
FireEye releases GoCrack, a free managed Password Cracking Tool
31.10.2017 securityweek Forensics
Early this week FireEye released a managed password cracking tool, dubbed GoCrack, that is able to execute tasks across multiple GPU servers.
Early this week FireEye released a managed password cracking tool, dubbed GoCrack, that is able to execute tasks across multiple GPU servers. GoCrack is an open source tool developed by FireEye’s Innovation and Custom Engineering (ICE) team that implements an easy-to-use, web-based real-time UI to create, view, and manage password cracking tasks.
Users can deploy a GoCrack server along with a worker on every GPU/CPU capable machine, the tasks will be automatically distributed across the GPU/CPU of the machines composing the network.
“FireEye’s Innovation and Custom Engineering (ICE) team released a tool today called GoCrack that allows red teams to efficiently manage password cracking tasks across multiple GPU servers by providing an easy-to-use, web-based real-time UI to create, view, and manage tasks.” reads the post published by FireEye. “Simply deploy a GoCrack server along with a worker on every GPU/CPU capable machine and the system will automatically distribute tasks across those GPU/CPU machines.”

GoCrack supports the hashcat v3.6+ engine and requires no external database server, the experts also implemented the support for both LDAP and database backed authentication.
FireEye plans to add support for both MySQL and Postgres database engines soon.
The server component can run on any Linux server with Docker installed, users with NVIDIA GPUs can use NVIDIA Docker to run the worker in a container with full access to the GPUs.
Password cracking is a very important activity for security professionals that aim to test password effectiveness and management.
“Some use cases for a password cracking tool can include cracking passwords on exfil archives, auditing password requirements in internal tools, and offensive/defensive operations.” continues FireEye.
GoCrack logs any sensitive actions for auditing purposes, the tool allows to hide task data unauthorized users.
“Modifications to a task, viewing of cracked passwords, downloading a task file, and other sensitive actions are logged and available for auditing by administrators,” continues the post. “Engine files (files used by the cracking engine) such as Dictionaries, Mangling Rules, etc. can be uploaded as ‘Shared’, which allows other users to use them in task yet do not grant them the ability to download or edit.”
You can download GoCrack code from the GitHub repository along with the tool itself.
Experts have no doubt about the fact that this could be soon a privileged instrument for threat actors looking to crack passwords.
FireEye Releases Managed Password Cracking Tool
31.10.2017 securityweek Forensics
FireEye on Monday released a tool designed to help red teams manage password cracking tasks across multiple GPU servers. Called GoCrack, the open source tool provides an easy-to-use, web-based real-time UI to create, view, and manage password cracking tasks.
Developed in house by FireEye's Innovation and Custom Engineering (ICE) team, users can deploy a GoCrack server along with a worker on every GPU/CPU capable machine with tasks being automatically distributed across the GPU/CPU machines.
GoCrack currently supports the hashcat v3.6+ engine and requires no external database server, and includes support for both LDAP and database backed authentication.
The server component can run on any Linux server running Docker, while users with NVIDIA GPUs can use NVIDIA Docker to run the worker in a container with full access to the GPUs.
“Password cracking tools are an effective way for security professionals to test password effectiveness, develop improved methods to securely store passwords, and audit current password requirements,” FireEye’s Christopher Schmitt explained in a blog post. “Some use cases for a password cracking tool can include cracking passwords on exfil archives, auditing password requirements in internal tools, and offensive/defensive operations."
The tool also includes the ability to hide task data from others unless they are the creator or have been granted access to the task.
“Modifications to a task, viewing of cracked passwords, downloading a task file, and other sensitive actions are logged and available for auditing by administrators,” Schmitt wrote. “Engine files (files used by the cracking engine) such as Dictionaries, Mangling Rules, etc. can be uploaded as 'Shared', which allows other users to use them in task yet do not grant them the ability to download or edit.”
GoCrack is available for download from GitHub, along its source code.
While FireEye says the tool is targeted for use within enterprise security teams, the tool will also serve useful for malicious actors looking to crack passwords which can be used in future attacks.
Support for MySQL and Postgres database engines for larger deployments are planned for the future, along with additional features and greater configuration of the hashcat engine.
Sage Ransomware Gets Anti-Analysis Capabilities
31.10.2017 securityweek Ransomware
The Sage ransomware, which emerged toward the beginning of this year, has added new functionality that allows it to escalate privileges and evade analysis, Fortinet warns.
The malware was highly active in early 2017, but hasn’t shown significant activity over the past six months. Recently found samples resembling a Sage variant observed in March this year, however, pack both anti-analysis and privilege escalation capabilities, Fortinet's security researchers warn.
Distributed via spam emails with malicious JavaScript attachments, Sage was also found to share the same distribution infrastructure with the Locky ransomware. The malware was also observed being distributed through document files with malicious macros. It leverages .info and .top top-level domain (TLD) names for malware delivery.
The ransomware uses the ChaCha20 encryption algorithm to encrypt the victim’s files and appends the .sage extension to them. Sage avoids infecting computers that have the following keyboard layouts: Belarusian, Kazak, Uzbek, Russian, Ukrainian, Sakha, and Latvian.
A look at Sage’s code shows that most strings have been encrypted in an attempt to conceal the malicious behavior. The authors used the ChaCha20 cipher for encryption and every encrypted string has its own hard-coded decryption key, Fortinet has discovered.
Furthermore, the malware now performs a variety of checks to determine if it is being loaded into a sandbox or a virtual machine for analysis.
The threat enumerates all active processes on the machine, computes a hash for every one of them, and then checks the hashes against a hardcoded list of blacklisted processes. It also checks the full path of where the malware executes and terminates if it includes strings such as sample, malw, sampel, virus, {sample’s MD5}, and {samples’s SHA1}.
The new Sage variant also checks the computer and user names to determine if they match a list of names normally used in sandbox environments. It also uses the x86 instruction CPUID to get the processor info and compare it to a list of blacklisted CPU IDs.
On top of these, the ransomware checks whether an antivirus runs on the computer (by enumerating the services running under Service Control Manager) and checks it against a set of blacklisted MAC addresses.
Sage was also found to be able to elevate its privilege either by exploiting a patched Windows kernel vulnerability (CVE-2015-0057) or by abusing eventvwr.exe and performing registry hijacking to bypass User Account Control (UAC).
The ransom note has been translated into six more languages, which suggests that the author may aim to target more countries in the future. Victims are instructed to access an onion site using the TOR browser and to pay a $2000 ransom to purchase the “SAGE Decrypter software.”
Vulnerabilities in Google Issue Tracker exposed details about unpatched flaws
31.10.2017 securityweek Vulnerebility
A flaw in the Google Issue Tracker, also known as the “Buganizer,” might have exposed details about unpatched flaws listed in the database.
A vulnerability in the Google Issue Tracker, also known as the “Buganizer,” might have exposed details about unpatched flaws listed in the database.
The flaw was reported by the bug hunter Alex Birsan who was awarded more than $15,000 in bounties for reporting this issue and two other vulnerabilities in the Issue Tracker.
![]()
One of the flaws allowed Birsan to manipulate a request to the system that would elevate his privileges, in this way he obtained every detail about a particular vulnerability.
Even if the Google Issue Tracker is open to everyone with a Google account, the majority of the issues in the database can only be viewed by Google employees. The expert found a bug that could have let him view every issue in the database.
Birsan found a JavaScript method that allows an individual to remove themselves from a CC list via a POST request like this one:
POST /action/issues/bulk_edit HTTP/1.1
{
"issueIds":[
67111111,
67111112
],
"actions":[
{
"fieldName":"ccs",
"value":"test@example.com",
"actionType":"REMOVE"
}
]
}
The request allowed him to access full details of any bug in the Google Issue Tracker.
“However, I noticed some oversights here that led to a huge problem:
Improper access control: There was no explicit check that the current user actually had access to the issues specified in
issueIds
before attempting to perform the given action.
Silent failure: If you provided an email address that was not currently in the CCs list, the endpoint would return a message stating the email had been removed successfully.
Full issue details in response: If no errors occurred during the action, another part of the system assumed that the user had proper permissions. Thus, every single detail about the given issue ID would be returned in the HTTP response body.”
Birsan said he provided the system a few consecutive tracking numbers to confirm the issue.
“Obviously, I could now see details about every issue in the database by simply replacing issueIds in the request above. Bingo!” said the expert.
The expert was also able to exfiltrate data about multiple tickets in a single request.
“I only tried viewing a few consecutive IDs, then attacked myself from an unrelated account to confirm the severity of this problem. Yes, I could see details about vulnerability reports, along with everything else hosted on the Buganizer. Even worse, I could exfiltrate data about multiple tickets in a single request, so monitoring all the internal activity in real time probably wouldn’t have triggered any rate limiters.” Birsan added.
Birsan reported the issues to Google that disabled affected endpoint just one hour later.
Recently it was disclosed a similar incident by Microsoft, its internal bug-tracking system, a cyberespionage group stolen company vulnerabilities DB back in 2013.
The knowledge of zero-day vulnerabilities and other issues in Google products would be exploited in targeted attacks in the wild.
Investigation Underway at Heathrow Airport After USB Drive Containing Sensitive Security Documents Found on Sidewalk
31.10.2017 securityweek Privacy
Security personnel at Heathrow Airport have an exciting investigation underway after confidential security documentation was found on a sidewalk in West London.
An unnamed man, on his way to the library, spotted a thumb drive on the sidewalk in Queen’s Park, West London. He pocketed the USB drive and continued on his way. He remembered the USB drive a few days later and returned to the library to view its contents. Recognizing the sensitive nature of the information, he then turned the USB drive over to The Sunday Mirror tabloid.
In their article on October 28th, the Mirror confirmed that the thumb drive contained at least 174 documents. These documents describe various security controls and protocols in place at Heathrow including:
timetables of roving security patrols
locations of CCTV cameras
types of security badges required to access restricted areas
maps of tunnels, access points and restricted areas
routes taken by the Queen and other VIPs to the Royal Suite private area at Heathrow, and
security protocols for VIPs travelling through the airport
Heathrow Airport
It is obvious how this information would benefit someone intent on disrupting the airport or causing harm to dignitaries or VIPs. Many documents were labeled as “confidential” or “restricted” highlighting their sensitive nature. In an interesting twist, these labels follow an older labeling scheme so there is a question of how up-to-date this information is. Even if the information is outdated, knowing former protocols and designs help a bad actor to anticipate the current solutions.
According to a Heathrow Airport spokesperson’s comment to CNN, “Heathrow’s top priority is the safety and security of our passengers and colleagues. The UK and Heathrow have some of the most robust aviation security measures in the world and we remain vigilant to evolving threats by updating our procedures on a daily basis. We have reviewed all of our security plans and are confident that Heathrow remains secure. We have also launched an internal investigation to understand how this happened and are taking steps to prevent a similar occurrence in future.”
The first step in any such investigation is to understand what the immediate risk is. If exposing this information increased the risk, new risk mitigations may be required. The next step is to understand how the information found its way onto an unsecured USB drive on a public street in London. The security team then needs to come up with solutions to prevent it from happening again. At a minimum, the Heathrow security team have a few busy days of investigation ahead. More likely there are changes to security protocols and procedures coming in response to sensitive information being exposed. Even if it was only exposed to one individual and one English tabloid, will Heathrow authorities be able to identify who originally dropped the thumb drive and how can they be sure it wasn’t copied?
New iPhone Brings Face Recognition (and Fears) to the Masses
30.10.2017 securityweek Apple
Apple will let you unlock the iPhone X with your face -- a move likely to bring facial recognition to the masses, along with concerns over how the technology may be used for nefarious purposes.
Apple's newest device, set to go on sale November 3, is designed to be unlocked with a facial scan with a number of privacy safeguards -- as the data will only be stored on the phone and not in any databases.
Unlocking one's phone with a face scan may offer added convenience and security for iPhone users, according to Apple, which claims its "neural engine" for FaceID cannot be tricked by a photo or hacker.
FaceID from Apple - Facial Recognition While other devices have offered facial recognition, Apple is the first to pack the technology allowing for a three-dimensional scan into a hand-held phone.
But despite Apple's safeguards, privacy activists fear the widespread use of facial recognition would "normalize" the technology and open the door to broader use by law enforcement, marketers or others of a largely unregulated tool.
"Apple has done a number of things well for privacy but it's not always going to be about the iPhone X," said Jay Stanley, a policy analyst with the American Civil Liberties Union.
"There are real reasons to worry that facial recognition will work its way into our culture and become a surveillance technology that is abused."
A study last year by Georgetown University researchers found nearly half of all Americans in a law enforcement database that includes facial recognition, without their consent.
Civil liberties groups have sued over the FBI's use of its "next generation" biometric database, which includes facial profiles, claiming it has a high error rate and the potential for tracking innocent people.
"We don't want police officers having a watch list embedded in their body cameras scanning faces on the sidewalk," said Stanley.
Clare Garvie -- the Georgetown University Law School associate who led the 2016 study on facial recognition databases -- agreed that Apple is taking a responsible approach but others might not.
"My concern is that the public is going to become inured or complacent about this," Garvie said.
- Advertisers, police, porn stars -

Widespread use of facial recognition "could make our lives more trackable by advertisers, by law enforcement and maybe someday by private individuals," she said.
Garvie said her research found significant errors in law enforcement facial recognition databases, opening up the possibility someone could be wrongly identified as a criminal suspect.
Another worry, she said, is that police could track individuals who have committed no crime simply for participating in demonstrations.
Shanghai and other Chinese cities have recently started deploying facial recognition to catch those who flout the rules of the road, including jaywalkers.
Facial recognition and related technologies can also be used by retail stores to identify potential shoplifters, and by casinos to pinpoint undesirable gamblers.
It can even be used to deliver personalized marketing messages -- and could have some other potentially unnerving applications.
Last year, a Russian photographer figured out how to match the faces of porn stars with their social media profiles to "doxx" them, or reveal their true identities.
This type of use "can create huge problems," said Garvie. "We have to consider the worst possible uses of the technology."
Apple's system uses 30,000 infrared dots to create a digital image which is stored in a "secure enclave," according to a white paper issued by the company on its security. It said the chances of a "random" person being able to unlock the device are one in a million, compared with one in 50,000 for its TouchID.
- Legal battle brewing -
Apple's FaceID is likely to touch off fresh legal battles about whether police can require someone to unlock a device.
FaceID "brings the company deeper into a legal debate" that stemmed from the introduction of fingerprint identification on smartphones, according to ACLU staff attorney Brett Max Kaufman.
Kaufman says in a blog post that courts will be grappling with the constitutional guarantees against unreasonable searches and self-incrimination if a suspect is forced to unlock a device.
US courts have generally ruled that it would violate a user's rights to give up a passcode because it is "testimonial" -- but that situation becomes murkier when biometrics are applied.
Apple appears to have anticipated this situation by allowing a user to press two buttons for two seconds to require a passcode, but Garvie said court battles over compelling the use of FaceID are likely.
Regardless of these concerns, Apple's introduction is likely to bring about widespread use of facial recognition technology.
"What Apple is doing here will popularize and get people more comfortable with the technology," said Patrick Moorhead, principal analyst at Moor Insights & Strategy, who follows the sector.
"If I look at Apple's track record of making things easy for consumers, I'm optimistic users are going to like this."
Garvie added it is important to have conversations about facial recognition because there is little regulation governing the use of the technology.
"The technology may well be inevitable," she said. "It is going to become part of everyone's lives if it isn't already."
Hamas-Linked 'Gaza Cybergang' Has New Tools, Targets
30.10.2017 securityweek CyberCrime
A threat actor believed to be linked to the Palestinian terrorist organization Hamas continues to target organizations in the Middle East and North Africa (MENA) region, and their operations now include some new tools and techniques, Kaspersky Lab reported on Monday.
The Arabic group has been active since at least 2012 and it’s tracked by various security firms as Gaza Cybergang, Gaza Hackers Team and Molerats. The cyberspies have targeted governments, oil and gas companies, media organizations, activists, diplomats, and politicians in countries such as Egypt, the United Arab Emirates, Yemen, Jordan, Libya, Iran, and Israel.
Based on its analysis, ClearSky reported last year that Hamas was likely behind the Gaza Cybergang attacks.
Kaspersky has been monitoring the group’s campaigns and says the attackers have continued to target government entities in the MENA region. A new target is an oil and gas company in the same region, from which the hackers stole information for more than a year.
While the group continues to rely on the Cobalt Strike tool and pieces of malware such as Downeks and the Quasar RAT, researchers have found evidence suggesting that it may also be using a Trojan designed to target Android devices. The malware, first spotted in April 2017 on a command and control (C&C) server used by the group, may be linked to a previously analyzed attack targeting Israeli soldiers.
Gaza Cybergang attacks typically start with an email containing a malicious attachment or link. In attacks launched after March 2017, Kaspersky also observed specially crafted Office files that delivered malware using macros. Since June 2017, the cyberspies have also leveraged an exploit for CVE 2017-0199, an Office vulnerability patched by Microsoft in April, when it had a zero-day status.
While it’s not uncommon for threat actors to use macros to deliver malware, a majority of attacks involve Word documents. However, in the Gaza Cybergang attacks, the hackers embedded their malicious macros in Microsoft Access database files. Kaspersky believes the use of Access files could increase chances of evading detection.
“Gaza Cybergang has demonstrated a large number of attacks, advanced social engineering, in addition to the active development of attacks, infrastructure and the utilization of new methods and techniques. Attackers are actively improving their toolkit in an effort to minimize their exposure to security products and services,” Kaspersky researchers said in a blog post. “Kaspersky Lab expects these types of attacks to intensify even more both in quality and quantity in the near term.”
Heathrow Probes How Security Data Found on London Street
30.10.2017 securityweek Privacy
Heathrow Airport said Sunday it has launched an internal investigation after a memory stick containing extensive security information was found on a London street by a member of the public.
The USB drive contained dozens of folders with maps, videos and documents -- some marked confidential or restricted -- detailing security at Europe's busiest airport, according to the Sunday Mirror newspaper, which first reported the incident.
A man discovered the unencrypted device discarded on a west London pavement, and handed it into the paper, which said it reviewed the contents and passed it on to Heathrow officials.
The airport said the breach led to an immediate review of all security plans and it was "confident that Heathrow remains secure".
A spokeswoman added: "We have also launched an internal investigation to understand how this happened and are taking steps to prevent a similar occurrence in future."
She declined to detail the contents on the USB and when the security lapse occurred.
The device reportedly contained 174 documents, some referencing measures used to protect Queen Elizabeth II, and others outlining the types of IDs needed for different areas of the airport.
It also included timetables of security patrols, and maps pointing to the positions of CCTV cameras, the Sunday Mirror said.
The incident comes as Britain's threat level remains at severe following a series of deadly terrorism attacks this year.
Heathrow, Britain's biggest airport which handled nearly 76 million passengers last year, is considered a prime target for terrorists.
The airport spokeswoman said safety and security were its "top priority".
"The UK and Heathrow have some of the most robust aviation security measures in the world and we remain vigilant to evolving threats by updating our procedures on a daily basis," she added.
Oracle Patches Critical Flaw in Identity Manager
30.10.2017 securityweek Vulnerebility
Oracle informed customers on Friday that its Identity Manager product is affected by a critical vulnerability that can be easily exploited by malicious actors.
Part of the company’s Oracle Fusion Middleware offering, Identity Manager is an enterprise identity management system that automatically manages user access privileges across all of the organization’s resources.
Oracle Identity Manager is affected by a flaw that allows an unauthenticated attacker with access to the network to take control of the product. The security hole exists due to a default account that can be accessed over HTTP.
The vulnerability, tracked as CVE-2017-10151 and assigned a CVSS score of 10, has been described by Oracle as easy to exploit without any user interaction.
“Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Identity Manager,” Oracle said in its advisory. “While the vulnerability is in Oracle Identity Manager, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in takeover of Oracle Identity Manager.”
Oracle has not provided any details, likely in an effort to prevent potential attacks before users have had the chance to install the patches.
The flaw affects Oracle Identity Manager versions 11.1.1.7, 11.1.1.9, 11.1.2.1.0, 11.1.2.2.0, 11.1.2.3.0 and 12.2.1.3.0. The company has released fixes for all versions.
Two of the Critical Patch Updates (CPUs) released by Oracle this year broke previous records in terms of the number of vulnerabilities they fixed. The round of patches issued in April addressed 299 flaws, and the one from July resolved 308 security holes.
The October 2017 CPU is also significant, with 252 vulnerabilities patched. Forty weaknesses have been patched this month in Fusion Middleware, including 26 that are remotely exploitable without authentication.
Police Probe Hack of London Plastic Surgery Clinic
30.10.2017 securityweek Incindent
British police said Tuesday they were investigating the theft of data from a London plastic surgery clinic, with reports that sensitive images of celebrities have been stolen.
London Bridge Plastic Surgery said it was still establishing the extent of the hack, adding that it believed those responsible have previously targeted US medical providers.
"On Tuesday, 17 October the Metropolitan Police Service was informed of a data theft from a cosmetic surgery clinic in London," the police force said in a statement.
"Detectives from the Met's Organised Crime Command are investigating," it said, adding that no arrests have been made.
The clinic, which is located in the upmarket Marylebone district, said it was "horrified" that its patients had been targeted.
"Regrettably, following investigations by our IT experts and the police, we believe that our security was breached and that data has been stolen," it said in a statement.
"The group behind the attack are highly sophisticated and well known to international law enforcement agencies, having targeted large US medical providers and corporations over the past year."
Clients include British former glamour model Katie Price, who has previously praised the clinic for an "amazing result" after a facelift.
The Daily Beast, a US news site, said a hacking group calling itself The Dark Overlord had sent their reporter stolen photos of genitalia during surgery, using a surgery email address.
"There are some royal families in here," the hackers were quoted as saying, claiming to have stolen a database including patients' names.
"We're going to pitch it all up for everyone to nab. The entire patient list with corresponding photos. The world has never seen a medical dump of a plastic surgeon to such degree," they said.
Researchers Downplay Size of Reaper IoT Botnet
30.10.2017 securityweek BotNet
The Mirai-like "Reaper" botnet that began infecting Internet of Things (IoT) devices in late September has only ensnared up to 20,000 bots so far, according to estimates from Arbor Networks.
Called Reaper, the botnet was said a couple of weeks ago to have infected over one million organizations worldwide, but Arbor claims that the actual size of the botnet fluctuates between 10,000 and 20,000 bots in total.
The botnet’s size, the researcher reveal, could change at any time. An additional 2 million hosts have been already identified by the botnet scanner as potential nodes, although they haven’t been ensnared into Reaper yet.
“At this time, it is not clear why these candidate bots have not been co-opted into the botnet. Possible explanations include: misidentification due to flaws in the scanning code, scalability/performance issues in the Reaper code injection infrastructure, or a deliberate decision by the Reaper botmasters to throttle back the propagation mechanism,” Arbor’s ASERT researchers note.
The botnet was likely created to launch distributed denial of service (DDoS) attacks and its operators are expected to offer it as a service for the intra-China DDoS-for-hire market. It can launch SYN-floods, ACK-floods, http floods, and DNS reflection/amplification attacks.
Reaper shows code similarities with Mirai, but isn’t considered a clone. While Mirai uses password cracking for infection, the new botnet exploits vulnerabilities in targeted IoT devices, Chinese security company Qihoo says.
The firm has discovered 9 vulnerability exploits integrated into the current samples, targeting devices from 7 different manufacturers, namely Dlink, Goahead, JAWS, Netgear, Vacron NVR, Linksys, and AVTECH. The exploits list is actively updated, with one targeting Vacron NVR that was added within two days after its public disclosure on October 8.
“The botnet has embedded more than 100 DNS open resolvers in its LUA sample, so DNS amplification attack can be easily carried out. About one-third of these open DNS servers have been used as reflector in real DNS amplification attacks. We have yet to see this type of config in any other Mirai variants,” Qihoo notes.
The Chinese company also discovered that the botnet is using four different IPs for command and control (C&C), each serving a different purpose: downloader, controller, reporter, and loader. At the time of analysis, the researchers hadn’t seen a DDoS attack command issued, despite the necessary code to support such commands being present in the source file.
“The only instructions we saw are to download samples. This means the attacker is still focusing on spreading the botnets,” the researchers concluded.
iPhone Apps you granted camera access can secretly take photos and record video
30.10.2017 securityaffairs Apple
A serious privacy issue in iPhone that could be exploited by iOS app developers to silently take your photos and record your live video by enabling cameras.
Do you use an iPhone? If yes, there is probably something that you need to know about it!
The Austrian developer and Google engineer, Felix Krause, has discovered a serious privacy issue in Apple iPhone that could be exploited by iOS app developers to silently take your photos and record your live video by enabling both front and back camera.
The iPhone users will never receive any notification from the device, technical details were shared by Krause in a blog post published Wednesday.
“iOS users often grant camera access to an app soon after they download it (e.g., to add an avatar or send a photo). These apps, like a messaging app or any news-feed-based app, can easily track the users face, take pictures, or live stream the front and back camera, without the user’s consent.” wrote Krause.
According to Krause, the issue is the direct consequence of the way Apple software handles camera access. Today almost any application, including WhatsApp, Facebook, and Snapchat, requests access to your camera to allow users to take a photo within the app.
Be careful, it is not a security vulnerability, instead, it is implemented by Apple for its devices that however can be exploited by ill-intentioned to silently monitor users’ activities.
Once the users granted camera permission, a developer could perform the following operations:
access both the front and the back camera
record you at any time the app is in the foreground
take pictures and videos without telling you
upload the pictures/videos it takes immediately
run real-time face recognition to detect facial features or expressions
It is enough to enable camera access just one time when the app asks for permission to gain full access to the camera without requiring any LED light or notification, it is scaring.
“All without indicating that your phone is recording you and your surrounding, no LEDs, no light or any other kind of indication.” continues the developer.
Krause developed a proof-of-concept app only to demonstrate how a malicious app could silently abuse such permissions to take pictures every second or even live stream video of the surrounding environment.
“This project is a proof of concept and should not be used in production. The goal is to highlight a privacy loophole that can be abused by iOS apps.” continues the developer.
Below a video PoC of the issue, which shows how the demo app takes photographs of the users using it every second. The app developed by the expert uses a facial recognition system to detect the owner is using it.
Krause urges Apple to introduce a way to mitigate the issue, for example by granting only temporary permissions to access the camera.
Another way to mitigate the issue is the implementation a warning light or a mechanism to notify to the iPhone owner that their camera in currently used by an application.
Waiting for a fix, Krause suggests to protect yourself by covering the camera, exactly like Mark Zuckerberg and former FBI Director James Comey do.
New Dutch legal framework could cause Mozilla to take off the Dutch CA from its trust list.
30.10.2017 securityaffairs Safety
Mozilla would remove the Dutch CA, the CA of the Staat de Nederlanden, from its trust list due to the new national legal framework.
The Dutch Information and Security Services Act will come into force in January 2018 and one of the main effects of the new legal framework is that country’s certificate authority, CA of the Staat de Nederlanden, could be taken off the Mozilla’s trust list.
The new security laws specifically address metadata retention powers and surveillance activities. Like legal frameworks adopted by other countries, the law grants broad-based interception powers for Dutch authorities.
Mozilla maintainers argue that under the new law, the CA of the Staat de Nederlanden could be forced by the Government to support interception by abusing SSL proxying.
The Dutch secret services, with the help of the CA of the Staat de Nederlanden, could access the encrypted traffic, a situation that threatens also other European states because in The Netherlands operates major transit services.
“The new “Wet op de inlichtingen- en veiligheidsdiensten (Wiv)” (Law for intelligence and security services) has been accepted by the Dutch Government. Provisions authorizing new powers for the Dutch intelligence and security services will become active starting January 1st, 2018.” wrote Chris Van Pelt
“This revision of the law will authorise intelligence and security to intercept and analyse cable-bound (Internet) traffic, and will include far-reaching authorisations, including covert technical attacks, to facilitate their access to encrypted traffic.”
“Article 45 1.b, explicitly authorises the use of ‘false keys’ in third party systems to obtain access to systems and data”.

