Incident response ve věku cloudů
17.10.2017 SecurityWorld Incidenty
Řešení pro reakce na incidenty může pomoci interním i externím týmům spolupracovat, sledovat procesy reakcí na incidenty a automatizovat důležité úlohy zabezpečení.
Většina šéfů zabezpečení informací zažívá drsné probuzení, když se setkají se svým prvním významným bezpečnostním problémem v cloudu.
Pokud zjistí kritickou zranitelnost, která vyžaduje opravu, může jim chybět povolení ke změnám v prostředí připraveném od poskytovatele cloudu. Jestliže firma síť nevlastní, nemusí existovat způsob, jak získat podrobnosti zásadní pro vyšetření incidentu.
Aby se v cloudu zabránilo významným bezpečnostním problémům, musí mít CISO plán reakcí na incidenty. Zde je návod, jak ho vytvořit:
Stanovte společný plán reakce s poskytovatelem cloudu. Pokud jste ještě do cloudu nepřešli, je nejpraktičtějším prvním krokem stanovení společného procesu reakcí. Je potřeba jasně definovat odpovědnosti a role a vzájemně si vyměnit kontaktní informace pro primární a sekundární kontakty.
Získejte podrobné vysvětlení toho, co u poskytovatele vyvolává reakci na incidenty a jak bude poskytovatel řešit různé problémy.
Vyhodnoťte způsob monitoringu a bezpečnostní opatření používané v daném cloudu. Pro zajištění efektivní reakce na bezpečnostní problémy související s cloudovou infrastrukturou je důležité pochopit, jaký druh monitorovacích a bezpečnostních opatření používá poskytovatel cloudu a jakým způsobem jsou pro vás tyto nástroje dostupné.
Pokud zjistíte, že jsou nedostatečné, hledejte způsoby, jak lze nasadit doplňující řešení, které to napraví.
3. Vytvořte plán obnovy. Rozhodněte, zda bude v případě výpadku u poskytovatele nutná obnova. Vytvořte plán obnovy, který určí, jestli se má použít alternativní poskytovatel, nebo interní vybavení, a určí také postup pro získání a přesun dat.
4. Vyhodnoťte forenzní nástroje pro cloudovou infrastrukturu. Zjistěte, jaké nástroje jsou k dispozici od poskytovatele cloudu a z dalších zdrojů pro forenzní šetření v případě incidentu. Pokud incident zahrnuje citlivé osobní údaje, mohl by přerůst v právní problém, takže je dostupnost vhodných nástrojů pro forenzní práci a sledování důkazů zásadní.
Zvládnutí incidentu v cloudu
Při reakci na incident je mnoho kroků stejných nehledě na to, zda k němu došlo v cloudu či v interní infrastruktuře. V případě cloudového incidentu však existují některé další kroky, které je nutné udělat:
Ihned kontaktujte tým reakce na incidenty daného poskytovatele a při své komunikaci buďte důrazní. Pokud je tým poskytovatele nedostupný, udělejte v souvislosti s incidentem vše, co je ve vašich možnostech pro jeho zastavení – například kontroly připojení ke cloudové službě a v případě pochyb také zrušení uživatelského přístupu ke cloudové službě.
Pokud nelze incident kontrolovat, ani zastavit, připravte si přesun na alternativní službu nebo si nakonfigurujte svůj interní server.
Cloud vám umožní odložit identifikaci a odstranění na dobu po skončení krize. Ve většině případů můžete okamžitě zahájit obnovu produkčních služeb vytvořením nové instance.
Nejlepší postupy
Jedním z kritických problémů, kterým mnoho podniků čelí, je nedostatek talentovaných pracovních sil s potřebnými schopnostmi pro správu zabezpečení. Je těžké najít vhodné kandidáty, a pokud je najdete, můžete čekat, že jim budete muset nabídnout vysoké platy.
Existují však některé kroky, které můžete udělat, abyste rychle zaškolili nové zaměstnance a zlepšili schopnosti pracovníků současných:
Podporujte spolupráci, která pomůže mladším zaměstnancům učit se ze zkušeností vedoucích analytiků. Jako bonus může spolupráce odhalit duplicitní činnosti, které lze odstranit.
Vytvářejte příručky, které popíšou standardní postupy pro reakce na incidenty. Samozřejmě nelze vytvořit návod pro každou možnou situaci, ale příručky mohou být cennými průvodci a vynikajícími školicími materiály. Jen nezapomínejte příručky aktualizovat, což je úloha, kterou lze často zautomatizovat.
Mnoho úloh lze automatizovat, zejména pokud se opakují a jsou rutinní. Běžné úlohy zabírají nepřijatelné množství času. Automatizace může uvolnit váš personál pro důležitější úkoly.
Podporujte vznik situační všímavosti z perspektivy historické i z perspektivy reálného času. Efektivní analýza minulých incidentů vám pomůže k lepšímu rozhodování o incidentech současných.
Analyzujte incidenty a vytvořte si databázi, která pomůže určit druhy problémů, potřebné schopnosti k jejich vyřešení, frekvenci různých typů incidentů a další skutečnosti. Analýza vám může pomoci identifikovat zranitelnosti a zjistit, kde lze zabezpečení zlepšit.
Jako většina nejlepších bezpečnostních postupů pro cloudové aplikace je také reakce na incidenty společnou odpovědností. Při plánování reakcí na budoucí incidenty je zásadní zajistit dostupnost správných kontaktů, nástrojů a procesů.
Mít platformu pro reakce na incidenty, která umožňuje spolupráci interních a externích týmů, sleduje procesy reakce na incidenty a automatizuje klíčové bezpečnostní úlohy, je v čase krize nezbytné, aby bylo možné rychle problémy zastavit a efektivně na ně reagovat.
Android Ransomware Abuses Accessibility Services
17.10.2017 securityweek Android
A newly discovered ransomware family targeting Android devices is abusing the platform’s accessibility services, ESET warns.
Dubbed DoubleLocker, this innovative Android malware doesn’t merely encrypt users’ data, but also locks the infected devices down, security researchers from ESET say.
The ransomware is based on the source code of BankBot banking Trojan, which is already known for misusing accessibility services on Android. However, the new malware family lacks the functions related to harvesting users’ banking credentials and instead uses two other tools for extorting money from its victims.
BankBot had its source code leaked online in late 2016, which already spawned numerous banking Trojan variations. However, DoubleLocker is the first Android ransomware to leverage the leaked code.
DoubleLocker mainly spreads as a fake Adobe Flash Player application downloadable through compromised websites. Once installed on the victim’s device, it requests activation of the accessibility service called “Google Play Service,” which allows it to gain administrator rights and set itself as the default Home application, without the user’s consent.
The malware also changes the device’s PIN code, thus blocking the victim out. The new PIN is a randomly generated value that isn’t stored on the device or sent out, thus preventing the user from recovering it. The attackers, however, have the possibility to remotely reset the PIN and unlock the device.
“Setting itself as a default home app – a launcher – is a trick that improves the malware’s persistence. Whenever the user clicks on the Home button, the ransomware gets activated and the device gets locked again. Thanks to using the accessibility service, the user doesn’t know that they launched malware by hitting Home,” explains ESET Malware Researcher Lukáš Štefanko.
Next, the ransomware encrypts all of the files located in the device’s primary storage directory. The malware uses the AES encryption algorithm for this operation and appends the .cryeye extension to the affected files.
The ransom note claims that the original files have been deleted and that users should pay the ransom within 24 hours. The malware asks for a 0.0130 Bitcoin ransom (around $50) and displays a QR code that should make it easier for victims to pay.
“DoubleLocker misuses Android accessibility services, which is a popular trick among cybercriminals. Its payload can change the device’s PIN, preventing the victim from accessing their device and encrypts the victim’s data. Such a combination hasn’t been seen yet in the Android ecosystem,” Štefanko says.
The security researcher also points out that, although the ransomware lacks the credential harvesting capabilities BankBot has, such functionality could be easily added to it.
“Given its banking malware roots, DoubleLocker may well be turned into what can be called ransom-bankers. Two-stage malware that first tries to wipe your bank or PayPal account and subsequently locks your device and data to request a ransom… Speculation aside, we spotted a test version of such a ransom-banker in the wild as long ago as May, 2017,” warns Štefanko.
Tech Giants Warn of Crypto Flaw in Infineon Chips
17.10.2017 securityweek Vulnerebility
Microsoft, Google, HP, Lenovo and Fujitsu have warned customers of a potentially serious crypto-related vulnerability affecting some chips made by German semiconductor manufacturer Infineon Technologies.
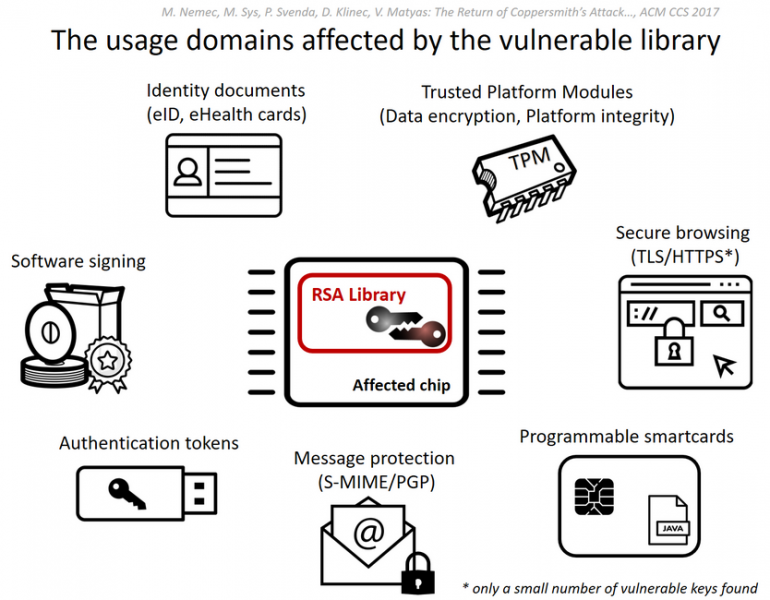
TPM vulnerability allows attackers to obtain private RSA keys
The flaw, tracked as CVE-2017-15361, is related to the Trusted Platform Module (TPM), an international standard designed for protecting crypto processes within computing devices, and for securely storing encryption keys, passwords, certificates and other sensitive data. TPM has been implemented in some Infineon microcontrollers in an effort to secure hardware.
The problem is that RSA encryption keys generated by the TPM (e.g. for disk encryption purposes) can be cracked due to the use of a technique known as “Fast Prime.” This is an algorithm that helps accelerate the generation of RSA public and private key pairs.
The issue was discovered by a team of researchers from the Masaryk University in the Czech Republic, Enigma Bridge in the UK, and Ca' Foscari University of Venice, Italy.
According to experts, the vulnerability allows an attacker who knows the public key to obtain the private RSA key. The attack can be carried out remotely and all keys generated by vulnerable chips are affected. Researchers said a 1024 bit RSA key can be cracked in 97 CPU days for a cost of $40-80 using an older Intel Xeon processor, and a 2048 bit key in 140 CPU years for a cost ranging between $20,000 and $40,000. Infineon estimated that a 2048 bit key can be cracked within one month using 600 CPUs.
“The private key can be misused for impersonation of a legitimate owner, decryption of sensitive messages, forgery of signatures (such as for software releases) and other related attacks,” researchers said.
“The actual impact of the vulnerability depends on the usage scenario, availability of the public keys and the lengths of keys used. We found and analyzed vulnerable keys in various domains including electronic citizen documents, authentication tokens, trusted boot devices, software package signing, TLS/HTTPS keys and PGP. The currently confirmed number of vulnerable keys found is about 760,000 but possibly up to two to three magnitudes more are vulnerable,” they added.

Full technical details will be released in early November at the ACM Conference on Computer and Communications Security (CCS).
Affected tech giants release advisories
The vulnerability was discovered at the end of January and it was reported to Infineon in February. The company has been working with affected hardware OEMs and PC manufacturers to address the problem.
Infineon has released a firmware update that patches the vulnerability, and Microsoft, Google, HP, Lenovo and Fujitsu have released security advisories to alert customers.
Microsoft, which said it had not been aware of any attacks in the wild, has released Windows security updates, but warned users that the TPM firmware updates also need to be installed and previously created keys should be reissued.
HP has released updates for many of its notebooks, mobile workstations, thin clients, commercial desktops, retail systems, and workstation desktops. The list of affected models includes Chromebook, Elite, EliteBook, mt and t thin clients, Pro, ProBook, Stream, ZBook, ZHAN, 260 G1/G2, 280 G1/G2, 406 G1/G2, Elite Slice, EliteDesk, EliteOne, ElitePOS, MP9, ProDesk, ProOne, RP9, Z workstations, Envy, Spectre, and OMEN X.
Lenovo said many of its products are not affected by the flaw. The list of impacted devices includes various ThinkCentre, ThinkPad and ThinkStation models.
Google has also shared a list of affected Chromebooks. The company said Chrome OS relies on TPM-generated RSA keys for several features, including to slow down brute-force attacks, for hardware backed encryption keys and certificates, and the certification process for Verified Access.
Fujitsu has released various tools to address the weakness in OEM mainboards, ESPRIMO desktop PCs, FUTRO thin clients, CELSIUS workstations, LIFEBOOK notebooks, STYLISTIC tablets, and PRIMERGY servers.
The WinMagic full disk encryption software is also affected, according to Infineon, but no advisory is available at the time of writing.
Adobe Patches Flash Zero-Day Exploited in Targeted Attacks
17.10.2017 securityweek Vulnerebility
A Flash Player security update released on Monday by Adobe patches a zero-day vulnerability that has been exploited in targeted attacks.
The security hole, tracked as CVE-2017-11292, has been described as a critical type confusion issue that could lead to remote code execution.
The vulnerability affects the Windows, Mac, Linux and Chrome OS versions of Flash Player, and it has been addressed with the release of versions 27.0.0.159 and 27.0.0.130. Microsoft will likely release an update as well to patch the Flash Player components used by its products.
The flaw was reported to Adobe by Anton Ivanov of Kaspersky Labs. The security firm revealed that the vulnerability has been exploited by a Middle Eastern threat actor known as BlackOasis to deliver FinFisher spyware.
CVE-2017-11292 is the first Flash Player zero-day vulnerability patched by Adobe in 2017.
The number of vulnerabilities found in Flash Player in the past months has decreased considerably – only four issues were resolved in August and September. While this may be a result of the decision to kill Flash Player by 2020, zero-day exploits affecting the software can still be highly valuable for malicious actors.
Earlier this month, when Adobe announced that it did not have any Patch Tuesday updates, SecurityWeek cautioned that the possibility of a zero-day being uncovered by the end of the month should not be ruled out.
*Updated with link and information that the zero-day has been exploited by BlackOasis to deliver FinFisher spyware
Dangerous WPA2 Flaw Exposes Wi-Fi Traffic to Snooping
17.10.2017 securityweek Vulnerebility
A series of vulnerabilities in the Wi-Fi standard render all Wi-Fi Protected Access II (WPA2) protocol implementations vulnerable to a new type of attack, security researchers have discovered.
Called Key Reinstallation Attack, or KRACK, the novel technique provides attackers who are within range of a victim to access information that was previously assumed to be safely encrypted. Thus, attackers can steal sensitive information such as credit card numbers, passwords, chat messages, emails, photos, and more.
Discovered by Mathy Vanhoef and Frank Piessens, the weaknesses reside in the Wi-Fi standard itself, meaning that all correct implementations of WPA2 are likely affected. The security researchers have already discovered that Android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys, and others, are affected by some variant of the attack.
The 4-way handshake that protected Wi-Fi networks use to generate a fresh session key is a 14-year-old function that has remained free from attacks until now, and even proved secure. What Vanhoef and Piessens discovered, however, was that the 4-way handshake is vulnerable to a key reinstallation attack.
The reserchers explained that an adversary could trick the victim into reinstalling an already-in-use key through manipulating and replaying handshake messages.
“When reinstalling the key, associated parameters such as the incremental transmit packet number (nonce) and receive packet number (replay counter) are reset to their initial value,” the researchers explain in their research paper (PDF).
The attack can break the PeerKey, group key, and Fast BSS Transition (FT) handshake, having a different impact on each of them, based on the data-confidentiality protocol in use.
While the attacker could replay and decrypt (but not forge) packets against AES-CCMP (thus hijacking TCP streams), they could replay, decrypt, and forge packets against WPATKIP and GCMP, with a catastrophic impact. GCMP is affected the most, as it uses the same authentication key in both communication directions.
“After establishing a man-in-the-middle position between an AP and client, an attacker can selectively manipulate the timing and transmission of messages in the WPA2 Four-way, Group Key, Fast Basic Service Set (BSS) Transition, PeerKey, Tunneled Direct-Link Setup (TDLS) PeerKey (TPK), or Wireless Network Management (WNM) Sleep Mode handshakes, resulting in out-of-sequence reception or retransmission of messages,” the US-CERT notes in an advisory.
The security researchers demonstrated their attack against Android 6.0, claiming that it is “exceptionally devastating” against the platform. Specifically, they explain that both Android and Linux can be forced into “(re)installing an all-zero encryption key.”
“All Wi-Fi clients we tested were vulnerable to our attack against the group key handshake. This enables an adversary to replay broadcast and multicast frames. When the 4-way or fast BSS transition handshake is attacked, the precise impact depends on the data-confidentiality protocol being used. In all cases though, it is possible to decrypt frames and thus hijack TCP connections. This enables the injection of data into unencrypted HTTP connections,” the paper reads.
The researchers also note that the key reinstallation attack even occurs spontaneously when certain handshake messages are lost due to background noise, meaning that implementations are reusing nonces even without an adversary being present.
Mitigation is possible through checking whether an already-in-use key is being installed and consequently not resetting associated nonces and replaying counters, the researchers note. Another solution would be to assure that a particular key is only installed once during a handshake execution.
While Vanhoef and Piessens argue that most WPA2 implementations are vulnerable, Iron Group CTO Alex Hudson points out that Wi-Fi offers a limited amount of physical security by requiring an attacker to be in proximity.
“So, you’re not suddenly vulnerable to everyone on the internet. It’s very weak protection, but this is important when reviewing your threat level,” he says.
Hudson also notes that only few protocols actually rely on WPA2 security: “Accessing secure websites over WiFi is still totally safe. Hopefully – but there is no guarantee – you don’t have much information going over your network that requires the encryption WPA2 provides,” he continues.
On a dedicated website, Vanhoef and Piessens published a list of CVE identifiers assigned to track affected products and explained that each of these identifiers represents a specific instantiation of a key reinstallation attack. Thus, each CVE describes a specific protocol vulnerability and some vendors could be affected by each of them.
The vulnerabilities are CVE-2017-13077, CVE-2017-13078, CVE-2017-13079, CVE-2017-13080, CVE-2017-13081, CVE-2017-13082, CVE-2017-13084, CVE-2017-13086, CVE-2017-13087, and CVE-2017-13088.
The security researchers also note that they are warning vendors of the discovered vulnerabilities, meaning that security updates addressing them are likely to be released. A list of notified vendors is available here.
"This issue can be resolved through straightforward software updates, and the Wi-Fi industry, including major platform providers, has already started deploying patches to Wi-Fi users," the Wi-Fi Alliance explained in a statement."
"There is no evidence that the vulnerability has been exploited maliciously, and Wi-Fi Alliance has taken immediate steps to ensure users can continue to count on Wi-Fi to deliver strong security protections," the Wi-Fi Alliance added. "Wi-Fi Alliance now requires testing for this vulnerability within our global certification lab network and has provided a vulnerability detection tool for use by any Wi-Fi Alliance member."
The new attack method will be presented at the ACM Conference on Computer and Communications Security (CCS) and at Black Hat 2017.
Middle East Group Uses Flash Zero-Day to Deliver Spyware
17.10.2017 securityweek Vulnerebility
A threat group believed to be located somewhere in the Middle East has been using a zero-day vulnerability in Adobe Flash Player to deliver a piece of spyware to targeted individuals.
The said Flash Player flaw, a remote code execution vulnerability identified as CVE-2017-11292, was patched by Adobe on Monday. Kaspersky Lab, whose researchers spotted the attacks and reported the security hole to Adobe, has published a blog post detailing the attacks.
According to the security firm, a Middle Eastern group it tracks as BlackOasis has been using CVE-2017-11292 in highly targeted attacks to deliver FinFisher, a controversial lawful interception tool also known as FinSpy and WingBird. Kaspersky believes that the country sponsoring BlackOasis is likely a customer of Gamma Group, the company behind FinFisher.
Last month, Microsoft patched a .NET zero-day that had been exploited by the same threat group via malicious Office documents to deliver FinFisher malware. That attack was first spotted by experts at FireEye, but Kaspersky made the connection to the latest attacks based on the command and control (C&C) server used by the hackers.
This is the fifth zero-day vulnerability attributed by Kaspersky Lab to the BlackOasis group since June 2015.
According to Kaspersky, attacks leveraging CVE-2017-11292 start with a malicious Office document delivered via email. The document includes an ActiveX object that contains the Flash exploit.
“The exploit is a memory corruption vulnerability that exists in the “com.adobe. tvsdk.mediacore. BufferControlParameters” class. If the exploit is successful, it will gain arbitrary read / write operations within memory, thus allowing it to execute a second stage shellcode,” Kaspersky researchers explained.
The second stage shellcode downloads and executes the latest version of the FinFisher spyware, and fetches a decoy document that is displayed to avoid raising suspicion. The latest version of the malware includes several new features designed to make it more difficult for researchers to analyze the threat.
Kaspersky reported seeing BlackOasis victims in Russia, Iraq, Afghanistan, Nigeria, Libya, Jordan, Tunisia, Saudi Arabia, Iran, the Netherlands, Bahrain, the United Kingdom and Angola.
“BlackOasis’ interests span a wide gamut of figures involved in Middle Eastern politics and verticals disproportionately relevant to the region. This includes prominent figures in the United Nations, opposition bloggers and activists, and regional news correspondents,” Kaspersky said. “During 2016, we observed a heavy interest in Angola, exemplified by lure documents indicating targets with suspected ties to oil, money laundering, and other illicit activities. There is also an interest in international activists and think tanks.”
Microsoft, which tracks the BlackOasis group as NEODYMIUM, reported last year that the threat actor had been using a Flash Player exploit (CVE-2016-4117) to deliver FinFisher malware. More than 80 percent of the victims were identified at the time in Turkey.
Email Attacks Use Fake VAT Returns to Deliver Malware
17.10.2017 securityweek Virus
Domain-based Message Authentication, Reporting and Conformance (DMARC) is designed to stop phishing. One of the most phished domain names in the world is the UK tax office, HMRC (@HMRC.gov.uk). HMRC has implemented DMARC to counter this phishing, and in November 2016 it announced, "We have already managed to reduce phishing emails by 300 million this year through spearheading the use of DMARC. It allows us and email service providers to identify fraudulent emails purporting to be from genuine HMRC domains and prevent their delivery to customers."
But DMARC is clearly no silver bullet. On October 13, 2017, Trustwave's SpiderLabs described a very recent, albeit short-lived, HMRC-based phishing campaign. "On 6th September, 2017, scammers launched a phishing attack using spoofed e-mail messages appearing to come from a HMRC support service domain and containing links to the infamous JRAT malware disguised as a VAT return document."
On that same day, the scammers registered the HMRC-lookalike domain hmirc-gov.co.uk from the LCN registrar. The phishing messages sent to targets were sent from this domain. They were from 'HMRC Business Help and Support Email' with the subject 'VAT Return Query'.
The content says, "Thank you for sending you VAT Return Online but there some queries about your submission. Kindly review the outlined errors in the attached document, correct and resubmit." It contains just two easily missed typographical/grammatical errors.
In reality, there is no attachment to the email. "The illusion of the attachment that can be seen in the message body," writes SpiderLabs, "is achieved using an embedded HTML image that is rigged with a URL pointing to the Microsoft OneDrive file sharing service." Attempting to access the non-existent attachment points the user to the OneDrive service and automatically downloads a file labeled 'VAT RETURN QUERY.ZIP'.
That file contains the JRAT bot. This version has an anti-anlysis mechanism and adds the process name to the 'Image File Execution' registry key so that scvhost.exe is executed instead.
DMARC can prevent phishing from genuine domains, but cannot prevent phishing from lookalike domains. When SecurityWeek checked the lookalike today, it found the LCN parked page. Technically, it is still registered to the scammers, but with no content. An LCN spokesperson told SecurityWeek that the registry had actually suspended the account after receiving an email on September 7 suggesting something 'fishy' about the domain name. This was just one day after the campaign had begun.
LCN was unable to provide any details on who had registered the domain because it had been registered with 'privacy' -- although it is doubtful whether any details would be accurate. After speaking to SecurityWeek, the LCN spokesperson admitted that the domain should not be reachable, and within five minutes it had disappeared from the internet.
What this episode indicates is that DMARC alone is not sufficient to prevent phishing. It can stop phishing from any domain owned by the spoofed organization, but cannot prevent phishing from look-alike domains. Large and important brands, like HMRC, can try to prevent the availability of look-alikes by registering them themselves or by liaising with registries to prevent them being sold -- but, as this incident shows, it is an almost impossible task.
The problem is so severe that Switzerland-based security firm High-Tech Bridge offers a free AI-based service called Trademark Abuse Radar, that will search for potentially dangerous domains. A search on 'HMRC' today returned a list of 7 HMRC-related domains that appear to be used for cyber-squatting and typosquatting purposes, and a further 24 domains "that seem to be used to conduct phishing attacks against tested domain name or brand."
SecurityWeek asked HMRC to comment on this incident, but have not yet had a reply. If anything is received it will be added to this article.
Firm Backs Vulnerability Management Service With $1 Million Guarantee
17.10.2017 securityweek Vulnerebility
San Francisco-based consulting firm AsTech has today announced a $1 million guarantee for its Qualys Managed Services offering. AsTech is one of a small but growing number of vendors applying a different approach to cyber insurance: a monetary guarantee against failure of their own products.
AsTech offers a range of niche managed services, including management of the Qualys vulnerability service. "
Qualys provides a highly rated cloud-based vulnerability management service. But like all services, its success can depend upon the quality of its implementation and use. The security skills shortage pressures organizations to buy-in such services, but also makes it difficult for them to apply them correctly. This is the raison d'etre for managed services: where organizations cannot be certain of implementing and operating their own cybersecurity, they can turn to a managed services provider to do it for them.
In general, the problem is that there is still nothing to guarantee the skills of the service provider; and the customer remains liable for the cost of any breach. Today, AsTech is disrupting this model by announcing that it has sufficient confidence in its own Qualys-based skills to guarantee that it will not fail its users.
"Qualys software suffers from the same problems suffered by most security controls," explains Nathan Wenzler, AsTech's chief security strategist. "Sometimes the configuration isn't properly set up, and sometimes it just deteriorates over time. We have the in-house expertise to ensure correct configuration and use. Now we're adding guaranteed risk mitigation on top of that. If we miss something, we take some of that risk away from the customer and put it back on ourselves."
Called Vigilance, AsTech is now offering an optional add-on insurance package for its Managed Qualys Service. It guarantees to cover breach-related costs caused by a failure of the Qualys implementation of up to $1 million. "We're guaranteeing that in setting up and tuning Qualys, we will find all of the vulnerabilities, we will find all of the assets, and we will tweak the tool to such a high degree of accuracy that for all perimeter-facing assets the customer will not miss anything that an attacker could exploit. Should an organization be breached from the perimeter and from a vulnerability that Qualys should be able to detect, then we will cover data breach costs that occur up to $1 million."
