manipulate this frequency, they can use it to exfiltrate data bit by bit – a certain frequency represents a “0” bit and a different frequency represents a “1” bit. The signal can be captured by a nearby antenna and decoded using software-defined radio.
Writing to the PLC memory in a specific cycle that causes a modulation in the frequency of the RF signal can be achieved by uploading a specially crafted ladder diagram to the device. Ladder diagrams are created with ladder logic, a programing language used to develop software for PLCs.
An attacker who has access to the targeted organization’s systems, specifically to its industrial controllers, can upload a malicious ladder diagram to a PLC and abuse it to exfiltrate sensitive data.
In the tests it conducted, CyberX managed to transmit data at a rate of 1 bit per second over a distance of roughly 1 meter (3 feet) with an off-the-shelf antenna. However, experts believe the distance can be increased using a higher quality antenna, and improvements made to signal processing algorithms can help increase the speed of the transmission.
The exfiltrated data can be captured using various methods, such as an antenna attached to a drone flying over the site, or by an adversary posing as cleaning staff and carrying an antenna in their pocket.
While the data exfiltration rate may seem very slow, experts believe the method can be useful for stealing small pieces of information typically collected in the reconnaissance phase of an attack launched by a sophisticated threat actor, including network topology, protocols and devices, intellectual property stored in HMIs and historians, and work schedules.
Researchers warned that these types of attacks are typically difficult to detect due to the fact that there aren’t any security solutions running on PLCs. Furthermore, once a device has been compromised, the malicious code persists for an extended period of time since they are rarely formatted.
“Organizations can prevent these types of attacks with continuous monitoring and behavioral anomaly detection,” Atch told SecurityWeek. “For example, this would immediately detect the cyber reconnaissance phase preceding data exfiltration -- such as devices scanning the network and querying devices for configuration information -- as well as unauthorized updates to PLC ladder logic code to deploy the specially-crafted code to generate encoded RF signals.”
StorageCrypt Ransomware Targets NAS Devices via SambaCry Exploit
7.12.2017 securityweek Ransomware
A new ransomware family is using the SambaCry vulnerability that was patched in May to infect network-attached storage (NAS) devices, researchers have discovered.
Dubbed StorageCrypt, the ransomware demands between 0.4 and 2 Bitcoins ($5,000 to $25,000) from its victims for decrypting the affected files.
To infect NAS devices, StorageCrypt abuses the Linux Samba vulnerability known as SambaCry and tracked as CVE-2017-7494. Affecting devices from major vendors, the bug allows remote attackers to execute arbitrary code on targeted systems by uploading a shared library to a writable share, and then causing the server to load that library.
The first attempt to abuse the vulnerability resulted in targeted systems being infected with a cryptocurrency miner. During summer, a piece of malware dubbed SHELLBIND started abusing the flaw to infect NAS devices.
StorageCrypt leverages the SambaCry in the same manner as SHELLBIND did, BleepingComputer’s Lawrence Abrams reveals. The attack relies on the exploit executing a command to download a file called sambacry, store it in the /tmp folder as apaceha, and then running it.
What the security researcher couldn’t yet determine is whether the executable is only used to install the ransomware or is also serves as a backdoor for future attacks.
Once StorageCrypt is up and running on the infected device, it encrypts and renames the files and appends the .locked extension to them. It also drops a ransom note containing the ransom amount, the attackers’ Bitcoin address, and email address JeanRenoAParis@protonmail.com.
The malware was also observed dropping two files on the infected NAS devices, namely Autorun.inf and 美女与野兽.exe (which reportedly translates to Beauty and the beast). The former file is meant to spread the Windows executable to the machines the folders on the NAS device are accessed from.
To stay protected from this ransomware or other malware abusing SambaCry, users are advised to apply the latest patches to ensure their devices aren’t vulnerable, as well as to disconnect NAS devices from the Internet. Setting up a firewall and using a VPN for secure access to the NAS should also be taken into consideration.
The StorageCrypt ransomware is the last malware in order of time exploiting SambaCry to target NAS Devices
7.12.2017 securityaffairs Ransomware
StorageCrypt Ransomware is the last malware in order of time exploiting the SambaCry vulnerability, it was developed to target NAS Devices.
Experts discovered a new strain of malware exploiting the SambaCry vulnerability (CVE-2017-7494), it has been called StorageCrypt Ransomware because it targets NAS Devices via SambaCry Exploit.
The StorageCrypt ransomware demands between 0.4 and 2 Bitcoins ($5,000 to $25,000) for decrypting the encrypted files.
“Recently BleepingComputer has received a flurry of support requests for a new ransomware being named StorageCrypt that is targeting NAS devices such as the Western Digital My Cloud.” wrote the malware expert Lawrence Abrams from BleepingComputer.
“Victims have been reporting that their files have been encrypted and a note left with a ransom demand of between .4 and 2 bitcoins to get their files back.”
Experts discovered that the malware exploits the Linux Samba vulnerability, aka SambaCry, that was patched in May.
The vulnerability could be exploited by remote attackers to execute arbitrary code on targeted systems by uploading a shared library to a writable share, and then causing the server to load that library.
In July, experts discovered a malware dubbed SHELLBIND that exploited the CVE-2017-7494 Samba vulnerability in attacks against Internet of Things devices.