Van Pelt pointed out that the Dutch CA is operated by PKIOverheid / Logius that is a division of the Ministry of Interior and Kingdom Relations that also operates the AIVD intelligence service.
For this reason, Van Pelt suggests to take off the Dutch CA from the Mozilla ‘s trust list.
Code Execution Flaws Patched in Apache OpenOffice
30.10.2017 securityweek Vulnerebility
Researchers at Cisco Talos have discovered three vulnerabilities in Apache OpenOffice that can be exploited by malicious actors for remote code execution using specially crafted document files.
Talos has classified the flaws as “high severity” with a CVSS score of 8.3, but the open source software’s developers have assigned them a severity rating of only “medium.”
The security holes, tracked as CVE-2017-9806, CVE-2017-12607 and CVE-2017-12608, affect the WW8Fonts and ImportOldFormatStyles components of the Writer application, and the PPTStyleSheet functionality in the Draw application.
An attacker can create special documents that trigger an out-of-bounds write, which can be leveraged to cause the application to enter a denial-of-service (DoS) condition and crash, or execute arbitrary code.
The vulnerabilities affect Apache OpenOffice versions 4.1.3 and prior, along with OpenOffice.org. Patches are included in version 4.1.4, which the Apache Software Foundation announced earlier this month.
While there is no evidence of exploitation in the wild, Cisco Talos has published detailed technical information that can be used to launch attacks.
“Vulnerabilities in office suite software such as word processors are very useful to attackers for client side attacks. Attackers often send malicious documents attached to emails exploiting such vulnerabilities to execute malicious commands when the victim is tricked into opening the file through some form of social engineering,” Talos researchers said in a blog post.
Last year, Cisco Talos researchers reported finding similar vulnerabilities in the open source office suite LibreOffice.
“We have monitored many campaigns using this attack vector for targeted attacks. The recently analysed attack against South Korean users is a good example. The adversaries used a vulnerability in the Hangul Word Processor(HWP) to infect their victims,” they added. “This shows how important it is to keep all applications up to date and not only the operating system.”
NotPetya Attack Had Significant Impact on Merck Revenue
30.10.2017 securityweek Ransomware
American pharmaceutical giant Merck reported last week that the recent NotPetya malware attack caused losses of hundreds of millions of dollars in revenue.
The company’s financial results for the third quarter show that worldwide sales decreased by 2 percent to $10.3 billion compared to the same quarter of 2016. This was partly blamed on sales reduced by roughly $240 million due to insufficient stock of Gardasil 9, a vaccine designed to prevent certain cancers and other diseases caused by human papillomavirus (HPV).
Merck said it had to borrow the product from the U.S. Centers for Disease Control and Prevention’s Pediatric Vaccine Stockpile due to a higher demand than originally planned and the temporary disruption to production caused by the NotPetya attack.
“Additionally, as expected, revenue was unfavorably impacted by approximately $135 million from lost sales in certain markets related to the cyber-attack,” the company said in its latest SEC filing.
Merck’s marketing and administrative expenses of $2.4 billion may have also been smaller if it wasn’t for remediation costs related to the cyberattack.
Shortly after the attack, the firm reported that the incident had disrupted its worldwide operations, including manufacturing, research and sales. By late July, the company had still not fully restored manufacturing operations.
Merck is one of several major companies hit by NotPetya, a piece of malware that infected tens of thousands of systems in more than 65 countries back in June. The malware initially appeared to be a piece of ransomware, but researchers later determined that it was actually a wiper as there was no way to recover encrypted files even if the ransom was paid.
FedEx reported losses of roughly $300 million, and Danish shipping giant AP Moller-Maersk estimated that the attack would cost it $200-$300 million. Significant losses were also reported by British consumer goods company Reckitt Benckiser ($130 million), Mondelez International ($150 million), and French construction giant Saint-Gobain ($387 million by the end of the year).
The threat group that launched the NotPetya attack may also be behind the recent Bad Rabbit ransomware campaign that hit many Russian organizations and some in Ukraine. While Bad Rabbit actually appears to be a piece of ransomware – users should be able to recover their files by paying the ransom and in some cases even if they don’t pay it – the number of affected organizations is much smaller.
Industrial Products of many vendors still vulnerable to KRACK attack
30.10.2017 securityaffairs Attack
Many industrial networking devices from various vendors are still vulnerable to the recently disclosed KRACK attack (Key Reinstallation Attack).
Many industrial networking devices are vulnerable to the recently disclosed KRACK attack (Key Reinstallation Attack), including products from major vendors such as Cisco, Rockwell Automation, and Sierra Wireless.
A few weeks ago, researchers discovered several key management flaws in the core of Wi-Fi Protected Access II (WPA2) protocol that could be exploited by an attacker to hack into Wi-Fi network and eavesdrop on the Internet communications0 stealing sensitive information (i.e. credit card numbers, passwords, chat messages, emails, and pictures).
Below the full list of WPA2 Vulnerabilities discovered in the WPA2 protocol.
CVE-2017-13077: Reinstallation of the pairwise encryption key (PTK-TK) in the 4-way handshake.
CVE-2017-13078: Reinstallation of the group key (GTK) in the 4-way handshake.
CVE-2017-13079: Reinstallation of the integrity group key (IGTK) in the 4-way handshake.
CVE-2017-13080: Reinstallation of the group key (GTK) in the group key handshake.
CVE-2017-13081: Reinstallation of the integrity group key (IGTK) in the group key handshake.
CVE-2017-13082: Accepting a retransmitted Fast BSS Transition (FT) Reassociation Request and reinstalling the pairwise encryption key (PTK-TK) while processing it.
CVE-2017-13084: Reinstallation of the STK key in the PeerKey handshake.
CVE-2017-13086: reinstallation of the Tunneled Direct-Link Setup (TDLS) PeerKey (TPK) key in the TDLS handshake.
CVE-2017-13087: reinstallation of the group key (GTK) when processing a Wireless Network Management (WNM) Sleep Mode Response frame.
CVE-2017-13088: reinstallation of the integrity group key (IGTK) when processing a Wireless Network Management (WNM) Sleep Mode Response frame.
The above vulnerabilities affect products from tens of vendors, some of them are already working to fix the problems. Recently the Rockwell Automation announced to have patched its Stratix wireless access point against the KRACK vulnerability, while Microsoft addressed the issue with the October 2017 Patch Tuesday.
Sierra Wireless issued a security advisory to inform customers that many of its products, including access points and client devices, are affected by the vulnerabilities. The vendor plans to release security updates over the coming months. Siemens is still assessing its products for vulnerable devices.
WPA2 implementations are some industrial communications products are affected exposing the industrial devices to Krack attack.
Cisco confirmed that its access points and other wireless infrastructure components are affected only by the CVE-2017-13082.
Cisco published a security advisory to confirm that many products, including Cisco 829 Industrial Integrated Services routers and Industrial Wireless 3700 series access points, are affected by multiple vulnerabilities in Wi-Fi Protected Access and Wi-Fi Protected Access II.
“Among these ten vulnerabilities, only one (CVE-2017-13082) may affect components of the wireless infrastructure (for example, Access Points), the other nine vulnerabilities affect only client devices.
Multiple Cisco wireless products are affected by these vulnerabilities.” states the security advisory.
“Cisco will release software updates that address these vulnerabilities. There are workarounds that addresses the vulnerabilities in CVE-2017-13077, CVE-2017-13078, CVE-2017-13079, CVE-2017-13080, CVE-2017-13081, and CVE-2017-13082. There are no workarounds for CVE-2017-13086, CVE-2017-13087, and CVE-2017-13088.”
Cisco still hasn’t released security updates for the vulnerable industrial products, however, the tech giant suggested workarounds for some of the flaws.
VPN Law Latest Step in Kremlin Online Crackdown: Experts
30.10.2017 securityweek BigBrothers
A law coming into force on Wednesday will give the Kremlin greater control over what Russians can access online ahead of a presidential election next March.
Providers of virtual private networks (VPNs) -- which let internet users access sites banned in one country by making it appear that they are browsing from abroad -- will be required to block websites listed by the Russian state communications watchdog.
The law is the latest in a raft of restrictions introduced by President Vladimir Putin's government and is expected to affect journalists and opposition activists, even though several VPN providers say they will not comply.
Videos by the punk band Pussy Riot and the blog of opposition leader Alexei Navalny have in the past been blocked under a law that allows authorities to blacklist websites they consider extremist.
"Journalists and activists who are using this to put out messages anonymously will be affected," Eva Galperin, director of cybersecurity at the US-based Electronic Frontier Foundation, told AFP.
Even if they are able to work around the new restrictions, the law will send a powerful message to activists, she said.
"If you're thinking about taking the steps that you need to stay anonymous from the government, you think maybe it's not worth it."
The law will likely be selectively applied and will probably not affect foreign business people using company VPNs, she said.
The measure is part of a wider crackdown on online communications, which this month saw the popular messaging app, Telegram, fined for failing to register with the Roskomnadzor communications watchdog and provide the FSB with information on user interactions.
Starting from 2018, companies on the Roskomnadzor register must also store all the data of Russian users inside the country, according to anti-terror legislation which was passed last year and decried by the opposition and internet companies.
On Thursday, the Russian parliament's lower house approved a draft law that would let the attorney general blacklist the websites of "undesirable organisations" without a court order.
- 'Less safe, less free' -
While falling short of a blanket ban on virtual private networks, the new law undermines one of their key purposes and "essentially asks VPN services to help enforce Russia's censorship regime", Harold Li, vice president at ExpressVPN International, told AFP by email.
"VPNs are central to online privacy, anonymity, and freedom of speech, so these restrictions represent an attack on digital rights," Li said.
"We hope and expect that most major VPN services will not bend to these new restrictions."
Providers ZenMate and Private Internet Access -- which said it removed all of its servers from Russia in 2016 after several of them were seized by authorities without notification -- have already announced that they would not enforce the list of banned websites.
Companies that do not comply are likely to see their own websites placed on the Russian blacklist.
Amnesty International has called the new legislation "a major blow to internet freedom" and Edward Snowden, the NSA whistleblower who lives in Russia, said the measure "makes Russia both less safe and less free".
Laws curbing internet freedoms were drafted following mass protests in 2011 and 2012 against Putin over disputed election results.
The new measures come into force ahead of presidential elections next March, when Putin is widely expected to extend his grip on power to 2024.
Russia's opposition groups rely heavily on the internet to make up for their lack of access to the mainstream media.
- 'Complete control' -
"The path that Russia chose four years ago is founded on the concept of digital sovereignty," said Sarkis Darbinyan, lawyer and director of the Digital Rights Centre.
"It's the idea that the government should control the domestic part of the internet. Western countries do not support this concept and so what we are seeing today is an Asian-style development of the internet," along the lines of China and Iran, he said.
But Galperin of the Electronic Frontier Foundation noted that even if the Kremlin's end goal is "complete control of communications on the internet", its technical capabilities still lag way behind China with its "Great Firewall".
Many of the invasive measures pushed by the Kremlin are comparable with the snooping powers demanded by Western governments, she said.
"Russia will frequently point to the fact that the FBI and (British Prime Minister) Theresa May want these powers as reasons why they should have them, and why they're compatible with human rights."
Hashcat 4.0.0 now can crack passwords and salts up to length 256
30.10.2017 securityaffairs Hacking
The new version of the tool, Hashcat 4.0.0 release is now available and includes the support to crack passwords and salts up to length 256.
Hashcat is likely the world’s fastest password recovery tool that is released as free software. It is available for Windows, Linux and OS X, and it is distributed as CPU-based or GPU-based applications.
The new version of the tool, Hashcat 4.0.0 release is now available and includes the support to crack passwords and salts up to length 256.
Users can download the tool here: https://hashcat.net/hashcat/.
The implementation of this new feature took a significant effort of the development team.
“Internally, this change took a lot of effort – many months of work. The first step was to add an OpenSSL-style low-level hash interface with the typical HashInit(), HashUpdate() and HashFinal() functions.” states the official announcement for Hashcat 4.0.0. “After that, every OpenCL kernel had to be rewritten from scratch using those functions. Adding the OpenSSL-style low-level hash functions also had the advantage that you can now add new kernels more easily to hashcat – but the disadvantage is that such kernels are slower than hand-optimized kernels.”
The developers initially added an OpenSSL-style low-level hash interface, later they have had rewritten from scratch the OpenCL kernel.
The new version also includes a self-test functionality to detect broken OpenCL runtimes on startup, it is the first time that such kind of feature is added to the tool.
Some older OpenCL runtimes were somewhat faulty and errors were hard to discover due to the lack of any error message.
“With this version, hashcat tries to crack a known hash on startup with a known password. Failing to crack a simple known hash is a bulletproof way to test whether your system is set up correctly.” continues the announcement.

Hashcat 4.0.0. added hash-mode 2501 = WPA/WPA2 PMK, it allows to run precomputed PMK lists against a hccapx. To precompute the PMK, the development team suggests using the wlanhcx2psk from hcxtools, it is a solution for capturing WLAN traffic and convert it to hashcat formats.
The new release of the popular password recovery tool also improved the macOS support.
“The evil “abort trap 6” error is now handled in a different way. There is no more need to maintain many different OpenCL devices in the hashcat.hctune database.” continues the announcement.
The new version of the tool also added the implementation for the following algorithms.
Added hash-mode 2500 = WPA/WPA2 (SHA256-AES-CMAC)
Added hash-mode 2501 = WPA/WPA2 PMK
Matrix Ransomware being distributed through malvertising
30.10.2017 securityaffairs Ransomware
Security expert Jérôme Segura from Malwarebytes has spotted that Matrix Ransomware has risen again, it is now being distributed through malvertising.
Malware researcher Jérôme Segura from Malwarebytes has discovered that Matrix Ransomware is now being distributed through malvertising campaign.


EKFiddle @EKFiddle
#RIGEK drops Matrix ransomware. Payload https://www.virustotal.com/#/file/522e7328b76109502231e9f80a2c83fb0c57c28db98b54e0e7f401e368401046/detection … SAZ https://drive.google.com/file/d/0B4QZ_nlBrTP5MngwY3lMeGQ4eTA/view?usp=sharing …
10:20 PM - Oct 26, 2017
1 1 Reply 28 28 Retweets 16 16 likes
Twitter Ads info and privacy
The Matrix Ransomware was first spotted in 2016, in April 2017 the threat intelligence expert Brad Duncan uncovered the EITest campaign using the RIG exploit kit to distribute this malware.
Since then the Matrix ransomware slightly disappeared from the threat landscape, but now it seems to be back and it is being delivered through malvertising campaign that triggers an Internet Explorer flaw (CVE-2016-0189) and Flash one(CVE-2015-8651).
When a computer is infected with the latest variant of the Matrix Ransomware, the malicious code will encrypt the files on the victim’s machine, scramble their file names, and append the .pyongyan001@yahoo.com extension to the file scrambled name.
The ransomware also drops a ransom note (#_#WhatWrongWithMyFiles#_#.rtf) in every folder that contains files it encrypted, then it will display a ransom screen.

