
Booking a Taxi for Faketoken
17.8.2017 Kaspersky Android
The Trojan-Banker.AndroidOS.Faketoken malware has been known about for already more than a year. Throughout the time of its existence, it has worked its way up from a primitive Trojan intercepting mTAN codes to an encrypter. The authors of its newer modifications continue to upgrade the malware, while its geographical spread is growing. Some of these modifications contain overlay mechanisms for about 2,000 financial apps. In one of the newest versions, we also detected a mechanism for attacking apps for booking taxis and paying traffic tickets issued by the Main Directorate for Road Traffic Safety.
Not so long ago, thanks to our colleagues from a large Russian bank, we detected a new Trojan sample, Faketoken.q, which contained a number of curious features.
Infection
We have not yet managed to reconstruct the entire chain of events leading to infection, but the application icon suggests that the malware sneaks onto smartphones through bulk SMS messages with a prompt to download some pictures.
The malware icon
The structure of the malware
The mobile Trojan that we examined consists of two parts. The first part is an obfuscated dropper (verdict: Trojan-Banker.AndroidOS.Fyec.az): files like this are usually obfuscated on the server side in order to resist detection. At first glance, it may seem that its code is gibberish:
However, this is code works quite well. It decrypts and launches the second part of the malware. This is standard practice these days, whereas unpacked Trojans are very rare.
The second part of the malware, which is a file with DAT extensions, contains the malware’s main features. The data becomes encrypted:
By decrypting the data, it is possible to obtain a rather legible code:
After the Trojan initiates, it hides its shortcut icon and starts to monitor all of the calls and whichever apps the user launches. Upon receiving a call from (or making a call to) a certain phone number, the malware begins to record the conversation and sends it to evildoers shortly after the conversation ends.
The code for recording a conversation
The authors of Faketoken.q kept the overlay features and simplified them considerably. So, the Trojan is capable of overlaying several banking and miscellaneous applications, such as Android Pay, Google Play Store, and apps for paying traffic tickets and booking flights, hotel rooms, and taxis.
Faketoken.q monitors active apps and, as soon as the user launches a specific one, it substitutes its UI with a fake one, prompting the victim to enter his or her bank card data. The substitution happens instantaneously, and the colors of the fake UI correspond to those of the original launched app.
It should be noted that all of the apps attacked by this malware sample have support for linking bank cards in order to make payments. However, the terms of some apps make it mandatory to link a bank card in order to use the service. As millions of Android users have these applications installed, the damage caused by Faketoken can be significant.
However, the following question may arise: what do fraudsters do in order to process a payment if they have to enter an SMS code sent by the bank? Evildoers successfully accomplish this by stealing incoming SMS messages and forwarding them to command-and-control servers.
We are inclined to believe that the version that we got our hands on is still unfinished, as screen overlays contain formatting artifacts, which make it easy for a victim to identify it as fake:
The screen overlays for the UI of a taxi-booking app
As screen overlays are a documented feature widely used in a large number of apps (window managers, messengers, etc.), protecting yourself against such fake overlays is quite complicated, a fact that is exploited by evildoers.
To this day we still have not registered a large number of attacks with the Faketoken sample, and we are inclined to believe that this is one of its test versions. According to the list of attacked applications, the Russian UI of the overlays, and the Russian language in the code, Faketoken.q is focused on attacking users from Russia and CIS countries.
Precautions
In order to avoid falling victim to Faketoken and apps similar to it, we strongly discourage the installation of third-party software on your Android device. A mobile security solution like Kaspersky Mobile Antivirus: Web Security & AppLock would be quite helpful too.
MD5
CF401E5D21DE36FF583B416FA06231D5
ShadowPad in corporate networks
17.8.2017 Kasprsky Cyber
ShadowPad, part 2: Technical Details (PDF)
In July 2017, during an investigation, suspicious DNS requests were identified in a partner’s network. The partner, which is a financial institution, discovered the requests originating on systems involved in the processing of financial transactions.
Further investigation showed that the source of the suspicious DNS queries was a software package produced by NetSarang. Founded in 1997, NetSarang Computer, Inc. develops, markets and supports secure connectivity solutions and specializes in the development of server management tools for large corporate networks. The company maintains headquarters in the United States and South Korea.
NetSarang website
Our analysis showed that recent versions of software produced and distributed by NetSarang had been surreptitiously modified to include an encrypted payload that could be remotely activated by a knowledgeable attacker.
The backdoor was embedded into one of the code libraries used by the software (nssock2.dll):
Backdoored dll in a list of loaded modules of Xshell5 sofware
Disposition of the NSSOCK2.DLL binary with embedded malicious code
The attackers hid their malicious intent in several layers of encrypted code. The tiered architecture prevents the actual business logics of the backdoor from being activated until a special packet is received from the first tier command and control (C&C) server (“activation C&C server”). Until then, it only transfers basic information, including the computer, domain and user names, every 8 hours.
Activation of the payload would be triggered via a specially crafted DNS TXT record for a specific domain. The domain name is generated based on the current month and year values, e.g. for August 2017 the domain name used would be “nylalobghyhirgh.com”.
DNS queries to C&C from backdoored nssock2.dll
Only when triggered by the first layer of C&C servers does the backdoor activate its second stage
The module performs a quick exchange with the controlling DNS server and provides basic target information (domain and user name, system date, network configuration) to the server. The C&C DNS server in return sends back the decryption key for the next stage of the code, effectively activating the backdoor. The data exchanged between the module and the C&C is encrypted with a proprietary algorithm and then encoded as readable latin characters. Each packet also contains an encrypted “magic” DWORD value “52 4F 4F 44” (‘DOOR’ if read as a little-endian value).
Our analysis indicates the embedded code acts as a modular backdoor platform. It can download and execute arbitrary code provided from the C&C server, as well as maintain a virtual file system (VFS) inside the registry. The VFS, and any additional files created by the code, are encrypted and stored in a location unique to each victim. The remote access capability includes a domain generation algorithm (DGA) for C&C servers which changes every month. The attackers behind this malware have already registered the domains covering July to December 2017, which indirectly confirms alleged start date of the attack as around mid July 2017.
Currently, we can confirm activated payload in a company in Hong Kong. Given that the NetSarang programs are used in hundreds of critical networks around the world, on servers and workstations belonging to system administrators, it is strongly recommended that companies take immediate action to identify and contain the compromised software.
Kaspersky Lab products detect and protect against the backdoored files as “Backdoor.Win32.ShadowPad.a”.
We informed NetSarang of the compromise and they immediately responded by pulling down the compromised software suite and replacing it with a previous clean version. The company has also published a message acknowledging our findings and warning their customers.
ShadowPad is an example of the dangers posed by a successful supply-chain attack. Given the opportunities for covert data collection, attackers are likely to pursue this type of attack again and again with other widely used software components. Luckily, NetSarang was fast to react to our notification and released a clean software update, most likely preventing hundreds of data-stealing attacks against their clients. This case is an example of the value of threat research as a means to secure the wider internet ecosystem. No single entity is in a position to defend all of the links in an institution’s software and hardware supply-chain. With successful and open cooperation, we can help weed out the attackers in our midst and protect the internet for all users, not just our own.
For more information please contact: intelreports@kaspersky.com
Frequently Asked Questions
What does the code do if activated?
If the backdoor were activated, the attacker would be able to upload files, create processes, and store information in a VFS contained within the victim’s registry. The VFS and any additional files created by the code are encrypted and stored in locations unique to each victim.
Which software packages were affected?
We have confirmed the presence of the malicious file (nssock2.dll) in the following packages previously available on the NetSarang site:
Xmanager Enterprise 5 Build 1232
Xme5.exe, Jul 17 2017, 55.08 MB
MD5: 0009f4b9972660eeb23ff3a9dccd8d86
SHA1: 12180ff028c1c38d99e8375dd6d01f47f6711b97
Xmanager 5 Build 1045
Xmgr5.exe, Jul 17 2017, 46.2 MB
MD5: b69ab19614ef15aa75baf26c869c9cdd
SHA1: 35c9dae68c129ebb7e7f65511b3a804ddbe4cf1d
Xshell 5 Build 1322
Xshell5.exe, Jul 17 2017, 31.58 MB
MD5: b2c302537ce8fbbcff0d45968cc0a826
SHA1: 7cf07efe04fe0012ed8beaa2dec5420a9b5561d6
Xftp 5 Build 1218
Xftp5.exe, Jul 17 2017, 30.7 MB
MD5: 78321ad1deefce193c8172ec982ddad1
SHA1: 08a67be4a4c5629ac3d12f0fdd1efc20aa4bdb2b
Xlpd 5 Build 1220
Xlpd5.exe, Jul 17 2017, 30.22 MB
MD5: 28228f337fdbe3ab34316a7132123c49
SHA1: 3d69fdd4e29ad65799be33ae812fe278b2b2dabe
Is NetSarang aware of this situation?
Yes, we contacted the vendor and received a swift response. Shortly after notification by Kaspersky Lab all malicious files were removed from NetSarang website.
How did you find the software was backdoored?
During an investigation, suspicious DNS requests were identified on a partner’s network. The partner, which is a financial institution, detected these requests on systems related to the processing of financial transactions. Our analysis showed that the source of these suspicious requests was a software package produced by NetSarang.
When did the malicious code first appear in the software?
A fragment of code was added in nssock2.dll (MD5: 97363d50a279492fda14cbab53429e75), compiled Thu Jul 13 01:23:01 2017. The file is signed with a legitimate NetSarang certificate (Serial number: 53 0C E1 4C 81 F3 62 10 A1 68 2A FF 17 9E 25 80). This code is not present in the nssock2.dll from March (MD5: ef0af7231360967c08efbdd2a94f9808) included with the NetSarang installation kits from April.
How do I detect if code is present on a system?
All Kaspersky Labs products detect and cure this threat as Backdoor.Win32.Shadowpad.a. If for some reason you can’t use an antimalware solution you can check if there were DNS requests from your organization to these domains:
ribotqtonut[.]com
nylalobghyhirgh[.]com
jkvmdmjyfcvkf[.]com
bafyvoruzgjitwr[.]com
xmponmzmxkxkh[.]com
tczafklirkl[.]com
notped[.]com
dnsgogle[.]com
operatingbox[.]com
paniesx[.]com
techniciantext[.]com
How do I clean any affected systems?
All Kaspersky Lab products successfully detect and disinfect the affected files as “Backdoor.Win32.Shadowpad.a” and actively protect against the threat.
If you do not have a Kaspersky product installed, then:
Update to the latest version of the NetSarang package.
Block DNS queries to the C2 domains listed in Appendix A.
What kind of companies/organizations/ are targeted by the attackers?
Based on the vendor profile, the attackers could be after a broad set of companies who rely on NetSarang software, which includes banking and financial industry, software and media, energy and utilities, computers and electronics, insurance, industrial and construction, manufacturing, pharmaceuticals, retail, telecommunications, transportation and logistics and other industries.
Who is behind this attack?
Attribution is hard and the attackers were very careful to not leave obvious traces. However certain techniques were known to be used in another malware like PlugX and Winnti, which were allegedly developed by Chinese-speaking actors.
How did the attackers manage to get access to create trojanized updates. Does that mean that NetSarang was hacked?
An investigation is in progress, but since code was signed and added to all software packages it could point to the fact that attackers either modified source codes or patched software on the build servers.
Appendix A – Indicators of Compromise
At this time, we have confirmed the presence of the malicious “nssock2.dll” in the following packages downloaded from the NetSarang site:
Xmanager Enterprise 5 Build 1232
Xme5.exe, Jul 17 2017, 55.08 MB
MD5: 0009f4b9972660eeb23ff3a9dccd8d86
SHA1: 12180ff028c1c38d99e8375dd6d01f47f6711b97
Xmanager 5 Build 1045
Xmgr5.exe, Jul 17 2017, 46.2 MB
MD5: b69ab19614ef15aa75baf26c869c9cdd
SHA1: 35c9dae68c129ebb7e7f65511b3a804ddbe4cf1d
Xshell 5 Build 1322
Xshell5.exe, Jul 17 2017, 31.58 MB
MD5: b2c302537ce8fbbcff0d45968cc0a826
SHA1: 7cf07efe04fe0012ed8beaa2dec5420a9b5561d6
Xftp 5 Build 1218
Xftp5.exe, Jul 17 2017, 30.7 MB
MD5: 78321ad1deefce193c8172ec982ddad1
SHA1: 08a67be4a4c5629ac3d12f0fdd1efc20aa4bdb2b
Xlpd 5 Build 1220
Xlpd5.exe, Jul 17 2017, 30.22 MB
MD5: 28228f337fdbe3ab34316a7132123c49
SHA1: 3d69fdd4e29ad65799be33ae812fe278b2b2dabe
Domains:
ribotqtonut[.]com
nylalobghyhirgh[.]com
jkvmdmjyfcvkf[.]com
bafyvoruzgjitwr[.]com
xmponmzmxkxkh[.]com
tczafklirkl[.]com
notped[.]com
dnsgogle[.]com
operatingbox[.]com
paniesx[.]com
techniciantext[.]com
DLL with the encrypted payload:
97363d50a279492fda14cbab53429e75
NetSarang packages which contain the DLL with the encrypted payload (same as above, just the list of MD5 sums):
0009f4b9972660eeb23ff3a9dccd8d86
b69ab19614ef15aa75baf26c869c9cdd
b2c302537ce8fbbcff0d45968cc0a826
78321ad1deefce193c8172ec982ddad1
28228f337fdbe3ab34316a7132123c49
File names:
nssock2.dll
Locky Ransomware Campaign Ramps Up
17.8.2017 securityweek Ransomware
The Locky ransomware family that dominated the charts last year has returned, and has been distributed through high volume campaigns over the past week.
Closely tied to the activity of the Necurs botnet, Locky has been nearly completely absent from the threat landscape this year. Following several months of total silence, the ransomware was present in spam runs in April and May, but went under the radar within weeks, as Necurs switched to distributing the Jaff ransomware.
On August 9, however, new spam campaigns dropping Locky caught the attention of security researchers. The first to observe the new ransomware variant was Racco42, who revealed that the spam messages contained subject lines similar to E [date] (random_numer).docx.
The Locky variant featured in that campaign was appending the .diablo6 extension to encrypted files and was downloaded by a VBS script packed inside a ZIP attachment. The malware demands a 0.49 Bitcoin ransom (currently about $2,250).
According to Fortinet, the malicious emails were mainly targeted at victims in the United States (37%) and Austria (36%). A large portion of them (10%) hit users in the UK. The security researchers also note that the new Locky variant packs the same capabilities as the last year version, and that free decryption isn’t possible.
Comodo, which performed a detailed analysis of the recent Locky attacks, calls the new ransomware variant IKARUSdilapidated, based on the appearance of the word in the code string. The security firm also says that tens of thousands of phishing emails featuring subject lines and attachments named similar to E [date] (random_numer) were observed over the course of several days dropping Locky.
A closer look at these emails revealed that 11,625 different IP addresses from 133 countries were used in this campaign, with Vietnam, India, Mexico, Turkey, and Indonesia being the top five. Most of the IP owners are telecom companies and ISPs, meaning that they belong “to infected, now compromised computers,” essentially forming a botnet, Comodo notes in a report shared with SecurityWeek.
Earlier this week, another Locky variant emerged, one that would append the .Lukitus extension to the encrypted files, Malwarebytes says. The spam emails feature either no subject or something similar to Emailing - CSI-034183_MB_S_7727518b6bab2 as subject line, and include a RAR or ZIP attachment that has JS files inside, which in turn download Locky.
To stay protected, users should keep their files backed up at all times and should also avoid opening attachments or clicking on links coming via email from unknown sources. Keeping the operating system and all applications on the computer updated at all times should also prevent infections from happening.
“It’s still too early to say if this campaign signals the start of Locky diving back into the ransomware race or if it is just testing the waters. We’ll probably see in the next few weeks or months,” Fortinet says.
U.S. Army to Protect Warfighters With Continuous Biometric Authentication
17.8.2017 securityweek BigBrothers
U.S. Army's NETCOM to Deploy Continuous Biometric Authentication Software to Protect Warfighters
The fundamental basis of security is to stop bad guys (or things) getting in; and then, if that fails, to discover those who got in as rapidly as possible. Authentication is used for the former, and network anomaly detection is increasingly used for the latter.
Both controls can be good in theory, but often fall down in practice; the more effective they are, the more intrusive they become. Authentication can be strengthened by enforcing strong unmemorable passwords, and multi-factor authentication -- often making it difficult and time-consuming for the user. Anomaly detection can be improved by reporting and responding to every single alert -- often overwhelming security analysts with the sheer volume of work.
To solve both problems, companies often set their security barriers lower than they could be. Authentication is made easier and alerts are set lower so that work is less interrupted. As a result, adversaries can get into the network and stay hidden long enough to cause damage -- and this is demonstrated every week by new announcements of both major and minor breaches.
Plurilock believes it may have the answer in low-friction continuous behavioral biometric user authentication. Called BioTracker, the product continuously (sampling every few seconds) monitors the user, analyzing key stroke and mouse patterns and using artificial intelligence (AI) to provide a probability score on the current user being the authorized user.
In its own words, Plurilock today announced, "The U.S. Army Network Enterprise Technology Command (NETCOM) will deploy Plurilock’s BioTracker continuous authentication cybersecurity software to protect the warfighter against adversarial identity compromise."
Keith Trippie, retired executive director for the Enterprise System Development Office with the U.S. Department of Homeland Security, explains, “BioTracker enhances government and corporate cybersecurity by bolstering existing authentication capabilities such as CACs, two-factor, multi-factor and even biometric authentication, to safeguard vital data, intelligence systems and privileged accounts from both sophisticated cyber campaigns and insider threats. Plurilock’s platform provides reliable, real-time visibility and security with virtually zero authorized user friction."
This means that the initial user authentication barrier can be set very low, so that daily work is not interrupted. From then on, BioTracker monitors the user against known biometric behavioral patterns. Plurilock claims that it takes just 20 minutes to learn a user’s keystroke style and speed, mouse use and other behaviors to build a biometric profile.
CEO Ian Paterson told SecurityWeek that face and voice recognition could be added to the mix, but they had been omitted because of privacy issues from both users and privacy regulations in a corporate environment. Other biometric methods such as fingerprint scans and iris scans increase user friction and remain point rather than continuous authentication.
"Our method," he said, "satisfies privacy issues and introduces zero user friction." Furthermore, he added, it solves a major weakness in biometric authentication. "People change, both with age and over time. BioTracker's continuous monitoring of the user's biometric behavior allows it to detect these slow and minute changes, feeding them back into the known user profile and maintaining biometric accuracy."
Continuous user monitoring marks a huge change from the binary accept/reject approach of traditional user authentication. It is made possible by BioTracker's AI engine. AI generally deals with probability scores rather than just on/off. This allows greater flexibility. For example, the possibility of false positives can be reduced by progressively limiting access. Thus, if for any reason, a user's pattern is slightly off (stress, illness, post-party hangover) BioTracker can be used to limit access to particularly sensitive parts of the network until the user's authenticity is validated.
It is more likely, however, that this biometric monitoring will clearly indicate whether the user is the authorized user. Since the sampling is done every few seconds, recognition that an intruder is on the network is confirmed within seconds of the intrusion. This is where BioTracker can reduce the workload on security analysts. Rather than having to wait for and triage a large number of network anomalies, the analysts know within seconds that it has occurred, and exactly where it occurred. Containment can be effected within minutes of the intrusion.
“Plurilock," explains Paterson, "offers dependable protection against security breaches with real-time detection and immediate notification in the event of unusual user behavior, to reduce risk and cut detection and resolution time from many months to mere minutes, saving precious time and money. Its proof-of-presence technology also ensures outstanding compliance to meet even the most stringent regulatory mandates, and because there are no manual authentication procedures required, it has zero impact on productivity. Users can go about their normal activities with the confidence that Plurilock has them covered.”
NotPetya Attack Costs Big Companies Millions
17.8.2017 securityweek Ransomware
Some of the big companies hit by the NotPetya malware in late June have reported losing hundreds of millions of dollars due to the cyberattack.
The NotPetya malware outbreak affected tens of thousands of systems in more than 65 countries, including ones belonging to major organizations such as Rosneft, AP Moller-Maersk, Merck, FedEx, Mondelez International, Nuance Communications, Reckitt Benckiser and Saint-Gobain. Many of the victims were located in Ukraine, the home of a tax software firm whose product was used as the main attack vector.
Researchers initially believed NotPetya (aka PetrWrap, exPetr, GoldenEye and Diskcoder.C) was a piece of ransomware, similar to WannaCry. However, a closer analysis revealed that it was actually a wiper and it was unlikely that victims could recover their files, even if they paid the ransom.
Financial reports published by the affected companies in the past few weeks show that the cyberattack has caused serious damage in many cases. FedEx-owned international delivery services company TNT Express, for instance, said there was a possibility that some business data may never be recovered.
Danish shipping giant AP Moller-Maersk estimates that the attack has cost it $200-$300 million. The conglomerate believes the cyberattack will have a significant impact on its finances in the third quarter due to revenue lost in July.
American pharmaceutical giant Merck had still been working on restoring operations in late July. In its latest financial results announcement, the firm said the cyberattack had disrupted its worldwide operations, including manufacturing, research and sales, but did not specify the exact losses caused by the incident.
Reckitt Benckiser, the British consumer goods company that makes Nurofen, Dettol and Durex, said the attack disrupted its ability to manufacture and distribute products. It estimated that the incident could have an impact of $130 million on its revenue.
Voice and language solutions provider Nuance Communications reported GAAP revenue of $486.2 million and non‑GAAP revenue of $495.6 million in the third quarter. The company estimates that the third-quarter GAAP revenues would have been $501.6 million and non-GAAP revenues $511.0 million had the malware incident not taken place. Nuance said its healthcare business was the most impacted.
Mondelez International, owner of U.K. chocolate maker Cadbury, estimated the cost of the attack at just over $150 million in lost sales and incremental expenses. The company, whose sales, distribution and financial networks were impacted by the malware, expects the recovery process to continue into the second half of 2017.
French construction giant Saint-Gobain said the attack led to donwtime of IT systems and supply chain disruptions. The NotPetya attack has had a negative impact of €220 million ($258 million) on sales and €65 million ($76 million) on operating income in the first half of 2017. Until the end of the year, total losses are expected to rise to €330 million ($387 million).
German consumer goods provider Beiersdorf was also hit by the attack and while it expects sales worth roughly €35 million ($41 million) to be shifted from the second quarter to the third, the company does not expect a material impact on its profits for this year.
Drupal maintainers fix several access bypass vulnerabilities in Drupal 8
17.8.2017 securityaffairs Vulnerebility
Drupal maintainers this week released security updates to fix several access bypass vulnerabilities in Drupal 8. Update your installation.
On Wednesday Drupal maintainers released security updates to fix several access bypass vulnerabilities in Drupal 8. The flaws affect several components, including the entity access system, the REST API and some views.
The most severe vulnerability patched by Drupal 8.3.7 is a critical issue, tracked as CVE-2017-6925 that affects the entity access system. The CVE-2017-6925 flaw can be exploited by an attacker to view, create, delete or update entities.
The flaw impacts only entities that don’t have UUIDs and ones that have different access restrictions on different revisions of the same entity.
“There is a vulnerability in the entity access system that could allow unwanted access to view, create, update, or delete entities. This only affects entities that do not use or do not have UUIDs, and entities that have different access restrictions on different revisions of the same entity.” reads the advisory.
Another access bypass vulnerability patched in the latest version of Drupal 8, CVE-2017-6924, resides in the REST API and could be exploited to bypass comment approval.
“When using the REST API, users without the correct permission can post comments via REST that are approved even if the user does not have permission to post approved comments,” Drupal continues the advisory. “This issue only affects sites that have the RESTful Web Services (rest) module enabled, the comment entity REST resource enabled, and where an attacker can access a user account on the site with permissions to post comments, or where anonymous users can post comments.”
This vulnerability has been rated because it affects only sites that have the RESTful Web Services module and the comment entity REST resource enabled.

Security advisory adds that are attackers needs access to a user account that is allowed to post comments to trigger the issue, or the targeted website needs to allow comments from anonymous users.
Another flaw rated as moderately critical fixed in Drupal 8 is tracked as CVE-2017-6923 and affects the “views” component.
“When creating a view, you can optionally use Ajax to update the displayed data via filter parameters. The views subsystem/module did not restrict access to the Ajax endpoint to only views configured to use Ajax. This is mitigated if you have access restrictions on the view,” Drupal said. “It is best practice to always include some form of access restrictions on all views, even if you are using another module to display them.”
Update your Drupal installation!
Cyber Criminals Hijack Chrome Extensions and put 4.7 Million Users at Risk
17.8.2017 securityaffairs CyberCrime
Developer accounts of popular chrome extensions being hijacked by cyber criminals, over 4.7 million users are at a risk of cyber attack.
Over 4.7 million users could be at risk after being exposed to malicious adverts and credentials theft due to developer accounts of popular chrome extensions being hijacked by cyber criminals.
A phishing campaign run by Cyber Criminals in July that targeted chrome extension developers, with the purpose of harvesting their Google account credentials, has led to 8 very popular chrome extensions being compromised.
“At the end of July and beginning of August, several Chrome Extensions were compromised after their author’s Google Account credentials were stolen via a phishing scheme. This resulted in hijacking of traffic and exposing users to potentially malicious popups and credential theft.” reported the analysis of the security firm Proofpoint.

Figure 1 – example of phishing email- source Proofpoint
Using the compromised developer accounts, the threat actors were able to inject code in to the legitimate extensions that would serve its users substituted adverts to adult websites, windows repair scams, and in some cases credentials harvesting. Research conducted by Proofpoint reported that the affected extensions include:
Web Developer- 1,044,016 users
Chrometana- 597, 577 users
Infinity New Tab- 476, 803 users
CopyFish- 37,397 uses
Web Paint- 53,930 users
Social Fixer- 182, 083 users
TouchVPN- 1,031,690 users
Betternet VPN- 1, 334,517 users
Some of the tactics used by the threat actors were to check whether the Chrome Extension had been installed for 10 minutes – commonly thought to bypass detection.
if ((Date.now() – installed) > 10 * 60 * 1000)
This check was made before proceeding with the rest of the extension code which resulted in retrieving a remote file “ga.js” from a server which the domain is generated via DGA (Domain Generation Algorithm), this call is made over HTTPS.
One of the objectives of compromised version of the extension was to attempt to substitute legitimate adverts on the victim’s browser, hijacking traffic from legitimate advertising networks and replacing with services (usually adult in nature), that the threat actors would profit from.
“While the attackers substituted ads on a wide range of websites, they devoted most of their energy to carefully crafted substitutions on adult websites” continues Proofpoint.
The adverts worked for a specific set of 33 banner sizes shown in the code snippet from 973820_BNX.js?rev=133 below:

Figure 2 Banner size for substituted malicious adverts source Proofpoint
Also, it was noted in the research conducted by Proofpoint concluded that similar pop up alerts known to be associated with the compromise of Infinity New Tab extension in May and fake EU cookie-consent alert last year were also found in this campaign.
In summary, attackers are increasingly targeting developers through a phishing email, as a way to gain access to a large user base to quickly generate traffic to their affiliate schemes or gather credentials than can be later harvested for profit.
This is a worrying trend and developers need to be more aware of the increased risks, it was only 6 months ago when researchers discovered that attackers were targeting developers of Github repositories to gain access to fintech or high tech companies.
The tactics on display in this particular campaign are not necessarily new but demonstrate the potential widespread impact of the phishing emails, but a question that hasn’t really been answered is why didn’t the developers have 2FA for their Google developer accounts?
TunnelBear VPN Audit Finds Few Vulnerabilities
17.8.2017 securityweek Vulnerebility
TunnelBear has commissioned a third-party audit of its virtual private network (VPN) application and only a few vulnerabilities have been found in recent versions of the product.
Germany-based security firm Cure53 has analyzed the entire TunnelBear infrastructure, including servers, clients, browser extensions and website. Two separate audits were conducted: one in late 2016 and one in the summer of 2017. In both cases, testers had access to servers and source code.
A significant number of serious vulnerabilities were uncovered in the initial tests, including three critical flaws affecting the browser extension and the macOS client.
Experts discovered that the browser extension VPN could easily be turned off by getting the targeted user to access a specially crafted webpage. The browser extension also allowed attackers to force victims into making requests with the VPN disabled.
As for the macOS client, it was affected by a vulnerability that could allow local root privilege escalation via a malicious application installed on the host.
During the 2016 testing, Cure53 also discovered three high severity flaws affecting the TunnelBear API and Android application. The API weaknesses allowed cross-site request forgery (CSRF) attacks that could be used to cancel subscriptions, and phishing attacks via invite emails. The Android app could have been caused to crash and lose the connection.
Testers also discovered 13 medium, 8 low and 13 informational issues during the initial audit.
Six months later, after TunnelBear worked on improving the security of its product, Cure53 conducted another assessment. This time, no critical vulnerabilities were discovered.
Experts did find one high severity bug that could have been exploited by an attacker with direct access to the server to obtain files containing sensitive information. Cure53 also identified four medium, three low severity, and five informational issues.
All vulnerabilities have been patched by TunnelBear; only some of the findings rated “informational” remain unaddressed.
“The progress made by TunnelBear over the course of half a year demonstrates how the potential of a security audit and advice in the VPN realm may be harnessed to hoist up the safeguarding strategies within the entire software compound,” Cure53 said in a summary report. “After undergoing the first challenging security test which ended with several critical & high severity findings, the TunnelBear team seems to have redoubled efforts on security.”
TunnelBear said it had initially planned not to release the results of the initial audit, but later determined that being transparent better demonstrated its investment in security.
“Our plan is to earn trust and move the VPN industry in a new direction around transparency. While many VPN companies will continue to live in obscurity, with claims of protecting your security, it’s our hope that by completing the industry's first 3rd party, public security audit, experts and consumers alike can be sure that TunnelBear delivers on its security promises,” TunnelBear said in a blog post.
Game of Thrones and HBO — Twitter, Facebook Accounts Hacked
17.8.2017 thehackernews Hacking
The Game of Thrones hacking saga continues, but this time it's the HBO's and GOT's official Twitter and Facebook accounts got compromised, rather than upcoming episodes.
As if the leak of episodes by hackers and the accidental airing of an upcoming episode of Game of Thrones by HBO itself were not enough, a notorious group of hackers took over the official Twitter and Facebook accounts for HBO as well as Game of Thrones Wednesday night.
The hacker group from Saudi Arabia, dubbed OurMine, claimed responsibility for the hack, posting a message on both HBO's official Twitter and Facebook accounts, which read:
"Hi, OurMine are here, we are just testing your security, HBO team, please contact us to upgrade the security," followed by a contact link for the group.
This message was followed by another one, wherein hackers asked people to make the hashtag #HBOhacked trending on Twitter, which it did.
Ourmine is the same group of hackers from Saudi Arabia that previously compromised social media accounts of major companies CEOs, including Twitter CEO Jack Dorsey, Facebook CEO Mark Zuckerberg, Google CEO Sundar Pichai, and Facebook-owned virtual reality company Oculus CEO Brendan Iribe.
In most of the cases, Ourmine hackers gain access to the social media accounts by credentials exposed in previous, publicly known data breaches.
However, the hacking group does not seem to ever go beyond just demonstrating its ability to take over the account, without doing much damage to the accounts or its protected information.
OurMine offers companies security against hacking, charging up to $5,000 for a "scan" of their social media accounts, site security holes, and other security vulnerabilities, and advertises its commercial services by breaking into famous accounts.
HBO managed to remove the offending tweets shortly after the hackers posted them.
Just yesterday, in a devastating blunder, HBO Spain accidentally aired Episode 6 of Game of Thrones season 7 five days prior to its official premiere.
The popular entertaining company is also facing a threat from hacker or group of hackers who claimed to have obtained nearly 1.5 terabytes of information from HBO.
Over two weeks ago, the unknown hackers dropped episodes of "Ballers" and "Room 104," along with a script of the fourth episode of Game of Thrones on the internet.
This leak was followed by another dump of a half-gigabyte sample of stolen data, including the company's emails, employment agreements, balance sheets, and the script of the upcoming GOT episode, demanding a ransom—nearly $6 Million in Bitcoins.
Although it was revealed that the company offered hackers $250,000 for extending the ransom payment deadline by one week, the proposal apparently failed to satisfy hackers, and they threatened to release more data every Sunday until the full ransom was paid.
Oopss! HBO Itself Accidentally Leaked 'Game of Thrones' Season 7 Episode 6
17.8.2017 thehackernews Hacking
HBO doesn't need hackers to leak its widely watched "Game of Thrones" episodes, as it is sufficient enough to leak them by its own.
In what seems to be a terrible blunder, HBO Spain appeared to have accidentally broadcast the next episode—Episode 6—of Game of Thrones season 7 five days before its official premiere.
And as expected, the GoT episode 6 quickly began circulating online.
HBO has recently been facing trouble from a hacker or group of hackers who claimed to have obtained nearly 1.5 terabytes of information from the entertainment company.
Late last month, the unknown hackers dropped upcoming episodes of "Ballers" as well as "Room 104," along with a script of the fourth episode of "Game of Thrones" on the internet.
The leak was followed by another dump of a half-gigabyte sample of stolen HBO data, including HBO's emails, employment agreements, and balance sheets, along with the script of the upcoming Game of Thrones episode, demanding a ransom—nearly $6 Million in Bitcoins.
A recently leaked screenshot of an email from an HBO executive also suggested that the company offered hackers $250,000 and requested them to extend the ransom payment deadline by one week.
Sadly, the proposal apparently failed to satisfy the desires of HBO hackers, and they threatened to release more data from its 1.5 terabytes of stolen data every Sunday until the complete ransom of millions of dollars was paid.
However, the recent leak has nothing to do with hackers, and rather the new unreleased episode was accidentally broadcast by HBO Nordic in Spain for about an hour before it was removed, first spotted by Reddit users.
The new GOT episode was purportedly available via the HBO's Spanish on-demand service.
Here's what HBO has to say about the latest leak:
"We have learned that the upcoming episode of Game of Thrones was accidentally posted for a brief time on the HBO Nordic and HBO España platforms."
"The error appears to have originated with a third-party vendor, and the episode was removed as soon as it was recognized. This is not connected to the recent cyber incident at HBO in the US."
Short footage and GIFs from the GOT S07E06 was started circulating on YouTube, Reddit, Instagram, Twitch and other streaming services.
The episode 6 of "Game of Thrones" will officially be premiered on Sunday at 9 p.m. on HBO.
NotPetya ransomware caused $300m losses to the shipping giant Maersk
17.8.2017 securityaffairs Ransomware
The transportation giant Maersk announced that it would incur hundreds of millions in U.S. dollar losses due to the NotPetya ransomware massive attack.
A.P. Moller-Maersk, the transportation and logistics firm, announced Tuesday that it would incur hundreds of millions in U.S. dollar losses due to the NotPetya ransomware massive attack.
According to the second quarter earnings report, there were expecting losses between $200 million and $300 million due to “significant business interruption” because the company was forced to temporarily halt critical systems infected with the ransomware.
“As soon as A.P. Moller – Maersk became aware that systems had been affected, action to respond was initiated including closing down infected networks. The malware was contained to only impact the container related businesses of A.P. Moller” reads the report. “A.P. Moller – Maersk also remained in full control of all vessels throughout the situation, and all employees were safe.”
The company said its Maersk Line APM Terminals and Damco systems were completely shut down in response to the incident as a precaution measure.
“These system shutdowns resulted in significant business interruption during the shutdown period, with limited financial impact in Q2, while the impact in Q3 is larger, due to temporary lost revenue in July (see guidance for 2017),” continues the report.
NotPetya hit hundreds of companies causing serious million of dollars damages, early August, the US pharmaceutical company Merck revealed that the massive NotPetya cyberattack has disrupted its worldwide operations.

Other major companies affected by the NotPetya attack were the Ukraine’s central bank, Russian oil giant Rosneft, advertising group WPP, and the law firm DLA Piper.
Two of the world’s largest consumer goods companies suffered serious problems, on July the companies Mondelez and Reckitt Benckiser warned of the impact of the NotPetya attack on their revenues.
The Mondelez International company estimated the NotPetya attack would cut three percentage points from second-quarter sales growth because of disruptions to shipping and invoices caused by the cyber attack.
The Reckitt Benckiser, the maker of Nurofen painkillers and Durex condoms, said it expected sales would be hit Q2 by an estimated £110m this year.
The company said that its expected overall profit to still exceed 2016 margins despite the impact of the cyberattack.
“This cyber-attack was a previously unseen type of malware, and updates and patches applied to both the Windows systems and antivirus were not an effective protection in this case,” the company said. “In response to this new type of malware, A.P. Moller – Maersk has put in place different and further protective measures and is continuing to review its systems to defend against attacks.”
After Westminster attack, now Scottish parliament hit by brute-forcing attack
17.8.2017 securityaffairs Attack
The Scottish Parliament has been targeted by a “brute force” attack, the assault is still ongoing and is similar to the one that hit the British Parliament.
The Scottish Parliament is under attack, crooks are brute-forcing email accounts in the attempt to access members’ emails.
The attack appears similar to the one that in June targeted the British Parliament and that caused the IT staff to shut down external access to mitigate the threat.
MSPs and Holyrood staff were warned on Tuesday that unidentified hackers were running “brute-force” attacks on systems in the devolved assembly,
“Chief executive Sir Paul Grice said the attack, from “external sources”, was similar to that which affected Westminster in June.
He confirmed the attack in a message to MSPs and staff with parliamentary email addresses, urging them to be vigilant.” reported the BBC.
“Mr Grice said “robust cyber security measures” identified the attack early, and systems “remain fully operational”.”

Mr Grice sent an email to MSPs and Parliament staff to check the security of their passwords and improve it as possible, he also announced a password reset for weak passwords. The IT staff at the Scottish Parliament is urging Legislators and support staff to update their passwords with longer and stronger combinations of letters, numbers and special characters in response.
“The parliament’s monitoring systems have identified that we are currently the subject of a brute force cyber attack from external sources.” reads Mr Grice’s email.
“This attack appears to be targeting parliamentary IT accounts in a similar way to that which affected the Westminster Parliament in June. Symptoms of the attack include account lockouts or failed logins.”
“The parliament’s robust cyber security measures identified this attack at an early stage and the additional security measures which we have in readiness for such situations have already been invoked. Our IT systems remain fully operational.”
Russian state-sponsored hackers were blamed for the attacks against Westminster systems occurred in June that led to the exposure of at least 90 accounts.
According to El Reg that has seen the message issued to all MSPs and staff at Holyrood, the cyber-attack is still ongoing and there is no evidence to suggest that the hackers have breached Scottish Parliament defences. IT systems continue to be fully operational.
Sincerely speaking I really don’t understand why sensitive email accounts are not protected by a two-factor authentication mechanism and why users are not forced to use strong passwords.
Researchers Uncover Infrastructure Behind Chthonic, Nymaim Trojans
17.8.2017 securityweek Virus
While analyzing malware that uses PowerShell for infection, Palo Alto Networks managed to uncover the infrastructure behind recent attacks that leveraged the Chthonic and Nymaim Trojans, along with other threats.
The analysis kicked off from one malicious sample, but resulted in security researchers from Palo Alto Networks being able to identify 707 IPs and 2,611 domains supposedly being utilized for malicious activity. While some of these resources are used to host malware, others are leveraged in other types of attacks and schemes, the researchers say.
Palo Alto Networks’ Jeff White explains that, while PowerShell is typically launched from Microsoft Office documents using VBA macros and is used to download and execute the actual malware, what determined the recent investigation was the fact that the analyzed code was downloading a file from the legitimate Notepad++ website.
After accessing the site to download the file directly and discovering that all looked normal, the researcher took a closer look at the VBA code and discovered multiple functions decoding information from various arrays, as well as the fact that the code was executing an already decoded PowerShell command.
By looking at variables in the PowerShell command, White eventually discovered 171 document samples, all fairly recent and all showing the same themes for lures, and also extracted the URLs used to download over two dozen payloads from half as many domains.
One of the discovered binaries, apparently compiled in August, was observed launching a legitimate executable and injecting code into it to “download further payloads through a POST request to various websites.” This behavior is shared across the original samples and White also matched observed HTTP requests to patterns already associated with the Chthonic banking Trojan.
Further analysis of the initial 171 documents revealed a set of 8 domains, while the analysis of POST and HTTP requests to them led the researcher to identifying over 5,000 observed samples as the Nymaim downloader Trojan.
Most of the samples came from only four sites: ejtmjealr[.]com, gefinsioje[.]com, gesofgamd[.]com, and ponedobla[.]bit. The ejtmjealr[.]com domain, the researcher points out, is clearly associated with ejdqzkd[.]com, a site discussed in a CERT.PL analysis of Nymaim earlier this year.
Looking at the passive resolutions for the discovered domains, the researcher found a total of 707 IP addresses associated with them.
Some of the IPs had a shared infrastructure, and the researcher used reverse DNS to uncover more sites linked to them, including an “idXXXXX.top” pattern supposedly associated Nymaim (similar to the “ejXXXXX.com” domains).
This eventually led to the discovery of all the domains associated with the IPs, and allowed the researcher to single out two clusters of infrastructure that also interconnect.
The investigation also revealed the infrastructure is also used for the distribution of other malware families, such as the Locky ransomware.
The shared infrastructure is also used to host a forum of illegal services, while some clusters of domains are “used by the Hancitor malware dropper to host the initial check-in and tracking.”
The security researchers published the lists of 707 IPs and 2,611 domains uncovered as part of this investigation on GitHub.
“These findings represent a collection of compromised websites, compromised registrar accounts used to spin up subdomains, domains used by malware DGA’s, phishing kits, carding forums, malware C2 sites, and a slew of other domains that revolve around criminal activity,” Palo Alto’s researcher concludes.
Access Bypass Vulnerabilities Patched in Drupal 8
17.8.2017 securityweek Vulnerebility
A Drupal 8 security update released on Wednesday addresses several access bypass vulnerabilities affecting components such as views, the REST API and the entity access system.
The most severe of the flaws patched by Drupal 8.3.7 is CVE-2017-6925, a critical issue affecting the entity access system. The weakness can be exploited to view, create, delete or update entities. According to Drupal developers, only entities that don’t have UUIDs and ones that have different access restrictions on different revisions of the same entity are impacted.
Another access bypass vulnerability patched in the latest version of Drupal is CVE-2017-6924, which involves the REST API being able to bypass comment approval.
“When using the REST API, users without the correct permission can post comments via REST that are approved even if the user does not have permission to post approved comments,” Drupal said in its advisory.
This issue has been classified as moderately critical as only sites that have the RESTful Web Services module and the comment entity REST resource enabled are affected. Furthermore, the attacker needs access to a user account that is allowed to post comments, or the targeted website needs to allow comments from anonymous users.
Another moderately critical flaw is CVE-2017-6923, which affects the “views” component. While this vulnerability does not affect the Drupal 7 core, it does impact the Drupal 7 Views module, for which an update has been made available.
“When creating a view, you can optionally use Ajax to update the displayed data via filter parameters. The views subsystem/module did not restrict access to the Ajax endpoint to only views configured to use Ajax. This is mitigated if you have access restrictions on the view,” Drupal said. “It is best practice to always include some form of access restrictions on all views, even if you are using another module to display them.”
Earlier this summer, Drupal updated versions 7 and 8 to address a vulnerability that had been exploited in spam campaigns since October 2016. The developers of the open source content management system (CMS) initially advised users to ensure that their websites are properly configured and later introduced a protection designed to prevent exploitation.
Common Source Code Used by Multiple Chinese DDoS Platforms
17.8.2017 securityweek Attack
An increase in Chinese websites offering online distributed denial of service (DDoS) capabilities was observed after a localized version of the source code of online booters was put up for sale, Talos reveals.
Because many of the websites were nearly identical, Talos security researchers initially believed that the same actor or group of actors was behind all of them. However, they discovered that multiple actors are operating them, and that they even launch attacks against one another.
The websites, most of which have been registered within the past six months, feature a simple interface where the user can select a target’s host, port, attack method, and duration of attack. The similarities emerge from the fact that the sites are based on the localized source code of an English-language DDoS platform that cybercriminals have been selling on hacker forums.
While both DDoS tools and services remain highly popular on the Chinese underground market, a shift to online DDoS platforms was recently observed, along with more frequent advertisements for such services. The available sites feature a nearly identical design and layout, displaying information on the number of active users, servers online, and the total number of attacks carried out, along with announcements from group administrators on recent updates, capabilities, and restrictions.
A sidebar allows users to “register an account, purchase an activation code to begin launching an attack, and then attack a target, either through the graphical interface set up on the website or through identical command line calls,” Talos explains.
The researchers discovered 32 nearly-identical Chinese online DDoS websites, most with the word “ddos” in their domain names (such as “shashenddos.club” or “87ddos.cc”), and the similarities between them suggested that a single actor could be responsible for all of them.
However, the researchers then discovered that the sites employed different third-party Chinese payment websites and different prices ranges, that different capabilities were advertised for the tools, and that the contact information and group chats for customer service were different on each site. Some services claimed 30-80 gigabit per second (Gbps) capabilities and others went up to 300 Gbps, while the difference in the number of attacks and users was vast as well.
The websites’ registration information also revealed key differences between actors. Although different names and emails were used for each of the analyzed websites, all “used Chinese registrars, the majority were registered in the past 3 months, and nearly all were registered in the past year.” Moreover, the researchers discovered that over half of the sites were hosted on Cloudflare IPs.
By following items spotted on a screenshot posted in a group chat run by a Chinese hacker group, the researchers discovered several forum posts offering the sale of source code for an online DDoS platform that was initially English-based but then translated into Chinese. Many of the postings were made in early 2017 or late 2016, and the images in said posts were identical to the websites observed.
“This is a foreign DDoS platform source code, it has already been Sinicized, everybody is welcome to test if they want to start a DDoS platform,” one of the forum ads reads, Talos says.
After obtaining a copy of the source code and analyzing it, the researchers concluded it corresponded to the DDoS websites observed, and that the platform relied on Bootstrap front-end design and Ajax to load content. They also linked the sites to Pixelcave, which offered Bootstrap-based website designs similar to the online Chinese DDoS websites (the company’s logo was present on many of the sites).
In addition to being able to pull information such as the amount and duration of attacks, or the number of concurrent attacks a user is allowed, the code shows that DDoS platforms allow customers to input a host, select an attack method, and duration. A blacklist for sites that cannot be attacked is also supported. Some even include a preloaded Terms of Service to absolve site admins from responsibility for the illegal use of the service.
“The code also allows administrators to monitor payments made, outstanding tickets, as well as an overview of the total amount of logins and attacks being contracted, and details about the attacks such as the host, duration of the attack, and which server is conducting the attack. The administrator can also set up an activation code system,” the researchers say.
While it’s clear that the source code was originally written in English and then modified so that the final platform would display Chinese language graphics, the researchers can’t establish where the original source code came from. They do point out, however, that there are several English language websites offering online DDoS services that have some similarities to the Chinese DDoS platforms.
“Online DDoS platforms remain popular because of their easy-to-use interfaces and the fact that they already provide all necessary infrastructure to the user, so there is no need to build a botnet or purchase additional services. Instead, the user purchases an activation code through a trusted payment site and then simply enters in their target. This serves the function of enabling even the most novice of actors the capability to launch powerful attacks, depending on the strength of the DDoS group’s backend infrastructure,” Talos concludes.
Researchers Uncover Infrastructure Behind Chthonic, Nymaim Trojans
17.8.2017 securityweek Virus
While analyzing malware that uses PowerShell for infection, Palo Alto Networks managed to uncover the infrastructure behind recent attacks that leveraged the Chthonic and Nymaim Trojans, along with other threats.
The analysis kicked off from one malicious sample, but resulted in security researchers from Palo Alto Networks being able to identify 707 IPs and 2,611 domains supposedly being utilized for malicious activity. While some of these resources are used to host malware, others are leveraged in other types of attacks and schemes, the researchers say.
Palo Alto Networks’ Jeff White explains that, while PowerShell is typically launched from Microsoft Office documents using VBA macros and is used to download and execute the actual malware, what determined the recent investigation was the fact that the analyzed code was downloading a file from the legitimate Notepad++ website.
After accessing the site to download the file directly and discovering that all looked normal, the researcher took a closer look at the VBA code and discovered multiple functions decoding information from various arrays, as well as the fact that the code was executing an already decoded PowerShell command.
By looking at variables in the PowerShell command, White eventually discovered 171 document samples, all fairly recent and all showing the same themes for lures, and also extracted the URLs used to download over two dozen payloads from half as many domains.
One of the discovered binaries, apparently compiled in August, was observed launching a legitimate executable and injecting code into it to “download further payloads through a POST request to various websites.” This behavior is shared across the original samples and White also matched observed HTTP requests to patterns already associated with the Chthonic banking Trojan.
Further analysis of the initial 171 documents revealed a set of 8 domains, while the analysis of POST and HTTP requests to them led the researcher to identifying over 5,000 observed samples as the Nymaim downloader Trojan.
Most of the samples came from only four sites: ejtmjealr[.]com, gefinsioje[.]com, gesofgamd[.]com, and ponedobla[.]bit. The ejtmjealr[.]com domain, the researcher points out, is clearly associated with ejdqzkd[.]com, a site discussed in a CERT.PL analysis of Nymaim earlier this year.
Looking at the passive resolutions for the discovered domains, the researcher found a total of 707 IP addresses associated with them.
Some of the IPs had a shared infrastructure, and the researcher used reverse DNS to uncover more sites linked to them, including an “idXXXXX.top” pattern supposedly associated Nymaim (similar to the “ejXXXXX.com” domains).
This eventually led to the discovery of all the domains associated with the IPs, and allowed the researcher to single out two clusters of infrastructure that also interconnect.
The investigation also revealed the infrastructure is also used for the distribution of other malware families, such as the Locky ransomware.
The shared infrastructure is also used to host a forum of illegal services, while some clusters of domains are “used by the Hancitor malware dropper to host the initial check-in and tracking.”
The security researchers published the lists of 707 IPs and 2,611 domains uncovered as part of this investigation on GitHub.
“These findings represent a collection of compromised websites, compromised registrar accounts used to spin up subdomains, domains used by malware DGA’s, phishing kits, carding forums, malware C2 sites, and a slew of other domains that revolve around criminal activity,” Palo Alto’s researcher concludes.
Information Security Spending to Reach $93 Billion in 2018: Gartner
16.8.2017 securityweek Security
Gartner has predicted that worldwide information security spending will reach $86.4 billion in 2017; a seven percent growth over the year. Spending is expected to increase to $93 billion in 2018.
The fastest growing sector is security services; especially in IT outsourcing, consulting and implementation services. The only area where growth is likely to slow down is hardware support services, which are becoming less necessary with the continuing adoption of virtual appliances, public cloud and Security as a Service (SaaS) solutions.
Much of the growth is thus expected to come from upgrading the IT infrastructure to a perceived more secure posture than by simply buying additional security products.
"Improving security is not just about spending on new technologies," said Sid Deshpande, principal research analyst at Gartner. "As seen in the recent spate of global security incidents, doing the basics right has never been more important. Organizations can improve their security posture significantly just by addressing basic security and risk related hygiene elements like threat centric vulnerability management, centralized log management, internal network segmentation, backups and system hardening," he said.
Faster growth is likely to come from the security testing market, particularly in relation to application security testing as part of DevOps. This is no surprise to RJ Gazarek, Product Manager at Thycotic. "Thycotic research on DevOps security practices," he told SecurityWeek, "has shown that more than 60% of DevOps organizations are not managing credentials in scripts in any way. This is a major security problem that needs to be addressed immediately, especially as more breaches are making the news, and people realize that the way into an organization is to find the department with the weakest security practice and get to work infiltrating."
Neither the growth nor the areas of growth surprise Nathan Wenzler, chief security strategist at AsTech. "If we watch how the trend of attacks has gone over the past several years, we see more and more criminals moving away from targeting servers and workstations, and toward applications and people," he explained.
"As an industry, we've gotten better and better about protecting devices; but now the focus has to turn to other assets, and thus, the increase in spending Gartner is forecasting in DevOps and services. Essentially, wherever the criminals go, corporate spending is soon to follow," Wenzler said.
There is, however, one area in which Gartner sees actual product growth: data leak prevention (DLP). The belief is that fears over the far-reaching and severe implications of the EU General Data Protection Regulation (GDPR) is spurring, and will continue to spur, DLP purchasing through 2018.
GDPR will come into force in May 2018. From that date onward, any company anywhere in the world that handles the personal information of European citizens could be liable for a fine of up to 4% of global turnover if they do not adequately protect that data. "The EU General Data Protection Regulation (GDPR) has created renewed interest, and will drive 65 percent of data loss prevention buying decisions today through 2018," says Gartner.
Where companies already have some form of DLP already in place, Gartner believes that interest is now focused on enhancing the DLP control: "specifically, integrated DLP such as data classification, data masking and data discovery." These will all be required for GDPR compliance, both in protecting the data and being able to retrieve it for removal if required by the user concerned.
Just this week, Amazon Web Services launched a new machine learning security service that helps its customers discover, classify and protect sensitive data.
However, some security experts believe that Gartner is being too conservative in its spending growth estimates. "Gartner has taken a very conservative evaluation on information security spending that it will grow by only 7%," Joseph Carson, chief security scientist at Thycotic, told SecurityWeek. I believe that the actual number will be much higher given that many aggressive regulations will come into enforcement in 2018, including the EU General Data Protection Regulation (GDPR).
"This," he continued, "will force many companies to increase spending on information security and response to avoid becoming either victims or receiving massive financial fines for failure to protect and secure. As we have seen, Maersk reports the cost of the June cyber-attack to be in excess of $300 million. With many other companies counting the losses of both WannaCry and NotPetya, they will likely prefer to prevent these from occurring rather than clean up the mess, resulting in huge financial losses."
But it's not all good news for North American and European vendors. Gartner also points out that China's recently approved cybersecurity law means that by 2020, 80% of large Chinese business security expenditure will be on locally produced products. This will be at the expense of U.S.-manufactured network security products.
In recent years, Asia/Pacific has been a dynamic market, growing by 24% in 2016. Gartner now predicts that, because of the more competitive pricing of Chinese solutions, end-user spending growth in Asia/Pacific will return to single-digit yearly growth from 2018 onward.
Hijacked Extensions Put 4.7 Million Chrome Users at Risk
16.8.2017 securityweek Hacking
More than 4.7 million users were apparently exposed to potentially malicious ads and credential theft after cybercriminals managed to hijack the developer accounts of several popular Chrome extensions.
The actors used phishing emails to gain access to the developers’ Google accounts and submit to the Chrome Web Store malicious versions of legitimate extensions. The malicious code injected in these tools was meant to modify the advertisements displayed to users and to grab specific credentials from the victims’ machines.
After taking a closer look at the incidents, Proofpoint concluded that 8 Chrome extensions have been compromised by the actor using the same modus operandi: Web Developer, Chrometana, Infinity New Tab, CopyFish, Web Paint, Social Fixer, TouchVPN, and Betternet VPN. At the moment, these extensions have a combined user base of more than 4.77 million users.
As previously reported, the phishing attack to compromise the developer accounts was pretty straightforward: an email purporting to come from Google Support prompted the targeted developers to log into their accounts to update some information. The login link in the email, however, would take developers to the attacker’s site instead, resulting in their credentials being stolen.
Next, the attackers would take over the compromised developer account and/or hijack their Chrome extension to replace it with a malicious variant. According to Proofpoint, the actor included in the code a check to ensure the extension has been installed for at least 10 minutes before starting the malicious behavior, most probably in an attempt to bypass detection.
The malicious code was also observed attempting to retrieve a remote file called ga.js over HTTPS, from a domain generated via a domain generation algorithm (DGA). Analysis of the malicious components in Web Developer revealed that the code from this step was meant to conditionally call additional scripts, including some that would harvest Cloudflare credentials after the victim’s login.
Next, “the compromised version of the extension attempts to substitute ads on the victim’s browser, hijacking traffic from legitimate advertising networks,” Proofpoint says, adding that the attackers focused mainly on carefully crafted substitution ads on adult websites, although they targeted a variety of other websites as well.
The ad substitutions work for 33 popular banner sizes including 468x60, 728x90, and many more spanning numerous aspect ratios, the researchers say. In many instances, the victims were presented with fake JavaScript alerts claiming that the computer required repairing. Clicking on these ads would redirect users to affiliate programs from which the threat actors could profit.
Proofpoint observed the compromised Web Developer extension directing victims to two such affiliates, but says that others may also have been used. The popup alerts were also associated with the compromise of the Infinity New Tab extension in May 2017, as well as with fake EU cookie-consent alerts last year.
“Threat actors continue to look for new ways to drive traffic to affiliate programs and effectively surface malicious advertisements to users. In the cases described here, they are leveraging compromised Chrome extensions to hijack traffic and substitute advertisements on victims’ browsers. Once they obtain developer credentials through emailed phishing campaigns, they can publish malicious versions of legitimate extensions. In addition to hijacking traffic and driving users to questionable affiliate programs, we have also observed them gathering and exfiltrating Cloudflare credentials, providing the actors with new means of potential future attacks,” Proofpoint concludes.
Pulse Wave DDoS Attacks Disrupt Hybrid Defenses
16.8.2017 securityweek Attack
A new method of launching distributed denial-of-service (DDoS) attacks dubbed “pulse wave” can be highly effective against organizations using “appliance first, cloud second” hybrid mitigation solutions, Imperva Incapsula warned on Wednesday.
The cloud-based security services provider has seen pulse wave DDoS attacks being launched over the past few months, some of them lasting for days and reaching as much as 350 gigabits per second (Gbps).
Typical DDoS attacks show a sawtooth pattern when visualized on a graph due to the ramp-up time needed for cybercriminals to mobilize botnets and reach their maximum potential.
In the case of pulse wave attacks, there is no ramp-up period — the DDoS traffic peaks almost immediately and drops shortly after. The process is repeated at regular intervals, which indicates that the attackers have precise control over their botnets.
Experts believe the malicious actors are capable of switching targets on-the-fly. A web resource can often be disrupted quickly with a powerful DDoS attack, but it can take hours for it to recover. That is why threat groups can launch an attack on one target, then quickly move to a different target, and then return to the initial target. During the time when there is no activity on the graph, the attack is likely aimed at another victim.
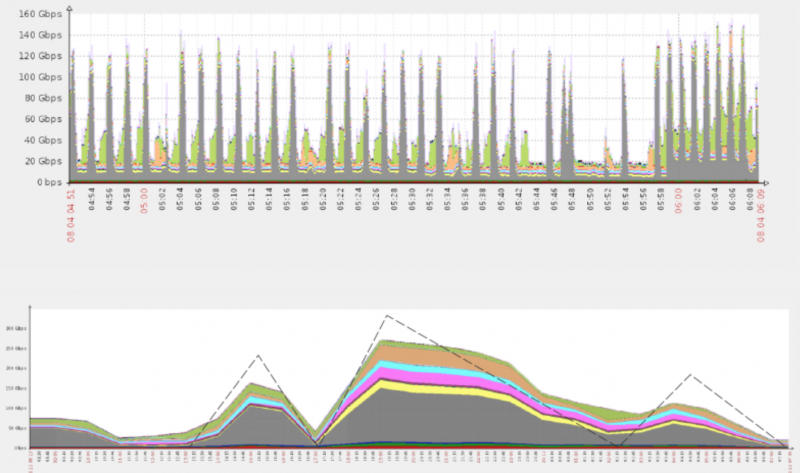
According to Imperva Incapsula, the peak capacity is reached within a few seconds and a new pulse is launched roughly every 10 minutes. Assaults last for at least one hour, but in most cases they can go on for several hours and even days.
Experts believe these types of attacks are particularly effective against “appliance first, cloud second” hybrid mitigation solutions, where on-premises DDoS protection appliances represent the first line of defense and the cloud is used as a backup option for when the appliance cannot handle the attack traffic on its own. The cloud platform is activated by the on-premises appliance, which sends it attack information that can be used to scrub incoming traffic.
The problem is that a single pulse in pulse wave attacks is enough to completely congest a network pipe, causing a DoS condition and preventing the appliance from activating the cloud platform.
“For the pulse duration, the entire network shuts down completely. By the time it recovers, another pulse shuts it down again, ad nauseam. If at some point the cloud is reconfigured to automatically activate itself at the sign of trouble, the scrubbing process is still significantly delayed because of the verification process,” explained Igal Zeifman, director of marketing at Imperva Incapsula.
“Additionally, the lack of communication prohibits the appliance from providing information required to create an attack signature. Even if the cloud does eventually come online, it still has to resample the traffic from scratch before initiating the filtering process,” Zeifman added.
Imperva Incapsula has observed such attacks against several high-value targets, including gaming and financial technology (fintech) companies. The security firm believes other threat actors will likely turn to pulse wave attacks in the future as it provides an easy way for them to double their attack output.
Cerber Ransomware now includes a feature to avoid canary files anti-malware
16.8.2017 securityaffairs Ransomware
Researchers at Cybereason have discovered a new strain of the Cerber ransomware that implements a new feature to avoid triggering canary files.
The canary files are a security measure for the early detection of threat like ransomware.
These files are located in specific positions of systems and an anti-ransomware application watches for any modification. If the watching anti-ransomware detects any attempt to encrypt these file the defense solution will trigger the necessary countermeasures.