SHELLBIND infected most network-attached storage (NAS) appliances, it exploits the Samba vulnerability (also known as SambaCry and EternalRed) to upload a shared library to a writable share, and then cause the server to load that library.
CVE-2017-7494 is a seven-year-old remote code execution vulnerability that affects all versions of the Samba software since 3.5.0. The flaw has been patched by the development team of the project.
The CVE-2017-7494 flaw can be easily exploited, just a line of code could be used for the hack under specific conditions:
make file- and printer-sharing port 445 reachable on the Internet,
configure shared files to have write privileges.
use known or guessable server paths for those files
The Samba vulnerability affects the products of several major vendors, including NAS appliances.
The Samba bug appears to be a network wormable issue that could be exploited by a malicious code to self-replicate from vulnerable machine to vulnerable machine without requiring user interaction.
In June, researchers at Kaspersky Lab set up honeypots to detect SambaCry attacks in the wild. The experts spotted a malware campaign that was exploiting the SambaCry vulnerability to infect Linux systems and install a cryptocurrency miner.
According to Lawrence Abrams, the StorageCrypt Ransomware relies on the exploit executing a command to download a file called sambacry, store it in the /tmp folder as apaceha, and then executing it.
It is still unclear if the executable only installs the StorageCrypt ransomware or if it is also used as a backdoor.
Once the ransomware infected a device, it encrypts the files and renames them by appending the .locked extension to them.
“When a file is encrypted it will be renamed so that the .locked extension is appended to the filename. The ransomware will also drop a ransom note named _READ_ME_FOR_DECRYPT.txt that contains the ransom amount, the bitcoin address to send payment to, and the email address JeanRenoAParis@protonmail.com to contact after payment.” continues Abrams.

The ransomware drops two files on the infected NAS devices, namely Autorun.inf and 美女与野兽.exe, the latter file is meant to spread the Windows executable to the machines the folders on the NAS device are accessed from.
To avoid being infected by the StorageCrypt ransomware or other malware exploiting the SambaCry flaw, users need to apply the latest. Users also need to disconnect NAS devices from the Internet, set up a firewall to protect the storage device and use a VPN for secure access to it.
Bitcoinového boomu využívají počítačoví piráti
7.12.2017 SecurityWorld Hacking
Rostoucí hodnotu Bitcoinů provází také nárůst malwaru zaměřeného právě na kryptoměnu.
Společnost Malwarebytes vykázala, že během jediného měsíce zastavila téměř 250 milionů pokusů o propašování těžebního malwaru do počítačů bez vědomí jejich uživatelů. Podle jiné firmy – Symantecu – je nárůst malwaru souvisejícího s těžbou kryptoměny za nedávné období desetinásobný.
Hackeři přitom k jeho šíření používají jak specializovaný software, tak nabourané webové stránky, ale i emaily. Jejich zvýšenou aktivitu podnítila právě rostoucí cena Bitcoinu, jehož hodnota se oproti začátku letošního roku zdesetinásobila a před pár dny překonala hranici 10 000 dolarů (214 500 Kč).
„Okolo kryptoměny se vytvořil obrovský hype a spousta lidí se na ní teď snaží vydělat,“ komentuje Candid Wuest ze Symantecu. Bitcoin přitom není primárním cílem kyberzlodějů – ti se, vzhledem k náročnosti jeho těžby, soustředí převážně na ostatní kryptoměny, jako je například Monero, jež si nežádá takový výkon, a k jehož těžbě lze zneužít třeba i chytrého mobilního telefonu. A jejich hodnota také stoupá.
Dle zprávy společnosti Malwarebytes její bezpečnostní software v těchto dnech zablokuje denně v průměru osm milionů pokusů o propašování těžebního malwaru do PC, a to většinou z webových stránek, které hackeři napadli. Škodlivý kód však mohou obsahovat i rozšíření či doplňky webových prohlížečů.
Jakmile se tento kód dostane do počítače, zapojí ho do těžebního procesu tak, že ždíme procesor téměř na 100 %. Na chytrých telefonech se to může projevit nejen snížením výkonu, ale také rychlým vybíjením baterie.
Donedávna těžební malware fungoval jen s využitím zapnutého prohlížeče oběti, nové typy však dokážou těžit i bez toho, aby byl prohlížeč zapnutý.
„Trik je v tom, že i když se prohlížeč jeví jako zavřený, další skrytý zůstává nadále otevřený,“ popisuje Jerome Segura z Malwarebytes, jak malware funguje. Uživatel si miniaturního okna skrytého pod panelem nástrojů prakticky nemá možnost všimnout.
Každá organizace je obětí mobilních útoků
7.12.2017 SecurityWorld Mobilní
Check Point Software Technologies představil výsledky první studie o dopadu mobilních útoků na podnikové prostředí. Studie vychází z dat od více než 850 organizací ze čtyř kontinentů. Výsledky jsou zřejmé: Podniková mobilní prostředí jsou zranitelná a hrozí útoky na obě hlavní mobilní platformy, Android i iOS.
Mobilní hrozby mohou ohrozit jakékoli zařízení a získat libovolný přístup k citlivým datům. V bezpečí před mobilními útoky není nikdo, od finančních společností a výrobních podniků až po vládní organizace.
