Hacker Distributes Backdoored IoT Vulnerability Scanning Script to Hack Script Kiddies
10.11.2017 thehackernews Vulnerebility
Nothing is free in this world.
If you are searching for free hacking tools on the Internet, then beware—most freely available tools, claiming to be the swiss army knife for hackers, are nothing but a scam.
For example, Cobian RAT and a Facebook hacking tool that we previously reported on The Hacker News actually could hack, but of the one who uses them and not the one you desire to hack.
Now, a security researcher has spotted another hacking tool—this time a PHP script—which is freely available on multiple popular underground hacking forums and allows anyone to find vulnerable internet-connected IP Cameras running the vulnerable version of GoAhead embedded web-server.
However, after closely analysing the scanning script, Newsky Security researcher Ankit Anubhav found that the tool also contains a secret backdoor, which essentially allows its creator to "hack the hacker."
"For an attacker’s point of view, it can be very beneficial to hack a hacker," Anubhav said.
"For example, if a script kiddie owns a botnet of 10,000 IoT and if he gets hacked, the entire botnet is now in control of the attacker who got control of the system of this script kiddie. Hence, by exploiting one device, he can add thousands of botnets to his army."
The rise of IoT botnet and release of Mirai's source code—the biggest IoT-based malware threat that emerged last year and took down Dyn DNS service—has encouraged criminal hackers to create their massive botnet either to launch DDoS attacks against their targets or to rent them to earn money.
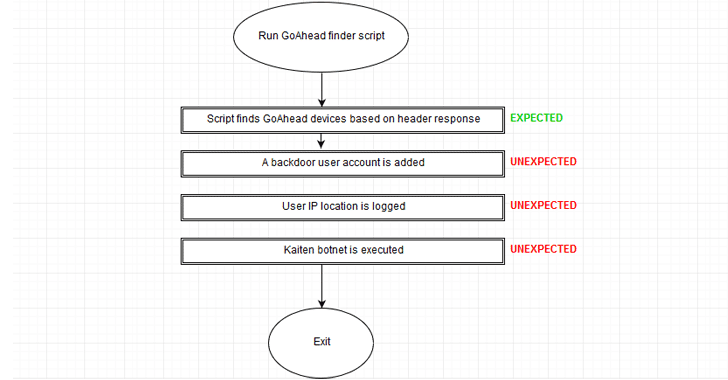
As shown in the self-explanatory flowchart, this IoT scanning script works in four steps:
First, it scans a set of IP addresses to find GoAhead servers vulnerable to a previously disclosed authentication bypass vulnerability (CVE-2017-8225) in Wireless IP Camera (P2P) WIFI CAM devices.
In the background, it secretly creates a backdoor user account (username: VM | password: Meme123) on the wannabe hacker's system, giving the attacker same privilege as root.
Script also extracts the IP address of the wannabe hacker, allowing script author to access the compromised systems remotely.
Moreover, it also runs another payload on the script kiddie’s system, eventually installing a well-known botnet, dubbed Kaiten.
This tool is another example of backdoored hacking tools increasingly being distributed at various underground forums to hack the hacker.
In September, a backdoored Cobian RAT builder kit was spotted on multiple underground hacking forums for free but was caught containing a backdoored module that aimed to provide the kit's authors access to all of the victim's data.
Last year, we reported about another Facebook hacking tool, dubbed Remtasu, that actually was a Windows-based Trojan with the capability to access Facebook account credentials, but of the one who uses it to hack someone else.
The bottom line: Watch out the free online stuff very carefully before using them.
Russian 'Fancy Bear' Hackers Using (Unpatched) Microsoft Office DDE Exploit
10.11.2017 thehackernews APT

Cybercriminals, including state-sponsored hackers, have started actively exploiting a newly discovered Microsoft Office vulnerability that Microsoft does not consider as a security issue and has already denied to patch it.
Last month, we reported how hackers could leverage a built-in feature of Microsoft Office feature, called Dynamic Data Exchange (DDE), to perform code execution on the targeted device without requiring Macros enabled or memory corruption.
DDE protocol is one of the several methods that Microsoft uses to allow two running applications to share the same data.
The protocol is being used by thousands of apps, including MS Excel, MS Word, Quattro Pro, and Visual Basic for one-time data transfers and for continuous exchanges for sending updates to one another.
Soon after the details of DDE attack went public, several reports emerged about various widespread attack campaigns abusing this technique in the wild to target several organisations with malware.
Now, for the first time, this DDE attack technique has been found leveraging by an Advanced Persistent Threat (APT) hacking group—APT28, which is well known as Fancy Bear and is widely believed to be backed by the Russian government.
Russian Hackers Using New York Terror Attack to Lure Victims
While analyzing a new spear phishing campaign, security researchers discovered that the Fancy Bear hackers have been leveraging the DDE vulnerability since late October, according to a recent report published Tuesday by McAfee researchers.
The campaign involved documents referencing the recent terrorist attack in New York City in an attempt to trick victims into clicking on the malicious documents, which eventually infects their systems with malware.
Since DDE is a Microsoft's legitimate feature, most antivirus solutions don't flag any warning or block the documents with DDE fields.
Therefore, anyone who clicks on the malicious attachment (with names like SabreGuard2017.docx or IsisAttackInNewYork.docx) inadvertently runs malicious code on his/her computer without any restriction or detection.
Once opened, the document runs contacts a command-and-control server to install the first stage of the malware called Seduploader on victims' machines using PowerShell commands.
Seduploader then profiles prospective victims by pulling basic host information from the infected system to the hackers. If the system is of interest, the attackers later install a more fully featured piece of spyware—X-Agent and Sedreco.
"APT28 is a resourceful threat actor that not only capitalizes on recent events to trick potential victims into infections but can also rapidly incorporate new exploitation techniques to increase its success," Mcafee researchers concluded.
"Given the publicity the Cy Con U.S campaign received in the press, it is possible APT28 actors moved away from using the VBA script employed in past actions and chose to incorporate the DDE technique to bypass network defenses."
This is not first malware campaign that has been spotted abusing the DDE attack technique.
Soon after the details of DDE attack technique went public, Cisco's Talos threat research group uncovered an attack campaign that was actively exploiting this attack technique to target several organisations with a fileless remote access trojan called DNSMessenger.
Late last month, researchers discovered a campaign that spread Locky ransomware and TrickBot banking trojan via Word documents that leveraged the DDE technique.
Another separate malware spam campaign discovered by security researchers also found distributing Hancitor malware (also known as Chanitor and Tordal) using Microsoft Office DDE exploit.
Protection Against DDE Malware Attacks
Since Microsoft does not provide any protection against such attacks, you can easily prevent yourself from falling victim to any malicious document abusing the Microsoft's DDE feature by disabling it entirely.
If you use Microsoft Word 2016 or Microsoft Excel 2016, go to Options → Advanced, and then remove the checkmark from "Update automatic links at open" which is listed under the general group on the page.
In MS Excel, you can also consider checking "Ignore other applications that use Dynamic Data Exchange (DDE)."
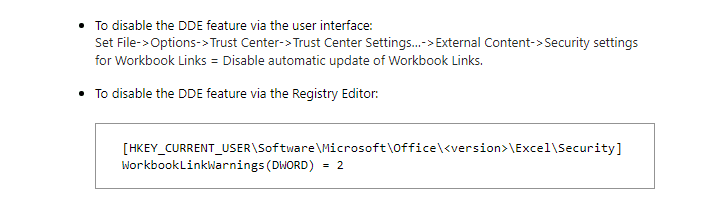
Moreover, Disable DDEAuto is a Registry file maintained on GitHub that disables the "update links" as well as "embedded files" functionality in MS Office documents when run.
You can detect Office documents abusing the DDE feature via a set of YARA rules in Office Open XML files published by the researchers at NVISO Labs.
However, the best way to protect yourself from such malware attacks is always to be suspicious of uninvited documents sent via emails and never click on links inside those documents unless adequately verifying the source.
Equifax: Hack Related Expenses Cost Company $87.5 Million in Q3
10.11.2017 securityweek Incindent
Equifax on Thursday said that during the third quarter of 2017, it incurred $87.5 million in expenses related to the massive hack that was disclosed on September 7, 2017.
The credit reporting agency provided a breakdown of expenses as follows: $55.5 million in product costs, $17.1 million professional fees—a good portion which likely was paid to FireEye's Mandiant division, attorney's, and any other firms hired as part of the incident investigation and response. Customer support costs was marked at $14.9 million.
The expenses related to the cybersecurity incident, the company says, include “costs to investigate and remediate the cybersecurity incident and legal and other professional services related thereto, all of which were expensed as incurred.”
The company also said that it would be liable for additional costs stemming from the free credit file monitoring and identity theft protection that it is offering all U.S. consumers.
“We have therefore recorded an estimate of the expenses necessary to provide this service to those who have signed up or will sign up by the January 31, 2018 deadline. We have incurred $4.7 million through September 30, 2017 and have estimated a range of additional costs between $56 million and $110 million,” Equifax said in an earnings release.
Soon after the breach was disclosed, Chief Security Officer Susan Mauldin and Chief Information Officer David Webb announced their immediate departure from the company.
Equifax says that it maintains data on more than 820 million consumers and more than 91 million businesses worldwide.
In addition to the direct costs associated with the breach, Equifax has lost billions in market cap due to a falling share price after the breach was disclosed. Immediately prior to the breach being disclosed, shares of Equifax traded at roughly $142. Shares of the company (NYSE: EFX) are currently trading at $106.20 in after hours trading.
Day Trader Indicted for Hacking, Securities Fraud
10.11.2017 securityweek Hacking
A day trader has been indicted on four counts for his alleged role in a scheme that involved hacking into online brokerage accounts and using them to make fraudulent transactions.
Joseph Willner, 42, of Ambler, Pennsylvania, has been charged with conspiracy to commit wire fraud, conspiracy to commit securities fraud and computer intrusions, securities fraud, and conspiracy to commit money laundering.
Charges were first brought against Willner late last month by the U.S. Securities and Exchange Commission (SEC), which claimed the man made at least $700,000 through unauthorized trades involving more than 100 hacked brokerage accounts. The U.S. Attorney’s Office for the Eastern District of New York and the Department of Justice Criminal Division’s Fraud Section announced bringing charges against Willner this week.
According to authorities, between September 2014 and May 2017, the suspect and other unnamed individuals hacked into online brokerage accounts and used that access to purchase stock at artificially high prices they set by placing short sale offers using their own brokerage accounts.
After purchasing stock through victims’ accounts at above-market prices, they repurchased the stock at below-market prices. These activities took place within minutes and the operators of the scheme quickly made a profit, which they laundered by acquiring bitcoins.
In one example described in the indictment, Wilner used his own brokerage account to place a short sale order for 537 shares priced at $14.88 per share and executed the trade against one of the hacked accounts. He then repurchased the shares at $9.40 per share, landing him a profit of nearly $3,000.
Members of the scheme often used direct messages on Twitter and IRC chatrooms to communicate.
Investigators determined that the actions of Willner and his co-conspirators, one of which has been described as a foreign national, cost brokerage firms more than $2 million.
Wilner was arrested in mid-June in his hometown. If convicted, he faces up to 20 years in prison, the Justice Department said.
“This case involves a 21st Century cyber boiler room, except the buyers were not even aware they were purchasing shares of stock,” said William F. Sweeney, Jr., Assistant Director-in-Charge at the FBI’s Field Office in New York.