Researchers at Cybereason have discovered a new strain of the Cerber ransomware that implements a new feature to avoid triggering canary files.
“To avoid encrypting canary files and triggering anti-ransomware programs,” reports Uri Sternfield, Cybereason’s lead researcher, “a new feature in Cerber now searches computers for any image file (.png, .bmp, .tiff, .jpg, etc.) and checks whether they are valid. Image files are commonly used as canary files. If a malformed image is found, Cerber skips the entire directory in which it is located and does not encrypt it.”
Using this technique the Cerber ransomware is able to evade detection based on canary files. Experts pointed out that this mechanism could ble used against the Cerber ransomware by placing false modified canary files ( i.e. malformed image file ) in any important directory of the system. In this way users can vaccinate any folder containing valuable content.
“While this trick might allow Cerber to evade some canary-file anti-ransomware solutions, it also makes it vulnerable,” explains Sternfield; “a user can ‘vaccinate’ any important directory against Cerber by creating an invalid image file inside it, for example by copying any non-image file to this directory and renaming it to .jpg. Cerber will assume that the file is a canary file installed by an anti-ransomware program on the user’s machine and refuse to encrypt it!”
Cybereason’s developed a free application dubbed RansomFree that protects users from ransomware and automatically generates canary files in valuable folders.
Nevertheless, it is easy to create malformed canary files, for example, by renaming non-image file to jpeg.
“Simply take any non-image file and rename it to .jpg, then copy this file into any folder which holds important documents. This has to be performed for each folder separately,” explained Sternfield.
DitM Dog In The Middle – New Hacking Technique to Eavesdropping
16.8.2017 securityaffairs Hacker techniques
During Defcon 25 hacking conference held in Las Vegas on July, a new eavesdropping attack technique was introduced, it was dubbed DitM (Dog In The Middle).
During Defcon 25 one of the biggest information security event that took place in Las Vegas on July 27-30 this year, a new eavesdropping attack technique was introduced.
At the BioHacking Village’s Pisa Room, the Brazilian information security researcher and senior security consultant at CIPHER, Rafael Fontes Souza presented a proof-of-concept demonstrating a new exploitation technique that can be used to hack user credentials and to intercept sensitive data.
The ‘Dog in the Middle’ technique, aka DitM, used man’s best friend as an attack tool. Rafael adapted a chest collar to carry a mobile phone and wireless network adapter.

The most noticeable feature of this technique is that the attack vectors are triggered automatically without any human interaction and include near field attacks such as fake access point, cellular base stations or local user attacks on a network.
A comprehensive set of exploitations can be implemented using DitM, like DNS hijacking, packet injection, evil twin, rogue router or ISP, among others.
How that’s done?
The targeted device will connect to a rogue wi-fi access point generated by the dog collar and clever DHCP configurations can push rules to allow IP allocation by the fake AP and traffic forwarding to fake and/or malicious websites.
“Information and user data can be easily stored and malicious files can also be injected remotely to control the compromised device”, explain Rafael.

The video demonstrating how the chest collar was assembled can be seen at Vimeo through the following link https://vimeo.com/227596613
and Rafael’s presentation can also be accessed through Slideshare here https://pt.slideshare.net/rafa_el_souza/my-dog-is-a-hacker-and-will-still-your-data.
This technique is as very good example of how rather conventional technology can be used to social engineering to compromise users. Who’d think man’s best friend could be used as an attack tool?
Article by Pedro Silveira (Marketing Director at Cipher)
Corrupt Federal Agent, Who Stole Bitcoins From Silk Road, Pleads Guilty To Money Laundering
16.8.2017 thehackernews CyberCrime
A former the United States Secret Service agent who stole hundreds of thousands of dollars worth of Bitcoins during an investigation into then-largest underground marketplace Silk Road has now pleaded guilty to money laundering.
Shaun W. Bridges is one of two former US undercover agents who pleaded guilty in 2015 to one count of money laundering and one count of obstruction and was sentenced in December same year to almost six years in prison for stealing over $800,000 in Bitcoin while investigating Silk Road.
35-years-old Bridges, who had been a Special Agent with the U.S. Secret Service for almost 6 years, along with his partner stole money from Silk Road accounts and framed someone else for the laundering, which even led the Silk Road founder Ross Ulbricht to plan a murder.
Ulbricht was convicted in February 2015 of running the Silk Road underground black market and is now serving life in prison sentence.
According to the Department of Justice, Bridges is believed to have stolen additional funds from a digital wallet belonging the Secret Service on two different occasions months after he was initially charged.
The missing Bitcoins were found by the Secret Service agency in December when Bridges was sentenced after admitting that he moved and stole approximately 1,600 Bitcoin (at the time valued nearly $359,005 and almost $6.6 million today).
According to his guilty plea in this case, Bridges said it used a private key to access a digital wallet belonging to the Secret Service account, and subsequently transferred the bitcoins to "other digital wallets at other Bitcoin exchanges to which only he had access."
"In the course of the investigation, U.S. agents were able to locate and seize approximately 600 of the stolen bitcoin and, as part of his plea, Bridges agreed to turn over the remaining stolen Bitcoin," the DoJ said in the statement.
Silk Road was shut down in 2013 after the arrest of Ulbricht. The FBI seized bitcoins (worth about $33.6 million, at the time) from the site, which were later sold in a series of auctions by the United States Marshals Service (USMS).
Before the shutdown, Silk Road was one of the most extensive, sophisticated, and widely-used illegal marketplaces on the internet.
The other Bridges' partner is a 47-year-old former Drug Enforcement Agency (DEA) special agent Carl Mark Force, who is also facing criminal charges.
On Tuesday, Bridges pleaded guilty to one count of money laundering before the United States District Court Judge of the Northern District of California. He will be sentenced on November 7, 2017.
Backdoor Found in Popular Server Management Software used by Hundreds of Companies
16.8.2017 thehackernews Virus
Cyber criminals are becoming more adept, innovative, and stealthy with each passing day. They are now adopting more clandestine techniques that come with limitless attack vectors and are harder to detect.
Recently, cyber crooks managed to infiltrate the update mechanism for a popular server management software package and altered it to include an advanced backdoor, which lasts for at least 17 days until researchers discovered it.
Dubbed ShadowPad, the secret backdoor gave attackers complete control over networks hidden behind legit cryptographically signed software sold by NetSarang—used by hundreds of banks, media firms, energy companies, and pharmaceutical firms, telecommunication providers, transportation and logistics and other industries—for 17 days starting last month.
Important Note — If you are using any of the affected product (listed below), we highly recommend you stop using it until you update them.
Hacker Injected Backdoor Through Software Update Mechanism
According to researchers at Kaspersky Labs, who discovered this well-hidden backdoor, someone managed to hijack the NetSarang's update mechanism and silently insert the backdoor in the software update, so that the malicious code would silently deliver to all of its clients with NetSarang's legitimate signed certificate.
The attackers of the Petya/NotPetya ransomware that infected computers around the world in June used the same tactic by compromising the update mechanism for Ukrainian financial software provider called MeDoc and swapped in a dodgy update including NotPetya.
"ShadowPad is an example of the dangers posed by a successful supply-chain attack," Kaspersky Lab researchers said in their blog post published Tuesday. "Given the opportunities for covert data collection, attackers are likely to pursue this type of attack again and again with other widely used software components."
The secret backdoor was located in the nssock2.dll library within NetSarang's Xmanager and Xshell software suites that went live on the NetSarang website on July 18.
However, Kaspersky Labs researchers discovered the backdoor and privately reported it to the company on August 4, and NetSarang immediately took action by pulling down the compromised software suite from its website and replacing it with a previous clean version.
The affected NetSarang's software packages are:
Xmanager Enterprise 5.0 Build 1232
Xmanager 5.0 Build 1045
Xshell 5.0 Build 1322
Xftp 5.0 Build 1218
Xlpd 5.0 Build 1220
Hackers Can Remotely Trigger Commands
The attackers hide the ShadowPad backdoor code in several layers of encrypted code that were decrypted only in intended cases.
"The tiered architecture prevents the actual business logics of the backdoor from being activated until a special packet is received from the first tier command and control (C&C) server (activation C&C server)," the researchers wrote.
Until then, the backdoor pings out every 8 hours to a command-and-control server with basic information on the compromised computers, including their domain names, network details, and usernames.
Here's how the attackers activate the backdoor:
The activation of the backdoor was eventually triggered by a specially crafted DNS TXT record for a specific domain name. The domain name is generated based on the current month and year, and performs a DNS lookup on it.
Once triggered, the command and control DNS server in return sends back the decryption key which is downloaded by the software for the next stage of the code, effectively activating the backdoor.
Once activated, the ShadowPad backdoor provides a full backdoor for an attacker to download and run arbitrary code, create processes, and maintain a virtual file system (VFS) in the registry, which is encrypted and stored in locations unique to each victim.
Kaspersky researchers said they could confirm activated backdoor in one case, against an unnamed company located in Hong Kong.
How to Detect this Backdoor and Protect Your Company
The company has rolled out an update to kill the malicious software on August 4, and is investigating how the backdoor code got into its software.
Anyone who has not updated their NetSarang software since then is highly recommended to upgrade to the latest version of the NetSarang package immediately to protect against any threats.
Additionally, check if there were DNS requests from your organization to the following list of domains. If yes, the requests to those domains should be blocked.
ribotqtonut[.]com
nylalobghyhirgh[.]com
jkvmdmjyfcvkf[.]com
bafyvoruzgjitwr[.]com
xmponmzmxkxkh[.]com
tczafklirkl[.]com
notped[.]com
dnsgogle[.]com
operatingbox[.]com
paniesx[.]com
techniciantext[.]com
NetSarang installation kits from April do not include the malicious library.
8 More Chrome Extensions Hijacked to Target 4.8 Million Users
16.8.2017 thehackernews Hacking
Google's Chrome web browser Extensions are under attack with a series of developers being hacked within last one month.
Almost two weeks ago, we reported how unknown attackers managed to compromise the Chrome Web Store account of a developer team and hijacked Copyfish extension, and then modified it to distribute spam correspondence to users.
Just two days after that incident, some unknown attackers then hijacked another popular extension 'Web Developer' and then updated it to directly inject advertisements into the web browser of over its 1 million users.
After Chris Pederick, the creator of 'Web Developer' Chrome extension that offers various web development tools to its users, reported to Proofpoint that his extension had been compromised, the security vendor analysed the issue and found further add-ons in the Chrome Store that had also been altered.
According to the latest report published by the researchers at Proofpoint on Monday, the expanded list of compromised Chrome Extensions are as below:
Chrometana (1.1.3)
Infinity New Tab (3.12.3)
CopyFish (2.8.5)
Web Paint (1.2.1)
Social Fixer (20.1.1)
Proofpoint researcher Kafeine also believes Chrome extensions TouchVPN and Betternet VPN were also compromised in the same way at the end of June.
In all the above cases, some unknown attackers first gained access to the developers' Google web accounts by sending out phishing emails with malicious links to steal account credentials.
Once the attackers gained access to the accounts, either they hijacked their respective extensions and then modified them to perform malicious tasks, or they add malicious Javascript code to them in an attempt to hijack traffic and expose users to fake ads and password theft in order to generate revenue.
In the case of the Copyfish extension, the attackers even moved the whole extension to one of its developers' accounts, preventing the software company from removing the infected extension from the Chrome store, even after being spotted compromised behaviour of the extension.
"Threat actors continue to look for new ways to drive traffic to affiliate programs and effectively surface malicious advertisements to users," researchers concluded. "In the cases described here, they are leveraging compromised Chrome extensions to hijack traffic and substitute advertisements on victims' browsers."
"Once they obtain developer credentials through emailed phishing campaigns, they can publish malicious versions of legitimate extensions."
At this time, it is unclear who is behind the hijackings of Chrome Web extensions.
The best way to protect yourself from such attacks is always to be suspicious of uninvited documents sent over a phishing email and never click on links inside those documents unless verifying the source.
Respond Software Automates SOC Analyst Decisions
16.8.2017 securityweek Security
Mountain View, Calif.-based Respond Software has emerged from stealth mode with a new product designed to automate the role of security analysts and $12 million in funding.
Founded by Mike Armistead, Robert Hipps and Chris Calvert, Respond Software develops solutions that aim to make security operations centers (SOCs) more efficient. The company’s goal is to create software that powers what it calls the “self-driving SOC.”
Respond Software
Respond Software’s first product, Respond Analyst, is designed to emulate the decision-making process of an experienced security analyst in an effort to address the problem of overwhelmed SOC staff and shortage of skilled personnel.
According to the company, when put to work in a large enterprise, its product managed to do the work of 26 full-time SOC analysts that process 75 events per hour (based on industry-average productivity data).
The product currently has two modules for network intrusion and compromised system incidents. Respond Analyst consumes data from a company’s existing security products and uses patent-pending Probabilistic Graphical Optimization (PGO) technology to conduct analytical checks and probabilistic scenario simulations to determine whether a potential incident should be escalated to incident response based on likelihood, extent and severity.
The system leverages human feedback from all Respond customers to continually improve its decision-making capabilities.
Respond Software has obtained $12 million in a series A funding round led by CRV and Foundation Capital, which brings the total since the company was founded last year to $15 million. Respond says market demand for the types of solutions it provides is high and expected to grow over the next few years.
“There could not be a more expert team to tackle transforming today’s reactive SOCs to the next generation – a true Security Response Center – much like autonomous vehicles are generating an entirely new ecosystem of capability in transportation,” said Max Gazor, general partner at CRV.
“It’s like having a million more trained analysts instantly at the ready. These days, every organization needs more security resources. With the Respond Software solution, they now have it in spades,” added Paul Holland, general partner at Foundation Capital.
The company’s advisors include Gerhard Eschelbeck, VP of security and privacy engineering at Google, Richard Seiersen, CISO and VP of trust at Twilio, and Izak Mutlu, former CISO of Salesforce.com.
Cerber Ransomware Creates Self-Inflicted Canary Vaccine
16.8.2017 securityweek Ransomware
Researchers Say Cerber Ransomware Now Has a Feature to Avoid Triggering "Canary Files"
The old canary-in-the-coal-mine and the new canary file serve the same purpose. Both are threat detectors: the former to detect the presence of poisonous gas in a mine, and the latter to detect an unauthorized presence in a file system. The canary file is particularly useful as an early-warning system for the presence of ransomware.
The concept is very simple. A bogus file designed to look like a prime ransomware target is strategically placed and watched by an anti-ransomware application. There is no valid reason for this file to be encrypted. If the watching anti-ransomware detects any attempt to do so, it knows that ransomware is present and can take the necessary action.
Cybereason researchers have discovered that the Cerber ransomware now includes a new feature to avoid triggering canary files. "To avoid encrypting canary files and triggering antiransomware programs," reports Uri Sternfield, Cybereason's lead researcher, "a new feature in Cerber now searches computers for any image file (.png, .bmp, .tiff, .jpg, etc.) and checks whether they are valid. Image files are commonly used as canary files. If a malformed image is found, Cerber skips the entire directory in which it is located and does not encrypt it."
This is typical of the continuous battle between any attacker and defender: measures and countermeasures. The canary file is a countermeasure -- evading canary files is a counter-countermeasure. But Sternfield points out that there is a potential weakness in the counter-countermeasure -- it effectively introduces a vaccine against this version of Cerber that can be used by anyone.
"While this trick might allow Cerber to evade some canary-file anti-ransomware solutions, it also makes it vulnerable," explains Sternfield; "a user can 'vaccinate' any important directory against Cerber by creating an invalid image file inside it, for example by copying any non-image file to this directory and renaming it to .jpg. Cerber will assume that the file is a canary file installed by an anti-ransomware program on the user's machine and refuse to encrypt it!"
Put simply, any valuable folder can be vaccinated by the inclusion of a malformed image file, such as a bogus .jpg. Cybereason's own free RansomFree product automatically does this, but it "only generates canary files in key locations and important folders," Sternfield told SecurityWeek.
Nevertheless, it is an easy process for any user. "Simply take any non-image file and rename it to .jpg, then copy this file into any folder which holds important documents. This has to be performed for each folder separately," he explained.
While this process can be used to protect valuable files from this version of Cerber, it would be wrong to treat it as a solution against ransomware in general. What the story really illustrates is the manner in which attackers and defenders closely watch each others' moves, always trying to outsmart the other.
Cybereason has already updated its own products to make use of the 'vaccine' in strategic folders. If the authors of this version of Cerber detect that the vaccine becomes an effective defense against their attack, they might simply drop their canary file detection process. At this point, the infected user will have to rely on the more traditional monitoring of canary files by an anti-ransomware product.
Cybereason raised $100 million in Series D funding in June 2017, which brought the total amount raised by the cyber attack detection firm to $189 million since its inception in 2012.
Amazon Launches AWS Data Protection Service
16.8.2017 securityweek Security
Amazon announced this week the launch of Macie, a new security service that helps Amazon Web Services (AWS) users discover, classify and protect sensitive data.
Amazon Macie uses machine learning to automatically identify and protect personally identifiable information (PII), intellectual property and other sensitive data, and informs users of how their data is being accessed or moved via dashboards and alerts.
When deployed, Amazon Macie creates a baseline and then uses a behavior analytics engine to detect risky or suspicious activity. Customers can define automated remediation actions, including for resetting passwords and access control lists (ACLs), and create custom alert management via CloudWatch Events for integration with existing security ticketing systems.
Security and compliance events that could pose a risk are classified into 20 categories, including API keys and credentials stored in source code, high-risk data events, credentials within unencrypted backups, and various activities that could represent the early stages of an attack.
The product can be integrated with security information and event management (SIEM) and managed security service provider (MSSP) services.
Pricing for Amazon Macie is based on the amount of data that is classified, captured and analyzed. Additional fees are charged for the optional Extended Data Retention feature, which increases the metadata retention period.
The Macie console can be found in the AWS Management Console. However, the service is currently supported only in Northern Virginia and Oregon, and it can only protect data stored in Amazon Simple Storage Service (S3) buckets. Next year, Amazon plans on adding support for EC2 environments, DynamoDB, RDS, EFS and AWS Glue.
Amazon Macie has already been used by companies such as Edmunds, Netflix and Autodesk.
The launch of Amazon Macie comes after many high-profile organizations have been caught leaking sensitive data via misconfigured S3 buckets. The list of affected entities includes the United States National Geospatial-Intelligence Agency (NGA), Verizon, Dow Jones & Company, and hundreds of millions of U.S. voters.
Backdoors Found in Tools Used by Hundreds of Organizations
16.8.2017 securityweek Virus
Many organizations around the world using connectivity tools from NetSarang are at risk after researchers at Kaspersky Lab discovered that malicious actors had planted a backdoor in several of the company’s products.
NetSarang, which has offices in the United States and South Korea, specializes in secure connectivity solutions. Some of its most popular products are Xshell, Xmanager, Xftp and Xlpd.
Kaspersky discovered a backdoor in these tools after one of its customers in the financial sector noticed suspicious DNS requests coming from a NetSarang software package. An investigation conducted by the vendor revealed that the latest versions of Xmanager Enterprise 5 (build 1232), Xmanager 5 (build 1045), Xshell 5 (build 1322), Xftp 5 (build 1218) and Xlpd 5 (build 1220) had been compromised.
Security experts believe the attackers either modified source code or patched the software on NetSarang’s build servers after gaining access to the company’s systems. The affected builds were released on July 18 and the backdoor was only discovered on August 4.
NetSarang’s products are used by hundreds of financial, software, media, energy, electronics, insurance, industrial, construction, manufacturing, retail, telecoms, pharmaceutical and transportation companies. However, Kaspersky has only seen the malicious payload being activated on the systems of a company in Hong Kong.
Kaspersky says the malware could be lying dormant on the networks of other organizations, but NetSarang said it alerted the antivirus industry so security products may have already neutralized the malicious files.
The malware, detected by Kaspersky as Backdoor.Win32.ShadowPad.a, communicates with its command and control (C&C) server via DNS queries sent once every eight hours. The requests contain information on the infected machine, including user name, domain name and host name.
If the infected system is of interest to the attackers, they activate a fully fledged backdoor that they can use to download and execute other malware.
“If the backdoor were activated, the attacker would be able to upload files, create processes, and store information in a VFS [virtual file system] contained within the victim’s registry. The VFS and any additional files created by the code are encrypted and stored in locations unique to each victim,” researchers explained.
Kaspersky said the threat group behind this attack was careful not to leave too much evidence, but researchers did find some links to PlugX and Winnti, malware believed to have been developed by Chinese-speaking actors.
The security firm has provided indicators of compromise (IoC) to help organizations detect these attacks. NetSarang has also published a security alert to inform customers of the steps that need to be taken to address the issue.
Last month, NetSarang informed customers that it had released an update for Xshell after documents published by WikiLeaks revealed that the tool had been targeted by the CIA’s BothanSpy malware.
ShadowPad backdoor was spread in corporate networks through software update mechanism
16.8.2017 securityaffairs Virus
Kaspersky Lab discovered attackers were able to modify the NetSarang software update process to include a malware tracked as ShadowPad backdoor.
Software update mechanism could be an efficient attack vector, news of the day is that hackers compromised the update process for a popular server management software package developed by NetSarang.
Attackers were able to modify the software update process last month and modified it to include a backdoor tracked as ShadowPad, that affected at least one victim’s machine in Hong Kong.
NetSarang Computer, Inc. provides secure connectivity solutions and specializes in the development of server management tools for large corporate networks in many industries, including financial services, energy, retail, technology, and media.
In July, researchers at Kaspersky Lab were investigating suspicious DNS requests in a partner’s network. The requests were found on systems used to process transactions in a customer’s network in the financial industry.
Further investigation into the DNS queries led them to NetSarang, that promptly sanitized its software update process by removing the malicious library nssock2.dll in its update package,
“In July 2017, during an investigation, suspicious DNS requests were identified in a partner’s network. The partner, which is a financial institution, discovered the requests originating on systems involved in the processing of financial transactions.” states the analysis published by Kaspersky.
“Further investigation showed that the source of the suspicious DNS queries was a software package produced by NetSarang.”
Attackers have surreptitiously modified the software distributed by NetSarang to include an encrypted payload that could be remotely activated.
The attackers leveraged several layers of encrypted code to hide their ShadowPad backdoor and activate it only through the receiving of a special packet from the first tier command and control (C&C) server (“activation C&C server”).
“Activation of the payload would be triggered via a specially crafted DNS TXT record for a specific domain. The domain name is generated based on the current month and year values, e.g. for August 2017 the domain name used would be “nylalobghyhirgh.com”.” continues the analysis.
The module sends back to the C&C DNS server basic target information (domain and user name, system date, network configuration) and in turn receives back the decryption key for the next stage of the code, activating the ShadowPad backdoor.
The data exchanged between the module and the C&C server is encrypted with a proprietary algorithm, experts noticed that each packet also contains an encrypted “magic” DWORD value “52 4F 4F 44” (‘DOOR’ if read as a little-endian value).

The ShadowPad backdoor is a modular platform that can be used to download and execute arbitrary code on the infected system, create processes, and maintain a virtual file system in the registry,
The remote access capability implemented for the ShadowPad backdoor includes a domain generation algorithm (DGA) for C&C servers which changes every month. Expert noticed that the thread actor behind the ShadowPad backdoor have already registered the domains covering July to December 2017, a circumstance that led them to believe that the start date of the attack is around mid-July 2017.
Kaspersky Lab revealed that the first known compile date for the ShadowPad backdoor is Jul 13, hackers signed the malicious code with a legitimate NetSarang certificate.
ShadowPad is an example of the dangers posed by an attack against software update process, recently other successful supply-chain attacks made the headlines such as the NotPetya that was spread through exploiting the software supply chain of the Ukrainian financial software provider MeDoc.
NetSarang customers urge to check their software to check the presence the backdoor. The affected versions of NetSarang containing the malicious nssock2.dll are Xmanager Enterprise 5 Build 1232, Xmanager 5 Build 1045, Xshell 5 Build 1322, Xftp 5 Build 1218 and Xlpd 5 Build 1220.
“Given that the NetSarang programs are used in hundreds of critical networks around the world, on servers and workstations belonging to system administrators, it is strongly recommended that companies take immediate action to identify and contain the compromised software,” states Kaspersky Lab.
Kaspersky published the list of Indicators of Compromise to help companies to check their systems.
Faulty firmware OTA update bricked hundreds of LockState smart locks
16.8.2017 securityaffairs Vulnerebility
Some models of LockState smart locks also used by AirBnB customers were bricked by an OTA firmware update leaving guests unable to access their rentals.
At the last Black Hat hacker conference, security experts demonstrated how to hack electronic locks, and the news I’m going to tell you demonstrates how annoying could be an incident to occurred to hundreds of smart locks.
While the number of IoT devices continues to increase, several times we questioned about the necessity to connect to the Internet objects that we ordinary use, such as a home appliance.
Last week, nearly hundreds of Internet-connected locks stopped working after a faulty software update.
The problem affected some models of remotely accessible smart locks manufactured by the US company LockState. Many users have complained that their Lockstate 6000i electronic locks started to fail from last Monday, following the firmware update, the built-in keypad was useless.
8 Aug
Ruffin Prevost @ruffinprevost
Hope @TechCrunch @IoTTechNews @TheNextWeb contact me & @boontdustie @jongaze @christop_eckert re: @LockState bricking locks, 2 weeks to fix.
Follow
LockState @LockState
I've seen your message and we are working to get all the 500 customers affected the help they need. We will help each of them equally.
6:17 PM - Aug 8, 2017
1 1 Reply Retweets 2 2 likes
Twitter Ads info and privacy
The LockState’s RemoteLock 6i (6000i) leverages the home Wi-Fi network to implement remote control and firmware updates. According to the colleagues at THN, LockState is also partner with Airbnb, Airbnb users have chosen these specific IoT devices to give their guests entry code in order to get into hotel properties without using physical keys.
Many Airbnb customers were not able to use the built-in keypad on the smart lock devices to unlock the doors.
smart locks LockState
LockState confirmed the problem was caused by a faulty OTA firmware update issued last week that caused a “fatal error” in the smart locks, following the incident the devices are unable to reconnect to the company’s web servers, this means that is is impossible to fix the problem with a new OTA update.
The experts explained that the problems were caused by the distribution to the to 6000i family of the firmware intended for 7000i model smart locks.