This is a cross between insurance (it transfers financial liability to a third-party) and a guarantee (it guarantees the performance of a product). AsTech is not the first vendor to provide such a guarantee -- it already has a similar guarantee for its Paragon Security Service; while last year SentinelOne announced a $1 million dollar warranty (up to $1000 per affected endpoint) for the performance of its product against ransomware.
"This is a new security model that we're applying to a lot of things," comments Wenzler. "We first did it with a security program we call Paragon which is specifically for application security: code review and vulnerability analysis and help with remediation, and we ensure that you will not be breached with a $5 million guarantee."
It is a model that has the potential to disrupt the growing 'traditional' insurance model for cybersecurity if enough vendors adopt it. AsTech is actively investigating what of its other services can be included within the Vigilance model. But it needs to be understood. For example, Vigilance for Qualys Managed Services is not a blanket insurance against all breaches. It only covers perimeter breaches through a vulnerability that is included within the Qualys vulnerability service -- which is considered to be one of the better vulnerability services. The Qualys Cloud Platform gives customers a continuous, always-on assessment of their global security and compliance posture, with 2-second visibility across all global IT assets, wherever they reside.
This potentially could lead to some grey areas. For example, compliance failure costs would not normally be covered. But compliance is becoming an increasingly complex area. The EU's General Data Protection Regulation isn't simply about data protection -- it is also about data governance. A fine for data governance non-compliance would not be covered by the AsTech insurance -- but a GDPR fine specifically relating to data loss caused by exploitation of a vulnerability known to Qualys would be covered.
"It's not going to cover compliance fees or fines," explained Wenzler; "only data breach-related costs, such as notification costs. Remediation, such as pay outs to customers for credit monitoring services, would be covered; but not costs like fines levied for compliance failures. The key is that the guarantee is related to data breaches -- so if a compliance fine is directly related to the data breach, it would be covered; but if the fine is related to general non-compliance, it would not be covered."
Vendor product guarantees is a nascent market with the potential to grow. "We're seeing a lot of interest from customers and other people who recognize that you can hire security people for just about anything, but you still run a level of risk if the person or group you hire makes a mistake, sets up a firewall incorrectly or whatever. At the end of the day you're still responsible and liable for the data and to your customers." Product guarantees can limit that liability in specific areas without the need for complex and costly general insurance.
Security Flaw Prompts Fears on Wi-Fi Connections
17.10.2017 securityweek Vulnerebility
A newly discovered flaw in the widely used Wi-Fi encryption protocol could leave millions of users vulnerable to attacks, prompting warnings Monday from the US government and security researchers worldwide.
The US government's Computer Emergency Response Team (CERT) issued a security bulletin saying the flaw can open the door to hackers seeking to eavesdrop on or hijack devices using wireless networks.
"Exploitation of these vulnerabilities could allow an attacker to take control of an affected system," said CERT, which is part of the US Department of Homeland Security.
The agency's warning came on the heels of research by computer scientists at the Belgian university KU Leuven, who dubbed the flaw KRACK, for Key Reinstallation Attack.
According to the news site Ars Technica, the discovery was a closely guarded secret for weeks to allow Wi-Fi systems to develop security patches.
Attackers can exploit the flaw in WPA2 -- the name for the encryption protocol -- "to read information that was previously assumed to be safely encrypted," said a blog post by KU Leuven researcher Mathy Vanhoef.
"This can be abused to steal sensitive information such as credit card numbers, passwords, chat messages, emails, photos, and so on. The attack works against all modern protected Wi-Fi networks."
The researcher said the flaw may also allow an attacker "to inject ransomware or other malware into websites."
The KRACK vulnerability allows attackers to circumvent the "key" on a Wi-Fi connection that keeps data private.
The Belgian researchers said in a paper that devices on all operating systems may be vulnerable to KRACK, including 41 percent of Android devices.
- 'Be afraid' -
The newly discovered flaw was serious because of the ubiquity of Wi-Fi and the difficulty in patching millions of wireless systems, according to researchers.
"Wow. Everyone needs to be afraid," said Rob Graham of Errata Security in a blog post.
"It means in practice, attackers can decrypt a lot of Wi-Fi traffic, with varying levels of difficulty depending on your precise network setup."
Alex Hudson, of the British-based digital service firm Iron Group, said the discovery means that "security built into Wi-Fi is likely ineffective, and we should not assume it provides any security."
Hudson said Wi-Fi users who browse the internet should still be safe due to encryption on most websites but that the flaw could affect a number of internet-connected devices.
"Almost certainly there are other problems that will come up, especially privacy issues with cheaper Internet-enabled devices that have poor security," Hudson said in a blog post.
Researchers at Finland-based security firm F-Secure said in a statement the discovery highlights longstanding concerns about Wi-Fi systems' vulnerability.
"The worst part of it is that it's an issue with Wi-Fi protocols, which means it affects practically every single person in the world that uses Wi-Fi networks," F-Secure said in a statement.
The F-Secure researchers said wireless network users can minimize the risks by using virtual private networks, and by updating devices including routers.
The Wi-Fi Alliance, an industry group which sets standards for wireless connections, said computer users should not panic.
"There is no evidence that the vulnerability has been exploited maliciously, and Wi-Fi Alliance has taken immediate steps to ensure users can continue to count on Wi-Fi to deliver strong security protections," the group said in a statement.
"Wi-Fi Alliance now requires testing for this vulnerability within our global certification lab network and has provided a vulnerability detection tool for use by any Wi-Fi Alliance member."
Microsoft said it released a patch on October 10 to protect users of Windows devices. "Customers who have Windows Update enabled and applied the security updates, are protected automatically," Microsoft said.
A Google spokesman said, "We're aware of the issue, and we will be patching any affected devices in the coming weeks."
Hackers Use New Flash Zero-Day Exploit to Distribute FinFisher Spyware
17.10.2017 thehackernews Vulnerebility
FinSpy—the infamous surveillance malware is back and infecting high-profile targets using a new Adobe Flash zero-day exploit delivered through Microsoft Office documents.
Security researchers from Kaspersky Labs have discovered a new zero-day remote code execution vulnerability in Adobe Flash, which was being actively exploited in the wild by a group of advanced persistent threat actors, known as BlackOasis.
The critical type confusion vulnerability, tracked as CVE-2017-11292, could lead to code execution and affects Flash Player 21.0.0.226 for major operating systems including Windows, Macintosh, Linux and Chrome OS.
Researchers say BlackOasis is the same group of attackers which were also responsible for exploiting another zero-day vulnerability (CVE-2017-8759) discovered by FireEye researchers in September 2017.
Also, the final FinSpy payload in the current attacks exploiting Flash zero-day (CVE-2017-11292) shares the same command and control (C&C) server as the payload used with CVE-2017-8759 (which is Windows .NET Framework remote code execution).
So far BlackOasis has targeted victims in various countries including Russia, Iraq, Afghanistan, Nigeria, Libya, Jordan, Tunisia, Saudi Arabia, Iran, the Netherlands, Bahrain, United Kingdom and Angola.
The newly reported Flash zero-day exploit is at least the 5th zero-day that BlackOasis group exploited since June 2015.
The zero-day exploit is delivered through Microsoft Office documents, particularly Word, attached to a spam email, and embedded within the Word file includes an ActiveX object which contains the Flash exploit.
The exploit deploys the FinSpy commercial malware as the attack's final payload.
"The Flash object contains an ActionScript which is responsible for extracting the exploit using a custom packer seen in other FinSpy exploits," the Kaspersky Labs researchers say.
FinSpy is a highly secret surveillance tool that has previously been associated with Gamma Group, a British company that legally sells surveillance and espionage software to government agencies across the world.
FinSpy, also known as FinFisher, has extensive spying capabilities on an infected system, including secretly conducting live surveillance by turning ON its webcams and microphones, recording everything the victim types on the keyboard, intercepting Skype calls, and exfiltration of files.
To get into a target's system, FinSpy usually makes use of various attack vectors, including spear phishing, manual installation with physical access to the affected device, zero-day exploits, and watering hole attacks.
"The attack using the recently discovered zero-day exploit is the third time this year we have seen FinSpy distribution through exploits to zero-day vulnerabilities," said Anton Ivanov, lead malware analyst at Kaspersky Lab.
"Previously, actors deploying this malware abused critical issues in Microsoft Word and Adobe products. We believe the number of attacks relying on FinSpy software, supported by zero day exploits such as the one described here, will continue to grow."
Kaspersky Lab reported the vulnerability to Adobe, and the company has addressed the vulnerability with the release of Adobe Flash Player versions 27.0.0.159 and 27.0.0.130.
Just last month, ESET researchers discovered legitimate downloads of several popular apps like WhatsApp, Skype, VLC Player and WinRAR (reportedly compromised at the ISP level) that were also distributing FinSpy.
So, businesses and government organizations around the world are strongly recommended to install the update from Adobe as soon as possible.
Microsoft will also likely be releasing a security update to patch the Flash Player components used by its products.
KRACK Demo: Critical Key Reinstallation Attack Against Widely-Used WPA2 Wi-Fi Protocol
17.10.2017 thehackernews Attack
Do you think your wireless network is secure because you're using WPA2 encryption?
If yes, think again!
Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an attacker to hack into your Wi-Fi network and eavesdrop on the Internet communications.
WPA2 is a 13-year-old WiFi authentication scheme widely used to secure WiFi connections, but the standard has been compromised, impacting almost all Wi-Fi devices—including in our homes and businesses, along with the networking companies that build them.
Dubbed KRACK—Key Reinstallation Attack—the proof-of-concept attack demonstrated by a team of researchers works against all modern protected Wi-Fi networks and can be abused to steal sensitive information like credit card numbers, passwords, chat messages, emails, and photos.
Since the weaknesses reside in the Wi-Fi standard itself, and not in the implementations or any individual product, any correct implementation of WPA2 is likely affected.
According to the researchers, the newly discovered attack works against:
Both WPA1 and WPA2,
Personal and enterprise networks,
Ciphers WPA-TKIP, AES-CCMP, and GCMP
In short, if your device supports WiFi, it is most likely affected. During their initial research, the researchers discovered that Android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys, and others, are all affected by the KRACK attacks.
It should be noted that the KRACK attack does not help attackers recover the targeted WiFi's password; instead, it allows them to decrypt WiFi users' data without cracking or knowing the actual password.
So merely changing your Wi-Fi network password does not prevent (or mitigate) KRACK attack.
Discovered by researcher Mathy Vanhoef of imec-DistriNet, KU Leuven, the KRACK attack works by exploiting a 4-way handshake of the WPA2 protocol that's used to establish a key for encrypting traffic.
For a successful KRACK attack, an attacker needs to trick a victim into re-installing an already-in-use key, which is achieved by manipulating and replaying cryptographic handshake messages.
"When the victim reinstalls the key, associated parameters such as the incremental transmit packet number (i.e. nonce) and receive packet number (i.e. replay counter) are reset to their initial value," the researcher writes.
"Essentially, to guarantee security, a key should only be installed and used once. Unfortunately, we found this is not guaranteed by the WPA2 protocol. By manipulating cryptographic handshakes, we can abuse this weakness in practice."
The research [PDF], titled Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2, has been published by Mathy Vanhoef of KU Leuven and Frank Piessens of imec-DistriNet, Nitesh Saxena and Maliheh Shirvanian of the University of Alabama at Birmingham, Yong Li of Huawei Technologies, and Sven Schäge of Ruhr-Universität Bochum.
The team has successfully executed the key reinstallation attack against an Android smartphone, showing how an attacker can decrypt all data that the victim transmits over a protected WiFi. You can watch the proof-of-concept (PoC) video demonstration above.
"Decryption of packets is possible because a key reinstallation attack causes the transmit nonces (sometimes also called packet numbers or initialization vectors) to be reset to zero. As a result, the same encryption key is used with nonce values that have already been used in the past," the researcher say.
The researchers say their key reinstallation attack could be exceptionally devastating against Linux and Android 6.0 or higher, because "Android and Linux can be tricked into (re)installing an all-zero encryption key (see below for more info)."
However, there's no need to panic, as you aren't vulnerable to just anyone on the internet because a successful exploitation of KRACK attack requires an attacker to be within physical proximity to the intended WiFi network.
WPA2 Vulnerabilities and their Brief Details
The key management vulnerabilities in the WPA2 protocol discovered by the researchers has been tracked as:
CVE-2017-13077: Reinstallation of the pairwise encryption key (PTK-TK) in the four-way handshake.
CVE-2017-13078: Reinstallation of the group key (GTK) in the four-way handshake.
CVE-2017-13079: Reinstallation of the integrity group key (IGTK) in the four-way handshake.
CVE-2017-13080: Reinstallation of the group key (GTK) in the group key handshake.
CVE-2017-13081: Reinstallation of the integrity group key (IGTK) in the group key handshake.
CVE-2017-13082: Accepting a retransmitted Fast BSS Transition (FT) Reassociation Request and reinstalling the pairwise encryption key (PTK-TK) while processing it.
CVE-2017-13084: Reinstallation of the STK key in the PeerKey handshake.
CVE-2017-13086: reinstallation of the Tunneled Direct-Link Setup (TDLS) PeerKey (TPK) key in the TDLS handshake.
CVE-2017-13087: reinstallation of the group key (GTK) while processing a Wireless Network Management (WNM) Sleep Mode Response frame.
CVE-2017-13088: reinstallation of the integrity group key (IGTK) while processing a Wireless Network Management (WNM) Sleep Mode Response frame.
The researchers discovered the vulnerabilities last year, but sent out notifications to several vendors on July 14, along with the United States Computer Emergency Readiness Team (US-CERT), who sent out a broad warning to hundreds of vendors on 28 August 2017.
"The impact of exploiting these vulnerabilities includes decryption, packet replay, TCP connection hijacking, HTTP content injection, and others," the US-CERT warned. "Note that as protocol-level issues, most or all correct implementations of the standard will be affected."
In order to patch these vulnerabilities, you need to wait for the firmware updates from your device vendors.
According to researchers, the communication over HTTPS is secure (but may not be 100 percent secure) and cannot be decrypted using the KRACK attack. So, you are advised to use a secure VPN service—which encrypts all your Internet traffic whether it’s HTTPS or HTTP.
You can read more information about these vulnerabilities on the KRACK attack's dedicated website, and the research paper.
The team has also promised to release a tool using which you can check whether if your WiFi network is vulnerable to the KRACK attack or not.
We will keep updating the story. Stay Tuned!
Update: Patches for Linux's hostapd (Host access point daemon) and WPA Supplicant are now available.
How A Drive-by Download Attack Locked Down Entire City for 4 Days
17.10.2017 thehackernews Attack
How A Drive-by Download Attack Locked Down Data of this City for 4 Days
We don't really know the pain and cost of a downtime event unless we are directly touched.
Be it a flood, electrical failure, ransomware attack or other broad geographic events; we don't know what it is really like to have to restore IT infrastructure unless we have had to do it ourselves.
We look at other people's backup and recovery issues and hope we are smarter or clever enough to keep it from happening to us.
Recovery from a downtime event includes inconvenience, extra work, embarrassment and yes, real pain.
A ransomware attack is a good example.
Unitrends—an American company specialised in backup and business continuity solutions—recently shared with us a real cyber-attack incident happened with one of their customers to describe the required steps they took to recover functionality following a CryptoLocker attack against a US city.
Also, how it cost city's Governance team days of production and hundreds of man-hours to recover.
The Challenge
Issaquah is a small city of 30,434 people in Washington, United States. According to Forbes, they are the 2nd fastest growing suburb in the state of Washington.
John T, IT Manager leads a team of five employees who execute all IT initiatives co-developed with the city's IT Governance team. John's team manages all technology, from phones, networks, servers, desktops, applications and cloud services.
The city has only two IT staff dedicated to infrastructure.
"We are spread so thin that logs are not monitored consistently," reports John. "We are slowly recovering from a decade of underinvestment in IT and have a large backlog of software, hardware and network upgrades."
Part of that underinvestment is that they continued to rely on a tape drive that was ten years old using Backup Exec.
They continued to stumble along until they were hit with a CryptoLocker ransomware attack.
The Infection
Here below find the complete story shared by John with us:
In the final analysis, we believe the ransomware attack originated from a "drive-by" where a single city employee visited and opened a .pdf file that had been compromised on a grant coordination site run by a non-profit. This is not an uncommon risk—a small company or organisation website that doesn’t have IT funding to keep up with the security risks in today’s lightspeed world.
Most entries in the User’s Log file were harmless, though the way this virus worked, it could have been downloaded at any time but still needed to be executed by the user. It could have been sitting on the hard drive for weeks (looking like a .pdf) before being executed, though we would need to interview the user to see if she remembers anything like this. This ransomware appeared to disable our anti-virus systems, and is known to remove all traces once finished.
This virus ran only in PC memory and did not turn up on any other devices in our system. It only attacked Microsoft Office, image, .pdf, and text files in folders on the user’s PC and file shares to which the user had to write access. It stopped encrypting files once the PC was restarted in safe mode. The lack of propagation could have been a result of either the virus being designed to reside solely in memory to prevent triggering alarms or because our anti-virus software intercepted it at other devices as it attempted to propagate.
The physical server that hosted the file also hosted five critical virtual application servers. After careful analysis, it was determined these were not compromised. We immediately moved these virtual machines onto a different host. This was done prior to kicking off the server restore to reduce processor and NIC load on the file server host.
When we began the file server restore process it quickly became apparent it would take a long time… four days as it turned out. A quick analysis revealed we had no other options to restore the file server. The backup.exe device did work and never failed or stopped during the restore process. It seems the scale of the restore was too big for the device capacity and it had to chunk the workout, making the process very long.
Fortunately for us, the attack had happened on a Thursday, so only Thursday and Friday office productivity was lost. Even so, our users were very negatively impacted and quite upset (as were we). This led to funding being released to move to a modern backup appliance.
The Real Cost to Recover from a Ransomware Attack
John said senior executives agreed to fund an upgrade to the backup system, and after a vendor selection process, his team chose what it felt was the best combination of features and capacity with reasonable costs.
If the same Ransomware attack occurred today with data backed up on the Unitrends Recovery Series 933S appliance the results would have been much different.
First, the attack would have been discovered very quickly as all Unitrends appliances include predictive analytic software and machine learning that will automatically recognise the effects of ransomware on backup files.
An email would then automatically be sent to administrators warning of the attack and identifying the affected files. Then the disaster recovery plan they had in place would be executed.
Secondly, deleting, reinstalling affected files and restarting affected servers would take minutes, not hours and probably not four days.
Critical applications could have been spun up instantly on the backup appliance using the last good backups made before the infection. This would greatly limit the negative impact on employees and office productivity.
The Results
There have been several backup and recovery incidents since the Unitrends Appliance was installed, reported John.
"We have used our backup appliance to recover files that were accidentally deleted by end users. We had also used it to recover virtual machines when we had a host system failure. The downtime in the latter case was limited to staff response time as the mission-critical backup VM was up in less than five minutes!"
"We also plan on moving to the cloud very soon since the Unitrends appliance comes with integrated cloud software. The biggest benefits we expect to see from the cloud are low-cost off-site storage, the ability to recover applications in the cloud if needed as a DraaS feature, and access from anywhere in case of a natural disaster type emergency."
"We now have peace of mind knowing that we can recover quickly when needed. We also have increased shared team knowledge on backup and DR with the easy-to-use user interface."
Yet Another Linux Kernel Privilege-Escalation Bug Discovered
17.10.2017 thehackernews Vulnerebility
Security researchers have discovered a new privilege-escalation vulnerability in Linux kernel that could allow a local attacker to execute code on the affected systems with elevated privileges.
Discovered by Venustech ADLab (Active-Defense Lab) researchers, the Linux kernel vulnerability (CVE-2017-15265) is due to a use-after-free memory error in the Advanced Linux Sound Architecture (ALSA) sequencer interface of the affected application.
The Advanced Linux Sound Architecture (ALSA) provides audio and MIDI functionality to the Linux operating system, and also bundles a userspace driven library for application developers, enabling direct (kernel) interaction with sound devices through ALSA libraries.
Successful exploitation of this vulnerability requires an attacker—with local access on the targeted system—to execute a maliciously crafted application on a targeted system, which allows the attacker to elevate his privilege to root on the targeted system, a Cisco advisory warned.
The vulnerability affects major distributions of the Linux operating system including RedHat, Debian, Ubuntu, and Suse, and is triggered by a slip in snd_seq_create_port().
This "snd_seq_create_port() creates a port object and returns its pointer, but it doesn't take the refcount, thus it can be deleted immediately by another thread," the researchers wrote in an advisory published Wednesday.
"Meanwhile, snd_seq_ioctl_create_port() still calls the function snd_seq_system_client_ev_port_start() with the created port object that is being deleted, and this triggers use-after-free."
The vulnerability has been patched in Linux kernel version 4.13.4-2, which was fixed just by taking the refcount properly at "snd_seq_create_port()" and letting the caller unref the object after use.
Administrators are advised to apply the appropriate updates on their Linux distributions as soon as they receive them from their respective distro. They're also recommended to allow only trusted users to access local systems and always monitor affected systems.
This flaw is yet another privilege escalation vulnerability recently uncovered in the Linux kernel.
Last month, a high-risk 2-year-old potential local privilege escalation flaw was patched in the Linux kernel that affected all major Linux distributions, including Red Hat, Debian, and CentOS.
In February, another privilege-escalation vulnerability that dates back to 2011 disclosed and patched in the Linux kernel which also affected major Linux distro, including Redhat, Debian, OpenSUSE, and Ubuntu.
BlackOasis APT leverages new Flash zero-day exploit to deploy FinSpy
17.10.2017 securityaffairs Vulnerebility APT
Security researchers from Kaspersky Labs spotted the BlackOasis APT group exploiting a new zero-day RCE vulnerability in Adobe Flash.
Security researchers from Kaspersky Labs have discovered a new zero-day remote code execution vulnerability in Adobe Flash, tracked as CVE-2017-11292, which was being actively exploited by hackers in the wild to deliver the surveillance software FinSpy.

Hackers belonging to the APT group known as BlackOasis are leveraging the Adobe Flash zero-day exploit in attacks against high-profile targets.
The critical type confusion vulnerability affects Flash Player 21.0.0.226 for Windows, Macintosh, Linux and Chrome OS.
“On October 10, 2017, Kaspersky Lab’s advanced exploit prevention systems identified a new Adobe Flash zero day exploit used in the wild against our customers. The exploit was delivered through a Microsoft Office document and the final payload was the latest version of FinSpy malware. We have reported the bug to Adobe who assigned it CVE-2017-11292 and released a patch earlier today:” reads the analysis published by Kaspersky.
The experts speculate the BlackOasis APT group is the same crew that exploited another RCE zero-day vulnerability, tracked CVE-2017-8759, discovered by FireEye researchers in September 2017.
According to FireEye, the CVE-2017-8759 was actively been exploited by an APT group to deliver the surveillance malware FinFisher Spyware (FinSpy) to a Russian-speaking “entity” via malicious Microsoft Office RTF files in July.
In both attacks, the BlackOasis APT exploited a zero-day exploit to deliver the FinSpy spyware, the hackers shared the same command and control (C&C).
The experts who monitored the activity of the BlackOasis group across the year confirmed it has utilized at least five zero days since June 2015:
CVE-2015-5119 – June 2015
CVE-2016-0984 – June 2015
CVE-2016-4117 – May 2016
CVE-2017-8759 – Sept 2017
CVE-2017-11292 – Oct 2017
BlackOasis hackers targeted individuals in numerous countries, including Russia, Iraq, Afghanistan, Nigeria, Libya, Jordan, Tunisia, Saudi Arabia, Iran, the Netherlands, Bahrain, United Kingdom and Angola.
“BlackOasis’ interests span a wide gamut of figures involved in Middle Eastern politics and verticals disproportionately relevant to the region. This includes prominent figures in the United Nations, opposition bloggers and activists, and regional news correspondents.” continues the analysis. “During 2016, we observed a heavy interest in Angola, exemplified by lure documents indicating targets with suspected ties to oil, money laundering, and other illicit activities. There is also an interest in international activists and think tanks.”
Researchers reported the zero-day exploit is delivered through Microsoft Office documents, particularly Word, attached to a spam email. The documents include an ActiveX object which contains the Flash exploit used to deliver the FinSpy spyware.
“The Flash object contains an ActionScript which is responsible for extracting the exploit using a custom packer seen in other FinSpy exploits,” the Kaspersky Labs researchers say.
FinSpy leveraged various attack vectors, including spear phishing, manual installation with physical access to the affected device, zero-day exploits, and watering hole attacks.
According to the experts, the number of attacks relying on FinFisher software, supported by zero-day exploits will continue to grow.
“The attack using the recently discovered zero-day exploit is the third time this year we have seen FinSpy distribution through exploits to zero-day vulnerabilities,” conclude Kaspersky Lab lead malware analyst Anton Ivanov
“Previously, actors deploying this malware abused critical issues in Microsoft Word and Adobe products. We believe the number of attacks relying on FinSpy software, supported by zero day exploits such as the one described here, will continue to grow.”
Kaspersky Lab reported the flaw to Adobe that addressed it with the release of Adobe Flash Player versions 27.0.0.159 and 27.0.0.130.
Wifi networks are vulnerable to WPA KRACK attack
17.10.2017 securityaffairs Attack
The KRACK attack allows an attacker to decrypt information included in protected WPA2 traffic. WPA2 standard has been compromised!
Boffins have discovered several key management flaws in the core of Wi-Fi Protected Access II (WPA2) protocol that could be exploited by an attacker to hack into Wi-Fi network and eavesdrop on the Internet communications0 stealing sensitive information (i.e. credit card numbers, passwords, chat messages, emails, and pictures).
WPA2 standard has been compromised, the flaws, in fact, reside in the Wi-Fi standard itself, and not in the numerous implementations.
The impact could be serious for both companies and home users, any working implementation of WPA2 is likely affected, the only limitation is that an attacker needs to be within the range of a victim to exploit the weaknesses.
The researchers devised an attack method dubbed KRACK attack (Key Reinstallation Attack), it works against almost any WPA2 Wi-Fi network.
The KRACK attack allows attackers to decrypt WiFi users’ data without cracking or knowing the password.
According to the researchers, the KRACK attack works against:
Both WPA1 and WPA2,
Personal and enterprise networks,
Ciphers WPA-TKIP, AES-CCMP, and GCMP
Initially, the researchers discovered that the vulnerabilities affect Android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys.
The vulnerabilities were found by the Belgian researcher Mathy Vanhoef of imec-DistriNet, KU Leuven.
The KRACK attack works by exploiting a 4-way handshake of the WPA2 protocol that’s used to establish a key for encrypting traffic.
“When the victim reinstalls the key, associated parameters such as the incremental transmit packet number (i.e. nonce) and receive packet number (i.e. replay counter) are reset to their initial value,” explained Vanhoef. “Essentially, to guarantee security, a key should only be installed and used once. Unfortunately, we found this is not guaranteed by the WPA2 protocol. By manipulating cryptographic handshakes, we can abuse this weakness in practice.”

The attacker just needs to trick a victim into re-installing an already-in-use key, which is achieved by manipulating and replaying cryptographic handshake messages.
The experts demonstrated how to execute the key reinstallation attack against an Android smartphone in order to decrypt a transmission over a protected WiFi.
According to the experts, the attack is exceptionally effective against Linux and Android 6.0 or higher, because “Android and Linux can be tricked into (re)installing an all-zero encryption key (see below for more info).”
“Although websites or apps may use HTTPS as an additional layer of protection, we warn that this extra protection can (still) be bypassed in a worrying number of situations. ” added the expert.
“Adversaries can use this attack to decrypt packets sent by clients, allowing them to intercept sensitive information such as passwords or cookies.” the researcher say.
