FormBook Campaigns Target U.S., South Korea
6.10.2017 securityweek BigBrothers
Various industries in the United States and South Korea were targeted during the third quarter of the year in several high-volume FormBook distribution campaigns, FireEye reports.
As part of these campaigns, the attackers used various delivery mechanisms, including PDF documents containing download links, DOC and XLS files with malicious macros, and archive files containing executables.
The security researchers noticed that the PDF and DOC/XLS documents were mainly used to target organizations in the U.S., while the archives were used both in the U.S. and South Korea attacks. Impacted sectors included aerospace, defense contractors, and manufacturing.
The attacks were aimed at infecting victims’ computers with the FormBook information stealer, a piece of malware being sold through various hacking forums since early 2016 and which recently registered an increase in activity.
FormBook was designed to steal a variety of information from the infected machine, including keystrokes, clipboard contents, HTTP/HTTPS/SPDY/HTTP2 forms and network requests, passwords from browsers and email clients, and screenshots, and send it to the command and control (C&C) server.
To perform its malicious routines, the malware injects itself into various processes and also installs the necessary function hooks to log keystrokes, steal clipboard contents, and extract data from HTTP sessions. Furthermore, the malware can execute commands received from the C&C to download and execute files, start processes, shutdown and reboot the system, and steal cookies and local passwords.
The threat typically uses C&C domains from newer generic top-level domains (gTLDs) such as .site, .website, .tech, .online, and .info. The domains associated with the malware’s recent activity have been registered using the WhoisGuard privacy protection service, while the server infrastructure is hosted by a Ukrainian company, FireEye discovered.
The campaigns employing PDF files to distribute the malware were using FedEx and DHL shipping/package delivery themes and a document-sharing theme. The documents, however, don’t contain malicious code, but include a link to download the payload. The malicious links recorded 716 hits across 36 countries, with the U.S. being affected the most (71% of attacks).
The email campaigns distributing FormBook via DOC and XLS files were using malicious macros for delivery. As soon as the user enabled the macro, a download URL retrieved an executable file with a PDF extension. Most of the emails targeted the United States (61% of attacks), with aerospace organizations and defense contractors being hit the most.
Emails carrying archive attachments (ZIP, RAR, ACE, and ISO) accounted for the highest distribution volume and leveraged a broad range of business related subject lines, often regarding payment or purchase orders. Most of the attacks targeted organizations in South Korea (31%) and the U.S. (22%), with the manufacturing industry being impacted the most.
The security researchers also note that FormBook was observed over the past few weeks downloading other malware families such as NanoCore.
Brad Duncan, Palo Alto Networks threat intelligence analyst and handler at the SANS Internet Storm Center, says that some of the analyzed post-infection traffic was identified as pertaining to the Punkey Point of Sale (POS) malware and not FormBook. The malware was distributed through RAR archives attached to fake FedEx delivery notices.
“While FormBook is not unique in either its functionality or distribution mechanisms, its relative ease of use, affordable pricing structure, and open availability make [it] an attractive option for cyber criminals of varying skill levels. The credentials and other data harvested by successful FormBook infections could be used for additional cyber-crime activities including, but not limited to: identity theft, continued phishing operations, bank fraud and extortion,” FireEye concludes.
Germany Drops Probe Into Mass NSA Surveillance
6.10.2017 securityweek BigBrothers
Prosecutors in Germany on Thursday closed an investigation into whether US and British intelligence services systematically carried out extensive spying on the country's citizens, citing a lack of hard evidence.
The inquiry was opened after revelations in 2013 by fugitive US intelligence leaker Edward Snowden that the National Security Agency (NSA) and its British partner were conducting sweeping Internet and phone data surveillance, including in Germany.
Chancellor Angela Merkel reacted angrily at the time to news that the NSA had tapped her mobile phone, telling Washington that spying between allies "is not on".
To Germany's embarrassment, news broke in 2015 that its own BND service had helped the NSA eavesdrop on EU targets including the French presidency and the European Commission.
Germany's federal prosecution service said Thursday that it had ended its inquiry into "the possible mass collection of telecommunication data of the German population by British and US intelligence services".
It said that although the services conducted "strategic signals intelligence" and tapped online communications, there was "no hard evidence" that they "illegally, systematically and massively" monitored German telecommunications and Internet traffic.
The prosecutors said their assessment was shared by Germany's BfV domestic security service, which handles counterespionage; the IT security agency BSI; the NSA parliamentary inquiry; and the operator of a major European internet hub in Germany.
They added that the "so-called Snowden documents" had documented the US spy service's "techniques and capabilities" but provided "no concrete evidence of actual espionage activities carried out by the NSA in or against Germany".
Russia Raises Tensions in Baltic Region With Testing of Cyber Weapons
6.10.2017 securityweek BigBrothers
"Russia has opened a new battlefront with NATO," claims the Wall Street Journal. "Russia may have tested cyber warfare on Latvia," says Reuters. These are two reports about two separate incidents in the Baltic area close to Russia's largest military war games since 2013: Zapad.
There are around 4,000 NATO troops in the region. Russia claims that around 13,000 Russian troops were involved in Zapad; but NATO puts the figure at 100,000.
The first incident revolves around hacking soldiers' smartphones. Two separate methodologies have been reported: the use of drones with sophisticated electronics equipment, and in an earlier incident, a mobile telephone tower (similar to law enforcement's use of stingray equipment). The sophistication of the attacks leaves little doubt that there is some state-sponsorship involved.
In the latest attack, only six smartphones are known to have been affected. According to the WSJ, one victim, U.S. Army Lt. Col. Christopher L'Heureux, "said at least six soldiers he commands have had phones or Facebook accounts hacked. He said he suspects the incidents were meant as a message that Russian intelligence forces were tracking him, could crack his passwords and wanted to intimidate his soldiers." It remains to be seen whether additional hacks surface in the coming days.
WSJ reports, "Military cyberespionage experts said the drone flights and cellphone data collection suggest Russia is trying to monitor troop levels at NATO's new bases to see if there are more forces present there than the alliance has publicly disclosed." U.S. military officials have, however, played down its significance, suggesting it is more harassment than a security risk.
The Reuters report claims, "Moscow was probably behind interruptions in Latvia's mobile communications network before Russia's war games last month, in an apparent test of its cyber attack tools, Baltic and NATO officials said, based on early intelligence of the drills." There is conjecture here. A communications jammer aimed towards the Swedish Gotland island was switched on. "One of the edges (of the beam) affected Latvia," said Karlis Serzants, the deputy chairman of the Latvian parliament's National Security Committee.
The effect of the jammer was to take out Latvia's emergency services' 112 hotline in a disruption that lasted about seven hours. This is the first time that the service has failed, and occurred on September 13, just prior to the most intensive period of the Russian Zapad war games.
While hacking smartphones would seem to be more allied to cyber-psychological warfare, disrupting telecommunications clearly has a cyberwar potential -- for both an offensive and defensive kinetic posture.
Both incidents show classic plausible deniability. While NATO might 'know' that the Russian government is behind the phone hacks, proving it to a legal certainty remains difficult. Similarly, since the jammer was not aimed at Latvia but merely caught it a glancing blow, it could be claimed to be accidental.
The fact remains, however, that Russia will have learnt much about the practical effects of the two incidents. The Baltic would appear to be the latest area for Russian offensive cyber testing, just as the Ukraine has been in recent years. U.S. Army Lieutenant General Ben Hodges, who heads U.S. Army forces in Europe, described the incidents to reporters as a sign of the progress Russia made in electronic warfare while NATO was fighting counter-insurgency campaigns in Afghanistan.
In her first official press briefing since taking office in August, Kay Bailey Hutchison (the US envoy to NATO) said, "I think it's a big concern. It has just come to light but I think it'll be an area of discussion and most certainly I know that ourselves and our allies are going to be immediately looking into it … and try to determine how it's happening and cut it off."
NATO itself has always stressed that its cyber strategy is purely defensive. This is moot: while NATO itself might not be developing offensive capabilities, its members almost certainly are. The U.S. Cyber Command, for example, recently conducted a week long denial of service attack against against the North Korean spy agency, the Reconnaissance General Bureau.
The reality is that international state cyber incidents are continuing to escalate in line with growing geopolitical tensions.
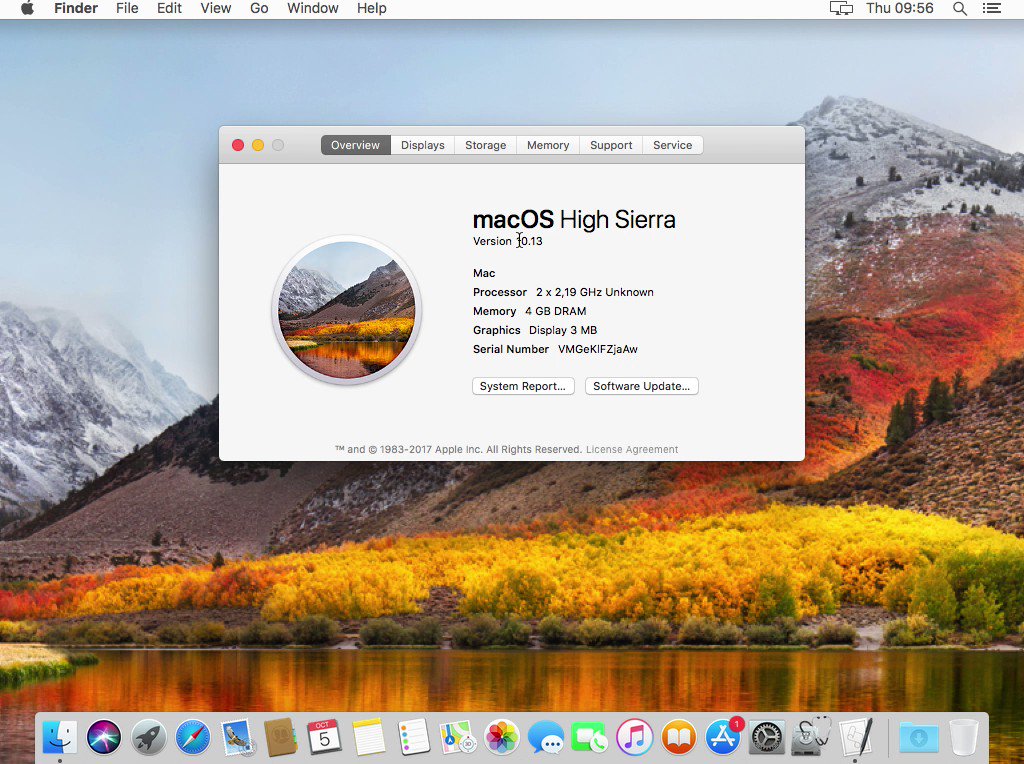
Apple file system flaw, macOS shows encrypted drive’s password in the hint box
6.10.2017 securityaffairs Apple
Apple released a patch for macOS High Sierra 10.13 that address also a flaw in Apple file system that exposes encrypted drive’s password in the hint box.
Apple yesterday released a security patch for macOS High Sierra 10.13 to fix vulnerabilities in the Apple file system (APFS) volumes and Keychain software.
The vulnerability in the Apple file system was first reported by Matheus Mariano, a developer at Leet Tech, and later confirmed also by the programmer Felix Schwartz.
5 Oct
Felix Schwarz @felix_schwarz
It becomes clearer every day that Apple shipped #APFS way too early. https://twitter.com/martiano_/status/913024208946556928 …
Follow
Felix Schwarz @felix_schwarz
Tried myself & it's true: #HighSierra shows the #APFS volume password as hint. Persists reboots, not stored in keychain. Wow. Just wow. pic.twitter.com/FkcHI9KHl9

53 53 Replies 1,126 1,126 Retweets 1,053 1,053 likes
Twitter Ads info and privacy
The vulnerability in the Apple file system tracked as CVE-2017-7149 could be exploited by a local attacker to gain access to an encrypted APFS volume.
“If a hint was set in Disk Utility when creating an APFS encrypted volume, the password was stored as the hint. This was addressed by clearing hint storage if the hint was the password, and by improving the logic for storing hints.” reads the description provided by Apple on its support website.
When users create an encrypted APFS volume on a Mac with an SSD using Apple’s Disk Utility app and set up a password hint, invoking the password hint mechanism while remounting the volume will display the current password in plaintext.

Here’s a video demonstrating the programming cockup:
Another flaw fixed by Apple tracked as CVE-2017-7150 affects the Keychain and was discovered by the popular expert Patrick Wardle. Wardle revealed that unsigned applications can steal macOS Keychain passwords from the latest version of macOS High Sierra and previous versions of macOS.
Many developers questioned the quality of macOS High Sierra 10.13 released at the end of September.
Follow
Brian Lopez @brianmario
Legitimately wondering of Apple accidentally shipped a pre-release version of High Sierra. So much of it is unfinished and unpolished.
4:39 AM - Sep 27, 2017
2 2 Replies Retweets likes
Russian firm provides North Korea with second Internet route
6.10.2017 securityaffairs BigBrothers
Dyn Research discovered traffic coming from North Korea running over the Russian TransTeleCom network, this is the second internet route of the regime.
North Korea gets a second Internet connection thanks to the support of a state-owned Russian firm. From the perspective of security analysts, this second connection will improve in a significant way the cyber capabilities of the North Korea undermining the US efforts to isolate the state.
The availability of a second line allows Pyongyang to improve significantly the resilience against attacks on their infrastructure.
The Russian firm TransTeleCom is the company that activated the second connection, the first one was provided by China Unicom starting at least since 2010.
The discovery of the second line was reported by experts at Dyn Research that monitors global internet connectivity.
“The possibility of disconnecting North Korea from the Internet just became much more difficult,” explained said Bryce Boland, the chief technology officer in the Asia-Pacific for security firm FireEye.

A few weeks ago, the US Cyber Command has launched a massive DDoS attack against North Korea’s Reconnaissance General Bureau (RGB). The attack hit the country infrastructure between September 22 and September 30.
North Korean infrastructure is vulnerable to such kind of attacks, for this reason, the improvement of its connectivity is a priority for Pyongyang.
“As part of the campaign, U.S. Cyber Command targeted hackers in North Korea’s military spy agency, the Reconnaissance General Bureau, by barraging their computer servers with traffic that choked off Internet access.” reported The Washington Post
“The Cyber Command operation, which was due to end Saturday, was part of the overall campaign set in motion many months ago. The effects were temporary and not destructive, officials said. Nonetheless, some North Korean hackers griped that lack of access to the Internet was interfering with their work, according to another U.S. official, who also spoke on the condition of anonymity to discuss a secret operation.”
North Korea is considered one of the most dangerous states in the cyberspace due to its aggressive conduct. It has a cyber army composed of 6,800 units of cyber soldiers that were already involved in operations against targets worldwide, including the Sony hack.
This isn’t the first time the North Korea infrastructure was targeted by foreign hackers, it has already happened shortly after the Sony attack and the attack was believed to be a US retaliation.
Experts discovered a SYSCON Backdoor using FTP Server as C&C
6.10.2017 securityaffairs BigBrothers
Security researchers with Trend Micro discovered a backdoor dubbed SYSCON that uses an FTP server for command and control (C&C) purposes.
The SYSCON backdoor is spreading through tainted documents that refer North Korea and target individuals connected to the Red Cross and the World Health Organization.

The use of an FTP server as C&C is uncommon for a botnet because the associated traffic is not difficult to monitor.
“Using an FTP server has some advantages. It is less common, and this fact may allow it to slip unnoticed by administrators and researchers. However, this also leaves the C&C traffic open for monitoring by others, including security researchers. In addition, thanks to a coding mistake by the attackers, this particular backdoor does not always run the right commands.” states the analysis published SYSCON.
The experts noticed that the weaponized documents used to spread the threat contain two long strings, with Base64 encoding using a custom alphabet, a technique that was used to deliver the Sanny malware back in 2012.
“Its similarities with the earlier Sanny attack are interesting. Both attacks used relatively unusual techniques for their C&C server, their structure is similar, and the encoding key is identical. Documents somehow tied to North Korea were also used. We cannot eliminate the possibility that both Sanny and this new malware family were the work of the same threat actor.” continues the analysis.
The Base64 strings are cabinet files that contain the 32-bit and 64-bit versions of the malicious code. When the victims open the file, the appropriate cabinet file based on the OS version is being extracted into the %Temp% folder.
The file determines the operating system version and either executes a BAT file or injects a DLL into the taskhost(ex) process to execute the BAT without triggering a UAC prompt.
The Install.bat copies the main malware ipnet.dll and the configuration file ipnet.ini into the %Windows%\System32, it configures new malicious COMSysApp service using the sc command line utility, adds the service parameters into the registry, starts the malicious service, and deletes all previously created files in the %Temp% directory.
The SYSCON malware uses the computer name as an identifier, then logs into the FTP server using credentials stored in the configuration file.
The researchers discovered a URL for the byethost free FTP service provider by decoding the configuration file.
On the server side, the commands are stored in .txt files. Every time a bot processes a command, the malicious code lists all currently running processes, then sends zipped and encoded data to the server.
The list of supported commands includes copy file to temp.ini, pack it to temp.zip, encode and upload; pack file to temp.zip, encode and upload; delete config file, write string to the new config file; put file to the given path on infected system; execute command but don’t report back; and execute downloaded file.
Malware researcher noticed that the authors of the threat made a coding mistake that caused the backdoor sometimes executing the wrong commands.
The researchers have found a typo error in the command processing loop, while the malware treats the commands as strings in wide character format, a parameter in one of the functions has an incorrect file name, thus preventing the process from executing.
IT administrators should monitor any connection to external FTP servers, they can be used not just for data exfiltration, but also for C&C activity as well.
Russian spies pilfered data from NSA Contractor’s home PC running a Kaspersky AV
6.10.2017 securityaffairs BigBrothers
Russian hackers allegedly exploited Kaspersky AV to hack into NSA contractor and steal the NSA exploit code. It complicates Kaspersky’s position.
Anonymous sources have claimed Russian intelligence extracted NSA exploits from a US government contractor’s home PC using Kaspersky Lab software.
Sources told the Wall Street Journal that a malicious code allowed cyber spies to exfiltrate classified code, documentation and other sensitive data. It is alleged Kremlin hackers exploited the security package in one way or another to identify those sensitive files and exfiltrate them.
“Hackers working for the Russian government stole details of how the U.S. penetrates foreign computer networks and defends against cyberattacks after a National Security Agency contractor removed the highly classified material and put it on his home computer, according to multiple people with knowledge of the matter.” states the Wall Street Journal.
“The hackers appear to have targeted the contractor after identifying the files through the contractor’s use of a popular antivirus software made by Russia-based Kaspersky Lab, these people said”
The security breach occurred in 2015, but it was discovered earlier this year. Experts speculate the stolen NSA exploit code and classified documents could be compared with code included in the Shadow Brokers dump that dates back to 2013.
According to the sources, the Kaspersky antivirus discovered the NSA exploit while scanning the machines. Once detected the malicious software the antivirus sent it back to a cloud service to inspect it, it is in this phase that the Russian intelligence allegedly exploited the software to establish a backdoor to the PC.
The WSJ’s sources don’t clarify the role of the Kaspersky firm in he cyber theft, it is unclear if it helped the Russian spies or if the hackers exploited some flaws in Kaspersky software to exfiltrate the exposed documents.
Another possibility is that, under Russian law, the Russian Government forced the Kaspersky personnel to hack into the computer containing the NSA code and exfiltrate it.
Kaspersky Lab was the company that first spotted malware used by the NSA-linked Equation Group and it is likely that the Russian intelligence exploited this knowledge for espionage purposes.

Kaspersky Lab promptly denied any involvement, below the official statement published by the company.
“Kaspersky Lab has not been provided any evidence substantiating the company’s involvement in the alleged incident reported by the Wall Street Journal on October 5, 2017, and it is unfortunate that news coverage of unproven claims continue to perpetuate accusations about the company.
“As a private company, Kaspersky Lab does not have inappropriate ties to any government, including Russia, and the only conclusion seems to be that Kaspersky Lab is caught in the middle of a geopolitical fight.
“We make no apologies for being aggressive in the battle against malware and cybercriminals. The company actively detects and mitigates malware infections, regardless of the source, and we have been proudly doing so for 20 years, which has led to continuous top ratings in independent malware detection tests. It’s also important to note that Kaspersky Lab products adhere to the cybersecurity industry’s strict standards and have similar levels of access and privileges to the systems they protect as any other popular security vendor in the U.S. and around the world.” – Attributable to Kaspersky Lab.
Follow
Eugene Kaspersky ✔@e_kaspersky
New conspiracy theory, anon sources media story coming. Note we make no apologies for being aggressive in the battle against cyberthreats
4:25 PM - Oct 5, 2017
105 105 Replies 105 105 Retweets 170 170 likes
Twitter Ads info and privacy
Since the US government is banning Kaspersky products from federal computers in September Kaspersky repeatedly offered up the source code of its products for officials to review.
“It’s a lot harder to beat your opponent when they’re reading your playbook, and it’s even worse when someone on your team gives it to them. If these reports are true, Russia has pulled that off,” said U.S. Senator Ben Sasse, a member of the Senate Armed Services Committee.
“The men and women of the US Intelligence Community are patriots; but, the NSA needs to get its head out of the sand and solve its contractor problem. Russia is a clear adversary in cyberspace and we can’t afford these self-inflicted injuries.”

Senator Ben Sasse ✔@SenSasse
Russia is a clear adversary in cyberspace and we can’t afford these self-inflicted injuries. https://www.sasse.senate.gov/public/index.cfm/press-releases?ID=B97F3D92-A6C1-48D8-935E-1F822754F164 …
7:51 PM - Oct 5, 2017
165 165 Replies 534 534 Retweets 1,030 1,030 likes
Twitter Ads info and privacy
The Kaspersky antivirus may have detected NSA malware being used in the wild, and intentionally or not have provided the Russian cyberspies the backdoor to steal the precious code.
Sincerely I’m disconcerted about the way such kind of code is managed by US intelligence, the code was stolen from a personal PC with running a Kaspersky Antivirus, is this the best way to keep a hacking tool?
The Senator Jeanne Shaheen (D-NH) also condemned the company and urges a strong action against the company.
“The strong ties between Kaspersky and the Kremlin are extremely alarming and have been well documented for some time,” she said today. “It’s astounding and deeply concerning that the Russian government continues to have this tool at their disposal to harm the United States.” reads the Shaheen’s statement.
Utilities Fear Cyberattacks Could Cause Electric Grid Disruptions: Survey
5.10.2017 securityweek Cyber
Many utility executives from around the world believe cyberattacks could cause disruptions to electric distribution grids in the next five years, according to a report published on Wednesday by professional services company Accenture.
Accenture conducted a survey of more than 100 utility executives from over 20 countries in Europe, North America, Asia Pacific and other regions. The respondents were decision-makers in processes related to smart grids.
The study shows that nearly two-thirds of respondents are concerned that there is at least a moderate risk of a cyberattack causing disruptions to electricity supply in the next five years.
Electric distribution grids face cyberattacks
Accenture found that 57% of respondents are concerned that a cyberattack would result in interruption to electricity supply, while 53% are worried about its impact on employee and/or customer safety.
Roughly half of respondents are concerned about theft of sensitive customer or employee data, and theft of company data and intellectual property. Ransomware and destruction of physical assets are also among the top concerns.
“A typical distribution grid has neither the size of a transmission network nor the same risks of cascading failure,” Accenture said in its report. “However, distribution grids have the same vulnerabilities and, as a potentially softer target, could be increasingly subject to attack. Breaches by a wide range of potential attackers could have devastating impacts along the entire electricity value chain, from generation through to consumers. A successful attack could erode public trust in the utility and raise questions about the security of all devices along the value chain.”
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
On a global scale, cyberattacks conducted by state-sponsored actors, including their own government, are considered the biggest risk to distribution networks. This is also the greatest concern in North America, but cybercriminals are seen as the biggest threat in Europe and the Asia Pacific region.
The study also shows that utility executives are concerned, at least to some extent, about the risks posed by the Internet of Things (IoT) devices found in consumers’ homes.
Despite concerns, more than 40% of respondents said their organizations did not fully integrate cybersecurity into their risk management processes.
Nearly one-third of respondents believe improved threat identification and sharing across the industry would have the greatest impact on their cybersecurity capabilities. Others believe the biggest impact would come from clearer understanding of OT implications for cybersecurity (20%), training and risk awareness (15%), a holistic security program (12%), a risk management framework incorporating cybersecurity (11%), and clear cybersecurity governance and roles (10%).
Fast Food Chain Sonic Confirms Card Breach
5.10.2017 securityweek Incindent
Sonic Drive-In, a fast food restaurant chain with more than 3,500 locations across the United States, confirmed on Wednesday that cybercriminals may have stolen customers’ credit and debit card information using a piece of malware.
The company has provided only little information about the incident, but says it’s working with law enforcement and third-party forensics firms to investigate the breach. Sonic said it delayed notifying customers of the intrusion at the request of law enforcement.
“Sonic Drive-In has discovered that credit and debit card numbers may have been acquired without authorization as part of a malware attack experienced at certain Sonic Drive-In locations,” the company stated.
Customers who used their cards at Sonic Drive-In locations this year are being offered 24 months of free fraud detection and identity theft protection services via Experian. Consumers can enroll until December 31.
While it’s unclear which locations were hit by the malware attack and how many customers are impacted, security blogger Brian Krebs last week learned of a cybercrime marketplace selling a batch of 5 million cards, at least some of which appear to come from Sonic’s systems.
The cards were put up for sale on September 18, but IBM researchers said the first batch appeared on a different cybercrime service that checks card validity for fraudsters on September 15, which suggested that the attackers had been collecting card data on an ongoing basis.
The data offered on the cybercrime website had been offered for $25-$50 per card. Interested parties could purchase information from cards owned by individuals in a certain state or city — fraudulent transactions made in the area of the victim are less likely to trigger any alarms.
Sonic’s shares dropped 2 percent to $24.74 on Wednesday.
“Will customer loyalty be shaken? If the past as with the Wendy’s breach is prologue, then the answer is a qualified maybe, and if so, then only slightly,” Robert W. Capps, VP of Business Development at NuData Security, told SecurityWeek after the breach came to light.
“However, this - coupled with the tsunami of recent breaches - might just be the game changers that lead US Federal authorities to better protect the data collection, processing and storage of customer data,” Capps added.
The list of major restaurant chains that informed customers of a payment card breach in the past year includes Wendy’s, Cicis, Arby’s, Chipotle, Shoney’s, and Noodles & Company.
North Korea Gets Second Web Connection Via Russian Firm
5.10.2017 securityweek BigBrothers
A state-owned Russian company has opened up a second internet connection for North Korea which could strengthen Pyongyang's cyber capabilities and undermine US efforts to isolate the regime, security experts said.
The activation of the new line from TransTeleCom was first detected Sunday by analysts at Dyn Research, which monitors global internet connectivity.
The new connection supplements the existing link provided by China Unicom, which has almost exclusively routed North Korean internet traffic since 2010.
The additional line gives Pyongyang "significantly more resilience against attacks on their network infrastructure," said Bryce Boland, the chief technology officer in the Asia-Pacific for cybersecurity firm FireEye.
The Washington Post reported earlier that the US Cyber Command had carried out attacks against hackers in North Korea aimed at cutting off their access to the Internet.
The operation ended Saturday, the report said.
North Korea has a 6,800-strong unit of trained cyberwarfare specialists, according to Seoul's defence ministry, and has been accused of launching high-profile cyberattacks including the 2014 hacking of Sony Pictures.
Related: U.S. Cyber Command Launched DDoS Attack Against N. Korea: Report
But with only one internet provider to rely on, the regime has often found itself vulnerable to external cyberattacks against its own network infrastructure.
North Korea suffered several internet connection failures -- some which lasted for hours -- shortly after the Sony attack, which many suspected to be a US retaliation.
With the alternate route from Russia, "the possibility of disconnecting North Korea from the Internet just became much more difficult," Boland said.
Firefox Support for Windows XP and Vista Ends June 2018
5.10.2017 securityweek Security
After annoucing in December 2016 that it plans to move Windows XP and Vista users to Firefox Extended Support Release (ESR), Mozilla this week announced that support for the two operating systems will be completely removed in June 2018.
Firefox is the last major browser to offer support for the two outdated and obsolete operating systems, but Mozilla has finally decided to change that.
Google cut the cord on Windows XP and Vista a while back, with Chrome 49 being the last release to work on the old platforms (the browser is currently at version 61). In early 2017, Google dropped support for the platforms in Gmail as well, by removing support for Chrome version 53 and below from the email service.
Despite releasing security updates for Windows XP to tackle Shadow Brokers exploits following the WannaCry outbreak, Microsoft isn’t supporting the platform either. The company ended support for the platform on April 8, 2014, when it released the last security updates for it.
Internet Explorer 8, which is used by as many as 88% of Windows XP users as their standard browser, hasn’t received security updates for almost two years.
“Today we are announcing June 2018 as the final end of life date for Firefox support on Windows XP and Vista. As one of the few browsers that continues to support Windows XP and Vista, Firefox users on these platforms can expect security updates until that date. Users do not need to take additional action to receive those updates,” Mozilla announced in a blog post.
The Internet organization is also encouraging users to upgrade to a versions of Windows that is supported by Microsoft. With no security updates available for unsupported platforms, known vulnerabilities and exploits put their users at risk.
Despite warnings, however, Windows XP and Vista continue to be widely used in enterprise environments. A June 2017 report revealed that the Metropolitan Police Service (MPS, or the Met) was still using over 10,000 XP machines on their network.
Bezpečnostní experti bijí na poplach. Útoků na bankovní účty přibývá
5.10.2017 Novinky/Bezpečnost Hacking
Motivace počítačových pirátů v posledních týdnech je jasná – peníze. Kyberzločinci se totiž stále častěji zaměřují na bankovní účty svých obětí. Vyplývá to z analýzy bezpečnostní společnosti Check Point o největších kybernetických hrozbách za měsíc srpen.
Podle kybernetických analytiků počítačoví piráti používají stále častěji bankovní trojské koně. Do žebříčku deseti nejrozšířenějších škodlivých kódů se totiž dostaly hned tři viry cílící na bankovní účty.
„Identifikují, kdy oběť navštíví webové stránky banky, a pak pomocí techniky webinject nebo sledováním stisknutých kláves kradou přihlašovací údaje a další citlivá data, jako jsou například PIN kódy. Trojské koně mohou také zkusit ukrást přihlašovací údaje přesměrováním obětí na falešné bankovní internetové stránky,“ zdůraznil Peter Kovalčík, SE Manager ve společnosti Check Point.
Hlavní motivací peníze
Do desítky nejrozšířenějších škodlivých kódů se dostaly bankovní trojské koně Zeus, Ramnit a Trickbot.
Daří se také vyděračským virům z rodiny ransomware. Například Globeimposter byl druhým nejčastějším malwarem na světě. Ačkoli byl objeven v květnu 2017, až do srpna se masivně nešířil. Globeimposter šifruje soubory a od obětí požaduje platbu za dešifrování cenných dat.
Touha po penězích je tak ze strany počítačových pirátů evidentní. „Finanční zisk je hlavním motivem pro drtivou většinu kyberzločinců a bohužel pro to mají k dispozici i celou řadu nástrojů,“ uvedl bezpečnostní expert.
Nejrozšířenější virus oslabil
„V Top 10 malwarových rodinách vidíme vysoce efektivní variantu ransomwaru i celou řadu bankovních trojanů, což znovu ukazuje, jak vynalézaví umí hackeři být ve snaze vydělat peníze. Organizace musí být při ochraně své sítě ostražité a proaktivní,“ dodal Kovalčík.
Celým statistikám nicméně vévodil škodlivý kód Roughted, který je využívaný k útokům na podnikové sítě. Ten kraloval žebříčku nejrozšířenějších virů už o měsíc dříve, aktuálně jeho podíl nicméně klesl z 18 % na méně než 12 %.
Tři nejrozšířenější škodlivé kódy
1. RoughTed
Rozsáhlá malvertisingová kampaň RoughTed je využívána k šíření odkazů na nebezpečné webové stránky a k šíření škodlivého obsahu, jako jsou scam, adware, exploit kity a ransomware. Může být použita k útoku na jakýkoli typ platformy a operačního systému, vyhne se nástrojům na blokování reklamy a sleduje chování uživatelů, aby byl finální útok co nejrelevantnější.
2. Globeimposter
Ransomware maskovaný jako varianta ransomwaru Globe. Byl objeven v květnu roku 2017 a je distribuován spamovými kampaněmi, malvertisingem a exploit kity. Při šifrování připojuje ke každému zašifrovanému souboru koncovku .crypt.
3. HackerDefender
Uživatelský rootkit pro Windows může být využit ke skrytí souborů, procesů a klíčů registru, a také k implementaci backdooru a přesměrování portu, který funguje na základě TCP portů otevřených stávajícími službami. Takže skryté backdoory není možné najít tradičními postupy.
CVE-2017-12617 Code Execution flaw patched in Apache Tomcat
5.10.2017 securityaffairs Vulnerebility
Several security vulnerabilities have been patched in recent weeks in Apache Tomcat, including the CVE-2017-12617 Code Execution vulnerability.
Several security vulnerabilities have been patched in recent weeks in Apache Tomcat. The list of fixed flaws recently addressed also included code execution vulnerabilities.
Apache Tomcat is the most widely used web application server, with over one million downloads per month and over 70% penetration in the enterprise datacenter.
On Tuesday, the Apache Tomcat development team publicly disclosed the presence of a remote code execution vulnerability, tracked as CVE-2017-12617, affecting the popular web application server. The Tomcat versions 9.x, 8.5.x, 8.0.x and 7.0.x are affected by the flaw.
The vulnerability classified as “important” severity, has been fixed in the versions 9.0.1, 8.5.23, 8.0.47 and 7.0.82.
The vulnerability only affected systems that have the HTTP PUT method enabled, it could be exploited by attackers to upload a malicious JSP file to a targeted server using a specially crafted request. Once the file has been uploaded, the code it contains could be executed by requesting the file.
Fortunately, the extent of the flaw is limited by the fact that it could be triggered only on the default servlet configured with the readonly parameter set to false or the WebDAV servlet enabled with the readonly parameter set to false.
“When running with HTTP PUTs enabled (e.g. via setting the read-only initialisation parameter of the Default servlet to false) it was possible to upload a JSP file to the server via a specially crafted request. This JSP could then be requested and any code it contained would be executed by the server.” states the security advisory.
“This configuration would allow any unauthenticated user to upload files (as used in WebDAV). It was discovered that the filter that prevents the uploading of JavaServer Pages (.jsp) can be circumvented. So JSPs can be uploaded, which then can be executed on the server.” wrote the security researcher Peter Stöckli.
“Now since this feature is typically not wanted, most publicly exposed system won’t have readonly set to false and are thus not affected.”
The proof-of-concept (PoC) exploit for the CVE-2017-12617 flaw is publicly available.
Stöckli highlighted the similarities between the CVE-2017-12617 flaw and the CVE-2017-12615 vulnerability that was fixed on September 19 with the release of version 7.0.81.
The Apache Tomcat 7 update released in September also addressed the CVE-2017-12616 that could be exploited by attackers to bypass security constraints and view the source code of JSPs via a specially crafted request.
CSE CybSec ZLAB Malware Analysis Report: APT28 Hospitality malware
5.10.2017 securityaffairs APT
The CSE CybSec Z-Lab Malware Lab analyzed the Hospitality malware used by the Russian APT28 group to target hotels in several European countries.
The Russian hacker group APT28, also known as Sofacy or Fancy Bear, is believed to be behind a series of attacks in last July against travelers staying in hotels in Europe and Middle East.
This attack is performed by sending spear phishing emails to the victims, masquerading as a hotel reservation form that, if opened and macros are enabled, installs a malware in the machine’s victim.
Why should Fancy bear do this? According to FireEye and other security firms, Sofacy is a cyberespionage group and a good tool to get info about people (possibly businessmen and politicians) hosted in important hotels, is to deceive them to install a spyware with a Command and Control that monitors the actions of all the victims.