“Your lock is among a small subset of locks that had a fatal error rendering it inoperable,” reads an email sent by LockState to affected customers. “After a software update was sent to your lock, it failed to reconnect to our web service making a remote fix impossible.”
Affected consumers have the following two options:
Users have to remove the back flap of the smart lock and send it to LockState that will apply a manual update, it is a time-consuming activity that will take 5-7 working days.
Users can ask for a replacement lock, which will take 14-18 days to ship, and then send the faulty model back to LockState.
LockState assured it will cover all shipping costs for the affected smart locks and will also provide one year of free service for the LockState Connect Portal, that is a subscription-based service which allows full remote control of all compatible smart home devices.
“We will pay for the shipping of your lock both to LockState and the return back to you within the continental US. We will also be providing you with 1 year of free service for the LockState Connect Portal for these locks” states the email.
TrickBot Using Legitimate Looking Sites With SSL Certificates
16.8.2017 securityweek BotNet
The TrickBot banking Trojan has been using legitimate SSL certificates alongside websites that closely resemble those of actual banks in recently observed attacks, security researchers warn.
Around for only one year, TrickBot has seen numerous updates and added various new capabilities. The malware recently gained worm-like capabilities and began targeting more than just users’ online banking information: it is now also going for Outlook and browser data.
Despite being fake, the sites could easily trick potential victims into believing they are real, especially given the use of servers with full email authentication and HTTPS, Brad Duncan, Palo Alto Networks analyst and handler at the SANS Internet Storm Center, reveals. The Trojan is distributed through malicious emails that use various lures to convince recipients into opening the attached documents.
As part of these attacks, miscreants sent emails from websites closely mimicking those of banks: hsbcdocs.co.uk, hmrccommunication.co.uk, lloydsbacs.co.uk, nationwidesecure.co.uk, natwestdocuments6.ml, santanderdocs.co.uk, santandersecuremessage.com, and securenatwest.co.uk. Almost all of the sites were registered through GoDaddy using various names or privacy services.
The spam emails used HTML attachments designed to download Office documents over HTTPS, in an attempt to evade detection through encrypted network traffic. Once the victim opens the Office document, they are asked to enable macros, which in turn download and execute the TrickBot banking Trojan.
As part of one campaign documented by My Online Security, the malicious emails were pretending to come from Santander Bank, distributed from the convincing look-a-like domain santanderdocs.co.uk. Many of these messages are apparently targeted at small and medium size businesses.
As part of a spam run observed by Cyren, the attackers were impersonating the Lloyds Bank, also using a seemingly correct URL (lloydsbacs.co.uk instead of lloydsbank.co.uk) and a legitimate SSL certificate. Because of the close resemblance with the legitimate URL, the targeted users are unlikely to spot the phishing attempt, especially given the use of an SSL certificate.
The security researchers observed a large number of such emails being sent over a very short period of time: they blocked 75,000 of such messages over a 25-minute period. Most of the messages appeared to be sent from a Dutch IP (5.149.255.107), already a known source of spam and which appears to host many malicious domains, including the one used in this run.
“TrickBot takes the phishing of banking credentials to another level by showing the correct URL of the online bank and confirmation of a legitimate SSL certificate, so even more alert users who pay any attention to these sorts of details will not see anything unusual,” Cyren notes.
The malicious emails have an Excel document attached. Called IncomingBACs.xlsm, the document asks the user to enable included macros, which results in TrickBot being downloaded and installed on the victim’s machine. The version used in these attacks comes with an encoded configuration module in the resource section of its binary and includes support for additional modules that are downloaded from controller domains.
Uber Settles Complaint Over Data Protection for Riders, Drivers
16.8.2017 securityweek Safety
Uber agreed to implement new data protection measures to settle complaints that it failed to prevent improper snooping on driver and customer information, officials said Tuesday.
The ridesharing giant had faced complaints that it allowed some employees to use the "God view" to monitor customer movements that could allow Uber managers to keep tabs on journalists investigating the ridesharing giant.
A separate complaint said that Uber had also failed to prevent a data breach that allowed hackers to gain access to personal information on some 100,000 drivers.
The Federal Trade Commission announced a settlement on an investigation into allegations that Uber failed to live up to data protection claims.
"Uber failed consumers in two key ways: First by misrepresenting the extent to which it monitored its employees' access to personal information about users and drivers, and second by misrepresenting that it took reasonable steps to secure that data," said FTC acting chairman Maureen Ohlhausen in a statement.
"This case shows that, even if you're a fast growing company, you can't leave consumers behind: you must honor your privacy and security promises."
The settlement contains no financial penalty, but Uber agreed to implement "a comprehensive privacy program" that will include independent audits, the FTC said. If it fails to live up to the agreement it could face fines.
The agency which enforces consumer and privacy protection said Uber had announced in November 2014 -- but failed to enforce -- a "strict policy" prohibiting employees from accessing rider and driver data except for legitimate business purposes.
The FTC added in a statement that Uber "did not take reasonable, low-cost measures" that could have prevented a breach by using better practices to protect data in the internet cloud.
Uber, which has become the world's most valuable venture-backed startup despite complaints from regulators and others, has been roiled by a series of revelations about a toxic work culture and questionable business practices.
Its chief executive Travis Kalanick resigned in June, but investors and board members are battling over his successor and a lawsuit by one investor alleges Kalanick has been working behind the scenes to manipulate the board.
Nigerian Behind Attacks Against Over 4,000 Businesses: Report
16.8.2017 securityweek CyberCrime
A single Nigerian national working on his own has orchestrated numerous malware infection campaigns targeting more than 4,000 organizations globally over the past four months, Check Point security researchers say.
The attacks have been aimed various companies in industries such as oil & gas, manufacturing, banking, and construction, in an attempt to steal data and commit fraud. Many of these are leading international names and some have had their defenses breached by the attacks, the security researchers reveal.
According to Check Point, at least a dozen companies are confirmed to have been infected during the campaign, including a marine and energy solutions company in Croatia, a transportation company in Abu Dhabi, a mining company in Egypt, a construction company in Dubai, an oil & gas firm in Kuwait, and a construction organization in Germany.
Despite the large scale of the campaign, behind it is not an expert gang of cybercriminals or a nation state actor, but “a relatively unskilled man in his mid-20s, operating from a location near the capital of Nigeria,” Check Point discovered.
Working on his own, the Nigerian national uses fraudulent emails seemingly coming from oil and gas giant Saudi Aramco, the world’s second largest daily oil producer. The phishing messages target financial departments within companies in an attempt to trick employees into revealing company bank details or into opening a malware-infected attachment.
The malware used in these attacks includes NetWire, a remote access Trojan that provides its operator with full control over infected machines, and Hawkeye, a software for logging key strokes (malware already associated with Nigerian cybercriminals). The attacks eventually resulted in a total of 14 successful infections. The cybercriminal ended up earning thousands of dollars in the process, the researchers say.
Despite showing a low level of cyber-skills, using crude and unsophisticated fraudulent emails, with almost no research or social engineering involved in creating them, the attacker was successful in his attempts.
The attacker used generic email titles, phrased as “Dear Sir/Ms,” sent the same email to numerous targets, “all in blind carbon copy, urging victims to send back banking details, perhaps for future scams.” He sent the emails from email addresses sale.cement_till_tw@yahoo.com, and cciticarinternational@yahoo.com.
The fraudster used old, generic and readily available online malware, as well as freeware to ‘scrape’ email addresses from corporate websites and used them as targets for his campaigns.
“The fact that the campaign was still effective, despite using only basic cyber-criminal techniques, highlights just how much of a problem these business email compromise (BEC) attacks have become,” Check Point said.
Last year, the FBI revealed that losses caused by BEC scams exceeded $3.1 billion. Victims are estimated to lose between $25,000 and $75,000 on average, per attack. However, it’s not only financial losses that victims should be concerned about, but also the fact that “the malware used by the criminal to infect organizations gives remote control over infected machines, and can perform keylogging functions. This enables harvesting of a variety of information from infected machines, such as details on the companies’ operations, assets and intellectual property.” Such details could be worth much more than the thousands of dollars obtained by fraud, Check Point says.
Another alarming aspect was that some of the targets are energy and infrastructure companies, which the unsophisticated cybercriminal was able to easily breach. Not only was the attacker able to compromise the networks of several large organizations, but he also managed to distribute his malware globally and remain under the radar for a long while.
“This highlights the need for all organizations to improve their security to protect against phishing and business email compromise scams, and to educate their employees to be cautious about opening emails, even from companies or individuals that they recognize,” Check Point said.
Warning: Two Dangerous Ransomware Are Back – Protect Your Computers
15.8.2017 thehackernews Ransomware
Ransomware has been around for a few years but has become an albatross around everyone's neck—from big businesses and financial institutions to hospitals and individuals worldwide—with cyber criminals making millions of dollars.
In just past few months, we saw a scary strain of ransomware attacks including WannaCry, Petya and LeakerLocker, which made chaos worldwide by shutting down hospitals, vehicle manufacturing, telecommunications, banks and many businesses.
Before WannaCry and Petya, the infamous Mamba full-disk-encrypting ransomware and the Locky ransomware had made chaos across the world last year, and the bad news is—they are back with their new and more damaging variants than ever before.
Diablo6: New Variant of Locky Ransomware
First surfaced in early 2016, Locky has been one of the largest distributed ransomware infections, infecting organisations across the globe.
By tricking victims into clicking on a malicious attachment, Locky ransomware encrypts nearly all file formats on a victim's computer and network and unlocks them until the ransom in Bitcoins is paid to attackers.
The ransomware has made many comebacks with its variants being distributed through Necurs botnet and Dridex botnet.
This time security researchers have discovered a fresh spam malware campaign distributing a new variant of Locky known as Diablo6 and targeting computers around the world, with the United States being the most targeted country, followed by Austria.
An independent security researcher using online alias Racco42 first spotted the new Locky variant that encrypts files on infected computers and appends the .diablo6 file extension.
Like usually, the ransomware variant comes in an email containing a Microsoft Word file as an attachment, which when opened, a VBS Downloader script is executed that then attempts to download the Locky Diablo6 payload from a remote file server.
The ransomware then encrypts the files using RSA-2048 key (AES CBC 256-bit encryption algorithm) on the infected computer before displaying a message that instructs victims to download and install Tor browser; and visit the attacker's site for further instructions and payments.
This Locky Diablo6 variant demands a sum of 0.49 Bitcoin (over $2,079) from victims to get their files back.
Unfortunately, at this time it is impossible to recover the files encrypted by the .Diablo6 extension, so users need to exercise caution while opening email attachments.
Return of Disk-Encrypting Mamba Ransomware
Mamba is another powerful and dangerous kind of ransomware infection that encrypts the entire hard disk on an affected computer instead of just files, leaving the system totally unusable unless a ransom is paid.
Similar tactics have also been employed by other ransomware attacks, including Petya and WannaCry, but the Mamba ransomware has been designed for destruction in corporates and other large organisations, rather than extorting Bitcoins.
Late last year, Mamba infected the San Francisco's Municipal Transportation Agency (MUNI) system's network over the Thanksgiving weekend, causing major train delays and forcing officials to shut down ticket machines and fare gates at some stations.
Now, security researchers at Kaspersky Lab have spotted a new campaign distributing Mamba infections, targeting corporate networks in countries, majorly in Brazil and Saudi Arabia.
Mamba is utilising a legitimate open source Windows disk encryption utility, called DiskCryptor, to fully lock up hard drives of computers in targeted organisations. So, there is no way to decrypt data as the encryption algorithms used by DiskCryptor are very strong.
Although it's not clear how the ransomware initially finds its way into a corporate network, researchers believe like most ransomware variants, Mamba might be using either an exploit kit on compromised or malicious sites or malicious attachments sent via an email.
The ransom note does not immediately demand money, rather the message displayed on the infected screen only claims that the victim's hard drive has been encrypted and offers two email addresses and a unique ID number to recover the key.
Here's How to Protect Yourself From Ransomware Attacks
Ransomware has become one of the largest threats to both individuals and enterprises with the last few months happening several widespread ransomware outbreaks.
Currently, there is no decryptor available to decrypt data locked by Mamba and Locky as well, so users are strongly advised to follow prevention measures in order to protect themselves.
Beware of Phishing emails: Always be suspicious of uninvited documents sent over an email and never click on links inside those documents unless verifying the source.
Backup Regularly: To always have a tight grip on all your important files and documents, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
Keep your Antivirus software and system Up-to-date: Always keep your antivirus software and systems updated to protect against latest threats.
Gmail for iOS Adds Anti-Phishing Feature that Warns of Suspicious Links
15.8.2017 thehackernews Apple
Phishing — is an older style of cyber-attack but remains one of the most common and efficient attack vectors for attackers, as a majority of banking malware and various ransomware attacks begin with a user clicking on a malicious link or opening a dangerous attachment in an email.
Phishing has evolved than ever before in the past few years – which is why it remains one of those threats that we have been combating for many years.
We have seen phishing campaigns that are so convincing and effective that even tech-savvy people can be tricked into giving away their credentials to hackers. And some that are "almost impossible to detect" and used to trick even the most careful users on the Internet.
To help combat this issue, Google has introduced a security defence for it's over a billion users that will help users weed out phishing emails from their Gmail inbox.
Google has rolled out new anti-phishing security checks for its Gmail app for iPhone users that will display a warning about potential phishing attempts when users click on a suspicious link from within the app on their iPhone or iPad.
This new feature will take nearly two weeks before it is available everywhere.
According to the tech giant, when a user clicks on a link that Google thinks could be suspicious, they will be displayed a pop-up, warning of an untrusted nature of the website they are attempting to visit.
Suspicious link
This link leads you to an untrusted site. Are you sure you want to proceed to example.com?
If the user ignores this first warning and continue, the Gmail app will display another warning with more detailed information about the suspected malicious website that the company finds it to be a malicious phishing page.
Warning – phishing (web forgery) suspected
The site you are trying to visit has been identified as a forgery, intended to trick you into disclosing financial, personal or other sensitive information.
You can continue to example.com at your own risk.
A similar feature has already been made available in the Gmail app for Android since May of this year.
Although the feature would surely not detect every phishing attempt that could compromise your credentials, we believe it will help users combat such attacks to much extent.
So, always exercise caution over what links you click mentioned in your emails or attachments you open.
Additionally, Gmail users need to enable two-factor authentication, so even if attackers have access to your credential, they will not be able to proceed further without your phone or the USB cryptographic key in order to access your account.
How Just Opening A Malicious PowerPoint File Could Compromise Your PC
15.8.2017 thehackernews Virus
A few months back we reported how opening a simple MS Word file could compromise your computer using a critical vulnerability in Microsoft Office.
The Microsoft Office remote code execution vulnerability (CVE-2017-0199) resided in the Windows Object Linking and Embedding (OLE) interface for which a patch was issued in April this year, but threat actors are still abusing the flaw through the different mediums.
Security researchers have spotted a new malware campaign that is leveraging the same exploit, but for the first time, hidden behind a specially crafted PowerPoint (PPSX) Presentation file.
According to the researchers at Trend Micro, who spotted the malware campaign, the targeted attack starts with a convincing spear-phishing email attachment, purportedly from a cable manufacturing provider and mainly targets companies involved in the electronics manufacturing industry.
Researchers believe this attack involves the use of a sender address disguised as a legitimate email sent by a sales and billing department.
Here's How the Attack Works:
The complete attack scenario is listed below:
Step 1: The attack begins with an email that contains a malicious PowerPoint (PPSX) file in the attachment, pretending to be shipping information about an order request.
Step 2: Once executed, the PPSX file calls an XML file programmed in it to download "logo.doc" file from a remote location and runs it via the PowerPoint Show animations feature.
Step 3: The malformed Logo.doc file then triggers the CVE-2017-0199 vulnerability, which downloads and executes RATMAN.exe on the targeted system.
Step 4: RATMAN.exe is a Trojanized version of the Remcos Remote Control tool, which when installed, allows attackers to control infected computers from its command-and-control server remotely.
Remcos is a legitimate and customizable remote access tool that allows users to control their system from anywhere in the world with some capabilities, like a download and execute the command, a keylogger, a screen logger, and recorders for both webcam and microphone.
Since the exploit is used to deliver infected Rich Text File (.RTF) documents, most detection methods for CVE-2017-0199 focuses on the RTF. So, the use of a new PPSX files allows attackers to evade antivirus detection as well.
The easiest way to prevent yourself completely from this attack is to download and apply patches released by Microsoft in April that will address the CVE-2017-0199 vulnerability.
Public Cloud Is Most Secure: Report
15.8.2017 securityweek Security
Public cloud environments are more secure than private and hybrid clouds and on-premises networks, according to data collected by cloud security solutions provider Alert Logic over a period of 18 months.
Alert Logic’s 2017 Cloud Security Report is based on the analysis of more than 2.2 million security incidents captured by the company’s products from more than 3,800 customers between August 2015 and January 2017.
The data shows that organizations using public cloud environments have encountered, on average, 405 security incidents, while hybrid networks have experienced nearly 1,000 incidents. Hosted private cloud environments and on-premises networks experienced 684 and 612 incidents, respectively.
In all cases, the most common type of security incident was SQL injection reconnaissance, followed by Joomla web application attacks and SQL injection. Web application attacks are by far the most common, followed by brute force, reconnaissance, and advanced malware attacks.
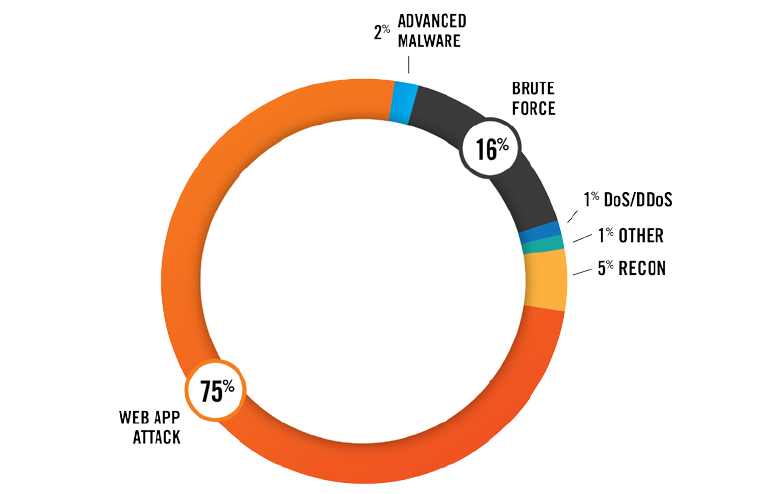
In the case of web attacks, the most common, accounting for 80 percent of incidents, are SQL injection and remote code execution. The most targeted are content management systems (CMSs) and e-commerce platforms such as Joomla, WordPress, Apache Struts and Magento.
Alert Logic observed more than 630,000 SQL injection attempts, including a few hundred attacks that were complex and likely launched by skilled and determined threat actors.
As for brute-force attacks, WordPress was the most targeted, followed by MS SQL and SSH. While malware attacks represented only 2 percent of the incidents observed by Alert Logic, the company said it had seen an increase in server-side ransomware infections.
“To be fair, our data set does not conclusively prove that public clouds are ‘more secure,’ if such a question can even be framed effectively or answered definitively,” explained Misha Govshteyn, founder of Alert Logic. “But we do know that within our customer base, we less frequently see malicious activity in public-cloud environments, even though web applications are one of the most dominant workloads there. And we know that web apps account for the highest share of attacks leading to breaches.”
“For the moment, even the public cloud is not so secure that there is nothing to worry about; far from it,” Govshteyn added. “While we saw close to 37% more incidents in on-premises data centers, this still leaves each public cloud deployment to withstand just over (on average) around 400 incidents in the 18-month period covered by this report. And even lower incident rates do not necessarily translate to lower risk – especially when, as is increasingly more common, businesses rely on the public cloud to handle their highest value assets.”
Webroot Acquires Security Awareness Training Firm Securecast
15.8.2017 securityweek Security
Endpoint and network security solutions provider Webroot announced on Tuesday that it has acquired Securecast, an Oregon-based company that specializes in security awareness training. Financial terms of the deal have not been disclosed.
Webroot has built on Securecast’s platform to offer managed service providers (MSPs) security awareness programs that their business customers can use to reduce the risks and costs associated with phishing, ransomware and other threats.
Webroot's Security Awareness Training offering is already available in beta and is expected to become generally available sometime this fall. Once it becomes generally available, it will be part of the company’s SecureAnywhere portfolio.
This fully hosted awareness-as-a-service platform includes a sophisticated phishing simulator that allows organizations to test their employees, and an end-user training program designed for educating employees on cybersecurity best practices.
The phishing simulator includes a template library that enables MSPs to test users with real-world attack scenarios. Companies can also design custom phishing attacks that are relevant to their line of business.
The platform is easy to use, it has reporting capabilities, and it includes all the tools needed for an organization to manage its own security awareness training campaign, Webroot said.
“The human factor is a consistent weakness in overall cyber defenses, and security awareness training is the only solution. As cyberattacks, such as phishing, become increasingly sophisticated, users are exposed to a variety of hidden threats that will compromise their own data along with their employer’s data,” said Chad Bacher, SVP of Product Strategy and Technology Alliances at Webroot. “Building on Securecast, Webroot will offer our MSP partners the security awareness training they need to address this evolving threat landscape, and build a profitable new line of business.”
Webroot said the decision to launch a security awareness training service comes in response to requests from MSPs for high-quality, cost-effective and ongoing training.
In its announcement of the acquisition, the security firm cites data from Verizon’s 2017 Data Breach Investigations Report, which revealed that 43 percent of breaches involved social engineering — in most cases phishing. The same Verizon report showed that in a company with 30 or more employees, roughly 15 percent of users who fell victim to phishing once took the bait a second time as well.
New "Disdain" Exploit Kit Spotted on Underground Forums
15.8.2017 securityweek Exploit
A new exploit kit (EK) has emerged recently on underground forums, where a malware developer is advertising it starting at just $80.
Called Disdain and discovered by malware analyst David Montenegro, the toolkit is available for rent on a daily, weekly, or monthly basis, priced at $80, $500, and $1,400, respectively. Security researchers have already managed to track the advert for the EK and learn more about its alleged capabilities.
According to Disdain’s author, the main features of the toolkit include domain rotator, RSA key exchange for exploits, panel server untraceable from payload server, geolocation, browser & IP tracking, and domain scanning capabilities.
The malware developer claims the toolkit can exploit over a dozen vulnerabilities in Firefox (CVE-2017-5375, CVE-2016-9078, CVE-2014-8636, CVE-2014-1510, CVE-2013-1710), Internet Explorer (CVE-2017-0037, CVE-2016-7200 (Edge as well), CVE-2016-0189, CVE-2015-2419, CVE-2014-6332, CVE-2013-2551), Flash (CVE-2016-4117, CVE-2016-1019, CVE-2015-5119), and Cisco Web Ex (CVE-2017-3823).
There has not been a malware distribution campaign fueled by this exploit kit found to date, likely because Disdain hasn’t been around long enough to prove it is a viable tool. Furthermore, its author, who goes by the name of Cehceny, doesn’t have a good reputation among cybercriminals and is considered a scammer on at least one underground hacking forum, BleepingComputer notes.
Although no botnet or malvertising campaign is redirecting traffic to Disdain’s landing pages at the moment, the toolkit could turn into a major threat if miscreants start employing it. As soon as users are redirected to one of the exploit kit’s pages, the toolkit can scan the potential victim’s browser and attempt to exploit one of the discovered vulnerabilities to install malware.
Disdain includes a large number of new exploits, which could help it gain traction, especially since the exploit kit landscape has been greatly shaken over the past year, starting with Angler and Nuclear, both of which went down in the first half of last year.
Exploit kit activity this year has been only a fraction of what it was in early 2016, and continues to diminish as more toolkits are taken down and very few new players observed. Cybercriminals, however, are turning to other methods of distributing malware, including spam emails and other types of attacks.
Stenografie – nová technika hackerů
15.8.2017 SecurityWorld
Analytici společnosti Kaspersky Lab zaznamenali nový znepokojivý trend. Během analýzy řady kyberšpionážních a kyberkriminálních kampaní zjistili, že hackeři čím dál častěji používají stenografii – digitální formu staré techniky ukrývání informací do obrazu. Tím se snaží skrýt stopy své zákeřné aktivity v infikovaných počítačích. V poslední době se podařilo zachytit několik malwarových aktivit zaměřených na kyberšpionáž a krádeže finančních informací využívajících tuto techniku.
V průběhu běžného cíleného kyberútoku si útočníci po úspěšné infiltraci napadené sítě snaží vybudovat stabilní zázemí. Následně sbírají cenné informace, které posílají na příkazový a řídicí server. Účinná bezpečnostní řešení nebo bezpečnostní odborníci jsou ve většině případů schopni zaznamenat přítomnost kyberzločinné aktivity v síti v její jakékoliv fázi, včetně finální, kdy infekce opouští systém.
Během ní totiž útok v systému zanechá své stopy, jako jsou například protokolovaná připojení k neznámé nebo zakázané IP adrese. Když je ale v průběhu útoku využita stenografie, stává se detekce této finální fáze velmi obtížnou.
Při takovém scénáři útočníci vloží informace, které chtějí ukrást, přímo do kódu jednoduchého vizuálního obrazového nebo video souboru, který následně odešlou do C&C. Kvůli tomu je velmi nepravděpodobné, že podobná událost bude detekována bezpečnostním řešením. Je to způsobeno tím, že po zásahu útočníkem nedojde k vizuální změně obrázku, ani ke změně jeho velikosti a dalších parametrů, čímž tedy nevyvolají žádný poplach. Stenografie je tak velmi lákavou technikou pro hackery především v situaci, kdy chtějí dostat ukradená data z napadené sítě.
Zaujal vás tento článek? Přehled nejzajímavějších zpráv získáte odebíráním našeho newsletteru »
V průběhu několika posledních měsíců pozorovali odborníci Kaspersky Lab minimálně tři kyberšpionážní operace, které tuto techniku využily. Více alarmující však je, že si tuto techniku osvojují i běžní kyberzločinci. Odborníci Kaspersky Lab se s ní setkali u pokročilých verzí trojských koní Zerp, ZeusVM, Kins, Triton a dalších.
Většina z těchto malwarových rodin útočí převážně na finanční instituce a uživatele finančních služeb. Stáváme se tak svědky přicházející masové adopce této techniky ze strany tvůrců malwaru, což bude mít důsledek na složitější detekci malwaru.
„I když to není poprvé, co se setkáváme s využitím pokročilé zákeřné techniky běžnými kyberzločinci, je tento případ se stenografií v něčem odlišný. Bezpečnostní průmysl totiž doposud nenašel způsob jak spolehlivě detekovat data vyváděná z napadeného systému touto cestou. Obrázky využívané kyberzločinci pro vyvedení ukradených informací jsou velmi velké. Ačkoliv existují algoritmy schopné automaticky detekovat tuto techniku, jejich masové využití by bylo velmi nákladné a vyžadovalo by obrovské množství výpočetního výkonu.
Na druhou stranu je poměrně snadné identifikovat obrázek obsahující ukradená cenná data za pomoci manuální analýzy. Tato metoda má nicméně svá omezení vzhledem k tomu, že je bezpečnostní analytik schopný za den zanalyzovat pouze omezené množství obrázků. Řešením je tak kombinace obojího – stoje a lidského faktoru,“ říká Alexey Shulmin, bezpečnostní odborník ve společnosti Kaspersky Lab.
HBO s hackery vyjednávat nebude. Ti mezitím zveřejnili další materiál
15.68.2017 Živě.cz
HBO s hackery vyjednávat nebude. Ti mezitím zveřejnili další materiál | https://www.facebook.com/pg/GameOfThrones/photos/?ref=page_internal
Televizní kanál HBO odmítá, že by vyjednával s hackery, kteří na začátku měsíce ukradli 1,5 TB jeho dat a postupně trousí některá z nich na internet. Teď v reakci na prohlášení HBO zveřejnili nové epizody seriálu Curb Your Enthusiams.
Prohlášení HBO odporuje uniklému screenshotu e-mailu, ve kterém společnost nabízí hackerů 250 tisíc dolarů jako výkupné. Tento screenshot ale zřejmě bude falešný – HBO říká, že nezaplatí ani dolar.
„S hackery nekomunikujeme a nebudeme komentovat každý malý kousek informace, který se na veřejnosti objeví. Nějaký materiál se ještě na internet zřejmě ještě dostane. My s tím nic neuděláme. Samozřejmě žádná firma nechce, aby její majetek byl ukraden a zveřejněn na internetu, my jsme se ale rozhodli věřit naší síle a koukat do předu,“ vysvětlovalo HBO serveru Variety.
Hackeři podle videa, které se objevilo v médiích, požadují „jejich šesti měsíční mzdu v bitcoinech“, přičemž tvrdí, že si ročně vydíráním firem vydělají až 15 milionů dolarů. Jako důkaz toho, že to myslí vážně, zveřejnili vedle Hry o trůny neodvysílané díly Ballers, Insecure nebo komedii Barry, plus e-maily programové viceprezidentky HBO Leslie Cohenové.
Televizní stanice momentálně s forenzními experty, policií a odborníky na kyberbezpečnost celou věc prošetřuje. K identitě útočníků se jí ale zatím přiblížit nepodařilo.
Děravý je Internet Explorer i Firefox. Kritické chyby řešilo i Adobe
15.8.2017 Novinky/Bezpečnost
Hned několik velkých softwarových společností muselo v uplynulém týdnu řešit kritické chyby ve svých produktech. Na pozoru by se tak měli mít lidé, kteří ve svých počítačích používají programy od Microsoftu, Adobe a Mozilly.
Na velké množství zranitelností v jednotlivých programech upozornil český Národní bezpečnostní tým CSIRT.CZ.
Poměrně velké množství trhlin bylo nalezeno v produktech Microsoftu. Programátoři amerického softwarového gigantu je však zvládli opravit v rámci pravidelných měsíčních aktualizací. „Zranitelnosti Microsoft opravil v prohlížečích Internet Explorer, Microsoft Edge, v operačních systémech Microsoft Windows a dále v produktech Microsoft SharePoint a Microsoft SQL Server,“ podotkl Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
S instalací neotálet
Objevené trhliny představují pro uživatele velké nebezpečí. „V nejzazším případě by zneužití těchto zranitelnosti mohlo umožnit vzdálenému útočníkovi převzít kontrolu nad stanicí oběti,“ zdůraznil Bašta.
To jinými slovy znamená, že prostřednictvím chyb mohou kyberzločinci propašovat na cizí počítač prakticky jakýkoli škodlivý kód, případně jej zcela ovládnout na dálku. Mohli se tak snadno dostat k uloženým datům, případně odchytávat přihlašovací údaje na různé webové služby.
S instalací aktualizací by tak uživatelé neměli v žádném případě otálet.
Desítky dalších zranitelností
To platí i v případě trhlin, které byly objeveny v programech od Adobe. Konkrétně v aplikacích Flash Player, Reader, Acrobat, Digital Editions a Experience Manager bylo objeveno dohromady přes 80 zranitelností. Pro všechny jsou naštěstí k dispozici již záplaty.
Více se o chybách v programech od Adobe dozvíte v našem dřívějším článku.
„Také společnost Mozilla vydala opravy pro webový prohlížeč Firefox. I v tomto případě byly opraveny kritické zranitelnosti a je doporučena aktualizace,“ uzavřel Bašta.
Stahovat všechny opravy jednotlivých programů je možné prostřednictvím automatických aktualizací, případně přímo z webových stránek daných tvůrců.
Overall Security of Password Managers Debatable, Cracking Firm Says
15.8.2017 securityweek Security
A password recovery firm has claimed that the overall security of password managers is debatable. "Are password managers more secure than keeping a list of passwords in a single Excel spreadsheet?" it asks. "Not necessarily," it concludes.
Announcing the latest version of the Elcomsoft Distributed Password Recovery (EDPR) tool, Oleg Afonin blogged that it can now recover the master passwords for the 1Password, KeePass, LastPass and Dashlane password managers. This can be a legitimate requirement for users who lose or forget their master password -- or in some cases for law enforcement looking for suspects' online account passwords for legal purposes.
"Obviously, if the master password is compromised, all other passwords stored in the vault are compromised as well," writes Afonin. For this reason, password managers go to great lengths to make that password irrecoverable. For example, he writes, "LastPass generates the encryption key by hashing the username and master password with 5,000 rounds of PBKDF2-SHA256, while 1Password employs even more rounds of hashing."
Despite this, Elcomsoft claims to be able to brute force the master keys. In its published benchmarks, it shows that of the four password managers, it takes longest to recover the keys for LastPass; followed by 1Password, Keepass and then Dashlane. It justifies its Excel spreadsheet comment by showing that it takes much longer to brute force encrypted Office 2016 documents than any of the tested four password managers.
In theory, anything can be brute forced if the 'attacker' has sufficient time and computing power available -- Elcomsoft is simply saying it can do so in a timely fashion. SecurityWeek spoke to Dashlane senior manager, Ryan Merchant, about the report; and it is noticeable, if understandable, that he did not address the cracking capabilities of EDPR. Instead, Merchant focused on the overall advantages of using a password manager.
"A web-based password manager keeps your passwords encrypted in secure databases in the cloud," said Merchant. "In order for anyone to access your account, they'll need to possess your strong master password in order to decrypt the password manager's database." This is, of course, exactly what Elcomsoft claims to be able to do.
However, the strength of the password manager, said the Merchant, really lies in its ease of use. "Instead of writing your passwords on sticky notes or reusing the same password for all of your accounts, password managers provide a safe place for you to store, manage, and protect your passwords and other private information," he said.
"Dashlane users in particular do not need to invent, know, type or remember any of their passwords. Dashlane does it for them. In a sense, a Dashlane user has digital accounts, not passwords," he continued. "We have already started to kill the password by making the actual passwords irrelevant to our users."
Password managers aid the user in creating strong, unique passwords for different accounts. This is both more secure and easier to manage than could be done manually by the vast majority of users. Its one theoretical weakness is that if the master password can be cracked, then all the users' different passwords are accessible. For this reason, the developers make it difficult for them to be brute-forced.
What Elcomsoft has done has make it possible, in extremis, for the user to recover them regardless. As a forensic tool, this becomes very valuable -- so long as it cannot also be used by adversaries. SecurityWeek raised this question with Olga Koksharova, marketing director at Elcomsoft.
"As for adversaries," she told SecurityWeek, "speaking about Elcomsoft Distributed Password Recovery it's always a question of being able to log into a system and having administrative rights that would allow them to install the tool and run it. However, adversaries might only need extract just some information from the computer in order to use it afterwards on another workstation with all necessary tools running. In case with password managers, we need to feed a particular file to EDPR in order to brute-force it."
It would not be easy, but it would -- under certain conditions -- be possible for an attacker to make use of EDPR. This, of course, would be much simpler if a user lost or had a mobile device stolen. Koksharova advises, "Never leave your computers with valuable information unattended (lending it to someone is out of question) and always protect the computer itself with strong passwords."
The moral from this story is simple: password managers will almost always be more secure than manually generated and managed passwords -- but they do not relieve the user from all responsibility. The password manager itself still needs to be protected.
Last week, Dashlane published the results of its 2017 Password Power Rankings study, which examined the password practices that different companies encourage or force onto their users.
Four Arrested in India for Leaking 'Game of Thrones' Episode
15.8.2017 securityweek Incindent
Four people have been arrested in India for leaking an episode from HBO's "Game of Thrones" television series before it was aired in the country, police said Monday.
Already the most pirated show in TV history, the popular fantasy drama -- which tells the story of noble families vying for the Iron Throne -- has been plagued by leaks in recent weeks following the premiere of the seventh season.
After receiving a complaint for a company "we investigated the case and have arrested four individuals for unauthorised publication of the fourth episode from season seven," Deputy Commissioner of Police Akbar Pathan told AFP.
He said the four -- accused of criminal breach of trust and computer-related offences -- would be detained until August 21 amid an investigation.
The case was filed by a Mumbai-based company responsible for storing and processing the TV episodes for an app, local media said.
The four arrested were company employees who possessed official credentials giving them access to the episodes, the reports added.
Game of Thrones has more Emmy Awards than any narrative show in history and airs in 170 countries, with viewership figures shattering records across the world.
As well as being a hit globally, it has a massive fan base in South Asia.
Showrunners David Benioff and D.B. Weiss last year announced the shortened run of seven and six episodes for the final two seasons and confirmed the summer return for season seven, a departure from the usual April premieres.
The show has been teasing winter's arrival since its pilot episode in 2011, and in the latest episode preview "Death Is The Enemy" has finally moved closer to showcasing a battle between a horde of undead "White Walkers" from the frozen North and a troop of warriors led by hero Jon Snow (Kit Harington).
Lawyer: British Hacking Suspect Will be Vindicated
15.8.2017 securityweek Hacking
A lawyer for a 23-year-old British computer security researcher accused of creating malware to attack the banking system on Monday called him a "hero" and predicted he would be "fully vindicated."
The lawyer commented after Marcus Hutchins -- who three months ago found a "kill switch" to stem the spread of the devastating WannaCry ransomware outbreak -- pleaded not guilty to US charges of creating and distributing malicious software.
Hutchins was arrested earlier this month in Las Vegas after attending the Def Con gathering of computer hackers.
The case stunned the computer security community and drew fire from critics who argued that researchers often work with computer code which can be deployed for malicious purposes.
"Marcus Hutchins is a brilliant young man and a hero," said Marcia Hofmann, an attorney affiliated with the Electronic Frontier Foundation, a digital rights group, who represented Hutchins at the hearing.
"He is going to vigorously defend himself against these charges. And when the evidence comes to light we are confident he will be fully vindicated."
A federal indictment accuses Hutchins and another individual of making and distributing Kronos "banking Trojan," a reference to malicious software designed to steal user names and passwords used at online banking sites.
The indictment set the time of the activity by Hutchins as being from July 2014 to July 2015.
A trial date was set for the case for October 23, according to participants at the hearing, who added that a federal magistrate agreed to allow Hutchins to reside in California while the case is pending.
Hutchins, who lives in Britain and remains free on $30,000 bail, works for a California-based computer security firm.
"We are very pleased that the court modified the terms (of bail) allowing him to return to his important work," said Brian Klein, the second attorney for Hutchins.
His arrest has sparked criticism from some researchers who argue that the case could dissuade "white hat hackers" -- those who find flaws to help fix them -- from cooperating with authorities.
Hutchins, known by the alias "Malwaretech," was charged in an indictment dated July 12 and unsealed in early August by federal authorities in Wisconsin.
According to the indictment, Hutchins was part of a conspiracy to distribute the hacking tool on so-called dark markets.
British Researcher Pleads Not Guilty to Creating Malware
15.8.2017 securityweek Virus
British cybersecurity researcher Marcus Hutchins, known online as “MalwareTech,” has pleaded not guilty in a U.S. court to charges related to creating and selling a banking Trojan named Kronos.
The 23-year-old expert from Ilfracombe, England, became famous and was named a “hero” a few weeks ago after he helped stop the WannaCry ransomware attack by registering a domain that acted as a kill switch for the malware. MalwareTech had not made his real identity known online, but the fame brought by the WannaCry incident led to reporters tracking him down.
On Monday, Hutchins, who works for LA-based Kryptos Logic, pleaded not guilty in a Wisconsin federal court to all the charges brought against him. The hacker cannot leave the United States during his trial and he will be tracked via GPS.
Interestingly, while he will be allowed to access the Internet in order to continue working, he has been prohibited from accessing the domain used to stop the WannaCry outbreak.
The researcher was arrested while preparing to return to the U.K. from Las Vegas, where the Black Hat and Def Con security conferences had taken place. He was later released on a $30,000 bond, an amount raised by his friends and supporters.
The expert and an unnamed individual who Hutchins allegedly conspired with have been charged with six counts related to the creation, advertising, sale and use of the Kronos malware.
According to authorities, which claim these activities took place in 2014 and 2015, Hutchins’ partner attempted to sell the malware on dark web marketplaces, including the recently shut down AlphaBay, for $2,000 and $3,000.
Many believe the charges against the British researcher are the result of a mistake, considering his involvement in malware analysis. Some believe code written by him may have been weaponized by cybercriminals. A legal defense donation page has been set up to raise the funds necessary to ensure that Hutchins gets a fair trial.
"Marcus Hutchins is a brilliant young man and a hero," said Marcia Hofmann, the EFF and Zeitgeist Law attorney representing Hutchins at the hearing on Monday. "He is going to vigorously defend himself against these charges. And when the evidence comes to light we are confident he will be fully vindicated."
Hutchins is also represented by Brian Klein, a partner at Baker Marquart.
PowerPoint Slide Show Files Used to Install Malware
15.8.2017 securityweek Virus
PowerPoint Slide Show Files Exploited for RAT Distribution
A Microsoft Office vulnerability patched by Microsoft in April, after threat actors had been using it in live attacks, is being abused in a new manner to infect computers with a remote access Trojan, Trend Micro warns.
Tracked as CVE-2017-0199, the originally zero-day remote code execution vulnerability was previously abused in attacks leveraging malicious Rich Text File (RTF) documents, exploiting a flaw in Office’s Object Linking and Embedding (OLE) interface to deliver malware such as the DRIDEX banking Trojan.
In recently observed attacks, however, CVE-2017-0199 is being exploited using a new method where PowerPoint Slide Show is abused for malware delivery. The malicious document is delivered as attachment to a spear-phishing email attachment, and the security researchers suggest that, as part of the attack, a sender address masquerading as that of a business partner is being used.
The email message is supposedly an order request, but no business documents are attached to it. What is attached, however, is a malicious PowerPoint Show (PPSX file) that supposedly leverages CVE-2017-8570, a different Microsoft Office vulnerability (supposedly an error made by the toolkit developer).
Once the file has been executed, however, PowerPoint initializes the script moniker and runs the remote malicious payload via the PowerPoint Show animations feature. After the CVE-2017-0199 vulnerability is successfully exploited, it downloads a file called logo.doc, which is instead an XML file with JavaScript code.
The JavaScript runs a PowerShell command to download and execute RATMAN.EXE from its command and control (C&C) server. This file is a Trojanized version of the REMCOS legitimate and customizable remote access tool (RAT) that, once executed, provides the attacker with the possibility to run remote commands on the user’s system.
The tool can be used to download and execute commands on the infected machine, to log keystrokes and screen activity, and to record audio and video using the system’s microphone and webcam. The Trojanized tool uses an unknown .NET protector to add more protection and obfuscation to hinder analysis even more, and also leverages encrypted communication.
“Ultimately, the use of a new method of attack is a practical consideration; since most detection methods for CVE-2017-0199 focuses on the RTF method of attack, the use of a new vector—PPSX files—allows attackers to evade antivirus detection,” Trend Micro notes.
As always when the use of malicious documents delivered via spam email is involved, users should pay extra caution when opening them (the same applies to clicking on links in emails), even if they come from seemingly legitimate sources. Organizations should also implement mitigation techniques against phishing attacks, to avoid compromise.
“Users should also always patch their systems with the latest security updates. Given that Microsoft already addressed this vulnerability back in April, users with updated patches are safe from these attacks,” the security researchers also note.
Dragos Raises $10 Million to Protect Critical Infrastructure From Cyber Attacks
15.8.2017 securityweek ICS
Dragos, a startup focused on protecting industrial control systems (ICS) and critical infrastructure from cyber threats, announced on Monday that it has raised $10 million through a Series A funding round.
According to Hanover, Maryland-based Dragos, the new funding will be used to hire additional staff to support rising customer demand fueled by recently announced partnerships with Deloitte and CrowdStrike.
Founded May 2016, Dragos offers three core offerings, along with its CyberLens network assessment tool. The three core offerings include the Dragos Platform, the Dragos Threat Operations Center, Global ICS Intelligence.
“This combination gives customers access to technology to monitor and respond to threats in the ICS, along with intelligence to make informed decisions about threats,” the company explains. “Services range from threat hunting to incident response, as well as lightweight software for routine assessments.”
Dragos has been under the spotlight recently for its analysis and report on CRASHOVERRIDE (AKA Industroyer), the malware used to disrupt power in a cyber attack against Ukraine’s national power company Ukrenergo last December. CRASHOVERRIDE is the only known malware that has successfully disrupted the electrical grid.
The company’s biggest technological differentiator is its behavioral analytics. Instead of “anomaly detection” and other types of machine learning-driven technologies that are hitting the market, the approach of Dragos is to codify human experience facing human adversaries. It identifies adversary tradecraft and turns it into behavioral analytics. As a result, defenders get context of what is going on and recommendations on what to do next, not merely a series of alerts.
Dragos was founded by Robert M. Lee, Jon Lavender and Justin Cavinee, former members of the U.S. intelligence community who worked on identifying, analyzing and responding to ICS-focused cyberattacks coming from nation-state attackers.
“Dragos exists to safeguard civilization,” said Lee, who serves as CEO of Dragos. “Critical infrastructure powers the global economy and the fabric of modern society.”
“We all strongly believe that civilian infrastructure should be off limits to any adversaries, no matter where the infrastructure is located in the world,” added Lee, who will be speaking on the subject of CRASHOVERRIDE at SecurityWeek’s 2017 ICS Cyber Security Conference in October.
The Series A round was led by investors Energy Impact Partners (EIP) and Allegis Capital. Additional support was provided by DataTribe, a cybersecurity “startup studio” that initially funded the company with a $1.2 million Seed round in August 2016
“Industrial control systems are unique unto themselves – hybrid digital and analog environments with very different operational temperaments,” said Bob Ackerman, founder and a Managing Director of cybersecurity investment firm Allegis Capital. “Unless you have lived your life in this environment, you can’t truly appreciate how different or complex ICS systems are.”
Attackers Combine Office Exploits to Avoid Detection
15.8.2017 securityweek Vulnerebility
Researchers at Cisco Talos have come across an attack that combines two Microsoft Office exploits, one old and one new, likely in an effort to avoid detection.
One of the exploits leverages CVE-2017-0199, an Office vulnerability patched by Microsoft in April with its monthly security updates. The security hole had been exploited in attacks before Microsoft released a fix. An exploit has since been added to the toolkits of numerous threat groups, including cybercriminals and cyberspies linked to China and Iran.
In the attacks observed by Cisco Talos, CVE-2017-0199 was used in combination with CVE-2012-0158, an old Office flaw that is still exploited in many campaigns.
The cybercriminals have apparently attempted to use these vulnerabilities to deliver the Lokibot banking Trojan. The attack also drops an older version of Ramnit, but experts believe a Ramnit infection component may have been picked up by accident somewhere along the way.
While the combination of exploits did not work as intended during Cisco’s tests, researchers have analyzed the code in order to determine what the attackers were hoping to accomplish.
“The attackers did not seem to have a good quality assurance process or perhaps the technical expertise to understand what will happen if they simply included an automatically generated CVE-2012-0158 exploit in combination with CVE-2017-0199,” said Cisco’s Vanja Svajcer.
In most attacks involving CVE-2017-0199, attackers send out specially crafted documents set up to exploit the vulnerability that exists in code responsible for handling OLE2Link embedded objects. By pointing a remote OLE2Link object to an HTML application file (HTA), the application will get executed and the malware is delivered.
One problem with this attack is that Word informs the user that the document contains links which may refer to other files and asks them if they want to update the document. While exploitation takes place regardless of the user’s answer, the dialog could still raise suspicion.
In the attack exploiting both vulnerabilities, the initial document exploits CVE-2017-0199, but instead of an HTA file, the OLE2Link object points to another document exploiting CVE-2012-0158, which in turn fetches Ramnit and Lokibot.
Due to some mistakes made by the cybercriminals, Word crashes when loading the second exploit. However, had the exploit chain worked, the malware would have been downloaded without the “document contains links” dialog being displayed.
“One has to wonder why did the attackers use the combination of a newer and an older exploit at all? The combination would not be executed if the targeted system had a patch against either of the exploits. In addition, if the targeted system was vulnerable to CVE-2012-0158 it would be much easier for the attackers to use a single exploit targeting this vulnerability,” Svajcer explained.
“An assumption we can make is that that the attackers used the combination to avoid Word displaying the prompt which may raise suspicions for the target end user. Another possibility is that they attempted to use this combination in order to avoid behavioral detection systems which may be triggering on the combination of Ole2Link in a word document and a download of an HTA file,” the expert added.
The Disdain exploit kit appears in the threat landscape
15.8.2017 securityaffairs Exploit
The Disdain exploit kit is available for rent on a daily, weekly, or monthly basis for prices of $80, $500, and $1,400 respectively.
The security researcher David Montenegro discovered a new exploit kit dubbed Disdain that is offered for rent on underground hacking forums by a malware developer using the pseudonym of Cehceny.
View image on TwitterView image on TwitterView image on Twitter
Follow
David Montenegro @CryptoInsane
Disdain Exploit Kit - New Exploit Kit up for sale in Underground Forum - Copy && Paste .. 🤔.. Beps Exploit Kit .. 🤔.. $./I_love_weekends.py
7:16 AM - Aug 9, 2017
1 1 Reply 18 18 Retweets 27 27 likes
Twitter Ads info and privacy
The Disdain exploit kit is available for rent on a daily, weekly, or monthly basis for prices of $80, $500, and $1,400 respectively.

After the Angler EK and Nuclear EK disappeared from the threat landscape, the Sundown EK conquered the criminal underground.
With the Sundown EK has been inactive since early this year, the Terror EK is being very popular in the cybercriminal ecosystem. The Disdain exploit kit appears very cheap compared to other exploit kits such as Nebula EK, that goes for rent on a daily, weekly, or monthly basis for prices of $100, $600, and $2,000 respectively.
According to security experts at Intsights that found an ad of the Disdain exploit kit on a Russian-speaking forum, its main features are:
Domain Rotator
RSA Key exchange for Exploits
Panel server is untraceable from Payload server
Geolocation available
Browser & IP tracking
Scan domain
When users visit a website hosting the Disdain exploit kit, it gathers info on the specific browser used by the visitor and attempts to use one of the exploits to deliver a malware on the victim’s machine.
Even is the Disdain exploit kit includes a limited number of exploits because it is very young, most of them are newer exploits. Below is the full list of exploits advertise by the author Cehceny:
CVE-2017-5375 – FF
CVE-2017-3823 – Extension (Cisco Web Ex)
CVE-2017-0037 – IE a
CVE-2016-9078 – FF
CVE-2016-7200 – EDGE + IE a
CVE-2016-4117 – FLASH
CVE-2016-1019 – FLASH
CVE-2016-0189 – IE
CVE-2015-5119 – FLASH
CVE-2015-2419 – IE
CVE-2014-8636 – FF
CVE-2014-6332 – IE
CVE-2014-1510 – FF
CVE-2013-2551 – IE
CVE-2013-1710 – FF
According to the experts at Bleepingcomputer, currently, there is no malvertising campaign or botnet leveraging the Disdain exploit kit because Cehceny is considered a scammer on at least one major underground hacking forum.
“The Disdain ad was first spotted last week. Currently, there is no malvertising campaign or botnet redirecting traffic to any Disdain “landing page,” according to a security researcher who spoke with Bleeping Computer about Disdain but did not want to reveal his name.” wrote Catalin Cimpanu.
“One reason why we haven’t seen any active campaign might be that Disdain’s author — Cehceny — is currently banned and marked as a “ripper” (scammer) on at least one major underground hacking forum.”
Looking at exploit kit market we are assisting to a rapid decline due to the difficulty of finding exploitable flaws in modern browsers.
Currently, most popular exploit kits are RIG, Rig-V, Terror, Magnitude, Kaixin, and Nebula.
Stay tuned!
North Korea-Linked Lazarus APT targets U.S. Defense contractors
15.8.2017 securityaffairs APT
The North Korea-linked Lazarus APT group as Lazarus is believed to be behind attacks targeting United States defense contractors.
According to Palo Alto Networks, the North Korea-linked Lazarus APT group as Lazarus is believed to be behind attacks targeting United States defense contractors.
The activity of the Lazarus APT Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. Security researchers discovered that North Korean Lazarus APT group was behind recent attacks on banks, including the Bangladesh cyber heist.

According to security experts, the group was behind, other large-scale cyber espionage campaigns against targets worldwide, including the Troy Operation, the DarkSeoul Operation, and the Sony Picture hack.
The Lazarus group, tracked by the U.S. government as Hidden Cobra, seems to be behind recent attacks against U.S. defense contractors, likely in cooperation with other hacker groups.
The last campaign conducted by the Lazarus APT leverages spear phishing emails containing weaponized Microsoft Office documents. The documents are written in English and embed malicious macros to deliver a malware.
The hackers used decoy documents describing job openings at some U.S. defense contractors, the hackers used the text of job descriptions available on the legitimate company’s website.
“Unit 42 researchers at Palo Alto Networks have discovered new attack activity targeting individuals involved with United States defense contractors. Through analysis of malicious code, files, and infrastructure it is clear the group behind this campaign is either directly responsible for or has cooperated with the group which conducted Operation Blockbuster Sequeland, ultimately, Operation Blockbuster (originally outlined by researchers from Novetta).” reads the analysis published by PaloAlto networks.
The macros used in this last campaign presents many similarities with other cyber espionage attacks attributed to the Lazarus APT, experts also found many links between the nature of the decoy document used, the payloads and the command and control (C&C) servers.
“Recently, we’ve identified weaponized Microsoft Office Document files which use the same malicious macros as attacks from earlier this year. Based on the contents of these latest decoy documents which are displayed to a victim after opening the weaponized document the attackers have switched targets from Korean language speakers to English language speakers. Most notably, decoy document themes now include job role descriptions and internal policies from US defense contractors.” continues the analysis.
“This reuse of macro source code, XOR keys used within the macro to decode implant payloads, and the functional overlap in the payloads the macros write to disk demonstrates the continued use of this tool set by this threat group. The use of an automated tool to build the weaponized documents would explain the common but not consistent reuse of metadata, payloads, and XOR keys within the documents,”
The experts highlighted that the tools and tactics used by the group have changed only little compared to previous cyber espionage campaigns, they have no doubt about the fact that threat actors will continue their operations.
I suggest reading the analysis that also includes Indicators of Compromise.
Rapid7 warns of Remote Desktop Protocol (RDP) exposure for millions of endpoints
15.8.2017 securityaffairs Hacker techniques
According to a new research conducted by experts at Rapid7, there are 4.1 million Windows endpoints exposed online via Remote Desktop Protocol (RDP).
The researchers discovered that there are 11 million open 3389/TCP endpoints, and that 4.1 million of them are RDP.
“We analyzed the responses, tallying any that appeared to be from RDP speaking endpoints, counting both error messages indicating possible client or server-side configuration issues as well as success messages.” states the analysis from Rapid7.
“11 million open 3389/TCP endpoints, and 4.1 million responded in such a way that they were RDP speaking of some manner or another. This number is shockingly high when you remember that this protocol is effectively a way to expose keyboard, mouse and ultimately a Windows desktop over the network.”
In May, Rapid7 published another study that revealed millions of devices exposed to cyber attacks via SMB, Telnet, RDP, and other types of improper configurations.
The study reported 10.8 million supposedly open RDP endpoints in early 2016, and 7.2 million such endpoints in the first quarter of this year.
The researchers pointed out that even if RDP is disabled by default on Windows, it is commonly exposed in internal networks for administration and maintenance purposes. The protocol poses serious risks, Microsoft addressed dozens of vulnerabilities in the Remote Desktop Protocol over the past fifteen years.
“The default RDP configuration on older versions of Windows left it vulnerable to several attacks when enabled; however, newer versions have upped the game considerably by requiring Network Level Authentication (NLA) by default. If you are interested in reading more about securing RDP, UC Berkeley has put together a helpful guide, and Tom Sellers, prior to joining Rapid7, wrote about specific risks related to RDP and how to address them.”
“RDP’s history from a security perspective is varied. Since at least 2002 there have been 20 Microsoft security updates specifically related to RDP and at least 24 separate CVEs”
ShadowBrokers revealed the existence of an NSA exploit, dubbed EsteemAudit exploit that targets Remote Desktop Protocol service (port 3389) on machines running no longer supported Microsoft Windows Server 2003 / Windows XP.
It has been estimated that over 24,000 systems remain vulnerable to the EsteemAudit exploit, for this reason, Microsoft released security updates for Windows XP to address ShadowBrokers vulnerabilities, including CVE-2017-0176 exploited by EsteemAudit.
Remote Desktop Protocol attacks are a privileged attack vector for malware distribution, especially ransomware.
There are many malware in the wild that already infects systems using as attack vector the Remote Desktop Protocol, (CrySiS, Dharma, and SamSam), the EsteemAudit exploit can potentially make these threats very aggressive and dangerous.
According to the Rapid7 report, most of the exposed Remote Desktop Protocol endpoints (28.8%, or over 1.1 million) are in the United States. China is at the second place for exposed RDP endpoints (17.7%, or around 730,000), followed by Germany (4.3%, ~ 177,000), Brazil (3.3%, ~ 137,000), and Korea (3.0%, ~ 123,000).

Giving a look at the organizations that own the IP addresses associated with exposed Remote Desktop Protocol endpoints the experts noticed that most of them belong to Amazon (7.73% of exposed endpoints), Alibaba (6.8%), Microsoft (4.96%), China Telecom (4.32%), and Comcast (2.07%).
Rapid7 reported that more than 83% of the Remote Desktop Protocol endpoints identified were willing to proceed with CredSSP as the security protocol, meaning that the RDP session was highly secured. Over 15% of the exposed endpoints indicated that they didn’t support SSL/TLS.
“Amazingly, over 83% of the RDP endpoints we identified indicated that they were willing to proceed with CredSSP as the security protocol, implying that the endpoint is willing to use one of the most secure protocols to authenticate and protect the RDP session. A small handful in the few thousand range selected SSL/TLS. Just over 15% indicated that they didn’t support SSL/TLS (despite our also proposing CredSSP…) or that they only supported the legacy “Standard RDP Security”, which is susceptible to man-in-the-middle attacks. Over 80% of exposed endpoints supporting common means for securing RDP sessions is rather impressive. ” Rapid7 points out.
WannaCry hero Marcus Hutchins pleads not guilty
15.8.2017 securityaffairs Ransomware
The 23-year-old expert Marcus Hutchins pleaded “not guilty” during a court hearing in Milwaukee, Wisconsin. His trial has been scheduled for October.
Yesterday, Marcus Hutchins, the WannaCry hero, has pleaded not guilty to charges of creating and selling malware at a hearing in Milwaukee, Wisconsin.
The court decided to relax the expert bail terms, allowing him to access the Internet and continues his ordinary working activities. The only restrictions on Hutchins is that the expert cannot visit the Wannacry server domain.
12h
MalwareTech ✔ @MalwareTechBlog
There's a lot of people I'd like to thank for amazing support over the past 11 days, which I will do when i get a chance to publish my blog.
Follow
MalwareTech ✔@MalwareTechBlog
i'm still on trial, still not allowed to go home, still on house arrest; but now i am allowed online. Will get my computers back soon.
9:58 PM - Aug 14, 2017
131 131 Replies 440 440 Retweets 1,715 1,715 likes
Twitter Ads info and privacy
The decision is unusual because computer crime suspects are not allowed to stay online.
The court allowed him to live in Los Angeles, where the company that hired him is located, but he is obliged to surrender his passport and he must wear a tracking device until his trial in October.
“Marcus Hutchins is a brilliant young man and a hero,” said Marcia Hofmann, founder of Zeigeist Law. “He is going to vigorously defend himself against these charges and when the evidence comes to light we are confident that he will be fully vindicated.”
Marcus Hutchins, also known as MalwareTech, is a 22-year-old security expert who made the headlines after discovering the “kill switch” that halted the outbreak of the WannaCry ransomware. Marcus Hutchins has been arrested in in Las Vegas after attending the Def Con hacking conference and was detained by the FBI in the state of Nevada.
The British security researcher was arrested on Thursday after being indicted on charges of creating the Kronos banking malware.
A second defendant whom identity was not revealed appears to be involved.
According to the investigators, Marcus Hutchins created the malware and shared it online, below the indictment issued by Eastern District of Wisconsin.
The prosecutors believe Hutchins created, shared, and masterminded the Kronos banking Trojan between July 2014 and July 2015.
“We are very pleased today that the court modified his terms to allow him to return to his important work,” said Hutchins lawyer Brian Klein, partner at Baker Marquart LLP.
North Korea-Linked Hackers Target U.S. Defense Contractors
14.8.2017 securityweek BigBrothers
The North Korea-linked cyber espionage group known as Lazarus is believed to be behind attacks targeting individuals involved with United States defense contractors, Palo Alto Networks reported on Monday.
The threat actor, which has been active since at least 2009, is said to be responsible for several high-profile attacks, including the 2014 attack targeting Sony Pictures. Links have also been found to the recent WannaCry ransomware attacks.
The Lazarus group, tracked by the U.S. government as Hidden Cobra and known by security firms for its Operation Blockbuster, Dark Seoul and Operation Troy campaigns, continues to be active. Recent attacks observed by Palo Alto Networks against U.S. defense contractors appear to have been launched either by this group directly or in cooperation with other cyberspies.
According to researchers, the hackers have sent out spear phishing emails containing weaponized Microsoft Office documents written in English that use macros to deliver a piece of malware.
Specifically, Palo Alto has seen decoy documents describing job openings at some U.S. defense contractors. The text in these documents appears to be an exact copy, including typos, of job descriptions available on the legitimate company’s website.
There are several links between these attacks and other recent campaigns, including very similar macros, decoy document details, command and control (C&C) servers, and payloads.
“This reuse of macro source code, XOR keys used within the macro to decode implant payloads, and the functional overlap in the payloads the macros write to disk demonstrates the continued use of this tool set by this threat group. The use of an automated tool to build the weaponized documents would explain the common but not consistent reuse of metadata, payloads, and XOR keys within the documents,” researchers explained.
Palo Alto Networks pointed out that the tools and tactics used by the group have changed only little compared to previous campaigns, despite the numerous reports describing its activities. This has led experts to believe that the Lazarus group will continue to launch targeted attacks.
While the gang has been tied to several espionage and destruction campaigns, many of its recent attacks appear to have focused on financial institutions, including Bangladesh’s central bank and banks in Poland.
Password Flaws Patched in PostgreSQL
14.8.2017 securityweek Vulnerebility
Security updates released last week by the developers of the open source object-relational database management system PostgreSQL address three vulnerabilities and more than 50 bugs reported in the last three months.
PostgreSQL, currently the fourth most popular database system, is affected by a vulnerability related to some authentication methods accepting empty passwords. Developers fixed the problem by disallowing empty passwords for all authentication methods.
“libpq, and by extension any connection driver that utilizes libpq, ignores empty passwords and does not transmit them to the server. When using libpq or a libpq-based connection driver to perform password-based authentication methods, it would appear that setting an empty password would be the equivalent of disabling password login. However, using a non-libpq based connection driver could allow a client with an empty password to log in,” PostgreSQL explained.
The flaw, tracked as CVE-2017-7546, is considered the most serious of the issues patched with the latest security updates, with a class “A” rating, which indicates that it can be exploited for privilege escalation without requiring prior login.
Another password-related issue is CVE-2017-7547, which could result in passwords being leaked to unauthorized users. This is the second attempt at patching this flaw, initially tracked as CVE-2017-7486.
PostgreSQL developers pointed out that applying the patch will only address the problem in new databases; a series of steps need to be taken to resolve the problem in existing databases.
The third vulnerability, tracked as CVE-2017-7548, can be exploited by any user to change data in a large object. The weakness exists due to the lack of a permission check associated with the lo_put() function, which should require the same permissions as lowrite().
Tom Lane, Michael Paquier, Heikki Linnakangas and Noah Misch have been credited for finding these vulnerabilities.
PostgreSQL users have been advised to update their installations as soon as possible to versions 9.6.4, 9.5.8, 9.4.13, 9.3.18 and 9.2.22. Users have been warned that version 9.2 will reach end-of-life in September 2017 and it will likely receive only one more update.
Dubious Report Highlights Known Risks of Cloud-Based Multiscanners
14.8.2017 securityweek Security
Over the past week, a debate has spurred over a report from security services firm DirectDefense, claiming that Carbon Black’s endpoint detection and response (EDR) solution, Cb Response, is a prolific data leaker and exposes client data.
DirectDefense claims that the issues is related to the product’s ability to automatically upload binaries to a cloud-based multiscanner (namely, Google-owned VirusTotal) to better assess whether they are malicious or not. Specifically, the company says that it was able to pinpoint files uploaded to the multiscanner using the API key associated with Cb Response.
DirectDefense claimed that this setup creates, “the world’s largest pay-for-play data exfiltration botnet,” because clients of the multiscanner can access any of the uploaded files, regardless of where they came from. Further, because Cb Response associates its API key to the uploaded files, one would be able to learn information on Carbon Black enterprise customers based on these files alone.
“When a new file appears on a protected endpoint, a cryptographic hash is calculated. This hash is then used to look the file up in Carbon Black’s cloud. If Carbon Black has a score for this file, it gives the existing score, but if no entry exists, it requests an upload of the file. Since Carbon Black doesn’t know if this previously unseen file is good or bad, it then sends the file to a secondary cloud-based multiscanner for scoring. This means that all new files are uploaded to Carbon Black at least once,” DirectDefense explains.
The explanation is accurate, but only up to a specific point: it doesn’t mention that customers have control over the option to upload binaries to VirusTotal, and that the feature is turned off by default. The report also fails to point out that Carbon Black actually warns customers of the risks involved in enabling the option to share files with VirusTotal, which is an external source.
“By electing to enable the ‘Scan unknown binaries with VirusTotal’ feature, your server will send unknown binaries to Carbon Black with your consent. By electing to enable the ‘Share binary hashes with VirusTotal’ feature, your server will send binary hashes and other metadata to Carbon Black with your consent. Each binary and/or hash and file metadata, as the case may be, will be submitted to VirusTotal and governed solely by the Terms of Service and Privacy Policy of VirusTotal. Carbon Black shall not be responsible for this submission or for any act or omission by VirusTotal,” the warning reads.
Carbon Black, which has already issued a response to the report, points out that the so-called “data leak” vulnerability – which DirectDefense says “is nearly impossible to stop […] with the architecture [Carbon Black] devised – is in fact a feature that only Cb Response customers benefit from. The company also notes that, not only is the option off by default, but it also includes “many options to ensure privacy, and a detailed warning before enabling.”
DirectDefense also claims to have downloaded some of the files supposedly uploaded by Cb Response, and that their analysis led to identifying data pertaining to specific companies, including a streaming company (AWS IAM credentials, Slack API keys, Google Play keys, Apple Store ID), a social media company (hardcoded AWS and Azure keys, along with internal proprietary information, such as usernames and passwords), and a financial services company (shared AWS keys that granted access to customer financial data, trade secrets).
While the report alleges that Carbon Black’s product is the data leaker, the actual issue resides with VirusTotal, which provides access to the analyzed files to those willing to pay. There are numerous other security products that upload files to VirusTotal, and DirectDefense also notes that this might be the case, and even points out that the cloud-based multiscanner is spreading these files further.
“Cloud-based multiscanners operate as for-profit businesses. They survive by charging for access to advanced tools sold to malware analysts, governments, corporate security teams, security companies, and basically whomever is willing to pay. Access to these tools includes access to the files submitted to the multiscanner corpus,” DirectDefense notes.
Some experts following the story have taken a similar route, denouncing the report for inaccurately presenting Carbon Black’s product as being at fault. Some even called the report down right biased, based on DirectDefense’s association with Cylance, a competitor of Carbon Black. Recently named Solutions Partner of the Year by Cylance and using hyperbole-based comments in their report, DirectDefense can be easily accused of intentional smearing.
Security expert Adrian Sanabria, co-founder of Savage Security, calls the report “bullshit” and DirectDefense “opens itself up to criticism and closer scrutiny” by picking on Carbon Black. The reason, he says, is that “dozens of other security vendors either have an option to automatically submit binaries (yes, whole binaries, not just the hash) to VirusTotal or do it without the customers’ knowledge altogether.”
Martin Zinaich, information security officer for the City of Tampa, also points out that the report is biased and that DirectDefense had a hidden agenda when writing it: “DirectDefense poorly executed their discovery disclosure and no doubt did so purposefully. Thereby continuing the role of valued solutions partner.”
However, he also notes that many security professionals would turn to sharing information with VirusTotal without a second thought: “Neither the use of VirusTotal nor the [Carbon Black] disclaimer would make even the most hypersensitive InfoSec professional contemplate data leaking to other users of said service. Moreover, it would hardly cross the mind of a typical endpoint administrator.”
“How many other vendors are leveraging a multiscanner with API access? DirectDefense’s clumsy disclosure should not take away from what they did in fact discover,” Zinaich points out.
In a post denouncing the manner in which some news outlets were quick to report on DirectDefense’s story without waiting for Carbon Black’s response, investigative journalist Brian Krebs too points out that the real issue is the use of VirusTotal within corporate networks without fully understanding what it involves.
“If DirectDefense’s report helped some security people better grasp the risks of oversharing with multiscanners like VirusTotal, that’s a plus,” Krebs notes. However, he also says that “overblown research reports” such as this one should not be taken for granted, especially if the company that discovered the so-called issue didn’t even bother to contact the affected vendor before going public.
So, is the automatic (or manual) upload of files to VirusTotal bad practice? Yes and no. It is both a feature and a risk, depending on how it is used and on how well security teams and admins understand what it involves. On the one hand, sending a file to a multiscanner clearly brings a great deal of benefits by increasing the chances of discovering malicious intent. On the other hand, however, if used irresponsibly, this option could result in data leaks, potentially doing more harm than good. Thus, fully understanding the risks associated with the practice should help companies improve their security stance.
Millions of Endpoints Exposed via RDP: Report
14.8.2017 securityweek Hacker techniques
There are 4.1 million Windows endpoints online that would accept communication via the Remote Desktop Protocol (RDP) in one way or another, a recent Rapid7 report reveals.
As part of a study focused on the overall RDP exposure of Windows endpoints, the security firm discovered that there are 11 million open 3389/TCP endpoints, and that 4.1 million of them are “RDP speaking of some manner or another.”
The research follows previous reports from the company, which revealed 10.8 million supposedly open RDP endpoints in early 2016, and 7.2 million such endpoints in the first quarter of this year. According to Rapid7, however, the actual risk doesn’t come from exposing the endpoint, but from exposing the protocol.
While RDP is disabled by default on Windows, it is commonly exposed in internal networks to enable easy access for administration and support. From a security perspective, however, the protocol poses great many risks, especially with Microsoft addressing two dozen vulnerabilities in it over the past fifteen years.
“The default RDP configuration on older versions of Windows left it vulnerable to several attacks when enabled; however, newer versions have upped the game considerably by requiring Network Level Authentication (NLA) by default,” Rapid7 notes.
Earlier this year, the EsteemAudit exploit that the ShadowBrokers made public after supposedly stealing it from the National Security Agency-related Equation Group was targeting RDP on Windows 2003 and XP systems. Microsoft released security updates for Windows XP to address ShadowBrokers vulnerabilities, including CVE-2017-0176, the bug EsteemAudit was exploiting.
In March this year, a security report revealed that RDP had surpassed email for ransomware distribution. After RDP was associated with the delivery of various ransomware variants, researchers concluded that attackers were increasingly relying on brute-forcing RDP credentials for the deployment of this type of malware.
“RDP finds itself exposed on the public internet more often than you might think. Depending on how RDP is configured, exposing it on the public internet ranges from suicidal on the weak end to not-too-unreasonable on the other. […] There are all manner of ways that RDP could end up exposed on the public internet, deliberately or otherwise,” Rapid7 notes.
According to their report, most of the exposed RDP endpoints (28.8%, or over 1.1 million) are located in the United States. China has a great deal of exposed RDP endpoints as well (17.7%, or around 730,000), followed by Germany (4.3%, ~ 177,000), Brazil (3.3%, ~ 137,000), and Korea (3.0%, ~ 123,000).
The security researchers also had a look at the organizations that own the IPs with exposed RDP endpoints: Amazon (7.73% of exposed endpoints), Alibaba (6.8%), Microsoft (4.96%), China Telecom (4.32%), and Comcast (2.07%).
This also revealed why some countries had significantly more exposed endpoints than others: most of the providers are known for their cloud, virtual, or physical hosting services, “where remote access to a Windows machine is a frequent necessity,” Rapid7 notes.
The security researchers also discovered that over 83% of the RDP endpoints identified were willing to proceed with CredSSP as the security protocol, meaning that the RDP session was highly secured. However, while some selected SSL/TLS, over 15% of the exposed endpoints indicated that they didn’t support SSL/TLS.
“While 83% of the RDP speaking endpoints support CredSSP, this does not mean that they don’t also support less secure options; it just means that if a client is willing, they can take the more secure route,” Rapid7 points out. However, the company also underlines that it’s highly impressive that over 80% of exposed endpoints include support for common means for securing RDP sessions.
HBO Offered Hackers $250,000 As Ransom to Prevent More Leaks
14.8.2017 thehackernews Ransomware
Hackers who recently hacked into HBO network and stole scripts, shows, and employee information documents, have now provided an email in which the United States cable channel offered them $250,000.
The company offered the payment as a "bounty payment" reward in which companies reward white-hat hackers for discovering cyber security vulnerabilities in their computer networks.
Late last month, the HBO hackers claimed to have obtained around 1.5 terabytes of information from HBO and dropped upcoming episodes of "Ballers" and "Room 104," and a script of the fourth episode of "Game of Thrones."
A week after that, the hackers released another half-gigabyte sample of its stolen HBO data, including company's emails, employment agreements, and financial balance sheets, along with the script of the upcoming episode of Game of Thrones, demanding a ransom—nearly $6 Million in Bitcoins.
Now, according to a screenshot of an email obtained by Variety, an HBO executive wrote that the company had not been able to acquire the amount of Bitcoin the hackers had demanded and requested them to extend the ransom payment deadline by one week.
"You have the advantage of having surprised us. In the spirit of professional cooperation, we are asking you to extend your deadline for one week," the HBO executive reportedly writes in the email.
"As a show of good faith on our side, we are willing to commit to making a bug bounty payment of $250,000 to you as soon as we can establish the necessary account and acquire Bitcoin, or we can wire the funds as soon as you give us the account information."
Since the offered amount is just 3 to 4 percent of what the hackers demanded, the proposal apparently failed to satisfy the greed of hackers, and they have threatened to release more files from its 1.5 terabytes of stolen data every Sunday until the ransom is paid.
Although HBO did not yet respond to the recently leaked email, a person familiar with HBO's response to the hack told Reuters that the company sent that email "as a stall tactic" and had never intended to make the $250,000 or the full $6 Million payment to the hackers.
The company previously said it was working with forensic experts and law enforcement.
"The review to date has not given us a reason to believe that our email system as a whole has been compromised. We continue to work around the clock with outside cyber security firms and law enforcement to resolve the incident," HBO spokesperson Jeff Cusson said.
If hackers have held on 1.5 terabytes of HBO data and the company refuses to pay the ransom, you should expect more leaks of upcoming episodes from your favourite shows.
Two days ago, the HBO hackers also released some of the stolen data from the company, including the home addresses and phone numbers belonging to some of the Game of Thrones show's stars.
At this moment, it is still unclear who is behind the hack. We will keep you updated with the latest information.
IPS as a Service Blocks WannaCry Spread Across the WAN
14.8.2017 thehackernews Ransomware
One of the most devastating aspects of the recent WannaCry ransomware attack was its self-propagating capability exploiting a vulnerability in the file access protocol, SMB v1.
Most enterprises defences are externally-facing, focused on stopping incoming email and web attacks. But, once attackers gain a foothold inside the network through malware, there are very few security controls that would prevent the spread of the attack between enterprise locations in the Wide Area Network (WAN).
This is partly due to the way enterprises deploy security tools, such as IPS appliances, and the effort needed to maintain those tools across multiple locations.
It’s for those reasons Cato Networks recently introduced a context-aware Intrusion Prevention System (IPS) as part of its secure SD-WAN service. There are several highlights in this announcement that challenge the basic concept of how IT security maintains an IPS device and sustains the effectiveness of its protection.
Cato Networks is a cloud-based, SD-WAN service provider that uniquely integrates network security into its SD-WAN offering.
The Cato IPS is fully converged with Cato’s other security services, which include next generation firewall (NGFW), secure web gateway (SWG), URL filtering, and malware protection.
With the IPS roll out, Cato continues its march towards providing secure networking everywhere while simplifying the overall IT stack for the enterprise.
Cato Networks IPS as a Service
With IPS as a service, Cato takes care of the work previously spent managing and maintaining the IPS appliances including sizing, capacity planning, patching, and signature management.
These are a complex task because IPS appliance performance is impacted by the mix of encrypted and unencrypted traffic and the number of active attack signatures.
Normally, IT professionals must spend time carefully calculating the effectiveness of a signature and its performance impact to avoid slowing-down traffic due to IPS appliance overload.
Cato addresses both issues. The Cato IPS leverages its elastic cloud platform to inspect any mix of encrypted and unencrypted traffic in real-time.
The decision of which signatures to deploy is made by the experts of Cato Research Labs. They consider the relevancy of the threat and the best way to describe it to the system. Often, an existing signature may already cover a specific attack vector.
New Kind of Signatures With Context-Aware Protection
The Cato IPS has another unique capability. Because it operates in the same software stack as all other network and security services and within a cloud network, it can access a rich set of context attributes.
This forms a foundation for very sophisticated signatures that are hard to compose with stand-alone IPS devices. The use of rich context makes Cato IPS signatures more accurate and more effective.
Context attributes include the application being accessed and the client being used to access it, user identity, geolocation, IP and domain reputation, the file type exchanged, and DNS activity associated with the session.
Cato shared on its blog how Cato IPS stopped the spread of the Wannacry ransomware across sites, and how Cato IPS detected command-and-control communication at one of its customer locations.
Interestingly, the IPS can extend its protection across sites and users without the need to deploy distributed appliances, another benefit of the system.
If you are a distributed enterprise and constraint by your ability to support a complex networking and security environment, Cato’s approach can improve your security posture while keeping overhead to a minimum.
Disclosure: This is a sponsored post from Cato Networks, and it is really coming at a great time because we were just thinking to share with you about how to prevent Wannacry like attacks from spreading across the enterprise networks.
OpDomesticTerrorism – Anonymous takes down Charlottesville website after the incident
14.8.2017 securityaffairs Crime
Anonymous launched the OpDomesticTerrorism and claimed responsibility for carrying out a DDoS attack on the website of Charlottesville city Virginia.
The hacktivist collective Anonymous launched the OpDomesticTerrorism and claimed responsibility for carrying out a DDoS attack on the official website of Charlottesville city Virginia. The website went offline under the prolonged attack that was powered in the wake of the incident in which many protestors were hit while protesting the rally organized by a group of white supremacists.
A car rammed into a crowd, killing one person and injuring over a dozen others. The police arrested the 20-year-old James Alex Fields Jr. of Ohio.
![The hacktivist collective Anonymous launched the OpDomesticTerrorism and claimed responsibility for carrying out a DDoS attack on the official website of Charlottesville city Virginia. The website went offline under the prolonged attack that was powered in the wake of the incident in which many protesters were hit while protesting against the rally organized by a group of white supremacists. Image Credit: DailyProgress The video of the incident was recorded by Brennan Gilmore who tweeted that “Video of car hitting anti-racist protestors. Let there be no confusion: this was deliberate terrorism. My prayers with victims. Stay home.” Follow Brennan Gilmore @brennanmgilmore Video of car hitting anti-racist protestors. Let there be no confusion: this was deliberate terrorism. My prayers with victims. Stay home. 8:13 PM - Aug 12, 2017 3,8933,893 Replies 86,24186,241 Retweets 94,26394,263 likes Twitter Ads info and privacy The DailyProgress reported that mayor of the city Mike Signer has confirmed that one person has died in the incident after a car plowed into a mass of Unite the Right counter-protesters. Soon after the deadly incident, Anonymous hacktivist conducted a series of DDoS attacks on the Charlottesville city website and successfully took it offline. Follow Anonymous @YourAnonGlobal TangoDown http://charlottesville.org #offline #OpDomesticTerrorism#DefendCville pic.twitter.com/rSriOHONnY 9:23 PM - Aug 12, 2017 44 Replies 4545 Retweets 5555 likes Twitter Ads info and privacy View image on Twitter Follow ÐΓξ∀MξΓ8F↑νξ @dreamer8five TangoDown http://charlottesville.org #offline #OpDomesticTerrorism#DefendCville 10:08 PM - Aug 12, 2017 11 Reply 22 Retweets 55 likes Twitter Ads info and privacy Here are a few screenshots showing the site is down. Isitdownrightnow, a platform that keeps an eye on the sites suffering cyber attack or outage has also confirmed that the site is down. At the time of publishing this article, the targeted website was down. However, for some users, the home page was loading at a slow speed. UPDATE / 5:04 PM, SUNDAY, AUGUST 13, 2017 GREENWICH MEAN TIME (GMT) In a detailed conversation with a prominent Anonymous Twitter handle @YourAnonGlobal, HackRead.com was told that the attack on Charlottesville city website was carried out by New World Hackers (NWH), a counterpart of Anonymous hacktivist group. Explaining their manifesto on this attack; @YourAnonGlobal stated that: “Our strategy relies on the unity of these direct actions (DDOS), as the ballot box is no defense against fascism and hatred, nor are the political parties in power now. We are seeing that victories we have won through hard struggle could very well be reversed. Our only chance is to build a movement that relies on the power of the people.” Remember, NWH is the same group known for their massive DDoS attacks on HSBC (Hongkong and Shanghai Banking Corporation UK). The attack was acknowledged by the bank confirming that it affected their servers on one of the most important days that is the payday. NWH on the other hand also confirmed to HackRead.com that they are the one behind the attack on Charlottesville city website. One of the NWH’s members told us that: “At the time we saw the police were not so helpful, they left the people to die which forced us to targeted the Charlottesville website to give them a message.” […] “New World Hackers are back, and we are delivering our own version of justice to the KKK, and government, in which ever way we please.” View image on Twitter Follow New World Hackers @nwhownz @YourAnonNews http://oathkeepers.org #offline #DefendCville#OpDomesticTerrorism 9:48 PM - Aug 12, 2017 55 Replies 5454 Retweets 9494 likes Twitter Ads info and privacy At the same time, YourAnonNews, one of the most prominent Anonymous Twitter handle has also Retweeted about the attack. Follow Anonymous @YourAnonNews Fuck Terrorists. The police did not protect it's citizens.https://twitter.com/YourAnonGlobal/status/896452052301352961 … 9:28 PM - Aug 12, 2017 88 Replies 107107 Retweets 255255 likes](https://i1.wp.com/securityaffairs.co/wordpress/wp-content/uploads/2017/08/Charlottesville-incident.jpg?resize=900%2C500)
The hacktivist collective Anonymous launched the OpDomesticTerrorism and claimed responsibility for carrying out a DDoS attack on the official website of Charlottesville city Virginia. The website went offline under the prolonged attack that was powered in the wake of the incident in which many protesters were hit while protesting against the rally organized by a group of white supremacists. Image Credit: DailyProgress The video of the incident was recorded by Brennan Gilmore who tweeted that “Video of car hitting anti-racist protestors. Let there be no confusion: this was deliberate terrorism. My prayers with victims. Stay home.” Follow Brennan Gilmore @brennanmgilmore Video of car hitting anti-racist protestors. Let there be no confusion: this was deliberate terrorism. My prayers with victims. Stay home. 8:13 PM - Aug 12, 2017 3,8933,893 Replies 86,24186,241 Retweets 94,26394,263 likes Twitter Ads info and privacy The DailyProgress reported that mayor of the city Mike Signer has confirmed that one person has died in the incident after a car plowed into a mass of Unite the Right counter-protesters. Soon after the deadly incident, Anonymous hacktivist conducted a series of DDoS attacks on the Charlottesville city website and successfully took it offline. Follow Anonymous @YourAnonGlobal TangoDown http://charlottesville.org #offline #OpDomesticTerrorism#DefendCville pic.twitter.com/rSriOHONnY 9:23 PM - Aug 12, 2017 44 Replies 4545 Retweets 5555 likes Twitter Ads info and privacy View image on Twitter Follow ÐΓξ∀MξΓ8F↑νξ @dreamer8five TangoDown http://charlottesville.org #offline #OpDomesticTerrorism#DefendCville 10:08 PM - Aug 12, 2017 11 Reply 22 Retweets 55 likes Twitter Ads info and privacy Here are a few screenshots showing the site is down. Isitdownrightnow, a platform that keeps an eye on the sites suffering cyber attack or outage has also confirmed that the site is down. At the time of publishing this article, the targeted website was down. However, for some users, the home page was loading at a slow speed. UPDATE / 5:04 PM, SUNDAY, AUGUST 13, 2017 GREENWICH MEAN TIME (GMT) In a detailed conversation with a prominent Anonymous Twitter handle @YourAnonGlobal, HackRead.com was told that the attack on Charlottesville city website was carried out by New World Hackers (NWH), a counterpart of Anonymous hacktivist group. Explaining their manifesto on this attack; @YourAnonGlobal stated that: “Our strategy relies on the unity of these direct actions (DDOS), as the ballot box is no defense against fascism and hatred, nor are the political parties in power now. We are seeing that victories we have won through hard struggle could very well be reversed. Our only chance is to build a movement that relies on the power of the people.” Remember, NWH is the same group known for their massive DDoS attacks on HSBC (Hongkong and Shanghai Banking Corporation UK). The attack was acknowledged by the bank confirming that it affected their servers on one of the most important days that is the payday. NWH on the other hand also confirmed to HackRead.com that they are the one behind the attack on Charlottesville city website. One of the NWH’s members told us that: “At the time we saw the police were not so helpful, they left the people to die which forced us to targeted the Charlottesville website to give them a message.” […] “New World Hackers are back, and we are delivering our own version of justice to the KKK, and government, in which ever way we please.” View image on Twitter Follow New World Hackers @nwhownz @YourAnonNews http://oathkeepers.org #offline #DefendCville#OpDomesticTerrorism 9:48 PM - Aug 12, 2017 55 Replies 5454 Retweets 9494 likes Twitter Ads info and privacy At the same time, YourAnonNews, one of the most prominent Anonymous Twitter handle has also Retweeted about the attack. Follow Anonymous @YourAnonNews Fuck Terrorists. The police did not protect it's citizens.https://twitter.com/YourAnonGlobal/status/896452052301352961 … 9:28 PM - Aug 12, 2017 88 Replies 107107 Retweets 255255 likes
Source: RT.com
Immediately after the incident, members of the activist group Anonymous launched a series of DDoS attacks on the Charlottesville city website.