“Decryption of packets is possible because a key reinstallation attack causes the transmit nonces (sometimes also called packet numbers or initialization vectors) to be reset to zero. As a result, the same encryption key is used with nonce values that have already been used in the past,”
Below the full list of WPA2 Vulnerabilities discovered in the WPA2 protocol.
CVE-2017-13077: Reinstallation of the pairwise encryption key (PTK-TK) in the 4-way handshake.
CVE-2017-13078: Reinstallation of the group key (GTK) in the 4-way handshake.
CVE-2017-13079: Reinstallation of the integrity group key (IGTK) in the 4-way handshake.
CVE-2017-13080: Reinstallation of the group key (GTK) in the group key handshake.
CVE-2017-13081: Reinstallation of the integrity group key (IGTK) in the group key handshake.
CVE-2017-13082: Accepting a retransmitted Fast BSS Transition (FT) Reassociation Request and reinstalling the pairwise encryption key (PTK-TK) while processing it.
CVE-2017-13084: Reinstallation of the STK key in the PeerKey handshake.
CVE-2017-13086: reinstallation of the Tunneled Direct-Link Setup (TDLS) PeerKey (TPK) key in the TDLS handshake.
CVE-2017-13087: reinstallation of the group key (GTK) when processing a Wireless Network Management (WNM) Sleep Mode Response frame.
CVE-2017-13088: reinstallation of the integrity group key (IGTK) when processing a Wireless Network Management (WNM) Sleep Mode Response frame.
The experts discovered the flaws last year and notified several vendors on July 14, the US-CERT also issued an alert to hundreds of vendors on 28 August 2017.
“US-CERT has become aware of several key management vulnerabilities in the 4-way handshake of the Wi-Fi Protected Access II (WPA2) security protocol. The impact of exploiting these vulnerabilities includes decryption, packet replay, TCP connection hijacking, HTTP content injection, and others. Note that as protocol-level issues, most or all correct implementations of the standard will be affected. The CERT/CC and the reporting researcher KU Leuven, will be publicly disclosing these vulnerabilities on 16 October 2017.” the US-CERT warned.
Users have to wait for firmware updates from their device vendors, security patches for Linux’s hostapd (Host access point daemon) and WPA Supplicant are already available.
Further details on the KRACK attack are included in the research paper titled “Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2”
The research team also plans to release a tool for the assessment of WiFi network.
Russia Fines Telegram For Not Giving Backdoor Access
16.10.2017 securityweek BigBrothers
A Russian court on Monday fined the popular Telegram messenger app for failing to provide the country's security services with encryption keys to read users' messaging data.
The court imposed an 800,000-ruble fine (about $14,000/12,000 euros) over Telegram's failure to "provide law enforcement agencies with information" about its users and their messages, TASS news agency reported.
The free instant messaging app, which lets people exchange messages, photos and videos in groups of up to 5,000 people, has attracted about 100 million users since its launch in 2013.
Telegram's self-exiled Russian founder Pavel Durov said in September the FSB had demanded backdoor access.
When Telegram did not provide the encryption keys, the FSB launched a formal complaint.
According to a scan of the complaint posted online by Durov, the FSB had sent a letter to Telegram in July demanding "information necessary to decode users' sent, received, delivered and processed electronic messages".
The fine is the latest move in an ongoing dispute between Telegram and the Russian authorities as Moscow pushes to increase surveillance of internet activities.
In June, Russia's state communications watchdog threatened to ban the app for failing to provide registration documents. Although Telegram later registered, it stopped short of agreeing to its data storage demands.
Companies on the register must provide the FSB with information on user interactions.
Starting from 2018, they must also keep all data from users in Russia according to controversial anti-terror legislation passed last year which was decried by internet companies and the opposition.
Telegram now has 10 days to appeal Monday's decision. If an appeal fails, the company will be given a grace period to hand over its encryption keys after which it could be blocked in Russia.
Asked about a potential block of the service, Kremlin spokesman Dmitry Peskov said: "As far as I know... there is no discussion of a block at this time."
'Tick' Cyber Espionage Group Linked to China
16.10.2017 securityweek BigBrothers
The cyber espionage group known as Bronze Butler and Tick continues to target Japan using custom-built malware. Evidence found by researchers suggests that the actor is based in China.
The first report on Tick was published in April 2016 by Symantec. However, the security firm pointed out at the time that the threat group had likely been active for at least a decade prior to its activities being discovered.
Tick has been known to use a downloader tracked as Gofarer and a data-stealing Trojan dubbed Daserf. A report published by Palo Alto Networks earlier this year linked the custom-built Daserf malware – based on command and control (C&C) servers – to a threat known as Minzen, XXMM, Wali and ShadowWali.
The first Tick attacks detailed by Symantec focused on technology, aquatic engineering, and broadcasting firms in Japan. Palo Alto Networks reported seeing campaigns aimed at defense and high-tech organizations in Japan and South Korea.
A new report published last week by SecureWorks links Tick to China based on several pieces of evidence. For example, the group uses T-SMB Scan tools created by a Chinese developer, an early version of the Minzen backdoor used Chinese characters in a service name, and there are links between Daserf and the NCPH group, which has been tied to the Chinese military.
Experts also pointed out that Tick activity has typically decreased during Chinese national holidays, and targeting intellectual property and economic intelligence from competing countries is something China has been known to do.
The attacks observed by the security firm were aimed at Japanese organizations in the critical infrastructure, manufacturing, heavy industry and international relations sectors. The hackers have mainly targeted intellectual property related to technology and development, business and sales information, emails and meeting schedules, product specifications, and network and system configuration files.
The report from SecureWorks also provides some information on Datper, a piece of malware used in 2016 and 2017, which experts believe was meant to replace Daserf. XXMM has been used by the threat actor in roughly the same period.
The Tick group has continued to use spear-phishing and watering hole attacks to breach the systems of its targets. However, SecureWorks has also seen attacks involving a zero-day vulnerability affecting a popular Japanese corporate tool.
The zero-day has been used to breach the systems of numerous Japanese organizations, but the hackers only proceeded with further activities in the case of companies that presented an interest. In some cases, the attackers managed to remain undetected within compromised networks for as much as five years.
Once it no longer needs any information from a target, Tick attempts to remove all evidence of its activities on the compromised networks.
Pizza Hut notifies card breach while users have already reported fraudulent transactions
16.10.2017 securityaffairs Incindent
Pizza Hut U.S. notified customers over the weekend a “temporary security intrusion” on PizzaHut.com that exposed payment card and contact information.
Pizza Hut U.S. notified customers over the weekend a “temporary security intrusion” on PizzaHut.com, the security breach might have exposed payment card and contact information.
The popular restaurant chain notified users via email, according to Pizza Hut, the hackers had access to the website for a total of roughly 28 hours, between the morning of October 1, 2017 through midday on October 2, 2017.
“Pizza Hut has recently identified a temporary security intrusion that occurred on our website,” reads the email sent by Pizza Hut.
“We have learned that the information of some customers who visited our website or mobile application during an approximately 28-hour period (from the morning of October 1, 2017, through midday on October 2, 2017) and subsequently placed an order may have been compromised.”
“Pizza Hut identified the security intrusion quickly and took immediate action to halt it,” the company added. “The security intrusion at issue impacted a small percentage of our customers and we estimate that less than one percent of the visits to our website over the course of the relevant week were affected.”

All those users that placed an order in this time window could be affected, the company estimates that less than one percent of website visits during that week were impacted.
Some of those customers are angry because of the delay in the notification, some of them also faced problems with their payment cards.
Follow
Peter Yoachim @PeterYoachim
Hey @pizzahut, thanks for telling me you got hacked 2 weeks after you lost my cc number. And a week after someone started using it.#timely
7:03 PM - Oct 14, 2017 · Seattle, WA
4 4 Replies 2 2 Retweets 3 3 likes
Twitter Ads info and privacy
Follow
Michael Richardson @marichardsonjr
@pizzahut great security there & thanks for the delay in notifying us after thieves already charged our accts. Keep up the excellent work
9:47 PM - Oct 14, 2017
1 1 Reply 2 2 Retweets 3 3 likes
Twitter Ads info and privacy
Follow
Dustin Falgout @dustinfalgout
@pizzahut, 2 wks after you lost my cc # and a week after someone started using it, I hear about the breach online. Ty 4 the heads up. #fail
10:54 PM - Oct 15, 2017
1 1 Reply Retweets likes
Twitter Ads info and privacy
External cybersecurity consultants hired by the company determined that the attackers may have obtained information such as name, billing ZIP code, delivery address, email address, and payment card data, including card number, expiration date and CVV.
Pizza Hut estimates that less than one percent of website visits during that week were impacted.
“The security intrusion at issue impacted a small percentage of our customers and we estimate that less than one percent of the visits to our website over the course of the relevant week were affected,” read a message sent only to those affected. “That said, we regret to say that we believe your information is among that impacted group.”
A call center operator told McClatchy that about 60,000 people across the U.S. were affected.
The restaurant chain was already a victim of a security breach, in 2012 two hackers that went by the names of Oday and Pyknic defaced the company’s Australia website and claimed to have obtained roughly 260,000 Australian payment cards.
Many other restaurant chains reported suffering a security breach in the past months, including Arby’s, Chipotle. Wendy’s, and Sonic Drive-In.
Linux kernel affected by a local privilege escalation vulnerability
16.10.2017 securityaffairs Vulnerebility
Cisco issued a security advisory on a local privilege escalation vulnerability in the Linux Kernel, patch it as soon as possible.
On Friday, Cisco issued a security advisory on a local privilege escalation vulnerability in the Advanced Linux Sound Architecture (ALSA).
The vulnerability in the Linux Kernel, tracked as CVE-2017-15265, is due to a use-after-free memory error in the ALSA sequencer interface, an attacker could exploit it by running a crafted application on a vulnerable system.
“A vulnerability in the Linux Kernel could allow a local attacker to gain elevated privileges on a targeted system.” reads the Cisco security advisory.
“The vulnerability is due to a use-after-free memory error in the ALSA sequencer interface of the affected application. An attacker could exploit this vulnerability by running a crafted application on a targeted system. A successful exploit could allow the attacker to gain elevated privileges on the targeted system.”
According to a discussion at SUSE’s Bugzilla, a patch for the Linux Kernel vulnerability was added to the ALSA git tree on October 11, .
“We may fix this in a few different ways, and in this patch, it’s fixed simply by taking the refcount properly at snd_seq_create_port() and letting the caller unref the object after use.” states the description on the ALSA git tree.
The use-after-free is triggered by a bug in snd_seq_create_port() as explained in the advisory:
“There is a potential race window opened at creating and deleting a port via ioctl, as spotted by fuzzing. snd_seq_create_port() creates a port object and returns its pointer, but it doesn’t take the refcount, thus it can be deleted immediately by another thread. Meanwhile, snd_seq_ioctl_create_port() still calls the function snd_seq_system_client_ev_port_start() with the created port object that is being deleted, and this triggers use-after-free” continues the description.
Kernel.org has confirmed the vulnerability, the good news is that to exploit this vulnerability, the attacker must have local access to the targeted system, a circumstance that drastically reduces the likelihood of a successful exploit.
Key Reinstallation Attacks
16.10.2017 Attack
Breaking WPA2 by forcing nonce reuse
INTRODUCTION
We discovered serious weaknesses in WPA2, a protocol that secures all modern protected Wi-Fi networks. An attacker within range of a victim can exploit these weaknesses using key reinstallation attacks (KRACKs). Concretely, attackers can use this novel attack technique to read information that was previously assumed to be safely encrypted. This can be abused to steal sensitive information such as credit card numbers, passwords, chat messages, emails, photos, and so on. The attack works against all modern protected Wi-Fi networks. Depending on the network configuration, it is also possible to inject and manipulate data. For example, an attacker might be able to inject ransomware or other malware into websites.
The weaknesses are in the Wi-Fi standard itself, and not in individual products or implementations. Therefore, any correct implementation of WPA2 is likely affected. To prevent the attack, users must update affected products as soon as security updates become available. Note that if your device supports Wi-Fi, it is most likely affected. During our initial research, we discovered ourselves that Android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys, and others, are all affected by some variant of the attacks. For more information about specific products, consult the database of CERT/CC, or contact your vendor.
The research behind the attack will be presented at the Computer and Communications Security (CCS) conference, and at the Black Hat Europe conference. Our detailed research paper can already be downloaded.
DEMONSTRATION Our attack is not limited to recovering login credentials (i.e. e-mail addresses and passwords). In general, any data or information that the victim transmits can be decrypted. Additionally, depending on the device being used and the network setup, it is also possible to decrypt data sent towards the victim (e.g. the content of a website). Although websites or apps may use HTTPS as an additional layer of protection, we warn that this extra protection can (still) be bypassed in a worrying number of situations. For example, HTTPS was previously bypassed in non-browser software, in Apple's iOS and OS X, in Android apps, in Android apps again, in backing apps, and even in VPN apps. DETAILS Key reinstallation attacks: high level description Key reinstallation attacks: concrete example against the 4-way handshake Practical impact The ability to decrypt packets can be used to decrypt TCP SYN packets. This allows an adversary to obtain the TCP sequence numbers of a connection, and hijack TCP connections. As a result, even though WPA2 is used, the adversary can now perform one of the most common attacks against open Wi-Fi networks: injecting malicious data into unencrypted HTTP connections. For example, an attacker can abuse this to inject ransomware or malware into websites that the victim is visiting. If the victim uses either the WPA-TKIP or GCMP encryption protocol, instead of AES-CCMP, the impact is especially catastrophic. Against these encryption protocols, nonce reuse enables an adversary to not only decrypt, but also to forge and inject packets. Moreover, because GCMP uses the same authentication key in both communication directions, and this key can be recovered if nonces are reused, it is especially affected. Note that support for GCMP is currently being rolled out under the name Wireless Gigabit (WiGig), and is expected to be adopted at a high rate over the next few years. The direction in which packets can be decrypted (and possibly forged) depends on the handshake being attacked. Simplified, when attacking the 4-way handshake, we can decrypt (and forge) packets sent by the client. When attacking the Fast BSS Transition (FT) handshake, we can decrypt (and forge) packets sent towards the client. Finally, most of our attacks also allow the replay of unicast, broadcast, and multicast frames. For further details, see Section 6 of our research paper. Note that our attacks do not recover the password of the Wi-Fi network. They also do not recover (any parts of) the fresh encryption key that is negotiated during the 4-way handshake. Android and Linux Assigned CVE identifiers CVE-2017-13077: Reinstallation of the pairwise encryption key (PTK-TK) in the 4-way handshake. PAPER Although this paper is made public now, it was already submitted for review on 19 May 2017. After this, only minor changes were made. As a result, the findings in the paper are already several months old. In the meantime, we have found easier techniques to carry out our key reinstallation attack against the 4-way handshake. With our novel attack technique, it is now trivial to exploit implementations that only accept encrypted retransmissions of message 3 of the 4-way handshake. In particular this means that attacking macOS and OpenBSD is significantly easier than discussed in the paper. We would like to highlight the following addendums and errata: Addendum: wpa_supplicant v2.6 Selected errata We also made a proof-of-concept script that exploits the all-zero key (re)installation present in certain Android and Linux devices. This script is the one that we used in the demonstration video. It will be released once everyone had a reasonable chance to update their devices (and we had a change to prepare the code repository for release). We remark that the reliability of our proof-of-concept script may depend on how close the victim is to the real network. If the victim is very close to the real network, the script may fail because the victim will always directly communicate with the real network, even if the victim is (forced) on a different Wi-Fi channel than this network. Q&A Should I change my Wi-Fi password? I'm using WPA2 with only AES. That's also vulnerable? You use the word "we" in this website. Who is we? Is my device vulnerable? What if there are no security updates for my router? How did you discover these vulnerabilities? The 4-way handshake was mathematically proven as secure. How is your attack possible? The longer answer is mentioned in the introduction of our research paper: our attacks do not violate the security properties proven in formal analysis of the 4-way handshake. In particular, these proofs state that the negotiated encryption key remains private, and that the identity of both the client and Access Point (AP) is confirmed. Our attacks do not leak the encryption key. Additionally, although normal data frames can be forged if TKIP or GCMP is used, an attacker cannot forge handshake messages and hence cannot impersonate the client or AP during handshakes. Therefore, the properties that were proven in formal analysis of the 4-way handshake remain true. However, the problem is that the proofs do not model key installation. Put differently, the formal models did not define when a negotiated key should be installed. In practice, this means the same key can be installed multiple times, thereby resetting nonces and replay counters used by the encryption protocol (e.g. by WPA-TKIP or AES-CCMP). Some attacks in paper seem hard Are people exploiting this in the wild? Should I temporarily use WEP until my devices are patched? Will the Wi-Fi standard be updated to address this? Is the Wi-Fi Alliance also addressing these vulnerabilities? The Wi-Fi Alliance has a plan to help remedy the discovered vulnerabilities in WPA2. Summarized, they will: Require testing for this vulnerability within their global certification lab network. How can these types of bugs be prevented? Why the domain name krackattacks.com? Did you get bug bounties for this? How does this attack compare to other attacks against WPA2? Are other protocols also affected by key reinstallation attacks? Is there is higher resolution version of the logo? When did you first notify vendors about the vulnerability? Why did OpenBSD silently release a patch before the embargo? So you expect to find other Wi-Fi vulnerabilities? Swedish transport agencies targeted in DDoS cyber attacks Swedish transport agencies were hit by cyber attacks on Wednesday and Thursday, October 11 and 12, is it Information Warfare? The first attack hit the Sweden Transport Administration (Trafikverket) on Wednesday and paralyzed the IT system that manages train orders triggering the agency in stopping or delaying trains while hackers were powering the attack. Local media reported the Trafikverket email system and website went down, preventing travelers from making reservations or getting information about the delays. The agency used Facebook to provide updates on the situation to the travelers. “The Swedish Transport Administration suffered during the night against Wednesday and during Wednesday morning of major IT disturbances that made the site down, which meant that travelers could not get information about the delays that occurred.” reported the Swedish public broadcaster SVT. “- Several systems were affected by IT interference, including our drive system that shows where the trains are located. Most systems are running now, but the problems are not completely solved, continuing delays are waiting, says Pär Aronsson, Press Communications Officer at the Swedish Transport Administration.” Trafikverket officials confirmed the DDoS attack was aimed at the agency’s service providers TDC and DGC with the intent to affect the agency’s operations. Trafikverket was able to restore service in a few hours, but the delays affected the entire day’s train operations. The day after, another DDoS attack hit the website of another government agency, the Sweden Transport Agency (Transportstyrelsen), and public transport operator Västtrafik. “Public transport operators Västtrafik in western Sweden were also hit by two similar overload attacks on Thursday, briefly crashing its ticket booking app and online travel planner.” reported The Local website. “It could be a prank or someone trying to investigate what kind of protection Trafikverket has,” Patrik Gylesjö, deputy CEO of internet provider DGC told Computer Sweden. Crooks or State-sponsored attacks? It is difficult to attribute the attacks to specific actors with the information available, experts speculate the involvement of a nation-state attacker who was probing Sweden’s transportation infrastructure. Someone noticed that the DDoS attacks hit Swedish transport agencies a week after the Russia conducted the Zapad drills that according to intelligence experts were conducted by Russia to test its cyber capabilities and simulate an attack on all Baltic countries, including the use of cyber weapons. Flaws in Siemens Building Automation Controllers open to hack. Fix them asap Siemens has released a firmware update that addresses two vulnerabilities in its BACnet Field Panel building automation controllers. The vulnerabilities affect APOGEE PXC and TALON TC BACnet automation controllers running a version of the firmware prior to 3.5. Both families of affected devices are widely used in commercial facilities to control a heating, ventilation and air conditioning (HVAC) equipment. This flaw, tracked as CVE-2017-9946, is classified as high severity and obtained a CVSS score of 7.5. According to the security advisory published by the US-CERT, an unauthenticated with access to the integrated webserver attacker can trigger the flaws to download sensitive information. “Successful exploitation of these vulnerabilities could allow unauthenticated attackers with access to the integrated webserver to download sensitive information.” states the US-CERT. The BACnet Field Panel allows facility operators to easily configure, monitor and control the automation controllers. The attackers can bypass the authentication mechanism to download sensitive information from a device. The company downplayed the flaw because the attacker requires network access to the web server. A second security vulnerability tracked as CVE-2017-9947 is a directory traversal issue that could be exploited by an attacker to obtain information on the structure of the file system on vulnerable devices. It is requested the network access to the web server for the exploitation also of this vulnerability. Below the information provided by Siemens: “Vulnerability 1 (CVE-2017-9946) – An attacker with network access to the integrated web server (80/tcp and 443/tcp) could bypass the authentication and download sensitive information from the device. and Siemens addressed both vulnerabilities with the release of firmware version 3.5 for BACnet Field Panel Advanced modules. Affected organizations need to install the security updates as soon as possible. Hacker interview – Speaking with ICEMAN: Banks holes like in Cheese The web journalist Marc Miller has interviewed one of the hackers of the ICEMAN group that claims to be behind the Operation ‘Emmental’ that targeted bank clients. What was your goal of the attack? How many of these operations are you doing at the same time? How many attacks did you already do? Where did you get your C2 servers? Are they yours? What kind of emails do you send to your victims? Is this operation similar to Banrisul? What are your expectations for the future and where do you want to go? In the past. he worked as a web front-end programmer. Also, he is passionate about hardware, hacking, security and marketing. Iranian hackers compromised the UK leader Theresa May’s email account along with other 9,000 emails Iranian hackers compromised 9,000 UK emails in ‘brute force’ cyber attack that was initially attributed to Russian state-sponsored hackers. “According to intelligence officials, the cyberattack “bombarded parliamentary email accounts” but only compromised about 1 percent of the accounts it affected. The attack was initially thought to be the result of amateur hackers and not a nation-state.” reported the Hill. According to The Times, the attack was initially attributed to Russia, but further investigation linked the offensive to Iranian hackers. “Iran carried out a “brute force” cyberattack on parliament that hit dozens of MPs this summer, according to a secret intelligence assessment.” reported The Times “Some 9,000 email accounts, including those belonging to Theresa May and other cabinet ministers, were subjected to a sustained attack on June 23. Ninety accounts were compromised.” “Whitehall officials admitted it was inevitable that the hackers had obtained sensitive material,” the Times reported. The investigation is still ongoing, for this reason, both The House of Commons and the National Cyber Security Centre did not comment the attack. Iranian hackers hit UK parliament The attack was discovered during a secret intelligence assessment, sources described the Iranian threat actors as “highly capable actors in the cyber world”. The UK Prime Minister along with Angela Merkel and Emmanuel Macron insist preserving the pact due to the implications on “shared national security interest.” A statement from the UK, France, and Germany said the International Atomic Energy Agency has “repeatedly confirmed” Iran’s compliance with the terms it signed up to. Back to the cyber attack that hit 9,000 email accounts, there are various hypotheses about the attackers’ motivation. The attack could be part of a wider cyber espionage campaign, but another concerning option is that Iran was trying to find embarrassing material to blackmail MPs. Iranian hackers are becoming even more aggressive even if experts believe that they are not particularly sophisticated. Recently we discussed the OilRig gang has been using a new Trojan in attacks aimed at targets in the Middle East. OilRig is just one of the Iran-linked hacker crews, other groups tracked by security experts are APT33, Rocket Kitten, Cobalt Gypsy (Magic Hound), Charming Kitten (aka Newscaster and NewsBeef) and CopyKittens. Payment Cards Stolen in Pizza Hut Website Hack Emails sent out by the restaurant chain to affected individuals describe the incident as a “temporary security intrusion” on PizzaHut.com. According to the company, the hackers only had access to the site between the morning of October 1, 2017 through midday on October 2, 2017 for a total of roughly 28 hours. Customers who used the Pizza Hut website or mobile app to place an order during this period could be affected. Pizza Hut said the breach was quickly detected and addressed, and it estimates that less than one percent of website visits during that week were impacted. McClatchy learned that roughly 60,000 people across the United States are affected by the incident. The restaurant chain said its external cybersecurity consultants determined that the attackers may have obtained information such as name, billing ZIP code, delivery address, email address, and payment card data, including card number, expiration date and CVV. Affected customers are being offered free credit protection services for one year. However, several people reported on social media that their payment cards have already been used for fraudulent transactions, possibly as a result of this breach. While it’s not uncommon for companies to inform customers of a breach only after completing at least an initial assessment, some of the individuals who reported seeing unauthorized charges on their cards are displeased with the fact that it took Pizza Hut two weeks to send out the notifications. This was not the first time hackers targeted Pizza Hut. Back in 2012, a group defaced the company’s Australia website and claimed to have obtained roughly 240,000 Australian payment cards. Several major restaurant chains reported suffering a data breach in the past months, including Sonic Drive-In, Wendy’s, Cicis, Arby’s, Chipotle, Shoney’s, and Noodles & Company. Siemens Patches Flaws in Building Automation Controllers The flaws, apparently discovered by Siemens itself, affect APOGEE PXC and TALON TC BACnet automation controllers running a version of the firmware prior to 3.5. The affected devices are used worldwide in commercial facilities to control a wide range of heating, ventilation and air conditioning (HVAC) equipment. The BACnet Field Panel provides a web server and a user interface that allow facility operators to easily configure, monitor and control the automation controllers. One problem found by Siemens in these products is that the authentication mechanism can be bypassed and an attacker can download sensitive information from a device. However, the vendor has pointed out that the attacker requires network access to the web server, which is accessible on TCP ports 80 and 443, in order to exploit the flaw. This vulnerability is tracked as CVE-2017-9946 and it’s considered high severity with a CVSS score of 7.5. Related: Learn More at SecurityWeek's 2017 ICS Cyber Security Conference The second security hole, tracked as CVE-2017-9947 with a severity rating of “medium,” is a directory traversal issue that allows an attacker to obtain information on the structure of the file system on affected devices. This vulnerability also requires network access to the web server for exploitation. While Siemens has not specified what kind of information is exposed, these types of vulnerabilities can often allow attackers to obtain information that could help them mount further attacks on the system. Siemens addressed the flaws with the release of firmware version 3.5 for BACnet Field Panel Advanced modules. Affected organizations have been advised to contact their local service for information on how to obtain the patch. Data Sample in Equifax Hack Scam Possibly From Third-Party Servers Hackers exploited a known Apache Struts vulnerability to breach the systems of Equifax. They had access between mid-May and late July and they may have stolen the details of over 145 million consumers in the United States, Canada and the United Kingdom. The compromised information included names, social security numbers (SSNs), dates of birth, addresses and, in some cases, driver’s license numbers, credit card numbers and dispute documents. Scammers have been trying to make a profit by claiming to sell the stolen Equifax data for several hundred bitcoins, worth millions of dollars. One scam was run by a group calling itself Equihax, which leaked the records of Donald Trump, Kim Kardashian and Bill Gates to prove that they had the Equifax data. They also provided the records of a non-famous individual in an effort to convince people that they were the real Equifax hackers. While they likely haven’t breached the credit reporting agency, they still may have obtained some Equifax customer data, but not from Equifax itself. Researchers Aditya K Sood and Rehan Jalil had been looking for potentially new cloud threats when they identified several unprotected AWS instances that referenced Equifax. “Upon accessing the HTTP service hosted on TCP port 9000/9001, we found that the web server returned a list of APIs,” Sood and Jalil explained in a blog post. “We then queried one of the APIs and found that it was possible to retrieve data.” While the misconfigured databases reference Equifax, the researchers determined that they actually belong to an unnamed securities lending company based in Chicago. More precisely, they are part of the firm’s QA systems. Some of the data stored in cleartext in the unprotected AWS cloud storage instances was valid, but some of it appeared to be test data, the experts said. A data sample provided by Sood to SecurityWeek after querying the unprotected servers was in the exact same format as the data shared by scammers, which could mean they and possibly others also discovered these servers. “It could be possible that scammers utilized this security flaw as well. The data dump is the same,” Sood told SecurityWeek. Sood and Jalil have not named Equifax in their blog post – they only reference a “credit bureau” – but there are various strings referencing “equifax” in the data they found. The credit bureau (i.e. Equifax) has confirmed to the researchers that it does not control the servers exposing data. The securities lending firm was contacted by the researchers, but it had not taken any action to protect the servers as of October 8. However, some of the sensitive data stored in the databases was encrypted between September 15, when the experts first found the servers, and October 8, when they conducted additional tests. The relationship between Equifax and the securities lending company is unclear. Equifax has not responded to SecurityWeek’s inquiry regarding these unprotected systems. Hyatt Hotels Hit by Another Card Breach The