Tales from the blockchain
2.11.2017 Kaspersky Cyber
Cryptocurrency has gradually evolved from an element of a new world, utopian economy to a business that has affected even those sectors of society least involved in information technology. At the same time, it has acquired a fair number of “undesirable” supporters who aim to enrich themselves at the expense of other users: attackers who release miners embedded in user JS scripts, or plan to implement miners into IoT devices at the production stage; hidden in countless variations of Trojans in conjunction with SMB exploits etc.
We will tell you two unusual success stories that happened on the “miner front”. The first story echoes the TinyNuke event and, in many respects gives an idea of the situation with miners. The second one proves that to get crypto-currency, you don’t need to “burn” the processor.
DiscordiaMiner and fights on forums
In early June, our analysts found a new and seemingly unremarkable Trojan that unloaded the miner of the popular Montero crypto-currency. However, in the course of further research, we uncovered many interesting details that we would like to share with you.
Kaspersky Lab products detect this Trojan as Trojan.Win32.DiscordiaMiner. It works as follows:
Creates a number of directories in the system to download the necessary files;
Copies itself in C:\ProgramData\MicrosoftCorporation\Windows\SystemData\Isass.exe;
Gets the update from the server;
Creates an autorun task;
Gets the miner files;
Gets the credentials of the user in whose name it wants to run the mining;
Starts the miner.
All interaction with the command server (C&C) occurs in the open, with the help of GET requests, without any check or verification. In all samples, the hxxp://api[.]boosting[.]online address is provided as the C&C. The line associated with the individual user (etc. MTn31JMWIT) and the address of the required resource – the list of files, the update, etc. – are added to the server address. Example: hxxp://api[.]boosting[.]online/MTn31JMWIT/getDiscordia
Discord on the forum
As mentioned above, at a certain point in its work, the Trojan is instructed to issue a command to run the miner: it specifies the email of the user who has “done the job”. It looks like this:
-user <user_email> -xmr
Using the value of the <user_email> argument, with the first line of the search results we get the Trojan-related topic on the Russian-language forum:
On this forum thread there is a wide discussion of the Trojan’s work details. The most interesting part of the discussion is on page 21 – the forum participants accuse the Trojan’s author of substituting users’ addresses with his own. Among other things, there is also a dialogue on the chat app, Telegram where the author explains this substitution as a banal mistake.
On the forum, the author of DiscordiaMiner references the short lifespan of this error as an argument in his defense:
He also mentions the figure of 200,000 infected machines. It is difficult to say how true this is. However, in the malware samples we received, the email that the “prosecutor” refers to is often named. Examples of other addresses: ilya-soro*****12@mail.ru, v*****re@gmail.com, topne*****arin@gmail.com, J ***** m @ yandex.ru, steamfa*****aunt1@mail.ru, me*****ook@gmail.com, x*****z@yandex.ru, piedmont ***** lines @ yahoo. com.
Among other things, in the course of the dispute the author mentions that the source codes of the Trojan DiscordiaMiner are now publicly available.
Indeed, the first line of the search results provides the link to the author’s repository.
In addition to the source codes, which really do coincide fully with the restored Trojan code, the repository also includes very informative diagrams of the Trojan’s operation, the samples of documents used for distribution as well as instructions for how exactly the UAC is to be bypassed. The pictures below are taken from the repository (which is currently unavailable).
The source codes are presented in full and, apparently, only the user-associated string (ClientID) varies from assembly to assembly.
Although the “dumping” of program source code is not unique, this case in many respects echoes the NukeBot story – the same disputes on a forum followed by the publication of the source codes by the author with the aim of “protecting honor and dignity”. Another common feature is the “minimalistic” design of both Trojans: NukeBot could only embed web-based injections into the browser, while DiscordiaMiner can download and run files from a remote server. But we cannot say whether these two bots have any more specific connections.
MD5
00B35FB5C534DEA3EA13C8BE4E4585CC
083FD078FECFE156B17A50F73666B43E
0AB8E9C539554CBA532DFC5BC5E10F77
377B9C329EBF7ACFE7DABA55A0E90E98
48E6714A486B67D237B07A7CF586B765
4BD80738059B5D34837633692F18EA08
4E79B826AE4EC544481784EF77E05DE4
4EF5A04A56004AA93167F31296CCACF7
539B092C176183EDCA6A69421B62BCE8
5F8E4CF0971B543525CA807B6A2EC73F
65CF0CC192E69EA54373758C130A983F
7F65252701C80F8D4C1484EE06597DF0
80B04BBC2F18E3FE4625C3E060DA5465
CryptoShuffler
It’s extremely rare for authors of mining software to become fabulously wealthy. With a few exceptions, the wallets used by attackers contain a total of $50-100, received from all incoming transfers during the entire period of the Trojan’s work. However, there are those that do not go down the beaten path, and benefit from “alternative” ways. The authors of the CryptoShuffler Trojan belong in this category.
Kaspersky Lab products detect this Trojan as Trojan-Banker.Win32.CryptoShuffler.gen. MD5 of the file in question is 0ad946c351af8b53eac06c9b8526f8e4
The key feature of CryptoShuffler is the following: instead of wasting processor time on mining, the Trojan simply substitutes the sender’s address in the clipboard! That was once the case with WebMoney and Bitcoin, but this malware sample is aimed at all popular cryptocurrencies.
As usually happens in the beginning, the Trojan writes itself into the registry for autoloading.
In later versions of the Trojan, this procedure is slightly different – if the module is implemented as a dynamically loaded library, its further run at the start is performed using the rundll32 system utility. The name of the called procedure and, concurrently, the main function of the represented library is call_directx_9.
The Trojan creates a thread of execution, in which it maintains unchanged the autorun branch specified in the screenshot above.
The substitution itself is performed using the API binding functions OpenClipboard \ GetClipboardData \ SetClipboardData
The search for the corresponding wallet in the string received from the clipboard is performed using regular expressions. Most popular cryptocurrency wallets have a fixed constant at the beginning of the string and a certain length – it is easy to create regular expressions for them. For example, the address of Bitcoin-wallets can be easily recognized by the digit “1” or “3” at the beginning of the string.
The body of the Trojan stores the wallets, corresponding to the specified cryptocurrencies. The main list looks like this.
WALLET Currency name
1v9UCfygQf3toN1vA5xyr7LhKmv9QWcwZ BITCOIN
D7uMywpgSyvy9J2RkyQ2oozT4xTmSSWGgR DOGECOIN
LeHrMiPzEUtJen73T5P1bVG2tG8PerzFR1 LITECOIN
Xv4M3y36iu6Fc5ikk8XuQBDFMtRz2xFXKm DASH
0xfb25b3d5ae0d6866da17c4de253ce439b71d0903 ETHEREUM
4ZFYNck6mZfG52RMdWThJEXq4Sjdszf719 MONERO
N6VeTbNiFG1oapzPZmeLLkkNC55FQGMTgr ???
t1VVkuasB7pNHPES2ei6LCqP1hZWb5rfPrB ZCASH
PM44dh7LNEjThgmscw8t5rb9LZqEPc2Upg ???
The biggest profit reaches the cybercriminals’ pockets from the users of Bitcoin wallets – at the time of writing, there were ~ 23 BTC on the balance of their wallet, which at the end of October amounted to approximately $140,000. The amounts in the remaining wallets range from tens to thousands of US dollars.
The malware described is a perfect example of a “rational” gain. The scheme of its operation is simple and effective: no access to pools, no network interaction, and no suspicious processor load.
MD5
095536CA531AE11A218789CF297E71ED
14461D5EA29B26BB88ABF79A36C1E449
1A05F51212DEA00C15B61E9C7B7E647B
1E785429526CC2621BAF8BB05ED17D86
2028383D63244013AA2F9366211E8682
25BF6A132AAE35A9D99E23794A41765F
39569EF2C295D1392C3BC53E70BCF158
50E52DBF0E78FCDDBC42657ED0661A3E
6EB7202BB156E6D90D4931054F9E3439
7AE273CD2243C4AFCC52FDA6BF1C2833
7EC256D0470B0755C952DB122C6BDD0B
80DF8640893E2D7CCD6F66FFF6216016
AA46F95F25C764A96F0FB3C75E1159F8
B7ADC8699CDC02D0AB2D1BB8BE1847F4
D45B0A257F8A0710C7B27980DE22616E
D9A2CD869152F24B1A5294A1C82B7E85
Automated System Defeats reCAPTCHA With High Accuracy
2.11.2017 securityaffairs IT
A newly devised system that targets the audio version of Google’s reCAPTCHA challenges can break them with very high accuracy.
Dubbed unCAPTCHA, the automated system designed by computer science experts from the University of Maryland (UM) is said to be able to defeat the audio reCaptcha system with 85% accuracy.
The system uses browser automation software to interact with the target site and engage with the captcha. The tool, which has been published on GitHub, can properly identify spoken numbers to pass the reCaptcha programmatically and trick the site into thinking their bot is a human, the authors claim.
“Specifically, unCaptcha targets the popular site Reddit by going through the motions of creating a new user, although unCaptcha stops before creating the user to mitigate the impact on Reddit,” the experts say.
To correctly bypass the captcha, which includes numbers that are read aloud at varied speeds, pitches, and accents through background noise, the attack identifies the audio message on the page, downloads it, and then automatically splits it by locations of speech.
Next, each number audio bit is uploaded to 6 different online audio transcription services that are free to use, namely IBM, Google Cloud, Google Speech Recognition, Sphinx, Wit-AI, and Bing Speech Recognition, and the results are collected.
“We ensemble the results from each of these to probabilistically enumerate the most likely string of numbers with a predetermined heuristic. These numbers are then organically typed into the captcha, and the captcha is completed. From testing, we have seen 92%+ accuracy in individual number identification, and 85%+ accuracy in defeating the audio captcha in its entirety,” the system’s authors reveal.
Another recently revealed tool for defeating CAPTCHA systems is targeting text-based systems and was designed to mimic the human eye. Called the Recursive Cortical Network (RCN), it incorporates neuroscience insights into a structured probabilistic generative model framework.
In a paper (PDF), the team of researchers behind RCN explain that the tool is capable of solving Google reCAPTCHA with a 66.6% accuracy, but that it is also highly efficient against other systems: 64.4% for BotDetect, 57.4% for Yahoo, and 57.1% for PayPal image challenges. The findings were published in the Science magazine.
“By drawing inspiration from systems neuroscience, we introduce a probabilistic generative model for vision in which message-passing based inference handles recognition, segmentation and reasoning in a unified way. The model demonstrates excellent generalization and occlusion-reasoning capabilities, and outperforms deep neural networks on a challenging scene text recognition benchmark while being 300-fold more data efficient,” the researchers say.
Smartphone Exploits Earn Hackers Over $500,000
2.11.2017 securityaffairs Congress
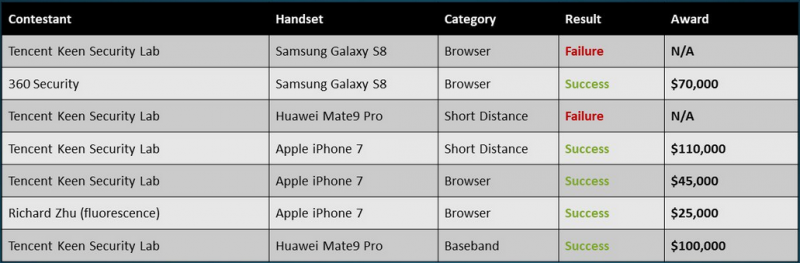
White hat hackers earned more than half a million dollars at this year’s Mobile Pwn2Own competition after successfully demonstrating exploits against Samsung’s Galaxy S8, Apple’s iPhone 7 and Huawei’s Mate 9 Pro.
The hacking contest, organized by Trend Micro’s Zero Day Initiative (ZDI) at the PacSec conference in Tokyo, Japan, offered more than $500,000 for exploit chains targeting browsers, short distance communications (Wi-Fi, Bluetooth and NFC), messaging, and baseband components in the Google Pixel, Galaxy S8, iPhone 7 and Mate 9 Pro.
All devices had been running the latest versions of the software and operating systems – Apple, Google and Huawei released patches the night before the event started.
On the first day, participants earned a total of $350,000 for disclosing vulnerabilities that allow attacks against Internet Browser on the Galaxy S8, Safari on the iPhone 7, Wi-Fi on the iPhone 7, and the baseband on the Mate 9 Pro.
On the second day, MWR Labs earned $25,000 for hacking Google Chrome of the Mate 9 Pro via 5 logic bugs in Huawei apps that allowed a browser sandbox escape and data exfiltration.
The same team took home an additional $25,000 after exploiting 11 flaws across six different apps to hack Internet Browser on the Galaxy S8. The exploit resulted in arbitrary code execution and sensitive data leakage.