To protect your system, it is essential to install all available security updates for any software installed on the machine, run a security software, and always backup your data.
Šíří se nový ransomware Bad Rabbit, maskuje se jako update Flashe
29.10.2017 Lupa.cz Viry
Počítačové systémy zatím zejména v Rusku a na Ukrajině začal 24. října napadat nový ransomware, pro který se začal používat název Bad Rabbit. Mezi napadenými jsou například ruská tisková agentura Interfax, platební systém v kyjevském metru či mezinárodní letiště v ukrajinské Oděse, informuje server ZDNet.
Podle antivirové firmy ESET stojí přinejmenším za nákazou v kyjevském metru nová varianta ransomwaru Diskcoder.D, který se před několika měsíci proslavil pod jménem Petya/nonPetya.
TIP: Vyděrači v počítači: jaká je nejlepší obrana proti ransomwaru?
Kaspersky Lab pro změnu informují o tom, že malware se do počítačů dostává z nakažených webových stránek. Maskuje se jako update pro Adobe Flash a pokouší se uživatele přesvědčit, aby soubor s malwarem sám spustil.
Podle firmy Check Point malware po nainstalování v počítači zašifruje soubory a za odemčení požaduje výkupné ve výši 0,05 bitcoinu. Na zaplacení dává lhůtu 40 hodin.

Ruská kyberšpionáž, čeští hackeři, zranitelné úřady. BIS vydala výroční zprávu
29.10.2017 Lupa.cz BigBrother
Bezpečnostní informační služba (BIS) tento týden zveřejnila svoji tradiční veřejnou výroční zprávu, tentokrát za rok 2016. Jedna sekce je věnovaná také kybernetické bezpečnosti.
Zpráva informuje, že členové české hackerské skupiny objevili zranitelnosti na webech několika státních institucí a na serveru hostujícím stránky státního představitele. Zmínky padly také o zranitelnosti na portálu jedné banky, plánech českých Anonymous, systému Visapoint nebo ruské kybernetické špionáži.
Celé znění sekce o kyberbezpečnosti ze zprávy BIS:
Obdobně jako v minulých letech monitorovala BIS problémy spojené s fungováním informačního systému Visapoint provozovaného Ministerstvem zahraničních věcí. V minulosti, především pak v roce 2015, se podařilo mnoho těchto problémů úspěšně odstranit, některé však přetrvávají.
Stálým problémem IS Visapoint zůstávají zápisy do systému prováděné automatizovanými softwarovými nástroji. Ty zaregistrují značné množství volných termínů pro pohovory, které jsou nezbytnou součástí žádostí o vízum, a brání tak běžným žadatelům zaregistrovat se standardním způsobem na pohovor na českém zastupitelském úřadu. Běžní žadatelé pak nemají jinou možnost, než od tzv. zprostředkovatele zaregistrovaný termín na pohovor za značnou finanční částku odkoupit.
V průběhu roku BIS informovala MZV o skutečnosti, že někteří ze zprostředkovatelů zápisů na volné termíny pohovorů nalezli způsob překonání pokročilého ochranného prvku reCAPTCHA, který MZV v té době využívalo v IS Visapoint jako ochranu proti automatizovaným softwarovým nástrojům. Ze snahy zprostředkovatelů zápisů překonat prvek reCAPTCHA je zřejmé, že registrace na volné termíny pohovorů je i nadále oblastí, ve které se pohybují značné finanční prostředky.
České hackerské skupiny
V průběhu roku 2016 BIS zjistila, že členové české hackerské skupiny objevili zranitelnosti na webových portálech několika státních institucí a na serveru hostujícím internetové stránky významného českého státního představitele. Skupina využila těchto zranitelností a umístila na portály skript na ovládání serveru (tzv. shell). S ohledem na dřívější i ostatní aktivity hackerské skupiny bylo možné předpokládat snahy o využití objevené zranitelnosti k finančnímu obohacení. Informace o zranitelnosti se mohla tato skupina pokusit prodat ať již přímo dotčeným státním institucím nebo např. osobám z hackerského prostředí.
Skupina objevila na portálu jedné v ČR působící banky konkrétní zranitelnost. Totožná skupina umístila do informačního systému další banky působící v ČR tzv. shell, který jejím členům pravděpodobně umožňoval přistupovat k dalším bankovním systémům. Tento shell měl zároveň sloužit jako tzv. backdoor, a měl tak členům skupiny umožňovat utajený přístup do informačního systému banky i v případě, že by byla odstraněna (tj. opravena nebo zablokována) zranitelnost, již zneužili k prvotnímu průniku do zmíněného informačního systému.
V závěru roku informovala BIS o plánech českých Anonymous uskutečnit elektronické útoky proti webovým portálům českých státních institucí v rámci akce Million Mask March (celosvětový hromadný pochod organizovaný „hnutím“ Anonymous), která se konala 5. listopadu 2016. Na základě obdobných případů z minulosti bylo možné předpokládat nejspíše jednoduché útoky typu (D)DoS, případně defacement, tedy takové útoky, které již čeští Anonymous v minulosti úspěšně provedli.
Zranitelnosti
BIS při šetření ke kompromitacím síťových zařízení kyberšpionážní kampaní získala také informace o konfiguraci portů na některých IP adresách patřících do rozsahu několika českých ministerstev. Některé porty otevřené do internetu umožňovaly přímý přístup k autentizačním formulářům využívaným pro administraci síťových zařízení umístěných na IP adresách spravovaných ministerstvy, v některých případech byla stále používána zastaralá varianta Key Exchange Algorithm, jejíž zranitelnosti již byly publikovány v otevřených zdrojích. BIS rovněž zjistila, že některá síťová zařízení měla v té době již zastaralý firmware.
V průběhu roku poskytla BIS Národnímu bezpečnostnímu úřadu informace o rozcestníku, který umožňuje přístup k doménám využívaným pro elektronické útoky. Tyto domény pak zpravidla slouží pro phishingové útoky, nebo jsou zdrojem pro stažení škodlivých kódů. Útoky z nich vycházející pravděpodobně souvisejí s kyberšpionáží či obecně s kybernetickým zločinem. Jejich existence představuje bezpečnostní riziko především pro možnost kompromitace kritické informační infrastruktury nebo významných informačních systémů na území ČR a následné špionáže či napadení.
Ruská kybernetická špionáž
BIS v roce 2016 pokračovala v šetření započatém již v roce 2015 zaměřeném na možnou kompromitaci routerů na IP adresách ve správě dvou českých státních úřadů. BIS získala nové informace technického charakteru, které mohly napomoci k odhalení případné kompromitace konkrétních routerů.
Kampaň APT28/Sofacy je v současné době zřejmě nejaktivnější a nejviditelnější ruskou kyberšpionážní kampaní s velice rozmanitými oblastmi působnosti – od primárních oblastí diplomacie a vojenství přes vědu a výzkum až k akademické sféře. Ačkoliv jde o jednu z nejstarších, nejlépe popsaných, a i v otevřených zdrojích identifikovaných kyberšpionážních kampaní, je její efektivita stále značná a lze předpokládat, že bude pokračovat i v budoucnu. Kampaň APT28/Sofacy necílí pouze na data jako taková, ale v poslední době se zaměřuje na krádeže osobních údajů a přihlašovacích údajů do informačních a komunikačních systémů. Zcizená data a informace mohou být využívány k nejrůznějším účelům – ať již k politickým nebo vědecko-průmyslovým, nebo například k dehonestaci určitých osob či přímo států, k dezinformacím, případně k vydírání. Ruská kyberšpionážní kampaň APT28/Sofacy byla v roce 2016, stejně jako v roce předcházejícím, proti českým cílům velice aktivní. Kampaň využívala k útokům proti českým cílům počítačovou infrastrukturu umístěnou v zahraničí. Zmíněná kampaň kompromitovala několik soukromých emailových účtů osob s vazbami na české vojenské prostředí. Útočníci kampaně APT28/Sofacy se z emailových účtů mohli dozvědět mj. mnohé osobní informace o jejich majitelích.
Cílem ruské kyberšpionážní kampaně APT28/Sofacy se stala také česká vojenská výzkumná instituce. V průběhu podzimu 2016 probíhala další vlna ruské kyberšpionážní kampaně APT28/Sofacy, která cílila na ministerstva zahraničních věcí a obrany v evropských státech.
Mimo výše zmíněné informovala BIS v roce 2016 své adresáty o elektronických útocích v rámci dalších konkrétních kyberšpionážních kampaní.
Ruský antivir chrání VZP i vnitro. Podle USA je bezpečnostním rizikem
29.10.2017 Idnes.cz BigBrother
Americké bezpečnostní složky jsou přesvědčené, že antivirový program ruské společnosti Kaspersky nejenom brání před viry, ale naopak slouží i jako zadní vrátka pro ruské hackery. V Česku ale Rusové chrání třeba i ministerstvo vnitra či VZP. Před hrozbou nepřímo ve výroční zprávě varovala i BIS.
Deník Wall Street Journal (WSJ) nedávno popsal, jak ruští útočníci s pomocí programu Kaspersky ukradli přísně tajné materiály národní bezpečnostní agentury NSA, což může vést k oslabení kybernetické obrany USA.
Program dle The New York Times (NYT) dokonce na počítačích, na kterých je nainstalovaný, nepátrá jen po virech, ale také hledá dokumenty, které jsou označené třeba jako „přísně tajné“, aby na jejich přítomnost upozornil ruskou vládu.
Americká vláda už v září všem federálním úřadům s okamžitou platností přikázala antivirus odinstalovat ze všech počítačů tamních úřadů.
MF DNES ovšem zmapovala, že v Česku ten samý antivirový program Kaspersky nerušeně používají klíčové instituce. K obraně svých počítačů si ho dle smlouvy z registru ze začátku roku smluv vybralo například i ministerstvo vnitra.
Na dotazy MF DNES ovšem neodpovědělo.
Kaspersky běží i na všech počítačích Všeobecné zdravotní pojišťovny, která spravuje citlivé zdravotní údaje více než šesti milionů Čechů.
Ani VZP důvod, proč Kaspersky používá, nekomentovala. „Vzhledem k charakteru vašich dotazů a dotazovaným skutečnostem zvolte prosím postup podle zákona o svobodném přístupu k informacím,“ odmítl otázky redakce mluvčí VZP Oldřich Tichý.
To, že pojišťovna antivirový program firmy se sídlem v Moskvě používá, MF DNES zjistila z registru smluv, kam VZP v několika případech vložila detailní popis všech svých počítačových systémů včetně hardwaru, softwaru i jejich obrany.
USA už nevěří firmě Kaspersky
Před používáním ruských či čínských informačních technologií přitom ve své výroční zprávě vydané v úterý důkladně, byť obecně, varovala Bezpečnostní a inforační služba (BIS).
„Ekonomická výhodnost se často dostává do rozporu s bezpečnostními zájmy. Typickým příkladem je bezpečnost státních ICT systémů, kdy pro určité dodavatele není problém naplnit formální bezpečnostní požadavky pro účast v tendru, ačkoliv jsou jasně spojeni s relevantními bezpečnostními riziky,“ uvádí BIS ve veřené části své zprávy.
Útok přes domácí počítač
Celkově Kaspersky hlásí, že mezi jeho zákazníky patří na 270 tisíc firem po cleém světě. Americká NSA má ale s programem hořkou zkušenost. Hackeři se k jejím tajným informacím při incidentu z roku 2015, který vyšel najevo nyní, nedostali přímo přes počítače tajné služby.
Na těch byl už tehdy ruský antivirus zakázaný. Jeden ze zaměstnanců NSA ale přenesl přísně tajné dokumenty do domácího počítače, na kterém antivirový program Kaspersky běžel.
A právě antivirový sken pak na zajímavé soubory podle nejmenovaných zdrojů WSJ upozornil hackery.
Ti dle dostupných informací získali i informace o tom, jak naopak americká NSA napadá systémy v zahraničí.
Firma nařčení považuje za politickou hru
NYT pak doplnily, že izraelské tajné služby sledovaly ještě mnohem širší počínání Kaspersky, který vyhledával citlivé dokumenty na všech počítačích, nanichž byl nainstalován. Ruským tajným službám tak mohl sloužit podobně jako Google, jen pro soukromé a zabezpečené počítače. Izraelci pak před hrozbou varovaly Američany.
Kaspersky se proti nařčení důkladně ohrazuje.
„Jsme soukromá společnost a nemáme nevhodné vazby na jakoukoliv vládu, včetně té ruské. Jediné rozumné vysvětlení je, že jsme se ocitli uprostřed geopolitického boje,“ odmítl nařčení z USA šéf firmy Eugene Kaspersky s tím, že mu připomíná scénář céčkového špionážního filmu.
Kompletní vyjádření Kaspersky Lab
„Společnost Kaspersky Lab nemá žádné vazby na vlády, nikdy nepomáhala a ani nebude pomáhat žádným vládám jakéhokoliv státu v kyberšpionážních aktivitách. Společnost má za sebou dvacetiletou historii v oboru IT bezpečnosti, přičemž vždy splňovala jak nejvyšší etické obchodní postupy, tak i důvěryhodné postupy vývoje nových technologií. Kaspersky Lab považuje za nepřijatelné, že je nespravedlivě obviňována z něčeho, k čemu neexistují jasné důkazy, které by toto nařčení potvrzovaly. Zdá se, že se společnost Kaspersky Lab jakožto soukromá firma stala nástrojem geopolitického boje, kdy se ji každá ze stran snaží využít jako pěšáka ve své politické hře.
Eugene Kaspersky, CEO a zakladatel Kaspersky Lab, opakovaně nabídl, že se setká s vládními představiteli a že bude vypovídat před Kongresem USA. Rovněž je připraven poskytnout zdrojový kód společnosti k oficiálnímu auditu, který pomůže vyřešit veškeré otázky vlády USA vztahující se ke společnosti. Kaspersky Lab zůstává i nadále k dispozici všem vládním organizacím, které budou vyžadovat spolupráci při jakékoli formě vyšetřování. Společnost je přesvědčena, že podrobnější přezkoumání jejích aktivit potvrdí, že jsou veškerá obvinění neopodstatněná.“
Kaspersky vystudoval kryptografii na škole podporované KGB a v minulosti pracoval v ruské vojenské rozvědce. Agentura Bloomberg informovala, že zaměstnanci Kaspersky tvořili doprovod ruských agentů FSB při jejich zásazích.
Firma nedávno oznámila celosvětový start svého antiviru pro domácí použití, který hodlá nabízet zdarma. Američtí bezpečnostní experti ale ruskému antiviru nedůvěřují.
„Antivirus poskytuje spolehlivý vzdálený přístup, který může být použitý k jakémukoliv účelu. Od spuštění zničujícího útoku, až po sledování tisíců nebo dokonce milionů uživatelů,“ řekl NYT bezpečnostní expert a někdejší příslušník NSA Blake Darché.
Kaspersky používá i brněnská městská policie či špičkové výzkumné instituce
To firmy i instituce musejí platit. Jak plyne z dokumentů umístěných v registru smluv, brněnská městská policie od Rusů koupila nejenom antivirový program, ale i zabezpečení e-mailových schránek a serverů za půl milionu.
Podle mluvčího Jakuba Ghanema si strážníci antivirus vybrali kvůli široké databázi virů. „Informace o programu Kaspersky jsme zaznamenali. Obracíme se na zprostředkovatelskou firmu s žádostí o vyjádření k bezpečnosti softwaru,“ konstatoval mluvčí strážníků Jakub Ghanem.
Že by prostřednictvím softwaru, který má počítače chránit, mohli naopak hackeři unikátní výzkumy krást, neobávají ani akademici. Antivirový program Kaspersky brání i počítače Ústavu fyzikální chemie pojmenovaném po Nobelistovi Jaroslavu Heyrovském.
Prestižní instituce nakoupila 250 licencí na tři roky za takřka sto tisíc korun. Stejný antivirový program ale nakoupil i Ústav informatiky akademie věd. A Mendelova univerzita v Brně pořídila rovnou 1500 licencí za 210 tisíc korun.
To, že české úřady antivirový program používají, se přitom příliš nelíbí šéfovi Národního úřadu pro kybernetickou a informační bezpečnost Dušanu Navrátilovi.
„Můj názor je ten, že bychom měli používat hardware či software pouze států, kteří jsou našimi spojenci – ať už v EU, či v NATO. Problém je v zákoně o veřejných zakázkách. Ten to takto rozlišovat neumožňuje,“ řekl před časem v rozhovoru pro MF DNES.
BIS varovala i před Číňany
Podezření západních agentů se ale netýká jen Rusů, ale i čínských firem.
Vyzvědačství má v Číně tradici. Proč by Česko mělo být výjimkou?
„V čínském hardwaru mohly existovat úmyslně vložené chyby. Ty mohou v případě potřeby posloužit k vyřazení komunikační infrastruktury protivníka nebo získání citlivých informací,“ varovala ve své zprávě před čínskými firmami Huawei a ZTE v roce 2014 i česká Bezpečnostní informační služba ČR (BIS).
Registr smluv ale nyní dokládá, že své počítačové sítě z výrobků Huawei skládá například i Státní úřad pro jadernou bezpečnost. Ministerstvo vnitra, policie i Úřad vlády ČR nakupují od Huawei mobily či modemy.
Jak dříve upozornily LN, zákazníkem firmy, kterou založil někdejší vojenský technik Žen Čeng-fej, je od roku 2014 i Hrad. Ten výměnou za stovky telefonů Číňanům poskytuje lístky na hradní akce či občasný pronájem prostor.
„Bez komentáře,“ nevyjádřil se národní šéf přes počítačovou bezpečnost Navrátil k tomu, zda on by si čínský telefon pořídil. Výrobkům Huawei se ale nevyhnou ani majitelé zcela jiných značek mobilů.
Firma je totiž masivním dodavatelem infrastruktury pro české mobilní operátory, přes kterou data z mobilů tečou. Zásadní konkurenty dlouhodobě trumfuje cenou.
I Huawei jakoukoliv nekalou spolupráci s čínskou vládou důrazně popírá.
IOActive disclosed 2 critical flaws in global satellite telecommunications Inmarsat’s SATCOM systems
29.10.2017securityaffairs Vulnerebility
Flaws in Stratos Global AmosConnect 8 PC-based SATCOM service impact thousands of customers worldwide running the newest version of the platform that is used in vessels.
Security researchers at IOActive have disclosed critical security vulnerabilities in the maritime Stratos Global’s AmosConnect 8.4.0 satellite-based shipboard communication platform.
AmosConnect 8 is a PC-based SATCOM service, introduced in 2010, that integrates many communication tools such as email, fax, telex, GSM text and interoffice communication.
According to the researchers from IOActive. Inmarsat, which owns Stratos Global, considered the research as irrelevant because it related to a communication platform that has been discontinued.
“When IOActive brought the potential vulnerability to our attention, early in 2017, and despite the product reaching end of life, Inmarsat issued a security patch that was applied to AC8 to greatly reduce the risk potentially posed.” reads the statement issued by Inmarsat.
The vendor speculated the attack scenario shown by the experts would be difficult to realize.
Experts at IOActive confirmed that the vulnerabilities impact thousands of customers worldwide running the newest version of the AmosConnect platform that is used in vessels.
The vulnerabilities discovered by the researchers include a “blind SQL injection, tracked as CVE-2017-3221, in a login form and a backdoor account (CVE-2017-3222) that gives attackers full system privileges.
The blind SQL injection vulnerability in AmosConnect 8 login form could be exploited by unauthenticated attackers to access login credentials of other users.
“A Blind SQL Injection vulnerability is present in the login form, allowing unauthenticated attackers to gain access to credentials stored in its internal database. The server stores usernames and passwords in plaintext, making this vulnerability trivial to exploit.” states the advisory published by IOActive.

