
The authors of the Orcus RAT target Bitcoin investors
9.12.2017 securityaffairs Virus
According to Fortinet, the authors of the Orcus RAT have started targeting Bitcoin investors with their malicious software.
Crooks always follow money trying to catch any opportunity, such as the recent spike in the value of Bitcoin. According to the experts from Fortinet, the authors of the Orcus RAT have started targeting Bitcoin investors with their malicious software.
The attack chain starts with phishing messages advertising a new Bitcoin trading bot application called “Gunbot” developed by GuntherLab.
The malicious emails come with a .ZIP attachment that includes a simple VB script that acts as a downloader, the script downloads a binary masquerading as a JPEG image file.
The downloaded binary is a Trojanized version of an open source inventory system tool named TTJ-Inventory System. The malicious code uses a hardcoded key to decrypt encoded code into another .NET PE executable that is loaded and executed directly to memory.
The malicious code verifies that it is the only instance running on the infected machine checking the presence of a mutex named “dgonfUsV”.
This binary contains three embedded PE executables in its resource, including the actual Orcus RAT server.
The three embedded PE executables are:
M – Orcus RAT server
PkawjfiajsVIOefjsakoekAOEFKasoefjsa – persistence watchdog
R – RunPE module
Experts discovered a RunPE module can execute modules without writing them to the system, and can also execute them under legitimate executables by running applications in suspended mode and then replacing the process’ memory with the malicious code.
“The RunPE module is not only able to execute other modules without writing their physical files in the system, but also to execute them under legitimate executables. This is usually done by executing an application in suspended mode, and then replacing the new process’ memory with the malicious code before resuming. It’s a common stealth technique. In this case, it uses components of the Microsoft .NET framework, MSBuild.exe and RegAsm.exe, as shells to hide their malicious processes.” reads the analysis published by Fortinet.
“The module from the PkawjfiajsVIOefjsakoekAOEFKasoefjsa resource acts as a watchdog to keep the malware running by repeatedly executing it unless the client decides to stop it by dropping ”stop.txt” in its directory.”
The Orcus RAT is around since early 2016, it implements common RAT features and it is also able to load plugins and execute C# and VB.net code on the remote machine in real-time.
“Orcus has been advertised as a Remote Administration Tool (RAT) since early 2016. It has all the features that would be expected from a RAT and probably more.” continues the analysis.
“The long list of the commands is documented on their website. But what separates Orcus from the others is its capability to load custom plugins developed by users, as well as plugins that are readily available from the Orcus repository. In addition to that, users can also execute C# and VB.net code on the remote machine in real-time.”
The Orcus RAT is a powerful spyware, it can disable the light indicator on webcams to spy on the victims without raising suspicion.
The malware can also implement a watchdog that restarts the server component and If the someone tries to kill its process it can trigger a Blue Screen of Death (BSOD).
Orcus also includes a plugin that can be used to power Distributed Denial of Service (DDoS) attacks.
Fortinet warns that the actors behind the Orcus RAT implemented some changes to the malware download site. (bltcointalk.com, which attempts to imitate Bitcoin forum bitcointalk.org).
“It is obvious that the malware download site https://bltcointalk.com is trying to imitate the bitcoin forum bitcointalk.org. When accessed, the website is just an open directory containing the previously mentioned as well as an archive with the filename. Unfortunately, in the middle of writing this article, the contents of the website changed before we could download an updated copy.” state the analysis published by Fortinet.
The researchers observed several websites that attempt to clone legitimate domains by changing a single letter in the URL, the overall domains belong to a pool used by crooks for different campaigns.
“It was no surprise, therefore, that we found other domains that use similar domain names with replaced letters. When accessed, most of the sites display the “We’ll be back soon!”message, which is the same page that is displayed when “index.phptopic=3D1715214.0/” is accessed in “bltcointalk.com”.” states the analysis.
“In our investigation of Orcus RAT, we have again proven again that its capabilities go beyond the scope of a harmless administration tool. Regardless of the developer’s claim and defense, the reality is that the application is being used in cybercrime campaigns.”
Technical details, including IoC are available in the blog post published by Fortinet.
Expert discovered a Keylogger component in HP notebook keyboard driver
9.12.2017 securityaffairs Hacking
A security researcher discovered that hundreds of notebook models contain a debugging code that could be abused by attackers as a keylogger component.
Hundreds of notebook models contain a debugging code that could be abused by attackers as a keylogger component. The code was discovered by a security researcher that goes online with the moniker ZwClose, the list of affected models and security patch are available at the following URL:
https://support.hp.com/us-en/document/c05827409
The list of affected notebooks includes 475 models, 303 consumer notebooks and 172 commercial notebooks, mobile thin clients, and mobile workstations. Affected model families include HP’s 25*, mt**, 15*, OMEN, ENVY, Pavilion, Stream, ZBook, EliteBook, and ProBook series, along with several Compaq models.
ZwClose
@zwclose
Oh well. Keylogger in HP's SynTP.sys. Off by default. Vendor contacted. Fix released and pushed. Blog post is on the way.