Z průzkumu například vyplývá, že:
100 % všech organizací zaznamenalo mobilní malwarový útok
54 je průměrný počet mobilních malwarových útoků na jednu organizaci
89 % společností zaznamenalo útok typu man-in-the-middle přes Wi-Fi
75 % organizací mělo v síti v průměru 35 rootovaných nebo jailbroken zařízení
„Útoky na mobilní zařízení překročily v roce 2017 útoky na osobní počítače ve frekvenci i finanční hodnotě a náš report pomáhá tento trend pochopit a vysvětlit,“ říká Petr Kadrmas, Secuity Engineer Eastern Europe ve společnosti Check Point. „Mobilní zařízení jsou pro kyberzločince v podstatě nová zadní vrátka a jsme proto rádi, že můžeme představit vylepšené řešení SandBlast Mobile, které proaktivně chrání organizace i jednotlivé zákazníky.“
Check Point upozorňuje, že útoky na mobilní zařízení se posunuly od známého malwaru a zneužití slabin v sítích a operačních systémech k zero-day malwaru, SMS útokům a zneužití Bluetooth zranitelností.
Bezpečnostní experti varovali před virem Redirector. Uživatele navede na škodlivé weby
7.12.2017 Novinky/Bezpečnost Viry
Antivirová společnost Eset vydala žebříček těch největších hrozeb za měsíc listopad. V nich kraloval trojský kůň Redirector, který dokáže v počítači udělat pěknou neplechu. Uživatele totiž přesměrovává na škodlivé weby. Lidé by si tak na něj měli dát velký pozor.
„Redirector je škodlivý kód, který automaticky přesměrovává internetový prohlížeč napadeného zařízení na škodlivé stránky, odkud uživatel může stáhnout do svého počítače další druhy malwaru. Škodlivý software bývá obvykle vložen přímo do HTLM kódu odkazovaných stránek,“ varoval Miroslav Dvořák, technický ředitel společnosti Eset.
Uživatel se tedy může tímto trojským koněm infikovat i v případě, kdy bude pracovat s nějakou infikovanou webovou stránkou.
„Jde o nepříjemný malware, který se projevuje automatickým otevíráním stránek s různým, často nesmyslným obsahem. K otevírání stránek dochází v nepravidelných intervalech a dané stránky mohou uživatele nabádat, aby si stáhl další software, například kvůli napadení jeho počítače a eliminaci škod,“ doplnil Dvořák.
Otevírá okna s nevyžádanou reklamou
Nevyžádaná okna internetového prohlížeče otevírá i druhý v listopadu nejčetněji zachycený malware v Česku, který nese plný název JS/Adware.AztecMedia. „Nepřesměrovává však na jiné internetové stránky, nýbrž otevírá okna s nevyžádanou reklamou a v některých případech dokáže dokonce i změnit domovskou stránku internetového prohlížeče,“ konstatoval bezpečnostní expert.
Třetím nejčastěji detekovaným škodlivým kódem v listopadu byl exploit SMB/Exploit.DoublePulsar. „Jde o nechvalně proslulý škodlivý kód, který ke svému šíření využíval ransomare WannaCry,“ zdůraznil Dvořák.
Škodlivý software ransomware pojmenovaný jako WannaCry nebo WanaCrypt0r 2.0 letos v květnu napadl 300 000 počítačů ve 150 zemích světa. Podle bezpečnostních expertů jde vůbec o největší útok ransomwaru vůbec.
Přehled deseti nejrozšířenějších virových hrozeb za uplynulý měsíc naleznete v tabulce níže:
Deset nejčastějších internetových hrozeb v České republice za říjen 2017:
1. JS/Redirector (3,91 %)
2. JS/Adware.AztecMedia (3,59 %)
3. SMB/Exploit.DoublePulsar (3,56 %)
4. JS/Danger.ScriptAttachment (3,03 %)
5. PowerShell/Agent.BS (2,75 %)
6. Java/Adwind (2,51 %)
7. Win32/GenKryptik (2,30 %)
8. PowerShell/Adware.Adposhel (2,23 %)
9. VBS/TrojanDownloader.Agent.PJJ (1,65 %)
10. JS/Kryptik.MX (1,44 %)
Zdroj: Eset
Firefox obsahuje kritickou bezpečnostní trhlinu. Útočníci mohou převzít kontrolu nad PC
7.12.2017 Novinky/Bezpečnost Zranitelnosti
Na pozoru by se měli mít uživatelé internetového prohlížeče Firefox od společnosti Mozilla. Obsahuje totiž kritickou bezpečnostní chybu, kterou mohou zneužít počítačoví piráti k infiltraci do cizího počítače. Tvůrci naštěstí již vydali bezpečnostní záplatu.
Před nově objevenou trhlinou varoval český Národní bezpečnostní tým CSIRT.CZ. Ten zároveň upozornil i na to, že opravy pro chybu jsou již k dispozici.
„U Firefoxu vydávaného společností Mozilla doporučujeme aktualizaci na verzi 57.0.1,“ prohlásil bezpečnostní analytik CSIRT.CZ Pavel Bašta s tím, že nejnovější verze prohlížeče s logem ohnivé lišky již trhlinu neobsahuje.
Chyba je kritická. To jinými slovy znamená, že útočníci mohou do počítače propašovat prakticky jakýkoli škodlivý kód. Klidně mohou i na dálku počítač zotročit a využít jej k DDoS útokům, případně mohou samozřejmě i odposlouchávat komunikaci uživatele, která na počítači probíhá.
