Eight counts of aggravated identity theft.

Kazakhstan-born Canadian citizen pleads guilty to 2014 Yahoo hack, he admits helping Russian Intelligence
29.11.2017 securityaffairs Crime
The Kazakhstan-born Canadian citizen Karim Baratov (22) has pleaded guilty to massive 2014 Yahoo hack that affected three billion accounts.
The Kazakhstan-born Canadian citizen Karim Baratov (22) (Kay, a.k.a Karim Taloverov, a.k.a Karim Akehmet Tokbergenov), has pleaded guilty to massive 2014 Yahoo data breach that affected three billion accounts.
Karim Baratov was arrested in Toronto at his home by the Toronto Police Department in March.
In the federal district court in San Francisco on Tuesday, Baratov admitted to helping the Russian intelligence and pleaded guilty to a total of nine counts, including:
One count of conspiring to violate the Computer Fraud and Abuse Act by stealing information from protected computers and causing damage to protected computers.
Eight counts of aggravated identity theft.
“As part of his plea agreement, Baratov not only admitted to his hacking activities on behalf of his co-conspirators in the FSB, but also to hacking more than 11,000 webmail accounts in total on behalf of the FSB conspirators and other customers from in or around 2010 until his March 2017 arrest by Canadian authorities. Baratov advertised his services through a network of primarily Russian-language hacker-for-hire web pages hosted on servers around the world.” reads the press release published by the Department of Justice.
“He admitted that he generally spearphished his victims, sending them emails from accounts he established to appear to belong to the webmail provider at which the victim’s account was hosted (such as Google or Yandex). Baratov’s spearphishing emails tricked victims into (i) visiting web pages he constructed to appear legitimate, as though they belonged to the victims’ webmail providers and (ii) entering their account credentials into those web pages. Once Baratov collected the victims’ account credentials, he sent his customers screen shots of the victims’ account contents to prove that he had obtained access and, upon receipt of payment, provided his customers the victims’ log-in credentials.”
In March, the US Justice Department charged two Russian intelligence officers (Dmitry Dokuchaev and Igor Sushchin) from Russia’s Federal Security Service (FSB) and two hackers (Alexsey Belan and Karim Baratov) for breaking into Yahoo servers in 2014.
Unlike Baratov, the hacker Alexsey Belan and both FSB officers currently reside in Russia.
According to prosecutors, the Russian Intelligence agency FSB directed the Yahoo hack and hired Baratov to target persons of interest to the FSB (i.e. Journalists, government officials, and technology company employees) that were using email accounts different from Yahoo ones.
“Baratov’s role in the charged conspiracy was to hack webmail accounts of individuals of interest to the FSB and send those accounts’ passwords to Dokuchaev in exchange for money,” his plea agreement reads.
Baratov’s lawyers tried to change the position of the man, they said that at the time of the hack, Baratov had no idea he was working with Russian intelligence.
Baratov hacked at least 80 non-Yahoo email accounts, including at least 50 Google accounts, he used spear phsting attack to trick victims into providing their credentials.
Baratov’s sentencing hearing will be held on 20th February next year in federal district court in San Francisco. The man could face up to 87 months in jail for the first charge and 24 months for the identity theft charges.
“These threats are even more insidious when cybercriminals such as Baratov are employed by foreign government agencies acting outside the rule of law.” US Attorney Brian Stretch said.
Baratov has also agreed to pay restitution to the affected Yahoo users and a fine up to $2,250,000 (at $250,000 per count).
Bitcoin Gold (BTG) dev team warns its users about a security breach
29.11.2017 securityaffairs Incindent
The development team of the Bitcoin Gold (BTG) cryptocurrency is warning all users users about a security breach involving its Windows version of wallet app
The development team of the Bitcoin Gold (BTG) cryptocurrency is warning all users users about a security breach involving the official Windows wallet application offered for download via its official website. Bitcoin Gold is the fork of the official Bitcoin cryptocurrency that was created on October 25.
The Bitcoin Gold website does not include links to the installers for the official wallet apps, but links to files hosted in a GitHub repository used by the development team
The development team of the Bitcoin Gold (BTG) explained that attackers gained access to this GitHub account and replaced the legitimate Windows installer with a “suspicious” file that were created to steal funds from the victims and other information.
Developers confirmed the Linux version of the official wallet app was not changed during the incident.
The development team discovered the security breach over the weekend when the experts noticed that the SHA-256 checksum for the Windows installer did not match the original SHA-256 checksum for the file present on the GitHub repository.
“Please be aware that for approximately 4.5 days, a link on our Download page and the file downloads on our Github release page have been serving two suspicious files of unknown origin.” reads the security advisory.
Below are the correct SHA-256 checksums for BTG’s Windows wallet app.
Windows file SHA-256:
53e01dd7366e87fb920645b29541f8487f6f9eec233cbb43032c60c0398fc9fa
bitcoingold-0.15.0-win64-setup.exe
Further investigation allowed the development team to discover that the “malicious” file was available in the GitHub repository between November 21, 2017, 09:39 UTC, and November 25, 2017, 22:30 UTC.
The bad news for end-users is that the malware was not detected by antivirus software.
“Until we know otherwise, all users should presume these files were created with malicious intent – to steal cryptocurrencies and/or user information. The file does not trigger antivirus / anti-malware software, but do not presume the file is safe.” continues the advisory.
“Any user who verified the SHA-256 checksum of the download against the checksum listed on our Download pages is already aware the file is not authentic and should not have used the file, but nobody should assume that all users take this important step.”

Affected users urge to transfer funds to new wallet addresses and reinstall affected computers.
“If the file was used, the computer on which it was used should be addressed with extreme caution; the file should be deleted, the machine should be thoroughly checked for malware and viruses (or wiped clean), and any cryptocurrencies with wallets accessible on that machine should be moved to new wallet addresses immediately,” suggested the Bitcoin Gold development team that meantime has restored the original files and has secured its GitHub account.
BTG is currently the fifth most popular cryptocurrency on the market, ranked behind Bitcoin (BTC), Ethereum (ETH), Bitcoin Cash (BCH), and Ripple (XRP).
A bug in macOS High Sierra allows Root access with no password
29.11.2017 securityaffairs Apple
macOS High Sierra is plagued by a vulnerability that can be exploited to gain root access to a machine with no password.
An easy exploitable vulnerability in macOS 10.13, aka macOS High Sierra, could be triggered by users to gain admin rights, or log in as root, without a password.
The vulnerability is exploitable via the authentication dialog box in the Apple macOS High Sierra that asks for an administrator’s username and password when the user needs to do specific actions like configure privacy and network settings.
From the user login screen, if the user provides “root” as the username, leave the password box blank, hit “enter” and then click on unlock a few times, the prompt disappears and he gains admin rights.
The attack scenario needs physical access to the machine to log in, once inside the attacker can perform several malicious activities such as install a malware.
Waiting for a fix, users should mitigate the bug not leaving vulnerable macOS High Sierra unattended, nor allowing remote desktop access.