Figure 1 – Screen of Word dropper.
The above figure shows an example of the weaponized document used by hackers as an attachment in spear phishing emails. The document contains a payload achievable when macro is enabled. In fact, the macro is a Visual Basic script used to decode the malicious payload and to create a series of files, according to the following scheme: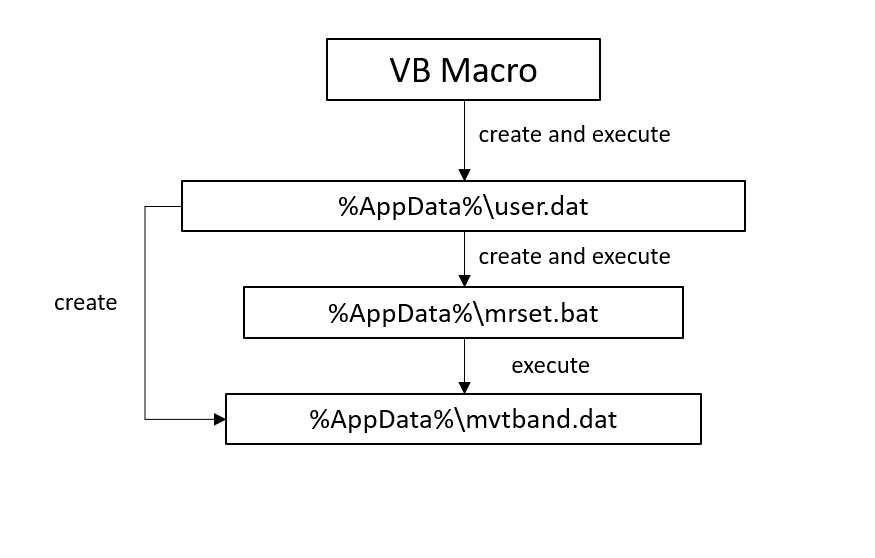
Figure 2 – Files’ creation and execution scheme
The file “mvtband.dat” is the core of the malware that contains a C2C client, which tries to connect to servers, “mvtband.net” and “mvband.net” in order to send the info gathered about the victim’s host and receive new commands to execute on it. In particular, the malware contacts these C&C servers with POST request on a random path. The body contains some info, among them the list of the executing processes, info about system settings, browser preferences, encrypted using its own algorithm. Moreover, from our advanced analysis, we discovered that Hospitality Malware takes screenshots of the machine that most likely it sends to the C2C together with other info. But, nowadays, these servers are blacklisted so we can’t analyze all the complete behavior of Hospitality Malware.
You can download the full ZLAB Malware Analysis Report at the following URL:
The Festive Complexities of SIGINT-Capable Threat Actors
5.10.2017 Kaspersky Security
Attribution is complicated under the best of circumstances. Sparse attributory indicators and the possibility of overt manipulation have proven enough for many researchers to shy away from the attribution space. And yet, we haven’t even discussed the worst-case scenarios. What happens to our research methods when threat actors start hacking each other? What happens when threat actors leverage another’s seemingly closed-source toolkit? Or better yet, what if they open-source an entire suite to generate so much noise that they’ll never be heard?
Thankfully, the 2017 VirusBulletin conference is upon us and, as in previous years, we’re taking the opportunity to dive into an exciting subject, guided by our experience from doing hands-on APT research.
During the past years, we discussed the evolution of anti-malware research into intelligence brokerage, the inherent problems with doing attribution based solely on fifth-domain indicators, and an attempt to have a balanced discussion between defensive cats and the sly mice that elude them. Continuing in this direction, this year we decided to put our heads together to understand the implications that the esoteric SIGINT practice of fourth-party collection could have on threat intelligence research.
A few types of SIGINT Collection
The means by which information is generated and collected is the most important part of an analyst’s work. One must be well aware of the means and source of the information analyzed in order to either compensate or exploit its provenance. For that reason, collection can be categorized by its means of generation in relation to the position of the parties involved, as discussed below. These definitions will serve as functional categories for our understanding as outsiders looking into the more complex spheres of collection dynamics.
To showcase the types of data collection, let’s imagine a competent entity named ‘Agency-A’ as a stand-in for a ‘God on the wire‘-style SIGINT agency interested in fourth-party collection.
There are multiple types of collection categories available to this entity. The more obvious being information collected by Agency-A directly (first-party) or shared with Agency-A by partner services (second-party). Third-party collection, or information collected via access to strategic organizations, whether they realize it or not, has gotten a lot of attention over the past few years. This would include ISPs, ad networks, or social media platforms that aggregate great troves of valuable data.
Similarly, we will use further entities Agency-B as a second semi-competent SIGINT agency upon which Agency-A can be recurringly predatory for the sake of explanation. When necessary an even less competent Agency-C will serve as prey.
Yet, things get most interesting when we start talking about:
“Fourth-party collection – …involves interception of a foreign intelligence service’s ‘computer network exploitation’ (CNE) activity in a variety of possible configurations. Given the nature of Agency-A as a cyber-capable SIGINT entity, two modes of fourth-party collection are available to it: passive and active. The former will take advantage of its existing visibility into data in transit either between hop points in the adversary’s infrastructure or perhaps in transit from the victim to the command-and-control servers themselves (whichever opportunity permits). On the other hand, active means involve the leveraging of diverse CNE capabilities to collect, replace, or disrupt the adversary’s campaign. Both present challenges we will explore in extensive detail further below.”
In less technical terms, fourth-party collection is the practice of spying on a spy spying on someone else. Or with age-old cryptographic interlocutors: Bob is obsessed with Alice. Alice is being spied on by her overzealous neighbour Eve. In order for Bob to be a creeper without arousing suspicion, he decides to spy on Eve with the purpose of getting to know Alice through Eve’s original privacy violation.
As you might expect there are different ways to do this and many of them enjoy the benefit of being near impossible to detect. Where possible, we have added examples of what to us looks like possible active attempts to collect on another’s collection. Otherwise, we have added thought experiments to help us wrap our heads around this shadowy practice. Two examples worth bringing to your attention (reproduced faithfully from our paper):
‘We heard you like popping boxes, so we popped your box so we can watch while you watch’
Attempting to highlight examples of fourth-party collection is a difficult exercise in the interpretation of shadows and vague remnants. While passive collection is beyond our ability to observe, active collection involves the risk of leaving a footprint in the form of artefacts. In the course of APT investigations, Kaspersky Lab’s Global Research and Analysis Team (GReAT) has encountered strange artefacts that defy immediate understanding in the context of the investigation itself. While we cannot be certain of the intent or provenance of these artefacts, they nonetheless fit a conceptual framework of active fourth-party collection. Here’s a few examples:
Crouching Yeti’s Pixelated Servers
In July 2014, we published our research on Crouching Yeti, also known as ‘Energetic Bear’, an APT actor active since at least 2010. Between 2010 and 2014, Crouching Yeti was involved in intrusions against a variety of sectors, including:
Industrial/machinery
Manufacturing
Pharmaceutical
Construction
Education
Information technology
Most of the victims we identified fell into the industrial and machine manufacturing sector, indicating vertical of special interest for this attacker.
To manage their victims, Crouching Yeti relied on a network of hacked websites which acted as command-and-control servers. For this, the attackers would install a PHP-based backend that could be used to collect data from or deliver commands to the victims. To manage the backend, the attackers used a control panel (also written in PHP) that, upon checking login credentials, would allow them to manage the information stolen from the victims.
In March 2014, while investigating one of the hacked sites used by Energetic Bear, we observed that for a brief period of time, the page for the control panel was modified to include an <img src> tag that pointed to a remote IP address in China. This remote 1×1 pixels wide image was likely intended to fingerprint the attackers as they logged into their control panel. The fingerprinting could have been used to collect attributory indicators. The usage of an IP address in China, which appeared to point to yet another hacked server, was most likely an attempt at a rudimentary false flag should this injection be discovered.
NetTraveler’s Most Leet Backdoor
While investigating the Nettraveler attacks, we obtained a disk image of a mothership server used by the threat actor. The mothership, a combination staging and relay server, contained a large number of scripts used by the attackers to interact with their malware, as well as VPN software and other IP masking solutions used to tunnel into their own hacking infrastructure.
Beyond the fortuitous boon of seizing such a content-rich server, GReAT researchers made a further unexpected discovery: the presence of a backdoor apparently placed by another entity.
We believe the backdoor was installed by an entity intent on maintaining prolonged access to the Nettraveler infrastructure or their stolen data. Considering that the NetTraveler operators had direct access to their mothership server and didn’t need a backdoor to operate it, we consider other possible interpretations less likely.
The artefact encountered is the following:
Name svchost.exe
MD5 58a4d93d386736cb9843a267c7c3c10b
Size 37,888
Interestingly, the backdoor is written in assembly and was injected into an empty Visual C executable that served as a template. This unusual implementation was likely chosen in order to confuse analysis or prevent detection by simple antivirus programs.
The backdoor is primitive and does nothing but listen to port 31337 (The most ‘LEET!’ port) and wait for a payload to be sent. The acceptable payload format is depicted here:
The assembly code is then executed and can perform any action chosen by the predatory attackers. The backdoor requires no authentication. Combining this sort of backdoor with Metasploit or other similar frameworks could have easily been used to control the system.
During the last years, we have seen a number of other peculiar incidents and cases which could constitute fourth party collection.”
To read the full paper and learn more about this, refer to “Walking in Your Enemy’s Shadow: When Fourth-Party Collection Becomes Attribution Hell”
NIST Readies to Tackle Internet's Global BGP Vulnerabilities
5.10.2017 securityweek Vulnerebility
NIST has published an update on its work on the new Secure Internet Domain Routing (SIDR) standards designed to provide the internet the security that is currently lacking from the Border Gateway Protocol (BGP).
BGP was designed in 1989 as a short-term fix for the earlier Exterior Gateway Protocol that could no longer handle the rapidly increasing size of the internet, and was in imminent danger of meltdown. The problem is that BGP was designed without any security, despite it being fundamental to the operation of the internet.
BGP controls the route that data takes from source to destination. It does this by keeping tabs on the availability of local stepping stones along that route. The availability of those stepping stones is maintained in regularly updated routing tables held locally. The problem is that there is no security applied to those tables -- in effect, the entire map of the internet is built on trust; and trust is in short supply in today's internet. Whole swathes of traffic can be hijacked.
"BGP forms the technical glue holding the internet together," explains NIST in Tuesday's post; "but historically, its lack of security mechanisms makes it an easy target for hacking."
The trust model underpinning BGP is easily abused, and has frequently been abused. Generally speaking, most abuse is thought to have be accidental -- but there have been enough suspicious incidents to demonstrate that the theoretic concern over BGP's security is not unfounded. Since the routing tables are locally stipulated and internationally distributed, a telecommunications company in one country is able to change the data routing for the entire world.
"As a result," warns NIST in a separate publication (SIDR, Part 1: Route Hijacks-- PDF), "attacks against internet routing functions are a significant and systemic threat to internet based information systems. The consequences of these attacks can: (1) deny access to internet services; (2) detour internet traffic to permit eavesdropping and to facilitate on-path attacks on endpoints (sites); (3) misdeliver internet network traffic to malicious endpoints; (4) undermine IP address-based reputation and filtering systems; and (5) cause routing instability in the internet."
One of the best known examples of route hijacking occurred in February 2008 when a Pakistani ISP tried to block YouTube after the government deemed a video depiction of Muhammad to be offensive. Its attempts to hijack YouTube deliveries to Pakistan effectively hijacked the world's YouTube making it virtually inaccessible anywhere. While the intent was intended, the result probably wasn't -- but other examples appear to be more clearly malicious.
In April of this year, 36 large network blocks were hijacked by the Russian government-controlled Rostelecom company. Researchers concluded that the BGP tables had been altered manually, probably at or by Rostelecom. What made it suspicious was the high concentration of technology and financial services companies that were included: such as MasterCard, Visa, HSBC and Symantec.
Because of the changes made to the BGP routing tables, traffic flowing into the affected networks was rerouted through Rostelecom's routers. "I would classify this as quite suspicious," said Dyn's Doug Madory at the time. "Typically accidental leaks appear more voluminous and indiscriminate. This would appear to be targeted to financial institutions."
Other examples include a scheme that ran for months in 2014 redirecting traffic within the Bitcoin infrastructure and resulting in the theft of $83,000 in Bitcoins; and a 2013 attack that detoured bank, telephony, and government data through routers in Belarus and Iceland.
While known BGP abuses have been relatively small in scope and limited in duration -- and sometimes accidental -- the vulnerabilities are real. "The fact that they haven't been dramatically exploited yet shouldn't make you feel better," warns NIST's Doug Montgomery. "Think of how much of our critical infrastructure relies on internet technology -- transportation, communication, financial systems, et cetera. Someday, someone will have the motivation."
NIST has been working with the DHS and IETF to develop a new set of BGP standards that will eliminate the problems. "The set of standards, known as Secure Inter-Domain Routing (SIDR), have been published by the Internet Engineering Task Force (IETF) and represent the first comprehensive effort to defend the internet's routing system from attack," wrote NIST yesterday.
There are three separate components that comprise SIDR: Resource Public Key Infrastructure (RPKI); BGP Origin Validation (BGP-OV); and BGP PATH Validation (BGP-PV). RPKI allows third-parties to cryptographically validate claims to ownership of internet address blocks and internet autonomous systems. Origin Validation provides protocol extensions and tools to allow BGP routers to use RPKI data to detect and filter unauthorized BGP route announcements. PATH Validation provides further protocol extensions that allow BGP routers to cryptographically verify the sequence of networks (the autonomous systems path) that comprise a BGP route.
The Origin Validation will deter simple route hijack attacks and misconfigurations (accidents), while PATH Validation will deter more sophisticated and stealthy route detour attacks. Together, says NIST, they provide a complete solution to the routing vulnerabilities identified in the original BGP.
Specifications for the three components are now complete. The third component -- PATH Validation, also known as BGPsec -- was published by IETF as RFC 8205 in September. Uptake, however, is a different matter. The first of the components (RPKI) is defined in RFC 6480 published in February 2012. By 2016, although all five Regional Internet Registries (RIRs -- AFRINIC, ARIN, APNIC, LACNIC and RIPE NCC) were RPKI able, adoption of route origin authorizations had been slow and patchy. ~7% of global BGP announcements were then covered by ROAs. RPKI adoption in Europe (~30% of its announced address space covered by ROAs) and Latin America (~13% of its announced address space covered by ROAs) was proceeding much faster than in North America (~3% of its announced address space was then covered by ROAs).
With the specification for the final SIDR component in place, NIST will now redirect its efforts. "With their publication," says the NIST announcement, "NIST's efforts will shift to helping the industry with adoption, including developing technical deployment guidance as well as working on improving the performance and scalability of implementations. As part of this technology transition effort, NIST's National Cybersecurity Center of Excellence (NCCoE) recently announced plans for a new project focused on Secure Inter-Domain Routing."
With SIDR, the 1989 temporary internet fix known as BGP is finally gaining security. Whether it can be globally implemented before a serious and well-resourced BGP attack disrupts the entire internet remains to be seen. As Montgomery said, "Someday, someone will have the motivation."
Oracle Announces New Cloud Security Services
5.10.2017 securityweek Security
Oracle announced this week at the company’s OpenWorld convention the launch of new cloud security services and improvements to existing products.
One of the new offerings is the Oracle Identity Security Operations Center (SOC), a context-aware intelligence and automation solution designed to help organizations detect and respond to sophisticated threats targeting users, applications, data and cloud workloads.
The Identity SOC leverages the newly released Oracle Security Monitoring and Analytics Cloud Service, which provides security incident and event management (SIEM) and user and entity behavioral analytics (UEBA) capabilities.
Two other major components of the Identity SOC are the Oracle CASB (Cloud Access Security Broker) Cloud Service, which enables organizations to protect business-critical cloud infrastructure and data, and the Oracle Identity Cloud Service, described by the company as a “next-generation comprehensive security and identity platform.”

Oracle also announced that the threat detection and data protection capabilities of the CASB Cloud Service have been expanded. The company says the service now offers enhanced security for both structured and unstructured data with new built-in data loss prevention (DLP) features, and new anti-malware and anti-ransomware capabilities.
The Identity SOC suite integrates with the new Oracle Management Cloud suite, a complete IT security and management solution that combines Management Cloud, Application Performance Monitoring Service, and Infrastructure Monitoring Cloud Service. The company said the security-related enhancements to Management Cloud are powered by machine learning.Oracle OpenWorld keynote
“Our vision for security and management is very simple. We need all of the data in one place. We need purpose-built machine learning that can be used by security and operations professionals, not data scientists. We need automated remediation that does not require human effort. And that’s what we’ve built with Oracle Management Cloud,” Oracle Executive Chairman and CTO Larry Ellison said in his keynote at OpenWorld.
Ellison compared the Management Cloud service to products offered by Splunk and attempted to convince the audience that Oracle’s solutions are far better. He also poked Amazon Web Services (AWS) when introducing his company’s new autonomous database.
Another new service announced by Oracle is the Configuration and Compliance Cloud Service, which helps organizations ensure continuous compliance.
Free Tool Detects, Exploits DLL Hijacking Vulnerabilities
5.10.2017 securityweek Forensics
DLL hijacking is not a new attack vector. It's been around for 20 years or more. It's not easy, but it's very effective. Once achieved it provides stealth and persistence -- precisely those attributes sought by advanced and state actors.
Forrest Williams, senior security researcher at Cybereason, spotted an incidence of DLL hijacking on a customer's network; and decided to tackle the problem. His solution was to develop a new scanner, a tool he calls Siofra, that will both detect a hijacking vulnerability and also provide an automated method of exploiting the vulnerability.
It is a drastic solution, and one that leaves him and his company open to criticism in the same way that Metasploit is criticized: it can help bad guys attack good guys. Williams first approached Microsoft and was told, this attack "is predicated on the attacker having written a malicious binary to the directory where the application is launched from. As described in the Windows library search order process, loading binaries from the application directory is by design. This does not meet the bar for security servicing."
The story behind Siofra, pronounced 'sheefra' (a 'changeling' in Celtic mythology) is told in a new blog post from Cybereason. The developer, Forrest Williams, discussed the problem with SecurityWeek. He tells the full story in an associated paper (PDF). His hope is that Siofra will eventually force Microsoft to address the DLL hijacking vulnerability in the same way that Mimikatz forced it to address the underlying problem with credentials in the latest release of Windows 10.
DLL hijacking occurs when a modified and weaponized DLL is called by an application instead of the original DLL. It is neither an easy nor a common attack; but a hijacked DLL can be left behind after a network compromise, allowing the attacker to withdraw while leaving a stealthy, persistent and dangerous malware behind. Because of the inherent difficulties, it is primarily used by advanced or state actors.
And it does happen. It happened with the recent CCleaner compromise, now thought to have been conducted by a Chinese state actor. "M.E.DOC is possibly a better example," said Williams. Here, the .net code in ZvitPublishedObjects.dll had been modified on multiple occasions to allow a malicious actor to gather data and download and execute arbitrary code. "It is even speculated", said Williams, "that the whole purpose of the M.E.DOC company was really to deliver a malicious payload [the NotPetya wiper] on behalf of the Russian government against Ukraine."
In both of these cases, it is thought that advanced state actors compromised the supply chain with DLL hijacking. So although the threat isn't common, it can be devastating; and as nation states continue to increase their cyber activity, so the threat and danger is likely to grow. The growing interaction between geopolitics and cybersecurity makes this inevitable.
For the moment, it appears that Microsoft is unwilling to address the problem. "The only real solution from Microsoft would be whitelisting or code signing so that no DLL is ever loaded into a Microsoft process unless it is digitally signed," explained Williams. "Thing is, they don't do this; and I think the reason they don't do this is because they won't be able to do backwards compatibility. Also," he added, "some Microsoft code is designed with 'just-in-time-compiling'. It's compiled as the code is run -- and there's no way to sign it. So there's no real way to create a whitelist. Windows simply wasn't designed with this issue in mind -- so it is design flaws that have prevented them fixing the issue to this day."
The design flaws will need to be designed out of Windows -- but it will take a lot of development effort from Microsoft. "It wouldn't be an easy fix," said Williams. "If attacks become more prevalent -- and right now they're not very common -- I think that Microsoft would definitely do something. After the release of the Mimikatz tool to steal credentials, making credential stealing much easier, Microsoft has now changed their design. They've fixed the issue in the latest Windows 10 release. But it took them a long time to do, and it needed someone to make it easy for the attackers with the release of Mimikatz, before they actually felt the pain and started to solve the problem. I don't think Microsoft would have fixed the underlying vulnerability that Mimikatz weaponized without it being released. So unless DLL hijacking becomes well-known and used, I don't think it will ever be fixed."
Williams hopes that Siofra will change the status quo; that is, force Microsoft to address the issue. Siofra is not the first DLL scanner. "But it has one unique addition," explains Williams. First it will find vulnerable DLLs; "but then it is able to create an almost identical copy of the DLL that it targets; so that when you exploit one of these vulnerabilities Siofra creates a DLL that is almost a perfect clone except that it's got a tiny modification that allows the attacker to add their own payload into the DLL. It's not just a scanner. There have been scanners before; but this scanner is much more powerful. It has the ability to create these attacks and exploit the vulnerability; and that's unique."
Williams has little doubt that DLL hijacking will continue and become a growing problem from advanced attackers. The problem is that the vulnerability is everywhere. "When I tested Siofra," he told SecurityWeek, "I did not find a single application that did not include at least one vulnerable DLL." This isn't limited to Microsoft applications, although it includes Windows Defender, Internet Explorer and WMI -- none of which were previously known to be vulnerable. But it also includes applications like Adobe Reader and Firefox. "No defensive software wants to delete high-trust applications like these." As a result, a hijacked DLL simply flies under the radar of anti-malware software.
"DLL hijacking," suggests Williams, "is the new rootkit."
New Microsoft Tool Analyzes Memory Corruption Bugs
5.10.2017 securityweek Forensics
A newly released analysis tool from Microsoft helps security engineers and developers investigate memory corruption bugs.
Called VulnScan, the tool has been designed and developed by the Microsoft Security Response Center (MSRC) to help determine the vulnerability type and root cause of memory corruption flaws. The utility was built on top of two internally developed tools, namely Debugging Tools for Windows (WinDbg) and Time Travel Debugging (TTD), the tech giant says.
WinDbg was created as a Windows debugger that has recently received a user interface makeover, while Time Travel Debugging is an internally developed framework designed to record and replay execution of Windows applications.
“By leveraging WinDbg and TTD, VulnScan is able to automatically deduce the root cause of the most common types of memory corruption issues. Application Verifier’s mechanism called PageHeap is used to trigger an access violation closer to the root cause of the issue,” Mateusz Krzywicki from MSRC explains.
The tool begins the analysis process from the crash location then progresses to determine the root cause. VulnScan includes support for five different classes of memory corruption issues, namely Out of bounds read/write, Use after free, Type confusion, Uninitialized memory use, and Null/constant pointer dereference.
According to Krzywicki, the tool can also detect integer overflows and underflows, along with basic out of bounds accesses caused by a bad loop counter value. Use-after-free bugs can be detected even without PageHeap enabled.
MSRC already makes use of the new tool as part of their automation framework called Sonar, which was designed to process externally reported proof of concept files. The platform can both reproduce issues and perform root cause analysis by employing multiple different environments.
Microsoft also plans on including VulnScan in the Microsoft Security Risk Detection service (Project Springfield). As part of this service, it will be used to de-duplicate crashes and provide extended analysis of vulnerabilities found through fuzzing.
“Over a 10-month period where VulnScan was used to triage all memory corruption issues for Microsoft Edge, Microsoft Internet Explorer and Microsoft Office products. It had a success rate around 85%, saving an estimated 500 hours of engineering time for MSRC engineers,” Krzywicki says.
The tool uses multi-branch taint analysis, meaning that it can sequentially track all values obtained from a single instruction. VulnScan also features a queue of registers and memory addresses associated with specific positions in the execution timeline and performs taint analysis separately for each branch, so that application data flow could be recreated in full.
Code Execution Flaws Patched in Apache Tomcat
5.10.2017 securityweek Vulnerebility
Several vulnerabilities, including ones that allow remote attackers to execute arbitrary code, have been patched in recent weeks in Apache Tomcat.
Developed by The Apache Software Foundation, Apache Tomcat is an open source implementation of the Java Servlet, JavaServer Pager (JSP), Java WebSocket and Java Expression Language technologies. Tomcat is said to be the most widely used web application server, with a presence in more than 70% of enterprise data centers.
Apache Tomcat developers informed users on Tuesday that the product is affected by a remote code execution vulnerability.Apache Tomcat vulnerabilities
The flaw, tracked as CVE-2017-12617 and classified as “important” severity, has been addressed with the release of versions 9.0.1, 8.5.23, 8.0.47 and 7.0.82. All previous 9.x, 8.5.x, 8.0.x and 7.0.x versions are impacted.
The vulnerability affects systems that have the HTTP PUT method enabled and it allows attackers to upload a malicious JSP file to a targeted server using a specially crafted request. The server would then execute the code in the JSP file when the file was requested. A proof-of-concept (PoC) exploit is publicly available.
While this sounds like a serious vulnerability, in only affects systems that have the default servlet configured with the readonly parameter set to false or the WebDAV servlet enabled with the readonly parameter set to false.
“Since this feature is typically not wanted, most publicly exposed system won’t have readonly set to false and are thus not affected,” explained Peter Stöckli of Alphabot Security.
This vulnerability is very similar to CVE-2017-12615, which Apache Tomcat developers patched on September 19 with the release of version 7.0.81. CVE-2017-12617 has been described by one individual as a “bypass for CVE-2017-12615.”
The Apache Tomcat 7 update released in September also patched CVE-2017-12616, a flaw that allows an attacker to bypass security constraints and view the source code of JSPs via a specially crafted request.
Apache Tomcat vulnerabilities are less likely to be exploited in the wild, compared to Apache Struts 2 flaws, which have been used in many attacks, including to breach the systems of U.S. credit reporting agency Equifax.
There was a worm targeting Apache Tomcat servers a few years ago, but it did not leverage any vulnerabilities; it used common username and password combinations to gain access.
Greek Court Orders Extradition of Russian Over 'Bitcoin Laundering'
4.10.2017 securityweek Crime
A Greek court ruled on Wednesday that a Russian national accused of helping criminals launder billions of dollars using Bitcoin should be extradited to the United States.
Alexander Vinnik, who headed BTC-e, an exchange he operated for the cyber currency, was indicted by a US court in July on 21 charges ranging from identity theft and facilitating drug trafficking to money laundering.
"These accusations have nothing to do with me," Vinnik, 37, said after the ruling by a court in the northern city of Thessaloniki.
He said he would appeal.
"We have not yet seen the reasons for the judgement but the legal conditions for extradition have not been met," said Vinnik's lawyer Alexandros Lykourezos.
The Greek Supreme Court will name the date of the appeal proceedings within 20 days, according to a judicial source.
But the final decision on whether to extradite Vinnik will be made by the Greek justice minister.
Vinnik has been languishing in a Greek jail since his arrest on July 25 in the tourist resort of Halkidiki, near Thessaloniki.
According to US authorities, Vinnik "stole identities, facilitated drug trafficking, and helped to launder criminal proceeds from syndicates around the world".
BTC-e, founded in 2011, became one of the world's largest and most widely used digital currency exchanges, but according to the US indictment, it was "heavily reliant on criminals".
In addition, BTC-e "was noted for its role in numerous ransomware and other cyber-criminal activity," receiving more than $4 billion (3.4 billion euros) worth of Bitcoin over the course of its operation.
Vinnik was also charged with receiving funds from the infamous hack of Mt. Gox -- an earlier digital currency exchange that eventually failed, in part due to losses attributable to hacking.
The Treasury Department has fined BTC-e $110 million for "wilfully violating" US anti-money laundering laws, and Vinnik $12 million.
Treasury Secretary Steven Mnuchin hailed Vinnik's arrest, saying that cracking down on illegal uses of Bitcoin is a key goal of US regulators.
In August, Russia also requested the extradition of Vinnik, who is wanted there on separate fraud charges totalling 9,500 euros.
Vinnik rejected the accusations, but said in September he would accept extradition to his home country. The Greek judiciary will rule on Russia's request on October 11.
Attribution Hell: Cyberspies Hacking Other Cyberspies
4.10.2017 securityweek CyberSpy
Fourth-party collection makes attribution hell
Cyber espionage attribution is almost never easy, but it becomes even more complicated when threat actors hack other threat actors and they start using each other’s tools and infrastructure in their operations.
On Wednesday, at the Virus Bulletin conference in Madrid, Spain, Kaspersky researchers Juan Andrés Guerrero-Saade and Costin Raiu pointed out that cyberspies hacking other cyberspies, which they call “fourth-party data collection,” is the worst case scenario when trying to link an attack to a certain actor.
Fourth-party collection takes place when a competent entity (Agency-A) actively or passively harvests information related to a foreign intelligence service’s (Agency-B) computer network exploitation activity.
Passive collection involves harvesting data while it’s in transit between hop points in Agency-B’s infrastructure or between the victim’s systems and Agency-B’s command and control (C&C) servers. This assumes that Agency-A has what Kaspersky researchers refer to as “god on the wire” status, which means it has regular and legitimate access to national or international taps.
Active collection involves Agency-A breaking into the C&C servers or backend-collection nodes of Agency-B. This can be achieved either by using stolen credentials or by exploiting vulnerabilities to plant a backdoor on the server – the latter scenario can be more efficient as it provides persistent access without raising suspicion.
Once it gains access to Agency-B’s systems, Agency-A can adopt its tools and infrastructure to launch attacks in their name. According to Guerrero-Saade and Raiu, Kaspersky Lab has investigated several campaigns that could involve fourth-party collection.
One example involves Crouching Yeti, a Russia-linked threat actor also known as Energetic Bear and Dragonfly. The group, known for campaigns targeting industrial companies, is believed to be responsible for recent attacks on energy facilities in the U.S.
In March 2014, while analyzing one of the compromised websites used by Crouching Yeti, Kaspersky researchers noticed that the control panel web page had been modified to fingerprint the attackers as they logged in. The collected data was sent to an IP address in China, which experts believe may have been a false flag.
Another example provided by Guerrero-Saade and Raiu involves NetTraveler, a China-linked cyber espionage group that was recently observed targeting military and aerospace organizations in Russia and neighboring countries. While analyzing the group’s activities, Kaspersky researchers gained access to one of its main servers and noticed that, in addition to NetTraveler’s own scripts and software, it contained a basic backdoor that had apparently been planted by another entity.
Researchers have also found evidence that suggests the cyberspies tracked as ScarCruft may have hijacked a website used by the threat actor known as DarkHotel and leveraged it in their own operations. This made some researchers believe that ScarCruft and DarkHotel were the same threat actor, when in reality they are not, as shown by their targets, exploits and types of attacks launched.
Benefits of fourth-party collection
According to Guerrero-Saade and Raiu, the byproducts and benefits of fourth-party collection include tasking-by-proxy, code reuse, and learning from adversaries.
As an example of tasking-by-proxy, Agency-A uses its access to Agency-B to map the systems of a targeted organization Agency-B already has access to. In this scenario, the most benefits can be gained if Agency-B has a stakeholder role in the targeted region or organization.Cyber attack attribution
“Not only is Agency-A able to lower its investment threshold for its own campaign in a foreign region thanks to fourth-party collection, it may also be able to leverage another threat actor’s access to further its own access,” said the Kaspersky researchers.
As for code reuse, the experts pointed out that there can be numerous benefits to obtaining a different group’s tools and implants. They noted that a piece of code found in two different malware families does not necessarily mean they were made by the same developers; it’s possible that the developers of one tool used code that they had stolen from another threat actor.
When it comes to learning from adversaries, Kaspersky believes the best example is ProjectSauron (Strider), an espionage group that has targeted China, Russia and Europe since at least 2011.
ProjectSauron has leveraged innovations from other top-tier threat actors such as Duqu, Flame, Regin and Equation, while avoiding some of the mistakes that these groups had made. Kaspersky has also determined that ProjectSauron could be a perfect example of Agency-A, as evidence suggests it may have the ability to obtain data as it travels from one country to another without needing access to either the source or destination servers.
“These covert dynamics in the space of cyberespionage further substantiate the difficulties underlying accurate security research and the need to track threat actors continually,” the researchers said.
The complete paper, titled “Walking in Your Enemy’s Shadow: When Fourth-Party Collection Becomes Attribution Hell,” is available in PDF format.
Spanish Court Agrees to Extradite Russian Hacking Suspect to US
4.10.2017 securityweek BigBrothers
Spain's High Court said Tuesday it had agreed to a US request to extradite a Russian man accused of controlling one of the world's top generators of spam and online extortion.
Peter Levashov from Saint Petersburg, a 37-year-old who goes by a string of names, was arrested at Barcelona airport on April 7 by Spanish authorities acting on a US warrant.
US prosecutors accuse the purported hacker of controlling the Kelihos network of tens of thousands of infected computers, stealing personal data and renting the network out to others to send spam emails by the millions and extort ransoms.
His defense team had argued that the US extradition demand was "politically motivated".
Levashov, a computer specialist, had served in the Russian army and worked for President Vladimir Putin's United Russia party, according to his lawyers.
In the course of his work he had access to confidential documents which he fears authorities in the US may demand he turn over to them if he is extradited there, the lawyers had argued.
But the High Court said in its ruling that "none of the allegations relating to the political motivation" for the extradition request "has been accepted".
Levachov has three days to appeal the court's decision.
A US federal grand jury in April slapped Levachov with an eight-count indictment. The charges include fraud, identity theft and conspiracy.
Levashov could allegedly order remotely the delivery of fraudulent spam and malicious computer viruses on behalf of whoever would pay him to do so.
US officials claim he was proud of his work and advertised the ever-improving effectiveness of his spam services with a standard price list. For legal ads, he charged $200 per million spam emails. For illegal scams and phishing attacks, it was $500 per million.
To help someone with a stock manipulation, he allegedly wanted a deposit of $5,000-$10,000 to share his list of 25 million traders. He also demanded five percent of the gains made on the stock.
During any 24-hour period, prosecutors say the botnet generated and distributed more than 2,500 unsolicited spam emails that advertised various criminal schemes.
Levashov has not been tied to Russian interference in last year's US presidential election.
But his operation depended on sending spam emails that allowed hackers to penetrate the computers of the Democratic Party to steal data. That was exactly the kind of botnet service he allegedly sold to criminals.
Which are most frequently blacklisted apps by enterprises?
4.10.2017 securityaffairs Mobil
Mobile security firm Appthority published an interesting report that revealed which Android and iOS applications are most frequently blacklisted by enterprises.
The company Appthority has published an interesting report that reveals which mobile apps, both Android and iOS, are most frequently blacklisted by enterprises.
“The mobile ecosystem in an enterprise comprises apps from managed devices, BYOD and COPE. Appthority compiled a list of the top 100 apps (50 iOS and 50 Android)
based on millions of scans of devices and apps in the enterprise. Using our Mobile Threat Protection solution, we determined the most common apps and their Mobile Threat Risk Scores” states the report.
According to the company, iOS apps are mainly blacklisted because many of them leak data. Whatsapp is the most commonly blacklisted iOS app because it sends information from the device’s address book to a remote server.
Giving a close look at the list of commonly blacklisted iOS apps, we can notice the presence of Pokemon GO, the risks for this app are related to the accesses to the device’s address book and camera, and tracking of the user’s location that poses users’ privacy at risk.
Another app that is commonly blacklisted is WinZip, the reason is that the application sends SMS messages.
This type of behavior can pose a serious risk in an enterprise environment, especially if the data is transmitted without being encrypted.
Let’s see now which are commonly blacklisted apps for Android. The firth thing that is immediately verifiable is that most of the top blacklisted iOS apps are in the social networking and entertainment category, meanwhile, in the case of Android apps they are in the ‘tools’ category.
The most frequently blacklisted Android app is Poot, a tool used by its users to root their devices. Other commonly blacklisted applications are AndroidSystemTheme, Where’s My Droid Pro, Weather, and Wild Crocodile Simulator.
The Android apps have been mainly blacklisted for data leakage or because they exhibit malicious behavior.