A researcher from China-based Qihoo 360 earned $20,000 for a partially successful exploit targeting the iPhone 7’s Wi-Fi component. The exploit worked properly, but one of the three vulnerabilities it leveraged had been previously disclosed at Pwn2Own by a different contestant. The same Chinese expert was awarded another $25,000 for hacking Safari on the iPhone 7.
The last entry came from the researcher Amat Cama (aka Acez), who earned $50,000 for a baseband exploit targeting the Galaxy S8. The exploit relied on a stack-based buffer overflow that allowed arbitrary code execution.
The total amount of money paid to researchers over the course of two days at Mobile Pwn2Own 2017 was $495,000. The Tencent Keen Security Lab team got the highest number of Master of Pwn points, which also earned them 65,000 ZDI reward points, worth roughly $25,000.

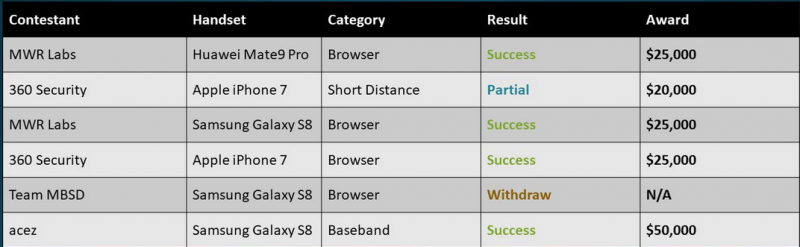
While one successful entry did target the Chrome browser, no one has attempted to demonstrate an exploit on Google’s Pixel phone.
Affected vendors have been provided the details of the vulnerabilities used at the event and ZDI will give them 90 days to release fixes before a limited advisory describing the flaws will be made public.
D-Link MEA Site Caught Running Cryptocurrency Mining Script—Or Was It Hacked?
2.11.2017 thehackernews CyberCrime
Last month the popular torrent website The Pirate Bay caused some uproar by adding a Javascript-based cryptocurrency miner to its site with no opt-out option, utilizing visitors' CPU power to mine Monero coins in an attempt to gain an extra source of revenue.
Now D-Link has been caught doing the same, although there's high chance that its website has been hacked.
D-Link's official website for Middle East (www.dlinkmea.com) has been found secretly adding a JavaScript-based cryptocurrency miner, according to a blog post published by security firm Seekurity on Tuesday.
Seekurity team was made aware of the issue after Facebook user Ahmed Samir reported that visiting on D-Link Middle East website caused his web browser utilizing a "super high CPU" power usage.
As shown in the screenshot below, a separate domain was loaded using a hidden iFrame for each page view, which included the cryptocurrency mining script.
Five days after Seekurity team reported the issue to D-Link, the company took down the website and redirected it to D-Link USA website (us.dlink.com), without responding to the security firm.
Since the company redirected the whole website to another domain instead of just removing a single line of hidden iFrame code, there are high chances that D-Link has recently been a victim of cyber attack.
Anyways, cryptocurrency mining has become a competitive revenue stream these days, and it is trending among hackers as well.
So, it would be no surprise if hackers compromise popular websites and embed their cryptocurrency miners to harness visitor's system computing power in an attempt to mine digital coins.
Just yesterday it was reported that more than 200 of the top 100,000 websites on the web were found hosting suspicious code from CoinHive and JSEcoin, two popular cryptocurrency mining services, forcing their visitors to run miner code on their computers unknowingly.
If you are using a good antivirus solution, like Malwarebytes and Kaspersky, then you are protected, as most security solutions have already started blocking cryptocurrency mining scripts to prevent their customers from unauthorized mining and extensive CPU usage.
Microsoft Engineer Installs Google Chrome Mid-Presentation After Edge Kept Crashing
2.11.2017 thehackernews Safety
Ever since the launch of Windows 10, Microsoft has been heavily pushing its Edge browser, claiming it to be the best web browser over its competitors like Mozilla Firefox, Opera and Google Chrome in terms of speed and battery performance.
However, Microsoft must admit that most users make use of Edge or Internet Explorer only to download Chrome, which is by far the world's most popular internet browser.
Something hilarious happened recently during a live demonstration when a Microsoft engineer caught on a video switching from Edge to Chrome after the default Windows 10 browser stopped responding in the middle of the presentation.
That is really embarrassing.
The incident happened in the middle of a Microsoft Ignite conference, where the Microsoft presenter Michael Leworthy was demonstrating how to one can migrate their applications and data to Microsoft Azure cloud service.
See what happens in the video below:
However, Leworthy was forced to pause his Azure presentation in the middle of live demo session to download and install Google's Chrome because the company's Edge browser kept on crashing.
Guess what? This somewhat embarrassing and somewhat hilarious incident was recorded and uploaded to YouTube by Microsoft itself. You can check out the video yourself.
"I love it when demos break," Leworthy said. "So while we’re talking here, I’m gonna go install Chrome," he continued and started laughing, with many people in the audience giggling and cheering.
"And we're not going to make Google better," Leworthy added as he refused to check the box that sends crash reports and statistics back to Google.
Although Internet Explorer has long been considered to be "the best browser to download Google Chrome," Microsoft Edge came out to be a competent successor to do the same thing even faster, as Leworthy took less than a minute to download and install Chrome.
2014 Data Breach – 46.2 Million Malaysian Mobile phone numbers leaked online
2.11.2017 securityaffairs CyberCrime
46.2 Million Malaysian Mobile phone numbers leaked online, authorities confirmed data were stolen from government servers and databases at a dozen telcos.
Millions of Malaysians have been affected by a major data breach, hackers have accessed 46.2 million cellphone accounts after they broke into government servers and databases at a dozen telcos in the country.
Considering that the population of Malaysia is 31.2 million, virtually everyone in the country was affected by the data breach at the Malaysians telecoms providers such as DiGi.Com and Celcom Axiata.
The stolen records include users’ mobile phone numbers, SIM card details, device serial numbers, and home addresses. The hackers also accessed some 80,000 medical records and compromised government websites such as Jobstreet.com.
The Malaysian Communications and Multimedia Commission, along with the police, are investigating the incident.
The news was first reported by the Malaysian news site lowyat.net on 19th October:
“The leak includes postpaid and prepaid numbers, customer details, addresses as well as sim card information – including unique IMEI and IMSI numbers.” reported the website.
“Time stamps on the files we downloaded indicate the leaked data was last updated between May and July 2014 between the various telcos. The exact numbers, broken down by telco/MVNO provider, and further broken down by prepaid or postpaid segments are as below.”
Telco/MVNO | Total Records | Last Updated |
|
|
|
Celcom Prepaid | 10,548,183 | 03-06-2014 |
Celcom Postpaid | 4,194,315 | 03-06-2014 |
Digi Prepaid | 11,411,815 | 30-05-2014 |
Digi Postpaid | 2,036,730 | 30-05-2014 |
Umobile postpaid + prepaid | 3,866,672 | 30-05-2014 |
Maxis Postpaid | 2,840,741 | 29-07-2014 |
Maxis Hotlink | 9,562,019 | 29-07-2014 |
Friendi Mobile | 43,523 | 29-06-2014 |
MerchantradeAsia | 446,203 | 07-07-2014 |
Tunetalk | 597,276 | unknown |
Redtone | 246,613 | 30-05-2014 |
XOX | 79,139 | 30-05-2014 |
Altel | 24,279 | unknown |
PLDT | 68,900 | 17-07-2014 |
EnablingAsia | 212,139 | 30-04-2014 |
|
|
|
Total | 46,178,547 |
|
According to Malaysian officials, nearly 50 million mobile phone account records were accessed by hackers.

Source Lowyat.net
Aside from the telco database, the authorities confirmed that 3 databases belonging to the Malaysian Medical Council (MMC), the Malaysian Medical Association (MMA), as well as the Malaysian Dental Association (MDA) have also been leaked.
Database | Total Records | Last Updated |
|
|
|
Malaysian Medical Association (MMA) | 15,965 | 05-02-2015 |
Malaysian Medical Council (MMC) | 61,062 | 06-03-2015 |
Malaysian Dental Association (MDA) | 4,282 | 25-01-2015 |
|
|
|
Total | 81,309 |
|
The compromised medical databases include personal information, MyKad numbers, mobile/work/home phone numbers, and work and residential addresses.
The website that reported the news is concerned that no remedial action has been taken by the service providers involved to protect the victims of the data breach.
“While it is the task of the authorities to narrow down the source of the breach, and ensure that a similar incident doesn’t happen again, the key to containing any more serious damage is protecting the individuals affected by the breach.” continues lowyat.net.
“We are urging the telco and MVNO companies mentioned above to alert and start immediately replacing the SIM cards of all affected customers, especially those who have not updated their SIM cards since 2014. While the leaked data alone isn’t sufficient to clone the SIM cards, the information available can be exploited to initiate multiple social engineering attacks against affected users.”
WordPress releases the version 4.8.3 to address a serious SQL Injection vulnerability
2.11.2017 securityaffairs Vulnerebility
WordPress developers fixed a serious SQL injection vulnerability on Tuesday with the release of version 4.8.3.. Apply it as soon as possible.
WordPress developers fixed a serious SQL injection vulnerability that was reported by the researcher Anthony Ferrara, VP of engineering at Lingo Live.
The issue was addressed on Tuesday with the release of version 4.8.3.
The vulnerability can be exploited via WordPress plugins and themes, an attacker can take over vulnerable websites by powering an SQL injection attack.
The new security release implemented hardening mechanisms to the WordPress code to prevent attacks.
“WordPress versions 4.8.2 and earlier are affected by an issue where $wpdb->prepare() can create unexpected and unsafe queries leading to potential SQL injection (SQLi). WordPress core is not directly vulnerable to this issue, but we’ve added hardening to prevent plugins and themes from accidentally causing a vulnerability. Reported by Anthony Ferrara.” read the description provided by WordPress.
The problem is linked to a SQL injection vulnerability discovered a few months ago by a researcher who goes online with the moniker “Slavco.” The issue was addressed with the release of WordPress 4.8.2 in September, but the fix introduced by the development team broke many websites. Furthermore, shortly after the patch was released, Ferrara, discovered that the latest release did not fix the vulnerability.

The WordPress security team took roughly 6 weeks to fix the problem and create a proper patch.
The researcher criticized the speed in approaching the issue by the WordPress security team, initially, he also planned on disclosing the details of the flaw without a concrete response from the organization.
Once established a contact, the things went better.
“It took literally 5 weeks to even get someone to consider the actual vulnerability. From there, it took me publicly threatening Full Disclosure to get the team to acknowledge the full scope of the issue (though they did start to engage deeper prior to the FD threat).
Once the issue was understood, we got to a really good place. If the entire interaction was like Oct 27 – Oct 31, I would have been ecstatic. Even if on a different time-line (the good part wasn’t the speed of the replies, but the content of the conversation).” explained Ferrara.
“Security reports should be treated “promptly”, but that doesn’t mean every second counts (usually). I get that there are competing priorities. But show attention. Show that you’ve read what’s written. And if someone tells you it seems like you don’t understand something, stop and get clarification.”
“It took literally 5 weeks to even get someone to consider the actual vulnerability. From there, it took me publicly threatening Full Disclosure to get the team to acknowledge the full scope of the issue (though they did start to engage deeper prior to the FD threat),” Ferrara said in a blog post.
“Security reports should be treated ‘promptly’, but that doesn’t mean every second counts (usually). I get that there are competing priorities. But show attention. Show that you’ve read what’s written. And if someone tells you it seems like you don’t understand something, stop and get clarification,”
Hurry Up, update your installations as soon as possible.
Silence Group is borrowing Carbanak TTPs in ongoing bank attacks
2.11.2017 securityaffairs Virus
A cybercrime gang called Silence targeted at least 10 banks in Russia, Armenia, and Malaysia borrowing hacking techniques from the Carbanak group.
A cybercrime gang called Silence targeted at least 10 banks in Russia, Armenia, and Malaysia borrowing hacking techniques from the dreaded Carbanak hacker group that stole as much as $1 billion from banks worldwide.
The Silence gang was uncovered by researchers at Kaspersky Lab who speculate it is imitating the notorious Carbanak group.
“In September 2017, we discovered a new targeted attack on financial institutions. Victims are mostly Russian banks but we also found infected organizations in Malaysia and Armenia. The attackers were using a known but still very effective technique for cybercriminals looking to make money: gaining persistent access to an internal banking network for a long period of time, making video recordings of the day to day activity on bank employees’ PCs, learning how things works in their target banks, what software is being used, and then using that knowledge to steal as much money as possible when ready.” states the report published by Kaspersky.
“We saw that technique before in Carbanak, and other similar cases worldwide.”
The attackers leverage spear-phishing emails with a malicious attachment, the experts pointed out that the Silence group first compromised banking infrastructure in order to send the messages from the addresses of bank employees.
At the time, experts from Kaspersky have no information on how much the Silence group had stolen to date, they confirmed the attacks are still ongoing.