The flaw was publicly disclosed via Twitter by the developer Lemi Orhan Ergan.
14h
Lemi Orhan Ergin
@lemiorhan
Dear @AppleSupport, we noticed a *HUGE* security issue at MacOS High Sierra. Anyone can login as "root" with empty password after clicking on login button several times. Are you aware of it @Apple?
Lemi Orhan Ergin
@lemiorhan
You can access it via System Preferences>Users & Groups>Click the lock to make changes. Then use "root" with no password. And try it for several times. Result is unbelievable! pic.twitter.com/m11qrEvECs
7:47 PM - Nov 28, 2017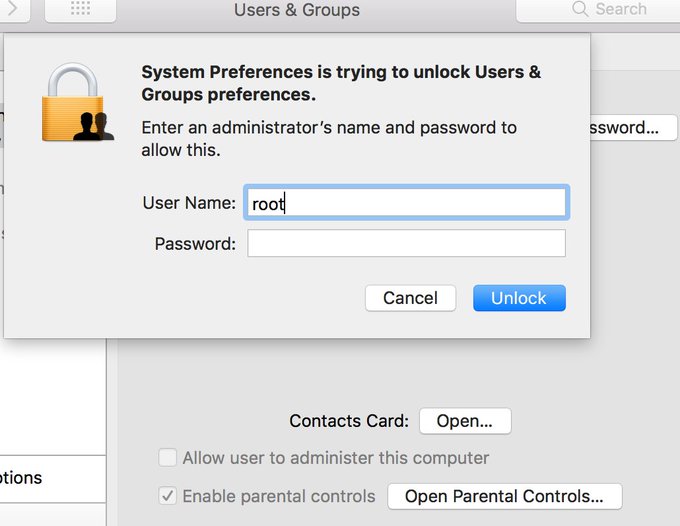
259 259 Replies 1,960 1,960 Retweets 2,124 2,124 likes
Twitter Ads info and privacy
With the access to the machine it is possible to disable FileVault encryption that protects the files from being seen or copied.
13h
The Register
✔
@TheRegister
Pro tip: You can log into macOS High Sierra as root with no password http://reg.cx/2vyD

Jon
@jonp__
oh god this actually works and it lets you do everything like turn off FileVault, well done Apple. pic.twitter.com/vQAqEK39Vk
9:31 PM - Nov 28, 2017
Replies 1 1 Retweet 4 4 likes
Twitter Ads info and privacy
Experts noticed that If they have a root account enabled and a password for it set, the trick will not work.
To set the password, type the following command from the Terminal.
sudo passwd -u root
macOS High Sierra
Apple promptly published this guide to enabling the root account and setting a password for it. If you have remote desktop access enabled for VNC, RDP, screen sharing and similar, it can be used to gain admin rights on your machine. Apple will release a patch to address the issue.
In October, macOS users noticed that another easy-to-exploit bug in macOS High Sierra was disclosing the password for encrypted drives.
In September, the cyber security expert Patrick Wardle, director of research at Synack, revealed that unsigned applications can steal macOS Keychain passwords from the latest version of macOS High Sierra and previous versions of macOS.
Můžeme ještě věřit chytrým telefonům?
29.11.2017 SecurityWorld Mobilní
Fenomén posledních měsíců? Ve smartphonech se objevují bezpečnostní mezery, které vytvářejí sami výrobci.
Víte o tom, že váš chytrý telefon může obsahovat skryté „funkce“, které vás činí zranitelnými? Nejde přitom o nedostatky z nedopatření, ale o vědomé designové prvky, díky nimž telefon funguje tak nějak za vašimi zády.
V telefonech od Googlu, Applu či OnePlus byl v posledních týdnech objeven předinstalovaný software rozbíhající potenciálně škodlivé procesy i navzdory tomu, že uživatelé se snažili přesně takovým zabránit. Je sice férově třeba říct, že motivy výrobců jsou správné, tyto procesy mají zrychlit výkon či usnadnit použití, neinformování zákazníků je však diskutabilní. Pojďme se podívat na pár příkladů těchto prohřešků proti důvěře…
Podle zjištění serveru Quartz zařízení s Androidem uplynulých jedenáct měsíců zasílala Googlu informace o poloze i přesto, že uživatelé měli tuto funkci vypnutou, a to i ve chvílích, kdy byl telefon bez SIM karty a neběžely na něm žádné aplikace. Dle Googlu to bylo kvůli analýze a snaze lepšího využití tzv. ID buněk v síti GSM pro rychlejší doručování SMS. Firma nasbíraná data údajně nijak nevyužila, ani je nemá uložená, a jejich sběr plánuje v prosinci ukončit.
Prohřešek Applu se týká pro změnu zapínání a vypínání Wi-Fi a Bluetooth, které lze od iOS 7 ovládat snadněji prostřednictvím tzv. Ovládacího centra. Funkcionalita má však jeden „háček“. Vypnutí Wi-Fi či Bluetooth z Ovládacího centra sice telefon odpojí od daných sítí a zařízení, ve skutečnosti však nevypne samotné Wi-Fi, respektive Bluetooth. iOS 11 se tak automaticky znovu napojí na nové hotspoty či zařízení, jestliže se objeví v dosahu anebo je-li telefon restartován. Chce-li uživatel opravdu vypnout Wi-Fi/Bluetooth, musí tak učinit skrz Nastavení. Apple o této rozdílné funkcionalitě informuje na své webové stránce podpory. Ale – kdo z vás tam kdy byl?
Vůbec nejvážněji se však jeví problém telefonů OnePlus, které jsou prodávány s aplikací, která může posloužit k jejich rootování. Jmenuje se EngineerMode a jde o diagnostický nástroj obvykle instalovaný na prototypy nebo zkrátka zařízení, která nejdou do prodeje pro veřejnost. Přístup k funkci umožňující rootování je sice chráněn heslem, to se však rychle objevilo veřejně na internetu a příliš polehčující okolnost není ani to, že ke zneužití aplikace je třeba mít k telefonu fyzicky přístup.
Podle OnePlus nejde o vážný bezpečnostní problém, jelikož je nepravděpodobné, aby se sešly všechny faktory umožňující zneužití, v příští softwarové aktualizaci však aplikaci odstraní. Naprostá většina uživatelů však o přítomnosti aplikace nemá tušení a firma zatím ani neuvedla, jak ji případně odinstalovat.
Vědomá přítomnost obsahu představujícího potenciální bezpečnostní riziko a neinformování uživatelů příliš neprospívá vzájemné důvěře mezi výrobcem a kupujícím. Ve všech zmíněných příkladech prakticky výrobce odebral uživateli možnost kontroly tím, že před ním skryl určitou skutečnost.