NATO to Increase Cyber Weaponry to Combat Russia
10.11.2017 securityweek BigBrothers
NATO members agreed Wednesday to increase the use of cyber weaponry and tactics during military operations, with the alliance also upgrading other capabilities to combat a resurgent Russia.
The changes are part of the alliance's biggest shakeup since the Cold War, with defence ministers backing the creation of two new command centres to help protect Europe.
The revamp reflects the "changed security environment" of recent years, NATO chief Jens Stoltenberg said at a meeting of defence ministers in Brussels.
The threat to the alliance's eastern flank has grown as a concern after Russia's annexation of Crimea in 2014.
"We are now integrating cyber effects into NATO missions and operations to respond to a changed and new security environment where cyber is part of the threat picture we have to respond to," Stoltenberg said.
"In any military conflict cyber will be an integral part and therefore we need to strengthen our cyber defences and our cyber capabilities," he added, noting that such tactics have been effective in the fight against IS in Iraq and Syria.
After years of stripping back its command structure since the end of the Cold War, NATO wants to add the new command centres -- one to protect lines of communication across the Atlantic and one to coordinate the movement of troops and equipment around Europe.
- NATO hit by cyber attacks -
The creation of a new NATO cyber operations hub comes as the alliance faces hundreds of attacks on its networks every month and fears grow over the Kremlin's electronic tactics.
NATO declared cyber -- where attackers disrupt websites, intercept communications and sabotage technologies used in combat -- as a conflict domain last year, putting it on a par with land, sea and air.
"We have seen a more assertive Russia, we have seen a Russia which has over many years invested heavily in their military capabilities," Stoltenberg said.
"NATO has to be able to respond to that. We are constantly adapting and what we are doing in Europe now is part of that adaptation."
Cyber capabilities will now be included in NATO missions in the same way as planes, tanks and ships -- fully integrated but still under the control of the contributing country.
The two-day meet at NATO headquarters will also cover the North Korean nuclear crisis, which will be the focus of a working dinner on Wednesday, where defence ministers will be joined by the EU's diplomatic chief Federica Mogherini.
US President Donald Trump arrived in on Beijing Wednesday to press China to do more to get Pyongyang to curb its nuclear and ballistic weapons programmes.
- US role in Syria? -
Tensions have soared since Pyongyang carried out its sixth nuclear test -- its most powerful to date.
"All NATO allies agree that we have to put strong pressure on North Korea because North Korea is responsible for reckless behaviour, irresponsible behaviour developing nuclear weapons and by developing missiles," Stoltenberg said.
On Thursday talks will turn to Afghanistan, where NATO plans to boost its training and support mission for local forces by some 3,000 troops.
Later in the day US Defense Secretary Jim Mattis will hold a separate meeting with partners from the coalition fighting IS in the Middle East, where the jihadists continue to lose territory.
As he flew to Europe, Mattis told reporters that coalition partners are looking to the United States for a clear plan about what follows the physical defeat of IS.
"Maybe three-quarters of the questions I am getting asked now is (about) going forward. They are now saying: 'What's next? How is it looking?'" Mattis said.
Following back-to-back losses, including of their Syrian and Iraqi strongholds of Raqa and Mosul, IS fighters are down to defending their last holdouts along the Euphrates River valley.
America's military involvement in Syria has until now been focused solely on fighting IS.
A French source also said allies were keen to hear what Mattis had to say about the role of Iran -- a key supporter of Syrian President Bashar al-Assad -- following Trump's tough rhetoric against Tehran.
Researcher Bypasses IDS Using IDS Signatures
10.11.2017 securityweek Attack
Bucharest - DefCamp 2017- Intrusion detection system (IDS) signatures can be used as an evasion technique to bypass the IDS itself, a security researcher claims.
During a presentation at the DefCamp 2017 security conference in Bucharest, Romania, Kirill Shipulin, a security researcher atPositive Technologies, explained that available IDS signatures can be turned against the system to paralyze its defenses. He also argued that compromises between performance and security can produce opportunities for bypass.
Signature-based IDS relies on discovering specific patterns for the detection of attacks, either by looking for byte sequences in network traffic, or for known malicious instruction sequences used by malware.
The main limitation of such systems is that they can’t detect attacks for which no pattern is available. However, there’s also the gap between when a new threat has been discovered and when its signature starts being applied to the IDS that an attacker can exploit without fearing that the intrusion could be detected.
Many of the available signatures have been designed to protect systems from public exploits, and designing high-quality signatures requires a wide range of skills from the developer in order to avoid false-positives, Shipulin says. What’s more, slow, inefficient signatures can create weaknesses in IDS, adding to the range of already available common bypass techniques.
“Signature are expert knowledge shaped into forms that the system understands. Developers usually have limited or no time to analyze a vulnerability in depth and devise a fix. They also need to focus on performance, and this could lead to errors,” the security researcher told SecurityWeek during an interview at DefCamp.
Some of the available signatures can be slow, requiring a lot of time to perform the necessary analysis. The researcher demonstrated that when such a rule meets bad traffic, the system can become paralyzed and can start dropping traffic. This can result in either denial of service or in the bypass of the detection system.
While planning IDS/IPS capacity, a rule of thumb to follow is to assign only a limited number of signatures and amount of traffic to each processor, thus ensuring that the system can do its job efficiently.
According to Shipulin, who performed his research using the open source Suricata network threat detection engine, it takes more time for a signature to find no match than to find any match. This hurts performance, he added.
Suricata, which was designed to use “a powerful and extensive rules and signature language” and offers support for standard input and output formats like YAML and JSON, was built in a special performance mode. However, a vulnerability addressed in the platform not long ago can be exploited to create bad traffic and load the system to the full, thus bypassing defenses.
Tracked as CVE-2017-15377 and impacting Suricata before 4.x, the vulnerability makes it possible to “trigger lots of redundant checks on the content of crafted network traffic with a certain signature.” Basically, the search engine would continue the check even after no match was found, and would stop only upon reaching inspection-recursion-limit (3,000 by default).
Suricata takes advantage of regular expressions (PCRE), and Shipulin discovered that he could determine the string an expression was designed to search for. Using amplification, he also discovered that he could load the system to the full: with a PCRE check taking around 1.5 million CPU ticks, a 1000 times amplification would result in over 3 billion ticks, which would be a second for the processor.
Paired with the fact that Suricata performs checks even after no match was found, this led the researcher to discover that he could use only 250Kb of network traffic per second to load to the full 8 out of 40 cores on a corporate server. At 10 HTTP POST requests per second, the system starts dropping packets and is bypassed. He used a clean installation, so the amount of network traffic required in real-life corporate networks could be much lower.
“There is no automatic way to detect slow signatures, which means that the discovered attack goes undetected,” the researcher said. “Once we manage to make the system to drop packets, we can shut it down,” he continues.
Shipulin also points out that there are other systems that use signature-based detection that attackers could abuse in a similar manner, especially since the attack vector is silent. However, he also points out that the signatures themselves aren’t the problem, but that they do require quality checking.
“This is only one method we found to create bad traffic and amplify slow signatures. There might be other methods, other cases, other keyword combinations that an actor could use to paralyze or bypass a defense system,” Shipulin told SecurityWeek.
Microsoft Issues Advisory for Mitigating DDE Attacks
10.11.2017 securityweek Attack
A security advisory published by Microsoft on Wednesday provides information on how users can protect themselves against recent attacks abusing the Dynamic Data Exchange (DDE) protocol.
DDE is designed for data exchanges between Office and other Windows applications. Researchers warned recently that the way DDE fields are processed could be abused by hackers to create documents that load malicious resources from an external server. The technique can be used as a substitute for macros in attacks involving documents.
DDE has been abused in attacks by various types of threat actors, including by cybercriminals who are trying to make a profit using the Locky ransomware and Russia-linked cyberspies known for targeting high-profile organizations.
While at some point it may release an update that would prevent DDE attacks, Microsoft highlighted that DDE is a legitimate feature and there already are several protections and mitigations in place.
The company pointed out that for an attack to work, victims need to be convinced to disable Protected Mode and click through some prompts referencing linked files and remote data.
Additionally, Microsoft said Office users can enable specific registry keys that improve security, including a key that disables automatic data updates from linked fields.
The tech giant has provided detailed information on how automatic link updates can be disabled in Excel, Outlook, Publisher and Word by setting specific registry keys. However, disabling the feature could impact legitimate functionality that leverages DDE and users might need to manually update fields.
In the case of Windows 10 Fall Creators Update, users are protected against DDE attacks by the Attack Surface Reduction (ASR) mitigation included in Windows Defender Exploit Guard.
Since malicious documents exploiting DDE are typically delivered via email, Microsoft has advised users to act with caution when opening suspicious attachments.
The latest report on DDE attacks comes from McAfee and it describes a campaign launched by the Russia-linked cyber espionage group tracked as APT28 and Fancy Bear. The attackers used documents referencing the recent terrorist attack in New York and the Saber Guardian military exercise to deliver reconnaissance malware.
Security Startup SlashNext Taps Cognitive Computing to Detect Attacks
10.11.2017 securityweek Attack
One effect of the improving ability of security defenses to detect malicious files has been the adversaries' switch from malware to social engineering and fileless attacks. It is an example of 'human reasoning', the ability to change tactics to defeat new defenses.
Pleasanton, Calif-based SlashNext believes that only human reasoning defenses can keep up with human reasoning attackers. It has launched a new product based on cognitive computing rather than supervised machine-learning. Called the Internet Access Protection System (IAPS), it is, says SlashNext CEO and founder Atif Mushtaq, "the industry's first security solution that uses the power of cognitive computing to detect advanced cyberattacks in the same way that humans do -- except without human limits and without human errors."
Rather than using malware signatures or sandboxes and behavioral analysis to detect malware, IAPS uses its own cognitive computing engine called Progressive Learning to detect attacks. It uses a protocol centric approach that works independent of OS or end-point device, and concentrates on the one single common factor for (almost) all cyberattacks: the internet access point. In this way, it is unconcerned whether it is phishing, or malware or fileless -- it aims to detect all attacks.
Doing so requires a new approach. While machine learning proved effective against many new variants of malware, it cannot detect new malware with previously unseen behaviors that do not match its pre-coded algorithms. SlashNext's new approach is to use cognitive computing -- which is designed to use computer processing power in a manner that mimics human intelligence.
The cloud-based Progressive Learning technology is capable of analyzing gigabits of internet-bound traffic in real time to detect indicators of compromise (IOCs). The IOCs are passed to a set of reasoning engines that behave like human researchers to determine whether they are malicious or not malicious. The result is fed back into the system as part of the peer-to-peer learning process that gives the system its self-teaching capability.
Sensors are deployed at all network egress points. They are simply installed and require neither configuration nor tweaking since all the heavy-lifting is done by Progressive Learning in the cloud. IAPS blocks malicious activity in real-time, prevents data exfiltration and stops machines accessing malicious sites. The concept is similar to having a team of expert threat hunters watching all traffic and analyzing it in real time. Just as human experts get more proficient with experience, so does IAPS understand changing adversary tactics as they evolve.
"The last few years have seen an explosion of social engineering attacks that don't rely on malware or exploits to penetrate defenses. That's left businesses urgently in need of an innovative new approach to security that goes far beyond the sandbox," said Gaurav Garg, Founding Partner of Wing Venture Capital. "By harnessing the power of cognitive computing in its IAPS, SlashNext is taking cyber defense to a completely new level."