Follow
Anonymous @YourAnonGlobal
TangoDown http://charlottesville.org #offline #OpDomesticTerrorism #DefendCville
9:23 PM - Aug 12, 2017
4 4 Replies 52 52 Retweets 65 65 likes
Twitter Ads info and privacy
At the time I was writing the site charlottesville.org is still down.
According to HackRead who received a comment from an Anonymous member that operates the Twitter account @YourAnonGlobal, the attack was carried out by New World Hackers (NWH).
The NWH confirmed to HackRead.com that they are the one behind the attack on Charlottesville city website.
“At the time we saw the police were not so helpful, they left the people to die which forced us to targeted the Charlottesville website to give them a message.” said one of the NWH’s members.
“New World Hackers are back, and we are delivering our own version of justice to the KKK, and government, in which ever way we please.”
The message spread by @YourAnonGlobal about the attack states:
“Our strategy relies on the unity of these direct actions (DDOS), as the ballot box is no defense against fascism and hatred, nor are the political parties in power now. We are seeing that victories we have won through hard struggle could very well be reversed. Our only chance is to build a movement that relies on the power of the people.”
New World Hackers @nwhownz
@YourAnonNews http://oathkeepers.org #offline #DefendCville #OpDomesticTerrorism
9:48 PM - Aug 12, 2017
5 5 Replies 56 56 Retweets 98 98 likes
Twitter Ads info and privacy
Anonymous is back, stay tuned!
Kenya opposition claims election results manipulated in cyber attack
14.8.2017 securityaffairs Cyber
Kenya opposition claims hackers have manipulated the results of the recent election by breaking into the database of Kenya’s electoral commission.
According to Kenya opposition, led by Raila Odinga, hackers have manipulated the results of the recent election by breaking into the database of Kenya’s electoral commission.
The President Uhuru Kenyatta was re-elected and èrotests and violence broke out almost immediately.
“At least 24 people, including a 9-year-old girl, have been killed in Kenya in the violence that erupted after the re-election of President Uhuru Kenyatta, according to the Kenya National Commission on Human Rights.” reported the CNN.
“Specifically, these cases indicate that the casualties were felled by bullets and the same has been corroborated by family and community members who have indicated that they were killed during the protests which broke out in various parts of the country,” the independent rights group said in a statement. Of those death, 17 were killed in the capital Nairobi, the group said.
Raila Odinga claims hackers have used the credential of a murdered employee of the electoral commission (IEBC), Chris Msando, to hack into an electronic voting system and manipulate the votes.
Msando was a top IT official at the IEBC that was tortured and killed in late July.
The politician supported his accusation by releasing an alleged log from an IEBC server that confirms it was altered to increase Kenyatta’s totals by 11 percent and hide the manipulation.
“These results are fake, it is a sham. They cannot be credible,” Odinga told journalists.
“This is an attack on our democracy. The 2017 general election was a fraud.”
He later released what he claimed was a log from an IEBC server to support his allegations that the server was configured to increase Kenyatta’s totals by 11 percent and cover up the modifications.
At the time I was writing the log was not yet verified by any independent researcher.
The electoral commission (IEBC) results showed Kenyatta obtaining 54.4 percent of the nearly 13 million ballots tallied, against Odinga’s 44.7 percent.
Odinga refused the result of the election and claims Kenyatta’s skullduggery, according to the politicians the hackers manipulated the results for both the presidential and the general election.
“The electoral fraud and fabrication of results was massive,” Odinga said. “It has always been common knowledge that Uhuru Kenyatta’s regime was a fraud. This takes Mr Kenyatta and [deputy president] William Ruto’s fraud … to another level.”
Odinga did not reveal the source of his information to protect it.
Odinga is inviting his supporters to “remain calm as we look deep into this matter,”
Anti-Israel and pro-Palestinian IsraBye wiper spreads as a ransomware
14.8.2017 securityaffairs Ransomware
Malware researchers discovered an anti-Israel & pro-Palestinian data wiper dubbed IsraBye that is spreading as a ransomware.
Malware researcher Jakub Kroustek from Avast has recently discovered an anti-Israel & pro-Palestinian data wiper dubbed IsraBye. Even if the lock screen claims that the files can be recovered, their content is replaced with an anti-Israel message. 
Jakub Kroustek @JakubKroustek
This is Ahmed. Ahmed likes .NET. Ahmed hates #Israel. Ahmed created a #wiper. Ahmed, now GTFO. #MalwareWithSounds https://www.virustotal.com/en/file/5a209e40e0659b40d3d20899c00757fa33dc00ddcac38a3c8df004ab9051de0d/analysis/ …
10:45 PM - Jul 29, 2017
9 9 Replies 59 59 Retweets 88 88 likes
Twitter Ads info and privacy
The anti-Israel wiper was discovered concurrently the Al Aqsa crisis triggered by the decision of Israeli authorities to install metal detectors and other measures at the Al Aqsa mosque in Jerusalem. The measures were refused by Palestinians.
Researchers at Bleepingcomputer have published an interesting video on the IsraBye:
The wiper has a modular architecture composed of 5 different executables. The first executable is the launcher and wiper called IsraBye.exe. When executed IsraBye.exe silently begin to wipe all attached drives by replacing their contents with the following message:
Fuck-israel, [username] You Will never Recover your Files Until Israel disepeare
The wiper doesn’t encrypt the file, but destroy them and once completed the process, it extracts the files Cry.exe, Cur.exe, Lock.exe, and Index.exe from the IsraBye.exe executable and launches them.
The Cry.exe executable replaces the desktop’s wallpaper with an anti-Israel or pro-Palestinian image.

IsraBye wallpaper (Source Bleepingcomputer)
The Cur.exe attaches an image that included the message “End of Israel” to the mouse cursor.
The Lock.exe performs the following three functions:
it will look for the procexp64, ProcessHacker, taskmgr, procexp, xns5 processes in order to terminate them.
it will launch Index.exe if it is not already running.
it will copy the main Israbye.exe file to the root of other drives as a file called ClickMe.exe in order to spread the malware.
The researcher Ido Naor noticed that creating a file called ClickMe.exe in the %Temp% folder it is possible to make IsraBye crashes when first starting.

Ido Naor @IdoNaor1
#israhell #israbye Thought I'd put an empty "ClickMe.exe" and make it crash. Well it did, obviously. Kill switch is a new trend now?
1:35 PM - Aug 3, 2017
3 3 Replies 5 5 Retweets 5 5 likes
Twitter Ads info and privacy
The Index.exe executable displays the lock screen and extracts a wav file and play it.
MUGHTHESEC, a signed Mac adware that hijacks the victim’s browser for profit
14.8.2017 securityaffairs Apple
Experts spotted a new signed Mac adware dubbed MUGHTHESEC that hijacks victim’s browser for profit and can be removed only reinstalling the OS.
According to the expert Patrick Wardle, Director of Research at Synack, a new strain of Mac adware is threatening Mac users, once infected a machine the only way to remove it is to reinstall the macOS.
The researcher and Mac expert Thomas Reed, speculate the new family of Mac adware dubbed Mughthesec is an improved version of the well known OperatorMac family.
7 Aug
Gavriel State @gavrielstate
Replying to @patrickwardle @thomasareed
Hi Patrick - sent you a zip file in email. Yes, there was a launchagents plist in there, but I killed it before archiving.
Follow
Thomas Reed @thomasareed
Thanks, Patrick sent me the hash too. Looks like a new variant of something we call OperatorMac (though that may be a bad name).
2:30 AM - Aug 8, 2017
1 1 Reply Retweets likes
Twitter Ads info and privacy
Other malware experts claim the threat has been in the wild at least since six months, but the detection rate on VirusTotal is still low.
Follow
Objective-See @objective_see
Made it to blog post #32! 😍 Read: "WTF is Mughthesec!? Poking on a Piece of Undetected Adware" 👾☠️🍎 https://objective-see.com/blog/blog_0x20.html … #adware #malware
8:54 PM - Aug 8, 2017
1 1 Reply 35 35 Retweets 29 29 likes
Twitter Ads info and privacy
The Mac Malware has been improved across the months, new features were implemented such as an MAC-address-based anti-VM detection system and components of Mughthesec are signed with a legitimate Apple developer certificate allowing it to bypass the Gatekeeper protection that normally prevents the installation of unsigned applications.
“In a nutshell, I think the issue isn’t that anything here is incredible new or exciting; more that existing security/mitigation strategies are rather failing miserably,” Wardle explained. “So we’ve got Gatekeeper that’s designed to block unsigned code from the internet to prevent users from getting tricked into installing malware (e.g. fake flash updaters)….which is a great idea. But now most Mac adware/malware is just signed with certs. So gatekeeper is basically a moot point. Normal-everyday users are still going to go around infecting themselves…and things designed to protect them; Gatekeeper/AV etc, really don’t offer any help.”
The adware is currently delivered as a file called Player.dmg that installs a legitimate version of the Adobe Flash Player for Mac, but also an unwanted app named Advanced Mac Cleaner, and two Safari extensions named Safe Finder and Booking.com.
“The PUPs are in my opinion, rather shady. I mean they automatically install browser plugins circumventing Apple’s security mechanisms in Safari,” Wardle said. “So sure, they ask for user permission to be installed during install, but then do things that generally the user probably doesn’t want. It’s that gray area between legit code and malware.”

Patrick Wardle believes the malware is spread via malvertising campaigns or via malicious ads and popups on shady websites. “Either way, user-interaction is likely required [for both the download and installation],” says Wardle.
Patrick Wardle described the threat with the following statement from his post published on the Objective-See blog.
“What is Mughthesec?” The answer; likely a new variant of the ‘SafeFinder/OperatorMac’ adware. Yes it’s rather unsophisticated macOS malware, but it’s installer is signed (to ‘bypass’ Gatekeeper) and at the time of this analysis no anti-virus engines were detected it….and mac users are being infected 😐
Speaking of infection, due to the fact that the installer is masquerading as Flash Player installer, it’s likely that this adware is relying on common infection techniques to gain new victims. If I had to guess its infection vector is likely one (or all?) of the following:
fake popups on ‘shady’ websites
malicious ads, perhaps on legit websites.
Either way, user-interaction is likely required. “
The malware, once installed, hijacks the victim’s browser for profit.
“A common tactic of adware is to hijack the victim’s browser (homepage, inject ads, etc) for financial gain,” Wardle said. “Mughthesec (which is installed when the user ‘agrees’ to install ‘Safe Finder’) appears to conform to goal.”
“If we open Safari; indeed the home page has been hijacked–though in a seemingly innocuous way,” Wardle said, adding that he did not test the sample on Google’s Chrome browser. “It simply displays a rather ‘clean’ search page—though looking at the source, we can see the inclusion of several scripts ‘Safe Finder’ scripts.”
Wardle highlighted that other files dropped by the adware on infected hosts allow the malware operator to drop other malicious payloads.
The presence of the Mughthesec infection must alert Mac users that will never know if other malware has been installed by crooks along with the adware, and for this reason, they should reinstall their Mac.
The return of Mamba ransomware
13.8.2017 Kaspersky Ransomware
At the end of 2016, there was a major attack against San Francisco’s Municipal Transportation Agency. The attack was done using Mamba ransomware. This ransomware uses a legitimate utility called DiskCryptor for full disk encryption. This month, we noted that the group behind this ransomware has resumed their attacks against corporations.
Attack Geography
We are currently observing attacks against corporations that are located in:
Brazil
Saudi Arabia
Attack Vector
As usual, this group gains access to an organization’s network and uses the psexec utility to execute the ransomware. Also, it is important to mention that for each machine in the victim’s network, the threat executor generates a password for the DiskCryptor utility. This password is passed via command line arguments to the ransomware dropper.
Example of malware execution
Technical Analysis
In a nutshell, the malicious activity can be separated into two stages:
Stage 1 (Preparation):
Create folder “C:\xampp\http“
Drop DiskCryptor components into the folder
Install DiskCryptor driver
Register system service called DefragmentService
Reboot victim machine
Stage 2 (Encryption):
Setup bootloader to MBR and encrypt disk partitions using DiskCryptor software
Clean up
Reboot victim machine
Stage 1 (Preparation)
As the trojan uses the DiskCryptor utility, the first stage deals with installing this tool on a victim machine. The malicious dropper stores DiskCryptor’s modules in their own resources.
DiskCryptor modules
Depending on OS information, the malware is able to choose between 32- or 64-bit DiskCryptor modules. The necessary modules will be dropped into the “C:\xampp\http” folder.
The malware drops the necessary modules
After that, it launches the dropped DiskCryptor installer.
The call of the DiskCryptor installer
When DiskCryptor is installed, the malware creates a service that has SERVICE_ALL_ACCESS and SERVICE_AUTO_START parameters.
The creation of the malicious service’s function
The last step of Stage 1 is to reboot the system.
Force reboot function
Stage 2 (Encryption)
Using the DiskCryptor software, the malware sets up a new bootloader to MBR.
The call for setting up a bootloader to MBR
The bootloader contains the ransom message for the victim.
Ransomware note
After the bootloader is set, disk partitions would be encrypted using a password, previously specified as a command line argument for the dropper.
The call tree of encryption processes
When the encryption ends, the system will be rebooted, and a victim will see a ransom note on the screen.
Ransom notes
Kaspersky Lab products detect this threat with the help of the System Watcher component with the following verdict: PDM:Trojan.Win32.Generic.
Decryption
Unfortunately, there is no way to decrypt data that has been encrypted using the DiskCryptor utility because this legitimate utility uses strong encryption algorithms.
Steganography in contemporary cyberattacks
13.8.2017 Kaspersky Cyber
Steganography is the practice of sending data in a concealed format so the very fact of sending the data is disguised. The word steganography is a combination of the Greek words στεγανός (steganos), meaning “covered, concealed, or protected”, and γράφειν (graphein) meaning “writing”.
Unlike cryptography, which conceals the contents of a secret message, steganography conceals the very fact that a message is communicated. The concept of steganography was first introduced in 1499, but the idea itself has existed since ancient times. There are stories of a method being used in the Roman Empire whereby a slave chosen to convey a secret message had his scalp shaved clean and a message was tattooed onto the skin. When the messenger’s hair grew back, he was dispatched on his mission. The receiver shaved the messenger’s scalp again and read the message.
In this article, the following definitions are used:
Payload: the information to be concealed and sent secretly, or the data covertly communicated;
Carrier (stego-container): any object where the payload is secretly embedded;
Stego-system: the methods and means used to create a concealed channel for communicating information;
Channel: the data communication channel via which the carrier is transferred;
Key: the key used to extract the payload from the carrier (not always applied).
Steganography was actively developed throughout the 20th century, as was steganalysis, or the practice of determining the fact that concealed information is being communicated within a carrier. (Basically, steganalysis is the practice of attacking stego-systems.) Today, however, a dangerous new trend is emerging: steganography is increasingly being used by actors creating malware and cyber-espionage tools. Most modern anti-malware solutions provide little, if any, protection from steganography, while any carrier in which a payload can be secretly carried poses a potential threat. It may contain data being exfiltrated by spyware, communication between a malicious program and its C&C, or new malware.
A variety of steganographic methods and algorithms have been scientifically developed and tested. A description of some of them is provided below.
In LSB steganography, the payload is encoded into and communicated in one or several least significant bits of the carrier. The smaller the number of bits used to carry the payload, the lower the impact on the original carrier signal.
Discrete cosine transform or DCT-based steganography is a sub-type of LSB steganography that is often applied on JPEG-format carriers (i.e., when JPEG images are used to carry the payload). In this method, the communicated data is secretly encoded into the DCT coefficients. With all other factors being equal, this method provides a somewhat lower data carrying capacity; one of the reasons for this is that the coefficient values of 0 and 1 cannot be altered, so no data can be encoded whenever the coefficients take on these values.
Palette-based image steganography is basically another sub-type of LSB steganography, in which the communicated data is encoded into least significant bits of the image palette rather than into those of the carrier. The obvious downside to this method is its low data carrying capacity.
Use of service fields in data formats. This is a relatively simple method, in which the payload is embedded into the service fields of the carrier’s headers. The downsides are, again, a low data carrying capacity and low payload protection: the embedded payload may be detected using regular image viewing software that can sometimes display the contents of the service fields.
Payload embedding is a method whereby the payload is encoded into the carrier and, upon delivery, is decoded using an algorithm known to both parties. Several payloads can be independently encoded into the same carrier provided that their embedding methods are orthogonal.
Wideband methods fall into the following types:
Pseudorandom sequence method, in which a secret carrier signal is modulated by a pseudorandom signal.
Frequency hopping method, in which the frequency of the carrier signal changes according to a specific pseudorandom law.
Overlay method – strictly speaking, this is not proper steganography, and is based on the fact that some data formats contain data size in a header, or the fact that the handler of such formats reads the file till it reaches the end-of-data marker. An example is the well-known RAR/JPEG method based on concatenating an image file, so that it is composed of a JPEG format section, followed by a RAR archive section. A JPEG viewer software program will read it till the boundary specified in the file’s header, while a RAR archiver tool will disregard everything prior to the RAR! signature that denotes the beginning of an archive. Therefore, if such a file is opened in an image file viewer, it will display the image, and if it is opened in a RAR archiver, it will display the contents of the RAR archive. The downside to this method is that the overlay added to the carrier segment can be easily identified by an analyst visually reviewing the file.
In this article, we will only review methods of concealing information in image-type carriers and in network communication. The application of steganography is, however, much wider than these two areas.
Recently, we have seen steganography used in the following malware programs and cyberespionage tools:
Microcin (AKA six little monkeys);
NetTraveler;
Zberp;
Enfal (its new loader called Zero.T);
Shamoon;
KinS;
ZeusVM;
Triton (Fibbit).
So why are malware authors increasingly using steganography in their creations? We see three main reasons for this:
It helps them conceal not just the data itself but the fact that data is being uploaded and downloaded;
It helps bypass DPI systems, which is relevant for corporate systems;
Use of steganography may help bypass security checks by anti-APT products, as the latter cannot process all image files (corporate networks contain too many of them, and the analysis algorithms are rather expensive).
For the end user, detecting a payload within a carrier may be a non-trivial task. As an example, let’s review the two images below. One is an empty carrier, and the other is a carrier with a payload. We will use the standard test image Lenna.
Both images are 786 486 bytes; however, the right-hand image contains the first 10 chapters of Nabokov’s novel Lolita.
Take a good look at these two images. Can you see any difference? They are identical in both size and appearance. However, one of them is a carrier containing an embedded message.
The problems are obvious:
Steganography is now very popular with malware and spyware writers;
Anti-malware tools generally, and perimeter security tools specifically, can do very little with payload-filled carriers. Such carriers are very difficult to detect, as they look like regular image files (or other types of files);
All steganography detection programs today are essentially proof-of-concept, and their logic cannot be implemented in commercial security tools because they are slow, have fairly low detection rates, and sometimes even contain errors in the math (we have seen some instances where this was the case).
A list was provided above (though it does not claim to be complete) of malicious programs that use steganography to conceal their communication. Let’s review one specific case from that list, the malicious loader Zero.T.
We detected this loader in late 2016, though our colleagues from Proofpoint were first to publish a description.
We named it Zero.T because of this string in its executable code (in the path leading to the project’s PBD file):
We will not dwell here on how the malicious loader penetrates the victim system and remains there, but will note that it loads a payload in the form of Bitmap files:
Then it processes them in a particular way to obtain malicious modules:
On the face of it, these three BMP files appear to be images:
However, they are more than just regular images; they are payload-filled carriers. In each of them, several (the algorithm allows for variability) least significant bits are replaced by the payload.
So, is there a way to determine whether an image is carrying a malicious payload or not? Yes, there are several ways of doing so, the simplest being a visual attack. It is based on forming new images from the source image, containing the least significant bits of different color planes.
Let’s see how this works using the Steve Jobs photo as a sample image.
We apply a visual attack to this image and construct new images from the separate significant bits in the appropriate order:
In the second and the third images, high entropy (high data density) areas are apparent – these contain the embedded payload.
Sounds simple, right? Yes and no. It’s simple in that an analyst – and even an average user – can easily see the embedded data; it’s difficult in that this sort of analysis is not easy to automate. Fortunately, scientists have long since developed a number of methods for detecting carriers with payloads, based on an image’s statistical characteristics. However, all of them are based on the assumption that the encoded payload has high entropy. This is true in most cases: since the container’s capacity is limited, the payload is compressed and/or encrypted before encoding, thus increasing its entropy.
However, our real-life example, the malicious loader Zero.T, does not compress its malicious modules before encoding. Instead, it increases the number of least significant bits it uses, which can be 1, 2 or 4. Yes, using a larger number of least significant bits introduces visual artefacts into the carrier image, which a regular user can detect visually. But we are talking about automatic analysis. So, the question we have to answer is: are statistical methods suitable for detecting embedded payloads with low levels of entropy?
Statistical methods of analysis: histogram method
This method was suggested in 2000 by Andreas Westfeld and Andreas Pfitzmann, and is also known as the chi-squared method. Below we give a brief overview.
The entire image raster is analyzed. For each color, the number of dots possessing that color is counted within the raster. (For simplicity, we are dealing with an image with one color plane.) This method assumes that the number of pixels possessing two adjacent colors (i.e. colors different only by one least significant bit) differs substantially for a regular image that does not contain an embedded payload (see Figure A below). For a carrier image with a payload, the number of pixels possessing these colors is similar (see Figure B).
Figure A. An empty carrier Figure B. A filled carrier.
The above is an easy way to visually represent this algorithm.
Strictly speaking, the algorithm consists of the following steps that must be executed sequentially:
The expected occurrence frequency for the pixels of color i in a payload-embedded image is calculated as follows:
The measured frequency of the occurrence of a pixel of specific color is determined as:
The chi-squared criterion for k-1 degrees of freedom is calculated as:
P is the probability that the distributions ni and ni* are equal under these conditions. It is calculated by integrating the density function:
Naturally, we have tested whether this method is suitable for detecting filled stego-containers. Here are the results.
Original image Visual attack image Chi-squared attack, 10 zones
The threshold values of the chi-squared distribution for p=0.95 and p=0.99 are 101.9705929 and 92.88655838 respectively. Thus, for the zones where the calculated chi-squared values are lower than the threshold, we can accept the original hypothesis “adjacent colors have similar frequency distributions, therefore we are dealing with a carrier image with a payload”.
Indeed, if we look at the visual attack images, we can clearly see that these zones contain an embedded payload. Thus, this method works for high-entropy payloads.
Statistical methods of analysis: RS method
Another statistical method of detecting payload carriers was suggested by Jessica Fridrich, Miroslav Goljan and Andreas Pfitzmann in 2001. It is called the RS method, where RS stands for ‘regular/singular’.
The analyzed image is divided into a set of pixel groups. A special flipping procedure is then applied for each group. Based on the values of the discriminant function before and after the flipping procedure is applied, all groups are divided into regular, singular and unusable groups.
This algorithm is based on the assumption that the number of regular and singular pixel groups must be approximately equal in the original image and in the image after flipping is applied. If the numbers of these groups change appreciably after flipping is applied, this indicates that the analyzed image is a carrier with a payload.
The algorithm consists of the following steps:
The original image is divided into groups of n pixels (x1, …, xn).
The so-called discriminant function is defined which assigns to each group of pixels G = (x1, …, xn) a real number f(x1, …, xn) ∈
The discriminant function for the groups of pixels (x1, …, xn) can be defined as follows:
Then we define the flipping function which has the following properties:
Depending on the discriminant function’s values prior to and after flipping is applied, all groups of pixels are divided into regular, singular and unusable groups:
We have put this method to the test as well, and obtained the following results. We used the same empty and payload-embedded carriers as in the previous test.
Original image Visual attack image Chi-squared attack, 10 zones
Note that this attack method does not pass the binary verdict in terms of “whether this specific carrier contains an embedded payload or not”; rather, it determines the approximate length of the embedded payload (as a percentage).
As can be seen from the results above, this method returned a verdict for the empty message that it was filled less than 1% with payload, and for the payload-embedded carrier it returned a verdict that it was about 44% filled. Obviously, these results are slightly off. Let’s look at the filled container: from the visual attack it follows that more than 50% of the container is filled, while the RS attack tells us that 44% of the container is filled. Therefore, we can apply this method if we establish a certain “trigger threshold”: our experiments showed that 10% is a sufficient threshold of reliability. If the RS attack claims that more than 10% of the container is full, you can trust this verdict and mark the container as full.
Now it’s time to test these two methods in real-world conditions, on the Zero.T carriers in which the payload has regular entropy.
We ran the appropriate tests and here are the results:
Original image Chi-squared attack RS attack
As we see, a chi-squared attack is not applicable on low entropy images – it yields unsatisfactory or inaccurate results. However, the RS attack worked well: in both cases, it detected a hidden payload in the image. However, what do we do if automatic analysis methods show there is no payload, but we still suspect there might be one?
In that case, we can apply specific procedures that have been developed for specific malware families to extract the payload. For the aforementioned Zero.T loader, we have written our own embedded payload extraction tool. Its operation can be schematically presented as follows.
Obviously, if we get a valid result (in this specific case, an executable file), then the source image has an embedded payload in it.
Is DNS tunneling also steganography?
Can we consider use of a DNS tunnel a subtype of steganography? Yes, definitely. For starters, let’s recap on how a DNS tunnel works.
From a user computer in a closed network, a request is sent to resolve a domain, for example the domain wL8nd3DdINcGYAAj7Hh0H56a8nd3DdINcGYAlFDHBurWzMt[.]imbadguy[.]com to an IP address. (In this URL, the second-level domain name is not meaningful.) The local DNS server forwards this request to an external DNS server. The latter, in turn, does not know the third-level domain name, so it passes this request forward. Thus, this DNS request follows a chain of redirections from one DNS server to another, and reaches the DNS server of the domain imbadguy[.]com.
Instead of resolving a DNS request at the DNS server, threat actors can extract the information they require from the received domain name by decoding its first part. For example, information about the user’s system can be transmitted in this way. In response, a threat actor’s DNS server also sends some information in a decoded format, putting it into the third- or higher-level domain name.
This means the attacker has 255 characters in reserve for each DNS resolution, up to 63 characters for subdomains. 63 characters’ worth of data is sent in each DNS request, and 63 characters are sent back in response, and so on. This makes it a decent data communications channel! Most importantly, it is concealed communication, as an unaided eye cannot see that any extra data is being communicated.
To specialists who are familiar with network protocols and, in particular, with DNS tunneling, a traffic dump containing this sort of communication will look quite suspicious – it will contain too many long domains that get successfully resolved. In this specific case, we are looking at the real-life example of traffic generated by the Trojan Backdoor.Win32.Denis, which uses a DNS tunnel as a concealed channel to communicate with its C&C.
A DNS tunnel can be detected with the help of any popular intrusion detection (IDS) tool such as Snort, Suiricata or BRO IDS. This can be done using various methods. For example, one obvious idea is to use the fact that domain names sent for DNS resolution are much longer than usual during tunneling. There are quite a few variations on this theme on the Internet:
alert udp any any -> any 53 (msg:”Large DNS Query, possible cover channel”; content:”|01 00 00 01 00 00 00 00 00 00|”; depth:10; offset:2; dsize:>40; sid:1235467;)
There is also this rather primitive approach:
Alert udp $HOME_NET and -> any 53 (msg: “Large DNS Query”; dsize: >100; sid:1234567;)
There is plenty of room for experimenting here, trying to find a balance between the number of false positives and detecting instances of actual DNS tunneling.
Apart from suspiciously long domain names, what other factors may be useful? Well, anomalous syntax of domain names is another factor. All of us have some idea of what typical domain names look like – they usually contain letters and numbers. But if a domain name contains Base64 characters, it will look pretty suspicious, won’t it? If this sort of domain name is also quite long, then it is clearly worth a closer look.
Many more such anomalies can be described. Regular expressions are of great help in detecting them.
We would like to note that even such a basic approach to detecting DNS tunnels works very well. We applied several of these rules for intrusion detection to the stream of malware samples sent to Kaspersky Lab for analysis, and detected several new, previously unknown backdoors that used DNS tunnels as a covert channel for C&C communication.
Conclusions
We are seeing a strong upward trend in malware developers using steganography for different purposes, including for concealing C&C communication and for downloading malicious modules. This is an effective approach considering payload detection tools are probabilistic and expensive, meaning most security solutions cannot afford to process all the objects that may contain steganography payloads.
However, effective solutions do exist – they are based on combinations of different methods of analysis, prompt pre-detections, analysis of meta-data of the potential payload carrier, etc. Today, such solutions are implemented in Kaspersky Lab’s Anti-Targeted Attack solution (KATA). With KATA deployed, an information security officer can promptly find out about a possible targeted attack on the protected perimeter and/or the fact that data is being exfiltrated.
Peace Breaks Out Between Microsoft and Kaspersky Lab
12.8.2017 securityweek IT
Microsoft Agrees to Kaspersky Lab's Demands
Microsoft and Kaspersky are friends again, and the whole anti-virus ecosystem is at peace.
Back in November 2016, Eugene Kaspersky declared, "That's It. I've Had Enough!" It wasn't just words. "We've taken the decision to address official bodies in various countries (including the EU and Russia) with a request to oblige Microsoft to cease its violation of anti-competition legislation and to remove the consequences of that violation." And he did just that, first in Russia and then in the EU.
Eugene Kaspersky, founder of Russia-based Kaspersky Lab, was not alone in his concerns. "Some time ago security companies started noticing that things were changing at Microsoft," Luis Corrons, technical director at PandaLabs told SecurityWeek. "It looked like they were more concerned about their own antivirus market share, and were trying to push the competition out -- not by being a best solution, but by taking advantage of being the developers of the operating system, and using any chance to tell the user to remove 3rd party security software and put theirs in its place."
Morten Kjaersgaard, CEO at Heimdal, gives more context. It started with Windows 8 in 2011, when Microsoft indicated that it would try to extend its position with its own Windows Defender. In the event, says Kjaersgaard, "The first Defender was not much better than Security Essentials." But battle lines had been drawn. The AV industry downplayed Windows Defender, and Microsoft promoted third-party products less forcefully. "Until recently," he added, "Windows Defender had not posed a real threat to the antivirus industry -- but with the Windows Defender continuously improving, it is now a bigger threat."
As Defender improved, so Microsoft seemed less and less willing to work with its 'competitors'. "We have to remember that antivirus is a multi-billion dollar business, both in the consumer and B2B space -- and here Kaspersky took a stance to publicly call out a situation, which long term could cause an antitrust case for Microsoft, similar to Internet Explorer."
That danger now seems to have been averted. "It's very important for both sides that Microsoft and the specialist security companies work as closely together as possible," comments ESET senior research fellow, David Harley; "especially as Windows 10 increases its market share, as presumably it will. A security monoculture isn't in the best interests of the consumer." This position is simple. If Windows Defender -- or any other single product -- dominates the market, attackers will have fewer defenses to beat while successful attacks will be more catastrophic. Diversity brings strength; monocultures bring weakness.
This week, Microsoft's Rob Lefferts blogged, that following discussions with its AV partners, Microsoft is "making updates to our AV partner requirements today that reflect the interests of the community and our shared customers. We will also implement changes in the Windows 10 Fall Creators Update."
These changes cover the complaints made by Kaspersky. Microsoft will work more closely with third-parties over compatibility reviews; will increase "the amount of time AV partners will have to review final builds before the next Windows 10 feature update is rolled out to customers"; will allow the third-parties to display their own renewal notices; and will modify how users are told that their antivirus application has expired.
Kaspersky is the only third-party vendor specifically mentioned in this announcement. It is clearly a response to the legal threats in both Russia and the EU. "We appreciate the feedback and continued dialogue with our partners and are pleased to have found common ground with Kaspersky Lab on the complaints raised in Russia and Europe," continues Lefferts. "We look forward to our continued partnership with the industry."
Kaspersky is satisfied. In its own Kaspersky Lab blog published yesterday it states, "We are absolutely satisfied with the changes that will be implemented in the Windows 10 Fall Creators Update, and we will be taking all necessary steps to withdraw our claims and inform all regulatory bodies that we no longer have any matters for Microsoft to address."
Peace has been restored. Whether it continues, remains to be seen (Microsoft will need to compete for share of a multi-billion market without resorting to any of the OS-specific trump cards that it undoubtedly holds). But there is one other issue worth considering. In parallel to Kaspersky's complaints to the Russian and EU authorities about Microsoft's practices, the US government has started to denounce Kaspersky over 'security concerns'. Last month the US General Services Administration (GSA) announced that Kaspersky had been removed from its list of approved vendors, making it more difficult for government agencies to obtain Kaspersky products.
Was the timing coincidental? Is it an economic version of the political tit-for-tat that we have seen between America and Russia for decades? Or is it genuine security concerns?
Heimdal's Kjaersgaard believes it is genuine if unfounded concern. "I believe that the US government is concerned that because Kaspersky, as an antivirus, has full access to a device, it could theoretically relay information from the device to Kaspersky, which another influential party in Kaspersky could use.
"I cannot say anything bad about Kaspersky at all," he added; "but nor can I comment if the US government has this stance for a reason. However, concern over the software you have on your computer is legitimate with anything you install."
Kaspersky is outraged at the US position. In its own statement, it says, "“Kaspersky Lab has no ties to any government, and the company has never helped, nor will help, any government in the world with its cyberespionage efforts... Kaspersky Lab believes it is completely unacceptable that the company is being unjustly accused without any hard evidence to back up these false allegations. Kaspersky Lab, a private company, seems to be caught in the middle of a geopolitical fight where each side is attempting to use the company as a pawn in their political game."
It will be interesting to see whether the new accord between Microsoft and Kaspersky will lead to a softening of attitudes from the US government.
DNA Contains Instructions for Biological and Computer Viruses
12.8.2017 securityaffairs Virus
University of Washington scientists have created an experiment that shows how DNA can be used to not only create biologic viruses, but also viruses that can infect computers.
Deoxyribonucleic acid (DNA) is one of the oldest methods for storing information. It is found in almost all living cells and DNA information is used in nature to determine “traits as diverse as the color of a person’s eyes, the scent of a rose, and the way in which bacteria infect a lung cell.“
It is comprised of four different “nucleotides,” which combine in different ways to provide genetic instructions for different outcomes. I like to think of it like binary machine code where the combinations of 0’s and 1’s are combined to define a program for a computer to execute. This is probably a common analogy since scientists have been encoding digital data into organic DNA for a while now.
In 2012, Harvard researchers encoded an entire book in DNA. In 2013, researchers at the European Bioinformatics Institute encoded Shakespearean sonnets, digital photos and recording from Dr. Martin Luther King Jr.’s “I have a dream” speech in DNA. University of Washington researchers and Microsoft Research staff collaborated to store an OK Go music video in DNA in 2016. Although this last one may sound frivolous, it is an example that the technology is becoming more capable and easier to work with. While it is unlikely that DNA will replace more traditional digital storage mediums, it will likely find a few use cases for which it is specifically well suited. In other words, we can expect the decoding of DNA information as a regular occurrence. And whenever information is being handled, we should expect the bad guys to try and profit from it in unique ways.
This is exactly what Tadayoshi Kohno at the University of Washington was thinking about when he and his team devised the experiment to encode a malicious virus in DNA — a virus that doesn’t compromise humans, but computers. While much of scientists’ work with DNA happens with organic materials, some of it requires computers to decode the DNA information into a digital format and this is where the research team focused their attack.
[We] “synthesized DNA strands that, after sequencing and post-processing, generated a file; when used as input into a vulnerable program, this file yielded an open socket for remote control“, the authors wrote in their paper titled “Computer Security, Privacy, and DNA Sequencing: Compromising Computers with Synthesized DNA, Privacy Leaks, and More”

The team admits that they created the “best possible environment” in which to test their theory. They changed the source code of the fqzcomp DNA compressor to include a fixed data buffer which would be vulnerable to a buffer overflow attack. The next step was to encode the buffer overflow data into synthetic DNA. Encoding digital information into DNA that uses only four nucleotides with physical restrictions on the combinations is challenging and took many iterations, but the team was eventually able to come up with a viable formula and it was sent to Integrated DNA Technologies for synthesis.
When the vial of DNA was received from the synthesis service, the team now had a computer program vulnerable to the exploit encoded on that DNA and the test was ready to go. They sequenced the DNA samples using the known-vulnerable fqzcomp compressor and 37% of the time the attack was successful — the buffer overflow compromised the computer system and could have granted unauthorized access to the perpetrators.
“[the] attack was fully translated only about 37 percent of the time since the sequencer’s parallel processing often cut it short or—another hazard of writing code in a physical object—the program decoded it backward. (A strand of DNA can be sequenced in either direction, but a code is meant to be read in only one. The researchers suggest in their paper that future, improved versions of the attack might be crafted as a palindrome.)”, reads the Wired Magazine.
Is this a viable attack? It depends on many factors. The bad guys would have to compromise software used in the DNA sequencing and analysis stages like these researchers did. Or they would have to find existing vulnerabilities in the software currently being used (not hard to imagine when you realize how many vulnerabilities exist in all software.) The bad guys would also have to arrange for the target to receive a sample of the specially crafted malicious DNA, or find a vulnerability that could be exploited by known samples that did not require modification. There are a variety of ways the DNA processes could be compromised but for now, they are all complex with a low probability of success. It will take a lot of (financial) motivation or time for malicious researchers to make these attacks viable. But we know it is possible, so we can start to think about the implications now.
“We know that if an adversary has control over the data a computer is processing, it can potentially take over that computer,” says Tadayoshi Kohno. “That means when you’re looking at the security of computational biology systems, you’re not only thinking about the network connectivity and the USB drive and the user at the keyboard but also the information stored in the DNA they’re sequencing. It’s about considering a different class of threat.”
Cyberspies Are Using Leaked NSA Hacking Tools to Spy On Hotels Guests
12.8.2017 thehackernews BigBrothers
Cyberspies Are Using Leaked NSA Hacking Tools to Spy On Hotels Guests
An infamous Russian-linked cyber-espionage group has been found re-using the same leaked NSA hacking tool that was deployed in the WannaCry and NotPetya outbreaks—this time to target Wi-Fi networks to spy on hotel guests in several European countries.
Security researchers at FireEye have uncovered an ongoing campaign that remotely steals credentials from high-value guests using Wi-Fi networks at European hotels and attributed it to the Fancy Bear hacking group.
Fancy Bear—also known as APT28, Sofacy, Sednit, and Pawn Storm—has been operating since at least 2007 and also been accused of hacking the Democratic National Committee (DNC) and Clinton Campaign in an attempt to influence the U.S. presidential election.
The newly-discovered campaign is also exploiting the Windows SMB exploit (CVE-2017-0143), called EternalBlue, which was one of many exploits allegedly used by the NSA for surveillance and leaked by the Shadow Brokers in April.
EternalBlue is a security vulnerability which leverages a version of Windows' Server Message Block (SMB) version 1 networking protocol to laterally spread across networks and also allowed the WannaCry and Petya ransomware to spread across the world quickly.
Since the EternalBlue code is available for anyone to use, cyber criminals are widely trying to use the exploit to make their malware more powerful.
Just last week, a new version of credential stealing TrickBot banking Trojan was found leveraging SMB to spread locally across networks, though the trojan was not leveraging EternalBlue at that time.
However, researchers have now found someone deploying the exploit to upgrade their attack.
"To spread through the hospitality company's network, APT28 used a version of the EternalBlue SMB exploit," FireEye researchers write. "This is the first time we have seen APT28 incorporate this exploit into their intrusions."
Researchers have seen ongoing attacks targeting a number of companies in the hospitality sector, including hotels in at least seven countries in Europe and one Middle Eastern country.
Here's How the Attack is Carried Out
The attacks began with a spear phishing email sent to one of the hotel employees. The email contains a malicious document named "Hotel_Reservation_Form.doc," which uses macros to decode and deploy GameFish, malware known to be used by Fancy Bear.
Once installed on the targeted hotel's network, GameFish uses the EternalBlue SMB exploit to laterally spread across the hotel network and find systems that control both guest and internal Wi-Fi networks.
Once under control, the malware deploys Responder, an open source penetration testing tool created by Laurent Gaffie of SpiderLabs, for NetBIOS Name Service (NBT-NS) poisoning in order to steal credentials sent over the wireless network.
While the hacking group carried out the attack against the hotel network, researchers believe that the group could also directly target "hotel guests of interest"—generally business and government personnel who travel in a foreign country.
The researchers revealed one such incident that occurred in 2016 where Fancy Bear accessed the computer and Outlook Web Access (OWA) account of a guest staying at a hotel in Europe, 12 hours after victim connected to the hotel’s Wi-Fi network.
This is not the only attack that apparently aimed at guests of hotels. South Korea-nexus Fallout Team (also known as DarkHotel) has previously carried out such attacks against Asian hotels to steal information from senior executives from large global companies during their business trips.
Duqu 2.0 malware also found targeting the WiFi networks of European hotels used by participants in the Iranian nuclear negotiations. Also, high-profile people visiting Russia and China may have their laptops and other electronic devices accessed.
The easiest way to protect yourself is to avoid connecting to hotel Wi-Fi networks or any other public or untrusted networks, and instead, use your mobile device hotspot to get access to the Internet.
More than 1,000 Spyware Apps Found On Android App Stores
12.8.2017 thehackernews Android
More than 1,000 Spyware Apps Found On Android App Stores
If you think you are downloading apps from Google Play Store and you are secure, then watch out!
Someone has managed to flood third-party app stores and Google Play Store with more than a thousand malicious apps, which can monitor almost anything a user does on their mobile device from silently recording calls to make outbound calls without the user’s interaction.
Dubbed SonicSpy, the spyware has been spreading aggressively across Android app stores since at least February and is being distributed by pretending itself to be a messaging app—and it actually offers a messaging service.
SonicSpy Can Perform a Whole Lots of Malicious Tasks
At the same time, the SonicSpy spyware apps perform various malicious tasks, including silently recording calls and audio from the microphone, hijacking the device's camera and snap photos, making outbound calls without the user's permission, and sending text messages to numbers chosen by the attacker.
Besides this, the SonicSpy spyware also steals user information including call logs, contacts and information about Wi-Fi access point the infected device has connected to, which could easily be used to track the user's location.
The spyware was discovered by security researchers at mobile security firm Lookout. The researchers also uncovered three versions of the SonicSpy-infected messaging app in the official Google Play Store, which had been downloaded thousands of times.
Although the apps in question—Soniac, Hulk Messenger and Troy Chat—have since been removed by Google from the Play Store, they are still widely available in third-party app stores along with other SonicSpy-infected apps.
Iraq Connection to the SonicSpy Spyware
The researchers believe the malware is related to a developer based in Iraq and say the overall SonicSpy malware family supports 73 different remote instructions that its attacker could execute on an infected Android device.
The connection of Iraq to the spyware stems from similarities between SonicSpy and SpyNote, another Android malware that was discovered in July 2016, which was masquerading as a Netflix app and was believed to have been written by an Iraqi hacker.
"There are many indicators that suggest the same actor is behind the development of both. For example, both families share code similarities, regularly make use of dynamic DNS services, and run on the non-standard 2222 port," says Lookout Security Research Services Technology Lead Michael Flossman.
Also, the important indicator is the name of the developer account behind Soniac, listed on the Google Play store, was "iraqiwebservice."
Here's How the SonicSpy Spyware Works
One of the SonicSpy-infected messaging apps that made it through Google's Play Store masqueraded as a communications tool called Soniac.
Once installed, Soniac removes its launcher icon from the smartphone menu to hide itself from the victim and connects to a command and control (C&C) server in an attempt to install a modified version of the Telegram app.
However, the app actually includes many malicious features which allowed the attackers to gain almost full control of the infected device and turn it a spy in your pocket that could silently record audio, make calls, take photos, and pilfer your personal data, including call logs, contacts and details about Wi-Fi access points.
Before being removed by Google, the app had already been downloaded between 1,000 and 5,000 times, but since it was part of a family of 1,000 variants, the malware could have infected many thousands more.
SonicSpy Could Get Into Play Store Again
Although SonicSpy-infected apps have now been removed from the Play Store, the researchers warned that the malware could potentially get into the Play Store again with another developer account and different app interface.
"The actors behind this family have shown that they're capable of getting their spyware into the official app store and as it's actively being developed, and its build process is automated, it's likely that SonicSpy will surface again in the future," the researchers warned.
While Google has taken many security measures to prevent malicious apps from making through Google's security checks, malicious apps still make their ways into the Play Store.
Just last month, we warned you about a clever malware, called Xavier, that was discovered in over 800 different Android apps that had been downloaded millions of times from Google Play Store and silently collected sensitive user data and can perform dangerous tasks.
In April, we reported about the BankBot banking trojan making its way to Google Play Store with the ability to get administrator privileges on infected devices and perform a broad range of malicious tasks, including stealing victim's bank logins.
In the same month, about 2 Million Android users fell victim to the FalseGuide malware hidden in more than 40 apps for popular mobile games, such as Pokémon Go and FIFA Mobile, on the official Google Play Store.
How to Protect yourself against such Malware
The easiest way to prevent yourself from being targeted by such clever malware, always beware of fishy apps, even when downloading them from official Google Play Store and try to stick to the trusted brands only.
Moreover, always look at the reviews left by users who have downloaded the app and verify app permissions before installing any app even from the official app stores and grant those permissions that are relevant for the app's purpose.
Also, do not download apps from third party source. Although in this case, the app is also being distributed through the official Play Store, most often victims became infected with such malware via untrusted third-party app stores.
Last but not the least, you are strongly advised to always keep good antivirus software on your device that can detect and block such malware before they infect your device, and keep your device and apps up-to-date.
Ukrainian Man Arrested For Distributing NotPetya Ransomware And Helping Tax Evaders
12.8.2017 thehackernews Ransomware