11:28 AM - Dec 6, 2017
Replies 2 2 Retweets 5 5 likes
Twitter Ads info and privacy
HP has released security updates for its drivers in order to remove the debugging code that was present in the SynTP.sys file, which is part of the Synaptics Touchpad driver.
HP customers know that the Synaptics Touchpad driver is shipped with many HP notebook models.
“HP had a keylogger in the keyboard driver. The keylogger saved scan codes to a WPP trace. The logging was disabled by default but could be enabled by setting a registry value (UAC required). ” reads the blog post published by the expert.
That registry key is:
HKLM\Software\Synaptics\%ProductName% HKLM\Software\Synaptics\%ProductName%\Default
The Windows software trace preprocessor (WPP) technique is used by developers for debugging code.
“WPP software tracing supplements and enhances WMI event tracing by adding ways to simplify tracing the operation of the trace provider. It is an efficient mechanism for the trace provider to log real-time binary messages. The logged messages can subsequently be converted to a human-readable trace of the operation of the trace provider.” states Microsoft.

Of course, the risk is that this debugging feature could be abused by vxers to enable the keylogging feature present in the code and spy on HP users. The native code runs at kernel level and is to detectable by security software.
Malware developers only need to bypass the UAC prompt when changing the registry key, and there are many ways to do it.
HP admitted the presence of keylogging code confirming it was used for debugging purposed and accidentally and left because of a forgetfulness, for this reason, the tech giant “released an update that removes the trace.”
The researcher that uses the Twitter handles THS explained that HP did not remove the keylogger functions in the new version, the company simply turn it on by setting SeeScanCode and EnableLog = 1 in Windows Registry.

THS
@__ths__
#HP did not remove the #keylogger functions in new version. Simply turn it on by setting SeeScanCode and EnableLog = 1 in Windows Registry.
10:26 AM - May 13, 2017
22 22 Replies 662 662 Retweets 475 475 likes
Twitter Ads info and privacy
In May, the security researcher Thorsten Schroeder of security firm Modzero discovered that a Conexant audio driver shipped with many HP laptops and tablet PCs was logging keystrokes. The expert discovered that MicTray64.exe application, which is installed with the Conexant audio driver package, is registered as a scheduled task in Windows systems and is able to monitor keystrokes to determine if the user has pressed any audio-related keys (e.g. mute/unmute).
Android Janus vulnerability allows attackers to inject Malware into legitimate apps avoiding detection
9.12.2017 securityaffairs Android
Google fixed a bug dubbed Janus that could be exploited by attackers to inject malicious code into Android apps without affecting an app’s signature.
Google fixed four dozen vulnerabilities this week, including a bug dubbed Janus that could be exploited by attackers to inject malicious code into Android apps without affecting an app’s signature verification certificates.
Millions of Android devices are at risk of a cyber attack due to this flaw (CVE-2017-13156), that allows attackers to secretly overwrite legitimate applications installed on victims’ mobile devices with a malware.
The vulnerability was reported to Google by security researchers from mobile security firm GuardSquare this summer and has been fixed now as part of the December Android Security Bulletin.
The attack technique discovered by Guardsquare allows by bypass anti-malware protection mechanisms and escalate privileges on targeted devices using signed apps that appear to be from trusted publishers.
“A serious vulnerability (CVE-2017-13156) in Android allows attackers to modify the code in applications without affecting their signatures. The root of the problem is that a file can be a valid APK file and a valid DEX file at the same time. We have named it the Janus vulnerability, after the Roman god of duality.” states the analysis published by Guardsquare.
The vulnerability affects in the way Android handles APK installation for some apps, allowing to add extra bytes of code to an APK file without modifying the app’s signature.
An APK file is an archive, just like Zip, that includes application code, resources, assets, signatures, certificates, and manifest file.
Earlier versions of Android (5.0 Lollipop and Marshmallow 6.0) also support a process virtual machine that helps to execute APK archives containing a compiled version of application code and files, compressed with DEX (Dalvik EXecutable) file format.
While installing an app, the OS checks APK header information to determine if the archive contains code in the compressed DEX files. If the APK archive contains DEX files, the process virtual machine decompiles the code accordingly and executes it; otherwise, it runs the code as a regular APK file.
It turns out that an APK archive can contain DEX files as well as regular application code simultaneously, without affecting its validity and signatures.Researchers discovered that it is possible to add extra bytes of code to the archive due to lack of file integrity checking.
“The Janus vulnerability stems from the possibility to add extra bytes to APK files and to DEX files. On the one hand, an APK file is a zip archive, which can contain arbitrary bytes at the start, before its zip entries (actually more generally, between its zip entries). The JAR signature scheme only takes into account the zip entries. It ignores any extra bytes when computing or verifying the application’s signature.” continue the analysis.
“On the other hand, a DEX file can contain arbitrary bytes at the end, after the regular sections of strings, classes, method definitions, etc. A file can, therefore, be a valid APK file and a valid DEX file at the same time.”