V případě automatických aktualizací se uživatelé Firefoxu nemusejí o nic starat. Pokud je však tato funkce vypnuta, je nutné navštívit webové stránky tvůrců a nejnovější záplatovanou verzi stáhnout manuálně.
Řada nových funkcí
Firefox se v listopadu dočkal velké aktualizace zvané Quantum, která přidala celou řadu nových funkcí. Má totiž zcela nový vzhled, nové jádro a je výrazně rychlejší než předchůdce.
V první řadě je třeba zmínit nové uživatelské rozhraní zvané Photon. To místo zaoblených panelů sází na ostře řezané linie, působí modernějším dojmem a je přehlednější. Nová domovská stránka nabízí zajímavý obsah pro opětovné navštívení a průvodce, který uživateli ukáže zajímavé funkce Firefoxu.
„Mnoho akcí v prohlížeči probíhá asynchronně, takže jsou rychlejší, plynulejší a neblokují zbytek Firefoxu. Například posouvání stránek (scrollování – pozn. red.), přepínání panelů nebo animace tlačítek použité ve Photonu,“ konstatoval Michal Stanke ze serveru Mozilla.cz.
Celá řada změn se ale dotkla i technické stránky prohlížeče. „Nová CSS knihovna Stylo zrychluje vykreslování stránek. Do Firefoxu se dostala v rámci projektu Quantum – odtud název verze,“ přiblížil Stanke jednu z předností.
Android Development Tools Riddled with Nasty Vulnerabilities
6.12.2017 securityweek Android
Java/Android developers are exposed to vulnerabilities affecting the development tools, both downloadable and cloud based, used in the Android application ecosystem, Check Point warns.
Check Point security researchers have discovered several vulnerabilities impacting the most common Android Integrated Development Environments (IDEs), namely Google’s Android Studio and JetBrains’ IntelliJ IDEA and Eclipse, along with major reverse engineering tools for Android applications, including APKTool, the Cuckoo-Droid service, and more.
The bugs were reported to the impacted IDE companies in May 2017 and have been already resolved in Google and JetBrains tools.
According to Check Point, their research focused on APKTool (Android Application Package Tool), which emerges as the most popular tool for reverse engineering third party Android apps, and which allows developers to decompile and build APK files.
Both of the tool’s features, however, are plagued by vulnerabilities, the researchers argue. The program’s source code revealed an XML External Entity (XXE) vulnerability in a function called “loadDocument,” which is being used in both core functionalities.
Because of this vulnerability, the entire OS file system of APKTool’s user is exposed, which allows an attacker exploiting the vulnerability to “potentially retrieve any file on the victim’s PC.” For that, a malicious “AndroidManifest.xml” file that exploits the issue is needed.
The researchers also analyzed the XML parser called “DocumentBuilderFactory” that is being used in the APKTool project and discovered multiple vulnerable implementations of the XML parser within other projects. It also led to the discovery that IDEs such as Intellij, Eclipse, and Android Studio are affected as well.
“By simply loading the malicious ‘AndroidManifest.xml’ file as part of any Android project, the IDEs start spitting out any file configured by the attacker,” the security researchers explain.
The researchers uploaded a malicious project library to GitHub and cloned it to an Android Studio project, which demonstrated that an attack abusing this vulnerability is successful. Other attack vectors were discovered as well, such as injecting a malicious AAR (Android Archive Library) containing the XXE payload into repositories.
“It is possible, for example, to upload an infected AAR to a public repository such as the central Maven repository. Cloning the infected AAR from the repository by the victim would allow the attacker to steal sensitive files such as configuration files, source code, company digital proprietary and much more from the OS file system,” Check Point says.
Next, the researchers discovered a vulnerability in APKTool that could allow an attacker to execute commands on the victim’s PC.
The issue was discovered in the configuration file “APKTOOL.YML,” which is employed for the advanced use of the tool, and which contains a section called “unknownFiles” that “allows users to include a non-standard file location that will be placed correctly on the rebuild process of an APK.”
The selected files are saved in a ‘Unknown’ folder and modifying the path of the “unknownFiles” section can result in injecting arbitrary files anywhere on the file system, because APKTool “does not validate the path of which the unknown files will be extracted from the packed APK.”
Injecting arbitrary files in the filesystem can lead to remote code execution, and any APKTool user/service is vulnerable when attempting to decode a crafted malicious APK.
“It is impossible to estimate the number of users of this well-known open source project. Yet, knowing that among them are some large services and companies, we contacted APKTool developer and IDE companies and are pleased to report that they all fixed the security issues and released updated and improved versions of their products,” Check Point concludes.
Mailsploit: Popular Email Apps Allow Spoofing, Code Injection
6.12.2017 securityweek Hacking
Tens of email clients, including some of the most popular applications, are plagued by flaws that can be exploited for address spoofing and, in some cases, even for code injection.
The attack method, dubbed Mailsploit, was discovered by Sabri Haddouche, a pentester and bug bounty hunter whose day job is at secure messaging firm Wire.
The researcher found that an attacker can easily spoof the sender’s address in an email, and even bypass spam filters and the DMARC protection mechanism. More than 30 email apps are impacted, including Apple Mail, Mozilla Thunderbird, Outlook and other applications from Microsoft, Yahoo Mail, Hushmail, and ProtonMail.