The second issue could be exploited by an attacker to execute arbitrary code on the platform server and potentially exposing sensitive data.
“The AmosConnect server features a built-in backdoor account with full system privileges. Among other things, this vulnerability allows attackers to execute commands with SYSTEM privileges on the remote system by abusing AmosConnect Task Manager.” continues IOActive.
IOActive notified the vulnerabilities Inmarsat in October 2016, and completed the disclosure process in July 2017, meantime the Inmarsat has discontinued the AmosConnect 8.0 version of the platform.
Currently, the vendor refuses connections from AmosConnect 8 email clients, so customers cannot use this software.
According to the experts form IOActive, Vessel networks are typically segmented and isolated from each other, typical subnets are:
Navigation systems network.
Industrial Control Systems (ICS) network.
IT systems network.
Bring-Your-Own-Device networks.
SATCOM.
The experts remarked that while the vulnerabilities recently discovered may only be exploited by an attacker with access to the IT systems network, within certain vessel configurations some networks might not be segmented, exposing vulnerable AmosConnect platforms to one or more of these networks.
“A typical scenario would make AmosConnect available to both the BYOD “guest” and IT networks; one can easily see how these vulnerabilities could be exploited by a local attacker to pivot from the guest network to the IT network.” concluded IOActive. “Also, some the vulnerabilities uncovered during our SATCOM research might enable attackers to access these systems via the satellite link.”
Mysterious hack allows attackers stealing Windows login credentials without user interaction
29.10.2017securityaffairs Hacking
Microsoft fixed a vulnerability that could allow hackers to steal Windows login credentials without any user interaction.
Microsoft fixed a serious vulnerability that could allow attackers to steal Windows NTLM password hashes without any user interaction.
The tech giant patched the issues only for recent versions Windows (Windows 10 and Server 2016), to trigger the flaw the attacker just needs to do is to place a specially crafted Shell Command File (SCF file) inside publicly accessible Windows folders.
Once the attacker has placed the file in the folder, it executes due to the security issue, gathers the machine NTLM password hash, and sends it back to the attacker’s server.
Then the attacker can easily crack the NTLM password hash to access the victim’s computer. The hack was reported to Microsoft in May by the Columbian security researcher Juan Diego.
“It is a known issue that Microsoft NTLM architecture has some failures, hash stealing is not something new, it is one of the first things a pentester tries when attacking a Microsoft environment. But, most of these techniques require user intervention or traffic interception to fulfill the attack.” wrote Juan Diego.
“These new attacks require no user interaction, everything is done from the attacker’s side, but of course, there are some conditions that need to be met to be successful with this attack.”
Older Windows versions remain vulnerable because the registry modifications are not compatible with older versions of the Windows Firewall.
“Accordingly to Microsoft, all Windows versions since 3.11 till Windows 10, Desktop and server are vulnerable to this kind of attack.” explained Diego.
“Honestly, I have only tested on Windows 7 and Windows 10, then I passed the ball to Microsoft 🙂”
The good news is that the hack doesn’t work against machines with shared folders that are protected by a password, and this is the default option in Windows limiting the extent of the vulnerability.
Windows login credentials shared folders
Nonetheless, in many cases the Windows users need to share folders without a password according to their needs, opening their systems for attacks.
Microsoft fixed the issue with the October Patch Tuesday via the ADV170014 security advisory.
Be careful, the ADV170014 is an optional patch, installing it is highly recommended.
Diego was not able to detail why the attack was possible, in previously known attacks leveraging SCF files, in order to trigger the flaw, the victim should have had access the folder.
In the attack scenario detailed by Diego, the SCF files are executed just after the attacker place it in the shared folder without needing user’s interaction.
According to Bleepingcomputers.com, Microsoft acknowledged another security researcher, Stefan Kanthak, for reporting the issue.
“While Diego has reported his attack to Microsoft, it was German researcher Stefan Kanthak who got an acknowledgment from Microsoft for the fixed issue, as he too reported similar bugs in March 2017.” reported Bleeping computer.
“Microsoft did (as every so often) a POOR job, the updates published this month close only 2 of the 6 distinct weaknesses I reported,” Kanthak told Bleeping via email, hinting that more ways to exploit pass-the-hash attacks exist.
Let me close with mitigation provided by Diego:
“Microsoft created a sort of patch to this vulnerability consisting in changing two registry keys to disable NTLM on the system. This registry keys are available only on Windows 10 and Windows Server 2016, and Microsoft has no intentions to backport to the other versions.
Another issue is that disabling NTLM will break a lot of environments, and that’s a huge concern for them.” suggested the expert.
“My suggestion is to use strong passwords, after the attack we need to crack the hash, that can take a lot of time if the password is complex, and can be frustrating for the attacker.
The better approach, don’t share folders without passwords, that’ll do the trick.”
Basetools underground hacking forum breached, hacker demands $50K ransom
29.10.2017securityaffairs Ransomware
Basetools underground hacking forum was breached, hackers demand a $50K ransom to avoid sharing stolen data, including admin identity, with law enforcement.
A hacker that goes online with the Twitter handle mat (@0xScripts) has breached a popular underground hacking forum and he is threatening to share the stolen archive to the law enforcement if the administrators will not pay $50,000.
The forum is Basetools.ws, its members trade any kind of illegal product and service, including stolen payment card data, hacking tools, and stolen account data.
The hacking forum accounts for over 150,000 users, and its listing includes more than 20,000 tools. The hackers published this week a sample of the stolen data online demanding a ransom to the operators of the forum.
The hacker ‘mat’ contacted also Security Affairs to notify the data breach.

Mat is threatening to share data on the forum’s administrator with US law enforcement agencies.
He provided me the evidence of the authenticity of the stolen data, he shared with me and BleepingComputer an image of the Basetools admin panel and an image containing the site admin’s login details and IP address.
“I dumped the tools they were selling, their login credentials for cpanel accounts” Mat @0xScripts told me, he also added the he hacked the forum alone.
“login credentials for shells backdoors spambot etc”
The listing includes:
credentials for RDP servers;
login credentials for shells and backdoors:
login credentials for spambots hosted on compromised websites;
login credentials for server SSH;
dump form several data breaches;
The data breach is very serious and could have significant consequences for cybercrime underground community. The stolen data includes Basetools seller data could be soon leaked online. The above credentials could be leaked online and used by many other threat actors in the wild.

Below another image published by BleepingComputer

At the time I was writing, the basetools underground hacking forum is offline
The hackers told me that he hacked the forum not only for money but also as a retaliation for the fact that its administrator has been manipulating stats.
“He’s not a reseller, basetools is manipulating the stats by putting him in top places everytime and earning stats are manipulated by basetools” the hacker told me.
“Basetools.pw is manipulating EARNING STATS & RESELLER STATS, Owner of this market has opened a reseller with name RedHat which always stays in First Place,” reads the ransom note.
Files Encrypted by Bad Rabbit Recoverable Without Paying Ransom
28.10.2017 securityweek Ransomware
Some users may be able to recover the files encrypted by the Bad Rabbit ransomware without paying the ransom, Kaspersky researchers discovered after analyzing the malware’s encryption functionality.
Once it infects a device, Bad Rabbit looks for certain file types and encrypts them. The disk is also encrypted and a ransom screen is displayed when the computer boots, preventing the victim from accessing the operating system. The disk encryption and bootloader functionality are provided by code derived from a legitimate utility named DiskCryptor.
Bad Rabbit has been linked to the NotPetya attack that caused significant disruptions to many companies back in late June. However, unlike NotPetya, which experts classified as a wiper due to the fact that victims could not recover their files even if they paid the ransom, files encrypted by Bad Rabbit can be recovered with the right decryption key.
While the encryption mechanisms used by the attackers, AES-128-CBC and RSA-2048, cannot be cracked, Kaspersky experts have identified some methods that may allow some victims to decrypt their disk and recover files.
When an infected computer boots up, users are informed that their files have been encrypted and they are instructed to make a payment in order to obtain the password needed for decryption. The same screen also allows victims who have already obtained a password to enter it and boot their system.
Kaspersky researchers discovered that the password needed to boot the system is not wiped from memory after it’s generated, giving users the opportunity to extract it before the process that creates the password, dispci.exe, is terminated. Entering this password boots the system and decrypts the disk, the security firm told SecurityWeek, but there is only a “slim chance” that victims will actually be able to extract the password.
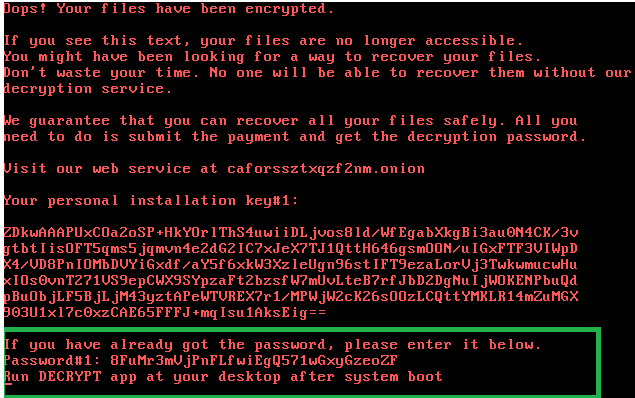
As for recovering files, experts noticed that Bad Rabbit does not delete shadow copies, which are backups made by Windows. If users enabled this backup functionality before the files were encrypted and the malware’s full disk encryption functionality failed for some reason or the disk is decrypted using the aforementioned method, the data can be restored via Windows or third-party utilities.
Kaspersky has also confirmed that Bad Rabbit does in fact use an NSA-linked exploit to spread; earlier reports claimed no exploits had been observed. The malware uses EternalRomance, which NotPetya also leveraged.
Based on the numerous similarities, the Bad Rabbit attack is believed to have been carried out by the same threat group that launched the NotPetya campaign, namely the Russia-linked threat actor known as BlackEnergy, TeleBots and Sandworm Team. Some are not convinced due to the fact that a majority of the victims were in Russia. Others pointed out, however, that the main target may have been Ukraine, where several major organizations were hit.
Vulnerabilities Found in Ship Communication System
28.10.2017 securityweek Vulnerebility
IOActive has long been interested in the security of satellite communications. In 2014, it published a report on “multiple high risk vulnerabilities” in all the satellite systems it studied.
More recently, it was prompted to examine the security of ship-based satellite communications following the release of a Shodan tool that tracks the location of VSAT systems (typically employed by vessels to provide Internet connectivity at sea). In particular, it examined an Inmarsat product, AmosConnect 8 (AC8), used by ships at sea to optimize and compress data in transit to reduce satellite costs.
“We have identified two critical vulnerabilities in this software,” blogged IOActive principal security consultant Mario Ballano on Thursday, “that allow pre-authenticated attackers to fully compromise an AmosConnect server. We have reported these vulnerabilities but there is no fix for them, as Inmarsat has discontinued AmosConnect 8.”
The two vulnerabilities are a blind SQL injection in the login form; and a privileged backdoor account. The former, writes Ballano, allows “unauthenticated attackers to gain access to credentials stored in its internal database. The server stores usernames and passwords in plaintext, making this vulnerability trivial to exploit.”
For the latter, he writes: “The AmosConnect server features a built-in backdoor account with full system privileges. Among other things, this vulnerability allows attackers to execute commands with SYSTEM privileges on the remote system by abusing AmosConnect Task Manager.”
These vulnerabilities can only be exploited by an attacker with access to the vessel's IT systems network. In theory, this could be separated from its operational network (ICS), its navigation network, its 'guest' BYOD network, and its 'SATCOM' network hosting the satellite communications equipment. Or there might be no segmentation -- there is unlikely to be complete segmentation.
“All in all,” writes Ballano, “these vulnerabilities pose a serious security risk. Attackers might be able to obtain corporate data, take over the server to mount further attacks, or pivot within the vessel networks.”
CERT agrees. Its Vulnerability Note VU#586501 comments, “Attackers having network access to an AmosConnect server can log into it using a backdoor account that has full system privileges. Among other things, this vulnerability allows attackers to execute commands with SYSTEM privileges on the remote system by abusing AmosConnect Task Manager.”
The NIST National Vulnerability Database classifies the vulnerability (CVE-2017-3222) as critical, with a severity score of 9.8.
Ballano adds, “some of the vulnerabilities uncovered during our SATCOM research might enable attackers to access these systems via the satellite link.”
However, CERT also adds, “As of July 2017, support for the Inmarsat AmosConnect8 service has been decommissioned and clients will no longer be able to download the software from the software distribution website.”
This has been confirmed in an Inmarsat statement emailed to SecurityWeek:
“Inmarsat had begun a process to retire AmosConnect 8 from our portfolio prior to IOActive's report and, in 2016, we communicated to our customers that the service would be terminated in July 2017.
“When IOActive brought the potential vulnerability to our attention, early in 2017, and despite the product reaching end of life, Inmarsat issued a security patch that was applied to AC8 to greatly reduce the risk potentially posed. We also removed the ability for users to download and activate AC8 from our public website.
“Inmarsat's central server no longer accepts connections from AmosConnect 8 email clients, so customers cannot use this software even if they wished too.”
The problem with this statement is that it differs from the disclosure timeline provided to SecurityWeek by Ballano. IOActive discovered the vulnerabilities in September 2016, and sent a vulnerability report to Inmarsat in October 2016. Inmarsat says it was told “early in 2017”. In reality, in November 2016, Inmarsat acknowledged the vulnerabilities, claimed they were only exploitable locally, and said they would be fixed.
At the end of January, Inmarsat told IOActive that a fix would be available on March 1, 2017; and later pushed this back to March 31. At the end of April, with no fix, IOActive warned that it would imminently disclose the vulnerabilities, and gave a week's notice on disclosure. IOActive received no further communication from Inmarsat, but did not publicly disclose the vulnerabilities until this week. Noticeably, Inmarsat never told IOActive that a fix had been produced.
Meanwhile, Inmarsat, has retired the product and advises customers to 'revert' to the earlier AC7. It says there is no problem because “customers cannot use this software [AC8] even if they wished too.”
But there may still be a problem. Ballano told SecurityWeek, “Bear in mind that [AC8] might be still vulnerable and open to attacks even if the Inmarsat infrastructure no longer accepts these clients. Customers would need to uninstall it and move to an alternative solution.”
Since writing this report, Inmarsat has provided a copy of the communication it sent to customers. Dated May 4, 2016 it confirms the intention to retire AC8 on June 30, 2017. The long term intention is to migrate customers to its newer high speed broadband Fleet Xpress product, while continuing to support AC7 during the transition.
However, this doesn't explain the poor communication between Inmarsat and IOActive. The bottom line is that Inmarsat AC8 customers were potentially using a product that Inmarsat knew to have vulnerabilities between October 2016 and July 2017. It is still important that all customers that have used AC8 should physically remove the software from their systems. It remains vulnerable even if not used.
Documents encrypted by Bad Rabbit ransomware could be recovered without paying ransom
28.10.2017 securityaffairs Ransomware
Files Encrypted by Bad Rabbit Recoverable Without Paying Ransom.
Some victims of the recent Bad Rabbit attack may be able to recover their files encrypted by the ransomware without paying the ransom.
The discovery was made by researchers at Kaspersky Lab that analyzed the encryption functionality implemented by the ransomware.
Once the ransomware infects a computer, it encrypts certain file types, it also encrypts the disk and a ransom note is displayed when the computer boots.
The Bad Rabbit leverages the open source library DiskCryptor in order to encrypt the user files.
According to the preliminary analysis published by experts at the CSE Cybsec Zlab, the malware authors likely reused some pieces of NotPetya code increasing the complexity of the code itself and fixing coding errors that transform NotPetya from a ransomware to a wiper.
Now researchers from Kaspersky Lab discovered that files encrypted by Bad Rabbit can be recovered with following specific procedures.
When infected computer boots up, the victims are informed that their files have been encrypted by Bad Rabbit, and the malicious code provides instruction to complete the payment to obtain the decryption key.
Kaspersky noticed that Bad Rabbit uses the same screen to allows victims who have received the decryption key to enter it and boot their system.
Malware researchers discovered that after the ransomware the decryption key, this isn’t wiped from memory. Unfortunately, there is only a “slim chance” that victims will be able to extract the password.
The experts also discovered that Bad Rabbit does not delete shadow copies, allowing victims to restore the files through this windows backup functionality.
“We have discovered that Bad Rabbit does not delete shadow copies after encrypting the victim’s files. It means that if the shadow copies had been enabled prior to infection and if the full disk encryption did not occur for some reason, then the victim can restore the original versions of the encrypted files by the means of the standard Windows mechanism or 3rd-party utilities.” reads the analysis published by Kaspersky.

According to malware researchers, NotPetya has been linked to BlackEnergy APT, for this reason, some experts suggest the same threat actor could be behind the Bad Rabbit ransomware.
UK Government links the WannaCry attack that crippled NHS to North Korea
28.10.2017 securityaffairs Ransomware
UK Government blamed North Korea for the WannaCry attack that affected a third of English hospitals.
“This attack, we believe quite strongly that it came from a foreign state,” Ben Wallace, a junior minister for security, told BBC Radio 4’s Today programme.
“North Korea was the state that we believe was involved in this worldwide attack,” he said, adding that the government was “as sure as possible”.
The massive WannaCry attack infected more than 300,000 computers in 150 countries, including in Britain’s National Health Service (NHS), the US logistics company FedEx and a factory of the car vendor Honda.
WannaCry is a ransomware which encrypts all files stored in your system and demands a $300 ransomware in worth bitcoins if you want to decrypt and recover these files.
According to the Britain’s National Audit Office, computers at 81 hospital groups across England out of the total number of 236 were infected.
The WannaCry attack caused severe problems to the NHS England, it forced the cancellation of some 19,500 medical appointments and affected roughly 600 general practitioners.

The National Audit Office confirmed that most of the affected facilities were running Windows 7 OS that had not been updated.
“It was a relatively unsophisticated attack and could have been prevented by the NHS following basic IT security best practice,” NAO chief Amyas Morse said.
“There are more sophisticated cyber threats out there than WannaCry so the Department (of Health) and the NHS need to get their act together to ensure the NHS is better protected against future attacks,”.
Unfortunately, the numerous recommendations in the NHS about cybersecurity, in particular about the security updates, were ignored.
It was a terrible lesson for the NHS, according to Dan Taylor, NHS Digital’s head of security, the organization had “learned a lot” from WannaCry attack.
Taylor defined the WannaCry attack as “an international attack on an unprecedented scale”.
The good news is that according to the NAO report affected British organizations did not pay any ransom. The UK Government is still assessing the current impact of the WannaCry attack, it still “does not know how much the disruption to services cost.”
Shortly after the WannaCry attack many security experts and firms linked the ransomware to the North Korean APT Lazarus group.
A new Ursnif Banking Trojan campaign targets Japan
28.10.2017 securityaffairs Virus
Crooks continues to target Japanese users, now the hackers leverage the Ursnif banking Trojan, aka Gozi, to hit the country.
According to researchers at IBM X-Force group, cyber criminals are delivering the infamous malware via spam campaigns that began last month. The Ursnif banking Trojan was the most active malware code in the financial sector in 2016 and the trend continued through 2017 to date.
In previous campaigns, the Ursnif banking Trojan targeted users in Japan, North America, Europe and Australia, currently, hackers have improved their evasion technique to target users in Japan.
“Ursnif’s activity is marked by both frequent code modifications and campaign activity in North America, Europe and Australia.” reads the X-Force report. “But one of its most popular targets in 2017 has been Japanese banks, where Ursnif’s operators were very active in late Q3 2017, starting in September. The threat actors continue to spam users in the region regularly as we move into Q4.”
The variants of the malware that targeted Japan also hot user credentials for local webmail, cloud storage, cryptocurrency exchange platforms and e-commerce sites.
The Ursnif banking Trojan was first spotted by experts in 2007, in 2019 its source code was accidentally leaked that lead to a continuous evolution of the threat that was improved over the years with new web-injection techniques and other features.
Back to the present, the latest version of Ursnif, so-called v2, is capable of many malicious activities including:
Script-based browser manipulation;
Webinjections and man-in-the-browser (MitB) functionality;
Form grabbing;
Screen capture and session video grabbing; and
Hidden VNC and SOCKS proxy attacks.
The malware targets banks in Bulgaria, Poland, Spain and the Czech Republic, North America, Australia and Japan with malspam.
“The delivery method of Ursnif payloads in Japan has been rather consistent throughout the campaigns observed this summer, featuring fake attachments purporting to come from financial services and payment card providers in Japan.” continues the analysis.