The hackers use legitimate administration tools to fly under the radar making hard the detection of the fraudulent activities.
“This kind of attack has become widespread in recent years, which is a very worrisome trend as it demonstrates that criminals are successful in their attacks.” states Kaspersky Lab.
“The spear-phishing infection vector is still the most popular way to initiate targeted campaigns. When used with already compromised infrastructure, and combined with .chm attachments, it seems to be a really effective way of spreading, at least among financial organizations.”

The group used backdoors to gain persistence on the targeted banks and monitor operations of its employees, the malicious code allows them to upload data, steal credentials, record the screen like the Carbanak does.
Screen grabs allow cyber criminals to create a video recording of daily activity on employees’ computers, such kind of information is essential for the cyber heists.
The experts discovered the hackers leverage a proprietary Microsoft online help format called Microsoft Compiled HTML Help (CHM) because CHM files are interactive and can run JavaScript.
“These files are highly interactive and can run a series of technologies including JavaScript, which can redirect a victim towards an external URL after simply opening the CHM. Attackers began exploiting CHM files to automatically run malicious payloads once the file is accessed.” Kaspersky Lab said.
“Once the attachment is opened by the victim, the embedded .htm content file (“start.htm”) is executed. This file contains JavaScript, and its goal is to download and execute another stage from a hardcoded URL”
Once the dropper is unpacked and executed from the C&C, a number of payload modules are dropped that allow the attackers to spy on the internal staff of the targeted banks.
One of those modules is the screen monitor, which leveraged the Windows GDI and API tools to create a pseudo-video stream of the victim’s activity by putting together all the collected bitmaps.
Further details are available in the report, including Indicators of Compromise.
Kaspersky will continue to monitor the Silence Group.
Facebook’s Zuckerberg Says Security Costs Will Hurt Profits
2.11.2017 securityweek Social
Facebook Chief Says Protecting Community is More Important Than Maximizing Profits
Social media giant Facebook said on Wednesday that significant investments by the company to secure its platform will impact its profitability.
The company announced its financial results for Q3 2017 after the bell on Wednesday, noting that capital expenditures for quarter were $1.76 billion. The company reported more than $10.3 billion in revenue during the quarter, and a profit of $4.7 billion.
Facebook Security"Our community continues to grow and our business is doing well," Mark Zuckerberg, Facebook founder and CEO, said in a statement. "But none of that matters if our services are used in ways that don't bring people closer together. We're serious about preventing abuse on our platforms. We're investing so much in security that it will impact our profitability. Protecting our community is more important than maximizing our profits."
33 year-old Zuckerberg did not detail any planned security investments or estimated costs.
The company has been under scrutiny over Russia-linked buyers who placed thousands of ads on the site in attempt to influence the U.S. presidential election.
Facebook’s security group is led by Chief Security Officer (CSO) Alex Stamos, who took the role in June 2015 after serving as CISO at Yahoo. Stamos replaced former CSO Joe Sullivan who left the social media giant in April to take the role of CSO at Uber.
In June, Facebook announced the roll-out of a redesigned security settings page, designed to make it easier for users to understand the options provided to them.
In October 2016, the company said that it had paid out a total of more than $5 million (at the time) to researchers who have helped the company find and patch vulnerabilities in its systems and products.
The company had an employee headcount of more than 23,000 as of September 30, 2017, an increase of 47% year-over-year.
DigiCert Addresses Mozilla's Concerns on Symantec CA Acquisition
2.11.2017 securityweek Safety
DigiCert has addressed the concerns raised by Mozilla and others regarding the company’s acquisition of Symantec’s certificate business after some web browser vendors announced that certificates issued by the security firm would no longer be trusted.
DigiCert has acquired Symantec’s website security and related public key infrastructure (PKI) solutions for $950 million in cash and a stake of roughly 30 percent in common stock equity. The acquisition was completed this week.
Mozilla and Google have decided to take action against Symantec after the company and its partners were involved in several incidents involving mississued TLS certificates. The web browser vendors want all existing certificates to be replaced within a year using a third-party’s infrastructure.
Symantec’s decision to sell its certificate business has left many wondering if this is part of a strategy to mitigate the penalties imposed by Google and Mozilla. Mozilla is concerned that despite the new certificates being issued under DigiCert’s name, Symantec management, personnel and infrastructure may still be involved to a great extent in the process of issuing certificates.
Jeremy Rowley, Executive VP of Product at DigiCert, on Tuesday responded to each of Mozilla’s concerns and provided some details about the company’s plans going forward.
Rowley said DigiCert will start validating and issuing all certificates requested through Symantec on December 1. While the company will still use Symantec’s front-end systems and hardware, TLS certificate validation and issuing will not be done through the old infrastructure.
DigiCert also plans on training Symantec validation and operation personnel, and while some managers from the security firm will remain on board, Rowley said DigiCert’s existing management team will oversee the transition.
Mozilla says it’s also concerned that Symantec’s processes might displace DigiCert’s processes.
“What we really hope to do is learn from both DigiCert’s and Symantec’s process to create something new during the transition that is better than either one alone. The integration between the two companies is a perfect time to look at how both companies can improve and implement something more secure and customer friendly,” Rowley said. “We have some good ideas on what to do, and I can’t wait to see them implemented in practice. From workflows to tools, I think the combination of DigiCert’s culture and Symantec’s manpower will let us move into some interesting and exciting areas.”
DigiCert competitor Comodo, whose CA business has been sold to private equity firm Francisco Partners, warned Symantec customers that DigiCert’s smaller infrastructure would not stand up to the task. However, Rowley pointed out that DigiCert has been working on scaling its infrastructure for the past two years – long before it decided to acquire Symantec’s CA – as it had been preparing for the increasing demand for certificates introduced by the Internet of Things (IoT).
On the other hand, some have raised concerns over Comodo CA’s acquisition by Francisco Partners, a company whose portfolio includes several surveillance-focused firms, considering that digital certificates are highly valuable assets for online surveillance purposes.
Website Blindspots Show GDPR is a Global Game Changer
2.11.2017 securityweek Privacy
One of the less publicized features of the European General Data Protection Regulation (GDPR) is that US companies can be held liable even if they do not actively trade with Europe. This is because the regulation is about the collection and storage of European personal information, not about business.
Any U.S. company that operates a website that collects user information (a log-in form, or perhaps a subscription application) could unwittingly collect protected European PII. That makes the company liable -- there are GDPR requirements over how it is collected (including explicit user consent, secure collection, and limitations on what is collected). Whether European regulators could do anything about that liability if the US company has no physical presence in Europe is a different matter.
Nevertheless, this highlights an area that is not well covered by many of the reports that warn about GDPR, that highlight the lack of business preparedness, and that offer solutions. IT and security teams are usually more aware of where data is stored and how it is processed than they are about where and how it is collected.
Research from RiskIQ published in June 2017 showed the potential extent of this blind-spot -- even with European organizations. The research found that 34% of all public web pages of FTSE 30 companies capturing personally identifiable information (PII) are in danger of violating GDPR by doing so insecurely.
It further found that these organizations have an average of 3,315 live websites; and that from these websites there is an average of 440 pages that collect PII per company. Thirty-four percent of these are insecure; 29% do not use encryption; and 3.5% are using old, vulnerable encryption algorithms.
It is even worse in the U.S. RiskIQ researched 25 of the 50 largest U.S. banks and found a per-organization average of 1,891 insecure login forms; 1,663 pages collecting PII insecurely; 1,326 EU first-party cookie violations; and 1,265 EU third-party cookie violations.
"GDPR is a global game changer that will pull the rest of the world toward setting a higher bar for protecting PII," comments Jarad Carleton, principal consultant, Digital Transformation, Frost & Sullivan Cybersecurity Practice. "However, to be compliant, you first need to know where PII is being collected, so proper process controls can be put around that data."
The problem is so extensive for larger organizations, that with little over six months to go, compliance in this area will be difficult to achieve.
"PII discovery, inventory, and compliance assessment is one of the major tasks for GDPR project teams," warns Lou Manousos, CEO of RiskIQ. "In our experience, most security and compliance teams have only partial visibility of the websites owned by their organization. They are left to engage users across the business in an effort to uncover them. And once they have compiled that list, inspecting tens of thousands of web pages is labor intensive and prone to error."
The solution will require some degree of automation -- and to that end RiskIQ has this week announced the addition of explicit GDPR compliance functionality to its Digital Footprint product.
RiskIQ Digital Footprint's new PII/GDPR analytics feature, says the company, helps expedite compliance during the initial and subsequent GDPR audit processes by actively identifying websites belonging to an organization, as well as highlighting issues with specific pages that collect PII. GDPR, coming into effect in May of 2018, applies to all organizations that actively engage with EU citizens -- even if they have no physical presence in the EU.
The product discovers, creates and assesses an interactive inventory of public-facing web assets. It highlights the pages that collect personal information through login forms, data collection forms, and persistent cookies. In short, it automates the process of finding GDPR web-based violations to enable more rapid and complete violation remediation.
"The new PII/GDPR analytics feature in RiskIQ Digital Footprint automates the once cumbersome and often inaccurate process of ongoing website PII discovery and assessment, helping to more efficiently support compliance obligations for large enterprises and multinational organizations," says Carleton.
RiskIQ's PII/GDPR analytics feature is immediately available and is included as part of its Digital Footprint Enterprise solution.
San Francisco, Calif.-based RiskIQ raised $30.5 million in Series C funding led by Georgian Partners in November 2016, bringing the total raised by the firm to $65 million.
Hilton Reaches $700,000 Settlement Over Data Breaches
2.11.2017 securityweek Incindent
U.S. hotel chain Hilton has reached a settlement with the states of New York and Vermont over the payment card breaches suffered by the company in 2014 and 2015.
Hilton has agreed to pay $700,000 – $400,000 to New York and $300,000 to Vermont – and promised to take steps to improve its data security and breach disclosure practices.
The Attorneys General of New York and Vermont launched an investigation into two separate security incidents reported by Hilton back in 2015. The hotel chain determined at the time that attackers had accessed information on at least 363,000 credit cards.
The first intrusion was discovered on February 10, 2015, when a computer services provider informed Hilton of suspicious traffic from one of its systems. An investigation revealed that malware designed to steal payment card data had been active on the company’s systems between November 18 and December 5, 2014.
In the second intrusion, discovered in July 2015, attackers used a piece of malware to collect more than 363,000 payment card numbers between April 21 and July 27, 2015. Investigators discovered the data in a file that had been prepared for exfiltration.
However, Hilton only informed customers about the breaches in November 2015, more than 9 months after the first intrusion was discovered. Hilton argued that there had been no evidence that the payment card data was actually exfiltrated by the attackers, but investigators were unable to review all logs due to steps taken by the cybercriminals to cover their tracks.
Authorities were displeased with the fact that it took the company so long to alert customers. In accordance with New York’s General Business Law, organizations must disclose data breaches in the “most expedient time possible and without unreasonable delay,” which Hilton did not do.
The investigation conducted by the Vermont and New York Attorneys General also revealed that Hilton had not been in compliance with certain requirements of the Payment Card Industry Data Security Standard (PCI DSS).
Authorities also determined that Hilton broke laws prohibiting deceptive acts and practices by telling customers that their personal information was protected using reasonable data security mechanisms.
As part of the settlement, in addition to paying $700,000, Hilton has agreed to notify consumers faster in case of future incidents, create and maintain a comprehensive data security program, and perform annual assessments for PCI DSS compliance.
Hilton is just one of the many hotel chains that suffered payment card breaches in the past few years. The list also includes Hyatt, Trump, Millennium, InterContinental, Omni, Mandarin Oriental, and Kimpton hotels.
Standalone Signal Desktop Messaging App Released
2.11.2017 securityweek Privacy
Signal, a popular secure messaging application, is now available for Windows, macOS, and Linux computers as a standalone program.
Developed by Open Whisper Systems, Signal provides users with end-to-end encrypted messaging functionality and is already used by millions of privacy-focused Android and iOS users. The server doesn’t have access to users’ communication and no data is stored on it, thus better keeping all conversations safe from eavesdropping.
The first Signal for desktop application was released in December 2015 in the form of a Chrome application that could provide users with the same features as the mobile software, namely end-to-end encryption, free private group, text, picture, and video messaging.
Now, the company has decided to make Signal Desktop available as a standalone application and to retire the Chrome app.
The standalone application was released with support for the 64-bit versions of Windows 7, 8, 8.1, and 10, for macOS 10.9 and above, and Linux distributions supporting APT, such as Ubuntu or Debian.
Using Signal Desktop requires pairing it with a phone first. People who have been using the Signal Desktop Chrome App can export their data and import it into the new Signal Desktop app as part of the setup process. Thus, users will be able to access all of their old conversations and contacts.
The standalone Signal Desktop application can be downloaded directly from the official website.