According to the Appthority report based on the analysis of 150 apps used in enterprise environments, for 86.7% of Android apps the connections are to a server located in the United States, followed by Ireland (7.7%), Germany (2.1%) and Sweden (0.7%). In the case of iOS apps, nearly 94% of connections go to servers in the United States, followed by Ireland (3.82%), the Netherlands (0.86%) and Germany (0.86%).
“A top enterprise security concern is often the countries to which mobile data is being sent. These maps reveal the top locations to which backend servers are connecting via the top 150 mobile apps in enterprise environments.
In this quarter’s data, we see a difference in the profile of backend connections between Android and iOS. ” continues the report.
“Android developers are connecting to a wider set of geographic locations, possibly leveraging lower cost structures overseas. Popular iOS apps have a much lower percentage of connections to countries such as China, Saudi Arabia and Chile than Android apps.”
The situation is similar for iOS apps for which 94% of connections go to servers in the United States, followed by Ireland (3.82%), the Netherlands (0.86%) and Germany (0.86%).
The management of mobile devices in enterprise environments is a crucial aspect of their security posture, for this reason, it is essential to assess and evaluate the risks they bring.
Let me suggest to give a look at the report, it also includes the list of the top 100 Android and iOS applications used in enterprises, along with their risk score.
Intezer researchers link CCleaner hack to Chinese APT17 hackers
4.10.2017 securityaffairs APT
Researchers from security firm Intezer speculate that the attack was powered by nation-state actor, likely the Chinese APT17 group.
Security experts continue to investigate the recent attack against the supply chain of the popular software CCleaner.
The hackers first compromised in July a CCleaner server, then exploited it to deliver a backdoored version of the 32-bit CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191. It has been estimated that between August 15 and September 12, over 2.27 million users downloaded the tainted version of CCleaner application.
The experts at Cisco Talos team that investigated the incident, while analyzing the command-and-control (C2) server used by the threat actor discovered a lightweight backdoor module (GeeSetup_x86.dll) that was delivered to a specific list of machines used by certain organizations.
The experts discovered that the threat actor that recently compromised the supply chain of the CCleaner software to distribute a tainted version of the popular software targeted at least 20 major international technology firms with a second-stage malware.
The experts analyzed a backup of a deleted database containing information on the infected machines, they discovered that the malicious code infected a total of 1,646,536 machines (based on MAC addresses), but just 40 of them received the second-stage backdoor.
Security experts who investigated the case discovered a link with a Chinese group of hackers.
Now, researchers from Intezer speculate that the attack was powered by nation-state actor, likely Chinese hackers belonging to the Axiom group, also known as APT17 or DeputyDog.
The most popular campaign attributed to the APT17 group is the attack on the Google’s infrastructure, also known as Operation Aurora. For almost a decade the APT17 targeted government organizations in several Southeast Asian countries and the US, NGOs, defense contractors, law firms, IT firms, and mining companies.
According to malware experts at Intezer, the first payload has many similarities with the code used by the Axiom group.
“Not only did the first payload have shared code between the Axiom group and CCBkdr, but the second did as well.” reads the analysis published by Intezer.
The stage 2 payload contains the same portion of code found in APT17 malware and that isn’t included in any public repository.

“The author probably copied and pasted the code, which is what often happens to avoid duplicative efforts: rewriting the same code for the same functionality twice. Due to the uniqueness of the shared code, we strongly concluded that the code was written by the same attacker,” said Intezer.
The researchers concluded that the level of complexity of the attack suggests the involvement of a state-sponsored actor, likely the APT17 group.
“The complexity and quality of this particular attack has led our team to conclude that it was most likely state-sponsored. Considering this new evidence, the malware can be attributed to the Axiom group due to both the nature of the attack itself and the specific code reuse throughout that our technology was able to uncover,” concluded Intezer.
It's 3 Billion! Yes, Every Single Yahoo Account Was Hacked In 2013 Data Breach
4.10.2017 thehackernews Incindent
The largest known hack of user data in the history just got tripled in size.
Yahoo, the internet company that's acquired by Verizon this year, now believes the total number of accounts compromised in the August 2013 data breach, which was disclosed in December last year, was not 1 billion—it's 3 Billion.
Yes, the record-breaking Yahoo data breach affected every user on its service at the time.
Late last year, Yahoo revealed the company had suffered a massive data breach in August 2013, which affected 1 billion user accounts.
The 2013 hack exposed user account information, including names, email addresses, telephone numbers, dates of births, hashed passwords (using MD5), and, in some cases, "encrypted or unencrypted security questions and answers," Yahoo said in 2016.
At that time, Yahoo did confirm that hackers did not obtain bank account details or credit card information tied to the Yahoo accounts.
The data breach was attributed to state-sponsored hackers. Since the disclosure of the breach last year, there have been many developments in the incident.
However, the recent announcement by Yahoo makes it clear that if you had an email account on Yahoo, you were part of the infamous data breach.
Oath, the Verizon subsidiary into which Yahoo was merged, made the announcement in a filing with the SEC on Tuesday, which reads:
"Subsequent to Yahoo's acquisition by Verizon, and during integration, the company recently obtained new intelligence and now believes, following an investigation with the assistance of outside forensic experts, that all Yahoo user accounts were affected by the August 2013 theft."
The statement clearly suggests that if you had an account on Yahoo in 2013, you were affected by the data breach.
So for whatever reason you did not change your password last year after the disclosure of this massive breach, you should now change your passwords immediately and enable two-factor authentication (2FA).
Also, if you are using the same password and answers to security questions somewhere else, change them too.
Deleting Yahoo account may not be a good option to opt for, as Yahoo recycles deleted accounts after 30 days, which would allow anyone to hijack it. So, even if you don't want to use your Yahoo account, just enable 2FA and leave it.
Yahoo has also started notifying the affected account holders, requiring them to change their passwords immediately, and assuring them that the stolen data "did not include passwords in clear text, payment card data, or bank account information."
One should note that this breach is separate from the 2014 breach disclosed by Yahoo in September last year, affecting as many as 500 Million user accounts.
Yahoo attributed the 2014 breach to a state-sponsored hacking group. In March 2016, US federal prosecutors charged two Russian intelligence officers and two criminal hackers in connection with the breach.
Recently, credit reporting service Equifax also announced that an additional 2.5 million American consumers were also impacted by the massive breach the company disclosed last month, bringing the total possible victims to 145.5 million from 143 million.
Whoops, Turns Out 2.5 Million More Americans Were Affected By Equifax Breach
4.10.2017 thehackernews Vulnerebility
Equifax data breach was bigger than initially reported, exposing highly sensitive information of more Americans than previously revealed.
Credit rating agency Equifax says an additional 2.5 million U.S. consumers were also impacted by the massive data breach the company disclosed last month, bringing the total possible victims to 145.5 million from 143 million.
Equifax last month announced that it had suffered a massive data breach that exposed highly sensitive data of hundreds of millions of its customers, which includes names, social security numbers, dates of birth and addresses.
In addition, credit card information for nearly 209,000 customers was also stolen, as well as certain documents with personally identifying information (PII) for approximately 182,000 Equifax consumers.
The breach was due to a critical vulnerability (CVE-2017-5638) in Apache Struts 2 framework, which Apache patched over two months earlier (on March 6) of the security incident.
Equifax was even informed by the US-CERT on March 8 to patch the flaw, but the company failed to identified or patched its systems against the issue, Equifax ex-CEO Richard Smith said in a statement [PDF] to the House Committee on Energy and Commerce.
"It appears that the breach occurred because of both human error and technology failures," Smith said. "Equifax's information security department also ran scans that should have identified any systems that were vulnerable to the Apache Struts issue...Unfortunately, however, the scans did not identify the Apache Struts vulnerability."
In the wake of the security incident, the company hired FireEye-owned security firm Mandiant to investigate the breach, which has now concluded the forensic portion of its investigation and plans to release the results "promptly."
Mandiant said a total of 145.5 million consumers might now potentially have been impacted by the breach, which is 2.5 million more than previously estimated. However, the firm did not identify any evidence of "new attacker activity."
"Mandiant did not identify any evidence of additional or new attacker activity or any access to new databases or tables," Equifax said in a Monday press release.
"Instead, this additional population of consumers was confirmed during Mandiant's completion of the remaining investigative tasks and quality assurance procedures built into the investigative process."
The forensic investigation also found that approximately 8,000 Canadian consumers were also impacted, which is much lower than the 100,000 initially estimated figure by the credit rating and reporting firm.
However, Equifax said that this figure "was preliminary and did not materialize."
"I want to apologize again to all impacted consumers. As this important phase of our work is now completed, we continue to take numerous steps to review and enhance our cybersecurity practices," newly appointed interim CEO, Paulino do Rego Barros, Jr. said.
"We also continue to work closely with our internal team and outside advisors to implement and accelerate long-term security improvements."
Equifax, which maintains data on over 820 million consumers and over 91 million businesses worldwide, also said the company would update its own notification by October 8 for its customers who want to check if they were among those affected by the data breach.
Google Finds 7 Security Flaws in Widely Used Dnsmasq Network Software
4.10.2017 thehackernews Vulnerebility
Security researchers have discovered not one or two, but a total of seven security vulnerabilities in the popular open source Dnsmasq network services software, three of which could allow remote code execution on a vulnerable system and hijack it.
Dnsmasq is a widely used lightweight network application tool designed to provide DNS (Domain Name System) forwarder, DHCP (Dynamic Host Configuration Protocol) server, router ads and network boot services for small networks.
Dnsmasq comes pre-installed on various devices and operating systems, including Linux distributions such as Ubuntu and Debian, home routers, smartphones and Internet of Things (IoT) devices. A shodan scan for "Dnsmasq" reveals around 1.1 million instances worldwide.
Recently, Google's security team reviewed Dnsmasq and discovered seven security issues, including DNS-related remote code execution, information disclosure, and denial-of-service (DoS) issues that can be triggered via DNS or DHCP.
"We discovered seven distinct issues (listed below) over the course of our regular internal security assessments," Google's security team wrote in a blog post published on Monday.
"Once we determined the severity of these issues, we worked to investigate their impact and exploitability and then produced internal proofs of concept for each of them. We also worked with the maintainer of Dnsmasq, Simon Kelley, to produce appropriate patches and mitigate the issue."
Since the vulnerabilities have now been patched by Dnsmasq developer and maintainer Simon Kelley, Google researchers have released details and proof-of-concept (PoC) exploit code for each of the vulnerabilities.
Out of seven vulnerabilities discovered by the team, three can be exploited to perform remote code execution, three can be used in denial of service attacks, and one information leakage flaw.
Here's the List of All Vulnerabilities:
CVE-2017-14491—A DNS-based remote code execution vulnerability in Dnsmasq versions before 2.76 is marked as the most severe that allows for unrestricted heap overflows, affecting both directly exposed and internal network setups.
CVE-2017-14492—Another remote code execution vulnerability due to a DHCP-based heap overflow issue.
CVE-2017-14493—Another noteworthy DHCP-based remote code execution bug caused by a stack buffer overflow. According to Google, this flaw is trivial to exploit if it's used in conjunction with the flaw (CVE-2017-14494) mentioned below.
CVE-2017-14494—An information leak in DHCP which can be combined with CVE-2017-14493 to allow attackers bypass ASLR security mechanism and execute arbitrary code on a target system.
CVE-2017-14495—A flaw in Dnsmasq which can be exploited to launch a denial of service (DoS) attack by exhausting memory via DNS. The flaw impacts dnsmasq only if one of these options is used: --add-mac, --add-cpe-id or --add-subnet.
CVE-2017-14496—Google's Android operating system is specifically affected by this DoS issue which can be exploited by a local hacker or one who is tethered directly to the device. However, Google pointed out the service itself is sandboxed, so the risk to Android users is reduced.
CVE-2017-14497—Another DoS issue wherein a large DNS query can crash the software.
Since all the issues have already been addressed with the release of Dnsmasq 2.78, Dnsmasq users are advised to update their installations as soon as possible.
To patch your devices, make sure to upgrade packages on your system. Google has updated its affected services and released the security fixes to Android partners on 5 September 2017 in October's Android security updates.
Other affected Google services are also claimed to be updated. Kubernetes versions 1.5.8, 1.6.11, 1.7.7, and 1.8.0 have also been updated with a patched Dnsmasq.
EtherParty Breach: Another Ethereum ICO Gets Hacked
4.10.2017 thehackernews Cyber
Etherparty announced Sunday that its ICO (Initial Coin Offering) website selling tokens for a blockchain-based smart contract tool was hacked and the address for sending funds to buy tokens was replaced by a fraudulent address controlled by the hackers.
Vancouver-based Etherparty is a smart contract creation tool that allows its users to create smart contracts on the blockchain. Companies like this launch ICO to let them raise funding from multiple sources.
Etherparty said the company launched its Fuel token sale on Sunday, October 1 at 9 A.M. PDT, but just 45 minutes, some unknown attackers hacked into its ICO website and replaced the legitimate address by their own, redirecting cryptocurrencies sent by investors into their digital wallet.
According to the details released by the Etherparty team, the company detected the hack after just 15 minutes and immediately took its website down for nearly one and half hour to fix the issue, preventing more people from sending funds to the hacker's address.
By 11:35 A.M. PDT, the website was rebuilt and switched to a new web server, which also includes a pro tip on the top of it that reads: "Always check the URL and verify the contract address before sending ETH to any ICO."
Although Etherparty did not reveal details on how many funds were stolen, the company was really quick in figuring out the whole incident, taking appropriate steps, and alerting people of the hacking incident by distributing a press release.
The blockchain company has also "promised to compensate any affected contributors, with its proprietary FUEL token, prior to the temporary website shutdown at 10 A.M. PDT." The Etherparty's ICO is still ongoing and open until October 29, 2017.
"Our team has been consistently and successfully thwarting potential security issues to avoid further escalation," Etherparty Founder Lisa Cheng said.
"However, we do acknowledge and apologise for the temporary disruption to our otherwise successful launch day. Etherparty is eager and committed to compensating all affected contributors for the inconvenience."
Etherparty also said despite the hacking incident, its ICO got off to a positive start, "selling over 10,000,000 FUEL tokens in the first hour," and sold more than 400,000,000 FUEL tokens before the official launch in the pre-sale.
This incident marks the latest cyber attack on an ICO, following a theft of nearly $471,000 worth of Ethereum in cyber attack that hit Enigma Project in August, around $8.4 Million worth of Ethereum in hack that hit Veritaseum's ICO in July, and $7 Million worth of Ether tokens during the hack of Israeli startup CoinDash's ICO a week prior to Veritaseum's ICO hack.
Due to rising concerns surrounding ICOs over such hacks and scams, regulators globally are taking action against ICO fundraising. China has already announced an immediate ban on all ICO across the country.
In the United States, the Securities and Exchange Commission (SEC) has also issued an official warning about the risks of ICOs but has not made a firm move yet.
Pět kybernetických hrozeb, které musí mít každý manažer IT bezpečnosti na paměti
4.10.2017 SecurityWorld Kyber
Sítě se vyvíjí nebývalým tempem. Fyzická a virtuální prostředí, privátní a veřejné cloudy a stoupající množství IoT a koncových zařízení zásadním způsobem zvětšují prostor pro potenciální útoky. Ochrana síťových prostředí klade před manažery počítačové bezpečnosti řadu složitých problémů. Částečně je to způsobeno tím, že roste rozsah a závažnost kybernetických hrozeb, které se snaží využít nových možností k útoku.
Manažeři informační bezpečnosti si musí uvědomovat zejména to, že:
Digitální stopa podniků i jednotlivců se rychle zvětšuje, včetně nových multicloudových strategií, a tím se zvětšuje prostor pro možné útoky.
Téměř každé zařízení je potenciálním cílem a téměř cokoli lze užít k provedení kyberútoku.
Hrozby jsou inteligentnější a útoky automatizovanější, což značně ztěžuje jejich odhalení.
Společnost Fortinet nedávno identifikovala pět faktorů, které stojí za změnami kyberbezpečnostního prostředí. Každý z nich komplikuje ochranu sítí, dat a komunikace před útočníky:
1. Internet věcí
Hovoříme-li o zařízeních internetu (IoT) věcí, můžeme je rozdělit do tří základních kategorií. Do první kategorie spadají spotřebitelská IoT zařízení. Jedná se o běžné přístroje jako chytré telefony, hodinky, domácí spotřebiče a domácí zábavní systémy.
Zbývající dvě kategorie zahrnují zařízení, jako je kontrola stavu skladových zásob, sledování polohy zařízení, lékařské přístroje nebo výrobní systémy. Informace, které tato zařízení poskytují v reálné čase, zvyšují produktivitu a efektivitu, což se projevuje v podobě konkurenční výhody. V dalších prostředích dokáží tyto nástroje šetřit energii a přírodní zdroje i chránit životy. U většiny IoT zařízení nelze konfigurovat zabezpečení a není možné instalovat bezpečnostního klienta. Odborníci očekávají, že v roce 2020 čtvrtina všech počítačových útoků bude cílit na IoT.
2. Zavádění cloudu
Cloud mění způsob, jakým podniky fungují. Do několika let bude 92 % všech pracovních zátěží zpracováváno v cloudových datových centrech a pouze zbývajících 8 % zůstane v tradičních lokálních datových centrech. Cloudové služby se však nachází mimo hranice podnikové sítě, a tedy i mimo dosah tradičních bezpečnostních řešení.
Ačkoli většina poskytovatelů cloudových služeb nabízí určitou úroveň zabezpečení a smlouvy o zaručené úrovni služeb (SLA), existuje dlouhá řada dalších faktorů, které je nutné řešit, například viditelnost dat a možnost sledování jejich pohybu mezi jednotlivými cloudovými prostředími, konzistentní uplatňování bezpečnostních pravidel, ukládání dat v cloudu, centralizovaná koordinace a správa pravidel nebo schopnost reagovat na škodlivý datový provoz, jehož původ je v cloudovém prostředí, nebo který jím protéká.
3. Vyděračský software
Neuplyne den, aby se mezi novinovými titulky neobjevila zpráva o vyděračském softwaru. Denně dochází k více než 4000 vyděračských útoků a měsíčně je zasaženo 30 až 50 tisíc zařízení. Největší ztráty při napadení vyděračským softwarem přitom představují náklady na výpadek systémů. 63 % podniků, které se loni staly obětí takového útoku, uvedlo, že u nich došlo k výpadku ohrožujícímu obchodní činnost. V případě napadení zdravotnických zařízení, může výpadek ohrožovat i životy.
4. SSL
Značnou část síťového provozu tvoří důvěrná nebo citlivá data šifrovaná pomocí technologií, jako je SSL. Šifrování SSL sice chrání data protékající podnikovými sítěmi, ale zneužívají ho také kyberzločinci k ukrytí malwaru, sondování sítě a škodlivého provozu. To znamená, že je nutné otevřít a prozkoumat každou zprávu a není-li závadná, opět ji zabalit a odeslat. Tato operace je extrémně náročná na výpočetní zdroje. Při velké zátěži bezpečnostních násrojů může docházet k výraznému snížení výkonu sítě. Podniky a organizace, které pracují s aplikacemi citlivými na rychlost přenosu dat, proto buď důležitý provoz nešifrují, nebo šifrovaný provoz nekontrolují. Obě varianty však výrazně zvyšují již tak velká bezpečnostní rizika.
5. Nedostatek kvalifikovaných bezpečnostních odborníků
Podniky se potýkají nejen se stále důmyslnějšími hrozbami, ale také s nedostatkem kvalifikovaných bezpečnostních odborníků a růstem nabídky bezpečnostního softwaru. Dnes na trhu práce chybí 1 milion odborníků, v roce 2020 to podle odhadů bude o polovinu více.
Podniky se vybavují k obraně proti novým bezpečnostním hrozbám a zavádí do svých distribuovaných sítí desítky bezpečnostních řešení od různých výrobců, jejichž správa a integrace je časově náročná a pracná, přičemž většina subjektů se i bez toho potýká s nedostatkem zdrojů. Řešením je konsolidovaný přístup, kdy tradiční bezpečnostní technologie budou integrované a automatizované v rámci jednotné, úzce provázané bezpečnostní architektury, která dokáže pojmout dnešní vysoce elastické sítě a přizpůsobovat se jejich rozvoji a zároveň sledovat a chránit zařízení a data kdekoli v celém podnikovém ekosystému.
Yahoo hack – All 3 Billion Yahoo accounts were hacked in 2013 attack
4.10.2017 securityaffairs Incindent
The Yahoo hack occurred in 2013 is bigger than originally stated, Verizon confirmed that all 3 Billion Yahoo accounts were hacked in the attack.
The Yahoo hack occurred in 2013, the biggest known data breach suffered by a tech company, is bigger than originally stated.
Verizon Communications, which acquired Yahoo for $4.48 billion in June, announced on Tuesday that the 2013 Yahoo hack affected all three billion of company user accounts.
Last year, Yahoo declared that the incident affected one billion accounts, and it wasn’t the unique incident suffered by the company. In 2014, hackers accessed 500 million accounts in a separate security breach.
Attackers accessed names, birth dates, phone numbers, security questions, backup email addresses and passwords of Yahoo, a gift for hackers that could use the same data to access any other account owned by Yahoo users that share same credentials. Unfortunately, the hashed passwords were protected with a weak algorithm that was very easy to crack.
The 2013 Yahoo hack influenced the deal to acquire Yahoo in June and had a significant impact on the price of the acquisition., it’s very strange that the real extent of the incident was disclosed only now.
“That investigators did not discover the full extent of the 2013 incident before Verizon closed the deal to acquire Yahoo in June was surprising to outside cybersecurity analysts.” reported The New York Time.
According to Verizon, the support of outside forensic experts allowed it to discover that every single account was exposed in the 2013 Yahoo hack.
“Subsequent to Yahoo’s acquisition by Verizon, and during integration, the company recently obtained new intelligence and now believes, following an investigation with the assistance of outside forensic experts, that all Yahoo user accounts were affected by the August 2013 theft. While this is not a new security issue, Yahoo is sending email notifications to the additional affected user accounts. The investigation indicates that the user account information that was stolen did not include passwords in clear text, payment card data, or bank account information. The company is continuing to work closely with law enforcement.” Verizon said in a statement issued on Tuesday.
“Our investment in Yahoo is allowing that team to continue to take significant steps to enhance their security, as well as benefit from Verizon’s experience and resources,”
On August, a hacking collective based in Eastern Europe began offering Yahoo’s data for sale on the Dark Web. According to security firm InfoArmor, the Yahoo database was sold for $300,000 on the dark web.
Unfortunately, at least three different buyers, including two “prominent spammers” paid the hacker to gain the entire database and likely use it in espionage activities.
“But last August, a geographically dispersed hacking collective based in Eastern Europe quietly began offering the whole database for sale, according to Andrew Komarov, chief intelligence officer at InfoArmor, an Arizona cybersecurity firm, who monitors the dark corners of the internet inhabited by criminals, spies and spammers.” reported the New York Times. “Three buyers — two known spammers and an entity that appeared more interested in espionage — paid about $300,000 each for a complete copy of the database, he said.”
According to InfoArmor, the hackers who broke into the Yahoo database are likely based in Eastern Europe.
2013 Yahoo hack
Yahoo still considers the breaches in 2014 and 2013 as unrelated events.
It is still unclear who is behind the attack, security experts attributed the 2013 Yahoo hack to a Russian APT group.
“In March, the Department of Justice charged four men, including two Russian intelligence officers, with the 2014 breach. Investigators said the Russian government used stolen Yahoo data to spy on a range of targets in the United States, including White House and military officials, bank executives and even a gambling regulator in Nevada, according to anindictment.” added The New York Time.
“The stolen data was also used to spy on Russian government officials and business executives, federal prosecutors said. What made that theft particularly egregious, Justice Department officials said, was that the two intelligence officers who were indicted had worked for an arm of Russia’s Federal Security Service, or F.S.B., that is charged with helping foreign intelligence agencies track cybercriminals.”
Once again let me suggest Yahoo users reset their passwords and change security questions as soon as possible on every website, including ones for which they used the same Yahoo credentials.
A new Ethereum ICO was hacked, the victim is Etherparty
4.10.2017 securityaffairs Attack
The Etherparty website is the last victim in order of time of a cyber attack involving an Ethereum ICO (Initial Coin Offering).
Another hack involving an Ethereum ICO (Initial Coin Offering) made the headlines, the victim is the Etherparty website that sells tokens for a blockchain-based smart contract tool. The attackers replaced the legitimate address for sending funds to buy tokens with a fraudulent one they controlled.
Etherparty is a platform for the creation of smart contract that leverages on the blockchain.
Etherparty launched its Fuel token sale on October 1 at 9 A.M. PDT, but just 45 minutes, attackers hacked into the ICO website and replaced the wallet address, hijacking cryptocurrencies sent by investors.
According to Etherparty, its staff detected the hack after 15 minutes and in response immediately took the ICO website down for nearly one and half hour preventing more investors from sending funds to the attackers’ wallet.
The website, hosted on a new server, went online at 11:35 A.M. PDT.
The website displays the following message to investors:
“Always check the URL and verify the contract address before sending ETH to any ICO.”
At the time it is unclear the exact amount of cryptocurrencies stolen by hackers, the company ensured that it will compensate “any affected contributors, with its proprietary FUEL token, prior to the temporary website shutdown at 10 A.M. PDT.”
The blockchain company has also “promised to compensate any affected contributors, with its proprietary FUEL token, prior to the temporary website shutdown at 10 A.M. PDT.”
“One hour after the ICO officially went live, the company identified a security issue, caused by a fraudulent contribution address, and temporarily shut down the website to protect all participants.” reads the press release published by the company on Medium.
“Etherparty’s site was later restored after the issue was resolved at 11:35 A.M. PDT, after going offline for 90 minutes. The blockchain company has promised to compensate any affected contributors, with its proprietary FUEL token, prior to the temporary website shutdown at 10 A.M. PDT.

