
Database of 1.4 Billion Credentials Found on Dark Web
11.12.2017 securityweek Incindent
Researchers have found a database of 1.4 billion clear text credentials in what appears to be the single largest aggregate database yet found on the dark web. These are not from a new breach, but a compilation of 252 previous breaches, including the previous largest combo list, Exploit.in.
The database was found by 4iQ on 5 December 2017. Announcing the discovery, the firm's founder and CTO Julio Casal, said, "This is not just a list. It is an aggregated, interactive database that allows for fast (one second response) searches and new breach imports... The database was recently updated with the last set of data inserted on 11/29/2017. The total amount of credentials (usernames/clear text password pairs) is 1,400,553,869."
It is a database designed to be used. It includes search tools and insert scripts explained in a README file. Another file called 'imported.log' lists the breach sources; for example '/inputbreach/linkedin110M_1 865M'. There are four such LinkedIn input files, in a total of 256 inputs.
The data is structured in an alphabetic directory tree fragmented in 1,981 pieces to allow fast searches. In a test, 4iQ notes, "searching for 'admin,' 'administrator' and 'root' returned 226,631 passwords of admin users in a few seconds." The combination of database structure and clear text credentials makes it an easy tool for bad actors to use for bad purposes. "Now even unsophisticated and newbie hackers can access the largest trove ever of sensitive credentials in an underground community forum," comments Casal. "Is the cyber crime epidemic about become exponentially worse?"
The raw data has probably been available to criminals on the dark web from soon after many of the breaches -- but this new database takes out much of the labor needed to use the stolen credentials.
"Large databases of passwords containing both hashed and clear text have been available for years, that are easy to download to use with password cracking software," Joe Carson, chief security scientist at password protection firm Thycotic, told SecurityWeek. "These password databases are available to both skilled hackers and script kiddies with basic knowledge that can be easily used with software that is easily downloadable from the internet. Today all you need is a computer and an internet connection to be a hacker."
But use of these databases still required effort. "In the past hackers would have accessed each breached database containing passwords, and correlated them on their own," he added; "but why do that when someone will do it for you and make it easy downloadable?"
Freelance security consultant and researcher Robin Wood (aka DigiNinja, author of the widely used Pipal password analyzer), explains how the database could be used by bad actors. "The most obvious," he says, "is to take large chunks of the files and spray them against popular sites to see which still work." This is basic 'credential stuffing'.
Carson notes that "previous research has found that at least 25 percent of leaked google passwords are still active and still work, which means that many people still fail to change their passwords even after a major data breach has occurred." The implication is that credential stuffing from this new database could prove very effective for the hackers.
Wood adds, "[The announcement] doesn't say whether the [discovery] lists which individual dump the creds came from, although it does say which sources were used to create the list; so that is a good list of targets to start with."
However, he also warns that the searchable nature of this database gives additional concerns. "It can also be used for more targeted attacks. Pick your target company and search for references to it in the list to find staff, contractors or suppliers. This could give both an initial foothold into the company, or -- if someone is already in -- to help move around if credentials have been reused internally."
What isn't clear is where this database has come from, nor why it has suddenly appeared on the dark web. Clearly, considerable time and effort has gone into its design and creation to make it large scale and easy to use; but it doesn't appear to have a direct monetization methodology for now. "There is not [sic] indication of the author of the database and tools," writes Casal, "although Bitcoin and Dogecoin wallets are included for donation." Of course, the author could be intending to 'charge' for future maintenance of the database with new additions as they become available.
"My first thought," comments Wood, "was whether this is the database that was behind the recently shut down LeakedBase site." LeakedBase was an online service that provided paid access to leaked credentials. It was shut down just days before 4iQ made its discovery. "Their database," continued Wood, "gave out clear text passwords, so it could be the same. Maybe the owners decided it was too risky running a site giving access to the creds but wanted to drop it out there and try to make some money off donations instead."
Whatever the reasons behind this database, its availability on the dark web provides an additional threat to users who don't change their passwords. "It is clear that people do not even change passwords after a major data breach," says Carson. "It is also poor hygiene that the companies impacted by these data breaches still do not force a password reset leaving many of their customers' accounts exposed and vulnerable to abuse by cybercriminals."
Dormant Keylogging Functionality Found in HP Laptops
11.12.2017 securityweek Hacking
A researcher has discovered that a touchpad driver present on hundreds of HP laptops includes functionality that can be abused for logging keystrokes. The vendor has released patches for a vast majority of affected devices.
Michael Myng was looking for ways to control the keyboard backlight functionality on HP laptops when he noticed that the driver from Synaptics (SynTP.sys) included keylogging functionality.