In late September, Open Whisper Systems revealed plans of a new private contact discovery service for Signal. The goal is to prevent anyone using modified Signal code to log the process of contact discovery the application performs when first installed, in order to determine which of one’s contacts also use the service.
In December 2016, after learning that ISPs in Egypt and the United Arab Emirates started blocking the Signal service and website, Open Whisper Systems announced a new feature for its Android application meant to bypass censorship. The technique they used is called domain fronting and relies on the use of different domain names at different layers of communication.
Windows 10 Exploit Guard Boosts Endpoint Defenses
2.11.2017 securityweek Vulnerebility
Courtesy of the Windows Defender Exploit Guard that ships with Windows 10 Fall Creators Update, systems running Microsoft’s Windows 10 operating system can fend off emerging threats, Microsoft says.
In June this year, Microsoft revealed that Windows Defender Exploit Guard will make the Enhanced Mitigation Experience Toolkit (EMET) native to Windows 10, and that it would also provide users with additional vulnerability mitigations.
Taking advantage of Microsoft Intelligent Security Graph (ISG), the Exploit Guard was designed to protect organizations from advanced threats, including zero day exploits. The tool contains four components: Attack Surface Reduction, Network protection, Controlled folder access, and Exploit protection.
Attack Surface Reduction (ASR), which is inherited from EMET, is a set of controls providing enterprises with protection from getting infected with malware by blocking Office-, script-, and email-based threats. ASR, Microsoft claims, can block the underlying behavior of malicious documents (such as Office files with malicious macros or malware-laden emails attachments) without hindering productive scenarios.
“By blocking malicious behaviors independent of what the threat or exploit is, ASR can protect enterprises from never before seen zero-day attacks like the recently discovered CVE-2017-8759, CVE-2017-11292, and CVE-2017-11826,” the company says.
When it comes to Office apps, ASR can block them from creating executable content, from launching child processes, and from injecting into processes, but can also block Win32 imports from macro code in Office and prevent obfuscated macro code from executing.
It can also block JavaScript, VBScript, and PowerShell codes that have been obfuscated and can prevent scripts from executing payload downloaded from Internet, in addition to blocking the execution of executable content dropped from email (webmail/mail-client).
For increased Network protection, Exploit Guard leverages data from ISG to vet, and if necessary block, all outbound connections before they are made, thus preventing malware to connect with a command-and-control server (C&C). The outbound network traffic is evaluated based on hostname and IP address-related reputation intelligence.
“Regardless if the outbound call is to phishing, socially engineered malware, or a C&C website, or if the call originates from a browser or a background process, network protection can intercept and kill the connection. These filtering capabilities can also augment and work in concert with similar protection capabilities from others security solutions, browsers, etc,” Microsoft notes.
Controlled folder access, first included in Windows 10 in Insider Preview Build 16232, was meant to monitor the changes applications make to files located in certain protected folders. It can lock down critical folders and allow only authorized apps to access them.
Thus, unauthorized apps, malicious and suspicious executable files, DLLs, scripts, and other programs will be denied access to the protected folders. This should prevent the encryption of files by ransomware, which usually target precious data such as documents, precious photos and videos, and other important files.
“By default, Controlled folder access protects common folders where documents and other important data are stored, but it’s also flexible. You can add additional folders to protect, including those on other drives. You can also allow apps that you trust to access protected folders, so if you’re using unique or custom app, your normal everyday productivity will be not affected,” Microsoft explains.
The exploit protection included in Windows Defender Exploit Guard, the company notes, represents a suite of vulnerability mitigation and hardening techniques that have been built directly into Windows 10. These represent the former EMET and are automatically configured and applied on the machines installing Windows 10 Fall Creators Update.
“To make the process of migrating to Exploit Protection and Windows Defender Exploit Guard easier, there is a PowerShell module that converts EMET XML settings files into Windows 10 mitigation policies for Exploit Guard. This PowerShell module also provides an additional interface for Windows Defender Security Center to configure its mitigation settings,” Microsoft says.
Management of the Windows Defender Exploit Guard components can be performed through Group Policy (GP), System Center Configuration Manager (SCCM), and Mobile Device Management (MDM) such as Microsoft Intune, the company reveals. Exploit Guard is also present in the Security Analytics dashboard of the Windows Defender ATP console.
New "Silence Trojan" Used in Ongoing Bank Attacks
2.11.2017 securityweek Virus
Silence Trojan is a Fresh Example of Cybercriminals Shifting From Attacks on Users to Direct Attacks Against Banks
Security researchers from Kaspersky Lab are monitoring an ongoing cyber attack against primarily Russian, but also Malaysian and Armenian, financial institutions. The attack is new and has been dubbed 'Silence'. The researchers make no attribution for the attackers, but note that the attack methodology is broadly similar to that used in earlier successful Carbanak bank attacks.
The attack starts with gaining access to the email account of an employee working in a financial institution. The method is not important -- it could be spam-delivered malware or via a re-used password leaked from an unrelated breach. However, once the attackers have access to a genuine employee's email, they can deliver more compelling spear-phishing attacks against the target bank's own employees.
Banks Targeted by Cybercriminals Using Silence TrojanTypically, say Kaspersky Lab's GReAT researchers in a report published Wednesday, "The cybercriminals using Silence send spear-phishing emails as initial infection vectors, often using the addresses of employees of an already infected financial institution, with a request to open an account in the attacked bank. The message looks like a routine request. Using this social engineering trick, it looks unsuspicious to the receiver."
The spear-phishing email carries a .CHM attachment. This is Microsoft's own online help format consisting of a collection of HTML pages, indexing and other navigation tools. The point is that CHM files are highly interactive and can contain and run JavaScript. If the target can be enticed to open the attachment, the embedded 'start.htm' is automatically run. The JavaScript downloads an obfuscated .VBS script, which in turn downloads the dropper.
In this instance, the dropper is a Win-32 executable that communicates with the attackers' C&C server. It sends the ID of the infected machine, and downloads and executes malicious payloads. These provide various functions such as screen recording and data uploading. As with the earlier Carbanak attacks, the Silence group now takes its time to learn and understand how the bank operates. The Carbanak group (also known as Anunak) is thought to have stolen upwards of $1 billion over the last few years.
Key to this 'learning' phase is the generation of pseudo screen videos. A downloaded 'monitoring and control' module "takes multiple screenshots of the victim's active screen, providing a real-time pseudo-video stream with all the victim's activity." Taking individual screenshots rather than a genuine video will use less system resources and help the process remain under the radar of the user.
The information contained in the 'video', however, is likely to provide useful data on how the bank works, URLs used in the bank's management systems, and further exploitable applications. This data is gathered and analyzed by the attackers until they have enough information to strike and steal as much money as possible.
“The Silence Trojan is a fresh example of cybercriminals shifting from attacks on users to direct attacks on banks. We have seen this trend growing recently, as more and more slick and professional APT-style cyber-robberies emerge and succeed. The most worrying thing here is that due to their in-the-shadow approach, these attacks may succeed regardless of the peculiarities of each bank’s security architecture,” notes Sergey Lozhkin, security expert at Kaspersky Lab.
So far, Kaspersky Lab has provided no information on which banks are being attacked, nor whether any (nor how much) money may have been stolen. Nevertheless, the attack is further corroboration that criminals are beginning to attack banks directly for large amounts rather than bank customers for small amounts.
In October 2017, SpiderLab's described a bank attack that combines cybercriminal and organized crime gangs to steal large amounts of cash via ATM devices. By compromising bank systems, and creating fake accounts with large overdrafts, the attackers were able to withdraw thousands of dollars from various ATMs. SpiderLabs believes that at least four banks in Russia and post-Soviet states have lost an average of $10 million dollars each in this process.
Patchovat, záplatovat, zadrátovat, zalepit …
2.11.2017 SecurityWorld Zabezpečení
díry a zranitelnosti operačních systémů a aplikací.
Na úvod pár faktů:
Věděli jste, že:
z celkového počtu odhalených kyber útoků na celém světě bylo 30 % zaměřeno na produkty společnosti Adobe a aplikací Java a Microsoft Internet Explorer?
mezi tři nejčastěji napadané technologie v tomto roce patřili Adobe Flash Player, Microsoft Internet Explorer a Microsoft Silverlight?
77 % ze všech odhalených vyděračských útoků (ransomware) bylo orientováno na oblasti obchodu a poskytování profesionálních služeb (28 %), státní správy (19 %), zdravotnictví (15 %) a maloobchodu (15 %)?
účinný proces patch managementu je pro mnoho IT oddělení stále velkou výzvou? Až 21 % IT oddělení provozuje systémy, které nemají ošetřenou vulnerabilitu (zranitelnost), která je známá již více než tři roky a u 12 % z nich dokonce i více jak pět let. Pro zkušené hackery nebo pro automatizované kyber zločince je zneužití těchto děr velmi jednoduché. A přitom se nabízí opravdu jednoduché řešení zavedením účinného programu pro ošetřování zranitelnosti systémů, v rámci pravidelného procesu patch managementu okamžitě dojde ke zvýšení obtížnosti jejich zneužití.
do roku 2020 se počet připojených zařízení zvýší ze současných 7 na více jak 20 miliard. Toto postupné sbližování klasických IT zařízení s jinými zařízeními (např. ze skupiny IoT) bude mít za následek enormní nárůst počtu zranitelností, které bude potřeba zvládnout.
… cílem každé organizace by mělo být vybudování odolného systému, který minimalizuje dopad závažných útoků na provoz podnikové sítě a systémů. Dosažení takto odolného systému je výzvou, výběrem a implementací správných bezpečnostních pravidel je možné toho dosáhnout. Bezpodmínečnou podmínkou je ovšem udržovat všechny IT systémy aktualizované. Mnoho úspěšných útoků vychází ze skutečnosti, že laptopy, desktopy, smartphony a další zařízení nemají nainstalovány poslední aktualizace a patche. Bez pravidelné aktualizace systémů a instalace patchí zůstanou zařízení s oslabeným zabezpečením, které mohou útočníci zneužít. …
Zdroj: NTT Security & NTT Data, 2017 Global Threat Intelligence Report
S odkazem na poslední vyděračské útoky (WannaCry a Petya/Petrwrap) je třeba si uvědomit, že se nejedná o žádný nám vzdálený problém. Bez vlivu nezůstaly řady společností a státních organizací v České republice i na Slovensku. Na druhou stranu je třeba si připustit, že se nikdy nepodaří těmto napadením zcela zabránit, což ovšem nesmí být argumentací pro ignorování těchto rizik. Pokud chcete, aby vaše systémy byly pod maximální možnou ochranou, musíte pravidelně provádět patchování, a to jak operačních systémů, tak aplikací, a nezapomínat na aplikace třetích stran. Jedním z výzkumů bylo zjištěno, že právě aplikace třetích stran se mohou stát až z 86% branou pro nezvané hosty do vaší sítě.
S udržováním systémů v aktuálním stavu vám pomohou specializované nástroje, které jsou schopny celý proces provádět zcela automatizovaně bez zbytečného nadužívání lidských zdrojů a s detailními zprávami z průběhu celého procesu patch managementu, například od společnosti Ivanti.
Právě s ohledem na výše uvedené bych se s vámi rád podělil o svou osobní zkušenost spojenou s touto problematikou. Ještě nedávno jsem stál na straně poskytovatele komplexních ICT služeb v roli manažera týmu, jehož úkolem bylo zajištění provozu všech IT služeb pro jednoho z nejvýznamnějších zákazníků. Jedním z rutinních úkolů mého týmu bylo i provádění pravidelného patchování operačního systému Microsoft Windows u fyzických i virtuálních serverů. Patchování bylo součástí servisní smlouvy se zákazníkem a nebylo možné jakkoliv tuto činnost omezovat, a to ani s ohledem na požadavek snižování výdajů na práci přesčas. Každý měsíc ve čtyřech týdenních cyklech bylo nutné naimplementovat vybraný seznam patchí na více jak 300 serverů, a to pouze o víkendech a přesně v době tomu vymezené. Podle platného procesu byl každý víkend třemi až čtyřmi techniky manuálně navolen seznam schválených patchí pro skupinu až 75 serverů a následně s podporou WSUSu spuštěn proces aktualizace, který byl po celou dobu víceméně aktivně techniky monitorován. Určitě si dokážete představit, že celková doba pravidelně představovala něco mezi 15 a 35 hodinami víkendové práce přesčas, kterou bylo nutné zaměstnancům proplatit. Jednalo se tak o nemalé prostředky v řádech tisíců eur měsíčně. Navíc tento systém neumožňoval technikům plnohodnotné využití volného času, který měli mít na odpočinek a rekonvalescenci po perném pracovním týdnu.