All affected vendors were notified in the past months. Yahoo, ProtonMail and Hushmail have already released patches, while others are still working on a fix. Some organizations, such as Mozilla and Opera, said they don’t plan on addressing this issue, and others have not informed Haddouche on whether or not fixes will be rolled out.
Mailsploit attacks are possible due to the way non-ASCII characters are encoded in email headers. These headers are required to contain only ASCII characters, but RFC-1342, published in 1992, provides a way to encode non-ASCII characters so that mail transfer agents (MTAs) can process the email.
Haddouche discovered that many email providers, including clients and web-based apps, fail to properly sanitize the decoded string, which leaves room for abuse.
For example, take the following string in the From parameter of the header:
From: =?utf-8?b?cG90dXNAd2hpdGVob3VzZS5nb3Y=?==?utf-8?Q?=00?==?utf-8?b?cG90dXNAd2hpdGVob3VzZS5nb3Y=?=@mailsploit.com
When decoded by Apple’s Mail application, it becomes:
From: potus@whitehouse.gov\0(potus@whitehouse.gov)@mailsploit.com
However, iOS discards everything after the null byte, and macOS displays only the first valid email address it detects, which leads to recipients seeing the sender as “potus@whitehouse.gov.”
The Mailsploit attack can be dangerous not only because of how the email address can be spoofed. Using this method also bypasses DMARC, a standard that aims to prevent spoofing by allowing senders and recipients to share information about the email they send to each other.
“The server still validates properly the DKIM signature of the original domain and not the spoofed one,” the researcher explained. “While MTAs not only don’t detect and block these spoofed email addresses, they will happily relay those emails as long as the original email seems trustworthy enough (the attacker can therefore ironically profit from setting up DMARC on that email address). This makes these spoofed emails virtually unstoppable at this point in time.”
In some cases, attackers can also execute arbitrary JavaScript code. This is possible by encoding the code they want to execute in the From parameter of the header. The code will get executed either when the malicious email is opened or when certain actions are performed (e.g. creating a new rule, replying to an email), depending on the application.
HBO Hacker Linked to Iranian Spy Group
6.12.2017 securityweek Hacking
A man accused by U.S. authorities of hacking into the systems of HBO and attempting to extort millions of dollars from the company has been linked by security researchers to an Iranian cyber espionage group tracked as Charming Kitten.
Security firm ClearSky has published a new report detailing the activities of Charming Kitten, which is also known as Newscaster and NewsBeef. The threat actor has been active since at least 2014 and it has targeted numerous entities in Iran, the U.S., Israel, the U.K. and other countries. Its attacks have often been aimed at individuals involved in academic research, human rights and the media.
The ClearSky report describes the group’s activities during 2016-2017, including the infrastructure used and a new piece of malware named DownPaper. It also details the connection between the individual accused of hacking HBO and Charming Kitten, and reveals the identities of two other alleged members of the group.
Behzad Mesri, also known as Skote Vahshat, was charged last month by U.S. prosecutors on seven counts related to hacking HBO, stealing scripts and other information on popular TV shows, and threatening to release the data unless the network paid $6 million in Bitcoin.
When they unsealed the indictment, authorities said Mesri had also launched cyberattacks on behalf of the Iranian military against military systems, nuclear software systems, and Israeli infrastructure. They also claimed he was a member of an Iran-based hacking group called Turk Black Hat, which conducts website defacements.
Collin Anderson, a researcher specializing in state-sponsored attacks, particularly ones attributed to Iran, was the first to point out that based on the information in the indictment, Mesri appeared to be a member of Charming Kitten.
ClearSky has also found connections between Masri and Charming Kitten. One of the links is through “ArYaIeIrAN,” another member of Turk Black Hat. Email addresses associated with this individual have been used to register several Charming Kitten domains. The same email address also registered a domain for an Iranian hosting firm named MahanServer, which has hosted Charming Kitten infrastructure.
The CEO of this company appears to be one Mohammad Rasoul Akbari, and ArYaIeIrAN could be one Mohammadamin Keshvari, who is listed as MahanServer’s only other employee on LinkedIn. Akbari is linked to Masri via their Facebook profiles.
“We estimate with medium certainty that the three are directly connected to Charming Kitten, and potentially, along with others – are Charming Kitten,” ClearSky wrote in its report.
In the past years, security researchers have linked several cyber espionage groups to Iran, including APT33, Rocket Kitten, Cobalt Gypsy (Magic Hound), and CopyKittens. There are many overlaps between these actors, both in terms of infrastructure and malware, which means the individuals identified by ClearSky could be part of other Iranian groups as well, not just Charming Kitten.
Corporate IoT Implementation Struggling, Survey Finds
6.12.2017 securityweek IoT
Security is the Primary Concern for Firms Implementing an IoT Strategy, IT Pros Say
Remaining competitive is the primary motivation for implementing a corporate 'internet of things' (IoT) strategy; but 90% of those doing so admit the implementation is struggling. Security is the primary concern, holding back 59% of organizations with a current IoT project.
Security is followed by the cost of implementation (46%); competing priorities (37%); an intimidatingly complex IT infrastructure (35%); and funding (32%). The figures come from a survey (PDF) published this week by Vanson Bourne, commissioned by the Wi-SUN Alliance, which questioned 350 IT decision makers from firms in the U.S., UK, Sweden and Denmark that are already investing in at least one IoT project.