The Etherparty ICO is still ongoing and it will be open until October 29, 2017. According to the company, the ICO had a great start “selling over 10,000,000 FUEL tokens in the first hour.” The company sold more than 400,000,000 FUEL tokens before the official launch in the pre-sale.
“Our team has been consistently and successfully thwarting potential security issues to avoid further escalation,” Etherparty Founder Lisa Cheng said.”However, we do acknowledge and apologise for the temporary disruption to our otherwise successful launch day. Etherparty is eager and committed to compensating all affected contributors for the inconvenience.”
This is the last hack in order of time, below the list of previous attacks in an ICO:
$471,000 worth of Ethereum in cyber attack that hit Enigma Project
$8.4 Million worth of Ethereum during Veritaseum’s Initial Coin Offering (ICO).
$7 Million worth of Ether during the hack of startup CoinDash’s ICO.
In response to the string of incidents the US Securities and Exchange Commission (SEC) issued an official warning about the risks of ICOs, meanwhile, China has already announced a ban on all ICO across the country.
2013 Hack Hit All 3 Billion Yahoo Accounts: Company
4.10.2017 securityweek Crime
Massive Breach Hits Yahoo
A 2013 hack affected all three billion accounts at Yahoo, triple the original estimate, the online giant's parent company said Tuesday following a new analysis of the incident.
The disclosure from Verizon, which acquired Yahoo's online assets earlier this year, revised upward the initial estimate of one billion accounts affected.
The statement said the estimate is based on "new intelligence" following an investigation with the assistance of outside forensic experts into the incident in August 2013.
"While this is not a new security issue, Yahoo is sending email notifications to the additional affected user accounts," said a statement issued by Verizon's internet unit known as Oath.
"The investigation indicates that the user account information that was stolen did not include passwords in clear text, payment card data, or bank account information. The company is continuing to work closely with law enforcement."
The Yahoo breach was already believed to be the largest ever in terms of numbers of users affected. But a recently disclosed breach by credit agency Equifax is seen as potentially more damaging because of the sensitivity of the data leaked.
- Yahoo brand lives on -
Although Yahoo is no longer an independent company -- its financial holdings are in a separate company now called Altaba -- Verizon has continued to operate the Yahoo brand, including its email service and a variety of news and entertainment websites.
Oath includes the Yahoo internet operations along with those of another former internet star, AOL.
"Verizon is committed to the highest standards of accountability and transparency, and we proactively work to ensure the safety and security of our users and networks in an evolving landscape of online threats," said Chandra McMahon, the company's chief information security officer.
"Our investment in Yahoo is allowing that team to continue to take significant steps to enhance their security, as well as benefit from Verizon's experience and resources."
Yahoo, which was once one of the leading internet firms, sold its main online operations to Verizon in a deal that closed in June for $4.48 billion.
The purchase price was cut following revelations of two major data breaches at Yahoo.
In addition to the 2013 breach, Yahoo said that hackers in 2014 stole personal data from more than 500 million of its user accounts.
The US Justice Department charged two Russian intelligence operatives and a pair of hackers over one of the attacks, which had apparent twin goals of espionage and financial gain.
Canadian authorities this year arrested Karim Baratov, 22, an immigrant from Kazakhstan, on a US warrant.
US authorities allege Russian intelligence agents hired Baratov and another hacker to carry out attacks on Yahoo from 2014 to 2016.
The attacks at Yahoo and Equifax have raised troubling questions about online security and data theft which may be used for fraud or espionage purposes.
Earlier Tuesday, a White House cybersecurity aide said officials were looking at using new types of identifiers online which would eliminate the use of social security numbers, which were leaked in the Equifax incident.
"I feel very strongly that the social security number has outlived its usefulness," Rob Joyce said.
For years, social security numbers have been used by Americans to open bank accounts or establish their identity when applying for credit. But stolen social security numbers can be used by criminals to open bogus accounts or for other types of identity theft.
Enterprises Blacklist iOS Apps Due to Data Leakage: Report
4.10.2017 securityweek Android iOS
A report published on Tuesday by mobile security firm Appthority reveals which Android and iOS applications are most frequently blacklisted by enterprises.
According to data collected by Appthority, iOS apps are typically blacklisted due to the fact that they leak data. The most commonly blacklisted iOS app is WhatsApp, which has a high risk rating due to the fact that it sends information from the device’s address book to a remote server.
Another commonly blacklisted iOS app is Pokemon GO, which accesses a device’s address book and camera, and tracks the user’s location. WinZip is also banned by many organizations due to the fact that it sends SMS messages.
This type of behavior can pose a serious risk in an enterprise environment, especially if the data is transmitted without being encrypted.
A majority of the top blacklisted iOS apps are in the social networking and entertainment category, as opposed to Android where many of the blacklisted applications are tools.
The most frequently blacklisted Android app is Poot, a tool that allows users to root their devices. Other commonly banned programs are AndroidSystemTheme, Where’s My Droid Pro, Weather, and Wild Crocodile Simulator.
While some Android apps have been blacklisted for tracking the user’s location or sending data unencrypted, in most cases the problem is that they exhibit malicious behavior.
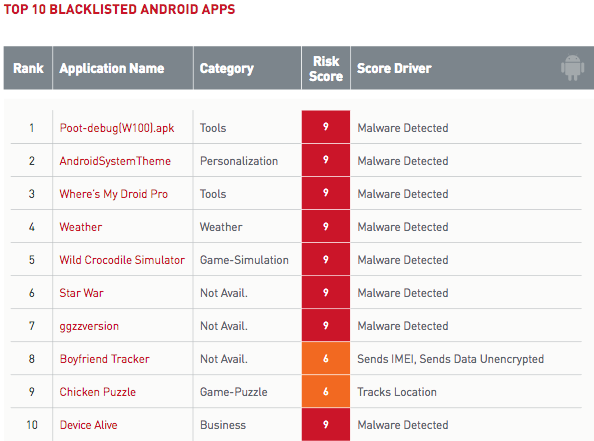
An analysis of the top 150 mobile apps found in enterprise environments showed that in the case of Android applications, 86.7% of connections are to a server located in the United States, followed by Ireland (7.7%), Germany (2.1%) and Sweden (0.7%). In the case of iOS apps, nearly 94% of connections go to servers in the United States, followed by Ireland (3.82%), the Netherlands (0.86%) and Germany (0.86%).
Appthority’s report also lists the top 100 Android and iOS applications used in enterprises, along with their risk score, which can help organizations assess the risks associated with apps commonly used by their employees.
“Enterprise security teams need to understand which mobile apps are being used, the risks they bring, and how their peers are utilizing mobile threat policies to more effectively secure corporate data,” explained Domingo Guerra, president and co-founder of Appthority. “With BYOD and COPE, many commonly used app-store approved apps are making their way into enterprises and posing risks to sensitive corporate data.”
Zero-Day flaws in 3 WordPress Plugins being exploited in the wild
3.10.2017 securityaffairs Vulnerebility
Security experts at Wordfence reported that Zero-Day vulnerabilities in three different WordPress plugins have been exploited in the wild.
Zero-day vulnerabilities in several WordPress plugins have been exploited by threat actors in the wild to hack vulnerable websites and deliver backdoors, the alarm was launched by security firm Wordfence.
The attackers have exploited three critical zero-day vulnerabilities in three distinct WordPress plugins. The flaws have been classified as critical PHP object injection issues, they affect the Appointments, Flickr Gallery, and RegistrationMagic-Custom Registration Forms plugins.
The attacks detected by Wordfence exploited the issue to create a file on targeted websites, the analysis of logs for compromised sites only showed a POST request to /wp-admin/admin-ajax.php.
“This vulnerability allowed attackers to cause a vulnerable website to fetch a remote file (a PHP backdoor) and save it to a location of their choice. It required no authentication or elevated privileges. For sites running Flickr Gallery, the attackers only had to send the exploit as POST request to the site’s root URL. For the other two plugins, the request would go to admin-ajax.php,” states the blog post published by Wordfence.

The researchers at Wordfence reported the zero-day flaws to the development team behind the flawed plugins, all of them promptly addressed the flaws with the following releases:
Appointments 2.2.2.
Flickr Gallery 1.5.3.
RegistrationMagic 3.7.9.3.
The impact of the issues is limited because the number of WordPress installs using them is modest, the experts counted 8,000 installs using RegistrationMagic, 9,000 for Appointments and 4,000 using the Flickr Gallery.
Recently Wordfence reported that 200,000 WordPress websites using the Display Widgets Plugin were impacted after it was updated to include malicious code.
The good news is that WordPress, as many other organizations, has been running a bug bounty program since May 2017 that already allowed to find many vulnerabilities in the popular CMS.
Google’s Security Research Team Identifies and Fixes 7 Vulnerabilities in Dnsmasq
3.10.2017 securityaffairs Vulnerebility
Google security experts disclosed seven distinct vulnerabilities in the Dnsmasq software package.
Regardless of what you may think of Google as a company, it is difficult to criticize their prolific and in-depth security research. The latest example is their disclosure of seven distinct issues in the Dnsmasq software package.
From the authors’ website, “Dnsmasq provides network infrastructure for small networks: DNS, DHCP, router advertisement and network boot.” In practice, the Dnsmasq code has been widely leveraged in routers, firewalls, IoT devices, virtualization frameworks and even mobile devices when you need to set up a portable hotspot. In other words, there is a lot of Dnsmasq code “in the wild” and bugs in this code could be a big deal depending on the nature of the vulnerabilities.
Of the seven issues identified by Google, three allow for Remote Command Execution, three are Denial of Service vulnerabilities, and one could result in “Information Leakage.”
Google has been working internally and with the Dnsmasq team to fix these issues. The project’s git repository has been updated with the appropriate patches, Dnsmasq v2.78 includes the patches and the October Google security patch update includes fixes for the Dnsmasq vulnerabilities. In addition, from the Google Security Blog, “Kubernetes versions 1.5.8, 1.6.11, 1.7.7 and 1.8.0 have been released with a patched DNS pod. Other affected Google services have been updated.”

Going above and beyond, Google has also submitted a patch to the Dnsmasq project which allows for Dnsmasq to be run under seccomp-bpf filtering — which provides some additional sandboxing protections should any new bugs be identified in the future.
And ensuring that you have all of the information necessary to manage your Dnsmasq risk, Google has also uploaded Python Proof of Concept code to their git repository.
You can download this code to test your environment, identify your vulnerabilities, and determine the priority to remediate based on your specific risk.
Security research and vulnerability disclosure are rarely straightforward. Timing, capabilities, and willingness to respond to issues by vendors and customers all must be considered and rarely align. Disclosing vulnerabilities increases the risk to organizations, but at the same time, it provides the necessary information to manage the risk. In this case, Google researchers and the Dnsmasq team worked together to provide all the right information and tools in a very responsible manner. Now it is up to Dnsmasq users to step up and patch where necessary.
Equifax hack affected 145.5 million individuals, 2.5M more than originally stated
3.10.2017 securityaffairs Cyber
Equifax data breach may affect 2.5 million more customers than originally stated, the overall number of exposed individuals reached 145.5 million.
Earlier this week, Equifax announced that additional 2.5 million U.S. consumers were exposed as a result of the massive data breach that affected the company in September. The credit reporting agency confirmed that a total of 145.5 million individuals have been exposed, hackers accessed names, social security numbers, dates of birth, addresses and, in some cases, driver’s license numbers and credit card numbers.
The company hired the security firm Mandiant to investigate the incident, it has already completed the forensic analysis of the affected systems.
“I was advised Sunday that the analysis of the number of consumers potentially impacted by the cybersecurity incident has been completed, and I directed that the results be promptly released,” said the appointed interim CEO, Paulino do Rego Barros, Jr. “Our priorities are transparency and improving support for consumers. I will continue to monitor our progress on a daily basis.”

According to Equifax, Mandiant was not able to find further evidence of new attacker activity or any unauthorized access to new databases or tables. and concluded that there is no evidence the attackers accessed databases located outside of the United States.
The experts have found no evidence the attackers have accessed databases located outside of the United States, personal information of only approximately 8,000 Canadian consumers was exposed. The figure is lower than previous thought, it was initially estimated that 100,000 Canadian consumers were affected.
“That number was preliminary and did not materialize,” Equifax said.
The Equifax hackers exploited a Struts 2 vulnerability, tracked as CVE-2017-5638, that was discovered in March.
In a statement to a congressional committee on Monday, former Equifax CEO Richard Smith explained that the company failed to patch the flaw in March after becoming aware of it. This admission aggravates the position of the company, according to Equifax policy, it experts would have required a patch to be applied within 48 hours.
Websites Hacked via Zero-Day Flaws in WordPress Plugins
3.10.2017 securityweek Vulnerebility
Zero-day flaws affecting several WordPress plugins have been exploited by malicious actors to plant backdoors and take control of vulnerable websites.
The attacks have been spotted by Wordfence, a company that specializes in protecting WordPress websites.
The firm’s investigation revealed that attackers had been exploiting previously unknown vulnerabilities in three WordPress plugins. The flaws, described as critical PHP object injection issues, affect the Appointments, Flickr Gallery, and RegistrationMagic-Custom Registration Forms plugins.
Attacks exploiting the zero-day vulnerability involved the creation of a file on targeted websites, but logs only showed a POST request to /wp-admin/admin-ajax.php, which made it look as if the file appeared out of nowhere, researchers said.
“This vulnerability allowed attackers to cause a vulnerable website to fetch a remote file (a PHP backdoor) and save it to a location of their choice. It required no authentication or elevated privileges. For sites running Flickr Gallery, the attackers only had to send the exploit as POST request to the site’s root URL. For the other two plugins, the request would go to admin-ajax.php,” Wordfence explained in a blog post.
The developers of the affected plugins were notified and they released updates to address the flaw. The security hole was patched in Appointments 2.2.2, Flickr Gallery 1.5.3 and RegistrationMagic 3.7.9.3.
While the vulnerability is critical, the plugins are only used by roughly 8,000 (RegistrationMagic), 9,000 (Appointments) and 4,000 (Flickr Gallery) WordPress websites.
This means that the number of potentially impacted websites is small compared to other incidents involving WordPress plugins. Wordfence reported last month that it had identified malicious functionality in a plugin present on roughly 200,000 websites.
While plugin flaws can be dangerous, it’s even more dangerous when attackers exploit zero-day or recently patched vulnerabilities affecting WordPress itself. Tens of thousands of sites were hacked within days after the existence of the weakness came to light in February.
WordPress has been running a bug bounty program since this past spring and it has so far paid out rewards totaling thousands of dollars.
Many Companies Unprepared for DNS Attacks: Survey
3.10.2017 securityweek Attack
Many companies are not prepared to deal with DNS attacks, and a quarter of the ones that have already been hit reported significant losses, according to a survey conducted by Dimensional Research on behalf of network security firm Infoblox.
Attacks on Domain Name System (DNS) services can have serious consequences, as demonstrated by the attack on Dyn last year. The attack, powered by the Mirai botnet, led to service disruptions for several major websites, including Twitter, GitHub, Etsy, Soundcloud, PagerDuty, Spotify and Airbnb.
The study from Dimensional Research and Infoblox, based on a survey of over 1,000 IT and security professionals worldwide, revealed that 3 out of 10 companies have already experienced DNS attacks and in most cases it resulted in downtime.
While more than half of the attacks resulted in a downtime of less than one hour, in 6% of cases the downtime lasted for between 8 and 24 hours, and some victims even reported service disruptions that lasted more than one day.
As for the financial losses caused by DNS attacks, 3% of respondents said they had lost more than $1 million, and nearly a quarter reported losses exceeding $100,000.
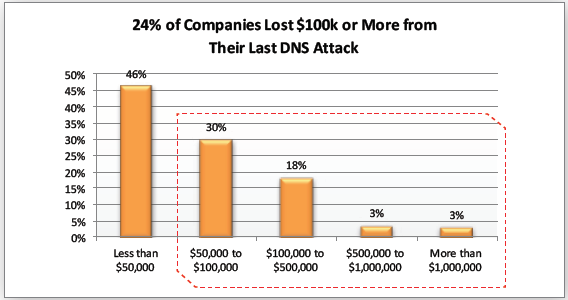
The research has not found any link between the type of DNS service used and the risk of attacks. Companies that used a cloud DNS service, a third-party service or their own service were attacked roughly the same.
According to the report, 22% of companies don’t have a backup DNS service, and 63% of them are not capable of defending against all common DNS attacks, such as hijacking, exploits, cache poisoning, protocol anomalies, reflection, NXDomain and amplification.
Nearly one-third of the 1,000 respondents said they were not confident their company could handle a DNS attack. However, the Dyn incident has had a clear impact on how DNS attacks are seen, causing one-third of firms to change their DNS security strategy.
The survey showed that only 11% of companies have security teams managing DNS, while in most cases the service is handled by IT infrastructure or operations teams. Nearly 90% of respondents complained that their DNS solutions failed to alert them of an occurring DNS attack.
“DNS attacks are likely to continue and increase, given that attacks have been extremely successful by impacting the target business 93% percent of the time. This success rate reveals that companies are vulnerable today with substandard DNS tools that are incapable of defending against common DNS attacks or properly alerting teams when they are under siege,” reads the report.
The Increasing Effect of Geopolitics on Cybersecurity
3.10.2017 securityweek Cyber
Cyber Warfare Can be Exerted by Any Nation With an Actual or Perceived Grievance Against Any Other Nation
The effect of geopolitics on cybersecurity can be seen daily – from Chinese cyber espionage to Russian attacks on the Ukraine and North Korea’s financially-motivated attacks against SWIFT and Bitcoins – and, of course, Russian interference in western elections and notably the US 2016 presidential election.
The primary cause is political mistrust between different geopolitical regions combined with the emergence of cyberspace as a de facto theater of war.
"Of course there is a connection between cybersecurity and geopolitics,” Ilia Kolochenko, CEO of High-Tech Bridge, told SecurityWeek. “Hackers are now acting as soldiers, and it's difficult to find a country that has never used a cyber weapon.”
Geopolitics, Cybersecurity and CyberwarA current example of geopolitical tensions can be seen in the recent ban on U.S. government agencies using a much-respected antivirus and endpoint protection product produced by Russian firm Kaspersky Lab. In September 2017, the U.S. Department of Homeland Security (DHS) issued a binding operational directive ordering government departments and agencies to stop using products from Kaspersky Lab, due to concerns regarding the company’s ties to Russian intelligence.
Kaspersky Lab has continually denied any inappropriate ties to the Russian intelligence services; and there is no public evidence to suggest otherwise.
“Kaspersky Lab has never helped, nor will help, any government in the world with its cyberespionage or offensive cyber efforts, and it’s disconcerting that a private company can be considered guilty until proven innocent, due to geopolitical issues,” it said in a statement.
There are many who believe that geopolitical mistrust is misplaced in the commercial world.
“Any cyber security strategy begins with trust,” comments Alan Levine, cyber security adviser to Wombat. “Can we trust the technology and services we procure? Has Kaspersky indicated even once that they can’t be trusted? Is this part of a parochial discussion about Russia equals bad? China bad? I’ve had colleagues in both countries, part of a trusted team I never had reason to second-guess.”
Nevertheless, the U.S. government’s distrust continues. It is against this background that we now examine the effect of geopolitics on cybersecurity; and ask whether there are any solutions to the problem.
Cyber as a Theater of War
Although not necessarily recognized at government level, few people involved with cybersecurity have any doubt that cyber warfare is current and ongoing. Governments are reluctant to openly acknowledge this reality for fear that recognition will require retaliation – and the big fear then is that it could escalate into kinetic warfare. Kinetic provocation leads to kinetic responses; cyber provocation tends not to. Consider, for example, the U.S. response to North Korea’s missile tests compared to the response to North Korea’s cyber attacks against Sony and SWIFT.
Cyber warfare has further advantages: the difficulty of attribution provides plausible deniability.
Attribution
Attribution is a major problem in cyberspace. Attackers can compromise servers in any part of the world. They can limit their activities to the working day of any geographical area. They can code in foreign languages; and they can reuse code snippets first used by different hacking groups. Such misdirection (false flags) is used by both nation state actors and cyber criminals.
An example of such occurred in 2015, when hackers initially thought to be the CyberCaliphate (that is, ISIS) almost destroyed the French TV5Monde television station. Attribution later turned to Fancy Bear (and by implication, the Russian state). Nevertheless, there remains no actual proof in the public domain that Fancy Bear has affiliations with the Russian Government.
Ironically, Kaspersky Lab researcher Juan Andrés Guerrero-Saade told SecurityWeek that if any organizations are equipped to accurately attribute attacks, it is the large nation signals intelligence agencies; that is, governments, because they have access to a much wider range of communications than is available to private researchers and research companies.
Governments also have access to old-fashioned spies, agents and other assets on the ground. When these resources provide physical evidence, intelligence agencies rarely acknowledge the source for fear of identifying their assets. The result is governments will sometimes make an attribution but decline to provide evidence; and it comes down to whether we trust our governments or not.
“Kaspersky is great software,” Eric O’Neill, General Counsel and Investigator at Carbon Black – and a former Investigative Specialist with the FBI – told SecurityWeek, “but I'd like to know what the U.S. Intelligence community isn't telling us.”
Plausible deniability
When it is impossible to openly prove the culprit, it is easy for the suspect to deny all knowledge. Following repeated denials of involvement in the US 2016 election hacks, Vladimir Putin finally suggested that it could have been ‘patriotic Russian hackers’.
“They got up today and read that something is going on internationally. If they are feeling patriotic they will start contributing, as they believe, to the justified fight against those speaking ill of Russia,” he said. But at the same time, he stressed that it had nothing to do with the Russian government.
This has been interpreted by some as a comment verging on a taunt: we did it; you know we did it; but you just cannot prove we did it. This is plausible deniability.
Escalation
Given the ease and success of cyber warfare attacks, it’s only natural that we see an escalation in its use. “In 2007, in Estonia,” explains Kenneth Geers, senior research scientist at Comodo and NATO Cyber Center Ambassador, “a distributed denial of service campaign primarily targeted online services. A decade later, in Ukraine, we have seen a far higher number and variety of attacks, spanning the political, diplomatic, business, military, critical infrastructure, and social media domains.”
The use of the internet as a means of disseminating political propaganda has also increased. Public awareness initially focused on Anonymous hacktivism, where the Anonymous group would deface or take down the websites of organizations or companies to which it objected.
This was followed by a series of social media account hacks by the Syrian Electronic Army (SEA), who used the accounts to disseminate pro-Assad views – often, it has to be said, through the use of humor.
This has now evolved into a complete and automated ‘fake news’ industry. In June 2017, Trend Micro published an analysis of this industry. Voter manipulation is available for a price. "Siguldin," says the report, "markets itself to be capable of manipulating almost any voting system in the Internet and bypassing security checks such as source IP address, Captcha, and authentication mechanisms in social media, SMS, and email as well as on-site registration among others."
During the run-up to the 2016 U.S. presidential elections, Fancy Bear allegedly broke into DNC servers to steal and release inflammatory emails – supposedly to manipulate the U.S. electorate into rejecting the Democrat candidate Hilary Clinton in favor of the Republican Donald Trump. The U.S. intelligence agencies have no doubt that this action was directed by the Kremlin – but, as with the accusations against Kaspersky Lab, there is no public proof offered.
While Russia is by no means the only nation engaging in cyber warfare (North Korea and Iran quickly come to mind), nevertheless Russia dominates the accusations. The technical excellence of the Russian hacking groups, whether or not affiliated to the FSB, escapes no-one: as long ago as September 2012, Trend Micro warned in the report Peter the Great vs. Sun Tzu, “East Asian hackers are not at the same skill level of maturity as their East European counterparts.”
It is against the background of rising US concern over Russian hacking that we should consider the current accusations levied against Kaspersky Lab. “I suspect that Kaspersky is merely a victim of the ongoing political fallout from the 2016 U.S. Presidential Election,” comments Geers. “This is what we must assume, absent published analysis of a demonstrable secret back door or intentionally weakened cryptography.”
The Effect of Geopolitics on Cybersecurity
The fundamental cause of cyber warfare is international political mistrust. As this escalates, so international cyber incidents increase – and there is little doubt that political mistrust is as high as it has ever been since the end of the Cold War. Sino-American tensions remain high, complicated by the unpredictability of a newly nuclear North Korea. The War on Terror that replaced the Cold War has seen the emergence of Iran as a sponsor of terror; both on the streets and in cyberspace. And Russia’s new found energy wealth sees Putin apparently determined to make the Russian Federation as powerful as the old Soviet Union.
Kinetically, the United States is probably the world’s sole Super Power; perhaps followed by China. Cyberspace, however, is a huge leveler. “What you’re seeing today is technology straining and sometimes eclipsing the ability of traditional constraints and institutions to keep them in check,” Christopher Bray, SVP/GM Consumer at Cylance Inc, told SecurityWeek. “It’s also resulting in smaller nations punching above their weight when it comes to cyber defensive and offensive capabilities, and exerting these new-found technological powers in advancing their geopolitical agendas as well as their desire to monitor their own populations to various degrees. This monitoring is always done in the interest of ‘national security’, but depending on the government in question, it can also lead into a more Orwellian direction.”
In short, cyber warfare can be exerted by any nation with an actual or perceived grievance against any other nation; and the implication of that is that it will continue to grow. This is likely to have several negative effects on cyberspace.
Balkanization
The first negative effect is already being felt: it is the balkanization of the internet. There are two aspects to this: the first is to protect the national internet from the global internet; and the second is to promote the use of locally produced products over foreign-produced, and therefore suspect, products. The Iranian, North Korean and Chinese intranets are the best known examples. China has embarked on a locally-produced product policy (China’s Cybersecurity Law) which will see 80% of large Chinese business security expenditure will be on locally produced products.
Other countries are embarking on different routes towards the same end: banning or at least deprecating the use of foreign-produced products (China’s Huawei and perhaps Russia’s Kaspersky in the U.S., for example), or using internet censorship and press restraint to limit the citizen’s access to foreign or distrusted information sources (as increasingly happens in the UK).
The problem with this effect of geopolitics is that it increases rather than decreases mistrust – and this ‘balkanization’ will likely, but not necessarily, have further negative effects on both cyber and national security.
Weakened cybersecurity
It is not at all clear that a ‘local product only’ policy can work. “Most major software products are written by personnel in numerous countries, and parent companies subcontract out much of the labor to coders whom they only know tenuously,” explains Geers. “Often, we have little choice but to use, for example, Chinese hardware, American software, French routers, and Israeli security applications… Are there spies working in many of the best-known software companies? Without a doubt. But in most cases, the companies in question do not know about them.”
Chris Roberts, chief security architect at Acalvio, agrees with this view. “Almost everything we have is brought in from somewhere else, manufactured elsewhere and/or supported elsewhere. Those microchips you have in your sensitive systems come from China… and if anyone is counting,” he added, “we (the U.S.) hold more in long term securities in Russia than they hold in us… so we’re basically shooting ourselves in our feet (with both barrels).”
The corollary is clear. Globalization market forces have produced the most efficient manner of producing high quality security products. Forced interference with that schema will likely lead to less than optimum cybersecurity. In our current example, if Kaspersky Lab’s protestation of innocence is true, then U.S. government agencies are restricted from purchasing an antivirus endpoint protection product that consistently performs at the top end of the spectrum in all third-party tests.
If cybersecurity is weakened by nationalism, then the national security that depends upon strong security products will also be weakened.
“Traditional political and military conflicts may drag us into a Cyber Cold War that will be bad both for technology and for the rule of domestic and international law,” says Geers. “The best place to see progress on cybersecurity, which is fundamentally an international problem that requires an international solution,” he continues, “is within the European Union and NATO, the world’s strongest political and military alliances. The combined law enforcement, network security, and intelligence power of 29 sovereign democracies far outweighs that of even Moscow or Beijing.”
The nationalism and ‘Britain First’ policies behind Brexit will weaken British and EU security. The full effect of a nationalist ‘America First’ policy will weaken global cybersecurity, and potentially – if it also weakens NATO – global kinetic security.
More complex business security
Concern over geopolitical influence on cybersecurity products simply makes a difficult job even more difficult. Steven Lentz, CSO at Samsung Research America, told SecurityWeek, “It's sad that we have to be aware of vendors like this, but that's the environment. Politics finds a way into everything nowadays. I just want a solution that does what it says and fits our environment. Now, with all the press of certain vendors in possible collusion with governments that may spy on the U.S., it makes it more complicated. I may like the vendor’s solution, but now I have to worry about possible malware or back doors,. It's sad.”
Martin Zinaich, ISO at the City of Tampa, doesn’t believe that the possibility of government backdoors in cybersecurity products makes an impossible job any more impossible. “If a government wanted to bury a backdoor, I have doubts that anyone would actually find it.” He also points out that the problem isn’t limited to to a nation’s own products. He notes the recent compromise of CCleaner, a product owned by Avast. Avast is a Czech-based antivirus company. There are suggestions that it was compromised by a hacking group known as Group 72; and there are further suggestions that Group 72 has affiliations with the Chinese government.
Is There a Solution?
There is no easy solution to the cybersecurity problems caused by geopolitics, although there are several proposals. The first is a set of internationally agreed ‘norms of cyber behavior’. One example was published by Microsoft in summer 2016.
The Microsoft Norms
The problem with norms is that they must first be agreed by everyone, and then obeyed by everyone before they can be called ‘norms’. “The impact of cybersecurity norms depends on whether they are implemented faithfully and whether violators are held accountable,” admits the report. However, accountability falls at the attribution problem – since it is almost impossible to prove attribution, it is impossible to hold deviant nations to account.
Microsoft’s proposed solution is an independent, international body of experts who would pronounce on attribution. “A public/private international body might be a highly constructive way to validate whether norms are being adhered to and may help create a more stable cyberspace in the future."
However, it is hard to see how this would work in practice: it is doubtful whether any state would accept responsibility just because a panel of adjudicators finds it culpable. Furthermore, each accused state would likely be supported strictly along the lines of their existing geopolitical spheres of influence.
For the foreseeable future, norms are not likely to be possible; and norms are most required when they are least achievable.
Product certification
Product certification is an approach that offers a partial solution. The idea is simple – an independent authority should analyze a hardware or software product and, if satisfied, certify it free of weaknesses or backdoors. Both government and business could then treat the product as trustworthy, regardless of source.
Over the years there have been many attempts at developing product certification schemes. In the UK, GCHQ runs a Commercial Product Assurance (CPA) scheme via the NCSC. ‘Foundation Grade’ certification ‘means the product is proven to demonstrate good commercial security practice and is suitable for lower threat environments.’ Noticeably, it doesn’t say it is free from foreign government backdoors.
A more recent initiative comes from the European Commission: a regulation proposal on ‘Information and Communication Technology cybersecurity certification’, published Sept. 13, 2017. The proposal has two key elements: that the European Union Agency for Network and Information Security (ENISA) is put on a permanent footing as Europe’s cybersecurity agency; and that ENISA should develop and control a new pan-European product certification scheme.
“ICT cybersecurity certification becomes particularly relevant in view of the increased use of technologies which require a high level of cybersecurity, such as connected and automated cars, electronic health or industrial automation control systems (IACS),” says the proposal.
The European approach has one main advantage over the UK approach – ENISA is at arms length from the politicians, and two arms lengths from the intelligence agencies. The CPA is controlled by an intelligence agency.; so while CPA may be trusted within the UK, its value to other countries may be suspect simply because of geopolitical tensions.
However, all certification schemes suffer from the same ultimate flaw: certification can never guarantee that there is no backdoor, and that one won't be added through means such as remote updates. Certifications can only affirm that none have been found.
Reverse engineering
Reverse engineering software code is probably the most effective way of detecting flaws and backdoors; but it is too time-consuming and costly to be generally effective. It can be done, however, in special circumstances; and the Huawei Cyber Security Evaluation Center (HCSEC) in Banbury, UK, is an example.
China’s Huawei telecommunications products are not universally trusted – and were banned in the U.S. in 2012 for fear of backdoors leaking information to China. The company was also banned from bidding on a contract to work on Australia’s National Broadband Network (NBN). The same is not now true in the UK, albeit by an unusual route.
In 2005, BT awarded a telecommunications contract to Huawei – but government ministers what not informed of any security concerns until 2006. By this time the Cabinet Office had been informed that blocking the contract “could have had serious diplomatic and trade implications as well as exposing the government to a potential claim for hundreds of millions of pounds in compensation from BT under a provision in the 1984 Act that makes the Government liable to offset any losses sustained in complying with the direction.”
The solution was to retrofit trust. HCSEC, commonly called The Cell, was launched in November 2010. Under GCHQ and now NCSC oversight, and with cooperation from Huawei, the UK is able to reverse engineer Huawei code looking for any flaws or backdoors.
Since 2015, the HCSEC Oversight Board – chaired by NCSC CEO Ciaran Martin – has produced annual reports. The third of these (PDF), published in July 2017, concludes “that in the year 2016-17, HCSEC fulfilled its obligations in respect of the provision of assurance that any risks to UK national security from Huawei’s involvement in the UK’s critical networks have been sufficiently mitigated. We are content to advise the National Security Adviser on this basis.”
In short, reverse engineering has retrofitted trust between the UK government and Huawei despite any geopolitical tensions that might exist between the UK and China. This is relevant to any discussion over geopolitics and Kaspersky Lab since the Russian firm has offered the same facility to the U.S. government.
In July 2017, Eugene Kaspersky told the Associated Press that the company will show its source code to the U.S. government if that gesture will foster trust. “Anything I can do to prove that we don’t behave maliciously I will do it,” he said. Kaspersky has continually reinforced his willingness to do so ever since.
Roberts believes that this could be a solution. “So, let’s go back to Russia given that’s the one that’s at the forefront of everyone’s mind.. why don’t we have a ‘gating’ system where we bring technologies in, assess them, reverse engineer them, and then when they’ve passed that ‘gate’ they can be let into the government etc? The UK does it, and as long as our geeks are more devious than their attackers we should be in good shape.”
There is no solution
Kaspersky Lab’s problem with the U.S. government is an example of the effect of geopolitics on cybersecurity – and the sad reality is that there is no way that Kaspersky Lab can prove its innocence. Consider, for example, the company’s statement on Russian law:
Russia Cyber Threats
“Regarding the Russian policies and laws being misinterpreted, the laws and tools in question are applicable to telecom companies and Internet Service Providers (ISPs), and contrary to the inaccurate reports, Kaspersky Lab is not subject to these laws or other government tools, including Russia’s System of Operative-Investigative Measures (SORM), since the company doesn’t provide communication services. Also, it’s important to note that the information received by the company, as well as traffic, is protected in accordance with legal requirements and stringent industry standards, including encryption, digital certificates and more.”
Carbon Black’s O’Neill responded, “I do not fault Kaspersky or the Federal Government for this decision. While the [DHS] directive may appear extreme, the Russia government has waged a silent war against the United States for years, most recently in attempting to influence our 2016 election.” He added, “Unfortunately for Kaspersky, our government has no good answer for whether Kaspersky could deny any request for assistance from Russian intelligence. While I expect that Kaspersky would immediately say no to any such request, the question is unfortunately not ‘would they’ but ‘could they’. I'm not certain Russian intelligence would take no for an answer.”
For so long as geopolitical tensions remain high, mistrust will prevail, and geopolitical effects on cybersecurity will increase.
Google Patches Critical Android Flaws With October 2017 Updates
3.10.2017 securityweek Vulnerebility
Google this week released its October 2017 Android patches, which address a total of 14 vulnerabilities in the mobile platform, including five rated Critical severity.
Split in two, the Android Security Bulletin—October 2017 resolves issues affecting various platform iterations, ranging from Android 4.4.4 to Android 8.0. The most severe of these could lead to arbitrary code execution or to applications being able to gain additional permissions without user interaction.
The first set of patches arrives on devices as part of the 2017-10-01 security patch level, meant to address a total of 8 vulnerabilities, including 3 Critical severity, 3 High risk, and 2 Medium severity.
With six vulnerabilities addressed in it, Media framework was the most impacted component. Three of these issues were rated Critical, all three leading to remote code execution. Additionally, a High severity elevation of privilege and two Moderate risk information disclosure bugs were addressed in it.
Other impacted components included framework, with a High severity elevation of privilege issue addressed in it, and System, with a High risk remote code execution bug patched.
The vulnerability addressed in System is CVE-2017-14496, a bug related to the Dnsmasq network services software. The release of Dnsmasq 2.78 on Monday addressed this issue and several others, including remote code execution flaws.
Google addressed six vulnerabilities as part of the 2017-10-05 security patch level, two listed as Critical severity and four listed as High risk.
The Critical bugs, one remote code execution and one elevation of privilege, along with a High risk elevation of privilege issue, impacted Qualcomm components. Two of the remaining High risk issues impacted Kernel components, while the third impacted MediaTek components. All three were elevation of privilege bugs.
In addition to the Android Security Bulletin, Google published a separate security bulletin detailing vulnerabilities addressed in Nexus and Pixel devices. As part of this month’s fixes, Google resolved issues affecting framework, Media framework, System, and Broadcom, HTC, Huawei, Kernel, Motorola, and Qualcomm components.
Fixes for a total of 38 vulnerabilities were included in the Pixel/Nexus Security Bulletin—October 2017: four High risk, 32 Medium severity, and 2 Low risk. Most of the issues were elevation of privilege and information disclosure bugs.
22 of the vulnerabilities were addressed in Qualcomm components, most of which affected WLAN. Media framework was the second most impacted component, with six vulnerabilities addressed in it, including one affecting all Android versions from 4.4.4 to 8.0.
Vendors Warn Customers of Dnsmasq Vulnerabilities
3.10.2017 securityweek Vulnerebility
Organizations, including several major tech companies, have started publishing security advisories to warn customers about serious vulnerabilities discovered by Google researchers in the Dnsmasq network services software.
Dnsmasq is a lightweight tool designed to provide DNS, DHCP, router advertisement and network boot services for small networks. The tool is used by many organizations, including in Linux distributions, networking devices, smartphones, cybersecurity appliances, and Internet of Things (IoT) devices. A scan for “Dnsmasq” via the Internet search engine Shodan reveals over 1.1 million instances worldwide.
Members of Google’s security team discovered recently that Dnsmasq is affected by seven potentially serious vulnerabilities. The flaws can be exploited via DNS or DHCP for remote code execution (CVE-2017-14491, CVE-2017-14492 and CVE-2017-14493), information leaks (CVE-2017-14494), and denial-of-service (DoS) attacks (CVE-2017-14495, CVE-2017-14496 and CVE-2017-13704).Dnsmasq vulnerabilities
The most critical vulnerability is CVE-2017-14491, a DNS-based remote code execution issue that affects both directly exposed and internal networks.
Simon Kelley, the creator and maintainer of Dnsmasq, released version 2.78 to address the vulnerabilities. This month’s security updates for Android also fix the flaws.
Some of the companies whose products use Dnsmasq have started releasing advisories to inform customers about the flaws and the availability of patches and mitigations. Kelley said some organizations received the information in advance, before the existence of the security holes was made public.
The CERT Coordination Center at Carnegie Mellon University has published a list of 99 vendors that could be affected by the Dnsmasq vulnerabilities, and some of them have confirmed that their products are impacted.
The developers of Linux distributions such as Debian, Red Hat, CentOS, Slackware and Ubuntu have already released patches.
Updates and advisories have also been made available by the creators of Kubernetes, an open-source platform for automating the deployment, scaling and management of containerized applications. Kubernetes is used, among others, by CoreOS, which has also released updates for impacted products.
Amazon Web Services (AWS) customers can use Dnsmasq to resolve hostname queries and the cloud giant has advised them to update the dnsmasq package to prevent potential attacks.
Cisco has also published an advisory, but it has not specified if any of its products are affected. The networking giant has — at least at some point — used Dnsmasq in its own products.
Software-driven cloud networking solutions provider Arista informed customers that its EOS and Cloud Vision Portal products are exposed to remote attacks exploiting CVE-2017-14491. The company has started releasing patches.
Network-attached storage (NAS) solutions provider Synology told customers that its Synology DiskStation Manager (DSM) and Synology Router Manager (SRM) products are affected. The company is working on releasing patches.
Security firm Sophos pointed out that most wireless routers and small footprint devices (i.e. IoT devices) are impacted by the flaws due to the fact that Dnsmasq is a default component in OpenWRT, a popular open source distribution for embedded devices.
Sophos’ own RED devices and cloud-managed access points are vulnerable to attacks. Patches will be made available soon.
Researchers Link CCleaner Attack to State-sponsored Chinese Hackers
3.10.2017 securityweek CyberCrime
The sophisticated supply chain attack that resulted in millions of users downloading a backdoored version of the popular CCleaner PC software utility was the work of state-sponsored Chinese hackers, according to a new report.
The attack started with the compromise of a CCleaner server in early July, which allowed hackers to inject backdoor code in two versions of the tool, namely 32-bit CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191. Between August 15 and September 12, over 2.27 million users downloaded the infected binaries.
Investigation into the attack revealed that the backdoored code was only the first stage of the intended user compromise, and that a second-stage payload had been delivered to a small number of selected targets.
After finding the backup of a deleted database containing information on the infected machines, investigators discovered that a total of 1,646,536 unique machines (based on MAC addresses) reported to the command and control (C&C) server. The stage 2 payload, however, was served to only 40 of them.
Soon after the investigation started, the security researchers looking into the incident discovered some connections to a known group of Chinese hackers, but no definite attribution was made.
Now, Intezer researchers suggest that the attack was state-sponsored and that it can indeed be attributed to Chinese hackers that are part of the Axiom group.
Also referred to as APT17 or DeputyDog, the group was previously associated with Operation Aurora, which started in 2009 and targeted companies such as Google, Adobe Systems, Juniper Networks, Rackspace, Yahoo, Symantec, Northrop Grumman, and Dow Chemical. The group specializes in supply chain attacks and Operation Aurora is considered one of the most sophisticated incidents ever.
According to Intezer, an analysis of the stage 2 payload used in the CCleaner attack provided a clear link to the Chinese hackers after the first payload (the backdoor in the installer) revealed shared code with Axiom group.
While looking at the backdoor, the researchers discovered unique code implementation “only previously seen in APT17 and not in any public repository.” Now, they reveal that the stage 2 payload contains code that is an exact match to APT17 malware seen before.
“The author probably copied and pasted the code, which is what often happens to avoid duplicative efforts: rewriting the same code for the same functionality twice. Due to the uniqueness of the shared code, we strongly concluded that the code was written by the same attacker,” Intezer’s Jay Rosenberg notes.
Analysis of the stage 2 payload revealed that one of the dropped modules is another backdoor designed to connect to a few domains. It would also connect to an IP to grab the next stage payload, which the researchers haven’t been able to identify until now.
“The complexity and quality of this particular attack has led our team to conclude that it was most likely state-sponsored. Considering this new evidence, the malware can be attributed to the Axiom group due to both the nature of the attack itself and the specific code reuse throughout that our technology was able to uncover,” Rosenberg concludes.
US Reviewing Better Tech Identifiers After Hacks: Trump Aide
3.10.2017 securityweek BigBrothers
US officials are studying ways to end the use of social security numbers for identification following a series of data breaches compromising the data for millions of Americans, a Trump administration official said Tuesday.
Rob Joyce, the White House cybersecurity coordinator, told a forum at the Washington Post that officials were studying ways to use "modern cryptographic identifiers" to replace social security numbers.
Joyce's comments come after news that some 145 million Americans may have had personal information leaked, including the important social security numbers, in a breach at Equifax, one of three big US firms which collect data for credit applications.
"I feel very strongly that the social security number has outlived its usefulness," Joyce said.
"It's a flawed system."
For years, social security numbers have been used by Americans to open bank accounts or establish their identity when applying for credit. But stolen social security numbers can be used by criminals to open bogus accounts or for other types of identity theft.
"If you think about it, every time we use the social security number we put it at risk," Joyce said.
"That is the identifier that connects you to all sort of credit and digital and information online."
He said the administration has asked officials from several agencies to come up with ideas for "a better system" which may involve cryptography.
This may involved "a public and private key" including "something that could be revoked if it has been compromised," Joyce added.
The official spoke as US lawmakers opened hearings on the Equifax breach, believed to be one of the worst because of the sensitivity of data leaked.
Former Equifax chief executive Richard Smith told a congressional panel that the breach stemmed from both human and technological error, while offering a fresh apology to consumers affected.
Equifax Breach Bigger Than Initially Reported
3.10.2017 securityweek CyberCrime
Number of U.S. Consumers Exposed by Equifax Breach Increased by 2.5 Million
Equifax on Monday afternoon said that 2.5 million additional U.S. consumers were exposed as a result of the massive data breach disclosed by the company last month. The credit reporting agency now says that a total of 145.5 million individuals have been exposed, after originally saying that 143 million had been impacted.
Data exposed as a result of cyber attack involved names, social security numbers, dates of birth, addresses and, in some cases, driver’s license numbers and credit card numbers.
According to Equifax, FireEye-owned Mandiant, which was retained by Equifax to investigate the breach, has completed the forensic portion of its investigation of the incident to finalize the consumers potentially impacted.
"I was advised Sunday that the analysis of the number of consumers potentially impacted by the cybersecurity incident has been completed, and I directed that the results be promptly released," newly appointed interim CEO, Paulino do Rego Barros, Jr. said. "Our priorities are transparency and improving support for consumers. I will continue to monitor our progress on a daily basis."
According to Equifax, Mandiant was not able to identify any evidence of additional or new attacker activity or any access to new databases or tables, and concluded that there is no evidence the attackers accessed databases located outside of the United States.
The investigation found that personal information of approximately 8,000 Canadian consumers was impacted, a figure lower than the 100,000 originally estimated by the company. “That number was preliminary and did not materialize,” Equifax said.
In a statement to a congressional committee on Monday, former Equifax CEO Richard Smith said the security team at Equifax failed to patch a vulnerability in March after becoming aware of the flaw, which according to Equifax policy, would have required a patch to be applied within 48 hours.
Equifax says that it maintains data on more than 820 million consumers and more than 91 million businesses worldwide.
Equifax Warned About Vulnerability, Didn't Patch It: Ex-CEO
3.10.2017 securityweek Vulnerebility
The security team at Equifax failed to patch a vulnerability in March after getting a warning about the flaw, opening up the credit agency to a breach affecting 143 million people, the former chief executive said Monday.
Former CEO Richard Smith, in a statement to a congressional committee released Monday, offered a timeline of the cyber attack which is believed to be the worst in terms of damaging information leaked -- including social security numbers and other sensitive data.
Smith said in prepared remarks to a House panel that the company on March 9 disseminated an internal memo warning about a software flaw identified by the government's Computer Emergency Response Team (CERT).
He added that Equifax policy would have required a patch to be applied within 48 hours and that this was not done -- but he could not explain why.
Equifax's information security department ran scans that should have identified any systems that were vulnerable but failed to identify any flaws in the software known as Apache Struts.
"I understand that Equifax's investigation into these issues is ongoing," he said in the statement.
"The company knows, however, that it was this unpatched vulnerability that allowed hackers to access personal identifying information."
Smith said he was notified of the breach on July 31, but was not aware "of the scope of this attack." He informed the company's lead director three weeks later, on August 22, and board meetings were held on the matter August 24 and 25.
Equifax, one of three major agencies which gathers data used in credit ratings for banks, has come under fire for waiting until September 7 to publicly disclose the breach, and investigators are looking into stock sales by two senior executives in August.
Smith stepped down last week amid the investigation, while indicating he would remain in a consulting capacity during the investigation, which includes a congressional hearing Tuesday.
Smith offered a fresh apology for the attack, saying in his statement: "As CEO I was ultimately responsible for what happened on my watch. Equifax was entrusted with Americans' private data and we let them down."
Imperva Report Q2 2017- Over 75% of DDoS targets were hit multiple times
3.10.2017 securityaffairs Attack
According to Imperva DDoS report, over 75% of targets were hit multiple times in Q2 2017, while the percentage was only 43.2% in the same period of 2016.
Imperva published the Global DDoS Threat Landscape for Q2 2017, the report shows an increase in the amount of persistent application layer DDoS attack over a one-year period.
According to Imperva, over 75% of targets were hit multiple times in Q2 2017, while the percentage was only 43.2% in the same period of 2016.
“We also saw an increase in the frequency of repeat application layer attacks. In total, 75.8 percent of target websites were hit by repeat assaults, the largest percentage we have on record. This was especially true for US based websites, 80.3 percent of which suffered multiple assaults. Moreover, of the 45 targets that suffered 50 or more attacks, 34 were hosted in the US.” states the report.
The researchers observed 973 application layer attacks per week in Q2
The number of application layer attacks observed each week has reached 973 in Q2 2017, it is a slight decrease respect previous quarter when Imperva observed 1,099 attacks per week.
Unfortunately, the number of mitigated network assaults decreased by 51%, falling from 296 per week in Q1 to 196 per week in Q2.
The largest network layer DDoS attack mitigated by Imperva in Q2 peaked at 350 Gbps, it was a so-called pulse wave attack that hit the target with alternating high-volume bursts, the time between each pulse is likely being used to mount a secondary assault on a different target.