Vzhledem k nutnosti zlepšit pracovní podmínky techniků, právě s ohledem na lepší vyvážení času na práci a odpočinek, ale také z důvodu požadavku snížit enormní náklady spojené s prací přesčas, začala společnost uvažovat o změně procesu. Vizí byla implementace takového softwarového nástroje, který celý proces plně automatizuje, minimalizuje možnost vzniku lidských chyb a poskytne detailní informace o celém jeho průběhu a výsledku. To vše za účasti pouze 1 technika, který ve stanovených časech provede kontrolu stavu a případně zkoriguje postup, kdy předpokládaná práce přesčas neměla přesáhnout 2 hodiny.
Apple Patches Dangerous KRACK Wi-Fi Vulnerabilities
1.11.2017 securityweek Apple
Apple on Tuesday released a new set of security patches for its products, including fixes for Wi-Fi vulnerabilities disclosed in mid October.
The security flaws can be exploited as part of a novel attack technique called KRACK, short for Key Reinstallation Attack, which could allow an actor within wireless range of a victim to access information assumed to be safely encrypted. The attacker could exfiltrate sensitive information such as credit card numbers, passwords, chat messages, emails, photos, and more.
The issues were found in the Wi-Fi standard itself, and all correct implementations of WPA2 were assumed to be affected. Industrial networking devices are impacted too, including products from Cisco, Rockwell Automation and Sierra Wireless. Vendors rushed to release patches after being informed on the bugs several months ago.
The KRACK-related vulnerability impacting iOS devices is tracked as CVE-2017-13080 and was addressed in iOS 11.1, for iPhone 7 and later, and iPad Pro 9.7-inch (early 2016) and later, Apple notes in an advisory.
iOS 11.1 resolves an additional 19 vulnerabilities impacting components such as CoreText, Kernel, Messages, Siri, StreamingZip, UIKit, and WebKit. These bugs could lead to arbitrary code execution, information disclosure, or to the modification of restricted areas of the file system.
WebKit was the most affected component, with 13 vulnerabilities addressed in it (10 of the issues were reported by Ivan Fratric of Google Project Zero). The bugs could lead to arbitrary code execution when processing maliciously crafted web content and were addressed through improved memory handling.
The same KRACK-related vulnerability was addressed in tvOS 11.1 and watchOS 4.1 as well. The former resolves 17 flaws in the platform, while the latter patches only 4 issues.
macOS High Sierra 10.13.1 includes patches for three KRACK-related flaws, namely CVE-2017-13077, CVE-2017-13078, and CVE-2017-13080.
The new platform iteration resolves an additional 145 vulnerabilities impacting components such as apache, APFS, AppleScript, Audio, CoreText, curl, Fonts, HFS, ImageIO, Kernel, libarchive, Open Scripting Architecture, Quick Look, QuickTime, Sandbox, and tcpdump.
An attacker exploiting these flaws could execute arbitrary code on the system, modify restricted areas of the file system, read kernel memory, leak sensitive user information, or cause denial of service. Some of the flaws could allow malicious apps to read restricted memory.
The most affected component was tcpdump, with 90 vulnerabilities addressed in it. Other components that saw a large number of issues addressed in them include apache, with 12 bugs, and Kernel, with 11 flaws.
Apple also released Safari 11.1 this week with patches for 14 issues, along with iTunes 12.7.1 for Windows and iCloud for Windows 7.1, each meant to address 13 issues. All three application releases resolve the aforementioned 13 vulnerabilities in WebKit.
Samsung, Apple, Huawei Phones Hacked at Mobile Pwn2Own
1.11.2017 securityweek Congress
Researchers have managed to hack the Samsung Galaxy S8, the iPhone 7 and the Huawei Mate 9 Pro on the first day of the Mobile Pwn2Own 2017 competition taking place alongside the PacSec conference in Tokyo, Japan.
The prize pool for the event organized by Trend Micro’s Zero Day Initiative (ZDI) exceeds $500,000 and participants have already earned a significant chunk on the first day.
The day started with an attempt from Tencent Keen Security Lab to demonstrate an exploit against the Internet Browser on a Samsung Galaxy S8. The attempt could have earned them $70,000, but it failed.
However, a researcher from the Chinese security firm Qihoo360 did manage to hack the Internet Browser on the Galaxy S8 (with persistence) and take home the $70,000. The expert achieved code execution in the browser and exploited a privilege escalation in a different Samsung app for persistence after a reboot.
As for attacks targeting Apple’s iPhone 7 with iOS 11.1, the Tencent Keen Security Lab team earned $110,000 for a total of four vulnerabilities allowing code execution via Wi-Fi and privilege escalation for persistence through a reboot. The same team earned an additional $45,000 for hacking Safari on the iPhone 7.
Richard Zhu, aka fluorescence, earned $20,000 for a Safari exploit on an iPhone 7 and a sandbox escape.
The Tencent Keen Security Lab team also took a crack at the Huawei Mate 9 Pro. Researchers failed to hack the device’s NFC system, but they did manage to develop an exploit targeting the Android phone’s baseband, which earned them $100,000.
This brings the total earned by participants on the first day of Mobile Pwn2Own 2017 to $345,000.
No one has attempted to hack Google’s Pixel phone or the company’s Chrome browser on the first day, but there are six more hacking attempts scheduled for the second day of the event.
The vulnerabilities exploited at the competition will be disclosed to Apple, Google, Samsung and Huawei, and they will be given 90 days to release a fix before limited details about the flaws are made public by ZDI.
CSE Malware ZLab – Full report of Bad Rabbit attack
1.11.2017 securityaffairs Ransomware
The researchers at CSE Cybsec ZLab have completed their analysis the Bad Rabbit ransomware, the report follows our preliminary analysis.
Introduction
Recently a new ransomware, called BadRabbit, infected systems in many countries, most of in East Europe, such as Ukraine and Russia. The malware was not totally new, it seems to be an evolution of the old NotPetya ransomware for some aspects, including:
The behavior after the reboot with a particular ransom note.
The spreading capability through lateral movements that relies on the SMB protocol and exploits a vulnerability based on vulnerability MS17-010.
There are also many differences with NotPetya, including, a more sophisticated behavior and the fixing of coding errors that transform NotPetya from a ransomware to a wiper, through the ad-hoc encrypting library “DiskCryptor”, for this purpose. These aspects suggest that the malware is a pure and correctly developed ransomware. Although there are some discrepancies:
The onion site indicated in the ransom note, “caforssztxqzf2nm[.]onion”, one the day after the initial infection, was no longer reachable. This implies that victims cannot pay the ransom to decrypt their files. But it’s strange that the onion site could be taken down so rapidly from authorities and it’s more probable that it could be taken down by the authors themselves.
Most of the compromised websites belong to restaurants, hotels and “house rental” services.
Most of the infected systems were in Ukraine, for example at the Odessa airport and Kiev metro. The targets are the same places previously targeted by NotPetya hackers.
These reasons make think that the malware isn’t a wiper for the design, but so de facto, because of the impossibility to pay the ransom and that the malware was written by the same authors of NotPetya and to be its evolution.
The full report includes technical details about the malware resulting from static and behavioral analysis. it also included Yara rules for the ransomware detection.
Malware Analysis Report: Bad Rabbit
Oracle issues an emergency patch for a bug in Oracle Identity Manager, apply it now!
1.11.2017 securityaffairs Vulnerebility
Oracle fixed a flaw in Oracle Identity Manager that was rated with a CVSS v3 score of 10.0 and can result in complete compromise of the software via an unauthenticated network attack.
Oracle issued an emergency patch for a vulnerability in Oracle Identity Manager, the flaw tracked as CVE-2017-10151 was rated 10 in severity on the CVSS scale.
“This Security Alert addresses CVE-2017-10151, a vulnerability affecting Oracle Identity Manager. This vulnerability has a CVSS v3 base score of 10.0, and can result in complete compromise of Oracle Identity Manager via an unauthenticated network attack.” states the security advisory published by Oracle.
The vulnerability could be exploited by an unauthenticated attacker to remotely take over the software.
“Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Identity Manager. While the vulnerability is in Oracle Identity Manager, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in takeover of Oracle Identity Manager.” states the advisory published on NIST’s National Vulnerability Database.
Oracle Identity Manager belongs the Oracle Fusion Middleware suite of web-based services, it manages user access privileges to enterprise resources and tasks.
The flaw affects the 11.1.1.7, 11.1.1.9, 11.1.2.1.0, 11.1.2.2.0, 11.1.2.3.0 and 12.2.1.3.0 versions.
The vulnerability is very easy to exploit and should be addressed immediately.
“Due to the severity of this vulnerability, Oracle strongly recommends that customers apply the updates provided by this Security Alert without delay,” continues the Oracle advisory. Oracle said.
“Product releases that are not under Premier Support or Extended Support are not tested for the presence of vulnerabilities addressed by this Security Alert. However, it is likely that earlier versions of affected releases are also affected by these vulnerabilities. As a result, Oracle recommends that customers upgrade to supported versions.”
Oracle Identity Manager emergency patch
This emergency patch comes after the recently released Oracle October CPU that addressed a total of 252 security vulnerabilities that affect multiple products, including 38 issued in the Fusion Middleware.
Most of the vulnerabilities fixed by Oracle could be remotely exploitable without authentication.
The October CPU was the last Oracle Critical Patch Update of 2017, this year the tech giant already resolved 1119 vulnerabilities, or 22% more than in 2016.
Threat Intelligence Firm Recorded Future Raises $25 Million
1.11.2017 securityweek IT
Threat intelligence provider Recorded Future today announced that it has raised $25 million in a Series E round of funding Led by Insight Venture Partners.
According to the Boston, Mass.-based company, the additional funding will be used to support growth and to expand its offerings to “solve a wider spectrum of cybersecurity challenges.”
Recorded Future LogoRecorded Future collects threat intelligence from open, technical, and dark web sources in real time and leverages machine learning to provide targeted analytics and alerts to clients. The company says that 86% of Fortune 100 companies use its services.

The company says that it processes "billions of data points" per day in multiple languages from the open, deep, and dark web to provide customers with a customized view of the threat landscape to reveal emerging attackers, methods, and indicators.
“Our goal remains clear: to support our customers by providing the best threat intelligence on the planet,” said Christopher Ahlberg, CEO and co-founder of Recorded Future. “With this cash infusion provided by Insight Venture Partners, we will be able to supercharge our efforts to explore new solutions to the issues plaguing the cybersecurity industry both today and in the future.”
Firefox to Block Canvas-based Browser Fingerprinting
1.11.2017 securityweek Privacy
Firefox will soon provide users with increased privacy by blocking browser fingerprinting performed through the HTML5 canvas element.
With the release of Firefox 58, users will have the option to block websites’ requests to retrieve information through canvas, which is currently used as a cookie-less method of tracking users on the web. Websites using this technique extract data from HTML <canvas> elements silently.
As soon as the change will be in effect, Firefox will behave similarly with the Tor Browser, which is based on Firefox ESR (Extended Support Release). Tor implemented the feature about four years ago.
According to discussion on the Mozilla bug tracker, Firefox 58 should display a popup when accessing a website that attempts to use an HTML < canvas > element to extract information, just like Tor does in such situations. Users will have the option to block the site’s request.
As Sophos notes, many companies are using browser fingerprinting as means to track users online without providing them with a choice. The technique involves tracking the browser itself rather than cookies or other beacons, which can be blocked or deleted.
The fingerprinting operation usually involves passively gathering information such as browser version number, operating system details, screen resolution, language, installed plugins and fonts, and the like. The more elements are used for fingerprinting, the easier it is to single out one’s browser from another user’s, the security firm points out.
“In canvas fingerprinting your browser is given instructions to render something (perhaps a combination of words and pictures) on a hidden canvas element. The resulting image is extracted from the canvas and passed through a hashing function, producing an ID,” Sophos explains.
By providing complex instructions, one can produce enough variation between visitors to ensure canvas fingerprinting is highly efficient. The information gathered this way can be shared among advertising partners and used for the profiling of users based on the affiliated websites they visit.
While Firefox will become the first major browser to take a stance against canvas-based fingerprinting, add-ons that allow users to block this activity already exist, such as Electronic Frontier Foundation’s Privacy Badger.
Google to Remove Support for PKP in Chrome
1.11.2017 securityweek Safety
Google is planning to deprecate and eventually completely remove support for public key pinning (PKP) from the Chrome web browser.
The first step in this direction would be to remove support for HTTP-based PKP (“dynamic pins”) from the browser. This is currently planned for Chrome 67, which is set to be released to the stable channel in late May 2018, Google engineer Chris Palmer says.
The next step involves removing support for built-in PKP (“static pins”). This should happen at a time “when Chrome requires Certificate Transparency for all publicly-trusted certificates,” but no specific date for the change has been provided as of now.
PKP is used to defend against certificate misissuance through a Web-exposed mechanism (HPKP) that allows sites to limit the set of certificate authorities (CAs) that can issue for their domain.