Attackers can prepend malicious code compiled in DEX format into an APK archive containing legitimate code with valid signatures, tricking app installation process to execute both codes on the device avoid detection.
The researchers developed a simple tool to create Janus applications as a proof of concept, the good news is that according to the experts, at this time, there are similar applications in the wild.
The Janus tool allows an attacker to inject an APK file with a malicious DEX (Dalvik Executable) file. DEX files make up the code inside Android programs that are zipped into single APKs.
The researchers described also possible attack scenarios, for example, an attacker can replace a trusted application with high privileges (i.e. a system app) by a modified update to abuse its permissions. Another attack scenario sees a hacker passing a modified clone of a sensitive application as a legitimate update, for instance in the context of banking or communications.
Android versions older than Nougat (7.0) and any Android devices that support the APK signature scheme v1 are affected by the Janus vulnerability.
The Android devices updated to support APK signature scheme v2, introduced in July 2016, are not impacted.
Unfortunately, most of Android users would not receive these patches for the next month, until their device manufacturers (OEMs) release custom updates for them.
Onapsis Helps SAP Customers Check GDPR Compliance
9.12.2017 securityweek Privacy
Onapsis, a company that specializes in securing SAP and Oracle business-critical applications, announced this week that it has added automated GDPR compliance capabilities to the Onapsis Security Platform.
The new functionality allows organizations using SAP products to quickly determine if they meet data protection requirements. The system is capable of identifying SAP systems that need to be compliant with the General Data Protection Regulation (GDPR), specifically systems that process or store user data. Onapsis believes a majority of SAP systems fall into this category.
Non-compliant systems are flagged by the Onapsis Security Platform and users are provided guidance on how to address the issue. Newly added systems that need to be GDPR compliant are automatically included in the next audit.
“In speaking to our customers, we know that GDPR is a complicated mandate and many organizations are struggling to determine if or how their SAP landscapes are relevant,” said Alex Horan, Director of Product Management at Onapsis. “With this in mind, Onapsis’s newly released audit policy within the Onapsis Security Platform (OSP) automatically evaluates any SAP system through the lens of the data protection requirements of GDPR. This includes both data at rest, data in transit and the assessment of data access or authorizations.”
GDPR, expected to come into effect in May 2018, requires businesses to protect the personal data and privacy of EU citizens. While the regulation is designed to protect the data of EU citizens, it affects organizations worldwide. Failure to comply can result in penalties of up to €20 million or 4% of global profit.
A study conducted earlier this year by the UK & Ireland SAP User Group showed that 86% of SAP customers did not fully understand the implications of GDPR. More than half of respondents said the increasing use of cloud technology and workforce mobility increased their compliance challenges.
SAP recommends its GRC (Governance, Risk, Compliance) solutions for ensuring GDPR compliance, and nearly half of the respondents taking part in the SAP User Group study had been leveraging SAP GRC. Many of those who had not used it believed GRC was either too expensive or too complicated.
IT Security Spending to Reach $96 Billion in 2018: Gartner
9.12.2017 securityweek IT
Gartner is predicting that worldwide security spend will reach $96 billion dollars in 2018. This is up 8% from the 2017 spend of $89 billion. Interestingly, the latest 2017 and 2018 figures show substantial increases over similar predictions made in August of this year. The earlier prediction has 2017 figures at $86.4 billion with 2018 figures at $93 billion.
Gartner suggests that organizations are spending more on security as a result of regulations, shifting buyer mindset, awareness of emerging threats and the evolution to a digital business strategy.
"Overall, a large portion of security spending is driven by an organization's reaction toward security breaches as more high profile cyberattacks and data breaches affect organizations worldwide," said Ruggero Contu, research director at Gartner. "Cyberattacks such as WannaCry and NotPetya, and most recently the Equifax breach, have a direct effect on security spend, because these types of attacks last up to three years."
A 2016 survey -- that questioned 512 respondents from eight countries: Australia, Canada, France, Germany, India, Singapore, the U.K. and the U.S. -- showed a direct link between security risks and security spend. Gartner believes that the breaches of 2017 will influence the spend in 2018. "As a result," it suggests, "security testing, IT outsourcing and security information and event management (SIEM) will be among the fastest-growing security subsegments driving growth in the infrastructure protection and security services segments."
This is likely to be bolstered by the effect of compliance concern. Regulations are increasing in number, scope, and the size of sanctions; and are getting personal. Europe's General Data Protection Regulation (GDPR) coming into effect in May 2018 can impose fines of up to 4% of global turnover. In the U.S., the newly introduced Data Security and Breach Notification Act proposes jail terms of up to five years for those who fail to comply. As the effect of these regulations on individual business leaders as well as the company filter through -- which can no longer be satisfied by a simple tick-box approach to security -- there is likely to be a knee-jerk reaction leading to increased security spend.
Some of this effect can be discounted. "Regulatory compliance and data privacy have been stimulating spending on security during the past three years, in the US (with regulations such as the Health Insurance Portability and Accountability Act, National Institute of Standards and Technology, and Overseas Citizenship of India) but most recently in Europe around the General Data Protection Regulation coming into force on 28th May 2018, as well as in China with the Cybersecurity Law that came into effect in June 2016. These regulations translate into increased spending, particularly in data security tools, privileged access management and SIEM."