Jako by říkal „Sami sobě důvěřujeme, uživatelé tedy nepotřebují informace, aby mohli dělat vlastní rozhodnutí.“ A Google a OnePlus reagovali až poté, co byli na problém upozorněni všímavými uživateli. Až jednoho napadne, co všechno chytré telefony dělají bez našeho vědomí…
Apple má vážnou chybu v macOS High Sierra: k Macu se může přihlásit kdokoli
29.11.2017 Lupa.cz Apple
Dokud se tenhle problé nevyřeší, žádný Mac není v bezpečí. Pokud má nainstalovanou nejnovější verzi operačního systému High Sierra 10.13.1 (17B48), může se do počítače dostat kdokoli, aniž by potřeboval znát login a heslo.
Chyba totiž umožňuje, aby si kdokoli na zamčeném Macu zpřístupnil účet s adinistrátorskými právy a přihlásil se k němu, informují zahraniční servery.
Na problém na Twitteru upozornil vývojář Lemi Orhan Ergin. Nejsnadnější způsob, jak ji zneužít, podle něj vede přes System Preferences > Users & Groups. Tam stačí kliknout na ikonu zámku a pak v okně pro jméno a heslo zadat „root“, heslo nechat prázdné a potvrdit (někdy je to nutné zkusit vícekrát).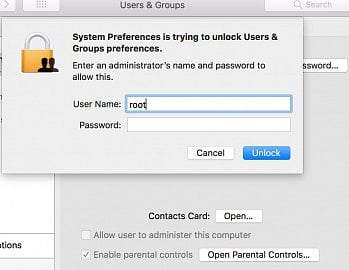
Ale pozor – už pokud tento postup jenom vyzkoušíte, vytvoříte si v počítači „root“ účet bez hesla, ke kterému se pak z přihlašovací obrazovky bude moci přihlásit kdokoli. Pokud jste to udělali, jediným momentálním řešením problému je nastavit preventivně k účtu „root“ nějaké heslo, aby se k Macu nebylo možné přihlásit bez něj (postup je k dispozici v nápovědě Applu).
Vytvoření root účtu s nějakým heslem je zatím také jediným způsobem, jak se před chybou ochránit, potvrdil také Apple. Firma chybu přiznala a oznámila, že pracuje na updatu, který ji vyřeší.
Top Secret US Army and NSA documents left exposed on Amazon S3 bucket
29.11.2017 securityaffairs
The experts from the security firm UpGuard have discovered another S3 bucket containing documents from INSCOM, that is a joint US Army and NSA agency.
A couple of weeks ago sensitive data from the US Army’s CENTCOM and PACOM divisions was exposed on an unsecured Amazon S3 bucket, experts from the security firm UpGuard found terabytes of US military social media surveillance.
Now the same team from UpGuard have discovered another S3 bucket containing documents from INSCOM, that is a joint US Army and NSA agency involved in intelligence, security, and information operations.
The S3 server contained a small number of files and folders, three of which were available for the download.
“Critical data belonging to the United States Army Intelligence and Security Command (INSCOM), a joint US Army and National Security Agency (NSA) Defense Department command tasked with gathering intelligence for US military and political leaders, leaked onto the public internet, exposing internal data and virtual systems used for classified communications to anyone with an internet connection.” reads the blog post published by UpGuard.
“Set to allow anyone entering the URL to see the exposed bucket’s contents, the repository, located at the AWS subdomain “inscom,” contained 47 viewable files and folders in the main repository, three of which were also downloadable. “
One of the files was an image of a virtual machine in Oracle Virtual Appliance (.ova) format. It was a Linux-based operating system and an attached virtual hard drive likely used for receiving Defense Department data from a remote location.
The experts were not able to access the data likely because it cannot be accessed without connecting to Pentagon systems.
The experts were able to analyzed the metadata of files stored on the virtual hard drive, they discovered that the SSD image was containing a huge trove of highly sensitive files, some of which were classified with the TOP SECRET and NOFORN (NO FOReign Nationals) security classifiers.
According to UpGuard, this was the first time it discovered classified information left freely accessible on Amazon S3 servers.

Another a folder in the same virtual machine image suggests that the system was also part of the Red Disk, a cloud computing platform that was part of the Distributed Common Ground System-Army (DCGS-A) intelligence platform.
“The exposed data also reveals sensitive details concerning the Defense Department’s battlefield intelligence platform, the Distributed Common Ground System – Army (DCGS-A) as well as the platform’s troubled cloud auxiliary, codenamed “Red Disk.”” continues the post.
The second downloadable file discovered by the experts is a plaintext ReadMe document stored on the virtual hard drive. The ReadMe file provides indications of instruction for the contents of the .ova and information on the location of additional Red Disk packages.
The third downloadable file was a compressed .jar titled “rtagger,” that seems to be a training snapshot for labeling and categorizing classified information, as well as assigning such data to “regions.”
According to UpGuard, the leak was the result of process errors within an IT environment.
“Regrettably, this cloud leak was entirely avoidable, the likely result of process errors within an IT environment that lacked the procedures needed to ensure something as impactful as a data repository containing classified information not be left publicly accessible,” said the UpGuard team. “Given how simple the immediate solution to such an ill-conceived configuration is […] the real question is, how can government agencies keep track of all their data and ensure they are correctly configured and secured?“
Kaspersky Security Bulletin – Story of the year 2017
29.11.2017 Kaspersky Analysis
Download the Kaspersky Security Bulletin: Story of the year 2017
Introduction: what we learned in 2017
In 2017, the ransomware threat suddenly and spectacularly evolved. Three unprecedented outbreaks transformed the landscape for ransomware, probably forever. The attacks targeted businesses and used worms and recently leaked exploits to self-propagate, encrypting data and demanding a ransom they didn’t really want. The perpetrators of these attacks are unlikely to be the common thieves usually lurking behind ransomware. At least one of the attacks carried flaws that suggest it may have been released too soon, another spread via compromised business software, two are related and the two biggest appear to have been designed for data destruction. The cost to victims of these three attacks is already running into hundreds of millions of dollars.
Welcome to ransomware in 2017 – the year global enterprises and industrial systems were added to the ever-growing list of victims, and targeted attackers started taking a serious interest in the threat. It was also a year of consistently high attack numbers, but limited innovation.
This short paper highlights some of the key moments.
The massive outbreaks that were not all they seemed
WannaCry
It all started on May 12, when the security community observed something it hadn’t seen for almost a decade: a cyberattack with a worm that spread uncontrollably. On this occasion the worm was designed to install the WannaCry crypto-ransomware on infected machines.
The WannaCry epidemic affected hundreds of thousands of computers around the globe. To propagate, the worm used an exploit dubbed EternalBlue and a backdoor DoublePulsar, both of which had been made public by the Shadow Brokers group a month prior to the outbreak. The worm automatically targeted all computers sharing the same local subnet as the infected machine, as well as random IP ranges outside the local network – spreading it rapidly across the world.
To infect a machine, WannaCry exploited a vulnerability in the Windows implementation of the SMB protocol. Microsoft had released an update to fix this vulnerability back in March 2017, but the number of unpatched machines remained so high that this hardly hindered the propagation of WannaCry.