Ukrainian authorities have arrested a 51-year-old man accused of distributing the infamous Petya ransomware (Petya.A, also known as NotPetya) — the same computer virus that massively hit numerous businesses, organisations and banks in Ukraine as well as different parts of Europe around 45 days ago.
However, the story is not as simple as it seems, which portrayed this man as a criminal. I recommend you to read complete article to understand the case better and then have an opinion accordingly.
Sergey Neverov (Сергей Неверов), father of two sons and the resident of the southern city of Nikopol, is a video blogger and computer enthusiast who was arrested by the Ukrainian police on Monday, August 7 from his home.
What Neverov Did?
According to a press release published on Thursday by the Ukrainian cyber police department, Neverov uploaded a video, showing how to infect a computer with Petya.A ransomware—and also shared a download link for NotPetya malware to his social media account.
After searching Neverov's home, the authorities seized his computers and other equipment, which were later analysed by the officers from the Ukrainian cyber-crime department, who discovered some files containing the malicious software.
However, the police confirmed that Neverov was neither the actual author of the NotPetya virus, nor he was behind the massive ransomware attack that crippled many businesses and banks in this summer.
The authorities charged Neverov of spreading a copy of NotPetya virus via his social media account that eventually infected at least 400 computers in Ukraine, and also believe that he had helped tax evaders — directly or indirectly.
Companies Intentionally Infected Their Computers to Avoid Paying Taxes & Fines
If you are not aware, 30th June was the last date in Ukraine for filing tax returns and unfortunately, during the same time NotPetya outcry began that encrypted sensitive files and documents for several businesses and organisations across the country.
Since firms that were infected by the virus were unable to submit tax reports on time and liable for paying huge fines for late submissions, the head of the parliamentary committee on tax and customs, Nina Yuzhanina, gave affected taxpayers some relief (through a statement on his Facebook profile) by extending the last date to 31st December, 2017.
Police believe the malware sample distributed by Neverov is being used by some businesses to deliberately infect their systems to avoid paying taxes on time as well as late tax return penalty.
Is Neverov a Hacker or Computer Enthusiast?
However, the story has another angle that indicates charges on Neverov are baseless.
As I mentioned, Neverov is a video-blogger with 11,000 followers on YouTube, who loves to play with computers and publish review videos on computer hardware and gadgets for informational purposes.
Neverov never tried to hide his identity, and even in some of his videos, he revealed his face and the exact GPS location to his house in Nikopol, which suggests that he had nothing to hide, neither his intentions were wrong.
When NotPetya outcry hit his country, Neverov got curious about the ransomware and started studying about the malware to understand how it works and to find a way to recover infected files without paying ransom to the attackers.
To get started, he downloaded a sample of NotPetya ransomware from the Internet and tested it on his computer, just like other malware analysts do.
In fact, while recording a video of the NotPetya infection to demonstrate its impact on a targeted computer, he failed two times in infecting his own computer.
When succeeded in the third attempt, Neverov uploaded the copy of NotPetya malware on file hosting website and shared the link on his social media account just for the informational purpose, saying "use at your own risk."
Moreover, it is important to note that Neverov would not be gaining any profit by distributing the ransomware because of NotPetya has been designed to blackmail victims into paying ransom amount to a specific Bitcoin address that belongs to the original attackers only.
If Convicted, Neverov Could Face 3 Years In Prison
Neverov, the computer enthusiast, has now been charged under article 361 (part 1) of the Criminal Code of Ukraine, which says:
"Unauthorized interference with the work of electronic computing machines (computers), automated systems, computer networks or telecommunication networks, ...which led to the leak, loss, fake, blocking information, distortion of the information processing or violation the established order it's routing."
Although this sanction provides maximum punishment of up to two years in prison, Neverov has been threatened to face up to three years in jail, according to the official comments from the law enforcement authorities.
The case seems somewhat similar to the one currently being faced by Marcus Hutchins, also known as MalwareTech, who gained famed for stopping the WannaCry ransomware.
Hutchins was arrested by the FBI while he was travelling to his home after attending Def Con event in the United States and has been charged with creating and distributing a banking malware.
Since Hutchins is a malware researcher, many infosec community members believe possibly a proof-of-concept code written and published by him publicly was re-used by the criminals to create the banking malware, which mistakenly framed him as the criminal mastermind.
Hutchins is set to face a hearing in the US district court on 14 August, so we still have to wait for more information about his case.
CIA's "CouchPotato" Collects Video Streams
12.8.2017 securityweek BigBrothers
WikiLeaks has published documents that describe a remote tool allegedly used by the U.S. Central Intelligence Agency (CIA) to collect RTSP/H.264 video streams.
Dubbed “CouchPotato,” the tool can apparently be used to collect the stream as a video file (AVI), or to capture still images (JPG) of frames from the stream, as long as these frames are “of significant change from a previously captured frame.”
To perform the video and image encoding and decoding operations, the tool leverages the free software project FFmpeg. However, many audio and video codecs, along with unnecessary features, have been removed from the FFmpeg version used by CouchPotato.
To provide the tool with image change detection features, the pHash image hashing algorithm has been integrated into FFmpeg’s image2 demuxer. CouchPotato also uses RTSP connectivity and “relies on being launched in an ICE v3 Fire and Collect compatible loader,” the tool’s user guide published on WikiLeaks reveals (PDF).
Thus, the use of this tool requires a loader that can support the ICE v3 specification (Fire and Collect are mentioned as suitable options, along with ShellTerm, which was used to test CouchPotato during development). Python 2 is required by the module handler script, which should also be run on a *nix host, the same host the loader runs onto.
To avoid being blocked by a firewall when sending or receiving data, CouchPotato should be injected into a non-critical host process on the target machine, the documents explained. The user manual specifically recommends not to launch out of a process critical to the system’s stability. The tool can be operated using a command-line interface.
Targeting RTSP and H.264 video formats, which are normally used by IP-based surveillance cameras streaming video content over LAN or the Internet, CouchPotato requires the video stream URL to function and doesn’t necessarily require compromising the target’s network.
The user guide published on WikiLeaks includes details on the various arguments the tools comes with support for, along with the various limitations and caveats the tool inherits, such as high CPU usage for the injected process.
Variety reports a failed attempt of HBO to Offer a ‘Bug Bounty’ to hackers
12.8.2017 securityaffairs Security
According to a report from a leaked memo by Variety, in response to the incident, HBO offered a reward of $250,000, a figure far from the HBO annual budget.
Cyber criminals claiming to have hacked television group HBO networks were demanding millions of dollars in ransom payments from the company while threatening to release more material.
The alleged hackers published a five-minute video letter to HBO chief Richard Plepler claiming to have “obtained valuable information” in a cyber attack. Cyber criminals said they had stolen 1.5 terabytes of data.
The author of the message dubbed himself “Mr. Smith,” confirmed his group obtained “highly confidential” documents and data, including scripts, contracts, and personnel files.
The crooks pretend to receive half of the group’s annual budget of $12 million to $15 million to stop leasing the files.
The hackers claim a long work to compromise the company network, it took six months to break into the company systems, they also added to have purchased $500,000 a year zero-day exploits that let them hack the firm exploiting flaws in Microsoft and other software used by HBO.
According to a report from a leaked memo by Variety, in response to the incident, HBO offered a reward of $250,000. The payment was offered as a “bug bounty,” to discover vulnerabilities in their its computer networks.
Unfortunately, “Mr. Smith” and his crew weren’t satisfied by the offer that doesn’t match their millionaire demands to stop leaking sensitive data, the crooks’ request would be more than $6 million.
HBO did not comment the report by Variety.
Last week, along with the video letter, the hackers released 3.4GB of files. The dump contained technical data related to the HBO’s internal network and administrator passwords, and of course the draft scripts from five Game of Thrones episodes. The huge trove of files also includes a month’s worth of emails from HBO’s vice president for film programming, Leslie Cohen.
HBO is working with forensic experts and law enforcement to identify the hackers and fix the flaws they have exploited to steal the precious content.
APT28 hackers are leveraging NSA Hacking tool to spy on Hotels guests
12.8.2017 securityaffairs APT
According to FireEye, the notorious Russia-linked APT28 group is behind an ongoing campaign targeting hotels in several European countries.
According to FireEye, the notorious Russia-linked APT28 group (Pawn Storm, Fancy Bear, Sofacy, Sednit and Strontium) is behind an ongoing campaign targeting hotels in several European countries.
The researchers observed many attacks targeting the networks of hotels to gain access the devices of government and business travelers via the guest Wi-Fi.
The hackers targeted several companies in the hospitality sector, including hotels in seven European countries and at least one in the Middle Eastern country.
The attack chain starts with a spear phishing email sent to a hotel employee, the messages use weaponized document named “Hotel_Reservation_Form.doc.” The embedded macros decode a dropper that delivers the GameFish malware. Experts noticed that the backdoor is the same used by the APT28 in a recent campaign that targeted Montenegro after the state officially joined NATO alliance despite the strong opposition from Russian Government that threatened to retaliate.
Once the hackers accessed the target network, they used the NSA-linked EternalBlue SMB exploit for lateral movements. According to the malware researchers at FireEye, this is the first time APT28 hackers had used this NSA exploit.
“APT28 is using novel techniques involving the EternalBlue exploit and the open source tool Responder to spread laterally through networks and likely target travelers. Once inside the network of a hospitality company, APT28 sought out machines that controlled both guest and internal Wi-Fi networks. No guest credentials were observed being stolen at the compromised hotels; however, in a separate incident that occurred in Fall 2016, APT28 gained initial access to a victim’s network via credentials likely stolen from a hotel Wi-Fi network.” reads the analysis published by FireEye.
The APT28 hackers also used the open source penetration testing tool Responder for NetBIOS Name Service (NBT-NS) poisoning.
“Upon gaining access to the machines connected to corporate and guest Wi-Fi networks, APT28 deployed Responder. Responder facilitates NetBIOS Name Service (NBT-NS) poisoning.
This technique listens for NBT-NS (UDP/137) broadcasts from victim computers attempting to connect to network resources. Once received, Responder masquerades as the sought-out resource and causes the victim computer to send the username and hashed password to the attacker-controlled machine. APT28 used this technique to steal usernames and hashed passwords that allowed escalation of privileges in the victim network,” continues FireEye.
The researchers reported details about an intrusion occurred in 2016, a user connected to a hotel’s Wi-Fi and 12 hours later APT28 hackers used stolen credentials to access his network and his Outlook Web Access (OWA) account.
This isn’t the first time hackers targeted travelers, the most important case is represented by the DarkHotel APT. The APT group targeted European hotels hosting participants in Iranian nuclear negotiations, and according to some reports, hackers spied on high-profile people visiting Russia and China.
“Cyber espionage activity against the hospitality industry is typically focused on collecting information on or from hotel guests of interest rather than on the hotel industry itself, though actors may also collect information on the hotel as a means of facilitating operations,” FireEye said. “Business and government personnel who are traveling, especially in a foreign country, must often rely on less secure systems to conduct business than at their home office, or may be unfamiliar with the additional threats posed while abroad.”
Peace Breaks Out Between Microsoft and Kaspersky Lab
11.8.2017 securityweek IT
Microsoft Agrees to Kaspersky Lab's Demands
Microsoft and Kaspersky are friends again, and the whole anti-virus ecosystem is at peace.
Back in November 2016, Eugene Kaspersky declared, "That's It. I've Had Enough!" It wasn't just words. "We've taken the decision to address official bodies in various countries (including the EU and Russia) with a request to oblige Microsoft to cease its violation of anti-competition legislation and to remove the consequences of that violation." And he did just that, first in Russia and then in the EU.
Eugene Kaspersky, founder of Russia-based Kaspersky Lab, was not alone in his concerns. "Some time ago security companies started noticing that things were changing at Microsoft," Luis Corrons, technical director at PandaLabs told SecurityWeek. "It looked like they were more concerned about their own antivirus market share, and were trying to push the competition out -- not by being a best solution, but by taking advantage of being the developers of the operating system, and using any chance to tell the user to remove 3rd party security software and put theirs in its place."
Morten Kjaersgaard, CEO at Heimdal, gives more context. It started with Windows 8 in 2011, when Microsoft indicated that it would try to extend its position with its own Windows Defender. In the event, says Kjaersgaard, "The first Defender was not much better than Security Essentials." But battle lines had been drawn. The AV industry downplayed Windows Defender, and Microsoft promoted third-party products less forcefully. "Until recently," he added, "Windows Defender had not posed a real threat to the antivirus industry -- but with the Windows Defender continuously improving, it is now a bigger threat."
As Defender improved, so Microsoft seemed less and less willing to work with its 'competitors'. "We have to remember that antivirus is a multi-billion dollar business, both in the consumer and B2B space -- and here Kaspersky took a stance to publicly call out a situation, which long term could cause an antitrust case for Microsoft, similar to Internet Explorer."
That danger now seems to have been averted. "It's very important for both sides that Microsoft and the specialist security companies work as closely together as possible," comments ESET senior research fellow, David Harley; "especially as Windows 10 increases its market share, as presumably it will. A security monoculture isn't in the best interests of the consumer." This position is simple. If Windows Defender -- or any other single product -- dominates the market, attackers will have fewer defenses to beat while successful attacks will be more catastrophic. Diversity brings strength; monocultures bring weakness.
This week, Microsoft's Rob Lefferts blogged, that following discussions with its AV partners, Microsoft is "making updates to our AV partner requirements today that reflect the interests of the community and our shared customers. We will also implement changes in the Windows 10 Fall Creators Update."
These changes cover the complaints made by Kaspersky. Microsoft will work more closely with third-parties over compatibility reviews; will increase "the amount of time AV partners will have to review final builds before the next Windows 10 feature update is rolled out to customers"; will allow the third-parties to display their own renewal notices; and will modify how users are told that their antivirus application has expired.
Kaspersky is the only third-party vendor specifically mentioned in this announcement. It is clearly a response to the legal threats in both Russia and the EU. "We appreciate the feedback and continued dialogue with our partners and are pleased to have found common ground with Kaspersky Lab on the complaints raised in Russia and Europe," continues Lefferts. "We look forward to our continued partnership with the industry."
Kaspersky is satisfied. In its own Kaspersky Lab blog published yesterday it states, "We are absolutely satisfied with the changes that will be implemented in the Windows 10 Fall Creators Update, and we will be taking all necessary steps to withdraw our claims and inform all regulatory bodies that we no longer have any matters for Microsoft to address."
Peace has been restored. Whether it continues, remains to be seen (Microsoft will need to compete for share of a multi-billion market without resorting to any of the OS-specific trump cards that it undoubtedly holds). But there is one other issue worth considering. In parallel to Kaspersky's complaints to the Russian and EU authorities about Microsoft's practices, the US government has started to denounce Kaspersky over 'security concerns'. Last month the US General Services Administration (GSA) announced that Kaspersky had been removed from its list of approved vendors, making it more difficult for government agencies to obtain Kaspersky products.
Was the timing coincidental? Is it an economic version of the political tit-for-tat that we have seen between America and Russia for decades? Or is it genuine security concerns?
Heimdal's Kjaersgaard believes it is genuine if unfounded concern. "I believe that the US government is concerned that because Kaspersky, as an antivirus, has full access to a device, it could theoretically relay information from the device to Kaspersky, which another influential party in Kaspersky could use.
"I cannot say anything bad about Kaspersky at all," he added; "but nor can I comment if the US government has this stance for a reason. However, concern over the software you have on your computer is legitimate with anything you install."
Kaspersky is outraged at the US position. In its own statement, it says, "“Kaspersky Lab has no ties to any government, and the company has never helped, nor will help, any government in the world with its cyberespionage efforts... Kaspersky Lab believes it is completely unacceptable that the company is being unjustly accused without any hard evidence to back up these false allegations. Kaspersky Lab, a private company, seems to be caught in the middle of a geopolitical fight where each side is attempting to use the company as a pawn in their political game."
It will be interesting to see whether the new accord between Microsoft and Kaspersky will lead to a softening of attitudes from the US government.
Hackers Say Humans Most Responsible for Security Breaches
11.8.2017 securityweek Security
Hackers Say Humans Are the Weakpoint and That Traditional Defenses Cannot Protect Them
Under the principle of set a thief to catch a thief, 250 hackers at Black Hat 2017 were asked about their hacking methods and practices. By understanding how they work and what they look for, defenders can better understand how to safeguard their own systems.
Thycotic surveyed (PDF) a cross section of hackers attending Black Hat. Fifty-one percent described themselves as white hats; 34% described themselves as grey hats using their skills for both good and bad causes; and 15% self-identified as out-and-out black hats.
The hackers' number one choice for fast and easy access to sensitive data is gaining access to privileged accounts (31%). Second is access to an email account (27%), and third is access to a user's endpoint (21%). All other routes combined totaled just 21%.
The hackers also confirmed that perimeter security, in the form of firewalls and anti-virus, is irrelevant and obsolete. Forty-three percent are least troubled by anti-virus and anti-malware defenses, while 29% are untroubled by firewalls. "Hackers today are able to bypass both firewalls and AV using well known applications and protocols or even VPN that hide within expected communications," explains Joseph Carson, Thycotic's chief security scientist. "For example, VOIP, streaming services etc. Because of the ability to hide within normal business applications or the use of authenticated stolen credentials, they are stating that these technologies are no longer sufficient to prevent cyber-attacks on their own."
Overall, the hackers find MFA and encryption their biggest obstacles. "As hackers increasingly target privileged accounts and user passwords," explains Thycotic, "it’s perhaps not surprising that the technologies they considered the toughest to beat include Multi-Factor Authentication (38%) and Encryption (32%), with endpoint protection and intrusion prevention far behind at 8% and 5 % respectively."
Ultimately, however, the hackers believe that humans are most responsible for security breaches. Only 5% consider that insufficient security software is the problem, while 85% named humans as most responsible for security breaches. The problem is 'cyber fatigue'.
Cyber fatigue is blamed on the constant pressure to obey policy and good practice. "'Remembering
and changing passwords' was the top source of cybersecurity fatigue (35%), a major vulnerability that hackers are all too willing to exploit," notes Thycotic. "Other contributing factors included 'Information overload' (30%), 'Never ending software updates' (20%) and 'Living under constant cyber security threats' (15%)."
Perhaps surprisingly, hackers do not consider threat intelligence solutions to be an obstacle. "Because Threat Intelligence solutions are also accessible to hackers, they may be able to easily identify how they work and therefore avoid detection them," suggests Thycotic.
The survey suggests that humans are a weakpoint, traditional perimeter defenses are ineffective, and user credentials are the target. "With traditional perimeter security technologies considered largely irrelevant, hackers are focusing more on gaining access to privileged accounts and email passwords by exploiting human vulnerabilities allowing the hacker to gain access abusing trusted identities," comments Carson. "More than ever, it is critical for businesses to mitigate these risks by implementing the right technologies and process to ward off unsuspecting attacks and access to sensitive data."
His conclusion is that "The new cybersecurity perimeter must incorporate an identity firewall built around employee and data using identity and access management technology controls which emphasizes the protection of privileged account credentials and enhances user passwords across the enterprise with multi-factor authentication."
SonicSpy Spyware Found in Over One Thousand Android Apps
11.8.2017 securityweek Android
Security researchers have found more than one thousand applications rigged with spyware over the past six months, including some distributed via Google Play.
The applications are part of the SonicSpy malware family and have been aggressively deployed since February 2017 by a threat actor likely based in Iraq, Lookout security researchers say. Google was informed on the malicious activity and has removed at least one of the offending apps from Google Play.
One sample found in Google Play was called Soniac and was posing as a messaging application. Although it does provide the advertised functionality by leveraging a customized version of the Telegram messaging app, the software also includes malicious components, Lookout says.
Once the malicious program has been installed on a device, its author is provided with “significant control” over that device. The overall SonicSpy family of malware includes support for 73 different remote instructions, yet only some are found in Soniac.
Among these, the security researchers mention the ability to silently record audio, an option to take photos with the camera, and the ability to make outbound calls. Additionally, the malware can send text messages to attacker-specified numbers and can retrieve information such as call logs, contacts, and information about Wi-Fi access points.
When executed, SonicSpy removes its launcher icon to hide itself from the victim, then attempts to establish a connection to the command and control (C&C) infrastructure (at arshad93.ddns[.]net). The malware also attempts to install its own custom version of Telegram, which it has stored in the res/raw directory under the name su.apk.
While analyzing the discovered samples, the security researchers found similarities with SpyNote, a malware family first detailed in mid-2016. Based on numerous indicators, the researchers suggest that the same actor is behind the development of both malware families.
According to Lookout, both SonicSpy and SpyNote share code similarities and both make use of dynamic DNS services, in addition to running on the non-standard 2222 port.
The SpyNote attacker, the researchers say, was using custom-built desktop software to inject malicious code into the Trojanized apps, thus allowing the victim to continue interacting with their legitimate functionality. The stream of observed SonicSpy apps suggests the actors behind it are using a similar automated-build process, yet the researchers haven’t recovered their desktop tooling until now.
Lookout also notes that the account behind Soniac, iraqwebservice, has previously posted two other SonicSpy samples to the Play Store, yet those are no longer live. Called Hulk Messenger and Troy Chat, the applications contained some functionality as other SonicSpy samples, but it’s unclear whether Google removed them or the actor behind them decided to remove them to evade detection.
“Anyone accessing sensitive information on their mobile device should be concerned about SonicSpy. The actors behind this family have shown that they're capable of getting their spyware into the official app store and as it's actively being developed, and its build process is automated, it's likely that SonicSpy will surface again in the future,” the security researchers conclude.
Russian Cyberspies Target Hotels in Europe
11.8.2017 securityweek CyberSpy
A notorious Russia-linked hacker group specializing in cyber espionage is believed to be behind an ongoing campaign targeting hotels in several European countries.
FireEye has linked the attacks with moderate confidence to APT28, a threat actor also known as Pawn Storm, Fancy Bear, Sofacy, Sednit and Strontium. The group is believed to have launched numerous high-profile attacks, including a campaign targeting last year’s presidential election in the United States.
While the recent attacks have targeted the networks of hotels, the security firm says there is some indication that the hackers may actually be looking to access the devices of government and business travelers via the guest Wi-Fi provided by these hotels.
FireEye has seen attacks targeting several companies in the hospitality sector, including hotels in seven European countries and one Middle Eastern country.
The attacks start with a spear phishing email sent to a hotel employee. The emails carry a document named “Hotel_Reservation_Form.doc,” which uses macros to decode a dropper that deploys GameFish, a piece of malware known to be used by APT28. This backdoor was used recently in a campaign launched by the threat group against Montenegro just as the country had been preparing to join NATO.
Once they gained access to the targeted hotel’s network, the hackers used the NSA-linked EternalBlue SMB exploit, which was also involved in the recent WannaCry and NotPetya outbreaks, to move laterally within the network. Researchers said this was the first time the group had used this exploit.
The cyberspies also used Responder, an open source penetration testing tool developed by Laurent Gaffie of SpiderLabs. They leveraged Responder for NetBIOS Name Service (NBT-NS) poisoning.
“This technique listens for NBT-NS (UDP/137) broadcasts from victim computers attempting to connect to network resources. Once received, Responder masquerades as the sought-out resource and causes the victim computer to send the username and hashed password to the attacker-controlled machine. APT28 used this technique to steal usernames and hashed passwords that allowed escalation of privileges in the victim network,” FireEye researchers explained.
In one incident that occurred in 2016, a user connected to a hotel’s Wi-Fi and 12 hours later their device was accessed by APT28 using stolen credentials. The attackers started moving through the victim’s network and accessed their Outlook Web Access (OWA) account.
While these attacks can be carried out remotely, in this case the attacker appeared to be on the same network and physically close to the victim.
Kaspersky reported recently that APT28 has been using two zero-day vulnerabilities in targeted attacks, and it has started experimenting with new macro techniques.
These are not the only attacks apparently aimed at travelers. Other campaigns include DarkHotel, which some have linked to South Korea, Duqu 2.0, targeting the networks of European hotels hosting participants in Iranian nuclear negotiations, and according to some reports, high-profile people visiting Russia and China may have their devices accessed.
“Cyber espionage activity against the hospitality industry is typically focused on collecting information on or from hotel guests of interest rather than on the hotel industry itself, though actors may also collect information on the hotel as a means of facilitating operations,” FireEye said. “Business and government personnel who are traveling, especially in a foreign country, must often rely on less secure systems to conduct business than at their home office, or may be unfamiliar with the additional threats posed while abroad.”
Symantec Patches Code Execution Flaw in Email Security Product
11.8.2017 securityweek Vulnerebility
Symantec has released an update for its Messaging Gateway email security product to address remote code execution and cross-site request forgery (CSRF) vulnerabilities.
The more serious of the security holes, tracked as CVE-2017-6327 and classified as high severity, is a remote code execution flaw discovered by Philip Pettersson.
“The Symantec Messaging Gateway can encounter an issue of remote code execution, which describes a situation whereby an individual may obtain the ability to execute commands remotely on a target machine or in a target process. In this type of occurrence, after gaining access to the system, the attacker may attempt to elevate their privileges,” Symantec said in its advisory.
The second flaw, rated low severity and identified as CVE-2017-6328, is a CSRF weakness identified by Dhiraj Mishra. The security bug allows an attacker to execute commands via a trusted user by getting the victim to access a specially crafted website.
The vulnerabilities affect Symantec Messaging Gateway versions prior to 10.6.3-267, which addresses the issues. In addition to applying patches, the company has advised customers to restrict access to administrative and management systems, and run applications with the lowest level of privilege needed.
There is no indication that any of these vulnerabilities have been exploited in the wild. US-CERT has also released an alert to encourage organizations to review Symantec’s advisory and install the necessary updates.
Software developed by Symantec, similar to the products of other security solutions providers, is often found to have vulnerabilities. In the past few years, white hat hackers have disclosed potentially serious flaws affecting the company’s Antivirus Engine, Endpoint Protection and various enterprise security products.
One of the most interesting weaknesses was discovered last year by Google Project Zero researcher Tavis Ormandy. The expert found a critical Antivirus Engine vulnerability that could have been exploited for arbitrary code execution simply by sending a specially crafted file to the victim.
HBO Offered 'Bounty' to Hackers: Report
11.8.2017 securityweek Security
HBO offered a reward of $250,000 in response to a data breach at the television group that produces "Game of Thrones," according to a report from a leaked memo.
The report by Variety on Thursday said HBO offered the payment as a "bug bounty," which is offered by companies to discover vulnerabilities in their computer networks.
The offer apparently failed to satisfy the attackers who have demanded a ransom of millions of dollars and are threatening to release more files from what is claimed to be a massive data breach.
HBO, a unit of the media group Time Warner, did not respond to a query about the Variety report.
Earlier this week, a video circulating online authored by someone identified only as "Mr. Smith" said the hackers had videos, scripts, personnel files and other sensitive data from the breach.
The hackers demanded "six month salary," which, according to the video, would be more than $6 million.
Last week the hacker group leaked one script of "Games of Thrones" and content from other HBO productions. HBO has said it was working with forensic experts and law enforcement in response to the attack.
Fuji Electric Patches Vulnerabilities in HMI Software
11.8.2017 securityweek Vulnerebility
Japanese electrical equipment company Fuji Electric has released an update for one of its human-machine interface (HMI) products to address several vulnerabilities.
The affected product is the Fuji Electric Monitouch V-SFT, an application that allows organizations to configure their HMI screens. The software is used worldwide in the critical manufacturing and energy sectors.
ICS-CERT informed organizations on Thursday that the Monitouch V-SFT software is affected by stack and heap buffer overflows and improper privilege management vulnerabilities that can be exploited to execute arbitrary code and escalate privileges.
The security holes were reported to the vendor by researchers Ariele Caltabiano (aka kimiya) and Fritz Sands through Trend Micro’s Zero Day Initiative (ZDI) in September 2016.
According to ZDI, the buffer overflow flaws, which allow a remote attacker to cause a crash or execute arbitrary code in the context of the targeted process, can be exploited by getting the targeted user to visit a malicious web page or open a malicious file.
The vulnerabilities, tracked as CVE-2017-9659 and CVE-2017-9660, exist due to the way the application parses V8 project files and is caused by the lack of proper validation for the length of user-supplied data prior to copying it to a fixed-length buffer.
While ZDI has classified the buffer overflows as medium severity bugs with a CVSS score of 6.8, ICS-CERT has rated the issues as high severity with a CVSS score of 7.3.
The third type of vulnerability affecting Fuji Electric’s Monitouch V-SFT is less severe. It allows a local attacker who has the ability to execute low-privileged code to escalate their permissions.
“The specific flaw exists within the configuration of Monitouch V-SFT. The software is installed with weak access controls on the executable files. An attacker can leverage this vulnerability to execute code in the context of any user of the software,” ZDI said in its advisory.
ICS-CERT says all these vulnerabilities have been patched by the vendor with the release of Monitouch V-SFT 5.4.43.0. In addition to applying the update, the agency has advised organizations to take measures to limit access to control systems.
Cyberattack Leaves Millions Without Mobile Phone Service in Venezuela
11.8.2017 securityweek Mobil
A massive cyberattack that took down government websites in Venezuela earlier this week also has left seven million mobile phone users without service, the government said Thursday.
A group that calls itself The Binary Guardians claimed responsibility for attacks that targeted the websites of the government, the supreme court and the National Assembly.
"These terrorist actions which affected the Movilnet's GSM platform on Wednesday left without communication seven of the state operator's 13 million users," Science and Technology Minister Hugbel Roa said.
Venezuela has two other private mobile phone operators: Spanish-owned Movistar and Digitel.
Roa said the outage was part of a wave of attacks that began Monday when dozens of government and private company websites were hacked.
Roa said there also have been nine cuts in the country's fiber optic network, which has cut off already precarious internet service to seven states.
"The attacks were carried out with the help of foreign agents, trying once again to disrupt our country's connectivity," Roa said, adding that an investigation was underway
Command Execution Flaw Affects Several Version Control Systems
11.8.2017 securityweek Vulnerebility
Several popular version control systems are affected by a potentially serious command execution vulnerability. The developers of the impacted products have released updates this week to patch the security hole.
The flaw affects version control systems such as Git (CVE-2017-1000117), Apache Subversion (CVE-2017-9800), Mercurial (CVE-2017-1000116) and CVS. No CVE identifier has been assigned for CVS as the system was last updated more than 9 years ago.
The vulnerability, discovered by Joern Schneeweisz of Recurity Labs, can be exploited by a remote attacker to execute arbitrary commands by getting the targeted user to click on a specially crafted “ssh://” URL.
“A malicious third-party can give a crafted ‘ssh://…’ URL to an unsuspecting victim, and an attempt to visit the URL can result in any program that exists on the victim's machine being executed. Such a URL could be placed in the .gitmodules file of a malicious project, and an unsuspecting victim could be tricked into running ‘git clone --recurse-submodules’ to trigger the vulnerability,” Git developers explained in their security advisory.
The Apache Software Foundation has also provided some details regarding how the security hole can be exploited in attacks targeting Subversion (SVN) users.
“A Subversion client sometimes connects to URLs provided by the repository. This happens in two primary cases: during 'checkout', 'export', 'update', and 'switch', when the tree being downloaded contains svn:externals properties; and when using 'svnsync sync' with one URL argument,” its advisory reads. “A maliciously constructed svn+ssh:// URL would cause Subversion clients to run an arbitrary shell command. Such a URL could be generated by a malicious server, by a malicious user committing to a honest server (to attack another user of that server's repositories), or by a proxy server.”
The developers of Git, Subversion and Mercurial have released patches and provided workarounds if available. The Git system is used by popular Linux distributions, which are also working on addressing the issue. GitLab has also released a fix for this vulnerability, which the organization has classified as “critical.”
While not all affected organizations rated the flaw as “critical,” Subversion developers have assigned it the highest severity rating. Schneeweisz explained in a blog post on Thursday that Subversion “was affected in the worst way.”
Malware campaign targets Russian-Speaking companies with a new Backdoor
11.8.2017 securityaffairs Virus
Trend Micro spotted a new espionage campaign that has been active for at least 2 months and that is targeting Russian-speaking firms with a new backdoor
Security experts at Trend Micro have spotted a new cyber espionage campaign that has been active for at least two months and that is targeting Russian-speaking enterprises delivering a new Windows-based backdoor, Trend Micro warns.
The hackers leverage on many exploits and Windows components to run malicious scripts to avoid detection. The last sample associated with this attack was uploaded to VirusTotal on June 6, 2017 and experts at Trend Micro observed five spam campaigns running from June 23 to July 27, 2017.
Hackers are targeting financial institutions and mining firms with different spear phishing messages.
The phishing messages are designed to appear as if they were sent from sales and billing departments and contain a weaponized Rich Text Format (RTF) file that exploits the CVE-2017-0199 flaw in Microsoft Office’s Windows Object Linking and Embedding (OLE) interface.
Once the exploit code is executed, it downloads a fake Excel XLS file embedded with malicious JavaScript. When opened, the Excel header is ignored and the file is treated as an HTML Application file by the Windows component mshta.exe.
“The exploit code downloads what is supposedly an XLS file from hxxps://wecloud[.]biz/m11[.]xls. This domain, to which all of the URLs used by this attack point to, is controlled by the attacker and was registered in early July.” states the analysis publiahed by Trend Micro.
“This fake Excel spreadsheet file is embedded with malicious JavaScript. The Excel header will actually be ignored and the file will be treated as an HTML Application file by mshta.exe, the Windows component that handles/opens HTA or HTML files.”
The JavaScript code calls the odbcconf.exe normal executable to run the DLL. Once executed, the DLL drops a SCT file (Windows scriptlet) in the %APPDATA% folder and appends the .TXT extension to it.
The DLL calls is used to power a Squiblydoo attack that leverages the Regsvr32 (Microsoft Register Server) to bypass restrictions on running scripts and evade application whitelisting protections such as AppLocker.
“This particular command uses the Regsvr32 (Microsoft Register Server) command-line utility, which is normally used to register and unregister OLE controls in the Windows registry, including DLL files. This attack method is also known as Squiblydoo—Regsvr32 is abused to bypass restrictions on running scripts.” continues the analysis. “It also means evading application whitelisting protections such as AppLocker. While Squiblydoo is already a known attack vector, this is the first time we’ve seen it combined with odbcconf.exe.”
In May, experts at FireEye spotted a new APT group that was targeting Vietnamese interests around the globe, the hackers leveraged the Squiblydoo technique to enable the download of a backdoor from APT32 infrastructure.
Next, the real backdoor is downloaded and executed, it is an XML file that is downloaded from the domain wecloud[.]biz. Also in this case, it is executed exploiting the same Regsvr32-abusing Squiblydoo attack technique.
“This is another SCT file with obfuscated JavaScript code that contains backdoor commands, which essentially allow attackers to take over an infected system. It attempts to connect to its C&C server at hxxps://wecloud[.]biz/mail/ajax[.]php and retrieve tasks to carry out, some of which are:
d&exec = download and execute PE file
gtfo = delete files/startup entries and terminate
more_eggs = download additional/new scripts
more_onion = run new script and terminate current script
more_power = run command shell commands
” reads the analysis.
Experts noticed that even if the attack chain appears complex, it starts leveraging a Microsoft Office exploit. The best defense still consists in patching and keeping software up-to-date.
Wikileaks – CIA CouchPotato remote tool can stealthy collect RTSP/H.264 video streams
11.8.2017 securityaffairs BigBrothers
WikiLeaks has published another Vault 7 leak, revealing the CIA tool CouchPotato that allows operators to remotely spy on video streams in real-time.
“Today, August 10th 2017, WikiLeaks publishes the the User Guide for the CoachPotato project of the CIA. CouchPotato is a remote tool for collection against RTSP/H.264 video streams. It provides the ability to collect either the stream as a video file (AVI) or capture still images (JPG) of frames from the stream that are of significant change from a previously captured frame. It utilizes ffmpeg for video and image encoding and decoding as well as RTSP connectivity. CouchPotato relies on being launched in an ICE v3 Fire and Collect compatible loader.” states Wikipedia.
The document leaked from the CIA details how the tool could be used by cyber spies to remotely capture RTSP/H.264 video streams.
The Real Time Streaming Protocol ( RTSP), is a network control protocol designed for controlling streaming media servers.
“CouchPotato is a remote tool for collection against RTSP/H.264 video streams. It provides the ability to collect either the stream as a video file (AVI) or capture still images (JPG) of frames from the stream that are of significant change from a previously captured frame. CouchPotato utilizes ffmpeg for video and image encoding and decoding as well as RTSP connectivity.” reads the user guide. “In order to minimize size of the DLL binary, many of the audio and video codecs along with other unnecessary features have been removed from the version of ffmpeg that CouchPotato is built with. pHash, an image hashing algorithm, has been incorporated into ffmpeg’s image2 demuxer to provide image change detection capabilities. CouchPotato relies on being launched in an ICE v3 Fire and Collectcompatible loader.”
CouchPotato
The CouchPotato tool utilizes FFmpeg for video and image encoding and decoding and Real Time Streaming Protocol connectivity.
The CouchPotato tool is hard to detect, it supports the file-less ICE v3 “Fire and Collect” loader, which is an in-memory code execution (ICE) technique.
The documents don’t include details on how the CIA operators compromise the target systems. It is likely the CouchPotato tool needs to be used in conjunction with other hacking tools to penetrate the targeted systems.
Below the list of release published by Wikileaks since March:
Couchpotato – 10 August, 2017
Dumbo– 03 August, 2017
Imperial – 27 July, 2017
UCL/RAYTHEON – 19 July, 2017
HighRise – 13 July, 2017
BothanSpy and Gyrfalcon – 06 July, 2017
OutlawCountry – 30 June, 2017
ELSA malware – 28 June, 2017
Cherry Blossom – 15 June, 2017
Pandemic – 1 June, 2017
Athena – 19 May, 2017
AfterMidnight – 12 May, 2017
Archimedes – 5 May, 2017
Scribbles – 28 April, 2017
Weeping Angel – 21 April, 2017
Hive – 14 April, 2017
Grasshopper – 7 April, 2017
Marble Framework – 31 March, 2017
Dark Matter – 23 March, 2017
Mysterious company is offering up to $250,000 for VM Hacks through a bug bounty
11.8.2017 securityaffairs Security
A mysterious company is offering up to $250,000 for virtual machine (VM) hacks. The “secret” bug bounty program was announced by Bugcrowd.
A mysterious company makes the headlines for offering up to $250,000 for virtual machine (VM) hacks. The “secret” bug bounty program was announced by the crowdsourced security testing platform Bugcrowd.
At the time I was writing the unique information available on the target is that it is an unreleased product.
The program is invitation-only, but anyone can apply for an invite, the organization will contact the final participants.
“Bugcrowd has an exciting opportunity to participate in a private, invite-only program with an undisclosed client, against an unreleased product – with rewards up to $250,000!” reads the announcement published on Bugcrowd.
Candidates must have specific skills on virtual environments, kernel and device driver security, firmware security, and advanced application security.

The hackers must focus their activities in:
Guest VM breakout/isolation failures
Code execution beyond the confines of your guest VM
Privilege escalation within the guest VM made possible by the underlying platform
Any vulnerabilities which could lead to compromise or leakage of data and directly affect the confidentiality or integrity of user data of which affects user privacy (including memory corruption, cross guest VM issues, persistent issues).
Denial/degrading service to other customers, or of the underlying platform itself (excluding DDoS)
Participants can earn between $5,000 and $250,000 for each vulnerability they will report, the duration of the bug bounty program is roughly of 8 weeks, it will start in September.
Bug bounty programs are becoming even more common in the IT security industry, VM hacks are among the issues considered more interesting by the experts. Last year, security experts earned $150,000 for or the hack of the VMware Workstation 12.5.1. reported at the hacking contest 2016 PwnFest held in South Korea at the 2016 Power Of Community (POC) security conference.
This year, during the Pwn2Own contest, the researchers at the Tencent Security’s Team Sniper earned $100,000 for a VMware Workstation exploit that could be exploited by attackers used to escape VMs.
Cyberattack Leaves Millions Without Mobile Phone Service in Venezuela
11.8.2017 securityweek Mobil
A massive cyberattack that took down government websites in Venezuela earlier this week also has left seven million mobile phone users without service, the government said Thursday.
A group that calls itself The Binary Guardians claimed responsibility for attacks that targeted the websites of the government, the supreme court and the National Assembly.
"These terrorist actions which affected the Movilnet's GSM platform on Wednesday left without communication seven of the state operator's 13 million users," Science and Technology Minister Hugbel Roa said.
Venezuela has two other private mobile phone operators: Spanish-owned Movistar and Digitel.
Roa said the outage was part of a wave of attacks that began Monday when dozens of government and private company websites were hacked.
Roa said there also have been nine cuts in the country's fiber optic network, which has cut off already precarious internet service to seven states.
"The attacks were carried out with the help of foreign agents, trying once again to disrupt our country's connectivity," Roa said, adding that an investigation was underway
Experts Who Hacked U.S. Air Force Earned $130,000
11.8.2017 securityweek BigBrothers
Hundreds of bug bounty hunters signed up for the U.S. Department of Defense’s “Hack the Air Force” initiative and they earned more than $130,000 for the vulnerabilities they reported.
Between May 30 and June 23, the Pentagon invited vetted researchers, members of the military and government civilians from the United States, the United Kingdom, Canada, Australia and New Zealand to take a crack at the Air Force’s networks. Hack the Air Force, hosted by the HackerOne platform, was the most open federal program to date.
A total of 272 hackers signed up and they submitted 207 valid vulnerability reports. The first flaw was reported in less than one minute of the bug bounty program’s launch.
The more than 200 vulnerabilities earned participants over $130,000, an average of $644 per flaw.
Only two of the white hat hackers who submitted valid reports were employed by the military. The researcher who earned the most was a 17-year-old who submitted 30 valid reports.
“Adversaries are constantly attempting to attack our websites, so we welcome a second opinion — and in this case, hundreds of second opinions — on the health and security of our online infrastructure,” said Peter Kim, CISO of the U.S. Air Force. “By engaging a global army of security researchers, we’re better able to assess our vulnerabilities and protect the Air Force’s efforts in the skies, on the ground and online.”
While the Hack the Air Force initiative is over, experts who find vulnerabilities in the organization’s systems can still report them to the Pentagon through its ongoing vulnerability disclosure program.
A total of 371 people registered for the previous Hack the Army program and they were awarded roughly $100,000 for 118 valid vulnerability reports. Hack the Pentagon received 138 valid submissions and it cost the U.S. government $150,000, half of which went to participants.
Unnamed Firm Offers $250,000 for VM Hacks
11.8.2017 securityweek Security
An unnamed company is prepared to offer up to $250,000 for virtual machine (VM) hacks as part of a “secret” bug bounty program, crowdsourced security testing platform Bugcrowd announced this week.
The program, which Bugcrowd has described as a hybrid approach, is invitation-only, but anyone can apply for an invite. White hat hackers who believe they have the necessary skills can send a submission and they will be contacted if they have been selected.
While the name of the company running this initiative has not been disclosed, Bugcrowd has revealed that the target is an unreleased product.
The ideal applicant for this program is someone skilled in the areas of virtualization, kernel and device driver security, firmware security, and advanced application security.
Focus areas include guest VM breakout, code execution outside the guest VM, privilege escalation within the guest via the underlying platform, flaws that could result in data leakage (e.g. memory corruption, cross-guest VM issues), and disruption of service to other customers (excluding DoS attacks).
Finding these types of security issues can earn participants between $5,000 and $250,000. The hackers who submit one of the best five reports describing their efforts, attempts, ideas for potential compromise, and other relevant information will be rewarded $10,000.
The bug bounty program will run for a period of roughly 8 weeks, between early September and late October.
It’s not uncommon for companies to pay out significant rewards for VM hacks. Last year, researchers earned $150,000 at a hacking competition in South Korea for finding serious vulnerabilities in VMware Workstation and Fusion.
At ZDI’s Pwn2Own contest, Tencent Security’s Team Sniper earned $100,000 for a VMware Workstation exploit that could be used to escape VMs.
Microsoft also announced recently that it’s prepared to pay up to $250,000 for critical vulnerabilities found in its Hyper-V hypervisor on Windows 10.
Google Pays $10,000 Bug Bounty to High School Student
11.8.2017 securityweek Security
Uruguayan high school student Ezequiel Pereira, who has aspirations of becoming a security researcher one day, has been awarded $10,000 for discovering and reporting a vulnerability in Google’s App Engine server.
While poking around App Engine by changing the Host header in requests sent to the server (*.appspot.com) – in an attempt to get access to internal App Engine apps (*.googleplex.com), Pereira stumbled upon a website that had no security measure in place.
Users accessing apps on googleplex.com are usually required to go through the MOMA login page, which acts as a proxy called “ÜberProxy.”
According to the student, who was using Burp for this endeavor because it allows to easily change the Host header and see the result, most of his attempts to access App Engine apps failed. The server was either returning a 404 Not Found error or was checking whether the request was coming from a Googler account ("username@google.com") instead of a normal Google account.
Eventually, however, he stumbled upon yaqs.googleplex.com, where no username check was performed and where other security measures also appeared to be lacking.
“The website's homepage redirected me to ‘/eng’, and that page was pretty interesting, it had many links to different sections about Google services and infrastructure, but before I visited any section, I read something in the footer: ‘Google Confidential’,” Pereira explains.
Immediately after discovering the issue, the student retraced the steps to make sure it could be reproduced, and then reported the vulnerability to Google, without further poking at the website.
To reproduce the bug using Burp, one would have to go to the Repeater tab, set the target host to "www.appspot.com" and the target port to "443," then check the "Use HTTPS" option, write a raw HTTP request: GET /eng HTTP/1.1
Host: yaqs.googleplex.com
(the request also includes two empty lines at the end), and hit Go.
By exploiting the vulnerability, an attacker could access “an internal Google website,” the student alleges.
The report was immediately confirmed by Google as valid, and the company informed Pereira several weeks later that he was awarded $10,000 for the discovery. Apparently, Google discovered a “few variants [of the exploit] that would have allowed an attacker access sensitive data,” which explains the high reward amount.
Disjointed Tools Challenge Security Operations: Survey
11.8.2017 securityweek Security
Insufficient staffing levels and quality, together with poor orchestration between too many security point products mean that complete breach intolerance is an aspiration not currently achieved by today's security operations centers (SOCs).
This is the conclusion of a new study by Forrester Consulting, commissioned by Endgame, a provider of enterprise threat protection solutions. Forrester surveyed a small number (156) of senior security decision makers (directors, C-Suite and VPs) in US companies with more than 1000 employees (84% have more than 5000 employees). The survey was conducted in May 2017.
'Complete breach intolerance' is defined as stopping all attacks before there is damage to systems or data loss. Breach statistics, however, show how difficult this will be. Of the companies surveyed, 92% have suffered at least one successful breach in the last year. One-third have suffered more than 20 breaches; and one-in-eight have suffered more than 50 successful breaches.
Currently unable to prevent all breaches, 64% of the organizations fear that the next breach could be the big one; or at least, it could be 'somewhat to significantly severe'. The two biggest fears are that it could lead to a loss of revenue, and brand damage. "We have a large presence in our community," said the CISO of a US banking company; "if we had a major breach, it would really be detrimental to our brand. Our reputation would be ruined for the most part."
SOCs are considered an important route to preventing this and improving breach intolerance. Seventy-six percent of the organizations already operate a SOC, with another 17% planning to deploy one in the next 12 months. However, adequately staffing a SOC remains a challenge. Looking at current staffing, only one position (malware engineer) is filled in more than 50% of the organizations. Only 44% of organizations have a Tier 1 analyst; 35% have a SIEM engineer; and only 24% have a forensics specialist. Perceived staff proficiency levels are even worse: 26% for the analyst; and 29% for the SIEM engineer and the forensics specialist.
Given the staffing issues, greater reliance has to be placed on the technology itself. However, inadequate and disjointed tools are a problem. Seventy-one percent of the respondents are using five or more technologies in their SOC, and one-third are using eight or more technologies. "What I'd like to do is reduce the overall risk footprint," said the CISO of a global energy company, "thus being able to reduce the number of tools. There's a lot of work that we're doing to try to reduce overlap of tools."
The primary purpose in reducing the number of tools is to streamline detection and lower false positives. "Lowering our false positives lowers our head count because we don't need as many people watching. That saves us money," said one of the respondents.
"Alert fatigue is a challenge," said another. "If my staff had time to take a look at our architecture, we would be able to reduce the number of tools that we had, or number of providers we had, and really look at things from a holistic approach and not a point solution-type approach. We would reduce the number of vendors we're using, which then in turn would reduce the alerts or reduce that fatigue."
Organizations are looking to reduce their vulnerabilities as well as build more automation between endpoint prevention, detection, and response capabilities, and they are using continuous monitoring to stop advanced threats, says Forrester. Other ways they are improving their strategy is by integrating endpoint security with network security for reduced operational friction.
Despite the challenges, Forrester believes that complete breach intolerance should still be sought. To achieve this, it says, "It is necessary to equip the SOC team with the right tools and skills." To achieve this, it offers four primary recommendations.
The first is the reverse of much current thinking. Since breaches will happen, recent advice has been to concentrate on detection (incident response) over prevention. However, SOCs are currently stretched by the detection alerts they need to triage. "The best way to efficiently achieve complete breach intolerance," suggests Forrester, "is to build a strong layer of prevention-focused controls to lower your organization's attack surface in the first place. This will lower the number of incidents that your SOC staff need to deal with and reduce the 'noise' seen by detection-focused tools."
The second is to reduce internal friction through integrated endpoint prevention, detection and remediation. "If you don't establish a solid foundation of automation and orchestration," it warns, "blind investments in prevention and detection likely won't have the intended effect and will leave you more vulnerable."
The third is to extend detection capabilities beyond static indicators of compromise, such as malware signatures. "Given the prevalence of fileless attacks and novel attack methods utilizing legitimate software, your detection capabilities must go beyond malicious file and process detection... Prioritize tools that include behavior-based detection from a process and user perspective."
The final recommendation is to advance staff skillsets. "While technology is not a substitute for people, you can only maximize it when you have staffed your team appropriately with skilled and trained resources. Remember," it says, "attackers learn new techniques and methodologies for compromising your environment; your defenders should be learning as well."
Kaspersky Details APT Trends for Q2 2017
11.8.2017 securityweek APT
While continuing to deploy their usual set of hacking tools onto compromised systems, advanced persistent threat (APT) actors were observed using leveraging zero-day vulnerabilities and quickly adopting new exploits during the second quarter of 2017, Kaspersky Lab reports.
According to the security company’s APT Trends report Q2 2017, threat actors such as Sofacy and Turla were observed using zero-day exploits targeting Microsoft’s Office and Windows products. The BlackOasis group too was associated with a zero-day that was quickly adopted by OilRig, while the Lazarus sub-group BlueNoroff adopted the National Security Agency-associated EternalBlue exploit.
In March and April, security researchers discovered three zero-day flaws the Sofacy and Turla Russian-speaking threat actors had been using in live attacks. Sofacy was associated with two vulnerabilities targeting Microsoft Office’s Encapsulated PostScript (CVE-2017-0262) and a Microsoft Windows Local Privilege Escalation (CVE-2017-0263), while Turla was targeting a different Office Encapsulated PostScript bug (CVE-2017-0261).
Both actors were observed dropping their usual payloads, namely GAMEFISH (Sofacy) and ICEDCOFFEE, also known as Shirime (Turla). The actors continued to target foreign ministries, governments, and other government-affiliated organizations in their attacks, Kaspersky reveals.
Sofacy was also seen experimenting with two new macro techniques, one leveraging the built-in ‘certutil’ utility in Microsoft Windows to extract a hardcoded payload within a macro, while the other was based on embedding Base64-encoded payloads within the EXIF metadata of malicious documents. Turla was observed using fake Adobe Flash installers for malware delivery.
In June, the BlackEnergy Russian-speaking actor launched the destructive NotPetya attack targeting organizations relying on the MEDoc software. Focused mainly on companies in Ukraine, the attack eventually hit around 65 countries worldwide, including Belgium, Brazil, France, Germany, India, Russia, and the United States.
The second quarter of the year also brought to the spotlight the activity of a cyber-espionage group called Longhorn. Revealed via Vault 7 files published by WikiLeaks, the group had been tracked by Kaspersky since 2014. The firm discovered at least three families of tools associated with the actor, and calls them Gray Lambert, Red Lambert, and Brown Lambert.
The malware can “orchestrate multiple sniffer victims on a network via broadcast, multicast, and unicast commands, allowing the operators to employ surgical precision in networks with many infected machines. The sniffers double as next-stage payload delivery mechanisms for an infected network. A notable feature of the Lambert campaigns is the level of precision with which targets are chosen; Gray Lambert’s victimology is primarily focused on strategic verticals in Asia and Middle East,” Kaspersky says.
A global malware attack that caught everyone’s attention in May was WannaCry, and security researchers eventually linked the attack to North Korea-tied Lazarus group (specifically, the sub-group called BlueNoroff, which is currently using the Manuscrypt backdoor to target financial organizations).
WannaCry was leveraging the EternalBlue exploit that ShadowBrokers made public in April (after Microsoft patched it in March) and which was supposedly stolen from the NSA-linked Equation group. WannaCry was accidentally stopped by a British researcher currently under arrest in the U.S. for his alleged involvement in the development and distribution of Kronos banking Trojan.
Another zero-day exploit (CVE-2017-0199) discovered in the second quarter of the year had been actively used by BlackOasis, a Middle Eastern actor observed using other zero-days in the past as well, and associated with the ‘lawful surveillance’ kit FinSpy. Soon after CVE-2017-0199 became public, another Middle Eastern actor adopted it, namely OilRig, which has been targeting organizations in Israel.
Other actors have been active during the second quarter of the year as well, including Chinese-speaking threat groups, but they continued to use their known tools in previously established manners. However, a new piece of MacOS malware called Demsty and targeting University researchers in Hong Kong, among others, did emerge in the timeframe (but Kaspersky isn’t yet certain that a Chinese-speaking actor is behind it).
Kaspersky also mentions the ShadowBrokers group in their APT report, referring to their activity of “dumping multiple tools and documentation allegedly stolen from Equation Group.” In April, the group leaked information suggesting that the NSAs had penetrated the SWIFT banking network to monitor the activity of various Middle East banks.
CouchPotato: CIA Hacking Tool to Remotely Spy On Video Streams in Real-Time
10.8.2017 thehackernews BigBrothers
After disclosing CIA's strategies to hijack and manipulate webcams and microphones to corrupt or delete recordings, WikiLeaks has now published another Vault 7 leak, revealing CIA's ability to spy on video streams remotely in real-time.
Dubbed 'CouchPotato,' document leaked from the CIA details how the CIA agents use a remote tool to stealthy collect RTSP/H.264 video streams.
Real Time Streaming Protocol, or RTSP, is a network control protocol designed for use in entertainment and communication systems for controlling streaming media servers.
CouchPotato gives CIA hackers ability to "collect either the stream as a video file (AVI) or capture still images (JPG) of frames from the stream that are of significant change from a previously captured frame," a leaked CIA manual reads.
The tool utilises FFmpeg for video and image encoding and decoding and Real Time Streaming Protocol connectivity.
The CouchPotato tool works stealthily without leaving any evidence on the targeted systems because it has been designed to support ICE v3 "Fire and Collect" loader, which is an in-memory code execution (ICE) technique that runs malicious code without the module code being written to the disk.
However, neither Wikileaks nor the leaked user guide details how the agency penetrates into the targeted systems at the first place, but since the publication has previously leaked many CIA malware, exploits and hacking tools to get into a network, the agency might have been using CouchPotato in combining with other tools.
Previous Vault 7 CIA Leaks
Since March, WikiLeaks has published 20 batches of "Vault 7" series, which includes the latest and last week leaks, along with the following batches:
Imperial — Details of at least 3 CIA-developed hacking tools and implants designed to target PCs running Apple Mac OS X and different flavours of Linux operating systems.
UCL/Raytheon — An alleged CIA contractor, which analysed in-the-wild malware and hacking tools and submitted at least five reports to the agency for help the CIA developed its own malware.
Highrise — An alleged CIA project that let the spying agency stealthy collects and forwards stolen data from compromised smartphones to its server via SMSes.
BothanSpy and Gyrfalcon — 2 alleged CIA implants that let the CIA intercept and exfiltrate SSH credentials from targeted Windows and Linux PCs using different attack vectors.
OutlawCountry – An alleged CIA project that allowed the spying agency to hack and remotely spy on systems running Linux OS.
ELSA – Alleged CIA malware that tracks geo-location of targeted computers and laptops running the Microsoft Windows OS.
Brutal Kangaroo – A tool suite for Microsoft Windows OS used by the CIA agents to target closed networks or air-gap computers within an organisation or enterprise without requiring any direct access.
Cherry Blossom – A framework employed by the agency to monitor the Internet activity of the targeted systems by exploiting flaws in Wi-Fi devices.
Pandemic – A CIA's project that allowed the spying agency to turn Windows file servers into covert attack machines that can silently infect other PCs of interest inside the same network.
Athena – A spyware framework that the agency designed to take full control over the infected Windows systems remotely and works against every version of Windows OS–from Windows XP to Windows 10.
AfterMidnight and Assassin – 2 alleged CIA malware frameworks for the Microsoft Windows platform that's meant to monitor and report back actions on the infected remote host PC and execute malicious actions.
Archimedes – Man-in-the-middle attack tool reportedly developed by the CIA to target computers and laptops inside a Local Area Network (LAN).
Scribbles – Software supposedly designed to embed 'web beacons' into confidential files and documents, allowing the CIA to track insiders and whistleblowers.
Grasshopper – A framework that allowed the spying agency to quickly create custom malware for breaking into Microsoft Windows OS and bypassing antivirus protection.
Marble – Source code of a secret anti-forensic framework used by the CIA agents to hide the actual source of its malware.
Dark Matter – Hacking tools the spying agency used to target iPhones and Macs.
Weeping Angel – Spying tool used by the CIA to infiltrate smart TVs, and transforming them into covert microphones.
Year Zero – CIA hacking tools and exploits for popular hardware and software.
Engineering Firm Exposed Electrical Infrastructure Details: Researchers
10.8.2017 securityweek ICS
Misconfiguration Issues with systems operated by Texas-based electrical engineering operator Power Quality Engineering (PQE) resulted in the information of various clients being exposed to the Internet, along with sensisitve corprorate information from PQE itself, UpGuard security researchers warn.
A port configured for public access and used for rsync server synchronization exposes data of clients such as Dell, the City of Austin, Oracle, and Texas Instruments, among others. A browser is all that an interested actor would need to access and download sensitive electrical infrastructure data that PQE inspectors examining customer facilities have compiled into reports, the researchers say.
Using a cyber risk scoring system developed by UpGuard, PQE was rated 181 out of a possible 950 when the data exposure was discovered. Thus, the company says, PQE "presents a number of potentially damaging attack vectors with this exposure.”
Not only does the incident reveal additional potential weak points in customer electrical systems, but publicly downloadable schematics could provide attackers with information on the “specific locations and configurations of government-operated top secret intelligence transmission zones within at least one Dell facility.”
In addition to the exposed customer data, the repository also contained a plain text file of internal PQE passwords, which provided potential attackers with further access to the company’s systems.
“This exposure illustrates several pertinent and common issues driving the spread of cyber risk today. The configuration of PQE’s rsync process to allow public access through an open port is an all too common state of affairs in IT environments. While IT personnel can restrict port access to only authorized PQE employees, such measures can easily be forgotten without processes in place to ensure security gaps are identified and closed immediately,” UpGuard says.
The data exposure was discovered after UpGuard Director of Cyber Risk Research Chris Vickery stumbled upon an open port configured to accept packets at an IP address that “returned a fully downloadable data repository originating from Power Quality Engineering.”
The repository contains folders such as “Clients,” “User,” and “Intuit,” yet the security researchers don’t know its actual size, despite downloading a 205 GB portion of data from it. The issue was discovered on July 6, 2017, and PQE secured its systems on July 8, after receiving notification from UpGuard.
The systems were accessible through port 873, which is used for command line utility rsync (remote synchronization) by default. To secure the data accessible through the port, a network admin would have to restrict the IP addresses that are allowed to access the port, using rsync’s “hosts allow/deny” functions. However, this option can be missed, as it requires an extra step when the utility is configured.
Because of this oversight, the PQE repository was able to be downloaded by anyone connecting to the unprotected IP address. The security researchers even discovered that the “Clients” folder in the main repository includes directories titled with the names of well-known corporations and public-sector organizations in Central Texas, including computer manufacturer Dell, software maker Oracle, telecom carrier SBC, and semiconductor manufacturers Freescale (now owned by NXP) and Texas Instruments, among others.
The exposed data includes reports and infrared imagery of weaknesses in clients’ power infrastructures, which were discovered and evaluated by PQE inspectors. “Such infrared studies and their associated reporting reveal, with high levels of specificity, energy infrastructure inspection results of clients like HealthSouth Rehabilitation Hospital of Austin,” the researchers explain.
One of the discovered folders was found to contain a document labeled “Director of Central Intelligence Directive No. 6/9,” which included details on Sensitive Compartmented Information Facility, or “SCIF”, which are secure rooms used by security-cleared individuals to receive sensitive information. Such rooms were designed in such a manner that external surveillance, eavesdropping, or interception information in the room was as difficult as possible.
The exposed documents revealed the precise location of such a SCIF in a Dell facility in central Texas. “The documents confirm the exquisitely stringent standards for the construction of such a room, complying with TEMPEST-level security standards for any acoustical or radio transmissions, and extending to such detailed specifications as the construction of intrusion-defeating air ducts surrounding the SCIF,” UpGuard notes.
Exposed data for other clients included schematics of solar fields, electrical gap analyses, proposals for future construction, inspection reports of aviation breakers at local airfields, maintenance reports for municipal fuel systems, and a “Hazardous Operations Report,” all pertaining to the City of Austin.
The security researchers also suggest that clients might have been further exposed, considering that a document in the repository’s “User” folder contained a number of plaintext PQE passwords, including at least one password for PQE’s GoDaddy account. The firm’s website could have been accessed and exploited to funnel visitors into a watering hole attack, the researchers suggest.
“The PQE data exposure presents a uniquely varied illustration of the many attack vectors a malicious actor can take in 2017 to exploit the sensitive data of enterprises for their own purposes. Of prime importance, however, is the process error which resulted in the data being exposed in the first place: the configuration of the rsync port to be open to public access,” UpGuard points out.
Experts found a link between the KONNI attacks and DarkHotel campaigns against NK
10.8.2017 securityaffairs APT
Experts at Cylance noticed that the decoy document used in KONNI attacks is similar to the one used in recent campaigns of the DarkHotel APT.
In May, Cisco Talos team discovered a RAT dubbed KONNI malware that targets organizations linked to North Korea.
The malware, dubbed by researchers “KONNI,” was undetected for more than 3 years and was used in highly targeted attacks. It was able to avoid detection due to a continuous evolution, the recent versions capable of executing arbitrary code on the target systems and stealing data.
“Talos has discovered an unknown Remote Administration Tool that we believe has been in use for over 3 years. During this time it has managed to avoid scrutiny by the security community. The current version of the malware allows the operator to steal files, keystrokes, perform screenshots, and execute arbitrary code on the infected host. Talos has named this malware KONNI. ” states the analysis published by Talos.
The malware has evolved over the years and its last release is able to log keystrokes, steal files, capture screenshots, and collect information about the infected system.
The KONNI malware was also spotted in at least two campaigns in 2017. Threat actors used a decoy document titled “Pyongyang e-mail lists – April 2017” and it contained the email addresses and phone numbers of individuals working at organizations such as the United Nations, UNICEF and embassies linked to North Korea.
Hackers also used a second decoy document, titled “Inter Agency List and Phonebook – April 2017” contained names and contact information for members of agencies, embassies and other organizations linked to North Korea.
Experts at Cylance noticed that the decoy document titled “Pyongyang e-mail lists – April 2017, presents many similarities with a document used in a recent campaign that experts at Bitdefender linked to DarkHotel.
The first Darkhotel espionage campaign was spotted by experts at Kaspersky Lab in late 2014, according to the researchers the APT group has been around for nearly a decade while targeting selected corporate executives traveling abroad.
According to the experts, threat actors behind the Darkhotel campaign aimed to steal sensitive data from executives while they are staying in luxury hotels, the worrying news is that the hacking crew is still active.
The attackers appeared high skilled professionals that exfiltrated data of interest with a surgical precision and deleting any trace of their activity. The researchers noticed that the gang never go after the same target twice.
According to the security firm Bitdefender, the DarkHotel APT is back and it is targeting government employees with an interest in North Korea with new techniques.
The hackers’ victims have been discovered in several countries, including North Korea, Russia, South Korea, Japan, Bangladesh, Thailand, Taiwan, China, the United States, India, Mozambique, Indonesia and Germany.
The new DarkHotel campaign dubbed “Inexsmar” leveraged on documents quite similar to the ones used in the KONNI attacks, the content has the same format and they have the same title.