“However, this exposes as part of the Open Web Platform considerations that are external to it: specifically, the choice and selection of CAs is a product-level security decision made by browsers or by OS vendors, and the choice and use of sub-CAs, cross-signing, and other aspects of the PKI hierarchy are made independently by CAs,” Palmer notes.
Thus, website admins could find it difficult to select a reliable set of keys to pin to, which has resulted in a low adoption of PKP. This could also hurt user experience through unexpected or spurious pinning errors that would result in error fatigue rather than user safety, Palmer argues.
According to him, some of the involved risks include the rendering of a site unusable and hostile pinning (when an attacker obtains a misissued certificate). He also notes that it is difficult “to build a pin-set that is guaranteed to work, due to the variance in both user-agent trust stores and CA operations.”
Google’s engineer explains that no website would be impacted by the removal of static or dynamic PKP, and that other major browsers don’t support key pinning either.
Only 375 of the Alex Top 1 Million sites were using HPKP as of August 2016, and only 76 were using the Report-Only (RO) variant. However, there has been a major surge in HPKP deployment earlier this year, “almost entirely caused by Tumblr deploying HPKP across their entire catalogue of sites,” Scott Helme notes. More than 3,000 sites were using it as of August 2017.
Web developers looking to defend against certificate misissuance are advised to use the Expect-CT header, which is said to be safer than HPKP due to increased flexibility when it comes to recovering from configuration errors. It also benefits from built-in support by a number of CAs and can be deployed on a domain without additional steps when obtaining certificates for the domain.
Comodo Sells Certificate Business to Private Equity Firm
1.11.2017 securityweek IT
Francisco Partners Acquires Comodo's Certifiate Authority Business
Tech-focused private equity firm Francisco Partners announced on Tuesday that it has acquired Comodo CA Limited, Comodo’s certificate authority business, for an undisclosed amount.
Comodo CA is the world’s largest provider of SSL certificates, with more than 91 million certificates issued to over 200,000 customers in 150 countries. Francisco Partners has acquired a majority stake in the company and says the investment will help support Comodo CA’s accelerated growth; the firm consistently reported double-digit revenue growth in the past several years.
Bill Holtz, former COO of Entrust and former CIO of Expedia, has been named Comodo CA’s chief executive officer (CEO). Bill Conner, currently the president and CEO of security firm SonicWall, has been appointed chairman of the board. Melih Abdulhayoglu, CEO and founder of the Comodo Group, will remain a minority owner and board observer.
“Bill Holtz and Bill Conner are very accomplished executives within the enterprise security market and we are thrilled to have them join Comodo CA,” said Brian Decker, head of security investing at Francisco Partners. “Their years of experience in the SSL and digital certificate business is invaluable for Francisco Partners in this investment as Comodo CA grows and expands its leadership from SSL certificates to IoT.”
Comodo has been trying to snatch customers from Symantec, which announced on Tuesday that it’s certificate business has been acquired by DigiCert for $950 million. Symantec decided to sell its website security and related public key infrastructure (PKI) solutions after Mozilla and Google announced their intent to revoke certificates issued by the company and its partners.
When the acquisition was first announced, Comodo warned Symantec customers that the migration to DigiCert’s platform, which is significantly smaller than Symantec’s infrastructure, “poses a huge execution and technology risk.”
Symantec and DigiCert promised customers a smooth transition, but Mozilla has raised some concerns about the acquisition, particularly regarding Symantec’s involvement in day-to-day operations after the transfer of ownership.
Meet MBR-ONI, Bootkit Ransomware Used as a Targeted Wiper
1.11.2017 securityweek Ransomware
Earlier this year a new ransomware, dubbed ONI, was discovered in Japan. It is described as a sub-species of the GlobeImposter ransomware. Researchers blogged in July, "When it infects it, it encrypts the file, assigns the extension .oni to the filename, and asks for payment to decrypt it."
Cybereason now suggests that it is less ransomware, and more "a wiper to cover up an elaborate hacking operation." In a report published today, Cybereason researchers have tied the use of ONI to sophisticated attacks on Japanese industry. Unlike traditional ransomware attacks, these incursions lasted between three and nine months, and only culminated in the use of ransomware. The ransomware was, in effect, used to hide the purpose and effect of the hack.
In the same investigation, Cybereason discovered a new bootkit ransomware, MBR-ONI, which modifies the MBR and encrypts disk partitions. "We concluded that both ONI and MBR-ONI stem from the same threat actor since they were used in conjunction in the same targeted attacks and their ransom note contains the same email address," say the researchers.
The name ONI derives from the file extension of the encrypted files: '.oni'. It can mean 'devil' in Japanese. The term also appears in the contact email address used in the ransom notes: "Oninoy0ru", which can translate as Japanese for 'Night of the Devil'.
In the attack instances analyzed by Cybereason, a shared modus operandi was observed. This started with successful spear-phishing attacks leading to the introduction of the Ammyy Admin Rat. This was followed by a period of reconnaissance and credential theft, and lateral movement "ultimately compromising critical assets, including the domain controller (DC), to gain full control over the network."
The final stage of the attack is the use of log wipers and ONI distributed via a rogue group policy (GPO), in what Cybereason describes as a 'scorched earth policy'. The GPO would copy a batch script from the DC server, wiping clean the Windows' event logs to cover the attackers' tracks and avoid log-based detection. The batch file used the wevtutil command along with the "cl" flag, clearing events from more than 460 specified event logs. ONI would also be copied from the DC and executed, encrypting a large array of files.
The new MBR-ONI is used more sparingly against just a handful of the endpoints. These were the critical assets such as the AD server and file servers. Although both ONI and MBR-ONI could technically be decrypted (and can consequently be classified as ransomware rather than wipers), "We suspect," say the researchers, "that MBR-ONI was used as a wiper to conceal the operation's true motive."
The researchers also suspect that EternalBlue was used with other tools to spread through the networks. Although the log wiping and data corruption caused by the attacks makes this difficult to confirm with certainty, it was noted the EternalBlue patch had not been installed on the compromised machines, and the vulnerable SMBv1 was still enabled.
The ONI ransomware shares code with GlobeImposter, and shows Russian language traces. "While this type of evidence could have been left there on purpose by the attackers as decoy," say the researchers, "it can also suggest that the attacks were carried out by Russian speakers or, at the very least, that the ransomware was written by Russian speakers."
The MBR-ONI ransomware uses the same ransom message and ID for all infected machines (the ONI ransomware used a different ID for each encrypted system). A modified version of the open-source DiskCryptor tool was used for the encryption. Although this could be decrypted if the attackers supply the right key, "we suspect that the attackers never intended to provide recovery for the encrypted machines. Instead, the program was meant to be used as a wiper to cover the attackers' footprints and conceal the attack's motive."
The researchers believe it is highly unlikely that ransom extortion is the motive for these ONI attacks in Japan. Why would an attacker spend up to nine months -- at any point during which he could be detected and ejected -- before invoking the encryption?
"Until now the security community categorized ONI as ransomware. While ONI and the newly discovered MBR-ONI exhibit all the characteristics of ransomware, our analysis strongly suggests that they might have actually been used as wipers to cover an elaborate scheme," comments Assaf Dahan, director of advanced security services at Cybereason. "As someone who led red teams, I can tell you that taking over a network in order to mass-distribute ransomware can be achieved in a matter of a few hours or days. It doesn't make much sense to remain on the network for so long and risk exposure, unless they had other motives."
"We do not dismiss the possibility that financial gain was the motive behind these attacks," concludes Cybereason. "However, given the nature of the attacks and the profile of the targeted companies, other motives should not be dismissed lightly."
And while the researchers note that ONI is specific to Japan, they also point out that there are increasing reports of ransomware being used as a wiper by both cybercriminals and nation states in other parts of the world: PetWrap, Mamba, SamSam, NotPetya, Shamoon and Bad Rabbit are all possible examples. Such scorched earth tactics help to tie up incident responders in attempts to decrypt files, while making attribution to specific nation-state actors very difficult.
This is a tactic predicted by Carbon Black in a report in September 2017: Ransomware will increasingly be adopted by sophisticated groups who will use it in a targeted manner, often to augment or disguise other purposes – or simply as an obfuscated nation-state cyber weapon.
Cybereason raised $100 million in Series D funding from Tokyo-based SoftBank Corp in June 2017.
Serious SQL Injection Flaw Patched in WordPress
1.11.2017 securityweek Vulnerebility
A serious SQL injection vulnerability was patched on Tuesday by WordPress developers with the release of version 4.8.3.
The flaw, discovered by Anthony Ferrara, can be exploited via WordPress plugins and themes to achieve SQL injection, which can often allow attackers to take control of vulnerable websites. Developers made some changes to the WordPress core in an effort to prevent exploitation.
The issue is related to a SQL injection vulnerability discovered a few months ago by a researcher who uses the online moniker “Slavco.” It was one of the nine flaws patched on September 19 with the release of WordPress 4.8.2.
The fix introduced by WordPress developers was controversial as it broke many websites. Furthermore, shortly after the patch was released, Ferrara, who is the VP of engineering at Lingo Live, discovered that the latest version did not fix the root cause of the vulnerability.
Ferrara immediately reported his findings to the WordPress security team, but it took them roughly 6 weeks to understand the problem and create a proper patch.
The researcher had initially planned on disclosing the details of the flaw without the availability of a patch after seeing that the WordPress security team was having problems seeing the full extent of the issue. He did however attempt to reach out to plugin developers and hosting providers in an effort to help them patch their products prior to disclosure.
“It took literally 5 weeks to even get someone to consider the actual vulnerability. From there, it took me publicly threatening Full Disclosure to get the team to acknowledge the full scope of the issue (though they did start to engage deeper prior to the FD threat),” Ferrara said in a blog post.
“Security reports should be treated ‘promptly’, but that doesn’t mean every second counts (usually). I get that there are competing priorities. But show attention. Show that you’ve read what’s written. And if someone tells you it seems like you don’t understand something, stop and get clarification,” he added.
WordPress website administrators have been advised to update their installations as soon as possible. It’s not uncommon for malicious actors to start exploiting WordPress vulnerabilities to hijack websites shortly after they are disclosed.
North Korea Denies Involvement in WannaCry Cyberattack
1.11.2017 securityweek BigBrothers
North Korea has slammed Britain for accusing it of being behind a global ransomware attack that hit the National Health Service, calling the allegation a "wicked attempt" to further tighten international sanctions against Pyongyang.
A third of Britain's public hospitals were affected by the WannaCry worm in May, according to a government report.
Up to 300,000 computers in 150 countries were hit by WannaCry, which seized systems and demanded payment in Bitcoin to return control to users.
Some researchers have pointed the finger at Pyongyang, saying that the code used was similar to past hacks blamed on Kim Jong-Un's regime.
British Home Office minister Ben Wallace told the BBC last week that London was "as sure as possible" that North Korea was responsible.
But a spokesman for the North's Korea-Europe Association denied the accusations and warned Britain against "groundless speculation".
"This is an act beyond the limit of our tolerance and it makes us question the real purpose behind the UK's move," he said, in a statement carried by the official Korean Central News Agency late Monday.
"The moves of the UK government to doggedly associate the DPRK with the cyberattack cannot be interpreted in any other way than a wicked attempt to lure the international community into harboring greater mistrust of the DPRK," the spokesman said, using the initials of the North's official name.
According to the South Korean government, the North has a 6,800-strong unit of trained cyberwarfare specialists. It has been accused of launching high-profile cyberattacks, including the 2014 hacking of Sony Pictures.
Experts say the North appears to have stepped up cyberattacks in recent years in a bid to earn hard foreign currency in the face of tougher United Nations sanctions imposed over its nuclear and missile programs.
Backdoor Attacks From Windigo Operation Still Active
1.11.2017 securityweek Attack
Windigo, a malicious operation uncovered over three years ago, continues to be active despite a takedown attempt in 2014 and the sentencing of one conspirator in August 2017.
At the core of Windigo was Linux/Ebury, an OpenSSH backdoor and credential stealer that was estimated to have infected over 25,000 servers worldwide during a two and a half year period prior to the botnet’s discovery. The systems were being abused to steal credentials, redirect web traffic to malicious sites, and send in excess of 30 million spam messages a day.
The operation was uncovered by ESET researchers who worked together with CERT-Bund, the Swedish National Infrastructure for Computing, and other agencies to take it down. In 2015, Finnish authorities apprehended Maxim Senakh, one of the conspirators behind the operation. He was extradited to the United States last year and sentenced to 46 months in federal prison in August this year.
While security researchers did notice a significant drop in the Windigo activity related to the web traffic redirection following Senakh’s arrest, the malicious operation was not put to rest completely, and the Ebury backdoor has evolved, ESET warns.
A new version of the malware that was discovered in February this year shows that its authors focused on evasion and on improving botnet’s resilience against takeover attempts. Furthermore, the malware now packs a new mechanism to hide the malicious files on the filesystem, the researchers discovered.