The problematic code is apparently part of a debugger implemented through the Windows software trace preprocessor (WPP). The feature is disabled by default, but a user with administrator privileges can enabled it by changing a value in the Windows registry, allowing them to log keystrokes to a local file.
Myng informed HP of his findings and the company released updates that remove the problematic debugging functionality for nearly all impacted products. However, devices from other vendors that use this Synaptics driver could be affected as well.
“A potential security vulnerability has been identified with certain versions of Synaptics touchpad drivers that impacts all Synaptics OEM partners,” HP said in its advisory. “A party would need administrative privileges in order to take advantage of the vulnerability. Neither Synaptics nor HP has access to customer data as a result of this issue.”
The vulnerability, classified by the vendor as “medium severity,” impacts more than 460 laptop models, including many EliteBook, mt, ProBook, Spectre Pro, Stream, ZBook, Envy, Pavilion, Split and Omen devices.
Some people have pointed out that an attacker who has the privileges required to activate the keylogger functionality could do anything on the system, including install a proper keylogger, and would not need to exploit this vulnerability. Others, however, believe it could still be useful for malicious actors since the keylogging mechanism is already in place.
This is not the first time keylogging functionality has been found in software shipped with HP laptops. Back in May, researchers discovered that a Conexant audio driver installed on some HP laptops had been logging keystrokes to a file.
MoneyTaker group: Group-IB uncovered a cyber gang attacking banks in the USA and Russia
11.12.2017 securityaffairs CyberCrime
Group-IB spotted the operations of a Russian-speaking cyber gang tracked as MoneyTaker group that stole as much as $10 million from US and Russian banks.
Researchers from security firm Group-IB has spotted the operations of a Russian-speaking cyber gang tracked as MoneyTaker that has stolen as much as $10 million from U.S. and Russian banks in the last 18 months,
According to the experts, in less than two years the MoneyTaker group conducted over 20 successful attacks on financial institutions and law firms in the USA, UK, and Russia.

The average amount of money stolen from U.S. banks was about $500,000, the hackers also stole over $3 million from three Russian lenders.
The group was primarily focused on card processing systems, including the AWS CBR (Russian Interbank System) and purportedly SWIFT (US). Experts believe that financial institutions in LATAM could have particularly exposed due to their usage of a STAR system.
The MoneyTaker group also targeted law firms and financial software vendors, Group-IB has confirmed that 20 companies were successfully hacked, with 16 attacks on US organizations, 3 attacks on Russian banks and 1 in the UK.
The researchers highlighted that the group remained under the radar by constantly changing their tools and switching tactics to evade detection.
“MoneyTaker uses publicly available tools, which makes the attribution and investigation process a non-trivial exercise,” explains Dmitry Volkov, Group-IB Co-Founder and Head of Intelligence. “In addition, incidents occur in different regions worldwide and at least one of the US Banks targeted had documents successfully exfiltrated from their networks, twice. Group-IB specialists expect new thefts in the near future and in order to reduce this risk, Group-IB would like to contribute our report identifying hacker tools, techniques as well as indicators of compromise we attribute to MoneyTaker operations”.
Group-IB first noticed the MoneyTaker group in 2016 when the hackers stole funds from a US bank by gaining access to First Data’s “STAR” network operator portal.
“In 2016, Group-IB identified 10 attacks conducted by MoneyTaker; 6 attacks on banks in the US, 1 attack on a US service provider, 1 attack on a bank in the UK and 2 attacks on Russian banks. Only one incident involving a Russian bank was promptly identified and prevented that is known to Group-IB.” reported the security firm.
“In 2017, the number of attacks has remained the same with 8 US banks, 1 law firm and bank in Russia being targeted. The geography, however, has narrowed to only the USA and Russia.”

The researchers at Group-IB discovered many similarities between 20 incidents throughout 2016 and 2017, hackers used same tools and shared the attack infrastructure. The attack infrastructure is complex and it was able to deliver payloads only to victims with IP addresses in group’s whitelist.
To evade detection, MoneyTaker employs SSL certificates generated using names of well-known brands such as Bank of America, Federal Reserve Bank, Microsoft, and Yahoo.
A look at the MoneyTaker arsenal reveals that the hackers use both borrowed and their custom tools, in one case they developed a keylogger that is also able to take ‘screenshots’ of the infected system.
In the arsenal of the group, there are ‘fileless’ malware whose persistence in the infected systems was obtained by using PowerShell and VBS scripts.
Experts observed the hackers using privilege escalation tools compiled based on codes presented at the Russian cybersecurity conference ZeroNights 2016. The group also used popular banking Trojans in their attacks such as Citadel and Kronos.
The Kronos malware was used to deliver the ScanPOS Point-of-Sale (POS) malware.