SlashNext was founded by Asif Mushtaq in 2014. Mushtaq previously spent 9 years as a senior scientist for FireEye, where he was the lead architect of FireEye's core malware detection system. SlashNext received $9 million in Series A funding in April 2017 from Norwest Venture Partners and Wing Venture Capital. IAPS is available now as a subscription service either direct from SlashNext or via a VAR.
WikiLeaks Says CIA Impersonated Kaspersky Lab
10.11.2017 securityweek BigBrothers
WikiLeaks has resumed its CIA leaks and it has now started publishing source code and other files associated with tools allegedly developed by the intelligence agency.
In March, WikiLeaks began publishing documentation files describing what appeared to be CIA hacking tools as part of a leak dubbed Vault 7. Roughly two dozen tools and projects were disclosed over the course of several months.
Now, after a two-month break, WikiLeaks announced a new round of leaks dubbed Vault 8, which provides source code and analysis for CIA tools. The organization pointed out that, similar to Vault 7, Vault 8 will not expose any zero-day or other vulnerabilities that could be used for malicious purposes.
“This publication will enable investigative journalists, forensic experts and the general public to better identify and understand covert CIA infrastructure components,” WikiLeaks said. “Source code published in this series contains software designed to run on servers controlled by the CIA.”WikiLeaks announces Vault 8 leaks
The first Vault 8 leak covers Hive, a project whose documentation was published by WikiLeaks in mid-April. The organization has now released source code and development logs for Hive.
Hive has been described as a tool designed to help malware communicate with a remote server without raising suspicion.
“Using Hive even if an implant is discovered on a target computer, attributing it to the CIA is difficult by just looking at the communication of the malware with other servers on the internet,” WikiLeaks said. “Hive provides a covert communications platform for a whole range of CIA malware to send exfiltrated information to CIA servers and to receive new instructions from operators at the CIA.”
Hive provides a communication channel between a piece of malware and what WikiLeaks describes as “cover domains.” These domains are boring-looking and they deliver harmless content when accessed.
However, malware implants communicating with these domains authenticate themselves and the traffic they generate is directed to a gateway called Honeycomb, which sends the data to its final destination.
Implants authenticate themselves using digital certificates that impersonate existing entities. One fake certificate is for Russia-based security firm Kaspersky Lab and it pretends to have been issued by South African certificate authority Thawte.
According to WikiLeaks, its analysis revealed that by using these fake certificates, the CIA made it look like data was being exfiltrated by one of the impersonated entities – in this case Kaspersky Lab.
“We have investigated the claims made in the Vault 8 report published on November 9 and can confirm the certificates in our name are fake,” Kaspersky Lab told SecurityWeek. “Our private keys, services and customers are all safe and unaffected.”
The news that the CIA may have impersonated Kaspersky Lab in its operations has led some to believe that the U.S. may have actually used such tools to falsely pin cyberattacks on Russia.
The U.S. government has banned the use of Kaspersky products due to the company’s alleged ties to Russian intelligence. A recent report also claimed that Kaspersky products had been used on the computer of an NSA contractor from which Russian hackers stole sensitive files. Kaspersky has denied the allegations and announced a new transparency initiative in an effort to clear its name.
Twilio Credentials Hardcoded in Mobile Apps Expose Calls, Texts
9.11.2017 securityweek Mobil Android iOS
Hundreds of mobile applications that use the Twilio SDK or REST API include hardcoded credentials that could be abused to access millions of calls and text messages, researchers warned on Thursday.
Appthority’s Mobile Threat Team has analyzed more than 1,100 iOS and Android applications that use Twilio, a cloud communications platform designed for developing voice and messaging apps.
Twilio’s documentation provides guidance on best security practices, but researchers found that 686 apps from 85 developers exposed Twilio account IDs and access tokens (i.e. passwords). Roughly one-third of the applications containing hardcoded Twilio credentials are business-related, and the ones designed for Android have been downloaded between 40 and 180 million times.
The affected apps, more than 170 of which are still available on Google Play and the Apple App Store, include software used for secure communications by a federal law enforcement agency, one that allows sales teams to record audio and annotate discussions in real-time, and navigation apps for AT&T and US Cellular customers.
Researchers estimated that by extracting the Twilio account credentials from the source code of these apps, malicious actors could have gained access to hundreds of millions of call records, calls and call audio recordings, and SMS and MMS messages. North America, the U.K. and Australia are the most affected regions.
The vulnerability, which Appthority has dubbed “Eavesdropper,” was discovered in April and Twilio was notified in July. The service provider has been working with the developers of the impacted apps to address the issue.
However, researchers pointed out that the only way for developers to properly address the problem is to get their users to install an updated version of their app that does not include hardcoded credentials and change their Twilio account tokens.
Hardcoded credentials can pose a serious risk, not just for apps that use Twilio. Appthority warned that roughly 40% of the analyzed applications also expose Amazon S3 credentials.
Researchers have found credentials for more than 2,000 Amazon accounts in the analyzed apps. A closer analysis showed that roughly 900 of the accounts are still active and they provide access to nearly 22,000 S3 buckets, including ones that store potentially sensitive information.
“Eavesdropper poses a serious enterprise data threat because it allows an attacker to access confidential company information, which may include a range of sensitive information often shared in an enterprise environment, such as negotiations, pricing discussions, recruiting calls, product and technology disclosures, health diagnoses, market data or M&A planning,” warned Seth Hardy, Appthority Director of Security Research. “An attacker could convert recorded audio files to text and search a massive data set for keywords and find valuable data.”
Earlier this year, Appthority reported that more than 1,000 iOS and Android applications installed on enterprise mobile devices had been exposing sensitive data via backend systems.
"Tick" Cyber Espionage Group Employs Steganography
9.11.2017 securityweek Krypto
The cyber espionage group known as "Tick" is using steganography to conceal their backdoor Trojan better, according to analysis from security firm Trend Micro.
Also referred to as Bronze Butler and REDBALDKNIGHT and believed to be based in China, the group is mainly targeting Japanese organizations, including biotechnology, electronics manufacturing, and industrial chemistry entities and government agencies. Although the first report on the group was published only last year, the hackers might have been active for at least a decade, Trend Micro's researchers say.
Malicious tools preferred by the threat actors include a downloader tracked as Gofarer and a data-stealing Trojan dubbed Daserf, which can execute shell commands and download and upload data. Now, Trend Micro says that variants of Daserf were used against entities outside Japan as well, including organizations in South Korea, Russia, Singapore, and China.
Furthermore, the security researchers say that various versions of Daserf employ different techniques and use steganography, which allows them to conceal themselves better by embedding codes in unexpected mediums or locations, such as images.
The hackers typically use spear phishing emails with attached malicious documents created using the Japanese word processor Ichitaro. These documents install and execute the Daserf backdoor on the victim’s machine.
Tick is believed to be regularly improving the Daserf Trojan to keep it under the radar.
Some malware variations also revealed that the group integrated steganography to conduct second-stage attacks and for command-and-control (C&C) communication. Through the use of steganography, the backdoor can not only bypass firewalls, but also change second-stage C&C communication or malware faster and more conveniently, Trend Micro says.
Daserf’s infection chain involves a downloader that retrieves the backdoor from a compromised site. After installation, the Trojan connects to another compromised site and downloads an image file, then connects to its C&C and awaits further commands.
The Tick hackers, Trend Micro notes, have been using steganography on other toolkits as well, namely xxmm2_builder and xxmm2_steganography. These are components of the XXMM downloader Trojan that can also be used as a first-stage backdoor. The researchers found that the same steganography algorithm was used on both XXMM and Daserf.
“Steganography is a particularly useful technique in purposeful cyberattacks: the longer their malicious activities stay undetected, the more they can steal and exfiltrate data. And indeed, the routine is increasingly gaining cybercriminal traction, in varying degrees of proficiency—from exploit kits, malvertising campaigns, banking Trojans, and C&C communication to even ransomware. In the case of REDBALDKNIGHT’s campaigns, the use of steganography is further compounded by their use of malware that can better evade detection and analysis,” Trend Micro concludes.
More Prison Time for Ex-Secret Service Agent Who Stole Bitcoins
9.11.2017 securityweek CyberCrime
A former U.S. Secret Service agent already convicted for stealing bitcoins from the now-defunct underground marketplace Silk Road has been handed another prison sentence for the theft of digital currency from the government, the Department of Justice announced this week.
Shaun W. Bridges, 35, of Laurel, Maryland, was sentenced in December 2015 to 71 months in prison for money laundering and obstruction of justice. Bridges, who had been part of the task force investigating Silk Road, stole 20,000 bitcoins, at the time worth roughly $350,000, from Silk Road customers using information obtained following the arrest of one of the site’s customer support representatives. Bridges liquidated the bitcoins in the spring of 2015 and earned $820,000.
According to authorities, before he began serving his sentence for the 2015 conviction, Bridges stole another 1,600 bitcoins from a digital wallet belonging to the U.S. government.
Court documents obtained by Ars Technica show that the former federal agent retained the private key for an account storing bitcoins seized from digital currency exchange Bitstamp. After resigning from the Secret Service, Bridges used the key to transfer roughly 1,600 of the Bitstamp bitcoins from the government’s digital wallet into his own.
Bridges pleaded guilty to money laundering charges related to this case and agreed to return the stolen bitcoins. He received a 24-month prison sentence, which will be served consecutively to the previous 71-month sentence. The defense had hoped to convince the judge to hand out a concurrent sentence.
Bridges is not the only former federal agent sentenced to prison as a result of illegal activities carried out during the investigation into Silk Road. In October 2015, a former Drug Enforcement Administration (DEA) agent, Carl M. Force, was sentenced to 78 months in prison after receiving hundreds of thousands of dollars worth of bitcoin from Ross Ulbricht, the mastermind of Silk Road, for inside information about the government’s investigation into the underground marketplace.
Ulbricht was sentenced to life in prison for his role in running Silk Road. He unsuccessfully appealed the sentence and his later bid for a new trial was denied.
Poland Eyes Cybersecurity in Skies
9.11.2017 securityweek CyberCrime
Poland on Wednesday agreed to test a cybersecurity pilot program for the aviation sector as Europe's EASA civil aviation authority tackles the potential threats posed by hackers to air traffic.
"We want to have a single point in the air transport sector that will coordinate all cybersecurity activities... for airlines, airports and air traffic," Piotr Samson, head of Poland's ULC civil aviation authority, said in Krakow, southern Poland, at a two-day conference co-hosted with the EASA.
While insisting that air travel is currently safe from cyber attacks, EASA executive director Patrick Ky told AFP it was incumbent on aviation authorities to take preventative measures to mitigate potential cyber-threats.
Polish officials attending the "Cybersecurity in Civil Aviation" conference also announced the creation of a "rapid reaction unit" for cybersecurity incidents.
Despite the assurances of experts in the field, computer systems failures triggered by hackers or accident have caused flight chaos in recent years.
Poland's flagship carrier LOT was briefly forced to suspend operations in June 2015 after a hack attack.
The airline's spokesman described the incident as the "first attack of its kind".
Thousands of British Airways passengers faced chaos in May as the airline was forced to cancel more than a hundred flights from London's Heathrow Airport following an IT system failure.
BA officials ruled out a cyber-attack, pointing instead to a power supply issue.
DDoS attacks in Q3 2017
9.11.2017 Kaspersky Analysis Attack
News Overview
In the third quarter of 2017, the trends of the preceding quarters continued to develop further. The number of DDoS attacks in China, the United States, South Korea and Russia increased, which were reflected in the statistics we gathered for botnets. A sharp surge in the number (more than 450 daily) and power (up to 15.8 million packets per second) of attacks was registered in the ‘Australian sector’. The cost of protection increased accordingly: for example, in early September, six IB vendors entered into a $50 million contract with the Singapore government (the previous three-year contract cost the state half that amount).