The experts also observed a malspam variant delivers an HTML link that points to a .zip file containing a JavaScript. The script launches another PowerShell script that fetches the Ursnif payload from a remote server.
“Recent Ursnif malspam campaigns used a macro evasion technique that launches PowerShell only after the user closes the malicious file. This method helps the malware evade sandbox detection.” continues the experts.
The above technique was implemented to allow the malware evading the sandbox.
Vxers behind the Ursnif have also leveraged the Tor network to hide command-and-control communications.
The situation in Japan has worsened since 2015 when the Shifu Trojan targets banks in the country before spreading across Europe.
Shifu’s activity in Japan faded in 2017, “but it was one of the pivotal organized cybercrime groups that opened the floodgates to other cybercrime actors such as URLZone, Rovnix and a step-up in Ursnif attacks.”
UK Blames North Korea for Cyberattack That Crippled Hospitals
27.10.2017 securityweek Cyber
Britain on Friday blamed North Korea for a ransomware attack this year that a new report revealed affected a third of English hospitals and could have been prevented with "basic" IT security.
"This attack, we believe quite strongly that it came from a foreign state," Ben Wallace, a junior minister for security, told BBC Radio 4's Today programme.
"North Korea was the state that we believe was involved in this worldwide attack," he said, adding that the government was "as sure as possible".
The WannaCry attack in May infected some 300,000 computers in 150 countries, including in Britain's National Health Service (NHS), Spanish telecoms company Telefonica and US logistics company FedEx.
Britain's National Audit Office revealed the attack had hit NHS England particularly hard, forcing the cancellation of some 19,500 medical appointments.
Computers at 81 hospital groups across England were affected -- a third of the total number of 236.
Some 600 general practitioners were also affected.
The facilities affected were running computer systems -- the majority Windows 7 -- that had not been updated to secure them against attacks, the NAO said.
"It was a relatively unsophisticated attack and could have been prevented by the NHS following basic IT security best practice," NAO chief Amyas Morse said.
"There are more sophisticated cyber threats out there than WannaCry so the Department (of Health) and the NHS need to get their act together to ensure the NHS is better protected against future attacks," he said.
The report revealed that there had been multiple warnings ahead of the attack about the weakness of IT security in the NHS but that recommendations for security updates were not respected.
Dan Taylor, NHS Digital's head of security said the NHS had "learned a lot" from WannaCry, calling it "an international attack on an unprecedented scale".
Ransomware attacks use a type of malware that encrypts files on an infected computer and demands money to unlock them.
The NAO said no ransom was paid by the NHS but the government "does not know how much the disruption to services cost."
Industrial Products Also Vulnerable to KRACK Wi-Fi Attack
27.10.2017 securityweek Attack
Some industrial networking devices are also vulnerable to the recently disclosed KRACK Wi-Fi attack, including products from Cisco, Rockwell Automation and Sierra Wireless.
KRACK, or Key Reinstallation Attack, is the name assigned to a series of vulnerabilities in the WPA2 protocol, which secures modern Wi-Fi networks. The flaws can allow an attacker within range of the targeted device to read information that the user believes is encrypted and, in some cases, possibly even inject and manipulate data (e.g. inject malware into a website).
The vulnerabilities are tracked as CVE-2017-13077, CVE-2017-13078, CVE-2017-13079, CVE-2017-13080, CVE-2017-13081, CVE-2017-13082, CVE-2017-13084, CVE-2017-13086, CVE-2017-13087 and CVE-2017-13088. The security holes have been confirmed to affect products from tens of vendors, but many of them have already started releasing patches.KRACK
Since a majority of WPA2 implementations are affected, it’s not surprising that some industrial communications products are also exposed to KRACK attacks.
Cisco pointed out that of the ten KRACK flaws, only CVE-2017-13082 affects access points and other wireless infrastructure components, while the rest impact client devices.
In the case of Cisco, many of the company’s products are affected, including Cisco 829 Industrial Integrated Services routers and Industrial Wireless 3700 series access points. The networking giant has yet to release patches for the vulnerable industrial products. However, workarounds are available for six of the flaws.
According to an advisory from ICS-CERT, Rockwell Automation is working on releasing a firmware update for its Stratix 5100 Wireless Access Point/Workgroup Bridge. These industrial devices are used worldwide in the critical manufacturing, energy, and water sectors.
Devices running version 15.3(3)JC1 and earlier are impacted by CVE-2017-13082. Until patches become available, Rockwell has advised customers to take steps to prevent potential attacks, including limiting access to control system, and ensuring that software is patched, security products are deployed and untrusted websites are not accessed.
Sierra Wireless has also released an advisory to inform customers that a dozen of its products, including access points and client devices, are affected by the vulnerabilities. The company has promised to release patches over the coming months.
The list of affected Sierra Wireless devices includes industrial products such as the FX30 rugged gateway and the AirLink MP70 router.
Siemens has yet to publish an advisory regarding the impact of KRACK on its products, but the company did say that its experts are investigating the flaws.
Analyzing an exploit for СVE-2017-11826
27.10.2017 Kaspersky Vulnerebility
The latest Patch Tuesday (17 October) brought patches for 62 vulnerabilities, including one that fixed СVE-2017-11826 – a critical zero-day vulnerability used to launch targeted attacks – in all versions of Microsoft Office.
The exploit for this vulnerability is an RTF document containing a DOCX document that exploits СVE-2017-11826 in the Office Open XML parser.
The exploit itself is in word/document.xml as follows:
Under the ECMA-376 standard for Office Open XML File Formats, the valid ‘font’ element describing the fonts used in the document must look like this:
In the body of the exploit the closing tag </w:font> is absent. The opening tag <w:font> is followed by the object element <o:idmap/> which cause ‘type confusion’ in the OOXML parser. Any object element can be used to successfully exploit this vulnerability. To pass one of the checks preceding the exploitation, there must be an OLEObject element in front of the <w:font> tag, and the length of the content of the attribute name must be no shorter than 32 bytes after conversion from UTF-8 into Unicode.
After conversion from UTF-8 to Unicode, E8 A3 AC E0 A2 80 becomes EC 88 88 08.
If all these conditions are fulfilled, this pointer will be dereferenced, and control will be transferred to the contents of this address with the offset 4.
To control the memory content at address 0x088888EC, the attackers apply the popular heap spraying technique with use of ActiveX components:
The exploit bypasses ASLR and DEP using ROP and gadgets from msvbvm60.dll. The msvbvm60.dll module is loaded from the RTF document with the help of a CLSID associated with this DLL:
The first part of ROP sets the ESP register’s value:
The second part of ROP is ignored: it was used to set the EIP register at 0x088883EC. The last ‘pop eax; retn’ gadget moves the address 0x729410D0 into EAX. This is the address for the VirtualProtect pointer in the Imports area of msvbvm60.dll from Kernel32.dll:
The VirtualProtect pointer is used in the next ROP gadget to call the function VirtualProtect(0x8888C90, 0x201, 0x40, 0x72A4C045). After this, control is transferred to the shellcode at the address 0x8888F70, which decrypts and executes the embedded DLL:
Kaspersky Lab’s security solutions detect exploits for СVE-2017-11826 as:
MSWord.Agent.ix;
MSOffice.CVE-2017-11826.a;
HEUR:Exploit.MSOffice.Generic.
IOC
cb3429e608144909ef25df2605c24ec253b10b6e99cbb6657afa6b92e9f32fb5
Bad Rabbit Ransomware Uses Leaked 'EternalRomance' NSA Exploit to Spread
27.10.2017 thehackernews Ransomware
A new widespread ransomware worm, known as "Bad Rabbit," that hit over 200 major organisations, primarily in Russia and Ukraine this week leverages a stolen NSA exploit released by the Shadow Brokers this April to spread across victims' networks.
Earlier it was reported that this week's crypto-ransomware outbreak did not use any National Security Agency-developed exploits, neither EternalRomance nor EternalBlue, but a recent report from Cisco's Talos Security Intelligence revealed that the Bad Rabbit ransomware did use EternalRomance exploit.
NotPetya ransomware (also known as ExPetr and Nyetya) that infected tens of thousands of systems back in June also leveraged the EternalRomance exploit, along with another NSA's leaked Windows hacking exploit EternalBlue, which was used in the WannaCry ransomware outbreak.
Bad Rabbit Uses EternalRomance SMB RCE Exploit
Bad Rabbit does not use EternalBlue but does leverage EternalRomance RCE exploit to spread across victims' networks.
Microsoft and F-Secure have also confirmed the presence of the exploit in the Bad Rabbit ransomware.
EternalRomance is one of many hacking tools allegedly belonged to the NSA's elite hacking team called Equation Group that were leaked by the infamous hacking group calling itself Shadow Brokers in April this year.
EternalRomance is a remote code execution exploit that takes advantage of a flaw (CVE-2017-0145) in Microsoft's Windows Server Message Block (SMB), a protocol for transferring data between connected Windows computers, to bypass security over file-sharing connections, thereby enabling remote code execution on Windows clients and servers.
Along with EternalChampion, EternalBlue, EternalSynergy and other NSA exploits released by the Shadow Brokers, the EternalRomance vulnerability was also patched by Microsoft this March with the release of a security bulletin (MS17-010).
Bad Rabbit was reportedly distributed via drive-by download attacks via compromised Russian media sites, using fake Adobe Flash players installer to lure victims' into install malware unwittingly and demanding 0.05 bitcoin (~ $285) from victims to unlock their systems.
How Bad Rabbit Ransomware Spreads In a Network
According to the researchers, Bad Rabbit first scans the internal network for open SMB shares, tries a hardcoded list of commonly used credentials to drop malware, and also uses Mimikatz post-exploitation tool to extract credentials from the affected systems.
Bad Rabbit can also exploit the Windows Management Instrumentation Command-line (WMIC) scripting interface in an attempt to execute code on other Windows systems on the network remotely, noted EndGame.
However, according to Cisco's Talos, Bad Rabbit also carries a code that uses EternalRomance, which allows remote hackers to propagate from an infected computer to other targets more efficiently.
"We can be fairly confident that BadRabbit includes an EternalRomance implementation used to overwrite a kernel’s session security context to enable it to launch remote services, while in Nyetya it was used to install the DoublePulsar backdoor," Talos researchers wrote.
"Both actions are possible due to the fact that EternalRomance allows the attacker to read/write arbitrary data into the kernel memory space."
Is Same Hacking Group Behind Bad Rabbit and NotPetya?
Since both Bad Rabbit and NotPetya uses the commercial DiskCryptor code to encrypt the victim's hard drive and "wiper" code that could erase hard drives attached to the infected system, the researchers believe it is "highly likely" the attackers behind both the ransomware outbreaks are same.
"It is highly likely that the same group of hackers was behind BadRabbit ransomware attack on October the 25th, 2017 and the epidemic of the NotPetya virus, which attacked the energy, telecommunications and financial sectors in Ukraine in June 2017," Russian security firm Group IB noted.
"Research revealed that the BadRabbit code was compiled from NotPetya sources. BadRabbit has same functions for computing hashes, network distribution logic and logs removal process, etc."
NotPetya has previously been linked to the Russian hacking group known as BlackEnergy and Sandworm Team, but since Bad Rabbit is primarily targeting Russia as well, not everyone seems convinced with the above assumptions.
How to Protect Yourself from Ransomware Attacks?
In order to protect yourself from Bad Rabbit, users are advised to disable WMI service to prevent the malware from spreading over your network.
Also, make sure to update your systems regularly and keep a good and effective anti-virus security suite on your system.
Since most ransomware spread through phishing emails, malicious adverts on websites, and third-party apps and programs, you should always exercise caution before falling for any of these.
Most importantly, to always have a tight grip on your valuable data, keep a good backup routine in place that makes and saves copies of your files to an external storage device that isn't always connected to your PC.
jQuery Official Blog Hacked — Stay Calm, Library is Safe!
27.10.2017 thehackernews Hacking
The official blog of jQuery—most popular JavaScript library used by millions of websites—has been hacked by some unknown hackers, using the pseudonym "str0ng" and "n3tr1x."
jQuery's blog website (blog.jquery.com) runs on WordPress—the world's most popular content management system (CMS) used by millions of websites.
While there is no evidence yet if the server (code.jquery.com) that host jQuery file was also compromised, The Hacker News took a screenshot (as shown above) and can confirm that the hackers merely published a simple blog post to deface the website.
The defaced blog post URL — http://blog.jquery.com/2017/10/26/hacked/ (now removed).
Since the above-mentioned blog post was published under the name of Leah Silber, a core member of jQuery team, it seems hackers were able to make their post live by compromising Silber's account—probably by reusing her password leaked in a previous data breach.
If not, the hackers might have gained unauthorized access to the website either by exploiting a (known or zero-day) vulnerability in Wordpress script or the server.
jQuery team has immediately removed the post created by the hackers as soon as they realized there was a compromise, but so far the organisation has not released any official statement about the incident.
This is not the first time when jQuery's website has been compromised. In 2014, the main domain (jQuery.com) was reportedly compromised, redirecting the site's visitors to a page hosting an exploit kit.
Since millions of websites directly use jQuery script hosted by jQuery server, today's attack could be worse if the hackers would have been able to compromised code.jquery.com in an attempt to replace the official jQuery file with the malicious one, putting billions of visitors of millions of websites at risk of malware attacks.
A similar incident took place yesterday, when a hacker managed to replace official JavaScript file hosted by Coinhive—a popular browser-based cryptocurrency miner—with a modified version that eventually tricked CPUs of millions of visitors of thousands of websites to mine cryptocurrencies for the hacker unknowingly.
Interestingly, Coinhive was also hacked via password reuse attack, allowing the attacker to gain its CloudFlare account and change DNS settings unauthorizedly.
We'll update you with more information on the incident. Stay tuned!
Hackers Could Turn LG Smart Appliances Into Remote-Controlled Spy Robot
27.10.2017 thehackernews Hacking
If your smart devices are smart enough to make your life easier, then their smart behaviour could also be exploited by hackers to invade your privacy or spy on you, if not secured properly.
Recent research conducted by security researchers at threat prevention firm Check Point highlights privacy concern surrounding smart home devices manufactured by LG.
Check Point researchers discovered a security vulnerability in LG SmartThinQ smart home devices that allowed them to hijack internet-connected devices like refrigerators, ovens, dishwashers, air conditioners, dryers, and washing machines manufactured by LG.
...and what's worse?
Hackers could even remotely take control of LG's Hom-Bot, a camera-equipped robotic vacuum cleaner, and access the live video feed to spy on anything in the device's vicinity.
This hack doesn't even require hacker and targeted device to be on the same network.
Dubbed HomeHack, the vulnerability resides in the mobile app and cloud application used to control LG's SmartThinkQ home appliances, allowing an attacker to remotely gain control of any connected appliance controlled by the app.
This vulnerability could allow hackers to remotely log into the SmartThinQ cloud application and take over the victim's LG account, according to the researchers.
Watch the Video Demonstration of the HomeHack Attack:
The researchers demonstrated the risks posed by this vulnerability by taking control of an LG Hom-Bot, which comes equipped with a security camera and motion detection sensors and reportedly owned by over one million users.
You can watch the video posted by the Check Point researchers, which shows how easy it is to hijack the appliance and use it to spy on users and their homes.
The issue is in the way SmartThinQ app processes logins, and exploiting the issue only requires a hacker with a moderate skill to know the email address of the target, and nothing else.
Since hackers can merely bypass a victim's login using the HomeHack flaw, there is no need for them to be on the same network as the victim, and primary IoT security tips such as avoid using default credentials, and always use a secure password also fails here.
Also, such devices which are supposed to give users remote access from an app cannot be put behind a firewall to keep them away from the exposure on the Internet.
In order to perform this hack, the hacker needs a rooted device and requires to intercept the app traffic with the LG server.
However, the LG app has a built-in anti-root mechanism, which immediately closes if detects the smartphone is rooted, and SSL pinning mechanism, which restricts intercepting traffic.
So, to bypass both security features, Check Point researchers said hackers could first decompile the source of the app, remove the functions that enable SSL pinning and anti-root from the app's code, recompile the app and install it on their rooted device.
Now, hackers can run this tempered app on their rooted smartphone and can set up a proxy which could allow them to intercept the application traffic.
Here's How the HomeHack Attack Works:
Researchers analyzed the login process of the SmartThinQ app and found that it contains the following requests:
Authentication request – the user would enter his/her login credentials, which would be validated by the company's backend server.
Signature request – creates a signature based on the above-provided username (i.e. the email address), and this signature has nothing do with the password.
Token request – an access token for the user account is generated using the signature response as a header and username as a parameter.
Login request – sends the above-generated access token in order to allow the user to login to the account.
However, researchers found that there's no dependency between the first step and the subsequent two mentioned above.
So, an attacker could first use his/her username to pass step one, and then intercept the traffic in order to change the username to the victim's username for steps two and three, which would effectively grant the attacker access to the victim's account.
Once in control of the target account, the attacker can control any LG device or appliance associated with that account, including refrigerators, ovens, dishwashers, washing machines and dryers, air conditioners, and robot vacuum cleaners.
Hackers can then change the settings on the hacked devices, or can simply switch on or off.
This Is What You Can Do Now:
Researchers disclosed the vulnerability to LG on July 31 and the device manufacturer issued an update to patch the issue in September.
So, if you own any LG SmartThinQ appliance, you are strongly advised to update to the LG SmartThinQ mobile app to the latest version (1.9.23) through Google Play Store, Apple App Store or the LG SmartThinQ settings.
Digging the Middle East and North African cybercrime underground market
27.10.2017 securityaffairs CyberCrime
Security experts from Trend Micro have published an interesting report on the Middle East and North African cybercrime underground market, enjoy it!
We explained several times that criminal communities adopt different tactics, techniques, and procedures (TTPs) depending on the location they operate. Experts at Trend Micro have highlighted the differences between the different underground communities, they detailed the Russian underground, the North American one, the Chinese one, the Japanese one and the Brazilian one,
The last report published by Trend Micro is full of interesting information about the Middle East and North African cybercrime underground marketplaces.
The marketplaces in this specific area are full of offers for malware tools and services, but experts warn that shopping these markets can be tricky for outsiders.
In many cases, registrations require a joining fee and the Arabic represents a high entry barrier.
“Our look into these digital souks also revealed how the Middle Eastern and North African underground is not a glass tank like North America’s, but more cautious like the Frenchunderground.” states the report. “Potential customers are barred from window-shopping, for instance, and viewing links or full forum posts requires an account. Registration is a lengthy process that involves paying for one’s membership in bitcoins and getting through the language barrier. English-based forums and sites do exist, but there are certain regional variances.”
Of course in these marketplaces, many actors offer for free also a wide range of hacking tools, malware components, and free instruction manuals. The underground markets in this region are characterized by the confluence of ideology and cybercrime, according to the researchers, there are not profit-driven like other black marketplaces.
Members readily handing out malware tools for free, they tend to cooperate with each other in planning and launching powerful cyber attacks such as DDoS attacks and malicious operations such as spam campaigns.
“Their underground marketplaces aren’t profit-driven like Russia’s, or China’s. There’s an ironic confluence of ideology and cybercrime in this region, where the “spirit of sharing” and sense of brotherhood are the apparent forces behind the distribution of crimeware. ” reads the report.
“A common practice among its players is to readily hand out codes, malware, and instruction manuals for free. Crypters, typically used to obfuscate malware, as well as SQL injection tools, keyloggers, and basic malware builders, are given away—a reflection of the culture within the regions’ underground scene.”
“The most interesting driver here is the deep permeation of religious influence – from what is sold to how users and sellers interact,” explained Ed Cabrera, chief cybersecurity officer for Trend Micro.
Even if the Middle East and North African cybercrime underground are young it is rapidly increasing, making this ecosystem very dangerous due to future attacks powered by its actors.
The researchers also highlighted another worrisome aspect of the ecosystem, its players are in continuous contact with the threat actors in the Russian underground, in many cases, malware coders and hackers are hired by Russians from the Middle East and North Africa.
The research was conducted in the period between July 2016 and December 2016, the researchers focused their investigation on the kind of merchandise available for sale in these black markets and their price lists.
The vast majority of products and services available in these marketplaces is the same that is available elsewhere, such as malware, hacking services, credit card and credential dumps, and stolen identity information.
“The marketplaces are also rife with do-it-yourself kits that provide the resources that even beginners can use to launch their own cyber criminal business. Developers typically sell their malware either as a single binary, or a bundle of binary and builder; and in some cases, access to a command-and-control (C&C) infrastructure.” continues the report.
Another element that characterized these black market is the low presence of weapons or drugs, visitors looking to buy these items were directed to forums in the North American underground instead.
Giving a look at the price list of the underground offering, markets in this area tended to be more expensive than in other regions.
Keylogger goes for $19 in Middle Eastern and North African forums, much more expensive than elsewhere, in the North American underground, it is possible to buy them for between $1 and $4.

The same is for credit card data, as usual, the final price depends on the country origin.

The stolen credentials and online accounts are also much more expensive, these commodities are very attractive for hackers that use them to access e-commerce
accounts and hijack government-owned systems and servers with weak authentication.
The following table shows that the highest price is for PayPal accounts belonging to Israeli users, they go for $50.

Port numbers for Internet-connected SCADA system were available for free in the criminal underworld in this region, while a WannaCry sample was available for just $50.
Let me stop here and suggest you read this excellent report.
Bad Rabbit Ransomware leverages the NSA Exploit for lateral movements
27.10.2017 securityaffairs Ransomware
Malware researchers at Cisco Talos team discovered the Bad Rabbit Ransomware leverages EternalRomance to propagate in the network.
New precious details emerge from the analysis of malware researchers at Cisco Talos and F-Secure who respectively discovered and confirmed the presence an NSA exploit in the Bad Rabbit ransomware.
On October 24, hundreds of organizations worldwide were hit by the Bad Rabbit ransomware, mostly in Russia and Ukraine.
The first reports on the ransomware revealed that the malicious code also relies on the Server Message Block (SMB) protocol to spread within the targeted network. Many experts excluded the use of the SMB exploits EternalBlue and EternalRomance for the lateral movements.
Previous reports confirmed that the Bad Rabbit ransomware does not use NSA-linked EternalBlue exploit, but researchers at Cisco Talos discovered the malicious code leverages EternalRomance to propagate in the network.
“Despite initial reports, we currently have no evidence that the EternalBlue exploit is being leveraged. However, we identified the usage of the EternalRomance exploit to propagate in the network. This exploit takes advantage of a vulnerability described in the Microsoft MS17-010 security bulletin. The vulnerability was also exploited during the Nyetya campaign.” reads the analysis published by the Talos team.