In an attack on a Russian bank through the AWS CBR, the MoneyTaker group used a tool called MoneyTaker v5.0 that has a modular structure that performs the following actions:
searches for payment orders and modifies them;
replaces original payment details with fraudulent ones;
erases traces;
Even after the attacks, the MoneyTaker group continues to spy on the victims, the group continuously exfiltrates internal banking documentation (admin guides, internal regulations and instructions, change request forms, transaction logs) to learn about bank operations in preparation for future attacks.
Experts from Group-IB also discovered MoneyTaker uses a Pentest framework Server and leverages Metasploit for the attacks.
“After successfully infecting one of the computers and gaining initial access to the system, the attackers perform reconnaissance of the local network in order to gain domain administrator privileges and eventually consolidate control over the network.” continues the firm.
Group-IB has already shared findings of its investigation with the Europol and Interpol.
Dark Web – The median price range for Android ransomware kits hits $200
11.12.2017 Securityaffairs Android
According to the firm Carbon Black, Android ransomware kits are very popular in the dark web, and the median price range for them hits $200.
According to the firm Carbon Black, Android ransomware kits are very popular in the dark web, more than 5,000 Android ransomware kit listings have been discovered in 2017.
Even if most ransomware kits are still focused on targeting Windows systems, Android ransomware kits are expected to grow in volume and price.
The median price range for Android ransomware kits hits $200, 20 times higher than the $10 median price of Windows ransomware kits.
Researchers at Carbon Black found 1,683 Android ransomware kits out of a total of 5,050, their price ranges from $250 up to $850.
The experts explicitly mentioned the case of the DoubleLocker ransomware for Android that was spotted early this year by security researchers from cybersecurity firm ESET. DoubleLocker is the first-ever ransomware to abuse the Android accessibility feature that implements alternative ways to interact with a mobile device, it was a new malware that not only encrypts the Android mobile devices but also changes PIN lock.

Well, experts at Carbon Black reported a case of a cybercriminal that wanted $854 for the Locker Android ransomware kit.
“We are already seeing an uptick in Android Ransomware kits in underground markets, selling for a much higher price. In our research, we discovered that the median price of ransomware targeting Windows OS is $10, whereas Android-capable ransomware has a median range of $200.” reads a report published by Carbon Black.
Rick McElroy, a Carbon Black security strategist, explained that there is a significant difference between typical iOS users and Android ones. Apple users have a tendency to buy new devices everytime a new model is on the market and update their applications and operating systems on a regular basis.
Android users being remiss in updating their devices, giving much more opportunities to the attackers.
“One of the most surprising things was how many Android devices are out there that have not been updated for two years now, and probably never will,” McElroy says. “Updates are usually simple to conduct, but many users simply don’t do them.”
Crooks choose to target Android users because Android holds the largest OS marketshare worldwide for smartphones, roughly 86% in the first quarter of Q1.
Another factor that influences the median price higher for Android ransomware kits is the level of coding sophistication that is needed to create these tools compared to the efforts necessary to develop similar kits for Windows.
“This speaks a bit to how easy it is to get ransomware onto a Windows system versus other operation systems,” McElroy says. “The longer a developer has to spend to get his ransomware to work effectively at scale the higher the price will be.”
The last catalyst that is driving the median price higher for Android ransomware kits is the spike in the value of Bitcoin. Bitcoin is the currency used for payments of the ransom, “with Bitcoin value increasing so quickly, the expansion of this space will likely be connected closely to the value of BTC.”
“However, as those attacks become tougher, and crypto-currency, such as Bitcoin, gains popularity; we believe ransom-based attacks such as screen-lock and file-encryption will gain popularity going forward.” concludes the report.
Severe flaws in most popular programming languages could expose to hack any secure application built on top of them
10.12.2017 securityaffairs Vulnerebility
Security expert discovered severe flaws in most popular programming languages that could expose to hack any secure application built on top of them.
Last week, IOActive Senior Security Consultant Fernando Arnaboldi presented at the Black Hat Europe 2017 security conference the results of an interesting research about vulnerabilities in several popular interpreted programming languages.
Arnaboldi analyzed the most popular programming languages (JavaScript, Perl, PHP, Python, and Ruby) using the fuzzing software testing technique.
The idea behind this excellent study is that securely developed applications may be affected by unidentified vulnerabilities in the underlying programming languages that could be triggered by attackers.
Fuzzing or fuzz testing is an automated software testing technique that involves providing invalid, unexpected, or random data as inputs to a computer application. The experts then monitor for exceptions such as crashes or failing built-in code assertions or for finding potential memory leaks.
Using this technique, Google experts discovered many flaws in popular software OpenSSL and Linux components.