The biggest success in combating DDoS attacks was the taking down of the huge (hundreds of thousands of devices in more than a hundred countries) WireX botnet. The botnet had been secretly working on Android devices and proliferating via legitimate Google Play applications. The joint actions of Google, Samsung and several large IT security vendors were required to take down the botnet. Given the deplorable state of security on the Internet of things and in micro-applications, such findings are now likely to occur on a fairly regular basis.
Cybercriminals are using their brains as well as their brawn. In mid-August, Imperva described Pulse Wave technology capable of increasing the power of a DDoS attack thanks to a vulnerability in hybrid and cloud technologies. The analysts at Imperva believe that most DDoS attacks will soon follow a similar pattern: short but powerful sudden “punctuated” attacks that last for several hours or several days.
The targets within the scope of the cybercriminals’ interest remain the same. In the political arena, the increase in the number of attacks has even triggered a process of qualitative change: some are voicing the belief that DDoS attacks are a legitimate form of democratic protest. However, the effectiveness of this method is still questionable: the two most notable political acts of the third quarter (an attack on the DreamHost hosting provider and on a libertarian site) achieved nothing apart from greater publicity for the attacked resources.
Cases of blackmail involving DDoS attacks – or rather, attempts that aren’t always very well executed –have become more frequent. While in the previous quarter companies preferred to pay off the attackers, mass mailings with threats are now often perceived as just another wave of spam.
As a means of applying pressure, DDoS attacks are still more beneficial in industries where downtime and communication failures lead to lost profits and reputation. The gaming industry is becoming even more attractive for cybercriminals: the profits here are estimated in the hundreds of billions of dollars, while security is still far from perfect, with hybrid gaming platforms vulnerable to attacks via the links between resources and applications.
In Q3, there were three high-profile incidents involving gaming platforms (not including the DDoS attack on Final Fantasy’s servers, which, according to Square Enix, began in June and lasted till the end of July).
Firstly, in mid-August, Blizzard Entertainment reported a flood of junk traffic that caused problems for players of Overwatch and World of Warcraft.
Secondly, at the beginning of September, the Americas Cardroom online poker site began to experience difficulties. The attack (not the first to target the resource) followed the notorious pattern “demonstrate force, demand a ransom”. The site’s management refused to pay, but was forced to cancel – or more precisely, to delay – a poker championship that was already under way.
At the end of the quarter, on 30 September, the site of the UK National Lottery was seriously affected: for 90 minutes players were unable to place their stakes online or via applications, which caused the service serious losses.
It appears that constant DDoS attacks on the entertainment industry is becoming the new normal: the largest companies will either have to seriously reconsider their approach to security or put customer loyalty at risk. Some of them have started eliminating possible vectors on their own. For example, Netflix (yet another entertainment platform that could lose customers due to a loss of communication) found a serious vulnerability in API and developed two tools to deal with the infected applications.
Probably the most curious attack of the quarter was also related to the entertainment and gaming industry: the cybercriminals hacked a US casino via a smart fish tank. It had nothing to do with DDoS attacks, but it’s interesting that criminals managed to break through to the mainframe and steal 100 GB of confidential data from the organization, although the fish tank was installed on its own VPN. It is highly likely that in the near future the entertainment and gaming sector will be on a par with the financial sector when it comes to the scope and ingenuity of large-scale attacks.
Quarter Trends
In term of trends, there was a fairly new vector of attacks related to the now notorious crypto- currencies. More and more attacks are targeting Initial Coin Offering (ICO) platforms – a type of crowdfunding. Since blockchain technology allows transactions to be conducted safely, ICOs are quickly gaining in popularity. But there are risks as well: with the rapid growth and the increasing turnover of crypto-currencies, such platforms are subjected to cyberattacks, including DDoS attacks. The broad availability of the platform guarantees reliable and secure transactions, while DDoS attacks are aimed at breaking the operability of the service and thus discrediting it or, even worse, creating a smokescreen for more sophisticated types of attacks.
Another detail of this quarter is the increase in the proportion of mixed, multi-component (SYN + TCP Connect + HTTP-flood + UDP flood) attacks. As forecasted earlier, they are gradually gaining in popularity. There is nothing fundamentally new in these attacks, but in the right hands they can be quite effective.
Statistics for botnet-assisted DDoS attacks
Methodology
Kaspersky Lab has extensive experience of combating cyber threats, including DDoS attacks of various complexity types and ranges. The experts of the company have been tracking the actions of botnets by using the DDoS Intelligence system.
Being part of the Kaspersky DDoS Prevention solution, the DDoS Intelligence system is intended to intercept and analyze commands sent to bots from command-and-control servers and requires neither infecting any user devices nor the actual execution of cybercriminals’ commands.
This report contains DDoS Intelligence statistics for the third quarter of 2017.
In the context of this report, it is assumed that an incident is a separate (single) DDoS-attack if the interval between botnet activity periods does not exceed 24 hours. For example, if the same web resource was attacked by the same botnet with an interval of 24 hours or more, then this incident is considered as two attacks. Also, bot requests originating from different botnets but directed at one resource count as separate attacks.
The geographical locations of DDoS-attack victims and C&C servers that were used to send commands are determined by their respective IP addresses. The number of unique targets of DDoS attacks in this report is counted by the number of unique IP addresses in the quarterly statistics.
It is important to note that DDoS Intelligence statistics are limited only to those botnets that have been detected and analyzed by Kaspersky Lab. It should also be noted that botnets are just one of the tools for performing DDoS attacks; thus, the data presented in this report do not cover every single DDoS attack occurred during the indicated period.
Q3 summary
Resources in 98 countries were attacked in Q3 2017 vs. 86 in Q2 2017.
As in Q2, around half of all attacks (51.56%) originated in China.
China, the US, and South Korea remained leaders in terms of both number of attacks and number of targets. According to the number of reported C&C servers, the same countries are make up the TOP 3, though South Korea calimed first place this time.
The longest DDoS attack was 215 hours, a decrease of 28% compared to Q2. At the same time, the share of attacks that lasted less than 50 hours remained practically unchanged (99.6% in Q3 vs. 99.7% in Q2).
As in the previous quarter, there was a considerable drop in the proportion of attacks over TCP (down to 11.2% from 28.2%) and ICPM (down to 7.1% from 9.42%). This caused a rise in the percentage of SYN floods and HTTP attacks.
The proportion of Linux botnets continued to grow. Such botnets were responsible for 69.62% of attacks in Q3 compared to 51.23% in Q2.
Geography of attacks
DDoS attacks were registered in 98 countries in Q3, where the largest number of the attacks were aimed at China (63.30% of all attacks), which is 5.3 p.p. higher than the previous quarter. South Korea’s share fell from 14.17% to 8.70%, moving it to third place. The US came second despite the percentage of attacks originating from this country falling from 14.03% to 12.98%.
The top 10 accounted for 93.56% of all attacks. Germany (1.24%) re-entered the top 10, replacing Italy out of the rating. Hong Kong (1.31%) dropped from 4th to 7th, having lost 1.07 p.p. Russia (1.58%) gained 0.35 p.p. and was once again in fourth place. The UK remained fifth while the Netherlands saw its share go up from 0.84% to 1.31%, moving it to sixth.
Distribution of DDoS attacks by country, Q2 2017 vs. Q3 2017
91.27% of all attacks were aimed at targets in the countries of the top 10 in Q3 2017.
Distribution of unique DDoS-attack targets by country, Q2 2017 vs. Q3 2017
China remained in first place: 51.56% of all targets were located in the territory of the country, an increase of 4.14 p.p. compared to Q2. At the same time, the US and South Korea remained second and third respectively, although the proportion of targets in the territories of both countries fell considerably: from 18.63% to 17.33% in the US, and from 16.35% to 11.11% in South Korea.
The share of targets located in the territory of Russia grew from 1.33% in Q2 to 2.24% in Q3, which saw Russia move up from seventh to fourth place. Australia and Italy left the top 10 and were replaced by France (1.43%) and Germany (1.65%).
Dynamics of the number of DDoS attacks
The number of attacks per day ranged from 296 (24 July) to 1508 (26 September) in Q3 2017. The peak numbers were registered on 27 July (1399) and 24 September (1497). A relative downturn was registered on 28 July (300), 31 May (240), and 25 September (297).
Dynamics of the number of DDoS attacks in Q3 2017*
*Since DDoS attacks may continuously last for several days, one attack may be counted several times in the timeline, i.e., once per day.
In Q3 2017, Monday remained the quietest day for DDoS attacks (10.39% vs 11.78% in the previous quarter), while Thursday became the busiest day (17.54%). Last quarter’s leader, Saturday, came second (15.59%) followed by Sunday (14.89%) and Tuesday (14.79%).
Distribution of DDoS attacks by day of the week, Q2 vs Q3 2017
Types and duration of DDoS attacks
As in the previous quarter, the number of SYN DDoS attacks continued to grow, rising from 53.26% to 60.43% in Q3 2017. At the same time, the percentage of TCP DDoS attacks plummeted from 18.18% to 11.19%, which did not affect second position in the rating for this type of attack. Both UDP and ICMP attacks became quite rare: their share dropped from 11.91% to 10.15% and from 9.38% to 7.08% respectively. Meanwhile, the popularity of HTTP attacks increased from 7.27% to 11.6%, which placed them in third.
Distribution of DDoS attacks by type, Q3 2017
The number of long-term attacks remained almost unchanged from the previous quarter: 0.02% of attacks lasted more than 150 hours (vs 0.01%). The longest attack lasted for 215 hours, 62 hours shorter than the record in Q2. At the same time, the share of attacks that lasted 4 hours or less dropped from 85.93% in Q2 to 76.09% in Q3. Thus, the percentage of attacks lasting from 5 to 49 and from 50 to 99 hours increased, accounting for 23.55% and 0.3% of all attacks respectively.
Distribution of DDoS attacks by duration (hours), Q2 vs Q3 2017
C&C servers and botnet types
The top 3 countries with the greatest number of detected C&C servers remained unchanged from Q2: South Korea, whose share grew from 49.11% to 50.16%, remained top. The US retained second place (16.94% vs 16.07% in Q2). China remained third although its share dropped from 7.74% to 5.86%. The top 3 countries accounted for 72.96% of C&C servers in total, which is only slightly more than in the previous quarter.
The top 10 included Italy (1.63%) and the UK (0.98%), which ousted Canada and Germany in Q3. Compared to Q2 2017, there was a significant increase in the shares of France (up to 2.93% from 1.79%) and Russia (up to 3.58% from 2.68%).
Distribution of botnet C&C servers by country in Q3 2017
In Q3, Linux-based botnets continued to win back positions from Windows: the share of detected Linux-based botnets comprised 69.62%, while the percentage of Windows-based botnets dropped to 30.38%.
Correlation between Windows- and Linux-based botnet attacks, Q3 2017
Conclusion
In the third quarter of 2017, we registered a considerable increase in the number of both DDoS attacks and their targets. Traditionally, China is the country with the largest number of attack sources and targets. It was followed by the United States and South Korea. The popularity of Windows OS as a basis for creating a botnet has fallen noticeably, while the share of Linux-based botnets increased proportionally.