However, since numerous surveys and analyses have demonstrated that many firms simply do not understand GDPR, are still far from being ready for GDPR, or don't (yet) believe it applies to them, there is likely to be sudden increased spending following the first legal actions against non-compliance. Any belief that European regulators might allow a 'bedding in' period should not be taken for granted.
At the end of November, three European activists (Max Schrems, whose action against Facebook ultimately led to the collapse of the EU/US Safe Harbor agreement; Paul Nemitz, director for fundamental rights and Union citizenship in the European Commission's Directorate-General for Justice; and Jan Philippe Albrecht, justice and home affairs spokesperson of the European Greens and the rapporteur for the GDPR) got together to announce 'NOYB [none of your business] -- European Center for Digital Rights'.
The purpose of NOYB is to close the gap between the public perception of privacy and the reality of corporate practice, including bringing cases to court. Since these are activists rather than regulators, they are likely to take private action where regulators may hesitate. In its August prediction, Gartner commented, "The EU General Data Protection Regulation (GDPR) has created renewed interest, and will drive 65 percent of data loss prevention buying decisions today through 2018." This could prove to be a conservative estimate.
Skills shortages, technical complexity and the threat landscape will continue to drive the move to automation and outsourcing, says Gartner. "Skill sets are scarce and therefore remain at a premium, leading organizations to seek external help from security consultants, managed security service providers and outsourcers," said Contu. "In 2018, spending on security outsourcing services will total $18.5 billion, an 11% increase from 2017. The IT outsourcing segment is the second-largest security spending segment after consulting."
This migration to service providers and outsourcers leads Gartner to predict that by 2019, total enterprise spending on security outsourcing services will be 75% of the spending on security software and hardware products, up from 63% in 2016.
"For the most part, I agree with Gartner's assessment that spending is likely to continue to grow overall in 2018," Nathan Wenzler, chief security strategist at AsTech, told SecurityWeek; "especially in identifying that the overall skills shortage will ultimately drive more companies to spend more in security services."
He believes that companies are "reaching something of a saturation point for security software, as they've been spending for the last several years to buy products that can protect their environments in different ways." But they don't have and cannot get "experienced security professionals who can deploy, use and maintain those products effectively in order to put the tools to work. Organizations will have little choice but to shift their spending to services in order to secure their networks and protect critical data."
But is 'more spending' necessarily 'better security'? Ilia Kolochenko, CEO of High-Tech Bridge, warns that it isn't necessarily so. He believes that a more coherent risk-based security approach could lead to improved security without necessarily increasing spend. "Many companies can even reduce their current budgets by implementing a risk-based approach to mitigate appropriate threats and vulnerabilities; and by rigorously selecting vendors based on technology and not marketing claims."
#OpUSA – OpIsrael – Anonymous hit Israel and threatens cyberattack on US Govt
9.12.2017 securityaffairs BigBrothers
#OpUSA – OpIsrael – The hacker collective Anonymous threatens cyber attacks on US Government and launched the offensive against the Israeli targets.
In the last hours, the hacktivists leaked online names, emails, and passwords of Israeli public employees and shared a list of US government sites to target, calling on action against them.
Anonymous leaked data belonging to only a handful of the sites, this is the retaliation of the collective against the US Government for its politics in the Middle East.
Anonymous operation aims to protect Palestine and protest against Donald Trump’s choice to recognize Jerusalem as the capital of Israel.
Below the message published on the blog of the website cyberguerilla.com:
“Anonymous OpUSA – OpIsrael: Israeli Gov’t hacked and dumped. Download link!
This Hack is part of the Operation US + Israel. #OpUSA – OpIsrael
The end of 2017 #Anonymous
Operation: https://pastebin.com/tgbkCQ61
Israel Gov’t hacked and dumped.
Download dump: https://mega.nz/#!ZWByDAbT
Decryption Key: !-Yvx4-wlzWEV5gagusHKcDF4eYeABfJxgDh_foO-D20
“Government of Israel and United State, our patience is exhausted!
No more words! Now only acts.
Anonymous can’t be silent when we see your actions.
Now its Anonymous time.“
We Are Anonymous,
We Are Legion,
We do not forgive,
We do not forget
Government of USA and Israel,
Expect us.“
Anonymous is calling for action against websites included in the United State and Israel Government Target list, the collective is inviting its members to hit in any way (i.e. Data Dump, Government Breach, Defacing, DDoSing ) these sites:
https://www.usa.gov/ = USA
https://www.gov.il/ = Israel
https://www.state.gov/ = USA
http://www.president.gov.il/ = Israel
https://www.whitehouse.gov/ = USA
http://itrade.gov.il/ = Israel
https://www.ssa.gov/ = USA
http://www.investinisrael.gov.il/ = Israel
https://www.data.gov/ = USA
http://www.antitrust.gov.il/ = Israel
https://www.irs.gov/ = USA
http://www.boi.org.il/en/ = Israel
https://www.federalreserve.gov/ = USA
http://www.space.gov.il/ = Israel
https://www.shabak.gov.il/ = Israel
The hackers aim to spread the #OpUSA and #OpIsrael by defacing any .us and .il domains, it is using the hashtags #OpUSA, #OpIsrael and #FreedomInWorld to make easy for sympathizers to see all the Anonymous posts on social media.