Below the list of Programming languages tested by the researcher with the fuzzing technique.
Arnaboldi developed a custom “differential fuzzer” XDiFF (Extended Differential Fuzzing Framework) that was specifically designed to test structure of programming languages.
The expert released XDiFF as an open source project on GitHub.
The experts identified most basic functions the programming languages and tested them with the XDiFF fuzzer.
“Before execution, the fuzzer generates all possible test cases by performing a
permutation between functions and payloads. The test cases combined one function of
the programming language at the time with different payloads” reads the research paper titled “Exposing Hidden Exploitable Behaviors in Programming Languages Using Differential Fuzzing.”
“Finding interesting vulnerabilities is entirely dependent on choosing the correct input,” Arnaboldi explained. “For this testing, less than 30 primitive values were used (i.e. a number, a letter, etc.) combined with special payloads. These special payloads were defined so as to help identify when the software attempted to access external resources.”
Before execution, the fuzzer generates all possible test cases by performing a
permutation between functions and payload that were tuned to expose vulnerabilities in the programming languages.
“The test cases combined one function of the programming language at the time with different payloads.” continues the paper.
Arnaboldi exposed severe vulnerabilities in all the programming languages he analyzed with his fuzzer, he discovered the following issues:
Python contains undocumented methods and local environment variables that can
be used for OS command execution.
Perl contains a typemaps function that can execute code like eval().
NodeJS outputs error messages that can disclose partial file contents.
JRuby loads and executes remote code on a function not designed for remote
code execution.
PHP constant’s names can be used to perform remote command execution.
“Assuming no malicious intentions, these vulnerabilities may be the result of mistakes or attempts to simplify software development. The vulnerabilities ultimately impact regular applications parsed by the affected interpreters; however, the fixes should be applied to the interpreters,” says Arnaboldi.
According to Arnaboldi, an attacker can exploit these flaws to hack even the most secure applications built on top of these programming languages.
“Software developers may unknowingly include code in an application that can be used in a way that the designer did not foresee,” concludes the expert. “Some of these behaviors pose a security risk to applications that were securely developed according to guidelines.”
National Institute of Standards and Technology releases a second Draft of the NIST Cybersecurity Framework
10.12.2017 securityaffairs Safety
The National Institute of Standards and Technology (NIST) has published a second draft of a proposed update to the NIST Cybersecurity Framework.
“On December 5, 2017 NIST published the second draft of the proposed update to the Framework for Improving Critical Infrastructure Cybersecurity (a.k.a., draft 2 of Cybersecurity Framework version 1.1).” states the NIST.
“This second draft update aims to clarify, refine, and enhance the Cybersecurity Framework, amplifying its value and making it easier to use. The new draft reflects comments received to date, including those from a public review process launched in January 2017 and a workshop in May 2017.”
The NIST Cybersecurity Framework was first released in 2014, it aims to help organizations, particularly ones in the critical infrastructure sector, in managing cybersecurity risks.

At the time, the NIST published the Framework for Improving Critical Infrastructure Security, a document that proposed cybersecurity standards and practices to build out a security program.
Today the NIST Cybersecurity Framework is considered a best practice guide implemented by numerous organizations and business.
The Cybersecurity Framework was developed based on an executive order issued by former U.S. President Barack Obama and current Trump’s administration also considers the Framework a set of best practices to be implemented by government agencies and critical infrastructure operators.
A cybersecurity executive order issued by the current administration of Donald Trump also requires federal agencies and critical infrastructure operators to use the framework.
After four years since its first release, NIST is now working on an updated version. A first draft of the NIST Cybersecurity Framework was released in January and now the second draft is available since December 5.
Like previous Version 1.0 issued in February 2014, this second draft is the result of extensive consultation with the private and public sectors.
The changes are based on 120 comments submitted in response to the first draft and discussions between 500 individuals who attended a workshop back in May.
According to the summary the update:
Declares applicability of Cybersecurity Framework for “technology,” which is minimally composed of Information Technology, operational technology, cyber-physical systems, and Internet of Things;
Enhances guidance for applying the Cybersecurity Framework to supply chain risk management;
Summarizes the relevance and utility of Cybersecurity Framework measurement for organizational self-assessment;
Better accounts for authorization, authentication, and identity proofing; and
Administratively updates the Informative References.
The second draft was released along with an updated roadmap that details plans for advancing the framework’s development process.
Every comment on the second draft of the NIST Cybersecurity Framework can be sent to cyberframework(at)nist.gov until January 19, 2018.
The NIST plans to release the final V1.1 within this fall, likely in “early calendar year 2018.”