After infecting a machine and executing a routine to spread further, WannaCry encrypted some valuable files belonging to the victim and displayed a ransom note. Full decryption of the affected files was impossible without paying the ransom – although our analysts discovered several flaws in WannaCry’s code that could allow some victims to restore some of their data without paying the ransom.
Impact of WannaCry
The attack was industry-agnostic, and victims were mainly organizations with networked systems. The ransomware also hit embedded systems. These often run on legacy OS and are therefore particularly vulnerable. Victims received a ransom demand to be paid in bitcoins. Reports suggests the ultimate number of victims could be as high as three-quarters of a million.
Car maker Renault had to close its largest factory in France and hospitals in the UK had to turn away patients. German transport giant Deutsche Bahn, Spain’s Telefónica, the West Bengal power distribution company, FedEx, Hitachi and the Russian Interior Ministry were all hit, too. A month after the initial outbreak had been contained, WannaCry was still claiming victims, including Honda, which was forced to shut down one of its production facilities, and 55 speed cameras in Victoria, Australia.
The unanswered questions about WannaCry
As a devastating high profile attack targeting businesses, WannaCry was extremely successful. As a ransomware plot to make lots of money, it was a failure. Spreading via a worm is not advisable for a threat that is most lucrative when silently stalking the shadows. Estimates suggest it only made around $55,000 in bitcoin, hampered by its high visibility. The code was poor in places, and there are suggestions that it escaped into the wild before it was fully ready. There are also a number of indicators, including early code similarities that suggest the group behind WannaCry is the infamous Korean-speaking threat actor Lazarus.
The true purpose of the WannaCry attack may never be known – was it ransomware gone wrong or a deliberate destructive attack disguised as ransomware?
ExPetr
The second big attack came just six weeks later, on June 27. This was spread predominantly through a supply chain infection and targeted machines mainly in Ukraine, Russia and western Europe. The company’s telemetry indicates that there were more than 5,000 attacked users. Victims received a ‘ransom demand’ of around $300, to be paid in bitcoins – although it turned out that even then they couldn’t get their files back.
ExPetr was a complex attack, involving several vectors of compromise. These included modified EternalBlue (also used by WannaCry) and EternalRomance exploits and the DoublePulsar backdoor for propagation within the corporate network; compromised MeDoc accounting software, which distributed the malware through software updates; and a compromised news website for Ukraine’s Bakhmut region that was used as a watering hole by the attackers.
What’s more, ExPetr was capable of spreading even to properly patched machines in the same local network as the initially infected computer. To do that, it harvested credentials from the infected system by means of a Mimikatz-like tool and proceeded with its lateral movement by means of the PsExec or WMIC instruments.
The encrypting component of ExPetr operated on two levels: encrypting the victim’s files with the AES-128 algorithm and then installing a modified bootloader taken from another malicious program – GoldenEye (the successor of the original Petya). This malicious bootloader encrypted the MFT, a critical data structure of the NTFS file system, and prevented further boot processes, asking for a ransom.
Impact of ExPetr
Victims of ExPetr included major organizations such as shipping ports, supermarkets, ad agencies and law firms: for example, Maersk, FedEx (TNT) and WPP. A month after the attack, TNT’s deliveries were still affected, with SMB customers suffering most. Another victim, consumer goods giant Reckitt Benckiser, lost access to 15,000 laptops, 2,000 servers and 500 computer systems in the space of just 45 minutes when the attack hit – and expects the cost to the business to be over $130 million. Maersk announced a revenue loss of around $300 million due to the attack.
The unanswered questions about ExPetr
Kaspersky Lab experts have found similarities between ExPetr and early variants of BlackEnergy’s KillDisk code – but the true motivation and purpose behind ExPetr also remain unknown.
BadRabbit
Then, in late October, another crypto-worm, BadRabbit, appeared. The initial infection started as a drive-by download served from a number of compromised websites and mimicking an update for Adobe Flash Player. When launched on a victim’s computer, BadRabbit’s worm component attempted to self-propagate using the EternalRomance exploit and to employ a lateral movement technique similar to the one utilized by ExPetr. Most of BadRabbit’s targets were located in Russia, Ukraine, Turkey and Germany.
The ransomware component of BadRabbit encrypted the victim’s files, followed by the whole disk partitions using modules of legitimate utility DiskCryptor. The analysis of the code of BadRabbit samples and techniques suggests there is a notable similarity between this malware and ExPetr. However, unlike ExPetr, BadRabbit does not appear to be a wiper, as its cryptographic scheme technically allows the threat actors to decrypt the victim’s computer.
Leaked exploits powered many new waves of attacks
The criminals behind the aforementioned ransomware outbreaks were not the only ones to use the code of exploits leaked by the Shadow Brokers to wreak havoc.
We have discovered some other not-so-notorious ransomware families that at some point used the same exploits. Among them are AES-NI (Trojan-Ransom.Win32.AecHu) and Uiwix (a variant of Trojan-Ransom.Win32.Cryptoff). These malware families are ‘pure’ ransomware in the sense that they do not contain any worm capabilities, i.e. cannot self-replicate, which is why they did not spread nearly as widely as WannaCry, for instance. However, the threat actors behind these malware families exploited the same vulnerabilities on victims’ computers during the initial infections.
Master keys released for several ransomware families
Apart from the large-scale epidemics that shook the world, in Q2 2017 an interesting trend emerged: several criminal groups behind different ransomware cryptors concluded their activities and published the secret keys needed to decrypt victims’ files.
Below is the list of families for which keys became public in Q2:
Crysis (Trojan-Ransom.Win32.Crusis);
AES-NI (Trojan-Ransom.Win32.AecHu);
xdata (Trojan-Ransom.Win32.AecHu);
Petya/Mischa/GoldenEye (Trojan-Ransom.Win32.Petr).
The Petya/Mischa/GoldenEye master key was released shortly after the outbreak of ExPetr and might have been an attempt by the original Petya authors to show that they were not the ones behind ExPetr.
The reappearance of Crysis
Despite the fact that the Crysis ransomware appeared to die in May 2017 following the release of all the master keys, it didn’t stay dead for long. In August, we started discovering numerous new samples of this ransomware and they turned out to be almost identical copies of the previously distributed samples, with only a few differences: they had new master public keys, new email addresses that victims were supposed to use to contact the criminals, and new extensions for the encrypted files. Everything else remained unchanged – even the timestamps in the PE headers. After thorough analysis of the old and new samples, our analysts concluded that most likely the new samples were created by binary patching the old ones using a hex editor. One reason for this might be that the criminals behind the new samples didn’t possess the source code and simply reverse-engineered the ransomware to raise it from the dead and use it for their own ends.
RDP infections continue to grow
In 2016, we noticed a new emerging trend among the most widespread ransomware. Instead of trying to trick the victim into launching a malicious executable or using exploit kits, the criminals turned to another infection vector. They were brute-forcing the RDP logins and passwords on machines that had RDP turned on and that were available for access from the Internet.