The purpose of the survey was to help Wi-SUN better understand how it is perceived in the IoT marketplace, and to help plan future operations. Wi-SUN is a non-profit alliance of around 170 major firms throughout the world with a mission to drive interoperable IoT communications based on open global standards in industrial IoT, with particular concern for utilities and smart cities.
Security Concerns Slow Use of IoT in the EnterpriseKey findings from the survey show that the U.S. (65% of respondents) is ahead of the other three countries surveyed with fully implemented IoT strategies. It is 47% in the UK, 44%in Sweden, and 24% in Denmark. The U.S. also leads in prioritizing IoT enablement: U.S. (73%), UK (64%), Sweden (62%) and Denmark (58%).
One clear outcome from the survey is the emphasis on security as the most important characteristic when considering an IoT implementation for both smart cities (84%) and utilities (85%). Second only to security is the preference for industry open standards: again 84% for smart cities, and 81% for utilities.
These two features fit well with the Wi-SUN network design specification. "Wi-SUN is about the communications layer," Phil Beecher, chair of the Wi-SUN Alliance, told SecurityWeek. "We're providing what could be seen as a large scale outdoor IoT wireless mesh that looks like an internet. It has all the resilience and reliability of a decentralized communication network. It doesn't specify any of the applications that run on top of that, so any application that runs over UDP or TCP can be run over Wi-SUN."
That, of course, is only part of a large-scale IoT network. "In a smart city," he continued, "we would provide wireless communication between street lights, or from street lights to traffic signals. But at strategic points there would be a connection to a high speed, probably fiber, connection to transport data to the network's back office." It's not a wifi network because the wifi range is too limiting. Instead Wi-SUN uses stronger radio communications able to cover up to several kilometers.
The security comes in two areas: certificate-based device authentication, and the mesh and wireless topology of the network itself.
"One of our strengths," continued Beecher, "is that we offer bi-directional communications at a fairly high data rate -- so we can do over-the-air upgrades to apply security patches. No device can connect to the network without being 'vetted'. This is based on the use of certificates. Every device has its own certificate burned in during production, and every device needs to have that certificate verified before it can join the network. Once it is verified and on the network, it is possible to download new code into that device."
The process cannot, of course, be retrofitted to old devices that can't be patched. Security here must be applied through traditional network gateways and routers; but in reality organizations with such devices should be considering renewing them with more modern devices -- and taking advantage of security updates and certificate-based security.
"This certificate authentication," said Beecher, "makes it very difficult for a remote attacker to hack any of the devices or a local attacker to tamper with the device. The mesh topology of the network also makes it difficult to deliver an effective DoS attack, whether by jamming or data overload, against the network."
Jamming is difficult because the network uses the military technique of frequency hopping. "You would need a high-power wide-band jammer," he explained. "This is difficult to achieve; although it is possible at, say, military levels. Otherwise Wi-SUN is largely immune to local jamming."
Senate Confirms New US Homeland Security Chief
6.12.2017 securityweek BigBrothers
The US Senate confirmed White House deputy chief of staff Kirstjen Nielsen as Secretary of Homeland Security on Tuesday, putting her in charge of implementing the Trump administration's immigration crackdown.
Nielsen is close to White House Chief of Staff John Kelly, who was President Donald Trump's first secretary at the Department of Homeland Security before he was brought in to discipline Trump's chaotic office at the end of July.
Nielsen, 45, is a lawyer and veteran of the national security sector. She served in the transportation security unit of DHS during the George W. Bush administration, and was also Bush's homeland security advisor in the White House.
Senate confirms Kirstjen Nielsen as US Homeland Security chief
Later she ran her own security advisory firm, Sunesis Consulting.
Known for expertise in cyber issues, she was named Kelly's chief of staff when he took over DHS at the beginning of the Trump administration, and then followed him to the White House.
Described as tough and no-nonsense, she nevertheless lacks the experience of running a massive organization like the 240,000-strong DHS.
The agency oversees a wide range of security issues, from immigration, to cyber, terror threats and disaster relief.
The Senate approved her nomination 62-37.
Her confirmation came on a day when DHS reclaimed substantial success in slowing illegal immigration across the southern border and arresting and deporting criminal aliens.
DHS said arrests of illegal immigrants were up 40 percent in the first nine months of the Trump administration, while border crossings plummeted based on tougher enforcement.
Trump has also ordered DHS to build a wall along the southern border.
But both Kelly and Nielsen have said that a wall on the entire 2,000 mile (3,200 kilometer) frontier with Mexico would be inappropriate, and that other measures, including electronic monitoring, would be required as well.
Mobile Response to Security Alerts Allows Immediate Action Anywhere, Anytime
6.12.2017 securityweek Mobil
Mobile Alerts Improve Incident Response
Cybersecurity is 24/7; cybersecurity staff are not. While larger corporations can arrange for 24/7 cover, most smaller organizations cannot do this. This means that senior security staff are effectively permanently 'on call' whether they are in the office, between offices, or at home.
A recent small survey by Barkly queried 95 IT and security professionals from companies with between 50 and 1,000 endpoints, "to learn more about how they're currently receiving and managing security alerts." Nearly half of the respondents (46%) said they had missed alerts while out of the office, while about 20% said that it had been necessary to return to the office to handle an alert that could not be managed remotely.