The organization aims to check if the revisions in version 1.1 reflect the changes in the current cybersecurity landscape. It is also important to evaluate the impact of the updated version on organizations currently implementing the version 1.0 of the framework.
Výdaje na IT bezpečnost porostou
10.12.2017 SecurityWorld Bezpečnost
Mezi respondenty nejnovějšího globálního průzkumu informační bezpečnosti (EY Global Information Security Survey; GISS) vyvolává hrozba kybernetických útoků značné obavy. EY se na nejpalčivější rizika a související protiopatření dotazovala více než dvanácti set odpovědných pracovníků a manažerů předních světových organizací.
Většina oslovených organizací tvrdí, že plánují výdaje na informační a kybernetickou bezpečnost zvýšit. Až 9 z 10 dotázaných očekává růst příslušných rozpočtů ještě v tomto roce. Téměř všichni zúčastnění (87 %) počítají se zvýšením výdajů až o polovinu, což by jim mělo umožnit reagovat na vývoj relevantních hrozeb.
Tři čtvrtiny dotázaných však zároveň pokládají za nejpravděpodobnější impuls k posílení těchto nákladů výskyt incidentu, který napáchá zjevné škody. Naproti tomu 64 % je přesvědčeno, že kvůli narušení kybernetické bezpečnosti bez prokazatelných dopadů by se příslušný rozpočet neměnil, přestože ve skutečnosti nebývají důsledky kybernetického napadení často bezprostředně očividné.
„Studie ukázala, že společnosti jsou stále ještě v reaktivním módu a nepřistupují ke kybernetickým hrozbám aktivně a strategicky,“ říká Petr Plecháček, ředitel oddělení IT poradenství EY v České republice. „S navýšením rozpočtu čekají na kybernetickou událost, která ohrozí celou společnost. Ani dramatický dopad útoků prostřednictvím tzv. ransomware v minulém roce není pro řadu společností motivací pro větší investice či revizi plánů obnovy,“ dodává.
Společnosti si přitom uvědomují, že nedostatek odpovídajících prostředků je vystavuje vyšší míře rizik a v 56 % případů proto hodlají svou strategii kybernetické bezpečnosti revidovat, resp. alokaci prostředků ověřit. Celá pětina však zároveň připouští, že pro podrobné vyhodnocení veškerých dopadů nemá k dispozici dostatek potřebných údajů.
„Dnes je potřeba lépe a rychleji chápat, co se děje a snažit se útoky předvídat. Patrně jedinou správnou cestou jsou investice do bezpečnostních nástrojů pro zrychlení a zkvalitnění datové analytiky a do konvergence bezpečnostních technologií,“ komentuje Plecháček.
Organizace se obávají především malware a nedbalého přístupu zaměstnanců
Malware (64 % oproti 52 % v roce 2016) a phishing (64 %, resp. 51 %) vycházejí z průzkumu jako hrozby, v jejichž důsledku expozice organizací vůči rizikům v uplynulých dvanácti měsících vzrostla nejvíce. Mezi nejpravděpodobnější příčiny, resp. původce kybernetických útoků se pak dle oslovených společností řadí nedbalý přístup pracovníků (77 %), organizovaní kyberzločinci (56 %) a záměrné jednání vlastních zaměstnanců (47 %).
„Zaměstnanci jsou svazováni bezpečnostními pravidly a mohou tím získat pocit falešného bezpečí,“ analyzuje výsledky studie Petr Plecháček, ředitel oddělení IT poradenství EY v České republice. „Kybernetické události jsou dnes častěji zmiňovány v mediích a je možné dojít k závěru, že se jedná o skutečnost, které nelze zabránit. Adaptace jedince, potažmo celé organizace na nové a měnící se vektory a formy útoků je však nikdy nekončící proces,“ dodává.
Vrcholovému managementu pravidelně reportuje zhruba polovina firem. Osoba odpovědná za kybernetickou bezpečnost je členem vedení ani ne ve čtvrtině případů a pouze 17 % řídících pracovníků má dostatečné odborné znalosti k tomu, aby účinnost preventivních bezpečnostních opatření dokázali náležitě posoudit.
Ve spojitosti s potlačováním pokročilých kybernetických útoků – tedy takových, které lze připisovat sofistikovaným útočníkům nebo organizovaným skupinám – si je mnoho organizací vědomo možných limitů vlastních bezpečnostních opatření. Tři čtvrtiny respondentů hodnotí účinnost metod, jejichž prostřednictvím by měl podnik případné slabiny odhalit, jako „velmi nízkou až střední“. Varovným signálem jsou i některé další výsledky: 12 % společností údajně nedisponuje žádným formalizovaným programem detekce bezpečnostních incidentů, 35 % aplikuje nedůsledné nebo vůbec žádné zásady ochrany dat, a 38 % nevyužívá řádné, resp. pouze případné procesy pro správu identity či řízení přístupu uživatelů.