The researchers observed a significant increase in attack complexity, multi-vector DDoS attacks accounted for 40.5 percent of all network layer DDoS assaults, a jump from 29 percent in the Q1.
Experts continue to observe short burst network layer attacks, 91.7% of them lasted less than an hour. Such kind of attacks was mostly launched by botnet-for-hire, pulse wave attacks and probing attempts are other principal causes behind the DDoS assaults.
The longest attack of Q2 2017 lasted for more than 147 hours, while 82.5% of attacks lasted less than 30 minutes.
“The largest application layer attack this quarter peaked at 89,134 RPS, which was significantly smaller than last quarter’s 176,393 RPS attack. This quarter’s attack, however, lasted for 48 days, more than twice as long as the one in Q1 2017.” continues the report.
During Q2 2017, 57.4% of all application layer assaults lasted for less than 30 minutes, while 7.4% of attacks lasted more than six hours and 1.7% being longer than 24 hours.
The most targeted country is the US, assaults against the U.S. accounted for 79.7% of all attacks, while China remained the top attacking county.
“China was responsible for 63 percent of attack traffic, once again topping our list of attacking countries. The US (6.4 percent) came in second. Turkey (2.1 percent), Ukraine (1.9 percent) and India (1.8 percent) respectively came in third, fourth and fifth place after each saw a significant increase in DDoS attack traffic originating from their territories.” closes the report.

UK National Lottery knocked offline by a DDoS attack on Saturday
3.10.2017 securityaffairs Attack
The UK National Lottery was knocked offline by a DDoS attack on Saturday, experts speculate the involvement of the dreaded Phantom Squad group.
On Saturday, a DDoS attack knocked offline the UK National Lottery impeding Britons to buy the tickets on the www.national-lottery.co.uk website or through its associated app.
According to DownDetector reports, thousands of angry gamblers were unable to participate the Lottery.

The National Lottery apologized to customers unable to use its online services.
Follow
The National Lottery ✔@TNLUK
We're very sorry that many players are currently unable to access The National Lottery website or app. Our 46,000 retailers are unaffected.
8:01 PM - Sep 30, 2017
205 205 Replies 25 25 Retweets 50 50 likes
Twitter Ads info and privacy
The National Lottery confirmed that the outage was caused by a major distributed denial-of-service (DDoS) attack, it hasn’t provided further details about the incident.
It is still unclear who is behind the attack and if the attackers attempted to blackmail the National Lottery.
Experts speculate that the DDoS attack was launched by the hacker group “Phantom Squad” that sent threatening emails earlier this month, warning of DDoS attacks on Saturday 30 2017 unless a ransom was paid.

Phantom Squad launched several cyber attacks against many firms in the gaming industry. In 2015 the hackers targeted the Electronic Arts and Steam, in 2016 the group and PoodleCorp hit Steam and Origin Servers.
The gaming industry is particularly exposed to DDoS attacks that could cause serious damage, and crooks are aware of such kind of exposure.
“DDoS attackers are only too aware that the online gaming and gambling industry are particularly reliant on their websites remaining accessible, and have no qualms about harnessing botnets to launch denial-of-service attacks to bring services to their knees.” reads a blog post published by ESET.
The incident demonstrates that the UK National Lottery, even if is considered a privileged target of hackers, hasn’t adequate countermeasures to mitigate the threat.
U.S. Cyber Command Launched DDoS Attack Against North Korea: Report
2.10.2017 securityweek BigBrothers
Non-destructive Cyber Attack Could be Considered a Warning to North Korean Regime
The United States Cyber Command has reportedly been engaged in offensive activity, namely a DDoS attack, against North Korea's military spy agency, the Reconnaissance General Bureau (RGB). The attack is thought to have commenced on September 22, and continued until September 30.
The attack occurred just five weeks after President Trump elevated U.S. Cyber Command to a Unified Combatant Command. At the time, Trump said, "The elevation of United States Cyber Command demonstrates our increased resolve against cyberspace threats and will help reassure our allies and partners and deter our adversaries. Through United States Cyber Command, we will tackle our cyberspace challenges in coordination with like-minded allies and partners as we strive to respond rapidly to evolving cyberspace security threats and opportunities globally."
North Korea CyberwarThe few details currently available on this DDoS attack come from a Washington Post report published Saturday. The report says that the Reconnaissance General Bureau was targeted, "by barraging their computer servers with traffic that choked off Internet access." The effects were temporary and non-destructive. "Nonetheless, some North Korean hackers griped that lack of access to the Internet was interfering with their work, according to another [anonymous] U.S. official."
The action seems to be partly in response to North Korean cyberattacks, and partly an aspect of a wide-ranging diplomatic offensive led by Secretary of State Rex Tillerson, who was in Beijing on Saturday. "What I can tell you," said a senior administration official to the Washington Post, "is that North Korea has itself been guilty of cyberattacks, and we are going to take appropriate measures to defend our networks and systems."
That this cyber attack was non-destructive and temporary suggests it could be considered more as a warning than a punishment. It is Cyber Command telling North Korea that it has its range and is capable of much stronger action. By being non-destructive it is probably hoped that it won't provoke kinetic retaliation; although it is quite likely to provoke cyber retaliation from North Korean hacking groups.
In July 2017, researchers from Recorded Future monitored internet traffic from North Korea. One of its conclusions was that "most state-sponsored activity is perpetrated from abroad." Recorded Future suggested that North Korean malicious activity most like originates from countries such as India, Malaysia, New Zealand, Nepal, Kenya, Mozambique, and Indonesia. Under these circumstances, it is unlikely that DDoSing the homeland would have much effect on the actual hackers; although it would disrupt coordinating control from the RGB.
"DDoSing the Reconnaissance General Bureau might not affect the hackers outside of North Korea directly," F-Secure's security adviser Sean Sullivan told SecurityWeek, "but it could possibly hamper communications, forcing them to use other (potentially monitored?) channels."
His colleague, Tom Van de Wiele, agreed and added, "Or as an extra bonus, to see what procedures they would go for versus what kind of panicky moves the organization makes, that [Cyber Command] could later abuse, monitor or exploit." The suggestion here is that it wasn't just a warning shot to North Korea, but an elaborate cyber reconnaissance project.
One thing not yet known is whether China had any involvement or collusion in the action. Since Tillerson was in Beijing at the time, and since all internet traffic into and out of North Korea is through China via a China Unicom link operating since 2010, it is a tempting thought. Either way, however, this potential choke point against North Korean cyber access is in the process of weakening.
Russia, on Sunday, started providing a second internet route for North Korea. The link started showing on Dyn Research peer observance tables at around 0900 UTC on October 1. Connectivity was clearly unstable for about three hours, but stabilized after that. In effect, it went live with a stable link between Russia and North Korea shortly after the U.S. Cyber Command action finished.
The route is supplied by Russian telecommunications company TransTeleCom. TransTeleCom is a subsidiary of the Russian railway operator, and lays its fiber optic lines alongside the railway tracks. A map on the company website shows a cable running to the North Korean border. It is assumed that this cable now connects Russia and North Korea via the Friendship Bridge across the Tumen River -- the only point at which the two countries connect.

The cabling has apparently been in place under an agreement between TransTeleCom and Korea Posts and Telecommunications Corp since 2009. The timing coincidence of it becoming live now could imply that opening the link between the two countries is in response to the U.S. Cyber Command attack. Alternatively, it could lend weight to the F-Secure hypothesis. If Cyber Command was aware that this would be happening, the DDoS attack could have been an attempt to provoke the Reconnaissance General Bureau into revealing channels to its overseas hacking groups prior to the Russian link giving North Korea additional communications options.
Three in Four DDoS Targets Hit Multiple Times: Imperva
2.10.2017 securityweek Attack
Amid an increase in frequency of repeat application layer distributed denial of service (DDoS) attacks during the second quarter of the year, over 75% of targets were hit multiple times, according to statistics from Imperva.
The company’s Global DDoS Threat Landscape for Q2 2017 shows an increase in the amount of persistent application layer assaults over a one-year period. Thus, while only 43.2% of targets were subjected to multiple attacks in the second quarter of 2016, the percentage increased to 75.8% during the same three-month window this year.
The number of application layer attacks observed each week has reached 973 in Q2 2017, down from 1,099 per week in the previous quarter. The number of mitigated network assaults decreased as well, falling from 296 per week in the prior quarter to only 196 per week.
The largest network layer attack that Imperva mitigated during the quarter peaked at 350 Gbps (gigabit per second) and employed a new tactic called a pulse wave attack. First described in August, this method of launching DDoS attacks can be used to pin down multiple targets with alternating high-volume bursts.
Imperva’s report also reveals that United States websites were hit the most with repeat application layer attacks. While the global percentage of targets hit multiple times is of 75.8%, it reaches 80.3% when U.S. websites are considered. Furthermore, the majority of targets that suffered 50 or more attacks were hosted in the US.
Multi-vector attacks went down significantly during the quarter, to only 21.7%, after reaching a record high 40.5% during the previous quarter. The decrease, Imperva says, can be attributed to the steep drop in 2-vector assaults, which fell from 33.5% to 9.4% quarter over quarter. 78.3% of all attacks consisted of a single vector, the company reveals.
The quarter also marked a continuation of a trend toward short burst network layer attacks (91.7% of assaults lasted less than an hour). Most of these attacks can be attributed to botnet-for-hire, but pulse wave assaults and probing attempts also added to the numbers. Overall, 82.5% of attacks lasted less than 30 minutes, while the longest attack of Q2 2017 lasted for more than 147 hours.
The largest application layer attack observed during the quarter peaked at 89,134 requests per second, which was merely half of the 176,393 RPS attack registered during the previous quarter. On the other hand, the attack lasted for 48 days, more than twice as long as the one in Q1 2017.
During Q2 2017, 57.4% of all application layer assaults lasted for less than 30 minutes, while the number of persistent attacks increased, with 7.4% of attacks lasting more than six hours and 1.7% being longer than 24 hours.
According to Imperva, the number of primitive bots grew from 90.4% in Q1 to 97.9% in Q2, which reflects an increase in non-sophisticated application layer attacks typically associated with botnet-for-hire services.
Attacks against the U.S. accounted for 79.7% of all attacks, although the country was home to only 61.4% of targets. According to Imperva’s report, 38% of DDoS targets in the U.S. were exposed to six or more DDoS attacks in the span of the quarter.
China remained the top attacking county, with more than 360,000 attacking devices and 63% of attack traffic. Imperva also reports an increase in attack traffic out of Turkey, Ukraine and India.
Google Finds Flaws in Dnsmasq Network Services Tool
2.10.2017 securityweek Vulnerebility
Google employees have identified a total of seven vulnerabilities, including ones that allow remote code execution, in the Dnsmasq network services software.
Written and maintained by Simon Kelley, Dnsmasq is a lightweight tool designed to provide DNS, DHCP, router advertisement and network boot services for small networks. Dnsmasq is used by Linux distributions, routers, smartphones and many Internet of Things (IoT) devices. A scan for “Dnsmasq” using the Internet search engine Shodan reveals over 1.1 million instances worldwide.
An analysis of Dnsmasq conducted by Google’s security team revealed seven issues, including remote code execution, information disclosure, and denial-of-service (DoS) flaws that can be exploited via DNS or DHCP.
One of the most interesting vulnerabilities found by Google researchers is CVE-2017-14491, a DNS-based remote code execution weakness that affects both directly exposed and internal networks.
Another noteworthy remote code execution bug is CVE-2017-14493, a DHCP-based issue caused by a stack buffer overflow. Experts noted that this flaw can be combined with a Dnsmasq information disclosure bug tracked as CVE-2017-14494 to bypass ASLR and execute arbitrary code.
One security hole that affects Android is CVE-2017-14496, a DoS issue that can be exploited by a local attacker or one who is tethered directly to the device. However, Google pointed out that the risk is low considering that the affected service is sandboxed.
The other vulnerabilities are CVE-2017-14492, a DHCP-based heap overflow that leads to RCE; and CVE-2017-14495 and CVE-2017-13704, both of which allow DoS attacks via DNS.
The Google Security Team has released proof-of-concept (PoC) code for each of the vulnerabilities.
The flaws have been addressed on Monday with the release of Dnsmasq 2.78. Google has also updated its affected services and provided the fixes to Android partners. This month’s Android security updates will also include the patches.
FBI Can Keep Details of iPhone Hack Secret: Judge
2.10.2017 securityweek Crime
A federal judge ruled last week that the U.S. Federal Bureau of Investigation (FBI) is not obligated to disclose the details of a hacking tool used to access data stored on an iPhone belonging to the man behind the 2015 mass shooting in San Bernardino, California.
USA Today, The Associated Press and Vice Media filed Freedom of Information Act (FOIA) requests in an effort to find out who helped the law enforcement agency hack the iPhone and how much it cost. The FBI refused to provide the information and a judge has agreed with the agency.
The FBI has managed to convince United States District Court Judge Tanya Chutkan that it should not be forced to disclose the information due to national security concerns.
The agency argued that releasing the vendor’s identity could allow adversaries to study that company’s publicly available products in an effort to find weaknesses and create better encryption technology that would prevent future attempts to use the iPhone hacking tool.
The FBI is also concerned that releasing the vendor’s name would subject the company to cyberattacks.
“Since the vendor is not as well equipped to guard against these types of attacks as is the FBI, revealing the vendor’s identity ‘risks disclosure, exploitation, and circumvention of a classified intelligence source and method’,” Judge Chutkan said in her ruling.
As for the price of hacking the San Bernardino terrorist’s iPhone, statements made by James Comey, former director of the FBI, and U.S. Senator Dianne Feinstein suggest that the agency paid roughly $1 million to have the phone unlocked.
However, the FBI did not want to disclose the exact amount, arguing that “revealing the price paid for the tool would allow adversaries to determine its usefulness and assess its nature, and would reveal where the FBI concentrates its resources in national security investigations.”
“Releasing the purchase price would designate a finite value for the technology and help adversaries determine whether the FBI can broadly utilize the technology to access their encrypted devices,” the judge said.
Hacking the iPhone of the San Bernardino shooter
In December 2015, Syed Rizwan Farook and his wife, Tashfeen Malik, killed 14 people in a mass shooting in San Bernardino, California. The attackers were later killed in a shootout with police.
Investigators believed at the time that Farook’s work-issued iPhone 5c could contain important evidence, but they could not access the data stored on it because the device was protected by a passcode and the security mechanisms implemented by Apple prevented brute-force attacks.
The FBI tried to convince a judge to force Apple to create a backdoor to the iPhone, but the tech giant refused, arguing that it would create a dangerous precedent. In the end, the law enforcement agency managed to hack Farook’s iPhone with the help of an unidentified “outside party.”
While the FBI reportedly paid roughly $1 million for the tool, which is said to work only for an iPhone 5c running iOS 9, experts later demonstrated that it could have been done via a relatively inexpensive hardware hacking technique called NAND mirroring, which the FBI dismissed in the early stages of the investigation.
Activists asked the FBI to disclose the methods used to crack the phone, but the agency said it had not obtained technical information on how the attack worked or what vulnerabilities it exploited.
Netgear Patches Over 50 Flaws in Routers, Switches, NAS Devices
2.10.2017 securityweek Vulnerebility
Netgear published more than 50 security advisories in the past two weeks to inform customers about the availability of patches for vulnerabilities affecting many of the company’s routers, switches, network-attached storage (NAS) devices, and wireless access points.
There are a total of 14 advisories describing vulnerabilities in various ReadyNAS devices, including command injections, security misconfigurations, and ten stored cross-site scripting (XSS) issues.
Netgear has also released more than a dozen advisories for remote code execution, security misconfiguration, command injection, administrator credentials disclosure, authentication bypass, stack overflow, arbitrary file read, and cross-site request forgery (CSRF) flaws affecting some of its routers. Some of the weaknesses also impact modems and DSL gateways.
The highest number of advisories released by the networking solutions provider describe problems in fully managed switches. There are 22 advisories for privilege escalation, stored and reflected XSS, denial-of-service (DoS), security misconfiguration, and directory traversal flaws.
As for wireless access points (APs), there are two advisories describing command injection vulnerabilities.
The vulnerabilities have been rated medium or high severity. No CVE identifiers have been assigned.
While a majority of the patched security holes appear to have been discovered by Netgear itself, the company has also credited Maxime Peterlin of ON-X Security for a high severity remote code execution issue in WNR2000v5 routers, Martin Rakhmanov of Trustwave for some serious router and modem flaws, and Beyond Security’s SecuriTeam Secure Disclosure program for a high severity command injection flaw in ReadyNAS Surveillance.
Netgear encourages security researchers to responsibly disclose vulnerabilities found in its products, including via a bug bounty program that offers rewards of up to $15,000 per vulnerability. The program has been running since the beginning of the year and it has resulted in payouts for more than 270 flaws, with the average bounty in the past three months at over $1,200.
However, some are still displeased with the way Netgear handles vulnerability reports. In a blog post describing the ReadyNAS Surveillance RCE flaw, Beyond Security said Netgear “acknowledging the receipt of the vulnerability information, [but] refused to respond to the technical claims, to give a fix timeline or coordinate an advisory.”
R6DB hacked. Rainbow Six Siege service’s database wiped and held for ransom
2.10.2017 securityaffairs Hacking
R6DB online gaming service that provides statistics for Rainbow Six Siege gamers, was hit by hackers who wiped its database and held the data for ransom.
The gaming industry is a privileged target for hackers, in the past several groups targeted the major company in the industry for profit and fun.
This time hackers targeted the R6DB service that provides statistics for Rainbow Six Siege players.
The hackers breached the service on September 30 and wiped the database, a PostgreSQL installation, asking the payment of a ransom.
The service went down over the weekend, in a statement released on Sunday, R6DB confirmed the attack and said that an automated bot accessed their server, wiped the archive, and left a ransom note.
In response to the incident, R6DB wipes the targeted server and completely reinstalled it. The company is currently working to restore as much of the wiped information as possible, unfortunately, some data should be definitively lost.
Follow
R6DB @Rainbow6_DB
new server is now useable!
some secondary data (past ranks, etc) might be missing for now.
updates are still running
6:13 PM - Oct 1, 2017
Replies 1 1 Retweet 14 14 likes
Twitter Ads info and privacy
Such kind of attack is not new, in the recent months, security experts reported waves of incursions in databases left open on the Internet.
Hackers targeted MongoDB, ElasticSearch, MySQL, Cassandra, Hadoop, and CouchDB installs.
In December 2016, one bad actor started compromising vulnerable MongoDB databases. Contents were downloaded and replaced by a ransom note demanding payment in exchange for a return of the missing data. By January, many hacking groups were involved and over 20,000 vulnerable MongoDB installations were compromised. With that many groups in competition, databases were compromised multiple times and ransom notes from one group were replaced by ransom notes from another group.
After this flurry of activity in the first few months of 2016, the number of MongoDB attacks quieted over the Summer. Attacks against MongoDB databases picked up again in September — at a much faster pace. “[it] took attackers from the first wave of MongoDB attacks nearly a month to rack up 45,000 ransomed DBs. The Cru3lty group managed [22,000] only last week.”
Back to the R6DB case, the database of the company was left open by the internal personnel after an unplanned migration, a company spokesman excluded that hackers kept any data.
“Due to the hectical and unplanned September migration, we didn’t have everything locked down yet, which led to this situation,” an R6DB spokesperson said. “They left a nice ransom message, but we have no reason to believe that they kept any data. On top of that our backups are useless, since they didn’t work on the Postgres codebase yet.”
R6DB said that no personal data on Rainbow Six Siege players was exposed because it doesn’t maintain such kind of info.
Gamers used R6DB to maintain statistics about their activities across time, this information was affected by the security breach.
“We basically lost all our historical data,” said R6DB. “Some profiles are gone. We can re-index them when searched for, but that’s a step we can’t do ourselves.”
“Progressions (aka historical data, aka charts) are [EXPLETIVE] They’ll fill up again over time, but the past is gone,” R6DB said. “[PC only] aliases are half-[REDACTED]. We still have some older data, but about a months worth of aliases is lost.”
Dream Market dark web drug dealer OxyMonster arrested on way to beard contest
2.10.2017 securityaffairs Crime
The Dream Market dark web drug dealer was arrested by US authorities after he traveled the US for this year’s annual World Beard and Mustache Championships.
A Dark-Web drug dealer was arrested by US authorities after he traveled the US for this year’s annual World Beard and Mustache Championships.
The French national Gal Vallerius (38) was arrested a few weeks ago while he was traveling from France to the United States of America for the competition.