Anonymous shared the code for the main deface page for OpUSA – OpIsrael here: https://ghostbin.com/paste/o3o88
Anonymous OpIsrael Israeli-US-hacking-2

The dump leaked by Anonymous is circulating online, it is a huge trove of data apparently containing the names and email addresses of government employees and alleged Mossad agents.
More news about the campaign is expected to be published on the Cyberguerrilla website.
Orcus RAT Campaign Targets Bitcoin Investors
8.12.2017 securityweek Virus
In an attempt to benefit from the recent spike in the value of Bitcoin, the authors of a remote access Trojan have started targeting Bitcoin investors with their malicious software, Fortinet has discovered.
The attack starts with phishing emails marketing a relatively new Bitcoin trading bot application called "Gunbot" developed by GuntherLab or Gunthy. However, the email actually delivers the Orcus RAT to the Bitcoin investors instead.
The phishing emails contain a .ZIP attachment that includes a simple VB script designed to download a binary masquerading as a JPEG image file. According to Fortinet, the attackers made no attempt in hiding their intentions, either because they didn’t want to or because they lack the technical knowledge to do so.
The downloaded executable is a Trojanized version of an open source inventory system tool named TTJ-Inventory System. A hardcoded key is used to decrypt encoded code into another .NET PE executable that is loaded and executed directly to memory.
The malware ensures it is the only instance running on the infected machine by checking for the existence of a mutex named “dgonfUsV”.
Fortinet has discovered that a RunPE module can execute modules without writing them to the system, and can also execute them under legitimate executables by running applications in suspended mode and then replacing the process’ memory with the malicious code. The persistence watchdog keeps the malware running by repeatedly executing it.
Advertised as a Remote Administration Tool since early 2016, Orcus has all the features such an application should include, but can also load plugins and can execute C# and VB.net code on the remote machine in real-time.
“Basically, if a server component gets ‘installed’ to your system, the person on the other side is practically in front of your machine while seeing and hearing you at the same time – yes, it can activate your microphone and webcam even without you knowing,” Fortinet notes.
The threat can also disable the light indicator on webcams, meaning that it can be used to spy on users, can implement a watchdog that restarts the server component and can also trigger a Blue Screen of Death (BSOD) if the user attempts to kill its process.
The malware also includes password retrieval and key logging functionality, the same as other RATs out there. Orcus also offers a plugin that can be used to perform Distributed Denial of Service (DDoS) attacks.
During their analysis, the security researchers also noticed that the actors behind the attack made some changes to the contents of the site distributing the malware (bltcointalk.com, which attempts to imitate Bitcoin forum bitcointalk.org). They also removed the aforementioned image file from the site and posted a ZIP file instead.
Fortinet's security researchers also discovered additional websites that attempt to imitate legitimate domains by changing a single letter in the URL. Thus, they believe that the actor cycles between the websites when switching to a new campaign.
“In our investigation of Orcus RAT, we have again proven again that its capabilities go beyond the scope of a harmless administration tool. Regardless of the developer’s claim and defense, the reality is that the application is being used in cybercrime campaigns,” Fortinet concludes.
NIST Publishes Second Draft of Cybersecurity Framework
8.12.2017 securityweek Safety
Framework for Improving Critical Infrastructure Cybersecurity 2.0
The National Institute of Standards and Technology (NIST) announced this week that it has published a second draft of a proposed update to the “Framework for Improving Critical Infrastructure Cybersecurity,” better known as the NIST Cybersecurity Framework.
Introduced in 2014, the framework is designed to help organizations, particularly ones in the critical infrastructure sector, manage cybersecurity risks. Some security firms and experts advise businesses to use the NIST Cybersecurity Framework as a best practice guide. Others, however, believe such static guidelines cannot keep up with the constantly evolving threat landscape, and malicious actors may even use it to devise their attack strategy.NIST updates Cybersecurity Framework
The Cybersecurity Framework was developed based on an executive order issued by former U.S. president Barack Obama. A cybersecurity executive order issued by the current administration of Donald Trump also requires federal agencies and critical infrastructure operators to use the framework.
Nearly four years have passed since the Cybersecurity Framework was released and NIST is now working on an updated version. A first draft was released in January and a second draft was made available on December 5.
According to NIST, the second draft for version 1.1 of the Cybersecurity Framework “focuses on clarifying, refining, and enhancing the Framework – amplifying its value and making it easier to use.”
The second draft also comes with an updated roadmap that details plans for advancing the framework’s development process.
The modifications are based on 120 comments submitted in response to the first draft and discussions between 500 individuals who attended a workshop back in May.