Schopnost čelit kybernetickým útokům mají zajišťovat tzv. centra bezpečnostního provozu (SOC). Ty by zároveň měly fungovat jako centralizovaná, strukturovaná a koordinační střediska veškerých aktivit organizace v oblasti kybernetické bezpečnosti. Zhruba polovina respondentů nicméně přiznává, že žádné takové služby nevyužívají, ať už interně nebo formou outsourcingu. Celkem 57 % nevyužívá takřka žádné analytické nástroje pro odhalování relevantních hrozeb. Pouze desetina dotázaných se domnívá, že by dokázali odhalit důmyslný kybernetický útok na jejich organizaci.
Všudypřítomné volání po konektivitě a rozmach internetu věcí (IoT) poskytují stále sofistikovanějším pachatelům kybernetických útoků nové možnosti, jak tyto moderní technologie zneužít. Ve výrobní sféře je však využití propojení strojů a technologií za využití IoT stále ještě nedoceněno. Polovina respondentů uvádí, že hlavní brzdou pro širší využití IoT je nedostatek kvalifikovaných lidí a financí.
„Jako zásadní brzdu rozvoje IoT řešení ve výrobních firmách považujeme obavu z možného napadení technologií či zneužití dat uložených na cloudu. Firmy tak často volí přístup‚ lepší nedělat nic‘, než aby čelili hypotetické hrozbě,“ říká Jan Burian, senior manažer oddělení podnikového poradenství společnosti EY. „Přitom právě využití cloudových IoT platforem umožňuje efektivní sběr, analýzu a vizualizace komplexních dat v reálném čase napříč technologiemi či jinými datovými vstupy,“ dodává.
Podle respondentů GISS je největší výzvou v oblasti bezpečnosti IoT mít přehled o všech použitých aplikacích a zařízeních, a zajistit jejich pravidelnou aktualizaci.
„IoT hraje významnou roli v rámci vytváření nových obchodních modelů, zejména u firem vyrábějící technologie, které lze na dálku monitorovat, aktualizovat jejich software či dodávat nové služby v celém průběhu životního cyklu. Tento záměr však vede k uzavírání systémů jednotlivých výrobců technologií vůči jiným IoT platformám, což v důsledku zvyšuje nároky na orientaci mezi jednotlivými platformami a významně ztěžuje orientaci potenciálním zákazníkům či uživatelům,“ uzavírá Burian.
Linux.ProxyM IoT Botnet now used to launch hacking attacks against websites
10.12.2017 securityaffairs IoT
A new IoT botnet leveraging the Linux.ProxyM malware is currently being used by crooks in a campaign attempting to hack websites.
Security experts at Doctor Web discovered a new IoT botnet leveraging the Linux.ProxyM malware that is currently being used in a campaign attempting to hack websites.
Experts first analyzed the Linux.ProxyM in July, it was used to create a proxy network through SOCKS proxy server on infected devices that are used to relay malicious traffic, disguising his real source.
The Trojan has been noted since February 2017 but peaked in late May.
According to Dr. Web, the number of devices infected with Linux.ProxyM reached 10,000 units in July since its discovery in February 2017.
The malware is able to target devices based on different architectures including x86, MIPS, MIPSEL, PowerPC, ARM, Superh, Motorola 68000, and SPARC.
“Linux.ProxyM is a malicious program for Linux which launches a SOCKS proxy server on an infected device. Cybercriminals can use it to anonymously perform destructive actions.” wrote Dr Web.
“The known assembly of this Trojan exists for devices possessing the following architectures: x86, MIPS, MIPSEL, PowerPC, ARM, Superh, Motorola 68000, and SPARC. It means Linux.ProxyM can infect almost any Linux device, including routers, set-top boxes, and other similar equipment.”
The campaign observed in September was abusing the botnet to send out spam emails, experts estimated that with each infected device generated around 400 messages per day in September.
Later attacks used the botnet to send out phishing emails, the messages supposedly came from DocuSign, a company that provides electronic signature technology and digital transaction management services for facilitating electronic exchanges of contracts and signed documents.
The phishing messages included a link to a fake DocuSign website that featured an authorization form, the attackers used this schema to trick victims into entering their credentials. Then the victims were being redirected to the real DocuSign authorization page.

In December, crooks started using the Linux.ProxyM’s proxy server to hack websites through various methods, including SQL injections, XSS (Cross-Site Scripting), and Local File Inclusion (LFI).