In 2017, this approach became one of the main propagation methods for several widespread families, such as Crysis, Purgen/GlobeImposter and Cryakl. This means that when securing a network, InfoSec specialists should keep this vector in mind and block RDP access from outside the corporate network.
Ransomware: a year in numbers
It is important not to read too much into the absolute numbers as they reflect changes in detection methodology as much as they do evolution of the landscape. Having said that, a few top line trends are worth noting:
The level of innovation appears to be declining – in 2017, 38 new strains of encryption ransomware were deemed interesting and different enough to be designated as new ‘families’, compared to 62 in 2016. This could be due to the fact that the crypto-ransomware model is fairly limited and it is becoming progressively more difficult for malware developers to invent something new.
There were many more modifications of new and existing ransomware detected in 2017: over 96,000 compared to 54,000 in 2016. The rise in modifications may reflect attempts by attackers to obfuscate their ransomware as security solutions get better at detecting them.
The number of attacks as defined by hits against Kaspersky Lab customers remained fairly constant. In fact, the big spikes of 2016 have been replaced with a more consistent monthly spread. Overall, just under 950,000 unique users were attacked in 2017, compared to around 1.5 million in 2016. However, this data includes both encryptors and their downloaders; if you look at the numbers for encryptors only, the attack data for 2017 is similar to 2016. This makes sense if you consider that many attackers are starting to distribute their ransomware through other means, such as brute-forcing passwords and manual launching. These numbers do not include the many computers around the world unprotected by our solutions that fell victim to WannaCry – this number has been estimated at around 727,000 unique IP addresses.
WannaCry, ExPetr and BadRabbit notwithstanding, the number of attacks targeting corporates increased only slightly: 26.2% in 2017 compared to 22.6% in 2016. Just over 4% of those targeted in 2017 were SMBs.
Further details on these trends, including the most affected countries and top ransomware families, can be found in the Kaspersky Security Bulletin 2017 Statistics Report.
According to Kaspersky Lab’s annual IT security survey
65% of businesses that were hit by ransomware in 2017 said they lost access to a significant amount or even all their data; while 29% said that although they were able to decrypt their data, a significant number of files were lost forever. These figures are largely consistent with those for 2016.
34% of those affected took a week if not more to restore full access, up from 29% in 2016.
36% paid the ransom – but 17% of them never recovered their data (32 and 19% in 2016).
Conclusion: what next for ransomware?
In 2017, we saw ransomware apparently being used by advanced threat actors to mount attacks for data destruction rather than for pure financial gain. The number of attacks on consumers, SMBs and enterprises remained high, but they mainly involved existing or modified code from known or generic families.
Is the ransomware business model starting to crack? Is there a more lucrative alternative for cybercriminals motivated by financial gain? One possibility could be cryptocurrency mining. Kaspersky Lab’s threat predictions for cryptocurrencies in 2018 suggest a rise in targeted attacks for the purpose of installing miners. While ransomware provides a potentially large but one-off income, miners can result in lower but longer earnings, and this could be a tempting prospect for many attackers in ransomware’s current turbulent landscape. But one thing’s for sure, ransomware won’t just disappear – neither as a direct threat, nor as a disguise for deeper attacks.
The fight against ransomware continues
Through collaboration: On July 25, 2016, the No More Ransom initiative was launched by Kaspersky Lab, the Dutch National Police, Europol, and McAfee. It is a unique example of the power of joint public-private collaboration to both fight cybercriminals and help their victims with expertise, tips and decryption tools. One year on, the project has 109 partners and is available in 26 languages. The online portal carries 54 decryption tools, which between them cover 104 families of ransomware. To date, more than 28,000 devices have been decrypted, depriving cybercriminals of an estimated US$9.5 million in ransom.
Through intelligence: Kaspersky Lab has monitored the ransomware threat from the start, and was one of the first to provide regular threat intelligence updates on extortion malware in order to boost industry awareness. The company publishes regular overviews of the evolving ransomware landscape, for instance, here and here.
Through technology: Kaspersky Lab offers multi-layered protection against this widespread and increasing threat, including a free anti-ransomware tool that anyone can download and use, regardless of the security solution they use. The company’s products include a further layer of technology: System Watcher that can block and roll back malicious changes made on a device, such as the encryption of files or blocked access to the monitor.
macOS Bug Allows Root Access With No Password
29.11.2017 securityweek Apple
macOS High Sierra is plagued by a bug that can be exploited to gain root access to a machine by leaving the password field blank. Apple is expected to quickly release a patch, especially since remote exploitation is also possible.
Ever since High Sierra came out, some users have complained that their admin accounts had become standard accounts after updating the operating system. While trying to find a solution for the problem, one user on Apple’s Developer Forums suggested logging in with “root” and no password in order to obtain the access needed to create an admin account.
This solution was suggested on November 13, and on November 28 someone realized that logging in to the root account with no password should not be possible and that this is a major vulnerability.
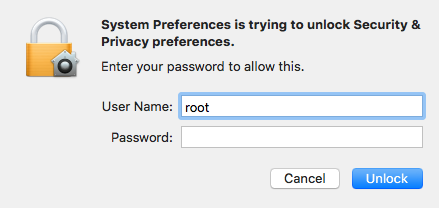
Gaining root access via this flaw requires entering the “root” username in the graphical user interface (GUI) and leaving the password field blank. A couple of attempts are required, but SecurityWeek can confirm that it’s easy to reproduce.
Access “System Preferences” from the Apple menu and click on any of the categories that require administrator privileges in order to make changes (e.g. Security & Privacy, Users & Groups, Parental Controls). Then click on the lock icon in the bottom left corner of the window and enter the username “root” with a blank password when prompted. Hit the Enter key or the Unlock button twice and root access is granted.
An analysis of the flaw revealed that an attempt to log in as root with a blank password actually activates a subroutine that creates the root account, which Apple has disabled by default. Once the root account has been activated, logging in as root with no password works on the first try.
While it may appear that the vulnerability can only be exploited by having physical access to the targeted machine, macOS hacker Patrick Wardle and others have managed to reproduce it remotely as well if sharing services are enabled on the device. Some experts warned that malicious actors could be scanning the Web for remotely accessible computers that they can attack using this security hole.
Apple is working on patching the vulnerability. In the meantime, users can protect themselves against potential attacks by manually setting a password for the root user. Disabling sharing services is also a good way to prevent remote exploitation of the flaw.
This is the second password-related bug found in macOS High Sierra recently. Back in October, a developer noticed that the operating system had leaked the passwords for encrypted Apple File System (APFS) volumes via the password hint.
IoT, Android Botnets Emerge as Powerful DDoS Tools: Akamai
29.11.2017 securityweek CyberCrime
Distributed denial of service (DDoS) attacks observed during the third quarter employed familiar vectors, but a newcomer that made headlines for abusing Android devices is expected to evolve, a new Akamai report suggests.