Comments and feedback on the second Cybersecurity Framework draft can be sent to NIST (cyberframework(at)nist.gov) until January 19, 2018. The organization has fallen behind on the development of the updated framework – it had initially anticipated that the final V1.1 would be published this fall, but it now hopes to have it done in “early calendar year 2018.”
NIST is particularly interested in learning if the revisions in version 1.1 reflect the changes in the current cybersecurity ecosystem, and the impact of the updated version on organizations currently using version 1.0 of the framework.
Microsoft Patches Critical Vulnerability in Malware Protection Engine
8.12.2017 securityweek Vulnerebility
Microsoft this week released an update for the Microsoft Malware Protection Engine (MPE) to address a critical severity remote code execution (RCE) vulnerability in it.
The flaw could lead to memory corruption and allow an attacker to execute arbitrary code to take control over a vulnerable machine. Discovered by UK's National Cyber Security Centre (NCSC), the bug is tracked as CVE-2017-11937.
Because code can be executed in the security context of the LocalSystem account, the attacker could take control of the system and install programs; view, change, or delete data; or create new accounts with full user rights.
Exploitation is possible if a specially crafted file is scanned by an affected version of the Microsoft Malware Protection Engine (the last vulnerable version is 1.1.14306.0).
There are multiple ways an actor could launch an attack leveraging the bug, Microsoft says. An attacker could lure the victim to a website containing the specially crafted file, or they could send the malicious file via email or instant messaging. They could also load the file to a site that accepts or hosts user-provided content, in a shared location.
“If the affected antimalware software has real-time protection turned on, the Microsoft Malware Protection Engine will scan files automatically, leading to exploitation of the vulnerability when the specially crafted file is scanned. If real-time scanning is not enabled, the attacker would need to wait until a scheduled scan occurs in order for the vulnerability to be exploited,” Microsoft explained.
The software giant also notes that all systems running an affected version of antimalware software are primarily at risk.
The company has issued an update to correct the manner in which the Microsoft Malware Protection Engine scans specially crafted files.
The update will be delivered automatically to the affected systems and no action is required of enterprise administrators or end users. The update should reach all impacted software within 48 hours of release.
Impacted applications include Microsoft Forefront and Microsoft Defender on Windows 7 SP1, Windows 8.1, Windows RT 8.1, Windows 10 Gold, 1511, 1607, and 1703, 1709 and Windows Server 2016, Windows Server version 1709, Microsoft Exchange Server 2013 and 2016, Microsoft Security Essentials, and Windows Intune Endpoint Protection.
Microsoft Malware Protection Engine version 1.1.14405.2 resolves the vulnerability.
The Indian Intelligence warns China is spying through 42 mobile apps
8.12.2017 securityaffairs BigBrothers
The Indian Intelligence warns China is spying its troops through 42 mobile apps, for this reason, the Intelligence Bureau asked soldiers to delete them.
The Indian Intelligence Bureau (IB) has warned that Chinese cyber spies are collecting confidential information about the Indian security installations through its popular mobile phone apps and devices.
The Intelligence Bureau issued an advisory to the troops posted at the international border.

Many Indian cybersecurity experts have raised concerns about the possible espionage attempts by the Chinese military intelligence agencies.
“According to reports, the advisory issued by the DIG (Intelligence) has directed the troops posted along the Line of Actual Control (LAC) to either delete a number of mobile applications from their smartphones or reformat the devices altogether to guard against online espionage attempts from across the border.” reported the website Zeenews.india.com.
The advisory includes a list of about 42 popular Chinese mobile apps, including WeChat, Truecaller, Weibo, UC Browser and UC News, that according to the Indian intelligence pose a serious threat to the security of the state.
The Indian intelligence suspect that these apps transmitting sensitive personal data to the Chinese Government.
The fresh advisory was issued while the troops from both sides continue to maintain high alertness levels along the LAC.
The intelligence agencies regularly warn the armed forces to avoid using Chinese apps to avoid the leakage of confidential information to a hostile state like China.
The IAF, for example, suggested its staff and their families to avoid using Chinese Xiaomi smartphones.
“The Army, as well as the central armed police forces like the Indo-Tibetan Border Police, are deployed along the 4,057km LAC, which stretches from Ladakh to Arunachal Pradesh.” continues the Zee Media Bureau.
“The IAF, for instance, had earlier asked all its officers and airmen as well as their families to avoid using Chinese Xiaomi smartphones and notebooks on the ground that they could transfer user data to remote servers located in China.”
The warning from IB is related to Chinese mobile apps for both Android and IoS OSs.
Hackerem, který Uberu ukradl data, byl dvacetiletý mladík z Floridy
8.12.2017 Idnes.cz Kriminalita
Za masivní únik dat společnosti Uber v říjnu 2016 byl zodpovědný dvacetiletý mladík z Floridy. Společnost mu zaplatila za to, že ukradené informace následně zničil. Snaha incident utajit stála Uber sto tisíc dolarů (přes dva miliony Kč). Nakonec však firma sama o průšvihu promluvila.