“[the hacking methods] are SQL injections (an injection of a malicious SQL code into a request to a website database), XSS (Cross-Site Scripting)—an attack method that involves adding a malicious script to a webpage, which is then executed on a computer when this page is opened, and Local File Inclusion (LFI).” continues the analysis.
“This kind of attack allows attackers to remotely read files on an attacked server using specially crafted commands. Among the attacked websites were game severs, forums and resources on other topics, including Russian websites.”
On Dec. 7, researchers at Dr. Web observed 20,000 attacks launched by the Linux.ProxyM botnet. About a month ago, the bots were launching nearly 40,000 attacks per day.

“Although Linux.ProxyM has only one function—a proxy server—cybercriminals continue finding new opportunities to use it for illegal actions and showing increasing interest in the ‘Internet of things’,” concludes Doctor Web.
Android Flaw Lets Hackers Inject Malware Into Apps Without Altering Signatures
10.12.2017 thehackernews Android
Millions of Android devices are at serious risk of a newly disclosed critical vulnerability that allows attackers to secretly overwrite legitimate applications installed on your smartphone with their malicious versions.
Dubbed Janus, the vulnerability allows attackers to modify the code of Android apps without affecting their signature verification certificates, eventually allowing them to distribute malicious update for the legitimate apps, which looks and works same as the original apps.
The vulnerability (CVE-2017-13156) was discovered and reported to Google by security researchers from mobile security firm GuardSquare this summer and has been patched by Google, among four dozen vulnerabilities, as part of its December Android Security Bulletin.
However, the worrisome part is that majority of Android users would not receive these patches for next few month, until their device manufacturers (OEMs) release custom updates for them, apparently leaving a large number of smartphone users vulnerable to hackers.
The vulnerability affects apps using APK signature scheme v1 installed on devices running Android versions 5 (Lollipop) and 6 (Marshmallow).
Explained: How Android Janus Vulnerability Works?
android-malware-hacking
The vulnerability resides in the way Android handles APK installation for some apps, leaving a possibility to add extra bytes of code to an APK file without affecting the application's signature.
Before proceeding further, you need to know some basics about an APK file.
A valid APK file is a type of archive file, just like Zip, which includes application code, resources, assets, signatures, certificates, and manifest file.
Earlier versions of Android operating system 5.0 (Lollipop) and 6.0 (Marshmallow) also support a process virtual machine that helps to execute APK archives containing a compiled version of application code and files, compressed with DEX (Dalvik EXecutable) file format.
While installing an Android app or its update, your device checks APK header information to determine if the archive contains code in the compressed DEX files.
If header says APK archive contains DEX files, the process virtual machine decompiles the code accordingly and executes it; otherwise, it runs the code as a regular APK file.
It turns out that an APK archive can contain DEX files as well as regular application code simultaneously, without affecting its validity and signatures.
Researchers find that this ability to add extra bytes of code due to lack of file integrity checking could allow attackers to prepend malicious code compiled in DEX format into an APK archive containing legitimate code with valid signatures, eventually tricking app installation process to execute both code on the targeted device without being detected.
In other words, the hack doesn't require attackers to modify the code of legitimate applications (that makes signatures invalid)—instead, the vulnerability allows malware authors to merely add some extra malicious lines of code to the original app.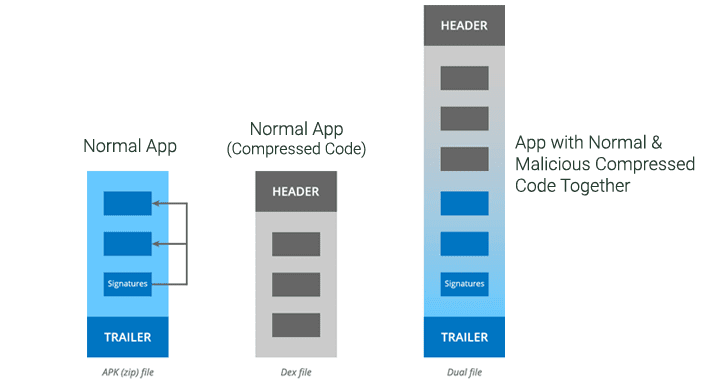
After creating malicious but valid versions of legitimate applications, hackers can distribute them using various attack vectors, including spam emails, third-party app stores delivering fake apps and updates, social engineering, and even man-in-the-middle attacks.
According to the researchers, it may be "relatively easy to trick some users because the application can still look exactly like the original application and has the proper signature."
I find man-in-the-middle attack more interesting, as it could allow hackers to push malicious installation for the apps designed to receive its updates over an unencrypted HTTP connection.
"When the user downloads an update of an application, the Android runtime compares its signature with the signature of the original version. If the signatures match, the Android runtime proceeds to install the update," GuardSquare explains.