The EternalRomance vulnerability was patched by Microsoft in March 2017 with the release of the MS17-010 security bulletin that also fixed the EternalChampion, EternalBlue and EternalSynergy exploits.
Both exploits were disclosed by the Shadow Brokers hacker group earlier this year when the crew leaked a portion of the arsenal of the NSA-Linked Equation Group, a database containing hacking tools and exploits.
Almost every analysis produced since the discovery of the Bad Rabbit ransomware revealed many similarities between Bad Rabbit and NotPetya, including the targeting of Ukraine and Russia, the usage of Mimikatz tool, and the same type of file encryption.
However, while NotPetya is a wiper disguised by a ransomware, Bad Rabbit appears to be a real ransomware.
Another interesting aspect emerged by further analysis is related to the alleged planning of the attack that seems to be dated back months ago. Some of the compromised domains used in the Bad Rabbit ransomware attack had been set up since at least July 2017 and some of the injection servers were first seen more than a year ago.
According to malware researchers, NotPetya has been linked to BlackEnergy APT, for this reason, some experts suggest the same threat actor could be behind the Bad Rabbit ransomware.
Profiling Tool Suggests 'Bad Rabbit' Not Financially Motivated
27.10.2017 securityweek Ransomware
Researchers at FireEye noticed that some of the websites redirecting users to the Bad Rabbit ransomware hosted a profiling framework, which could suggest that the attack was not financially motivated.
The Bad Rabbit attack, which led to the infection of hundreds of machines in Russia and Ukraine with ransomware, started with users being redirected to 1dnscontrol[.]com, a domain that served a malware dropper disguised as a Flash Player installer. Users had to manually execute the file in order to become infected.
FireEye noticed that several compromised websites redirecting to the 1dnscontrol domain had hosted a profiling tool. Tracked by the company as BACKSWING, the framework has been seen on more than 50 websites since September 2016, and four of them redirected users to Bad Rabbit ransomware this week.
BACKSWING is designed to collect information about a user’s browsing session - including User-Agent, HTTP Referrer, cookies, and the current domain - and sends it back to a command and control (C&C) server.
FireEye has seen two versions of the tool, the second version replacing the first one on several websites starting with October 5. BACKSWING v2 was mostly injected into legitimate JavaScript resources hosted by affected sites.
“Malicious profilers allow attackers to obtain more information about potential victims before deploying payloads (in this case, the BADRABBIT ‘flash update’ dropper),” FireEye researchers explained. “While FireEye has not directly observed BACKSWING delivering BADRABBIT, BACKSWING was observed on multiple websites that were seen referring FireEye customers to 1dnscontrol[.]com, which hosted the BADRABBIT dropper.”
If BACKSWING was in fact used by the threat group behind the Bad Rabbit ransomware, it would suggest that the attack was not financially motivated, as a profit-driven actor would not care about who they’re infecting as long as they make money.
This also reinforces the theory that the Bad Rabbit operation was conducted by the Russia-linked threat group known as BlackEnergy, TeleBots and Sandworm Team, which is also believed to be behind the NotPetya wiper attack that targeted Ukraine and other countries in June.
“We observed a spike of BACKSWING instances on Ukrainian sites, with a significant increase in May 2017. While some sites hosting BACKSWING do not have a clear strategic link, the pattern of deployment raises the possibility of a strategic sponsor with specific regional interests,” FireEye said.
While many similarities have been found between NotPetya and Bad Rabbit, one major difference is that the latter mainly hit enterprises and most of the victims are in Russia. However, the relatively small number of Ukrainian organizations affected by the malware include high profile targets, such as the airport in Odessa, the Kiev subway, the State Aviation Service of Ukraine, and the Transport Ministry of Ukraine.
Contrary to initial reports, the Bad Rabbit ransomware does in fact appear to leverage an NSA-linked exploit to spread within compromised networks. The exploit in question is called EternalRomance and its details were leaked by the hacker group Shadow Brokers back in April. The vulnerability leveraged by the exploit was patched by Microsoft in March. EternalRomance was also one of the exploits leveraged by the NotPetya wiper.
'Bad Rabbit' Ransomware Uses NSA Exploit to Spread
26.10.2017 securityweek Ransomware
Contrary to initial reports, the Bad Rabbit ransomware that hit Russia and Ukraine this week does in fact leverage an exploit linked to the U.S. National Security Agency (NSA).
Similar to the NotPetya wiper that infected tens of thousands of systems back in late June, Bad Rabbit also uses the Server Message Block (SMB) protocol to spread within the compromised network. However, researchers initially claimed that, unlike NotPetya, the ransomware did not use either of the SMB exploits tracked as EternalBlue and EternalRomance.
It turns out that while Bad Rabbit does not use EternalBlue, it does in fact leverage EternalRomance to propagate in the network. The presence of the exploit was first reported by Cisco Talos and later confirmed by F-Secure.
The EternalRomance vulnerability was addressed by Microsoft in March 2017 with the release of a security bulletin that also patched the EternalChampion, EternalBlue and EternalSynergy exploits.
Details of these flaws were made public by a hacker group calling itself Shadow Brokers earlier this year. The group claims to have obtained these and many other exploits from the NSA and that they were used by one of the agency’s teams known in the cybersecurity industry as the Equation Group.
When the exploits were made public by the Shadow Brokers in April, Microsoft pointed out that they had already been fixed, which has led some to believe that the tech giant learned about the vulnerabilities from the NSA itself.
The initial analysis showed many connections between Bad Rabbit and NotPetya, including targeting of Ukraine and Russia, binaries signed with expired certificates, use of Mimikatz for credential-grabbing, reboots and persistence via scheduled tasks, removal of event logs and USN change journals, and the same type of file encryption and ransomware functionality.
One of the most significant differences is the fact that Bad Rabbit appears to be an actual ransomware and, at least in theory, users can recover their encrypted files if they pay the ransom. NotPetya, on the other hand, has been classified as a wiper due to the fact that the ransom payment functionality is not implemented properly, making the recovery of files impossible.
Another major difference is the fact that Bad Rabbit mostly affected enterprises, particularly in Russia. However, it’s worth noting that many of the victims in Ukraine are high-profile organizations.
NotPetya has been linked to the Russian threat actor known as BlackEnergy, TeleBots and Sandworm Team, which suggests that the same group may be behind the Bad Rabbit attacks as well, although not everyone seems convinced.
An analysis of the Bad Rabbit infrastructure showed that some of the compromised domains used in the attack had been set up since at least July and some of the injection servers were first seen more than a year ago.
Skybox Raises $150 Million to Advance its Security Management Product
26.10.2017 securityweek Security
Security analytics firm Skybox announced Wednesday that it has secured $150 million growth equity comprising $100 million from CVC Capital Partners’ Growth Fund (CVC Growth), and $50 million from Pantheon. This more than doubles existing investment in the firm, which now stands at around $280 million. It received $96 million from Providence Strategic Growth (PSG) in February 2016.
Skybox was originally founded in 2002 in Jerusalem, Israel, by Gidi Cohen and Eran Reshef. It is now headquartered in San Jose, California, but with its development center in Herzliya Pituach in the Tel Aviv District of Israel.
Skybox offers cybersecurity management software that provides visibility into its customers' unique attack surface. It uses analytics to detect and prioritize risk exposure, and provides recommendations on how to address those exposures. Customers are large Global 5000 organizations and financial institutions, and government agencies; and include six of the top 10 global banks, 10 global telecommunications firms, five of the world’s largest consumer goods manufacturers and 10 of the largest energy providers globally.
The combination of increasingly sophisticated attackers from both cybercriminal gangs and state-sponsored attacks, combined with the more complex IT infrastructures evolving from accelerating digital transformation provides the backdrop for Skybox. In the first half of 2017, Skybox showed a 62 percent increase in sales and 59 percent increase in product transactions compared to the same period last year (January 1 - June 30).
“Enterprises, governments... everyone is either embarking on or going through massive digital transformation, and this means new challenges for security because the attack surface of these organizations is growing more complex,” said Cohen. “We’ve been consistently evolving our technology to meet those challenges. With this investment, we’ll accelerate that innovation, focusing on some of the most critical areas, such as security management for the cloud and the OT networks that control critical infrastructure.”
“Skybox’s track record is impressive and there is clear demand for their solutions,” said Jason Glass, senior managing director of CVC Growth Partners. “It is a true leader in cybersecurity management, helping organizations better protect themselves and become more efficient.”
Skybox announced, “This round of funding will enable an accelerated investment in sales and marketing, customer care and R&D. It will also be used for potential M&A activity, to capitalize on the approximately $10 billion market opportunity in cybersecurity management.”
However, in an interview with the Israeli business publication Globes, CEO Cohen also indicated that some of the money would be used to buy out existing investors. “As well as injecting new capital into the company, some of the existing investors in Skybox, including employees, have sold their holdings.” He added, “The buying of shares was a significant part of this financing round.”
The company said it has a compound annual growth rate (CAGR) of 46 percent, and positive cash flow between 2014 and 2016.
Moving Target Defense Startup Cryptonite Emerges From Stealth
26.10.2017 securityweek BigBrothers
Cryptonite, a Rockville, Maryland-based startup that aims to prevent reconnaissance and lateral movement in the network using moving target defense and micro-segmentation technologies, has emerged from stealth mode.
The company’s product, the CryptoniteNXT network appliance, implements what is known as a Zero Trust environment, which is achieved by minimizing access to resources and visibility within the network to the absolute minimal subset needed by users to carry out their job.
CryptoniteNXT, which sits between the perimeter firewall and the organization’s internal wired and wireless networking devices (i.e. switches and wireless access points), uses a concept known as moving target defense (MTD) to make systems “invisible.”CryptoniteNXT
The MTD technology, implemented by a CryptoniteNXT component named Net Guard, aims to prevent an attacker who already has access from mapping the network and finding vulnerable systems that they could exploit. This solution can also provide protection against insiders and malicious actors who are already on the network when the product is deployed as previous network maps become unusable.
“CryptoniteNXT Net Guard does this by transforming the endpoint’s view of the network into a dynamic, abstract structure, in effect making the once static network into a dynamic moving target,” Cryptonite said. “Net Guard MTD creates a mapping from the obfuscated network to the real network to enable the flow of traffic across the traditional network infrastructure.”
In order to restrict lateral movement within the network, CryptoniteNXT uses a component named Micro Shield Segmentation. This ensures that users only have visibility into the machines needed to do their job, preventing malicious insiders and attackers from moving freely across the network.
Cryptonite says the product and the Zero Trust environment it creates can be used to address a wide range of risks, including ones associated with the lack of updates and patches, insecure IoT devices, and mobile devices.
Initial research and development into Cryptonite’s MTD technology was funded by the U.S. Department of Homeland Security (DHS) and the Department of Defense (DoD).
Cryptonite, a spin-off of Maryland defense contractor Intelligent Automation (IAI), is led by President and CEO Michael Simon, and Justin Yackoski, CTO and former lead researcher at IAI.
Cryptonite is backed by several investors, including Tenable founder Ron Gula; David Walker, founder of Pangia Technologies; Al Nardslico, founder of SMS; Abtin Buergari, founder of Modus eDiscovery; Don Rogers, co-founder of Shulman Rogers; and Dr. Leonard Haynes, co-founder of IAI.
Microsoft Open Sources Website Scanning Tool 'Sonar'
26.10.2017 securityweek Security
Microsoft announced this week the availability of Sonar, an open source linting and website scanning tool designed to help developers identify and fix performance and security issues.
Developed by the Microsoft Edge team, Sonar has been made open source and donated to the JS Foundation. Microsoft will continue making improvements to the project, but external contributions are also welcome.
Linting is the process of analyzing code for potential errors. Sonar looks for a wide range of issues, including related to performance, accessibility, security, Progressive Web Apps (PWA), and interoperability.Sonar open source tool
In the case of security, Sonar looks for eight types of weaknesses, including SSL configuration problems using SSL Labs’ SSL Server Test.
Another test looks for HTTPS connections that don’t use the Strict-Transport-Security header, which ensures that a website can only be accessed via secure connections to prevent man-in-the-middle (MitM) attacks.
Developers can also verify if their applications or sites are vulnerable to attacks that rely on MIME sniffing, which allows browsers to detect file formats even if the media type is incorrect. While MIME sniffing has benefits, it also introduces some security risks, which can be mitigated if the website uses the X-Content-Type-Options: nosniff HTTP response header.
Sonar also checks if the set-cookie header defines the Secure and HttpOnly attributes, which prevent session hijacking via cross-site scripting (XSS) attacks by ensuring that cookies cannot be transmitted over HTTP and their value cannot be accessed via JavaScript.
Another useful feature for security is Sonar’s ability to determine if a website is running a vulnerable client-side JavaScript library or framework. It does this by using Snyk’s Vulnerability DB and js-library-detector.
Sonar is also designed to ensure that headers don’t leak potentially sensitive data, and prevent unauthorized redirects that could lead users to malicious websites.
Sonar can be used locally as a command line tool, but an online version is also available. The tool can be integrated with several other products, including aXe Core, AMP validator, snyk.io, SSL Labs, and Cloudinary.
Security Flaw Could Have Let Hackers Turn on Smart Ovens
26.10.2017 securityweek Vulnerebility
A security flaw in LG's smart home devices gave hackers a way to control the household appliances of millions of customers, including the ability to turn on ovens, a computer security firm revealed on Thursday.
Check Point Software Technologies said the vulnerability, called "HomeHack", in the LG SmartThinkQ mobile app and cloud application allowed their research team to take over a user's account and control connected appliances such as their oven, refrigerator, dishwasher, washing machine, air conditioner and more.
The HomeHack vulnerability also "gave attackers the potential to spy on users' home activities via the Hom-Bot robot vacuum cleaner video camera," Check Point said in a statement.
LG's internet-connected ovens can be remotely set to pre-heat, meaning malicious hackers could create a potential safety risk.
LG sold 80 million smart home devices across the world in 2016, all of which were potentially affected by the flaw.
But the South Korean electronics giant said it fixed the problem by updating its application in September after being alerted by Check Point.
LG recommends all users update their SmartThinkQ mobile phone app as well as each connected home device.
"As more and more smart devices are being used in the home, hackers will shift their focus from targeting individual devices, to hacking the apps that control networks of devices," Check Point head of product vulnerability Oded Vanunu said in a statement.
Hackers broke into the celeb London Bridge Plastic Surgery clinic
26.10.2017 securityaffairs Hacking
The celeb London Bridge Plastic Surgery clinic confirmed in a statement that it has been the victim of a cyber attack.
The story I’m going to tell you shows the risks of cyber attacks to users’ privacy, a plastic surgery clinic frequented by celebrities suffered a security data breach.
The clinic is the London Bridge Plastic Surgery, among its clients there are celebrities like Katie. The clinic confirmed in a statement that it has been the victim of a cyber attack, the alleged culprit is a well-known hacker that goes online with the moniker The Dark Overlord.
In April the hacker ‘The Dark Overlord’ claimed to have stolen and leaked online episodes from the forthcoming season of the TV show Orange Is The New Black.
“We can confirm that the Clinic has been the victim of a cyber attack. We took measures to block the attack immediately in order to protect patient information and we informed the Metropolitan Police who launched an investigation,” states the statement issued by the London Bridge Plastic Surgery (LBPS).
“Regrettably, following investigations by our IT experts and the police, we believe that our security was breached and that data has been stolen. We are still working to establish exactly what data has been compromised,”
“The Dark Overlord, a hacking group known for mocking and extorting victims, has now stolen highly personal photos from a plastic surgeon in London.” reported Joseph Cox from The Daily Beast.
The Dark Overlord contacted Cox using an email account belonging to LBPS to prove they had compromised the systems at the clinic. The group sent The Daily Beast a cache of photos of LBPS operations.
The cache includes highly graphic and close-up images showing surgery on male and female genitalia, other pictures show apparent patients bodies post-operation, and in some cases they include faces.
“None of a selection of tested photos returned any matches from Google reverse image searches, implying that they were indeed obtained from a private source. Several pictures include LBPS’ chief surgeon Chris Inglefield, wearing his distinctive, multi-colored head scarves. In one image, he is wearing an identical head scarf to that in an image on LBPS’ website.” continues Cox.
The hacker crew also claims that stolen data contains information on royal families and it is threatening to leak the patient list and their photos.
The clinic was not prepared to this cyber attack, it was shocked by the event as admitted in the statement.
“We are horrified that they have now targeted our patients,” continued.” states the LBPS statement.
“Security and patient confidentiality has always been of the utmost importance to us. We invest in market-leading technology to keep our data secure and our systems are updated daily. We are deeply saddened that our security has been breached. We are profoundly sorry for any distress this data breach may cause our patients and our team are available around the clock to speak to anyone who has any concerns by calling 0203 858 0664,”
The British authorities are investigating the data breach.
Krebs reported that Dell lost Control of dellbackupandrecoverycloudstorage Domain in June 2017
26.10.2017 securityaffairs Security
The popular investigator Brian Krebs reported that the tech giant Dell lost the control of dellbackupandrecoverycloudstorage domain in June 2017.
It is really embarrassing, Dell forgot to renew the domain www.dellbackupandrecoverycloudstorage.com name that was used by the tech giant to install operating systems on the PC it has sold. The incident was discovered by a third-party entity that blamed the vendor for spreading malware through the domain.
According to the popular investigator Brian Krebs who first reported the news, the domain is administered by a third party, which didn’t renew the domain in June 2017.
“It’s not yet clear how or why DellBackupandRecoveryCloudStorage.com got away from SoftThinks.com — an Austin, Tex.-based software backup and imaging solutions provider that originally registered the domain back in mid-2013 and has controlled it for most of the time since. But someone at SoftThinks apparently forgot to renew the domain in mid-June 2017.” states Brian Krebs.
The www.dellbackupandrecoverycloudstorage.com domain provides information about Dell’s data protection products and is used as a back-end for an app called the “Dell Backup and Recovery Application” that is a solution bundled with Dell PCs. Dell defines the app as “a safe, simple, and reliable backup and recovery solution that can protect your system (OS, applications, drivers, settings) and data (music, photos, videos, documents, and other important files) from data loss.”
The Dell Backup and Recovery Application are also used by Dell to allows PC owners to do a factory reset of their machines.
Krebs alleges the domain redirected to websites hosting malware, according to AlienVault‘s Open Threat Exchange the Internet address that was assigned to DellBackupandRecoveryCloudStorage.com in late June is an Amazon server which is “actively malicious.”
“Reached for comment about the domain snafu, Dell spokesperson Ellen Murphy shared the following statement:
“A domain as part of the cloud backup feature for the Dell Backup and Recovery (DBAR) application, www.dellbackupandrecoverycloudstorage.com, expired on June 1, 2017 and was subsequently purchased by a third party. The domain reference in the DBAR application was not updated, so DBAR continued to reach out to the domain after it expired. Dell was alerted of this error and it was addressed. Dell discontinued the Dell Backup and Recovery application in 2016.””
Krebs warned of scammers that are contacting Dell customers pretending to be Dell tech support specialists. The scammers employ social engineering techniques to make their scams more convincing by reading off the unique Dell “service tag” code printed on each Dell customer’s PC or laptop.
“How can scammers have all this data if Dell’s service and support system isn’t compromised, many Dell customers have asked? And still ask: I’ve had three readers quiz me about these Dell service tag scams in the past week alone. Dell continues to be silent on what may be going on with the service tag scams, and has urged Dell customers targeted by such scams to report them to the company.” concluded Krebs.
This is not the first time the registration related incidents caused problems to organizations. Earlier this month, a service on the Equifax website set up for obtaining free and discounted credit reports had been redirecting users to websites offering a fake Flash Player installer.
Symantec Claims It Is Leapfrogging the Competition
26.10.2017 securityweek Safety
The latest version of Symantec Endpoint Protection, SEP 14.1, adds new capabilities to the signatureless machine learning malware detection SEP product it introduced last year, and integrates with other Symantec security solutions. The stated purpose is to provide end-to-end protection for endpoints in a single agent.
The key features announced this week include the addition of deception and device hardening in SEP 14.1; together with integration with a new version of Symantec Endpoint Detection and Response, and integration with the new Mobile Threat Defense originally acquired with the purchase of Skycure in July 2017.
Deception is new to SEP. It is the deployment of deceptors -- or decoy files, folders and registries -- within the environment. The deceptors are designed to look valuable to an adversary who succeeds in accessing the system; but they contain nothing of consequence. The idea is to attract the adversary, slow him down on a wild goose chase, and alert the security team to his presence.
“The security team can learn through watching what the adversaries are doing -- how they are trying to manifest their malware,” explains Sri Sundaralingam, head of product marketing at Symantec. “The defenders can then neutralize the attack, and include new understanding in their security posture to block any similar type of attack in the future.” Symantec is the first of the traditional endpoint security vendors to integrate deception with their endpoint product. “It means,” continues Sundaralingam, “we provide a multi-level defense against ransomware and zero-day day attacks, and we improve the customer's overall security posture.”