According to the Miami Herald, the authorities arrested Vallerius on August 31 upon landing at Atlanta International Airport on a distribution complaint filed in Miami federal court.
“A border search of his laptop upon his arrival at Atlanta International Airport confirmed his identity as ‘OxyMonster,’ ” according to a Drug Enforcement Administration affidavit.
“Vallerius’ laptop also contained the Tor browser, which allows users to conceal their true internet protocol addresses on that network; his log-in credential for Dream Market, an eBay-type marketplace for illegal narcotics and drug paraphernalia; and $500,000 worth of bitcoin.” reported the Miami Herald,
Law enforcement searching his laptop identified Vallerius as the crook that was handling the online moniker “OxyMonster” to sell drugs on an illegal underground dark web marketplace called Dream Market.
According to Drug Enforcement Administration (DEA) affidavit, Vallerius had a crucial role in the Dream Market black market, he was an administrator, senior moderator and also a vendor.
“The Dream Market web site is specifically designed to facilitate illegal commerce by working to ensure the anonymity of its administrators, as well as the buyers and sellers who participate in commerce on the web site,” according to the DEA affidavit.
At the end of August, there were more than 94,000 listings, including drugs such as opioids, ecstasy and steroids.
The US authorities believe the man was involved in the sale of various types of drugs on Dream Market between May 2015 and August 2017. including cocaine, LSD, methamphetamine, fentanyl, and oxycodone.
The agents searching the Vallerius’s laptop discovered his log-in credential for Dream Market and found roughly $500,000 worth of bitcoins, and the overwhelming evidence, a PGP encryption key entitled OxyMonster.
The laptop also contained the Tor browser, used by the man to anonymously access the Internet and the black market on the Tor Web.
Vallerius is now expected to be transferred from Atlanta to Miami, where he will be facing a fresh conspiracy indictment.
This arrest is just the last success in order of time of law enforcement, a few months ago, Europol along with FBI, Drug Enforcement Agency and Dutch National Police dismantled two major underground markets, AlphaBay and Hansa.
Benefitted from the shutdown of its rivals, Dream Market had a total of 94,236 listings as of 29 August 2017. Now, if Vallerius is found admin of the platform, his arrest could bring an end to Dream Market as well.
Who Knows Your (Sex) Secrets? Internet of Sex Toys
1.1.0.2017 securityaffairs Vulnerebility
Security researchers with Pen Test Partners have discovered a vulnerability in the Lovense Hush sex toys, an IoT-enabled butt plug.
The recent discovery that internet connected sex toys have major security and privacy flaws should come as no shock but this does raise the issue of how to both satisfy the consumer’s needs while providing maximum protection. The most recent flaw was discovered in the Lovense Hush sex toy – an IoT-enabled butt plug – by Pen Test Partners.
The flaw involves Bluetooth Low Energy (BLE) technology and the poor security design of sex toys themselves. According to Pen Test, the Hush could be located even on a city-wide basis and can be easily hacked if not connected to a cell phone.
First, the device makes itself known on Bluetooth under the Hush BLE name, LVS-Z001. Simple scans using an ordinary cell phone or Blue tooth enabled notepad can identify such devices at a fairly good distance. The simple naming feature will clearly show that someone has the sex toy nearby even if it is connected or “paired” with a Bluetooth control device such as a personal cell phone. While this does present privacy issues with in-home use – the device may also be found on users in public.
“Recently I was in Berlin, walking with a Bluetooth discovery app, this one is Lightblue,” noted the PTP researcher. “I was genuinely surprised to see the Hush BLE name, LVS-Z001, pop up.”
“BINGO! This is genuinely the discovery of a Hush plug, ready and waiting for anyone to connect to it, on a public street.”
BLE technology also enables these toys to be located using radio triangulation techniques. It is possible with multiple trackers to identify the specific individual who may be carrying one. There are other methods such as gateway scanners placed in storefronts will trigger a hit on the device as one passes through the entrance.
This raises the likelihood that large organizations can use a combination of camera facial recognition and scanning to identify the specific individual equipped with a sex toy or if the gateway scanner is placed at a check-out/purchase register – commercial stores could identify the specific user and obtain account information along with marketing data from the device itself.
The PTP researchers used Bluefruit hardware to see the BLE command packets sent by the sextoy using Wireshark software. The PTP researchers noted this low cost hacking enabled them to see control command codes sent to the Hush device. The commands themselves can be reproduced and replayed using a simple BLE dongle available for about £5 ($7 US dollars). A hacker could send short hex character strings to command the Hush to turn on, vibrate at various levels or turn off.
The BLE connection did not require any pin entry so there was no security present to command the Hush device. This security problem with Bluetooth is not uncommon with most devices. In fact, most Bluetooth devices either have no pin or a fixed pin value of 0000 or 1234. This poor security issue is shared by a wide variety of IOT sex toys tested by PTP including the Kiiroo Fleshlight, Lelo and Lovense Nora and Max.
“Loading a configuration at the factory could allow for a unique PIN to be created for each adult toy. This is an expensive option, as devices will have to be powered up and flashed. A PIN sticker per device will also add cost.” continues PTP researchers.
There are problems inherent with Bluetooth itself that lends toward security and privacy breaches. Current Bluetooth devices will resort to an open status once the battery runs out or when they become disconnected from the controlling cell phone. Once this occurs, a hacker can establish complete control. Current Bluetooth 4.0 technology also specifies that only one cell phone can control your Bluetooth device. This protocol makes it hard to either reset the authorization or jam the connection. However, Bluetooth 4.2 is very different. The 4.2 protocol allows multiple cell phones to control a single device, complicating the situation and making it far easier for a hacker to gain illicit access.
These sex toys are bound to become more sophisticated in the near future; storing additional usage data locally, recording sessions, and as we have seen, become equipped with other sensors such as cameras and GPS location devices. The fact that they are also connection to the Internet or to devices that are Internet connected raises the specter of both security and privacy issues. The possibility that a public figure may be embarrassed is only one of a myriad of privacy concerns such as collection of mass surveillance information using these devices to track, monitor, and monetize through marketing.
While at present unlikely, there is also a danger of physical harm since similar technology is already in a number of other devices such as Bluetooth hearing aids and medical devices. Several recent research efforts have focused in on the danger posed by unsecure IOT devices and shown that they can be enabled to cause physical damage and even kill.
While manufacturers could adopt a higher level of security – this will add to both the expense and complexity controlling such devices. The Bluetooth naming convention could be altered to display a randomized string or mac address rather than the fixed name of “LVS-Z001” – thus solving the privacy issue of being detected by a wireless search. In addition, the user could be required to program the device upon first use with a secure pin, thus disabling any attempt to hack it.

Manufacturers are unlikely to address these issues since they are viewed as “overhead” and not a prime concern. In fact, as I noted, some makers may already be working with other large corporations to provide data mining on a scale never before imagined by marketing wizards. It is therefore not in the interest to reduce potential monetization but instead maximizing it with no security nor privacy.
The challenges of security and privacy in the Internet connected world have gone from the office, to the factory, to the home even into the bedroom and beyond. It is certain that the “giggle” factor of involving sex will distract some from the real problems lurking behind the weak security attached to these devices. The consumer and governmental watchdogs have yet to catch up to the risk posed to the general public. It may be uncomfortable to ask questions and raise such issues but they must be addressed before someone gets hurt.
High-severity flaw opens Siemens Industrial Switches to attacks
1.10.2017 securityaffairs Vulnerebility
Siemens has started releasing security patches to fix a high severity access control vulnerability in its industrial switches tracked as CVE-2017-12736.
The flaw was discovered by experts at Siemens and could be exploited by remote attackers to hack some of Siemens industrial communications devices.
The vulnerability affects SCALANCE X industrial Ethernet switches, and Ruggedcom switches and serial-to-ethernet devices running the Rugged Operating System (ROS).

The flaw resides in the Ruggedcom Discovery Protocol (RCDP), which allows the Ruggedcom Explorer management tool to discover and configure ROS-based devices.
According to Siemens, the RCDP is not configured properly after a device is commissioned, this allows an unauthenticated attacker who has access to the network to remotely perform administrative actions.
“RUGGEDCOM switches and serial-to-Ethernet devices are used to connect devices that
operate in harsh environments such as electric utility substations and traffic control cabinets.
SCALANCE X switches are used to connect industrial components like Programmable Logic
Controllers (PLCs) or Human Machine Interfaces (HMIs). ” states the security advisory published by Siemens.
“After initial configuration, the RCDP is still able to write to the device under certain conditions, potentially allowing users located in the adjacent network of the targeted device to perform unauthorized administrative actions,”
Siemens has rolled out the release of ROS 5.0.1 to fix the issue in Ruggedcom RSL910 devices and the version 4.3.4 to address the flaw in other ROS-based devices.
An update has also been rolled out for Ruggedcom Explorer.
Siemens hasn’t released security updates for SCALANCE XB-200, XC-200, XP-200, XR300-WG, XR-500 and XM-400 switches, users can mitigate possible attacks by manually disabling RCDP.
The ICS-CERT published a security advisory that includes NCCIC/ICS-CERT recommendations to minimize the risk of exploitation of the vulnerabilities.
Specifically, users should:
Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.
Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.
Crooks spreads backdoor devised as a security WordPress Plugin
1.10.2017 securityaffairs Vulnerebility
Experts from Sucuri discovered crooks are spreading a fake WordPress plugin dubbed X-WP-SPAM-SHIELD-PRO containing a backdoor.
A fake WordPress plugin dubbed X-WP-SPAM-SHIELD-PRO containing a backdoor was spread by crooks abusing the popularity of WP-SpamShield Anti-Spam, a WordPress antispam tool.
The WP-SpamShield Anti-Spam plugin has over 100,000 installs for this reason attackers decided to abuse it.
Researchers with Sucuri that discovered that the X-WP-SPAM-SHIELD-PRO disable other plugins, even the ones used to protect the install, steal data, and add a hidden admin account.
The X-WP-SPAM-SHIELD-PRO features legitimate structure and file names, but that all of its contents are fake.
“In the case of the X-WP-SPAM-SHIELD-PRO plugin, we identified a legitimate structure and file names. We also found legitimate, “security-related” file names in the ./includes folder.” states the blog post published by Sucuri.
“After checking each of the files, the contents turned out to be simple hacktools serving the purpose of the attacker.”
The experts used as an example the class-social-facebook.php, while the name suggests it was used by the author to implements defense countermeasures against threats via Facebook, it was designed to list all of the active plugins and disable them.
The code includes other files, class-term-metabox-formatter.php and class-admin-user-profile.php, the first one contains the code to grab the WordPress version, and the second one provides a list of all admin users in the WordPress install.
The fake plugin also includes a file called plugin-header.php, used by crooks designed to add an additional administrator account – mw01main – to the WordPress installation.
“The plugin-header.php file contains code to add an additional administrator account – mw01main – to your site. It also contains code to delete itself.” states Sucuri.
“This is the first time during this research investigation that we’ve noticed a reference to some external site – mainwall.org. There’s a clearly visible username, password and the email used for the new administrator account which an attacker could use login to your site. Nasty.”

Further analysis of the fake plugin revealed the presence of a code that notifies attackers each time an administrator activated it on the website.
The fake plugin implements a custom sendPost() function that is used to collect information from the WordPress install and send it to the attackers.
“This function collects information about the user, password, current site this plugin is active on, server IP address, and few other pieces of sensitive data. This information is then sent back to their server using the POST method, making it difficult to detect within your site logs.” continues the analysis.
The author of the fake plugin also implemented an update feature that allows the attackers to upload any file to the site. The attackers could upload a ZIP archive, unpack it to the system, and then delete the archive.
The malicious X-WP-SPAM-SHIELD-PRO plugin was not available in the WordPress repository, WordPress administrators have to install plugins only from official and trusted repositories.
Millions of Macs open to EFI Firmware Hacks even if they are up-to-date
1.10.2017 securityaffairs Apple
A group of researchers with Duo Security demonstrated that millions of Up-to-Date Apple Macs are vulnerable to EFI Firmware attacks.
In 2015, the security researcher Trammell Hudson demonstrated at the Chaos Computer Congress in Hamburg, how it is possible to infect Apple Mac PCs exploiting the Thunderbolt port.
Since the disclosure of the attack against the Apple firmware, the company has regularly bundled EFI updates with macOS security and software updates to avoid its exploitation.
Now researchers at Duo Security have discovered that many macOS security and software updates are incomplete exposing millions of Up-to-Date Macs to EFI Firmware hacks.
The researchers analyzed over 73,000 Macs systems and discovered that a worrisome number of Apple Mac computers either fails to install security patches for EFI firmware vulnerabilities or doesn’t install security updates at all.
“We then gathered OS version, build number, Mac model version, and EFI firmware version from over 73,000 real-world Mac systems deployed in organizations across a number of industry verticals to give us a large dataset of the Apple EFI environments that are in production use.” states the report published by the experts.
“Our research has shown there are considerable discrepancies in how Apple provides security support to its EFI firmware as compared to how they support the security of the OS and software.”
According to the research paper, 4.2 percent of machines in production environments are running EFI versions different from what they should be running.
“On average, 4.2% of real-world Macs used in the production environments analyzed are running an EFI firmware version that’s different from what they should be running, based on the hardware model, the OS version, and the EFI version released with that OS version.” states the research paper.
The situation is worse for certain Mac models, such as the iMac 21.5 inch of late 2015 for which experts observed a 43 percent discrepancy. The experts noticed that 16 combinations of Mac hardware and OSes had never received any EFI firmware update during the lifetime of the 10.10 to 10.12 versions of OS X/macOS.
The situation is, even more, critic because Apple does not even warn its customers of the failed EFI update process or technical problems resulting in millions of Macs users vulnerable to cyber attacks.
Thunderstrike EFI firmware attacks
Apple uses Intel-designed Extensible Firmware Interface (EFI) for Mac computers that runs before macOS boots up and has higher-level privileges. An EFI malware could be exploited by attackers to gain full control of the device without being detected.
“In addition to the ability to circumvent higher level security controls, attacking EFI also makes the adversary very stealthy and hard to detect (it’s hard to trust the OS to tell you the truth about the state of the EFI); it also makes the adversary very difficult to remove – installing a new OS or even replacing the hard disk entirely is not enough to dislodge them.” states the Duo researchers.
You will be surprised by knowing the numbers for some specific Mac models—43% of the analysed iMac models (21.5″ of late 2015) were running outdated, insecure firmware, and at least 16 Mac models had never received any EFI firmware updates when Mac OS X 10.10 and 10.12.6 was available.

“For the main EFI vulnerabilities that were acknowledged by Apple and patched during the time of our analysis, there were surprising numbers of models of Macs that received no update to their EFI despite continuing to receive software security updates,” Duo researchers say.
It is very disconcerting to know that even if users are running the latest version of macOS and have installed all the security updates issued by the tech giant they are still exposed to cyber attack.
“Even if you’re running the most recent version of macOS and have installed the latest patches that have been released, our data shows there is a non-trivial chance that the EFI firmware you’re running might not be the most up-to-date version,”
Duo experts also found 47 models that were running 10.12, 10.11, 10.10 versions of macOS and did not receive the EFI firmware update that addressed the known vulnerability, Thunderstrike 1.
While 31 models did not receive did not receive an EFI patch for Thunderstrike 2.
The Thunderstrike attacks were first exploited by the National Security Agency (NSA), agents. According to documents belonging to the WikiLeaks Vault 7 data dumps, the agency developed the “Sonic Screwdriver” project, which is a “mechanism for executing code on peripheral devices while a Mac laptop or desktop is booting”allowing an attacker to boot its attack software for example from a USB stick “even when a firmware password is enabled”.
The technique allows a local attacker to boot its hacking tool using a peripheral device (i.e. USB stick, screwdriver),“even when a firmware password is enabled” on the device. This implied that the Sonic Screwdriver allows attackers to modify the read-only memory of a device, the documents revealed that malware is stored in the Apple Thunderbolt-to-Ethernet adapter.
More details on the research are available in the Duo Labs whitepaper, Mac users can check if they are running the latest version of EFI for their systems by using free open-source tool EFIgy.
Phish For The Future – spear-phishing attacks target Internet Freedom Activists
1.10.2017 securityaffairs Phishing
EFF published the report on “Phish For The Future,” an advanced persistent spearphishing campaign targeting Freedom Activists.
The Electronic Frontier Foundation (EFF) confirmed that a sophisticated spear-phishing campaign targeted the employees of Internet freedom NGOs “Free Press” and “Fight for the Future”
The EFF revealed that it is aware at least 70 attempts to steal the credentials of net neutrality activists between July 7 and August 8.
Hackers attempted to gather credentials associated with online services, including Google, Dropbox, and LinkedIn, and at least in one case, they succeeded.
The hackers compromised an account and used to launch spear-phishing attacks against other targets.
According to the experts, the campaign was managed by a single threat actor, they pointed out that attackers did not use malware to targets victims.
“This report describes “Phish For The Future,” an advanced persistent spearphishing campaign targeting digital civil liberties activists at Free Press and Fight For the Future. Between July 7th and August 8th of 2017 we observed almost 70 spearphishing attempts against employees of internet freedom NGOs Fight for the Future and Free Press, all coming from the same attackers.” reads the report published by EFF.
The attackers used various social engineering technique to trick victims into providing their credentials.
In some cases, attackers used fake LinkedIn notification messages containing links to Gmail phishing sites.

“Another attack pretended to be from a target’s husband, sharing family photos; the email was forged to include the husband’s name. ” continues the report.
In another attempt, the attackers sent messages related to a YouTube aggressive and hateful comment for a real YouTube video that the target had uploaded.
Who is behind the attack?
The EFF only pointed out that the threat actor appears to be working from an office, with Saturday and Sunday off, during working hours associated with the UTC+3 – UTC+5:30 timezones. This circumstance suggests that attackers may be located in Eastern Europe, Russia, part of the Middle East, or India, but Saturday and Sunday are not weekend days in many Middle Eastern countries.
Unfortunately, the IP from which the one compromised account was accessed did not provide any clues as it was associated with a VPN service.
“The sophistication of the targeting, the accuracy of the credential phishing pages, the working hours, and the persistent nature of the attacks seem to indicate that the attackers are professionals and had a budget for this campaign,” continues the analysis.
Cyber criminals or state-sponsored hackers?
Researchers with the EFF don’t believe the spear-phishing campaign against Freedom Activists has been carried out by a nation-state actor.
“Although this phishing campaign does not appear to have been carried out by a nation-state actor and does not involve malware, it serves as an important reminder that civil society is under attack. It is important for all activists, including those working on digital civil liberties issues in the United States, to be aware that they may be targeted by persistent actors who are well-informed about their targets’ personal and professional connections,” the EFF said.
Millions of Up-to-Date Apple Macs Remain Vulnerable to EFI Firmware Hacks
30.9.2017 thehackernews Apple
"Always keep your operating system and software up-to-date."
This is one of the most popular and critical advice that every security expert strongly suggests you to follow to prevent yourself from major cyber attacks.
However, even if you attempt to install every damn software update that lands to your system, there is a good chance of your computer remaining outdated and vulnerable.
Researchers from security firm Duo Labs analysed over 73,000 Macs systems and discovered that a surprising number of Apple Mac computers either fails to install patches for EFI firmware vulnerabilities or doesn't receive any update at all.
Apple uses Intel-designed Extensible Firmware Interface (EFI) for Mac computers that work at a lower level than a computer's OS and hypervisors—and controls the boot process.
EFI runs before macOS boots up and has higher-level privileges that, if exploited by attackers, could allow EFI malware to control everything without being detected.
"In addition to the ability to circumvent higher level security controls, attacking EFI also makes the adversary very stealthy and hard to detect (it’s hard to trust the OS to tell you the truth about the state of the EFI); it also makes the adversary very difficult to remove—installing a new OS or even replacing the hard disk entirely is not enough to dislodge them," Duo researchers say.
What's worse? In addition to neglecting to push out EFI updates to some systems, Apple does not even warn its users of the failed EFI update process or technical glitch, leaving millions of Macs users vulnerable to sophisticated and advanced persistent cyber attacks.
On average, Duo said 4.2% of 73,324 real-world Macs used in the enterprise environments were found running a different EFI firmware version they should not be running—based on the hardware model, the operating system version, and the EFI version released with that OS.
You will be surprised by knowing the numbers for some specific Mac models—43% of the analysed iMac models (21.5" of late 2015) were running outdated, insecure firmware, and at least 16 Mac models had never received any EFI firmware updates when Mac OS X 10.10 and 10.12.6 was available.
"For the main EFI vulnerabilities that were acknowledged by Apple and patched during the time of our analysis, there were surprising numbers of models of Macs that received no update to their EFI despite continuing to receive software security updates," Duo researchers say.
"Even if you’re running the most recent version of macOS and have installed the latest patches that have been released, our data shows there is a non-trivial chance that the EFI firmware you’re running might not be the most up-to-date version,"
Duo also found 47 models that were running 10.12, 10.11, 10.10 versions of macOS and did not receive the EFI firmware update with patches to address the known vulnerability, Thunderstrike 1.
While 31 models did not get the EFI firmware patch addressing the remote version of the same flaw, Thunderstrike 2.
The Thunderstrike attacks, initially developed by the National Security Agency (NSA), were also exposed in the WikiLeaks Vault 7 data dumps, which also mentioned the attack relies on the outdated firmware.
More details on the vulnerable Mac models can be found in the Duo Labs research report.
According to the researchers, their research was focused on the Mac ecosystem as Apple is in a somewhat unique position of controlling the full stack, but it can be widely deployed.
"However, we are of the belief that the main issues we have discovered are generally relevant across all vendors tasked with securing EFI firmware and are not solely Apple," the researchers said.
Enterprises with a large number of Mac computers should review their models outlined in the Duo Labs whitepaper, "The Apple of Your EFI: Findings From an Empirical Study of EFI Security," to see if their models are out-of-date.
Mac users and administrators can also check if they are running the latest version of EFI for their systems by using free open-source tool EFIgy, which will soon be made available by the company.
Amazon's Whole Foods Market Suffers Credit Card Breach In Some Stores
29.9.2017 thehackernews Incindent
Another day, another data breach. This time Amazon-owned grocery chain has fallen victim to a credit card security breach.
Whole Foods Market—acquired by Amazon for $13.7 billion in late August—disclosed Thursday that hackers were able to gain unauthorized access to credit card information for its customers who made purchases at certain venues like taprooms and full table-service restaurants located within some stores.
Whole Foods Market has around 500 stores in the United States, United Kingdom, and Canada.
The company did not disclose details about the targeted locations or the total number of customers affected by the breach, but it did mention that hackers targeted some of its point-of-sale (POS) terminals in an attempt to steal customer data, including credit details.
The company also said people who only shopped for groceries at Whole Foods were not affected, neither the hackers were able to access Amazon transactions in the security breach.
Instead, only certain venues such as taprooms and table-service restaurants located within its stores—which use a separate POS system—were impacted.
Whole Foods Market has hired a cybersecurity firm to help it investigate the credit card breach and contacted law enforcement authorities of this incident.
"When Whole Foods Market learned of this, the company launched an investigation, obtained the help of a leading cybersecurity forensics firm, contacted law enforcement, and is taking appropriate measures to address the issue," Whole Foods said in a statement on its website.
The company is also encouraging its customers to closely monitor their credit card statements and "report any unauthorized charges to the issuing bank."
According to Whole Foods Market, none of the affected systems being investigated are, in any way, connected to Amazon.com systems.
Whole Foods Market has become the latest of the victim of the high-profile cyber attack. Earlier this month, Global tax and auditing firm Deloitte suffered a cyber attack that resulted in the theft of private emails and documents of some of its clients.
Also last week, the U.S. Securities and Exchange Commission (SEC) also disclosed that unknown hackers managed to hack its financial document filing system and illegally profited from the stolen information.
Last month, credit rating agency Equifax publicly disclosed a breach of its systems that exposed personal details, including names, addresses, birthdays and Social Security numbers, of potentially 143 million US customers.
Dark-Web Drug Dealer Arrested After He Travelled US for World Beard Championships
29.9.2017 thehackernews Crime
United States authorities arrested suspected dark web drug kingpin late last month while he was travelling from his base in France to the United States of America for this year’s annual World Beard and Mustache Championships.
Gal Vallerius, a 38-year-old French national, was travelling to Austin, Texas, for the competition but was caught by U.S. authorities on August 31 upon landing at Atlanta International Airport on a distribution complaint filed in Miami federal court, The Miami Herald reported Tuesday.
Authorities confirmed Vallerius' identity to the online moniker "OxyMonster," which was previously used to sell drugs on an illegal underground dark web marketplace called Dream Market by searching his laptop that the brown-beard contestant carried with him.
Alleged Moderator/Admin Of Dark-Web Dream Market
According to Drug Enforcement Administration (DEA) affidavit filed in September, Vallerius was an administrator, senior moderator and vendor on Dream Market, an eBay-type marketplace for illegal narcotics and drug paraphernalia.
Vallerius was suspected of openly advertising and selling drugs including cocaine, LSD, methamphetamine, fentanyl and oxycodone, on Dream Market between May 2015 and August 2017.
After searching his laptop, officials confirmed Vallerius' log-in credential for Dream Market and uncovered roughly $500,000 worth of bitcoins—the currency used to complete the transactions—and a PGP encryption key entitled OxyMonster.
Vallerius' laptop also contained the Tor browser, which lets users hide their true internet protocol (IP) addresses, allowing them to operate anonymously on the network.
According to the Miami Herald, the suspect is now expected to be transferred from Atlanta to Miami, where he will be facing a fresh conspiracy indictment that carries up to life in federal prison.
U.S. authorities have been cracking down on dark web marketplaces. A few months back, Europol along with FBI, DEA (Drug Enforcement Agency) and Dutch National Police disrupted two major underground markets, AlphaBay and Hansa.
Benefitted from the shutdown of its rivals, Dream Market had a total of 94,236 listings as of 29 August 2017. Now, if Vallerius is found admin of the platform, his arrest could bring an end to Dream Market as well.
Hackers Exploiting Microsoft Servers to Mine Monero - Makes $63,000 In 3 Months
29.9.2017 thehackernews Hacking
Mining cryptocurrencies can be a costly investment as it takes a monstrous amount of computing power, and thus hackers have started using malware that steals computing resources of computers it hijacks to make lots of dollars in digital currency.
Security researchers at security firm ESET have spotted one such malware that infected hundreds of Windows web servers with a malicious cryptocurrency miner and helped cybercriminals made more than $63,000 worth of Monero (XMR) in just three months.
According to a report published by ESET today, cybercriminals only made modifications to legitimate open source Monero mining software and exploited a known vulnerability in Microsoft IIS 6.0 to secretly install the miner on unpatched Windows servers.
Although ESET's investigation does not identify the attackers, it reports that the attackers have been infecting unpatched Windows web servers with the cryptocurrency miner since at least May 2017 to mine 'Monero,' a Bitcoin-like cryptocurrency.
The vulnerability (CVE-2017-7269) exploited by the attackers was discovered in March 2017 by Zhiniang Peng and Chen Wu and resides in the WebDAV service of Microsoft IIS version 6.0—the web server in Windows Server 2003 R2.
Therefore, hackers are only targeting unpatched machines running Windows Server 2003 to make them part of a botnet, which has already helped them made over $63,000 worth of Monero.
Since the vulnerability is on a web server, which is meant to be visible from the internet, it can be accessed and exploited by anyone. You can learn more about the vulnerability here.
The newly discovered malware mines Monero that has a total market valuation of about $1.4 billion, which is far behind Bitcoin in market capitalisation, but cybercriminals’ love for Monero is due to its focus on privacy.
Unlike Bitcoin, Monero offers untraceable transactions and is anonymous cryptocurrency in the world today.
Another reason of hackers favouring Monero is that it uses a proof-of-work algorithm called CryptoNight, which suits computer or server CPUs and GPUs, while Bitcoin mining requires specific mining hardware.
However, this is not the first time when analysts have spotted such malware mining Monero by stealing computing resources of compromised computers.
In mid-May, Proofpoint researcher Kafeine discovered cryptocurrency mining malware, called 'Adylkuzz,' which was using EternalBlue exploit—created by the NSA and dumped last month by the Shadow Brokers in April—to infect unpatched Windows systems to mine Monero.
A week before that, GuardiCore researchers discovered a new botnet malware, dubbed BondNet, that was also infecting Windows systems, with a combination of techniques, for primarily mining Monero.
Mac Firmware Updates Are Failing and Leaving Systems Vulnerable: Report
29.9.2017 securityweek Apple
There is a discrepancy between the frequency and thoroughness of Apple's Mac Operating System (OS X) and app security updates, and updates for the underlying firmware (EFI) on Mac computers. Researchers have found that on a sample of 73,324 Macs deployed in production settings, 4.2% are running outdated EFI -- leaving them potentially vulnerable to new exploits.
EFI is the modern form of BIOS -- it's where the instructions for getting the system successfully started are kept. As such, it occupies privilege level ring -2 and is responsible for loading the operating system from ring 0. In short, instructions on the firmware sit below the operating system and below all of the applications (including security software) that run on top of the operating system. Any malware that can be installed into this firmware is virtually invisible and almost impossible to clear.
The discrepancy between EFI and OS updates was discovered by Duo Security and announced in a report (PDF) and blog published today. The report will be presented by authors Rich Smith and Pepijn Bruienneat at this year's ekoparty conference in Buenos Aires.
The research started from the hypothesis that firmware and software updates do not necessarily proceed in step. Macs were chosen, say the authors in their blog post, because "Apple is in a somewhat unique position of controlling the full stack from hardware, through firmware, OS, and all the way up to application software and can be considered widely deployed." This made the research simpler, but they stress that they do not believe the issues they discovered are unique to Apple.
Since 2015, Apple has released EFI updates contained within its larger OS and security updates. This meant that the researchers could examine the current operating system build on a Mac, and know what firmware version should also be installed. "The comparison and observed discrepancies between these two datasets," explain the authors, "gives us a way to look at the deviance between the expected state of a Mac’s EFI and the actual state as we observed from systems in real-world use."
The researchers then analyzed more than 70,000 Macs being used in production environments and found that 4.2% were running firmware versions pre-dating the versions that could have been expected. For some Mac versions, the discrepancy was even greater; for example, 43% of the iMac 21.5" model from late 2015 were running incorrect versions of the EFI firmware.
"The size of this discrepancy is somewhat surprising," note the authors, "given that the latest version of EFI firmware should be automatically installed alongside the OS updates." Since the firmware updates are delivered as part of the OS updates, they would be installed automatically and invisibly (to the user) at the same time. The implication is that this is an issue stemming from Apple, and not some 'patch later' policy from the user.
Firmware attacks are neither simple nor that common, and tend to be used only against high-value targets. However, Duo Security points out that insecure firmware can leave users unknowingly susceptible to previously disclosed vulnerabilities such as Thunderstrike and the recent WikiLeaks Vault 7 data dumps that detail attacks against firmware.
Home users should probably not worry too much; however, says Smith, "The sophisticated and targeted nature of firmware attacks should be of particular concern to those who have higher security clearance or access to sensitive information at their respective organizations."
Back in 2012, Kaspersky Lab detailed targeted attacks against OS X users among Uyghur activists. This would be an example of a well-resourced attacker (possibly state-sponsored) attacking a high-value target (political dissidents). Had the attacks succeeded against the Mac firmware, they would not have been so easily discovered by Kaspersky Lab.
This is because, in Smith's words, EFI compromises offer three particularly worrying characteristics: they are low level, exceptionally stealthy, and highly persistent. They can read and write arbitrarily to disk or memory before the machine boots; they can deliver false information to any security tool trying to find them; and they can resist re-boots, re-installing the operating system, and even replacing the hard disk altogether.
The solution to the problem is to try to match the firmware with the OS updates; that is, to get EFI and OS back in step. Duo provides apps to help users discover the firmware in use. Where this is not possible, Smith suggests, "it would be well worth considering replacing Macs that cannot have updated EFI firmware applied, or moving them into roles where they are not exposed to EFI attacks (physically secure, controlled network access). While EFI attacks are currently considered both sophisticated and targeted, depending on the nature of the work your organization does and the value of the data you work with, it’s quite possible that EFI attacks fall within your threat model. In this regard, vulnerability to EFI security issues should carry the same weight as vulnerability to software security issues."
Duo Security reported its findings to Apple in late June. Apple has acknowledged a problem. "Interactions with Apple have been very positive," comments Smith, "and they seemed to genuinely appreciate the work and agreed with our methodologies, findings and conclusions. Despite the issues we found, we truly believe that Apple is leading the way in terms of taking EFI security seriously. They have continued to take steps forward with the release of macOS 10.13 (High Sierra). They have a world class firmware security team and we are excited to see the new security approaches they will take in future to keep the EFI environment even more secure."
Legitimate VMware Binary Abused for Banking Trojan Distribution
29.9.2017 securityweek Virus
A recently discovered banking Trojan campaign has been abusing a legitimate VMware binary to trick security products into allowing malicious binaries to load, Cisco researchers reveal.
The campaign, the security researchers say, also attempts to remain stealthy by using multiple methods of re-direction when infecting the victims’ machines. Furthermore, the attackers use a variety of anti-analysis techniques, while also employing a final payload written in Delphi, a technique rather unique to the banking Trojan landscape.
Focusing mainly on users in Brazil, the attack starts with malicious spam emails featuring messages written in Portuguese. The attackers are also attempting to convince the victim to open a malicious HTML attachment posing as a Boleto invoice.
The HTML file contains a URL that first redirects to a goo.gl URL shortener, which in turn redirects to a RAR archive containing a JAR file with malicious code that instalsl a banking Trojan. The Java code sets up the working environment of the malware and then downloads additional files from a remote server.
The Java code renames the downloaded binaries and also executes a legitimate binary from VMware, which is even signed with a VMware digital signature, the security researchers say. By loading a legitimate binary, the attackers attempt to trick security programs into trusting the libraries it would load.
One of these libraries, however, is a malicious file named vmwarebase.dll, meant to inject and execute code in explorer.exe or notepad.exe. The banking Trojan’s main module was designed to terminate the processes of analysis tools and create an autostart registry key.
The module also gets the title of the window in the foreground of the user, thus being able to identify if any of the windows pertains to a targeted financial institution located in Brazil. The Trojan then uses web injects to trick users into revealing their login credentials.
One other binary the main module loads is packed using Themida, which makes its analysis very difficult, the security researchers say. The malware was also observed sending specific strings to the command and control server each time an action was performed on the infected system.
“Financial gain will continue to be a huge motivator for attackers and as with this sample the evolution of the malware continues to grow. Using commercial packing platforms like Themida will continue to make analysis difficult for analysts and shows that some attackers are willing to obtain these types of commercial packers in an attempt to thwart analysis,” Cisco concludes.
Backdoor Masquerades as Popular WordPress Plugin
29.9.2017 securityweek Vulnerebility
A fake WordPress plugin containing a backdoor attempts to trick users into believing it is a version of a popular plugin that has over 100,000 installs.
Dubbed X-WP-SPAM-SHIELD-PRO, the offending plugin was abusing the popularity of WP-SpamShield Anti-Spam, a tool designed to help WordPress site admins fight a variety of spam.
Code used by author of the backdoor was designed to disable other plugins, including security-related ones, steal data, and add a hidden admin account.
While analyzing X-WP-SPAM-SHIELD-PRO, Sucuri security researchers discovered that it features legitimate structure and file names, but that all of its contents are fake. None of the components forming it behave as expected but instead serve a hidden purpose.
One of the files is called class-social-facebook.php, suggesting it would block any potential unwanted Facebook spam. Instead, it was designed to list all of the active plugins within the WordPress installation, including security ones, and then disable all of them. Thus, it could potentially break the website, rendering it unusable.
Two other files, class-term-metabox-formatter.php and class-admin-user-profile.php, were designed for data gathering purposes. The former grabs the WordPress version, while the latter fetches a list of all admin users in the WordPress installation. Thus, the attacker has the information needed to compromise a website.
One other file, called plugin-header.php, was designed to add an additional administrator account – mw01main – to the site. The file, which contains code to delete itself, points to the external site mainwall.org, while also revealing the username, password, and the email that the attacker could use to login to the compromised website.
The fake plugin also includes code to ping home, meaning that the attackers were informed each time an administrator activated it on website. Thus, the attackers would immediately know when a new site is accessible.
A custom sendPost(); function in the plugin was found to collect a great deal of information from the compromised sites and send it to the attackers: user, password, current site the plugin is active on, server IP address, and other sensitive data as well. Sent using the POST method, the data exfiltration is difficult to detect within the site logs.
An update functionality was also discovered, which is a backdoor that allows the attackers to upload anything to the site. Basically, the actors could simply upload a ZIP archive, unpack it to the compromised system, and then delete the archive, Sucuri explains.
The ZIP archive the attackers’ site supplied during the investigation was corrupted and the researchers weren’t able to recover it. However, after restoring a partial archive structure, the researchers concluded it was related to the well-known All In One SEO Pack WordPress plugin. It’s unclear if the attackers were trying to infect the plugin with malicious code, or if they were simply performing a test.
The good news is that the malicious X-WP-SPAM-SHIELD-PRO plugin never made it to the WordPress repository. Admins are advised to install plugins only from reliable sources, as well as to audit and update the already installed ones on a regular basis.
Serious Flaw Exposes Siemens Industrial Switches to Attacks
29.9.2017 securityweek Vulnerebility
Siemens has started releasing patches to address a high severity access control vulnerability that can be exploited to remotely hack some of its industrial communications devices.
The flaw, discovered by Siemens itself and tracked as CVE-2017-12736, affects SCALANCE X industrial ethernet switches, and Ruggedcom switches and serial-to-ethernet devices running the Rugged Operating System (ROS).