V listopadu oznámila společnost Uber, že jí v říjnu 2016 byla odcizeny data celkem 57 milionů zákazníků, která obsahovala jejich jména, adresy, telefonní čísla a e-mailové adresy.
Součástí přiznání alternativní taxislužby byla i jedna zajímavá skutečnost. Hacker, který informace ukradl, dostal zaplaceno 100 000 dolarů (téměr 2,2 milionu korun), aby svou kořist zničil, a celý incident tak zůstal v tajnosti.
Avšak detaily o hackerovi, ani o způsobu vyplacení těchto peněz firma neposkytla. Až nyní podrobnosti zjistila agentura Reuters. Tři lidé spojeni s touto aférou potvrdili agentuře, že šlo o dvacetiletého muže z Floridy, který dostal zaplaceno prostřednictvím programu „bug bounty“ (odměna za chybu), jenž se normálně využívá pro odhalení menších slabin v kódu.
Tento program je primárně určen pro bezpečnostní analytiky, kteří jsou odměňovaní za odhalené chyby ve firemním softwaru, uvedly pro Reuters tři zmiňované zdroje. Agentuře se ale nepodařilo zjistit identitu dotyčného hackera.
Nový generální ředitel Uberu Dara Khosrowshahi uvedl v prohlášení o úniku dat, že propustil dva vysoce postavené zaměstnance bezpečnostního oddělení, kteří tento incident v říjnu 2016 řešili.
Není jasné, kdo udělal konečné rozhodnutí v otázce výkupného hackerovi, aby únik dat zůstal utajený, ale zdroje citované agenturou Reuters potvrzují, že tehdejší generální ředitel Travis Kalanick o incidentu a následné platbě hackerovi věděl.
Security Flaw Left Major Banking Apps Vulnerable to MiTM Attacks Over SSL
8.12.2017 thehackernews Vulnerebility
A team of security researchers has discovered a critical implementation flaw in major mobile banking applications that left banking credentials of millions of users vulnerable to hackers.
The vulnerability was discovered by researchers of the Security and Privacy Group at the University of Birmingham, who tested hundreds of different banking apps—both iOS and Android—and found that several of them were affected by a common issue, leaving their users vulnerable to man-in-the-middle attacks.
The affected banking apps include HSBC, NatWest, Co-op, Santander, and Allied Irish bank, which have now been updated after researchers reported them of the issue.
According to a research paper [PDF] published by researchers, vulnerable applications could have allowed an attacker, connected to the same network as the victim, to intercept SSL connection and retrieve the user's banking credentials, like usernames and passwords/pincodes—even if the apps are using SSL pinning feature.
SSL pinning is a security feature that prevents man-in-the-middle (MITM) attacks by enabling an additional layer of trust between the listed hosts and devices.
When implemented, SSL pinning helps to neutralize network-based attacks wherein attackers could attempt to use valid certificates issued by rogue certification authorities.
"If a single CA acted maliciously or were compromised, which has happened before, valid certificates for any domain could be generated allowing an attacker to Man-in-the-Middle all apps trusting that CA certificate," the researchers wrote in their paper.
However, there are two key parts to verify an SSL connection—the first (authentication) is to verify whether the certificate is from a trusted source and the second (authorization) is to make sure the server you are connecting to presents the right certificate.
Researchers found that due to lack of hostname verification, several banking applications were not checking if they connected to a trusted source.
Verifying a hostname ensures the hostname in the URL to which the banking app connects matches the hostname in the digital certificate that the server sends back as part of the SSL connection.
"TLS misconfiguration vulnerabilities are clearly common; however none of the existing frameworks will detect that a client pins a root or intermediate certificate, but fails to check the hostname in the leaf," the paper reads.
Besides this issue, the researchers also detailed an "in-app phishing attack" affecting Santander and Allied Irish Banks, which could have allowed attackers to hijack part of the victim's screen while the app was running and use it to phish for the victim's login credentials.
To test this vulnerability in hundreds of banking apps quickly and without requiring to purchase certificates, researchers created a new automated tool, dubbed Spinner.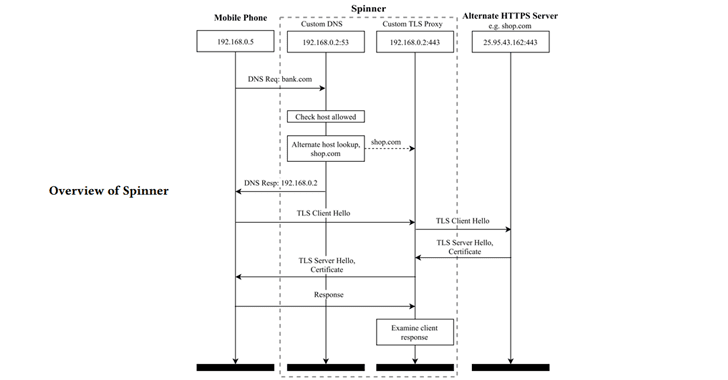
Spinner leverages Censys IoT search engine for finding certificate chains for alternate hosts that only differ in the leaf certificate.