If a deceptor triggers and alerts the security team, it means that a breach has already occurred. Here the integration with the new EDR product (Advance Threat Protection or ATP 3.0) comes into play to help with incident response.
“The endpoint product will recognize that a bad guy is trying to tamper with one of the deceptors,” Sundaralingam told SecurityWeek, “and it will notify the SOC team through a set of triggered descriptive alerts that will describe how the attacker is tampering with the deceptor files.” This helps the security team understand what the adversary is trying to do. Is there, for example, some unpatched vulnerability on the system? It's a proactive defense mechanism to help the customer detect and respond to an actual, but perhaps hitherto unknown, compromise.
“Deception firstly detects the presence of a stealthy attack,” he continued; “secondly, it tells the security team what the attackers are trying to do, what system files they are seeking to compromise and so on (providing additional intelligence on how to amend the security posture to eliminate this and similar attacks); and thirdly it can slow the attack down sufficiently for the security team to take action.”
The integration with EDR then enables incident responders to collect data on an ongoing exploitation, providing additional information for them to locate the origins of the breach. “Combining Deception with EDR and Symantec Analytics can give the defenders an end-to-end picture of the incursion, and ensure an effective response,” he said.
Coupled with the new ATP 3.0 EDR, is a new EDR Cloud offering -- the same purpose but offered as a cloud-based SaaS. The cloud offering isn't limited to environments with Symantec endpoints -- it works equally well for customers with mixed environments. “It records endpoint activity and collects data that can be used to look for new emerging attacks like fileless attacks.” It enhances investigator productivity with pre-built incident response playbooks that bring the skills and best practices of the most experienced security analysts to any organization, resulting in significantly lower costs, claims Symantec.
Device hardening is a new add-on for SEP 14. “It allows customers to lock down known good applications, to monitor the not so well-known apps, and to isolate suspicious applications -- it's application isolation,” Sundaralingam explained. Every app can be assessed and given a risk rating. Symantec already has what it calls 'the world's largest civilian blacklist and whitelist databases'. “Important apps like Office will be protected from unpatched 0-day exploits. Grey-area apps will be monitored, so that files downloaded via those apps can be blocked. We call it castles and jails,” he added: “we put the good apps in the castle and protect them; we put the suspicious apps in the jail and we monitor and control what those apps are doing.”
Also new is mobile threat defense through SEP Mobile. This is the rebranded and integrated mobile security product acquired with the purchase of Skycure. SEP mobile brings desk-top quality security to mobile devices, protecting both BYOD and corporate-owned products across both Android and iOS devices used in the corporate environment.
Sundaralingam believes that the mobile threat vector hasn't been given sufficient attention. “There are mobile device managers (MDMs) in wide use; but they are just that: managers. They don't defend the devices. SEP Mobile provides mobile device protection.”
Symantec's strategy outlined in this week's announcement combines new products with increased integration around SEP 14.1 as the centerpiece. The purpose is to provide comprehensive endpoint protection through a single framework. Apart from the new products, existing products are now integrated -- including, for example, the CloudSOC CASB acquired with BlueCoat. “It's a very ambitious integration of a wide range of security capabilities,” said Sundaralingam. “We believe we are leapfrogging all the other vendors of endpoint security; both existing vendors and the new emerging products that tend to be limited in the areas they cover.”
'Bad Rabbit' Attack Infrastructure Set Up Months Ago
26.10.2017 securityweek Ransomware
The infrastructure used by the Bad Rabbit ransomware was set up months ago and an increasing amount of evidence links the malware to the NotPetya attack launched in late June, which some experts believe was the work of a Russian threat actor.
A majority of the Bad Rabbit victims are in Russia – over 80% according to some reports – where the ransomware hit several media outlets, including Interfax. Significant infections have also been observed in Ukraine, where the malware reportedly hit major organizations such as the airport in Odessa, the Kiev subway, the State Aviation Service of Ukraine, and the Transport Ministry of Ukraine.
Infections have also been spotted in Bulgaria, Turkey, Germany, Japan, the United States, South Korea and Poland.
Unlike the NotPetya attack, which hit tens of thousands of systems in more than 65 countries, Bad Rabbit, delivered by attackers via fake Flash Player installers, only infected a few hundred machines mainly belonging to enterprises. The attack began on October 24 at around 10 AM UTC and the majority of infection attempts were detected in the first couple of hours.
Analysis conducted by researchers and security firms showed many connections between Bad Rabbit and NotPetya, including the use of legitimate features such as SMB to spread within the compromised network. However, Bad Rabbit does not use EternalBlue or any other exploit.
The security researcher known online as Bart Blaze has published a useful table summarizing the similarities and differences between NotPetya and Bad Rabbit. The similarities include targeting of Ukraine and Russia, binaries signed with expired certificates, use of Mimikatz for credential-grabbing, reboots and persistence via scheduled tasks, removal of event logs and USN change journals, and the same type of file encryption and ransomware functionality.
One of the most significant differences is the fact that Bad Rabbit appears to be an actual ransomware and, at least in theory, users can recover their encrypted files if they pay the ransom; unlike NotPetya, which has been classified as a wiper due to the fact that the ransom payment functionality is not implemented properly, making the recovery of files impossible.
Bad Rabbit infrastructure
Kaspersky Lab researcher Costin Raiu pointed out that several of the compromised domains used in the Bad Rabbit attack had been set up for malicious activity since at least July.
An analysis by RiskIQ shows that some of the injection servers involved in the attack were set up more than a year ago.
“While this list is most likely incomplete, it does show that it’s part of a long-running campaign. The operators of this campaign have been able to use this position to target unique visitors based on IP space they associate with their targets,” explained RiskIQ’s Yonathan Klijnsma.
“The thing we do not understand at this point is why they decided to burn this information position to mass distribute the BadRabbit ransomware rather than save it for another type of malware. The goal of the attack using ExPetya back in June was simple: cause as much disruption in the Ukraine and those associated with Ukraine as possible which also seems the case in the BadRabbit attack,” Klijnsma added.
Russian security firm Group-IB noted that the domain serving the fake Flash Player installer, 1dnscontrol[dot]com, was hosted by Inferno, which is run by the same people as 3NT Solutions and V3Servers. The activities of this hosting company were detailed back in 2014 by British researcher Conrad Longmore, who has now provided an updated list of IP addresses that he believes should be blocked by organizations.
“The domain name 1dnscontrol.com was registered on 22 March 2016 and is currently prolonged. There are a number of malicious domains associated with this site, which relate back to 2011. It is possible that these domains have also been compromised or are used for analogous attacks,” Group-IB said.
Links to BlackEnergy
NotPetya, which is also tracked as Diskcoder, Petya, Petrwrap, exPetr and GoldenEye, was linked back in early July to a threat group known as TeleBots, BlackEnergy and Sandworm Team, which experts have tied to Russia and which is believed to be behind cyberattacks on Ukraine’s power grid.
NotPetya was linked to BlackEnergy based on similarities to a wiper used by the threat actor, Yara rules detecting both BlackEnergy and NotPetya malware, and previous ransomware attacks that hit Ukraine.
Several security firms and researchers pointed out that if the NotPetya attack was conducted by BlackEnergy, and Bad Rabbit was created by the same developers that made NotPetya, the obvious conclusion would be that Bad Rabbit is also the work of the Russia-linked hackers.
Bezpečnostní experti varovali před agresivním vyděračským virem
26.10.2017 Novinky/Bezpečnost Viry
Internetem se masivně šířil nový vyděračský virus zvaný Bad Rabbit, tedy v překladu Zlý králík. Maskoval se přitom za aktualizaci oblíbeného programu pro přehrávání videí Flash Player, upozornil bezpečnostní tým Cisco Talos.
Bad Rabbit tedy patří do rodiny vyděračských virů označovaných souhrnným názvem ransomware. Tento nezvaný návštěvník útočí velmi podobně jako škodlivý kód Nyetya, který hrál hlavní roli při jednom z nedávných globálních útoků.
„Do zařízení se škodlivý software dostane tak, že jej uživatelé stáhnou a spustí v domnění, že jde o aktualizaci oblíbeného nástroje Flash Player. Uživatelům, kteří navštíví infikované webové stránky, se zobrazí aktualizační okno s možnostmi ‚Remind later‘ a ‚Install‘. Obě varianty ale vedou k infekci,“ uvedli bezpečnostní experti z Cisco Talos.
Útočil především na východní Evropu a Rusko
Podle nich tento záškodník útočil především ve východní Evropě a Rusku. Není nicméně vyloučeno, že na něj mohli na internetu narazit také tuzemští uživatelé. „Podle dostupných informací byl malware aktivní přibližně šest hodin před tím, než byla zdrojová webová stránka odstraněna,“ konstatovali bezpečnostní experti.
Přestože samotný útok trval jen pár hodin, byl velmi masivní. „Zatím není zcela jasné, jaká ransomwarová varianta byla k útokům použita, ale znovu se ukazuje, jak nebezpečný ransomware může být. A jak rychle může narušit životně důležité služby, pokud není použito správné zabezpečení,“ řekl Petr Kadrmas, bezpečnostní výzkumník ve společnosti Check Point.
Ten zároveň připomněl, jak v poslední době podobných útoků přibývá. „Počet ransomwarových útoků se v první polovině roku 2017 zdvojnásobil ve srovnání se stejným obdobím v roce 2016, ale 99 % organizací stále ještě nemá základní kyberbezpečnostní technologie, které mohou podobným útokům zabránit. Pokud by měly organizace odpovídající bezpečnostní mechanismy, mohly by zabránit i těmto útokům,” uzavřel Kadrmas.
Útočil především na firmy
Jak patrné, útok vyděračského viru Bad Rabbit cílil především na společnosti a organizace. Není samozřejmě vyloučeno, že mohl zablokovat také počítače běžných uživatelů, právě naopak – je to velmi pravděpodobné.
Organizace by měly při ochraně svých počítačových systémů používat víceúrovňový přístup: blokovat přístup ke škodlivým webům, zablokovat možné stahování malwaru a pomocí ochrany koncových bodů zastavit napadení zařízení. To všechno samozřejmě v kombinaci se zásadami správného zálohování a bezpečnostního školení uživatelů.
Firms Increasingly Turn to Machine Learning for Security Solutions
26.10.2017 securityweek Security
Forty-seven percent of organizations have already deployed machine learning (ML) solutions, with another 23% engaged in pilot projects, to help detect increasingly sophisticated incursions and lower the cost of response.
A study (PDF) commissioned by Cylance and undertaken by Enterprise Strategy Group (ESG) surveyed 300 IT and security professionals from mid-market and large enterprises. The respondents are located in the United States (43%), Japan (21%), United Kingdom (13%), France (12%), and Germany (11%); and all are involved in the purchase process for endpoint security.
The study sought to identify the 'top of mind' security threats, and the impact those threats have on endpoint security purchasing decisions.
Phishing is the biggest concern for most respondents. In the last two years, 55% have experienced phishing with a malicious attachment, 54% have experienced phishing with a link to a malicious website, and 29% have experienced instant messaging phishing with a link to a malicious website.
Phishing -- particularly spear-phishing -- has proven resilient against technological solutions. Although there are current attempts to develop ML solutions, some researchers believe it will not be possible. “With such a small number of known spearphishing instances, standard machine learning approaches seem unlikely to succeed: the training set is too small and the class imbalance too extreme,” notes a recent research paper.
ESG suggests that training is the best solution to phishing. “Organizations can reduce phishing response rates and raise security awareness by training employees to recognize spoofed emails and texts, and to practice good hygiene, such as checking URLs before clicking links,” says the report. “Training repetition, phishing simulations, and red teams, where an independent group attempts to induce bad employee behavior, can reinforce initial cybersecurity training, and 35% of organizations that have suffered a security incident are instituting additional end-user training.”
However, it is not the phishing itself that is the problem, but what the phishing leads to -- which is usually, ultimately, malware. Asked which threats are the most difficult to detect, 43% of respondents replied, 'unknown malware'; 31% replied 'zero-day exploits of new and unknown vulnerabilities', and 29% replied 'fileless attacks which employ weaponized content'.
These are precisely the attacks that signature-based detection systems cannot recognize, and where machine-learning behavioral detection systems excel.
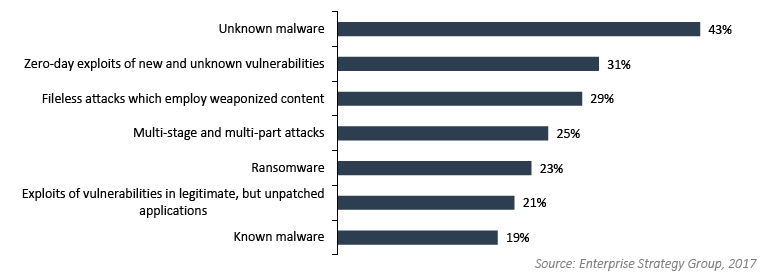
Ransomware, unsurprisingly, gets special consideration. “At 46%,” states the report, “nearly half of the respondents noted that their organization had been the victim of a ransomware attack in the last year and more than half of those (56%) reported more than 5% of their organization’s endpoints were infected. It is noteworthy that only 12% of affected organizations paid the ransom.”
But neither paying the ransom nor restoring impacted data from backup are necessarily the solution. “Nearly a quarter of research participants whose organizations have been recent ransomware victims stated that they experienced a recurrence of the same ransomware on the same endpoints and 38% experienced the same ransomware but on different endpoints.”
Somewhat surprisingly, financial loss (15%) and data loss (19%) are dwarfed by interruptions to standard business processes (32%) as the main effect of a security incident. Given the time and effort required to discover and remove malicious files with the risk of missing something, many organizations simply re-image the system from a golden master. This is still time-consuming.
“Twenty-nine percent of respondents said their organization reimages 100 or more systems every month, and 12% said their organization reimages more than 500 systems per month. It takes a dedicated team of IT professionals to reimage hundreds of endpoints each month, and the volume of infections hints at inadequacies in endpoint security controls,” says the report.
Just as cyber criminals have evolved their attacks to defeat first-generation signature based defenses with polymorphic malware and fileless attacks, it seems that security professionals are aware of the problems and are actively investigating or deploying second-generation ML-based behavioral detection systems in response.
Cylance, which commissioned the survey, raised $100 million is Series D financing in June 2016.
Removal Attempt Turns Android Banking Trojan Into Ransomware
26.10.2017 securityweek Ransomware
Researchers at SfyLabs have detailed the capabilities of an Android banking Trojan named LokiBot that is designed to turn into a piece of ransomware when users attempt to remove it from their devices.
LokiBot has been around since at least June and its authors have been rolling out new features nearly every week.
Once it infects an Android device (running Android version 4.0 or later), the malware starts displaying overlay screens on top of banking and other popular apps in an effort to trick victims into handing over their information. The malware targets roughly 100 banking applications and popular apps such as WhatsApp, Skype and Outlook.
The malware can also open the user’s web browser and navigate to a specified page, reply to SMS messages, and launch banking apps.
“Combine this with the fact that LokiBot can show notifications which seem to come from other apps, containing for example a message that new funds have been deposited to the victim’s account and interesting phishing attack scenarios arise!” SfyLabs researchers said in a blog post. “The phishing notifications use the original icon of the application they try to impersonate. In addition, the phone is made to vibrate right before the notification is shown so the victim will take notice of it. When the notification is tapped it will trigger an overlay attack.”
The most interesting feature, which has led researchers to classify LokiBot as a hybrid Android malware, is its ability to turn into ransomware when users attempt to remove it.
Specifically, when users try to revoke its admin privileges, the malware initiates a procedure to encrypt all files on the device’s external storage and locks the screen with a typical ransom demand claiming that the phone is locked for “viewing child pornography.” Victims are given 48 hours to pay a $70 - $100 “fine” in bitcoin.
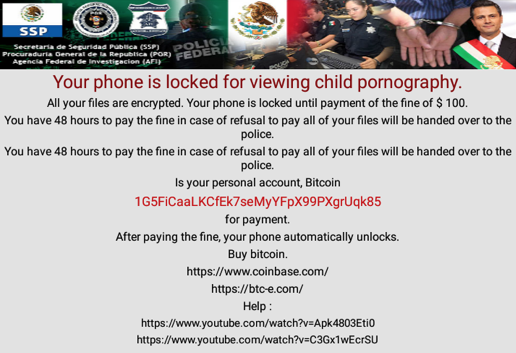
SfyLabs found that the bitcoin address provided by the cybercriminals already stores cryptocurrency worth roughly $1.5 million. However, it’s unlikely that the entire amount comes from LokiBot attacks as the campaigns spotted by experts generally have only around 1,000 bots and the cost of the Trojan itself is $2,000.
Researchers noticed that while the screen-locking functionality works, the malware doesn’t actually encrypt files. Due to an error, files are automatically restored after being encrypted, but with a different name.
The malware’s developers have implemented some mechanisms designed to prevent dynamic analysis, but they are not particularly sophisticated, especially compared to other malware.
It’s worth noting that there is another Loki Bot malware that targets Windows devices. This threat is designed to steal data from infected computers and it has reportedly been used as a secondary payload in the NotPetya attack launched in late June.
Ochrana osobních údajů: bezpečnost je základním předpokladem digitalizace
26.10.2017 SecurityWorld Zabezpečení
Tak jako kdysi zlatý prach jsou data v 21. století klíčem k bohatství a jejich objem se každé dva roky zdvojnásobuje (v roce 2020 podle odhadů dosáhne 44 bilionů gigabytů). Data umožňují podnikům všech oborů a velikostí do maximální možné míry poznat své zákazníky a všechny podniky hledají způsoby, jak efektivně údaje o svých stávajících (i potenciálních) zákaznících využít. Například analýza dat v téměř reálném čase a reakce na získané poznatky umožňuje výrazně zlepšit obsluhu zákazníka – od lepších produktů a rychlejších služeb po personalizovanou komunikaci a na míru připravené odměny.
Datový poklad však není volně dosažitelný každému. To, co podniky láká – vlastnictví a užívání dat – je zároveň může vystavit značnému právnímu riziku a nebezpečí ztráty pověsti. Stejně se vzedmula vlna zájmu o využití dat, začínají si zákazníci sále více uvědomovat své právo na ochranu soukromí a možné dopady sdělování svých osobních údajů.
Podniky, které nedokáží dostatečně zabezpečit údaje o svých zákaznících se nejen vystavují právnímu postihu, ale nanejvýš pravděpodobně také utrpí jejich reputace a důvěryhodnost. Z bezpečnostních selhání musí vyvozovat osobní důsledky i nejvýše postavení manažeři. Bývalá generální ředitelka společnosti Yahoo! Marissa Mayer přišla o roční prémie, protože firma nezvládla patřičně reagovat na narušení bezpečnosti, při němž došlo ke krádeži osobních údajů více než 1 miliardy uživatelů.
Na poptávku po právní ochraně soukromí reagují i úřední aparáty a přijímají předpisy, jako je evropské Obecné nařízení o ochraně osobních údajů (GDPR), které nabývá účinnosti 28. května 2018 a zaručuje ochranu osobních údajů všem obyvatelům Evropské unie bez ohledu na to, kde jsou jejich data uložena nebo zpracovávána.
Toto nařízení bude mít dopad na podniky z celého světa, nikoli jen evropské. Zdaleka ne všechny subjekty jsou však na GDPR připravené. V průzkumu uvedlo 8 % z dotázaných britských firem, že dosud nezavedlo žádná z opatření nutných ke splnění povinností vyplývajících z GDPR. Obdobná situace panuje v Německu (8 %) a Francii (12 %).
Podniky se tak pohybují na tenkém ledě. Pro své strategie digitální transformace potřebují nezbytně uchovávat data a využívat je tak, aby dosáhly konkurenční výhody. Zároveň musí data chránit proti stále důmyslnějším hrozbám, přičemž digitalizovat znamená vystavovat podnik útokům z více různých směrů.
Možnost volby a zachování kontroly
Podniky usilují o úplnou digitalizaci, díky níž získají akceschopnost, bezpečnost, přizpůsobivost a nákladovou efektivitu. Na první pohled se může zdát, že akceschopnost a přizpůsobivost jsou v protikladu s bezpečností. Pokud však má podnik maximálně těžit z přínosů digitalizace, musí se věnovat všem jejím aspektům. Gartner to popisuje jako „využití digitálních technologií ke změně obchodního modelu a nalezení nových příležitostí k tvorbě zisku a hodnoty“.
Před nedávnem vyšla studie výzkumné společnosti 451 Research, jejíž zpracování zadaly společnosti VMware a Atos, která zkoumala hlavní trendy a očekávání ohledně zavádění cloudu. Ze studie vyplývá, že zlepšování akceschopnosti a přizpůsobivosti patří mezi tři rozhodující faktory u plánovaných cloudových projektů amerických a evropských podniků a jsou dvěma hlavními faktory, které ovlivňují rozhodování o zavedení správné infrastruktury pro digitalizaci.
V minulosti obecně panovala situace buď-anebo – podnik, který chtěl být mobilní a připojený se otevíral útokům, celková digitalizace se vylučovala s dodržováním zákonných povinností a odpovědné správy a vyšší bezpečnost byla na úkor zákaznické zkušenosti.
Tento názor je stále hluboce zakořeněný – studie společnosti 451 Research, která zkoumala, jak cloudové technologie podporují digitální transformaci, zjistila nejen to, že 48 % evropských podniků (50 % ve Velké Británii, 42 % v Německu a 49 % ve Francii) zvažuje přesun aplikací do privátních cloudů z důvodů bezpečnosti a možnosti kontroly, ale také že bezpečnost zůstává jednou z hlavních překážek zavádění cloudu obecně. Je to pochopitelné, uvážíme-li, že podle společnosti Gartner potřeba předcházet únikům dat z veřejných cloudů do roku 2018 přiměje 20 % podniků k zavedení programů správy zabezpečení dat.
V podnicích také přetrvává zvyk nijak nekoordinovaného nákupu technologií, kdy si různé jednotky pořizují IT produkty a služby dle svého uvážení a bez vědomí IT. Zejména se jedná o snadný nákup veřejných cloudových služeb jako pohotového řešení, které zajistí akceschopnost a rychlost při uvádění produktů a služeb na trh, aniž by bylo nutné procházet korporátním procesem schvalování, zabezpečení a řízení shody.
Infrastruktura, která dokáže ochránit nejcennější komoditu 21. století
Naneštěstí neexistuje jediný univerzální přístup, který by vyhovoval ve všech situacích. Každý podnik musí nalézt infrastrukturu, která bude vyhovovat jeho specifickým potřebám a pokrývat požadavky pomocí kombinace různých prostředí. Privátní cloudy rozhodně nabízí bezpečná prostředí, ale veřejné cloudy je překonávají z hlediska flexibility. Je také důležité vědět, jak vznikají aplikace – od vývoje a testování po produkční nasazení, přičemž každý krok může fungovat nejlépe v jiném prostředí. Snadná migrace mezi různými typy prostředí je tedy základním předpokladem efektivního uvádění produktů a služeb na trh při zachování bezpečnosti a souladu s regulatorními a zákonnými požadavky.
Teoreticky to vypadá jako vynikající nápad, ale je to reálné v praxi? Skutečně platí, že žádný podnik nemůže požívat výhod digitalizace a zároveň se zachovat bezpečnost?
Ne, neplatí. Olympijské hry jsou toho skvělým příkladem – olympiáda v Riu v roce 2016 byla nejen skutečně digitální událostí v ještě větším rozsahu než o čtyři roky dříve Londýn a s efektivnějším využitím výpočetního výkonu, ale její systémy dokázaly chránit data tisíců sportovců, novinářů, dobrovolníků a dalších osob a zároveň zpracovávat akreditace a přístup v pevně stanovených termínech. Každou sekundu se také potýkaly se 400 hackerskými útoky, tedy 510 miliony kyberbezpečnostních událostí za celou dobu trvání her. To je dvojnásobný počet útoků, něž kolika čelil Londýn 2012.
Bez ochrany dat nelze podnikat
Skutečností je, že podniky jsou a budou posuzovány podle ochrany dat. Zavedení GDPR pomůže zvýšit povědomí o opatřeních, která by měly podniky přijmout, a má dalekosáhlé důsledky pro každou firmy, která se dotkne evropského trhu, bez ohledu na to, kde sídlí.