This new threat is the Android-based WireX botnet, which managed to infect 150,000 devices within a matter of weeks, the company’s Third Quarter, 2017 State of the Internet / Security Report (PDF), points out. Distributed through legitimate-looking infected apps in Google Play, the botnet managed to spread fast and might have grown even bigger if it wasn’t for the joint effort of several tech companies.
Akamai, which was involved in the botnet’s takedown, expects WireX to persist, evolve, and flourish, the same as the infamous Mirai Internet of Things (IoT) botnet did. Highly active last year, Mirai had a much lower presence on the threat landscape during Q3, with the largest attack powered by it only peaking at 109 Gbps (gigabit per second).
Regardless, Akamai believes that organizations should be prepared for the possibility of registering much larger DDoS attacks coming from these threats. The holiday season is expected bring along incidents where new attack techniques are abused.
“The lure of easy access to poorly-secured end nodes and easily-available source code make it likely that Mirai-based attacks won’t be fading in the near future,” said Martin McKeay, senior security advocate and senior editor, State of the Internet / Security Report. “Our experience suggests that an army of new potential attackers comes online every day. Couple with that, the ubiquity of Android software and the growth in the Internet of Things are amplifying the risk/reward challenges that enterprises face to tremendous levels.”
According to Akamai’s report, the overall number of DDoS attacks observed during the third quarter of the year grew only 8% from Q2, the same as infrastructure layer (layers 3 & 4) attacks did. Web application assaults, on the other hand, continued to rise significantly (30%) on quarter and registered a massive 69% increase compared to last year, the report shows.
Attackers made heavy use of SQL injection (SQLi) during the third quarter, with the attack vector registering a 62% increase compared to the previous year, and going up 19% on quarter. This, however, isn’t surprising, considering that the latest version of the OWASP Top 10 2017 has “injection” (inclusive of SQLi) as the top ranked vulnerability category.
Reflection-based attacks registered a very small increase (4%), while the average number of attacks per target reached 36, up 13% compared to the second quarter of the year. The target hit the most was a gaming customer which Akamai says endured 612 DDoS attacks during the time frame, or 7 attacks per day, on average.
Akamai’s report also reveals a large increase (217% year-on-year) in attacks sourcing from the United States, the top source country for web application incidents. The county was also the target of the bulk of the web application attack traffic seen by Akamai during the third quarter, at 300 million (5 times the number seen in the next-highest country, Russia).
The continuous increase in DDoS attacks shows that defenders need to set up protections against this type of assaults too, in addition to keeping software and firmware updates at all times. Massive attacks such as NotPetya are proof of that, while massive cyber incidents such as Yahoo admitting that all of its 3 billion accounts had been compromised and the Equifax breach reveal that no one is safe.
“The third quarter’s headlines have illustrated the severe financial and business toll that cyber-attacks have had on businesses across many industries. With data showing that attacks are on the upswing as we head into the critical end-of-year and holiday season, the implication is clear: cyber security can only be ignored at great peril,” Akamai notes.
Privacy Rights in Balance as Supreme Court Hears Cellphone Tracking Case
29.11.2017 securityweek Mobil
Privacy rights in the digital age face a crucial test Wednesday when the Supreme Court hears a case over police use of a person's location data from cellphone towers.
Civil liberties advocates from both the right and the left have called for the US high court to agree that privacy rights guaranteed by the US Constitution's Fourth Amendment extend to electronic data held by third parties -- phone companies in this case -- but by implication any data held by social media companies or stored in the digital cloud.
But law enforcement authorities, faced with the challenges of phones used under false identities and with unbreakable encryption, say access to such data is crucial to fighting crime.
"This case will likely decide whether the 4th Amendment is to retain its vitality in the digital age, as it becomes virtually impossible for any of us to go about our daily lives without leaving trails of digital data behind us," said Nathan Wessler, a staff attorney with the American Civil Liberties Union.
Cell Phone Privacy Case
The specific case under review, Carpenter vs US, involves the arrest of a man named Timothy Carpenter in 2011. To investigate a spate of armed holdups, police studied cell tower data going back four months and it eventually linked Carpenter to the robbery locations.
The police had obtained some 12,898 location points on Carpenter from two phone companies. Carpenter challenged his conviction, saying it hinged on private information that should not have been provided without a court-issued warrant. The data, for example, showed when he slept at home and elsewhere, and when he was in a church.
- Constitutional test case -
The Fourth Amendment guarantees the privacy of citizens from "unreasonable searches and seizures", and says police must obtain warrants based on "probable cause" if they want to search a suspect's "persons, houses, papers, and effects."
Parties on both sides of the case agree that the law did not anticipate an era when everyone relies on a cellphone and that technology providers can amass data on a person from their phone use.
"This is a challenging case.... On one hand, the law must keep up as technology changes to maintain privacy protections. On the other hand, the blunt instrument of the Fourth Amendment shouldn't be forced beyond its proper role," wrote Orin Kerr, a law professor at George Washington University Law School who backs the government in this case.
A broad range of private and industry groups submitted arguments to the court detailing why the nine justices should extend privacy protections to the kind of data the case focuses on.
They note that a whole range of devices used by people today, from cellphones to home appliances to watches and baby monitors, automatically deliver data to technology and communications companies which store it away.
- 'Unreasonable' search? -
The government and law enforcement officials argue this data should be accessible to police because it is not addressed by the Fourth Amendment, and is not truly private, since it is in the hands of third parties. Getting cell tower data is no different than collecting information from human witnesses in the public space, they say.
They also say that asking for it as part of an investigation is not an "unreasonable" search banned by the Constitution.
But civil libertarian groups reject that argument, saying the data gives far more information on a person than what a single witness could say.
"Even in limited quantities, cell phone location information can be a telltale sign of private social, political, and religious activities protected by the Constitution," said the Brennan Center For Justice.
All agree, though, that what the court eventually decides, which could take months, will set a standard on digital privacy for years if not decades.
"I don't think it's an exaggeration to say that is the most important Fourth Amendment case that we have seen in a generation," said Wessler.
"It really promises to decide whether the mere use of modern technologies is going to make our lives into an open book for the government, without the protection of a warrant."
Hackers can easily target container ships by hacking load plans due to its vulnerable messaging system
28.11.2017 securityaffairs Hacking
Ship loading and container load plans are vulnerable to hack because are created without using a secure messaging system.
Transportation is not immune from hacking attacks, aircraft and vessels can be compromised by cyber criminals and nations state actors exactly like any other system.
Today let’s speak about ship loading and container load plans that are vulnerable to hack because are created without using a secure messaging system.
Electronic messages that are exchanged between the entities responsible for these activities include a huge quantity of information that could be used by ill-intentioned to to target naval transportation entities, including shipping lines, terminals, and port authorities.
Large vessels rely a system called BAPLIE to displace thousands of containers, it is used to inform port authorities where to place every single container, and it is regularly updated by ship’s manufacturers.

Researchers at the security firm Pen Test Partners who analyzed BAPLIE discovered that if customers do not use the latest version are open to cyber attacks that can allow crooks to send fake container’s data to the customs (obscure the real contents and weight of the load).