Looking at the files’ description it is possible to notice that they are both titled “Pyongyang directory” and they were both authored by “Divya Jacob.”

Experts at Cylance who analyzed the KONNI malware believe that the malware’s authors once discovered due to their revelations will switch tactic and will release new variants that will include better obfuscation capabilities.
“The KONNI malware is a relatively new RAT. The implemented features are straightforward to analyze and there has been little attempt to mask the malware’s true purpose. The basic features for a backdoor are all present, including host profiling and remote access and control. ” concluded Cylance.
“Given the recent attention, we expect to see new variants surface in the coming months with better obfuscation and perhaps additional capabilities.”
Chinese Quantum Satellite Sends First ‘Unhackable’ Data to Earth
10.8.2017 thehackernews IT
In what appears to be the world's first quantum satellite transmission, China has successfully sent an "unbreakable" code over a long distance from an orbiting satellite to the Earth, achieving a milestone in the next generation encryption based on "quantum cryptography."
In August last year, China launched the world's first quantum communication satellite into the Earth’s orbit aboard a Long March-2D rocket to test the fundamental laws of quantum mechanics at space.
Dubbed Quantum Science Satellite, nicknamed Micius or Mozi (Chinese: 墨子), the satellite was designed to establish a 'Hack-Proof' communications system in this age of global surveillance by transmitting unbreakable encryption keys from space to the ground.
Now, it has been reported that using this satellite, the Chinese scientists at the Quantum Experiments at Space Scale (QUESS) project were able to send secret "quantum key distribution" (QKD) data by beaming photons from the space to the ground stations over longer distances than ever before.
The Chinese scientists successfully sent quantum keys over a distance of 1,200 Km (745 miles) from space to Earth at a transmission rate up to 20 of magnitudes more efficient than that expected using an optical fibre of the same length, lead scientist Pan Jianwei told the official Xinhua news agency.
"That, for instance, can meet the demand of making an absolute safe phone call or transmitting a large amount of bank data," Jianwei said.
The Quantum Science Satellite could become the world's first transcontinental quantum key distribution network of its kind and China hopes to erect a global quantum cryptography-based communications network in 2030.
Theoretically, the use quantum cryptography for encryption is secure against any interception, as the information is encoded in a quantum particle in a way that it'll be destroyed as soon as the system detects any intrusion attempts.
"Satellite-based quantum key distribution can be linked to metropolitan quantum networks where fibres are sufficient and convenient to connect numerous users within a city over 100 km," Jianwei said.
"We can thus envision a space-ground integrated quantum network, enabling quantum cryptography- most likely the first commercial application of quantum information- useful at a global scale."
China has largely been ambitious to realise the importance of Quantum technology that's believed to be a new era of faster and more powerful super computers.
From past two decades, Quantum technology has been a top strategic focus in China's 5-year economic development plan. While the U.S. invested about $200 Million a year in quantum research, China spent $101 Billion in quantum physics in 2015.
How Top Companies Accidentally Leaking Terabytes of Sensitive Data Online
10.8.2017 thehackernews Incindent
An anti-malware detection service provider and premium security firm has been accused of leaking terabytes of confidential data from several Fortune 1000 companies, including customer credentials, financial records, network intelligence and other sensitive data.
However, in response to the accusations, the security firm confirmed that they are not pulling sensitive files from its customers; instead, it's up to companies—who are accidentally (but explicitly) sharing their sensitive data to leverage an optional cloud-based anti-malware service.
On Wednesday, Information security firm DirectDefense published a blog post, claiming that they found a major issue with endpoint detection and response (EDR) solution offered by US-based company Carbon Black, alleging that the company is leaking hundreds of thousands of sensitive files from its customers.
Carbon Black is a leading incident response and threat hunting company that offers security products to nearly thirty of the largest 100 public and privately held companies in the US, including Silicon Valley leaders in internet search, social media, government, and finance.
DirectDefense Claims 'Carbon Black' Leaking Data
According to DirectDefense, the company's CB Response is responsible for leaking a massive amount of its customers' data—from cloud keys and app store keys to credentials and other sensitive trade secrets—due to its dependence on third-party multi-scanner services.
Carbon Black specialises in next-generation antivirus plus endpoint detection and response (EDR) solutions in one cloud-delivered platform that stops malware and other cyber attacks.
The product works by identifying "good" and "bad" files and then creating their whitelist to prevent its clients from running harmful files on their systems. So, the tool continuously evaluates an enormous and ever-expanding pool of files for a potential infection.
DirectDefence claims whenever the tool encounters a new file on its clients' computer that it has never seen before, it first uploads the file to Carbon Black servers, and then company forwards a copy of that file to VirusTotal multiscanner service (owned by Google) that contains dozens of antivirus engines to check if the file is good or bad.
But according to DirectDefense President Jim Broome:
"Cloud-based multi-scanner service [VirusTotal] operate as for-profit businesses. They survive by charging for access to advanced tools sold to malware analysts, governments, corporate security teams, security companies, and basically whomever is willing to pay."
So, anyone who is willing to pay would get access to the multiscanner and eventually access to the files submitted to its database.
Broome called the scheme as "the world's largest pay-for-play data exfiltration botnet."
Broome says he discovered this issue in mid-2016 when his company was working on a potential breach on its client’s computer.
While using the VirusTotal cloud-based multi-scanner to search for a possible piece of malware which it suspected of infecting its client, his staff came across a batch of internal applications belonging to a "very large telecommunications equipment vendor."
After digging deeper, the team discovered that the files were uploaded by Carbon Black, as identified by its unique API key (32d05c66). Once the team had that primary key, it was able to locate "hundreds of thousands of files comprising terabytes of data."
"We downloaded about 100 files (we found JAR files and script files to be the easiest to analyse by script), and ran these files through some simple pattern matching," Broome writes.
"When we got hits, we’d try to extrapolate where they came from. We were not trying to be exhaustive in the analysis, and only repeated this operation a few times to see if it still held true."
DirectDefense Found Sensitive Data Leaked From Top Companies
Broome says he identified three companies to whom the files his team downloaded belonged, though he doesn't disclose the names of the affected companies.
Here is some information DirectDefense revealed about the three affected companies:
Large Streaming Media Company
The first company was a large streaming media firm, and files associated with this company contained, among other sensitive files:
Amazon Web Services (AWS) Identity and Access Management (IAM) Credentials
Slack API Keys
The Company’s Crowd (Atlassian Single Sign On)
Admin Credentials
Google Play keys
Apple Store ID
Social Media Company
The second company was a social media company, and files associated with this firm included:
Hardcoded AWS and Azure keys
Other internal proprietary information, like usernames and passwords
Financial Services Company
The third firm is a financial services provider, for which researchers discovered:
Shared AWS keys that granted access to customer financial data
Trade secrets that included financial models and possibly direct consumer data
"Our intention with releasing this information was not to attack customers or security vendors," Broome writes, and we don’t pretend that we’ve performed an exhaustive analysis of the breadth of the leaks. We only know that every time we looked, we found this same serious breach of confidentiality."
Carbon Black Explains the Origin of Data Leak
However, in response to DirectDefence allegations, Carbon Black Co-founder and CTO Michael Viscuso published a blog post today explaining that their CB Response tool doesn't upload all files automatically to VirusTotal; instead, the feature comes disabled by default, leaving the choice to users to use its multiscanner service.
"Cb Response has a feature that allows customers to send their unknown or suspicious binaries to these cloud-based multi-scanners (specifically VirusTotal) automatically," Viscuso writes.
"We allow customers to opt into these services and inform them of the privacy risks associated with sharing."
"If the customer enables the second option (complete binaries with VirusTotal) Cb Response ensures that the customer understands the risks associated with uploading full binaries to a public multi-scanner service with an explicit warning"
This means, at first place, top-notch companies are accidentally (but explicitly) leaking their sensitive files on VirusTotal database.
Broome also suspects that this issue is not unique to Carbon Black, other EDR providers may also be leaking its customers' data in the same way.
Malware Encoded Into DNA Hacks the Computer that Reads It
10.8.2017 thehackernews Virus
Do you know — 1 Gram of DNA Can Store 1,000,000,000 Terabyte of Data for 1000+ Years?
Even in March this year, a team of researchers successfully stored digital data — an entire operating system, a movie, an Amazon gift card, a study and a computer virus — in the strands of DNA.
But what if someone stores a malicious program into the DNA, just like an infected USB storage, to hijack the computer that reads it.
A team of researchers from the University of Washington in Seattle have demonstrated the first successful DNA-based exploit of a computer system that executes the malicious code written into the synthesised DNA strands while reading it.
To carry out the hack, the researchers created biological malware and encoded it in a short stretch of DNA, which allowed them to gain "full control" of a computer that tried to process the genetic data when read by a DNA sequencing machine.
The DNA-based hack becomes possible due to lack of security in multiple DNA processing software available online, which contains insecure function calls and buffer overflow vulnerabilities.
"We analysed the security of 13 commonly used, open source programs. We selected these programs methodically, choosing ones written in C/C++," reads the research paper [PDF], titled "Computer Security, Privacy, and DNA Sequencing: Compromising Computers with Synthesized DNA, Privacy Leaks, and More."
"We found that existing biological analysis programs have a much higher frequency of insecure C runtime library function calls (e.g., strcpy). This suggests that DNA processing software has not incorporated modern software security best practices."
To create the biological malware, the researchers translated a simple computer program into a short stretch of 176 DNA letters, denoted as A, G, C, and T, each representing a binary pair (A=00, C=01, G=10, T=11).
The exploit took advantage of a basic buffer overflow attack, in which a software program executes the malicious command because it falls outside maximum length.
The command then contacted a server controlled by the team, from where the researchers took control of a computer in their laboratory they were using to analyse the DNA file.
"Our exploit did not target a program used by biologists in the field; rather it targeted one that we modified to contain a known vulnerability," the researchers said.
Although this kind of hack probably doesn't pose any threat anytime soon, the team warned that hackers could in future use fake blood or spit samples to gain access to computers, steal information, or hack medical equipments installed at forensic labs, hospitals and the DNA-based data storage centers.
The researchers will be presenting this first "DNA-based exploit of a computer system" at the next week's Usenix Security Symposium in Vancouver. For the more in-depth explanation on the DNA-based hack, you can head on to the research paper.
Free Access to Legal Docs Provided by Flaw in PACER Court System
10.8.2017 securityweek Vulnerebility
A vulnerability found in the Public Access to Court Electronic Records (PACER) system operated by the Administrative Office of the U.S. Courts could have been exploited by hackers to access legal documents through the accounts of legitimate users.
PACER is an online public access service that allows users to upload and download case and docket information from federal appellate, district and bankruptcy courts. PACER charges $0.10 per page and users are billed every quarter.
The Free Law Project discovered that the system was affected by a cross-site request forgery (CSRF) vulnerability that could have been leveraged to download content from PACER without getting billed for it.
CSRF vulnerabilities are highly common, but that does not make them any less dangerous. The lack of CSRF protection on a website allows other pages opened in the same web browser to interact with the unprotected site.
In the case of PACER, a hacker could have obtained docket reports and other documents at no cost by getting a legitimate user to visit a malicious website while being logged in to the court system. The legitimate user would get billed for the files downloaded by the attacker.
“For users of PACER, unpaid fees can result in damage to their credit, and debt collectors sent to their door at the behest of the AO. They would never know why their PACER bill skyrocketed,” the organization said in a blog post. “For the Administrative Office of the courts, this vulnerability could create chaos in their billing department, and could badly damage the reputation of the organization.”
Free Law Project also believes attackers may have been able to exploit the flaw to upload documents on behalf of lawyers via PACER’s Case Management/Electronic Case Files (CM/ECF) system, but the Administrative Office of the U.S. Courts claimed it was not possible.
“The PACER/ECF system has an annual revenue of around $150M/year, and has around 1.6M registered users. At this scale, this type of vulnerability is extremely troubling,” Free Law Project said. ”Cross site request forgeries are not novel and do not require sophisticated hackers or researchers to discover. We identified this problem while gathering data from PACER, not while attempting to hack it or to research vulnerabilities.”
Free Law Project initially said it was “quite possible” the vulnerability had been exploited in the wild, but in a blog post published on Wednesday it clarified that it has no knowledge of the flaw being exploited. A proof-of-concept (PoC) exploit is available on the organization’s website.
The vulnerability was discovered and reported in mid-February and it was patched by all jurisdictions earlier this month.
Most Web Services Don't Care How Weak Your Password Is
10.8.2017 securityweek Security
Password Strength Not Enforced by Popular Websites
GoDaddy has the best password policy among consumer websites; Netflix, Pandora, Spotify and Uber have the worst. This is the finding of a new study into the password practices that different companies encourage or force onto their users.
Dashlane, developer of the Dashlane password manager app that can synchronize passwords across all platforms, has published the findings of its 2017 Password Power Rankings study. It used five researchers to examine the password security criteria of 37 popular consumer sites, and 11 popular enterprise sites. Each site was given one point for each of five good practice criteria.
The criteria tested were password length (that is, at least 8 characters); a required mix of alpha and numeric characters; a password strength assessment tool (such as a color-coded or measurement bar); brute-force challenge or account locking (after ten false logins); and an MFA option. Three points out of the maximum five are considerate to be 'adequate' for the minimum threshold for good password security.
Dashlane accepts that password choice is the responsibility of end users, but believes that the service websites also have a responsibility to help the user. "It's our job as users to be especially vigilant about our cybersecurity, and that starts with having strong and unique passwords for every account," said Dashlane CEO Emmanuel Schalit. "However, companies are responsible for their users, and should guide them toward better password practices."
Of the 37 consumer sites examined, only GoDaddy received a 5/5 score. A further 19 sites are deemed adequate, with either 3 or 4 out of 5. At the top end, this includes many of the sites that could be expected to do well: Apple, Microsoft, PayPal and Skype. Only just adequate includes Facebook, Google, Reddit, Slack, Snapchat, WordPress and Yahoo.
More worrying, however, are those that failed. Amazon, eBay, and Twitter were among those scoring just two points. Dropbox, Evernote and Pinterest scored only one point; and of course, Netflix scored zero.
There is a similar divergence of scores among the enterprise websites. Only Stripe and QuickBooks got top marks, with Basecamp and Salesforce gaining a credible four points. GitHub, MailChimp and SendGrid are 'adequate' with three points. DocuSign and MongoDB (mLab) scored a disappointing two points; while, worryingly, Amazon Web Services and Freshbooks scored only one point.
It should be stressed that this survey relates only to the way in which the service provider helps the user in password choice and use -- it says nothing about the overall security posture of the website itself (for example, whether behavioral access controls are implemented internally and operated passively). Nevertheless, user credentials are frequently involved in data breaches, and service providers should do everything possible to strengthen their defense.
Dashlane noted a few very worrying specifics. Its researchers were able to create passwords using nothing but the lower-case letter 'a' on sites that include Amazon, Dropbox, Google, Instagram, LinkedIn, Netflix, Spotify, Uber, and Venmo. Netflix and Spotify actually accepted 'aaaa' passwords. The concern here is that if such simple passwords are acceptable, many users will choose a similarly simple -- and common -- password.
Earlier this year, an analysis of 10 million passwords revealed that the 25 most popular passwords are used to secure over 50% of accounts. Dashlane's recommendation to online service providers in such cases is basically fourfold. Firstly, passwords should have a minimum length of eight characters. Secondly, they should be required to be a case-sensitive mix of upper and lowercase alpha and numeric characters. Thirdly, the service provider should ban the most popular passwords. And finally, in case an attacker is working through a list of common passwords, an automatic account lock should be applied after a pre-defined number of failed accounts.
While such practices from the service providers will help the user, every web user must remember that that it is his or her responsibility to choose a strong and unique password for each different account.
SAP Security Patch Day – August 2017 addresses 19 vulnerabilities
10.8.2017 securityaffairs Vulnerebility
SAP just released another set of security patches for its products to address a total of 19 vulnerabilities, most common vulnerability type is XSS.
On Tuesday, SAP released a set of security patches to address a total of 19 software vulnerabilities, most of them are rated medium. The most common vulnerability type is cross site scripting (XSS).
Among the most critical vulnerabilities fixed by SAP, there is an SQL injection in SAP CRM WebClient User Interface (SAP Security Note 2450979) that could be exploited by a remote attacker to steal sensitive data (customer datasets, pricing, sales, and prospective bids) by sending a special request.
The situation is serious, the exploitation of the flaw could have a dramatic impact on the victims.
“Cross-Site Scripting remains the most widespread security loophole in SAP Applications with 20% of the released Notes addressing this type of issues,” read the analysis published by the company ERPScan.
“Vulnerabilities in SAP Customer Relationship Management module deserves attention. The number of SAP Security Notes for this module totals 393. This month, 3 Notes belong to this area, including an SQL Injection which allows stealing sensitive customer data.”
The most severe flaws fixed by SAP are:
a Directory Traversal vulnerability (CVSS Base Score: 7.7) in SAP NetWeaver AS Java Web Container.
a Code Injection vulnerability (CVSS Base Score: 7.4) in Visual Composer 04s iviews.
a Cross-Site AJAX Requests vulnerability (CVSS Base Score: 7.3) in SAP BusinessObjects (in a third-party Java library used by the application).
SAP post is here.
“SAP Product Security Response Team collaborates frequently with research companies like ERPScan to ensure a responsible disclosure of vulnerabilities. All vulnerabilities in question have been fixed, and security patches are available for download on the SAP Support Portal. We strongly advise our customers to secure their SAP landscape by applying the available security patches immediately.”
Cyber criminals demand HBO millions to stop leaking its material
10.8.2017 securityaffairs CyberCrime
Cyber gang demands HBO CEO to pay multimillion-dollar ransom to avoid 1.5TB of shows and confidential corporate data being leaked online.
Crooks claiming to have hacked television group HBO networks were demanding millions of dollars in ransom payments from the company while threatening to release more material.
The alleged hackers published a five-minute video letter to HBO chief Richard Plepler claiming to have “obtained valuable information” in a cyber attack. Cyber criminals said they had stolen 1.5 terabytes of data.
The author of the message dubbed himself “Mr. Smith,” he confirmed his group obtained “highly confidential” documents and data, including scripts, contracts, and personnel files.
According to the website Databreaches.net, on Monday hackers leaked 10 files including what appears to be another script of the fantasy series “Game of Thrones.”
Along with the video letter, the hackers released 3.4GB of files. The dump contained technical data related to the HBO’s internal network and administrator passwords, and of course the draft scripts from five Game of Thrones episodes. The huge trove of files also includes a month’s worth of emails from HBO’s vice president for film programming, Leslie Cohen.
The hackers claim a long work to compromise the HBO network, it took six months to break into the company systems, they also added to have purchased $500,000 a year zero-day exploits that let them hack the firm exploiting flaws in Microsoft and other software used by HBO.

The crooks pretend to receive half of the HBO group’s annual budget of $12 million to $15 million to stop leasing the files.
“We want XXX dollars to stop leaking your data,” “HBO spends 12 million for Market Research and 5 million for GOT7 advertisements. So consider us another budget for your advertisements!”
The video message comes a few days after a leak of one script of “Games of Thrones” and clips from other series.
The hackers claim HBO was his 17th victim and that “only 3 of our past targets refused to pay and were punished very badly and 2 of them collapsed entirely.”
HBO fears that hackers will leak other material and that “the forensic review is ongoing.”
“While it has been reported that a number of emails have been made public, the review to date has not given us a reason to believe that our email system as a whole has been compromised,” the statement from the Time Warner unit said. “We continue to work around the clock with outside cybersecurity firms and law enforcement to resolve the incident.”
Mamba ransomware is back and targets organizations in Brazil and Saudi Arabia
10.8.2017 securityaffairs Ransomware
Researchers at Kaspersky Lab discovered a new wave of attack leveraging the Mamba ransomware that hit organizations in Brazil and Saudi Arabia.
Mamba ransomware is one of the first malware that encrypted hard drives rather than files that was detected in public attacks.
Mamba leverages a disk-level encryption strategy instead of the conventional file-based one.
A similar Ransomware, called Petya, made the headlines for the recent massive attack and its disk encryption strategy. The first sample of Mamba Ransomware discovered in the wild were using a full disk encryption open source tool called DiskCryptor to strongly encrypt the data.
Mamba mostly targeted organizations in Brazil, it was also used by crooks in the attack against the San Francisco Municipal Transportation Agency occurred in November.
Researchers at Kaspersky Lab discovered a new wave of attack leveraging the Mamba ransomware that hit organizations in Brazil and Saudi Arabia.
Like the NotPetya massive attack, also Mamba appears to have been designed for sabotage, it is unclear if the malware was developed by crooks or by a nation-state actor.
Unlike the NotPetya attacks, it is not excluded that Mamba victims could decrypt their data.
“Authors of wiper malware are not able to decrypt victims’ machines. For example, if you remember the ExPetr [malware], it uses a randomly generated key to encrypt a victim machine, but the trojan doesn’t save the key for further decryption,” said Kaspersky Lab researcher Orkhan Memedov. “So, we have a reason to call it ‘a wiper.’ However, in case of Mamba the key should be passed to the trojan as a command line argument, it means that the criminal knows this key and, in theory, the criminal is able to decrypt the machine.”
Mamba was first spotted on September 2016 when experts at Morphus Labs discovered the infection of machines belonging to an energy company in Brazil with subsidiaries in the United States and India.
The researchers shared a detailed analysis on Security Affairs, they explained that once the malware has infected a Windows machine, it overwrites the existing Master Boot Record, with a custom MBR and encrypts the hard drive using the DiskCryptor tool.
“Unfortunately there is no way to decrypt data that has been encrypted with the DiskCryptor utility, because this legitimate utility uses strong encryption algorithms,” explained Kaspersky Lab.
The last samples of Mamba ransomware show an unusual ransom note that instead of demanding for money like the original Mamba, it provides two email addresses and an ID number to be used to recover the encryption key.

The threat actor behind the new wave of Mamba ransomware attacks leverages the PSEXEC utility to execute the malware on the corporate network once it has penetrated it. PSEXEC is the same tool used by NotPetya to spread within target networks.
The attack chain described by Kaspersky has two phases, in the first one attackers drop the DiskCryptor tool into a new folder created by the malware. The persistence is obtained by registering a system service called DefragmentService, then the system is rebooted.
The second phase sets up the new bootloader and encrypts disk partitions using DiskCryptor, then the machine is rebooted.
“It is important to mention that for each machine in a victim’s network, the threat actor generates a password for the DiskCryptor utility,” Kaspersky Lab said in its report. “This password is passed via command line arguments to the ransomware dropper.”
FBI masqueraded the NIT in a video-bait to unmask sextortionist on Tor
10.8.2017 securityaffairs CyberCrime
The FBI used a NIT involving a specially crafted video file to unmask a sextortionist that via Tor was threatening youngsters.
The FBI has used once again the network investigative technique (NIT) for unmasking Tor users, this time the feds used it to arrest a suspected sextortionist. The man is accused of having tricked young girls into sharing nude pics of themselves and then blackmailed them.
The network investigative technique (NIT) was used in the past to unmask Tor user, it allows feds to gather suspects’ real IP address, the MAC address and other pieces of information and sent them to the FBI servers.
The FBI used a NIT involving a specially crafted video file that once opened causes the media player to contact an FBI-controlled server leaking the above information that can be used to identify the suspect’s ISP and, with a subpoena, the subscriber’s identity.
Using this technique, the FBI arrested Buster Hernandez, 26, who was charged with multiple counts of sexual exploitation of a child, threats to use an explosive device, and threats to injure. The man was using Facebook to lure the young victims and extort them to send him pictures of themselves naked.
“Terrorizing young victims through the use of social media and hiding behind the anonymity of the Internet will not be tolerated by this office,” said US Attorney Josh Minkler. “Those who think they can outwit law enforcement and are above being caught should think again. Mr Hernandez’s reign of terror is over.”

The man was using the name “Brian Kil” while he was sending messages to blackmail the victims threatening them to reveal compromising pictures. With this technique, he was asking more images to the young victims.
“When Victim 1 refused to provide additional images as demanded, Hernandez is alleged to have made physical threats to Victim 1, stating “I am coming for you. I will slaughter your entire class and save you for last.” He further made threats to law enforcement saying, “I will add a dozen dead police to my tally…Try me pigs, I will finish you off as well.” continues the US Attorney.
The FBI was involved in the investigation in December 2015, when it received FBI the request of help by the Brownsburg police, Indiana, where two of the victims lived. The police were not able to identify the man because he was using Tor.
The threats caused two schools to be closed for an entire day.
Hernandez is suspected to have “sextorted” a number of victims in at least 10 federal districts.
“This was a unique and complex investigation that highlights the tenacity, perseverance, expertise and dedication of the FBI Indianapolis’ Crimes Against Children Task Force and was a top priority. Innovative techniques were utilized, solutions to roadblocks created and partnerships with key private sector partners were developed,” said W. Jay Abbott, Special Agent in Charge of the FBI’s Indianapolis Division. “I stood in front of concerned parents and community members and told them we would find the person who had been victimizing these young girls and, with the tireless work of our agents and partners, we never gave up.”
V ohrožení bylo přes milión uživatelů. Útočníci se zaměřili na Chrome
9.8.2017 Novinky/Bezpečnost Zranitelnosti
Terčem počítačových pirátů se stal v poslední době internetový prohlížeč Chrome. Podařilo se jim totiž zotročit jedno rozšíření určené právě pro tento browser, kvůli tomu tak bylo ohroženo přes milión uživatelů. Upozornil na to český Národní bezpečnostní tým CSIRT.CZ.
„Bylo uneseno rozšíření Web Developers pro Chrome, které používá více než milión uživatelů,“ konstatoval Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Útok tedy zjednodušeně řečeno probíhal tak, že si toho ani obezřetní uživatelé nemohli všimnout. Samotní počítačoví piráti totiž vydali aktualizaci s pořadovým číslem 0.4.9, která byla automaticky distribuována na počítače uživatelů.
Zisky z reklamy
A právě v tom byl kámen úrazu, neboť kyberzločinci chování tohoto doplňku upravili. „Nová verze obsahovala mechanismus pro vkládání vlastních reklam útočníků do webových stránek navštívených uživatelem,“ podotkl Bašta.
Útočníci tak mohli kasírovat nemalé částky za zobrazování reklamy. Uživatelům se tak logicky v prohlížečích zobrazovaly i nabídky, které by jinak na daných webech neměly co dělat.
„Vývojářům se podařilo během několika hodin získat zpět vládu nad ukradeným účtem a vydat novou verzi 0.5. Na tu by měli uživatelé okamžitě přejít,“ poradil bezpečnostní expert.
Pozor na hesla
Ten zároveň upozornil, že útočníkům mohlo jít i o něco jiného než zisky z reklamy – například o krádež přihlašovacích údajů do různých on-line služeb. „Dále je doporučováno zvážit změnu hesel pro všechny webové účty a anulovat přihlašovací tokeny a cookies pro všechny webové stránky, které byly navštíveny v době používání infikovaného rozšíření,“ uzavřel Bašta.
Tento útok jasně ukazuje, jak jsou moderní počítačové systémy zranitelné. Útočníci totiž mohou škodlivý kód propašovat do počítače i v případě, kdy se uživatel chová příkladně a dbá na bezpečnostní poučky. Jednoduše zneužijí nějaký program, který je již na daném stroji nainstalovaný.
Záplatovací úterý nabídlo opravy pro Windows a další také o prázdninách
9.8.2017 CNEWS.cz Zranitelnosti
Velký servisní den pro Microsoft.
Včera večer proběhlo další záplatovací úterý. Někteří tak obdrží větší servisní aktualizaci po pouhém týdnu. Poznámky k vydání tvrdí, že se aktualizace dotýkají těchto produktů: Internet Explorer, Edge, Windows, SharePoint, Flash Player a SQL Server.
Srpnové opravné balíčky formou kumulativních aktualizací putují k Desítkám, Osmičkám a Sedmičkám:
aktualizace KB4034674 pro Windows 10 v1703 zvedá číslo sestavení na 15063.540,
aktualizace KB4034658 pro Windows 10 v1607 zvedá číslo sestavení na 14393.1593,
aktualizace KB4034660 pro Windows 10 v1511 zvedá číslo sestavení na 10586.1045,
aktualizace KB4034668 pro Windows 10 v1507 zvedá číslo sestavení na 10240.17533,
aktualizace KB4034681 pro Windows 8.1 přináší všechny opravy,
aktualizace KB4034672 pro Windows 8.1 přináší jen záplaty,
aktualizace KB4034664 pro Windows 7 přináší všechny opravy,
aktualizace KB4034679 pro Windows 7 přináší jen záplaty.
Je čas aktualizovat
Je čas aktualizovat
Běžné opravy pro poslední vydání Desítek odhalila aktualizace v minulém týdnu, jak již bylo uvedeno, tato nová navíc přidává jen pár záležitostí. Pokud jste zmíněný balíček nezískali, dostanete tyto opravy tentokrát. Připomínám, že aktualizace jsou kumulativní, tudíž obsahuj všechny dříve vydané opravy. Seznam změn pro KB4034674 vypadá následovně:
Pravidla poskytovaná službou Mobile Device Management jsou nadřazena pravidlům poskytnutým v původní sadě základní konfigurace zařízení od správce či správkyně.
Pravidlo s názvem Site to Zone Assignment List nebylo aktivní, přestože jste ho zapnuli.
Průvodce tvorbou pravidel AppLocker padal při vybírání účtů.
Byl vyřešen problém s přesměrováním do složky a blokováním profilu na neprimárním počítači.
Porušení přístupu v Mobile Device Manager Enterprise způsobovalo výskyt upozornění na chyby.
Byla opravena slabá místa v zabezpečení v Edgi, komponentě Windows Search, skriptovacím jádře, knihovně Windows PDF, Hyper-V, Windows Serveru, ovladačích běžících v jádrovém režimu, subsystému pro Linux, Windows shellu, ovladači Common Log File System, Internet Exploreru, a v jádře Microsoft JET Database.
Nebezpečné chyby mají Flash Player, Acrobat i Reader. Piráti je mohou zneužít
9.8.2017 Novinky/Bezpečnost Zranitelnosti
Hned několik desítek chyb bylo objeveno v populárních programech od společnosti Adobe. Týkají se například oblíbeného programu Flash Player, který slouží k přehrávání videí na internetu a po celém světě jej používají stovky miliónů lidí. Chyby se nevyhnuly ani programům Acrobat a Reader, které slouží k práci s PDF dokumenty. Záplaty od společnosti je však již možné stahovat.
„Společnost Adobe vydala záplaty pro produkty Flash Player, Reader, Acrobat, Digital Editions a Experience Manager, které opravují více než 80 zranitelností objevených externími výzkumníky,“ uvedl Pavel Bašta, bezpečnostní analytik Národního bezpečnostního týmu CSIRT.CZ, který je provozován sdružením CZ.NIC.
Ten zároveň varoval, že objevené zranitelnosti se nemusí vyplácet podceňovat. „Seznam obsahuje zranitelnosti jako critical memory corruption, use-after-free, heap overflow a další, které mohou být zneužity ke vzdálenému spuštění kódu,“ přiblížil technickou stránku věci Bašta.
Propašují virus, zotročí počítač
To jinými slovy znamená, že prostřednictvím chyb mohou kyberzločinci propašovat na cizí počítač prakticky jakýkoli škodlivý kód, případně jej zcela ovládnout na dálku. Mohli se tak snadno dostat k uloženým datům, případně odchytávat přihlašovací údaje na různé webové služby.
Takový stroj se pak klidně i bez vědomí uživatele může stát součástí botnetu (síť zotročených počítačů), který kyberzločinci zpravidla zneužívají k rozesílání spamu nebo k DDoS útokům.
Častý terč útoků
Stahovat záplatu je možné prostřednictvím automatických aktualizací daného programu nebo prostřednictvím stránek společnosti Adobe.
Flash Player používá na celém světě několik stovek miliónů lidí. Právě kvůli velké popularitě se na Flash Player zaměřují kybernetičtí nájezdníci pravidelně. Podle analýzy bezpečnostní společnosti Record Future cílilo osm z deseti nejrozšířenějších hrozeb v roce 2015 právě na tento přehrávač videí.
To je i jeden z hlavních důvodů, proč se společnost Adobe rozhodla Flash Player sprovodit ze světa. Podle dřívějšího oznámení jej bude podporovat už jen tři roky.
Kyberzločin stále roste
9.8.2017 SecurityWorld Kriminalita
V letošním druhém čtvrtletí jsme byli svědky velkého nárůstu aktivity sofistikovaných kyberzločineckých skupin. Zaznamenali jsme tak značné množství pokročilých škodlivých nástrojů včetně tří zero-day exploitů a dvou doposud nevídaných útoků: WannaCry a ExPetr. Expertní analýzou těchto dvou útoků odborníci zjistili, že kyberzločincům kód unikl ještě před tím, než byl zcela připraven – což je neobvyklá situace pro útočníky se špičkovým zázemím. Tyto a další trendy přináší nejaktuálnější report o kybernetických hrozbách společnosti Kaspersky Lab.
V období od dubna do června došlo k výraznému vývoji cílených útoků pocházejících mimo jiné od ruskojazyčných, anglicky mluvících, korejských a čínských kyberzločinců. Tento vývoj má dalekosáhlý vliv na firemní IT zabezpečení.
K zákeřným sofistikovaným aktivitám dochází nepřetržitě téměř všude na světě. Tím se zvyšuje riziko, že dojde k podružnému poškození společností a nekomerčních organizací v rámci kybernetického boje.
Zaujal vás tento článek? Přehled nejzajímavějších zpráv získáte odebíráním našeho newsletteru »
Destruktivní epidemie WannaCry a Expetr, za jejichž rozšíření do firemních systémů po celém světě údajně měly být zodpovědné určité státy, se tak staly prvním, ale pravděpodobně ne posledním příkladem nového nebezpečného trendu.
Mezi nejvýznamnější incidenty druhého čtvrtletí 2017 se řadí:
Tři zero-day Windows exploity zneužité ruskojazyčnými zločinci Sofacy a Turla. Skupina Sofacy, známá také jako APT28 nebo FancyBear, použila exploity proti řadě evropských cílů včetně vládních a politických organizací. Tito aktéři také zkoušeli použít experimentální nástroje například proti představiteli francouzské politické strany před tamními parlamentními volbami.
Gray Lambert – odborníci Kaspersky Lab analyzovali doposud nejpokročilejší sadu nástrojů skupiny Lambert. Jedná se o vysoce sofistikovanou a komplexní kyberšpionážní rodinu pocházející z anglicky mluvícího prostředí. V souvislosti s ní byly identifikovány dvě nové malwarové rodiny.
Útok WannaCry z 12. května a ExPetr z 27. června. Ačkoliv byly oba útoky velmi rozdílné svou povahou a cíli, oba se ukázaly jako překvapivě neúčinné „ransomwary“. Například v případě útoku WannaCry způsobilo jeho rychlé celosvětové šíření a velký počet obětí to, že se bitcoinový účet jeho strůjců stal středem pozornosti, což jim znemožnilo tyto peníze vybrat. To naznačuje, že skutečným cílem útoku WannaCry bylo zničení dat. Odborníci Kaspersky Lab dále odhalili vazby mezi skupinami Lazarus a WannaCry. Podobný vzor destruktivního malwaru, maskovaného jako ransomware, se objevil i v případě útoku ExPetr.
ExPetr, který útočil na organizace na Ukrajině, v Rusku i jinde po Evropě, se zprvu projevoval také jako ransomware, ale nakonec se ukázalo, že je čistě destruktivní. Motiv útoků ExPetr je doposud záhadou. Analytici z Kaspersky Lab dávají tyto útoky do souvislosti se zločinci známými jako Black Energy.
Kenya Opposition Claims Vote Has Been Hacked
9.8.2017 securityweek BigBrothers
Hackers broke into the database of Kenya's electoral commission and manipulated the results of the election, the leader of the country's opposition coalition alleged on Wednesday.
Vote counting is ongoing in east Africa's strongest democracy after Tuesday's election where voters were asked to either re-elect President Uhuru Kenyatta or replace him with longtime opposition leader Raila Odinga.
Odinga claims hackers used the credential of a murdered employee of the electoral commission (IEBC) to hack into an electronic voting system and activate an algorithm that inflated Kenyatta's votes.
"These results are fake, it is a sham. They cannot be credible," Odinga told reporters at a morning press conference.
"This is an attack on our democracy. The 2017 general election was a fraud."
He later released what he claimed was a log from an IEBC server to support his allegations that the server was configured to increase Kenyatta's totals by 11 percent and cover up the modifications.
The log, and Odinga's allegations, have not been independently verified.
With ballots from 92 percent of polling stations counted, electoral commission (IEBC) results showed Kenyatta leading, with 54.4 percent of the nearly 13 million ballots tallied, against Odinga's 44.7 percent, a difference of 1.3 million votes.
But Odinga believes the vote is actually in his favour, and tweeted that a count of ballots by his National Super Alliance (NASA) coalition showed him in the lead.
He said the hacking affected all the results, both the presidential and the general election.
The hackers were able to access the system using the credentials of Chris Msando, a top IT official at the IEBC found tortured and murdered in late July, Odinga said.
He would not say how he got the information, saying he wanted to protect his source.
The 72-year-old is making his fourth bid for the presidency, and has previously accused his rivals of stealing victory from him through rigging in 2007 and in 2013.
In 2007, the disputed vote resulted in two months of ethnically driven political violence that killed 1,100 people and displaced 600,000, a major blow to a nation seen as a regional bastion of stability.
The contested election in 2013 was taken to the courts and ended largely peacefully, though Odinga lost.
Odinga urged his supporters to "remain calm as we look deep into this matter," but added: "I don't control the people."
U.S. Charges Two Iranians With Hacking, Credit Card Fraud
9.8.2017 securityweek CyberCrime
The U.S. Department of Justice announced on Tuesday that two Iranian nationals have been charged with credit card fraud and computer hacking. They were indicted in Columbia, South Carolina, where the FBI’s local cyber squad investigated the case.
Arash Amiri Abedian, 31, and Danial Jeloudar, 27, both believed to be living in the Islamic Republic of Iran, allegedly used hacking and other methods to steal payment card data and other information which they used to obtain money, goods and services from victims in the United States and elsewhere.
According to authorities, between 2011 and 2016, Abedian used malware to capture credit card data and other personal information provided by individuals on certain merchants’ websites. He used the information to steal identities and obtain various goods and services.Arash Amiri AbedianDanial Jeloudar
Investigators determined that, in February 2012, Abedian sent Jeloudar roughly 30,000 payment card records. Jeloudar later used stolen card data to acquire equipment, servers and web hosting services from a company in South Carolina.
Jeloudar is also said to have used stolen customer information to extort a California-based merchant. He threatened to leak the data unless the company made a Bitcoin payment. He also threatened to tell the company’s customers that their information had been compromised and launched a distributed denial-of-service (DDoS) attack on the merchant’s website.
Abedian and Jeloudar have been charged with conspiracy, wire fraud, access device fraud, and aggravated identity theft. They have been added to the FBI’s Cyber Most Wanted list, but no reward has been offered for information leading to their arrest.
Abedian and Jeloudar are not the only Iranians charged in the United States with cyber crimes. Last year, the Justice Department announced charges against seven suspects believed to have launched distributed denial-of-service (DDoS) attacks on U.S. banks.
Last month, two Iranians were indicted in the U.S. for hacking a defense contractor and stealing sensitive software used to design bullets and warheads. They allegedly sold the stolen software to Iranian universities, the military and the government.
Fuzzing Tests Show ICS Protocols Least Mature
9.8.2017 securityweek ICS
Fuzzing tests conducted last year by customers of Synopsys, a company that provides tools and services for designing chips and electronic systems, revealed that protocols used in industrial control systems (ICS) are the least mature.
Fuzzing is a testing technique designed for finding software vulnerabilities by sending malformed input to the targeted application. If the software crashes or behaves unexpectedly, it could indicate the presence of a security flaw and further investigation is warranted. If the number of crashes is high and the time to first failure (TTFF) is short, the likelihood of exploitable vulnerabilities increases.
Synopsys’ State of Fuzzing 2017 report is based on 4.8 billion results obtained in 2016 from tests targeting 250 protocols used in industrial, Internet of Things (IoT), automotive, financial services, government, healthcare and other sectors.
In the case of ICS, Synopsys customers tested protocols such as IEC-61850 MMS, IEC-104 Server, Modbus PLC, OPC UA, DNP3 and MQTT. There are also some protocols used for both ICS and IoT, including CIP and CoAP Server.
Many of these protocols had the TTFF within five minutes. Modbus, for instance, had 37 failures after 1.5 million tests and an average test runtime of 16 minutes. The OPC UA protocol had over 16,000 failures with a testing runtime of 4.5 hours.