"The updated application inherits the permissions of the original application. Attackers can, therefore, use the Janus vulnerability to mislead the update process and get an unverified code with powerful permissions installed on the devices of unsuspecting users."
"For experts, the common reverse engineering tools do not show the injected code. Users should always be vigilant when downloading applications and updates," the security firm added.
Since this vulnerability does not affect Android 7 (Nougat) and latest, which supports APK signature scheme version 2, users running older Android versions are highly recommended to upgrade their device OS (if available).
It's unfortunate, but if your device manufacturer neither offers security patches nor the latest Android version, then you should not install apps and updates from outside of Google Play Store to minimise the risk of being hacked.
Researchers also advised Android developers always to apply signature scheme v2 in order to ensure their apps cannot be tampered with.
Pre-Installed Keylogger Found On Over 460 HP Laptop Models
10.12.2017 thehackernews Hacking
HP has an awful history of 'accidentally' leaving keyloggers onto its customers' laptops. At least two times this year, HP laptops were caught with pre-installed keylogger or spyware applications.
I was following a tweet made by a security researcher claiming to have found a built-in keylogger in several HP laptops, and now he went public with his findings.
A security researcher who goes by the name of ZwClose discovered a keylogger in several Hewlett-Packard (HP) laptops that could allow hackers to record your every keystroke and steal sensitive data, including passwords, account information, and credit card details.
The Keylogger was found embedded in the SynTP.sys file, a part of Synaptics touchpad driver that ships with HP notebook computers, leaving more than 460 HP Notebook models vulnerable to hackers.
Although the keylogger component is disabled by default, hackers can make use of available open source tools for bypassing User Account Control (UAC) to enable built-in keylogger "by setting a registry value."
Here’s the location of the registry key:
HKLM\Software\Synaptics\%ProductName%
HKLM\Software\Synaptics\%ProductName%\Default
The researcher reported the keylogger component to HP last month, and the company acknowledges the presence of keylogger, saying it was actually "a debug trace" which was left accidentally, but has now been removed.
"A potential security vulnerability has been identified with certain versions of Synaptics touchpad drivers that impact all Synaptics OEM partners," HP says in its advisory, calling the keylogger as a potential, local loss of confidentiality.
"A party would need administrative privileges in order to take advantage of the vulnerability. Neither Synaptics nor HP has access to customer data as a result of this issue."
The company has released a Driver update for all the affected HP Notebook Models. If you own an HP laptop, you can look for updates for your model. The list of affected HP notebooks can be found at the HP Support website.
This is not the very first time when a keylogger has been detected in HP laptops. In May this year, a built-in keylogger was found in an HP audio driver that was silently recording all of its users' keystrokes and storing them in a human-readable file.
IoT Botnet Used in Website Hacking Attacks
9.12.2017 securityweek IoT BotNet
Embedded Malware Launches SOCKS Proxy Server on Infected IoT Devices
A botnet of Linux-based Internet of Things (IoT) devices is currently being used in a campaign attempting to hack websites, Doctor Web security researchers warn.
Called Linux.ProxyM, the malware has been around since February of this year, and was previously used in spam campaigns. The Trojan was designed to launch a SOCKS proxy server on infected devices and allows attackers to leverage the proxy to perform nefarious operations while hiding their tracks.
To date, the malware has been observed targeting devices with the following architectures: x86, MIPS, MIPSEL, PowerPC, ARM, Superh, Motorola 68000, and SPARC. Basically, it can infect “almost any Linux device, including routers, set-top boxes, and other similar equipment,” the researchers say.
Previous malicious campaigns leveraging the botnet were sending spam emails, with each infected device generating around 400 messages per day in September, Doctor Web says.
Soon after, the bot started sending phishing messages. The emails supposedly came from DocuSign, a service providing users with the possibility to download, view, sign, and track the status of electronic documents.
The phishing messages included a link to a fake DocuSign website that featured an authorization form, in an attempt to trick users into entering their credentials. After that, the victims were being redirected to the real DocuSign authorization page, while their login details had been sent to the attackers.
In December, Linux.ProxyM’s proxy server started being used to hack websites through various methods, including SQL injections, Cross-Site Scripting, and Local File Inclusion (LFI). The actors operating the botnet targeted game severs and forums, and resources on other topics, including Russian websites.
On Dec. 7, the security researchers observed 20,000 attacks launched by the botnet. About a month ago, the bots were launching nearly 40,000 attacks per day.
“Although Linux.ProxyM has only one function—a proxy server—cybercriminals continue finding new opportunities to use it for illegal actions and showing increasing interest in the ‘Internet of things’,” Doctor Web points out.