The malware continues to use a domain generation algorithm (DGA) for data exfiltration if the operator hasn’t connected to the infected system via the OpenSSH backdoor for three days, but changes were made to the DGA itself, ESET reveals.
Ebury now includes self-hiding techniques the researchers refer to as a “userland rootkit.” For that, the malware hooks the readdir or readdir64 function to list directory entries. Should the Ebury shared library file be the next directory structure to return, the hook skips it and returns the subsequent entry instead.
To activate the hooks, Ebury injects its dynamic library into every descendant process of sshd. Thus, Ebury’s dynamic library is loaded when the new process is executed, and the malware’s constructor is called, executing the hooking routines.
In addition to being Linux-distribution-specific, earlier versions of the backdoor used to work only on very specific versions of OpenSSH, but the newer version replaced the OpenSSH patching routines with function hooking. Thus, the researchers were able to execute the malware on multiple Linux distributions.
The threat also features a hardened backdoor mechanism that no longer relies on a password encoded in the SSH client version string. Now, the backdoor’s activation requires a private key to authenticate, an extra check supposedly added to prevent unauthorized use of Ebury-compromised servers.
The new version of Ebury features new installation methods, the security researchers discovered. Just as previous versions, the malware adds the payload inside the libkeyutils.so library, but does it differently than before, and also has different deployment scripts and techniques based on the Linux distribution running on the targeted system.
“Ebury now uses self-hiding techniques and new ways to inject into OpenSSH related processes. Furthermore, it uses a new domain generation algorithm (DGA) to find which domain TXT record to fetch. The exfiltration server IP address is concealed in these data, signed with the attackers’ private key. An expiration date was added to the signed data to defend against signature reuse, thus mitigating potential sinkhole attempts. Windigo’s operators regularly monitor publicly shared IoCs and quickly adapt to fool available indicators,” ESET concludes.
Mozilla Raises Concerns Over DigiCert Acquiring Symantec CA
1.11.2017 securityweek Safety
Mozilla has raised some concerns regarding DigiCert acquiring Symantec’s website security and related public key infrastructure (PKI) solutions after major web browser vendors announced that certificates issued by the security firm would no longer be trusted.
Due to a series of incidents involving mississued TLS certificates, Mozilla and Google want Symantec and its partners to replace all existing certificates within a year. Furthermore, new certificates will need to be issued through the infrastructure of a subordinate certificate authority (CA).
Microsoft and Apple have yet to make any public comments on the matter, but they will likely follow in the footsteps of Mozilla and Google.
Instead of finding a subordinate CA to help it issue new certificates, Symantec has decided to sell its certificate business to DigiCert for $950 million in cash and a stake of roughly 30 percent in common stock equity of the DigiCert business. The companies announced on Tuesday that the acquisition has been completed.
DigiCert has reached out to Mozilla to see if the organization has any concerns over the acquisition. Mozilla is primarily concerned that while the new certificates will be issued under DigiCert’s name, Symantec will be involved in the process and it will introduce the problematic practices that led to the current situation.
“It would not be appropriate for a CA to escape root program sanctions by restructuring, or by purchasing another CA through M&A and continuing operations under that CA’s name, essentially unchanged,” explained Gervase Markham, a software engineer at the Mozilla Foundation. “And examination of historical corporate merger and acquisition activity, including deals involving Symantec, show that it’s possible for an M&A billed as the ‘purchase of B by A’ to end up with name A and yet be mostly managed by the executives of B.”
Mozilla informed DigiCert that it has four primary concerns. The organization does not want the day-to-day issuance of certificates to rely too much on Symantec’s old infrastructure.
Mozilla also cautioned about Symantec’s validation and operations personnel continuing their work without first receiving training from DigiCert. Furthermore, the web browser vendor is concerned that Symantec’s processes may actually displace DigiCert’s existing processes.
Finally, Mozilla has advised DigiCert not to allow Symantec to control the CA organization, particularly when it comes to providing technical and policy direction and oversight of the PKI.
“We hope that this provides useful guidance about our concerns, and note that our final opinion of the trustworthiness of the resulting entity will depend on the facts and behavior of the resulting organization. Mozilla reserves the right to include or exclude organizations or root certificates from our root store at our sole discretion,” Markham said.
Symantec and DigiCert promised customers an easy transition, but competitors have taken the opportunity to point out that the process could pose problems.
Comodo CA, which tech-focused private equity firm Francisco Partners acquired this week for an undisclosed amount, warned that “DigiCert does not have the same infrastructure as Symantec, as a much smaller Certificate authority it never had the need to. Therefore, the eventual platform migration poses a huge execution and technology risk for all Symantec Enterprise customers and channel partners.”
MBR-ONI ransomware involved in targeted attacks against Japanese organizations
1.11.2017 securityaffairs Ransomware
MBR-ONI is a new ransomware that is being used for targeted attacks in Japan, experts speculate it was used to cover larger hacking campaigns.
MBR-ONI is a new ransomware that is being used for targeted attacks in Japan, it is a bootkit ransomware that uses a modified version of the legitimate open-source disk encryption utility DiskCryptor to encrypt the file.
DiskCryptor is the same utility that was used by the recently discovered Bad Rabbit ransomware that targeted systems worldwide, mostly in Russia and Ukraine.
Experts from security intelligence firm Cybereason who analyzed the MBR-ONI malware speculate it has been used as wipers delete any track of targeted attacks against Japanese organizations.
“For several months Cybereason has been following the concerning rise of ONI, a family of ransomware involved in targeted attacks against Japanese companies.” states the analysis published by Cybereason.
“We suspect that the ONI ransomware was used as a wiper to cover up an elaborate hacking operation. These targeted attacks lasted between three to nine months and all ended with an attempt to encrypt hundreds of machines at once. “
The MBR-ONI was used by attackers in conjunction with ONI, that appears to be an earlier strain of ransomware developed by the same threat actors.
While ONI was used against most of the computers on targeted networks, MBR-ONI was used on only a limited number of endpoints. These endpoints were critical assets (Active Directory server, file servers, etc).
In the recent years, other wipers were used in targeted attacks including NotPetya, Mamba, SamSam, Shamoon and Bad Rabbit.
In the string of attacks against Japanese organizations, attackers leveraged on spear-phishing emails carrying weaponised Office documents that were used to deliver the Ammyy Admin RAT.
All the attacks that involved the ONI ransomware against Japanese companies across different industries shared the same pattern.
“The penetration vector used in the observed attacks consisted of spear-phishing emails that carried password-protected zip files containing weaponized Office documents.” continues the analysis.
“Once the victims extracted the zip file and opened the document, they were lured into enabling a macro. That launched a VBScript that downloaded and executed the Ammyy Admin RAT.”
Experts observed Ammyy Admin RAT installs on the compromised environment dated from December 2016 to September 2017, a circumstance that suggests that the attacks were carried over a period at least nine months.
Once the attackers penetrated the target’s environment, they will try to spread compromising critical assets such file servers, application servers and the domain controller (DC).
Researchers suspect that the threat actor used the NSA-leaked exploit EternalBlue, in conjunction with other tools to spread throughout the network.

ONI appears to share code with GlobeImposter ransomware, some routines are identical, while MBR-ONI shares a large portion of its code from DiskCryptor.
“While the ONI attacks presented in this blog are specific to Japan, we believe they also point to a concerning global trend. Using ransomware in targeted hacking operations is still quite uncommon compared to the popularity of ransomware in the overall cyber threat landscape.” concluded the experts.
Experts spotted a new strain of the Sage Ransomware that implements Anti-Analysis capabilities
1.11.2017 securityaffairs Ransomware
Security experts from Fortinet spotted a new strain of the Sage ransomware that included new functionalities, such as anti-analysis capabilities.
Sage 2.0 is a new ransomware first observed in December and not now it is distributed via malicious spam. Sage is considered a variant of CryLocker ransomware, it is being distributed by the Sundown and RIG exploit kits.
The malicious code discovered by Fortinet comes after a few months of apparent inactivity and were spread via spam emails with malicious JavaScript attachments.
“The Sage ransomware variant appears to have been out of circulation for a while in the malware scene. Since we published our article on Sage 2.0 last February, and the discovery of version 2.2 in March, the FortiGuard Labs team hasn’t seen significant activity with this malware for over six months.” states the analysis published by Fortinet.
“However, we just recently found new Sage samples that, while they appear to still be Sage 2.2, now have added tricks focused on anti-analysis and privilege escalation. In this article, we will share our findings of these recent updates.”
The Sage ransomware was also being distributed through weaponized documents, it leverages .info and .top top-level domain (TLD) names for malware delivery.
The ransomware implements the ChaCha20 encryption algorithm to encrypt the victim’s files and it doesn’t infect machines with Belarusian, Kazak, Uzbek, Russian, Ukrainian, Sakha, and Latvian keyboard layouts.
The threat actors behind this campaign have translated the ransom note into at least six languages, a circumstance that suggests they plan to target more countries in the future. in order to decrypt files, victims are instructed to access an onion site using the TOR browser and to pay a $2000 ransom to purchase the “SAGE Decrypter software.”

Once the malicious code has encrypted a file it will append the .sage extension to it.
The malware researchers discovered encrypted strings in the source code of the malware, a clear attempt of the author of obfuscating the code. The strings are encrypted using the Chacha20 cipher, the experts noticed that every encrypted string has its own hard-coded decryption key.
The new Sage ransomware implements several anti-analysis checks, for example, it enumerates all active processes on the machine, calculates the hash for every each one, and then compares the hashes against a hardcoded list of blacklisted processes.
The malware also checks the full path of where it executes to determine if the filename or directory name contains strings that are commonly used in the paths for analyzing malware samples.
The new strain of the Sage ransomware also checks the computer and user names to determine if they match a list of names used in sandbox environments, a similar check is conducted on the x86 instruction CPUID to get the processor info.
On top of these, the ransomware checks whether an antivirus runs on the computer (by enumerating the services running under Service Control Manager) and checks it against a set of blacklisted MAC addresses.
The ransomware checks whether an antivirus software is running on the machine, it does it by enumerating the services running under Service Control Manager.
“it checks to see if the computer has an instance of a running Antivirus and checks it against a set of blacklisted MAC addresses. The malware checks if there is an Antivirus running by enumerating the services running under Service Control Manager, computing these services names to a Murmurhash3, and then checking them against its list of hard-coded hashes. Table 2 and Table 3, respectively, list some of the blacklisted Antivirus services names and MAC addresses.” continues the analysis.
The experts discovered that this variant of Sage is able to elevate its privilege either by exploiting a patched Windows kernel vulnerability (CVE-2015-0057) or by abusing eventvwr.exe and performing registry hijacking to bypass User Account Control (UAC).
Firefox 58 to Block Canvas Browser Fingerprinting By Default to Stop Online Tracking
31.10.2017 thehackernews Privacy
Do you know? Thousands of websites use HTML5 Canvas—a method supported by all major browsers that allow websites to dynamically draw graphics on web pages—to track and potentially identify users across the websites by secretly fingerprinting their web browsers.
Over three years ago, the concern surrounding browser fingerprinting was highlighted by computer security experts from Princeton University and KU Leuven University in Belgium.
In 2014, the researchers demonstrated how browser's native Canvas element can be used to draw unique images to assign each user's device a number (a fingerprint) that uniquely identifies them.
These fingerprints are then used to detect when that specific user visits affiliated websites and create a profile of the user's web browsing habits, which is then shared among advertising partners for targeted advertisements.
Since then many third-party plugins and add-ons (ex. Canvas Defender) emerged online to help users identify and block Canvas fingerprinting, but no web browser except Tor browser by default blocks Canvas fingerprinting.
Good news—the wait is over.
Mozilla is testing a new feature in the upcoming version of its Firefox web browser that will grant users the ability to block canvas fingerprinting.
The browser will now explicitly ask user permission if any website or service attempts to use HTML5 Canvas Image Data in Firefox, according to a discussion on the Firefox bug tracking forum.
The permission prompt that Firefox displays reads:
"Will you allow [site] to use your HTML5 canvas image data? This may be used to uniquely identify your computer."
Once you get this message, it's up to you whether you want to allow access to canvas fingerprinting or just block it. You can also check the "always remember my decision" box to remember your choice on future visits as well.
Starting with Firefox 58, this feature would be made available for every Firefox user from January 2018, but those who want to try it early can install the latest pre-release version of the browser, i.e. Firefox Nightly.
Besides providing users control over canvas fingerprinting, Firefox 58 will also remove the controversial WoSign and its subsidiary StartCom root certificates from Mozilla's root store.
With the release of Firefox 52, Mozilla already stopped allowing websites to access the Battery Status API and the information about the website visitor’s device, and also implemented protection against system font fingerprinting.
iPhone Apps With Camera Permissions Can Secretly Take Your Photos Without You Noticing
31.10.2017 thehackernews Apple
Are you a proud iPhone owner? If yes, this could freak you up. Trust me!