This information is used by port authorities and law enforcement to choose which containers have to be examined, altering data could allow criminal organizations to avoid controls.
The attackers could be interested in manipulating container weight and ship balance to make the ship more and more unstable as heavy goods are inadvertently loaded in the wrong position of the vessels.
“Criminals less interested in destabilising ships but perhaps instead stealing goods by rerouting containers, would use COPRAR / COPARN / CODECO / COARRI messages instead. These deal with shipping line to terminal messaging and vice versa.” reads the post published by Pen Test Partners.
“There’s evidence to suggest that ship and terminal messaging systems have been exploited in the past for routing drugs and theft of valuables.”
The experts at Pen Test Partners warned about the transmission channel used to send load plans from the ship to the port, they discovered that in many cases the personnel involved in the operations use USB devices for exchanging data between ship and terminal.
This procedure opens the door to a malware-based attack because the computer having load plan software might also be used for surfing the web or emailing.
Researcher claims that interoperability is vital between shipload plan and the various ports that it visits so that the load plan is securely transmitted to the port.
“Interoperability between the ship load plan and the hundreds of ports it may visit is essential – this leads to a race to the bottom in terms of securing and transmitting the load plan to the port. Simple = USB = vulnerable” states a separate report published by the security firm.
“This is ripe for attack. The consequences are financial, environmental and possibly even fatal.”
The manipulation of load plans could have dramatic impact on the shipping lines, operators, terminals and ports have to continuously assess their infrastructure, including messaging systems.
Bulletproof 360 website was hacked. Personal and financial data exposed
28.11.2017 securityaffairs Hacking
The website of the coffee vendor Bulletproof 360 was infected with a malware that stole customers’ financial and personal data.
The firm Bulletproof 360, Inc. manufactures coffee and tea products, and dietary supplements for upgrading mind and body. It serves customers online, as well as through stores in the United States and internationally.
The company specializing in butter-infused coffee confirmed that the attackers injected malicious code into its website stealing payment card details for months.
Bulletproof 360 Inc. revealed that from May 20 to October 19, except on October 14, crooks have stolen personal and financial information customers entered on its website.
Stolen data included bank card numbers, expiration dates, and security codes (CVV), as well as names, postal addresses, and email addresses.

Bulletproof Coffee Cold Brew ready to go (PRNewsfoto/Bulletproof 360, Inc.)
The security breach was discovered mid-October, but it was publicly disclosed only on Monday to California officials, in compliance with the US state’s security breach notification laws.
“In mid-October 2017, Bulletproof identified unauthorized computer code that had been added to the software that operates the checkout page at www.bulletproof.com. When we discovered the unauthorized code, we immediately removed it and began an investigation. We have been working with leading computer security firms to examine our systems. We have also been working with law enforcement.” reads the letter sent by the company to the customers.
“Based on our investigation, we determined that the unauthorized code may have been capable of capturing information entered during the checkout process during the period from May 20, 2017 through October 13, 2017 and October 15-19, 2017. You are receiving this notice because your payment card may have been entered on the checkout page during this time period. “
Bulletproof 360 announced it is working diligently to improve the security of its systems and has vowed to prevent future similar security breach.
The company is inviting its customers to remain vigilant to the possibility of fraud by reviewing their payment card account statements for any unauthorized activity. The company said it will cover any costs associated with reimbursing fraudulent charges.
“If you incurred costs that your financial institution declined to reimburse related to fraudulent charges on a payment card you used for an online transaction with Bulletproof during the relevant time period, please contact us at the number below. We will reimburse you for any such reasonable, documented costs that your financial institution declined to pay” concludes the letter.
The company is known to consider cyber security as a pillar for its business, its CEO Dave Asprey worked at NetScaler, BlueCoat, and Trend Micro as a cloud security expert.
Google detects Android Tizi Spyware that spies on popular apps like WhatsApp and Telegram
28.11.2017 securityaffairs Virus
Google identified a new family of Android malware dubbed Tizi spyware by using Google Play Protect, it spies on popular apps like WhatsApp and Telegram.
In May, Google introduced the defense system called Google Play Protect to protect the Android devices, it implements a machine learning and app usage analysis to identify any malicious activity on the mobile device.
Recently, Google identified a new family of Android malware dubbed Tizi spyware by using Google Play Protect. Tizi infected targeted devices in African countries, specifically in Kenya, Nigeria, and Tanzania.

Tizi is a fully-featured Android backdoor with rooting capabilities that installs spyware to steal sensitive data from popular social media applications, including Facebook, Twitter, WhatsApp, Viber, Skype, LinkedIn, and Telegram.
“The Google Play Protect security team discovered this family in September 2017 when device scans found an app with rooting capabilities that exploited old vulnerabilities,” reads a blog post published by Google. “The team used this app to find more applications in the Tizi family, the oldest of which is from October 2015.”
The mobile apps infected with Tizi spyware are being advertised on social media websites and 3rd-party app stores.
Once installed on the target device, the malicious app gains root access to install spyware, then the malicious code contacts the command-and-control servers by sending an SMS text message with the GPS coordinates of the infected device to a specific number.Experts discovered that the Tizi malware is installed by the backdoor that exploits known vulnerabilities, including CVE-2012-4220, CVE-2013-2596, CVE-2013-2597, CVE-2013-2595, CVE-2013-2094, CVE-2013-6282, CVE-2014-3153, CVE-2015-3636, and CVE-2015-1805.
If none of the above flaws could be used to install the Tizi spyware, the backdoor will attempt to perform some actions get higher privileges, for example asking the user to grant them.
“If a Tizi app is unable to take control of a device because the vulnerabilities it tries to use are are all patched, it will still attempt to perform some actions through the high level of permissions it asks the user to grant to it, mainly around reading and sending SMS messages and monitoring, redirecting, and preventing outgoing phone calls.” continues Google.
The Tizi spyware is able to communicate with the command-and-control servers over regular HTTPS, and also through the MQTT messaging protocol using a custom server.
The Tizi spyware contains various capabilities common to commercial spyware:
Stealing data from popular social media platforms, including Facebook, Twitter, WhatsApp, Viber, Skype, LinkedIn, and Telegram.
Recording calls from WhatsApp, Viber, and Skype.
Sending and receive SMS messages.
Accessing calendar events, call log, contacts, photos, and list of installed apps
Stealing Wi-Fi encryption keys.
Recording ambient audio and take pictures without displaying the image on the device’s screen.
Google has identified 1,300 Android devices infected by Tizi and removed it, it also shared suggestions to reduce the chance of users’ devices being infected.
Check permissions: Be cautious with apps that request unreasonable permissions. For example, a flashlight app shouldn’t need access to send SMS messages.
Enable a secure lock screen: Pick a PIN, pattern, or password that is easy for you to remember and hard for others to guess.
Update your device: Keep your device up-to-date with the latest security patches. Tizi exploited older and publicly known security vulnerabilities, so devices that have up-to-date security patches are less exposed to this kind of attack.