Among this quarter’s trends were increased attacks on ICO platforms: in Q3, crypto-currency was widely discussed both on the Internet and in the mass media, and cybercriminals did not ignore its popularity. Yet another detail of this quarter is the growth in the proportion of multi-component attacks, consisting of various combinations of SYN, TCP Connect, HTTP flood and UDP flood techniques.
Slibují výdělek na internetu, nakonec ale důvěřivce připraví o peníze
9.11.2017 Novinky/Bezpečnost Kriminalita
Na uživatele oblíbené směnárny s kybernetickými měnami Poloniex se zaměřili v posledních měsících počítačoví piráti. Snažili se jim podstrčit falešnou aplikaci, díky které získají přístup k jejich účtům. Jejich virtuální mince, které je možné směnit za skutečné peníze, by pak mohli snadno odcizit. Upozornili na to bezpečnostní experti z antivirové společnosti Eset.

FOTO: repro poloniex.com
Bitcoiny a další virtuální měny
Virtuálních měn existuje mnoho. Jednou z nejstarších a aktuálně nejpopulárnějších jsou tzv. bitcoiny. Ty vznikly už v roce 2009, větší popularitě se ale těší v posledních letech. Tato měna byla vytvořena tak, aby se nedala ovlivňovat žádnou vládou ani centrální bankou.
Kybernetické mince „razí“ síť počítačů se specializovaným softwarem naprogramovaným tak, aby uvolňoval nové mince stabilním, ale stále klesajícím tempem. Počet mincí v oběhu má dosáhnout nakonec 21 miliónů, což má být kolem roku 2140.
Bitcoiny a další kryptoměny se těší velké popularitě především coby prostředek pro investici. Kurzy však často kolísají. Evropský bankovní úřad kvůli tomu dokonce varoval spotřebitele, že neregulované virtuální měny představují velké riziko. Jejich vklady totiž nejsou nijak chráněny.
Právě Eset odhalil dvě podvodné aplikace v internetovém obchodě Google play, které byly určeny pro zařízení s operačním systémem Android. Obě se přitom snažily vypadat jako legitimní programy internetové směnárny Poloniex.
Útočníci se tak snažili vylákat od svých obětí přihlašovací údaje, aby získali přístup nejen k účtům na Poloniexu, ale také k e-mailovým schránkám na Gmailu. „Okolo kryptoměn je v současné době hodně rozruchu a počítačoví zločinci se pokoušejí chopit jakékoli nové příležitosti, která se jim naskytne,“ uvedl Miroslav Dvořák, technický ředitel společnosti Eset.
„Ať již v uvozovkách krádeží výpočetního výkonu zařízení uživatelů za účelem těžení kryptoměn přes prohlížeče internetu nebo tím, že infikují nedostatečně aktualizované počítače. Také se snaží využívat falešné webové stránky a aplikace zaměřené na získávání osobních dat,“ doplnil Dvořák.
Napálily se tisíce lidí
První škodlivá aplikace byla umístěna do Google Play pod jménem „POLONIEX“ a nabízel ji vývojář „Poloniex“. Vtip byl právě v tom, že název falešné aplikace byl napsán velkými písmeny. Od konce srpna do poloviny září si ji nainstalovalo navzdory varovným hodnocením od dalších uživatelů a negativním recenzím na 5000 lidí.
Druhá aplikace „POLONIEX EXCHANGE“ od vývojáře „POLONIEX COMPANY“ se na Google Play objevila 15. října 2017 a zaznamenala 500 stažení, než ji Google na základě oznámení od společnosti Eset odstranil. Také zde byl název falešné aplikace psán velkými písmeny.
Kolik uživatelů nakonec své přihlašovací údaje dalo všanc kyberzločincům a kolik si počítačoví piráti na úkor podvedených lidí vydělali, není v tuto chvíli jasné.
Tak velké množství uživatelů se nicméně napálilo patrně kvůli tomu, že Poloniex je jednou z nejvyužívanějších směnáren kryptoměn na světě. Obchodovat je zde možné s více než 100 různými typy virtuálních mincí, samozřejmě včetně nejpopulárnějších bitcoinů.
Hacking Team: co všechno uměl a jak to dokázal?
9.11.2017 Root.cz BigBrother
Úspěšný útok na Hacking Team svlékl do naha jednu z velkých společností, která nabízí počítačové útoky a sledování na objednávku. Co všechno firma zákazníkům nabízela? Proč se jí takové útoky dařily?
Na letošní konferenci OpenAlt zazněla také velmi zajímavá přednáška o případu společnosti Hacking Team, která dlouhá léta prodávala své služby vládám a organizacím po celém světě. Všechny detaily se provalily s bezpečnostním průnikem, při kterém firmě unikla prakticky všechna data. Umožnila nám nahlédnout pod pokličku takové společnosti.
Od hackování ke „vzdálenému monitorování“
Petr Hanáček z FIT VUT v Brně začal svou přednášku jako příběh z Milána, kde žili dva přátelé, kteří se živili počítačovou bezpečností. Občas něco konzultovali, občas něco hackli, až za nimi přišla policie. Ale ne je zatknout, ale aby s nimi spolupracovali. Tak vznikla intenzivní spolupráce, ale už se nehackovalo, ale „vzdáleně monitorovalo“.
Tak vznikla firma Hacking Team, která vytvořila systém nejprve pojmenovaný Galileo, pak Da Vinci a nakonec Remote Control System. Pak začali své služby prodávat dalším firmám, tajným službám a podobně. Ani se tím moc netajili, veřejně své služby inzerovali a zveřejňovali, kolik států si je pronajímá. Informace o jejich činnosti jsme měli jen zprostředkovaně, když se provalil nějaký hack. Mezinárodní novinářská organizace pak zmapovala 21 podezřelých států, které pravděpodobně s Hacking Teamem spolupracovaly. To už jsme věděli, co dělají, pro koho to dělají, ale neznali jsme žádné detaily. Chyběly informace o obchodním modelu, jejich schopnostech a znalostech.

Pak přišel 5. červenec 2015, kdy Hacking Team ochutnal vlastní medicíny a byl hacknut. A to tak, že úplně, uteklo jim v podstatě všechno – celkem 400 GB dat. Útočníci se dostali k mnoha citlivým informacím a všechno to zveřejnili na internetu. Na Twitteru Hacking Teamu zveřejnili zprávu o tom, že firma nemá co skrývat a každý se může podívat. Tím jsme dostali unikátní příležitost se podívat, jak přesně taková společnost funguje. Není samozřejmě jediná, takových společností existuje mnoho.
Velký unik otevřel velký svět
Firmě unikl například kompletní seznam klientů, do té doby jsme znali jen asi čtvrtinu z nich. Mezi klienty z Evropské unie se najdeme taky, takže Hacking Team pracoval i pro nás. Znepokojivé je, že mezi státy byly i některé ne úplně slušné země. Bůh ví, k čemu ten software zneužívaly. Mezi nejlépe platící země patří Mexiko, Itálie, Maroko. Česko se nachází přibližně uprostřed seznamu.
Unikl taky přibližně milion e-mailů, netrvalo dlouho a někdo naprogramoval vyhledávač, ve kterém je možné si jednotlivé zprávy filtrovat. Unikly také kompletní účetní doklady, ze kterých plyne, že si služby nekupovaly jen státy, ale například také banky. Není jasné, k čemu zrovna banka takové služby potřebuje, ale je možné zjistit, že šlo konkrétně o oddělení interního auditu. Zajímavá je například také objednávka od americké DEA, která by měla mít dostatek vlastních amerických odborníků.
Podařilo se získat také přístupová hesla k mnoha různým službám jako jsou anonymizéry nebo i SSH účty na různých serverech. Mnoho z hesel bylo velmi triviálních jako kittens nebo P4ssword. Některá hesla byla zahašovaná, takže bylo potřeba na ně pustit duhové tabulky a podařilo se je odhalit.

Zveřejněny byly také ceníky, které dávají alespoň přibližnou představu o cenách. Většina částek za útok se pohybuje okolo 40 000 eur. Neznamená to, že ke všem nabídkám existuje útočný kód. Nemá smysl ho psát hned, ale čekalo se, až přijde kritické množství objednávek a pak se teprve kód napsal. Ceník tedy trochu lže a nedává přesnou představu o aktuálních schopnostech firmy.
Hacking Team u nás přímo neprodávala, ale měl sjednanou spolupráci s českou společností, která služby lokálně přeprodávala. Podle mailové komunikace se bavili o tom, že by se mohly jejich služby prodávat také českému NBÚ. Nakonec k tomu ale nedošlo, protože NBÚ má za úkol potírat kybernetické bezpečnostní hrozby a Hacking Team je někde na pomezí, proto byl nápad pro jistotu shozen ze stolu.
Co Hacking Team uměl?
O konkrétních možnostech Hacking Teamu dává přehled prezentace, která je součástí úniku. Nabízel například sledování webového prohlížeče, odposlech mikrofonu, sledování klávesnice, natáčení uživatele webovou kamerou a podobně. Na mobilních telefonech to bylo navíc sledování historie volání, lokalizace uživatele a odposlech uživatele. Na mobilu má odposlech úplně jiný rozměr, protože si sebou vlastně nosíte v kapse vlastní štěnici.
Nabízené služby vypadají velmi lákavě, protože nabízejí odpověď na řadu scénářů. Možnosti jsou až tak zajímavé, že se dá pochybovat o tom, že to Hacking Team všechno opravdu dokáže. Výrobci nám totiž tvrdí, že jejich přístroje jsou skvělé a bezpečné a najednou tu je firma, která tvrdí, že dokáže cokoliv.
Klient dostává vlastní aplikaci, která mu dovoluje ovládat celý systém a objednávat si v něm jednotlivé útoky. Celá akce začne tím, že si v aplikaci naklikáme objekt a potom si necháme vygenerovat soubor s exploitem. Původně šlo o samoobsluhu, ale uživatelé zacházeli s drahocennými exploity velmi ledabyle a nechávali je povalovat po internetu a tím zvyšovali riziko prozrazení. Proto se přešlo na klasický ticketovací systém a balíček s exploitem připravovali na požádání přímo lidé v Hacking Teamu.
Výsledkem je například wordovský dokument, který je vyroben přesně tak, aby ho dotyčný čekal, například na základě předchozí komunikace, kterou už chvíli sledujeme. To je nejkomplikovanější varianta proti paranoidním obětem. U ostatních si to můžu zjednodušit a poslat třeba poděkování e-mailovým přátelům.

Je také možné škodlivý kód vložit například do webové stránky, která je kopií nějakého webu. Hacking Team umí i dodat krabičku s názvem Network injector, která konkrétnímu uživateli zamění původní stránku za napadenou. Často si tuto akci ale umí objednatel zajistit sám, takže instalace krabičky není potřeba.
Jakmile je kód u oběti, je možné si sednout ke konzoli a začít programovat útok. Je například možné zvolit, kdy a co chceme provádět. Kdybychom třeba používali mobil jako štěnici a trvale odesílali data, velmi rychle vybijeme baterii. Můžeme proto nahrávat do souboru a buďto odesílat v nějakých intervalech nebo ještě lépe počkat, až se mobil dostane na Wi-Fi.
Takto je možné zařízení sledovat, získávat z něj informace a zařazovat je také do kontextu. Je to krásná aplikace, vypadá to jako z nějakého amerického filmu. Umožňuje například sledovat setkávání jednotlivých obětí, analyzovat obsah, vytvářet profily jednotlivých cílů a podobně. Je vidět, že se Hacking Team staral o svoje zákazníky a vytvářel jim aplikaci, se kterou je radost pracovat.