incident affects three hotels in the United States (all in Hawaii), three in Puerto Rico, 18 in China, four in Mexico, three in Saudi Arabia, three in South Korea, and one each in Brazil, Colombia, Guam, India, Indonesia, Japan and Malaysia. According to Hyatt, malware planted by cybercriminals on certain hotel IT systems harvested information from payment cards manually entered or swiped at some hotel front desks between March 18, 2017 and July 2, 2017. The malware was designed to steal data such as cardholder name, card number, expiration date, and internal verification code. No other information appears to have been compromised.Hyatt Hotels hacked again “While we estimate that the incident affected a small percentage of payment cards used by guests who visited the group of affected Hyatt hotels during the at-risk time period, the available information and data does not allow Hyatt to identify each specific payment card that may have been affected,” said Chuck Floyd, global president of operations at Hyatt Hotels Corporation. Back in 2015, Hyatt suffered a payment card breach that affected 250 of its hotels worldwide. The company claimed at the time that it had strengthened the security of its systems. “Our enhanced cybersecurity measures and additional layers of defense implemented over time helped to identify and resolve the issue,” Floyd said this week. However, the company’s enhanced security measures were obviously not enough, given that hackers had access to its systems for well over three months. “The harvested customer payment card data – including expiration dates and verification codes - is extremely valuable data that will be sold on the Dark Web or used in credit card cycling scams. It’s also easily combined with other stolen data to build entirely new synthetic personas for all manner of fraud,” explained Lisa Baergen, marketing director at NuData Security. “The travel and leisure industry – like so many consumer-facing sectors - has time and again shown itself extremely vulnerable to breaches,” Baergen added. “This latest concerning breach is just one more reason why companies such as Hyatt must adopt more advanced security and authentication measures based on trusted identity, and consumers must diligently, routinely check their credit files for suspicious credit applications and consider freezing their credit profiles.” Malicious Redirects on Equifax, TransUnion Sites Caused by Third-Party Script Independent security analyst Randy Abrams noticed recently that an Equifax service designed for obtaining free and discounted credit reports had been redirecting users to a website set up to serve adware disguised as a Flash Player installer. While initially it appeared that Equifax’s website had been hacked, the company’s investigation revealed that the malicious redirects occurred due to a third-party vendor’s script. “Despite early media reports, Equifax can confirm that its systems were not compromised and that the reported issue did not affect our consumer online dispute portal,” Equifax stated. The redirection chain, often seen in malvertising attacks, results in users being taken to a scammy or malicious website, depending on their geographical location and the type of device they use to access the affected webpage. Researchers at Malwarebytes have analyzed the incident and determined that the redirection occurs due to a web analytics script from Digital River-owned Fireclick. A search for the script involved in the attack (fireclick.js) revealed that it had also been used on the Central America website of TransUnion, whose customers were also redirected to shady sites. Both Equifax and TransUnion have removed the problematic script from their websites. Equifax took the affected service offline and had not restored it at the time of writing. “The issue involves a third-party vendor that Equifax uses to collect website performance data, and that vendor’s code running on an Equifax website was serving malicious content. Since we learned of the issue, the vendor’s code was removed from the webpage and we have taken the webpage offline to conduct further analysis,” an Equifax spokesperson explained. In addition to adware, Malwarebytes said the redirection chain also took users to fake surveys and even the RIG exploit kit, which is typically leveraged to deliver ransomware and other malware. The security firm found the same Fireclick script on several other websites as well. “Many websites include javascript from third parties for a variety of purposes, including analytics, ads, styling, and many other webpage features. Equifax included this Fireclick library on their own website, but it pulls in some javascript from another site, netflame.cc, that appears to have been hacked. When the Equifax site loads Fireclick, which loads netflame.cc code, the victim’s browser is redirected to malware,” explained Jeff Williams, CTO and co-founder of Contrast Security. “Anyone using the Fireclick library may have been affected, and the attackers may not even know that they compromised Equifax. A more targeted attack could have used the netflame.cc code to access victim’s data from the Equifax page, submit false data on behalf of the victim, or deface the Equifax page. The attack could have been made invisible to the victim and could have been much more difficult to detect,” Williams added. Some Hacker News users noticed that the netflame.cc domain was owned by Digital River until November 2016, when the registration information changed to show that the new owner was an individual from Thailand. It’s unclear if this has played any part in the recent incident affecting Equifax and TransUnion. Security Concerns Hamper Migration to Office 365: Report The study is based on a survey of more than 1,100 organizations of all sizes from North America, Europe, Africa and the Middle East. Nearly two-thirds of respondents said they are using Office 365 and 49% of the remaining organizations plan on migrating. While the number of organizations that started using Office 365 has increased, the adoption rate has declined compared to 2015-2016, when the number of subscriptions doubled. Nearly 44% of organizations that haven’t moved to Office 365 decided against migrating due to security concerns. Of the companies that plan on migrating, more than 73% said they were concerned about advanced threats in their future Office 365 environment. Nearly 70% of those that have already started using Office 365 are also concerned about sophisticated threats. More than 86% of respondents are concerned about phishing, impersonation and social engineering attacks, while 92% are concerned about ransomware. “The very high rates of concern about security—including worries about latent threats, advanced malware, phishing and spear phishing, and especially ransomware—may be the single most important contributing factor to the overall decline in the rate of adoption that the survey revealed,” Barracuda said in its report. How well are these organizations prepared to handle potential attacks? Only one-third of respondents said they have a third-party security solution designed to protect them against phishing and other social engineering attacks, and 69% said they provide training for their employees. Despite the fact that email has been one of the main ransomware delivery vectors, more than half of respondents don’t use DMARC or DKIM/SPF, protocols designed to detect and prevent email spoofing. Microsoft offers its own security service for Office 365, Advanced Threat Protection (ATP), but only 15% of respondents said they use it. On the other hand, many are either using or are planning on using third-party solutions for Office 365 security, archiving and backup. “Overall, respondents reported significant doubts about the effectiveness of native security and other features of Office 365. In particular, they had concerns about these features’ ability to protect them effectively against ransomware, phishing, and spear-phishing or social-engineering attacks,” Barracuda said. In the past months, there have been several reports of serious vulnerabilities affecting Office 365 and even sophisticated attacks targeting users of the platform. Android Trojan Infrastructure Serves Fake Adobe Flash Apps The threat was first detailed last month, when SfyLabs researchers revealed that communication between infected bots and the command and control (C&C) server was performed using Twitter. Written from scratch, Red Alert is capable of stealing login credentials, intercepting SMS messages, and stealing contacts. Targeting financial institutions and media organizations, the malware is using overlays to steal banking credentials and can also block and log incoming calls from banks, thus preventing intrusion detection. Now, the RiskIQ researchers say they have managed to identify the infrastructure related to the malware. Starting from a single domain (that resolves to IP address 185.48.56[.]83), the researchers were able to find the email address used to register the domain (loadingexe@yandex.ru), and discovered additional eight domains of interest. Thus, the researchers found two malicious apps purporting to be Adobe Flash Player updates and which were hosted on two of these sites, namely g-shoock[.]xyz and g-shoock[.]ru. These malicious apps can access network state, get tasks, connect to the Internet, read phone state and SMS, receive SMS messages, and write SMS. They also support commands such as RECEIVE_BOOT_COMPLETED, SYSTEM_ALERT_WINDOW, and WAKE_LOCK. The two domains, which started resolving around the beginning of June 2017, revealed connections to a larger actor-owned infrastructure. They overlap via passive DNS on the same IP address first associated with Red Alert. The security researchers also discovered that the infrastructure is still active and that additional Adobe Flash typosquatting domains have been registered by the actor in recent days. These domains too are used for the downloading of APK files. “While, at this time, VirusTotal shows the APK file in question as not malicious, its connection to infrastructure previously connected to known malicious apps and the fact that the domains are typosquatting Adobe’s brand leads RiskIQ to assess that this is, in fact, malicious,” the security researchers note. Last month, SfyLabs revealed that Red Alert would also masquerade as popular applications such as WhatsApp and Viber, Google Market update, and even Android system updates. The researchers also noted that the Trojan was targeting at least 60 banking applications with HTML overlays. Bug Caused Microsoft Outlook to Send Emails in Cleartext Discovered by SEC Consult researchers, the bug impacted Outlook’s S/MIME functionality and was supposedly introduced about six months ago. Both Microsoft Outlook 2016 32-bit and 64-bit editions are affected. The S/MIME standard is used for end-to-end encryption and for the signing of emails, and is supported by most popular mail clients, including Microsoft Outlook, Mozilla Thunderbird, Apple Mail, and mail clients for mobile devices. However, mail clients need to be configured to use S/MIME through installing a personal certificate and exchanging certificates with communication partners. Even the United States Department of Defense uses S/MIME, but there isn’t much information available on other organizations that use the standard, SEC Consult says. Tracked as CVE-2017-11776, the Outlook flaw resulted in emails not being encrypted as expected when S/MIME encryption was in use. Because of this issue, the contents of S/MIME encrypted mails would show in Outlook Web Access (OWA), which led to the vulnerability’s discovery, the researchers say. No action is required from an attacker looking to trigger the vulnerability. "There is a bug in Outlook that causes S/MIME encrypted mails to be send in encrypted and unencrypted form (within one single mail) to your mail server (and the recipient's mail server and client and any intermediate mail servers). The impact is that a supposedly S/MIME encrypted mail can be read without the private keys of the recipient. This results in total loss of security properties provided by S/MIME encryption,” SEC Consult explains. The vulnerability is difficult to spot by the sender, as there is no indication of it in the “Sent Items” folder. In fact, Outlook would display the message as if it was properly encrypted, the researchers explain. Because the vulnerability impacts the mail body S/MIME encryption and not transport level security (TLS), only emails sent from Outlook are impacted. The issue has no effect on incoming S/MIME encrypted mails, where Outlook acts as the recipient. The security researchers also explain that only messages sent in "Plain Text" format are affected by the vulnerability. What should be noted, however, is that Outlook formats mails in “Plain Text” by default when replying to “Plain Text” formatted emails. According to SEC Consult, most security conscious organizations only use "Plain Text" formatted emails, and even DoD recommends the exclusive use of "Plain Text" formatted emails (PDF). Depending on the used transport protocol, the scope of the vulnerability differs. In Outlook with Exchange, plaintext leaks one hop only if the recipient and sender are in the same domain. In Outlook using SMTP, the plaintext leaks to all mail servers along the path and the recipient. The vulnerability was addressed in both Microsoft Outlook 2016 editions on October 10, 2017, as part of Microsoft’s regular set of monthly patches. “The much harder problem is to determine the actual impact and remediate the legacy of affected mails containing confidential data,” SEC Consult notes. Equifax Website Redirects Users to Adware, Scams Independent security analyst Randy Abrams wanted to find his credit report on Equifax’s website when he was redirected to a website offering a fake Flash Player installer. The browsing session was taken through multiple domains before the final page was reached. It’s not uncommon for cybercriminals to deliver malware using fake Flash Player installers, but in this case the website pushed adware. Equifax website redirects to fake Flash installer The Equifax webpage, hosted at aa.econsumer.equifax.com, did not redirect the connection when accessed by SecurityWeek on Thursday morning. Abrams believes Equifax removed the malicious code from its website sometime on Wednesday. An analysis of the domains involved in the redirection chain shows that they can lead not only to adware. The final destination depends on the type of device and the geographical location of the user. SecurityWeek has seen redirects to fake Android and iOS updates, premium SMS services, and other scammy sites. Various online security services detect the domains involved in the attack as malicious, and while there is no evidence of actual malware being served, the possibility cannot be ruled out. After visiting the compromised site several times from the same device, the user is taken to a website belonging to a legitimate business that is likely trying to promote its site via ad networks or SEO (search engine optimization) services. Contacted by SecurityWeek, an Equifax spokesperson stated, “We are aware of the situation identified on the equifax.com website in the credit report assistance link. Our IT and Security teams are looking into this matter, and out of an abundance of caution have temporarily taken this page offline. When it becomes available or we have more information to share, we will.” Equifax recently informed customers that hackers breached its systems after exploiting an Apache Struts 2 vulnerability that had been patched and exploited in the wild since March. The attackers gained access to the personal information of more than 140 million individuals, including hundreds of thousands of Canadian and British citizens. “I'm really not trying to kick Equifax while they are down. There are already 150 million other people doing that. I just sort of tripped over them,” Abrams said in a blog post. “I know that nobody is surprised at my find, but watching Equifax is getting to be like watching a video of United Airlines ‘deplaning’ a passenger... It hurts,” he added. Many of Equifax’s cybersecurity failings came to light following the breach, including the fact that the company directed customers to the wrong website and website vulnerabilities. UPDATE. After an investigation, Equifax determined that the problem was caused by a third-party vendor's code. The company has provided the following statement to SecurityWeek: “Despite early media reports, Equifax can confirm that its systems were not compromised and that the reported issue did not affect our consumer online dispute portal. The issue involves a third-party vendor that Equifax uses to collect website performance data, and that vendor’s code running on an Equifax website was serving malicious content. Since we learned of the issue, the vendor’s code was removed from the webpage and we have taken the webpage offline to conduct further analysis.” UPDATE 2. The same script also caused problems for another Big Three credit reporting agency, TransUnion. These Cities House the Largest Bot Populations in the U.S. According to the security company, Chicago currently hosts 4.69% of the bots in the U. S., while Washington, D.C. hosts 4.13% of them. Atlanta is placed third, with 3.49% of the bots, followed by Ashburn (3.23%) and New York (3.22%). Portland (3.18%), Los Angeles (2.02%), Las Vegas (1.98%), San Jose (1.96%), and Tampa (1.57%) round up top 10. These bots represent Internet-connected devices of any kind (including laptops, phones, connected devices, baby monitors, servers, etc.), which can be remotely controlled by attackers after being infected with malware. Based on the malware infecting them and on their operators, these devices work together in networks called botnets. The bots are usually remotely controlled without the knowledge of their owners. Botnet sizes range from hundreds or thousands of infected devices to hundreds of thousands or even millions of bots. They can be used to spread malware, send spam emails, perform distributed denial of service (DDoS) attacks, or perform other types of online crime. In 2016, botnets such as Mirai or Bashlite brought to the spotlight the danger poorly secured Internet of Things (IoT) devices pose when they become part of botnets. Mirai alone infected around half a million IoT devices and abused them to launch some of the largest DDoS attacks in history. Last year alone, the number of bots that was added to the global botnet was of 6.7 million, Symantec says. “More than 689 million people were victims of online crime in the past year, and bots and botnets are a key tool in the cyber attacker’s arsenal. It’s not just computers that are providing criminals with their robot army; in 2016, we saw cyber criminals making increasing use of smartphones and Internet of Things (IoT) devices to strengthen their botnet ranks. Servers also offer a much larger bandwidth capacity for a DDoS attack than traditional consumer PCs,” Candid Wueest, Norton Security expert, says. According to Kevin Haley, security expert at Symantec, the size of bot population is usually growing in cities where a large number of Internet-connected devices exists, or where the number of high-speed, Internet-connected devices is increasing. However, although the size and location of a botnet might be connected, they are not indicative of where the operator lives, Symantec points out. Botnets are global in nature and infected devices from any country could be used to hit targets in any other country, while being controlled by an actor living in a completely different area. When it comes to botnets, infection vectors differ from a device to another. Malicious links, malicious attachments in emails or social media messages, and compromised websites can all be used to infect devices. Some attackers might use automated tools to find and directly target vulnerable devices, as it happened with Mirai. Hackers Used Government Servers in DNSMessenger Attacks First uncovered in early March, the DNSMessenger attack involved the use of DNS requests to establish communication between a PowerShell RAT and its command and control (C&C) servers. Completely fileless and invisible to most standard defenses, the attack was highly targeted and researchers attributed it to a sophisticated threat actor. Cisco now says that additional attacks leveraging this type of malware were discovered, targeting several organizations in an attempt to infect them with malware. Specific to this campaign is the use of DNS TXT records to create a bidirectional C&C channel and directly interact with the Windows Command Processor. The attackers use spear phishing emails to spread the malware and leverage U.S. state government servers to host the malicious code necessary in the later stages of the infection chain. The emails, Cisco reveals, are spoofed to seem as if they were sent from the Securities and Exchange Commission (SEC) Electronic Data Gathering, Analysis, and Retrieval (EDGAR) system. In March this year, attacks targeting U.S. organizations and focused on personnel that handle filings to the SEC were attributed to the hacking group known as FIN7. The incidents were later tied to a framework used in the DNSMessenger campaign as well, as all attacks were supposedly orchestrated by a single threat group. “The organizations targeted in this latest malware campaign were similar to those targeted during previous DNSMessenger campaigns. These attacks were highly targeted in nature, the use of obfuscation as well as the presence of a complex multi-stage infection process indicates that this is a sophisticated and highly motivated threat actor that is continuing to operate,” Cisco Talos reports. The spear phishing emails used in the new attack contained attached Microsoft Word documents (also made to appear as if originating from SEC) that would leverage Dynamic Data Exchange (DDE) to perform code execution. When opened, the documents would prompt the user to allow the retrieval of content from included external links. The DDEAUTO field used by the malicious document retrieved code initially hosted on a compromised Louisiana state government website. The downloaded code is executed using PowerShell and is responsible for achieving persistence and starting the next stage of the infection chain. Heavily obfuscated, the next stage of infection establishes communication with the C&C and receives code via DNS. When this step is completed, the result string is decoded and decompressed and then passed to the Powershell IEX cmdlet to execute the code retrieved. Cisco’s researchers weren’t able to obtain the next stage of PowerShell code from the C&C server and believe that this could be so because of the highly targeted nature of the attack. The actors behind the operation might be restricting communications to evade analysis. Other researchers, however, were able to retrieve the code and reveal that it contains the usual set of information gathering capabilities. The stage 4 code, which includes a different structure of DNS records being used for commands, apparently exfiltrates data via a hardcoded web form. This attack, Cisco concludes, shows the level of sophistication associated with threats facing organizations today: it includes multiple layers of obfuscation, it limits compromise to only the organizations of interest, and uses new techniques to execute malicious code on systems (leverages WMI, ADS, scheduled tasks, and registry keys to obtain persistence). High-Tech Bridge Launches Free Service for Testing Mobile Apps Mobile X-Ray can test native and hybrid applications, including security and privacy aspects, using dynamic application security testing (DAST), static application security testing (SAST), data encryption testing for communications with APIs and web services, and behavioral analysis. The service looks for the most common types of vulnerabilities, including ones covered by the OWASP Mobile Top Ten, and provides a user-friendly report that includes remediation guidance. The test results include examples of both insecure and secure code. In the case of Android apps, developers can upload the APK to Mobile X-Ray, but iOS apps can only be tested if they are compiled as a Simulator app in Xcode. A test scan conducted by SecurityWeek for the latest beta version of WhatsApp for Android revealed five high severity issues, including hard-coded encryption keys, the use of a weak initialization vector, the use of an intent filter, and the existence of a clear text database. While not all these weaknesses may be exploitable, the test informs developers of the potential issues they need to look into. The assessment can take less than a minute, but it can also take up to a couple of hours, depending on application complexity and overall system workload. "Mobile applications have become an inseparable part of everyday business and private life. In light of skyrocketing data breaches, many different research reports urge the enhancement of mobile application security and privacy,” said Ilia Kolochenko, CEO and founder of High-Tech Bridge. “Unfortunately, most developers just don't have enough resources, time or budget to properly test their mobile app before going to production. At High-Tech Bridge, we are excited to fulfil this gap and offer a unique online service for the benefit of the cybersecurity community and independent developers.” While the Mobile X-Ray tool can be highly useful for application developers, many critical vulnerabilities exist in backend systems, for which High-Tech Bridge recommends its ImmuniWeb Mobile product. Data obtained by the security firm via its ImmuniWeb Mobile product shows that 88% of APIs and web services in the backend are affected by vulnerabilities that allow access to sensitive data, and 69% of APIs and web services do not include mechanisms for mitigating common web attacks. Nearly all the Android applications tested by High-Tech Bridge had at least one vulnerability covered by the OWASP Mobile Top Ten, and more than 78% of them had at least one high and two medium risk flaws. In the case of iOS apps, 85% were found to have at least one of the top OWASP vulnerabilities, and roughly 69% had at least one high and two medium risk security holes. Flaws in SmartVista Payment Platform Expose Sensitive Data The SmartVista platform is used by major organizations around the world for online banking, e-commerce, ATM and card management, and fraud prevention. The core components of the SmartVista suite are the Front-End and Back-Office systems. Researchers at Rapid7 discovered that the SmartVista Front-End, specifically version 2.2.10 revision 287921, is affected by two SQL injection vulnerabilities. According to the security firm, an attacker who has access to the SmartVista Front-End interface can exploit the flaws to obtain data stored in the backend database. The “Transactions” page in the “Customer Service” section of SmartVista Front-End allows users to view transaction details associated with a specified card or account. However, the fields where the card and account number are entered fail to sanitize user-supplied input. This allows a malicious actor to use specially crafted queries to get the application to display data from the backend database, including usernames, passwords, card numbers, and other transaction details. Rapid7 researchers demonstrated that entering a Boolean search term such as ‘ or ‘1’=’1, in the “Account Number” field resulted in all transactions being displayed. While there is a 5 second delay when a similar Boolean search term is entered into the “Card Number” field, a time-based SQL injection attack is still possible. Rapid7 reported its findings to BPC on May 10, but a patch has yet to be released. CERT/CC and SwissCERT have also tried contacting the vendor, but without any success. The security firm gives vendors at least 60 days before publicly disclosing vulnerabilities found in their products. SecurityWeek has reached out to BPC for comment and will update this article if the company responds. “Users should contact BPC support for more details. In the meantime, access to the management interface of SmartVista should be as limited as possible, and audits of successful and failed logins should be performed regularly. A web application firewall (WAF) can help mitigate, or at least complicate, exploitation that relies on common SQL injection techniques,” Rapid7 advised users. F-35 Stealth Fighter Data Stolen in Australia Defence Hack The 50-person aerospace engineering firm was compromised in July last year but the national cyber security agency, the Australian Signals Directorate (ASD), only became aware of the breach in November, technology website ZDNet Australia reported. Some 30GB of "sensitive data" subjected to restricted access under the US government's International Traffic in Arms Regulations rules were stolen, ASD's Mitchell Clarke told a security conference Wednesday according to ZDNet. Clarke, who worked on the case and did not name the subcontractor, said information about the F-35, the US' latest generation of fighter jets, as well as the P8, an advanced submarine hunter and surveillance craft, were lifted. Another document was a wireframe diagram of one of the Australian navy's new ships, where a viewer could "zoom in down to the captain's chair". The hackers used a tool called "China Chopper" which according to security experts is widely used by Chinese actors, and had gained access via an internet-facing server, he said. In other parts of the network, the subcontractor also used internet-facing services that still had their default passwords "admin" and "guest". Those brought in to assess the attack nicknamed the hacker Alf after a character on the popular Australian soap "Home and Away", Clarke said. The three month period where they were unaware of the breach they dubbed "Alf's Mystery Happy Fun Time". Defence Industry Minister Christopher Pyne told reporters in Adelaide "the information they have breached is commercial". "It is not classified and it is not dangerous in terms of the military," he said. Pyne added that Australia was increasingly a target for cyber criminals as it was undertaking a massive Aus$50 billion (US$39 billion) submarine project which he described as the world's largest. The nation has also committed to buy 72 F-35A aircraft for Aus$17 billion. He would not comment who might be behind the breach, only stating that the government was spending billions of dollars on cyber security. Western governments have long accused hackers in China of plundering industrial, corporate and military secrets. The revelations came just days after Assistant Minister for Cyber Security Dan Tehan said there were 47,000 cyber incidents in the last 12 months, a 15 percent jump from the previous year. A key worry was 734 attacks that hit private sector national interest and critical infrastructure providers during the period, Tehan said. Last year, the government's Cyber Security Centre revealed that foreign spies installed malicious software on the Bureau of Meteorology's system and stole an unknown number of documents. Kaspersky in Focus as US-Russia Cyber-Tensions Rise The Russian-based company has been accused of being a vehicle for hackers to steal security secrets from the US National Security Agency, and was banned by all American government agencies last month. But it remains unclear if Kaspersky was part of a scheme or an unwilling accomplice in an espionage effort. The software firm has argued it has no ties to any government and said in a recent statement it is simply "caught in the middle of a geopolitical fight." But the latest accusations highlight what some see as a simmering cyberwar between the two powers. Related: The Increasing Effect of Geopolitics on Cybersecurity "Currently, we're losing," said James Lewis, a fellow with the Washington-based Center for Strategic and International Studies. "It's not the kind of conflict we're used to." The Kaspersky allegations come in the wake of an apparent Russian-led effort to manipulate social media and influence the 2016 US presidential election. Russia has an advantage because "they have figured out how to use our civil liberties against us and there's not much we can do about it," Lewis said. "We don't have a group that does this kind of psychological warfare and we don't have the legal authority to defend against it." Peter Singer, a New America Foundation strategist and author who has written on 21st century warfare, agreed that Russia is gaining ground in this cyber conflict. "If it's a 'cyberwar,' it is a akin to a Cold War-style back-and-forth of everything from stealing secrets to political influence operations," Singer said. "Given that the Russians have so far got away with no real consequences for the biggest, most impactful operation, the hacks and influence campaign targeting the 2016 US election, I'd say they are doing pretty well." - Cat-and-mouse game - But Gabriel Weimann, a professor at Israel's University of Haifa and author who has written on cybersecurity, said it may be premature to declare Russia the winner. "We don't really know the achievements of NSA in monitoring the web, this kind of information is secret," Weimann said. "This is a cat-and-mouse game. You respond to breaking in and the other side responds and it becomes more dangerous and more sophisticated." On Tuesday, the New York Times reported that Israeli intelligence had hacked into the Kaspersky network and upon detecting the Russian intrusion, alerted the United States, which led to a decision last month for Kaspersky software to be removed from US government computers. The online news site CyberScoop, citing anonymous sources, reported separately this week that Kaspersky as early as 2015 sought to promote its anti-virus software as a tool to track extremists in the Middle East. The report said that some US officials were intrigued by the offer, but that technical members of the intelligence community interpreted this as meaning that Kaspersky's anti-virus software could be used as a spying tool. CyberScoop said that Russian officials from the FSB, the successor to the KGB, told US officials in 2015 not to interfere with Kaspersky software, a message that set off alarm bells. The Wall Street Journal meanwhile reported that the Russian government was able to modify Kaspersky software to turn it into an espionage tool. Anti-virus software such as those created by Kaspersky can become a tool for espionage because it scans and can access all files in a computer or network. Eugene Kaspersky, founder of the company which bears his name, has long denied any connection to the Russian government but said on Twitter Monday he was launching an internal investigation into the latest allegations. A company statement this week said, "Kaspersky Lab has never helped, nor will help, for any government in the world with its cyberespionage efforts, and contrary to erroneous reports, Kaspersky Lab software does not contain any undeclared capabilities such as backdoors as that would be illegal and unethical." Weimann said he believes Kaspersky was likely "piggybacked" by the Russian government for espionage rather than a willing participant. Lewis agreed, saying Kaspersky is probably "an unwilling tool" in the Russian espionage effort. Lewis said that Eugene Kaspersky "would love to be (part of) a private company headquartered in London but the Russian government won't let him." Akamai to Acquire DNS Security Firm Nominum Terms of the deal were not disclosed, but the all-cash transaction is scheduled to close in Q4 2017, Akamai said. “By combining Nominum’s carrier-grade cybersecurity solutions with Akamai’s enterprise security offerings and threat intelligence, Akamai intends to serve a larger base of carrier and enterprise customers with more comprehensive security products,” Akamai explained. “These products will be designed to more effectively identify, block, and mitigate cybersecurity threats such as malware, ransomware, phishing, and data exfiltration.” In early 2017, Akamai lauched a new offering designed to protect enterprises against malware, phishing and data exfiltration attempts through the analysis of DNS requests. According to a recent report, many companies are not prepared to deal with DNS attacks, and a quarter of the ones that have already been hit reported significant losses. The study from Dimensional Research and Infoblox, based on a survey of over 1,000 IT and security professionals worldwide, revealed that 3 out of 10 companies have already experienced DNS attacks and in most cases it resulted in downtime. Redwood City, Calif.