Google Play Protect: Ensure Google Play Protect is enabled.
Locate your device: Practice finding your device, because you are far more likely to lose your device than install a PHA.
ICOs: The Lawless Land of Cryptocurrency Fundraising
28.11.2017 securityweek IT
From raising $30 million in 30 seconds to being endorsed by Paris Hilton or vanishing into thin air: anything is possible in the risky new world of cryptocurrency fundraising, but regulators are lurking.
Bypassing oversight of any kind, Initial Coin Offerings (ICOs) have sprung from nowhere to become a hugely popular way for start-ups to raise funds online, offering self-created digital "tokens" or coins to any willing buyer.
ICOs herald "the democratisation of investment", said Nil Besombes, a French blogger specialized in digital currencies.
But in the lawless Wild West of ICOs, the risks are legion and Besombes himself admits to losing "the equivalent of 1,800 euros" when he fell for a slick online sales pitch -- only for the company to disappear without a trace.
"It's like gambling," he told AFP.
While the term ICO may suggest a link with conventional Initial Public Offerings (IPOs), there is no flotation on the stock market and the ICO investor typically holds no ownership stake in the company which would entitle them to a slice of profits distributed as dividends.
ICOs are thus essentially a form of crowdfunding where participants are betting that the value of their "tokens" will go up and that they will eventually be able to trade them for established cryptocurrencies like bitcoin and Ethereum, which can in turn be exchanged for traditional currencies.
ICOs have exploded this year with investors pouring $3.6 billion into 228 projects, according to data from Coinschedule. In 2016, that figure stood at just $96 million for 46 ICOs.
By June of this year, the money raised through ICOs surpassed that of early stage venture capital investments, the traditional way for young companies to raise funds from wealthy investors.
The ICO craze has drawn the attention of regulators around the world, who have warned of the risks of fraud, the volatility of virtual currencies and the lack of clarity on what a "token" represents.
"A lot of ICOs see values plummet by 80 or 90 percent but they can rebound strongly once the project begins to deliver results," said Tristan Colombet, head of the French auction platform Domraider, itself funded by an ICO.
The "tokens" offered by his company are currently worth just a third of what they were at the launch, to the dismay of investors.
Colombet says things will pick up "in early 2018" when his system to track auctions online and in the auctioneering room in real time is fully implemented, using the same "blockchain" technology that underpins bitcoin and many of the tech start-ups in the ICO universe.
Celebs and 'digital gold'
The gold rush fever surrounding ICOs is partly down to the soaring success of bitcoin, which first hit parity with the US dollar in 2011, two years after it was created.
Since then, the world's best-known virtual currency has enjoyed a meteoric rise, defying predictions of a crash. It has now surpassed $9,500.
Many ICO investors are lured by the possibility of stumbling upon the next "digital gold".
Firms issuing ICOs have raised their visibility by enlisting celebrities like LA socialite Paris Hilton, hip-hop producer DJ Khaled and US boxer Floyd Mayweather to tout their digital tokens on social media.
The endorsements prompted the US Securities and Exchange Commission to warn this month that celebrities "often do not have sufficient expertise" to judge such investments, and that they must disclose if they are receiving compensation for promoting ICOs.
Scrambling to respond
The proliferation of ICOs has forced regulators around the world to take notice, their responses ranging from a crackdown to a wait-and-see approach.
China and South Korea have banned ICOs outright, while European supervisory bodies have voiced strong concerns.
The UK's financial regulator cautioned against the "very high-risk, speculative investments", while Germany's powerful Bundesbank central bank warned that the ICO trend was "attracting fraudsters".
The European Securities and Markets Authority (ESMA) said investors risked having no legal recourse in case of a dispute, as ICOs tend to fall "outside of the scope of EU laws and regulations".
Canadian and Russian regulators however have chosen another path by creating so-called "regulatory sandboxes", a framework that allows ICO firms to experiment for a certain time without falling foul of securities laws.
"We welcome this type of innovation," said Louis Morisset, president of the Canadian Securities Administrators, while stressing that ICO issuers should "understand what obligations may apply".
Bulletproof Coffee Failed to Keep Hackers Out
28.11.2017 securityweek Cyber
Bulletproof 360, the Bellevue, Wash.-based company that offers Bulletproof coffee and dietary supplements, is having trouble keeping cybercriminals out of its systems. The firm has sent out several notifications in the past year informing customers that hackers may have obtained their personal and payment card information.
Bulletproof only has three physical stores in Seattle and Los Angeles, but many people buy the company’s products from its website, which appears to have been breached several times in the past year.
The company first discovered that hackers had broken into its website on February 23, 2017. An investigation revealed that cybercriminals had compromised Bulletproof’s e-commerce system and they may have obtained payment card data submitted by users who had made online purchases, including names, card numbers, expiration dates, and CVVs. The exposed data also included email addresses, physical addresses and phone numbers.
An initial investigation found that the hackers had access to Bulletproof’s systems from October 26, 2016 until January 31, 2017. However, the final forensics report revealed that the attackers actually had access until May 30, 2017, which triggered a second breach notification for the period between February and May 2017.
Bulletproof then initiated another internal investigation, which showed that hackers had compromised the checkout page on its website, bulletproof.com, in an effort to capture payment card data submitted by customers making online purchases. This time, the attackers appeared to have had access between August 28, 2017 and September 5, 2017.
In the notifications sent out on September 15, the company told customers that it had “implemented enhanced security measures, including installing a new website security platform, implementing a security information and event management system (SIEM), and implementing enhanced logging” in an effort to prevent future incidents.
However, the new security measures did not help much and this week Bulletproof started sending out a new round of data breach notifications. It turns out that cybercriminals may have also intercepted information submitted to the company via the checkout page on its website between May 20 and October 13, 2017, and October 15-19, 2017.
The company has promised to reimburse affected customers for costs incurred as a result of these breaches if their financial institution refuses to reimburse them. It remains to be seen if this is the last breach notice sent out by the company or if hackers will gain access to its systems once again – if they haven’t done so already.
UPDATE. Bulletproof has sent SecurityWeek the following statement:
We became aware of a security incident involving our ecommerce website after noticing unusual activity relating to customer online transactions. We then began an immediate investigation of our website, engaged three computer security firms to examine our systems for any signs of an issue, and notified law enforcement. Our investigation earlier determined that an unknown third party had compromised our e-commerce system, potentially affecting customer payment card information used for online transactions on Bulletproof’s e-commerce website from October 26, 2016 to May 30, 2017. Working with the security firms, we recently determined that payment card information used on our ecommerce website from October 26, 2016 through October 13, 2017 and from October 15-19, 2017 may have been compromised. We immediately removed the code and have notified potentially affected customers of the incident.
Protecting our customers’ information remains a top priority and we regret any inconvenience or concern this may cause our customers. We recognize the importance of protecting our customers’ payment card information. We are continuing to work with the three security firms to implement enhanced security measures to try to prevent a similar incident from happening in the future.