"Given the certificate for a target domain, the tool queries for certificate chains for alternate hosts that only differ in the leaf certificate. The tool then redirects the traffic from the app under test to a website which has a certificate signed by the same CA certificate, but of course a different hostname (Common Name)," the researchers explain.
"If the connection fails during the establishment phase then we know the app detected the wrong hostname. Whereas, if the connection is established and encrypted application data is transferred by the client before the connection fails then we know the app has accepted the hostname and is vulnerable."
The trio, Chris McMahon Stone, Tom Chothia, and Flavio D. Garcia, worked with the National Cyber Security Centre (NCSC) to notify all affected banks, which then resolved the issues before they publicly disclosed their research this week.
Microsoft Issues Emergency Windows Security Update For A Critical Vulnerability
8.12.2017 thehackernews Vulnerebility
If your computer is running Microsoft's Windows operating system, then you need to apply this emergency patch immediately. By immediately, I mean now!
Microsoft has just released an emergency security patch to address a critical remote code execution (RCE) vulnerability in its Malware Protection Engine (MPE) that could allow an attacker to take full control of a victim's PC.
Enabled by default, Microsoft Malware Protection Engine offers the core cybersecurity capabilities, like scanning, detection, and cleaning, for the company's antivirus and antimalware programs in all of its products.
According to Microsoft, the vulnerability affects a large number of Microsoft security products, including Windows Defender and Microsoft Security Essentials along with Endpoint Protection, Forefront Endpoint Protection, and Exchange Server 2013 and 2016, impacting Windows 7, Windows 8.1, Windows 10, Windows RT 8.1, and Windows Server.
Tracked as CVE-2017-11937, the vulnerability is a memory corruption issue which is triggered when the Malware Protection Engine scans a specially crafted file to check for any potential threat.
Flaw Lets Hackers Take Full Control of Your Computer
Successful exploitation of the flaw could allow a remote attacker to execute malicious code in the security context of the LocalSystem account and take control of the target's computer.
Microsoft said an attacker could place a specially crafted malicious file in a location that is scanned by the Malware Protection Engine to exploit the memory corruption flaw which eventually leads to remote code execution.
"There are many ways that an attacker could place a specially crafted file in a location that is scanned by the Microsoft Malware Protection Engine. For example, an attacker could use a website to deliver a specially crafted file to the victim's system that is scanned when the website is viewed by the user," the report from Microsoft explained.
Other ways to deliver a specially crafted file could be via emails or Instant Messenger services. The attacker could also "take advantage of websites that accept or host user-provided content, to upload a specially crafted file to a shared location that is scanned by the Malware Protection Engine running on the hosting server," the report said.
Patch! Patch! Patch!
Microsoft assured its customers that the vulnerability was fixed before any misuses in the wild.
The company has released an out-of-band critical update for the flaw and advised users to install it as soon as possible. Most home users and many enterprise customers will get the emergency patch automatically over the air.
The security vulnerability was discovered and reported to Microsoft by the UK's National Cyber Security Centre (NCSC), a cyber defense organization of Britain's signals intelligence and cybersecurity agency, known as GCHQ.
The emergency fix comes just days before Microsoft is scheduled to roll out its December Patch Tuesday updates.
Rockwell Automation Patches Serious Flaw in FactoryTalk Product
8.12.2017 securityweek Vulnerebility
ICS-CERT informed organizations this week that Rockwell Automation has patched a high severity denial-of-service (DoS) vulnerability in one of its FactoryTalk products.
The vulnerability affects version 2.90 and earlier of FactoryTalk Alarms and Events (FTAE), a FactoryTalk Services Platform component installed by the Studio 5000 Logix Designer PLC programming and configuration tool, and the FactoryTalk View SE HMI software.
FTAE provides a consistent view of alarms and events via a View SE HMI system. The product is used worldwide in sectors such as critical infrastructure, entertainment, automotive, food and beverage, and water and wastewater.
The security hole, reported to Rockwell Automation by an unnamed company in the oil and gas sector, is tracked as CVE-2017-14022 and it has been assigned a CVSS score of 7.5. It allows an unauthenticated attacker with remote access to the product to cause its history archiver service to stall or terminate by sending specially crafted packets to TCP port 403.
“The history archiver service of FactoryTalk Alarms and Events is used to archive alarms and events to a Microsoft SQL Server database. Disrupting this capability can result in a loss of information, the criticality of which depends on the type of environment that the product is used in. The service must be restarted in order to restore operation,” Rockwell Automation said in an advisory published last month.
The vulnerability was addressed with the release of a patch for FactoryTalk Alarms and Events 2.90. Users of version 2.81 and earlier have been advised to update to version 2.90 and then apply the patch.
Alternatively, attacks can be mitigated by disabling TCP port 403. This port is typically used to log alarms and events via the historian service to a specified SQL Server database. However, if the historian and the FTAE services are on the same machine, port 403 is not needed as the information is logged to the local host. If the two services are on different machines, port 403 is needed and the mitigation cannot be applied.