The issue is related to the Ruggedcom Discovery Protocol (RCDP), which allows the Ruggedcom Explorer management tool to discover and configure ROS-based devices regardless of their IP network configuration.Siemens Ruggedcom switch
The problem, according to Siemens, is that the protocol is not configured properly after a device is commissioned, allowing an unauthenticated attacker who has access to the network to remotely perform administrative actions.
“After initial configuration, the RCDP is still able to write to the device under certain conditions, potentially allowing users located in the adjacent network of the targeted device to perform unauthorized administrative actions,” Siemens said in its advisory.
The issue has so far been addressed in Ruggedcom RSL910 devices with the release of ROS 5.0.1 and in other ROS-based products with version 4.3.4. An update has also been rolled out for Ruggedcom Explorer.
In the case of SCALANCE XB-200, XC-200, XP-200, XR300-WG, XR-500 and XM-400 switches, patches have not been made available, but users can mitigate possible attacks by manually disabling RCDP.
Ruggedcom switches are typically used to connect devices in harsh environments, such as traffic control cabinets and electric utility substations, while SCALANCE X switches are used to connect programmable logic controllers (PLCs), human-machine interfaces (HMI) and other industrial components. According to ICS-CERT, the affected products are deployed worldwide.
This is the third round of patches released by Siemens for its Ruggedcom devices this year. High severity flaws were also addressed by the German automation giant in early and late March.
Kyberzločinci cílí na PC i mobily
29.9.2017 Novinky/Bezpečnost Kyber
S novými viry se v posledních týdnech doslova roztrhl pytel. Tyto škodlivé kódy se přitom již nezaměřují pouze na klasické počítače, stále častěji se je kyberzločinci snaží propašovat také do chytrých telefonů.
Důvod je jasný. Zatímco na zabezpečení počítačů si většina uživatelů dává již velký pozor, u mobilů řeší riziko kybernetických útoků málokdo. A to platí i o počítačových tabletech.
Přitom právě na zmiňovaných zařízeních uživatelé velmi často uchovávají citlivé osobní údaje, přístupová hesla a v neposlední řadě je používají také k obsluze svých bankovních účtů.
Právě poslední zmiňovaná činnost je pro počítačové piráty patrně nejatraktivnější. Pokud se počítačoví piráti dostanou k přihlašovacím údajům do internetového bankovnictví, jsou jen krůček od vybílení účtu. Stačí, aby se jim podařilo na telefon propašovat dalšího nezvaného návštěvníka, který dovede odchytávat SMS zprávy pro potvrzení plateb.
Právě proto je důležité chránit antivirovými programy a dalšími bezpečnostními nástroji nejen PC, ale také chytré telefony.
Důležitá je prevence
Před podobnými nezvanými hosty dokážou počítače, tablety i chytré telefony ochránit speciální programy. Kromě klasických antivirů jde například o aplikace, které se soustředí pouze na špionážní software a hledání trojských koňů.
Jiné programy zase dokážou v operačním systému nalézt tzv. keyloggery, které jsou schopné zaznamenávat stisk každé klávesy a nasbíraná data odesílat útočníkovi. Na PC i mobilu by měl být nainstalován vždy jen jeden bezpečnostní program svého druhu. Dva antiviry na disku dokážou udělat pěknou neplechu. Samotný antivirus ale zárukou bezpečí není.
Velmi důležité jsou také aktualizace, protože právě chyby v operačním systému a nejrůznějších programech počítačoví piráti velmi často zneužívají k tomu, aby do něj propašovali nezvané návštěvníky.
Sledují každý krok uživatele
Před novým virem, který je vylepšenou verzí bankovního malwaru zvaného Svpeng, varoval bezpečnostní expert ze společnosti Kaspersky Lab Roman Unuchek. Právě on totiž hrozbu objevil jako první.
Tento vylepšený záškodnický program jasně ukazuje, jak se v poslední době počítačoví piráti vyvíjejí. Kombinují různé škodlivé kódy tak, aby byli schopni nepozorovaně ukrást z cizího zařízení citlivá data a následně je zneužít – v tomto konkrétním případě je řeč o přístupových údajích do internetového bankovnictví.
Podvodníkům jde nejčastěji o peníze.
Většina bankovních trojských koňů je totiž poměrně snadno odhalitelná, alespoň pokud se bavíme o těch určených pro chytré telefony. Uživateli totiž na displeji podstrčí při pokusu o přihlášení do internetového bankovnictví podvodnou stránku, u které jde však velmi často poznat, že jde o padělek. Pozornější uživatelé tak zpravidla na tento trik nenaletí a kyberzločincům své přihlašovací údaje na zlatém podnose nenaservírují.
I když výjimky se pochopitelně také najdou. Upravená verze škodlivého viru Svpeng je však daleko sofistikovanější. Obsahuje totiž zabudovaný keylogger, který zaznamenává doslova veškerou činnost uživatele na napadeném smartphonu. Počítačoví piráti se tak dozvědí přihlašovací údaje i ve chvíli, kdy je uživatel skutečně zadává do legitimního formuláře banky.
Další část trojského koně se pak postará o zbytek – odchytne potvrzovací zprávu a zneužije ji. Počítačoví piráti pak mohou velmi snadno vybílit svým obětem celý účet.
Podvodníci to zkoušejí i přes tiskárny
Na pozoru by se měli mít v poslední době lidé, kteří obdrží e-mail s naskenovaným souborem. I když se může na první pohled zdát, že jej zaslala skutečně nějaká tiskárna, ve skutečnosti jde o podvod. A počítačovým pirátům jde pouze o to, aby mohli důvěřivce oškubat. Na množící se podvody upozornil český Národní bezpečnostní tým CSIRT.CZ.
Podle něho zneužívají podvodníci fakt, že moderní tiskárny skutečně dokážou naskenované dokumenty odeslat přímo do e-mailové schránky. „Aktuálně zaznamenáváme zvýšený výskyt e-mailů přesvědčivě se tvářících jako oskenovaný soubor poslaný tiskárnou,“ uvedl Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Podle něj nebezpečí tkví právě v příloze, která je součástí nevyžádaného e-mailu. „V příloze je přiložený archív s příponou .rar. V archívu je zabalený .vbs skript, který již poté dokáže napáchat škodu,“ podotkl Bašta.
„Dle některých výzkumníků se s největší pravděpodobností jedná o novou variantu ransomwaru Locky, který šifruje soubory oběti a přidává jim následně příponu .lukitus. Námi zachycený vzorek je v současnosti úspěšně detekován pouze některými antiviry,“ varoval bezpečnostní expert.
To jinými slovy znamená, že nový škodlivý kód, který se šíří prostřednictvím příloh v e-mailu, nemusí antivirové programy vůbec rozeznat. Uživatelé tak po otevření přílohy vlastně ani nemusí vědět, že si zavirovali počítač.
Nebezpečný červ pro mobily
Milióny chytrých telefonů s operačním systémem Android z různých koutů světa se podařilo kyberzločincům infikovat nebezpečným červem, který lidem postupně tahal z kapes peníze. Z napadených zařízení totiž odesílal placené prémiové SMS zprávy.
Tímto škodlivým kódem zvaným ExpensiveWall se počítačovým pirátům podařilo infikovat nejméně 50 aplikací, které byly dostupné prostřednictvím oficiálního obchodu Google Play. To jinými slovy znamená, že do svého zařízení si lidé nezvaného návštěvníka stáhli s nějakým dalším programem, aniž to tušili. Všechny infikované programy – například aplikace Lovely Wallpaper – již byly z internetového obchodu staženy. I taky ale podle odhadů bezpečnostních expertů stihli počítačoví piráti škodlivým kódem nakazit až 4,2 miliónu zařízení.
Číslo přitom není v žádném případě konečné, neboť červ ExpensiveWall se vedle oficiálního obchodu Googlu šířil pravděpodobně také skrze aplikace nabízené na různých internetových fórech apod. Podle Check Pointu tak počet infikovaných zařízení dohromady pravděpodobně překročil číslovku 21 miliónů.
Je důležité upozornit na to, že jakákoliv infikovaná aplikace nainstalovaná na zařízení před tím, než byla odstraněna z Google Play, stále zůstává na zařízeních uživatelů aktivní. Uživatelé, kteří tyto aplikace stáhli, jsou proto stále v nebezpečí a musí je ručně odstranit ze svých zařízení.
Legitimní aplikace mohou být zavirované
CCleaner je velmi oblíbený program, který slouží k čištění zbytkových souborů v počítači. Jedna z jeho posledních aktualizací však obsahovala virus, jímž byly infikovány dva milióny počítačů. Výjimkou nejsou ani stroje z České republiky, i když přesný počet tuzemských obětí zatím není známý.
Škodlivým kódem přitom byla nakažena oficiální verze programu dostupná přímo na stránkách výrobce. Virus v aplikaci CCleaner objevil tým bezpečnostních výzkumníků Cisco Talos, který neprodleně informoval zástupce Avastu o tom, že jsou jejich uživatelé v ohrožení.
V počítači přitom virus, který se šířil prostřednictvím CCleaneru, dokáže udělat pěknou neplechu. „Pokud je tento malware v počítači uživatele nainstalovaný, mohou získat hackeři přístup do uživatelova počítače i do ostatních propojených systémů,“ uvedli bezpečnostní experti.
„Následně pak mohou získat přístup k citlivým datům či přístupovým údajům k internetovému bankovnictví nebo jiným účtům,“ zdůraznili výzkumníci z týmu Cisco Talos s tím, že hrozba je tedy pro uživatele velmi vážná. Že byla jedna z aktualizací CCleaneru skutečně zavirovaná, potvrdili už i zástupci antivirové společnosti Avast. Právě tento podnik za vývojem bezplatného nástroje pro čištění počítačů stojí.
Antivirové programy jednoduše obejdou
Bezpečnostní experti ze společnosti Check Point odhalili nový způsob, jak mohou počítačoví piráti relativně snadno obejít zabezpečení počítačů s operačním systémem Windows 10. Tato metoda přitom nezneužívá žádnou bezpečnostní trhlinu, ale jednu z funkcí tohoto operačního systému.
„Technika nazvaná Bashware využívá novou funkci Windows 10 nazvanou Subsystem for Linux (WSL), která ještě nedávno byla jen v betaverzi, ale nyní už je plně podporovanou funkcí Windows,“ uvedl Petr Kadrmas, bezpečnostní odborník ze společnosti Check Point.
Jde o oblíbený linuxový terminál (Bash), jenž je dostupný pro uživatele operačního systému Windows a umožňuje nativně spustit soubory z Linuxu v operačním systému Windows. Tento hybridní koncept tedy umožňuje současně kombinovat systémy Linux a Windows.
Bezpečnostní řešení v desítkách však ale ještě stále nejsou přizpůsobena pro sledování procesů spustitelných linuxových souborů. „Kyberzločincům se tak otevírají nová dvířka, jak nepozorovaně spustit škodlivý kód a využít funkce WSL k maskovaní před bezpečnostními produkty, které ještě neimplementovaly odpovídající detekční mechanismy,“ zdůraznil Kadrmas.
„Check Point testoval tuto techniku na většině předních antivirových a bezpečnostních produktů a malware nebyl detekován. Bashware tak může potenciálně ovlivnit libovolný ze 400 miliónů počítačů, které v současné době pracují se systémem Windows 10,“ podotkl bezpečnostní expert.
Na hrozbu nemůže z logiky věci zareagovat samotný Microsoft, ale tvůrci jednotlivých antivirových řešení. Ta musí být schopna pracovat jak v prostředí Windows, tak Linuxu. V opačném případě jsou uživatelé vystaveni riziku.
Viry se nevyhýbají ani internetu věcí. Rozesílají spam
29.9.2017 Novinky/Bezpečnost Viry
S tím, jak roste počet chytrých zařízeních zapojených do internetu věcí (IoT), roste i zájem hackerů o jejich zneužití. Stále častěji se tak stávají obětí malwaru, jako je například Mirai. Botnety tvořené těmito ovládnutými zařízeními jsou určeny především k DDoS útoků, nový výzkum však ukázal, že je hackeři používají i pro masové rozesílání nevyžádané pošty.
Analýza, kterou provedla ruská bezpečnostní firma Doctor Web, odhalila, že linuxový trojan Linux.ProxyM používaný počítačovými zločinci k zajištění své online anonymity, dostal nedávno aktualizaci. Ta do něj přidala funkci pro rozesílání spamu.
Trojan Linux.ProxyM byl objevený letos v únoru. Provozuje SOCKS proxy server nakaženém IoT Zařízení a má schopnost detekovat tzv. honeypoty (anglicky „hrnce medu“), což jsou informační systémy, jejichž úkolem je přitahovat potenciální útočníky a zaznamenat jejich činnost. Díky tomu je pro antivirové systémy nesnadné ho odhalit.
Virus může fungovat na téměř všech linuxových zařízeních, včetně routerů, set-top boxů a dalších zařízeních, které fungují na architekturách x86, MIPS, PowerPC, MIPSEL, ARM, Motorola 68000, Superh a SPARC.
Problém je však v tom, že uživatelé v současnosti nemohou zařízení pro internet věcí jakkoliv chránit. Zatímco pro běžné počítače jsou k dispozici antivirové programy a další bezpečnostní software, pro chytré žárovky, mobilem ovladatelné termostaty a další podobnou elektroniku zatím nic podobného není.
Amazon-owned grocery chain Whole Foods Market suffered payment card breach
29.9.2017 securityaffairs Incindent
News of the day is that another big company suffered a security breach, the victim is the Amazon-owned grocery chain Whole Foods Market.
has fallen victim to a credit card security breach.
Whole Foods Market has around 500 stores in the United States, United Kingdom, and Canada, the company acquired by Amazon for $13.7 billion in late August, it now notified customers a credit card security breach.
According to the security breach notification, crooks were able to gain unauthorized access to credit card information for customers who made purchases at certain venues like taprooms and full table-service restaurants located within some stores.
“Whole Foods Market recently received information regarding unauthorized access of payment card information used at certain venues such as taprooms and full table-service restaurants located within some stores.” read the data breach notification announcement. “These venues use a different point of sale system than the company’s primary store checkout systems, and payment cards used at the primary store checkout systems were not affected.”
At the time there the firm hasn’t provided details about the attack, it is still unclear which locations were affected and the total number of customers impacted.

The attackers targeted point-of-sale (POS) systems to siphon customer financial data.
The company pointed out that customers that used their payment cards only for groceries at Whole Foods were not affected, hackers targeted only certain venues which use a separate POS system.
Whole Foods Market clarified that hackers were not able to access Amazon transactions in the security breach.
The company is already investigating the incident and has hired a cybersecurity firm to help it, of course the firm promptly reported the incident to law enforcement.
“When Whole Foods Market learned of this, the company launched an investigation, obtained the help of a leading cybersecurity forensics firm, contacted law enforcement, and is taking appropriate measures to address the issue,” states Whole Foods.
The firm encourages its customers to monitor their credit card statements and bank accounts and report any unauthorized charges.
This is the last data breach suffered by major organizations, last week it Deloitte confirmed a security breach that exposed private emails and documents of some of its clients.
Recently credit rating agency Equifax publicly disclosed a major breach that affected 143 million Americans, meanwhile the U.S. Securities and Exchange Commission (SEC) also admitted that hackers compromised its financial document filing system.
Crooks hacked Microsoft servers to mine Monero, they earned $63K in 3 months
29.9.2017 securityaffairs CyberCrime
Experts from security firm ESET discovered cyber criminals exploiting Microsoft Servers to mine Monero and already earned $63,000 in 3 Months.
Mining cryptocurrencies is a profitable business, but it is also expensive because it needs significant investment in computing power. Crooks are using malicious code that steals computing resources of victims’ machine and the number of attacks aimed to mine cryptocurrencies continues to increase.
Security researchers at security firm ESET have discovered a malware campaign that infected hundreds of Windows web servers with a malicious cryptocurrency miner. According to the experts, the criminal gang behind the attack made more than $63,000 worth of Monero (XMR) in just three months.

Crooks modified a legitimate open source Monero mining code and exploited a known buffer overflow vulnerability (CVE-2017-7269) in Microsoft IIS 6.0 to deploy the miner on unpatched Windows servers.
“One such operation has been going on since at least May 2017, with attackers infecting unpatched Windows webservers with a malicious cryptocurrency miner. The goal: use the servers’ computing power to mine Monero (XMR), one of the newer cryptocurrency alternatives to Bitcoin.” states a report published by ESET.
“To achieve this, attackers modified legitimate open source Monero mining software and exploited a known vulnerability in Microsoft IIS 6.0 to covertly install the miner on unpatched servers. Over the course of three months, the crooks behind the campaign have created a botnet of several hundred infected servers and made over USD 63,000 worth of Monero.”
The impact of the CVE-2017-7269 vulnerability is significant, according to data provided by the W3Techs, Microsoft’s IIS is currently the third most popular web server solution in the wild (11.4% of all websites). IIS 6.0 accounts for 11.3%, roughly 1.3% of all websites on the Internet. According to BuiltWith, IS 6.0 version is currently used by 2.3% of the entire Internet, over 8.3 million live websites are using IIS 6.0.
The vulnerability doesn’t affect newer versions of Microsoft Internet Information Services.
In order to mitigate the risk of cyber attacks, it is possible to disable the WebDAV service on IIS 6.0 installations.
Crooks are focusing their efforts on Monero cryptocurrency because of its focus on privacy and because it has a good mining profitability, it leverages on the proof-of-work algorithm called CryptoNight, which suits computer or server CPUs and GPU without requiring specific mining hardware.
Recently security experts have detected an increasing number of miners, in August a new fileless miner dubbed CoinMiner appeared in the wild, it uses NSA EternalBlue exploit and WMI tool to spread.
On May 2017 security experts at Proofpoint discovered that many machines weren’t infected by WannaCry because they were previously infected by the Adylkuzz cryptocurrency mining malware that uses the NSA EternalBlue exploit.to spread and infect machines to involve in a Monero botnet.
In the same month, GuardiCore malware experts discovered a new botnet malware, dubbed BondNet, that at the time infected an estimated 15,000 Windows server computers worldwide for mining Monero.
Senate Passes MAIN STREET Cybersecurity Act for Small Business
29.9.2017 securityweek BigBrothers
The U.S. Senate has passed the MAIN STREET Cybersecurity Act on Sept. 28, which will require NIST to "disseminate clear and concise resources to help small business concerns identify, assess, manage, and reduce their cybersecurity risks."
Co-sponsored by Senators Maria Cantwell (D-WA), Brian Schatz (D-HI), James Risch (R-ID), John Thune (R-SD) and Bill Nelson (D-Fla.), and introduced in March 2017, MAIN STREET's full title is 'Making Available Information Now to Strengthen Trust and Resilience and Enhance Enterprise Technology Cybersecurity Act of 2017'.
The basic requirement is that NIST shall provide cybersecurity resources specifically geared for small businesses (SMEs). Those resources are to promote awareness of simple, basic controls; a workplace cybersecurity culture; and third-party stakeholder relationships, in order to assist SMEs in mitigating common cybersecurity risks. The resources are to be technology-neutral that can be implemented using commercial and off-the-shelf technologies.
They are to be consistent with the requirements of the Cybersecurity Enhancement Act of 2014, which gave more weight and support to the NIST Cybersecurity Framework. While widely used by large organizations, the NIST framework is usually ignored by SMEs.
In a statement of support for MAIN STREET issued in March, Sen. John Thune, chairman of the Senate Committee on Commerce, Science, and Transportation, pointed out that SMEs provide more than half of all jobs in the U.S., but are unprepared for the effect of cyberattacks. According to figures from the National Cybersecurity Alliance, 60% of small businesses are forced to close following an attack.
"Cyberattacks can have catastrophic effects on small businesses and their customers," he said. "This legislation offers important resources, specifically meeting the unique needs of small businesses, to help them guard sensitive data and systems from thieves and hackers."
"In 2012, nearly 71 percent of cyberattacks occurred in businesses with fewer than 100 employees," said Senator Risch. "These attacks seriously compromise not only the businesses, but also their employees' and customers' personal information. As we work to reduce our nation's cyber vulnerabilities, we must be equally mindful of our responsibility to uniformly educate all small business owners on how to deter these threats."
The small business version of the NIST Framework will need to provide a cybersecurity framework that does not require the high level of investment needed for the full NIST Framework. However, like the full version, it will be voluntary for business. Whether SMBs actually derive practical benefit remains to be seen.
The Ponemon 2016 State of Cybersecurity in SMBs survey found that 50% of small businesses had suffered a data breach in the previous 12 months. SMEs are clearly a target for cybercriminal attacks, but are unprepared to stop them. The primary reasons are twofold: SMEs often think they are too small to be a target, and that effective security can only be achieved with the resources of a large organization.
The first is simply wrong: small businesses are increasingly targeted for extortion (such as ransomware) and credential theft (especially where that business might be part of the supply chain of larger organizations). It is hoped that the new small business Cybersecurity Act will change the second.
A survey of 1,420 small business owners published in March 2017 by Manta suggests that only 69% of small business owners currently have controls in place to prevent hacks -- meaning 1 in 3 small business owners have no safeguards in place. Where controls are used, they tend to be basic: such as antivirus software (17%), firewalls (16%), and spam filters (14%).
"Overall," concludes Manta, "with the growth in hackers targeting small businesses, owners should invest more heavily in cyber defense to prevent attacks, which can often be more crippling for a small business than a large corporation."
Andy Halataei, Senior Vice President for Government Affairs of the Information Technology Industry Council, said at the time the bill was introduced, "Small businesses often don't have the resources they need to guard against sophisticated cyber-attacks, and this legislation can be the helping hand small businesses need to help reduce their cybersecurity risks." He added, "By offering small businesses federal agencies' resources and coordinated support, they can better manage risks, protect customer privacy, and focus on growing their ventures."
The reality for small businesses today is that they face threats from both criminals and government legislation. Legal regulatory requirements, like common cybercriminals, do not differentiate hugely between large and small businesses. For example, any business of whatever size that does business with a member state of the European Union will be subject to the strict requirements of the European General Data Protection Regulation (GDPR) by May 2018.
The MAIN STREET Cybersecurity Act of 2017 will hopefully help SMEs protect themselves from both hackers and regulators. It is expected that this Act will rapidly pass through the final stages to become law.
Amazon's Whole Foods Investigating Payment Card Breach
29.9.2017 securityweek Incindent
Whole Foods Market, the supermarket chain acquired recently by Amazon for $13.7 billion, informed customers this week that it has launched an investigation after learning that some of its point-of-sale (PoS) systems may have been hacked.
The company has provided only few details as the investigation is ongoing. However, it said the incident appears to impact taprooms and full table-service restaurants located within some of its stores.

Whole Foods pointed out that these venues rely on different PoS systems than the store that houses them. The affected payment systems are also not connected to Amazon.com, the company said.Whole Foods hacked
Law enforcement has been notified and a cyber security firm has been called in to assist Whole Foods’ investigation. The supermarket chain has promised to provide additional information as it learns more about the incident.
“While most Whole Foods Market stores do not have these taprooms and restaurants, Whole Foods Market encourages its customers to closely monitor their payment card statements and report any unauthorized charges to the issuing bank,” the company told customers.
The company’s statement suggests that it learned of the data breach from an external source – it’s likely that payment card issuers noticed a pattern of fraudulent transactions involving cards used at Whole Foods Market locations.
“Companies face threats every day and breaches will occur. In a contested environment like this, segmenting the networks, like Whole Foods did with its unique restaurant and taproom environment, saves other parts of the business from also being breached,” said Michael Daly, CTO of Raytheon's cybersecurity businesses.
“Financial systems within the larger Whole Foods system were not affected. The climate and operations controls were not compromised protecting massive amounts of food and inventory. Whether the segmented approach was happenstance or not, there is a lesson to be taken from today’s breach,” Daly added.
Fast food restaurant chain Sonic Drive-In is also investigating a possible data breach. Millions of payment cards that may have come from the company’s systems were recently put up for sale on a cybercrime marketplace.
DNSSEC Key Rollover Delayed to Prevent Users Going Offline
29.9.2017 securityweek Safety
The Internet Corporation for Assigned Names and Numbers (ICANN) announced this week that the replacement of the root zone key signing key (KSK) for the Domain Name System Security Extensions (DNSSEC) protocol has been postponed by at least one quarter due to the failure of some network operators to install the new key.
ICANN estimates that roughly 750 million people worldwide are affected by the KSK rollover. The change of the key was initially planned for October 11, but ICANN has recently learned that many network operators and Internet service providers (ISPs) are not prepared, which would lead to tens of millions of users going offline.
Data provided by a recently added DNS protocol feature has allowed ICANN to see how many DNSSEC-validating resolvers have been configured with the new root KSK. The data shows that roughly 6-8% of these systems still use the KSK from 2010, the year when the DNSSEC protocol was introduced.KSK rollover postponed by ICANN
This means that as many as 60 million users may have been kicked off the Internet had ICANN decided to stick to the original date of October 11.
“Throughout the project we have emphasized that the root KSK is being rolled under normal operational conditions and have proceeded cautiously and without haste,” explained Matt Larson, VP of Research at ICANN’s Office of the CTO. “The decision to postpone was taken in that spirit of caution because there is no operational pressure to proceed given our continued confidence in the security of KSK-2010.”
While some network operators may need to manually configure the new KSK and they have failed to do so, ICANN believes some organizations may not know they are unprepared for the key rollover. These organizations configured their systems to automatically update the key, but the process failed due to software defects, operator errors or some other cause.
A new date has not been set for the key rollover, but ICANN has decided to delay it for at least one quarter.
DNSSEC and the KSK rollover
Since DNS, the system that translates domain names to IP addresses, was not designed with security in mind, the DNSSEC protocol was introduced to prevent users from being directed to malicious websites via DNS spoofing attacks.
DNSSEC aims to achieve this by cryptographically signing DNS information, including the root zone, which is the highest level of the DNS structure. If DNSSEC is used, the root zone vouches for the public key of the .com zone (or other TLD zone), which in turn vouches for all .com domains. Since the root zone is at the top of the DNS hierarchy, there is no higher level to vouch for it so its zone key is configured as a “trust anchor,” a key that is declared trustworthy.
The trust anchor key is called a key signing key (KSK), and all recursive name servers performing DNSSEC validation need to have the root zone’s KSK set as a trust anchor. These name server are typically operated by Internet service providers (ISPs) and enterprises, and if the KSK is not configured properly, DNS resolution will not work for their users.
Since it could get compromised, ICANN plans to periodically change, or roll, the KSK. A new KSK was generated in October 2016 and the plan was to have it replace the original key by October 11. According to the initial schedule, the old KSK would have been revoked on January 11, 2018.
Sophisticated Phishing Attacks Target Internet Freedom Activists
28.9.2017 securityweek Phishing
The Electronic Frontier Foundation (EFF) revealed on Wednesday that employees of Internet freedom NGOs “Free Press” and “Fight for the Future” have been targeted in sophisticated spear-phishing attacks.
The EFF is aware of nearly 70 attempts to steal the credentials of net neutrality activists between July 7 and August 8. The attacks, believed to be the work of a single entity, were designed to steal credentials associated with Google, Dropbox, LinkedIn and other online services.
At least one account was hijacked and abused to send out more phishing emails to other individuals within the victim organization. The EFF said the attacks did not involve any malware and it’s unclear what the attackers had hoped to accomplish once they obtained account credentials.
The attackers used various tricks to lure targeted individuals to their phishing pages. In some cases, they sent out fake LinkedIn notification messages that contained links to Gmail phishing sites. Other messages showed that the attackers had studied their targets – Fight For The Future Campaign Director Evan Greer was targeted via an email asking about her music, and another employee received malicious emails purporting to be from her husband.
The hackers also sent emails that appeared to notify a user of comments to their YouTube video, ones with clickbait headlines referencing net neutrality and tabloid topics, and fake subscriptions to adult websites.
The EFF has not attributed these attacks to a specific actor or country, but the organization did point out that the individuals behind the attacks appear to be working from an office, with Saturday and Sunday off, during working hours associated with the UTC+3 - UTC+5:30 timezones.
These timezones cover countries and regions such as Eastern Europe, Russia, part of the Middle East, and India. However, it’s worth noting that Saturday and Sunday are not weekend days in many Middle Eastern countries. The IP from which the one compromised account was accessed did not provide any clues as it was associated with a VPN service.
“The sophistication of the targeting, the accuracy of the credential phishing pages, the working hours, and the persistent nature of the attacks seem to indicate that the attackers are professionals and had a budget for this campaign,” the EFF’s Eva Galperin and Cooper Quintin said in a blog post.
However, the EFF does not believe the campaign has been carried out by a nation-state actor.
“Although this phishing campaign does not appear to have been carried out by a nation-state actor and does not involve malware, it serves as an important reminder that civil society is under attack. It is important for all activists, including those working on digital civil liberties issues in the United States, to be aware that they may be targeted by persistent actors who are well-informed about their targets’ personal and professional connections,” the EFF said.
Google Expands HSTS Preload List
28.9.2017 securityweek Safety
Google this week announced the addition of more of its top-level domains (TLDs) to the HTTPS Strict Transport Security (HSTS) preload list.
Built into all major Web browsers, including Chrome, Firefox, Safari, Internet Explorer/Edge, and Opera, the HSTS preload list consists of a list of hostnames for which browsers automatically enforce HTTPS-secured connections, thus ensuring the safety of their users.
Because of the HSTS preload list, browsers will avoid making insecure connections to the sites included in it, even if the user doesn’t type HTTPS when trying to connect to a domain. Because of this set, the browser never loads an http-to-https redirect page, which could be intercepted.
The HSTS preload list, which is maintained by the Internet giant itself, can contain individual domains or subdomains, along with TLDs, which can be added through the HSTS website.
Google, which is an avid HTTPS promoter, added the .google TLD to the list in 2015 and is now rolling out HSTS for a larger number of TLDs, starting with .foo and .dev.
“The use of TLD-level HSTS allows such namespaces to be secure by default. Registrants receive guaranteed protection for themselves and their users simply by choosing a secure TLD for their website and configuring an SSL certificate, without having to add individual domains or subdomains to the HSTS preload list,” Ben McIlwain, Google Registry, notes in a blog post.
McIlwain also explains that it usually takes months before a domain name added to the list will reach the majority of users via a browser upgrade. Thus, using an already-secured TLD ensures that users benefit from immediate protection.
Adding an entire TLD to the HSTS preload list also provides increased efficiency, because all domains under that TLD are secured and adding them individually isn’t required, McIlwain says.
Considering the number of websites that use HSTS at the moment, Google’s move is certainly welcomed. Only 4.8% of all the websites use the HSTS mechanism, which ensures users that connect to them only via secure connections. This percentage has remained almost the same for a long time, although HSTS was implemented over four years ago.
In March last year, Netcraft’s Paul Mutton explained that the 95% of web servers that lack HSTS remain vulnerable to trivial connection hijacking, thus exposing users to phishing, pharming, and man-in-the-middle (MiTM) attacks.
In October 2015, David Holmes, an evangelist for F5 Networks, pointed out in a SecurityWeek column that HSTS was meant to resolve a vulnerability when a site accepts both unencrypted (HTTP) and encrypted (HTTPS) requests. The incorrect implementation of HSTS could allow an attacker to prevent the browser from receiving HTTPS redirects, he said.
Monero Miner Infects Hundreds of Windows Servers
28.9.2017 securityweek Vulnerebility
Hundreds of servers have been infected with Monero mining malware after miscreants managed to exploit a vulnerability in Microsoft IIS 6.0, ESET warns.
The infection campaign has been ongoing since at least May 2017 and has resulted in the attackers creating a botnet and mining over $63,000 worth of Monero (XMR) to date. The actors behind this campaign modified a legitimate open source Monero mining software and installed it on unpatched servers.
The malicious software used in this campaign is a fork of a legitimate open source Monero CPU miner called xmrig, which was released in May 2017. The crooks simply copied the original open source codebase and made only a few changes to it when creating their mining tool.
Specifically, they only added hardcoded command line arguments of their own wallet address and mining pool URL. They also included arguments to kill all previously running instances of the software itself, an operation that couldn’t have taken the crooks more than several minutes, ESET notes.
The malware distribution was performed via brute-force scans for the CVE-2017-7269 vulnerability from two IP addresses that point to servers in the Amazon Web Services cloud. The security flaw resides in the WebDAV service, part of Microsoft IIS version 6.0, the webserver in Windows Server 2003 R2.
“This vulnerability is especially susceptible to exploitation, since it’s located in a webserver service, which in most cases is meant to be visible from the internet and therefore can be easily accessed and exploited by anyone,” the researchers note.
The payload is delivered in the form of an alphanumeric string, as the attackers simply replaced the string leading to execution from the publicly available proof-of-concept.
The researchers also observed that the miner has been appearing in waves since May, which would suggest that the attackers are scanning the Internet for vulnerable machines on a regular basis. The attackers perform the scans from what appears to be a machine hosted on an Amazon cloud server.
Because Microsoft ended regular support for Windows Server 2003 in July 2015, a patch for the vulnerability was released only in June 2017. Furthermore, as the update process for the platform isn’t always easy, many systems continue to be vulnerable.
As part of this campaign, the infected machines were making around XMR 5.5 daily by the end of August, and supposedly made more than XMR420 (around $63,000) in total over the course of three months.
Although very active at the end of August, the attackers have gone quiet since the beginning of September, with no new infections observed. Moreover, the miner lacks a persistence mechanism and the botnet has been losing compromised machines.
Although the total number of victims isn’t known, ESET estimates that hundreds of servers were compromised, based on the total hash rate produced by the attacker.
“We see that minimal know-how together with very low operating costs and a low risk of getting caught – in this case, misusing legitimate open-source cryptocurrency mining software and targeting old systems likely to be left unpatched – can be sufficient for securing a relatively high outcome,” ESET concludes.
CISCO addressed several critical IOS flaws that expose devices to remote attacks
29.9.2017 securityaffairs Vulnerebility
Cisco has released security updates for its IOS Operating System to fix more than a dozen critical and high severity vulnerabilities.
Cisco has released updates for its IOS software to fix more than a dozen critical and high severity vulnerabilities that could be exploited by attackers to remotely take over company’s switches and routers.
Giving a close look at the flaws addressed by CISCO, we find the CVE-2017-12229 vulnerability that affects the REST API and that could be exploited by a remote attacker to bypass authentication and gain access to the web-based user interface of network devices running vulnerable versions of the IOS software.
“A vulnerability in the REST API of the web-based user interface (web UI) of Cisco IOS XE Software could allow an unauthenticated, remote attacker to bypass authentication to the REST API of the web UI of the affected software.” reads the CISCO security advisory.
“The vulnerability is due to insufficient input validation for the REST API of the affected software. An attacker could exploit this vulnerability by sending a malicious API request to an affected device. A successful exploit could allow the attacker to bypass authentication and gain access to the web UI of the affected software.”