Kde se vezme exploit?
Je skutečně možné takto snadno zařízení napadnout? Abychom to mohli udělat, musíme mít připravené nějaké exploity. Hacking Team ve skutečnosti nabízel mnoho možností, jak zařízení infikovat. Je možné použít CD nebo flash disk, použít například port Firewire nebo třeba přímou instalaci po vyjmutí disku.
Stejně tak je možné infikovat vzdáleně pomocí knihovny zero-day exploitů. Vytvořili například nový nástroj melting tool, který dokáže kód injektovat přímo do provozu během stahování obsahu z internetu. Prakticky všechno bylo prováděno vzdáleným přístupem, přestože je to složitější, dražší a náročnější než lokální napadení zařízení. Vyžaduje to sice rozsáhlou knihovnu exploitů, ale většina klientů nechtěla s fyzickým útokem nic mít.
Hacking Team využíval několik různých kategorií útoků: nejjednodušší sociální, veřejně dostupné exploity až zero-day exploity. Ty jsou jako čerstvě maso, nevydrží věčně. Potřebuji mít nějaký mechanismus dodávání stále čerstvé zásoby exploitů. Nemůžu si je nasyslit do budoucna, protože po pěti letech už nebudou fungovat. Opravdu citlivé operace si Hacking Team chránil a pracoval s nimi sám, aby nedošlo k úniku a tím znehodnocení exploitu.

Zdroje exploitů jsou různé, firma může buďto vytvářet útočný kód sama nebo je nakupovat. Není příliš reálné, aby firma sama hledala všechny chyby. Hacking Team hledal různé cestičky, včetně některých velmi kreativních. Snažila se například spolupracovat s univerzitami, které by například během nějakého výzkumu objevovaly a posílaly bezpečnostní chyby. Hlavním zdrojem je ale nákup exploitů od lidí, kteří se tím živí.
Příkladem je například Vitalij Toropov, který do roku 2015 aktivně a veřejně hledal a hlásil bezpečnostní chyby v software. Pak ale přestal. Nebo je spíš přestal dávat do otevřených databází. Víme, že začal exploity prodávat Hacking Teamu a udělal si z toho dobrou živnost. Posílal normální faktury, které se našly v Hacking Teamu. Firma poté vypracovala systém, který jí umožnil nakupovat efektivně a automatizovaně pomocí vyplňování dotazníků. Dnes jsme už dále, existuje portál Zerodium, který funguje jako aukční server na exploity. Najdou se tu levné útoky na známé redakční systémy jako WordPress, Drupal a Joomla, ale i požadavek na „svatý grál“ v podobě vzdáleného útoku na zařízení od Apple.
Nejčastěji byly využívány dva konkrétní exploity: útok na jádro Windows – konkrétně knihovnu ATMFD.dll a také Flash player. První chyba se týká programu Adobe Type Manager, který do Windows přidával podporu True Type fontů. Původně šlo o samostatný program, který se později stal součástí systému. Chyba přežila několik desetiletí a mnoho verzí Windows. Ten kód je i v desítkách, ale je už samozřejmě opravený. Hacking Team byl prozrazen těsně před vydáním Windows 10, takže Microsoft stihl vydat záplatu.
Chyba ve Flashi se pak zneužívala tak, že se vložil flashový objekt do powerpointové prezentace. Při jejím otevření došlo k načtení a spuštění Flashe, který byl přes díru zneužit ke stažení útočného kódu, který pak prováděl samotný útok. Zajímavé ale je, že na první pohled jde o dva velmi rozdílné exploity pro různé technologie. Že by se jeden člověk zabýval dvěma tak rozdílnými systémy a hledal v nich slabiny? Mají ovšem jednu společnou věc: oba nástroje programovala společnost Adobe. Vitalij Toropov se tedy při své práci zaměřil na produkty jedné společnosti, která má z hlediska bezpečnosti velmi špatnou pověst.
Stále stejné chyby už 40 let
Nejčastěji jsou stále zneužívány chyby přetečení zásobníku, kdy programátor používá pro kopírování řetězců nebezpečné knihovní funkce. První popis se přitom objevil už v roce 1972, poprvé to bylo v praxi zneužito v roce 1988 a v roce 1996 se objevil první vyčerpávající návod, který dokázal použít kdokoliv: Smashing The Stack For Fun And Profit. Je to tu s námi třicet let a měli bychom být schopni s tím už pracovat. Naštěstí není nebezpečných funkcí tolik a je možné napsat vyhledávací software, který programátora upozorní na nebezpečné chování.
Jsme ale v roce 2017 a problém není stále uspokojivě vyřešen. My vlastně nechceme psát kód bez chyb a snažíme se to nějak obejít. Je to například ASLR, který přesouvá data v paměti náhodně, ale ani ten není samospásný. Před dvaceti lety by to bylo ultimátní řešení, které by zabránilo všem útokům. Dnes už jsou známy postranní kanály, které nám dovolují zjistit, kde se v paměti dané části nacházejí. Těch kanálů navíc stále přibývá.
Můžeme například použít také NX bit, kanárky a další. Všechno se to ale ukazuje být nefunkční. Útočníci totiž umí tato opatření obcházet. Pokud například pomocí NX bitu zakážeme spouštění kódu na zásobníku, může útočník zneužít už existující kód v regulérním programu. Najde si užitečné části původního programu, které končí instrukcí ret a ty využije. Takto si pak může svůj útočný kód poskládat. Je to jen jedna z mnoha možností, ale ukazuje to, že je to pro útočníka řešitelné.
Hlavní problém je, že programování v C skrývá mnoho dalších pastí jako například přetečení integeru. O mnoha pastech navíc programátor často netuší. Například že funkce abs může vrátit i zápornou hodnotu nebo že sečtení dvou kladných integerů může vrátit záporný výsledek. Tuší takové věci náš běžný student informatiky? Já nevím.
Velmi často se objevují nové způsoby zneužití programátorských chyb, o kterých jsme dříve nevěděli nebo jsme si nedokázali zneužití představit. Navíc tyto chyby není možné zachytit při překladu. Jedinou možností je psát kódy bez chyb.
Experts can hack most CPUs since 2008 over USB by triggering Intel Management Engine flaw
9.11.2017 securityaffairs Vulnerebility
Intel’s management engine – in most Positive Technologies plans to demonstrate at the next Black Hat conference how to hack over USB into Intel Management Engine of most CPUs since 2008.
Experts from Positive Technologies that in September announced to have devised a technique a to attack the Intel Management Engine, now provided more details about it and plan to demonstrate the God-mode hack in December 2017.
The God-mode hack could be exploited by “an attacker of the machine to run unsigned code in the Platform Controller Hub on any motherboard,” experts devised a technique to access the Intel Management Engine (IME) from the USB port
The security issues affecting the IME were first reported in March by the security expert Maksim Malyutin of Embedi.
A critical remote code execution (RCE) vulnerability tracked as CVE-2017-5689 was discovered in the remote management features implemented on computers shipped with Intel Chipset in past 9 years.
The vulnerability affects the Intel Management Engine (ME) technologies such as Active Management Technology (AMT), Small Business Technology (SBT), and Intel Standard Manageability (ISM) and could be exploited by hackers to remotely take over the vulnerable systems.

The remote management features allow system administrators to remotely manage computers over an enterprise network. Such kind of features are implemented only in enterprise solutions and doesn’t affect chips running on Intel-based consumer PCs.
“There is an escalation of privilege vulnerability in Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology versions firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 that can allow an unprivileged attacker to gain control of the manageability features provided by these products. This vulnerability does not exist on Intel-based consumer PCs. ” reads the advisory published by Intel.
The vulnerability rated by Intel as highly critical could be exploited in two ways:
An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs: Intel® Active Management Technology (AMT) and Intel® Standard Manageability (ISM).
CVSSv3 9.8 Critical /AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs: Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology (SBT).
CVSSv3 8.4 High /AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
An attacker can exploit the vulnerability to remotely access the vulnerable machine and perform in a stealth way malicious activities, including to deliver a malware.
Back to the present, experts were able to exploits the Joint Test Action Group (JTAG) debugging ports to target the IME.

Maxim Goryachy @h0t_max
Game over! We (I and @_markel___ ) have obtained fully functional JTAG for Intel CSME via USB DCI. #intelme #jtag #inteldci
3:33 PM - Nov 8, 2017
43 43 Replies 576 576 Retweets 710 710 likes
Twitter Ads info and privacy
In this blog post written in Russian language is confirmed that researchers at Positive Technologies have used the hardware debugging (JTAG) for Intel Management Engine, to gain full access to all PCH devices (Platform Controller Hub) using Intel Direct Connect Interface (DCI) technology (via USB interface).

Summarizing, the attack recently devised is possible by accessing to USB, Positive Technologies plans to demonstrate it at Black Hat.
Google Syzkaller fuzzer allowed to discover several flaws in Linux USB Subsystem
9.11.2017 securityaffairs Vulnerebility
The Google researcher Andrey Konovalov discovered several vulnerabilities in the Linux kernel USB subsystem using the Google Syzkaller fuzzer.
Google researcher Andrey Konovalov has discovered many security vulnerabilities in Linux USB Subsystem.
The expert used a fuzzing tool developed by Google dubbed Syzkaller fuzzer, he discovered tens of vulnerabilities, including 22 security flaws.
Konovalov published a detailed analysis of 14 vulnerabilities that have been classified as use-after-free, general protection fault, out-of-bounds read, and NULL pointer dereference issues. An attacker can trigger the vulnerabilities to cause a denial-of-service (DoS) condition, one of the issues might be exploited to execute an arbitrary code.
The expert pointed out that an attacker needs to have physical access to the targeted system and connect a malicious USB device to trigger the vulnerabilities.
“Below are the details for 14 vulnerabilities found with syzkaller in the Linux kernel USB subsystem. All of them can be triggered with a crafted malicious USB device in case an attacker has physical access to the machine.” reads the security advisory.
Other experts who replied to the advisory pointed out that an attacker who has remote access to a machine may be able to update the firmware on connected USB drives to plant exploits for these flaws and create malicious devices.
“Perhaps not only in that case, but also in case an attacker has remote access to a USB device (perhaps most commonly via remote access to the machine, with privileges to access the USB device) sufficient to replace that device’s firmware (thereby crafting a malicious device).” suggested one of the users.
For example, many USB-connected FPGA boards, Bitcoin miners (“ASICs”), etc. may reasonably be made available to a non-root user (such as via udev rules), and they commonly permit microcontroller firmware update to be performed via USB as well. John the Ripper bleeding-jumbo currently loads firmware into MCUs on ZTEX 1.15y boards at startup (if the firmware in EEPROM is different), and we recommend running it as non-root with udev rules setup to grant access to non-root users in group “ztex” (this setup is described in doc/README-ZTEX).”
Linux kernel versions 4.13.4 and later address many of the vulnerabilities found by Konovalov, unfortunately many of the bugs remain unpatched.
Back in February, the Google researcher discovered a local privilege escalation vulnerability tracked as CVE-2017-6074 that it is an 11-year old flaw.
The flaw was discovered by Konovalov in the DCCP (Datagram Congestion Control Protocol) implementation the same kernel fuzzing tool Syzkaller.
The privilege-escalation issue was affecting all the major Linux distro, including Debian, OpenSUSE, Redhat, and Ubuntu.