-based Nominum says more than 100 service providers use its DNS technology in over 40 countries, which processes 1.6 trillion queries daily. Spy vs Spy vs Spy as Israel Watches Russian Hackers: NYT The Russian intrusion detected more than two years ago used anti-virus software manufactured by the Russian firm Kaspersky Lab as an ad hoc global search tool, the Times said, quoting current and former government officials. The software is used by 400 million people around the world, including by officials at some two dozen American government agencies, the Times reported. Israeli intelligence had hacked into the Kaspersky network and upon detecting the Russian intrusion, alerted the United States. This led to a decision last month for Kaspersky software to be removed from US government computers, the Times said. It is known that Russian hackers stole classified documents from a National Security Agency employee who had stored them on his home computer which featured Kaspersky antivirus software, the paper said. It said that it is not yet publicly known what other secrets the Russians may have obtained from US government agencies by using Kaspersky software as "a sort of Google search for sensitive information." The Times said Kaspersky Lab denied any knowledge of or involvement in the Russian hacking. SDL Development Library Allows Code Execution via GIMP Files SDL provides low level access to audio, mouse, keyboard, joystick and graphics hardware, making it ideal for developing games, emulators and video playback software. The library has been used for the development of hundreds of games, including ones made by Valve, and the VLC media player. Cisco Talos researcher Yves Younan discovered that SDL is affected by memory corruption vulnerabilities that can be exploited remotely to execute arbitrary code on the host by using specially crafted files that the library would process. The attack scenarios described by Talos in its advisories involve XCF files designed to trigger the vulnerabilities. XCF is the native image format of the popular image-editing tool GIMP. One of the flaws is an integer overflow (CVE-2017-2888) that can be triggered when creating a new RGB surface via a call to the “CreateRGBSurface” function. “A sufficiently large width and height value passed to this function could cause a multiplication operation to overflow, thus resulting in too little memory being allocated. Subsequent writes would then be out-of-bounds,” Cisco said in its advisory. The second vulnerability is a buffer overflow (CVE-2017-2887) that exists in the XCF property handling functionality of the SDL_image image file loading library. “This vulnerability manifests due to insufficient validation of data read from a file and subsequent use of the data. In this case, the `id` and `length` attributes read from an XCF image file are used without validation, potentially resulting in a stack-based buffer overflow,” Cisco said. The vulnerabilities affect SDL 2.0.5 and SDL_image 2.0.1. Cisco said the flaws were patched with the release of SDL 2.0.6, but the release notes for this version don’t mention any security fixes. Ransomware is a Booming Industry That Continues to Evolve Carbon Black's researchers monitored 21 of the largest dark web marketplaces trading ransomware (out of an estimated 6,300+ dark web marketplaces doing so) during August and September 2017. The results are astonishing, with more than 45,000 current listings. Prices range from Android lockscreen ransomware for $1.00 to custom code for more than $1000. The median cost of a ransomware offering is just $10.50. The total amount of money involved is equally astonishing. According to FBI figures, ransom payments in 2016 were around $1 billion dollars; up from $24 million in 2015. According to Carbon Black's research, ransomware developers can expect to earn approximately $100,000 (tax free) per annum. This compares to an average salary of $69,000 (before tax) for legitimate software developers. The difference is even greater in many east European countries where much malware is thought to be developed. Ransomware sales on the dark web have grown from less then $400,000 in 2016 to around $6.25 million in 2017. "The underground ransomware economy is now an industry that resembles commercial software — complete with development, support, distribution, quality assurance and even help desks," notes the report. Carbon Black's security strategist Rick McElroy expects this underground business to evolve and develop much like legitimate industries. "I expect that we will see consolidation between the developers and their products," he told SecurityWeek. The simple reality is that the ransomware industry is growing because it is profitable. Dismantling the industry must therefore concentrate on removing that profitability. Carbon Black describes the industry as having a five-point supply chain: creation, distribution, encryption, payment and command and control. "If defenders can break or interrupt even one link of the chain," it suggests, "the entire attack falls apart." Disrupting the creation will be impossible while young coders are unable to find legitimate jobs, and can earn attractive sums through developing ransomware. Distribution disruption is equally difficult when the marketplace can be hidden within the dark web. Encryption is similarly impossible to control -- powerful encryption systems are readily available in the public domain. Payment is the weakest link. In the supply chain it is the collection and tracking of ransoms paid -- but if no ransom is paid, then the entire industry will collapse. "We need to STOP paying ransoms", says the report. "The system only works if victims choose to pay. Until people decide not to pay, this problem will only continue to grow." McElroy agreed in conversation that this is a difficult ask. Nevertheless, he believes that if enough victims in either a particular country, or target industry, refuse to pay, the criminals will simply target different areas or industries where the returns will be greater. It doesn't solve the problem, but it simply exports it elsewhere. Preventing the need to pay a ransom would have a similar effect. This could relatively easily be achieved by improved security controls -- but ensuring that people and organizations have those controls in place is difficult if not impossible to achieve. Against this background, the ransomware industry will continue to grow -- and it will continue to evolve. So far, ransomware has largely been in the hands of relatively unskilled coders; sophistication has not been necessary. Carbon Black sees this changing. To a certain extent the signs are already visible: WannaCry and NotPetya are examples. In the former, the ransomware was unsophisticated while in the latter decryption was never intended. However, the distribution of the ransomware via leaked NSA exploits was a new development. Carbon Black describes this use of ransomware as a false flag. A closely related new development it expects will be the malware's use as a smokescreen. "Using already existing techniques of deleting Volume Shadow Copies, which deletes potential file backups, and the deletion of Windows event logs, adversaries can thwart many incident response efforts by forcing responders to focus on decrypting files instead of investigating data and credentials exfiltrated." The ransomware -- or more specifically the encryption element of ransomware -- will be used to hide and obfuscate traces of more traditional cyber thefts and cyberespionage. All of this is likely as the ransomware industry evolves. McElroy told SecurityWeek he expects to see consolidation. The effect is likely to concentrate ransomware into the hands of more sophisticated coders. One effect of paying a ransom is that it tells the attackers that the victim can be coerced. Carbon Black expects to see more sophisticated developers employing more advanced morphing and persistence techniques to remain on the victim's network after decryption -- so that they can extort a second time in the future. Cloud App Security Firm ShiftLeft Exits Stealth With $9 Million in Funding The company’s fully automated security-as-a-service (SECaaS) solution is designed to help organizations secure their applications by providing threat detection capabilities in the continuous integration (CI) and continuous development (CD) processes. ShiftLeft’s product extracts all security-relevant information from the codebase of each software build and uses it to create a custom Microagent that provides runtime protection. The product can identify potential risks and point developers to the line of code that causes the issue.ShiftLeft emerges from stealth According to ShiftLeft, the solution can help identify known and unknown vulnerabilities, including issues introduced by the usage of open source software, and data leakage without false positives. Developers can prioritize bug fixes, DevOps teams can obtain deep visibility into data flows, while security teams can protect applications without disrupting the pace of the CI/CD process. “The adoption of Cloud increases the pace of innovation by allowing us to deliver features even faster,” said Chetan Conikee, CTO and co-founder of ShiftLeft. “But this pace of change defeats traditional security.ShiftLeft embraces this change to enhance security for cloud-native applications by creating a custom Microagent for each version of each application. This application-specific security is both automated and accurate. We no longer have to buy off-the-shelf security products, write policies, and tune them manually as we sift through hundreds of false positives.” The announcement of ShiftLeft’s formal launch was accompanied by news that the company raised $9.3 million in a Series A funding round led by Bain Capital Ventures and Mayfield, with participation from individual investors such as Sanjay Poonen, COO of VMware; Tobias Knaup, CTO of Mesosphere; and Prabhu Goel, creator of Verilog. North Korean Hackers Targeted U.S. Electric Firms: Report The state-sponsored actors conducted a reconnaissance attack against electric companies in the United States on Sept. 22, 2017, via spear-phishing emails, but the incident did not lead to a disruption, the security company reports. In fact, no evidence was found that North Korea-linked actors would even have the capability to compromise or manipulate the industrial control systems (ICS) networks that regulate the supply of power. Attacks targeting the energy sector aren’t new, and FireEye says it has detected “more than 20 cyber threat groups suspected to be sponsored by at least four other nation-states attempting to gain access to targets in the energy sector that could have been used to cause disruptions.” Given the current tensions with North Korea, the attacks should come at no surprise. Utility executives worldwide fear that cyber-attacks could cause disruptions to electric distribution grids. To improve the resilience and security of critical energy infrastructure, the United States Department of Energy announced last month plans to invest over $20 million in cyber security. Last month, Symantec warned of Russian hackers hitting the energy sector in the United States and other countries with a focus on gaining access to control systems. Iranian-backed cyber espionage actors were observed targeting energy organizations too, and so were Chinese hackers last year. While North Korea-linked hackers were accused of targeting South’s nuclear power plants operated by Korea Hydro and Nuclear Power (KHNP), the attack apparently focused on stealing sensitive KHNP documents, “as part of an effort to exaggerate the access they had and embarrass the South Korean Government,” FireEye says. The technique is apparently used by the North Korean government either to instill fear or to meet domestic propaganda purposes. Cyber actors linked to the country, however, don’t appear to possess the ability to take the technical and operational steps required in attacks aimed at disrupting energy sector operations. The spear-phishing activity observed last month “was early-stage reconnaissance, and not necessarily indicative of an imminent, disruptive cyber-attack that might take months to prepare if it went undetected (judging from past experiences with other cyber threat groups),” the security researchers point out. The suspected North Korean actions are supposedly part of an attempt to demonstrate a deterrent capability rather than the first stages of a larger attack. “For North Korea, even limited compromise of power companies would probably be exaggerated and hailed as a victory by Pyongyang,” FireEye says. On the other hand, an increasing number of nation-states are developing the capability to disable the operations of power utilities. Moreover, because North Korea-linked actors are bold, they likely remain committed to targeting the energy sector, especially in South Korea and among the U.S. and its allies, the researchers believe. These actors have already been associated with various cyber-attacks this year, including one targeting South’s wartime operational plans, and several hitting crypto-currency exchanges, possibly in an attempt to bolster finances. Hackers with ties to North Korea were also deemed a serious threat to banks earlier this year. “North Korea linked hackers are among the most prolific nation-state threats, targeting not only the U.S. and South Korea but the global financial system and nations worldwide. Their motivations vary from economic enrichment to traditional espionage to sabotage, but all share the hallmark of an ascendant cyber power willing to violate international norms with little regard for potential blowback,” FireEye concludes. "It doesn't seem like a phishing attack deserves too much attention these days - especially one that was unsuccessful in penetrating target networks,” Eddie Habibi, CEO of PAS Global, told SecurityWeek. “The fact that it was North Korea isn't a big surprise nor that power was in the crosshairs. What is worth noting is that as tensions continue to rise with North Korea, we should expect the intensity of cyber attacks aimed at U.S. critical infrastructure to rise as well.” Trump Issues Threat Sharing Directive to Intelligence Community Inter-agency information sharing has been a pressing issue and problem since 9/11 when it was suggested that different agencies had partial information about the terrorist plot, but there was no way to 'connect the dots' and see the overall picture. Since then there have been numerous initiatives to improve information sharing -- such as the Cybersecurity Information Sharing Act (CISA) and the CTIC and IC ITE projects. IC ITE is a long-term intelligence community initiative to provide what this new memorandum seems to require. The current strategy document, produced by the Office of the Director of National Intelligence (at that time, James Clapper) states (PDF): "The IC ITE represents a strategic shift from agency-centric information technology (IT) to a common enterprise platform where the Intelligence Community (IC) can easily and securely share technology, information, and capabilities across the Community." However, the timeframe covered by this document is 2016 to 2020 -- and it may be that the new Trump memorandum is seeking to speed the process. Trump has been a critic of the intelligence community since before his election. It is not clear whether this memorandum is designed to replace the existing projects or merely to hasten their completion. Memoranda are used by presidents in a manner similar to executive orders, and place a similar legal requirement on government agencies. They have been described as 'an executive order by another name'. The gist of the memorandum is that the intelligence community must establish a 'threat actor' information sharing architecture under guidance from NIST, and present their plan to the president within 270 days. "The Secretary of Defense, the Attorney General, the Secretary of Homeland Security, and the Director of National Intelligence, in coordination with the Secretary of State, the Secretary of the Treasury, and the Secretary of Energy, shall, through the Assistant to the President for Homeland Security and Counterterrorism, submit to the President a plan to implement this memorandum." There is no indication on how the threat sharing is to be implemented; and of course no guarantee that the president will accept the plans. There is, however, a strong concentration on the need to share personal information of potential threat actors. "National security threat actor information," states the memorandum, "comprises identity attributes and associated information about individuals, organizations, groups, or networks assessed to be a threat to the safety, security, or national interests of the United States that fall into one or more of the categories listed in the annex to this memorandum." 'Identity attributes' are then defined as "Information (including biometric and biographic data) that can be used independently or in combination with other data to identify a specific individual." It is the lack of detail that is most worrying. The devil is always in the detail, comments Christopher Bray, SVP at Cylance Inc. The big question, he suggests, is how this can be translated into policy while respecting applicable laws, civil liberties and individual privacy. "These are extremely important questions that need to be crisply defined and addressed within established legal and constitutional frameworks," he told SecurityWeek. "You only need to think about the clumsy implementation of the 'no fly list' and the examples of completely innocent people arbitrarily getting placed on it in error -- with lack of a clear process for recourse or getting removed, to see what a minefield this could become if not thought through well." Will this be implemented into anything meaningful at all, he wonders, or just become 'policy shelf-ware' that someone can point to later as having 'done something'. Nathan Wenzler, chief security strategist at AsTech, sees nothing that addresses the long-standing problems for information sharing. "The challenge previously is that each of the agencies involved tends to collect information that is very specific to their purposes and it is in that specificity that there is fear that others who possess the data will be able to discern how that data was obtained and collected. This has caused many in the intelligence community to fear the compromise of those data gathering sources, whether human or technological, and has made previous efforts to integrate and share such data nearly impossible." Like Bray, he is also concerned about the privacy impact of the memorandum. "The potential for compromise to intelligence sources, the vast privacy concerns that will exist should any U.S. citizen wrongly be targeted in these profiling efforts, and the fact that effectively locating multiple copies of the same data sets in different places means that cyber attackers have more potential targets in which to steal this information means this memorandum creates far more questions than it begins to answer." Ross Rustici, senior director, intelligence services at Cybereason, wonders if the memorandum is designed to increase the capability of the CTIC, "which was stood up in the twilight of Obama's administration. The idea behind the CTIC," he told SecurityWeek, "was to create a new cyber threat center for cyber. However, because the initial operating capacity was being built as the administration was packing up it never got the full capability or support necessary to be effective." However, he also suggests that the memorandum is indicative of the slow progress made to date. It "shows how little the creation of the Director of National Intelligence and the 9/11 Commission has impacted business as usual in the intelligence community. In addition, the focus on 'threat actors and their networks' speaks to something beyond sharing data for defending networks. This directive is about increasing the intelligence community's ability to share all the dots they already have to connect them better." Researchers Warn of Cyber Risks for Olympic Games A report by University of California researchers said the efforts to disrupt the 2016 US election should serve as warning about the impact of a cyber-attack on the games. The report released four months ahead of the Pyeongchang Winter Games cited "an increasing supply of opportunities for digital manipulation as sports incorporate new technologies designed to improve athlete training, accessorize the fan experience, and even help officials decide the results." The researchers said hackers could do damage by infiltrating stadium or scoring systems, or by releasing sensitive data on athletes. Fans or transport systems could also be targeted. "Most serious would be physical harm caused to the athletes or spectators; in such a case, the event would be overshadowed and likely cancelled as a result of these more serious harms," said the report by the university's Center for Long-Term Cybersecurity. "Attacks on the integrity of the sporting event would also be serious... interference with the outcome could result in a decreased sense of trust that would have lasting impacts on the sport." Cybersecurity has become more important as sporting events have introduced new technologies for everything from tickets to replays and scoring verification. In recent years, hackers have increasingly sought to target sporting events, the researchers noted. In one case, the hacker group known as Anonymous hacked into the Formula One website to protest a race held in Bahrain. And during the 2014 World Cup of football, phishing attacks from "hacktivists" infiltrated email accounts local for many Brazilian officials organizing the event. Betsy Cooper, director of the center, said the report does not seek to evaluate how well-prepared Olympics organizers are for cybersecurity. "Because the landscape of sports is changing so dramatically, it would be very difficult to predict today what that future risk landscape might look like even in a few years, let alone in 2024 or 2028," she said. "It's very clear from our research that those in charge of preparing for future Olympic Games are taking security extremely seriously, which will be a great benefit as those games go forward." Accenture Exposed Data via Unprotected Cloud Storage Bucket The cloud storage containers were discovered on September 17 by Chris Vickery of cyber resilience company UpGuard and they were secured a couple of days later after Vickery notified Accenture of his findings. The largest of the buckets stored 137 GB of data, including 40,000 plaintext passwords, hashed passwords, access keys for the Enstratus cloud infrastructure management platform, email data, and information on the consulting firm’s ASGARD database. The same container also stored credentials for Accenture’s Google and Azure accounts, and data dumps from an event tracker, including IP addresses and other Accenture client data. Another bucket stored internal access keys and credentials for an API apparently used by Accenture to authenticate credentials, configuration files for the same API, a master access key for the company’s AWS Key Management Service account, and private signing keys. The unprotected containers also stored information on Accenture’s cloud stores, including VPN keys and other data that UpGuard believes could have been used by malicious actors to obtain insight into the company’s operations. Some of the private keys and certificates found in one of the buckets may have allowed attackers to decrypt traffic between Accenture and its clients, UpGuard said. “Taken together, the significance of these exposed buckets is hard to overstate. In the hands of competent threat actors, these cloud servers, accessible to anyone stumbling across their URLs, could have exposed both Accenture and its thousands of top-flight corporate customers to malicious attacks that could have done an untold amount of financial damage,” explained UpGuard’s Dan O’Sullivan. “It is possible a malicious actor could have used the exposed keys to impersonate Accenture, dwelling silently within the company’s IT environment to gather more information,” O’Sullivan added. However, Accenture, whose customers include 94 of the Fortune Global 100 companies, has downplayed the potential impact of the leak, claiming that there was no risk to any of its clients and that no active credentials or other information had been compromised. The company said none of the exposed files stored production data and the credentials could not have been used to access customer systems. Accenture is also confident that its security systems would have caught any intrusion attempts. This is not the first time UpGuard has found an unprotected AWS S3 bucket exposing sensitive information. In the past months, the company discovered that a Republican Party contractor exposing the details of 198 million American voters, recruiting firm TalentPen exposing information on job applicants at security firm TigerSwan, a call center services provider exposing the details of Verizon customers, and Booz Allen Hamilton exposing U.S. military files. In all cases, data was leaked online due to unprotected Amazon Web Services (AWS) S3 buckets. In order to help organizations prevent leaks caused by third-party vendors, UpGuard announced on Tuesday the launch of CyberRisk, a new product that automates risk assessment for third-party vendors. Hackers Can Execute Code on Windows via DNS Responses The security hole, tracked as CVE-2017-11779, was discovered by researchers at Bishop Fox and it affects Windows Server 2012 and 2016, Windows 8.1 and Windows 10. Microsoft said the vulnerability exists due to the way the Windows DNSAPI (dnsapi.dll) handles DNS responses. The vendor said there was no evidence of exploitation in the wild and believes the weakness is “less likely” to be exploited. According to Bishop Fox, an attacker needs to be in a man-in-the-middle (MitM) position in order to exploit the flaw (e.g. via an unprotected public Wi-Fi connection that the victim connects to). However, if this requirement has been achieved, the attacker can execute arbitrary code in the context of the application that made the DNS request (e.g. web browser). The attack does not require user interaction, it offers unlimited exploit attempts, and there is nothing to alert the user of unauthorized activity. Bishop Fox said the attack relies on three buffer overflow vulnerabilities that can be triggered using malformed NSEC3 records in reply to a DNS request made by the user’s web browser or another application. NSEC3 is a resource record that provides authenticated denial of existence and it’s part of the Domain Name System Security Extensions (DNSSEC) protocol, which is designed to prevent DNS spoofing attacks. “[The vulnerability] can affect processes running at different privilege levels (including SYSTEM) and the DnsCache service under svchost.exe restarts on failure,” Bishop Fox researchers said in a blog post. “This means an attacker can first kill the DnsCache service to have a more deterministic starting state of the heap, exploit the issue multiple times to leak addresses for defeating ASLR, and then use the disclosed addresses when delivering the final exploit.” “As a constraint, at this point it is unknown if a malicious payload could successfully traverse a recursive DNS server,” they added. “To date, tested DNS resolvers do not accept the malformed record.” Bishop Fox has published a blog post containing technical details on CVE-2017-11779 and a video providing a high level explanation of the flaw: Microsoft’s latest security updates also fix an Office zero-day that has been exploited to deliver data-stealing malware in targeted attacks (CVE-2017-11826), and more than two dozen other critical vulnerabilities. Nearly 700,000 UK Nationals Affected by Equifax Breach: Company "Although our UK business was not breached, the attack regrettably compromised the personal information of a range of UK consumers," the company said in an emailed statement. The company, which last month announced one of the most potentially damaging data breaches affecting some 145 million Americans, said the attackers also accessed a file containing 15.2 million records on 693,665 British nationals. "Equifax takes this illegal and unprecedented breach of consumers' data extremely seriously and has begun writing to the groups of consumers outlined below to notify them of the nature of the breach and offer them appropriate advice," the statement said. The company said it waited for a forensic analysis of the cyber attack before determining its course of action for Britons. "Once again, I would like to extend my most sincere apologies to anyone who has been concerned about or impacted by this criminal act," said Patricio Remon, president for Europe at Equifax Ltd. "It has been regrettable that we have not been able to contact consumers who may have been impacted until now, but it would not have been appropriate for us to do so until the full facts of this complex attack were known, and the full forensics investigation was completed." Last week, former Equifax chief Richard Smith blamed a combination of human and technical error for the breach, which is not the largest on record but which could have leaked sensitive financial information on consumers. An internal investigation determined the unauthorized access occurred from mid-May through July 2017, according to the company. Equifax collects information about people and businesses around the world and provides credit ratings used for decisions regarding loans and other financial matters. Hacking the Election: Security Flaws Need Fixing, Researchers Say A report with detailed findings from a July hacker conference which demonstrated how voting machines could be manipulated concluded that numerous vulnerabilities exist, posing a national security threat. The researchers analyzed the results of the "voting village" hacking contest at the DefCon gathering of hackers in Las Vegas this year, which showed how ballot machines could be compromised within minutes. "These machines were pretty easy to hack," said Jeff Moss, the DefCon founder who presented the report at the Atlantic Council in Washington. "The problem is not going away. It's only going to accelerate." The report said the DefCon hack was just the tip of the iceberg -- with potential weaknesses in voter databases, tabulating software and other parts of the system. The researchers said most voting machines examined included at least some foreign-manufactured parts, raising the possibility that malware could be introduced even before the devices are delivered. "This discovery means that a hacker's point-of-entry into an entire make or model of voting machine could happen well before that voting machine rolls off the production line," the report said. "With an ability to infiltrate voting infrastructure at any point in the supply chain process, then the ability to synchronize and inflict large-scale damage becomes a real possibility." - No certainty on 2016 - Harri Hursti, a researcher with Nordic Innovation Labs and a co-author of the report, said it's impossible to say with certainty if votes were tampered with in 2016 because many systems "don't have the capacity" to be audited. The report said five US states operate entirely on paperless systems which have no paper trail to be reviewed and another nine states are partially paperless. "The only way to know is if the hacker tells you," he said, adding that "it can be done without leaving tracks." Douglas Lute, former US ambassador to NATO who presented the report, said in a forward to the report that the findings highlight "a serious national security issue that strikes at the core of our democracy." Although some researchers in the past have shown individual machines could be breached, this report suggests a range of vulnerabilities across a range of hardware, software and databases. "What the report shows is that if relative rookies can hack a voting system so quickly, it is difficult to deny that a nefarious actor -- like Russia -- with unlimited time and resources, could not do much greater damage," said University of Chicago cybersecurity instructor Jake Braun, another co-author. The threat becomes all the more grave "when you consider they could hack an entire line of voting machines, remotely and all at once via the supply chain," he added. In presenting the findings, the researchers said members of the DefCon hacker community would work with academics and security researchers in a new coalition aimed at improving election security. Microsoft Patches Office Zero-Day Used to Deliver Malware The actively exploited vulnerability, tracked as CVE-2017-11826 and classified by Microsoft as “important,” is caused by a memory corruption issue. It allows a remote attacker to execute arbitrary code by getting the targeted user to open a specially crafted file. The zero-day affects all supported versions of Office. The weakness was reported to Microsoft by researchers at China-based security firm Qihoo 360. The experts said they first observed an attack exploiting this vulnerability on September 28. The attacks targeted a small number of the company’s customers and they involved malicious RTF files. Qihoo 360 has not provided too many details, but its analysis of the command and control (C&C) server used by the attackers showed that the operation was initiated in August and the first attacks were launched in September. Researchers said the hackers used phishing techniques to get the targeted users to open the malicious documents. The final payload was a Trojan designed to steal sensitive information from infected devices. Qihoo 360 said the attack also involved a DLL hijacking vulnerability in a “well-known” security product. The affected cybersecurity vendor has not been named, but DLL hijacking flaws have been found in the products of several companies, including Symantec, Kaspersky Lab, Rapid7, F-Secure and Comodo. Microsoft has also patched two vulnerabilities whose details were publicly disclosed before fixes were made available. This includes an XSS vulnerability in SharePoint (CVE-2017-11777), and a denial-of-service (DoS) issue in the Windows subsystem for Linux (CVE-2017-8703). A total of 27 flaws have been classified as critical, including a remote code execution vulnerability related to Windows DNSAPI (CVE-2017-11779). Microsoft also published an advisory to warn users of a security feature bypass affecting the firmware of Infineon Trusted Platform Modules (TPMs). The updates released by Microsoft last month patched roughly 80 vulnerabilities, including a .NET zero-day that had been exploited to deliver FinFisher malware to Russian-speaking individuals. Adobe has not released any Patch Tuesday updates. If no patches are released until the