CISCO also fixed the vulnerability CVE-2017-12230, it is a critical flaw that affects the web-based user interface that could be exploited by an authenticated attacker to escalate privileges. The problem is related to the creation of new users via the web interface that are given elevated privileges by default.
“A vulnerability in the web-based user interface (web UI) of Cisco IOS XE Software could allow an authenticated, remote attacker to elevate their privileges on an affected device.” reads the CISCO security advisory.
“The vulnerability is due to incorrect default permission settings for new users who are created by using the web UI of the affected software. An attacker could exploit this vulnerability by using the web UI of the affected software to create a new user and then logging into the web UI as the newly created user. A successful exploit could allow the attacker to elevate their privileges on the affected device.”
The last security critical flaw is CVE-2017-12240 and affects the DHCP relay subsystem in IOS and IOS XE software. The vulnerability could be exploited by a remote and unauthenticated attacker that can execute arbitrary code and gain full control of the targeted system. The flaw could be also exploited to cause a denial-of-service (DoS) condition by triggering a buffer overflow via specially crafted DHCPv4 packets.
“The vulnerability is due to a buffer overflow condition in the DHCP relay subsystem of the affected software. An attacker could exploit this vulnerability by sending a crafted DHCP Version 4 (DHCPv4) packet to an affected system. A successful exploit could allow the attacker to execute arbitrary code and gain full control of the affected system or cause the affected system to reload, resulting in a DoS condition.” states the CISCO advisory.
Cisco also addressed a total of 11 high severity vulnerability affecting various components of the IOS and/or IOS XE software.
The list of flaws includes DoS vulnerabilities affecting Catalyst switches, Integrated Services routers, industrial Ethernet switches, ASR 1000 series routers, and cBR-8 Converged Broadband routers.
The networking giant has also addressed two serious authentication bypass and certificate validation vulnerabilities.
Signal announces private contact discovery to improve users’privacy
29.9.2017 securityaffairs BigBrothers
Open Whisper Systems announced that it’s working on a new private contact discovery service for its popular communications app Signal.
Signal is considered the most secure instant messaging app, searching for it on the Internet it is possible to read the Edward Snowden’ testimony:
“Use anything by Open Whisper Systems” Snowden says.
The Cryptographer and Professor at Johns Hopkins University Matt Green and the popular security expert Bruce Schneier are other two admirers of the Signal app
Signal was also approved by the U.S. Senate for official communications among staff members.
Open Whisper Systems aims to improve the contact discovery feature, currently when a user signs up for Signal, the phone numbers in their device’s address book are compared to entries in a database on Open Whisper Systems servers to determine which interlocutors use Signal.
The verification uses truncated SHA256 hashes of the phone numbers, but as you know hashes can be cracked by attackers.
Even if Open Whisper Systems does not log contact discovery requests, theoretically a persistent attacker (i.e. APT group) can modify the code on Signal servers and starts these requests.
Signal developers are working to avoid such attack scenario leveraging in Intel’s Software Guard Extensions (SGX) technology supported by modern Intel chips.
The SGX technology allows developers to protect a certain portion of code and data from disclosure or modifications. The code is placed in a secure memory area of execution dubbed “enclave.”
“Modern Intel chips support a feature called Software Guard Extensions (SGX). SGX allows applications to provision a “secure enclave” that is isolated from the host operating system and kernel, similar to technologies like ARM’s TrustZone. SGX enclaves also support a feature called remote attestation. Remote attestation provides a cryptographic guarantee of the code that is running in a remote enclave over a network.” states Open Whisper Systems.
The idea of the Signal development team is to run contact discovery service in an SGX enclave.
The private contact discovery leveraging the SGX technology could be composed of the following steps at a high level:
Run a contact discovery service in a secure SGX enclave.
Clients that wish to perform contact discovery negotiate a secure connection over the network all the way through the remote OS to the enclave.
Clients perform remote attestation to ensure that the code which is running in the enclave is the same as the expected published open source code.
Clients transmit the encrypted identifiers from their address book to the enclave.
The enclave looks up a client’s contacts in the set of all registered users and encrypts the results back to the client.
The SGX also supports what “remote attestation” that allows the client to guarantee of the code that is running in a remote enclave over a network.

“This would allow a server to stream media content to a client enclave with the assurance that the client software requesting the media is the “authentic” software that will play the media only once, instead of custom software that reverse engineered the network API call and will publish the media as a torrent instead.” continues Open Whisper Systems.
“Since the enclave attests to the software that’s running remotely, and since the remote server and OS have no visibility into the enclave, the service learns nothing about the contents of the client request. It’s almost as if the client is executing the query locally on the client device,” .
Open Whisper Systems plans to integrate the feature in the next few months.
If you are interested in analyzing source code for the private contact discovery service you can visit the official GitHub repository.
‘Illusion Gap’ attack method bypasses Windows Defender and executes malware
29.9.2017 securityaffairs Attack
Researchers have developed an attack method dubbed Illusion Gap for bypassing Windows Defender that will allow avoiding antivirus detection.
Researchers from security firm CyberArk have devised a new technique dubbed ‘Illusion Gap’ that allows attackers to bypass Windows Defender.
The technique leverages on the fact that Windows Defender detection can be bypassed by tricking the antivirus into scanning a different file than the one actually executing.
The technique affects the scanning process over SMB shares, the experts explained that Antivirus solutions use to detect the execution of an executable file by a kernel callback (nt!PspCallProcessNotifyRoutines and nt!PsCallImageNotifyRoutines) and then scan the file, usually with a user-mode agent.
The Illusion Gap attack may possibly affect other antivirus and defense solutions that the experts have not yet tested.
If the executable file is already present on disk, the Antivirus will not scan it on process creation because it has already scanned it on file creation. However, running an executable from an SMB share trigger the Antivirus scan the file even on process creation.
The researchers demonstrated that a possible attack method consists into tricking the antivirus into scanning a different file than the one actually executing.
To ensure that one file is served to the Windows PE Loader and another to Windows Defender,
Researchers used a custom implemented SMB server to ensure that one file is served to the Windows PE Loader and another to Windows Defender.
“We want to serve different files, one for Windows PE Loader and another for the Windows Defender Antivirus over SMB. We can achieve that using a custom implemented SMB server.” reads the analysis published by the experts. “When a process creation is made by Windows PE Loader, a request will be made to the SMB server for the executable file, and we will serve file A, which is malicious. When Windows Defender requests the executed file, we will serve file B, which is benign. This way, file B will be scanned while file A will be executed. But at first, we have to identify which request is made by whom.”

To bypass the Windows Defender, an attacker would need to implement the SMB protocol and create a “pseudo-server” that is able to discriminate between Windows Defender requests and normal ones.
“In order to abuse Windows Defender, an attacker would have to implement the SMB protocol and create a “pseudo-server” that can differentiate Windows Defender’s request from normal requests. For instance, decline the oplock request and return STATUS_OPLOCK_NOT_GRANTED. This will fail the scan and the malicious file will just execute without any interruptions:”
It is possible to have the same effect by blocking all handle creation requests with the impersonation level SEC_IDENTIFY.
CyberArk reported the ‘Illusion Gap’ attack to Microsoft, but the Tech giant doesn’t consider it as a security vulnerability.
“Based on your report, successful attack requires a user to run/trust content from an untrusted SMB share backed by a custom server that can change its behavior depending on the access pattern. This doesn’t seem to be a security issue but a feature,” reads the Microsoft’s Response on CyberArk Labs findings on Illusion Gap.
Espionage Attack Uses Scripts for Data Exfiltration
28.9.2017 securityweek CyberSpy
A recently detected espionage campaign is delivered via malicious emails, but maintains presence on compromised machines by using scripts instead of a binary payload, Malwarebytes researchers have discovered.
The campaign was targeting a Saudi Arabia Government entity with emails containing a Word document weaponized with malicious macros. The scripts delivered using the macros were able achieve persistence on compromised systems and maintain communication with a command and control (C&C) server.
The attackers use scripts to fingerprint the victims’ machines and to deliver commands that are then executed via PowerShell. Communication with the server is made via hacked websites acting as proxies, Malwarebytes has discovered.
Featuring the logo of a Saudi Government branch, the malicious document, which also includes several Base64 encoded strings alongside the macro, prompts the victim to “Enable Content,” claiming it is in protected view.
The malicious VBScript first attempts to disable or lower security settings within Microsoft Excel and Word through altering corresponding registry keys. The script also fingerprints the victim for their IP address, and then proceeds to retrieve a stream of data from the Pastebin website using its own proxy.
The fetched data is converted into two scripts, one PowerShell and one Visual Basic. The latter is used for persistence via a Run key in the registry and a scheduled task and also acts as the launcher for the PowerShell script. Both are stored as hidden system files under the Documents folder.
The PowerShell script also carries instructions to lower the security settings for Microsoft Office, but its main function is to exfiltrate data and communicate with the C&C.
Data is exfiltrated via several hardcoded websites acting as a proxy.
The use of scripts as part of this campaign provides increased flexibility due to the modularity of the attack, in addition to ensuring increased stealth. While traditional malware can use a packer, this attack can’t, thus having to rely on various encoding techniques.
“This attack is very different from the typical malicious spam we see on a daily basis, blasting Locky or some banking Trojan. Indeed, there is no malicious binary payload (although one could be downloaded by the C&C) which makes us think the attackers are trying to keep a low profile and remain on the system while collecting information from their target,” the security researchers say.
Thousands of Malware Variants Found on Industrial Systems: Kaspersky
28.9.2017 securityweek ICS
Kaspersky said it had detected roughly 18,000 malware samples belonging to more than 2,500 families on industrial control systems (ICS) in the first half of 2017.
According to the company’s “Threat Landscape for Industrial Automation Systems” report for the first six months of the year, nearly 38 percent of the industrial systems protected globally by its products were targeted during this period. This is 1.6 percent less than in the second half of 2016.
Attempts to download malware or access malicious websites (e.g. phishing pages) were blocked by the company’s products on over 20 percent of the protected ICS devices.
Windows malware was neutralized on more than half of targeted systems. However, in many cases, attackers used scripting languages such as VBS, JavaScript, .NET, AutoCAD, Word macros and Java to implement malicious functionality.
“For computers that are part of industrial infrastructure, the Internet remains the main source of infection,” Kaspersky said in its report. “Contributing factors include interfaces between corporate and industrial networks, availability of limited Internet access from industrial networks, and connection of computers on industrial networks to the Internet via mobile phone operators’ networks (using mobile phones, USB modems and/or Wi-Fi routers with 3G/LTE support).”
The security firm, which last year launched a global computer emergency response team (CERT) focusing on ICS, noted that the number of attacks on these systems dropped in January, but returned to previous levels in the next months.
Kaspersky pointed out that many of the threats targeting ICS in the first half of 2017 were ransomware. The company’s products identified 33 different file-encrypting ransomware families on industrial automation systems.
Unsurprisingly, the highest percentage of attacks involved the notorious WannaCry ransomware, which leveraged NSA-linked exploits that can be triggered without user interaction.
Rockwell Automation, Schneider Electric, Honeywell, Siemens, ABB and other ICS providers published alerts at the time to warn customers about the possibility of being hit by WannaCry.
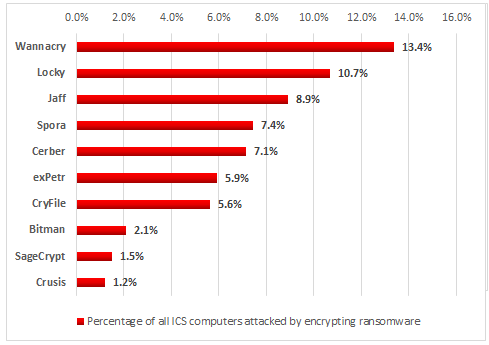
"Illusion Gap" Attack Bypasses Windows Defender
28.9.2017 securityweek Attack
Windows Defender detection can be bypassed by tricking the antivirus application into scanning a different file or nothing at all, CyberArk Labs reveals.
The technique, which affects the scanning process over SMB shares, allows any malware to bypass Windows Defender and possibly other antivirus applications, researchers from CyberArk say.
Antivirus applications typically catch the execution of an executable file by a kernel callback and then scan the file, usually by requesting the user-mode agent to do so. The operation is different for executables already on the disk compared to those from a SMB share, the researchers explain.
If the executable file is already located on the hard drive, the antivirus won’t scan the process creation, because it scanned the file creation. However, the antivirus would scan the process creation when the executable is run directly from a SMB share, the security researchers explain.
One of the attack vectors involves tricking the antivirus into scanning a different file than the one actually executing. To ensure that one file is served to the Windows PE Loader and another to Windows Defender, a custom implemented SMB server is used.
Thus, when the process creation is made by Windows PE Loader and a request is made to the SMB server for the executable file, a malicious file is delivered. However, when Windows Defender requests the executed file, a benign file is served to ensure that the antivirus doesn’t stop the execution.
Thus, to abuse Windows Defender, an attacker would simply need to implement the SMB protocol and create a “pseudo-server” capable of differentiating between normal requests and those coming from Windows Defender.
One example, the researchers say, would be to decline the oplock request and return STATUS_OPLOCK_NOT_GRANTED, which would result in the scan failing and the malicious file being executed without interruptions. By blocking all handle creation requests with the impersonation level SEC_IDENTIFY one can also block the antivirus from scanning the file.
The attack is possible because the SMB protocol offers transparent integration into Windows, meaning that “accessing a remote file is performed like accessing a local file.” Thus, an attacker would need to create a handle to the file and then perform any operations using specific functions. However, replacing the file is possible for each operation, the researchers say.
CyberArk has contacted Microsoft to report the attack, but the company apparently doesn’t view the issue as a security vulnerability. In fact, the tech giant considers that the various special conditions required to trigger the bypass can be seen as a feature.
“Based on your report, successful attack requires a user to run/trust content from an untrusted SMB share backed by a custom server that can change its behavior depending on the access pattern. This doesn’t seem to be a security issue but a feature,” Microsoft reportedly told CyberArk.
Apple Silently Patched macOS Security Bypass Flaw
28.9.2017 securityweek Apple
Researchers claim Apple has silently patched a macOS vulnerability that can be exploited to bypass one of the operating system’s security features and execute arbitrary JavaScript code without restrictions.
The issue, discovered by Filippo Cavallarin of Italian security firm Segment, has been described as a local JavaScript quarantine bypass flaw and it has been assigned a risk rating of 3/5.
When a file is downloaded from the Internet, macOS places it in “quarantine” by assigning it the com.apple.quarantine extended attribute. This ensures that the user is alerted of the potential security risks before the file is executed.
Cavallarin said he found a way to bypass the file quarantine feature by exploiting DOM-based cross-site scripting (XSS) vulnerabilities in an HTML file named rhtmlPlayer.html, which is stored in the /System/Library/CoreServices folder of the OS.
According to the researcher, this file contains two DOM-based XSS vulnerabilities that can be exploited by hackers via Uniform Resource Identifier (URI) components.
One way to exploit the flaw is to use .webloc files, which allow users to save website addresses to the local system. On macOS, these types of files are automatically opened with the Safari web browser.
The attacker needs to embed the JavaScript code they want executed into a .webloc file, send it to the victim, and convince them to open it. Segment has published a detailed technical advisory and a video showing how an attacker can exploit this vulnerability to steal sensitive data from the targeted device:
The vulnerability is said to affect macOS 10.12, 10.11, 10.10 and likely prior versions of the operating system. The issue was reported to Apple via Beyond Security’s SecuriTeam Secure Disclosure (SSD) program and it was addressed without any mention in macOS High Sierra 10.13, which Apple released earlier this week.
Beyond Security told SecurityWeek that it informed Apple of the flaw on July 27. The company said the tech giant did not respond to its questions regarding the issue in the past two weeks.
SecurityWeek has reached out to Apple for clarifications and will update this article if the company responds.
This is not the only macOS vulnerability disclosed in recent days. Earlier this month, researcher Patrick Wardle demonstrated how unsigned apps can steal data from the Keychain password management system, and how attackers can bypass the Secure Kernel Extension Loading (SKEL) security feature.
Threat Landscape for Industrial Automation Systems in H1 2017
28.9.2017 Kaspersky ICS
Full report (PDF)
Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT) publishes the results of its research on the threat landscape for industrial automation systems for the first six months of 2017.
All statistical data used in this report was collected using the Kaspersky Security Network (KSN), a distributed antivirus network. The data was received from those KSN users who gave their consent to have data anonymously transferred from their computers.
The data was received from computers protected by Kaspersky Lab products that Kaspersky Lab ICS CERT categorizes as part of the industrial infrastructure at organizations. This group includes Windows computers that perform one or several of the following functions:
supervisory control and data acquisition (SCADA) servers,
data storage servers (Historian),
data gateways (OPC),
stationary workstations of engineers and operators,
mobile workstations of engineers and operators,
Human Machine Interface (HMI).
This group also includes computers of employees at contractor organizations and computers of industrial control network administrators and software developers who develop software for industrial automation systems.
Main Events
In April, the Shadow Brokers hacker group opened access to a National Security Agency (NSA) archive containing exploits and attack tools.
At first, Shadow Brokers tried to sell their archive. Later, most of it was published. The data that was made public included exploits for network equipment and routers, for banking systems, for UNIX-like systems and for various versions of Windows. Some of the vulnerabilities published were previously unknown zero-day vulnerabilities.
In June 2017, the results of research into the CrashOverride/Industroyer malware were published. Experts from ESET and Dragos Inc., as well as a number of independent researchers, came to the conclusion that the malware was designed to disrupt the operation of industrial control systems (ICS), particularly electrical substations. CrashOverride/Industroyer is capable of directly controlling switches and circuit breakers in electrical substation circuits.
Kaspersky Lab ICS CERT experts reported on Business Email Compromise (BEC) attacks carried out by Nigerian threat actors that were primarily targeting industrial and large transportation and logistics companies. In the attacks analyzed by Kaspersky Lab, industrial companies account for over 80% of potential victims. All in all, over 500 attacked companies were discovered in more than 50 countries.
An important development in the first six months of 2017 was the leak of an archive from a special unit of the US Central Intelligence Agency. The archive included information on CIA hacking tools: malware, including zero-day exploits, malicious remote access tools and related documentation. Part of the archive was published on WikiLeaks.
Ransomware has become a significant threat for companies, including industrial enterprises. It is particularly dangerous for enterprises that have critical infrastructure facilities, since malware activity can disrupt industrial processes.
During the first six months of 2017, attacks by encryption ransomware belonging to 33 different families were blocked on ICS computers. Fortunately, we did not find any dedicated programs designed specifically to block industrial automation software among the malware samples detected.
Based on the number of machines attacked, WannaCry ranked highest in the first half of 2017 – it accounted for 13.4% of all computers in industrial infrastructure attacked by encryption ransomware.
TOP 10 most widespread encryption Trojan families, H1 2017
WannaCry infections were possible because of typical industrial network configuration errors. We analyzed all infection pathways and came to the conclusion that in most cases industrial automation systems had been attacked by WannaCry malware from the local corporate network and through VPN connections.
Threat Statistics
In the first half of 2017, Kaspersky Lab products blocked attack attempts on 37.6% of ICS computers protected by them globally, which is 1.6 percentage points less than in the second half of 2016.
While the proportion of machines attacked grew from one month to the next in the second half of 2016, the dynamics were somewhat different in the first six months of 2017. We saw attacker activity fall in January, then the proportion of computers attacked rose back to its former level in February and March and then it gradually declined again from April to June.
Percentage of ICS computers attacked globally by month,
July 2016 – June 2017
In terms of the use cases and the technologies used, industrial networks are becoming increasingly similar to corporate networks. Consequently, the threat landscape for industrial systems is becoming similar to the threat landscape for corporate systems.
About 18,000 different modifications of malware belonging to more than 2,500 different families were detected on industrial automation systems in the first half of 2017.
In the first half of 2017, attempts to download malware from the Internet or access known malicious or phishing web resources were blocked on 20.4% of ICS computers.
For computers that are part of industrial infrastructure, the Internet remains the main source of infection. Contributing factors include interfaces between corporate and industrial networks, availability of limited Internet access from industrial networks, and connection of computers on industrial networks to the Internet via mobile phone operators’ networks (using mobile phones, USB modems and/or Wi-Fi routers with 3G/LTE support).
Main sources of threats blocked on ICS computers, H1 2017
Malware in the form of Windows (Win32/Win 64) executable files was blocked on more than 50% of all computers attacked. Instead of developing an executable file, threat actors often implement malicious functionality using a script language, which is executed by interpreters that are already installed on the computer of a would-be victim. A ranking of the main platforms used by malware apart from Windows is provided below.
Platforms used by malware, H1 2017
Note that attackers often use small loaders written in JavaScript, Visual Basic Script or Powershell, which are launched using command-line parameters for the relevant interpreters.
A simple example of a complex cyberattack
28.9.2017 Kaspersky Cyber
We’re already used to the fact that complex cyberattacks use 0-day vulnerabilities, bypassing digital signature checks, virtual file systems, non-standard encryption algorithms and other tricks. Sometimes, however, all of this may be done in much simpler ways, as was the case in the malicious campaign that we detected a while ago – we named it ‘Microcin’ after microini, one of the malicious components used in it.
We detected a suspicious RTF file. The document contained an exploit to the previously known and patched vulnerability CVE-2015-1641; however, its code had been modified considerably. Remarkably, the malicious document was delivered via websites that targeted a very narrow audience, so we suspected early on that we were dealing with a targeted attack. The threat actors took aim at users visiting forums with discussions on the state-subsidized housing that Russian military personnel and their families are entitled to.
A forum post with a link to the malicious document
This approach appears to be very effective, as it substantially increases the chance that a potential victim will download and open the malicious document: the hosting forum is legitimate, and the malicious document is named accordingly (“Housing acceptance procedure” in Russian).
All links in the forum messages lead to the URL address files[.]maintr**plus[.]com, where the RTF document with the exploit was hosted. The threat actors sometimes used PPT files containing an executable PE file which did not contain the exploit, as the payload was launched by a script embedded into the PPT file.
If a Microsoft Office vulnerability is successfully exploited, the exploit creates an executable PE file on the hard drive and launches it for execution. The malicious program is a platform used to deploy extra (add-on) malicious modules, store them stealthily and thus add new capabilities for the threat actors. The attack unfolds in several stages, as described below:
The exploit is activated, and an appropriate (32-bit or 64-bit) version of the malicious program is installed on the victim computer, depending on the type of operating system installed on it. To do this installation, malicious code is injected into the system process ‘explorer.exe’ rather than into its memory. The malicious program has a modular structure: its main body is stored in the registry, while its add-on modules are downloaded following the instruction arriving from the C&C server. DLL hijacking (use of a modified system library) is used to ensure that the main module is launched each time the system is rebooted.
The main module of the malicious program receives an instruction to download and launch add-on modules, which opens new capabilities for the threat actors.
The malicious add-on modules provide opportunities to control the victim system, take screenshots of windows and intercept information entered from the keyboard. We have seen them in other cyber-espionage campaigns as well.
The threat actors use PowerSploit, a modified set of PowerShell scripts, and various utilities to steal files and passwords found on the victim computer.
The cybercriminals were primarily interested in .doc, .ppt, .xls, .docx, .pptx, .xlsx, .pdf, .txt and .rtf files on the victim computers. The harvested files were packed into a password-protected archive and sent to the threat actors’ server.
Overall, the tactics, techniques and procedures that the cybercriminals used in their attacks can hardly be considered complicated or expensive. However, there were a few things that caught our eye:
The payload (at least one of the modules) is delivered using some simple steganography. Within traffic, it looks like a download of a regular JPEG image; however, the encrypted payload is loaded immediately after the image data. Microcin searches for a special ‘ABCD’ label in such a file; it is followed by a special structure, after which the payload comes, to be decrypted by Microcin. This way, new, platform-independent code and/or PE files can be delivered.
If the Microcin installer detects the processes of some anti-malware programs running in the system, then, during installation, it skips the step of injecting into ‘explorer.exe’, and the modified system library used for establishing the malicious program within the system is placed into the folder %WINDIR%; to do this, the system app ‘wusa.exe’ is used with the parameter “/extract” (on operating systems with UAC).
Conclusion
No fundamentally new technologies are used in this malicious campaign, be it 0-day vulnerabilities or innovations in invasion or camouflaging techniques. The threat actors’ toolkit includes the following:
A watering hole attack with a Microsoft Office exploit;
Fileless storage of the main set of malicious functions (i.e., the shellcode) and the add-on modules;
Invasion into a system process without injecting code into its memory;
DLL hijacking applied to a system process as a means of ensuring automatic launch that does not leave any traces in the registry’s autorun keys.
The attackers also make use of PowerShell scripts that are used extensively in penetration tests. We have seen backdoors being used in different targeted attacks, while PowerSploit is an open-source project. However, cybercriminals can use known technologies as well to achieve their goals.
The most interesting part of this malicious campaign, in our view, is the attack vectors used in it. The organizations that are likely to find themselves on the cybercriminals’ target lists often do not pay any attention to these vectors.
First, if your corporate infrastructure is well protected and therefore ‘expensive’ to attack (i.e., an attack may require expensive 0-day exploits and other complicated tools), then the attackers will most likely attempt to attack your rank-and-file employees. This step follows a simple logic: an employee’s personal IT resources (such as his/her computer or mobile device) may become the ‘door’ leading into your corporate perimeter without the need of launching a direct attack. Therefore, it is important for organizations to inform their employees about the existing cyber threats and how they work.
Second, Microcin is just one out of a multitude of malicious campaigns that use tools and methods that are difficult to detect using standard or even corporate-class security solutions. Therefore, we recommend that large corporations and government agencies use comprehensive security solutions to protect against targeted attacks. These products are capable of detecting an ongoing attack, even if it employs only a minimum of manifestly malicious tools, as the attackers instead seek to use legal tools for penetration testing, remote control and other tasks.
The implementation of a comprehensive security system can substantially reduce the risk of the organization falling victim to a targeted attack, even though it is still unknown at the time of the attack. There is no way around it; without proper protection, your secrets may be stolen, and information is often more valuable than the cost of its reliable protection.
For more details of this malicious attack, please read Attachment (PDF).
FIN7 Hackers Use LNK Embedded Objects in Fileless Attacks
28.9.2017 securityweek Virus
The infamous FIN7 hacking group has been distributing malware through a LNK file embedded in a Word document via the Object Linking and Embedding (OLE) technology, Cisco Talos security researchers say.
FIN7, also known as Anunak, or Carbanak, is a financially motivated group that has been highly active since the beginning of this year.
While analyzing the attack, the Talos researchers found that the hackers were using an RTF document containing an LNK embedded OLE object that extracted a JavaScript bot and injected an information stealer into memory using PowerShell. The tactic allowed the final payload to be executed onto the target machine without it ever touching the disk.
The use of RTF documents containing an embedded JavaScript OLE object isn’t a novel technique, and the use of LNK files for infection has been associated with the FIN7 group before. What the security researchers did discover, however, was that the JavaScript differs from one attack to another in order to avoid detection.
In early 2017, the group had been using multiple tools in attacks, and began refining their phishing techniques several months later, while also leveraging shims for persistence.
The use of reflective DLL injection PowerShell code in association with LNK embedded OLE objects for malware delivery shows that the sophisticated group is consistently changing techniques between attacks to avoid detection, Cisco Talos notes.
As part of the analyzed attack, the LNK file is used to execute wscript.exe with the beginning of the JavaScript chain from a Word document object.
The DLL’s analysis reveals data stealing functionality and the targeting of a multitude of applications for this purpose, namely Outlook, Firefox, Google Chrome, Chromium, and forks of Chromium and Opera browsers.
The stolen data is dumped to %APPDATA%\%USERNAME%.ini, then read and encrypted using the SimpleEncrypt function, after which it is sent to a hardcoded command and control (C&C) server using POST requests. The Google Apps Script hosting service is included among the hardcoded addresses, which is not surprising, as the Carbanak group was seen abusing Google services before.
“The FIN7 group is an example of an advanced adversary targeting a variety of industries using conventional technologies that ship with most versions of Microsoft Windows. Through the use of Microsoft Word documents to ship entire malware platforms they have the ability to leverage scripting languages to access ActiveX controls, and "file-less" techniques to inject shipped portable executables into memory using PowerShell without ever having the portable executable touch disk,” Cisco concludes.