In comparison, the Address Resolution Protocol (ARP), which is used to convert an IP address into a physical address and is the most mature protocol, had zero failures after over 340,000 tests with an average runtime of 30 hours.
Four of the five least mature protocols, based on average TTFF, are ICS protocols, including IEC-61850 MMS, Modbus PLC, DNP3 and MQTT.
“The protocols typically associated with ICS showed the most immaturity,” Synopsys said in its report. “Many demonstrated rapid time to first failures, with IEC-61850 MMS measured in a matter of seconds. This has bearing on IoT, as many of the protocols used in ICS are also used in IoT. Clearly, more testing is needed for the protocols within ICS and IoT, as the potential for discovering more vulnerabilities is greater in these industry verticals than in others.”
The most mature protocols, based on tests conducted by Synopsys customers, are Bluetooth LE Health, DHCPv4 Client, Bluetooth LE, ARP Client, PNG and E-LMI – each with 0 failures.
Firefox Makes Adobe Flash Click-to-Activate by Default
9.8.2017 securityweek IT
Starting with the release of Firefox 55 this week, the Adobe Flash plugin is no longer active by default in Mozilla’s web browser, and users of the new version will be required to activate it for each website they visit.
According to Mozilla, not only is the Adobe Flash plugin click-to-activate disabled by default with the new release, but it is also allowed only on http:// and https:// URL schemes. Users can now choose on which sites they want to activate the plugin, and can also opt in for Firefox to remember the settings. Some sites, however, won’t be allowed to run plugins, Mozilla says.
Mozilla plans on fully removing Flash from Firefox in early 2020, but will continue to support it in Firefox Extended Support Release (ESR) until the end of 2020. From then onward, the browser will refuse to load the plugin.
Google Chrome and Microsoft Edge started blocking Flash by default last year, and Adobe announced last month that it will stop supporting the plugin by the end of 2020: “we will stop updating and distributing the Flash Player,” the company said at the end of July 2017. In addition to Google, Microsoft, and Mozilla, Apple and Facebook too announced plans to remove Flash.
In addition to deactivating Flash, the new browser release resolves around 30 security vulnerabilities, 5 of which were rated Critical risk. These include an XUL injection in the style editor in devtools (CVE-2017-7798), Use-after-free in WebSockets during disconnection (CVE-2017-7800), Use-after-free with marquee during window resizing (CVE-2017-7801), and Memory safety bugs (CVE-2017-7779 and CVE-2017-7780).
Firefox 55 also resolves 11 High severity flaws, including 4 use-after-free bugs, 3 buffer overflows, out-of-bounds issue, same-origin policy bypass, domain hijacking, and memory protection bypass vulnerabilities.
The browser includes patches for 7 Medium severity issues: spoofing following page navigation with data, CSP information leak with frame-ancestors containing paths, WindowsDllDetourPatcher allocates memory without DEP protections, Elliptic curve point addition error when using mixed Jacobian-affine coordinates, Linux file truncation via sandbox broker, CSP containing 'sandbox' improperly applied, and Self-XSS XUL injection in about:webrtc.
6 Low risk vulnerabilities were addressed in this release: DOS attack through long username in URL, Sandboxed about:srcdoc iframes do not inherit CSP directives, Failure to enable HSTS when two STS headers are sent for a connection, Windows crash reporter reads extra memory for some non-null-terminated registry values, Windows updater can delete any file named update.log, and Response header name interning leaks across origins.
Firefox 55 also brings along various new features and improvements, such as Windows support for WebVR and a setting to enable Hardware VP9 acceleration on Windows 10 Anniversary Edition. Now, Firefox for Windows 64-bit is installed by default on all 64-bit systems that have at least 2GB of RAM.
The updated browser release is available for Windows, Mac, Linux, and Android.
North Korea Campaigns Show Link Between KONNI and DarkHotel
9.8.2017 securityweek CyberCrime
Decoy documents used in two recent cyber espionage campaigns apparently aimed at entities linked to North Korea show a connection between the DarkHotel attacks and a piece of malware named KONNI.
KONNI is a remote access trojan (RAT) that managed to stay under the radar for more than 3 years. The malware has evolved over the past years and it’s currently capable of logging keystrokes, stealing files, capturing screenshots, and collecting information about the infected machine.
KONNI has mainly been used to target organizations linked to North Korea. One of the campaigns spotted by researchers at Cisco Talos this year involves a dropper named “Pyongyang Directory Group email April 2017 RC_Office_Coordination_Associate.scr,” which opens a Word document when executed.
Researchers at Cylance noticed that this decoy document, titled “Pyongyang e-mail lists - April 2017,” is very similar to a document delivered in a recent campaign linked by Bitdefender to DarkHotel, a threat group that has been around for nearly a decade.
DarkHotel came to light in November 2014, when Kaspersky published a report detailing a sophisticated cyber espionage campaign targeting business travelers in the Asia-Pacific region. The group, whose members appear to be Korean speakers, possibly from South Korea, has targeted individuals in North Korea, Russia, South Korea, Japan, Bangladesh, Thailand, Taiwan, China, the United States, India, Mozambique, Indonesia and Germany.
The new DarkHotel campaign analyzed by Bitdefender, dubbed “Inexsmar” by the security firm, was aimed at government employees with an interest in North Korea. One of the decoy documents used in the attack is very similar to the one seen in the KONNI attacks – it’s titled “Pyongyang e-mail lists - September 2016” and its content has the same format.
Furthermore, an analysis of the files’ description revealed that they are both titled “Pyongyang directory” and they were both authored by an individual named “Divya Jacob.”
Cylance has conducted a detailed analysis of KONNI and the company’s experts believe that, as a result of the recent attention, the malware’s authors will release new variants that will include better obfuscation and additional capabilities.
Black Hat 2017 – Hacking the electronic locks to open the doors could be easy
9.8.2017 securityaffairs Hacking
Many times we have seen in movies hackers and spies breaking electronic locks with any kind of electrical equipment. Is it possible?
Many times, we have seen in movies hackers and spies breaking electronic locks with any kind of electrical equipment.
A pocket device that in a few seconds is able to try all the possible combination and find the correct one to open the door.
At Black Hat 2017 hacker conference, the expert Colin O’Flynn presented an interesting report on breaking electronic door locks.
O’Flynn focused his analysis on two samples of home electronic locks and he found the first model vulnerable to so-called Evil Maid attacks. The attacker needs the physical access to the lock’s internal component to add their own code to open the door whenever he needs.
The curious thing is that step-by-step instructions on how to add the code are reported right inside the battery compartment.

The expert noticed that the systems lack of authentication to enter the code, no user code or master code is requested.
The second model is vulnerable to a different attack from the outside. The outer part of the lock contains a module with a touch-screen for entering a PIN code that can be easily extracted by the attacker with a common knife to access the connector.
O’Flynn analyzed the way the external and internal components the lock interact and devised a device that appears exactly like the one used by hackers in the movie.
After studying how the external and internal parts of the lock interact,
The device could be used to brute-force the combination by directly connecting it to the connector. The attack works because there is no authentication in place to check with component communicates with the connector.

The expert noticed a security measure implemented by the electronic lock manufacturer against brute-force attacks, after more than three incorrect tries the device triggers the alarm.
Nevertheless, O’Flynn discovered that it was possible to reset the counter of the failed-attempts by applying a certain voltage to the external connector’s contacts and causing the system reboot.
O’Flynn created a device that can check toughly 120 codes per minute, trying all possible four-digit PIN combinations for the electronic lock the entire process can take about 85 minutes in the worst case. The experts explained that in most cases, a half-hour to an hour is the time necessary to the hack.
O’Flynn also devised a method to discover the six-digits master code with an improved brute-force attack. Normally to discover a six-digit code it is necessary a week, but the expert noticed that when you enter the first four of six numbers of the master code, the system either shows an error message or waits for the other two numbers to be entered, confirming to the attacker that the first four digits are correct.
This method requires 85 minutes to brute-force the first four numbers of the master code and one minute more for the remaining two numbers. The attacker can then use the master code to reset the access code.
O’Flynn reported the issues to the electronic lock manufacturer, who confirmed that they will be fixed as soon as possible.
Electronic locks are still not totally secure!
Microsoft Issues Security Patches for 25 Critical Vulnerabilities
8.8.2017 thehackernews Vulnerebility
Here we are again…
As part of its August Patch Tuesday, Microsoft has today released a large batch of 48 security updates for all supported versions Windows systems and other products.
This month's security updates cover vulnerabilities in Microsoft's Windows operating systems, Internet Explorer, Microsoft Edge, Microsoft SharePoint, Adobe Flash Player, Windows Hyper-V and Microsoft SQL Server.
The security updates address a range of issues including 25 critical, 21 rated important and two moderate in severity.
The most interesting and critical vulnerability of this month is Windows Search Remote Code Execution Vulnerability (CVE-2017-8620), affects all versions of Windows 7 and Windows 10, which could be used as a wormable attack like the one used in WannaCry ransomware, as it utilises the SMBv1 connection.
An attacker could remotely exploit the vulnerability through an SMB connection to elevate privileges and take control of the targeted Windows computer.
"A remote code execution vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights," Microsoft explains.
"In addition to security changes for the vulnerabilities, updates include defense-in-depth updates to help improve security-related features."
Microsoft also released a security update for the Adobe Flash Player for Internet Explorer, although the company would end its support for Flash at the end of 2020.
Users and IT administrators are strongly recommended to apply security patches as soon as possible to keep away hackers and cybercriminals from taking control over your computer.
For installing security updates, simply head on to Settings → Update & security → Windows Update → Check for updates, or you can install the updates manually.
SAP Resolves 19 Vulnerabilities With August 2017 Security Notes
8.8.2017 securityweek Vulnerebility
SAP this week released another set of security patches for its products to address a total of 19 vulnerabilities, most of which are rated Medium severity.
A total of 16 security notes were included in the SAP Security Patch Day in August 2017: three rated High risk, 11 rated Medium severity, and two Low risk.
SAP also released 3 Support Package Notes, for a total of 19 patches. 1 of the notes was released after the second Tuesday of the previous month and before the second Tuesday of this month.
The most important of these issues include a Directory Traversal vulnerability (CVSS Base Score: 7.7) in SAP NetWeaver AS Java Web Container, a Code Injection vulnerability (CVSS Base Score: 7.4) in Visual Composer 04s iviews, and a Cross-Site AJAX Requests vulnerability (CVSS Base Score: 7.3) in SAP BusinessObjects (in a third-party Java library used by the application).
The Visual Composer 04s iviews flaw “allows attackers to inject malicious code into the back end application. By simply having end users access a specially crafted URL, unwanted applications can be started on the client machine by an attacker. Depending on who makes use of your Enterprise Portal, clients in this sense could be employees, customers, partners or suppliers,” Onapsis reveals.
According to the company, which specializes in securing SAP and Oracle applications, a large number of Visual Composer versions, starting from 7.00, are affected. Thus, even if the component might not be actively used within an organization, it could be leveraged as part of an attack.
The most common vulnerability type resolved this month was cross-site scripting. Five such issues were addressed in SAP applications, along with two directory traversal bugs, two open redirects, two cross-site request forgery flaws, two SQL injections, one missing authorization check, one information disclosure, one code injection, one SSRF bug, one implementation flaw, and one denial of service.
“Cross-Site Scripting remains the most widespread security loophole in SAP Applications with 20% of the released Notes addressing this type of issues,” ERPScan, another company focused on securing SAP and Oracle software, says.
One of the XSS issues resolved this month impacted the Adobe Flex Software Development Kit, meaning that custom applications written with the help of the library are susceptible to XSS vulnerability, ERPScan points out. SAP’s Web Dynpro Flex appears affected.
The bug was initially found in 2011 and patched when the appropriate patch was released in March 2012. It allowed an attacker to remotely inject arbitrary web script or HTML by the use of vectors related to the loading of modules from different domains.
Because the issue impacts a library, applying the fix won’t eliminate the vulnerability, as all applications written using the vulnerable library need to be rebuilt using the patched version of the SDK.
According to ERPScan, a Cross-site scripting vulnerability in SAP Customer Relationship Management IPC Pricing (CVSS Base Score: 6.1) module deserves attention, as it could allow an attacker to inject a malicious script into a page. The script would have access to cookies, session tokens, and other critical information stored and used for interaction with a web application. Thus, an attacker could learn business-critical information and even get control over this information, or can abuse the flaw for the unauthorized modifying of displayed content.
“It’s been another SAP Notes Day without any critical (Hot News) patch update. Despite it not being a critical month, the high priority notes mentioned above should be treated as soon as possible. […] Almost all bug types are included within this release, despite most of them having a medium priority tag,” Onapsis notes.
FireEye Says Network Secure After Analyst Accounts Compromised
8.8.2017 securityweek Incindent
On July 31, 2017, a hacker claimed to have been deep inside Mandiant's infrastructure. FireEye, which bought Mandiant for $1 billion in January 2014, responded: "Our investigation continues, but thus far we have found no evidence FireEye or Mandiant systems were compromised."
Yesterday FireEye published its preliminary findings. "The Attacker did not breach, compromise or access our corporate network, despite multiple failed attempts to do so." Investigations will continue, but "we do not anticipate any significant new discoveries," wrote Steven Booth, FireEye VP & CSO.
Booth explains that Adi Peretz, whom FireEye describes as the 'Victim', had some personal on-line accounts compromised by the unknown Attacker; but neither the FireEye corporate network nor the Victim's personal or corporate devices were either breached or compromised.
All of the data released by the Attacker came from the online accounts, including Peretz' LinkedIn, Hotmail and OneDrive accounts. This data included three FireEye corporate documents, which the Attacker obtained from the Victim's personal online accounts. "All of the other documents released by the Attacker were previously publicly available or were screen captures created by the Attacker." writes Booth."
The interesting part of FireEye's account of the data loss is not stated, but can be inferred. "We confirmed the Victim's passwords and/or credentials to his personal social media and email accounts were among those exposed in at least eight publicly disclosed third party breaches (including LinkedIn) dating back to 2016 and earlier."
But while LinkedIn and Hotmail have both been subject to past breaches, there is no such public account of a OneDrive breach. If there has been no OneDrive breach, there are two implications: first, Peretz shared his credentials across multiple accounts; and secondly, he did not routinely and regularly change them. Both should be highly recommended. (SecurityWeek has reached out to Microsoft for information on any previous OneDrive breach.)
We can also assume that Peretz did not automatically use two-factor authentication where it was available. "We worked with the Victim to secure his personal online accounts, including implementing multi-factor authentication where possible," writes Booth. Peretz, it would seem, did not practice strong password hygiene for his own accounts.
SecurityWeek reached out to Steven Booth for confirmation on this, and to ask whether FireEye staff are or will be subject to specific corporate policy rules over password use and management. We received a brief statement from the communications team: "Normally we'd be happy to comment on something like this, but in this case we can't add additional comment to the blog post."
FireEye's corporate security is clearly stronger. Although the Attacker claimed to have gained access to the corporate network, the investigation identified only failed login attempts. We can expect that staff practices will also be stronger in future.
Microsoft Patches Windows Search Flaw Exploited in Attacks
8.8.2017 securityweek Vulnerebility
Microsoft’s Patch Tuesday updates for August 2017 address a total of 48 vulnerabilities in Windows, Internet Explorer, Edge, SQL Server, SharePoint Server, Office and Outlook.
Microsoft has classified 25 of the flaws as critical and 21 as important. Two of the patched vulnerabilities were disclosed before fixes were made available, and one vulnerability has been exploited in attacks.
The security hole being exploited by malicious actors is CVE-2017-8620, a Windows Search vulnerability that can allow a remote attacker to execute arbitrary code and take control of the targeted system. The issue, discovered by Nicolas Joly of MSRC Vulnerabilities and Mitigations, exists due to the way Windows Search handles objects in memory.
“To exploit the vulnerability, the attacker could send specially crafted messages to the Windows Search service. An attacker with access to a target computer could exploit this vulnerability to elevate privileges and take control of the computer,” Microsoft said in its advisory. “Additionally, in an enterprise scenario, a remote unauthenticated attacker could remotely trigger the vulnerability through an SMB connection and then take control of a target computer.”
The bug is similar to CVE-2017-8543, a Windows Search code execution vulnerability patched by Microsoft in June. This flaw had also been actively exploited when Microsoft released a patch. It’s unclear if CVE-2017-8543 and CVE-2017-8620 are linked since no details have surfaced about either of the attacks.
The vulnerabilities whose details have been publicly disclosed are important severity denial-of-service (DoS) and privilege escalation issues affecting Windows, namely the subsystem for Linux and error reporting components, respectively.
Another interesting vulnerability, according to Trend Micro’s Zero Day Initiative (ZDI) is CVE-2017-8664, an important remote code execution flaw affecting Windows Hyper-V.
“To exploit the vulnerability, an attacker could run a specially crafted application on a guest operating system that could cause the Hyper-V host operating system to execute arbitrary code,” Microsoft said. “An attacker who successfully exploited the vulnerability could execute arbitrary code on the host operating system.”
Adobe also released updates for several of its products on Tuesday, including a Flash Player update that patches two vulnerabilities. Microsoft has also updated the Flash Player libraries used by its products.
UK Introduces Data Protection Bill to Replace GDPR After Brexit
8.8.2017 securityweek Privacy
The UK government has announced its plans for a new Data Protection Bill. This was foreshadowed in the Queen's Speech of 21 June when she announced, "A new law will ensure that the United Kingdom retains its world-class regime protecting personal data."
This law is, in effect, the European General Data Protection Regulation designed to withstand Brexit. The UK will still be part of the European Union when GDPR comes into effect in May 2018. However, the government is already under great pressure to transpose 40 years of European laws onto the British statute books in time for the actual severance. It makes sense, therefore, to prepare a GDPR-compliant UK law immediately.
The wording of the new Bill is not expected to become public until September. However, the Department for Digital, Culture Media & Sport yesterday published a 30 page Statement of Intent (PDF) in which The Rt Hon Matt Hancock MP, Minister of State for Digital, explains, "Implementation will be done in a way that as far as possible preserves the concepts of the Data Protection Act to ensure that the transition for all is as smooth as possible, while complying with the GDPR and DPLED in full."
It follows, then, that US companies that operate in compliance with the UK Data Protection Bill will (or should) be automatically in compliance with GDPR. The reverse is not necessarily true. For example, while the GDPR requires the use of anonymized or pseudonymised (its own term) personal data, the new DP Bill will: "Create a new offence of intentionally or recklessly re-identifying individuals from anonymised or pseudonymised data. Offenders who knowingly handle or process such data will also be guilty of an offence. The maximum penalty would be an unlimited fine."
Since this is new, and we do not yet know the detail of the proposed Bill, it is impossible to tell whether there will be any attempt to make this a worldwide offense. It is difficult, however, to see how it could be enforced in foreign jurisdictions where the company or persons concerned have no direct presence within the UK.
Other new elements include a new offence of altering records with intent to prevent disclosure following a subject access request (with an unlimited fine in England and Wales); while criminal justice agencies (read law enforcement) will have "A more prescriptive logging requirement applied to specific operations of automated processing systems including collection, alteration, consultation, disclosure, combination and erasure of data, so a full audit trail will be available."
Another feature that will undoubtedly change will be the ultimate court of appeal in case of dispute. For the GDPR it will be the European Court of Justice (as it will be in the UK until Brexit takes effect). "At Brexit (depending on its nature)," Dr Brian Bandey, a Doctor of Law specializing in international cyber laws, told SecurityWeek, "the GDPR's effectiveness as a law will terminate. I believe it likely that simultaneously with that event, the new Data Protection Bill will come into force. I expect the whole of the Data Protection Act 1998 will be repealed. It is at that time that the Supreme Court will be the ultimate Court of Appeal with respect to this matter."
Whether the UK's Supreme Court will be as aggressive in upholding the constitution (the UK does not have a written constitution in the usual sense of the term) as has the European Court, remains to be seen. David Flint, a senior partner at MacRoberts LLP, does not see a problem. He believes that the overriding motivation behind the new Bill is to ensure smooth ongoing business trading between the UK and the EU. GDPR 'adequacy' thus becomes an essential element.
"The fact that UK citizens cannot appeal to the ECJ is arguably a loss," he told SecurityWeek, "but in practice it is difficult to see how a UK court could or would not take cognizance of the decisions of the ECJ in interpreting the UK Act; were they to diverge in interpretation, again the adequacy finding would be in jeopardy."
What does seem likely is that not all the 'optional' elements of GDPR will be enacted within the new DPB. The Open Rights Group has already issued a statement saying, "We are disappointed that UK Ministers are not taking up the option in EU law to allow consumer privacy groups to lodge independent data protection complaints as they can currently do under consumer rights laws."
However, says Flint, "The 2017 UK Data Protection Bill is designed to cover the limited number of instances within the GDPR in which Member States are able to make choices or derogations; issues such as the age of consent for children, for automatic profiling, law enforcement and research. We are told that the UK is adopting a UK solution to these questions."
It seems, then, that any divergences between the UK Data Protection Bill and the GDPR will largely be limited to UK relevance only. Where US companies are concerned, future post-Brexit trading with the UK will be subject to the same conditions and the same potential fines for non-compliance, as they will be for trading with the European Union under GDPR.
HBO Hackers Demand Millions in Ransom Note
8.8.2017 securityweek Hacking
Hackers claiming to have breached HBO were demanding millions of dollars in ransom payments from the television group, while threatening to release more files from what is claimed to be a massive data breach.
A video circulating online directs a message to HBO chief Richard Plepler claiming that the group "obtained valuable information" in an attack that yielded a whopping 1.5 terabytes of data.
The message was authored by someone identified only as "Mr. Smith."
The website Databreaches.net reported that 10 files were leaked Monday as part of the demand including what may be another script of the popular fantasy series "Game of Thrones."
The video revealed a letter stating the hackers obtained "highly confidential" documents and data including scripts, contracts and personnel files.
"We want XXX dollars to stop leaking your data," the letter said, later alluding to a figure of half the group's annual budget of $12 million to $15 million.
It went on to say, "HBO spends 12 million for Market Research and 5 million for GOT7 advertisements. So consider us another budget for your advertisements!"
The message comes a week after a leak of one script of "Games of Thrones" and content from other productions.
The letter said HBO was the 17th target for the hacking group and that "only 3 of our past targets refused to pay and were punished very badly and 2 of them collapsed entirely."
HBO said in a statement that it believed that further leaks might emerge from the breach and that "the forensic review is ongoing."
"While it has been reported that a number of emails have been made public, the review to date has not given us a reason to believe that our email system as a whole has been compromised," the statement from the Time Warner unit said. "We continue to work around the clock with outside cybersecurity firms and law enforcement to resolve the incident."
Campaign Targets Russian-Speaking Enterprises With New Backdoor
8.8.2017 securityweek Cyber
A malicious email campaign that has been active for at least two months is targeting Russian-speaking enterprises and delivering a new Windows-based backdoor, Trend Micro warns.
The attack relies on a variety of exploits and Windows components to run malicious scripts in an attempt to make detection and blocking more challenging. The earliest sample associated with the attack was uploaded to VirusTotal on June 6, 2017 and Trend Micro observed five spam runs from June 23 to July 27, 2017. The campaign is believed to be ongoing.
Targets in this attack included financial institutions (such as banks) and mining firms. Trend Micro's researchers noticed that the attackers have diversified their tactics by sending different, targeted emails for each run. Because of the emails’ limited distribution and specificity in social engineering lures, they should be considered part of a spear-phishing campaign, Trend Micro says.
The emails look as if they come from sales and billing departments and contain a malformed Rich Text Format (RTF) file that exploits a vulnerability (CVE-2017-0199) in Microsoft Office’s Windows Object Linking and Embedding (OLE) interface that was patched in April (the flaw is still being abused by threat actors such as Cobalt and CopyKittens).
Once the exploit code was executed, it downloads a fake XLS file embedded with malicious JavaScript. When opened, the Excel header is ignored and the file is treated as an HTML Application file by the Windows component mshta.exe.
The JavaScript code calls the odbcconf.exe normal executable, which performs various tasks associated with Microsoft Data Access Components, to run the DLL. Once executed, the DLL drops a file in the %APPDATA% folder and appends the .TXT extension to it, although this is an SCT file (Windows scriptlet) normally used to declare variables, define expressions, and add functional codes in web pages, but packed with malicious, obfuscated JavaScript as part of this attack.
The DLL calls the Regsvr32 (Microsoft Register Server) command-line utility to execute with specific parameters. Called Squiblydoo, this attack method abuses Regsvr32 to bypass restrictions on running scripts and evade application whitelisting protections such as AppLocker, and was previously associated with the activities of Vietnamese hacking group APT32.
“While Squiblydoo is already a known attack vector, this is the first time we’ve seen it combined with odbcconf.exe,” Trend Micro notes.
Next, another XML file is executed, after being downloaded from the domain wecloud[.]biz. This is the main backdoor used in this attack, which is executed using the same Regsvr32-abusing Squiblydoo attack technique.
The backdoor is a SCT file with obfuscated JavaScript code inside and supports commands that “essentially allow attackers to take over an infected system.” The backdoor attempts to connect to the command and control (C&C) server at hxxps://wecloud[.]biz/mail/ajax[.]php and retrieve tasks.
Based on the received commands, the malware can download and execute Portable Executable (PE) files, delete files/startup entries and terminate, download additional/new scripts, run new script and terminate current script, or run command shell commands.
“While the later stages of the infection chain required the use of various Windows components, the entry point still involves the use of a Microsoft Office exploit. Patching and keeping software up-to-date will protect users. Alternately, employing firewalls, intrusion detection and prevention systems, virtual patching, and URL categorization, as well as enforcing robust patch management policies, will significantly reduce the system’s attack surface,” Trend Micro notes.
Google Resolves Critical Vulnerabilities in Android's Media Framework
8.8.2017 securityweek Vulnerebility
Google this week published its August 2017 Android security bulletin, which includes information on more than 40 vulnerabilities addressed in the mobile operating system this month, including 10 Critical flaws addressed in media framework.
This month’s Android security bulletin is split into two security patch level strings and contains one of the lowest number of patches since Google started delivering these monthly updates two years ago.
The first of the security patch level strings included in the bulletin (the 2017-08-01 security patch level) addresses 28 security bugs in three Android components: framework, libraries, and media framework. 10 of the issues were rated Critical severity, 15 High risk, and 3 Moderate severity, Google’s advisory reveals.
Media framework was the most impacted component, as it saw a total of 26 vulnerabilities being resolved in it: 10 Critical remote code execution bugs, 14 High risk denial of service and elevation of privilege issues, and 2 Moderate information disclosure vulnerabilities.
“The most severe vulnerability in this section could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process,” Google says.
One elevation of privilege was addressed in framework and one remote code execution in libraries.
The second security patch level string in the August 2017 Android security bulletin (the 2017-08-05 security patch level) addresses 14 vulnerabilities in Broadcom, Kernel, MediaTek, and Qualcomm components.
One remote code execution flaw (Moderate risk) was resolved in Broadcom components; five elevation of privilege bugs (one High and four Moderate severity) were addressed in Kernel components; two elevation of privilege issues (one High, one Moderate) were found in MediaTek components; and five elevation of privilege and one information disclosure vulnerabilities (all Medium risk) were resolved in Qualcomm components.
Three of the vulnerabilities in Kernel components (CVE-2017-10663, CVE-2017-10662, and CVE-2017-0750) were discovered by Trend Micro researchers and could cause memory corruption on the affected devices, leading to code execution in the kernel context. The flaws could be triggered by an app when a malicious disk using the F2FS (Flash-Friendly File System) is mounted.
Optimized for usage in devices with NAND memory, the F2FS file system is set as default on Android devices that ship with support for it, including those from Motorola, Huawei, and OnePlus, thus putting millions of users at risk, Trend Micro says. For the exploit to run, however, an attacker would need to compromise a privileged process with mount permission first.
“The problem for Linux may even be worse. Linux systems have supported F2FS since version 3.8 of the kernel was released in February 2013. Any Linux device with a kernel newer than this date is potentially at risk. However, not all distributions have enabled F2FS support by default. Systems where USB devices are set up to be automatically mounted upon insertion are most at risk, as this would mean simply inserting a malicious F2FS device would allow the exploit to work,” the security company notes.
Google devices will also receive patches for 9 other security vulnerabilities, if applicable, the Internet giant revealed. These include six information disclosure, two elevation of privilege, and one denial of service flaws, all rated Low severity. All Google devices will be updated to the August 05, 2017 security patch level over-the-air update (OTA).
Adobe Patches 69 Flaws in Reader, Acrobat
8.8.2017 securityweek Vulnerebility
Security updates released by Adobe for its Flash Player, Reader, Acrobat, Digital Editions and Experience Manager products address more than 80 vulnerabilities discovered by external researchers.
A majority of the flaws, 69, were patched in Reader and Acrobat 2017.009.20058, 2017.008.30051 and 2015.006.30306 and earlier versions on Windows and Mac.
The list includes critical memory corruption, use-after-free, heap overflow, and type confusion vulnerabilities that can be exploited for remote code execution. While a majority of the security holes rated critical allow arbitrary code execution, some of the issues classified as critical can lead to information disclosure.
The flaws rated important, which can also lead to remote code execution and information disclosure, have been described as insufficient verification of data authenticity, memory corruption, security bypass, and use-after-free issues.
Independent researchers and the employees of several firms have been credited for reporting these vulnerabilities, many via Trend Micro’s Zero Day Initiative (ZDI). Ke Liu of Tencent's Xuanwu LAB has reported the highest number of flaws.
Adobe has updated Flash Player to version 26.0.0.151 on all platforms. The latest release addresses only two vulnerabilities, including an important security bypass issue that can lead to information disclosure (CVE-2017-3085) and a critical type confusion flaw that can lead to remote code execution (CVE-2017-3106).
Mateusz Jurczyk and Natalie Silvanovich of Google Project Zero reported the code execution vulnerability and Björn Ruytenberg discovered the information disclosure bug via ZDI.
Adobe announced recently that, after consultations with technology partners, it has decided to end support for Flash Player by the end of 2020.
In the Experience Manager enterprise content management product, Adobe patched three moderate and important severity vulnerabilities that can be exploited for information disclosure and arbitrary code execution. The issues were reported to the company anonymously.
The latest updates for the Windows, Mac, iOS and Android versions of the Adobe Digital Editions ebook reader fix nine vulnerabilities discovered by Steven Seeley of Source Incite, Jaanus Kääp of Clarified Security, and Riusksk of Tencent.
The most severe of them, CVE-2017-11274 and CVE-2017-11272, have been described as critical remote code execution and information disclosure weaknesses.
Adobe is not aware of any attacks exploiting these vulnerabilities. Only the Flash Player patches have a priority rating of 1, which means they are more likely to be exploited by hackers.
Game of Thrones (Season 7) Episode 5 Script Leaked — Hacker Demands Millions in Ransom
8.8.2017 thehackernews Hacking
The hacking group that recently hacked HBO has just dropped its third trove of documents, including a month emails of one of the company's executives, and a detailed script of the upcoming fifth episode of "Game of Thrones" Season 7, set to be aired on August 13.
The latest release is the second leak from the hackers who claimed to have obtained around 1.5 terabytes of information from HBO, following the release of upcoming episodes of "Ballers" and "Room 104," and a script of the fourth episode of "Game of Thrones."
With the release of another half-gigabyte sample of its stolen HBO data, the hacking group has finally demanded a ransom worth millions of dollars from the entertainment giant in order to prevent further leaks.
The latest HBO data dump includes company's several internal documents, including emails, employment agreements, financial balance sheets, and marketing-strategy PDFs, along with the script of the yet-to-air 5th episode of Game of Thrones, all watermarked with "HBO is Falling."
The hackers reportedly sent a video message to HBO President and CEO Richard Plepler and demanded his "six-month salary in Bitcoin" — which is almost $6 Million — as a ransom for the stolen data otherwise they'll continue to leak.
In the video letter, written by "Mr. Smith" posing as the group of hackers behind the leak, the hackers demanded an unspecified amount of money from Plepler.
"We successfully breached into your huge network. HBO was one of our difficult targets to deal with, but we succeeded (it took about 6 months)," the letter reads as quoted by Wired.
"Our demand is clear and Non-Negotiable: We want XXXX dollars to stop leaking your Data. HBO spends 12 million for Market Research and 5 million for GOT7 advertisements. So consider us another budget for your advertisements!"
Last week when the hackers released the first batch of stolen data, HBO confirmed the cyber attack on its network but did not confirm how much data the hackers have stolen and whether it included upcoming episodes of the widely watched Game Of Thrones.
The ransom note adds that the deadline for that payment is only 3 days, but does not include a date. The video letter ends with an image of the "Night King" villain from Game of Thrones with his arms raised—the word "standing" in one hand and "falling" in the other.
Data Breaches also published some parts of the ransom demand the hackers, which call themselves white hats, sent to HBO.
In an internal email sent to to the HBO staff last week, Plepler said: "Many people have expressed particular concern about our e-mail system. At this time, we do not believe that our email system as a whole has been compromised, but the forensic review is ongoing."
HBO spokesperson Jeff Cusson told the publication that the company had been expecting more data to emerge from its data breach, but that the company's "forensic review is ongoing."
"The review to date has not given us a reason to believe that our email system as a whole has been compromised," Cusson says. "We continue to work around the clock with outside cyber security firms and law enforcement to resolve the incident."
If hackers have indeed stolen 1.5 terabytes of data from HBO and the company refuse to pay the ransom, users should expect more leaks of upcoming episodes from their favourite shows.
At this moment, it is still unclear who is behind the hack. We will update the story with the latest information.
Hotspot Shield VPN Accused of Spying On Its Users' Web Traffic
8.8.2017 thehackernews Privacy
"Privacy" is a bit of an Internet buzzword nowadays as the business model of the Internet has now shifted towards data collection.
Although Virtual Private Network (VPN) is one of the best solutions to protect your privacy and data on the Internet, you should be more vigilant while choosing a VPN service which actually respects your privacy.
If you are using popular free virtual private networking service Hotspot Shield, your data could be at a significant risk.
A privacy advocacy group has filed a complaint with the Federal Trade Commission (FTC) against virtual private networking provider Hotspot Shield for reportedly violating its own privacy policy of "complete anonymity" promised to its users.
The 14-page-long complaint filed Monday morning by the Centre for Democracy and Technology (CDT), a US non-profit advocacy group for digital rights, accused Hotspot Shield of allegedly tracking, intercepting and collecting its customers' data.
Developed by Anchorfree GmbH, Hotspot Shield is a VPN service available for free on Google Play Store and Apple Mac App Store with an estimated 500 million users around the world.
Also Read: Secure VPNs (Get Lifetime Subscription) To Prevent ISPs From Spying On You
VPN is a set of networks conjugated together to establish secure connections over the Internet and encrypts your data, thereby securing your identity on the Internet and improving your online security and privacy.
The VPN services are mostly used by privacy advocates, journalists, digital activists and protesters to bypass censorship and geo-blocking of content.
Hotspot Shield does just Opposite of What All it Promises
The Hotspot Shield VPN app promises to "secure all online activities," hide users' IP addresses and their identities, protect them from tracking, and keep no connections logs while protecting its user’s internet traffic using an encrypted channel.
However, according to research conducted by the CDT along with Carnegie Mellon University, the Hotspot Shield app fails to live up to all promises and instead logs connections, monitors users' browsing habits, and redirects online traffic and sells customer data to advertisers.
"It is thusly unfair for Hotspot Shield to present itself as a 48 mechanism for protecting the privacy and security of consumer information while profiting off of that information by collecting and sharing access to it with undisclosed third parties," the CDT complaint reads.
"Consumers who employ Hotspot Shield VPN do so to protect their privacy, and Hotspot Shield’s use of aggressive logging practices and third-party partnerships harm its consumers' declared privacy interests."
Hotspot Shield also found injecting Javascript code using iframes for advertising and tracking purposes.
Reverse engineering of the apps source code also revealed that the VPN uses more than five different third-party tracking libraries.
Researchers also found that the VPN app discloses sensitive data, including names of wireless networks (via SSID/BSSID info), along with unique identifiers such as Media Access Control addresses, and device IMEI numbers.
Also Read: Secure VPN Services — Get Up to 91% Discount On Lifetime Subscriptions
The CDT also claims that the VPN service sometimes "redirects e-commerce traffic to partnering domains."
If users try to visit any commercial website, the VPN app redirects that traffic to partner sites, including ad companies, to generate revenue.
"For example, when a user connects through the VPN to access specific commercial web domains, including major online retailers like www.target.com and www.macys.com,the application can intercept and redirect HTTP requests to partner websites that include online advertising companies," the complaint reads.
The CDT wants the FTC to start an investigation into what the Hotspot Shield's "unfair and deceptive trade practices" and to order the company to stop mispresenting privacy and security promises while marketing its app.
Microsoft to Ban WoSign, StartCom Certificates
8.8.2017 securityweek Security
Windows Will Not Trust New Certificates Issued by WoSign and StartCom After September 2017
Microsoft has finally announced its decision in the case of Chinese certificate authority (CA) WoSign and its subsidiary StartCom. The company has informed customers that its products will soon stop trusting new certificates issued by these CAs.
Following a series of incidents and problems brought to the attention of the web browser community since January 2015, Mozilla, Apple and Google have decided to revoke trust in certificates from WoSign and StartCom.
The list of problems includes backdating certificates to bypass restrictions, issuing certificates without authorization, and misleading browser vendors about WoSign's acquisition of StartCom and their relationship.
Microsoft has now also announced its decision regarding WoSign and StartCom certificates. Windows will continue to trust certificates issued before September 26, 2017, until they expire. However, new certificates issued by the firms after September 2017 will no longer work.
“Microsoft has concluded that the Chinese Certificate Authorities (CAs) WoSign and StartCom have failed to maintain the standards required by our Trusted Root Program,” the company said on Tuesday. “Observed unacceptable security practices include back-dating SHA-1 certificates, mis-issuances of certificates, accidental certificate revocation, duplicate certificate serial numbers, and multiple CAB Forum Baseline Requirements (BR) violations.”
Google also plans on taking drastic action against the two CAs next month. The tech giant has set up a whitelist for some Alexa Top 1M websites using certificates from WoSign and StartCom, but the whitelist will be removed starting with Chrome 61, currently scheduled for release in mid-September.
StartCom and WoSign are not the only CAs that got into trouble with web browser vendors as a result of misissued certificates. Symantec recently announced its decision to sell its certificate business to DigiCert for $950 million after Google announced that all certificates issued by the company will have to be replaced by October 2018, and new certificates would have to be issued through the infrastructure of a subordinate CA.
Smoke Loader Backdoor Gets Anti-Analysis Improvements
8.8.2017 securityweek Virus
The infamous Smoke Loader backdoor now has more complex anti-analysis techniques that allow it to remain a potent malware delivery mechanism, PhishLabs security researchers warn.
Also known as Dofoil, Smoke Loader has been advertised on dark web forums since at least mid-2011. Packing a modular design, the malware can receive secondary execution instructions and/or download additional functional modules. Lately, the loader has been used in the distribution of malware such as the TrickBot banking Trojan and GlobeImposter ransomware.
The Smoke Loader installer, the security researchers explain, spawns an EnumTools thread to detect and evade analysis tools, and uses an API to enumerate running analysis utilities. The malware checks for twelve analysis processes via a hash-based method, and terminates itself if one is found running. As part of an anti-VM check, it also queries the name and the volume information of the infected machine, along with a registry key.
“There are two main paths of execution in Smoke Loader, the installer and the loader. The installer path runs prior to spawning and injects into a new instance of a Windows Explorer process. Post injection, the loader runs and executes the core functionality of the module. Before injection occurs, Smoke Loader performs several checks to determine information about the system on which it is running,” PhishLabs says.
Smoke Loader was observed leveraging the VirtualProtect API call to change the protection of the allocated memory region, the security researchers reveal. Toward the end of the loader execution path, the malware also checks whether injection should occur, and execution continues if injection has not yet been performed.
The malware was observed performing networking checks to ensure the loader has Internet access (it can generate fake traffic for that). The security researchers also noticed that, unlike previous versions, the latest Smoke Loader variant uses a custom XOR-based algorithm to decode strings within the sample. Previously, the strings weren’t encoded.
“While Smoke Loader’s distribution is not as wide spread as other malware families, it is under continued development and very effective at what it does. The loader’s longevity indicates that the developers are committed to persistence and protection of their loader from the latest analysis techniques. Even though it dates back to 2011, the loader has undergone several transformations that allow it to continue to be a potent malware delivery mechanism in 2017,” PhishLabs concludes.
APT Trends report Q2 2017
8.8.2017 Kaspersky APT
Introduction
Since 2014, Kaspersky Lab’s Global Research and Analysis Team (GReAT) has been providing threat intelligence reports to a wide-range of customers worldwide, leading to the delivery of a full and dedicated private reporting service. Prior to the new service offering, GReAT published research online for the general public in an effort to help combat the ever-increasing threat from nation-state and other advanced actors. Since we began offering a threat intelligence service, all deep technical details on advanced campaigns are first pushed to our subscriber base. At the same time, to remain true to our efforts to help make the internet safer, important incidents, such as WannaCry or Petya are covered in both private and public reports.
Kaspersky’s Private Threat Intelligence Portal (TIP)
In Q1 of 2017 we published our first APT Trends report, highlighting our top research findings over the last few months. We will continue to publish quarterly reports as a representative snapshot of what has been offered in greater detail in our private reports in order to highlight significant events and findings we feel most users should be aware of. If you would like to learn more about our intelligence reports or request more information for a specific report, readers are encouraged to contact: intelreports@kaspersky.com.
Russian-Speaking Actors
The second quarter of 2017 has seen multiple incidents involving Russian-speaking threat actors. Topping the list of ‘attention grabbers’ were the Sofacy and Turla threat actors.
March and April started off with a bang, with the discovery of three zero-day exploits being used in-the-wild by Sofacy and Turla: two of these targeted Microsoft Office’s Encapsulated PostScript (EPS) and the third being a Microsoft Windows Local Privilege Escalation (LPE). Sofacy was discovered utilizing both CVE-2017-0262 (an EPS vulnerability) and CVE-2017-0263 (LPE) over the Easter holiday, targeting a swath of users throughout Europe. Prior to this attack, Turla was also discovered using CVE-2017-0261 (a different EPS vulnerability). Neither actor appeared to deviate from their usual payload repertoire, with Sofacy dropping their typical GAMEFISH payload and Turla utilizing what we refer to as ICEDCOFFEE (a.k.a. Shirime). Targeting for these attacks was also directly within the normal wheelhouse for both actors, focusing mainly on foreign ministries, governments, and other government-affiliated organizations.
GReAT produced additional reports on Sofacy and Turla beyond those mentioned above. In April, we notified customers of two new experimental macro techniques utilized by Sofacy. These techniques, while not particularly sophisticated, caught our attention as they had not been seen before in-the-wild. The first technique involved using the built-in ‘certutil’ utility in Microsoft Windows to extract a hardcoded payload within a macro. The second technique involved embedding Base64-encoded payloads within the EXIF metadata of the malicious documents. While the targeting for this new set of activity was again fairly standard, we discovered some noteworthy targeting against a French political party member prior to the 2017 elections. Moving into May and June, we wrote two additional reports of interest involving these two actors: the first was an update on the long running “Mosquito Turla” campaign showing the usage of fake Adobe Flash installers and continued targeting of foreign Ministries. The other documented yet another update on Sofacy’s unique Delphi payload we call ‘Zebrocy’.
June saw the massive outbreak of a piece of malware dubbed “ExPetr”. While initial assessments presumed that this was yet another ransomware attack à la WannaCry, a deeper assessment by GReAT places the initial intent as constituting an operation destructive in nature. We were also able to confidently identify the initial distribution of the malware, as well as indicate a low confidence assessment that the attacks may share traits with the BlackEnergy actors.
Below is a summary of report titles produced for the Eastern European region only. As stated above, if you would like to learn more about our threat intelligence products or request more information on a specific report, please direct inquiries to intelreports@kaspersky.com.
Sofacy Dabbling in New Macro Techniques
Sofacy Using Two Zero Days in Recent Targeted Attacks – early warning
Turla EPS Zero Day – early warning
Mosquito Turla Targets Foreign Affairs Globally
Update on Zebrocy Activity June 2017
ExPetr motivation and attribution – Early alert
BlackBox ATM attacks using SDC bus injection
English-Speaking Actors
English-speaking actors are always particularly fascinating due to their history of complex tooling and campaigns. Actors like Regin and Project Sauron have proven fascinating examples of new techniques leveraged in long-lasting, hard to catch campaigns and as such make ideal subjects for further research. Not to be outdone, Equation and the Lamberts were the subjects of our most recent investigations.
Continuing our practice of conducting malware paleontology while integrating new discoveries, we published a report on EQUATIONVECTOR, an Equation backdoor first used as early as 2006. This backdoor is a fascinating passive-active shellcode staging implant. It’s one of the earliest noted instances of a NObody But US (‘NOBUS’) backdoor for staging further attacks. Despite its age, the EQUATIONVECTOR backdoor (identified as ‘PeddleCheap’ in the latest ShadowBrokers disclosures) incorporates many advanced techniques for prolonged stealthy operations in victim networks, allowing the Equation operators to deliver further payloads without arousing suspicion. The report tracks the development of these tools through subsequent iterations year-by-year.
Our tracking of the Lamberts toolkit continues with the publication of the Gray Lambert report in June, the most advanced Lambert known to date. This too is a NOBUS backdoor, a passive implant operating strictly in user-land. The intricate usefulness of Gray Lambert lies in its ability to orchestrate multiple sniffer victims on a network via broadcast, multicast, and unicast commands, allowing the operators to employ surgical precision in networks with many infected machines. The sniffers double as next-stage payload delivery mechanisms for an infected network. A notable feature of the Lambert campaigns is the level of precision with which targets are chosen; Gray Lambert’s victimology is primarily focused on strategic verticals in Asia and Middle East. During this investigation, GReAT researchers have also discovered two additional Lambert families (Red Lambert and Brown Lambert) currently under investigation for Q3. Below is a list of report titles for reference:
EQUATIONVECTOR – A Generational Breakdown of the PeddleCheap Multifunctional Backdoor
The Gray Lambert – A Leap in Sophistication to User-land NOBUS Passive Implants
Korean-speaking Actors
Our researchers focusing on attacks with a Korean nexus also had a very busy quarter, producing seven reports on the Lazarus group and WannaCry attacks. Most of the reports on Lazarus directly involved a sub-group we refer to as BlueNoroff. They are the arm that focuses mainly on financial gain, targeting banks, ATMs, and other “money-makers”. We revealed to customers a previously unknown piece of malware dubbed ‘Manuscrypt’ used by Lazarus to target not only diplomatic targets in South Korea, but also people using virtual currency and electronic payment sites. Most recently, ‘Manuscrypt’ has become the primary backdoor used by the BlueNoroff sub-group to target financial institutions.
WannaCry also created quite a stir in the second quarter, with our analysts producing three reports and multiple blog posts on this emerging threat. What proved most interesting to us, was the probable linkage to Lazarus group as the source of the attacks, as well as the origins of the malware. GReAT researchers were able to trace back some of its earliest usage and show that before the ‘EternalBlue’ exploit was added to version 2, WannaCry v1 was used in spearphishing attacks months prior. Here is a listing of our reports from Q2 on actors with a Korean nexus:
Manuscrypt – malware family distributed by Lazarus
Lazarus actor targets carders
Lazarus-linked ATM Malware On the Loose In South Korea
Lazarus targets electronic currency operators
WannaCry – major ransomware attack hitting businesses worldwide – early alert
WannaCry possibly tied to the Lazarus APT Group
The First WannaCry Spearphish and Module Distribution
Middle Eastern Actors
While there wasn’t much high-end activity involving Middle Eastern actors, we did produce two reports revolving around the use of a zero-day exploit (CVE-2017-0199). The most notable involved an actor we refer to as BlackOasis and their usage of the exploit in-the-wild prior to its discovery. We have previously reported on BlackOasis using other zero-days in the past; CVE-2016-4117 in May 2016, CVE-2016-0984 in June 2015, and CVE-2015-5119 in June 2015. It is believed that BlackOasis is a customer of Gamma Group and utilizes the popular ‘lawful surveillance’ kit FinSpy. Other than the usage of the exploit, this report was significant because it also showed one of the earliest known uses of a new version of FinSpy, which is still being analyzed by our researchers.
After the discovery of CVE-2017-0199, a plethora of threat actors also began to leverage this exploit in their attacks. We reported to customers on the usage of this exploit by a well-known Middle Eastern actor dubbed ‘OilRig’. OilRig has actively targeted many organizations in Israel with the exploit via spearphishes appearing to originate from well-known doctors within Ben Gurion University. While their execution was less than stellar, it highlighted the widespread usage of this exploit shortly after its discovery.
OilRig exploiting CVE-2017-0199 in new campaign
BlackOasis using Ole2Link zero day exploit in the wild
Chinese-Speaking Actors
On the Chinese speaking front, we felt it necessary to produce two reports to our customers. While Chinese speaking actors are active on a daily basis, not much has changed and we prefer to avoid producing reports on ‘yet another instance of APTxx’ for the sake of padding our numbers. Instead we try to focus on new and exciting campaigns that warrant special attention.
One of those reports detailed a new finding regarding a fileless version of the well-known ‘HiKit’ malware dubbed ‘Hias’. We have reported on Hias in the past, and one of our researchers was finally able to discover the persistence mechanism used, which also allowed us to tie the activity to an actor we call ‘CloudComputating’.
Another report detailed a new campaign we referred to as ‘IndigoZebra’. This campaign was targeting former Soviet Republics with a wide swath of malware including Meterpreter, Poison Ivy, xDown, and a previously unknown malware called ‘xCaon’. This campaign shares ties with other well-known Chinese-speaking actors, but no definitive attribution has been made at this time.
Updated technical analysis of Hias RAT
IndigoZebra – Intelligence preparation to high-level summits in Middle Asia
Best of the rest
Sometimes we find new and exciting campaigns or entirely new threat actors to report to our subscribers without being able to make an immediate or definitive determination on regional provenance. Several reports fell into this category in the last quarter. ChasingAdder is a report describing a new persistence technique that hijacked a legitimate WMI DLL for the purposes of loading a malicious payload. This activity targeted high-profile diplomatic, military, and research organizations beginning in the fall of 2016, but to date we have not been able to pinpoint the specific actor responsible.
Demsty is a new piece of MacOS malware that is targeting University researchers in Hong Kong, among others. At the time of writing, we have a low confidence assessment that the campaign was conducted by Chinese-speaking actors, and thus categorize this as ‘Unknown’ until greater evidence comes to light.
During Q2, the mischievous ShadowBrokers also continued their regular activities dumping multiple tools and documentation allegedly stolen from Equation Group. In April, the ShadowBrokers released another dump of information detailing the alleged targeting of SWIFT service bureaus and other banks by Equation Group. Since some of our customers are financial entities, we found it necessary to evaluate the data and provide an expert’s opinion on the validity of the dump.
Reports in the ‘unknown’ category:
ShadowBrokers’ Lost in translation leak – SWIFT attacks analysis
ChasingAdder – WMI DLL Hijacking Trojan Targeting High Profile Victims
University Researchers Located in Hong Kong Targeted with Demsty
Predictions
Based on the trends we’ve seen over the last three months, as well as foreseeable geopolitical events, we have listed a few predictions for the upcoming quarter (Q3). As always, this isn’t an exact science and some cases won’t come to fruition. Analyzing current and future events and combining those with the motivations of known active actors can help organizations prepare for likely forthcoming activity:
Misinformation campaigns will remain a threat to countries with upcoming elections, specifically Germany and Norway, as they have been previous targets for Eastern European based actors.
‘Lawful Surveillance’ tools will continue to be utilized by governments that don’t have well-established Cyber Operations capabilities, mainly based out of the Middle East. Companies such as Gamma Group, Hacking Team, and NSO will continue to offer new zero-day exploits to those customers. As prices increase and exchanges thrive, new organizations and marketplaces will continue popping up.
Destructive malware disguised as ransomware will continue to be a problem. In the last quarter we’ve seen two instances of this, and with the continued release of tools / exploits from dumps like Vault7 and ShadowBrokers, this is going to be a new alarming trend to deal with.
In China, the past months have been marked by the dwindling economic growth, rising tensions with North Korea and the US, and increased exchanges between South Korean / Japanese / American organizations. In addition to these, the 19th Party Congress is set to be held in the fall of 2017 and according to multiple public predictions, it is likely that some major changes will happen in the leadership. It’s possible that these events will have wide regional influences that could affect the way that threat actors operate in Asia, both in terms of targeting and TTPs.
Targeting energy-related companies and organizations will be on the rise. Countries such as Norway may be a top target moving forward given their control on oil and gas in the region in the buildup to an election. Saudi Arabia will also top the charts for potential targeting as they have in years past.
Lower-tier threat actors continue to increase cyber-espionage efforts and capabilities both in complexity and size. Expect more activity with varied technical capabilities coming from lesser known or previously unseen actors.
How to keep yourself protected
One of the biggest problems when it comes to leveraging threat intelligence is judging the quality of the data and how it can be used for defense. For instance, we may observe an increase in the number of fileless attacks or attacks in which all IOCs are unique or specific per victim. In such situations, having not only host-based IOCs, but also network IOCs and Yara rules that can help identify malware in all cases is very important.
Another problem comes from the fact that many threat intelligence providers have a limited world view and their data covers only a small set of threats. It’s easy for an enterprise to fall into the trap of thinking that ‘actor X’ is not something they need to worry because their focus has been only certain countries or certain industry sectors; only to discover later that their ignorance left them blind to those attacks.
As shown by many incidents, but especially by WannaCry and ExPetr’s EternalBlue-based spreading subroutines, vulnerabilities remain a key approach to infecting systems. Therefore timely patching is of utmost importance – which, being one of the most tedious IT maintenance tasks, works much better with good automation. Kaspersky Endpoint Security for Business Advanced and Kaspersky Total Security include Vulnerability & Patch management components, offering convenient tools for making patching much easier, and much less time-consuming for IT staff.
Given the above, it is highly recommended that prevention (such as endpoint protection) along with advanced detection capabilities, such as a solution that can detect all types of anomalies and scrutinize suspicious files at a deeper level, be present on users’ systems. The Kaspersky Anti Targeted Attack solution (KATA) matches events coming from different infrastructure levels, discerns anomalies and aggregates them into incidents, while also studying related artifacts in a safe environment of a sandbox. As with most Kaspersky products, KATA is powered by HuMachine Intelligence, which is backed by on premise and in lab-running machine learning processes coupled with real-time analyst expertise and our understanding of threat intelligence big data.
The best way to prevent attackers from finding and leveraging security holes, is to eliminate the holes altogether, including those involving improper system configurations or errors in proprietary applications. For this, Kaspersky Penetration Testing and Application Security Assessment services can become a convenient and highly effective solution, providing not only data on found vulnerabilities, but also advising on how to fix it, further strengthening corporate security.
Internetové hrozby v Česku: Chromex v červenci srovnal krok s malwarem Danger
8.8.2017 SecurityWorld Viry
Eset varuje před trojským koněm JS/Chromex.Submelius, který se šíří přes neoficiální streamovací služby.
Sledování neoficiálních streamovacích stránek na internetu se během léta řadě Čechů nevyplatí. Mnoho těchto webů je totiž infikováno trojským koněm JS/Chromex.Submelius a pro spuštění videa vyžadují několikeré kliknutí na náhled videa, které otevírá nová okna prohlížeče a zobrazuje v nich reklamy.
Tyto weby v některých případech fungují na doménách .cz a .sk a obsahují nabídky instalace škodlivých pluginů. Eset zaznamenal během července takřka stejný počet detekcí tohoto trojského koně jako u v poslední době nejčastější tuzemské internetové hrozby, malwaru JS/Danger.ScriptAttachment.
JS/Chromex.Submeliux o prvním prázdninovém měsíci představoval 16,72 procenta zachycených hrozeb, malware JS/Danger.ScriptAttachment dosáhl podílu 17,50 procenta.
„Nárůst detekcí trojského koně JS/Chromex.Submeliux může souviset s obdobím prázdnin. Právě v této době více uživatelů využívá neoficiální streamovací služby a stahuje si nabízené pluginy,“ říká Miroslav Dvořák, technický ředitel společnosti Eset. „Pluginy však mají naprosto opačný efekt. Navíc mohou do napadeného zařízení instalovat downloader,“ vysvětluje Dvořák.
Nejčetnější internetovou hrozbou zůstává JS/Danger.ScriptAttachment. Tento škodlivý kód se šíří především prostřednictvím příloh nevyžádaných e-mailů.
„Neškodí jen sám o sobě, dokáže do napadeného zařízení stáhnout další škodlivé kódy včetně vyděračského ransomware, který zašifruje obsah zařízení a požaduje po oběti výkupné,“ varuje Dvořák.
Třetí nejčastěji zaznamenanou hrozbou v červenci byl škodlivý kód JS/Adware.AztecMedia. Ten v internetovém prohlížeči otevírá nevyžádaná okna s reklamou. V některých případech dokáže dokonce i změnit domovskou stránku internetového prohlížeče. V červenci představoval 4,36 procenta zaznamenaných hrozeb v České republice.
Deset nejčastějších internetových hrozeb v České republice za červenec 2017:
1. JS/Danger.ScriptAttachment (17,50 %)
2. JS/Chromex.Submeliux (16,72 %)
3. JS/Adware.AztecMedia (4,36 %)
4. Win32/GenKryptik (2,29 %)
5. SMB/Exploit.DoublePulsar (2,25 %)
6. PDF/Fraud (1,90 %)
7. JS/Adware.BNXAds (1,88 %)
8. Java/Kryptik.FN (1,77 %)
9. Java/Kryptik.FL (1,76 %)
10. HTML/Frame (1,44 %)
Hackeři ovládli stránky venezuelské vlády, podpořili rebely
8.8.2017 Novinky/Bezpečnost BigBrother
Do boje proti vládě venezuelského prezidenta Nicoláse Madura vytáhli po parlamentní opozici a statisících protestujících lidí rovněž počítačoví piráti. Skupina hackerů v pondělí napadla stránky vlády a několika dalších státních orgánů a dala najevo podporu vzbouřencům z kasáren na severu země, jejichž vzpouru o víkendu potlačily bezpečnostní složky. Uvedl to web stanice BBC.
Venezuelský prezident Nicolás Maduro
"Dny diktatury jsou sečteny," objevilo se ve zprávě hackerů na stránkách vlády, volební komise či venezuelského námořnictva. Opozice stále častěji označuje Madurovy kroky za diktátorské a tento pojem se začal objevovat zejména v souvislosti se široce kritizovanými volbami Ústavodárného shromáždění, které opozice bojkotovala jako Madurovu snahu nedemokraticky si upevnit moc.
Hackeři dali najevo podporu skupině vojáků a civilistů, která vyhlásila v kasárnách ve třetím největším městě země Valencie rebelii. Vláda ji následně potlačila, přičemž zemřel nejméně jeden člověk. Maduro označil rebely za teroristy.
Ve Venezuele už od dubna trvají téměř každodenní protesty proti vládě, kterou opozice viní z ekonomické a politické krize. Při demonstracích, proti nimž tvrdě zasahuje policie, zemřelo už přes 120 lidí. Podle opozice roste počet vojáků, kterým se nelíbí užití síly proti demonstrantům a autoritářská vláda. Od dubna skončily ve vězení nejméně dvě desítky armádních důstojníků kvůli "rebelii a zradě".
China's Web Users Fear Losing Tools to Bypass 'Great Firewall'
8.8.2017 securityweek BigBrothers
Enterprising internet users in China fear the tools they use to tunnel through the country's "Great Firewall" may soon disappear, as Beijing tightens its grip on the web.
Tens of millions of people are estimated to use Virtual Private Networks (VPNs) to bypass Chinese internet restrictions -- getting access to blocked websites such as Facebook and Twitter.
Beijing has for years turned a blind eye to these holes in its Great Firewall, but recent events suggest the virtual tunnels may soon be bricked up.
In January China's Ministry of Industry and Information Technology (MIIT) announced it would be banning the use of unlicensed providers of the services.
In the months since the rule's announcement, rumours have swirled that a crackdown was coming, but there was little clarity on what exactly the rule meant and how, or even if, it would be implemented.
In the past few weeks, however, omens of significant tightening seem to be everywhere.
Several luxury hotels in Beijing have said they will stop using the tools, which once provided unfiltered Internet as a convenience to their customers.
On Thursday, a cloud service provider in the capital notified users that it would practise shutting down and reporting VPN providers on the orders of Beijing's Public Security bureau.
Tech giants Apple and Amazon, too, have moved to limit their customers' access to the tools in China in what has been seen as a voluntary move to get ahead of the impending crackdown.
On Sunday, Apple said it was removing a number of the programs from its app store, while Amazon's Chinese partner said that customers would no longer be allowed to use "illegal" VPNs on its cloud service.
"There have been many rounds of government murmurings about VPN crackdowns, and foreign and Chinese businesses had grown used to only minor or temporary restrictions," said Graham Webster, a senior researcher scholar at Yale Law School.
But "this time appears different."
'You cannot lock the heart'
For now, however, it still remains unclear who will be able to access VPNs and under what circumstances, a situation that has left both companies and regular users on tenterhooks.
Ordinary people have reacted to the new rules with a mixture of annoyance and quiet defiance.
"You've blocked the last way to watch US TV dramas, as well as my Facebook friends!" one user of China's Twitter-like Weibo platform said after the Apple announcement.
"You can lock my cellphone, but you cannot lock my heart."
Firms are casting around for information about the developments and have expressed alarm at the potential impact on the way they do business.
In a statement, the European Chamber of Commerce told AFP it "has not seen any updated official document concerning restrictions on VPN use by companies," adding that in a recent survey of its members almost half expressed concern that the "continued strengthening of measures to tighten Internet control and access are having an even bigger negative impact on their companies".
"Our members' success depends on instantaneous access to information worldwide, and the ability to freely communicate with affiliates, suppliers and customers around the world," William Zarit, Chairman of the American Chamber of Commerce in China said in a statement to AFP.
"Recent regulatory developments, including limiting VPN use, have created uncertainty for cross-border data communication."
Apple has come under fire for bowing to the rules, but in an earnings call Tuesday CEO Tim Cook said the firm had to follow local laws.
He said Apple was "hopeful that over time the restrictions we're seeing are lessened, because innovation really requires freedom to collaborate and communicate".
'Tighten Internet control'
Analysts said that Beijing was likely not looking to choke off VPNS completely, but was instead seeking to control them more tightly.
James Gong, an expert on Chinese cyber law at Herbert Smith Freehills, said that the regulations are not targeted at companies.
The government can "shut things down, but that's not their purpose," he said.
Instead "they want to drive all the traffic through the network operators so all of the connections will be transparent to them".
Paul Triolo, head of global technology at the Eurasia Group, said he believes that the ultimate goal is not to cut off all VPNs but to "get visibility on (their) use so that they know what is going in and out and can turn off selectively if they want to or need to".
In a statement to AFP last month, MIIT explained that under the new rules, companies will only be allowed to rent VPN services from "telecommunications operators that have set up an international communications entry and exit office in accordance with the law".
Previously released MIIT regulations state that only state-owned telecoms can set up the offices, effectively guaranteeing that all licensed VPNs are operated by the state.
A representative from state-owned telecom China Unicom confirmed to AFP that it was legally allowed to rent VPN services to businesses, as long as they provide proof of registration in China.
"It's highly unlikely that all VPN access would be eliminated," Yale's Webster said, but added in the future the software might be increasingly "expensive and government-controlled".
FTC Complaint Alleges Hotspot Shield Collects User Data
8.8.2017 securityweek IT
A complaint filed with the Federal Trade Commission (FTC) on Monday alleges that the popular free Virtual Private Network (VPN) service Hotspot Shield collects a large amount of data and intercepts user traffic.
Submitted by the Center for Democracy & Technology (CDT), the complaint (PDF) urges the FTC to investigate the data security and data sharing practices of Hotspot Shield, alleging they are “unfair and deceptive trade practices.” The complaint also claims the service engages into undisclosed data sharing and traffic redirection practices despite promising to protect the users’ privacy.
CDT, a nonprofit technology advocacy organization, suggests that Hotspot Shield’s privacy policy contradicts the advertised privacy and security claims. The service claims to keep no logs of a user’s online activity or personal information, and to store no user data, while also saying that it doesn’t track users and doesn’t sell their information.
The privacy and security claims are highlighted as key features of the Hotspot Shield VPN mobile applications in both iTunes and Google Play storefronts, but the service’s privacy policy “describes more elaborate logging practices,” the complaint reads. A source code analysis of Hotspot Shield backs these allegations, CDT says.
The organization also claims that “the VPN promises to connect advertisers to users who frequent websites in particular categories and while most VPNs prevent internet service providers from seeing a user’s internet traffic, that traffic is often visible in unencrypted form to Hotspot Shield. VPNs typically log data about user connections to help with troubleshooting technical issues, but Hotspot Shield uses this information to identify user locations and serve advertisements."
CDT also points out that Hotspot Shield’s privacy policy says that it doesn’t collect personal user information, claiming that IP addresses and unique device identifiers aren’t considered personal information by the free VPN provider. Moreover, the complaint claims the service deploys persistent cookies and that it also “works with unaffiliated entities to customize advertising and marketing messages.”
Furthermore, the complaint alleges that Hotspot Shield insists it doesn’t make money from selling customer data, but that the service also promises to connect advertisers to users that frequently access travel, retail, business, and finance websites. CDT points out that these partners can link information about users’ web-viewing habits even if they are provided only with hashed or proxy IP addresses.
An analysis of Hotspot Shield’s functionality, data sharing, and network connections was performed by Carnegie Mellon University’s Mobile App Compliance System. Researchers downloaded and tested the Android app and found “undisclosed data sharing practices with third party advertising networks” when analyzing the application permissions.
They also discovered that the app discloses sensitive information such as names of wireless networks (via SSID/BSSID information), along with identifiers such as Media Access Control addresses, and device IMEI numbers.
The VPN was also found to inject JavaScript codes using iframes for advertising and tracking purposes, and to be using more than five different third-party tracking libraries. The apps also redirect e-commerce traffic to partnering domains, the complaint also claims.
“People often use VPNs because they do not trust the network they’re connected to, but they think less about whether they can trust the VPN service itself. For many internet users, it’s difficult to fully understand what VPNs are doing with their browsing data. Hotspot Shield tells customers that their privacy and security are ‘guaranteed’ but their actual practices starkly contradict this. They are sharing sensitive information with third party advertisers and exposing users’ data to leaks or outside attacks,” Michelle De Mooy, Director of CDT’s Privacy & Data Project, said.
Irish electricity transmission system operator EirGrid targeted by a nation-state actor
8.8.2017 securityaffairs BigBrothers
The Irish electricity transmission system operator EirGrid was targeted by a state-sponsored actor, the hackers weren’t discovered at least for two months.
The Irish electricity transmission system operator EirGrid was targeted by a state-sponsored attack. EirGrid is the state-owned company that operates the electricity transmission grid across the Ireland, it also supplies the distribution network operated by ESB Networks that powers every electricity customer in the country.
According to the Independent.ie, a nation-state actor, using IP addresses sourced in Ghana and Bulgaria targeted the company. The hackers first gained access to a Vodafone network used by EirGrid in the UK in April, then they compromised the routers used by Irish operator in Wales and Northern Ireland.
The hackers were able to install “a virtual wire tap”, also known as Generic Routing Encapsulation (GRE) tunnel into Eirgrid’s Vodafone router located in Shotton. The GRE allowed them to access the unencrypted traffic sent to and from the companies.
According to the Independent.ie the hackers weren’t discovered at least for two months and the worst aspect of the story is that sources informed of the hack confirmed that it is still not known if any malware still present onto EirGrid’s control systems.
An attacker could be interested in hacking systems at the company to trigger a massive power outage across the country.
“Independent.ie has learned that the hack came to light after a tip-off from Vodafone and the National Cyber Security centre in the UK to EirGrid.” reported the Independent.ie.
“Vodafone discovered that there had been a breach on their Direct Internet Access (DIA) service which is internet provider to Eirgrid’s interconnector site in Shotton, Wales. The original breach took place on April 20 and lasted just short of seven hours.”
A source said that both Vodafone and the National Cyber Security Centre believe the attack was powered by a nation-state actor, while police services in Ireland and the UK do not believe that it was powered by foreign hackers.
Independent.ie discovered that all communications leaving the Eirgrid site and passing through the DIA router were “monitored and maybe interrogated” by a third party with direct access to the device.
At the time of this post, Vodafone is still investigating the volume of traffic transferred over the GRE tunnel.
“However it was able to tell the state supplier that all the compromised router devices had their firmware and files copied by the attackers.” state the Independent.
“A source said this allows the hackers to inspect the network configuration of Vodafone and “possibly launch a further more devious attack through some unknown vulnerabilities”.”
A further internal investigation revealed that the offices of the System Operator for Northern Ireland (SONI), that is wholly owned by EirGrid, were also exposed due to the cyber attack.
“At EirGrid Group, the security of our computer network and of the electricity control system is an utmost priority.” said David Martin, a spokesperson for EirGrid Group.
“We take all necessary steps to ensure that our systems are secure and protected and we remain vigilant to potential cyber threats, by continuously monitoring the external environment and by engaging with the relevant authorities.”
“It is EirGrid Group’s policy not to comment publicly on specific operational matters related to cyber security, however, we are aware of the currently reported focus on energy companies and national infrastructure and wish to state that our computer systems have not been breached.”
“Vodafone does not comment on specific security incidents. In such cases we always work closely with the relevant authorities to investigate and take immediate actions to contain the issue and protect our customers.” said a Vodafone spokesman.
Spam Rate Hits Two-Year High
7.8.2017 securityweek Spam
In July 2017, global spam rate reached the highest level registered since March 2015, fueled by the emergence of malware families attempting to self-spread via email, according to Symantec.
The global spam rate last month was 54.9%, registering a 0.6 percentage point increase compared to the previous month. Driving the rate upwards was, among other factors, the appearance of malware variants that could spread via spam emails.
The surge was also mirrored in an increase in email malware rate, which reached one in 359 emails in July, up from one in 451 during the previous month. This is the highest rate registered this year, but still lower than the levels registered at the end of last year (the rate reached one in 111 emails in November 2016).
The number of new malware variants, however, went down in July 2017, dropping from 66.3 million to 58.7 million variants, Symantec’s Latest Intelligence report shows.
“This trend in malware being distributed through email seems to be catching on, with several infamous malware families recently adding functionality that allows them to spread via spam email,” Symantec said.
Earlier this year, threats such as WannaCry and NotPetya proved how effective worm-like spreading capabilities could be, and various malware families out there adopted similar tactics. The Emotet banking Trojan added the ability to steal email credentials from infected computers and use them to send spam and spread itself.
The TrickBot banking malware added a module to leverage SMB and spread to computers on the same network (but the functionality isn’t yet active) and also started targeting Outlook data. A ransomware family called Reyptson was observed last month packing the ability to steal Thunderbird email client credentials to send spam messages containing a link to its executable.
“Attackers are increasingly making use of tools already installed on targeted computers or are running simple scripts and shellcode directly in memory. This allows them to minimize the risk of their attacks being discovered and blocked by traditional security tools,” Symantec notes.
The rate of phishing attacks went up as well, reaching one in 1,968 emails, the highest level observed during the past 12 months. The number of web attacks blocked by Symantec decreased slightly, from 1,159,398 per day to 1,158,985 per day. Despite that, July was the fourth consecutive month with elevated web attack activity.
The Mining sector had the highest spam rate (59.1%), followed by Manufacturing (56.9%). The Mining sector had the highest phishing rate at one in 1,263 emails, while the Agriculture, Forestry, & Fishing sector had the highest email malware rate at one in 152 emails.
During July, security researchers also discovered a new type of attack targeting fresh installations of WordPress. As part of the attack, cybercriminals are scanning for a specific setup URL used in new installations of the content management system, and then take over the installation as it hasn’t been yet configured, replacing legitimate resources with their own, and even compromising hosting accounts and all other sites on that account.
Schneider Electric, Claroty Partner on Industrial Network Security
7.8.2017 securityweek ICS
Energy management and automation giant Schneider Electric has teamed up with industrial cybersecurity startup Claroty to offer its customers solutions for protecting industrial control systems (ICS) and operational technology (OT) networks.
Claroty, which emerged from stealth mode in September 2016 with $32 million in funding, will market its products through Schneider’s Collaborative Automation Partner Program (CAPP).
Schneider’s CAPP enables its customers to find the right technology solutions and integrate them with the company’s own offering. Claroty, whose products have undergone rigorous testing to ensure interoperability, will provide network monitoring solutions.
Claroty’s platform is designed to protect ICS and continuously monitor OT networks for threats without disrupting operations. The product enables organizations to control remote employee and third-party access to critical systems, including record their sessions. It also creates a detailed inventory of industrial network assets, identifies configuration issues, monitors traffic, and looks for anomalies that could indicate the presence of a malicious actor.
The product can be integrated with Schneider Electric’s existing cybersecurity and edge control offerings through the company’s EcoStruxure architecture.
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
“At Schneider Electric we recognize the urgent need to assist our customers in enhancing their safety and cybersecurity programs. One way we are addressing this need is through partnering with Claroty to provide real-time network monitoring and anomaly-detection,” said David Doggett, senior director of cybersecurity for Schneider Electric’s Industry Business.
“Passive network intrusion detection techniques are critical for applications where system availability is paramount,” Doggett added. “Claroty’s platform can strengthen solutions against known cyber attacks that have bypassed existing boundary protections. The technology can also alert network operators about novel attack vectors or attacks initiated by rogue insiders using existing tools and credentials.”
Schneider Electric is not the only automation giant that has teamed up with Claroty. In February, Rockwell Automation announced a partnership with the company for combined security offerings.
British model Chloe Ayling kidnapped by Black Death group for auction in the dark web
7.8.2017 securityaffairs Crime
The British model Chloe Ayling kidnapped in Italy by an alleged member of the ‘Black Death’ organisation who offered her on the Dark Web
The 20-year-old British model Chloe Ayling was kidnapped in Milan, Italy, to be auctioned off on a pornographic website on the dark web. According to the declaration of the model to the Italian State Police, Chloe Ayling was assaulted, drugged, handcuffed and stuck in a travel bag.
The model arrived in Milan on July 10 to have a photo shoot booked through her agent, but it was a trap.
When she walked into the apartment where the photo shoot was supposed to take place, at least two men assaulted her.
She was loaded into the trunk of a car and taken to a chalet in Lemie, a remote town in the Italian Alps, where she was kept handcuffed to a wooden chest of drawers in a bedroom for a week,
The Polish national Lukasz Herba (30), who resides in the United Kingdom, was arrested on kidnapping charges on July 17 outside the British consulate in Milan while he was accompanying the woman.
Herba told her he had earned €15 million over five years of selling women, many of whom were sent to Arab countries.
The story is very strange, there are still unclear points, for example why Lukasz Herba decided to bring the model to the consulate.
According to the investigation, the man acted with the support of accomplices, he used an encrypted account to ask the model’s agent a $300,000 ransom worth of Bitcoin to halt the online auction from going ahead.
The man claims to be a member of the “the Black Death” group, an organization operating in the dark web involved in illegal trafficking and trading of illegal products, including drugs, weapons, and explosives.
Below the ‘Black Death’ full statement of British model’s release published by the Mirror:
“You are being released as a huge generosity from Black Death Group. Your release does, however, come with a warning and you should read this letter very carefully.You are certainly aware of your value on human slavery market (sic) and must make a note that this isn’t personal, this is business. For your release we have taken a number of factors into consideration.A mistake was made by capturing you, especially considering you are a young mother that should have in no circumstances be lured into kidnapping.Second important factor (sic) you are very well aware of is your overall protection by one of our main and very well respected men who made a very clear and solid stance in your case.You will, upon your landing in your home country cease any investigation activities related to your kidnapping. You also agreed to sneak a pre-determined set of information in to the media and we will expect to see evidence that has been done in the near future.
“The ad by Black Death Group – which refers to victims as “merchandise” – also features a series of horrifying promises about the women they traffic and a list of the woman’s personal details – including her dimensions.” continues The Mirror.
A letter from the group which explains how the model was treated with “huge generosity” in being released (Image: Splash News)
The Black Death claims they can “kidnap a specific target for your needs” and assure free “EU delivery” of victims.
In 2015, the journalist Joseph Cox tried to infiltrate the group, he tried to buy a girl called ‘Nicole’ being advertised on their site.
Joseph discovered a link to Black Death website on the social media site Reddit, he emailed the group stating he was “interested in the girl”, adding he “wanted to see more photos first.”
Cox said the Black Death group replied with “Do not contact us just to ask questions”, followed up with “Who are you, how do you know about is? Who recommended us?” Cox received a list of detailed instructions for an online auction of girls in which he could view a live stream of them.
“After requesting to see the girls without offering any upfront payments, Joseph’s access was denied.”
The group continuously changes the address of their website in the dark web, according to Cox in the short time after he contacted Black Death, another girl was added to their website.
The crooks started a bid of $180,000, they included the high-quality images of the victims. The images contained no pieces of metadata, and a reverse image search did not return any results.
An adviser to from the National Crime Agency’s UK Human Trafficking Centre told Joseph Cox: “The dark web is not somewhere we can pick up a lot of stuff from.”
The adviser highlighted that there were a number of obvious differences between Black Death and other organized human trafficking groups selling men and women online.
Investigation is still ongoing in Italy, Poland, and UK.
Experimental Mozilla Send service allows users share encrypted copy of huge files
7.8.2017 securityaffairs Krypto
Mozilla Send service allows users to make an encrypted copy of a local file, store it on a remote server, and share it with a single recipient.
Mozilla has presented Send, an experimental service that allows users to make an encrypted copy of a local file, store it on a remote server, and share it with a single recipient. The service allows to easily share large files in a secure way.
Once the copy has been shared, the data will be deleted from the server.