end of the month, it will be the first time since July 2012. Adobe Releases No 'Patch Tuesday' Updates Adobe typically releases security updates for its products on the second Tuesday of every month, also known as “Patch Tuesday.” In some months, patches were released a few days sooner – particularly when zero-day vulnerabilities had been discovered – or a few days later. Adobe says it does not have any security updates this month, but it has still advised users to update Flash Player to the latest version. Only a total of four vulnerabilities were patched in Flash Player in August and September. The number of flaws discovered by researchers has decreased dramatically in the past period, particularly after Adobe announced its intention to kill the application by 2020. Nevertheless, Flash Player exploits could still be valuable to malicious actors and we cannot rule out the possibility that a zero-day will be uncovered by the end of the month and the company will be forced to release a patch after all. The last Flash Player zero-day was addressed in December 2016. Apple, Facebook, Google, Microsoft and Mozilla have recently outlined their plans for moving away from Flash Player. Mozilla announced in August that it had disabled the Flash plugin by default with the release of Firefox 55. Since March 2008, when Adobe started announcing security updates on its Product Security Incident Response Team (PSIRT) blog, the only months when no vulnerability fixes were announced were May 2008, September 2008, January 2009, March 2010, July 2010, January 2011, July 2011 and July 2012. Hybrid Bank Heists Net Millions in Cash for Criminals Organized crime and cybercriminals are working together to steal large amounts of cash from banks. The money is taken in multiple but relatively small amounts from ATMs. Organized crime sets up the accounts and collects the cash, while cybercriminals hack the banks and manipulate the accounts. The details come from a study (PDF) published today. In mid-to-late 2017, Trustwave SpiderLabs was asked to investigate a number of bank breaches that had occurred in post-Soviet countries -- and found a series of common features. Money was being stolen via ATMs from what appeared to be legitimate accounts. Because the accounts were 'legitimate', alarms were not raised; and in many cases the thefts only became apparent long after the event. The process requires an alliance between organized crime (such as Mafia, Yakuza, etc) and cyber criminals. Organized crime controls the manpower -- the mules. The mules are supplied with fake IDs. They establish rogue accounts with the targeted banks, and request debit cards. Once the debit cards are received, they are sent outside of the country -- part of keeping the attack low profile is not to steal money via ATMs in a country where the bank has a presence. The next stage is for the cybercriminals to compromise the target bank. This would normally be by phishing and social engineering. "While the physical activities involving application for accounts and debit cards were taking place at the bank's various branches in the country," notes the report, "the cyber attackers gained initial entry, moved laterally and compromised multiple systems inside the bank's network." From here the attackers crossed over to the bank's third-party processor using the established connectivity between bank and processor. The next stage was privilege escalation within the processor, and the delivery of multiple payloads. Key was Mipko, which is advertised as an 'employee monitor'. This enabled them to locate the privileged accounts that could alter customer card conditions. This allowed the attackers to locate and alter the conditions on the rogue accounts. They activated the overdraft settings and changed the limit from the default value of zero to ranges varying from $25,000 to $35,000. All of this was coordinated with the cash withdrawals via overseas ATMs. "The physical counterparts stationed at various locations in Europe and the Russian Federation" notes the report, "then cashed out substantial amounts of money for each of these cards from ATM terminals. Cash withdrawals across the region began within minutes of the first OD property change made to the debit cards on the card management application... Within the next few hours the operation concluded, removing up to USD$10 million from each bank." The process from account manipulation to foreign cash withdrawals took only about five hours. But the withdrawals were not the final act of the attack. "Almost two hours after the last withdrawal occurred the criminals wiped the server," Thanassis Diogos, SpiderLabs managing consultant, told SecurityWeek. "They were sure that their actions would trigger an investigation, so they were most probably trying to remove evidence from the crime scene. And they succeeded to a point because the internal server used for maintaining external connections had nothing to do the with card processing infrastructure. So the IT department never associated the failure of that system with the incident -- it was only at the point of log analysis that it pointed to that system." SpiderLabs has seen the same process in four separate banks (two in Russia, and two in post-Soviet states); and is investigating a possible fifth in Africa. It is not clear whether it is the same gang in all cases. "The malware used differs per case but methodology was the same," said Diogos. It could be the same gang using different malware under different conditions, or it could be different gangs altogether, since "underground forums share these ideas." One thing that is clear is the growing cooperation between organized crime (feet on the street) and criminal hackers -- although at this stage it is not clear whether hacking crews are contacting criminal gangs, or criminal gangs are recruiting hacking crews. "One way or another," said Diogos, "the spread of electronic devices and data digitization has come under crime's scope." The total amount lost to this particular methodology is not known. It is generally believed that financial institutions do not own up to all of their losses in order to maintain faith in their brand. "Our investigations have revealed victim losses currently around approximately USD$40 million. However, when taking into account the undiscovered or uninvestigated attacks along with investigations undertaken by internal groups or third parties, we estimate losses to be in the hundreds of millions in USD. All global financial institutions should consider this threat seriously and take steps to mitigate it." New ATMii Malware Can Empty ATMs Dubbed ATMii, the threat was first spotted in April this year, featuring an injector module (exe.exe) and the module to be injected (dll.dll). Actors using the malware need direct access to a target ATM (either over the network or physically) to install it. During analysis, the security researchers discovered that the injector, an unprotected command line application, was written in Visual C with a fake compilation timestamp of four years ago. The malware features support for a Windows version more recent than Windows XP, which is the platform most ATMs run. The injector targets the proprietary ATM software process called atmapp.exe to inject the second module into it. However, the injector appears fairly poorly written, being dependent on several parameters and catching an exception if no parameter is given. The supported parameters include /load, which attempts to inject dll.dll into atmapp.exe, /cmd, which creates or updates the C:\ATM\c.ini file (which is used by the injected DLL to read commands), and /unload, which attempts to unload injected library from atmapp.exe process, while restoring its state. Based on available commands, the malware can scan for the CASH_UNIT XFS service, can dispense a desired amount of cash (where the “amount” and “currency” are used as parameters), retrieve information about ATM cash cassettes and write it to the log file, and remove the C:\ATM\c.ini file. The injected module tries to find the ATM’s CASH_UNIT service id, as it cannot function without this service. After finding it, it stores the result and starts passing all further calls to a function in charge of reading, parsing, and executing the commands from the C:\ATM\c.ini file. “ATMii is yet another example of how criminals can use legitimate proprietary libraries and a small piece of code to dispense money from an ATM. Some appropriate countermeasures against such attacks are default-deny policies and device control. The first measure prevents criminals from running their own code on the ATM’s internal PC, while the second measure will prevent them from connecting new devices, such as USB sticks,” Kaspersky concludes. UK's Top Spy Agency Coming Out of the Shadows: GCHQ Director The UK's Government Communications Headquarters (GCHQ) is one of the UK's more secretive intelligence agencies. Its existence was not acknowledged until 1976, when investigative journalists Duncan Campbell and Mark Hosenball (an American journalist working in the UK) 'outed' the organization in an article in Time Out. Hosenball was rapidly deported because he was deemed to be a threat to UK national security. GCHQ started life at the end of the First World War as the Government Code and Cypher School (GC&CS). It operated from Bletchley Park during the Second World War where it, and particularly Alan Turing, were instrumental in breaking the German Enigma encryption system. Even that was not acknowledged for thirty years. The organization moved to Cheltenham, now occupying the 'doughnut', after the war -- and changed its name to GCHQ. In the early 1970s, a GCHQ staff member named James Ellis developed the concept of public key encryption -- but not being a mathematician, could not make a working implementation. It was not until the 1980s that the Americans Whitfield Diffie and Martin Hellman independently discovered public key encryption. GCHQ's efforts were not publicly disclosed until 1997. This predilection for secrecy is, overtly at least, slowly breaking down. It probably started and is an inevitable consequence of the evolution of the new National Cyber Security Centre (NCSC), which is part of GCHQ. Communications has always been the domain of GCHQ; but the rise of the internet means that crime and communications intelligence cannot realistically be separated. Locating NCSC within GCHQ is logical, where it is able to draw upon the enormous GCHQ cyber expertise to combat crime -- whether that is terrorist related or organized crime related. However, fighting crime cannot be done in the publicity vacuum that has been the traditional domain of GCHQ. NCSC, currently celebrating its first anniversary, talks to and works with business, and advises the public on cyber security awareness. GCHQ is very slowly emerging from the shadows. The process of emergence was highlighted on Saturday when the director of GCHQ, Jeremy Fleming, made his most extensive public comment so far in an article published in the Telegraph. He moved from MI5 to GCHQ in March 2017. Without going into details on the amount, he writes, "The Government's investment in a bigger GCHQ gives us a chance to recruit the brightest and best from across our society -- as the threat becomes more diverse, so must the workforce that tackles it." Inside GCHQ 3 "By its nature," wrote Fleming, NCSC "has to work closely with the private sector; it works at lower (or without) security classifications, proactively engages with the media, and has a high profile in schools and universities. All of this can feel deeply challenging for a GCHQ that by necessity has worked in the shadows." Fleming describes GCHQ as being 'at the heart of the nation's security.' "Over the past year," he writes, GCHQ/NCSC "has responded to nearly 600 significant incidents requiring a national, coordinated response. In dealing with these cases, from the WannaCry ransomware affecting the NHS through the attack on Parliament to lesser-known but important compromises and criminal attacks, the NCSC drew on GCHQ's data, analytical capabilities, skills and partnerships, which help us to prevent attacks as well as respond to them." The WannaCry attack typifies the need to combine cyber intelligence and cybercrime activities. Ransomware is mainstream criminal activity; but the WannaCry outbreak is thought to have been delivered by nation-state actors working for North Korea. The combination of geopolitics and cybersecurity is getting increasingly entwined. "Keeping our citizens safe and free online must become and remain as much part of our mission as our global intelligence reach and our round-the-clock efforts against terrorism," he concludes. It remains to be seen whether almost a century of secrecy can be altered in the new GCHQ. Whether it can or not, however, the combination of GCHQ and NCSC expertise is broadly welcomed. "The efforts of the British government to assure cybersecurity and online safety for its citizens are laudable, and should serve as an example to other countries," commented Ilia Kolochenko, CEO of High-Tech Bridge. He warns, however, that it is an impossible task for a single nation. "However, the Internet is an open world without borders, and thus it's not an easy task to keep digital peace in a particular country or geographical area. It is virtually impossible to keep citizens of a particular country safe." Since the problem is international and not entirely cyber-related, so must be the solution. Cybersecurity cannot be achieved, "without first resolving the intertwined problems of cybercrime, poverty, political crises and nation-state attacks. International cooperation, global economic and political stability -- are vitally important to fight skyrocketing cybercrime." Peter Yapp, Deputy Director at NCSC, will be speaking on a panel at SecurityWeek's 2017 ICS Cyber Security Conference on Oct. 25 in Atlanta to discuss the growing global threat of international intrusions and cyberattacks on critical national infrastructure. Yapp will be joined by Simon Hodgkinson, CISO at BP; Dr. Kevin Jones, Head of Cyber Security Architecture, Innovation and Scouting at Airbus; and Dr. Chris Hankin, Director at the UK ICS cyber security Research Institute (RITICS). UpGuard Automates Vendor Risk Management The new CyberRisk product scans each third-party vendor’s assets for cybersecurity weaknesses and assigns them a risk score based on UpGuard’s Cybersecurity Threat Assessment Rating (CSTAR) system. UpGuard, formerly known as ScriptRock, has raised nearly $27 million since 2012, including $17 million in a Series B funding round last year. Several major data breaches discovered by the company in the past months showed the risks posed by third-party vendors. UpGuard The list of incidents includes a Republican Party contractor exposing the details of 198 million American voters, recruiting firm TalentPen exposing information on job applicants at security firm TigerSwan, a call center services provider exposing the details of Verizon customers, and Booz Allen Hamilton exposing U.S. military files. In all cases, data was leaked online due to unprotected Amazon Web Services (AWS) S3 buckets. UpGuard’s CyberRisk solution aims to help organizations prevent such incidents byproviding detailed information on their third-party vendors’ security posture. UpGuard’s Cloudscanner analyzes billions of web properties every day in search of risk factors that could lead to data breaches. The targeted vendor is then assigned a CSTAR risk score ranging between 0 and 950. This score takes into account several factors, including an organization’s size, infrastructure, asset configurations, exposure, industry trends, and device vulnerabilities. Since the security firm’s automated scans cannot detect all potential weaknesses, CyberRisk provides integrated questionnaires that organizations can send to their vendors. The customer simply has to select which categories they want the questionnaire to cover and enter the targeted vendor’s email address. Once the vendor completes the questionnaire, the results of the assessment are stored in the respective company’s risk profile. “Just as companies do background checks on prospective employee hires, it only makes sense that they conduct similar assessments of any third-party business partners before granting them access to their corporate data,” said Mike Baukes, co-founder and co-CEO of UpGuard. “Unfortunately, many organizations still lack the processes and tools to conduct a comprehensive audit of internal and external factors affecting vendor risk. This is evidenced by the sheer number breaches occurring on a daily basis. This is an epidemic. Our CyberRisk product not only integrates both critical aspects, but we take it several steps further by providing our customers with clear remediation guidance to become truly cyber resilient,” Baukes added. North Korea Hacked Seoul's War Plans: Report North Korean computer hackers have stolen hundreds of classified military documents from South Korea including detailed wartime operational plans involving its US ally, a report said Tuesday. Rhee Cheol-Hee, a lawmaker for the ruling Democratic party, said the hackers broke into the South's military network in September last year and gained access to 235 gigabytes of sensitive data, the Chosun Ilbo daily reported. Among the leaked documents was Operational Plans 5015 for use in case of war with the North and including procedures for "decapitation" attacks on leader Kim Jong-Un, the paper quoted Rhee as saying. Rhee, a member of parliament's defence committee, could not be reached for comment, but his office said he had been quoted correctly. The report comes amid heightened fears of conflict on the Korean peninsula, fuelled by US President Donald Trump's continued threats of military action against Pyongyang to tame its weapons ambitions. In his latest tweet over the weekend, Trump reiterated that diplomatic efforts with North Korea have consistently failed, adding that "only one thing will work." Pentagon spokesman Colonel Rob Manning said he was aware of the report, but declined to confirm or deny any aspect of it. "I can assure you that we are confident in the security of our operations plans and our ability to deal with any threat from North Korea," Manning told Pentagon reporters. "I am not going to address whether or not that (hack) has occurred. What I am going to tell you is that the (South Korea)-US alliance, that bilateral entity, is there to deal with those types of situation and safeguard against them." - 80 percent unidentified - Citing Seoul's defence ministry, Rhee said that 80 percent of the leaked documents had yet to be identified. But the contingency plan for the South's special forces was stolen, he said, as well as details about annual joint military drills with the US and information on key military facilities and power plants. A ministry spokesman declined to confirm the report, citing intelligence matters. In May, the ministry said North Korea had hacked into Seoul's military intranet but did not say what had been leaked. Pyongyang has a 6,800-strong unit of trained cyberwarfare specialists, according to the South Korean government. It has been accused of launching high-profile cyberattacks, including the 2014 hacking of Sony Pictures. The Chosun Ilbo story was the second report Tuesday of military-related cyber-attacks in the Asia-Pacific. Australia's government said separately an unidentified defence contractor had been hacked and a "significant amount of data" stolen. There were 47,000 cyber-incidents in the last 12 months, a 15 percent increase from the previous year, Minister for Cyber Security Dan Tehan said in Canberra as he unveiled a report by the Cyber Security Centre. The defence contractor was exploited via an internet-facing server, with the cyber-criminals using remote administrative access to remain in its network, the report said. The hacker was reportedly based in China, but Tehan told the Australian Broadcasting Corporation that "we don't know and we cannot confirm exactly who the actor was." Iranian Cyberspies Use New Trojan in Middle East Attacks The threat actor, known as OilRig, was recently spotted launching attacks against an organization within the government of the United Arab Emirates (UAE). When it first discovered the group’s activities back in May 2016, Palo Alto Networks believed the attacks had been carried out by a known group, but researchers later determined that the campaign was actually the work of a new actor, which is now tracked as OilRig. OilRig has been known to use a remote access trojan (RAT) named ISMDoor, which researchers also identified in attacks launched by another Iran-linked cyberspy group known as Greenbug.OilRig hackers use new Trojan In attacks seen by Palo Alto Networks in July 2017, OilRig had started using a new piece of malware dubbed “ISMAgent,” which appeared to be a variant of the ISMDoor RAT. In even more recent attacks, observed by experts in August 2017, a new injector Trojan was used by the attackers. The new malware, tracked as “ISMInjector,” is a tool that has a sophisticated architecture and it includes anti-analysis techniques that were not previously leveraged by this group. “The complex structure and inclusion of new anti-analysis techniques may suggest that this group is increasing their development efforts in order to evade detection and gain higher efficacy in their attacks,” Palo Alto Networks researchers said in a blog post. In the attack aimed at the UAE government, hackers delivered their malware using malicious documents attached to emails with the subject line “Important Issue.” What made the emails interesting was the fact that they came from the targeted organization’s own domain. While experts initially believed that the attackers had spoofed the sender, they later determined that they actually used a compromised Outlook Web Access (OWA) account whose credentials they obtained in a previous phishing attack. The malicious documents sent to the UAE government, tracked by Palo Alto as “ThreeDollars,” delivered the new ISMInjector Trojan, which in turn dropped a variant of the ISMAgent backdoor by injecting it into a remote process it created. In order to make analysis of ISMInjector more difficult, the malware’s developers have relied on what researchers call “state machines” to create a new process and inject the payload into that process. Each state is responsible for conducting a particular action and it specifies the next state that should be executed. Since the states are not executed in sequential order, researchers analyzing the malware have to jump around in the code to determine how it works, which makes it more challenging to investigate the threat. Analysis of the malware is further complicated by the use of a crypter. Iran appears to have several cyber espionage groups, including APT33, Rocket Kitten, Cobalt Gypsy (Magic Hound), Charming Kitten (aka Newscaster and NewsBeef) and CopyKittens. FIN7 Hackers Change Attack Techniques Highly active since the beginning of 2017, FIN7 (also known as Anunak, or Carbanak) started distributing malware via LNK files embedded in Word documents using the Object Linking and Embedding (OLE) technology. The attack employed a fileless infection method, with no files being written to disk. The hackers have since switched to using CMD files instead of LNK ones, most probably in an attempt to evade detection. The CMD, the researchers explain, would write JScript to “tt.txt” under the current user’s home directory. Next, the batch script copies itself to “pp.txt” under the same directory, and then runs WScript using the JScript engine on the file. According to ICEBRG, the JScript code then reads from the “pp.txt” file, evaluating anything after the first character for each line in the file. However, it skips the first four lines, which represent the CMD code itself. The same as with the LNK files, however, the use of OLE embedded CMD files results in code execution on the victim’s machine. The use of commented out code isn’t new either, and has been previously associated with FIN7. The security researchers also observed a series of changes to the obfuscation strategy the hackers are using for their unique backdoor, HALFBAKED, which has been continuously morphing over the past year. Until now, different stages of the HALFBAKED codebase used base64 encoding, stored in a string array variable called “srcTxt,” the researchers explain. Now, the name is obfuscated and the base64 string is broken down into multiple strings within an array. Furthermore, the backdoor now includes a built-in command called “getNK2”which is meant to retrieve the victim’s Microsoft Outlook email client auto-complete list. The command was likely named after the NK2 file that contains a list of auto-complete addresses for Microsoft Outlook 2007 and 2010. “This may suggest the actor’s desire to obtain new phishing targets within a victim organization. If any of these new targets fell victim to the phishing lure, it would allow FIN7 to increase their foothold within a victim organization’s network and potentially pivot to new areas,” the researchers note. Although newer versions of Outlook no longer use the NK2 file, the backdoor targets them as well, because the hackers also wrote functionality to handle them within the same “getNK2” command. “Detection authors must make trade-offs to optimize signature performance; narrow signatures lead to high fidelity detections, but risk missing changes in actor behaviors, meanwhile broader detection patterns provide better coverage, at the risk of more false positives. Combatting a well-resourced and adaptive adversary requires a layered approach of both signature styles,” ICEBRG concludes. Varied Patch Process by Microsoft Exposes Windows Users: Google Researcher The researchers explain that, because Microsoft silently patches reported vulnerabilities in major Windows 10 releases, such as the Creators Update or the Fall Creators Update, Windows 8 and Windows 7 users become exposed to vulnerabilities that affect their platform iterations as well. The issue is that attackers can compare patched Windows 10 builds with the previous, unpatched builds to discover the addressed issues and then target older and still vulnerable platform iterations. By comparing the builds, attackers can discover the vulnerabilities and technical details surrounding them. Called patch diffing, the technique of comparing binaries is also employed to discover so-called 1-day bugs, or vulnerabilities affecting users who are slow to install security patches, Mateusz Jurczyk of Google Project Zero explains. Another technique that attackers can use is binary diffing, which allows them to discover differences between “two or more versions of a single product, if they share the same core code and coexist on the market, but are serviced independently by the vendor.” The Windows operating system is one product binary diffing can be used on, as it currently has three versions under active support, namely Windows 7, 8, and 10. Despite Windows 7 having the largest desktop market share at the moment, at nearly 50%, only the most recent platform iteration is receiving structural security improvements. “This creates a false sense of security for users of the older systems, and leaves them vulnerable to software flaws which can be detected merely by spotting subtle changes in the corresponding code in different versions of Windows,” the security researcher says. In a blog post, Jurczyk shows how binary diffing was used “to find instances of 0-day uninitialized kernel memory disclosure to user-mode programs.” Such issues can be used in local privilege escalation exploit chains or to expose sensitive data stored in the kernel address space, he argues. “Security-relevant differences in concurrently supported branches of a single product may be used by malicious actors to pinpoint significant weaknesses or just regular bugs in the more dated versions of said software. Not only does it leave some customers exposed to attacks, but it also visibly reveals what the attack vectors are, which works directly against user security,” Jurczyk notes. Contacted by SecurityWeek, a Microsoft spokesperson provided the following statement: “Windows has a customer commitment to investigate reported security issues, and proactively update impacted devices as soon as possible. Additionally, we continually invest in defense-in-depth security, and recommend customers use Windows 10 and the Microsoft Edge browser for the best protection.” Patches aimed to address the specific vulnerabilities Google’s researcher mentions in his post were released to all supported Windows versions, the Microsoft spokesperson also pointed out. Website Attacks Surge: Report The number of attacks aimed at websites has increased considerably in the past months, according to a new report published on Monday by SiteLock. SiteLock’s Website Security Insider report, which is based on the analysis of more than 6.3 million sites, shows that there were, on average, 63 attack attempts per day on websites in the second quarter of the year. In comparison, the company saw only 22 attacks per day in 2016. According to the company, 87% of these attacks involved malicious bots, including ones operated by cybercriminals, spammers and data scrapers. As for attacks that did not involve bots, more than 57% of requests were blocked by SiteLock due to the fact that they came from countries blacklisted by its customers, and 36% were illegal resource access attempts, including command injections, directory traversals and file system access. When it comes to content management systems (CMS), SiteLock says the risk of attacks on WordPress websites is twice as high as in the case of the “average site.” The security firm discovered that 69% of compromised WordPress websites had the latest WordPress core security patches installed, which indicates that the attack was likely carried out via a vulnerable theme or plugin. The higher the number of plugins, the more likely it is for a WordPress website to get hacked, and researchers found that 44% of the plugins in the official WordPress repository have not been updated in more than a year. This includes over 120 plugins that have at least 50,000 active installs. Joomla and Drupal are also at elevated risk of attacks, especially since they haven’t always offered reverse compatibility with legacy features, making their administrators less likely to install updates. In the case of Joomla, SiteLock found that 19% of the sites it observed had been using version 1.5, for which support ended in September 2012. An analysis of the malicious code planted on compromised websites showed that 62% of threats were related to spam, while nearly a quarter were backdoors. Worryingly, many websites don’t have adequate protections in place and their administrators are often alerted to malicious activity by web browser warnings such as the ones displayed in Firefox via Phishing Protection and in Chrome via Safe Browsing. “Browser warnings about compromised websites are usually driven by blacklists maintained by search engines, where search engine crawlers have recognized that malicious code is present on the website they’re attempting to index,” SiteLock explained in its report. “For many website owners this practice creates an assumption that if there are no warnings, then there isn’t an issue. Unfortunately, this incorrect assumption puts both the website and its visitors in danger. In three out of four cases, infected websites were not flagged by search engines” SiteLock has surveyed more than 20,000 owners and over 40% of them falsely believe that their hosting provider is responsible for securing their websites. SecureWorks shed light on BRONZE BUTLER group that targets Japanese Enterprises Researchers with Counter Threat Unit at SecureWorks continues to monitor the Bronze Butler cyberespionage group (aka Tick). According to the experts, the group is linked to the People’s Republic of China and is focused on exfiltrating confidential data. “BRONZE BUTLER’s operations suggest a long-standing intent to exfiltrate intellectual property and other confidential data from Japanese organizations. Intrusions observed by CTU™ researchers indicate a focus on networks involved in critical infrastructure, heavy industry, manufacturing, and international relations.” states the analysis published by SecureWorks. SecureWorks detailed TTPs of the Bronze Butler group, the hackers used spearphishing, strategic web compromises (SWCs) in their targeted attacks and leveraged zero-day exploit to compromise targeted systems. The threat actor used to maintain access to compromised environments and periodically revisiting them to exfiltrate further data. “BRONZE BUTLER uses spearphishing emails and SWCs to compromise target networks, often leveraging Flash. The group has used phishing emails with Flash animation attachments to download and execute Daserf malware, and has also leveraged Flash exploits for SWC attacks.” continues the analysis. Experts observed Bronze Butler leveraging an Adobe Flash zero-day vulnerability (CVE-2016-7836) in a popular Japanese corporate desktop management tool called SKYSEA Client View. Experts highlighted the ability of the group in discovering a zero-day flaw in a software used in a certain region. The researchers documented one of the malware in the arsenal of the group, the Daserf backdoor that allows gaining full control over the compromised system. Bronze Butler developed two versions of the tool over time, in 2016, the hackers shifted from using Daserf to two remote access trojans (RATS) called xxmm and Datper. The following image shows some of the proprietary tools used by the group between 2012 and 2017. Analyzing the intent of the group, the researchers concluded the group may be tasked by multiple teams or organizations. “The focus on intellectual property, product details, and corporate information suggests that the group seeks information that they believe might be of value to competing organizations. The diverse targeting suggests that BRONZE BUTLER may be tasked by multiple teams or organizations with varying priorities.” concluded the report. Bronze Butler is still active and must be considered a very capable gang. Ukraine Police Warns of New NotPetya-Style Large Scale CyberAttack Presentation by Alexander Adamov, CEO at NioGuard Security Lab Scam Alert: Your Trusted Friends Can Hack Your Facebook Account If you receive a message from any of your Facebook Friends asking for urgent help to recover their Facebook account, since they've added you as one of their 'Trusted Contacts'—just don’t blindly believe it. The best way to protect yourself is always to be vigilant to every recovery emails you receive, and read the recovery message or email carefully, even if it is sent by one of your actual friends. New Ransomware Not Just Encrypts Your Android But Also Changes PIN Lock Once installed, the malware requests user for the activation of 'Google Play Services' accessibility feature, as shown in the demonstration video. Microsoft Issues Patches For Severe Flaws, Including Office Zero-Day & DNS Attack For full technical details, you can watch the video demonstration by Bishop Fox’s Dan Petro and head on to Bishop Fox’s blog post. Hackers Steal $60 Million from Taiwanese Bank; Two Suspects Arrested Israel Hacked Kaspersky, Caught Russian Spies Hacking American Spies, But... Buggy Microsoft Outlook Sending Encrypted S/MIME Emails With Plaintext Copy For Months MS Office Built-in Feature Allows Malware Execution Without Macros Enabled If allowed, the malicious document will communicate to the attacker hosted content in order to retrieve code that'll be executed to initiate the DNSMessenger malware infection.