Given these figures, it is not surprising that 76% said that their ability to respond to alerts efficiently and speedily would improve if they could both receive and respond via a mobile device.
"The ability to react quickly can be crucial," commented Barkly's Jonathan Crowe, "especially with a resurgence of worming capabilities [think WannaCry and NotPetya] making it possible for malware to spread throughout and across organizations faster than ever."
Barkly has now released a mobile version of the complete Barkly Management Portal, allowing security staff to actively respond to new alerts at any time.
"With mobile incident response Barkly empowers security leaders to view and respond to blocked attacks wherever they are, from the convenience of their phone or tablet," said Mike Duffy, CEO of Barkly, calling it a 'game-changer'.
Josh Holmes, IT Director of Pennington Law agrees: "When an alert comes in, I need to quickly understand what Barkly blocked and what next actions to take. The ability to receive and immediately respond to alerts from my phone is invaluable."
Barkly's endpoint protection SaaS technology combines both supervised and unsupervised machine learning to continuously 'disambiguate' good and bad behavior -- rapidly detecting old-style malware file attacks and newer fileless attacks. "You cannot claim to do endpoint protection unless you can stop both file-based and fileless attacks before they get through and harm the client," Barkly CTO Jack Danahy told SecurityWeek. "A fileless attack is ten times more likely to succeed than a file-based attack."
The new mobile portal isn't simply the ability to access a cloud-based control panel via a mobile browser. "With this release, we completely re-architected and redesigned our cloud-portal for mobile responsiveness," Barkly's senior product marketing manager Allison Averill told SecurityWeek. "That means when customers log in to our portal on a mobile device, they see a mobile-specific design that makes it easier to accomplish their key workflows on mobile."
Industrial Firms Slow to Adopt Cybersecurity Measures: Honeywell
6.12.2017 securityweek Cyber
Industrial companies are slow to adopt cyber security capabilities and technology to protect their data and operations, according to a report released on Wednesday by industrial giant Honeywell.
A survey of 130 strategic decision makers from around the world revealed that more than half of industrial organizations have suffered a cybersecurity incident, including ones involving removable media, denial-of-service (DoS) attacks, malware, hackers breaking into plant IT systems, state-sponsored attacks, and direct attacks on control systems.
However, the study found that organizations underinvest in cybersecurity best practices in terms of people, processes and technology – three elements that need to work in harmony for an organizational culture that takes security seriously, Honeywell said.
Forty percent of respondents said they do have a cybersecurity chief in their organization and 15 percent plan on creating the role in the future. When it comes to having someone in charge of cybersecurity for manufacturing, only 35 percent of firms surveyed by Honeywell said they have someone in this role.
As for cybersecurity processes, nearly half of organizations have an enterprise- and plant-wide IT account management policy, and 22 percent plan on implementing one within the next year. A similar percentage also has or plans on having a definitive list of connections to the plant and what data flows through them.
Only one-third of respondents said they continually monitor their systems for suspicious activity and one quarter claim they plan on implementing such measures within a year. On the other hand, roughly 70 percent of organizations conduct risk assessments at least once a year, and more than 60 percent test their firewalls at least yearly.
When it comes to adoption of cybersecurity technologies, the Honeywell study shows that many organizations still have a long way to go. A majority of companies only have a firewall between plant and business systems, and only less than one-third have implemented proper access control and authentication measures for devices in the plant.
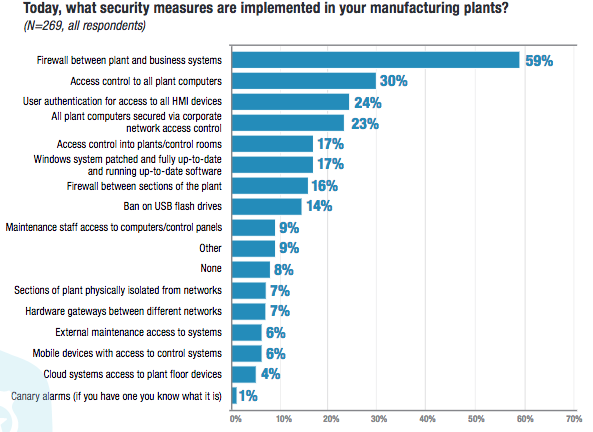
While the industrial sector is typically slower to adopt new technologies compared to other sectors, many organizations either already have an initiative for digital transformation or they plan on having one within a year. As companies move towards the adoption of the Industrial Internet of Things (IIoT), the main technology pitfall is cyber security, Honeywell said.
The company has advised organizations to ensure that cybersecurity is on the CEO’s agenda. Security needs to be part of the digital transformation strategy, and organizations must focus on adopting best practices.
Honeywell’s complete report, titled “Putting Industrial Cyber Security at the Top of the CEO Agenda,” is available for download in PDF format.
MailSploit vulnerabilities allow email spoofing with more than 30 email clients
6.12.2017 securityaffairs Vulnerebility
A security researcher discovered a collection of vulnerabilities dubbed MailSploit affecting more than 30 popular email client software.
Email spoofing is quite simple and it is an important activity in any phishing/spear phishing attack.
Attackers modify email headers and send an email with the forged sender address to trick recipients into opening the message believing they are receiving it from a trusted source.
The security researcher Sabri Haddouche has discovered a collection of vulnerabilities affecting more than 30 popular email client software that could be exploited by an attacker to send spoofed messages bypassing anti-spoofing systems.