The Send service is offered through Mozilla’s Test Pilot program for previewing new features developed for the Firefox browser.
The Send service was developed on Node.js backed by a Redis database running on Amazon Web Services. It relies on the Web Cryptography JavaScript API with the AES-GCM algorithm for client side encryption. Using the Send service is very simple, upon selecting a local file, the Mozilla application encrypts it client-side and uploads it to AWS.
Then the user will receive an URL generated by the Mozilla Send service that contains the encryption key, this link can be shared with the recipient of the file.
“Each link created by Send will expire after one download or 24 hours, and all sent files will be automatically deleted from the Send server,” reads a blog post published by Mozilla.
Of course, the first thought is for privacy issues, but Mozilla clarified that it would not be able to unlock a stored file, even upon receipt of a lawful warrant.
Giving a look at the generated URL it is possible to note that a portion of the link after the character ‘#’ contains the generated key that is not sent to the Mozilla server.
Experts argue that anyway AWS is able to recover a file, for example, upon receipt of a lawful warrant it could be forced to retain them. The Send service sends the file name and other data in plain text.
The keys generated by the Mozilla Send service might be recoverable from the messaging service used to share it or from log files.
Send service is an ongoing experimental project, Mozilla is updating it continuously, if you are curious you can access the GitHub repository and look at the open issues.
FireEye Provides Update on the alleged data breach revealed late July
7.8.2017 securityaffairs Incindent
Late July, hackers posted details alleged stolen from a system belonging to a Senior Analyst at security firm FireEye/Mandiant. The company provides update.
Late July, hackers have posted details alleged stolen from a system belonging to Adi Peretz, a Senior Threat Intelligence Analyst at security firm FireEye/Mandiant.
The leaked archive is a 337MB PST file containing the expert’s emails. Leaked archive also includes images of its accounts, including One Drive, Live, LinkedIn, geo-tracking of personal devices for at least a year, billing records and PayPal receipts.

“In addition to that are images detailing the compromise of their One Drive account, Live account, LinkedIn account, geo-tracking of personal devices for at least a year, billing records and PayPal receipts, credentials for an engineering portal at FireEye, WebEx and JIRA portals, as well as Live and Amazon accounts. There are also records related to an alleged customer, Bank Hapoalim, and internal documentation and presentations, including one for the IDF (Israel Defense Forces) from 2016.” reported Salted Hash.
The security firm has denied any intrusion in its systems, while the hackers who published the alleged Mandiant Internal Leaks claimed it was part of the ongoing campaign #OpLeakTheAnalyst.
Today FireEye provides an update on the event following its investigation into allegations made earlier this week that FireEye had been breached. As background, on July 31,
According to the security firm, the hackers did not hack the company network or the Adi Peretz’s personal or corporate computers.
The login credentials used by Peretz were exposed in the past in numerous data breaches, including LinkedIn.
The experts discovered that the attackers started using the stolen credentials to access several of the Victim’s personal online accounts (LinkedIn, Hotmail and OneDrive accounts) in September 2016.
The documents publicly released were obtained from the Victim’s personal online accounts and many of them were already available online.
Below the list of conclusions published by FireEye in a blog post.
The Attacker did not breach, compromise or access our corporate network, despite multiple failed attempts to do so.
The Attacker did not breach, compromise or access the Victim’s personal or corporate computers, laptops or other devices.
We confirmed the Victim’s passwords and/or credentials to his personal social media and email accounts were among those exposed in at least eight publicly disclosed third party breaches (including LinkedIn) dating back to 2016 and earlier.
Starting in September 2016, the Attacker used those stolen passwords and/or credentials to access several of the Victim’s personal online accounts, including LinkedIn, Hotmail and OneDrive accounts.
The Attacker publicly released three FireEye corporate documents, which he obtained from the Victim’s personal online accounts.
All of the other documents released by the Attacker were previously publicly available or were screen captures created by the Attacker.
A number of the screen captures created by the Attacker and posted online are misleading, and seem intentionally so. They falsely implied successful access to our corporate network, despite the fact that we identified only failed login attempts from the Attacker.
FireEye highlighted that the Victim supports a small number of customers, only two of them were impacted by the leak.
Below the actions conducted by FireEye:
We contacted the two identified customers as soon as we learned of this incident and have kept them apprised of the situation throughout the week.
We immediately contained the Victim’s systems.
We collected and reviewed forensic data from the Victim’s systems.
We disabled the Victim’s FireEye corporate accounts.
We worked with the Victim to regain control of his personal online accounts.
We worked with the Victim to secure his personal online accounts, including implementing multi-factor authentication where possible.
We communicated to all FireEye employees, both verbally and in writing, a reminder to be vigilant and provided detailed steps to best secure their personal accounts.
We worked with the Victim and his online third party service providers to obtain any available log data that could assist our investigation.
We reviewed all data sent to and from FireEye email to the Victim’s online accounts.
We reviewed authentication and access activity on the Victim’s corporate, single sign-on (SSO), multi-factor, and third-party accounts.
The investigation is still ongoing.
Německo musí podle expertů přitvrdit postupy proti kyberzločinu
7.8.2017 Novinky/Bezpečnost BigBrother
Tvrdší postup v boji proti kyberkriminalitě, ilegálním praktikám v anonymní sféře internetu známé jako darknet a dalším organizovaným zločineckým strukturám požaduje šéf německého Spolkového kriminálního úřadu (BKA) Holger Münch. Proti hrozbám na internetu se nedá bojovat zbraněmi z doby kamenné, řekl listu Die Welt a v interview požaduje zpřísnění zákonů a zejména trestního postihu kyberzločinců.
"Profesionální hackeři mohou způsobit ohromné škody. Představují nebezpečí pro bezpečnost i ekonomiku. A to se musí výrazně odrazit ve výměře trestu," prohlásil Münch. Poukázal přitom na 82 000 případů kyberzločinů zaregistrovaných v loňském roce se škodou vyčíslenou na více než 51 miliónů eur (asi 1,3 miliardy korun).
Na darknetu bují obchody s drogami, zbraněmi a dětskou pornografií, napsal Die Welt. Ten, kdo tyto ilegální platformy provozuje, ale musí počítat jen s mírnými tresty, stejně jako prostí hackeři.
Názorně o tom svědčí podle deníku jeden z nedávných případů. Profesionální hacker, 29letý Brit Daniel K. narozený v Izraeli, působící pod přezdívkou Spiderman, byl po mnohaměsíčním pátrání v únoru dopaden na londýnském letišti. Spiderman stál v listopadu 2016 za kyberútokem na servery telekomunikační skupiny Deutsche Telekom - výpadek sítě tehdy postihl kolem 1,25 miliónu jejích zákazníků, kteří se museli několik dnů obejít bez internetu, telefonu a digitální televize. Telekom vyčíslil způsobenou škodu na více než dva milióny eur (asi 52 miliónů korun).
Trestní zákoník musí být reformován
Před soudem ale Spiderman vyvázl v porovnání s výší způsobené škody s nanejvýš mírným trestem. Koncem července ho zemský soud v Kolíně nad Rýnem odsoudil k podmínečnému trestu jednoho roku a osmi měsíců odnětí svobody. Horní hranice trestní sazby přitom činí deset let, obžaloba žádala dva roky. Soud ale poukázal na plné doznání obžalovaného a lítost, kterou projevil.
"Trestní zákoník za kybernetické zločiny musí být reformován a modernizován, jinak nemohou být dostatečně potrestány mnohé ze zločinů, s nimiž se setkáváme," řekl německému listu Georg Ungefuk z generální prokuratury ve Frankfurtu nad Mohanem, dlouholetý uznávaný odborník působící v Ústřední agentuře pro boj s internetovou kriminalitou (ZIT).
Bavorský ministr vnitra Joachim Herrmann, jehož strana by ho ráda viděla na postu spolkového ministra vnitra po zářijových parlamentních volbách, říká, že Německo potřebuje komplexnější přístup ke kyberkriminalitě, navzdory své decentralizované federální struktuře, která převádí velkou odpovědnost na jednotlivé spolkové země.
"Kompetence mezi spolkovou vládou, spolkovými zeměmi a armádou jsou v kybernetické sféře dokonce ještě nejasnější než v boji proti terorismu," řekl Herrmann listu Die Welt. "Potřebujeme nové struktury."
Flaws in solar panels potentially threatening European power grids
7.8.2017 securityaffairs Hacking
The Horus scenario, is a scenario describing a large scale cyber attack targeting the vital electrical infrastructure triggering flaws found in solar panels
Willem Westerhof, a Dutch security researcher at the security firm ITsec has found a serious vulnerability in a component of solar panels that could be exploited by hackers to cause widespread outages in European power grids.
The vulnerability resides in the inverters that are the components of solar panels used to convert direct current to alternating current.
The vulnerabilities affect the inverters manufactured by the German market leader SMA. Westerhof reported the issued to the company in December 2016, and SMA invited him to discuss his findings. Unfortunately, after six months nothing is changed and the SMA still hasn’t solved the issue.
Westerhof has published a detailed analysis of the vulnerability and of the attack scenario that was dubbed by the expert Horus Scenario, after the Egyptian deity.
According to the Dutch newspaper Volkskrant, Westerhof claims that the security flaw affects thousands of Internet-connected inverters used in European power grids.

Source Volkskrant.nl
The attack scenario hypothesized by the expert is disconcerting, it sees hackers taking control of a large number of inverters and switch them off simultaneously. The attack can cause a huge power outage in large parts of Europe.
According to a research conducted by Westerhof, vulnerable solar panels manage around 17 gigawatts of power, clearly, a successful cyber attack could have a catastrophic effect.
Volkskrant reports that in 2006, more than 10 million people were left in the dark after a power shortage in Germany triggered blackouts across western Europe late Saturday night. Many capital cities were affected by the outage, including Paris and Madrid spent hours without power because of that incident.
The German power grid had to deal with a five-gigawatt shortage, while the attack scenario presented by Westerhof could cause a 17-gigawatt shortage, more than three times greater.
SMA explained that the inverters are properly secured and the company told Volkskrant’s journalists that the vulnerabilities only affect a limited range of products. The manufacturer also confirmed that its engineers are working on technical corrections.
Inverters of solar panels are just an example of the billion of IoT devices that could be targeted by hackers. Solar panels are becoming ever more widespread, it is neccssary to solve the issued as soon as possible.
US Army bans use of Chinese DJI drones over cyber security concerns
7.8.2017 securityaffairs BigBrothers
The US Army has ordered its units to stop using Chinese DJI drones because of “cyber vulnerabilities” in the products.
The US Army is going to ban its units from using drones manufactured by the Chinese firm DJI due to “cyber vulnerabilities”.
The decision was based on the findings of a research conducted by the Army Research Laboratory and the navy that discovered vulnerabilities in DJI products.
A memo issued by the US Army’s Lieutenant General Joseph Anderson orders all US Army units that are currently employing DJI drones to stop using them.
DJI (Da-Jiang Innovation Corporation) is a Chinese firm based in Shenzhen, Goldman Sachs and Oppenheimer estimated in 2016 that DJI had about 70 percent share of the global commercial and consumer drone market.
In the memo, soldiers are also ordered to remove all batteries and storage media from their DJI drones and await further instructions.
“Due to increased awareness of cyber vulnerabilities associated with DJI products, it is directed that the US Army halt use of all DJI products,” states the memo.
DJI disappointed to read about the alleged ban of the US Army of using DJI drones.

DJI’s Public Relations Manager, Michael Perry, sent the following email to sUAS News:
“We are surprised and disappointed to read reports of the U.S. Army’s unprompted restriction on DJI drones as we were not consulted during their decision. We are happy to work directly with any organization, including the U.S. Army, that has concerns about our management of cyber issues.”
“We’ll be reaching out to the U.S. Army to confirm the memo and to understand what is specifically meant by ‘cyber vulnerabilities’.”
A U.S. Army spokesperson confirmed that the memo was issued and added that they are currently reviewing it.
The DJI made the headlines in April 2016 when the company received the pressure of the Chinese government to gain access to the data collected by its drones, included telemetry, GPS location data, flight records and possibly video shot by users and uploaded to its servers.
WannaCry Hero Marcus Hutchins pleads not guilty to malware claims
5.8.2017 securityaffairs Ransomware
Yesterday the judge approved to release the researcher Marcus Hutchins on bail for a bond of $30,000 under certain conditions.
Marcus Hutchins, also known as MalwareTech, is the 22-year-old security expert who made the headlines after discovering the “kill switch” that halted the outbreak of the WannaCry ransomware. Marcus Hutchins has been arrested in in Las Vegas after attending the Def Con hacking conference and was detained by the FBI in the state of Nevada.
The British security researcher was arrested on Thursday after being indicted on charges of creating the Kronos banking malware.
According to the investigators, Marcus Hutchins created the malware and shared it online, below the indictment issued by Eastern District of Wisconsin.
The prosecutors believe Hutchins created, shared, and masterminded the Kronos banking Trojan between July 2014 and July 2015.

On Friday, at 3pm Pacific Time, the young malware expert appeared before a judge, pleaded not guilty to the charges against him. The judge approved to release the researcher on bail for a bond of $30,000 under certain conditions.
MalwareTech is prohibited from accessing the Internet, he must wear a GPS tracker, and he cannot contact the unnamed co-defendant mentioned in the FBI’s indictment.
Unfortunately, even though that hearing finished at 3.30pm, Hutchins was not able to get to the bail office in time as it closes at 4pm, so he will spend the weekend in jail.
On Tuesday he will appear before a judge in Wisconsin for his next court appearance.
“He’s dedicated his life to researching malware and not trying to harm people,” said one of Hutchins attorneys, Adrian Lobo. “Using the internet for good is what he’s done.”
Lobo explained to the journalists that Hutchins was able to raise bail money from his supporters.
The US Department of Justice prosecutors mentioned a recent trip of the expert to a gun range as proof that he should be denied bail and kept in jail. Lobo defined the prosecution’s proposal as “garbage.”
Hutchins’ lawyers clarified the expert is not in any way behind the Kronos banking Trojan.
South Korean investigators confirmed National Intelligence Service interference in 2012 election
5.8.2017 securityaffairs BigBrothers
South Korean investigators confirmed that National Intelligence Service attempted to influence 2012 presidential election.
South Korean investigators confirmed that National Intelligence Service (NIS) attempted to manipulate voters to help conservative win parliamentary and presidential elections.
According to the National Intelligence Service (NIS), the Agency conducted a two-years PSYOPs involving up to 30 teams to manipulate the 2012 elections.

The Agency recruited tech-savvy civilians that operated through social media aiming to influence the voter sentiments.
The internal investigation results confirm the scale of the campaign was far wider than previously thought.
“The teams were charged with spreading pro-government opinions and suppressing anti-government views, branding them as pro-North Korean forces’ attempts to disturb state affairs”, reads the statement.
At the time the South Korean leader was the conservative Lee Myung-Bak, and Park Geun-Hye won the presidential election in December 2012 defeating liberal Moon Jae-In.
Park was impeached and dismissed over corruption and abuse of power, the prosecutors accused Park of colluding with Choi Soon-sil to pressure major South Korean companies such as Samsung into paying tens of millions of dollars in bribes in return for business favors.
Moon won South Korea presidential election in May, he started a reform of the National Intelligence Service and ordered a supplementary effort in gathering intelligence on North Korea and foreign affairs.
A spokesman for Park’s party, the Liberty Korea, declared the inquiry was “politically motivated”.
“The NIS says it will dissociate itself from politics but it is meddling in politics again by starting this probe,” Kang Hyo-Sang said in a statement.
The internal probe found former NIS chief Won Sei-Hoon orchestrated a campaign against Moon, muzzling the press and supporting pro-government conservative civic groups. The agency also spied on major opposition politicians.
The NIS was also accused of building a false spying case against a former Seoul city official who had escaped to South Korea from the North in 2004.
Wannacry authors make a $143,000 withdraw from Bitcoin wallets, whilst the internet is distracted!
5.8.2017 securityaffairs Ransomware
On Wednesday some very interesting and seemly unrelated events happened in regards to Wannacry. First Marcus Hutchins (AKA @Malwaretech), the security researcher who discovered the kill switch and stopped the spread of Wannacry was arrested whilst returning to the UK from Las Vegas- on suspicion of creating malware (covered here).
But the second event which will be covered in the article related to an event that seemed to of passed most of Twitter and the internet by. The WannaCry wallets from the orchestrators behind the ransomware outbreak (that famously affected companies globally including the NHS), were emptied to the tune of $143,000. Interestingly the Bitcoin generated through ransom payments from the global attack had not been touched until Wednesday.
A twitter bot created by Quartz, to monitor the wallets for payments during the original outbreak, first noticed the activity at 11:10pm ET, according to the twitter account a total of $70,000 was withdrawn from the following three transactions:
7.34128314 BTC ($20,055.52 USD) has just been withdrawn from a bitcoin wallet tied to #wcry ransomware. https://t.co/wX2k9pJLNQ
— actual ransom (@actual_ransom) August 3, 2017
8.73261636 BTC ($23,856.48 USD) has just been withdrawn from a bitcoin wallet tied to #wcry ransomware. https://t.co/KRxgNpBGgz
— actual ransom (@actual_ransom) August 3, 2017
9.67641378 BTC ($26,434.83 USD) has just been withdrawn from a bitcoin wallet tied to #wcry ransomware. https://t.co/CJLiu6cyvr
— actual ransom (@actual_ransom) August 3, 2017
Source QZ.com
The twitter bot the reported only 15 minutes later that the remainder of the monies were moved from the Bitcoin wallets, it is highly likely that these were laundered using a mixing service making it very hard to track the source and destination of the payments through making a high volume of small transactions to a large number of wallets.

Given the orchestrators of the Wannacry outbreak is widely suspected to be the Lazarus Group which have connections to North Korea, the timing and motivation of the BTC exfiltration could be a dig towards Marcus Hutchins, who stopped the spread of the attack, or just a coincidence, at this juncture there is no evidence to call it either way.
But it is also known that Lazarus, in particular, Bluenoroff are a financially motivated group, with the attacks on banks, financial, and trading companies in Bangladesh in 2014 and the now famous $81million Cyber-Heist of the Bangladesh central bank’s account at the Federal Reserve Bank of New York.
In summary, with the attackers behind Wannacry and NotPetya thought by many not to be financially motivated, it seems that even they still could not resist the opportunity to silently move their ill-gotten gains, whist the internet was distracted by other events!
Microsoft Attempts To Fix Stuxnet For The Third Time
5.8.2017 securityaffairs Vulnerebility
Microsoft released a new security update on June 17th in an attempt to patch a vulnerability which allowed the Stuxnet Virus to exploit Windows systems.
The Stuxnet Virus which attacks Industrial Control Systems was first discovered in 2010 when it infected Iranian Programmable Logic Controllers. Stuxnet compromises controllers by first targeting Windows operating systems and networks. Propagating through infected Windows machines it locates Siemens software used to manage controllers. Stuxnet then collects information on the systems and in the case of the Iranian centrifuges caused them to malfunction, destroying the nuclear material they were enriching.

Attempts by Microsoft to fix the vulnerability did not address how LNK files use attributes to identify folder location. Microsoft’s explanation states LNK files were able to bypass the fix, resulting in a previously an unexpected vulnerability.
Affected Versions include:
Microsoft Windows 10 Version 1607 for 32-bit Systems
Microsoft Windows 10 Version 1607 for x64-based Systems
Microsoft Windows 10 for 32-bit Systems
Microsoft Windows 10 for x64-based Systems
Microsoft Windows 10 version 1511 for 32-bit Systems
Microsoft Windows 10 version 1511 for x64-based Systems
Microsoft Windows 10 version 1703 for 32-bit Systems
Microsoft Windows 10 version 1703 for x64-based Systems
Microsoft Windows 7 for 32-bit Systems SP1
Microsoft Windows 7 for x64-based Systems SP1
Microsoft Windows 8.1 for 32-bit Systems
Microsoft Windows 8.1 for x64-based Systems
Microsoft Windows RT 8.1
Microsoft Windows Server 2008 R2 for Itanium-based Systems SP1
Microsoft Windows Server 2008 R2 for x64-based Systems SP1
Microsoft Windows Server 2008 for 32-bit Systems SP2
Microsoft Windows Server 2008 for Itanium-based Systems SP2
Microsoft Windows Server 2008 for x64-based Systems SP2
Microsoft Windows Server 2012
Microsoft Windows Server 2012 R2
Microsoft Windows Server 2016
Discovering Microsoft’s two previous attempts to fix the vulnerability had failed Microsoft released the June patch to address vulnerability CVE-2017-8464. Microsoft confirmed that the flaw had been exploited in the wild. Exploits for the vulnerability are currently available for Metasploit, with videos available on Youtube on how to exploit the vulnerability.
According to an advisory published by the CERT Coordination Center at Carnegie Mellon University, hackers already know another method for bypassing Microsoft’s patches for the above issue.
“The fix for CVE-2010-2568 and the subsequent fix for CVE-2015-0096 are both insufficient in that they not take into account LNK files that use the SpecialFolderDataBlock or KnownFolderDataBlock attributes to specify the location of a folder. Such files are able to bypass the whitelisting first implemented in the fix for CVE-2010-2568,” CERT/CC said in its advisory.
“By convincing a user to display a specially-crafted shortcut file, an attacker may be able to execute arbitrary code with the privileges of the user. Depending on the operating system and AutoRun/AutoPlay configuration, this can happen automatically by connecting a USB device,”
Additional steps can be taken to prevent the exploitation of this vulnerability by blocking outgoing connections on TCP and UDP ports 139 and 445.
Hacker, který porazil celosvětový vir WannaCry, si před zatčením dopřával pohádkový luxus
4.8.2017 Novinky/Bezpečnost Kriminalita
Třiadvacetiletý americký hacker Marcus Hutchins, který zastavil celosvětové šíření počítačového viru WannaCry, ale hrozí mu 40 let žaláře za jiné „aktivity“, si před dopadením v Las Vegas žil na vysoké noze. Pronajal si dům za v přepočtu téměř 150 miliónů korun, jezdil v Lamborghini a obrážel bujaré večírky. Ve čtvrtek ale jízda skončila.
Hacker Marcus Hutchins
FOTO: Frank Augstein, ČTK/AP
Dnes 19:27 - Las Vegas
Hutchinse zadrželi ve čtvrtek ve VIP salónku letiště Las Vegas. Chystal se odtamtud vrátit do Devonu v rodné Británii, kde žije se svými rodiči. Ve Vegas byl týden.
Účastnil se tam každoročního sjezdu hackerů z celého světa. Kromě toho ale podle listu The Daily Mail flámoval. Když si zrovna Hutchins neužíval na večírku nebo nevyspával kocovinu, relaxoval u bazénu pronajaté vily. Ten je vůbec největším soukromým bazénem v Las Vegas.
3 Aug
William Turton ✔ @WilliamTurton
Before being nabbed by the FBI, famed security researcher was spending big in Las Vegas https://theoutline.com/post/2054/the-wannacry-hacker-hero-was-spending-big-in-vegas-before-his-arrest …
Follow
William Turton ✔@WilliamTurton
Hutchins and friends were staying in a $1,900 a night mansion with "the biggest private pool in Las Vegas." https://theoutline.com/post/2054/the-wannacry-hacker-hero-was-spending-big-in-vegas-before-his-arrest … pic.twitter.com/C0yR0ztLpo
9:21 PM - Aug 3, 2017
12 12 Replies 8 8 Retweets 14 14 likes
Twitter Ads info and privacy
Přebytečnou energii si jezdil vybít pronajatým Lamborghini Huracán v hodnotě v přepočtu 5,8 miliónu korun na střelnici.
Měl mít na kontě šest trojských koňů
Americká FBI mladého počítačového experta viní z vývoje hned šesti trojských koňů, tedy škodlivých programů, které jsou schopny mimo jiné odcizit uživatelská jména a hesla pro přihlašování do informačních systémů.
Jeden z malwarů, nazývaný, Kronos, byl podle FBI zodpovědný za krádeže z bankovních účtů ve Francii. Hutchins měl škodlivý kód napsat a druhý obviněný, jehož identitu úřady nezveřejnily, ho měl prodat. Hackerská komunita stojí za Hutchinsem a tvrdí, že jde o vykonstruované obvinění.
Hacker Sentenced to 46 Months in Prison for Spreading Linux Malware
4.8.2017 thehackernews Virus
A Russian man accused of infecting tens of thousands of computer servers worldwide to generate millions in fraudulent payments has been imprisoned for 46 months (nearly four years) in a United States' federal prison.
41-year-old Maxim Senakh, of Velikii Novgorod, was arrested by Finnish police in August 2015 for his role in the development and maintenance of the infamous Linux botnet called Ebury that siphoned millions of dollars from victims worldwide.
Senakh was extradited to the United States in February 2016 to face charges and pleaded guilty in late March this year after admitting of creating a massive Ebury botnet and personally being profited from the scheme.
First spotted in 2011, Ebury is an SSH backdoor Trojan for Linux and Unix-style operating systems, such as FreeBSD or Solaris, which gives attackers full shell control of an infected machine remotely even if the password for affected user account is changed regularly.
Senakh and his associates used the malware to build an Ebury botnet network of thousands of compromised Linux systems, which had the capacity of sending over 35 million spam messages and redirecting more than 500,000 online visitors to exploit kits every day.
Senakh fraudulently generated millions of dollars in revenue running spam campaigns and committing advertising click frauds.
"Working within a massive criminal enterprise, Maxim Senakh helped create a sophisticated infrastructure that victimized thousands of Internet users across the world," said Acting U.S. Attorney Brooker.
"As society becomes more reliant on computers, cyber criminals like Senakh pose a serious threat. This Office, along with our law enforcement partners, is committed to detecting and prosecuting cyber criminals no matter where they reside."
Ebury first came into headlines in 2011 after Donald Ryan Austin, 27, of El Portal, Florida, installed the Trojan on multiple servers owned by kernel.org and the Linux Foundation, which maintain and distribute the Linux operating system kernel.
Austin, with no connection to the Ebury criminal gang, was arrested in September last year and was charged with 4 counts of intentional transmission causing damage to a protected computer.
Linux-malware-backdoor
Senakh was facing up to a combined 30 years in prison, after pleading guilty to conspiracy to commit wire fraud as well as violate the Computer Fraud and Abuse Act.
However, a US judge on Thursday sentenced Senakh to 46 months in prison, the Department of Justice announced on Thursday. The case was investigated by the Federal Bureau of Investigation's field office in Minneapolis.
Senakh will be deported back to Russia following his release from the U.S. prison.
Arrest Shines Light on Shadowy Community of Good, Bad Hackers
4.8.2017 securityweek Hacking
Two months ago, Marcus Hutchins was an "accidental hero," a young computer whiz living with his parents in Britain who found the "kill switch" to the devastating WannaCry ransomware.
Today, the 23-year-old is in a US federal prison, charged with creating and distributing malicious software designed to attack the banking system.
His arrest this week stunned the computer security community and shines a light on the shadowy world of those who sometimes straddle the line between legal and illegal activities.
Hutchins' arrest following Def Con in Las Vegas, one of the world's largest gathering of hackers, delivered "an extreme shock," according to Gabriella Coleman, a McGill University professor who studies the hacker community.
"The community at Def Con would not admire a hacker who was doing hard core criminal activity for profit or damage -- that is frowned upon," Coleman told AFP.
"But there are people who do security research... who understand that sometimes in order to improve security, you have to stick your nose in areas that may break the law. They don't want to hurt anyone but they are doing it for research."
Hackers are generally classified as "white hats" if they stay within the law and "black hats" if they cross the line.
At gatherings like Def Con, "you have people who dabble on both sides of the fence," said Rick Holland, vice president at the security firm Digital Shadows.
An indictment unsealed by US authorities charges Hutchins and a second individual -- whose name was redacted -- of making and distributing in 2014 and 2015 the Kronos "banking Trojan," a reference to malicious software designed to steal user names and passwords used at online banking sites.
- Hacker mindset -
James Scott, a senior fellow who follows cybersecurity at the Institute for Critical Infrastructure Technology, said it is sometimes difficult to separate the white hats from the black hats.
The hacker mindset includes "an insatiable need to satisfy their intellectual curiosity," Scott said.
"Hackers have that thing, they can't sleep. It's persistent and it's constant and it can drive you nuts."
Scott said he did not know details of the Hutchins case but that it is possible he wrote code that someone else "weaponized."
Some friends and collaborators of Hutchins said they found the allegations hard to believe.
"He worked with me on a project in 2014 he refused payment for," said a tweet from Jake Williams of Rendition InfoSec. "This is incongruous with a black hat writing code for money at the same time."
Security researcher Andrew Mabbitt tweeted that Hutchins "spent his career stopping malware, not writing it."
- Chilling effect -
Regardless of the outcome of the case, some security professionals said the arrest could erode trust between the hacker community and law enforcement.
Coleman said many hackers and researchers already tread carefully in light of the Computer Fraud and Abuse Act, a law that makes it illegal to access a computer system without authorization and has been roundly criticized by some security professionals.
"The statute is very broad and it can be wielded as a tool against researchers," Coleman said.
She noted that many in the hacker community are still reeling over the 2013 suicide of activist Aaron Swartz, who was charged under the same law for illegally downloading academic journals.
Hutchins' arrest "might actually drive certain security researchers further underground," said John Dickson of Denim Group, a security consultancy.
"I know several security researchers from Europe, whom I consider on the 'white hat' side of the house, who will no longer travel to the US to be on the safe side."
Holland of Digital Shadows added that it may lead to "strains in the security community, and it could make people more circumspect about who they may collaborate with."
Scott said the arrest may be counterproductive for cybersecurity because hackers like Hutchins help expose security flaws in order to fix them.
"The establishment needs hackers more than hackers need the establishment," he said.
Scott added that Hutchins' obvious talents could make him an asset for national security instead of a liability.
"I wouldn't be surprised if a federal agency made him an offer he can't refuse," Scott said.
"A guy like that should be at Fort Meade," he added, referring to the headquarters of the National Security Agency.
South Korea Spy Agency Admits Attempting to Rig Election
4.8.2017 securityweek BigBrothers
South Korea's spy agency has admitted that it had engaged in a far-reaching attempt to manipulate voters as it sought to help conservatives win parliamentary and presidential elections.
In-house investigators from the National Intelligence Service (NIS) confirmed that the agency's cyber warfare unit organised and operated up to 30 teams for more than two years in the run-up to the 2012 elections, the agency said in a statement late Thursday.
They hired internet-savvy civilians and sought to sway voter opinions through postings on portals and Twitter.
"The teams were charged with spreading pro-government opinions and suppressing anti-government views, branding them as pro-North Korean forces' attempts to disturb state affairs", it said.
At the time the country was led by the conservative Lee Myung-Bak, and in the event the December 2012 presidential election was won by his now-disgraced colleague Park Geun-Hye, who defeated liberal Moon Jae-In.
Moon won South Korea's presidential vote in May this year after Park was impeached and dismissed over corruption and abuse of power, and ordered an investigation.
He has vowed to reform the NIS to prevent it meddling in elections and make it focus on collecting and analysing intelligence on North Korea and foreign affairs.
A spokesman for Park's party, now in opposition and renamed Liberty Korea, said Friday the inquiry was "politically motivated".
"The NIS says it will dissociate itself from politics but it is meddling in politics again by starting this probe," Kang Hyo-Sang said in a statement.
Former NIS chief Won Sei-Hoon is being tried for the second time for leading an online smear campaign against Moon, after his initial conviction was overturned on appeal.
But the NIS investigation results suggest the scale of the voter manipulation was far wider than previously thought.
The internal probe also found Won ordered the agency to muzzle the press, provide support for pro-government conservative civic groups and put some major opposition politicians under secret surveillance.
The modern-day NIS has been tainted by a series of scandals, including the forging of documents to build a false spying case against a former Seoul city official who had escaped to South Korea from the North in 2004.