As a proof-of-concept we executed a key reinstallation attack against an Android smartphone. In this demonstration, the attacker is able to decrypt all data that the victim transmits. For an attacker this is easy to accomplish, because our key reinstallation attack is exceptionally devastating against Linux and Android 6.0 or higher. This is because Android and Linux can be tricked into (re)installing an all-zero encryption key (see below for more info). When attacking other devices, it is harder to decrypt all packets, although a large number of packets can nevertheless be decrypted. In any case, the following demonstration highlights the type of information that an attacker can obtain when performing key reinstallation attacks against protected Wi-Fi networks:
Our main attack is against the 4-way handshake of the WPA2 protocol. This handshake is executed when a client wants to join a protected Wi-Fi network, and is used to confirm that both the client and access point possess the correct credentials (e.g. the pre-shared password of the network). At the same time, the 4-way handshake also negotiates a fresh encryption key that will be used to encrypt all subsequent traffic. Currently, all modern protected Wi-Fi networks use the 4-way handshake. This implies all these networks are affected by (some variant of) our attack. For instance, the attack works against personal and enterprise Wi-Fi networks, against the older WPA and the latest WPA2 standard, and even against networks that only use AES. All our attacks against WPA2 use a novel technique called a key reinstallation attack (KRACK):
In a key reinstallation attack, the adversary tricks a victim into reinstalling an already-in-use key. This is achieved by manipulating and replaying cryptographic handshake messages. When the victim reinstalls the key, associated parameters such as the incremental transmit packet number (i.e. nonce) and receive packet number (i.e. replay counter) are reset to their initial value. Essentially, to guarantee security, a key should only be installed and used once. Unfortunately, we found this is not guaranteed by the WPA2 protocol. By manipulating cryptographic handshakes, we can abuse this weakness in practice.
As described in the introduction of the research paper, the idea behind a key reinstallation attack can be summarized as follows. When a client joins a network, it executes the 4-way handshake to negotiate a fresh encryption key. It will install this key after receiving message 3 of the 4-way handshake. Once the key is installed, it will be used to encrypt normal data frames using an encryption protocol. However, because messages may be lost or dropped, the Access Point (AP) will retransmit message 3 if it did not receive an appropriate response as acknowledgment. As a result, the client may receive message 3 multiple times. Each time it receives this message, it will reinstall the same encryption key, and thereby reset the incremental transmit packet number (nonce) and receive replay counter used by the encryption protocol. We show that an attacker can force these nonce resets by collecting and replaying retransmissions of message 3 of the 4-way handshake. By forcing nonce reuse in this manner, the encryption protocol can be attacked, e.g., packets can be replayed, decrypted, and/or forged. The same technique can also be used to attack the group key, PeerKey, TDLS, and fast BSS transition handshake.
In our opinion, the most widespread and practically impactful attack is the key reinstallation attack against the 4-way handshake. We base this judgement on two observations. First, during our own research we found that most clients were affected by it. Second, adversaries can use this attack to decrypt packets sent by clients, allowing them to intercept sensitive information such as passwords or cookies. Decryption of packets is possible because a key reinstallation attack causes the transmit nonces (sometimes also called packet numbers or initialization vectors) to be reset to zero. As a result, the same encryption key is used with nonce values that have already been used in the past. In turn, this causes all encryption protocols of WPA2 to reuse keystream when encrypting packets. In case a message that reuses keystream has known content, it becomes trivial to derive the used keystream. This keystream can then be used to decrypt messages with the same nonce. When there is no known content, it is harder to decrypt packets, although still possible in several cases (e.g. English text can still be decrypted). In practice, finding packets with known content is not a problem, so it should be assumed that any packet can be decrypted.
Our attack is especially catastrophic against version 2.4 and above of wpa_supplicant, a Wi-Fi client commonly used on Linux. Here, the client will install an all-zero encryption key instead of reinstalling the real key. This vulnerability appears to be caused by a remark in the Wi-Fi standard that suggests to clear the encryption key from memory once it has been installed for the first time. When the client now receives a retransmitted message 3 of the 4-way handshake, it will reinstall the now-cleared encryption key, effectively installing an all-zero key. Because Android uses wpa_supplicant, Android 6.0 and above also contains this vulnerability. This makes it trivial to intercept and manipulate traffic sent by these Linux and Android devices. Note that currently 41% of Android devices are vulnerable to this exceptionally devastating variant of our attack.
The following Common Vulnerabilities and Exposures (CVE) identifiers were assigned to track which products are affected by specific instantiations of our key reinstallation attack:
CVE-2017-13078: Reinstallation of the group key (GTK) in the 4-way handshake.
CVE-2017-13079: Reinstallation of the integrity group key (IGTK) in the 4-way handshake.
CVE-2017-13080: Reinstallation of the group key (GTK) in the group key handshake.
CVE-2017-13081: Reinstallation of the integrity group key (IGTK) in the group key handshake.
CVE-2017-13082: Accepting a retransmitted Fast BSS Transition (FT) Reassociation Request and reinstalling the pairwise encryption key (PTK-TK) while processing it.
CVE-2017-13084: Reinstallation of the STK key in the PeerKey handshake.
CVE-2017-13086: reinstallation of the Tunneled Direct-Link Setup (TDLS) PeerKey (TPK) key in the TDLS handshake.
CVE-2017-13087: reinstallation of the group key (GTK) when processing a Wireless Network Management (WNM) Sleep Mode Response frame.
CVE-2017-13088: reinstallation of the integrity group key (IGTK) when processing a Wireless Network Management (WNM) Sleep Mode Response frame.
Note that each CVE identifier represents a specific instantiation of a key reinstallation attack. This means each CVE ID describes a specific protocol vulnerability, and therefore many vendors are affected by each individual CVE ID. You can also read vulnerability note VU#228519 of CERT/CC for additional details on which products are known to be affected.
Our research paper behind the attack is titled Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2 and will be presented at the Computer and Communications Security (CCS) conference on Wednesday 1 November 2017.
Linux's wpa_supplicant v2.6 is also vulnerable to the installation of an all-zero encryption key in the 4-way handshake. This was discovered by John A. Van Boxtel. The new attack works by injecting a forged message 1, with the same ANonce as used in the original message 1, before forwarding the retransmitted message 3 to the victim.
Addendum: other vulnerable handshakes
After our initial research as reported in the paper, we discovered that the TDLS handshake and WNM Sleep Mode Response frame are also vulnerable to key reinstallation attacks.
In Figure 9 at stage 3 of the attack, the frame transmitted from the adversary to the authenticator should say a ReassoReq instead of ReassoResp.
TOOLS
We have made scripts to detect whether an implementation of the 4-way handshake, group key handshake, or Fast BSS Transition (FT) handshake is vulnerable to key reinstallation attacks. These scripts will be released once we had the time to clean up their usage instructions.
Do we now need WPA3?
No, luckily implementations can be patched in a backwards-compatible manner. This means a patched client can still communicate with an unpatched access point, and vice versa. In other words, a patched client or access points sends exactly the same handshake messages as before, and at exactly the same moments in time. However, the security updates will assure a key is only installed once, preventing our attacks. So again, update all your devices once security updates are available.
Changing the password of your Wi-Fi network does not prevent (or mitigate) the attack. So you do not have to update the password of your Wi-Fi network. Instead, you should make sure all your devices are updated, and you should also update the firmware of your router. After updating your router, you can optionally change the Wi-Fi password as an extra precaution.
Yes, that network configuration is also vulnerable. The attack works against both WPA1 and WPA2, against personal and enterprise networks, and against any cipher suite being used (WPA-TKIP, AES-CCMP, and GCMP). So everyone should update their devices to prevent the attack!
I use the word "we" because that's what I'm used to writing in papers. In practice, all the work is done by me, with me being Mathy Vanhoef. My awesome supervisor is added under an honorary authorship to the research paper for his excellent general guidance. But all the real work was done on my own. So the author list of academic papers does not represent division of work :)
Probably. Any device that uses Wi-Fi is likely vulnerable. Contact your vendor for more information.
Our main attack is against the 4-way handshake, and does not exploit access points, but instead targets clients. So it might be that your router does not require security updates. We strongly advise you to contact your vendor for more details. In general though, you can try to mitigate attacks against routers and access points by disabling client functionality (which is for example used in repeater modes) and disabling 802.11r (fast roaming). For ordinary home users, your priority should be updating clients such as laptops and smartphones.
When working on the final (i.e. camera-ready) version of another paper, I was double-checking some claims we made regarding OpenBSD's implementation of the 4-way handshake. In a sense I was slacking off, because I was supposed to be just finishing the paper, instead of staring at code. But there I was, inspecting some code I already read a hundred times, to avoid having to work on the next paragraph. It was at that time that a particular call to ic_set_key caught my attention. This function is called when processing message 3 of the 4-way handshake, and it installs the pairwise key to the driver. While staring at that line of code I thought “Ha. I wonder what happens if that function is called twice”. At the time I (correctly) guessed that calling it twice might reset the nonces associated to the key. And since message 3 can be retransmitted by the Access Point, in practice it might indeed be called twice. “Better make a note of that. Other vendors might also call such a function twice. But let's first finish this paper...”. A few weeks later, after finishing the paper and completing some other work, I investigated this new idea in more detail. And the rest is history.
The brief answer is that the formal proof does not assure a key is installed once. Instead, it only assures the negotiated key remains secret, and that handshake messages cannot be forged.
We have follow-up work making our attacks (against for example macOS and OpenBSD) significantly more general and easier to execute. So although we agree that some of the attack scenarios in the paper are rather impractical, do not let this fool you into believing key reinstallations attacks cannot be abused in practice.
We are not in a position to determine if this vulnerability has been (or is being) actively exploited in the wild. That said, key reinstallations can actually occur spontaneously without an adversary being present! This may for example happen if the last message of a handshake is lost due to background noise, causing a retransmission of the previous message. When processing this retransmitted message, keys may be reinstalled, resulting in nonce reuse just like in a real attack.
NO! Keep using WPA2.
There seems to be an agreement that the Wi-Fi standard should be updated to explicitly prevent our attacks. These updates likely will be backwards-compatible with older implementations of WPA2. Time will tell whether and how the standard will be updated.
For those unfamiliar with Wi-Fi, the Wi-Fi Alliance is an organization which certifies that Wi-Fi devices conform to certain standards of interoperability. Among other things, this assures that Wi-Fi products from different vendors work well together.
Provide a vulnerability detection tool for use by any Wi-Fi Alliance member (this tool is based on my own detection tool that determines if a device is vulnerable to some of the discovered key reinstallation attacks).
Broadly communicate details on this vulnerability, including remedies, to device vendors. Additionally, vendors are encouraged to work with their solution providers to rapidly integrate any necessary patches.
Communicate the importance for users to ensure they have installed the latest recommended security updates from device manufacturers.
Why did you use match.com as an example in the demonstration video?
Users share a lot of personal information on websites such as match.com. So this example highlights all the sensitive information an attacker can obtain, and hopefully with this example people also better realize the potential (personal) impact. We also hope this example makes people aware of all the information these dating websites may be collecting.
We need more rigorous inspections of protocol implementations. This requires help and additional research from the academic community! Together with other researchers, we hope to organize workshop(s) to improve and verify the correctness of security protocol implementations.
First, I'm aware that KRACK attacks is a pleonasm, since KRACK stands for key reinstallation attack and hence already contains the word attack. But the domain name rhymes, so that's why it's used.
I haven't applied for any bug bounties yet, nor have I received one already.
This is the first attack against the WPA2 protocol that doesn't rely on password guessing. Indeed, other attacks against WPA2-enabled network are against surrounding technologies such as Wi-Fi Protected Setup (WPS), or are attacks against older standards such as WPA-TKIP. Put differently, none of the existing attacks were against the 4-way handshake or against cipher suites defined in the WPA2 protocol. In contrast, our key reinstallation attack against the 4-way handshake (and against other handshakes) highlights vulnerabilities in the WPA2 protocol itself.
We expect that certain implementations of other protocols may be vulnerable to similar attacks. So it's a good idea to audit security protocol implementations with this attack in mind. However, we consider it unlikely that other protocol standards are affected by similar attacks (or at least so we hope). Nevertheless, it's still a good idea to audit other protocols!
Yes there is. And a big thank you goes to the person that made the logo!
We sent out notifications to vendors whose products we tested ourselves around 14 July 2017. After communicating with these vendors, we realized how widespread the weaknesses we discovered are (only then did I truly convince myself it was indeed a protocol weaknesses and not a set of implementation bugs). At that point, we decided to let CERT/CC help with the disclosure of the vulnerabilities. In turn, CERT/CC sent out a broad notification to vendors on 28 August 2017.
OpenBSD was notified of the vulnerability on 15 July 2017, before CERT/CC was involved in the coordination. Quite quickly, Theo de Raadt replied and critiqued the tentative disclosure deadline: “In the open source world, if a person writes a diff and has to sit on it for a month, that is very discouraging”. Note that I wrote and included a suggested diff for OpenBSD already, and that at the time the tentative disclosure deadline was around the end of August. As a compromise, I allowed them to silently patch the vulnerability. In hindsight this was a bad decision, since others might rediscover the vulnerability by inspecting their silent patch. To avoid this problem in the future, OpenBSD will now receive vulnerability notifications closer to the end of an embargo.
“I think we're just getting started.” — Master Chief, Halo 1
16.10.2017 securityaffairs Attack
Swedish transport authorities were hit by cyber attacks on Wednesday and Thursday, October 11 and 12. The attacks have brought down several IT systems causing delays of the train transportation. 
SVT’s reporter is witnessing major delays and bad information at Stockholm Central, where many trains are delayed. PHOTO: SOFIA LINDAHL / SVT
16.10.2017 securityaffairs ICS
This week Siemens has released a firmware update for its BACnet Field Panel building automation products that solved two vulnerabilities, one of which is classified as high severity. 
CVSS Base Score 7.5
CVSS Vector CVSS:3.0″
“Vulnerability 2 (CVE-2017-9947) – A directory traversal vulnerability could allow a remote attacker with network access to the integrated web server (80/tcp and 443/tcp) to obtain information on the structure of the file system of the affected devices.
CVSS Base Score 5.3
CVSS Vector CVSS:3.0″
16.10.2017 securityaffairs Hacking
Operation “Emmental” is the nickname for a grand-scale phishing campaign targeting bank clients. The goal of the campaign is to receive fraudulent payments by taking actions (e.g. money transfers) on behalf of the legitimate end user.
By phishing the victims with a mobile application which mimics the bank’s genuine application, the hackers steal the two-factor-authentication tokens used during the login (both user/passwords and SMS verification code) and then issuing money transfers by SMS Services offered by the bank, together with sending these sensitive credentials to the hackers infrastructure.
The ICEMAN group, which first came to knowing after contacting me to claim responsibility for the Banrisul Bank attack in Brazil, now claim they have committed many of the reported “Emmental” attacks as well. The hacker’s intentions and motives are shown at first in this exclusive interview.
We need more bank accounts to sell. The beauty of what we do with “Emmental”, like you call it is that we can now aim at high-end customers. That’s much bigger than the people we usually scam. Also, this whole attack was a huge challenge, we wanted to see if we could overcome something tough (security wise) and on the way make some real money. I’m the one who wrote the core of the app, perhaps.
Was it all your idea?
Not really, some other guys on the web shared their tricks with us. They only did it for a dozen clients or so. We took it to the next step and did it on a grand scale targeting banks worldwide.
U mean different banks? Several. We mass email and mass SMS which basically sending our stuff to everyone. If it lands on a client of a bank we know and target – we’re taking him in. U have no idea how many targets we manage to obtain control on.
Where do you get information about potential targets?
Easily, we have fake identities which are established as legitimate companies, which through them we buy data from marketing companies. Using these “companies” we can do all sort of other things.
Such as?
For example, let’s just say that companies signing mechanisms are not a wall for us as they are for other hackers.
I see, but once you get to their phone, do you need to operate each target?
Nah, only when the verification comes in. After testing on individuals, we worked hard on automation and now we’ve got the whole thing automated on multiple servers on different cloud services. Once we were done with our infrastructure we didn’t need to do anything anymore but cashing it in and keeping the whole thing maintained.
Depends on what u call an “attack”, we successfully stole from hundreds of individuals worldwide. We’re not the only ones doing it. We got some mates doing other attacks that were already reported, but I’m not really gonna say anything about them. All I say is… just wait you will see.
How could you fake an app without the bank’s attention?
They do notice it, they let the security companies know, and then the security mobile apps blocks and removes us. At the same time, they try using law enforcement take down our C2 infrastructure and block communications to it. But that’s the game, it’s a cat and mouse game in which we currently win.
For the special operations, we use unique methods we developed in-house, but for most activity we use a chain of hacked servers and rented cloud services.
How do you pay for cloud services?
More and more companies accept BTC, in the past, it was harder.
For some ops we use our “companies” we established.
What about the language barrier? You seemed to impersonate banks worldwide.
Yeah, that was the only problem, we don’t really speak most of the languages there, so we had to improvise
What artifacts from the attack can you reveal me?
I’ll send u some screen-shots later on if my guys will approve it
Do your teammates have different roles? Or is everyone doing everything?
I’m responsible for the phishing and the app (expert at Java). We have another member who’s a killer at the server side aspect, and another guy supplies us with infrastructure. Our top guy is a cellular genius. He knows everything related to SMS protocols, 2G or 3G communications and such, he worked on a communication company in his past, so he helps us break through the phones and get what we want. Other guys are mostly working on “speared marketing”, general programming, UI and such. We’re like a small international startup company.
Are you all sitting together?
Nobody sits together these days. We’ve got a nice group chat with our own XMPP servers. To tell u the truth, I don’t even know where half the other guys are from. But as long as we can PGP or discuss through forums or pidgin, we’re good.
Like I said, most mails we send are automated but using advanced marketing solutions like the legitimate marketing companies use. Very few are truly tailored made. For example, we might check on a target using data we acquired as mentioned earlier and see what he’s into – business or sports or whatever – and then we’ll send him something that looks officially and related to that matter. He’s going to press it since he likes it, and then we unleash our RAT on him.
We don’t talk about Banrisul anymore
I saw numerous reports about our actions, generally the main players we should be afraid of are the Russians or the Feds, but clearly, nobody has a f**king clue on how to take us down… My intention is to go on with this until it dies out or until it will be too hard \ time consuming to maintain. It’s not like that’s our only operation…
Besides the questions above, many other questions asked were not given answers, or simply ignored. We will update on any news from our contact at the ICEMAN group.
About the Author: Marc Miller
Marc Miller is a web journalist, focused on cybercrime.
He started a blog called: THE PURPLE HAT – Cyber Gangs NAKED, dedicated to exposing the methods and works of cybercrime gangs such as “CARBANAK” or similar sophisticated syndicated Cybercrime organizations.
16.10.2017 securityaffairs BigBrothers
On June 23, around 9,000 email accounts, including those belonging to Theresa May and other Cabinet Ministers, were hacked in the 12-hour “sustained and determined” attack cyber attack.
“It was the not most sophisticated attack, but nor did it need to be.” a second source added. “It is possible they were simply testing their capability.”
The revelations come as Donald Trump has threatened to terminate the 2015 Iran nuclear deal if Congress and US allies fail to amend the agreement in significant ways.
16.10.2017 securitweek Hacking
Pizza Hut U.S. informed customers over the weekend that their payment card and contact information may have been compromised after cybercriminals breached its website.
15.10.2017 securityweek Vulnerebility
Siemens has released a firmware update for its BACnet Field Panel building automation products to address two vulnerabilities, including one classified as high severity.
15.10.2017 securityweek Spam
A data sample provided last month by scammers trying to make a profit by claiming to have breached U.S. credit reporting agency Equifax may have been obtained from unprotected Amazon Web Services (AWS) instances owned by a different company. 
15.10.2017 securityweek Incindent
Chicago-based hotel operator Hyatt Hotels Corporation informed customers this week that their credit card information may have been stolen by cybercriminals. This is the second data breach discovered by the company within a period of two years.
15.10.2017 securityweek Virus
Two of the “Big Three” U.S. credit reporting agencies, Equifax and TransUnion, were hit by a cybersecurity incident caused by the use of a third-party web analytics script. 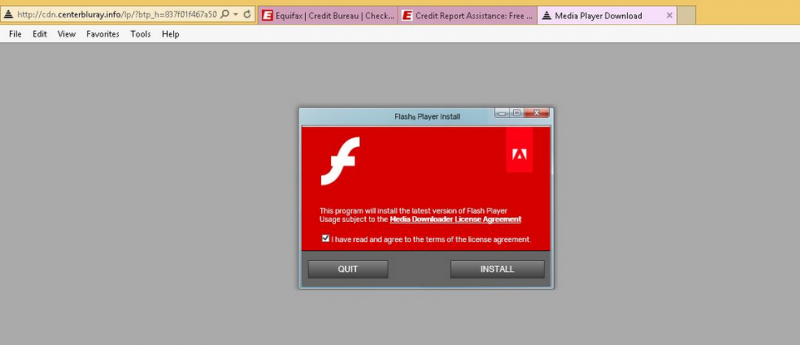
15.10.2017 securityweek Security
An increasing number of organizations have started using Microsoft’s Office 365 platform, but many haven’t migrated due to security concerns, according to a report published on Thursday by Barracuda Networks. 
15.10.2017 securityweek Android
The recently discovered Red Alert 2 Android Trojan is using an infrastructure that serves fake Adobe Flash Android apps to unsuspecting users, RiskIQ has discovered.
15.10.2017 securityweek Vulnerebility
A vulnerability that that was recently addressed by Microsoft as part of the October 2017 Patch Tuesday could result in Outlook sending emails in cleartext when S/MIME encryption was supposed to be used.
15.10.2017 securityweek Incindent
A security researcher noticed recently that an Equifax service designed for obtaining free and discounted credit reports had been redirecting users to websites set up to serve adware and scams. 
15.10.2017 securityweek BotNet
Botnets are widespread worldwide, serving whichever purpose they were designed to, and the United States is one of the largest sources of botnet attacks. Across the country, Chicago and Washington D.C. are home to the largest number of bots (infected hosts), Symantec has discovered.
15.10.2017 securityweek Attack
A recently discovered DNSMessenger campaign is abusing compromised U.S. state government servers to host malware, Cisco Talos security researchers say.
15.10.2017 securityweek Mobil
Web security company High-Tech Bridge announced on Thursday the launch of a free online service that allows mobile application developers to test their iOS and Android apps. 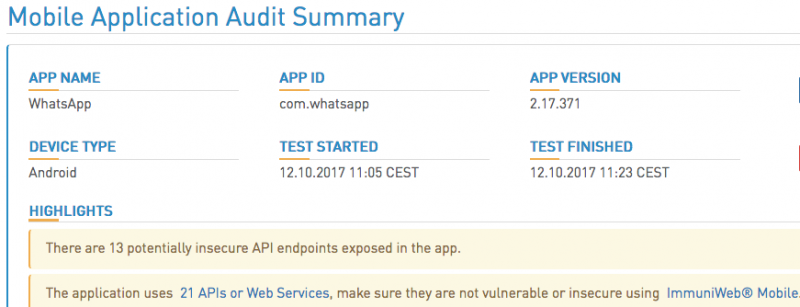
15.10.2017 securityweek Vulnerebility
Unpatched SQL injection vulnerabilities found by Rapid7 researchers in the SmartVista e-payments suite from Switzerland-based BPC Banking Technologies can expose sensitive information.
15.10.2017 securityweek CyberWar
Sensitive data about Australia's F-35 stealth fighter and P-8 surveillance aircraft programmes were stolen when a defence subcontractor was hacked using a tool widely used by Chinese cyber criminals, officials said Thursday.
15.10.2017 securityweek BigBrothers
The security software firm Kaspersky has become the focal point in an escalating conflict in cyberspace between the United States and Russia.
15.10.2017 securityweek Security
Akamai Technologies announced on Wednesday that it has agreed to acquire Nominum, a privately-held provider of DNS security solutions for carriers and enterprises.
15.10.2017 securityweek BigBrothers
Israeli spies observed Russian government hackers in real time as they scoured computers around the world for the codenames of US intelligence programs, The New York Times reported Tuesday night.
15.10.2017 securityweek Vulnerebility
Researchers at Cisco’s Talos security intelligence and research group have discovered two high severity remote code execution vulnerabilities in Simple DirectMedia Layer (SDL), a popular cross-platform development library.
15.10.2017 securityweek Ransomware
The ransomware marketplace has grown by a phenomenal 2,502% from 2016 to 2017. This is the amount of money spent by criminals on ransomware software. It is a market fueled by the technical simplicity of the malware, the rise of Ransomware-as-a-Service, the guaranteed return on investment for criminals, the availability of Tor and crypto currencies to hide tracks; and a lack of fundamental security controls among victims.
15.10.2017 securityweek Incindent
ShiftLeft emerged from stealth mode on Wednesday with a new solution designed to protect cloud applications and microservices, and with more than $9 million in funding.
15.10.2017 securityweek BigBrothers
Hackers likely affiliated with the North Korean government seem to lack the ability to disrupt the U.S. power supply, according to a new report from FireEye.
15.10.2017 securityweek BigBrothers
President Trump issued a memorandum on Oct. 5 requiring the intelligence community to establish an inter-agency information sharing network. Agency heads are required to submit a plan within 270 days. Missing from the memorandum is any mention of existing projects such as the Cyber Threat Intelligence Center (CTIC) or the Intelligence Community IT Enterprise (IC ITE, pronounced 'eyesight').
15.10.2017 securityweek Cyber
The Olympic Games offer a tempting target for hackers and other malicious actors, with potentially devastating consequences for one of the world's premier sporting events, researchers said Tuesday.
15.10.2017 securityweek Incindent
Consulting and technology services giant Accenture inadvertently exposed potentially sensitive information by leaving it unprotected in four Amazon Web Services (AWS) S3 buckets.
15.10.2017 securityweek Vulnerebility
One of the 62 vulnerabilities patched by Microsoft with the October security updates is a critical Windows flaw that allows remote attackers to execute arbitrary code on a targeted machine via specially crafted DNS responses.
15.10.2017 securityweek Incindent
Nearly 700,000 British consumers may have had personal data compromised in the massive breach at Equifax, the US credit reporting agency said Tuesday.
15.10.2017 securityweek BigBrothers
Hackers could have easily infiltrated US voting machines in 2016 and are likely to try again in light of vulnerabilities in electronic polling systems, a group of researchers said Tuesday.
15.10.2017 securityweek Vulnerebility
Microsoft’s Patch Tuesday updates for October 2017 address a total of 62 vulnerabilities, including a critical Office zero-day flaw that has been exploited in targeted attacks.
15.10.2017 securityweek Vulnerebility
Adobe released an update for Flash Player on Tuesday, but it does not include any security fixes. If no patches are released by the end of the month, it will be the first time since July 2012.
15.10.2017 securityweek Crime
Sophisticated and Stealthy Bank Attack Combines Cyber and Organized Crime
15.10.2017 securityweek Virus
A newly detailed malware targeting automated teller machines (ATM) allows attackers to completely drain available cash, Kaspersky Lab researchers have discovered.