Zároveň je nutné počítat s tím, že zákazníci nebudou ochotni se vzdát funkcionality a komfortu. Zajištění bezpečnosti je jedním z klíčových prvků digitalizace – každý podnik, který chce těžit z jejích výhod, musí na bezpečnosti pracovat stejně jako na akceschopnosti, přizpůsobitelnosti a nákladové efektivitě. A správná infrastruktura zásadním způsobem pomáhá patřičnou rovnováhu nastolit.
Kaspersky Lab poskytne svůj zdrojový kód k přezkoumání třetí stranou
26.10.2017 SecurityWorld BigBrother
Společnost Kaspersky Lab oznámila globální iniciativu pro transparentnost – Global Transparency Initiative. Touto iniciativou chce Kaspersky zapojit do prověřování důvěryhodnosti svých produktů, interních procesů a obchodních praktik širší informačně-bezpečnostní komunitu a další zainteresované strany. Reaguje tak na rostoucí spekulace kolem možné nedůvěryhodnosti jejích produktů.
Kromě iniciativy firma zároveň zavádí další mechanismy pro podporu odpovědnosti, čímž chce společnost prokázat, že jakékoliv bezpečnostní problémy řeší okamžitě a důkladně. V rámci iniciativy chce rovněž pro nezávislé posouzení poskytnout zdrojový kód svého softwaru, včetně jeho aktualizací a pravidel detekce hrozeb.
Počáteční fáze této iniciativy bude zahrnovat:
1) Začátek nezávislého přezkoumání zdrojového kódu společnosti do prvního čtvrtletí roku 2018. Podobná přezkoumání budou následně provedena i u aktualizací softwaru a pravidel pro detekci hrozeb.
2) Zahájení nezávislého posouzení (i) procesů bezpečného rozvoje společnosti a (ii) strategií na zmírňování rizika v oblasti softwaru a dodavatelského řetězce do prvního čtvrtletí 2018.
3) Ve spolupráci s nezávislou stranou navržení dodatečných kontrolních procesů, které budou řídit postupy společnosti v oblasti zpracování dat. Nezávislá strana následně do 1. čtvrtletí 2018 doloží, že Kaspersky Lab tyto kontroly dodržuje.
4) Vytvoření tří Center transparentnosti (Transparency Centers), kdy první vznikne v roce 2018. Jejich cílem bude řešit jakékoliv problémy s bezpečností společně se zákazníky, důvěryhodnými partnery a zástupci vlády. Centra budou sloužit jako zařízení, kde budou mít důvěryhodní partneři přístup k přezkoumáním firemního kódu, aktualizacím softwaru a pravidlům pro detekci hrozeb a dalším záležitostem. Tato centra budou do roku 2020 otevřena v Asii, Evropě a USA.
5) Do konce roku 2017 budou navýšeny odměny za nalezení programových chyb až do výše 100 000 dolarů. Odměny se týkají zjištění nejzávažnějších zranitelností v rámci programu Coordinated Disclousure Vulnerability. Tento fakt má ještě více motivovat nezávislé bezpečnostní výzkumníky k tomu, aby nám pomohli detekovat zranitelnosti a minimalizovat následky zákeřných aktivit.
V návaznosti na tuto počáteční fázi Global Transparency Initiative by Kaspersky Lab chtěla na základě zpětné vazby od informačně-bezpečnostní komunity a dalších zainteresovaných stran stanovit náplň další fáze. Ta odstartuje ve druhé polovině příštího roku.
Společnost bude pravidelně informovat o detailech a vývoji této iniciativy a s ní spojených aktivitách.
Bad Rabbit ransomware
25.10.2017 Kaspersky Ransomware
What happened?
On October 24th we observed notifications of mass attacks with ransomware called Bad Rabbit. It has been targeting organizations and consumers, mostly in Russia but there have also been reports of victims in Ukraine. Here’s what a ransom message looks like for the unlucky victims:
What is bad rabbit?
Bad Rabbit is a previously unknown ransomware family.
How is bad rabbit distributed?
The ransomware dropper was distributed with the help of drive-by attacks. While the target is visiting a legitimate website, a malware dropper is being downloaded from the threat actor’s infrastructure. No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer.
We’ve detected a number of compromised websites, all of which were news or media websites.
Whom does it target?
Most of the targets are located in Russia. Similar but fewer attacks have also been seen in other countries – Ukraine, Turkey and Germany. Overall, there are almost 200 targets, according to the KSN statistics.
Since when does Kaspersky Lab detect the threat?
We have been proactively detecting the original vector attack since it began on the morning of October 24. The attack lasted until midday, although we are still detecting ongoing attacks.
How is it different to ExPetr? Or it is the same malware?
Our observations suggest that this been a targeted attack against corporate networks, using methods similar to those used during the ExPetr attack.
Technical details
According to our telemetry, the ransomware is spread via a drive-by attack.
The ransomware dropper is distributed from hxxp://1dnscontrol[.]com/flash_install.php
Also according to our telemetry data, victims are redirected to this malware web resource from legitimate news websites.
The downloaded file named install_flash_player.exe needs to be manually launched by the victim. To operate correctly, it needs elevated administrative privileges which it attempts to obtain using the standard UAC prompt. If started, it will save the malicious DLL as C:\Windows\infpub.dat and launch it using rundll32.
Pseudocode of the procedure that installs the malicious DLL
infpub.dat appears to be capable of brute-forcing NTLM login credentials to Windows machines that have pseudo-random IP addresses.
The hard-coded list of credentials
infpub.dat will also install the malicious executable dispci.exe into C:\Windows and create a task to launch it.
Pseudocode of the procedure that creates the task which launches the malicious executable
What’s more, infpub.dat acts as a typical file encrypting ransomware: it finds the victim’s data files using an embedded extension list and encrypts them using the criminal’s public RSA-2048 key.
The public key of the criminals and the extension list
The criminal’s public key parameters:
Public-Key: (2048 bit)
Modulus:
00:e5:c9:43:b9:51:6b:e6:c4:31:67:e7:de:42:55:
6f:65:c1:0a:d2:4e:2e:09:21:79:4a:43:a4:17:d0:
37:b5:1e:8e:ff:10:2d:f3:df:cf:56:1a:30:be:ed:
93:7c:14:d1:b2:70:6c:f3:78:5c:14:7f:21:8c:6d:
95:e4:5e:43:c5:71:68:4b:1a:53:a9:5b:11:e2:53:
a6:e4:a0:76:4b:c6:a9:e1:38:a7:1b:f1:8d:fd:25:
4d:04:5c:25:96:94:61:57:fb:d1:58:d9:8a:80:a2:
1d:44:eb:e4:1f:1c:80:2e:e2:72:52:e0:99:94:8a:
1a:27:9b:41:d1:89:00:4c:41:c4:c9:1b:0b:72:7b:
59:62:c7:70:1f:53:fe:36:65:e2:36:0d:8c:1f:99:
59:f5:b1:0e:93:b6:13:31:fc:15:28:da:ad:1d:a5:
f4:2c:93:b2:02:4c:78:35:1d:03:3c:e1:4b:0d:03:
8d:5b:d3:8e:85:94:a4:47:1d:d5:ec:f0:b7:43:6f:
47:1e:1c:a2:29:50:8f:26:c3:96:d6:5d:66:36:dc:
0b:ec:a5:fe:ee:47:cd:7b:40:9e:7c:1c:84:59:f4:
81:b7:5b:5b:92:f8:dd:78:fd:b1:06:73:e3:6f:71:
84:d4:60:3f:a0:67:06:8e:b5:dc:eb:05:7c:58:ab:
1f:61
Exponent: 65537 (0x10001)
The executable dispci.exe appears to be derived from the code base of the legitimate utility DiskCryptor. It acts as the disk encryption module which also installs the modified bootloader and prevents the normal boot-up process of the infected machine.
An interesting detail that we noticed when analyzing the sample of this threat: it looks like the criminals behind this malware are fans of the famous books & TV show series Game Of Thrones. Some of the strings used throughout the code are the names of different characters from this series.
Dragon names from Game Of Thrones
Character name from Game Of Thrones
Kaspersky Lab experts are working on a detailed analysis of this ransomware to find possible flaws in its cryptographic routines.
Kaspersky Lab corporate customers are also advised to:
make sure that all protection mechanisms are activated as recommended; and that KSN and System Watcher components (which are enabled by default) are not disabled.
update the antivirus databases immediately.
The abovementioned measures should be sufficient. However, as additional precautions we advise the following:
restricting execution of files with the paths c:\windows\infpub.dat and C:\Windows\cscc.dat in Kaspersky Endpoint Security.
configuring and enabling Default Deny mode in the Application Startup Control component of Kaspersky Endpoint Security to ensure and enforce proactive defense against this and other attacks.
Kaspersky Lab products detect this threat with the following verdicts:
Trojan-Ransom.Win32.Gen.ftl
DangerousObject.Multi.Generic
PDM:Trojan.Win32.Generic
IOCs:
http://1dnscontrol[.]com/
fbbdc39af1139aebba4da004475e8839 – install_flash_player.exe
1d724f95c61f1055f0d02c2154bbccd3 – C:\Windows\infpub.dat
b14d8faf7f0cbcfad051cefe5f39645f – C:\Windows\dispci.exe
Dangerous liaisons
25.10.2017 Kaspersky Android iOS
Investigating the security of online dating apps
It seems just about everyone has written about the dangers of online dating, from psychology magazines to crime chronicles. But there is one less obvious threat not related to hooking up with strangers – and that is the mobile apps used to facilitate the process. We’re talking here about intercepting and stealing personal information and the de-anonymization of a dating service that could cause victims no end of troubles – from messages being sent out in their names to blackmail. We took the most popular apps and analyzed what sort of user data they were capable of handing over to criminals and under what conditions.
We studied the following online dating applications:
Tinder for Android and iOS
Bumble for Android and iOS
OK Cupid for Android and iOS
Badoo for Android and iOS
Mamba for Android and iOS
Zoosk for Android and iOS
Happn for Android and iOS
WeChat for Android and iOS
Paktor for Android and iOS
By de-anonymization we mean the user’s real name being established from a social media network profile where use of an alias is meaningless.
User tracking capabilities
First of all, we checked how easy it was to track users with the data available in the app. If the app included an option to show your place of work, it was fairly easy to match the name of a user and their page on a social network. This in turn could allow criminals to gather much more data about the victim, track their movements, identify their circle of friends and acquaintances. This data can then be used to stalk the victim.
Discovering a user’s profile on a social network also means other app restrictions, such as the ban on writing each other messages, can be circumvented. Some apps only allow users with premium (paid) accounts to send messages, while others prevent men from starting a conversation. These restrictions don’t usually apply on social media, and anyone can write to whomever they like.
More specifically, in Tinder, Happn and Bumble users can add information about their job and education. Using that information, we managed in 60% of cases to identify users’ pages on various social media, including Facebook and LinkedIn, as well as their full names and surnames.
An example of an account that gives workplace information that was used to identify the user on other social media networks
In Happn for Android there is an additional search option: among the data about the users being viewed that the server sends to the application, there is the parameter fb_id – a specially generated identification number for the Facebook account. The app uses it to find out how many friends the user has in common on Facebook. This is done using the authentication token the app receives from Facebook. By modifying this request slightly – removing some of the original request and leaving the token – you can find out the name of the user in the Facebook account for any Happn users viewed.
Data received by the Android version of Happn
It’s even easier to find a user account with the iOS version: the server returns the user’s real Facebook user ID to the application.
Data received by the iOS version of Happn
Information about users in all the other apps is usually limited to just photos, age, first name or nickname. We couldn’t find any accounts for people on other social networks using just this information. Even a search of Google images didn’t help. In one case the search recognized Adam Sandler in a photo, despite it being of a woman that looked nothing like the actor.
The Paktor app allows you to find out email addresses, and not just of those users that are viewed. All you need to do is intercept the traffic, which is easy enough to do on your own device. As a result, an attacker can end up with the email addresses not only of those users whose profiles they viewed but also for other users – the app receives a list of users from the server with data that includes email addresses. This problem is found in both the Android and iOS versions of the app. We have reported it to the developers.
Fragment of data that includes a user’s email address
Some of the apps in our study allow you to attach an Instagram account to your profile. The information extracted from it also helped us establish real names: many people on Instagram use their real name, while others include it in the account name. Using this information, you can then find a Facebook or LinkedIn account.
Location
Most of the apps in our research are vulnerable when it comes to identifying user locations prior to an attack, although this threat has already been mentioned in several studies (for instance, here and here). We found that users of Tinder, Mamba, Zoosk, Happn, WeChat, and Paktor are particularly susceptible to this.
Screenshot of the Android version of WeChat showing the distance to users
The attack is based on a function that displays the distance to other users, usually to those whose profile is currently being viewed. Even though the application doesn’t show in which direction, the location can be learned by moving around the victim and recording data about the distance to them. This method is quite laborious, though the services themselves simplify the task: an attacker can remain in one place, while feeding fake coordinates to a service, each time receiving data about the distance to the profile owner.
Mamba for Android displays the distance to a user
Different apps show the distance to a user with varying accuracy: from a few dozen meters up to a kilometer. The less accurate an app is, the more measurements you need to make.
As well as the distance to a user, Happn shows how many times “you’ve crossed paths” with them
Unprotected transmission of traffic
During our research, we also checked what sort of data the apps exchange with their servers. We were interested in what could be intercepted if, for example, the user connects to an unprotected wireless network – to carry out an attack it’s sufficient for a cybercriminal to be on the same network. Even if the Wi-Fi traffic is encrypted, it can still be intercepted on an access point if it’s controlled by a cybercriminal.
Most of the applications use SSL when communicating with a server, but some things remain unencrypted. For example, Tinder, Paktor and Bumble for Android and the iOS version of Badoo upload photos via HTTP, i.e., in unencrypted format. This allows an attacker, for example, to see which accounts the victim is currently viewing.
HTTP requests for photos from the Tinder app
The Android version of Paktor uses the quantumgraph analytics module that transmits a lot of information in unencrypted format, including the user’s name, date of birth and GPS coordinates. In addition, the module sends the server information about which app functions the victim is currently using. It should be noted that in the iOS version of Paktor all traffic is encrypted.
The unencrypted data the quantumgraph module transmits to the server includes the user’s coordinates
Although Badoo uses encryption, its Android version uploads data (GPS coordinates, device and mobile operator information, etc.) to the server in an unencrypted format if it can’t connect to the server via HTTPS.
Badoo transmitting the user’s coordinates in an unencrypted format
The Mamba dating service stands apart from all the other apps. First of all, the Android version of Mamba includes a flurry analytics module that uploads information about the device (producer, model, etc.) to the server in an unencrypted format. Secondly, the iOS version of the Mamba application connects to the server using the HTTP protocol, without any encryption at all.
Mamba transmits data in an unencrypted format, including messages
This makes it easy for an attacker to view and even modify all the data that the app exchanges with the servers, including personal information. Moreover, by using part of the intercepted data, it is possible to gain access to account management.
Using intercepted data, it’s possible to access account management and, for example, send messages
Mamba: messages sent following the interception of data
Despite data being encrypted by default in the Android version of Mamba, the application sometimes connects to the server via unencrypted HTTP. By intercepting the data used for these connections, an attacker can also get control of someone else’s account. We reported our findings to the developers, and they promised to fix these problems.
An unencrypted request by Mamba
We also managed to detect this in Zoosk for both platforms – some of the communication between the app and the server is via HTTP, and the data is transmitted in requests, which can be intercepted to give an attacker the temporary ability to manage the account. It should be noted that the data can only be intercepted at that moment when the user is loading new photos or videos to the application, i.e., not always. We told the developers about this problem, and they fixed it.
Unencrypted request by Zoosk
In addition, the Android version of Zoosk uses the mobup advertising module. By intercepting this module’s requests, you can find out the GPS coordinates of the user, their age, sex, model of smartphone – all this is transmitted in unencrypted format. If an attacker controls a Wi-Fi access point, they can change the ads shown in the app to any they like, including malicious ads.
An unencrypted request from the mopub ad unit also contains the user’s coordinates
The iOS version of the WeChat app connects to the server via HTTP, but all data transmitted in this way remains encrypted.
Data in SSL
In general, the apps in our investigation and their additional modules use the HTTPS protocol (HTTP Secure) to communicate with their servers. The security of HTTPS is based on the server having a certificate, the reliability of which can be verified. In other words, the protocol makes it possible to protect against man-in-the-middle attacks (MITM): the certificate must be checked to ensure it really does belong to the specified server.
We checked how good the dating apps are at withstanding this type of attack. This involved installing a ‘homemade’ certificate on the test device that allowed us to ‘spy on’ the encrypted traffic between the server and the application, and whether the latter verifies the validity of the certificate.
It’s worth noting that installing a third-party certificate on an Android device is very easy, and the user can be tricked into doing it. All you need to do is lure the victim to a site containing the certificate (if the attacker controls the network, this can be any resource) and convince them to click a download button. After that, the system itself will start installation of the certificate, requesting the PIN once (if it is installed) and suggesting a certificate name.
Everything’s a lot more complicated with iOS. First, you need to install a configuration profile, and the user needs to confirm this action several times and enter the password or PIN number of the device several times. Then you need to go into the settings and add the certificate from the installed profile to the list of trusted certificates.
It turned out that most of the apps in our investigation are to some extent vulnerable to an MITM attack. Only Badoo and Bumble, plus the Android version of Zoosk, use the right approach and check the server certificate.
It should be noted that though WeChat continued to work with a fake certificate, it encrypted all the transmitted data that we intercepted, which can be considered a success since the gathered information can’t be used.
Message from Happn in intercepted traffic
Remember that most of the programs in our study use authorization via Facebook. This means the user’s password is protected, though a token that allows temporary authorization in the app can be stolen.
Token in a Tinder app request
A token is a key used for authorization that is issued by the authentication service (in our example Facebook) at the request of the user. It is issued for a limited time, usually two to three weeks, after which the app must request access again. Using the token, the program gets all the necessary data for authentication and can authenticate the user on its servers by simply verifying the credibility of the token.
Example of authorization via Facebook
It’s interesting that Mamba sends a generated password to the email address after registration using the Facebook account. The same password is then used for authorization on the server. Thus, in the app, you can intercept a token or even a login and password pairing, meaning an attacker can log in to the app.
App files (Android)
We decided to check what sort of app data is stored on the device. Although the data is protected by the system, and other applications don’t have access to it, it can be obtained with superuser rights (root). Because there are no widespread malicious programs for iOS that can get superuser rights, we believe that for Apple device owners this threat is not relevant. So only Android applications were considered in this part of the study.
Superuser rights are not that rare when it comes to Android devices. According to KSN, in the second quarter of 2017 they were installed on smartphones by more than 5% of users. In addition, some Trojans can gain root access themselves, taking advantage of vulnerabilities in the operating system. Studies on the availability of personal information in mobile apps were carried out a couple of years ago and, as we can see, little has changed since then.
Analysis showed that most dating applications are not ready for such attacks; by taking advantage of superuser rights, we managed to get authorization tokens (mainly from Facebook) from almost all the apps. Authorization via Facebook, when the user doesn’t need to come up with new logins and passwords, is a good strategy that increases the security of the account, but only if the Facebook account is protected with a strong password. However, the application token itself is often not stored securely enough.
Tinder app file with a token
Using the generated Facebook token, you can get temporary authorization in the dating application, gaining full access to the account. In the case of Mamba, we even managed to get a password and login – they can be easily decrypted using a key stored in the app itself.
Mamba app file with encrypted password
Most of the apps in our study (Tinder, Bumble, OK Cupid, Badoo, Happn and Paktor) store the message history in the same folder as the token. As a result, once the attacker has obtained superuser rights, they will have access to correspondence.
Paktor app database with messages
In addition, almost all the apps store photos of other users in the smartphone’s memory. This is because apps use standard methods to open web pages: the system caches photos that can be opened. With access to the cache folder, you can find out which profiles the user has viewed.
Conclusion
Having gathered together all the vulnerabilities found in the studied dating apps, we get the following table:
App Location Stalking HTTP (Android) HTTP (iOS) HTTPS Messages Token
Tinder + 60% Low Low + + +
Bumble – 50% Low NO – + +
OK Cupid – 0% NO NO + + +
Badoo – 0% Medium NO – + +
Mamba + 0% High High + – +
Zoosk + 0% High High –
(+ iOS) – +
Happn + 100% NO NO + + +
WeChat + 0% NO NO – – –
Paktor + 100% emails Medium NO + + +
Location — determining user location (“+” – possible, “-” not possible)
Stalking — finding the full name of the user, as well as their accounts in other social networks, the percentage of detected users (percentage indicates the number of successful identifications)
HTTP — the ability to intercept any data from the application sent in an unencrypted form (“NO” – could not find the data, “Low” – non-dangerous data, “Medium” – data that can be dangerous, “High” – intercepted data that can be used to get account management).
HTTPS — interception of data transmitted inside the encrypted connection (“+” – possible, “-” not possible).
Messages — access to user messages by using root rights (“+” – possible, “-” not possible).
TOKEN — possibility to steal authentication token by using root rights (“+” – possible, “-” not possible).
As you can see from the table, some apps practically do not protect users’ personal information. However, overall, things could be worse, even with the proviso that in practice we didn’t study too closely the possibility of locating specific users of the services. Of course, we are not going to discourage people from using dating apps, but we would like to give some recommendations on how to use them more safely. First, our universal advice is to avoid public Wi-Fi access points, especially those that are not protected by a password, use a VPN, and install a security solution on your smartphone that can detect malware. These are all very relevant for the situation in question and help prevent the theft of personal information. Secondly, do not specify your place of work, or any other information that could identify you. Safe dating!