In May, Konovalov reported a privilege escalation bug tracked as CVE-2017-7308 that could be exploited via packet sockets.
Russia-Linked APT28 group observed using DDE attack to deliver malware
9.11.2017 securityaffairs APT
Security experts at McAfee observed the Russian APT28 group using the recently reported the DDE attack technique to deliver malware in espionage campaign.
Security experts at McAfee observed the Russian APT group APT28 using the recently reported the DDE technique to deliver malware in targeted attacks.
The cyber spies were conducting a cyber espionage campaign that involved blank documents whose name referenced the recent terrorist attack in New York City.
“During our monitoring of activities around the APT28 threat group, McAfee Advanced Threat Research analysts identified a malicious Word document that appears to leverage the Microsoft Office Dynamic Data Exchange (DDE) technique that has been previously reported by Advanced Threat Research. This document likely marks the first observed use of this technique by APT28.” reported McAfee.
The Dynamic Data Exchange (DDE) is a protocol designed to allow data transferring between applications, attackers have devised a method to achieve the execution of malicious code embedded in Office documents without user’s interaction by using DDE.
The DDE protocol allows an Office application to load data from another Office application, it was replaced by Microsoft with Object Linking and Embedding (OLE), but it is still supported.
The DDE technique was implemented by several threat actors such as the FIN7 APT group in DNSMessenger malware attacks, and the operators behind the Hancitor malware campaign spotted and detailed by Internet Storm Center (ISC) handler Brad Duncan.
Recently the technique was used by threat actors behind the Necurs botnet to deliver the Locky ransomware.
Unfortunately, Microsoft doesn’t plan to introduce security countermeasures to mitigate the DDE attack because the tech giant considers the feature as legit.
In the recent campaign conducted by APT28, hackers used a document referencing the New York City attack to deliver the first-stage payload tracked as Seduploader.
The Seduploader malware, also known as GAMEFISH backdoor, Sednit, JHUHUGIT and Sofacy, is a strain of malware that has been already used by the threat actor in other campaigns against NATO representatives.
The Seduploader is a reconnaissance malware that was used for years by APT28, it is composed of 2 files: a dropper and a payload.
The malware is downloaded from a remote server using PowerShell commands, experts
The analysis of the malware and command and control (C&C) domains used in the campaign revealed the campaign involving DDE started on October 25.
According to the experts, the recent attacks are part of a campaign that also involved documents referencing Saber Guardian, a multinational military exercise involving approximately 25,000 military personnel from over 20 participating nations. The military exercise was conducted by the U.S. Army in Eastern Europe in an effort to deter an invasion (by Russia) into NATO territory.

Just two week ago, researchers with Cisco Talos have spotted another cyber espionage campaign conducted by the APT28 group targeting individuals with spear-phishing messages using documents referencing a NATO cybersecurity conference.
The hackers targeted individuals with a specific interest in the CyCon US cybersecurity conference organized by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) in collaboration with the Army Cyber Institute at West Point on November 7-8 in Washington, D.C.
“APT28 is a resourceful threat actor that not only capitalizes on recent events to trick potential victims into infections, but can also rapidly incorporate new exploitation techniques to increase its success. Given the publicity the Cy Con U.S campaign received in the press, it is possible APT28 actors moved away from using the VBA script employed in past actions and chose to incorporate the DDE technique to bypass network defenses.” concluded McAfee. “Finally, the use of recent domestic events and a prominent US military exercise focused on deterring Russian aggression highlight APT28’s ability and interest in exploiting geopolitical events for their operations.”
Where DevOps Could Be Increasing The Attack Surface
9.11.2017 securityweek Attack
Survey Finds That DevOps Often Improves IT Efficiency While Weakening IT Security
The basic premise behind DevOps is that combining the development team and the operations team into a single cohesive unit will improve efficiency. It's all about breaking down silos. But there is one silo that frequently remains excluded: security. The obvious solution is to adopt DevSecOps rather than just DevOps; that is, remove another silo in the name of greater overall IT efficiency.
It doesn't seem to be happening. Early details from CyberArk's Advanced Threat Landscape 2018 report, due to be released in January, show that in at least one area, DevOps is increasing the attack surface -- privileged accounts. Privileged accounts are essential within DevOps, but CyberArk's figures suggest that they are not well protected.
CyberArk, founded in Israel in 1999, is headquartered in Newton, Mass. During September and October 2017, it commissioned Vanson Bourne to survey more than 1,000 IT security decision makers. It found that DevOps and security professionals have what it describes as "worrying knowledge gaps about where privileged accounts and secrets exist across the IT infrastructure." For example, 99% of the respondents failed to identify all the locations where privileged accounts or secrets exist.
The greatest knowledge gap is with source code repositories such as GitHub. Eighty-four percent of the respondents failed to recognize GitHub as a location for privileged accounts. This is followed by microservices (80%), cloud environments (78%), and continuous integration and continuous deployment (CI/CD) tools used by DevOps (76%).
"As organizations employ DevOps, more privileged account credentials and secrets are being created and shared across interconnected business ecosystems," said Elizabeth Lawler, vice president of DevOps security at CyberArk. "Even though dedicated technology exists, with few organizations managing and securing secrets, they become prime targets for attacks. In the hands of an external attacker or malicious insider, compromised credentials and secrets can allow attackers to take full control of an organization's entire IT infrastructure. So it's worrying that the rush to achieve IT and business advantages through DevOps is outpacing awareness of an expanded - and unmanaged - privileged attack surface."
This doesn't mean that DevOps is unaware of the security issue. Thirty-seven percent of DevOps professionals using the cloud said compromised DevOps tools and environments represent one of their organization's greatest security vulnerabilities. The main problem is the discontinuity between the security and DevOps teams. About 75% of security teams do not have a privileged account security strategy for the organization's DevOps, while there is no integration at all between security and DevOps in almost two-thirds of occasions.
As a result, security-aware DevOps professionals have tried to do things themselves. Twenty-two percent have built their own security solution to protect and manage secrets for DevOps projects. "Building your own security solutions is arguably OK up to a point," comments Lawler, "but is not a scalable way forward. From Jenkins to Puppet to Chef, there are no common standards between different tools, which means you must figure out every single tool to know how to secure it. DevOps really needs its own security stack, and security teams must bring something to the table here. They can provide a systemised approach that helps the DevOps teams maintain security while accelerating application delivery and boosting productivity."
When companies break down and integrate the development and operations silos in favor of efficiency, they need to ensure that security does not remain in its own silo outside of DevOps. It's not always an easy ask. DevOps is all about efficiency and speed; security is often seen as anathema to efficiency and speed. Nevertheless, CyberArk's survey demonstrates it is an essential step if companies wish to use DevOps to improve rather than weaken overall corporate security.
"Tick" Cyber Espionage Group Employs Steganography
9.11.2017 securityweek Krypto
The cyber espionage group known as "Tick" is using steganography to conceal their backdoor Trojan better, according to analysis from security firm Trend Micro.
Also referred to as Bronze Butler and REDBALDKNIGHT and believed to be based in China, the group is mainly targeting Japanese organizations, including biotechnology, electronics manufacturing, and industrial chemistry entities and government agencies. Although the first report on the group was published only last year, the hackers might have been active for at least a decade, Trend Micro's researchers say.
Malicious tools preferred by the threat actors include a downloader tracked as Gofarer and a data-stealing Trojan dubbed Daserf, which can execute shell commands and download and upload data. Now, Trend Micro says that variants of Daserf were used against entities outside Japan as well, including organizations in South Korea, Russia, Singapore, and China.
Furthermore, the security researchers say that various versions of Daserf employ different techniques and use steganography, which allows them to conceal themselves better by embedding codes in unexpected mediums or locations, such as images.
The hackers typically use spear phishing emails with attached malicious documents created using the Japanese word processor Ichitaro. These documents install and execute the Daserf backdoor on the victim’s machine.
Tick is believed to be regularly improving the Daserf Trojan to keep it under the radar.
Some malware variations also revealed that the group integrated steganography to conduct second-stage attacks and for command-and-control (C&C) communication. Through the use of steganography, the backdoor can not only bypass firewalls, but also change second-stage C&C communication or malware faster and more conveniently, Trend Micro says.
Daserf’s infection chain involves a downloader that retrieves the backdoor from a compromised site. After installation, the Trojan connects to another compromised site and downloads an image file, then connects to its C&C and awaits further commands.
The Tick hackers, Trend Micro notes, have been using steganography on other toolkits as well, namely xxmm2_builder and xxmm2_steganography. These are components of the XXMM downloader Trojan that can also be used as a first-stage backdoor. The researchers found that the same steganography algorithm was used on both XXMM and Daserf.
“Steganography is a particularly useful technique in purposeful cyberattacks: the longer their malicious activities stay undetected, the more they can steal and exfiltrate data. And indeed, the routine is increasingly gaining cybercriminal traction, in varying degrees of proficiency—from exploit kits, malvertising campaigns, banking Trojans, and C&C communication to even ransomware. In the case of REDBALDKNIGHT’s campaigns, the use of steganography is further compounded by their use of malware that can better evade detection and analysis,” Trend Micro concludes.
More Prison Time for Ex-Federal Agent Who Stole Bitcoins
9.11.2017 securityweek CyberCrime
A former U.S. Secret Service agent already convicted for stealing bitcoins from the now-defunct underground marketplace Silk Road has been handed another prison sentence for the theft of digital currency from the government, the Department of Justice announced this week.
Shaun W. Bridges, 35, of Laurel, Maryland, was sentenced in December 2015 to 71 months in prison for money laundering and obstruction of justice. Bridges, who had been part of the task force investigating Silk Road, stole 20,000 bitcoins, at the time worth roughly $350,000, from Silk Road customers using information obtained following the arrest of one of the site’s customer support representatives. Bridges liquidated the bitcoins in the spring of 2015 and earned $820,000.
According to authorities, before he began serving his sentence for the 2015 conviction, Bridges stole another 1,600 bitcoins from a digital wallet belonging to the U.S. government.
Court documents obtained by Ars Technica show that the former federal agent retained the private key for an account storing bitcoins seized from digital currency exchange Bitstamp. After resigning from the Secret Service, Bridges used the key to transfer roughly 1,600 of the Bitstamp bitcoins from the government’s digital wallet into his own.
Bridges pleaded guilty to money laundering charges related to this case and agreed to return the stolen bitcoins. He received a 24-month prison sentence, which will be served consecutively to the previous 71-month sentence. The defense had hoped to convince the judge to hand out a concurrent sentence.
Bridges is not the only former federal agent sentenced to prison as a result of illegal activities carried out during the investigation into Silk Road. In October 2015, a former Drug Enforcement Administration (DEA) agent, Carl M. Force, was sentenced to 78 months in prison after receiving hundreds of thousands of dollars worth of bitcoin from Ross Ulbricht, the mastermind of Silk Road, for inside information about the government’s investigation into the underground marketplace.
Ulbricht was sentenced to life in prison for his role in running Silk Road. He unsuccessfully appealed the sentence and his later bid for a new trial was denied.
Many Vulnerabilities Found in Linux USB Subsystem
9.11.2017 securityweek Vulnerebility
A Google researcher has found a significant number of vulnerabilities in the Linux kernel USB subsystem using the Syzkaller fuzzer.
The fuzzing tool developed by Google helped Andrey Konovalov find tens of bugs, including 22 security flaws that have been assigned CVE identifiers. In an advisory published this week, the expert detailed 14 of the vulnerabilities he discovered.