15.10.2017 securityweek BigBrothers
Inside GCHQ 3 (Image Copyright GCHQ)
Much of that funding, he says, will go into making GCHQ a cyber organization as much as an intelligence organization. The difference is moot, since GCHQ has been using its cyber expertise for many years. Part of the Edward Snowden revelations disclosed a GCHQ project known as Tempora, which allegedly covertly gathered vast troves of personal internet communications which were then shared with the U.S. National Security Agency (NSA). GCHQ was also accused of targeting a Belgian telecommunications company, Belgacom, where staff computers were infected with malware in a 'quantum insert' attack to secure access to customers.
15.10.2017 securityweek Safety
Cyber resilience company UpGuard announced on Tuesday the launch of a new product designed to help organizations automate risk assessment for third-party vendors.
15.10.2017 securityweek BigBrothers
North Korea Hackers
15.10.2017 securityweek BigBrothers
A cyberespionage group previously linked to Iran has been using a new Trojan in attacks aimed at entities in the Middle East, Palo Alto Networks reported on Monday.
15.10.2017 securityweek Hacking
The financially-motivated FIN7 hacking group recently switched to a new delivery technique and has been employing a different malware obfuscation method, ICEBRG security researchers reveal.
15.10.2017 securityweek Vulnerebility
Not all Windows releases receive the same treatment when it comes to security patches, leaving some users exposed to known vulnerabilities, security researchers from Google's Project Zero team warn.
15.10.2017 securityweek Analysis
Websites Hit by 63 Attacks Per Day, Says SiteLock
15.10.2017 Securityaffairs Security
Researchers with Counter Threat Unit at SecureWorks are monitoring the Bronze Butler cyberespionage group (aka Tick). The hacker group has been targeting Japanese heavy industry, manufacturing and international relations at least since 2012, 
14.10.2017 thehackernews CyberWar
Remember NotPetya?
The Ransomware that shut down thousands of businesses, organisations and banks in Ukraine as well as different parts of Europe in June this year.
Now, Ukrainian government authorities are once again warning its citizens to brace themselves for next wave of "large-scale" NotPetya-like cyber attack.
According to a press release published Thursday by the Secret Service of Ukraine (SBU), the next major cyber attack could take place between October 13 and 17 when Ukraine celebrates Defender of Ukraine Day (in Ukrainian: День захисника України, Den' zakhysnyka Ukrayiny).
Authorities warn the cyber attack can once again be conducted through a malicious software update against state government institutions and private companies.
The attackers of the NotPetya ransomware also used the same tactic—compromising the update mechanism for Ukrainian financial software provider called MeDoc and swapping in a dodgy update including the NotPetya computer virus.
The virus then knocked computers in Ukrainian government agencies and businesses offline before spreading rapidly via corporate networks of multinational companies with operations or suppliers in eastern Europe.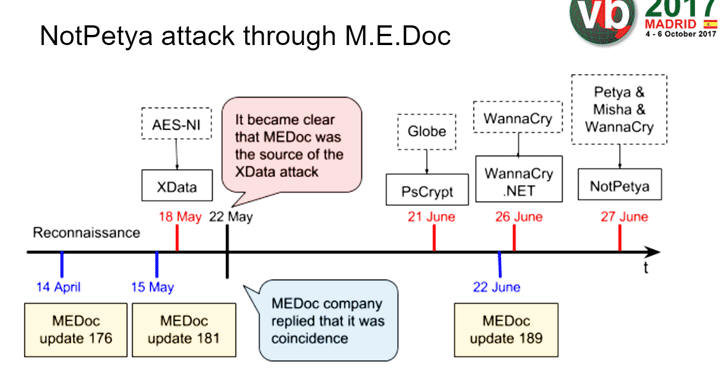
The country blamed Russia for the NotPetya attacks, while Russia denied any involvement.
Not just ransomware and wiper malware, Ukraine has previously been a victim of power grid attacks that knocked its residents out of electricity for hours on two different occasions.
The latest warning by the Ukrainian secret service told government and businesses to make sure their computers and networks were protected against any intrusion.
"SBU notifies about preparing for a new wave of large-scale attack against the state institutions and private companies. The basic aim—to violate normal operation of information systems, that may destabilize the situation in the country," the press release reads.
"The SBU experts received data that the attack can be conducted with the use of software updating, including public applied software. The mechanism of its realization will be similar to cyber-attack of June 2017."
To protect themselves against the next large-scale cyber attack, the SBU advised businesses to follow some recommendations, which includes:
Updating signatures of virus protection software on the server and in the workstation computers.
Conducting redundancy of information, which is processed on the computer equipment.
Providing daily updating of system software, including Windows operating system of all versions.
Since the supply chain attacks are not easy to detect and prevent, users are strongly advised to keep regular backups of their important files on a separate drive or storage that are only temporarily connected for worst case scenarios.
Most importantly, always keep a good antivirus on your system that can detect and block any malware intrusion before it can infect your device, and keep it up-to-date for latest infection-detection.
14.10.2017 thehackernews Social
Researchers have detected a new Facebook phishing scam that can even trick an experienced technical user into falling victim to the scam, helping an attacker gain access to your Facebook account.
This latest social media scam is abusing "Trusted Contact"—a Facebook account recovery feature that sends secret access codes to a few of your close friends in order to help you regain access to your Facebook account in case you forget your password or lost access to your account.
According to a public security alert published by AccessNow, the attack initiates by an already compromised account of one of your friends, asking for urgent help to get back into his/her Facebook account.
The attacker explains that you are listed as one of his/her Trusted Contacts on Facebook and asks you to check your email for a recovery code and share with the attacker (who's hiding behind the identity of your friend).
However, in actual, the code you received is not the key to unlock your friend's account, but instead, the attacker initiated "Forgot my password" request for your account in an attempt to hijack your Facebook account.
Knowing that a friend is in trouble, apparently one would share the code without giving a second thought.
"The new attack targets people using Facebook, and it relies on your lack of knowledge about the platform's Trusted Contacts feature," Access Now warns.
You should know Facebook's Trusted Contacts feature doesn't work the way this phishing attack suggests. To understand how this feature works, you can head on to this Facebook post.
The Access Now says, "So far we're seeing the majority of reports [falling victims to this new Facebook phishing scam] from human right defenders and activists from the Middle East and North Africa."
Although this latest Facebook scam is initiated using a compromised Facebook account of one of your friends, any of your Facebook friend can also intentionally trick you into handing over your Facebook account to them (looking at the way how people accept friend requests sent by anyone on the social media platform).
Stay Safe!
14.10.2017 thehackernews Ransomware
DoubleLocker—as the name suggests, it locks device twice.
Security researchers from Slovakia-based security software maker ESET have discovered a new Android ransomware that not just encrypts users’ data, but also locks them out of their devices by changing lock screen PIN.
On top of that:
DoubleLocker is the first-ever ransomware to misuse Android accessibility—a feature that provides users alternative ways to interact with their smartphone devices, and mainly misused by Android banking Trojans to steal banking credentials.
"Given its banking malware roots, DoubleLocker may well be turned into what could be called ransom-bankers," said Lukáš Štefanko, the malware researcher at ESET.
"Two-stage malware that first tries to wipe your bank or PayPal account and subsequently locks your device and data to request a ransom."
Researchers believe DoubleLocker ransomware could be upgraded in future to steal banking credentials as well, other than just extorting money as ransom.
First spotted in May this year, DoubleLocker Android ransomware is spreading as a fake Adobe Flash update via compromised websites.
Here's How the DoubleLocker Ransomware Works:
After obtaining this accessibility permission, the malware abuses it to gain device's administrator rights and sets itself as a default home application (the launcher)—all without the user's knowledge.
"Setting itself as a default home app – a launcher – is a trick that improves the malware's persistence," explains Štefanko.
"Whenever the user clicks on the home button, the ransomware gets activated, and the device gets locked again. Thanks to using the accessibility service, the user does not know that they launch malware by hitting Home."
Once executed, DoubleLocker first changes the device PIN to a random value that neither attacker knows nor stored anywhere and meanwhile the malware encrypts all the files using AES encryption algorithm.
DoubleLocker ransomware demands 0.0130 BTC (approximately USD 74.38 at time of writing) and threatens victims to pay the ransom within 24 hours.
If the ransom is paid, the attacker provides the decryption key to unlock the files and remotely resets the PIN to unlock the victim's device.
How to Protect Yourself From DoubleLocker Ransomware
According to the researchers, so far there is no way to unlock encrypted files, though, for non-rooted devices, users can factory-reset their phone to unlock the phone and get rid of the DoubleLocker ransomware.
However, for rooted Android devices with debugging mode enabled, victims can use Android Debug Bridge (ADB) tool to reset PIN without formatting their phones.
The best way to protect yourself from avoiding falling victims to such ransomware attacks is to always download apps from trusted sources, like Google play Store, and stick to verified developers.
Also, never click on links provided in SMS or emails. Even if the email looks legit, go directly to the website of origin and verify any possible updates.
Moreover, most importantly, keep a good antivirus app on your smartphone that can detect and block such malware before it can infect your device, and always keep it and other apps up-to-date.
14.10.2017 thehackernews Vulnerebility
As part of its "October Patch Tuesday," Microsoft has today released a large batch of security updates to patch a total of 62 vulnerabilities in its products, including a severe MS office zero-day flaw that has been exploited in the wild.
Security updates also include patches for Microsoft Windows operating systems, Internet Explorer, Microsoft Edge, Skype, Microsoft Lync and Microsoft SharePoint Server.
Besides the MS Office vulnerability, the company has also addressed two other publicly disclosed (but not yet targeted in the wild) vulnerabilities that affect the SharePoint Server and the Windows Subsystem for Linux.
October patch Tuesday also fixes a critical Windows DNS vulnerability that could be exploited by a malicious DNS server to execute arbitrary code on the targeted system. Below you can find a brief technical explanation of all above mentioned critical and important vulnerabilities.
Microsoft Office Memory Corruption Vulnerability (CVE-2017-11826)
This vulnerability, classified by Microsoft as "important," is caused by a memory corruption issue. It affects all supported versions of MS Office and has been actively exploited by the attackers in targeted attacks.
An attacker could exploit this vulnerability either by sending a specially crafted Microsoft Office file to the victims and convincing them to open it, or hosting a site containing specially crafted files and tricking victims to visit it.
Once opened, the malicious code within the booby-trapped Office file will execute with the same rights as the logged-in user. So, users with least privilege on their systems are less impacted than those having higher admin rights.
The vulnerability was reported to Microsoft by security researchers at China-based security firm Qihoo 360 Core Security, who initially detected an in-the-wild cyber attack which involved malicious RTF files and leveraged this vulnerability on September 28.
Microsoft Windows DNSAPI Remote Code Execution Vulnerability (CVE-2017-11779)
Among other critical vulnerabilities patched by Microsoft include a critical remote code execution flaw in the Windows DNS client that affects computers running Windows 8.1 and Windows 10, and Windows Server 2012 through 2016.
The vulnerability can be triggered by a malicious DNS response, allowing an attacker gain arbitrary code execution on Windows clients or Windows Server installations in the context of the software application that made the DNS request.
Nick Freeman, a security researcher from security firm Bishop Fox, discovered the vulnerability and demonstrated how an attacker connected to a public Wi-Fi network could run malicious code on a victim's machine, escalate privileges and take full control over the target computer or server.
"This means that if an attacker controls your DNS server (e.g., through a Man-in-the-Middle attack or a malicious coffee-shop hotspot) – they can gain access to your system," the researcher explains.
"This doesn’t only affect web browsers – your computer makes DNS queries in the background all the time, and any query can be responded to in order to trigger this issue."
Windows Subsystem for Linux Denial of Service Vulnerability (CVE-2017-8703)
This denial of service (DoS) issue is yet another noteworthy vulnerability which resides in Windows Subsystem for Linux.
The vulnerability, classified by Microsoft as "important," was previously publicly disclosed, but wasn't found actively exploited in the wild.
The vulnerability could allow an attacker to execute a malicious application to affect an object in the memory, which eventually allows that the application to crash the target system and made it unresponsive.
The only affected Microsoft product by this vulnerability is Windows 10 (Version 1703). "The update addresses the vulnerability by correcting how Windows Subsystem for Linux handles objects in memory," Microsoft said in its advisory.
Microsoft Office SharePoint XSS Vulnerability (CVE-2017-11777)
Another previously disclosed but not yet under attack vulnerability is a cross-site scripting (XSS) flaw in Microsoft SharePoint Server that affects SharePoint Enterprise Server 2013 Service Pack 1 and SharePoint Enterprise Server 2016.
The vulnerability, also classified by Microsoft as "important," can be exploited by sending a maliciously crafted request to an affected SharePoint server.
Successful exploitation of this vulnerability could allow an attacker to perform cross-site scripting attacks on affected systems and execute malicious script in the same security context of the current user.
"The attacks could allow the attacker to read content that the attacker is not authorised to read, use the victim's identity to take actions on the SharePoint site on behalf of the user, such as change permissions and delete content, and inject malicious content in the browser of the user," Microsoft explains.
Besides these, the company has patched a total of 19 vulnerabilities in the scripting engine in Edge and Internet Explorer that could allow web pages to achieve remote-code execution, with the logged-in user's permissions, via memory corruption flaws.
Just opening a web page could potentially land you in trouble by executing malware, spyware, ransomware, and other nasty software on the vulnerable computer.
More RCE And Other Vulnerabilities
Redmond also patched two vulnerabilities in the Windows font library that can allow a web page or document to execute malicious code on a vulnerable machine and hijack it on opening a file with a specially crafted embedded font or visiting a website hosting the malicious file.
The update also includes fixes for a bug in Windows TRIE (CVE-2017-11769) that allows DLL files to achieve remote code execution, a programming error (CVE-2017-11776) in Outlook that leaves its emails open to snooping over supposedly secure connections.
Other issues patched this month include two remote code execution flaws in the Windows Shell and a remote code execution bug in Windows Search.
Microsoft also published an advisory warning user of a security feature bypass issue affecting the firmware of Infineon Trusted Platform Modules (TPMs).
Surprisingly, Adobe Flash does not include any security patches. Meanwhile, Adobe has skipped October's Patch Tuesday altogether.
Users are strongly advised to apply October security patches as soon as possible in order to keep hackers and cybercriminals away from taking control over their computers.
For installing security updates, simply head on to Settings → Update & security → Windows Update → Check for updates, or you can install the updates manually.
14.10.2017 thehackernews CyberCrime
A Taiwanese bank has become the latest to fall victim to hackers siphoning off millions of dollars by targeting the backbone of the world financial system, SWIFT.
SWIFT, or Society for Worldwide Interbank Telecommunication, is a global financial messaging system that thousands of banks and commercial organizations across the world use to transfer billions of dollars every day.
Hackers reportedly last week managed to steal almost $60 Million from Far Eastern International Bank in Taiwan by planting malware on the bank's servers and through the SWIFT interbank banking system.
According to Taiwanese state-owned news agency Central News Agency, most of the stolen money has now been recovered, with only $500,000 remaining, and authorities have made two arrests in connection with the bank cyber-heist.
Far Eastern on Friday admitted that some unknown hackers managed to install malware on computers and servers within its organization, and most crucially, onto a SWIFT terminal employed by the bank.
Once there, the hackers then obtained credentials needed for payment transfers and then transferred almost $60 million to fraudulent accounts based in the United States, Cambodia and Sri Lanka.
In the wake of the cyber heist, Taiwan Premier William Lai ordered government agencies to review their information security defences and develop appropriate measures to deal with future cyber incidents.
The Criminal Investigation Bureau (CIB) of Taiwan said that it has launched an investigation into the cyber heist and asked the bank to submit details about its computer operations. The bureau has also informed the Interpol of the case and asked for assistance.
Most of the stolen funds have been recovered, and two arrests connected to the cyber theft have already been made in Sri Lanka by the police, and one of them is Litro Gas company chairman Shalila Moonesinghe, according to the Colombo Gazette.
Moonesinghe was arrested by the CIB after the authorities allegedly found $1.1 million of the stolen Taiwanese funds in his personal bank account.
However, the federal authorities are still looking for the third suspect.
"We are looking at some US$1.3 million that had come into three accounts in Sri Lanka," an unnamed Sri Lankan officer involved in the investigation was quoted as saying in an AFP report. "We have taken two people into custody, and we are looking for one more person."
It wasn't the first case in which malware was implanted into a bank's SWIFT network to steal millions of dollars. Last year, some unknown hackers targeted banks worldwide by gaining access to SWIFT that is being used to transfer billions of dollars every day.
Earlier last year, hackers managed to steal $81 Million from the Bangladesh central bank's account in the New York Federal Reserve in a similar way—by hacking into SWIFT network using a piece of malware and obtaining credentials needed for payment transfers.
In May same year, another incident was reported in which hackers targeted an unnamed commercial bank and malware installed on SWIFT was used against the banks' PDF reader.
In May 2016, another case involving SWIFT emerged wherein cybercriminals managed to steal around $12 million from an Ecuadorian bank called Banco del Austro (BDA) by attacking the Swift global network.
Also in June 2016, Hackers stole $10 million from an unnamed bank in Ukraine by exploiting the SWIFT international banking system.
14.10.2017 thehackernews BigBrothers
The cold cyber war has just turned hot.
According to a story published today by the New York Times, Israeli government hackers hacked into Kaspersky’s network in 2015 and caught Russian government hackers red-handed hacking US government hackers with the help of Kaspersky.
In other words — Russia spying on America, Israel spying on Russia and America spying on everyone.
What the F^#% is going around?
It is like one is blaming another for doing exactly the same thing it is doing against someone else. Wow!
Well, the fact that everyone is spying on everyone is neither new nor any secret. However, somehow now Kaspersky Labs is at the centre of this international espionage tale for its alleged devil role.
Just last week, the Wall Street Journal, an American media agency, published a story against the Kaspersky, a Russian antivirus provider, claiming that the Russian government hackers stole highly classified NSA documents and hacking tools in 2015 from a staffer's home PC with the help of Kaspersky Antivirus.
Even if the incident is real, quoting multiple anonymous sources from US intelligence community, Wall Street Journal article failed to provide any substantial evidence to prove if Kaspersky was intentionally involved with the Russian spies or some hackers simply exploited any zero-day vulnerability in the Antivirus product.
Now, the latest NYT story, again quoting an anonymous source from Israeli Intelligence Agency, seems another attempt to justify the claims made by WSJ article about Russians hacking NSA secrets.
"The role of Israeli intelligence in uncovering [the Kaspersky Labs] breach and the Russian hackers’ use of Kaspersky software in the broader search for American secrets have not previously been disclosed," the NYT reported.
According to the report, United States officials began an immediate investigation in 2015 after Israel officials notified the U.S. National Security Agency (NSA) about the possible breach.
Indeed, in mid-2015, Moscow-based Kaspersky Lab detected sophisticated cyber-espionage backdoor within its corporate network and released a detailed report about the intrusion, although the company did not blame Israel for the attack.
At the time, Kaspersky said that some of the attack code the company detected shared digital fingerprints first found in the infamous Stuxnet worm, same malware which was developed by America and Israel to sabotage Iran's nuclear program in 2010.
This suspicion of malicious Kaspersky’s behaviour eventually leads the U.S. Department of Homeland Security (DHS) to ban and remove Kaspersky antivirus software from all of its government computers.
Moreover, just last month, the U.S. National Intelligence Council shared a classified report with NATO allies concluding that the Russian FSB intelligence agency had access to Kaspersky's databases and as well as the source code.
However, Kaspersky Lab has always denied any knowledge of, or involvement in, any cyber espionage operations.
"Kaspersky Lab has never helped, nor will help, any government in the world with its cyberespionage efforts," Kaspersky's founder Eugene Kaspersky said in a statement.
Eugene today also announced that he has just launched an internal investigation to cross-check if United States LEA has relevant facts.
Eugene previously admitted there's a possibility that NSA hacking tools could have been picked up as malware by their Anti-malware scanner because antivirus products are designed to work in that way.
"We absolutely and aggressively detect and clean malware infections no matter the source," the antivirus company said.
Until now it is quite tough to judge if Kaspersky was involved in any wrongdoing, but the ball is in America's court, who has to provide the actual evidence to the world about the highly classified Israeli counter-intelligence operation.
14.10.2017 thehackernews Vulnerebility
Beware, If you are using S/MIME protocol over Microsoft Outlook to encrypt your email communication, you need to watch out.
From at least last 6 months, your messages were being sent in both encrypted and unencrypted forms, exposing all your secret and sensitive communications to potential eavesdroppers.
S/MIME, or Secure/Multipurpose Internet Mail Extensions, is an end-to-end encryption protocol—based on public-key cryptography and works just like SSL connections—that enables users to send digitally signed and encrypted messages.
According to a security advisory published by SEC Consult earlier this week, a severe bug (CVE-2017-11776) in Microsoft Outlook email client causes S/MIME encrypted emails to be sent with their unencrypted versions attached.
When Outlook users make use of S/MIME to encrypt their messages and format their emails as plain text, the vulnerability allows the seemingly encrypted emails to be sent in both encrypted as well as human-readable clear text forms, the researchers explain.
Users would be unaware of this security issue, as the messages would appear as encrypted in the Outlook application's "Sent Items" folder.
"To trigger the vulnerability, no active involvement by an attacker is required. An attacker might remain completely passive," the advisory reads.
"The impact is that a supposedly S/MIME encrypted mail can be read without the private keys of the recipient. This results in total loss of security properties provided by S/MIME encryption."
Therefore, attackers with access to the unencrypted server-to-server or client-to-server connections could easily take advantage of this vulnerability to read the email communications in the plain text.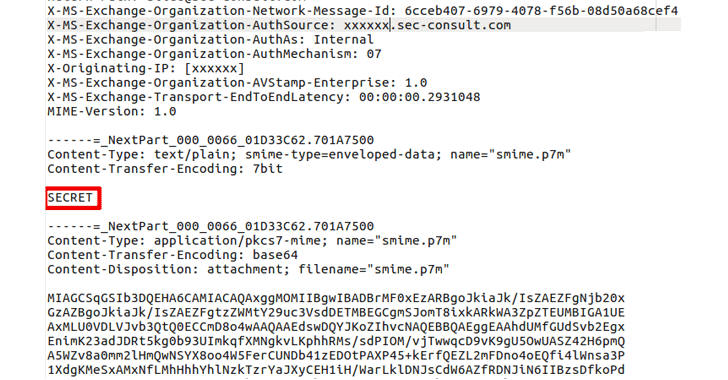
So if you used Outlook's S/MIME encryption for emails in the past 6 months, your emails have not been encrypted at all; instead, they went out in plain text.
According to the researchers, the scope of the vulnerability depends on how you have Outlook configured.
1. Outlook with Exchange (Impact limited to the first hop)
If you are using Outlook with Exchange, the plain text version of the encrypted emails will only reach one hop (to the sender's exchange), as sending emails to external exchange remove the plaintext part from the message.
But if the recipient and sender are in the same domain (exchange), the plain text part will be forwarded to the recipient as well.
2. Outlook using SMTP (Impact on the entire mail path)
If you are running Outlook with SMTP, the plain text version of the encrypted emails will not only be received by the recipient but also by all mail servers along the path.
Security researcher Kevin Beaumont independently verified the authenticity of the vulnerability, tweeting "Outlook S/MIME bug is absolutely reproducible, I just did it. Does not need an attacker. Microsoft has classified it wrong."
Patch Outlook & Other Critical Windows Vulnerabilities
SEC researchers discovered the issue in May and responsibly reported it to Microsoft, but did not hear back from the tech giant.
Microsoft released a patch to fix the bug in this month's release of security updates, and rated the issue as "important," claiming the exploitation of this vulnerability was "unlikely" in the wild.
So, if you use Outlook's S/MIME for encrypting your sensitive emails, you are advised to patch your system and software as soon as possible.
14.10.2017 thehackernews Virus
Since new forms of cybercrime are on the rise, traditional techniques seem to be shifting towards more clandestine that involve the exploitation of standard system tools and protocols, which are not always monitored.
Security researchers at Cisco's Talos threat research group have discovered one such attack campaign spreading malware-equipped Microsoft Word documents that perform code execution on the targeted device without requiring Macros enabled or memory corruption.
This Macro-less code execution in MSWord technique, described in detail on Monday by a pair of security researchers from Sensepost, Etienne Stalmans and Saif El-Sherei, which leverages a built-in feature of MS Office, called Dynamic Data Exchange (DDE), to perform code execution.
Dynamic Data Exchange (DDE) protocol is one of the several methods that Microsoft allows two running applications to share the same data. The protocol can be used by applications for one-time data transfers and for continuous exchanges in which apps send updates to one another as new data becomes available.
Thousands of applications use the DDE protocol, including Microsoft's Excel, MS Word, Quattro Pro, and Visual Basic.
The exploitation technique that the researchers described displays no "security" warnings to victims, except asking them if they want to execute the application specified in the command—however, this popup alert could also be eliminated "with proper syntax modification," the researchers say.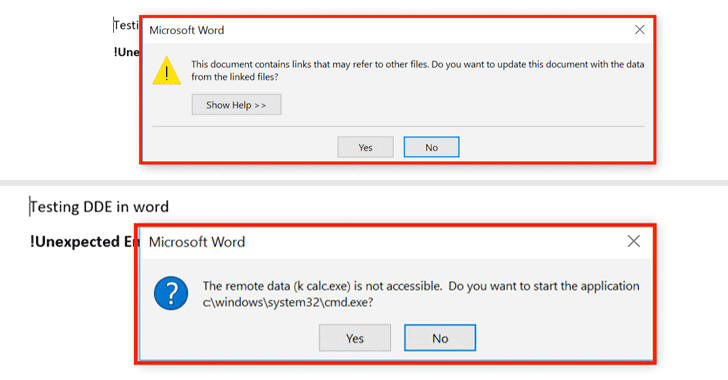
The duo has also provided a proof-of-concept video demonstrating the technique.
MS Word DDE Attack Being Actively Exploited In the Wild
As described by Cisco researchers, this technique was found actively being exploited in the wild by hackers to target several organisations using spear phishing emails, which were spoofed to make them look as if they're sent by the Securities and Exchange Commission (SEC) and convince users into opening them.
"The emails themselves contained a malicious attachment [MS Word] that when opened would initiate a sophisticated multi-stage infection process leading to infection with DNSMessenger malware," reads a blog post published by Talos researchers.
Earlier March, Talos researchers found attackers distributing DNSMessenger—a completely fileless remote access trojan (RAT) that uses DNS queries to conduct malicious PowerShell commands on compromised computers.
Once opened, victims would be prompted with a message informing them that the document contains links to external files, asking them to allow or deny the content to be retrieved and displayed.
"Interestingly, the DDEAUTO field used by this malicious document retrieved code that the attacker had initially hosted on a Louisiana state government website, which was seemingly compromised and used for this purpose," the researchers say.
How to Protect Yourself And Detect MS Word DDE Attacks
What's more worrying? Microsoft doesn't consider this as a security issue, rather according to the company the DDE protocol is a feature that can not be removed but could be improved with better warning alerts for users in future.
Although there's no direct way to disable DDE code execution, users can proactively monitor system event logs to check possible exploitation.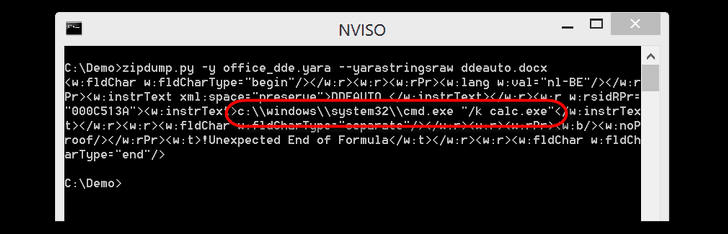
Besides this, the researchers at NVISO Labs have also shared two YARA rules to detect DDE vector in Office Open XML files.
The best way to protect yourself from such malware attacks is always to be suspicious of any uninvited document sent via an email and never click on links inside those documents unless properly verifying the source.