The collection of flaws discovered by Haddouche was dubbed MailSploit, the list of vulnerable clients includes Apple Mail (macOS, iOS, and watchOS), Mozilla Thunderbird, several Microsoft email clients, Yahoo Mail, ProtonMail, and others.
It is curious to highlight that almost any affected email client has implemented anti-spoofing mechanisms, such as DKIM and DMARC.
MailSploit flaws affect the way email clients and web interfaces parse “From” header.
The expert set up a dedicated website that contains details about the set vulnerabilities.
“Mailsploit is a collection of bugs in email clients that allow effective sender spoofing and code injection attacks. The spoofing is not detected by Mail Transfer Agents (MTA) aka email servers, therefore circumventing spoofing protection mechanisms such as DMARC (DKIM/SPF) or spam filters.” reads the website.
“Bugs were found in over 30 applications, including prominent ones like Apple Mail (macOS, iOS and watchOS), Mozilla Thunderbird, various Microsoft email clients, Yahoo! Mail, ProtonMail and others.”
Haddouche explained that flaws result from the lack of input sanitization by flawed email clients, they are not related to vulnerabilities in DMARC mechanisms.
The researcher published a PoC, he used the email of the US President potus@whitehouse.gov, he explained that all headers must only contain ASCII characters, including the “From” header.
“The trick resides in using RFC-1342 (from 1992!), a recommendation that provides a way to encode non-ASCII chars inside email headers in a such way that it won’t confuse the MTAs processing the email.” continues the expert.
“Unfortunately, most email clients and web interfaces don’t properly sanitize the string after decoding which leads to this email spoofing attack.”
Haddouche created a payload by encoding non-ASCII characters inside the email headers, with this trick he was able to send a spoofed email from an official address belonging to President of the United States.
“Using a combination of control characters such as new lines or null-byte, it can result in hiding or removing the domain part of the original email,” explained Haddouche.

Below a video PoC of the attack published by the expert.
Haddouche also discovered that some of the email clients, including Hushmail, Open Mailbox, Spark, and Airmail, are affected by cross-site scripting (XSS) vulnerabilities.
The researcher reported the MailSploit flaw to 33 different client applications, in 8 cases development teams have already patched the issues before the public disclosure and 12 are currently working on patches.
It is important to highlight that Mozilla and Opera will not release any fix because classified the MailSploit as a server-side issue.
“All vendors were contacted at least 3 months prior to the publication, some of them even 4 or 5 months before the publication.” concluded the expert.
“The spoofing bug was found and confirmed in 33 different products. As of Dec 5th 2017, it was fixed in 8 products (~ 24%) and triaged for 12 additional products (~ 36%). Two vendors (Mozilla and Opera) said they won’t fix the bug (they consider it to be a server-side problem) and another one (Mailbird) closed the ticket without responding.
As for the remaining 12 products (~ 36%), the vendors have received the bug report but have not commented on whether they will address it.”
TeamViewer fixes a flaw that allows users sharing a desktop session to gain control of the other’s PC
6.12.2017 securityaffairs Vulnerebility
TeamViewer released a patch to fix a vulnerability that allows users sharing a desktop session to gain control of the other’s computer without permission.
Remote support software company TeamViewer released a patch to address a vulnerability that allows users sharing a desktop session to gain control of the other’s computer without permission.
TeamViewer confirmed the existence of the vulnerability after its public disclosure and promptly issued a patch for Windows users on Tuesday.
The flaw was first reported by the Reddit user “xpl0yt” early this week, he also linked to a proof-of-concept injectable C++ dll that uses naked inline hooking and direct memory modification to change TeamViewer permissions.
This allows a user to “enable the ‘switch sides’ feature which is normally only active after the user has already authenticated control with the client, and initiated a change of control/sides.”
The PoC was published onGitHub by a user named “gellin,” This flaw could be exploited to gain control of the presenter’s session or the viewer’s session without permission.
“As the Server – Enables extra menu item options on the right side pop-up menu. Most useful so far to enable the “switch sides” feature which is normally only active after you have already authenticated control with the client, and initiated a change of control/sides.” reads the description privided by Gellin on GitHub.
“As the Client – Allows for control of mouse with disregard to servers current control settings and permissions.”

The attacker would have to inject the PoC code into their own process with a tool such as a DLL injector.
“Once the code is injected into the process it’s programmed to modify the memory values within your own process that enables GUI elements that give you the options to switch control of the session,” Gellin told Threat Post. “Once you’ve made the request to switch controls there are no additional check on the server-side before it grants you access.”
Gellin explained that such kind of attack is easy to detect and stop by ending the session, however, gellin highlighted that before the patch was deployed, that attacker could exploit the flaw to disable a host’s visual input and force the targeted computer’s screen go black, hiding any malicious operation on the target.
The flaw affects Windows, macOS and Linux versions of the popular software. According to Axel Schmidt, senior PR manager for TeamViewer, the company will release a patch for macOS and Linux versions within Wednesday.
Users that have configured TeamViewer to accept automatic updates will get the patch automatically, however, patches could take up to three to seven days before the update is installed. Users that do not have automatic updates set will receive a notification about the availability of the update.
Such kind of flaw could be rapidly exploited by threat actors in the wild, especially by attackers carrying out malicious tech support scams.