The vulnerabilities have been described as use-after-free, general protection fault, out-of-bounds read, and NULL pointer dereference issues that can be exploited to cause a denial-of-service (DoS) condition. The expert said some of the flaws might have a different impact as well, which typically means they could allow arbitrary code execution.
Konovalov pointed out that an attacker needs to have physical access to the targeted system and connect a malicious USB device in order to exploit the vulnerabilities. Others suggested that an attacker who has remote access to a machine may be able to update the firmware on connected USB drives to plant exploits for these flaws and create malicious devices.
Fixes for many of the vulnerabilities found by Konovalov are included in Linux kernel versions 4.13.4 and later, but many of the issues remain unpatched. On the other hand, Linux distributions don’t seem too concerned about these security holes and assigned them low severity ratings.
These are not the only flaws discovered by the Google researcher in the Linux kernel. Back in February, he reported finding a locally exploitable code execution weakness that had been present in the kernel for more than 11 years. This double-free vulnerability (CVE-2017-6074) was also identified using the Syzkaller fuzzer.
In May, he disclosed the details of a privilege escalation bug that could be exploited via packet sockets.
An analysis of more than 600 CVEs conducted last year showed that the average lifetime of a Linux kernel vulnerability is 5 years.
Amazon Adds New Encryption, Security Features to S3
8.11.2017 securityweek Security
Amazon announced this week that it has added five new security and encryption features to its Simple Storage Service (S3), including one that alerts users of publicly accessible buckets.
Improperly configured S3 buckets can expose an organization’s sensitive files, as demonstrated by several recent incidents involving companies such as Viacom, Verizon, Accenture, Booz Allen Hamilton, and Dow Jones.
In an effort to help organizations avoid data leaks, Amazon introduced permission checks that provide clear information and indicators about publicly accessible buckets. The feature was made available shortly after Amazon announced the launch of a set of managed configuration rules designed to help users secure their S3 buckets.
With the introduction of permission checks, users immediately know if a bucket is configured for public access via the main page of the S3 Console and in each bucket’s own page.
Users can now also install an encryption configuration to mandate that all objects in a bucket must be stored in encrypted form. This means that customers will not have to create a bucket policy for rejecting non-encrypted objects.
Two of the new features are related to Cross-Region Replication, functionality that allows users to copy mission-critical objects and data to a bucket in a different AWS account. Objects are typically copied with the associated access control list (ACL) and tags, but a new feature enables users to replace the ACL while the data is in transit to ensure that the owner of the destination bucket has full access.
When administrators use Cross-Region Replication, they can now also replicate objects that are encrypted with keys managed via the AWS Key Management Service (KMS).
The last new feature is related to S3 inventory reports, which now provide information on the encryption status of each object.
All the new features are immediately available at no extra charge.
Experts Find Faster Way to Exploit Infineon Chip Crypto Flaw
8.11.2017 securityweek Krypto
A recently disclosed crypto-related vulnerability affecting some Infineon chips can be exploited in a shorter amount of time than initially believed, researchers demonstrated.
A team of experts from the Czech Republic, the U.K. and Italy showed recently that millions of products using chips from German semiconductor manufacturer Infineon Technologies are affected by a vulnerability related to a library responsible for generating RSA encryption keys.
The flaw, tracked as CVE-2017-15361 and dubbed ROCA (Return of the Coppersmith Attack), allows an attacker who knows the public key to obtain the private RSA key. Depending on what the product is used for, an attacker can use the compromised private key to impersonate legitimate users, decrypt messages, and forge software signatures.
Microsoft, Google, HP, Lenovo, Fujitsu and other companies published advisories to warn customers of the risks. The flaw also impacts Gemalto’s IDPrime.NET smart cards, which are no longer sold by the firm but are still used by many organizations worldwide.
The vulnerability also affects Estonia’s national ID cards, which are also supplied by Gemalto. Estonia has decided to suspend roughly 760,000 ID cards, which are also used by citizens to vote, in response to the incident. The IDs used in other countries could be vulnerable as well, according to some reports.
Researchers said a 1024-bit RSA key can be cracked in 97 CPU days for a cost of $40-80 using an older Intel Xeon processor, and a 2048-bit key in 140 CPU years for a cost ranging between $20,000 and $40,000.
Estonia assured citizens that large-scale vote fraud would be too expensive to conduct – some estimated that the cost for hacking all ID cards would be roughly €60 billion ($70 billion) at a cost of approximately $80,000 per card.
However, researchers Daniel J. Bernstein and Tanja Lange pointed out over the weekend that the actual cost of obtaining the RSA keys was in reality much lower, even before they found a faster way to conduct an attack. Furthermore, they highlighted that vote fraud would not require all cards to be compromised as even 10% could make a difference.
The $80,000 estimate cited by Estonia refers to an initial algorithm used by the original authors of the research. They later managed to decrease costs to $20,000.
Bernstein and Lange attempted to conduct an attack using only the limited information made available by the original researchers. They not only managed to replicate the attack, but they also found a way to obtain a 2048-bit key 5-25% faster, which further reduces the cost of an attack.
Bernstein and Lange also noted that the issue with Infineon chips has actually been known since August 2016 and they are concerned that malicious actors may have been exploiting the flaw before the ROCA disclosure.
“Attackers could already have figured out the whole attack from [the 2016 research paper],” the experts said in a blog post. “Or attackers could have looked at Infineon keys on their own and found the same information. Our best guess is that serious attackers found the Infineon vulnerability years ago and have been quietly exploiting it since then.”
Android Security Bulletin—November 2017 – Google addresses critical flaws and high-risk KRACK vulnerabilities in Android
8.11.2017 securityaffairs Android
Android Security Bulletin—November 2017 – Google addresses critical vulnerabilities and high-risk KRACK flaws in Android OS.
Google released the Android Security Bulletin—November 2017 that address 31 vulnerabilities, 9 of which are critical remote code execution flaws.
The Android Security Bulletin includes three different security patch levels.
The 2017-11-01 and 2017-11-05 patch levels contain fixes for both Critical and High severity issues.
The 2017-11-06 patch level addresses only High-risk KRACK vulnerabilities.
“Android partners were notified of all issues in the 2017-11-01 and 2017-11-05 patch levels at least a month before publication. Android partners were notified of all issues in the 2017-11-06 patch level within the last month. Source code patches for these issues will be released to the Android Open Source Project (AOSP) repository in the next 48 hours. We will revise this bulletin with the AOSP links when they are available.” states the Android Security Bulletin—November 2017.
The 2017-11-01 security patch level addresses 11 issues, 6 of which are Critical RCE, 3 High severity elevation of privilege bugs, and 2 High severity information disclosure vulnerabilities.
The largest number of vulnerabilities affects the Media framework, the security patchers addressed 7 issues.
CVE REFERENCES TYPE SEVERITY UPDATED AOSP VERSIONS
CVE-2017-0832 A-62887820 RCE Critical 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-0833 A-62896384 RCE Critical 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-0834 A-63125953 RCE Critical 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-0835 A-63316832 RCE Critical 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-0836 A-64893226 RCE Critical 5.0.2, 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-0839 A-64478003 ID High 5.0.2, 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
CVE-2017-0840 A-62948670 ID High 5.0.2, 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0
The 2017-11-05 security patch level addressed 11 vulnerabilities, including 3 Critical RCE vulnerabilities, 7 High risk elevation of privilege bugs, and 1 High severity information disclosure. Qualcomm components were most impacted, the bulletin addressed 7 issues, one of the vulnerabilities could be exploited by a remote attacker to execute arbitrary code within the context of a privileged process.
CVE REFERENCES TYPE SEVERITY COMPONENT
CVE-2017-11013 A-64453535
QC-CR#2058261 [2] RCE Critical WLAN
CVE-2017-11015 A-64438728
QC-CR#2060959 [2] RCE Critical WLAN
CVE-2017-11014 A-64438727
QC-CR#2060959 RCE Critical WLAN
CVE-2017-11092 A-62949902*
QC-CR#2077454 EoP High GPU driver
CVE-2017-9690 A-36575870*
QC-CR#2045285 EoP High QBT1000 driver
CVE-2017-11017 A-64453575
QC-CR#2055629 EoP High Linux boot
CVE-2017-11028 A-64453533
QC-CR#2008683 [2] ID High Camera
The 2017-11-06 security patch level addresses 9 vulnerabilities related to the KRACK attack.

Starting in October 2017, Google began releasing a separate security bulletin for Nexus and Pixel devices.
The Pixel / Nexus Security Bulletin—November 2017 includes patches for over 50 bugs affecting components such as Framework, Media framework, Runtime, System, and Kernel, MediaTek, NVIDIA, and Qualcomm components.
A regular GitHub user accidentally triggered a flaw Ethereum Parity Wallet that locked up $280 million in Ether
8.11.2017 securityaffairs Hacking
A GitHub user accidentally triggered a flaw in the Parity Wallet library contract of the standard multi-sig contract that locked up $280 million in Ether.
Ethereum made again the headlines, someone has accidentally triggered a vulnerability in the popular Parity Wallet that locked up $280 million in Ether, including $90 million raised by Parity Technologies’s founder Gavin Woods.
The huge amount of money from dozens of Ethereum wallets operated by the Smart contract coding startup Parity Technologies the was permanently locked up.
It has been estimated that Parity wallets constitute roughly 20% of the entire Ethereum network.
Parity Technologies, which is behind the popular Ethereum Parity Wallet, announced the incident that was caused by a severe vulnerability in its “multisignature” wallets created after this July 20. Owners of the affected wallets will be not able to move their funds.
” A vulnerability in the Parity Wallet library contract of the standard multi-sig contract has been found.” reads the announcement.
“Following the fix for the original multi-sig issue that had been exploited on 19th of July (function visibility), a new version of the Parity Wallet library contract was deployed on 20th of July. However that code still contained another issue – it was possible to turn the Parity Wallet library contract into a regular multi-sig wallet and become an owner of it by calling the
initWallet
function. It would seem that issue was triggered accidentally 6th Nov 2017 02:33:47 PM +UTC and subsequently a user suicided the library-turned-into-wallet, wiping out the library code which in turn rendered all multi-sig contracts unusable since their logic (any state-modifying function) was inside the library.”
The vulnerability was triggered by a regular GitHub user, “devops199,” who allegedly accidentally removed a critical library code from the source code, this operation turned all multi-sig contracts into a regular wallet address with devops199 as its owner.
Devops199 then killed the wallet contract, making all Parity multisignature wallets tied to that contract useless, and locking up their funds.
“These (https://pastebin.com/ejakDR1f) multi_sig wallets deployed using Parity were using the library located at “0x863df6bfa4469f3ead0be8f9f2aae51c91a907b4″ address,” devops199 explained on GitHub.
“I made myself the owner of ‘0x863df6bfa4469f3ead0be8f9f2aae51c91a907b4’ contract and killed it and now when I query the dependent contracts ‘isowner(<any_addr>)’ they all return TRUE because the delegate call made to a died contract.”
Ethereum Parity Wallet
In July, an unknown hacker has stolen nearly $32 million in funds from Parity multisignature wallets, the attacker triggered a vulnerability to compromise at least three accounts and steal nearly 153,000 units of Ether.
Parity released on 20th of July, a new version of the Parity Wallet library contract that addressed the flaw, but the code was still affected by another issue that allowed the devops199 user to turn the Parity Wallet library contract into a regular wallet.
Parity immediately froze all affected multi-sig wallets while working to fix the problem, it plans to provide further details shortly.