Your iPhone has a serious privacy concern that allows iOS app developers to take your photographs and record your live video using both front and back camera—all without any notification or your consent.
This alarming privacy concern in Apple's mobile operating system was highlighted by an Austrian developer and Google engineer, Felix Krause, who detailed the issue in his blog post published Wednesday.
The issue, Krause noted, is in the way Apple's software handles camera access.
Apparently, there is a legitimate reason for many apps, such as Facebook, WhatsApp, and Snapchat, to request access to your camera, in an effort to take a photo within the app.
So, this permissions system is not a bug or a flaw instead it is a feature, and it works exactly in the way Apple has designed it, but Krause said any malicious app could take advantage of this feature to silently record users activities.
iPhone Apps Can Silently Turn On Cameras at Any Time
Krause explained that that granting camera permission could enable iOS app developers to access:
both the front and the back camera of your device,
photograph and record you at any time the app is in the foreground,
upload the recorded and captured content immediately, and
run real-time face detection to read your facial expressions
...and all without warning or alerting you in any way.
Since Apple only requires users to enable camera access one time when they are asked to grant blanket permission to an app and gives free access to the camera without requiring any LED light or notification, Krause explained that a malicious app could leverage this loophole to go far beyond its intended level of access to spy on users.
The researcher has even developed a proof-of-concept app only to demonstrate how a malicious app could abuse such permissions to silently take your pictures every second as you use the app, or even live stream video of your surrounding from your front and rear cameras without notifying you.
Krause said his "goal [to build the demo app] is to highlight a privacy loophole that can be abused by iOS apps."
Krause has also provided a short video demonstration of the issue, which shows the demo app taking photographs of the person using it every second. The app also included a facial recognition system to detect the person using it.
The researcher warned that such a rogue app could record "stunning video material from bathrooms around the world, using both the front and the back camera, while the user scrolls through a social feed or plays a game."
How to Protect Your Privacy?
There is a little user can do to protect them.
Krause recommended Apple to introduce a way to grant temporary permissions to access the camera, allowing apps to take a picture during a limited period of time, and then revokes it after that.
Another way is to introduce a warning light or notification to the iPhone that informs people when they are being recorded.
Most importantly, do not let any malicious app enter your smartphone. For this, always download apps from an official app store and read reviews left by other users about the app and its developer.
According to Krause, for now, the only practical way to protect yourself is to cover your camera, just like Facebook CEO Mark Zuckerberg and ex-FBI Director James Comey do.
Wait, Do You Really Think That’s A YouTube URL? Spoofing Links On Facebook
31.10.2017 thehackernews Social
While scrolling on Facebook how you decide which link/article should be clicked or opened?
Facebook timeline and Messenger display title, description, thumbnail image and URL of every shared-link, and this information are enough to decide if the content is of your interest or not.
Since Facebook is full of spam, clickbait and fake news articles these days, most users do not click every second link served to them.
But yes, the possibility of opening an article is much higher when the content of your interest comes from a legitimate and authoritative website, like YouTube or Instagram.
However, what if a link shared from a legitimate website lands you into trouble?
Even before links shared on Facebook could not be edited, but to stop the spread of misinformation and false news, the social media giant also removed the ability for Pages to edit title, description, thumbnail image of a link in July 2017.
However, it turns out that—spammers can spoof URLs of the shared-links to trick users into visiting pages they do not expect, redirecting them to phishing or fake news websites with malware or malicious content.
Discovered by 24-year-old security researcher Barak Tawily, a simple trick could allow anyone to spoof URLs by exploiting the way Facebook fetch link previews.
In brief, Facebook scans shared-link for Open Graph meta tags to determine page properties, specifically 'og:url', 'og:image' and 'og:title' to fetch its URL, thumbnail image and title respectively.
Interestingly, Tawily found that Facebook does not validate if the link mentioned in 'og:url' meta tag is same as the page URL, allowing spammers to spread malicious web pages on Facebook with spoofed URLs by just adding legitimate URLs in 'og:url' Open Graph meta tag on their websites.
"In my opinion, all Facebook users think that preview data shown by Facebook is reliable, and will click the links they are interested in, which makes them easily targeted by attackers that abuse this feature in order to perform several types of attacks, including phishing campaigns/ads/click fraud pay-per-click," Tawily told The Hacker News.
Tawily reported the issue to Facebook, but the social media giant refused to recognise it as a security flaw and referred that Facebook uses "Linkshim" to protect against such attacks.
If you are unaware, every time a link is clicked on Facebook, a system called "Linkshim" checks that URL against the company's own blacklist of malicious links to avoid phishing and malicious websites.
This means if an attacker is using a new domain for generating spoofed links, it would not be easy for Linkshim system to identify if it is malicious.
Although Linkshim also uses machine learning to identify never-seen-before malicious pages by scanning its content, Tawily found that the protection mechanism could be bypassed by serving non-malicious content explicitly to Facebook bot based on User-Agent or IP address.
Tawily has also provided a demo video to show the attack in action. You can watch the video above.
Since there is no way to check the actual URL behind a shared link on Facebook without opening it, there is a little user can do to protect themselves except being vigilant.
Highly Critical Flaw (CVSS Score 10) Lets Hackers Hijack Oracle Identity Manager
31.10.2017 thehackernews Vulnerebility
A highly critical vulnerability has been discovered in Oracle's enterprise identity management system that can be easily exploited by remote, unauthenticated attackers to take full control over the affected systems.
The critical vulnerability tracked as CVE-2017-10151, has been assigned the highest CVSS score of 10 and is easy to exploit without any user interaction, Oracle said in its advisory published Monday without revealing many details about the issue.
The vulnerability affects Oracle Identity Manager (OIM) component of Oracle Fusion Middleware—an enterprise identity management system that automatically manages users' access privileges within enterprises.
The security loophole is due to a "default account" that an unauthenticated attacker over the same network can access via HTTP to compromise Oracle Identity Manager.
Oracle has not released complete details of the vulnerability in an effort to prevent exploitation in the wild, but here the "default account" could be a secret account with hard-coded or no password.
"This vulnerability is remotely exploitable without authentication, i.e., may be exploited over a network without requiring user credentials," Oracle's advisory reads.
The easily exploitable vulnerability affects Oracle Identity Manager versions 11.1.1.7, 11.1.1.9, 11.1.2.1.0, 11.1.2.2.0, 11.1.2.3.0 and 12.2.1.3.0.
Oracle has released patches for all versions of its affected products, so you are advised to install the patches before hackers get a chance to exploit the vulnerability to target your enterprise.
"Due to the severity of this vulnerability, Oracle strongly recommends that customers apply the updates provided by this Security Alert without delay," the company warned.
Product releases that are not under Premier Support or Extended Support are not tested for the presence of the vulnerability.
However, Oracle said it was "likely that earlier versions of affected releases are also affected by these vulnerabilities. As a result, Oracle recommends that customers upgrade to supported versions."
The security patch for this vulnerability comes just about two weeks after Oracle's regular Critical Patch Update (CPU) for October 2017, which patches a total of 252 vulnerabilities in its products, including 40 in Fusion Middleware out of which 26 are remotely exploitable without authentication.
IBM Helps Banks Prevent New Account Fraud
31.10.2017 securityweek Incindent
IBM Security announced on Tuesday the launch of a product designed to help banks and other service providers protect their customers against new account fraud (NAF).
As an increasing number of financial institutions allow consumers to open new accounts via the Internet – without the need to physically visit a branch and verify their identity – it has become easier for fraudsters to make a profit using the vast amounts of personal information available for sale on the dark web.
Social security numbers, dates of birth, security questions and other personally identifiable information (PII) is often available for sale for just a few dollars, allowing fraudsters to open new bank accounts that they can use for various types of illegal activities.
IBM’s Trusteer New Account Fraud aims to help financial institutions and other organizations identify fraudulent accounts. The product leverages machine learning to assess risks by checking device and network information associated with the user creating the new account in order to verify their identity.
The solution compares the IP address, geolocation and time zone data, and behavioral biometrics against IBM’s global fraud network. If the data does not match the legitimate user, the activity is likely fraudulent.
IBM pointed out that an individual does not need to be a customer of the bank where the fraudster attempts to open a new account. Organizations that deploy the product will be warned of fraudulent activity even if the targeted consumer is not their customer.
“To address NAF, it is most critical to detect it at its earliest stage: the enrollment process. This way, the provider can stop the process before any damage is done to the rightful owner of the stolen data or to the provider itself,” explained Limor Kessem, executive security advisor at IBM.
“To shorten the time to detection, service providers need a proven way to assess the risk of a new digital identity, predict potential fraud during the enrollment process and detect issues without impacting the legitimate users that frequent the site,” she added. “There are some challenges here, especially since fraudsters use valid or partially valid information to open new accounts, which can sometimes enable their scams to go unnoticed.”
A Javelin Strategy & Research study published earlier this year showed that 15.4 million U.S. consumers fell victim to identity fraud in 2016, and losses resulting from NAF are expected to reach $8 billion by next year.
Google Bug Tracker Exposed Details of Unpatched Vulnerabilities
31.10.2017 securityweek Vulnerebility
A bug bounty hunter has earned more than $15,000 from Google after finding several potentially serious vulnerabilities related to the company’s Issue Tracker, including one that exposed the details of unpatched flaws.
Google’s Issue Tracker, also known as the “Buganizer,” is a tool used internally by the company to track bugs and feature requests during product development, and more recently it has been used to handle vulnerability reports. While some of the issues tracked via the tool are available to the public, a majority are restricted to Google employees, users who work with the company on specific projects, and the individual who submitted the report. Users can take part in a discussion on a topic by sending an email to an address that specifies the category and ID of the issue.
Alex Birsan analyzed the Google Issue Tracker earlier this month and discovered a total of three vulnerabilities. The most serious of them could have been exploited to access the entire database, including private reports describing security holes.
This was possible due to the presence of a feature that allows users to remove themselves from the CC list of a topic in case they lose interest. The functionality works via a POST request. However, due to an improper access control flaw, the system did not check if the user making the request actually had access to the issue they were trying to unsubscribe from. This led to another component of the system assuming that the user had permission to access the specified thread, and provide every single detail about the vulnerability or bug in the body of the HTTP response.
By going through consecutive issue IDs, an attacker may have been able to find the details of critical vulnerabilities affecting Google products. Birsan pointed out that no rate limiting mechanism had been in place, allowing mass data harvesting.
Google assigned the vulnerability the highest priority rating and addressed it within an hour. The company awarded the researcher $7,500 for responsibly disclosing the security hole.
While this appears to be a critical vulnerability that should have earned a much higher bounty, Birsan noted that thousands of issues are submitted every hour and serious flaws are patched almost immediately, making it difficult for an attacker to find something that they could exploit.
“When I first started hunting for this information leak, I assumed it would be the Holy Grail of Google bugs, because it discloses information about every other bug,” Birsan said. “However, after finding it, I quickly realized that the impact would be minimized, because all the dangerous vulnerabilities get neutralized within the hour anyway.”
This was not the only vulnerability discovered by Birsan while analyzing the Google Issue Tracker. While trying to obtain an @google.com email address to gain access to restricted threads – @google.com addresses are reserved for Google employees – the expert noticed that he could change any new @gmail.com address to @google.com if the new address was not confirmed by clicking on a link received via email.
While the @google.com account he obtained did not provide access to systems restricted to Google employees, Birsan said it did provide “a lot of extra benefits in other places across the internet.” Google confirmed the issue within hours and awarded the researcher $3,133.7.
Birsan also found a way to obtain information about non-public issues by leveraging the starring functionality – i.e. clicking on the star icon corresponding to an issue to receive email notifications when a new comment is added. By sending out multiple starring requests with the issue ID changed in each request, the white hat hacker noticed that he started receiving emails related to numerous problems reported by users.
However, a closer inspection revealed that the exposed topics were only related to translations and they would not provide any real value to an attacker. Nevertheless, Google classified it as a critical vulnerability and awarded the researcher $5,000.
Bug trackers can store highly valuable information, which is why they are likely to be targeted by malicious actors. The most serious incidents related to bug trackers involve Mozilla and Microsoft, both of which had their systems breached in the past years.
“Bug trackers used within prominent tech companies can be a hugely lucrative target for attackers looking to improve their 0-day capabilities,” Tripwire researcher Craig Young told SecurityWeek. “Access to a private bug tracker gives the attackers lead time toward crafting an exploit as well as for finding related bugs before the public security community has a chance to do so. (Often times a critical bug can indicate a functional area which is under-tested and therefore a good place to look for other bugs or variants.)”
“A clever attacker might also take advantage of unauthorized bug tracker access to delay patch releases by manipulating data in the tracker (e.g. delaying when developers see the report, changing pertinent details so that the bug does not reproduce, or even just closing out tickets as invalid),” Young added.